#the windows experience has moved to linus
Text
I logged on to let you guys know that I uninstalled mobile and am finishing mastodon migration TODAY after getting a bonus mini panik from autoplay audio ads.... I haven't been on desktop in a few weeks... Want to guess how long it took me to find my own blog on this nightmare desktop UI?
Too long. Too. fucking. Long. It's called "unintuitive ui" if it's not downright hostile (ie: stay longer for ads!).
Feel free to reply "why don't you just remember to turn your sound down every single time you stop listening to music like any of us have that kind of time and attention" to be autoblocked.
Stay tuned. I'll probably drop the new location in the next few hours as I tweak things.
I am moving ALL the sub-blogs, so we can understand that takes a little time, yes?
Yah, you can drop useful Mastodon related asks in my box.
#mastodon#tumblr updates#dont touch me#tumblr has moved to mastodon#the windows experience has moved to linus#always chasing that TAZ#social media#tumblr ui#cw for violence but put a knife in your ear#i am here to READ#if i wanted video i would go to a video platform#if youre making this a video platform im out#esp with autoplay#like you really need to ask my permission first#mastodon migration#tumblr exodus#compost the ceo and board
0 notes
Text
# LGBTQ+ Romance Book Reviews: A Dive into Diverse Love Stories
The landscape of romance literature has been evolving rapidly, embracing the rich tapestry of human experience and love in all its forms. LGBTQ+ romance novels have surged in popularity, offering readers a chance to explore stories that resonate with their lives or open their eyes to the experiences of others. This article delves into the world of LGBTQ+ romance books, highlighting notable titles, trends, and the impact these stories have on readers and society.
## The Rise of LGBTQ+ Romance Literature
In recent years, there has been a significant increase in the availability and popularity of LGBTQ+ romance novels. Publishers are recognizing the demand for diverse love stories that reflect a broader spectrum of romantic experiences. This shift is not only a win for inclusivity but also enriches the genre with a variety of narratives and perspectives.
### Key Trends in LGBTQ+ Romance Publishing
Diversity in Representation: There's a growing effort to include a wide range of identities and orientations, moving beyond the gay and lesbian focus to include bisexual, transgender, queer, intersex, asexual (LGBTQIA+), and more.
Genre Blending: LGBTQ+ romances are breaking into sub-genres such as fantasy, historical, paranormal, and young adult, offering readers a vast landscape of settings and plots.
Own Voices: There's an emphasis on "own voices" novels, which are written by authors who share their characters' identities, providing authentic and nuanced portrayals.
## Noteworthy LGBTQ+ Romance Novels
Among the plethora of LGBTQ+ romance novels, some stand out for their storytelling, character development, and impact. Here are a few noteworthy examples:
### "Red, White & Royal Blue" by Casey McQuiston
This novel tells the story of Alex Claremont-Diaz, the First Son of the United States, and Prince Henry of Wales. What starts as a rivalry turns into a secret romance that challenges their lives and responsibilities. It's a heartwarming tale of love, identity, and duty, celebrated for its humor and emotional depth.
### "The House in the Cerulean Sea" by TJ Klune
Though not strictly a romance novel, this book features a sweet love story between Linus Baker, a caseworker for magical youth, and Arthur Parnassus, the master of the orphanage. It's a beautiful story about acceptance, family, and finding love in unexpected places.
### "Honey Girl" by Morgan Rogers
This debut novel explores the life of Grace Porter, a newly minted PhD in astronomy who, after a wild night in Vegas, finds herself married to a woman she barely knows. It's a poignant exploration of identity, mental health, and the complexities of love.
## The Impact of LGBTQ+ Romance Novels
LGBTQ+ romance novels do more than just entertain. They play a crucial role in visibility, representation, and even education. By showcasing diverse relationships and identities, these books can foster empathy, challenge stereotypes, and provide solace to readers who see their experiences reflected in literature.
### Visibility and Representation
For many in the LGBTQ+ community, seeing their lives and loves depicted in romance novels is affirming. It sends a powerful message that their stories are worth telling and their love is worth celebrating. This visibility can be particularly impactful for those who feel isolated or marginalized.
### Challenging Stereotypes and Norms
LGBTQ+ romance novels often challenge societal norms and stereotypes about gender and sexuality. By presenting complex characters and relationships, these books encourage readers to question their assumptions and broaden their understanding of what love can look like.
### Educational Value
For readers outside the LGBTQ+ community, these novels can serve as windows into experiences different from their own. They offer opportunities to learn about the challenges, triumphs, and nuances of LGBTQ+ lives, fostering empathy and understanding.
## Conclusion
LGBTQ+ romance novels are a vibrant and essential part of the literary world. They offer rich, diverse narratives that celebrate love in all its forms. As the genre continues to evolve, it promises to bring even more stories that resonate with readers, challenge prejudices, and broaden horizons. Whether you're looking for a sweet love story, a steamy romance, or a tale that explores the complexities of identity and society, there's an LGBTQ+ romance novel out there for you.
In reviewing these books, it's clear that the power of love transcends boundaries. Through the pages of LGBTQ+ romance novels, readers can find laughter, tears, inspiration, and a sense of connection. As this genre grows, it will undoubtedly continue to enrich the literary landscape and the lives of those who dive into its stories.
0 notes
Text

If you read and enjoyed "The House in the Cerulean Sea" by T.J. Klune, you might also like "A Man Called Ove" by Fredrik Backman!
The House in the Cerulean Sea: "A magical island. A dangerous task. A burning secret. Linus Baker leads a quiet, solitary life. At forty, he lives in a tiny house with a devious cat and his old records. As a Case Worker at the Department in Charge Of Magical Youth, he spends his days overseeing the well-being of children in government-sanctioned orphanages. When Linus is unexpectedly summoned by Extremely Upper Management he's given a curious and highly classified assignment: travel to Marsyas Island Orphanage, where six dangerous children reside: a gnome, a sprite, a wyvern, an unidentifiable green blob, a were-Pomeranian, and the Antichrist. Linus must set aside his fears and determine whether or not they're likely to bring about the end of days. But the children aren't the only secret the island keeps. Their caretaker is the charming and enigmatic Arthur Parnassus, who will do anything to keep his wards safe. As Arthur and Linus grow closer, long-held secrets are exposed, and Linus must make a choice: destroy a home or watch the world burn. An enchanting story, masterfully told, The House in the Cerulean Sea is about the profound experience of discovering an unlikely family in an unexpected place-and realizing that family is yours"
A Man Called Ove: "Meet Ove. He's a curmudgeon; the kind of man who points at people he dislikes as if they were burglars caught outside his bedroom window. He has staunch principles, strict routines, and a short fuse. People call him 'the bitter neighbour from hell'. But must Ove be bitter just because he doesn't walk around with a smile plastered to his face all the time? Behind the cranky exterior there is a story and a sadness. So when one November morning a chatty young couple with two chatty young daughters move in next door and accidentally flatten Ove's mailbox, it is the lead-in to a comical and heartwarming tale of unkempt cats, unexpected friendship, and the ancient art of backing up a U-Haul. All of which will change one cranky old man and a local residents' association to their very foundations."
2 notes
·
View notes
Text
A Quiet Place (Part 2)
Summary: Part 2 that i promised for this piece: here. Still inspired by a chaotic rp @chibi-mushroom and @animacreates are doing. This one takes place a month-ish after the last, and further dives into what trauma the foster siblings got themselves into beforehand.
Rating: K+ (for a precision f-strike on Brain’s part)
Word Count: 2,409 words
If you liked this story, please reblog!
---
They kept the blanket on the couch just for her. Not that she had any reliance on the purposely quiet nature of Oswald's hobby room. It was just… a good place to be, that's all. Oswald held true to his word- Ortensia really didn't bother him when he was in that room. The closest she ever got was a polite knock on the door to say that dinner was ready. He even held true on ignoring Sabrina whenever she went under the afghan blanket. Even on days like today when she sat up and simply had the blanket draped over her shoulders; he would come into the room, notice she was there with a little nod, then continue on as if she wasn't there. It was… nice. It came in handy when she decided to do her homework in the hobby room.
But she wasn't here to do her homework today. She was waiting for Oswald. Sabrina hugged the blanket as close as possible while she kicked her legs over the couch. Her face was between a scowl and upset. She and Brain had been with Ortensia and Oswald for nearly a month now- one of the longest times they'd ever stayed with a single family before. The absolute longest had been at six months. It was another nice couple, like Oswald and Ortensia, until they were expecting their first child. In the rush for the new baby, Sabrina started to cling to the caretakers. She didn't know a baby was a lot to care for. She just knew that her dependance on this one family who seemed so nice were suddenly drifting away. They didn't even bother to give her a second chance at being a good kid after she accidentally pushed their foster mother down the stairs. It was an accident. Honest. She only wanted to help arrange things for the baby too...
“One of these days I'll learn to say no to her.” Oswald grumbled as he entered the hobby room. It nearly gave Sabrina a start, having been too busy wondering just what happened to that particular foster family. “She and Ortensia. Make me talk to that rat. As if I'd ever-”
“I want to watch a Audrey Hepburn movie.”
It was almost funny watching him jump at her voice. Then again, it probably was rather surprising that she wanted to have a conversation with him- even if it was just a request to watch a movie. But there was a glint of determination in her eye. Oswald noticed it and nearly tossed his trouble out the window. This kid needed that attention at the moment.
“Alright.” he agreed. He went over to the bookshelf holding the VHS tapes as he asked, “What are you in the mood for? Funny Face? Love in the Afternoon? Charade?”
“I want to watch Sabrina.”
Oswald cocked an eyebrow as he pulled it from the shelf. “I thought you hated that one?”
“I do. A lot.” she agreed, rather prudently. “But I wanna watch it anyway.”
“Alright then.” her caretaker laughed. “If you're so sure, we'll watch Sabrina, Sabrina.”
The child gave a rather smug grin as he came back over. She was rather pleased as he turned on the TV and got the movie ready. Oswald plunked himself on the couch with a grunt. He then eased into it with a long, well needed sigh.
“Can I lay on you?”
Oswald blinked. He looked over at Sabrina to see her give him the same glare she gave her schoolwork. It was a look of deep thought. Of experimenting. Of very harsh scrutinizing.
“Sure.” he agreed. “Can't guarantee I'm any good as a pillow, though. Do you mind?”
