#serverless data analytics
Explore tagged Tumblr posts
Text
0 notes
Text
Business Intelligence Solutions: Unleashing the Power of Managed Analytics

In today's dynamic business landscape, the effective utilization of data is pivotal for informed decision-making and sustained growth. Business Intelligence (BI) solutions have emerged as a cornerstone, offering organizations the ability to glean actionable insights from their data. This article explores the transformative impact of BI solutions and how managed analytics, coupled with outsourced IT management, is reshaping the way businesses harness the power of data.
1. Proactive IT Support and Managed IT Services:
BI solutions thrive in an environment supported by proactive IT services. Managed IT services, which include proactive support and maintenance, ensure the seamless operation of BI tools. This proactive approach not only enhances the reliability of analytics but also minimizes downtime, allowing businesses to make real-time decisions.
2. Advanced Analytics and Data Visualization Services:
Managed analytics encompass advanced analytics services that go beyond basic reporting. Data visualization services play a crucial role, translating complex data sets into visually appealing and understandable insights. This facilitates better communication and comprehension of data-driven findings across all levels of an organization.
3. Cloud Management Solutions and Migration Strategies:
The integration of cloud management solutions is a game-changer for BI. Cloud migration solutions offer scalability, flexibility, and cost-efficiency. Managed BI services leverage cloud optimization solutions, ensuring that businesses make the most of cloud resources while maintaining peak performance.
4. Data Science Solutions and Hybrid Cloud Integration:
BI solutions often involve intricate data science methodologies. Managed analytics extend to data science solutions, enabling organizations to employ predictive analytics and machine learning for more accurate forecasting. Hybrid cloud solutions provide the necessary infrastructure for hosting and processing data across different environments securely.
5. IT Consultation Services and Strategic Managed Services:
Strategic IT consultation services are instrumental in aligning BI strategies with overall business objectives. Managed services, including serverless computing and big data consulting, are designed to optimize the performance of BI tools, ensuring they adapt to evolving business requirements.
6. Cloud Consulting Services and Holistic Cloud Management:
BI solutions benefit from specialized cloud consulting services. These services guide organizations in selecting the most suitable cloud platforms and architectures for their BI needs. Holistic cloud management services oversee the entire cloud ecosystem, ensuring optimal performance and security.
In conclusion, the convergence of BI solutions and managed analytics is reshaping the way businesses interpret and leverage their data. With the right blend of outsourced IT management, advanced analytics, and cloud solutions, organizations can unlock the full potential of their data, gaining a competitive edge in today's data-driven era.
#it consultation services#managed service#serverless computing#big data consulting#business intelligence solutions#Scholarnest#Scholarnest Technologies#cloud consulting services#cloud management#cloud management services#data visualization services#managed it services#advanced analytics services#cloud management solution#cloud migration solutions#cloud optimization solutions#data science solutions#hybrid cloud solutions#outsourced it management#proactive it support
0 notes
Text
#AI#BigData#CloudComputing#DataAnalytics#DataPlatforms#DataScience#IoT#IIoT#PyTorch#Python#RStats#TensorFlow#Java#JavaScript#ReactJS#GoLang#Serverless#4 types of data analytics#analytics#aws iot analytics#big data#big data analytics#data analysis#data analytics#data analytics career#data analytics job#data analytics project#data analytics roadmap#data analytics trends#data handling in iot
0 notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text
Exploring the Azure Technology Stack: A Solution Architect’s Journey
Kavin
As a solution architect, my career revolves around solving complex problems and designing systems that are scalable, secure, and efficient. The rise of cloud computing has transformed the way we think about technology, and Microsoft Azure has been at the forefront of this evolution. With its diverse and powerful technology stack, Azure offers endless possibilities for businesses and developers alike. My journey with Azure began with Microsoft Azure training online, which not only deepened my understanding of cloud concepts but also helped me unlock the potential of Azure’s ecosystem.
In this blog, I will share my experience working with a specific Azure technology stack that has proven to be transformative in various projects. This stack primarily focuses on serverless computing, container orchestration, DevOps integration, and globally distributed data management. Let’s dive into how these components come together to create robust solutions for modern business challenges.

Understanding the Azure Ecosystem
Azure’s ecosystem is vast, encompassing services that cater to infrastructure, application development, analytics, machine learning, and more. For this blog, I will focus on a specific stack that includes:
Azure Functions for serverless computing.
Azure Kubernetes Service (AKS) for container orchestration.
Azure DevOps for streamlined development and deployment.
Azure Cosmos DB for globally distributed, scalable data storage.
Each of these services has unique strengths, and when used together, they form a powerful foundation for building modern, cloud-native applications.
1. Azure Functions: Embracing Serverless Architecture
Serverless computing has redefined how we build and deploy applications. With Azure Functions, developers can focus on writing code without worrying about managing infrastructure. Azure Functions supports multiple programming languages and offers seamless integration with other Azure services.
Real-World Application
In one of my projects, we needed to process real-time data from IoT devices deployed across multiple locations. Azure Functions was the perfect choice for this task. By integrating Azure Functions with Azure Event Hubs, we were able to create an event-driven architecture that processed millions of events daily. The serverless nature of Azure Functions allowed us to scale dynamically based on workload, ensuring cost-efficiency and high performance.
Key Benefits:
Auto-scaling: Automatically adjusts to handle workload variations.
Cost-effective: Pay only for the resources consumed during function execution.
Integration-ready: Easily connects with services like Logic Apps, Event Grid, and API Management.
2. Azure Kubernetes Service (AKS): The Power of Containers
Containers have become the backbone of modern application development, and Azure Kubernetes Service (AKS) simplifies container orchestration. AKS provides a managed Kubernetes environment, making it easier to deploy, manage, and scale containerized applications.
Real-World Application
In a project for a healthcare client, we built a microservices architecture using AKS. Each service—such as patient records, appointment scheduling, and billing—was containerized and deployed on AKS. This approach provided several advantages:
Isolation: Each service operated independently, improving fault tolerance.
