#subpoena interpreter
Text
How to manifest an SP
The Neville Goddard way and my interpretation:

Neville:
“When I decided to marry the lady who now bears my name, I applied this principle. At the time, I was terribly involved. I had married at the age of eighteen and became a father at nineteen. We separated that year, but I never sought a divorce; therefore, my separation was not legal in the state of New York.”
Moonie:
Neville had specific circumstances in front of him:
- He wasn't legally divorced
- The Ancient laws of the New York city were getting on his way of marrying his 2nd wife
Neville:
“Sixteen years later, when I fell in love and wanted to marry my present wife, I decided to sleep as though we were married. While sleeping, physically in my hotel room, I slept imaginatively in an apartment, she in one bed and I in the other. My dancing partner did not want me to marry, so she told my wife that I would be seeking a divorce and to make herself scarce – which she did, taking up residence in another state. But I persisted! Night after night I slept in the assumption that I was happily married to the girl I love."
Moonie:
As you can see, despite the annoying circumstances, Neville still believed in his imagination even if his 1st wife wasn't around, even if his 1st wife didn't sign the divorce papers, he still believed in his imagination more than his 3D or his human senses. He slept in the assumption that he was happily married to the girl he loved even if his 3D was showing him the opposite.
Neville:
“Within a week I received a call requesting me to be in court the next Tuesday morning at 10:00 A.M., giving me no reason why I should be there, I dismissed the request, thinking it was a hoax played on me by a friend. So the next Tuesday morning at 9:30 A.M.I was unshaved and only casually dressed, when the phone rang and a lady said: “It would be to your advantage, as a public figure, to be in court this morning, as your wife is on trial. “What a shock! I quickly thanked the lady, caught a taxi, and arrived just as the court began. My wife had been caught lifting a few items from a store in New York City, which she had not paid for. Asking to speak on her behalf I said: “She is my wife and the mother of my son. Although we have been separated for sixteen years, as far as I know, she has never done this before and I do not think she will ever do it again. We have a marvellous son. Please do nothing to her to reflect in any way upon our son, who lives with me. If I may say something, she is eight years my senior and may be passing through a certain emotional state which prompted her to do what she did. If you must sentence her, then please suspend it.”
Moonie:
Despite the fact that his 1st wife was "running away" from signing the divorce papers or facing Neville so he could marry his second wife, Neville didn't hold any grudges against his ex wife because he believed that his imagination was greater than anything. So Neville experienced a very unique bridge of events, which then later on led him to get whatever he wanted in his 3D
Neville:
“The judge then said to me, “In all of my years on the bench I have never heard an appeal like this. Your wife tells me you want a divorce, and here you could have tangible evidence for it, yet you plead for her release.” He then sentenced her for six months and suspended the sentence. My wife waited for me at the back of the room and said: “Neville, that was a decent thing to do. Give me the subpoena and I will sign it.” We took a taxi together and I did that which was not legal: I served my own subpoena and she signed it. “Now, who was the cause of her misfortune? She lived in another state but came to New York City to do an act for which she was to be caught and tried.
Moonie:
See? She was in another state, but when she came to New York, she was "forced" to do a specific act, which later on became Neville's bridge of events to marrying his 2nd wife. Neville focused on the desire, aka marrying his 2nd wife and not the circumstances (the divorce papers).
Neville:
So, I say: every being in the world will serve your purpose, so in the end, you will say: “Father forgive them, for they know not what they do." “They will move under compulsion to do your will, just as my wife did.” “I tell this story only to illustrate a principle. You do not need to ask anyone to aid you in the answer to a prayer, for the simple reason that God is omnipotent and omniscient. He is in you as your own wonderful I Am ness. Everyone on the outside is your servant, your slave, ready and able to do your will.“
Moonie:
So if people have to move for you, then THEY WILL. Do you want your desire to get externalized faster? Forget about the timing and "trying" and start BEING. If 5000 people have to move for you in order for you to get your desire in a materialized way then they will have to run for you
Neville:
“All you need do is know what you want, Construct a scene which would imply the fulfilment of your desire. Enter the scene and remain there. If your imaginal counsellor (your feeling of fulfilment) agrees with that which is used to illustrate your fulfilled desire, your fantasy will become a fact. If it does not, start all over again by creating a new scene and enter it. In my own case the scene was a bedroom of an apartment, with my wife in one bed and I in the other, denoting that I was no longer living in a hotel alone. I fell asleep in that state, and within one week I had the necessary papers to start action on a divorce.“
Moonie:
You really don't need to beg, or lift up a finger to get whatever you want. Don't focus on the problem, focus on the solution, don't focus on the circumstance, focus on the end goal.
He really proved himself that all he needed to do was to stay true to his imagination.
Do you want your shit faster?
- go straight to the end, accept that your desire is yours (has already been externalized and is yours)
- stand firm
- forgive yourself, forgive the people in your reality bcs they are just playing their roles in your reality.
- It is not your job to worry about "the how" or "the when", your job is to define+decide your desire, then believe and trust yourself that its already yours
Because THERE IS NO SEPARATION
#law of assumption#manifestation#neville goddard#law of allowing#manifesting#law of manifestation#joseph murphy#law of assumption community#state of being#loass#manifested#manifest abundance#manifesation#manifest sp#manifesting specific person#specific person#imagination creates reality#assumptions create reality#law of assumption coach#moonie#tenbinary#neville goddard lectures#the power of imagination#state of mind#void state#sats#shifting mindset#shifting reality#there are no limitations#there is always movement
521 notes
·
View notes
Text

The TF 141 Compatibility Love Report
For: @gardenthatneversleeps
Disclaimer:
This is based on my personal opinion and interpretation of you and the character.
the user makes no claims to be a real doctor (or any medical professional, really). Any mandatory subpoenas issued by the court in retaliation for your disapproval of the users anecdotal assessment, will be met with gaslighting, gatekeeping and girl bossing of the highest degree.
The Doc says your TF 141 Perfect Match is…
John ‘Soap’ MacTavish!

Romance: You may be a little more shy or conservative when it comes to love, maybe someone who prefers to know outright their partner's feelings for them. Soap would work best for you as a partner who both encourages (relentlessly begs) you to do things you’re afraid of and will work to protect your pride. Soap is passionate in a way that is all encompassing, he would be the type to shower you with love and attention without further prompting.
Breakfast in bed, early mornings drinking coffee on the porch with whispers of the future he sees with you and silly impromptu rom com moments would make the relationship with you flourish! He’s also incredibly intelligent and can offer insight on anything that’s on your mind. Even if it’s just giving an opinion on if you should drop that friend or explaining the intricacies of bomb making, he’s open to give his insight.
In my (un)professional opinion you also like the thrill of controlled danger. Soap is a rugged, known hothead who fights adamantly about the causes and people who he cares for, so you would be the hairline trigger for this loyal (dog) man. After some time with him you would find yourself acting like an old married couple whose disagreements lead to more passionate makeup sessions which leads me next to…
Sex: Soap is someone who wouldn’t blink an eye at your more kinkier requests and will put all his efforts into fulfilling your fantasies. You want to roleplay or string him up by his nipples, he’s asking for your input on his acting believability and googling techniques for safe rigging. He’s also known to be a dirty, disgusting DOG for a reason! The man isn’t shy about flipping you around and tonguing you down to an inch of your life. He’d also welcome being dommed if you ever felt a desire for it. He’s also not one who is easily embarrassed, he lives by the motto of ‘ask for forgiveness, not permission’ and will laugh if you swat him for getting a little too close to a forbidden hole while he’s slurping you up like chicken noodle soup. Like I said, Soap is passionate and if you like seeing big burly men beg, he’s the one for you!
Possible points of Contention:
Hotheaded and hard to talk down when feeling righteous
Will not stop humping your leg while sleeping
Prone to pranking
Motor mouth lol
Your Poly Pairing (haha) is….

SoapGaz- For the reasons listed previously, SoapGaz would be your best poly pairing! Both men would dote on you and combine forces to enshrine you in a ball of love. Gaz’s more charming and considerate nature would act as a balm for any Soap related mishaps. The beauty equivalent to Soap's beast in every way! Will also have you clawing out of bed on hands and knees as you try to avoid going into the light. (Sorry they’re not going to stop asking for one more big O, you’re doomed. :D )
#yall should know im a lil to invested in my own insanity lmao#if you don't agree sorry!#I've already run off into the wind with your payment lmao#the doc is in
18 notes
·
View notes
Text
Erin Reed at Erin In The Morning:
In an interview with ABC News on Sunday, JD Vance claimed that Minnesota Governor and Harris VP running mate Tim Walz signed a bill allowing the state to kidnap a transgender child if their parents did not approve of their transition. However, the bill Vance referenced actually provides refuge for transgender youth and their parents fleeing unsafe states where their care is criminalized. The legislation contains no provision allowing the state to “kidnap” children when their parents do not support their gender transition. These claims arise from an intentional misinterpretation of a provision that specifically applies to custody disputes between parents in different states.