Sabrina shook her head, then nearly fell headfirst into his lap like she immediately passed out. Oswald would have thought that was the case before she carefully moved herself to face the TV.
“Comfy?” he jokingly asked. She gave a small nod, which only got another chuckle out of him. “Can I put my hand on your head? You didn't really leave me a good spot for it.”
“Don't braid my hair.” came the rather sharp answer.
“I won't.” he laughed in agreement.
Sabrina made herself a bit more comfortable before focusing on the movie. This one really wasn't her favorite. The title character, the one who shared her name, was a girl who was enamored with a guy whose family had hired her father as their chauffeur. That Sabrina loved David (the guy) so much that when she was sent to Paris to learn how to cook, she tried to kill herself. David's much older brother, Linus, found Sabrina and stopped her before she could go through with it. When the Sabrina in the movie came back from Paris, David was attracted to her because she looked like a woman. But Linus didn't want David to fall in love with Sabrina, he had his brother arranged to marry a sugar plantation heiress so he could produce a lot of sturdy plastics in their family's name. And so, he did something that our Sabrina found quite ridiculous; he tried to make the movie Sabrina fall in love with him instead. Suffice to say, it worked on both accounts. Sabrina fell in love with Linus, and Linus fell in love with Sabrina. In the end, they were on a one-way cruise boat going to Paris, happy and in love.
If our Sabrina had her way, that movie would have gone very differently. The first change would have been when David decided he liked movie Sabrina because she looked pretty now. Instead of going along with him finally liking her, our Sabrina would have pranked him. She would have made him work for her affection after spending most of their lives pretending she didn't exist. And when Linus tried to sway her away from David? Our Sabrina would have come clean. She would have admitted that she was just messing with David. Perhaps she still loved him, maybe not. Either way, she could still fall in love with Linus, but it would have been over a mutual dislike for how dumb David was.
There were some funny lines in the movie, though. Our Sabrina couldn't deny that. One of the ones she enjoyed was coming up right about now. It was when movie Sabrina was in Paris, and her father was reading a letter he had gotten from her during breakfast.
“What about David? What'd she say about David?” the cook happily asked as she made something in the background.
“Not a word.” the father said as he went through the letter.
“That's good.” the butler nodded as he took a bite from his toast.
“No, wait a minute,” the father then said. “Here's something. 'I don't think of David very much anymore.'”
“That's good.” a maid at the kitchen table nodded.
“'Except at night.'”
“That's bad.” the butler frowned, taking another bite.
“'I decided to be sensible the other day, and tore up David's picture.'”
“That's good.” the bartender nodded as he was washing a glass at the sink.
“'Could you please airmail me some scotch tape.'”
“That's bad.” the cook dismally noted.
Our Sabrina couldn't help her little snicker. She liked the way the actors bounced off each other into perfect comedic timing. Oswald noticed it and gave a smirk of his own.
“You're a good kid.” he idly noted, giving her hair a gentle pat.
The child shrank. “No I'm not.”
“You are, and you deserve the world.”
“Stop.” the child desperately begged, even sitting up to be at his eye level. “I don't want you to talk like that. I don't want you to ever talk like that. Bad things always happen to the people that do.”
Oswald just looked at her for a moment. “Like what?” he asked, trying to play it off as a joke. But her face… It was too serious. Too… terrified.
“They get mean.” she insisted. “They say that they care, but then they decide they don't want you anymore. You try to defend your brother, and you get yelled at instead. Or… or maybe they just wanted your brother, so they're mean to you every time he's not looking. And he doesn't always know. He just says that you're just scared, and exaggerating, and… and…!”
“Sabrina,” Oswald said, interrupting her and even gently taking her by the shoulders. Even if he didn't have a strong grip on her, she still tried to struggle out of it. “Sabrina, listen to me. Ortensia and I will never do that to you. To both of you. You have my absolute word.”
The child violently shook her head. “No!” she cried before breaking free of his hold. She hid herself in a corner of the couch, blanket over her head, and refused to budge. In her desperation, she even shouted at him, “I don't exist! I'm under the blanket and I don't exist now!”
He wasn't going to lie, Oswald almost broke that one ounce of trust she had in him. But he couldn’t. Instead, he tried to relax in his seat again and tried to focus on the movie. It was hard when all he wanted to do was give that little girl a hug.
The movie now had switched back to what the heroine was during in Paris. She was in her second class where they were learning how to make souffle. The instructor was shrewd- he had something negative to say about every student’s effort. Once he told movie Sabrina that her souffle was ‘too low’, the titular girl went off to the side with an older student. This student was a character only used to justify a dress movie Sabrina would wear later, and Oswald knew that his Sabrina preferred the chemistry between these two than movie Sabrina and Linus.
“I don't know what happened.” movie Sabrina sighed as the two of them placed their souffles on the table.
“I'll tell you what happened, dear.” the older student laughed. “You forgot to turn on the oven.”
Movie Sabrina’s face went into one of disappointment as she let out a sullen, “Oh!”
“I've been watching you for a long time, mademoiselle.” the older student admitted. “Your mind has not been on the cooking. Your mind has been elsewhere. You're in love, and I would venture to one step further that you are unhappily in love.”
“Does it show?” movie Sabrina asked, casting her gaze down.
“Very clearly. A woman happily in love, she burns the souffle. A woman unhappily in love, she forgets to turn on the oven.”
Oswald took a look back at Sabrina. Even under all of the covers, you could see how tightly she had tensed up. All he could think was, ‘Oh, kid…’ and really wish he could have gotten to these two siblings sooner. He didn’t leave her while the movie still played. When it ended, he got up to rewind the tape and carefully made his way back to the shelf to put it away. Never once did his Sabrina move. He hoped she had gone to sleep instead of still being catanoic. At least he knew he had the heart for this parenting thing; people who didn’t care wouldn’t have the insatiable urge to cuddle that poor kid, kiss her forehead, and promise her the world so long as they lived. Tell her the lies you always told kids when they were sad- it would get better, the world’s brighter than this, sticks and stones may break your bones but words will never hurt you.
Would they even work on her? He had severe doubts about it after today.
“I might have dinner up here tonight,” he said out loud. It wasn’t directed toward little Sabrina, but it was a habit to communicate his intentions when he left the hobby room while she was still there. “I’ve really been meaning to work on that blasted clock all week.”
No response from the lump on the couch. He didn’t know if that was a good thing, or a bad one.
Again, resisting the urge to just hold the child and never letting go, Oswald let out a small sigh as he headed on out. He gently closed the door behind him, then started to make his way to the living room. Finding that Blaine was relaxing on the living room sofa was a small relief. He sure did look comfortable- back against the armrest, feet up on the sofa, and laptop balanced on his knees.
“Hey you,” Oswald teased, “No making scam sites until you have your own bank account. I won’t let you trace that stuff back to me.”
Like a true teenager, Blaine just slowly lulled his head over to look at his caretaker. A smirk was etched on his face in seeing Oswald there.
“I’m a renegade foster kid,” he said in delight, “I already have my own bank account. Those poor suckers think I’m 28, and Sabi’s a college student.”
“Going for a bachelor's, then?”
“Master’s actually.”
“Ah.” Oswald snorted. But the thought of their futures made him frown. “Blaine, I've got a question.”
“Fire way.”
“Do you still have the number of your case worker?”
“Sure do. Got it on speed dial.” There was a pause, then the boy asked in a rather defensive tone, “Why?”
To this, Oswald nervously rubbed the back of his neck. It was only now dawning on him how terrifying the request would sound to these kids. So he tried his best to lighten the situation a bit by saying, “Do you think there's a nice way to ask if I murder your previous foster parents? They've got a lot to answer for.”
Turns out, Blaine's glare was just as ice cold as Sabrina's.
“You don’t need the case worker to tell you that.” Blaine darkly informed Oswald. “I can tell you exactly who decided to gaslight Sabi in a heartbeat. Among others.”
“I hate that you know what the word is…” Oswald mumbled under his breath as he rubbed the back of his neck. Blaine cocked an eyebrow at him in response.
“You really are a good one.” he decided with a click of his tongue. He turned his attention back to his laptop before adding in a dark voice, “Don't fuck it up.”
And Oswald had no intention of doing so- not over his dead body.
#writing#writing stuff#writers on tumblr#kingdom hearts#epic mickey#kh blaine#blaine#kh brain#brain#oswald the lucky rabbit#oswald#kingdom hearts oc#kh oc#kingdom hearts fanfiction#kh fanfiction#fanfiction#fanfic#kh fan fic#fan fic#fan fiction
2 notes
·
View notes
Text
What Are the Most Significant Reasons to Learn Python Programming?
Python is an open-source, high-level programming language that has been designed for usage with a wide range of operating systems. Because of its dynamic and diverse character, it is said regarded as the most powerful programming language. Python is uncomplicated to use, with straightforward syntax, and newcomers to the language find it extremely easy to grasp the ideas. Python is in great demand in the industry, having been utilized by pioneer websites such as YouTube and Drop Box. Register for Python Training if you wish to get the benefits of Python.

Let us now look at the main reasons why the Python language is utilized by such a wide variety of individuals.
Object Oriented Programming
Object Oriented Programming is a sophisticated Python technique that enables for the construction and reuse of data structures. Because of its reusability, the task is completed more efficiently and in less time. Object oriented programming has been applied to classes and numerous interactive objects in recent years. Object Oriented Programming methods may be applied to any software and executed in any programming language.
Readability
The Python coding language is relatively simple to grasp due to its basic syntax. As a result, Python may be used as a prototype and then implemented in another programming language after the code has been tested.
Python is completely free.
Python is a free and open-source programming language that allows for unlimited use. It can be changed, shared, and used commercially under this open-source license. The license is even available for the complete source code, with free support. CPython, the most frequently used Python implementation, is compatible with all operating systems. As a result of its well-designed, strong software with scalable and portable features, C++ has become a commonly used programming language.
Programming at a higher speed
Python is a high-level language, and programming in it is far faster than programming in other low-level languages.
Cross-platform compatibility
Python can run on all major operating systems, including Mac OS, Microsoft Windows, Linus, and Unix. This programming language provides the greatest experience while working with any operating system.
Integration Capabilities
Following are the notable integration capabilities of Python:
• Process control capabilities are strong.