Scalability: AKS scaled specific services based on demand, optimizing resource usage.
Observability: Using Azure Monitor, we gained deep insights into application performance and quickly resolved issues.
The integration of AKS with Azure DevOps further streamlined our CI/CD pipelines, enabling rapid deployment and updates without downtime.
Key Benefits:
Managed Kubernetes: Reduces operational overhead with automated updates and patching.
Multi-region support: Enables global application deployments.
Built-in security: Integrates with Azure Active Directory and offers role-based access control (RBAC).
3. Azure DevOps: Streamlining Development Workflows
Azure DevOps is an all-in-one platform for managing development workflows, from planning to deployment. It includes tools like Azure Repos, Azure Pipelines, and Azure Artifacts, which support collaboration and automation.
Real-World Application
For an e-commerce client, we used Azure DevOps to establish an efficient CI/CD pipeline. The project involved multiple teams working on front-end, back-end, and database components. Azure DevOps provided:
Version control: Using Azure Repos for centralized code management.
Automated pipelines: Azure Pipelines for building, testing, and deploying code.
Artifact management: Storing dependencies in Azure Artifacts for seamless integration.
The result? Deployment cycles that previously took weeks were reduced to just a few hours, enabling faster time-to-market and improved customer satisfaction.
Key Benefits:
End-to-end integration: Unifies tools for seamless development and deployment.
Scalability: Supports projects of all sizes, from startups to enterprises.
Collaboration: Facilitates team communication with built-in dashboards and tracking.

4. Azure Cosmos DB: Global Data at Scale
Azure Cosmos DB is a globally distributed, multi-model database service designed for mission-critical applications. It guarantees low latency, high availability, and scalability, making it ideal for applications requiring real-time data access across multiple regions.
Real-World Application
In a project for a financial services company, we used Azure Cosmos DB to manage transaction data across multiple continents. The database’s multi-region replication ensure data consistency and availability, even during regional outages. Additionally, Cosmos DB’s support for multiple APIs (SQL, MongoDB, Cassandra, etc.) allowed us to integrate seamlessly with existing systems.
Key Benefits:
Global distribution: Data is replicated across regions with minimal latency.
Flexibility: Supports various data models, including key-value, document, and graph.
SLAs: Offers industry-leading SLAs for availability, throughput, and latency.
Building a Cohesive Solution
Combining these Azure services creates a technology stack that is flexible, scalable, and efficient. Here’s how they work together in a hypothetical solution:
Data Ingestion: IoT devices send data to Azure Event Hubs.
Processing: Azure Functions processes the data in real-time.
Storage: Processed data is stored in Azure Cosmos DB for global access.
Application Logic: Containerized microservices run on AKS, providing APIs for accessing and manipulating data.
Deployment: Azure DevOps manages the CI/CD pipeline, ensuring seamless updates to the application.
This architecture demonstrates how Azure’s technology stack can address modern business challenges while maintaining high performance and reliability.
Final Thoughts
My journey with Azure has been both rewarding and transformative. The training I received at ACTE Institute provided me with a strong foundation to explore Azure’s capabilities and apply them effectively in real-world scenarios. For those new to cloud computing, I recommend starting with a solid training program that offers hands-on experience and practical insights.
As the demand for cloud professionals continues to grow, specializing in Azure’s technology stack can open doors to exciting opportunities. If you’re based in Hyderabad or prefer online learning, consider enrolling in Microsoft Azure training in Hyderabad to kickstart your journey.
Azure’s ecosystem is continuously evolving, offering new tools and features to address emerging challenges. By staying committed to learning and experimenting, we can harness the full potential of this powerful platform and drive innovation in every project we undertake.
#cybersecurity#database#marketingstrategy#digitalmarketing#adtech#artificialintelligence#machinelearning#ai
2 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Aible And Google Cloud: Gen AI Models Sets Business Security
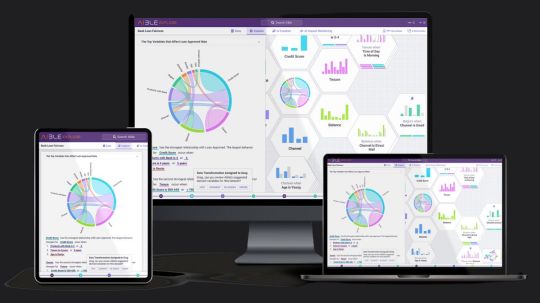
Enterprise controls and generative AI for business users in real time.
Aible
With solutions for customer acquisition, churn avoidance, demand prediction, preventive maintenance, and more, Aible is a pioneer in producing business impact from AI in less than 30 days. Teams can use AI to extract company value from raw enterprise data. Previously using BigQuery’s serverless architecture to save analytics costs, Aible is now working with Google Cloud to provide users the confidence and security to create, train, and implement generative AI models on their own data.
The following important factors have surfaced as market awareness of generative AI’s potential grows:
Enabling enterprise-grade control
Businesses want to utilize their corporate data to allow new AI experiences, but they also want to make sure they have control over their data to prevent unintentional usage of it to train AI models.
Reducing and preventing hallucinations
The possibility that models may produce illogical or non-factual information is another particular danger associated with general artificial intelligence.
Empowering business users
Enabling and empowering business people to utilize gen AI models with the least amount of hassle is one of the most beneficial use cases, even if gen AI supports many enterprise use cases.
Scaling use cases for gen AI
Businesses need a method for gathering and implementing their most promising use cases at scale, as well as for establishing standardized best practices and controls.
Regarding data privacy, policy, and regulatory compliance, the majority of enterprises have a low risk tolerance. However, given its potential to drive change, they do not see postponing the deployment of Gen AI as a feasible solution to market and competitive challenges. As a consequence, Aible sought an AI strategy that would protect client data while enabling a broad range of corporate users to swiftly adapt to a fast changing environment.
