#the original email account was deleted without my consent there’s no getting it back and staff won’t answer my many many messages and posts
Text
Does everyone remember how I’ve mentioned that this blog is only accessible through the mobile app that it has me signed in on because I no longer have access to my old email and do not remember my old password and after many many attempts to contact @staff regarding being given the ability to change the email so I can log in if I need to rather than just hope the app keeps me logged in I have still not received any response. That being said for the last few years I just figured I would make another blog with my correct email when I am inevitably not able to access this blog anymore which is why my likes and following list is public so that if I had to make another blog I could still see those to reference but I’ve been thinking about it the last few months and I’m worried how many of my friends I would lose because I would be on another blog and even if I sent them a message maybe they wouldn’t see it or think it was legit or something? Also then it’s kind of begging people to follow you if you slide in their DM’s like hey we actually know each other and we’re friends I’m just on a different blog! So I was thinking maybe I should make another blog with my current email address that I won’t lose access to and then just list it in the bio and pinned post on this blog? So that my friends (you!) could stay with me if I lost access to this, what do you think?
#I’m probably going to pin this and then reblog it a few times over the next few days cause I really have been thinking about this quite a bi#quite a bit I’m interested to know if you guys think it’s a good idea#💜#the original email account was deleted without my consent there’s no getting it back and staff won’t answer my many many messages and posts#so I suppose I could make a new blog and link it here?
16 notes
·
View notes
Text
So a story of me trying to adapt to modern ways.
When i was a mere 20 year old I would carry in my back pocket a notebook and I would scribble ideas and poetry and just stuff that inspired me. But of course I have to adapt to modern way of doing this, as I have fallen out of the original habit. So I started a email account and send texts from my phone to that email account as my new “notebook.” So I am driving around today after work and I want to record an idea I had for my story that I am thinking of building a campaign around, called “The Boogie Shoes Burgle” So I struggle with magic systems and I have a hard time imagining the mechanics of how magic works in my worlds because I believe in hard scientific principles. I have been getting better at just letting whatever be will be but there are somethings I need worked out to some degree. Today I figured out how magic could work in my campaign without getting into particle physics. I was driving and thought I could get the Google assistant to write my notes for me and send it to the “notebook”. But while the ability of the device to hear you is amazing, comprehension via word choice is lacking and though we could be in awe of a surveillance ability our Artificial intelligence is very lacking. We got good tech but dumb AI. Anyways this is me arguing with the text to speech feature. Have fun.
“ So I'm looking to add a layer to my world in the Boogie Boogie Shoes burgo Virgo bird golf Virgo these are all wrong it is burger burger you Virgo spelled b burgle is spelled you got it there there it is okay so delete everything except Virgo no not Virgo Burgaw no not Burgaw Bergl bergel bergel you have it right there why are you what how am I taking burgle in a way that you are not understanding you know I'm saying Virgo stop saying Virgo or Burgaw or whatever weird Wings there's whatever weird shoes burgle Boogie Shoes burgle yes that's it okay so magic works by the waste appointed by mind flayers outputted yes and a low-level psychic or telepathic ability in humans and the thin layer between the real Dimension and an elemental Dimension that sort of like layered over are the real reality okay so true magic is the summation of Mind flayer waste particles human being telepathic or psychic abilities and a thin barrier between the real world and dreaming Elementals that's Magic and consent and and send end of message send send a message stop composition end stop”
I am an old man.
6 notes
·
View notes
Text
Original quotes can be found on Quora by searching Veruca Guerra.
MEMES are available on Facebook accounts of phones stolen about a month ago, during time my husband and I were in custody, for looting to succeed, and that's all it seems; search 602.334.8231 and 623.216.2042. Other memes exist on Twitter, Instagram, and in apple hidden folders for iPhone x imei 35.353.939.725.469.9, purchased by a cosigner, who may have become a better engineer ever since Galaxy S9+ R38FB40WPK fell into hands of Modena Apartment janitor friends of his, and 480.450.8800 may have content available on the server as well.
See these names, too: Philanthr0pia, Philanthr0pia Noir, Lemon Jaw, genociple, imei.blood, Vera.Fi.1984, Veruca.Axis, Veruca.Dex, Vera.Karavchuk.5, polygraph_meth, c_ghett0, Cigarette Butt, DEAprogram, banprofi, intel_io, radiotheropath, ibm2nite, SatanQA@yahoo, and about 100 emails I have originated, but no longer have access to, some of which continue to remunerate profit or royalties, without paying their creator. None of the problems I have listed are legally there due to health or medication ritual - as I have not given consent to WebMD not Dignity Health to have voted me off my medications, and they would be in violation of HIPAA if they even knew of my medical routine, or habits as they call them, since I was not the individual who contacted them, even if it was done from my email, and no guardian, account manager, or representative has been hired by myself to collect payment for any of my written works, in case this was failed to be reported by the system internet technology presides over. I currently Bank with B of A, in case Zendesk Itself feels bad about logging into Omnipoems gmail/ Google
All of these have been used, edited, and deleted in part - or posted to - by unauthorized users, so the sooner those locations are identified, the sooner I can get back to writing and making memes.
1 note
·
View note
Photo

New Post has been published on https://randykopplin.com/a-sure-fire-way-to-lose-an-online-business-and-reputation/
A Sure-Fire Way To Lose An Online Business and Reputation

A Sure-Fire Way To Lose An Online Business and Reputation

Broken links, lost domains need to be well managed to prevent hacking, trojan horses and viruses being distributed to your visitors and members.
Broken Links Are Bad For Business. What Is A Broken Link?
Broken links are links that don’t work. Some of the reasons why links don’t work include:
A website is no longer available
A webpage was moved without a redirect being added
The URL structure of a website was changed
Linking to a third-party page, and not knowing when they change the URL or move the page
Whatever the cause, broken links are frustrating errors that need to be addressed immediately. If you click a broken link, you’ll see a 404-page error or similar message explaining the webpage is not available.

Broken Links Negatively Affect SEO
Search engines see links as a vote for a website’s quality. Links to your website and links within your website can affect where your website ranks in search results. Google frowns upon dead links. Because of this, it’s best practice to either remove or update broken links.
Cleaning up broken links can add context to your website, improve user experience, and make content within your website easier for visitors and search engines to discover. On the other hand, websites with too many broken links can be a signal of low quality to search engines.
