#smtp_server
Explore tagged Tumblr posts
Text

Python code snippets to demonstrate general flaws in card usage and fraud detection:
1. Example code to check if a card is valid:
```python
def check_card_validity(card_number):
# Implement logic to check card validity
# Return True if the card is valid, False otherwise
pass
```
2. Example code to detect fraudulent transactions:
```python
def detect_fraudulent_transactions(transaction_data):
# Implement logic to detect suspicious transactions based on behavioral patterns
# Return a list of suspicious transactions
pass
```

As a supplement, here are examples of how contactless technology and artificial intelligence can be combined to improve productivity, prevent fraud, and handle card replacement in cases of theft and fraud, among others. Python code snippets are provided as proof of concept (POC):
1. Behavior pattern analysis
```python
# Example of behavior pattern analysis in Python
# Sample data
transactions = [10, 15, 20, 25, 30, 35, 40]
# Function to analyze behavior patterns
def analyze_patterns(transactions):
average = sum(transactions) / len(transactions)
standard_deviation = (sum([(x - average) ** 2 for x in transactions]) / len(transactions)) ** 0.5
if standard_deviation > 10:
print("Unstable behavior pattern")
else:
print("Stable behavior pattern")
# Function call
analyze_patterns(transactions)
```
2. Comparison with previous transactions
```python
# Example of comparison with previous transactions in Python
# Sample data
previous_transactions = [10, 15, 20, 25, 30]
new_transaction = 35
# Function to compare with previous transactions
def compare_transactions(previous_transactions, new_transaction):
if new_transaction in previous_transactions:
print("Repeated transaction")
else:
print("New transaction")
# Function call
compare_transactions(previous_transactions, new_transaction)
```
3. Anomaly detection to develop an effective fraud detection system:
A Python code snippet for anomaly detection in citizen card transactions can be implemented using machine learning algorithms, such as Isolation Forest. This algorithm can identify unusual behavior patterns in transactions and classify them as potential frauds.
```python
from sklearn.ensemble import IsolationForest
# Load transaction data
transactions = load_data()
# Train the anomaly detection model
model = IsolationForest(contamination=0.05)
model.fit(transactions)
# Detect anomalies in transactions
results = model.predict(transactions)
# Identify transactions considered as frauds
fraudulent_transactions = transactions[results == -1]
```
4. Assistance in communication in case of frauds using SMS, Email, Interactive Voice Response (IVR) calls to the card administration, police authorities, and card owner:
A Python code snippet to assist in communication in case of frauds can use libraries for sending SMS and email messages, as well as integration with IVR (Interactive Voice Response) systems.
```python
import smtplib
from twilio.rest import Client
# Configure email service credentials
smtp_server = 'smtp.example.com'
smtp_port = 587
email_address = '[email protected]'
email_password = 'your_email_password'
# Send email to card administration
def send_email_administration(message):
server = smtplib.SMTP(smtp_server, smtp_port)
server.starttls()
server.login(email_address, email_password)
server.sendmail(email_address, '[email protected]', message)
server.quit()
# Send SMS to card owner
def send_sms_owner(message):
account_sid = 'your_twilio_account_sid'
auth_token = 'your_twilio_auth_token'
client = Client(account_sid, auth_token)
message = client.messages.create(
body=message,
from_='your_twilio_phone_number',
to='card_owner_phone_number'
)
# Make IVR call to police authorities
def make_ivr_call_police(message):
# Code to make IVR call
pass
# Example usage:
fraud_message = 'A suspicious transaction has been detected with your citizen card. Please contact the card administration immediately.'
send_email_administration(fraud_message)
send_sms_owner(fraud_message)
make_ivr_call_police(fraud_message)
```
5. Use of RFID at the reading point for blocking in case of misuse:
The use of RFID (Radio Frequency Identification) at the reading point allows for identification and authentication of the citizen card. If misuse of the card is detected, a Python code snippet can be implemented to block the card.