In order to provide clients complete control over how their data is used and accessed while creating, training, or optimizing AI models, Aible chose to utilize Vertex AI, Google Cloud’s AI platform.
Enabling enterprise-grade controls
Because of Google Cloud’s design methodology, users don’t need to take any more steps to ensure that their data is safe from day one. Google Cloud tenant projects immediately benefit from security and privacy thanks to Google AI products and services. For example, protected customer data in Cloud Storage may be accessed and used by Vertex AI Agent Builder, Enterprise Search, and Conversation AI. Customer-managed encryption keys (CMEK) can be used to further safeguard this data.
With Aible‘s Infrastructure as Code methodology, you can quickly incorporate all of Google Cloud’s advantages into your own applications. Whether you choose open models like LLama or Gemma, third-party models like Anthropic and Cohere, or Google gen AI models like Gemini, the whole experience is fully protected in the Vertex AI Model Garden.
In order to create a system that may activate third-party gen AI models without disclosing private data outside of Google Cloud, Aible additionally collaborated with its client advisory council, which consists of Fortune 100 organizations. Aible merely transmits high-level statistics on clusters which may be hidden if necessary instead of raw data to an external model. For instance, rather of transmitting raw sales data, it may communicate counts and averages depending on product or area.
This makes use of k-anonymity, a privacy approach that protects data privacy by never disclosing information about groups of people smaller than k. You may alter the default value of k; the more private the information transmission, the higher the k value. Aible makes the data transmission even more secure by changing the names of variables like “Country” to “Variable A” and values like “Italy” to “Value X” when masking is used.
Mitigating hallucination risk
It’s crucial to use grounding, retrieval augmented generation (RAG), and other strategies to lessen and lower the likelihood of hallucinations while employing gen AI. Aible, a partner of Built with Google Cloud AI, offers automated analysis to support human-in-the-loop review procedures, giving human specialists the right tools that can outperform manual labor.
Using its auto-generated Information Model (IM), an explainable AI that verifies facts based on the context contained in your structured corporate data at scale and double checks gen AI replies to avoid making incorrect conclusions, is one of the main ways Aible helps eliminate hallucinations.
Hallucinations are addressed in two ways by Aible’s Information Model:
It has been shown that the IM helps lessen hallucinations by grounding gen AI models on a relevant subset of data.
To verify each fact, Aible parses through the outputs of Gen AI and compares them to millions of responses that the Information Model already knows.
This is comparable to Google Cloud’s Vertex AI grounding features, which let you link models to dependable information sources, like as your company’s papers or the Internet, to base replies in certain data sources. A fact that has been automatically verified is shown in blue with the words “If it’s blue, it’s true.” Additionally, you may examine a matching chart created only by the Information Model and verify a certain pattern or variable.
The graphic below illustrates how Aible and Google Cloud collaborate to provide an end-to-end serverless environment that prioritizes artificial intelligence. Aible can analyze datasets of any size since it leverages BigQuery to efficiently analyze and conduct serverless queries across millions of variable combinations. One Fortune 500 client of Aible and Google Cloud, for instance, was able to automatically analyze over 75 datasets, which included 150 million questions and answers with 100 million rows of data. That assessment only cost $80 in total.
Aible may also access Model Garden, which contains Gemini and other top open-source and third-party models, by using Vertex AI. This implies that Aible may use AI models that are not Google-generated while yet enjoying the advantages of extra security measures like masking and k-anonymity.
All of your feedback, reinforcement learning, and Low-Rank Adaptation (LoRA) data are safely stored in your Google Cloud project and are never accessed by Aible.
Read more on Govindhtech.com
#Aible#GenAI#GenAIModels#BusinessSecurity#AI#BigQuery#AImodels#VertexAI#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
AWS Security 101: Protecting Your Cloud Investments
In the ever-evolving landscape of technology, few names resonate as strongly as Amazon.com. This global giant, known for its e-commerce prowess, has a lesser-known but equally influential arm: Amazon Web Services (AWS). AWS is a powerhouse in the world of cloud computing, offering a vast and sophisticated array of services and products. In this comprehensive guide, we'll embark on a journey to explore the facets and features of AWS that make it a driving force for individuals, companies, and organizations seeking to utilise cloud computing to its fullest capacity.

Amazon Web Services (AWS): A Technological Titan
At its core, AWS is a cloud computing platform that empowers users to create, deploy, and manage applications and infrastructure with unparalleled scalability, flexibility, and cost-effectiveness. It's not just a platform; it's a digital transformation enabler. Let's dive deeper into some of the key components and features that define AWS:
1. Compute Services: The Heart of Scalability
AWS boasts services like Amazon EC2 (Elastic Compute Cloud), a scalable virtual server solution, and AWS Lambda for serverless computing. These services provide users with the capability to efficiently run applications and workloads with precision and ease. Whether you need to host a simple website or power a complex data-processing application, AWS's compute services have you covered.
2. Storage Services: Your Data's Secure Haven
In the age of data, storage is paramount. AWS offers a diverse set of storage options. Amazon S3 (Simple Storage Service) caters to scalable object storage needs, while Amazon EBS (Elastic Block Store) is ideal for block storage requirements. For archival purposes, Amazon Glacier is the go-to solution. This comprehensive array of storage choices ensures that diverse storage needs are met, and your data is stored securely.
3. Database Services: Managing Complexity with Ease
AWS provides managed database services that simplify the complexity of database management. Amazon RDS (Relational Database Service) is perfect for relational databases, while Amazon DynamoDB offers a seamless solution for NoSQL databases. Amazon Redshift, on the other hand, caters to data warehousing needs. These services take the headache out of database administration, allowing you to focus on innovation.
4. Networking Services: Building Strong Connections
Network isolation and robust networking capabilities are made easy with Amazon VPC (Virtual Private Cloud). AWS Direct Connect facilitates dedicated network connections, and Amazon Route 53 takes care of DNS services, ensuring that your network needs are comprehensively addressed. In an era where connectivity is king, AWS's networking services rule the realm.