The natural tendency for links to eventually break is called link rot, and it’s a widespread issue. It has been found in past studies that you can expect to lose about a quarter of the links on your website every seven years. One of the main reasons link rot exists is because websites become unavailable when they are abandoned or when interests change. Both websites and active links aren’t active forever, so regularly fixing broken links is a good practice, especially since links within your website can affect how high your website ranks in search results.

Lost Domains Are Very Often Hijacked
Domain Hijacking is a form of theft where the attacker takes access of a domain name without the consent of the original registrant. Hijacking can happen due to security flaws on your end or the end of your domain/hosting company.
How is it done?
These days businesses are coming online, and their web properties are a major asset to companies. One reason that can cause your domain name to be hijacked could be your negligence towards security. When you register a new domain; the provider gives you access to the domain’s Control Panel. This panel lets you change your domain’s settings that point to the original server. You will have provided an email address to gain administrative access. If the hacker can access this administrative email account, he can also have control over the domain’s control panel and eventually all the settings.
Another reason is that your domain registration expired, and auto-renewal is disabled. Someone may register your domain in the meantime and you will be left with nothing. You cannot take any actions on the hijacker as his/her actions are completely legal. So to avoid this from happening, you have to make sure you’ve enabled auto-renewal on your domain names and register domains for longer durations.
What are hijacked domains used for?
Malicious use
Usually, the hijacked domains become inaccessible, and if the website was a source of income, you’ve started losing your money as well as your online identity. The hijacker might replace your website with another similar looking website and misuse it for Phishing or other malicious activity. This might fool your users and lead them to enter their sensitive credentials on a fake website.
Domain Transfer
The hacker may transfer the domain’s ownership to some other name. In this case, it is very difficult in fact almost impossible to get your domain back. The hacker may impersonate you and request the domain provider to transfer the domain to some other account or entirely different domain provider. This is a very difficult scenario as you may need legal help here. Also, if you are not able to convince the domain provider about your situation, the company may decline to cooperate.
Recovering a stolen domain name is not always an easy job, and it is therefore imperative that you maintain adequate website security. You need to be protected from any form of website hijacking and theft. There’ve been many cases where the website owners were forced to change their domain names as they were left out with no other option and legal help was way too expensive. So, to avoid any such circumstances, you should keep your Control Panel & email account password secured and enable Domain Privacy Protection.
Using Your Website Resources For Financial Gains
Cybercrime is big! Many times, hackers will try to use your site to direct visitors to:
Some other website that will pay commission to them
Look-alike websites that will steal your personal and financial information
All they need to do is to insert a link that you won’t know is present on your website. When search engines like Google crawl your site, it will index the malicious link and present it on the results page. If somebody uses that link, they will be directed to some other websites and hackers can make money out of that redirection.
The look-alike, spoof websites are more common as they benefit hackers more by providing them with your information. Once your information – such as email ID or credit card information is with them, they’ll use it for personal gains.
What Is A Trojan Or Trojan Horse?

A Trojan is also known as a Trojan horse. It is a type of malicious software developed by hackers to disguise as legitimate software to gain access to target users' systems. Users are typically tricked by some attractive social media adds who then directed to the malicious website thereby loading and executing Trojans on their systems.
Cyber-criminals use Trojans to spy on the victim user, gain illegal access to the system to extract sensitive data.
These actions can include:
Deletes Data
Copies data
Modifies Data
Blocks Data
Disrupts the performance of the target computers or networks
How To Prevent Hacking
There will always be attempts to compromise your site. But if you are prepared, you can prevent hacking by a good percentage. Think of the following as precautions that will help you:
Use A Good Web Firewall
This prevents and shuts down the website as soon as an offensive is launched. And make sure that it is configured correctly.

Update Your Blogging Software & Plugins.
Plugins related to WordPress are often updated, but website owners do not update the ones on their sites as they are unaware or scared to go for the update. They fear the website may be affected as a result. If you are using WordPress you should update the plugins regularly.

SNAP does have some tech-savvy skills to get it to work properly. Most people will just throw in the towel and not even bother with it as it can give problems connecting to social sites due to the recent changes in algorithms and security updates. Markethive has the answer with its SNAP Department. Professional setup and maintenance are available to ensure the safety and ongoing success of your business.
Conclusion
If you own any type of website, social network, blogging site or marketing platform, you need to be on top of your game when it comes to maintaining security. It’s ferocious out there so there’s no room for complacency or ignorance. Even if you don’t own a platform but are working from it, check that the owner has fully complied with these extremely important housekeeping rules for your safety and the safety of your followers. Failing to do so will see its inevitable demise of both your business and reputation.


Deb Williams
Market Manager for Markethive, a global Market Network, and Writer for the Crypto/Blockchain Industry. Also a strong advocate for technology, progress, and freedom of speech. I embrace "Change" with a passion and my purpose in life is to help people understand, accept and move forward with enthusiasm to achieve their goals.
FOLLOW US ON…
Website: https://markethive.com
Token Site: http://markethive.io/
Telegram: https://t.me/markethive_support
Twitter: https://twitter.com/markethive/
Github: https://github.com/markethive /
Reddit: https://www.reddit.com/r/markethive/
Crunchbase: https://www.crunchbase.com/organization/markethive
Medium: https://www.medium.com/@markethive
Bitcointalk: https://bitcointalk.org/index.php?topic=3309067.msg34535452#msg34535452
Telegram News: t.me/Markethive
LinkedIn: https://linkedin.com/company/Markethive
Facebook: https://facebook.com/MarketHive
Youtube: https://youtube.com/Markethive
Randy Kopplin
0 notes
Text
Trans-inclusive Design
Late one night a few years ago, a panicked professor emailed me: “My transgender student’s legal name is showing on our online discussion board. How can I keep him from being outed to his classmates?” Short story: we couldn’t. The professor created an offline workaround with the student. Years later this problem persists not just in campus systems, but in many systems we use every day.
To anyone who’d call that an unusual situation, it’s not. We are all already designing for trans users—1 in 250 people in the US identifies as transgender or gender non-binary (based on current estimates), and the number is rising.
We are web professionals; we can do better than an offline workaround. The choices we make impact the online and offline experiences of real people who are trans, non-binary, or gender-variant—choices that can affirm or exclude, uplift or annoy, help or harm.
The rest of this article assumes you agree with the concept that trans people are human beings who deserve dignity, respect, and care. If you are seeking a primer on trans-related vocabulary and concepts, please read up and come back later.