```python
import RPi.GPIO as GPIO
import time
# Configure RFID pin
rfid_pin = 18
GPIO.setmode(GPIO.BCM)
GPIO.setup(rfid_pin, GPIO.IN)
# Check the state of the citizen card at the reading point
def check_citizen_card():
if GPIO.input(rfid_pin) == GPIO.HIGH:
return True
else:
return False
# Block the citizen card
def block_citizen_card():
# Code to send card blocking command
pass
# Example usage:
if check_citizen_card():
block_citizen_card()
```
These examples demonstrate how contactless technology and artificial intelligence can be combined to enhance security, improve efficiency, and mitigate risks associated with card usage and fraud.
6. Cancelation of the card in cases of fraud:
To cancel the card in cases of fraud, it's necessary to contact the card administration. The Python code snippet below illustrates how this communication can be done through an API.
```python
import requests
# Cancel the citizen card in cases of fraud
def cancel_citizen_card():
url = 'https://api.example.com/card_cancellation'
headers = {'Authorization': 'Bearer your_api_token'}
response = requests.post(url, headers=headers)
if response.status_code == 200:
print('Citizen card canceled successfully.')
else:
print('Error canceling the citizen card.')
# Example usage:
cancel_citizen_card()
```
7. Replacement of the card in case of fraud:
The process of replacing the card in case of fraud can be done by submitting a request to the card administration. Below is an example of a Python code snippet that can be used to make this request through an API.
```python
import requests
# Request card replacement in case of fraud
def request_card_replacement():
url = 'https://api.example.com/card_replacement'
headers = {'Authorization': 'Bearer your_api_token'}
response = requests.post(url, headers=headers)
if response.status_code == 200:
print('Request for card replacement sent successfully.')
else:
print('Error sending the request for card replacement.')
# Example usage:
request_card_replacement()
```
8. Monitoring system for real-time fraud detection:
A Python code snippet can be implemented to continuously monitor transactions in real-time and detect fraudulent activities using AI algorithms.
```python
import time
# Function to monitor transactions for real-time fraud detection
def monitor_transactions():
while True:
new_transaction = get_new_transaction() # Function to fetch new transaction data
if is_fraudulent(new_transaction): # Function to determine if the transaction is fraudulent
notify_authorities(new_transaction) # Function to notify authorities about the fraudulent transaction
time.sleep(1) # Check for new transactions every second
# Example usage:
monitor_transactions()
```
9. Enhanced authentication using AI-powered biometrics:
Implementing AI-powered biometric authentication can further enhance security. Below is an example of how facial recognition can be integrated into the authentication process:
```python
import face_recognition
# Function to authenticate user using facial recognition
def authenticate_user(image_path):
known_image = face_recognition.load_image_file("known_user.jpg") # Load known user image
unknown_image = face_recognition.load_image_file(image_path) # Load unknown image for authentication
# Encode facial features
known_encoding = face_recognition.face_encodings(known_image)[0]
unknown_encoding = face_recognition.face_encodings(unknown_image)[0]
# Compare facial features
results = face_recognition.compare_faces([known_encoding], unknown_encoding)
if results[0]:
print("User authenticated successfully.")
else:
print("Authentication failed. Face not recognized.")
# Example usage:
authenticate_user("unknown_user.jpg") # Provide path to the unknown user's image
```
10. Automated fraud reporting and analysis:
Developing an automated system for fraud reporting and analysis using AI can streamline the process. Here's an example of how such a system can be implemented:
```python
import pandas as pd
from sklearn.ensemble import RandomForestClassifier
# Function to report and analyze fraud using AI
def report_and_analyze_fraud(transaction_data):
# Load transaction data into a DataFrame
df = pd.DataFrame(transaction_data)
# Feature engineering and data preprocessing
# ...
# Train a machine learning model to detect fraud
model = RandomForestClassifier()
model.fit(X_train, y_train)
# Predict fraud on new data
predicted_fraud = model.predict(X_test)