• Capability to be incorporated as a scripting programming language
• Ease of development of online services
If you want to work with Python, enroll in one of the Python Instruction Institutes, where applicants receive additional benefits from the training. See Python Programming Course for further details. Highly experienced and competent instructors lead training sessions to ensure that candidates have a thorough knowledge. Mock exams are provided online for aspirants to assess their level of comprehension. Analytical reports will be provided with accurate test findings. Aspirants can also choose from various learning options such as corporate training, boot camp training, classroom training, and so on.
How to Choose a Python Course
When looking for a Python training course, the options might be befuddling and intimidating. There are websites that promise to be able to teach you Python in less than half an hour! Of course, that's rubbish. However, you'd be amazed how many people fall for this type of commercial ploy. (Do not become one of them.)
On the other side, there are three-day boot camps that cost $1,000 or more (plus hundreds of dollars in plane fare, hotel and dining costs). These are genuine, and many of them provide good instruction, but for the majority of individuals, they are not the greatest option. These boot camp-style sessions are ideal if you a) already have some programming expertise in other computer languages and b) need to learn Python quickly for a professional project. In reality, it's probable that the majority of people completing these boot camps aren't paying their own tuition - their employers are.
But what if you're a complete Python noob? What if you want to learn this flexible and cutting-edge language but lack programming expertise, much alone a few thousand dollars to spend on a boot camp? Are there any Python training classes that might be appropriate for you? There are, indeed! Of course, some are superior to others. Here are some pointers to consider while selecting a Python training course or book: Check to see if it is truly appropriate for actual beginners - many publications and courses use the term "beginners" extremely loosely. They may be presuming you have some Python experience but lack advanced grasp of the language. You should double-check it before making a purchase. Make sure the lessons are brief and easy to understand so that you can move quickly yet not become overwhelmed. Another essential factor to consider is the cost. A beginner's Python training should not cost more than $100. Because Python training is such a popular industry right now, some firms charge extra, but you can get a fantastic beginner's course in Python for far under $100.
Make sure the lessons are brief and easy to understand so that you can move quickly yet not become overwhelmed. Another essential factor to consider is the cost. A Data analysis using Python training for beginner's should not cost more than $100. Because Python training is such a popular industry right now, some firms charge extra, but you can get a fantastic beginner's course in Python for far under $100.
You can also join our Spoken English classes online .
1 note
·
View note
Photo

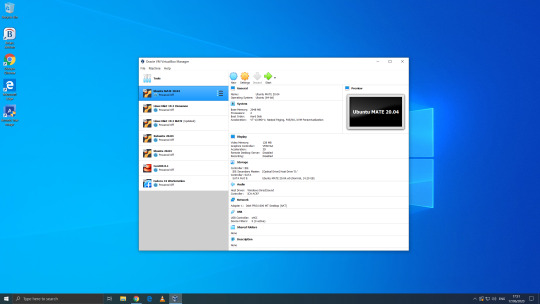
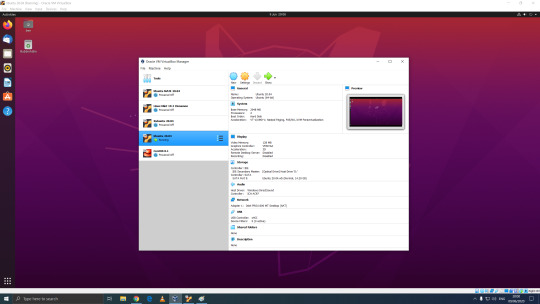
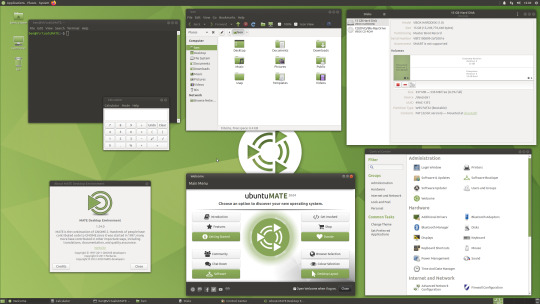

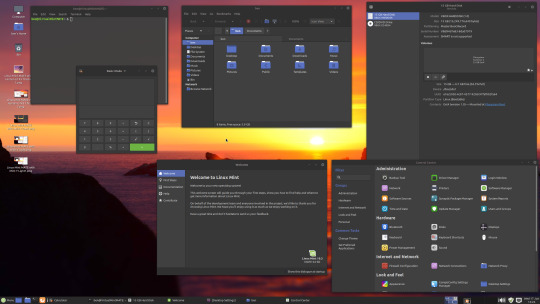

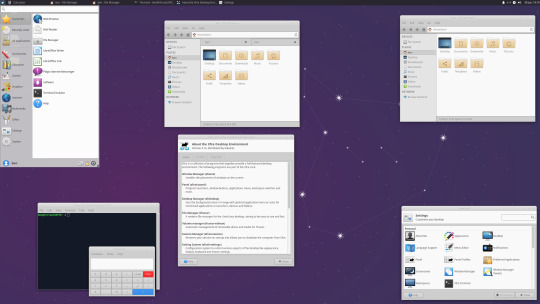
06.06.20
We went to the Oracle VirtualBox site and downloaded and installed VirtualBox 6.0. Oracle VM VirtualBox is free, open source virtual machine software maintained by Oracle Corp.
It was originally an Innotek product before Innotek was acquired by Sun Microsystems in 2008. Sun Microsystems was in turn acquired by Oracle in 2010. The alternative software to Oracle VM VirtualBox is VMware workstation.
I have been using Oracle VM VirtualBox since 2016 and have learnt a lot of information about how it works and how to install various operating systems.
Virtualbox can run Linux guest operating systems and Microsoft Windows guest operating systems. It can emulate both 64-bit operating systems and 32-bit operating systems.
Each operating system you add to VirtualBox is treated as a Guest. The guest operating system is running in its own virtual environment, which emulates a real machine on your PC. This means that anything you do in it does not affect your PC. The guest runs in a console:
About the VBox console:
The VirtualBox console displays the active virtual machine. It shows the virtual guest operating system activity icons in the status bar. The console can be re-sized, minimised and forced closed from the title bar.
It is not recommended to force close an active guest operating system as this acts like switching off mains power. Your guest operating system should be shut down cleanly.
You can select different viewing modes in the view list or use the shortcut keys assigned with them. These mode include full screen mode, seamless mode and scaled mode.
VirtualBox website link: https://www.virtualbox.org/
VirtualBox wiki link: https://en.wikipedia.org/wiki/VirtualBox
After setting it up, I went to find some Linux-based operating systems to download. Each download is a disc image file with the file extension .iso.
I chose:
Ubuntu MATE 20.04 LTS (Long Term Support)
This operating system uses the MATE Desktop Environment, which is the continuation of the former GNOME 2 Desktop. I like this desktop environment because it has a very configurable interface.
Ubuntu MATE: https://ubuntu-mate.org/
Wiki link: https://en.wikipedia.org/wiki/Ubuntu_MATE
Linux Mint Cinnamon 19.3 Tricia (based on Ubuntu 18.04 LTS)
This operating system uses the Cinnamon Desktop Environment which is based on GNOME 3. Cinnamon uses MGSE (Mint Gnome Shell Extensions), which re-creates a more traditional desktop linux experience whilst also looking modern.
I like this desktop environment because it looks modern and feels familiar to those who come from Windows.
Linux Mint: https://www.linuxmint.com/
Wiki link: https://en.wikipedia.org/wiki/Linux_Mint
Linux Mint MATE 19.3 Tricia (based on Ubuntu 18.04 LTS)
Linux Mint edition featuring the MATE Desktop Environment. I like this desktop environment because like Ubuntu MATE, it is very configurable. It also features Linux Mints system updating utility.
Ubuntu 20.04 LTS
This version of Ubuntu is the main version by Canonical Ltd. This operating system uses the GNOME 3 Desktop Environment.
Ubuntu came out in 2004 and used GNOME 2 as it’s desktop environment until 2011, when it changed to the now discontinued Unity Desktop. In 2017, Canonical announced it would return to GNOME. I like this desktop environment as unlike the GNOME 3 default interface, Ubuntu uses its own orange style theme and adds a Unity like dock on the left of the screen.
Ubuntu: https://ubuntu.com/
Wiki link: https://en.wikipedia.org/wiki/Ubuntu
Xubuntu 20.04 LTS
This operating system uses the XFCE Desktop Environment which aims to be lightweight on system resources and has a really configurable user interface. Xfce once stood for XForms Common Environment. The menu system is called the Whisker Menu. I like this desktop environment because like MATE it is very configurable.
The Ubuntu 20.04 Long Term Release is code named: Focal Fossa. All Ubuntu based distros use .deb (Debian Package Manager) for software installation.
Xubuntu: https://xubuntu.org/
Wiki link: https://en.wikipedia.org/wiki/Xfce
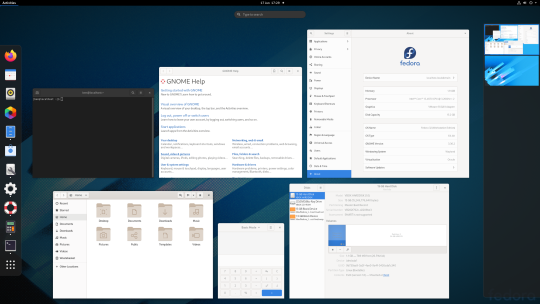
Fedora Workstation 32
Fedora is a Linux distribution developed by the community-supported Fedora Project which is sponsored primarily by Red Hat, a subsidiary of IBM, with additional support from other companies. Fedora is used by Linus Torvalds who is the creator of the Linux kernel.
Fedora is the upstream source of the commercial Red Hat Enterprise Linux distribution.
Since the release of Fedora 30, five different editions are currently available: Workstation, focused on the personal computer, Server for servers, CoreOS, focused on cloud computing, Silverblue, focused on an immutable desktop specialized to container-based workflows and IoT, focused on IoT devices.
I like this desktop environment because it looks fresh and modern. This operating system features the latest version of the GNOME Desktop Environment.
The screenshot of Fedora shows the ‘Activities’ dial screen which gives you a Visual overview of your GNOME Desktop.
With the Activities screen, you can see and control currently opened app windows, all installed applications, search system and switch desktop work spaces.