I’m going to cover issues touching on content, images, forms, databases, IA, privacy, and AI—just enough to get you thinking about the decisions you make every day and some specific ideas to get you started.
“Tried making a Bitmoji again, but I always get disillusioned immediately by their binary gender model from literally step 1 and end up not using it. I don’t feel represented.”
Editorial note: All personal statements quoted in this article have been graciously shared with the express consent of the original authors.
How we can get things right
Gender is expansively misconstrued as some interchangeable term for anatomical features. Unlike the constellation of human biological forms (our sex), gender is culturally constructed and varies depending on where you are in the world. It has its own diversity.
Asking for gender when it is not needed; limiting the gender options users can select; assuming things about users based on gender; or simply excluding folks from our designs are all ways we reify the man-woman gender binary in design decisions.
Names are fundamentally important
If we do nothing else, we must get names right. Names are the difference between past and present, invalidation and affirmation, and sometimes safety and danger.
Yet, many of the systems we use and create don’t offer name flexibility.
Many programmers and designers have a few misconceptions about names, such as assuming people have one moniker that they go by all the time, despite how common it is for names to change over a lifetime. People might update them after a change in marital status, family situation, or gender, or perhaps someone is known by a nickname, westernized name, or variation on a first name.
In most locales, legally changing names is extremely difficult, extremely expensive, requires medical documentation, or is completely out of the question.
Changes to name and gender marker are even more complicated; they tend to be two separate, long-drawn-out processes. To make matters worse, laws vary from state to state within the U.S. and most only recognize two genders—man and woman—rather than allowing non-binary options.Not all trans people change their names, but for those who do, it’s a serious and significant decision that shouldn’t be sabotaged. We can design systems that protect the lives and privacy of our users, respect the fluid nature of personal identity, and act as an electronic curb cut that helps everyone in the process.
Deadnaming
One need only search Twitter for “deadname app” to get an idea of how apps can leave users in the lurch. Some of the most alarming examples involve apps and sites that facilitate real-life interactions (which already involve a measure of risk for everyone).
“Lyft made it completely impossible for me to change my name on its app even when it was legally changed. I reached out to their support multiple times and attempted to delete the account and start over with no result. I was completely dependent on this service for groceries, appointments, and work, and was emotionally exhausted every single time I needed a ride. I ended up redownloading Uber - even though there was a strike against the service - which I felt awful doing. But Uber allowed me to change my name without any hoops to jump through, so for the sake of my mental health, I had to.”
Trans people are more likely to experience financial hardship, so using payment apps to ask for donations is often necessary. Some of these services may reveal private information as a matter of course, leaving them exposed and potentially at risk.
There are also ramifications when linked services rely on our data sources for name information, instigating an unpredictable cascade effect with little or no recourse to prevent the sharing of sensitive details.
These are examples of deadnaming. Deadnaming is what happens when someone’s previous or birth name is used, rather than the name the person uses now. Deadnaming is invalidating at the least, even as a faux pas, but can be psychologically devastating at the other extreme, even putting lives at risk.The experiences of trans, non-binary, or gender-variant folk can vary widely, and they live in disparate conditions throughout the world. Many are thriving and creating new and joyful ways to resist and undo gender norms, despite the common negative narrative around trans lives. Others can face hardship; trans people are more likely to be unstably housed, underemployed, underpaid, and targets of violence in and out of their homes, workplaces, and intimate relationships. The ramifications are amplified for people of color and those with disabilities, as well as those in precarious living/working situations and environments where exposure can put them in harm’s way.
Design for name changes
Here’s what we can do:
Design for renaming. Emma Humphries’ talk on renaming covers this nicely. Airbnb has developed policies and procedures for users who’ve transitioned, allowing users to keep their review histories intact with amended names and/or pronouns.
Get rid of “real name” requirements. Allow people to use names they go by rather than their legal first names.
Clarify when you actually need a legal name, and only use that in conjunction with a display name field.
Have a name change process that allows users to change their names without legal documentation. (It’s likely that you have procedures for marriage-related name changes already.)
Ensure users can still change their display names when connecting with other data sources to populate users’ names.
Don’t place onerous restrictions on changes. Once someone creates a username, web address, or profile URL, allow them to change it.
Draft a code of conduct if you’re part of an online community, and make sure to include policies around deadnaming. Twitter banned deadnaming last year.
Allow people to be forgotten. When people delete their accounts for whatever reason, help them make sure that their data is not lingering in your systems or in other places online.
Update the systems users don’t see, too
Identity management systems can be a mess, and name changes can reveal the failures among those systems, including hidden systems that users don’t see.
One Twitter user’s health insurance company kept their ID number between jobs but changed their gender. Another user updated their display name but got an email confirmation addressed to their legal name.
Hidden information can also undermine job opportunities:
“At a university as a student, I transitioned and changed my name and gender to be a woman. TWELVE YEARS later after being hired to work in the Libraries, the Libraries HR coordinator emailed me that I was listed as male still in the database. He changed it on my asking, but I have to wonder how long… was it a factor in my being turned down for jobs I applied to… who had seen that..?”
Emma Humphries details the hidden systems that can carry out-of-date information about users. Her tips for database design include:
Don’t use emails as unique IDs.
Use an invariant user ID internally, and link the user’s current email and display name to it.
Images
Visuals should allow room for representation and imagination rather than a narrow subset of the usual suspects: figures who appear to be straight, cisgender, able-bodied, and white/Caucasian.
What we can do is feature a variety of gender presentations, as well as not assume someone’s gender identity if they buy certain items.
Some companies, like Wildfang and Thinx, offer a broad array of images representing different races, body sizes, and gender expressions on their websites and in their ads.
Many are also choosing not to hire models, allowing room for imagination and versatility:
“I got a catalog for a ‘classic menswear company’ that features zero photos of any person of any gender. Now if only I could afford an $800 blazer...”
Here's what we can do:
Actively recruit diverse groups of models for photos. And pay them!
If you can’t shoot your own photos, Broadly has recently launched a trans-inclusive stock photo collection free for wide use. Avataaars allows users to create an avatar without selecting a gender.
Information architecture
How we organize information is a political act and a non-neutral decision (librarians have said this for a while). This applies to gender-based classifications.
Many companies that sell consumer goods incorporate gender into their product design and marketing, no matter what. The product itself might be inherently gender-neutral (such as clothing, toys, bikes, or even wine), but these design and marketing decisions can directly impact the information architecture of websites.