In the interview, Vance sat down with "This Week" co-anchor Jonathan Karl, who pushed back against the claims:
[Karl: “[Trump] said that Tim Walz signed a letter letting the state kidnap children to change their gender, allowing pedophiles to be exempt from crimes… this is not true, this is not remotely true.”
Vance: “What President Trump said, Jon, is that Tim Walz has supported taking children from their parents if the parents don't consent to gender reassignment, that is crazy…Tim Walz gets on his high horse about ‘mind your own damn business.’ One way of minding your own damn business, Jon, is to not try to take my children away from me.”
Karl: “He has not signed a law allowing the state to kidnap children to change their sexual identity.”
Vance: “What I just explained to you I would describe as kidnapping.”
Karl: “That’s crazy, come on.”]
The claim that HF 146, also known as the “Trans Refuge Law,” would allow the state to kidnap children stems from a deliberately misleading interpretation of the bill. Terry Schilling, president of the American Principles Project and director of millions of dollars in anti-transgender ads targeting Democrats, pointed to a section of the bill stating that the state can take jurisdiction if a child is “present in the state” and has been unable to obtain gender-affirming healthcare. Deliberate misinterpretations of this clause is the primary source of false claims about the Minnesota law.
What Vance, Schilling, and others fail to mention is that the provision in question applies to Section 518D of Minnesota law, known as the Uniform Child Custody Jurisdiction and Enforcement Act. This act, adopted by most states in the U.S., addresses disputes between divorced parents when one parent lives in or moves to a different state, or when multiple states have competing claims to jurisdiction over custody cases.
The specific provision highlighted by Schilling and referred to by Trump and Vance states that the state can take “temporary emergency jurisdiction.” This does not equate to taking custody of the child; rather, it allows a judge to hear a case in a custody dispute where one parent resides in a state that criminalizes trans care and the other in a state where such care is legal. Notably, it does not even tell the judge who should be awarded custody, it merely allows a court in Minnesota to hear such a custody dispute.
[...]
Most importantly, the claim that Walz supports the state “kidnapping children” from their parents to “trans” them is absolutely false. Walz signed a bill making the state a refuge for transgender people fleeing states that criminalize their care. The bill not only responds to states like Texas and Florida, which have indeed threatened to remove transgender kids from supportive parents, but also to cases where attorneys general attempted to subpoena medical records across state lines, such as when Attorney General Ken Paxton sought medical records from Seattle Children’s Hospital; a similar law protected transgender youth who received care there. Similar protections have also since been extended to abortion patients and providers, who face nearly identical issues.
Appearing on ABC’s This Week on Sunday, JD Vance (R) baselessly claimed that Minnesota Gov. Tim Walz (D) signed a bill (HF146) that allow the state to “kidnap children”. The bill in question deals with custody disputes and trans safe refuge.
Interviewer Jonathan Karl called out Vance’s bogus lie with this: “He has not signed a law allowing the state to kidnap children to change their sexual identity.”
From the 08.11.2024 edition of ABC's This Week:
youtube
#J.D. Vance#Jonathan Karl#ABC News#ABC#This Week#Tim Walz#Transgender Safe Refuge#Transgender#Gender Affirming Healthcare#Minnesota HF146#Terry Schilling#Donald Trump#Custody Disputes
16 notes
·
View notes
Text
Elon Musk’s Malign Influence in Brazil

At 11:02 a.m. Eastern Daylight Time on April 7, 2024, Elon Musk—billionaire investor, tech CEO, and would-be Imperator of Mars—posted on the social media platform he owns, calling for the judge who presides over Brazil’s powerful Superior Electoral Tribunal (TSE) to “resign or be impeached.” In Musk’s view, the judge, Alexandre de Moraes, was guilty of the high crime of censorship.
Days before, Substack author Michael Shellenberger reprised his Twitter files gambit in a post accusing the TSE of “anti-democratic election interference” and decrying the “birth of the Censorship Industrial Complex in Brazil.” The Republican-controlled United States House Judiciary Committee later released a sealed Brazilian Court order, apparently obtained by subpoena, showing that the TSE had ordered Musk to take down about 150 accounts involved in spreading false information about the 2022 Brazilian elections. False claims of fraud in that election culminated in an attempt by ousted President Bolsonaro’s supporters to spark a coup d’etat. In defiance of the TSE, Musk said he would reinstate those accounts; in response, Moraes announced he would include Musk in an investigation into the “digital militias” which contributed to the January 8th, 2022 riots which followed Bolsonaro’s loss. Musk ultimately relented. The accounts remained offline, and the platform formerly known as Twitter avoided a potential ban in one of its largest markets.
In the Brazilian context, Musk is perhaps best understood as a far-right variant of what the US government sometimes calls “malign foreign influence” (a term I have long disliked for its potentially xenophobic interpretations, despite the often good intentions of those that use it). Even when he plays the fool, Musk and his ilk should be considered with deadly seriousness.
Continue reading.
27 notes
·
View notes
Text
The third day of trial in a Manatee County murder case that’s gained national attention as the "Black Swan murder" commenced Thursday.
Former ballerina Ashley Benefield is accused of shooting and killing her husband on Sept. 27, 2020, following an argument.
Family members from both sides, including the victim’s brother and older daughter who testified Monday, were once again in court.
The morning started with the judge reprimanding the victim’s daughter, Eva Benefield, about actions that could have been interpreted as a violation of the subpoena over social media presence and a conversation with a member of the media. After getting context and clarification, the judge admonished Eva Benefield and denied a motion by the defense to strike her out as a rebuttal witness.
The judge also dispensed a matter concerning a member of the jury being witnessed in a nearby restaurant overhearing television commentary about the case. However, it was learned that the juror had immediately asked for the TV to be turned off and was obliged by the restaurant staff.
Among the testimonies that the six-person jury would hear today includes from a Manatee County investigator with the technical services unit who specialized in forensics access and analysis of related data in a case. This would include accessing the phones and computers of the deceased victim and the defendant.
The courtroom also saw various text message conversations between the couple during around a three-day period before the shooting happened.
A medical examiner and a ballistics expert are also expected to take the stand Thursday.
According to court records, a custody battle is at the center of this case. On Tuesday, Douglass Benefield’s lawyer described the contentious situation surrounding the birth of the child and visitation leading up to the day of the murder which happened at Ashley Benefield’s mother’s home in Lakewood Ranch.
Sarasota lawyer Stephanie Murphy said her client was preparing for a Sept. 30 divorce hearing separate from the ongoing custody hearings before Ashley shot him. Alicia Byers, the defendant’s mother who had last seen Doug arriving at her home with a U-Haul truck as she was leaving with the couple’s child to the park, was also among the testimonies the court heard including from a psychologist, a social worker and more sheriff’s office detectives.
The prosecution is also expected to rest its case before lawyers for Ashley Benefield can begin to mount their client’s defense.
Benefield is facing 25 years to life in prison and has maintained that her estranged husband who she said had been abusive and was trying to get away from was aggressive that day when she shot and killed him. In opening statements, her lawyers declared that she was justified in her own self-defense and had previously tried to use Florida’s "Stand Your Ground Law" in a bid for immunity from prosecution but that motion was denied by the judge.
It’s not clear yet if or when Ashley Benefield will take the stand to defend herself. The trial is expected to last about three weeks.
3 notes
·
View notes
Text

The Heritage Foundation Project 2025, Page 8
“Cultural institutions like public libraries and public health agencies are only as “independent” from public accountability as elected officials and voters permit.”
Two things I take away from this.
The first is that the concept of independence is implicitly anathema under Project 2025. The idea that an institution would take up and interpret a mission according to a set of internalized best practices, professionalism, evidence, and political agnosticism is unacceptable.
I realize that no human activity can ever be completely apolitical or free of error and bias, but there’s no room for benefit of the doubt that the Heritage Foundation has a set of what it is going to assert as objective truths about how public institutions must undertake their work and especially in the case of public health and libraries it will almost certainly not be in consultation with veteran practitioners.
We must avoid uncritical worship of expertise but we must also take expertise seriously rather than dismiss it out of hand because it disagrees with our aesthetic preferences.
The second is the positioning of public libraries and public health.
The CIA ran a clandestine abduction and torture program and then destroyed the tapes when subpoenaed by Congress. This wasn’t during the Cold War, it was in the 2000s.
There’s been exactly zero public reckoning with the efficacy and downstream consequences of the widespread use of drone strikes and kill capture raids as part of the Global War on Terror.
Dept of Homeland Security is accused of so many abuses of undocumented migrants that there are wars that have resulted in fewer civilian deaths.