Fedora: https://getfedora.org/
Wiki link: https://en.wikipedia.org/wiki/Fedora_(operating_system)
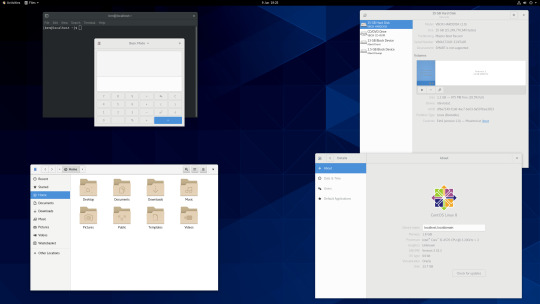
CentOS 8.1
CentOS (Community Enterprise Operating System) is a Linux distribution that provides a free, community-supported computing platform functionally compatible with its upstream source operating system, Red Hat Enterprise Linux (RHEL). It is maintained by The CentOS Project (affiliated with Red Hat). Both operating systems use GNOME 3 as their default desktop environment.
It is basically a free version of Red Hat Enterprise Linux, with the Red Hat branding removed and update servers pointing away from Red Hat servers.
Red Hat Enterprise Linux is a commercial focused Linux distro.
All Red Hat Linux based distros such as RHEL, CentOS and Fedora use .rpm (Red Hat Package Manager) for software installation.
CentOS and Red Hat Enterprise Linux can be installed on servers, workstations and desktops. Both are very popular on mission critical commercial server systems as it is designed to be flexible and very stable.
I thought this Linux distro is interesting because unlike the Ubuntu based distros above, installation of CentOS is more involved, you set up software sources, installed software, desktop and operating system components.
CentOS runs on a lot of web servers.
CentOS: https://www.centos.org/
RHEL:
https://www.redhat.com/en/technologies/linux-platforms/enterprise-linux
CentOS Wiki link: https://en.wikipedia.org/wiki/CentOS
RHEL Wiki link: https://en.wikipedia.org/wiki/Red_Hat_Enterprise_Linux
VirtualBox requires the installation of Guest Additions, which adds extra features to the virtual machine, such as the ability to scale the resolution of the guest operating system, better 3D acceleration and the ability to move files between the Guest and Host machine.
To install Guest Additions on a Linux guest, you will need to use the terminal. installation of this is different on .deb and .rpm builds of Linux.
4 notes
·
View notes
Text
Star Trek: Discovery - ‘An Obol for Charon’ Review

Burnham: "You found yourself among the stars. You found your strength, your bravery."
By nature I love brevity: Though it's over-the-top and melodramatic at times, and perhaps too much was crammed into this single story, 'An Obol for Charon' is an episode in the true spirit of Star Trek. The character interactions and the performances are absolute gold.
'An Obol for Charon' borrows from such classic Trek as 'The Corbomite Maneuver,' 'Babel,' and too many TNG episodes to count. While I don't think that the only way to keep a classic Trek feel is to borrow story elements from other episodes, this is a step in the right direction. DIS has had a different style and tone from the other shows all through Season One, which is one of the numerous criticisms the show's detractors love to use.
Where 'Charon' really shines, though, is in its characters and their interactions. Interesting pairs or groups of characters spark off of one another in this episode, and it's fascinating to see their dynamics. The first pairing I want to look at is new engineer Jett Reno (Tig Notaro) and Stamets. Notaro again infuses her character with the sort of dry yet light humor she employed in 'Brother' earlier this season. Her sarcastic clash with Stamets is interesting because she resembles who he used to be. Remember back in 'Context is for Kings,' when Burnham first came to engineering? Stamets was stiff and reserved, with a biting wit that he used on anyone he didn't like. Now, after his loopy encounters with the Spore Drive and the emotional blow he took from Dr. Culber's death, he's an emotionally responsive, caring human being. He may be tired of the world and resigned to his unhappiness, but he's grown a lot from the stick-in-the-mud he was in 'Context.' Reno isn't as far along the spectrum as Stamets was back then, but she's certainly no stranger to those sarcastic, cynical tendencies. Her interactions with our present-day Stamets, as annoying to him as they are, provide a window into how much our engineer turned spore pilot has grown since 'Context.' It's very welcome.
Along the same line of Stamets' emotional openness are his interactions with Tilly here. This relationship has been steadily growing since the start of the show, and it feels quite earned. He's lovely as he deals with her and comforts her through the very stressful and scary experience she's going through. The scene where he sings her favorite song with her to distract her from the drill he has to stick into her head is both stressful and sweet at the same time. I am loving the dynamic between these two this season. More, please.
The crew continues to feel like a family in this episode. From the opening briefing - Discovery's first, if I'm not mistaken - to their silent tribute to Saru later on, everyone seems to have nailed down their team dynamic. It shows. We got a name for our Saurian friend Linus, who first appeared in 'Brother' and might very well fit in better on The Orville, and Cmdr. Nhan from the same episode returned to do... pretty much nothing. This episode also marks Rebecca Romjin's first appearance as Number One from 'The Cage.' We haven't seen much of her performance yet, so I won't judge it too much as of right now, but she seemed perhaps a bit more emotional than Majel Barrett's Number One. To be fair, unemotional was about all Majel Barrett could do convincingly - why do you think she was the computer voice for so long? - but I feel like Romjin should try to follow the established canonical character. That said, I liked her scene with Pike. I hope they finally canonize her name in her future appearances.
This brings us to the final important character interaction in this episode, probably even its centerpiece. This is the relationship between Burnham and Saru. Quite honestly, this one fell a bit more flat with me. While the pair's dynamic has been steadily evolving ever since 'The Vulcan Hello' way back, I don't really feel like they've gotten to this point yet. At the end of Season One, I'd have said they were over their animosity, and possibly now friendly towards one another. I would never have said they were close enough yet to be good friends, let alone calling each other 'family.' The other thing is that the dramatic death fake out for Saru was way too over-the-top and drawn out for me. They should not have done all that only to save him at the last second. Even though I knew in the back of my head that they wouldn't kill him, I found myself thinking he might die. Now, while some consider this a good thing because it gives the story stakes, there is a difference between worrying that a character will die and this. Here, it was getting to the point where the only emotionally satisfying ending would have been to kill him. It felt like a cheap cop-out when he didn't die. And even though he's now experiencing a huge change in his life, and this will probably fuel many wonderful Saru stories going forward, it still felt like a very low-consequence storyline. That said, I think Sonequa Martin-Green and Doug Jones did the absolute best that could be done with the writing, and I am very impressed with their work. No complaints there.
I don't have a whole lot to say about the peril/sentient sphere plot. It worked, especially the Babel stuff, and it was very much in the spirit of New Life and New Civilizations. Though it was a bit derivative of other Trek fare, I couldn't point to a specific episode they were copying, unlike pretty much every episode of The Orville ever. The sphere's connection to Saru was well set-up and worked, and the ship's malfunctions made sense and weren't too plot-convenient.
A few major developments from this episode. The first is that we seem to be getting much closer to Spock. If the narrative is any indication, we may see him in the next few episodes. This is due to the Disco's chase of his shuttle as well as Burnham's newfound willingness to connect with him. The second major development is May and her newly named species the JahSepp. The revelation that there are beings in the Mycelial Network and that they are harmed by the Disco's jumps is very interesting. Maybe this will be the reason that the ship will stop using the drive, and possibly the explanation for why the technology doesn't appear in later Trek. The third and final development is the loss of Saru's ganglia. The character has, as he says, been defined by fear up until now. It will be interesting to see him adjust to life without that fear going forward, as well as whatever changes he has in his abilities now that his ganglia are gone. His ability to sense and understand people's emotions will be severely limited by this. I look forward to doing more with this.
Strange New Worlds:
This episode took place entirely aboard the Disco.
New Life and New Civilizations:
Firstly, we encountered the sphere. It's fairly run-of-the-mill as far as Trek 'obelisk' species go, but it worked fine. Secondly, we learned that May's species is called the JahSepp. They live in the mycelial network, and the Disco's jumps hurt them. Are there other species living in the network? And how will all this lead to the resurrection of Dr. Culber that many of us suspect is coming?
Pensees:
-What is it with this season and colds?
-Of course, the sphere was red. Is it connected to our larger mystery?
-Saru's multi-lingual abilities came up again here. I didn't think the mention earlier this season felt like an obvious set-up, so that's a point for continuity.
-So, I guess solar energy becomes a way more viable method of powering the earth at some point in the future, if Stamets is being accurate. That's cool. Also, I'll take incidentally topical television lines for $1000, Alex.
-What was Pike doing in the hallway when he met Burnham and Saru on the way to sickbay? He never explained it.
-I liked Saru's sentiment about having never shared his own language, while he learned so many others.
-There were a few rough cuts in one of the scenes between Burnham and Saru. Burnham started moving away in one shot, then was standing still when it cut.
-Everyone rising as Saru left the bridge was a nice touch. Or it would have been, if he'd actually been going to die.
-Another mention of Saru's sister Siranna, who appeared in the Short Trek 'The Brightest Star.'
-More stellar performances by Bahia Watson as well as the main cast. Mary Wiseman and Anthony Rapp in particular were wonderful to watch.
Quotes:
Pike, to Burnham: "My abiding trust in you does not eclipse the mission at hand."
Reno: "I didn't realize a greenhouse could be 'critical' or 'propulsive'?"
Stamets: "It's my version of the house dressing, but it saves your life."
Reno: "Huh."
Saru: "I am a... a slave to my biology."
Saru: "It will be a slow process, like army ants eating a water buffalo."
Saru: "I am dying, Captain, but I am certainly not dead."
4.5 out of 6 life-saving house dressings.
CoramDeo thinks his spaceship knows which way to go.
#Star Trek#Star Trek Discovery#Michael Burnham#Saru#Sylvia Tilly#Paul Stamets#Christopher Pike#Jett Reno#Disco#Star Trek Reviews#Doux Reviews#TV Reviews
12 notes
·
View notes
Text
Locksmith near me in London FAQ - 2022

How to Find a Locksmith Near Me in London in 2022
If you need a locksmith near me in London, you will have to spend some time looking for one. Please search for a trustworthy locksmith, but you also have to make sure that you check out their website to ensure that they have all the details you need.
Moreover, it would help to read customer reviews and ratings to determine whether they are worthy of your trust. After all, no one wants to be taken advantage of, so you should only hire a trustworthy locksmith.
What does locksmith mean?