5. Security and Identity: Fortifying the Digital Fortress
In a world where data security is non-negotiable, AWS prioritizes security with services like AWS IAM (Identity and Access Management) for access control and AWS KMS (Key Management Service) for encryption key management. Your data remains fortified, and access is strictly controlled, giving you peace of mind in the digital age.
6. Analytics and Machine Learning: Unleashing the Power of Data
In the era of big data and machine learning, AWS is at the forefront. Services like Amazon EMR (Elastic MapReduce) handle big data processing, while Amazon SageMaker provides the tools for developing and training machine learning models. Your data becomes a strategic asset, and innovation knows no bounds.
7. Application Integration: Seamlessness in Action
AWS fosters seamless application integration with services like Amazon SQS (Simple Queue Service) for message queuing and Amazon SNS (Simple Notification Service) for event-driven communication. Your applications work together harmoniously, creating a cohesive digital ecosystem.
8. Developer Tools: Powering Innovation
AWS equips developers with a suite of powerful tools, including AWS CodeDeploy, AWS CodeCommit, and AWS CodeBuild. These tools simplify software development and deployment processes, allowing your teams to focus on innovation and productivity.
9. Management and Monitoring: Streamlined Resource Control
Effective resource management and monitoring are facilitated by AWS CloudWatch for monitoring and AWS CloudFormation for infrastructure as code (IaC) management. Managing your cloud resources becomes a streamlined and efficient process, reducing operational overhead.
10. Global Reach: Empowering Global Presence
With data centers, known as Availability Zones, scattered across multiple regions worldwide, AWS enables users to deploy applications close to end-users. This results in optimal performance and latency, crucial for global digital operations.

In conclusion, Amazon Web Services (AWS) is not just a cloud computing platform; it's a technological titan that empowers organizations and individuals to harness the full potential of cloud computing. Whether you're an aspiring IT professional looking to build a career in the cloud or a seasoned expert seeking to sharpen your skills, understanding AWS is paramount.
In today's technology-driven landscape, AWS expertise opens doors to endless opportunities. At ACTE Institute, we recognize the transformative power of AWS, and we offer comprehensive training programs to help individuals and organizations master the AWS platform. We are your trusted partner on the journey of continuous learning and professional growth. Embrace AWS, embark on a path of limitless possibilities in the world of technology, and let ACTE Institute be your guiding light. Your potential awaits, and together, we can reach new heights in the ever-evolving world of cloud computing. Welcome to the AWS Advantage, and let's explore the boundless horizons of technology together!
8 notes
·
View notes
Text
Azure Data Engineering Tools For Data Engineers
Azure is a cloud computing platform provided by Microsoft, which presents an extensive array of data engineering tools. These tools serve to assist data engineers in constructing and upholding data systems that possess the qualities of scalability, reliability, and security. Moreover, Azure data engineering tools facilitate the creation and management of data systems that cater to the unique requirements of an organization.
In this article, we will explore nine key Azure data engineering tools that should be in every data engineer’s toolkit. Whether you’re a beginner in data engineering or aiming to enhance your skills, these Azure tools are crucial for your career development.
Microsoft Azure Databricks
Azure Databricks is a managed version of Databricks, a popular data analytics and machine learning platform. It offers one-click installation, faster workflows, and collaborative workspaces for data scientists and engineers. Azure Databricks seamlessly integrates with Azure’s computation and storage resources, making it an excellent choice for collaborative data projects.
Microsoft Azure Data Factory
Microsoft Azure Data Factory (ADF) is a fully-managed, serverless data integration tool designed to handle data at scale. It enables data engineers to acquire, analyze, and process large volumes of data efficiently. ADF supports various use cases, including data engineering, operational data integration, analytics, and data warehousing.
Microsoft Azure Stream Analytics
Azure Stream Analytics is a real-time, complex event-processing engine designed to analyze and process large volumes of fast-streaming data from various sources. It is a critical tool for data engineers dealing with real-time data analysis and processing.
Microsoft Azure Data Lake Storage
Azure Data Lake Storage provides a scalable and secure data lake solution for data scientists, developers, and analysts. It allows organizations to store data of any type and size while supporting low-latency workloads. Data engineers can take advantage of this infrastructure to build and maintain data pipelines. Azure Data Lake Storage also offers enterprise-grade security features for data collaboration.
Microsoft Azure Synapse Analytics
Azure Synapse Analytics is an integrated platform solution that combines data warehousing, data connectors, ETL pipelines, analytics tools, big data scalability, and visualization capabilities. Data engineers can efficiently process data for warehousing and analytics using Synapse Pipelines’ ETL and data integration capabilities.
Microsoft Azure Cosmos DB
Azure Cosmos DB is a fully managed and server-less distributed database service that supports multiple data models, including PostgreSQL, MongoDB, and Apache Cassandra. It offers automatic and immediate scalability, single-digit millisecond reads and writes, and high availability for NoSQL data. Azure Cosmos DB is a versatile tool for data engineers looking to develop high-performance applications.
Microsoft Azure SQL Database
Azure SQL Database is a fully managed and continually updated relational database service in the cloud. It offers native support for services like Azure Functions and Azure App Service, simplifying application development. Data engineers can use Azure SQL Database to handle real-time data ingestion tasks efficiently.
Microsoft Azure MariaDB
Azure Database for MariaDB provides seamless integration with Azure Web Apps and supports popular open-source frameworks and languages like WordPress and Drupal. It offers built-in monitoring, security, automatic backups, and patching at no additional cost.
Microsoft Azure PostgreSQL Database
Azure PostgreSQL Database is a fully managed open-source database service designed to emphasize application innovation rather than database management. It supports various open-source frameworks and languages and offers superior security, performance optimization through AI, and high uptime guarantees.