A not insignificant part of the right believes that the FBI and Dept of Justice are complicit in persecuting Trump to sabotage his 2024 candidacy after colluding to undermine his Presidency and reelection bid.
But in the eyes of the Heritage Foundation, public libraries and public health are the menaces most worth singling out by name as dangerous renegades who must be brought back into compliance.
The Heritage Foundation is not 4Chan. It is not a collection of Substack cranks posting into the void. It’s a respected conservative think tank. Conservative politicians and government officials turn to it and it’s like for policy proposals and often ghost written legislation.
Take them seriously.
Take them literally.
#civil rights#intellectual freedom#donald trump#heritage foundation#project 2025#fascism#nationalist conservatism#conservatism#libraries are for everyone#books & libraries#books and reading#public health#public libraries
3 notes
·
View notes
Text
The House January 6 select committee is considering a criminal referral to the justice department against Donald Trump for obstruction of an official proceeding of Congress and conspiracy to defraud the United States on the recommendation of a special subcommittee, according to sources familiar with the matter.
The recommendations on the former president – made by the subcommittee examining referrals – were based on renewed examinations of the evidence that indicated Trump’s attempts to impede the certification of the 2020 election results amounted to potential crimes.
The select committee could pursue additional criminal referrals for Trump and others, given the subcommittee raised the obstruction of an official proceeding and conspiracy to defraud statutes among a range of options, including insurrection, and discussions about referrals continued on Thursday, said the sources.
The referrals could also largely be symbolic since Congress has no ability to compel prosecutions by the justice department, which has increasingly ramped up its own investigations into Trump’s efforts to overturn the 2020 election and subpoenaed top aides to appear before federal grand juries.
The recommendations presage a moment of high political drama next Monday, when the full panel will vote publicly to adopt its final report and formally decide on making referrals, and increase pressure on the attorney general, Merrick Garland, to seek charges over January 6.
Trump could be referred for obstruction of an official proceeding, the subcommittee is said to have concluded, because he attempted to impede the certification and did so with a “consciousness of wrongdoing” – as the panel has previously interpreted the intent threshold.
The former president was seen to have met the elements of the offense since he relentlessly pressured Mike Pence to refuse to count electoral college votes for Joe Biden, despite knowing he had lost the election and had been told the plan was illegal.
Trump could also be referred for conspiracy to defraud the United States, the subcommittee suggested, arguing the former president violated the statute that prohibits entering into an agreement to obstruct a lawful function of government by dishonest means.
The conspiracy charge was seen to be broadly applicable because Trump’s agreement with key lawyers – and potentially even the rioters – did not need to be overt, while the plan to have Pence reject Biden slates of electors with Trump slates that did not exist was deceitful.
The discussions about referring Trump for obstruction of an official proceeding and conspiracy to defraud appeared to build upon the major win for the panel in May, when a federal judge found that Trump and the lawyer John Eastman likely engaged in felonies in trying to subvert the 2020 election.
In the ruling, US district court judge David Carter in California ruled that Trump and Eastman had concocted a “coup in search of a legal theory” and ordered Eastman to turn over his most sensitive emails to the investigation, citing the crime-fraud exception to attorney-client privilege.
The emails later showed that Eastman had admitted that he knew that having Pence interrupt the January 6 certification was illegal – and yet urged Pence’s counsel Greg Jacob that the then-vice president should move ahead with the plot anyway.
The panel may not adopt all of the options presented by the subcommittee – it also suggested civil referrals to the House ethics committee for GOP congressmen and the disbarment of some Trump lawyers, among a number of options, though a witness tampering referral for Trump is no longer under consideration.
But members on the select committee have resolved to suggest criminal and civil charges to some degree, and any referral letters would be accompanied by supporting evidence not dissimilar to prosecution memorandums that are routinely drawn up by the justice department, one of the sources said.
A spokesman for the select committee declined to comment.
Regardless of how the panel proceeds against Trump, the intention to make criminal referrals against the former president has been practically an open secret for months as its members have used the issue of potential criminality to reinforce the seriousness of Trump’s conduct.
The recommendations from the subcommittee – led by congressman Jamie Raskin and comprised of vice-chair Liz Cheney, Adam Schiff and Zoe Lofgren, all members with a legal background – follow internal discussions for nearly a year that Trump committed crimes in seeking to nullify his defeat.
Even before the select committee filed its civil suit to Carter, Cheney read aloud parts of the the obstruction statute at a public business meeting last December. And then throughout public hearings in the summer, the panel detailed their findings like prosecutors, treating the public like a jury at trial.
If the members decide to move forward with criminal referrals against Trump in particular – essentially a letter informing the justice department they uncovered evidence of crimes – they would be creating a roadmap for a prosecution put together by the select committee’s top lawyers.
The select committee’s investigation has been principally driven by color-coded teams of investigative lawyers, many of whom have previously worked as federal prosecutors, conducting more than 1,000 witness interviews and reviewing documents and communications from Trump’s confidantes.
Still, the justice department has no obligation to take up any criminal referrals and, at this stage, could have a better perspective about the strength of criminal charges as it escalates its own January 6 inquiries with an investigative arsenal far more potent than possessed by Congress.
In recent months, an increasing number of top Trump advisors and election officials in states where Trump tried to nullify his defeat have been subpoenaed to testify before an increasing number of federal grand juries in Washington hearing evidence about events connected to the Capitol attack.
The recent subpoenas to election officials have demanded any and all communications involving Trump and the Trump campaign from June 2020 to January 2021, as part of the investigations into Trump’s so-called fake electors scheme, according to two subpoenas reviewed by the Guardian.
2 notes
·
View notes
Text
In the United States, the protection of journalists' confidential sources is not governed by a single federal law but rather by a combination of state laws, federal common law, and constitutional interpretations. Here are the key elements that shape the legal landscape regarding the protection of journalistic sources in the U.S.:
### 1. **First Amendment Protections:**
- The First Amendment to the U.S. Constitution guarantees freedom of the press, which courts have interpreted to include some level of protection for journalists' confidential sources. However, this protection is not absolute.
- The landmark Supreme Court case *Branzburg v. Hayes* (1972) held that journalists do not have an absolute First Amendment right to refuse to testify before grand juries. The Court ruled that the obligation to testify was the same for journalists as for other citizens, particularly in criminal investigations.
### 2. **Federal Common Law:**
- Following *Branzburg*, federal courts have developed a qualified privilege based on the First Amendment. This qualified privilege means that journalists may be able to protect their sources unless the government can show a compelling need for the information that cannot be obtained by alternative means.
- The balancing test involves evaluating the relevance of the information, the necessity for it, and whether the information can be obtained by alternative means.
### 3. **State Shield Laws:**
- Many states have enacted "shield laws" that provide varying degrees of protection for journalists and their sources. These laws differ significantly from state to state in terms of scope and strength.
- Some states offer absolute protection, meaning journalists cannot be compelled to reveal their sources under any circumstances, while others provide only qualified protection, requiring a balancing test similar to the federal common law approach.
- Examples of states with strong shield laws include California, New York, and New Jersey, each offering robust protections for journalists.
### 4. **Federal Legislation Attempts:**
- There have been multiple attempts to pass a federal shield law, such as the proposed Free Flow of Information Act. However, these efforts have not yet resulted in a federal statute.
- A federal shield law would create a consistent standard across the country, providing uniform protection for journalists in federal cases.
### 5. **Judicial Precedents and Subpoenas:**
- Courts often follow a three-part test to determine whether to compel a journalist to reveal sources:
1. **Relevance and Importance:** The information sought must be highly relevant and material to the case.
2. **Exhaustion of Alternatives:** The party seeking the information must have exhausted all other means of obtaining it.
3. **Compelling Interest:** There must be a compelling and overriding interest in obtaining the information.
### 6. **Recent Developments:**
- High-profile cases, such as those involving leaks of classified information or whistleblower revelations, continue to test the boundaries of these protections.
- The Department of Justice (DOJ) has policies in place that provide guidelines for subpoenaing journalists, typically requiring approval from senior DOJ officials and considering the importance of the journalist's role in informing the public.
### Summary:
- **First Amendment:** Provides some level of protection, but not absolute.
- **Federal Common Law:** Offers a qualified privilege based on a balancing test.
- **State Shield Laws:** Vary widely, with some states providing strong protections and others offering limited or no protection.
- **Federal Shield Law:** No comprehensive federal statute yet, but ongoing legislative efforts.
- **Judicial Precedents:** Courts use a balancing test to decide on compelling disclosure.
The legal landscape in the U.S. is a patchwork of protections that offer varying degrees of security for journalists and their sources, depending on the jurisdiction and the specifics of each case.