Here's what we can do:
Evaluate why any menus, categories, or tags are based on gender, and how it can be done differently:
“Nike has a ‘gender neutral’ clothing category, yet it’s listed under ‘men’ and ‘women’ in the website architecture. 🤔”
Forms
Forms, surveys, and other types of data gathering are surefire ways to include or exclude people. If you ask for information you don’t need or limit the options that people can select, you risk losing them as users.
Here's what we can do:
Critically evaluate why you are asking for personal information, including gender. Will that information be used to help someone, or sell things to your advertisers?
"Why does the @CocaCola site make me select a gender just to make a purchase? Guess my family isn't getting personalized Coke bottles for Christmas."
If you are asking users for their gender, you’d better have a good reason and options that include everyone. A gender field should have more than two options, or should ask for pronouns instead. When including more than binary options, actually record the selections in your databases instead of reclassifying answers as male/female/null, otherwise you risk losing trust when disingenuous design decisions become public.
Honorifics are infrequently used these days, but it takes little work to add gender-inclusive titles to a list. For English-language sites, “Mx.” can go alongside “Mr.” and “Ms.” without fuss. United Airlines debuted this option earlier this year.
Content
Here's what we can do:
Avoid inappropriately gendered language. Your style guide should include singular “they” instead of “he/she” or “s/he,” and exclude frequently used words and phrases that exclude trans folks. Resources such as this transgender style guide are a quick way to check your language and benchmark your own content guidelines.
Check assumptions about gender and biology. Not everyone who can have a period, can get pregnant, or can breastfeed identifies as women or mothers—just as not everyone who identifies as women or mothers can have periods, can get pregnant, or can breastfeed. Thinx, a company that sells period underwear, has an inclusive tagline: “For people with periods.”
Avoid reinforcing the binary. Groups of people aren’t “ladies and gentlemen” or “boys and girls.” They are folks, people, colleagues, “y’all,” or even “all y’all.”
Pronouns aren’t “preferred”—they’re just pronouns. Calling pronouns preferred suggests that they’re optional and are replacing a “true” pronoun.
Avoid reinforcing stereotypes about trans people. Not all trans people are interested in medically transitioning, or in “passing.” They also aren’t fragile or in need of a savior. Gender is separate from sexual orientation. You can’t “tell” someone is trans.
Privacy, surveillance, and nefarious AI
We’ve heard the story of algorithms identifying a pregnant teen before her parents knew. What if an algorithm predicts or reveals information about your gender identity?
Inferences. Users’ genders are assumed based on their purchase/browsing history.
Recommendations. A user bought something before they transitioned and it shows up in “recommended because you bought X.”
Predictions. Users’ genders are not only inferred but used to predict something else based on characteristics of that gender. Even if you don’t tell big websites what your gender is, they assume one for you based on your interests. That kind of reductive essentialism can harm people of all genders. One of this article’s peer readers summed this up:
“Gender markers are a poor proxy for tastes. I like dresses, cute flats, and Raspberry Pis.”
Flashbacks. “On this day” algorithms remind users of the past, sometimes for better (“I’ve come so far”) or for worse (“don’t remind me”).
AI-based discrimination
AI and surveillance software can also reinforce norms about what men’s and women’s bodies should look like, resulting in harrowing airline travel experiences and creating AI-based discrimination for trans people.
So, too, can trans folks’ public data be used for projects that they don’t consent to. Just because we can use AI for something—like determining gender based on a face scan—doesn’t mean we should.
Here's what we can do:
Read up and proactively mitigate bias.AI and algorithms can reflect developers’ biases and perpetuate stereotypes about how people’s bodies should look. Use AI to challenge the gender binary rather than reinforce it. Design for privacy first. Hire more types of people who represent different lived experiences.
Toward a gender-inclusive web
The ideas I’ve offered here are only starting points. How you choose to create space for trans folks is going to be up to you. I don’t have all the solutions here, and there is no singular trans experience. Also, language, definitions, and concepts change rapidly.
We shouldn’t use any of these facts as excuses to keep us from trying.
When we start to think about design impact on trans folks, the ideas we bring into question can benefit everyone. Our designs should go beyond including—they should affirm and validate. Ideally, they will also reflect organizational cultures that support diversity and inclusion.
Here's what we can do:
Keep learning. Learn how to be a good ally. Pay trans user research participants to help validate your design assumptions. Hire trans people on your team and don't hang them out to dry or make them do all the hard work around inclusion and equity. Make it everyone’s job to build a more just web and world for everybody.
Editorial note: All personal statements quoted in this article have been graciously shared with the express consent of the original authors.
This article is stronger and wiser thanks to Mica McPheeters at A List Apart and the following peer readers. Thank you.
Jake Atchison
Katherine Deibel, Ph.D.
Justina F. Hall
Austyn Higgs
Emma Humphries
Tara Robertson
Levi R. Walter
Trans-inclusive Design published first on https://deskbysnafu.tumblr.com/
0 notes
Text
GDPR is coming, but what does it mean to my school?
You may have heard of the General Data Protection Regulation (or GDPR); if you haven’t, it is a change in the legislation regarding how personal data can be stored and used and it comes into effect on the 25th May 2018. But what does it actually mean? What do we need to change in order to be compliant with this new law?
Why GDPR?
Global communications has changed significantly in the last 50 years, and with the growth of internet technologies and computing, it was inevitable that data privacy laws would need redoing - especially considering the legislation it replaces in the UK is now 20 years old (Data Protection Act 1998).
Apart from legislative reasons, there are real problems that GDPR aims to solve. It has become clear over the past 10 years that personal data is a valuable commodity (just look at Google and Facebook among other companies), where products and services are free at the point of use, supported by advertising and other processes that use the data collected.
Over the past few years there have also been a string of huge data breaches that have shown companies are hoovering up massive amounts of personal data, which has led to questions such as:
What processes do they have in place to keep the data secure?
Are they handling the data correctly?
Do they have permission to use the data in the ways they are using it?
Do they even need to hold the data in order to perform the function we asked them to perform?
GDPR will strengthen and unify data protection for individuals within the EU, and will force all organisations processing personal data about EU citizens to abide by the new regulation.
What is personal data?
Personal data is defined as any information relating to an identifiable person who can be directly or indirectly identified from it. This is basic information such as name and email address, photos, and IDs.
This includes any electronically gathered and/or stored information, as well as paper-based storage.