Whether you’re a novice data engineer or an experienced professional, mastering these Azure data engineering tools is essential for advancing your career in the data-driven world. As technology evolves and data continues to grow, data engineers with expertise in Azure tools are in high demand. Start your journey to becoming a proficient data engineer with these powerful Azure tools and resources.
Unlock the full potential of your data engineering career with Datavalley. As you start your journey to becoming a skilled data engineer, it’s essential to equip yourself with the right tools and knowledge. The Azure data engineering tools we’ve explored in this article are your gateway to effectively managing and using data for impactful insights and decision-making.
To take your data engineering skills to the next level and gain practical, hands-on experience with these tools, we invite you to join the courses at Datavalley. Our comprehensive data engineering courses are designed to provide you with the expertise you need to excel in the dynamic field of data engineering. Whether you’re just starting or looking to advance your career, Datavalley’s courses offer a structured learning path and real-world projects that will set you on the path to success.
Course format:
Subject: Data Engineering Classes: 200 hours of live classes Lectures: 199 lectures Projects: Collaborative projects and mini projects for each module Level: All levels Scholarship: Up to 70% scholarship on this course Interactive activities: labs, quizzes, scenario walk-throughs Placement Assistance: Resume preparation, soft skills training, interview preparation
Subject: DevOps Classes: 180+ hours of live classes Lectures: 300 lectures Projects: Collaborative projects and mini projects for each module Level: All levels Scholarship: Up to 67% scholarship on this course Interactive activities: labs, quizzes, scenario walk-throughs Placement Assistance: Resume preparation, soft skills training, interview preparation
For more details on the Data Engineering courses, visit Datavalley’s official website.
#datavalley#dataexperts#data engineering#data analytics#dataexcellence#data science#power bi#business intelligence#data analytics course#data science course#data engineering course#data engineering training
3 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Build and design multiple types of applications that are cross-language, platform, and cost-effective by understanding core Azure principles and foundational conceptsKey FeaturesGet familiar with the different design patterns available in Microsoft AzureDevelop Azure cloud architecture and a pipeline management systemGet to know the security best practices for your Azure deploymentBook DescriptionThanks to its support for high availability, scalability, security, performance, and disaster recovery, Azure has been widely adopted to create and deploy different types of application with ease. Updated for the latest developments, this third edition of Azure for Architects helps you get to grips with the core concepts of designing serverless architecture, including containers, Kubernetes deployments, and big data solutions.You'll learn how to architect solutions such as serverless functions, you'll discover deployment patterns for containers and Kubernetes, and you'll explore large-scale big data processing using Spark and Databricks. As you advance, you'll implement DevOps using Azure DevOps, work with intelligent solutions using Azure Cognitive Services, and integrate security, high availability, and scalability into each solution. Finally, you'll delve into Azure security concepts such as OAuth, OpenConnect, and managed identities.By the end of this book, you'll have gained the confidence to design intelligent Azure solutions based on containers and serverless functions.What you will learnUnderstand the components of the Azure cloud platformUse cloud design patternsUse enterprise security guidelines for your Azure deploymentDesign and implement serverless and integration solutionsBuild efficient data solutions on AzureUnderstand container services on AzureWho this book is forIf you are a cloud architect, DevOps engineer, or a developer looking to learn about the key architectural aspects of the Azure cloud platform, this book is for you. A basic understanding of the Azure cloud platform will help you grasp the concepts covered in this book more effectively.Table of ContentsGetting started with AzureAzure solution availability, scalability, and monitoringDesign pattern– Networks, storage, messaging, and eventsAutomating architecture on AzureDesigning policies, locks, and tags for Azure deploymentsCost Management for Azure solutionsAzure OLTP solutionsArchitecting secure applications on AzureAzure Big Data solutionsServerless in Azure – Working with Azure FunctionsAzure solutions using Azure Logic Apps, Event Grid, and FunctionsAzure Big Data eventing solutionsIntegrating Azure DevOpsArchitecting Azure Kubernetes solutionsCross-subscription deployments using ARM templatesARM template modular design and implementationDesigning IoT SolutionsAzure Synapse Analytics for architectsArchitecting intelligent solutions ASIN : B08DCKS8QB Publisher : Packt Publishing; 3rd edition (17 July 2020) Language : English File size : 72.0 MB Text-to-Speech : Enabled Screen Reader : Supported Enhanced
typesetting : Enabled X-Ray : Not Enabled Word Wise : Not Enabled Print length : 840 pages [ad_2]
0 notes
Text
Navigate with better data. | AntStack

Integrate data-driven decision-making into your business. Leverage modern and serverless data platforms to make the most of your data and navigate to the future.
#serverless consulting#serverless application development#serverless application#serverless tools#serverless mobile applications#serverless security#AntStack Application Development#serverless data analytics#serverless data engineering#serverless databases
0 notes
Text
Future-Proofing Your Business: The Role of Managed Services in Tech Evolution

In the ever-evolving landscape of technology, businesses are increasingly turning to managed services to stay ahead of the curve and future-proof their operations. As the demands on IT infrastructure grow, leveraging outsourced IT management becomes not just a choice but a strategic necessity. This article explores the pivotal role of managed services in driving tech evolution and ensuring the resilience and agility of your business.
The Foundations of Managed Services:
1. Outsourced IT Management:
Managed IT services involve outsourcing the responsibility for maintaining, anticipating, and managing a company's IT systems. This approach allows businesses to tap into the expertise of external providers, freeing up internal resources to focus on core business functions.
2. Proactive IT Support:
Unlike traditional reactive IT support, managed services operate proactively. Providers actively monitor systems, identify potential issues before they escalate, and implement preventive measures, ensuring a more stable and reliable IT environment.
Advanced Tech Solutions:
3. Data Visualization and Advanced Analytics:
Managed services extend beyond basic IT support, offering specialized solutions such as data visualization and advanced analytics services. This empowers businesses to derive meaningful insights from their data, enabling better decision-making and strategic planning.