The word locksmith is related to many other professions that use lock-related tools. Locks are designed to prevent unauthorized access to a building, and locksmiths play an essential role. They have extensive knowledge of locks and can open doors using specialized tools and techniques. While some locksmiths have specialized tools to break locks, others use simple hand tools and have basic skills. Regardless of the skill level of a locksmith, they all have a common purpose: to unlock doors.
A locksmith is not required to make a new key, but a well-made duplicate is more likely to be functional. They also have experience in making locks and should be able to activate the lock's warranty if required. There are some risks associated with locksmithing, so be careful when choosing a locksmith. If you have a locksmith's license, check whether they are insured. In addition to insurance, ask if they offer guarantees for their work.
What's another word for a locksmith?
Locksmiths perform a variety of jobs, from installing locks to adjusting them. Their job duties also include making duplicate keys and managing staff keys. Locksmiths often work on doors, windows, safes, and vehicles, adjusting and repairing security locks to keep them secure.
The word locksmith originated in the 19th century when the debate over full disclosure centered on the security of lock systems.
A locksmith is a professional who designs and manufactures locks. He also makes keys and operates a key-making machine. While this profession is primarily associated with men, women, and small businesses, locksmiths also help secure people's lives worldwide. Locksmiths are experts in locks and can make the perfect lock for any situation.
While locksmithing is a traditional trade, many countries require apprentices. The level of formal education required to become a locksmith varies widely, from a simple training certificate from an employer to a full diploma from an engineering college.
How long has a locksmith been around?
Locks have been around for centuries; we can find evidence of locks as far back as ancient Egypt. During that time, locks were made from wooden materials and used keys to move pins that would unlock the door bar.
Historians have even found evidence of a wooden lock dating back to 704BC! Today, locks have many different functions, and one of the best ways to keep your belongings secure is to invest in a quality lock.
Linus Yale Jr. first invented Locks in the late 1700s, and his company began mass-producing them in the early 1800s. This design became the world's most common type of lock, and it is still used today. Locksmiths have been in business for centuries.
Can a locksmith open any lock?
If you have locked yourself out of your home, you should call a locksmith to help you get in. They are trained professionals with advanced skills who can open any lock. The tools and techniques can help them open a door without damaging it. They work with total concentration and knowledge to get inside any lock and unlock it. The tools they use depend on the type of lock, the type of issue, and the condition of the key.
If you're locked out of your house, a local locksmith in London can help you. Locksmiths are experts at opening various locks, including those on safes. In addition to picking locks, they can also unlock combinations. Some locking devices are complicated to bypass, and a licensed locksmith can use these skills to get into your home or car. To unlock a safe, the locksmith must first know how it works. If the locksmith can't figure out how to work the lock, he will probably use the method of key cutting.
When should I call a locksmith?
You may have been locked out of your home and can't open the door. If you are in a hurry, you may accidentally lock the key inside the lock. Calling a London locksmith is an excellent option for you - they should be able to get to you within 29 minutes or less. There are also tips to avoid calling a locksmith in central London. The following list will help you find a reputable locksmith in the city.
In an emergency, call a locksmith as soon as possible. The locksmith will be able to respond quickly, as it is an emergency. If you cannot get out of your car quickly, try knocking on a neighbor's door. Let the neighbor know what's going on and try to get a place to wait until he arrives. Don't force the lock to open or get into the car yourself - it won't work.
Can a locksmith recommend a lock?
Can a locksmith recommend a lock? The answer depends on the situation. Generally, locks are made with varying designs and strength requirements. A professional locksmith can advise on a lock that meets your requirements and is not only attractive but also secure. Often, customers do not know their options, which could put the security of their homes at risk. Locksmiths are experienced professionals who can recommend locks that protect your property and give you peace of mind.
A locksmith's market knowledge allows him to recommend suitable products for different situations. He knows which quality products are available and what capacity they hold. And this allows them to complete a job in record time. Unlike a handyperson, a locksmith has a standard price list for each job. Handypersons charge by the hour, which often exceeds standard installation fees. While a locksmith's fee may be higher than a handyperson's, he can still recommend a lock that meets your security needs.
Can I trust in a locksmith recommendation?
If your friends have recommended a locksmith, you can trust their recommendation. The locksmith must have professional credentials and training, so check for these. Also, look for customer reviews, especially if they are negative. If the locksmith has a poor reputation, there are problems with their service. Try to contact a former customer of the locksmith to get feedback on the service they received.
A reputable local locksmith will give you a written invoice that shows the exact price you paid for the service, including parts and labor. A reliable locksmith will also provide you with a written estimate and the company's contact information. You must keep a copy of the locksmith's contact information nearby in case you need them. You can also call the locksmith directly if you have any questions or concerns about their service.
Do I have to use the locksmith recommended by friends and family? Yes, but be careful when you do. Many customers fall victim to the locksmith scam. It is possible to trust recommendations from friends and family, but you must also check the locksmith's online reputation. Many untrustworthy locksmiths will have poor reviews on review websites and lack a web presence. And this may indicate that they have something to hide. You should be wary of these locksmiths and avoid them if you can.
Locksmith near me in London services
If you're locked out, you may be wondering where to turn for help. Locksmiths in London can provide various services, from lock repairs to security systems. Services offered by these professionals range from installing new mortice bolts and window locks to 24-hour emergency callouts. For more information, you can read through the following tips. For a start, it's essential to know what you're looking for in a locksmith near me.
A dependable locksmith is an absolute necessity for any home or business. It should be able to reach you fast and complete whatever work is necessary for a timely manner. You'll want to find someone who's professional and experienced and can keep your property secure. London locksmith services are among the most highly rated in the country. If you need a locksmith in London, contact the company you can trust.
uPVC doors use a multi-point locking mechanism. The lock works by lifting a handle that points three hooks vertically—the key controls these hooks, which lock or unlock the door. Depending on the complexity of the lock, a London locksmith near me can help you with this problem. While you can try to tackle repairs yourself, it's safer to call a locksmith sooner rather than later and have a specialist take care of any emergency lockout issues.
London Lock Alert 24hr Ltd - Locksmith near me
3rd Floor, 207 Regent Street, W1B 3HH
London, UK
+4420 8191 1809
https://london-locksmith-24h.co.uk/
#locksmith near me#upvc doors#London#locksmith in London#emergency lockout#security systems#recommend locks#repair#lock#key#locked out
1 note
·
View note
Text
Wwe All Star Free Download

Related: Wwe All Stars Wii - Wwe All Stars Psp - Download Wwe All Stars - Wwe All Stars Demo - Wwe All Stars Pc
License: Shareware
The world’s fastest hedgehog, Sonic, and the SEGA All-Stars are zooming on to your Android phone or tablet for the ultimate party racing showdown. Race as your favorite character across 16 white-knuckle courses in a frantic race to the finish line.
Stay ahead of the pack by dodging traps, firing missiles and, if all else fails, wreaking havoc with your All-Star moves! Whether racing on your own, or battling it out with friends, anything can happen in this crazy competition where winning is only part of the fun!
MEET THE ALL-STARS
Race to the finish as one of 13 iconic SEGA characters and take to the track by car, monster truck, bike, plane and even a banana! Each vehicle has unique handling characteristics, and each character’s All-Star move will speed you to victory!
START YOUR ENGINES
Rev up your skills with 25..
Platform: Android 2.x, Android 3.x, Android 4.4, Android 4.x
Publisher:SEGA of America
Date: 20-04-2014
Size: 461824 KB
Free wwe chanpions all star telecharger download software at UpdateStar. Download Skype and start calling for free all over the world. The calls have excellent. John Cena: Wwe Cena vs all Super Star Match Video John Cena and Brock Lesnar get into a brawl that clears the entire locker room: Raw, April 9, 2012 John Cena and Brock Lesnar get into a brawl that clears the entire locker room: Raw, April 9, 2012 John Cena, Batista & Rey Mysterio vs. Randy Orton & Jeri-Show: Tribute to the Troops, Dec.
License: Shareware
A19bbc 2c thermostat. It’s the bottom of the ninth and the team is down two-zero.. It’s Charlie Brown’s chance to be a hero. Will the Peanuts gang win the biggest baseball game of the summer?
Charlie Brown’s All Stars! magically springs to life in this charming interactive storybook designed for your Android tablet and smartphone. Peanuts fans will delight in sharing this classic story of team spirit and friendship with a whole new generation of underdogs!
https://foxalert217.tumblr.com/post/656907166572281857/download-biblia-reina-valera-1960. Download Reina Valera 1960 Biblia (RVR60) for FREE Download the free Bible RVR60 and start your day fresh with a daily verse and carry your soft-copy of the RVR60 Bible with you anytime. Download Santa Biblia Reina Valera 1960 for Android to biblia Reina Valera 1960 es la mejor aplicacin para llevar la Palabra de Dios a todos lados. Biblia Reina Valera 1960 free download - biblia reina valera 1960, Reina Valera 1960 Santa Biblia, Santa Biblia Reina Valera 1960, and many more programs.
Touch, tilt and swipe your way through tons of summer fun with your favourite Peanuts characters! Take to the mound with Charlie Brown, swing a bat with Linus and make a very special uniform with Lucy and the rest of the team.
Platform: Android 2.x, Android 3.x, Android 4.4, Android 4.x
Publisher:Loud Crow Interactive Inc.
Date: 13-05-2014
Size: 236544 KB
License: Freeware
Game Description
All Stars Tennis is a next generation social arcade tennis game, with fast and fun game play and an awesome range of player styles, unlock-able equipment, and tournaments.
An easy-to-learn, hard-to-master arcade experience with intuitive swipe and tap controls, awesome 3D Tennis physics and cartoon graphics, and amazing levels of player character customization!
Play in the major grand slams and world tournaments against over 90 players as you climb the AllStars Tennis ranks, or challenge your Facebook friends and other players for high score dominance and weekly in-game prizes!
Summary of grand slam features -
• Create your favorite player and climb the AllStars Tennis ranks across 9 tournaments
• Action packed adrenalin fun with awesome fast swipe controls for all the shots
• Amazing..