There are also ‘special categories’ of personal data that schools are likely to handle, such as ethnicity and health information, which have additional rules around how the data should be stored and handled.
Controllers and Processors
GDPR applies to both controllers and processors, so all parties involved can be liable.
As a controller you are required to determine the purposes and means of processing personal data, and you have legal obligations to ensure your contracts with data processors are GDPR compliant.
As a processor you are responsible for processing personal data on behalf of a controller, you are required to maintain records of personal data and processing activities.
Collecting Data
You must have a good reason to collect and hold personal data, which needs to fall into one of the six lawful bases:
The Data Subject has given explicit consent for the data to be collected and used for a particular purpose
It is necessary to process the to fulfil a contract you have with the Data Subject
It is necessary to process the data to comply with a legal obligation you have
It is necessary to process the data to protect the vital interests of someone
It is necessary to process the data to perform a task in the public interest
It is necessary to process the data for the purposes of your legitimate interests
Each piece of personal data processed by the school must be attributed to one of these bases otherwise the processing is not lawful. Much of the personal data processed by a school (or other state funded educational establishment) will fall under the public task base. But you should always ensure that this is the case. For example, it’s lawful to collect student address and telephone number under public task but it is not lawful to then share that with other third parties for a ‘non-core’ task without gaining appropriate consent.
Reasons for processing data
The new regulations are designed to prevent organisations from collecting massive amounts of personal data, when they don’t necessarily need it for the purpose it was collected for, or that purpose has been served and there is no longer a need to keep it.
Part of preparing for the new regulations is going to be about auditing all the personal data you hold, and determining whether you actually need it. This process should also be documented, because we will all have personal data that we no longer need. Documenting what data there is, why you need it or how it has been discarded, is evidence that you have proper processes in place should a data breach occur.
This alone is not going to be a simple task, when you get down to stores of unstructured data, such as Word documents, spreadsheets, and email archives; determining whether they contain personal data, why it was created, and who’s data it contains, then deciding what to do with that data is not going to be an easy task.
What is a data breach?
The definition of a personal data breach is now more robust and clear than previous legislation; a personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data.
Whether accidental or deliberate, anything that causes personal data to be lost, destroyed, corrupted,disclosed or unavailable, for whatever reason (for example, if it becomes encrypted by malware), can be considered a breach, and the ICO must be notified within 72 hours of the breach being discovered.
If the breach is significant enough to adversely affect the rights or freedoms of data subject(s), they must also be notified.
All this adds up to mean that you must have a plan in place for how data is to be protected,, how your systems should be monitored for data breaches, and for what happens if a breach occurs. Staff will need training on how to handle data and record how it is used.
Rights of the Individual
GDPR is designed to give control over personal data back to the data subject, as and such it defines a number of individual rights over that data that organisations must adhere to, they are:
The right to be informed
The right of access
The right to rectification
The right to erasure
The right to restrict processing
The right to data portability
The right to object
Rights in relation to automated decision making and profiling
Individuals whose data you will be processing now have the right to be informed about the collection of any of their personal data, the reason you are collecting it, how it will be processed, who it will be shared with, and how long it will be held for.
They also have the right to request to see that data, for that data to be available for use by other services that the individual requires, for any incorrect information to be corrected, or for data be deleted (depending on the basis for the data being processed). They can also restrict usage of the data, and for personal data processed on the basis of their consent, the individual has the right to withdraw consent at any time.
The basis for processing the personal data of a child is also more complex, as parental consent may also be required.
Conclusion
The current data protection act places a statutory requirement upon schools to comply and GDPR is an evolution of these requirements, with transparency and accountability on both the controller and processors’ part, and on control over that data for the data subject.
It is not going to be an easy task for any organisation to evaluate and consolidate the data they have, and put in place the training and processes needed to remain compliant in the future. But GDPR is not something that will ever be completed; it is an ethos and a set of processes that need weaving into every area of your organisation where personal data is handled, and as its implementation matures we will no doubt see organisations struggle with certain aspects.
The 25 May 2018, when the legislation comes into force, should not be viewed as a finishing line, but by developing a plan to get to a place of compliance, and getting the people in your organisation to start thinking about how data is handled and processed, you will be well on the road.
For more help with knowing your obligations and developing your plan, you can access our GDPR Guidance for Schools and Colleges:
GDPR Guidance for Schools and Colleges
This article was originally published by SWGfL
GDPR
data protection
360data
from RSSMix.com Mix ID 8239594 https://www.saferinternet.org.uk/blog/gdpr-coming-what-does-it-mean-my-school
via IFTTT
0 notes
Text
GDPR is coming, but what does it mean to my school?
You may have heard of the General Data Protection Regulation (or GDPR); if you haven’t, it is a change in the legislation regarding how personal data can be stored and used and it comes into effect on the 25th May 2018. But what does it actually mean? What do we need to change in order to be compliant with this new law?
Why GDPR?
Global communications has changed significantly in the last 50 years, and with the growth of internet technologies and computing, it was inevitable that data privacy laws would need redoing - especially considering the legislation it replaces in the UK is now 20 years old (Data Protection Act 1998).
Apart from legislative reasons, there are real problems that GDPR aims to solve. It has become clear over the past 10 years that personal data is a valuable commodity (just look at Google and Facebook among other companies), where products and services are free at the point of use, supported by advertising and other processes that use the data collected.
Over the past few years there have also been a string of huge data breaches that have shown companies are hoovering up massive amounts of personal data, which has led to questions such as:
What processes do they have in place to keep the data secure?
Are they handling the data correctly?
Do they have permission to use the data in the ways they are using it?
Do they even need to hold the data in order to perform the function we asked them to perform?
GDPR will strengthen and unify data protection for individuals within the EU, and will force all organisations processing personal data about EU citizens to abide by the new regulation.
What is personal data?
Personal data is defined as any information relating to an identifiable person who can be directly or indirectly identified from it. This is basic information such as name and email address, photos, and IDs.
This includes any electronically gathered and/or stored information, as well as paper-based storage.
There are also ‘special categories’ of personal data that schools are likely to handle, such as ethnicity and health information, which have additional rules around how the data should be stored and handled.
Controllers and Processors
GDPR applies to both controllers and processors, so all parties involved can be liable.
As a controller you are required to determine the purposes and means of processing personal data, and you have legal obligations to ensure your contracts with data processors are GDPR compliant.
As a processor you are responsible for processing personal data on behalf of a controller, you are required to maintain records of personal data and processing activities.