4. Cloud Management and Migration Solutions:
Cloud computing is at the forefront of tech evolution, and managed services play a crucial role in facilitating seamless cloud management and migration solutions. Whether it's adopting a hybrid cloud approach or optimizing existing cloud infrastructure, managed services ensure efficient and secure cloud operations.
5. Data Science Solutions:
The integration of data science solutions into managed services allows businesses to harness the power of predictive analytics, machine learning, and artificial intelligence. This not only enhances operational efficiency but also opens avenues for innovation and competitive advantage.
6. Hybrid Cloud Solutions:
Managed services excel in providing hybrid cloud solutions, allowing businesses to balance the benefits of both public and private clouds. This flexibility enables organizations to adapt to changing needs, ensuring optimal performance and scalability.
Strategic IT Consultation:
7. IT Consultation Services:
Managed service providers offer strategic IT consultation services, guiding businesses through technology decisions aligned with their goals. From serverless computing to big data consulting, these consultations ensure that IT infrastructure is not just maintained but strategically aligned with business objectives.
8. Business Intelligence Solutions:
Harnessing business intelligence solutions through managed services enables organizations to turn data into actionable insights. This facilitates informed decision-making, driving efficiencies and fostering a data-driven culture.
9. Cloud Consulting Services:
Cloud adoption is a transformative journey, and managed services provide crucial support through cloud consulting. This includes planning, implementation, and ongoing management, ensuring businesses leverage the full potential of cloud technologies.
The Evolutionary Edge:
10. Cloud Management Services:
As businesses increasingly rely on cloud technologies, managed services offer specialized cloud management services. This includes optimizing resources, ensuring security, and implementing best practices for efficient cloud operations.
In conclusion, future-proofing your business in the rapidly evolving tech landscape necessitates a strategic approach to IT management. Managed services not only provide essential IT support but also act as catalysts for innovation and technological advancement. By embracing outsourced IT management, businesses can tap into a wealth of expertise, leverage advanced tech solutions, and receive strategic guidance, ensuring they are well-prepared for the challenges and opportunities that lie ahead. The future belongs to those who proactively evolve, and managed services are the key to staying ahead of the curve.
#it consultation services#managed service#serverless computing#big data consulting#business intelligence solutions#cloud consulting services#cloud management#cloud management services#data visualization services#managed it services#advanced analytics services#cloud management solution#cloud migration solutions#cloud optimization solutions#data science solutions#hybrid cloud solutions#outsourced it management#proactive it support
1 note
·
View note
Text
#AI#BigData#CloudComputing#DataAnalytics#DataPlatforms#DataScience#IoT#IIoT#PyTorch#Python#RStats#TensorFlow#Java#JavaScript#ReactJS#GoLang#Serverless#4 types of data analytics#analytics#aws iot analytics#big data#big data analytics#data analysis#data analytics#data analytics career#data analytics job#data analytics project#data analytics roadmap#data analytics trends#data handling in iot
0 notes
Text
Getting Started with Cloud-Native Data Processing Using DataStreamX
Transforming Data Streams with Cloudtopiaa’s Real-Time Infrastructure
In today’s data-driven world, the ability to process data in real time is critical for businesses aiming to stay competitive. Whether it’s monitoring IoT devices, analyzing sensor data, or powering intelligent applications, cloud-native data processing has become a game-changer. In this guide, we’ll explore how you can leverage DataStreamX, Cloudtopiaa’s robust data processing engine, for building scalable, real-time systems.
What is Cloud-Native Data Processing?
Cloud-native data processing is an approach where data is collected, processed, and analyzed directly on cloud infrastructure, leveraging the scalability, security, and flexibility of cloud services. This means you can easily manage data pipelines without worrying about physical servers or complex on-premises setups.
Key Benefits of Cloud-Native Data Processing:
Scalability: Easily process data from a few devices to thousands.
Low Latency: Achieve real-time insights without delays.
Cost-Efficiency: Pay only for the resources you use, thanks to serverless cloud technology.
Reliability: Built-in fault tolerance and data redundancy ensure uptime.
Introducing DataStreamX: Real-Time Infrastructure on Cloudtopiaa
DataStreamX is a powerful, low-code, cloud-native data processing engine designed to handle real-time data streams on Cloudtopiaa. It allows businesses to ingest, process, and visualize data in seconds, making it perfect for a wide range of applications:
IoT (Internet of Things) data monitoring
Real-time analytics for smart cities
Edge computing for industrial systems
Event-based automation for smart homes
Core Features of DataStreamX:
Real-Time Processing: Handle continuous data streams without delay.
Serverless Cloud Architecture: No need for complex server management.
Flexible Data Adapters: Connect easily with MQTT, HTTP, APIs, and more.
Scalable Pipelines: Process data from a few devices to thousands seamlessly.
Secure Infrastructure: End-to-end encryption and role-based access control.
Setting Up Your Cloud-Native Data Processing Pipeline
Follow these simple steps to create a data processing pipeline using DataStreamX on Cloudtopiaa:
Step 1: Log into Cloudtopiaa
Visit Cloudtopiaa Platform.
Access the DataStreamX dashboard.
Step 2: Create Your First Data Stream
Choose the type of data stream (e.g., MQTT for IoT data).
Set up your input source (sensors, APIs, cloud storage).
Step 3: Configure Real-Time Processing Rules
Define your processing logic (e.g., filter temperature data above 50°C).
Set triggers for real-time alerts.
Step 4: Visualize Your Data
Use Cloudtopiaa’s dashboard to see real-time data visualizations.
Customize your view with graphs, metrics, and alerts.
Real-World Use Case: Smart Home Temperature Monitoring
Imagine you have a smart home setup with temperature sensors in different rooms. You want to monitor these in real-time and receive alerts if temperatures exceed a safe limit.
Here’s how DataStreamX can help:
Sensors send temperature data to Cloudtopiaa.