0 notes
Text
does using a vpn affect safeassign
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does using a vpn affect safeassign
VPN privacy implications
Understanding VPN Privacy Implications
Virtual Private Networks (VPNs) are hailed for their ability to bolster online privacy and security. However, delving deeper, it becomes evident that the privacy implications of VPN usage are nuanced and multifaceted.
Firstly, VPNs encrypt your internet traffic, shielding it from prying eyes such as hackers, government surveillance, and internet service providers (ISPs). This encryption ensures that sensitive information, like passwords and financial data, remains confidential, especially when connected to public Wi-Fi networks.
Moreover, VPNs obscure your IP address, replacing it with one from the VPN server's location. While this masks your real location and enhances anonymity, it also raises concerns. Some VPN providers log user activity, potentially compromising privacy if these logs are subpoenaed or breached.
Another aspect to consider is the jurisdiction of the VPN provider. Different countries have varying data retention laws and government surveillance programs. Opting for a VPN headquartered in a jurisdiction with strict privacy laws can mitigate potential privacy risks.
However, VPNs aren't a foolproof solution. They can't protect against all forms of online tracking, such as browser fingerprinting and tracking cookies. Additionally, using a VPN doesn't absolve users from practicing good digital hygiene, such as regularly updating software and avoiding suspicious websites.
Furthermore, VPNs aren't immune to vulnerabilities and security breaches. In recent years, several VPN providers have been exposed for security flaws and data leaks, underscoring the importance of choosing a reputable provider with a track record of transparency and security.
In conclusion, while VPNs offer significant privacy benefits, users must understand the complexities and potential risks involved. By selecting a trustworthy provider, practicing good security habits, and staying informed about evolving privacy threats, individuals can maximize the privacy advantages offered by VPNs while minimizing associated risks.
SafeAssign accuracy
SafeAssign is a crucial tool in the academic world, designed to ensure the integrity of student submissions by detecting potential plagiarism. It employs advanced algorithms to compare submitted documents against a vast database of academic content, internet sources, and previously submitted papers. While SafeAssign is a valuable resource, it's essential to understand its accuracy and limitations.
One key aspect of SafeAssign accuracy is its ability to detect matching text within documents. It analyzes the content for similarities, including verbatim text and paraphrased passages, and generates a report highlighting potential matches. This process helps educators identify instances of plagiarism and guide students toward proper citation practices.
However, SafeAssign's accuracy is not infallible. It may occasionally produce false positives or overlook subtle instances of plagiarism, particularly if the text has been heavily paraphrased or rephrased. Additionally, SafeAssign relies on the content available in its database, which may not encompass every possible source. Consequently, it's possible for students to evade detection by using obscure or unpublished materials.
Educators must exercise judgment when interpreting SafeAssign reports. While a high similarity index may indicate plagiarism, it's essential to review the flagged passages contextually and consider the nature of the assignment. Additionally, engaging students in discussions about academic integrity and proper citation practices can help mitigate plagiarism and foster a culture of ethical scholarship.
In conclusion, SafeAssign offers valuable support in maintaining academic integrity by detecting potential instances of plagiarism. However, its accuracy is contingent upon various factors, including the comprehensiveness of its database and the complexity of the analyzed text. Educators should use SafeAssign as a tool in conjunction with their expertise to promote academic honesty effectively.
Internet anonymity and plagiarism detection
Internet anonymity poses a double-edged sword when it comes to plagiarism detection. While it offers individuals the freedom to express themselves without fear of repercussions, it also enables plagiarism to thrive unchecked. Plagiarism detection relies heavily on tracking the digital footprint of content, including its source and publication history. However, when individuals operate under the veil of anonymity, it becomes challenging to trace the origin of content accurately.
One of the primary challenges in detecting plagiarism in anonymous content is the lack of identifiable markers. Without clear authorship or ownership, distinguishing between original work and plagiarized material becomes increasingly complex. Traditional methods of plagiarism detection, such as comparing texts against existing databases or analyzing writing styles, may prove ineffective when dealing with anonymous content.
Moreover, internet anonymity provides plagiarists with a shield against accountability. Without the risk of being identified, individuals are more emboldened to engage in unethical practices, such as copying content without proper attribution or permission. This not only undermines the integrity of academic and creative endeavors but also erodes trust within online communities.
To address the issue of plagiarism in anonymous content, innovative approaches to detection are necessary. Advanced algorithms capable of analyzing linguistic patterns and contextual cues may offer a more nuanced understanding of authorship, even in the absence of explicit identifiers. Additionally, fostering a culture of academic integrity and ethical content creation can encourage individuals to uphold standards of originality, regardless of anonymity.
In conclusion, while internet anonymity empowers individuals to share their thoughts and ideas freely, it also poses significant challenges for plagiarism detection. As online communities continue to evolve, efforts to combat plagiarism must adapt accordingly, leveraging technology and promoting ethical practices to preserve the integrity of digital content.
VPN encryption methods
VPN encryption methods are crucial for ensuring the security and privacy of internet users. When utilizing a Virtual Private Network (VPN), various encryption techniques are employed to protect data transmissions from being intercepted or accessed by unauthorized parties.
One of the most commonly used VPN encryption methods is the Advanced Encryption Standard (AES). AES is a symmetric encryption algorithm that is highly secure and widely trusted for protecting data. It offers different key lengths, such as 128-bit, 192-bit, and 256-bit, with longer key lengths providing stronger encryption.
Another popular encryption protocol used by VPNs is Secure Socket Layer (SSL) or its successor, Transport Layer Security (TLS). SSL and TLS create a secure tunnel between the user's device and the VPN server, encrypting data transmitted through the connection. These protocols are often utilized for securing online transactions and communications.
Internet Protocol Security (IPsec) is another encryption method commonly used by VPNs to secure data transfers. IPsec operates at the network layer of the OSI model, encrypting and authenticating IP packets to ensure the confidentiality and integrity of transmitted data.
In addition to these encryption methods, VPNs may also incorporate other techniques such as Datagram Transport Layer Security (DTLS), Point-to-Point Tunneling Protocol (PPTP), or Layer 2 Tunneling Protocol (L2TP) to enhance security and privacy.
Overall, VPN encryption methods play a vital role in safeguarding sensitive information and ensuring online anonymity for users. By understanding the different encryption techniques utilized by VPN services, individuals can make informed decisions to protect their data and maintain their privacy while browsing the internet.
SafeAssign plagiarism detection accuracy
SafeAssign plagiarism detection accuracy is a crucial aspect of ensuring academic integrity and honesty in educational institutions. SafeAssign, developed by Blackboard, is a widely used tool that helps educators identify potential plagiarism in students' work by comparing it to a vast database of academic papers, articles, and other sources.
The accuracy of SafeAssign in detecting plagiarism is largely dependent on several factors. Firstly, the comprehensiveness and currency of the database play a significant role. The larger and more up-to-date the database, the better the tool can identify similarities between submitted work and existing content.
Another factor influencing SafeAssign's accuracy is the algorithm it employs to analyze text. SafeAssign uses sophisticated algorithms to detect similarities in language, sentence structure, and even formatting, enhancing its ability to identify potential instances of plagiarism accurately.
Additionally, the settings and parameters chosen by educators when using SafeAssign can impact its accuracy. Adjusting settings such as the sensitivity level can fine-tune the tool's ability to detect plagiarism, balancing between identifying genuine matches and avoiding false positives.
However, despite its advancements, SafeAssign may not be infallible. It's essential for educators to interpret the results critically and consider contextual factors such as paraphrasing and citation styles, which may influence the detection process.
Overall, while SafeAssign offers a valuable means of detecting plagiarism, its accuracy ultimately relies on the quality of its database, the effectiveness of its algorithms, and the careful configuration by educators. By leveraging SafeAssign effectively, educational institutions can uphold academic integrity and promote a culture of originality and ethical scholarship among students.
0 notes
Text

Jack Smith Torches Judge Cannon in Late-Night Filing, Could Seek Appeal
Smith is threatening a writ of mandamus over Cannon's latest order.
Brett Meiselas Meidas Touch Network
youtube
Special Counsel Jack Smith issued a scorching response to a request made by Judge Aileen Cannon, who demanded that Government and Donald Trump submit a set of hypothetical jury instructions to two completely erroneous premises that lacked a fundamental understanding of the issues at center of the stolen documents case. Smith's response, in no uncertain terms, challenges the legal premises underlying the request, asserting that they are fundamentally flawed and could distort the trial.
The crux of the issue lies in the interpretation of the Presidential Records Act (PRA) and its relevance to the charges faced by Donald Trump. The Government argues that the distinction between "personal" and "Presidential" records under the PRA should not determine whether the former President's possession of highly classified documents is authorized under the Espionage Act. Smith explains that the PRA should play no role in the jury instructions regarding the elements of the Espionage Act.