Collecting Data
You must have a good reason to collect and hold personal data, which needs to fall into one of the six lawful bases:
The Data Subject has given explicit consent for the data to be collected and used for a particular purpose
It is necessary to process the to fulfil a contract you have with the Data Subject
It is necessary to process the data to comply with a legal obligation you have
It is necessary to process the data to protect the vital interests of someone
It is necessary to process the data to perform a task in the public interest
It is necessary to process the data for the purposes of your legitimate interests
Each piece of personal data processed by the school must be attributed to one of these bases otherwise the processing is not lawful. Much of the personal data processed by a school (or other state funded educational establishment) will fall under the public task base. But you should always ensure that this is the case. For example, it’s lawful to collect student address and telephone number under public task but it is not lawful to then share that with other third parties for a ‘non-core’ task without gaining appropriate consent.
Reasons for processing data
The new regulations are designed to prevent organisations from collecting massive amounts of personal data, when they don’t necessarily need it for the purpose it was collected for, or that purpose has been served and there is no longer a need to keep it.
Part of preparing for the new regulations is going to be about auditing all the personal data you hold, and determining whether you actually need it. This process should also be documented, because we will all have personal data that we no longer need. Documenting what data there is, why you need it or how it has been discarded, is evidence that you have proper processes in place should a data breach occur.
This alone is not going to be a simple task, when you get down to stores of unstructured data, such as Word documents, spreadsheets, and email archives; determining whether they contain personal data, why it was created, and who’s data it contains, then deciding what to do with that data is not going to be an easy task.
What is a data breach?
The definition of a personal data breach is now more robust and clear than previous legislation; a personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data.
Whether accidental or deliberate, anything that causes personal data to be lost, destroyed, corrupted,disclosed or unavailable, for whatever reason (for example, if it becomes encrypted by malware), can be considered a breach, and the ICO must be notified within 72 hours of the breach being discovered.
If the breach is significant enough to adversely affect the rights or freedoms of data subject(s), they must also be notified.
All this adds up to mean that you must have a plan in place for how data is to be protected,, how your systems should be monitored for data breaches, and for what happens if a breach occurs. Staff will need training on how to handle data and record how it is used.
Rights of the Individual
GDPR is designed to give control over personal data back to the data subject, as and such it defines a number of individual rights over that data that organisations must adhere to, they are:
The right to be informed
The right of access
The right to rectification
The right to erasure
The right to restrict processing
The right to data portability
The right to object
Rights in relation to automated decision making and profiling
Individuals whose data you will be processing now have the right to be informed about the collection of any of their personal data, the reason you are collecting it, how it will be processed, who it will be shared with, and how long it will be held for.
They also have the right to request to see that data, for that data to be available for use by other services that the individual requires, for any incorrect information to be corrected, or for data be deleted (depending on the basis for the data being processed). They can also restrict usage of the data, and for personal data processed on the basis of their consent, the individual has the right to withdraw consent at any time.
The basis for processing the personal data of a child is also more complex, as parental consent may also be required.
Conclusion
The current data protection act places a statutory requirement upon schools to comply and GDPR is an evolution of these requirements, with transparency and accountability on both the controller and processors’ part, and on control over that data for the data subject.
It is not going to be an easy task for any organisation to evaluate and consolidate the data they have, and put in place the training and processes needed to remain compliant in the future. But GDPR is not something that will ever be completed; it is an ethos and a set of processes that need weaving into every area of your organisation where personal data is handled, and as its implementation matures we will no doubt see organisations struggle with certain aspects.
The 25 May 2018, when the legislation comes into force, should not be viewed as a finishing line, but by developing a plan to get to a place of compliance, and getting the people in your organisation to start thinking about how data is handled and processed, you will be well on the road.
For more help with knowing your obligations and developing your plan, you can access our GDPR Guidance for Schools and Colleges:
GDPR Guidance for Schools and Colleges
This article was originally published by SWGfL
GDPR
data protection
360data
from Safer Internet Centre https://www.saferinternet.org.uk/blog/gdpr-coming-what-does-it-mean-my-school
via IFTTT
0 notes
Text
GDPR is coming, but what does it mean to my school?
You may have heard of the General Data Protection Regulation (or GDPR); if you haven’t, it is a change in the legislation regarding how personal data can be stored and used and it comes into effect on the 25th May 2018. But what does it actually mean? What do we need to change in order to be compliant with this new law?
Why GDPR?
Global communications has changed significantly in the last 50 years, and with the growth of internet technologies and computing, it was inevitable that data privacy laws would need redoing - especially considering the legislation it replaces in the UK is now 20 years old (Data Protection Act 1998).
Apart from legislative reasons, there are real problems that GDPR aims to solve. It has become clear over the past 10 years that personal data is a valuable commodity (just look at Google and Facebook among other companies), where products and services are free at the point of use, supported by advertising and other processes that use the data collected.
Over the past few years there have also been a string of huge data breaches that have shown companies are hoovering up massive amounts of personal data, which has led to questions such as:
What processes do they have in place to keep the data secure?
Are they handling the data correctly?
Do they have permission to use the data in the ways they are using it?
Do they even need to hold the data in order to perform the function we asked them to perform?
GDPR will strengthen and unify data protection for individuals within the EU, and will force all organisations processing personal data about EU citizens to abide by the new regulation.
What is personal data?
Personal data is defined as any information relating to an identifiable person who can be directly or indirectly identified from it. This is basic information such as name and email address, photos, and IDs.
This includes any electronically gathered and/or stored information, as well as paper-based storage.
There are also ‘special categories’ of personal data that schools are likely to handle, such as ethnicity and health information, which have additional rules around how the data should be stored and handled.
Controllers and Processors
GDPR applies to both controllers and processors, so all parties involved can be liable.
As a controller you are required to determine the purposes and means of processing personal data, and you have legal obligations to ensure your contracts with data processors are GDPR compliant.
As a processor you are responsible for processing personal data on behalf of a controller, you are required to maintain records of personal data and processing activities.
Collecting Data
You must have a good reason to collect and hold personal data, which needs to fall into one of the six lawful bases:
The Data Subject has given explicit consent for the data to be collected and used for a particular purpose
It is necessary to process the to fulfil a contract you have with the Data Subject
It is necessary to process the data to comply with a legal obligation you have
It is necessary to process the data to protect the vital interests of someone
It is necessary to process the data to perform a task in the public interest
It is necessary to process the data for the purposes of your legitimate interests
Each piece of personal data processed by the school must be attributed to one of these bases otherwise the processing is not lawful. Much of the personal data processed by a school (or other state funded educational establishment) will fall under the public task base. But you should always ensure that this is the case. For example, it’s lawful to collect student address and telephone number under public task but it is not lawful to then share that with other third parties for a ‘non-core’ task without gaining appropriate consent.