Platform: Android 2.x, Android 3.x, Android 4.4, Android 4.x
Publisher:BubbleGum Interactive
Date: 25-05-2014
Size: 51200 KB
License: Freeware
Super Mario All-Stars, known in Japan as Super Mario Collection, is a video game that was developed and published by Nintendo for the Super Nintendo Entertainment System in 1993. It contains enhanced remakes of Super Mario Bros., Super Mario Bros.: The Lost Levels (Japanese: Super Mario Bros. 2), Super Mario Bros. 2 (Japanese: Super Mario USA), and Super Mario Bros. 3. There was also an alternate version (entitled Super Mario All-Stars + Super Mario World) bundled with the Super Nintendo in December 1994 that included Super Mario World.
Platform: Windows
Publisher:gameguerilla.com
Date:
Size: 1781 KB
License: Shareware
Embrace the Queen and Shoot the Moon! Discover a new set of friends with an exciting game of Championship Hearts All-Stars! Our 24 All-Star characters span across 5 levels of difficulty to suit the player in you. Savvy Hearts players will love challenging realistic opponents, while Hearts beginners get some extra help with our personal in-game DreamCoach(TM). We'll go beyond just showing you what to play, we'll explain why you should play it. Learn the more you play! Enjoy Hearts at any time of day with Championship Hearts All-Stars! Benefits: *Challenge 24 fun and realistic All-Star opponents across 5 skill levels.
Platform: Windows
Publisher:DreamQuest Software
Date: 1-3-2012
Size: 6714 KB
License: Shareware
Discard and Knock Your Way to Victory! Discover a new set of friends with an exciting game of Championship Gin All-Stars! Our 24 All-Star characters span across 5 levels of difficulty to suit the player in you. Savvy Gin players will love challenging realistic opponents, while Gin beginners get some extra help with our personal in-game DreamCoach(TM). We'll go beyond just showing you what to play, we'll explain why you should play it. Learn the more you play! Enjoy Gin at any time of day with Championship Gin All-Stars! Benefits: *Challenge 24 fun and realistic All-Star opponents across 5 skill levels.
Platform: WinOther
Publisher:DreamQuest Software
Date: 10-08-2012
Size: 6717 KB
License: Shareware
Plunder Melds and Run with this Jewel! Discover a new set of friends with an exciting game of Championship Rummy All-Stars! Our 24 All-Star characters span across 5 levels of difficulty to suit the player in you. Savvy Rummy players will love challenging realistic opponents, while Rummy beginners get some extra help with our personal in-game DreamCoach(TM). We'll go beyond just showing you what to play, we'll explain why you should play it. Learn the more you play! Enjoy Rummy at any time of day with Championship Rummy All-Stars! Benefits: *Challenge 24 fun and realistic All-Star opponents across 5 skill levels.
Platform: WinOther
Publisher:DreamQuest Software
Date: 05-09-2012
Size: 6717 KB
License: Freeware
This is a fan-based Magic the Gathering set that tries to implement the gameplay and characters of popular Warcraft map DotA All-Stars.
Platform: WinOther
Publisher:dota-mtg.sourceforge.net
Date: 07-05-2012
Size: 5634 KB
License: Freeware
Funny Sketches is a 2D physics-based puzzle game. It uses Box2D and Qt. The aim of the game is to guide a red ball to reach allstars in the level. To do this you can draw polygons and circles with your mouse!.
Platform: WinOther
Publisher:funnysketches.sourceforge.net
Date: 22-06-2012
Size: 17336 KB
License: Freeware
DotA Parser is a PHP Code to read DotA AllStars Replay files. The project is in Italian based on a working project about Warcraft III Replay Parser.
Platform: WinOther
Publisher:dotaparser.sourceforge.net
Date: 12-10-2012
Size: 2466 KB
License: Freeware
Objetivo a lograr un juego similar a el MultiHero (Pagina Oficial: http://multihero.sitesled.com/) basado en la libreria dx_lib32 v2.2(Creada por EX3,web oficial: http://dxlib32.se32.com/) la cual usa directX 8.1 en vb6
Super Smash Bross ALLSTARS License - Public Domain.
Platform: WinOther
Publisher:Supersmashbross
Date:
License: Freeware
The Mushroomland Battles: Quest For Quan is a SDL clone of the battle game found in Super Mario All-Stars / Super Mario Bros 3 for the Super Nintendo Entertainment System.
Platform: WinOther
Publisher:Mushroombattles
Date:
License: Shareware
You think the lion is the king of the jungle? The elephant might have something to say about that. This screensaver presents a host of images highlighting this majestic giant. These pictures were selected by users as the best of the best in elephant photography. Elephant All-Stars is a free screensaver created by RateMyScreensaver.com. Screensaver Picture Count: 18 Screensaver Type: Slideshow Credit: All images in this screensaver fall under one of the following licenses: Creative Commons, Attribution ShareAlike 2.
Platform: Windows
Publisher:ratemyscreensaver.com
Date:
Size: 4915 KB
License: Freeware


Another classic Match-3 game launch on Android Market.
Your mission is to win Jewels Star, pass the levels and try to get allstars in each level.
How to play:
1: Match 3 or more identical jewels.
2: Match the jewels until the board transparency,the Jewels star will appear.
3: Make the jewels star down to last line to pass the level.
Tips: Eliminate the jewels quickly can get extra scores.
Features:
- More than 350 levels and 8 pretty scenes in the game, including starry sky,mountains,snow world and so on.
Platform: Android, Windows
Publisher:ITREEGAMER
Date:
Size: 5222 KB
License: Freeware
A classic hexagon Match-3 game launch on Android Market.
Your mission is to win the Jewels Star. Pass the levels and try to get allstars in each level.
How to play:
1: Match 3 or more identical jewels.
2: Match the jewels until the bottom board,the Jewels star will appear.
3: Make the jewels star down to last line to pass the level.
Tips: Eliminate the jewels quickly can get extra scores.
Features:
- More than 300 levels and multiple pretty scenes in the game.
- Match 4 jewels can win a bomb and 1 lighting.
Platform: Android, Windows
Publisher:ITREEGAMER
Date:
Size: 5632 KB
License: Freeware
Fun and addictive Match-3 game!
Another classic Match-3 game launch on google play.
Your mission is to win Dragon Egg, pass the levels and try to get allstars in each level.
How to play:
1: Match 3 or more identical jewels.
2: Match the jewels until the board transparency,the Dragon Egg will appear.
3: Make the Dragon Egg down to last line to pass the level.
Tips: Eliminate the jewels quickly can get extra scores.
Features:
- More than 200 levels and 6 pretty scenes in the game, including Forests, caves, floating islands and etc.
Platform: Android, Windows
Publisher:ITREEGAMER
Date:
Size: 8294 KB
License: Freeware
In Off Road, speed isn't always your friend. Learn the limits, slow down and use the brakes more often.
A True Off Road Racing Game and best of all its FREE!
Advance in two ways:
Use brute SPEED to beat the time or,
Get allstars using your SKILL of Car handling.
FEATURES
** Great Physics
** Beautiful Artsy Graphics
** Manual Car Setup
** Awesome Damage system
** Dynamic Environment
** Great Controls
** Regular Updates
** Loads of FUN
Become a fan of Racer: Off Road on Facebook and
get updates, driving tips and tricks.
Platform: Android, Windows
Publisher:Soft Brew Mobile
Date:
Size: 12288 KB
License: Freeware
A classic hexagon Match-3 game launch on Android Market.
Your mission is to win the Jewels Star. Pass the levels and try to get allstars in each level.
How to play:
1: Match 3 or more identical jewels.
2: Match the jewels until the bottom board,the Jewels star will appear.
3: Make the jewels star down to last line to pass the level.
Tips: Eliminate the jewels quickly can get extra scores.
Features:
- More than 300 levels and multiple pretty scenes in the game.
- Match 4 jewels can win a bomb and 1 lighting.
Platform: Android, Windows
Publisher:Jewels World Games
Date:
Size: 5734 KB
License: Freeware
Classic Arcade fun for your mobile! Help Rob the Ranger to collect allstars without hitting dangerous monsters! But take care, your limited air will decrease fast!. Tektronix wavestar software download.
Platform: Windows
Publisher:Softgames Mobile Entertainment Services GmbH
Date:
Size: 1024 KB
License: Shareware
Starzzle is an addictive puzzle game where you have to pick allstars over 84 levels across 4 different worlds. If you are man enough probe yourself finishing the existing 31 challenges and try to be in our top ten highscores!.
Wwe All Stars Free Download For Xbox 360
Platform: Windows
Publisher:Bionic-Thumbs
Date:
Size: 17408 KB

0 notes
Text
Should software companies invest in rewriting C code in Rust?
T he C programming language was designed by by Dennis Ritchie close to 50 years ago. It is a general-purpose procedural programming language. Throughout the years, C has dominated the market for a few fundamental reasons. It is the easiest language to port to any new hardware architecture or operating system platform. While any language that compiles to native machine language can be used to write the base of an operating system, C remained the choice due to its portability. C also produces very fast code that runs directly on computer processors. However, with its versatility came some short comings.
C allows a wide range of software bugs and these software bugs are often the root cause for security issues. Some common sources of bugs in C code are "buffer overflows", "off-by-one errors", and "out of bounds reads". This is in addition to dangling pointers and memory leaks. C and C++ software are especially vulnerable as they have no language specific mechanisms for bounds checking or any of the sort. While C++ has smart pointers, nothing forces their use although C++ is an attractive choice due to being able to consume C libraries. All these issues are been the cause of many security exploits. C, inherently, is not memory safe.
So, what is the alternative if we are writing system software where bytecode and languages running in a virtual machine, such as java and C#, are not an option?
Ten years ago, Mozilla, the authors of the popular Firefox web browser, which was written in C++ with a graphics interface in XUL, an extensible xml syntax language for user interfaces, started a new project called Rust. Rust is a new programming language that promises to overcome the deficiencies in C. This makes it an attractive option to replace C. Rust moves a lot of the runtime issues in C to compile time issues. For instance, if your program or library is going to read memory outside an array index, the application will not run and if the index number is read at runtime, the application will stop running and you will not get wrong results. This prevents security bugs caused by reading incorrect or random data from memory. Such bugs have often caused headaches for Windows users and people utilizing server software written in C due to the excessive security implications. In addition to that, Rust has a strict ownership system that makes software very robust. This ownership system avoids memory leaks and pointers to random data. This saves time for developers and allows them to concentrate on algorithm writing instead of fighting with the programming language.
This raises a question. Should companies invest in porting their C code to Rust? I would say yes and for the following reasons.