Importantly, Smith emphasizes the urgency of the Court's decision on this matter. He asserts that if the Court wrongly concludes that the legal premise represents a correct formulation of the law, it must inform the parties well in advance of the trial. This is crucial to allow the Government the opportunity to consider appellate review before jeopardy attaches, laying the groundwork to seek mandamus against Judge Cannon, which could ultimately end in Cannon getting booted from the case.
Smith warns that presenting to the jury a factual determination based on incorrect legal premises could lead to a "high probability of failure of a prosecution." Therefore, the Government insists on the importance of seeking prompt appellate review if necessary.
Smith explains that Trump's invocation of the PRA is not grounded in any decisions he made during his presidency. Instead, it is portrayed as a post hoc justification concocted after leaving the White House. Smith contends that there is no basis in law or fact for this legal presumption and urges the Court to reject Trump's efforts to inject the PRA into the case.
Smith provides a detailed account of Trump's actions following his departure from office, demonstrating a consistent acknowledgment that the documents were presidential records. Even as late as May 2022, Trump's attorney accepted a grand jury subpoena related to the classified documents without contesting their presidential status.
Furthermore, Smith refutes the notion that Trump's alleged designation of the documents as personal, if it ever occurred, would shield him from prosecution under Section 793(e). He argues that authorization to possess classified information is governed by Executive Order 13526, not the PRA, and that Trump's purported designation holds no legal weight in the context of unauthorized possession.
Smith asserts that the proposed jury instructions would lead to confusion and potential miscarriages of justice. By directing the jury to determine the classification of documents under the PRA, the instructions conflate a factual determination with a legal one, thereby muddying the waters of the case.
In response to Judge Cannon's request, Smith provides alternative jury instructions that adhere to the correct legal framework. These instructions clarify that unauthorized possession of classified information is determined by whether an individual holds a security clearance, has a need-to-know basis, and complies with safeguarding regulations outlined in Executive Order 13526. In both hypothetical scenarios, the Special Counsel makes clear that the instructions, as defined by Judge Cannon, would be incorrect. In his conclusion, Smith once again emphasizes that he will be forced to take action should Judge Cannon not reject Trump's erroneous legal premise, which should have never been considered in the first place.
Smith concludes: "If, however, the Court does not reject that erroneous legal premise, it should make that decision clear now, long before jeopardy attaches, to allow the Government the opportunity to seek appellate review. "
0 notes
Text
Understanding On-Page SEO for Law Firms

For legal professionals, the structured nature of legal documents is a familiar and essential aspect of their work. This article draws an analogy between the structured format of legal documents and the importance of on-page SEO for law firm websites.
The Structure of Legal Documents and Web Pages
Just as legal documents such as legislation, subpoenas, and court filings follow a specific structure, web pages also have their own set of structural rules. This structure is not just for aesthetics; it serves a functional purpose. For legal professionals, understanding the structure of a document is second nature. Similarly, understanding the structure of a web page is crucial for effective on-page SEO.
The Role of Headings in On-Page SEO
In the realm of on-page SEO, the use of headings plays a pivotal role. Comparable to chapters and sections in legal documents, web pages have titles, headings, and tags that organize content.
- Title Tags: The title of a web page, akin to the title of a legal document, tells both the visitor and search engines what the page is about.
- Heading 1 (H1): This is the main heading of a page, indicating the most important topic, similar to the main heading of a legal brief.
- Heading 2 (H2) and Heading 3 (H3): These support the main heading, much like subsections in a legal document, providing structure and detail.
Failure to use these headings appropriately is akin to omitting chapter titles in legal documents, leading to confusion and decreased readability.
The Importance of Alt Text and Metadata
In legal documents, details matter. Even small particulars can impact interpretations or rulings. Similarly, on a web page, supplementary elements like alt text and metadata may seem minor, but optimizing them is vital for on-page SEO.
Alt Text for Images
Images on a page should always have accompanying alt text, conveyed to the user when hovering over the image and to search engines scanning the page. Much like captions under images in legal briefs, alt text identifies what the image depicts and is necessary for compliance to ADA standards.
For a family law firm, an image of a gavel could have alt text such as “Family law rulings are decided in court with a gavel.” This provides additional context and keywords for search engines, improving visibility for relevant searches.
Metadata
Metadata contains technical data about a page mainly seen by search engines during crawling. This includes descriptive title tags and meta descriptions summarizing page content.
Quality metadata acts much like the fine print details and technical clarifications in legal documents that shape interpretations. Properly optimized metadata provides search engines more context about relevancy.
Fictional Example:
For example, a child custody page could have a title tag: Child Custody Lawyers in Austin, Texas - Mothers' & Fathers' Rights. This clearly signals the page's geographic service area and practice specialty.
The Impact of Optimization
Fine-tuning alt text, metadata, headings and all other on-page elements tailors a site's structure for search engines without changing visible content. Much like proofreading a legal doc before submission, this optimization scrutinizes each building block. The reward, for both websites and court filings, is properly framed information for the intended audience.
For a law firm website, every bit of on-page SEO counts when striving for search visibility. Consult our legal marketing experts to audit your site and structure content for maximum exposure.
This additional section expands on the analogy between legal documents and websites by exploring supplementary details like alt text and metadata that may seem insignificant but can profoundly impact outcomes and interpretations for the better. It sustains the central comparison while providing further education on technical on-page SEO.A Fictional Example
Consider a law firm, 'Smith & Associates', specializing in family law. Their website lacks proper headings, making it challenging for visitors and search engines to navigate. After an SEO overhaul, where each service page is structured with clear H1 and supporting H2s and H3s, the firm sees a notable increase in website traffic and client inquiries. This improvement is directly linked to the enhanced clarity and search engine visibility provided by the structured headings.
FAQs
1. Why is on-page SEO important for law firm websites?
On-page SEO is crucial for law firm websites as it helps search engines understand the content and relevance of the site, thereby improving visibility and attracting potential clients.
2. How are legal document structures similar to web page structures?
Both legal documents and web pages follow a hierarchical structure with titles, headings, and subheadings, ensuring clarity, organization, and ease of navigation for the reader.
3. Can improving on-page SEO impact a law firm's business?
Absolutely. Improving on-page SEO can significantly increase a law firm's website visibility, attract more traffic, and ultimately lead to an increase in client inquiries and business growth.
4. Why is alt text important for images from an SEO perspective?
Alt text provides a textual description of images on web pages. This helps search engines understand what the image conveys and index that content, improving visibility for related search queries.
5. How can optimizing metadata help with SEO?
Metadata gives search engines more clues about the topic and contents of a web page. Well-crafted page titles, descriptions and other metadata details allow search algorithms to determine relevancy for queries more accurately.
6. What aspects of on-page SEO are most similar to details in legal documents?
Elements like metadata and alt text may seem insignificant, but just like legal document fine print, these supplementary details have an out sized impact on shaping interpretations by search engines. Properly optimizing them is vital.
7. What role does alt text play for accessibility?
Alt text makes website images accessible for those using screen readers. It describes images for visually impaired visitors, much like captions do for sighted users. Optimized alt text improves both accessibility and SEO.
This additional FAQ ties back to the new section's focus on alt text and metadata as crucial details for on-page SEO, similar to how even small particulars in legal filings can have an immense impact.
At Local Legal Marketing, we employ a meticulous yet holistic approach to on-page SEO built upon our decades of experience promoting law firm websites. We are well-versed in the technical elements like metadata and alt text as well as higher-level content structuring with precise use of titles and headings.
We have partnered with over law firms to significantly boost their web visibility and convert website traffic into more clients. Our award-winning service includes:
- Comprehensive on-page SEO audits and recommendations
- Content optimization, including alt text, metadata, and structural tagging
- Graphic design improvements for enhanced branding
- Detailed reporting on rankings and traffic
Delve into our case studies of legal websites we have transformed.
When you are ready to attract more clients and grow your practice online, contact Local Legal Marketing at for a consultation at (727) 320-7686. Our holistic yet meticulous approach,and SEO expertise, delivers results.
Read the full article
0 notes
Text
Joel Riley Connecticut's Expert in the Investigative Process, Ensuring Fairness and Compliance
Investigative Process Expertise: A Foundation of Fairness
Joel C Riley is a distinguished professional in the field, with over two decades of experience in human resources. His extensive background in investigative processes has honed his expertise, allowing him to excel in various management roles. With a focus on complex organizational matters, he has established himself as an expert in labor relations, negotiations, HR functions, laws, training, investigations, and managerial responsibilities. Central to his approach is a dedication to fairness and compliance, ensuring investigations adhere to rigorous standards. With his in-depth knowledge and specialized skills, Joel conducts thorough and impartial investigations.
The initial step in any investigation is to create a meticulously crafted plan that outlines the investigation's scope, objectives, and methodologies. Investigative process experts excel at developing these plans, which take into account legal and ethical considerations. They ensure that investigations are conducted transparently, and that individuals' rights are respected.