Reasons for processing data
The new regulations are designed to prevent organisations from collecting massive amounts of personal data, when they don’t necessarily need it for the purpose it was collected for, or that purpose has been served and there is no longer a need to keep it.
Part of preparing for the new regulations is going to be about auditing all the personal data you hold, and determining whether you actually need it. This process should also be documented, because we will all have personal data that we no longer need. Documenting what data there is, why you need it or how it has been discarded, is evidence that you have proper processes in place should a data breach occur.
This alone is not going to be a simple task, when you get down to stores of unstructured data, such as Word documents, spreadsheets, and email archives; determining whether they contain personal data, why it was created, and who’s data it contains, then deciding what to do with that data is not going to be an easy task.
What is a data breach?
The definition of a personal data breach is now more robust and clear than previous legislation; a personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data.
Whether accidental or deliberate, anything that causes personal data to be lost, destroyed, corrupted,disclosed or unavailable, for whatever reason (for example, if it becomes encrypted by malware), can be considered a breach, and the ICO must be notified within 72 hours of the breach being discovered.
If the breach is significant enough to adversely affect the rights or freedoms of data subject(s), they must also be notified.
All this adds up to mean that you must have a plan in place for how data is to be protected,, how your systems should be monitored for data breaches, and for what happens if a breach occurs. Staff will need training on how to handle data and record how it is used.
Rights of the Individual
GDPR is designed to give control over personal data back to the data subject, as and such it defines a number of individual rights over that data that organisations must adhere to, they are:
The right to be informed
The right of access
The right to rectification
The right to erasure
The right to restrict processing
The right to data portability
The right to object
Rights in relation to automated decision making and profiling
Individuals whose data you will be processing now have the right to be informed about the collection of any of their personal data, the reason you are collecting it, how it will be processed, who it will be shared with, and how long it will be held for.
They also have the right to request to see that data, for that data to be available for use by other services that the individual requires, for any incorrect information to be corrected, or for data be deleted (depending on the basis for the data being processed). They can also restrict usage of the data, and for personal data processed on the basis of their consent, the individual has the right to withdraw consent at any time.
The basis for processing the personal data of a child is also more complex, as parental consent may also be required.
Conclusion
The current data protection act places a statutory requirement upon schools to comply and GDPR is an evolution of these requirements, with transparency and accountability on both the controller and processors’ part, and on control over that data for the data subject.
It is not going to be an easy task for any organisation to evaluate and consolidate the data they have, and put in place the training and processes needed to remain compliant in the future. But GDPR is not something that will ever be completed; it is an ethos and a set of processes that need weaving into every area of your organisation where personal data is handled, and as its implementation matures we will no doubt see organisations struggle with certain aspects.
The 25 May 2018, when the legislation comes into force, should not be viewed as a finishing line, but by developing a plan to get to a place of compliance, and getting the people in your organisation to start thinking about how data is handled and processed, you will be well on the road.
For more help with knowing your obligations and developing your plan, you can access our GDPR Guidance for Schools and Colleges:
GDPR Guidance for Schools and Colleges
This article was originally published by SWGfL
GDPR
data protection
360data
from Safer Internet Centre https://www.saferinternet.org.uk/blog/gdpr-coming-what-does-it-mean-my-school
via IFTTT
0 notes
Text
How to take your data back from Facebook and delete your account

Want to protect your data on Facebook, or just plain get rid of your account? I’ve got you covered. (AP Photo/Marcio Jose Sanchez, File)
Want to protect your data on Facebook, or just plain get rid of your account? I’ve got you covered. (AP Photo/Marcio Jose Sanchez, File)
Facebook (FB), the world’s largest social network, is in hot water yet again. The company, which was already facing scrutiny for selling ads to foreign groups seeking to disrupt the 2016 U.S. presidential election and inadvertently facilitating the spread of fake news and conspiracy theories, is getting hammered for allowing the profile data of 50 million Americans to be used by political operatives without users’ consent.
The group that used the data, Cambridge Analytica, did so to create and spread highly targeted advertisements seeking to elect Donald Trump and discredit Hillary Clinton in the lead up to the presidential election. But the organization received that information through questionable means, according to the New York Times.
The entire mess might have you wondering how you can control who sees your data on Facebook, or even how to delete your profile entirely. If that’s the case, I’ve got you covered.
Here’s how to control your data on Facebook, and, if you’re particularly fed up, how to delete your account entirely.
The data Facebook uses
Facebook lays out exactly what data it collects to craft a profile about you that can be used to target you with specific ads on its Data Use Policy site. And, as you might expect, it collects everything. Any post, like, comment, picture, video, friend you’ve added, news article or inside joke you’ve put on Facebook can be used as a means to serve you advertisements.
Facebook uses your personal information to match you up with various advertisements on the social network.
Facebook can also use data like your date of birth, location and other information to provide you with ads you might find relevant, and improve the site itself.
Think of it as the built-in cost of using a massive service like Facebook for free.
It’s not just the information you share on Facebook that gets scooped up, though. All of those sites and services you log into using your Facebook account have access to some of your data, and how they handle that info is up to them.
Then there’s the content friends post about you. Yes, all of those pictures, memes and stories your friends tag you in get collected by Facebook, too. And unfortunately, you don’t have control of that information since you didn’t post it.
It’s important to note that Facebook isn’t the only company that collects and uses your data like this. Google (GOOG, GOOGL) and Twitter (TWTR) also use information about you to determine which advertisements to show you and help advertisers better target their campaigns.
Controlling your data
Facebook considers information you share publicly to be fair game for use with targeted advertisements. And while you can change the visibility of some of your data such as posts and photos, information like your name, profile picture and cover photo, networks, gender, username and user ID (how apps identify you) are always considered public.
If you want to see fewer ads regarding a specific topic on Facebook, you can visit the Facebook Ad Preferences site. From here, you can control what kind of information Facebook thinks it knows about you. You won’t actually be able to delete that data, but you’ll be able to control the kinds of ads you see.