The rust standard language and standard libraries are constantly under development to add convenience methods and language features. Basically, Rust is designed with the developer in mind.
Thanks to its memory safety strength, Rust saves money and developer resources that would otherwise be wasted on hunting difficult to find security bugs.
Rust has built-in unit testing features. Every piece of software in development should have two kinds of tests. The first type is unit tests which test individual libraries and pieces of code by isolating them and making sure they produce their intended results. The second type is integration tests. Integration tests make sure the entire software system continues to function as intended after changes to the code in any part of the software are committed. There are many 3rd party libraries for testing C and C++ software. Every software company adopts a different testing system. This is not required under Rust since it has built in unit testing and integration testing features. As we mentioned in the previous point, Rust is designed with the developer in mind.
Another reason why it makes sense for companies to invest in porting their C code to Rust is interoperability. Rust has tools to provide C API headers. In other words, you can write safe code in Rust and allow C and C++ applications to use it. The opposite is also true. Rust has community provided crates that bind to many popular existing C libraries.
Microsoft is also adopting Rust, albeit gradually. About 70% of the security bugs in the Windows platform are memory safety bugs. It is important to mention that the Microsoft’s platform of software including Microsoft Windows and Office make heavy use of C and C++. This makes Microsoft the owners of the world’s largest C and C++ codebases. However, Microsoft is now working on rust bindings for windows runtime libraries and is hosting them on Github. This gives Rust credibility and encourages other companies to follow through as well.
Linus Torvalds, the man behind the Linux kernel development, is often regarded as one of the most experienced and knowledgeable C developers. Currently, the Linux kernel is mostly C and Assembly code. It is developed by companies such as Intel, Microsoft, Google, and many individual developers. Torvalds has often rejected the use of C++ in the Kernel. Nevertheless, he has shown no objection towards including rust code in the Linux kernel.
If you are writing new system software, I highly recommend Rust. The community is unique and helpful. My experience also shows that its adoption and gradually porting C code to Rust yields not only cost savings but provides highly efficient software.
I hope you have enjoyed my article. Please visit my website if you need a true Murex expert that can help you out. I am an experienced IT consultant and I often have articles and tutorials that can be beneficial to my readers.
0 notes
Text
Most Significant Reasons to Learn Python Programming Course?
Our Python Programming Course
Python is an open-source, high-level programming language that has been designed for usage with a wide range of operating systems. Because of its dynamic and diverse character, it is said regarded as the most powerful programming language. Python is uncomplicated to use, with straightforward syntax, and newcomers to the language find it extremely easy to grasp the ideas. Python is in great demand in the industry, having been utilized by pioneer websites such as YouTube and DropBox. Register for Python Training if you wish to get the benefits of Python.
With the Python programming course, you can discover how to bridge web development and data analytics. Python modules interact with a variety of databases, making it an excellent choice for large-scale data analysis. The Python programming language is often the best choice for introductory courses in data science and machine learning.
Let us now look at the main reasons why the Python language is utilized by such a wide variety of individuals.
Object-Oriented
Python Programming Course
Object-Oriented Programming is a sophisticated Python technique that enables the construction and reuse of data structures. Because of its reusability, the task is completed more efficiently and in less time. Object-oriented programming has been applied to classes and numerous interactive objects in recent years. Object-Oriented Programming methods may be applied to any software and executed in any programming language.
Readability
The Python coding language is relatively simple to grasp due to its basic syntax. As a result, Python may be used as a prototype and then implemented in another programming language after the code has been tested.
Python is completely free.
Python is a free and open-source programming language that allows for unlimited use. It can be changed, shared, and used commercially under this open-source license. The license is even available for the complete source code, with free support. CPython, the most frequently used Python implementation, is compatible with all operating systems. As a result of its well-designed, strong software with scalable and portable features, C++ has become a commonly used programming language.
Programming at a higher speed
Python is a high-level language, and programming in it is far faster than programming in other low-level languages.
Cross-platform compatibility
Python can run on all major operating systems, including Mac OS, Microsoft Windows, Linus, and Unix. This programming language provides the greatest experience while working with any operating system.
Integration Capabilities
Following are the notable integration capabilities of Python:Process control capabilities are strong.
• Capability to be incorporated as a scripting programming language
• Ease of development of online services
If you want to work with Python, enroll in one of the Python Instruction Institutes, where applicants receive additional benefits from the training.
Highly experienced and competent instructors lead training sessions to ensure that candidates have a thorough knowledge. Mock exams are provided online for aspirants to assess their level of comprehension. Analytical reports will be provided with accurate test findings. Aspirants can also choose from various learning options such as corporate training, boot camp training, classroom training, and so on.
How to Choose a
Python Programming Course
When looking for a Python programming course, the options might be befuddling and intimidating. There are websites that promise to be able to teach you Python in less than half an hour! Of course, that’s rubbish. However, you’d be amazed how many people fall for this type of commercial ploy. (Do not become one of them.)
On the other side, there are three-day boot camps that cost $1,000 or more (plus hundreds of dollars in plane fare, hotel and dining costs) in python language. These are genuine, and many of them provide good instruction, but for the majority of individuals, they are not the greatest option.
These boot camp-style sessions are ideal if you a) already have some programming expertise in other computer languages and b) need to learn Python quickly for a professional project. In reality, it’s probable that the majority of people completing these boot camps aren’t paying their own tuition – their employers are.
But what if you’re a complete Python noob? What if you want to learn this flexible and cutting-edge language but lack programming expertise, much alone a few thousand dollars to spend on a boot camp? Are there any Python programming course that might be appropriate for you? There are, indeed! Of course, some are superior to others.
Here are some pointers to consider while selecting a python for market research course or book: Check to see if it is truly appropriate for actual beginners – many publications and courses use the term “beginners” extremely loosely. They may be presuming you have some Python experience but lack an advanced grasp of the language. You should double-check it before making a purchase.
Make sure the lessons are brief and easy to understand so that you can move quickly yet not become overwhelmed. Another essential factor to consider is the cost. A beginner’s Python training should not cost more than $100. Because Python training is such a popular industry right now, some firms charge extra, but you can get a fantastic beginner’s course in Python for far under $100.
Make sure the lessons are brief and easy to understand so that you can move quickly yet not become overwhelmed. Another essential factor to consider is the cost. A Data analysis using Python for beginner’s should not cost more than $100. Because Python training is such a popular industry right now, some firms charge extra, but you can get a fantastic beginner’s course in Python for far under $100.
0 notes
Text
GNOME Wiki
I hate hate hate when I search gnome and this comes up! I love your name but I am not looking for you! Anyways here is the wiki article about it thought because it is still part of the gnome family...
GNOME

GNOME (/(ɡ)noʊm/) is a free and open-source desktop environment for Unix-like operating systems. GNOME was originally an acronym for GNU Network Object Model Environment, but the acronym was dropped because it no longer reflected the vision of the GNOME project.
GNOME is part of the GNU Project and developed by The GNOME Project which is composed of both volunteers and paid contributors, the largest corporate contributor being Red Hat. It is an international project that aims to develop software frameworks for the development of software, to program end-user applications based on these frameworks, and to coordinate efforts for internationalization and localization and accessibility of that software.
GNOME 3 is the default desktop environment on many major Linux distributions including Fedora, Debian, Ubuntu, SUSE Linux Enterprise (exclusively), Red Hat Enterprise Linux, CentOS, Pop! OS, Oracle Linux, SteamOS, Tails and Endless OS, as well as Solaris, a major Unix operating system; and provided as an official edition by Manjaro; also the continued fork of the last GNOME 2 release that goes under the name MATE is default on many Linux distros that targets low usage of system resources.
History
GNOME 1

GNOME was started on 15 August 1997 by Miguel de Icaza and Federico Mena as a free software project to develop a desktop environment and applications for it. It was founded in part because K Desktop Environment, which was growing in popularity, relied on the Qt widget toolkit which used a proprietary software license until version 2.0 (June 1999). In place of Qt, GTK (GIMP Toolkit) was chosen as the base of GNOME. GTK uses the GNU Lesser General Public License (LGPL), a free software license that allows software linking to it to use a much wider set of licenses, including proprietary software licenses. GNOME itself is licensed under the LGPL for its libraries, and the GNU General Public License (GPL) for its applications.
The name "GNOME" was initially an acronym of GNU Network Object Model Environment, referring to the original intention of creating a distributed object framework similar to Microsoft's OLE, but the acronym was eventually dropped because it no longer reflected the vision of the GNOME project.
The California startup Eazel developed the Nautilus file manager from 1999 to 2001. De Icaza and Nat Friedman founded Helix Code (later Ximian) in 1999 in Massachusetts; this company developed GNOME's infrastructure and applications, and in 2003 was purchased by Novell.
During the transition to GNOME 2 around the year 2001 and shortly thereafter there were brief talks about creating a GNOME Office suite. On 15 September 2003 GNOME-Office 1.0, consisting of AbiWord 2.0, GNOME-DB 1.0 and Gnumeric 1.2.0 was released. Although some release planning for GNOME Office 1.2 was happening on gnome-office mailing list, and Gnumeric 1.4 was announced as a part of it, the 1.2 release of the suite itself never materialized. As of 4 May 2014 GNOME wiki only mentions "GNOME/Gtk applications that are useful in an office environment".
GNOME 2
GNOME 2 was very similar to a conventional desktop interface, featuring a simple desktop in which users could interact with virtual objects, such as windows, icons, and files. GNOME 2 started out with Sawfish, but later switched to Metacity as its default window manager. The handling of windows, applications, and files in GNOME 2 is similar to that of contemporary desktop operating systems. In the default configuration of GNOME 2, the desktop has a launcher menu for quick access to installed programs and file locations; open windows may be accessed by a taskbar along the bottom of the screen, and the top-right corner features a notification area for programs to display notices while running in the background. However, these features can be moved to almost any position or orientation the user desires, replaced with other functions or removed altogether.
As of 2009, GNOME 2 was the default desktop for OpenSolaris. The MATE desktop environment is a fork of the GNOME 2 codebase (see Criticism, below.)