A well-structured investigation plan plays a crucial role in ensuring a thorough and effective examination. It not only establishes clear objectives but also provides a comprehensive outline of the specific areas to be examined. By carefully defining the scope of the investigation, the plan helps investigators focus their efforts on gathering relevant information and evidence.
In addition to outlining the investigative techniques and tools to be employed, the plan also takes into consideration the importance of adhering to a realistic timeline. By setting achievable milestones and deadlines, investigators can effectively manage their time and resources, maximizing the chances of a successful outcome. Moreover, a robust investigation plan ensures alignment with applicable laws, regulations, and company policies. By considering legal and regulatory requirements from the outset, the plan helps maintain the integrity and legality of the investigative process. This not only protects the rights of individuals involved but also ensures that the investigation withstands scrutiny and upholds ethical standards.
Unbiased Evidence Collection
In the realm of investigations, the collection of evidence serves as a critical juncture, necessitating a deep-rooted understanding of both legal prerequisites and ethical boundaries. Experts in the investigative process, like Joel Riley CT, stand out in this arena through their adeptness in amassing evidence in an impartial manner, steadfastly adhering to the loftiest benchmarks of equity and fairness. Their proficiency is rooted in extensive experience and comprehensive education, spanning the gamut from labor relations and HR functions to laws and management, ensuring compliance with all stipulated legal requirements in this pivotal phase of the process.
They prioritize impartiality, ensuring that the investigation team remains neutral and doesn't favor any party involved. The experts establish and maintain a secure chain of custody for all collected evidence, preventing tampering or contamination. They diligently adhere to laws and regulations governing evidence collection, such as obtaining search warrants or subpoenas when necessary. Moreover, they protect the privacy and rights of individuals involved, safeguarding sensitive and confidential information throughout the process.
Thorough and Impartial Analysis
Joel Riley Connecticut is a stand-out figure in this field, being well-versed in the meticulous analysis required following evidence collection. This part of the investigative process is fundamental, as it involves drawing logical conclusions and making informed decisions. Professionals like Riley excel in this phase, objectively evaluating the collected data without prejudice. They interpret the findings, apply their in-depth understanding, and devise strategies accordingly, ensuring the integrity of the process is maintained throughout.
They focus on data integrity, reviewing all evidence with precision and attention to detail. By cross-referencing evidence, they identify inconsistencies or discrepancies that warrant further investigation. Maintaining objectivity throughout the analysis process, they steer clear of confirmation bias or other forms of cognitive bias. Their reporting is clear and concise, providing a comprehensive account of the investigation's results.
By diligently adhering to these guiding principles, investigative process experts meticulously ensure that their analysis is not only accurate but also free from any bias that could potentially compromise the fairness, impartiality, and integrity of the investigation process. This commitment to objectivity and thoroughness allows for a comprehensive examination of the facts, which in turn fosters a greater sense of trust and confidence in the investigative findings.
Reporting and Recommendations
Joel Riley Wallingford CT meticulously prepares comprehensive reports after completing an in-depth analysis. These reports, which summarize the findings and propose recommendations for future actions, play a pivotal role in guiding decision-makers within organizations or regulatory bodies. Drawing from his extensive experience in labor relations, negotiations, HR functions, and management, his contributions ensure that the decision-making process is informed by accurate and thorough information.
These reports are marked by transparency, as they document the investigative process, methodologies, and findings in a clear and understandable manner. They also ensure that recommendations align with applicable laws, regulations, and company policies. Objectivity remains paramount, as experts present the findings and recommendations without favoring any particular outcome or stakeholder.
In this era of transparency and compliance, the importance of individuals with expert knowledge in the investigative process simply cannot be overstated. An exemplary professional in this domain is Joel Riley Connecticut. He has a rich history of helping organizations navigate complex challenges requiring meticulous investigations. His expertise spans the gamut from strategic planning to unbiased evidence collection, impartial analysis, and transparent reporting. All of these are vital components for maintaining the integrity of the investigative process. In a world where fairness is paramount, organizations that leverage the skills of investigative process professionals show their commitment to upholding ethical standards and protecting the rights of individuals.
0 notes
Text
BlackRock's Spot Bitcoin ETF Application: A Game Changer for Regulators?

The moment finance giant BlackRock filed to create a spot Bitcoin ETF in the U.S., market watchers wondered whether the world's biggest asset manager had a better chance of approval than the many rejected predecessors. They quickly fixated on a mechanism within the application that allows suspicious trades to be flagged to the authorities.
Influence of Surveillance-Sharing Agreement (SSA)
BlackRock's application sparked a flurry of follow-on filings with the now-ubiquitous Surveillance-Sharing Agreement (SSA) added. But what's more likely to influence the U.S. Securities and Exchange Commission (SEC)'s decision is an information-sharing deal that flips the position of power in the arrangement and gives regulators the right to demand extra background.
Information-Sharing Deal: The Power Shift
While the SEC's requirement for surveillance sharing to prevent market manipulation of crypto is not new – it first appeared in the Winklevoss Bitcoin ETF application in 2017 – details of a "Coinbase and NASDAQ Information Sharing Term Sheet" shared with CoinDesk point to something more.
Push vs. Pull: The Nuance
The nuance here can be characterized as the difference between push and pull. The SSA concerns data surveillance carried out by the spot exchange, Coinbase (COIN) in this case, which can be pushed to regulators, ETF providers, and listing exchanges if deemed suspicious. Information-sharing agreements, in contrast, allow regulators and ETF providers to pull data from the exchange.
The Scope of Information Sharing
The information in question could be about specific trades or traders, and the agreement also compels a crypto exchange to share data up to and including personally identifiable information (PII), such as the customer's name and address. Information-sharing agreements do not appear in any of the spot Bitcoin ETF filings, but the structure is found in other markets.
An important caveat is that an information-sharing request has to be very specific, not dissimilar to a subpoena, according to a person familiar with the matter.
Ensuring Success of ETFs
"It can't just be a fishing expedition, where it's all of the information attached to any trade that was made between two given points in time," said the person, who asked to remain unidentified. "The obvious concern is that crypto traders, almost by definition, don't like having information shared about them. It's sort of anathema to the ethos of crypto in general. But for the ETF to be successful, have to do it."
Bitcoin ETF Application History
Going back to 2017, the SEC has highlighted the need for Bitcoin ETF applications to have a surveillance-sharing agreement with a regulated market of significant size, but firms have lacked clarity and an objective standard when it comes to interpreting this.
The inclusion of an information-sharing agreement, as opposed to simply surveillance sharing, makes sense because it means an ETF is not reliant on an unregulated market, said Matt Hougan, chief investment officer at Bitwise Asset Management. Bitwise has applied for an ETF numerous times.
Approval Ratings
The combination of surveillance sharing and information sharing is a structure known to brokers and exchanges in equities markets, where the regulator has the authority to request more information about the end client's trading history.
Whenever a broker has a client that sends an order to Nasdaq, for example, and that order is flagged as suspicious by the exchange's SMARTS surveillance system, then the broker and the exchange are required to file a suspicious activity report (SAR).
Regulators investigating a SAR can go on to this "second step," said Dave Weisberger, CEO of crypto trading platform CoinRoutes, which is requesting PII to identify whether the same beneficial owners are behind a given set of trades, creating a consolidated audit trail.
"Coinbase, Nasdaq, and BlackRock are likely saying that if there is suspicious activity – and they are surveilling for it – then the regulator can request who's doing it, but they're not just going to give out PII willy-nilly. There is going to have to be suspicious activity. That is the equivalency here," Weisberger said in an interview, adding:
"If that is true, I believe the SEC will not only approve this ETF but will approve it and take a victory lap. And considering how unpopular this SEC is, I suspect they need to do that now."
Conclusion
BlackRock's spot Bitcoin ETF application, coupled with innovative surveillance-sharing and information-sharing agreements, has the potential to reshape the regulatory landscape. By allowing regulators to pull data from exchanges and uncover suspicious activities, these mechanisms provide a more robust framework for overseeing the crypto market. As the SEC weighs the advantages and concerns associated with these agreements, the decision on approving the ETF will likely be a turning point for the future of cryptocurrency regulation.
For more articles visit: Cryptotechnews24
Source: coindesk.com
Related Posts
Read the full article
#BitcoinETF#BlackRock#Coinbase#CryptoNews#cryptotraders#datasurveillance#marketmanipulation#NASDAQ#personallyidentifiableinformation#PII#regulatorydecisions#SEC#spotBitcoinETF#subpoena#tradeinformation
0 notes
Text
Neil Salonen should stand trial for committing perjury based on new evidence!