DataStreamX processes the data in real-time.
If any sensor records a temperature above the set threshold, an alert is triggered.
The dashboard displays real-time temperature graphs, allowing you to monitor conditions instantly.
Best Practices for Cloud-Native Data Processing
Optimize Data Streams: Only collect and process necessary data.
Use Serverless Architecture: Avoid the hassle of managing servers.
Secure Your Streams: Use role-based access control and encrypted communication.
Visualize for Insight: Build real-time dashboards to monitor data trends.
Why Choose Cloudtopiaa for Real-Time Data Processing?
Cloudtopiaa’s DataStreamX offers a complete solution for cloud-native data processing with:
High Availability: Reliable infrastructure with minimal downtime.
Ease of Use: Low-code interface for quick setup.
Scalability: Seamlessly handle thousands of data streams.
Cost-Effective: Only pay for what you use.
Start Your Cloud-Native Data Journey Today
Ready to transform your data processing with cloud-native technology? With DataStreamX on Cloudtopiaa, you can create powerful, scalable, and secure data pipelines with just a few clicks.
👉 Get started with Cloudtopiaa and DataStreamX now: Cloudtopiaa Platform
#cloudtopiaa#CloudNative#DataProcessing#RealTimeData#Cloudtopiaa#DataStreamX#ServerlessCloud#SmartInfrastructure#EdgeComputing#DataAnalytics#TechInnovation
0 notes
Text
Before the Firewall: EDSPL’s Visionary Approach to Cyber Defense

Unlocking the Future of Cyber Resilience
In a world where digital threats are evolving faster than organizations can respond, traditional security practices no longer suffice. Hackers no longer “try” to break in—they expect to. For companies clinging to outdated protocols, this mindset shift is disastrous.
Enter EDSPL, a name synonymous with forward-thinking in the cybersecurity landscape. With an approach built on foresight, adaptability, and deep-rooted intelligence, EDSPL redefines what it means to defend digital frontiers.
Beyond Perimeters: A New Way to Think About Security
For decades, firewalls were considered the first and final gatekeepers. They filtered traffic, monitored endpoints, and acted as the digital equivalent of a fortress wall. But threats don’t wait at the gates—they worm through weaknesses before rules are written.
EDSPL's strategy doesn’t begin at the wall—it begins before the threat even arrives. By identifying weak links, anticipating behaviors, and neutralizing vulnerabilities at inception, this approach ensures an organization’s shield is active even during peace.
Why Post-Incident Action Isn’t Enough Anymore
Once damage is done, it’s already too late. Breach aftermath includes regulatory penalties, customer churn, operational halts, and irrevocable trust erosion. Traditional solutions operate in reactionary mode—cleaning up after the storm.
EDSPL rewrites that narrative. Rather than waiting to respond, its systems monitor, assess, and simulate threats from day zero. Preparation begins before deployment. Validation precedes integration. Proactive decisions prevent reactive disasters.
A Culture of Vigilance Over a Stack of Tools
Contrary to popular belief, cybersecurity is less about firewalls and more about behaviors. Tools assist. Culture shields. When people recognize risks, companies create invisible armor.
EDSPL’s training modules, custom learning paths, real-time phishing simulations, and scenario-based awareness sessions empower human layers to outperform artificial ones. With aligned mindsets and empowered employees, security becomes instinct—not obligation.
Anticipation Over Analysis: Intelligent Pattern Prediction
Threat actors use sophisticated tools. EDSPL counters with smarter intuition. Through behavioral analytics, intent recognition, and anomaly baselining, the system detects the undetectable.
It isn’t just about noticing malware signatures—it’s about recognizing suspicious deviation before it becomes malicious. This kind of prediction creates time—an extremely scarce cybersecurity asset.
Securing Roots: From Line-of-Code to Cloud-Native Workloads
Security shouldn’t begin with a data center—it should start with developers. Vulnerabilities injected at early stages can linger, mutate, and devastate entire systems.
EDSPL secures code pipelines, CI/CD workflows, container environments, and serverless functions, ensuring no opportunity arises for backdoors. From development to deployment, every node is assessed and authenticated.
Hyper-Personalized Defense Models for Every Sector
What works for healthcare doesn’t apply to fintech. Industrial IoT threats differ from eCommerce risks. EDSPL builds adaptive, context-driven, and industry-aligned architectures tailored to each ecosystem’s pulse.
Whether the organization deals in data-heavy analytics, remote collaboration, or hybrid infrastructure, its security needs are unique—and EDSPL treats them that way.
Decoding Attacks Before They’re Even Launched
Modern adversaries aren’t just coders—they’re strategists. They study networks, mimic trusted behaviors, and exploit unnoticed entry points.
EDSPL’s threat intelligence systems decode attacker motives, monitor dark web activity, and identify evolving tactics before they manifest. From ransomware kits in forums to zero-day exploit chatter, defense begins at reconnaissance.
Unseen Doesn’t Mean Untouched: Internal Risks are Real
While most solutions focus on external invaders, internal risks are often more dangerous. Malicious insiders, negligence, or misconfigurations can compromise years of investment.
Through access control models, least-privilege enforcement, and contextual identity validation, EDSPL ensures that trust isn’t blind—it’s earned at every interaction.
Monitoring That Sees the Forest and Every Leaf
Log dumps don’t equal visibility. Alerts without insight are noise. EDSPL's Security Operations Center (SOC) is built not just to watch, but to understand.
By combining SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation, and Response), and XDR (Extended Detection and Response), the system provides cohesive threat narratives. This means quicker decision-making, sharper resolution, and lower false positives.
Vulnerability Testing That Doesn’t Wait for Schedules
Penetration testing once a year? Too slow. Automated scans every month? Too shallow.
EDSPL uses continuous breach simulation, adversary emulation, and multi-layered red teaming to stress-test defenses constantly. If something fails, it’s discovered internally—before anyone else does.