# Report fraud and analyze patterns
# ...
# Example usage:
transaction_data = load_transaction_data() # Function to load transaction data
report_and_analyze_fraud(transaction_data)
```
11. Enhanced anomaly detection using machine learning:
Implementing machine learning algorithms for anomaly detection can improve fraud detection accuracy. Here's an example using an Isolation Forest algorithm:
```python
from sklearn.ensemble import IsolationForest
# Function for anomaly detection using Isolation Forest
def detect_anomalies(transaction_data):
model = IsolationForest(contamination=0.05)
model.fit(transaction_data)
anomalies = model.predict(transaction_data)
return anomalies
# Example usage:
transaction_data = load_transaction_data() # Function to load transaction data
anomalies = detect_anomalies(transaction_data)
print("Anomalies detected:", sum(anomalies == -1))
```
12. Integration with fraud intelligence databases:
Utilizing external fraud intelligence databases can enhance fraud detection capabilities. Here's an example of integrating with a hypothetical fraud database API:
```python
import requests
# Function to check transaction against fraud database
def check_fraud_database(transaction_data):
url = 'https://api.frauddb.example.com/check'
headers = {'Authorization': 'Bearer your_api_token'}
response = requests.post(url, headers=headers, json=transaction_data)
if response.status_code == 200:
result = response.json()
if result['is_fraud']:
print("Fraudulent transaction detected based on external database.")
else:
print("No fraud detected based on external database.")
else:
print("Error accessing fraud database API.")
# Example usage:
transaction_data = load_transaction_data() # Function to load transaction data
check_fraud_database(transaction_data)
```
13. Continuous monitoring with AI-powered alerting:
Implementing continuous monitoring with AI-powered alerting can provide real-time notifications of suspicious activities. Here's an example using a hypothetical alerting system:
```python
import time
# Function for continuous monitoring with AI-powered alerting
def continuous_monitoring():
while True:
new_transaction = get_new_transaction() # Function to fetch new transaction data
if is_suspicious(new_transaction): # Function to determine if the transaction is suspicious
send_alert(new_transaction) # Function to send alert
time.sleep(1) # Check for new transactions every second
# Example usage:
continuous_monitoring()
```
These examples showcase how AI and contactless technology can be integrated into various aspects of citizen card management, including fraud detection, authentication, and reporting, to improve overall security and efficiency.

RDIDINI PROMPT ENGINEER
0 notes
Text

I'll build your optimized Mautic marketing automation tool to support up to 1 million contacts. I'll tie in your SMTP service (Amazon SES recommended), including bounce management.
1 note
·
View note
Link
2 notes
·
View notes
Text
Configure PHP mail() with GMAIL
Gmail
Enable access to less secure APP on yout account
Sendmail
Download sendmail
After downloading, extract to C:\php\lib\sendmail
Edit the file sendmail.ini with this values:
[sendmail] smtp_server=smtp.gmail.com smtp_port=465 smtp_ssl=ssl default_domain=localhost error_logfile=error.log debug_logfile=debug.log auth_username= enter your gmail account here auth_password= enter the password for that account here ; pop3_server= ; pop3_username= ; pop3_password= ; force_sender= ; force_recipient= hostname=localhost
PHP
Edit in file php.ini this values and uncomment this extensions:
[mail function]
...
sendmail_path = "C:\php\lib\sendmail\sendmail.exe -t -i"
...
extension=openssl extension=sockets
Apache
Uncomment the LoadModule SSL in file httpd.conf:
LoadModule ssl_module modules/mod_ssl.so
font
0 notes
Text
Deploying Mastodon on Digital Ocean

Mastodon is the new social media platform, a decentralized alternative to Twitter that is currently blowing up. This is a step by step guide on how to run your own Mastodon instance on Digital Ocean.
Set up a Droplet
Create a new docker droplet:
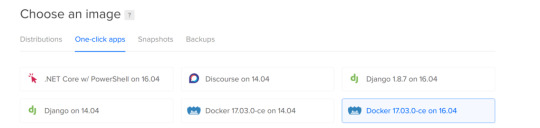
This droplet has almost everything we will need preinstalled.
You will receive an email from DO with the credentials you can use to log in to start setting up the server.
Connect to the server as a root user, using ip and password from the email:
ssh root@[ip-from-email]
You will be prompted to change the default password, so do that.