For example, Facebook recognizes that I’ve interacted with pages about action role-playing games, Hulu, the Wall Street Journal and others. If I no longer want to see ads about those topics, I can simply click the “X” icon in the top right corner of each interest.
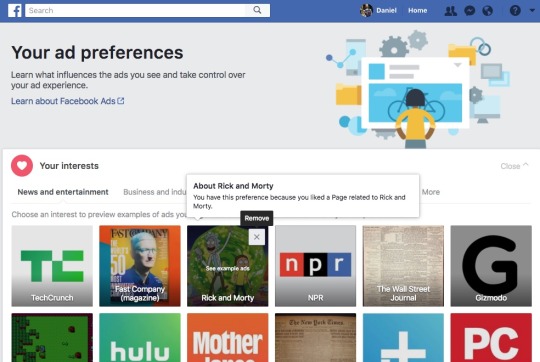
You can delete categories that Facebook thinks you have interest in to stop seeing ads on specific topics.
You can also remove yourself from categories that Facebook matches you up with that help advertisers serve you certain ads. Facebook, for instance, lists me as being an engaged shopper, commuter, console gamer and early adopter. I can, however, remove myself from those categories to stop seeing ads based on that content.
Similarly, you can choose to prevent Facebook from showing you online interest-based ads or ads on apps and websites by opting out of these settings.
Then there are apps including games and services like Spotify that can access your basic Facebook profile information. If you never want to use those services again, you can disable them from your Facebook account by turning off Facebook Platform applications. Once you do that, these outside apps will no longer have access to your profile data.
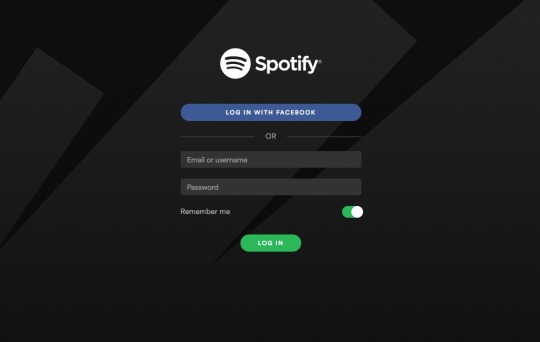
If you revoke access Spotify’s access to your Facebook profile, you’ll need to create a new Spotify login.
For apps like Spotify, which allows you to log in with your Facebook account, you’ll need to cancel your Facebook-based profile and start a new one with a standard login.
Deleting Facebook
Of course, if you’re completely at the end of your rope when it comes to Facebook, you can simply choose to erase your presence from the service by deleting your account. Before you do so, though, it’s worth noting that getting rid of your Facebook account also means you’ll be cutting yourself off from a large chunk of your online social circle.
You won’t be able to spy on that one guy who dumped you in high school or call out Brad when he tells you he was too sick to hang out last night, but still managed to post pictures of himself at the bar with Sharon.
If you’re willing to give that up, along with the ability to send and receive invitations to various parties, which is why I primarily use the service, then you can take the leap and say goodbye to your account.
Before you do that, though, you should know that deleting your account means saying goodbye to all of those photos and videos you’ve uploaded to the service over the years. To save those, you can download your Facebook archive by navigating to the Settings menu from the Facebook desktop site.
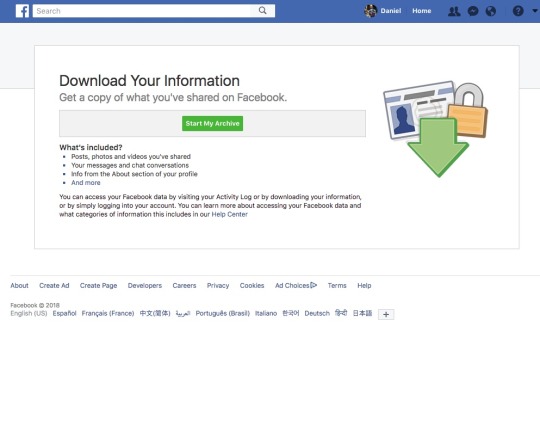
You might want to archive your Facebook data before you delete your account entirely.
Next, click “General” and select “Download a copy of your Facebook data” at the bottom of the page. This will ensure you have access to everything you’ve posted on the site since you originally joined.
Now you can delete your account. To do so you’ll need to follow this link, as Facebook seems to purposely make it difficult to end your relationship with the site.
Click “Delete my Account,” and you’ll see a pop-up window asking you if you’re sure you want to delete your profile. You’ll then need to enter your password and fill out a Captcha to confirm your decision.
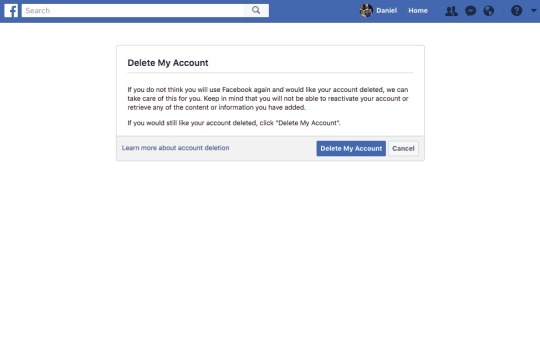
Facebook seems to purposely make it hard to delete your account.
It could take up to 90 days for Facebook to fully delete all of the information you’ve uploaded to its servers. During that time, no one will be able to interact with your account.
Unfortunately, some things won’t be deleted during this process including posts you’ve been tagged in or messages you’ve previously sent to friends.
And that’s that. You’re now done with Facebook forever. Unless, that is, you’ve got Messenger, WhatsApp or Instagram, all of which are owned by Facebook.
Come on. You didn’t really think it would be that easy to leave, did you?
More from Dan:
Facebook users don’t care about its myriad scandals
Here’s Cortana’s March Madness bracket
Alexa predicts Villanova will win March Madness
How to live stream every March Madness game
Fitbit is dead set on taking down the Apple Watch
Email Daniel Howley at [email protected]; follow him on Twitter at @DanielHowley.
Follow Yahoo Finance on Facebook, Twitter, Instagram, and LinkedIn
#tech#$FB#Cambridge Analytica#_revsp:yahoofinance.com#social networking#Delete Facebook#how-to#_lmsid:a077000000BAh3wAAD#$twtr#$GOOGL#_uuid:9ae57fb5-7370-31a2-ae4d-bdf7f9e85421#$GOOG#FB#_author:Daniel Howley#Facebook#social media
0 notes