Compliance That Drives Confidence, Not Just Certification
Security isn’t about ticking boxes—it’s about building confidence with customers, partners, and regulators.
Whether it’s GDPR, HIPAA, PCI DSS, ISO 27001, or industry-specific regulations, EDSPL ensures compliance isn’t reactive. Instead, it’s integrated into every workflow, providing not just legal assurance but brand credibility.
Future-Proofing Through Innovation
Cyber threats don’t rest—and neither does EDSPL.
AI-assisted defense orchestration,
Machine learning-driven anomaly detection,
Quantum-resilient encryption exploration,
Zero Trust architecture implementations,
Cloud-native protection layers (CNAPP),
...are just some innovations currently under development to ensure readiness for challenges yet to come.
Case Study Snapshot: Retail Chain Averted Breach Disaster
A retail enterprise with 200+ outlets reported unusual POS behavior. EDSPL’s pre-deployment monitoring had already detected policy violations at a firmware level. Within hours, code rollback and segmentation stopped a massive compromise.
Customer data remained untouched. Business continued. Brand reputation stayed intact. All because the breach was prevented—before the firewall even came into play.
Zero Trust, Infinite Confidence
No trust is assumed. Every action is verified. Each access request is evaluated in real time. EDSPL implements Zero Trust frameworks not as checklists but as dynamic, evolving ecosystems.
Even internal traffic is interrogated. This approach nullifies lateral movement, halting attackers even if one layer falls.
From Insight to Foresight: Bridging Business and Security
Business leaders often struggle to relate risk to revenue. EDSPL translates vulnerabilities into KPIs, ensuring boardrooms understand what's at stake—and how it's being protected.
Dashboards show more than threats—they show impact, trends, and value creation. This ensures security is not just a cost center but a driver of operational resilience.
Clients Choose EDSPL Because Trust Is Earned
Large manufacturers, healthtech firms, financial institutions, and critical infrastructure providers place their trust in EDSPL—not because of marketing, but because of performance.
Testimonials praise responsiveness, adaptability, and strategic alignment. Long-term partnerships prove that EDSPL delivers not just technology, but transformation.
Please visit our website to know more about this blog https://edspl.net/blog/before-the-firewall-edspl-s-visionary-approach-to-cyber-defence/
0 notes
Text
From Novice to Pro: Master the Cloud with AWS Training!
In today's rapidly evolving technology landscape, cloud computing has emerged as a game-changer, providing businesses with unparalleled flexibility, scalability, and cost-efficiency. Among the various cloud platforms available, Amazon Web Services (AWS) stands out as a leader, offering a comprehensive suite of services and solutions. Whether you are a fresh graduate eager to kickstart your career or a seasoned professional looking to upskill, AWS training can be the gateway to success in the cloud. This article explores the key components of AWS training, the reasons why it is a compelling choice, the promising placement opportunities it brings, and the numerous benefits it offers.

Key Components of AWS Training
1. Foundational Knowledge: Building a Strong Base
AWS training starts by laying a solid foundation of cloud computing concepts and AWS-specific terminology. It covers essential topics such as virtualization, storage types, networking, and security fundamentals. This groundwork ensures that even individuals with little to no prior knowledge of cloud computing can grasp the intricacies of AWS technology easily.
2. Core Services: Exploring the AWS Portfolio
Once the fundamentals are in place, AWS training delves into the vast array of core services offered by the platform. Participants learn about compute services like Amazon Elastic Compute Cloud (EC2), storage options such as Amazon Simple Storage Service (S3), and database solutions like Amazon Relational Database Service (RDS). Additionally, they gain insights into services that enhance performance, scalability, and security, such as Amazon Virtual Private Cloud (VPC), AWS Identity and Access Management (IAM), and AWS CloudTrail.
3. Specialized Domains: Nurturing Expertise
As participants progress through the training, they have the opportunity to explore advanced and specialized areas within AWS. These can include topics like machine learning, big data analytics, Internet of Things (IoT), serverless computing, and DevOps practices. By delving into these niches, individuals can gain expertise in specific domains and position themselves as sought-after professionals in the industry.

Reasons to Choose AWS Training
1. Industry Dominance: Aligning with the Market Leader
One of the significant reasons to choose AWS training is the platform's unrivaled market dominance. With a staggering market share, AWS is trusted and adopted by businesses across industries worldwide. By acquiring AWS skills, individuals become part of the ecosystem that powers the digital transformation of numerous organizations, enhancing their career prospects significantly.
2. Comprehensive Learning Resources: Abundance of Educational Tools
AWS training offers a wealth of comprehensive learning resources, ranging from extensive documentation, tutorials, and whitepapers to hands-on labs and interactive courses. These resources cater to different learning preferences, enabling individuals to choose their preferred mode of learning and acquire a deep understanding of AWS services and concepts.
3. Recognized Certifications: Validating Expertise
AWS certifications are globally recognized credentials that validate an individual's competence in using AWS services and solutions effectively. By completing AWS training and obtaining certifications like AWS Certified Solutions Architect or AWS Certified Developer, individuals can boost their professional credibility, open doors to new job opportunities, and command higher salaries in the job market.
Placement Opportunities
Upon completing AWS training, individuals can explore a multitude of placement opportunities. The demand for professionals skilled in AWS is soaring, as organizations increasingly migrate their infrastructure to the cloud or adopt hybrid cloud strategies. From startups to multinational corporations, industries spanning finance, healthcare, retail, and more seek talented individuals who can architect, develop, and manage cloud-based solutions using AWS. This robust demand translates into a plethora of rewarding career options and a higher likelihood of finding positions that align with one's interests and aspirations.

In conclusion, mastering the cloud with AWS training at ACTE institute provides individuals with a solid foundation, comprehensive knowledge, and specialized expertise in one of the most dominant cloud platforms available. The reasons to choose AWS training are compelling, ranging from the industry's unparalleled market position to the top ranking state.
9 notes
·
View notes