Don Diligent posted the following on February 6, 2017

Excerpts from Memorandum on Behalf of the Rev. Sun Myung Moon Submitted to Members of the Subcommittee on International Organizations and the Committee on International Relations of the United States House of Representatives
This Memorandum is respectfully submitted to the membership of the Subcommittee on International Organizations (the “Subcommittee”) and the Committee on International Relations (the “Committee”) by the undersigned counsel for Rev. Sun Myung Moon. We have been advised that the Subcommittee has authorized a subpoena directed to Rev. Moon in connection with the Subcommittee’s pending investigation of Korean-American relations, and that it is now considering whether such a subpoena should in fact be issued.
Chairman Fraser has suggested, without disclosing his basis for doing so, the existence of possible links between the KCIA and “persons or organizations affiliated with the Rev. Sun Myung Moon.” However, during the recent public hearings conducted by the Subcommittee, the purely speculative nature of any such inference became clear…charges were rebutted by Neil Albert Salonen in his testimony before an executive session of the Subcommittee.
In fact, both Rev. Moon and other members of the Church have made repeated and emphatic statements – both before the Subcommittee and in other forums – that the Unification Church has no affiliation, either overt or covert, with the South Korean Government or any agency thereof, and that Rev. Sun Myung Moon is a religious leader who has no association or connection with any governmental agency or body.
Even more importantly, logical analysis supports the proposition that there is no link between the Korean government and the Unification Church.
In light of the speculative nature of the Subcommittee’s “evidence”…it is respectfully submitted that before the Subcomittee can legitimately summon Rev. Moon as a witness, it must demonstrate by direct and reliable evidence that an affiliation exists between the Unification Church and the Korean government…“Unevaluated” and speculative testimony and intelligence reports – especially where demonstrably erroneous in their description of underlying facts simply do not and cannot satisfy the Subcommittee’s burden.
Moreover, the religious faith of individual members of the Unification Church will necessarily be affected by compelling their religious leader to testify…
At a minimum, the Subcommittee must first adduce reliable, first-hand information showing that Rev. Moon is an agent of the Korean government. Only on the basis of such information should the Committee permit the subpoena to be served.
DATED: New York, New York May 12, 1978
Respectfully submitted,
Law Offices of Charles A. Stillman
Attorneys for Rev. Sun Myung Moon
Excerpt from Investigation of Korean-American Relations (Moonies, aka Unification Church)Relations with the Park Government
In the late 1950’s, Moon’s message was favorably received by four young, English-speaking Korean Army officers, all of whom were later to provide important contacts with the post-1961 Korean Government. One was Pak Bo Hi, who had joined the ROK Army in 1950. Han Sang Keuk (aka Bud Han), a follower of Moon’s since the late 1950’s, became a personal assistant to Kim Jong Pil, the architect of the 1961 coup and founder of the KCIA. Kim Sang In (Steve Kim) retired from the ROK Army in May 1961, joined the KCIA and became an interpreter for Kim Jong Pil]. He continued as a close personal aide to Kim Jong Pil until 1966. At that time, Steve Kim returned to his position as KCIA officer, later to become the KCIA’s chief of station in Mexico City. He was a close friend of Pak Bo Hi and a supporter of the UC. The fourth, Han Sang Kil, was a military attache at the ROK Embassy in Washington in the late 1960’s. Executive branch reports also linked him to the KCIA. On leaving the service of the ROK Government, Han became Moon’s personal secretary and tutor to his children.
From page 6 of New Age Frontiers - December 1962
Dear Miss Kim (Young Oon Kim),
Thanks you so much for your letter. In 1960, we tried to locate you in Oregon but later found you had moved to California. As you no doubt realize, activities of the last months have excluded any letter writing–even my close friends (your (her) three dedicated students)Sang, Bo Hi, and Bud. I hope some day we can meet. Mrs. Butterwick joins in sending all good wishes.
Lt. Col. John T. Butterwick
690 Geneva Place
Davis Islands, Tampa 6. Fla.
Excerpt from A History Of The Unification Church In America, 1959–74 - Emergence of a National Movement - Michael L. Mickler
Jong Pil Kim. Chairman of the newly emerged Supreme Council for National Reconstruction (SCNR) in Korea, Jong Pil Kim journeyed to the United States in November, 1961, for talks with American leaders and a meeting with President John Kennedy. After the talks, he spent two days in San Francisco before returning to Korea. During his stay in the Bay Area, Miss Kim received a call from a Colonel Han, a church member and one of Jong Pil Kim’s aides and interpreters. He had arranged for Miss Kim and five American members not only to attend a reception but also to have an audience with the chairman.
At the reception, members met another aide who had recently joined the church, and in the private audience Miss Kim spoke of her work in America. In addition, each American member gave a brief testimony of their experiences with the church. While the meeting was relatively routine, its significance was enormous for a community which was struggling with obscurity and rejection.
Excerpts from pages 25-28 of New Age Frontiers - September 1967
Message of Governor Kyong Whan Pak
On Sunday, July 30, we had a visitor from Korea who is the Governor of Kangwon Province, Kyong Whan Pak. He is the first governor to invite our group to lecture for anti-Communist purposes. He is visiting America at the invitation of the State Department. Mr, Bo Hi Pak invited him to meet with us on Sunday, and he gave the following talk after the service:
“…This is my third trip to the United States. The first trip was made at the same time as Mr. Pak for purposes of study. The second trip, also under military auspices, was in 1959. This time, my third trip, I came at the invitation of the State Department…Before I became governor, 90 percent of my activity was in military life…I have formed a group which is nothing like an organized religious body…I plan to train 3000 rural youth…with a new ideology to counteract the Communist ideology…”
“There are about sixty young people from the Unification Church who are assisting me in the training of the young people…I chose them to assist me in the program…Each month these young people of the Unification Church give an antiCommunist lecture…In order to help them materially, I have issued bus passes to them to use in their travels in the province Kang Won…I would like to express my whole-hearted congratulations for the expansion of the Unification movement abroad, particularly in America…I would also like to extend the invitation to you to visit Korea, particularly my province. I will be most happy to welcome you and show you around.”
Excerpt from New Age Frontiers - November 1970
Nora Spurgin - More Inspiring Give and Take in Korea
October 14…A visit to the Korean CIA was scheduled for us in the afternoon. We were given a guided tour through exhibitions of North Korean culture and history; a briefing on statistics about present North Korea; a movie on North Korea; and discussion (questions and answers) with a spy who had defected from North Korea.
Excerpt from The Rising Tide - March 3, 1975
Mr. and Mrs. Fefferman and FLF President Neil Salonen, together with representatives of the Japanese and European couples who participated in the wedding, Unification Church President Young Whi Kim and German Unification Church President Paul Werner met with Korean Prime Minister Kim Jong-pil on February 5 in Seoul. Rev. Kim presented the Prime Minister with a contribution of more than U.S. $100,000 for the Korean New Village Movement, from contributions given by the 3600 wedding participants.
Related articles below
Materialism Revisited by Neil Salonen (1968)
Moon’s religion was always involved in politics: ‘From Korea with Love’ by John D. Marks
Allen Tate Wood on Sun Myung Moon and the UC (and Freedom Leadership Foundation and Neil Salonen)
Korean Moonshine (1979?)
Neil Salonen asked about ‘Pikareum’ on TV
Prime Minister Kishi of Japan, organised crime and the Moon involvement in Japanese politics gained protection for the UC
World Domination – Sun Myung Moon’s many attempts ended in failure
On Salonen, Moon, and U.S. Politics
#neil salonen#unification church#moonies#flf#freedom leadership foundation#dan fefferman#susan fefferman#kcia#nora spurgin#current members#leadership#UC leadership#church leadership#the rising tide#fraser committee#young hwi kim#young whi kim#new village movement#Korean New Village Movement#sang kil han#bo hi pak#republic of korea#south korean government#south korea
0 notes
Text
The Evolution Of Different Legal Service Providers
We seek to learn all business stakeholders by combining related tutorial theory with data-driven analysis and punctiliously drawn examples of profitable innovations. Most legal service providers operate on a county or state level and often have elder law applications or employees members dedicated to serving older adults. Increase your aggressive edge by delivering more sophisticated legal services in a fraction of the time it traditionally takes whereas sustaining your cost-advantages.
This service walks you through all the mandatory steps and paperwork to guard your mental property. Remember that when you provide contract help with sources they should perform the work, you may be including value to what they carry to the table. An upcharge is an affordable approach to cowl the bills of those further assets you’re providing. In common, it's a good suggestion in your engagement letters to discuss your use of sources and the rates at which you are billing for them.
Phone help representatives are available 14 hours per day during the week and nine hours per day on weekends. If you’re not pleased with the final product, merely contact customer legal service providers service inside 60 days for a full refund. Whether you’re planning your estate or renting out a property, LegalZoom makes it fast and painless to get the documents you want.