Then create a new user with the username you like, and grant him the sudo powers:
adduser ray gpasswd -a ray sudo
Connect domain name
Let’s also immediately point your domain name to the droplet. After buying the domain(I recommend using namecheap), change the Custom DNS settings to look like this:

Then, in DO’s networking tab, create a domain, and add an A record pointing to the droplet:
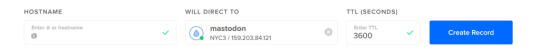
Now you will be able to ssh into your server using your new username and a domain name:
Install and configure basic stuff
Update and upgrade all the software:
sudo apt-get update && sudo apt-get upgrade
Install nginx(we’ll use it to serve our droplet on the right port), and your favorite text editor:
sudo apt-get install nginx emacs
Now let’s add docker to the sudo group, that will allow us to run all the docker commands without sudo:
sudo usermod -aG docker $USER sudo service docker restart
Clone and configure Mastodon
Clone the repo and cd into it:
git clone https://github.com/tootsuite/mastodon.git cd mastodon
Now let’s configure some settings. First, rename the file .env.production.sample into .env.production and open it.
Set the database username/password settings:
DB_USER=your_username DB_NAME=your_databasename DB_PASS=your_password
Set your domain name:
LOCAL_DOMAIN=hackertribe.io
And enable https:
LOCAL_HTTPS=true
Run docker-compose run --rm web rake secret to generate PAPERCLIP_SECRET, SECRET_KEY_BASE, and OTP_SECRET.
Configure the email server
Create a SendGrid account, go to Settings > API Keys, and generate an API key.
Then set up the config like this:
SMTP_SERVER=smtp.sendgrid.net SMTP_PORT=587 SMTP_LOGIN=apikey SMTP_PASSWORD=<your-api-key> [email protected]
(for SMTP_LOGIN literally just use “apikey”)
Configure the site info
Open the file /mastodon/config/settings.yml, and enter the information about your instance(title, description, etc).
Build the containers
Before we can build the containers, we need to add a swap file, without it my $10/month droplet was running out of memory during the build process. To add swap, execute these commands:
sudo fallocate -l 1G /swapfile sudo chmod 600 /swapfile sudo mkswap /swapfile sudo swapon /swapfile
(you can read more in depth about it here)
Now let’s finally build our containers! (It will take a few minutes)
docker-compose build docker-compose up -d
(the -d flag means that we want to run it in the background mode. You can try running it without this flag, and you will see the log of everything that’s going on on the screen)
Create the DB and migrate
Now we need to run several commands in the db container to create the database.
SSH into the container:
docker exec -i -t mastodon_db_1 /bin/bash
Switch to the postgres user:
su - postgres
Create a user for your db(use the username and password you’ve just set in the .env.production)
createuser -P your_username
Create a database, giving the ownership rights to the user:
createdb your_databasename -O your_username
Now you can get back to your own user, and run the migrations:
docker-compose run --rm web rails db:migrate
Precompile assets
Now you can precompile the assets:
docker-compose run --rm web rails assets:precompile
After this has finished, restart the containers:
docker stop $(docker ps -a -q) && docker-compose up -d
And now your mastodon instance will run on yourdomain.com:3000!!
Setting up nginx and SSL
First, follow this guide to generate SSL keys and set up the basic nginx configuration.
Then, because the docker containers are serving the application on the port 3000, we will need to use nginx to proxy all the requests to them.
Create the file /etc/nginx/sites-enabled/mastodon_nginx.conf, and copy the settings from here.
Now, after you restart nginx:
sudo /etc/init.d/nginx restart
It will serve your Mastodon instance!
Conclusion
Congratulations =) Create an account, test thinigs, and invite some people to use your instance!
I also recommend submitting a link to your instance to this list to make it easier for people to discover it.
If something doesn’t work or you have any questions — feel free to email me at [email protected], or toot at me at @[email protected]. I will be happy to help!
Also, everyone is always welcome to join the instance I’m hosting and maintaining — hackertribe.io.
Originally published on my blog. Come subscribe to it for more cool articles and tutorials on web development, programming, startups, and general tech!
Deploying Mastodon on Digital Ocean was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Check out more of my posts at https://medium.com/@rayalez
#rationality#technology#science#startups#philosophy#psychology#humor#comedy#funny#article#writing#med
0 notes