As a team they provide help corresponding to finding defendants and witnesses; making ready third-party subpoenas; Westlaw and LexisNexis legal research; doc review; e-discovery and knowledge collection assistance and more. As the legal occupation pivots from training in traditional law office space to working from shared spaces, hybrid places of work, and even the fully virtual law workplace legal service, ALSPs provide experience and effectivity for attorneys and law firms. LSW, a number one and trusted LPO, supplies high quality legal outsourcing solutions, strategic control & dramatic cost-savings to law firms, attorneys and corporates worldwide. We imagine in seamless integration along with your objectives and might serve as an extension of your legal division on your increased operational efficiency.
As a quantity one progressive research and advocacy organization, our mission is to remove poverty in North Carolina by ensuring that each family in the state has entry to the resources, services and honest treatment it needs to realize... The mission of the Children’s Law Center of Central North Carolina is to provide children legal services with quality legal advocacy focusing on home violence points, high battle custody circumstances and guaranteeing access to training. Our final goal is to enable youngsters to develop up in protected environments and to become emotionally wholesome adults.
Offer holistic and value-driven options to shoppers by combining high quality expertise with technology. Work more carefully with your shoppers by reviewing paperwork faster with excessive accuracy to interpret quality results and supply meaningful insights. If you’re an entrepreneur initially of your small law services business journey, then you could need legal services that may aid with enterprise formation solutions. However, if your corporation is already established, then you could need help with contracts and hiring new employees. You additionally get a flat 25% low cost on legal services not covered in your contract together with your designated law agency.
1 note
·
View note
Text

I posted 3,412 times in 2022
That's 574 more posts than 2021!
146 posts created (4%)
3,266 posts reblogged (96%)
Blogs I reblogged the most:
@cephalopodvictorious
@ardent-ace
@whetstonefires
@angeloftheeasterngate
@doccywhomst
I tagged 1,957 of my posts in 2022
Only 43% of my posts had no tags
#queue - 87 posts
#us politics - 76 posts
#youtube - 65 posts
#oh tumblr - 50 posts
#dracula daily - 40 posts
#vile puns - 29 posts
#critters - 27 posts
#funny - 27 posts
#cats - 22 posts
#other people's art - 22 posts
Longest Tag: 140 characters
#my therapist didn't understand why i was peeved at that 'the good news is the only vaccinated people in the study who died had comorbidities
My Top Posts in 2022:
#5
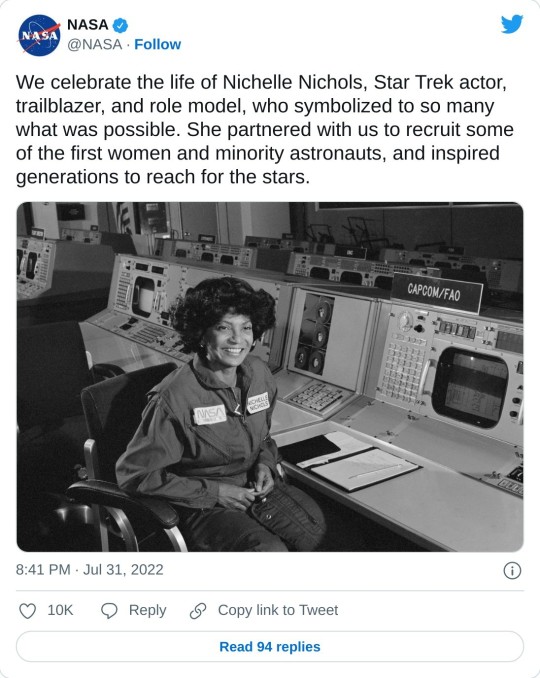
1,209 notes - Posted July 31, 2022
#4
This woman may have a point, although I fear she overestimates the amount of work Elon Musk does vs what he takes credit for.
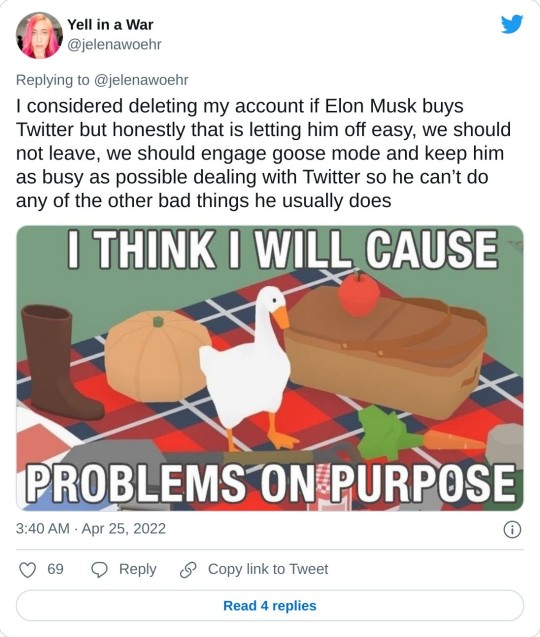
See link above for her whole thread, but the parts that jumped out at me:
At first I thought “how terrible, I hate Elon Musk” and then I realized that having to own Twitter is an entirely appropriate punishment for Elon Musk
The world’s richest man would rather be subpoenaed twice a year to testify before Congress about why he used the official @/Twitter account to post 12 Reddit memes calling for the overthrow of the government than just like… having sex in a luxury submarine?
[...]
I considered deleting my account if Elon Musk buys Twitter but honestly that is letting him off easy, we should not leave, we should engage goose mode and keep him as busy as possible dealing with Twitter so he can’t do any of the other bad things he usually does
[Image: screencap from Horrible Goose Game with caption "I think I will cause problems on purpose" /end image]
Like… think about it… if we all make sure that Twitter is as enormous a headache as possible… and his gigantic ego is fully invested in proving he can “fix Twitter…”
We can completely freeze all of his other destructive activities. Goodbye monkey torture hobby!!!
I mean sure he can still just hire people to do the other stuff BUT it is fairly well established with Elon that, once his attention wanders, his projects never move again (see: HyperLoop).
He has the same collection of abandoned craft projects I do, his are just expensive.
Anyway I think maybe the entire cosmic purpose of Twitter all along was to become a massive Elon-distraction device.
He is our Minotaur. We are his labyrinth. All things are processing according to a greater plan.
2,332 notes - Posted April 24, 2022
#3
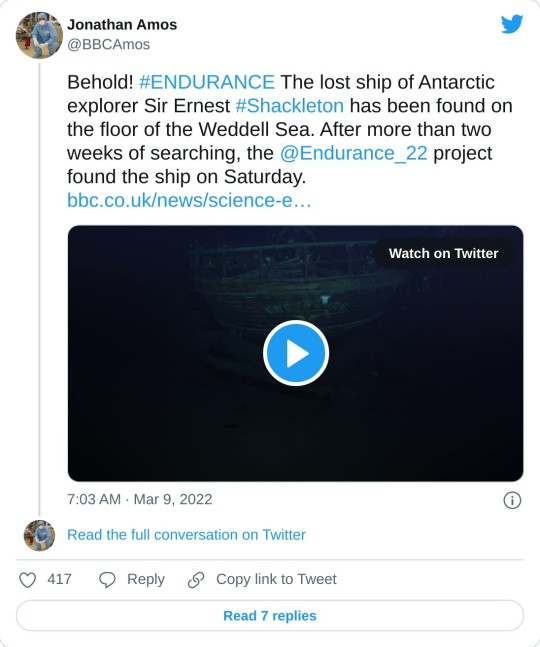
The Endurance was trapped in Antarctic ice for about a year and finally sank in November 1915:

Famously, Ernest Shackleton used a jury-rigged lifeboat to sail over 700 miles to a whaling station, seek help, return and rescue his entire crew, which imo is a greater feat than reaching the South Pole. The ocean currents circling Antartica are some of the stormiest and coldest in the world. How the heck do you cross that in a small open boat without sinking, starving, or freezing to death?
Anyway, I'm impressed that the Endurance looks to be in pretty good shape considering how much it got crushed by pack ice. And it was just discovered yesterday (March 9)!
5,415 notes - Posted March 9, 2022
#2

19,263 notes - Posted June 10, 2022
My #1 post of 2022
[Description: Tiktok compilation of two dancers in sweats or other gym clothes interpreting various iPhone alert sounds as dance moves synchronized with and vaguely mimicking the sound effects.]
26,166 notes - Posted June 29, 2022
Get your Tumblr 2022 Year in Review →
--------
Well at least #3 is an actual educational post, which I'm proud to have posted before news media, since I just happened to catch the initial tweet rippling across archaeology twitter.
#2 is educational too, actually: there's a good reason why those early reconstructions of pterosaurs look like flying possums.
Here's the director's cut Endurance/Shackleton post in which I recounted their incredible saga with actual photos from the expedition
0 notes