GNOME 3
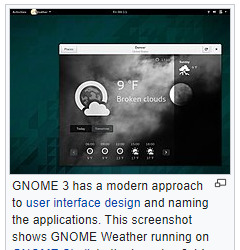
GNOME 1 and 2 followed the traditional desktop metaphor, but GNOME 3, released in 2011, changed this with GNOME Shell, a more abstract metaphor where switching between different tasks and virtual desktops takes place in a separate area called "Overview". Also, since Mutter replaced Metacity as the default window manager, the minimize and maximize buttons no longer appear by default, and the title bar, menu bar and tool bar combined in one horizontal bar called "header bar" via Client-Side Decoration mechanism. Adwaita replaced Clearlooks as the default theme. Many GNOME Core Applications also went through redesigns to provide a more consistent user experience.
Criticism
The release of GNOME 3, notable for its move away from the traditional menu bar and taskbar, has caused considerable controversy in the GNU and Linux community. Many users and developers have expressed concerns about usability. A few projects have been initiated to continue development of GNOME 2.x or to modify GNOME 3.x to be more like the 2.x releases.
GNOME 3 aims to provide a single interface for desktop computers and tablet computers. This means using only input techniques that work on all those devices, requiring abandonment of certain concepts to which desktop users were accustomed, such as right-clicking, or saving files on the desktop.
These major changes initially evoked widespread criticism. The MATE desktop environment was forked from the GNOME 2 code-base with the intent of retaining the traditional GNOME 2 interface, whilst keeping compatibility with modern Linux technology, such as GTK 3. The Linux Mint team addressed the issue in another way by developing the "Mint GNOME Shell Extensions" that ran on top of GNOME Shell and allowed it to be used via the traditional desktop metaphor. This eventually led to the creation of the Cinnamon user interface, which was forked from the GNOME 3 codebase.
Among those critical of the early releases of GNOME 3 is Linus Torvalds, the creator of the Linux kernel. Torvalds abandoned GNOME for a while after the release of GNOME 3.0, saying "The developers have apparently decided that it's 'too complicated' to actually do real work on your desktop, and have decided to make it really annoying to do". Torvalds stated that his objections were universally held by the varied Linux developers he knew. In 2013, Torvalds resumed using GNOME, saying "things had gotten much better in the past year" but noting that "they have extensions now that are still much too hard to find; but with extensions you can make your desktop look almost as good as it used to look two years ago". Torvalds has suggested that the "GNOME Tweak Tool" should be merged into GNOME 3.
As of 2015, critical reception has been much more positive. For example, Debian, a Linux distribution that had historically used GNOME 2, switched to Xfce when GNOME 3 was released but readopted GNOME 3 in time for the release of Debian 8 "Jessie".
Releases
Release cycle
Each of the component software products in the GNOME project has its own version number and release schedule. However, individual module maintainers coordinate their efforts to create a full GNOME stable release on an approximately six-month schedule, alongside its underlying libraries such as GTK and GLib. Some experimental projects are excluded from these releases.
GNOME version numbers follow the scheme v.xx.yy. Here, v is a major version, which can include large changes such as ABI breakage; these have no regular schedule and occur in response to requirements for large-scale changes. xx is a minor version, released on the above schedule of approximately every 6 months, in which the 1- or 2-digit number's parity indicates the type of release: if xx is even (e.g. 3.20) the release is considered stable, whereas if xx is odd it represents a current development snapshot (e.g. 3.21) that will eventually evolve into the next stable release. yy indicates a point release, e.g. 3.20.6; these are made on a frequency of weeks in order to fix issues, add non-breaking enhancements, etc.
GNOME releases are made to the main FTP server in the form of source code with configure scripts, which are compiled by operating system vendors and integrated with the rest of their systems before distribution. Most vendors only use stable and tested versions of GNOME, and provide it in the form of easily installed, pre-compiled packages. The source code of every stable and development version of GNOME is stored in the GNOME git source code repository. Interested users can always obtain a snapshot of the _master_ development branch or any other branch/tag and build a cutting-edge version for their own use.
A number of build-scripts (such as JHBuild or formerly GARNOME) are available to help automate the process of compiling the source code.
Release history
Features
User interface design
See also:
Worse is better, KISS principle, Principles of user interface design, Minimalism (computing), Usability
The Official GNOME Human Interface Guidelines
Since GNOME 2, productivity has been a key focus for GNOME. To meet this end, the GNOME Human Interface Guidelines (HIG) were created. All GNOME programs share a coherent style of graphical user interface (GUI) but are not limited to the employment of the same GUI widgets. Rather, the design of the GNOME GUI is guided by concepts described in the GNOME HIG, itself relying on insights from cognitive ergonomics.[74] Following the HIG, developers can create high-quality, consistent, and usable GUI programs, as it addresses everything from GUI design to recommended pixel-based layout of widgets.
During the GNOME 2 rewrite, many settings deemed of little value to the majority of users were removed. Havoc Pennington summarized the usability work in his 2002 essay "Free Software UI", emphasizing the idea that all preferences have a cost, and it is better to make software behave correctly by default than to add a UI preference to get the desired behavior:
A traditional free software application is configurable so that it has the union of all features anyone's ever seen in any equivalent application on any other historical platform. Or even configurable to be the union of all applications that anyone's ever seen on any historical platform (Emacs *cough*).
Does this hurt anything? Yes it does. It turns out that preferences have a cost. Of course, some preferences also have important benefits – and can be crucial interface features. But each one has a price, and you have to carefully consider its value. Many users and developers don't understand this, and end up with a lot of cost and little value for their preferences dollar.
Accessibility
GNOME aims to make and keep the desktop environment physically and cognitively ergonomic for people with disabilities. The GNOME HIG tries to take this into account as far as possible but specific issues are solved by special software.
GNOME addresses computer accessibility issues by using the Accessibility Toolkit (ATK) application programming interface, which allows enhancing user experience by using special input methods and speech synthesis and speech recognition software. Particular utilities are registered with ATK using Assistive Technology Service Provider Interface (AT-SPI), and become globally used throughout the desktop. Several assistive technology providers, including Orca screen reader and Dasher input method, were developed specifically for use with GNOME.
Internationalization and localization
Main article:
Internationalization and localization
The internationalization and localization of GNOME software relies on locale.
Desktop
GNOME provides three different login sessions for desktop:
GNOME Flashback

GNOME Flashback is an official session for GNOME 3. It is based on GNOME Panel and Metacity (window manager), it is lightweight, has lower hardware requirements and uses less system resources (memory and CPU) than GNOME Shell. It provides a traditional and highly customizable taskbar (panel) with many plug-ins bundled in one package (gnome-applets) including a customizable start menu. It provides a similar user experience to the GNOME 2.x series and has customization capacities as built-in.
GNOME Flashback consists of the following components:
Metacity (window manager)
GNOME Panel – a highly configurable taskbar
gnome-applets – a collection of useful applets for the GNOME Panel
GNOME Shell

This session is based on GNOME Shell and Mutter (window manager). It is default and offers a mobile-like paradigm for launching applications and accessing open windows and virtual desktops, but through the use of extensions it is possible for the appearance to be that of a traditional taskbar and provide a basic start menu. This session uses more RAM and CPU due to use of JavaScript for GNOME Shell and all of its extensions, and requiring 3D acceleration.
GNOME Shell is the default graphical shell of GNOME. It features a top bar holding (from left to right) an Activities button, an application menu, a clock and an integrated system status menu.[80][81] The application menu displays the name of the application in focus and provides access to functions such as accessing the application's preferences, closing the application, or creating a new application window. The status menu holds various system status indicators, shortcuts to system settings, and session actions including logging out, switching users, locking the screen, and suspending the computer.
Clicking on the Activities button, moving the mouse to the top-left hot corner or pressing the Super key brings up the Overview.[82] The Overview gives users an overview of current activities and provides a way to switch between windows and workspaces and to launch applications. The Dash on the left houses shortcuts to favorite applications and open windows and an application picker button to show a list of all installed applications.[80] A search bar appears at the top and a workspace list for switching between workspaces is on the right. Notifications appear from the bottom of the screen.[83]
GNOME Classic
Beginning with GNOME 3.8, GNOME provides a suite of officially supported GNOME Shell extensions that provide Applications menu (a basic start menu) and "Places menu" on the top bar, and a panel with windows list at the bottom of the screen that lets quickly minimize and restore open windows, a "Show Desktop" button in the bottom left and virtual desktops in the bottom right corner.
Mobile
By using GNOME Shell, client-side decoration, and the libhandy library, GNOME and its applications provide a responsive user interface that works on all the three desktop, tablet, and mobile form factors without the need to be designed and compiled separately for each one.
Development
GNOME is developed by The GNOME Project, and, like most free software projects, GNOME development is loosely managed. Discussion chiefly occurs on a number of public mailing lists.GNOME developers and users gather at an annual GUADEC meeting to discuss the current state and the future direction of GNOME.[ GNOME incorporates standards and programs from freedesktop.org to better support interoperability with other desktops.
GNOME is mainly written in C, XML, C++, C#, HTML, Vala, Python, JavaScript, CSS, and more. A number of language bindings are available
Development platform
The GLib data structures and utilities library, GObject object and type system and GTK widget toolkit comprise the central part of GNOME development platform. This foundation is further extended with D-Bus IPC framework, Cairo 2D vector-based drawing library, Clutter accelerated graphics library, Pango international text rendering library, PulseAudio low-level audio API, GStreamer multimedia framework, and several specialized libraries including NetworkManager, PackageKit, Telepathy (instant messaging) and WebKit.[90]
GNOME Display Manager (GDM), which manages user sessions, X and Wayland alike.
Tracker automatically searches the specified directories for files and keeps an index of them to provide fast search; heavily integrated into GNOME Shell and GNOME Files
GVfs, an abstraction layer framework for file systems augmenting GIO; well integrated into GNOME Files and GNOME Disks
dconf a backend for GSettings
Mutter, the Wayland compositor and X Window Manager
Linux color management, udev, etc.
Evolution Data Server, responsible for managing mail, calendar, address book, tasks and memo information
Meson is replacing GNU Build System (autotools) as build automation tools of choice
BuildStream a distribution agnostic build and integration tool
Dependencies
The GNOME desktop environment does not consist solely of the graphical control element library GTK and the core applications that make use of it. There are quite a few additional software packages that make up the GNOME desktop environment, such as the above.
Wayland or X Window SystemMain article:
Wayland (display server protocol)
GNOME runs on Wayland and the X Window System. Wayland support was introduced in GNOME 3.10 and deemed "for the majority of users […] a usable day to day experience" by 3.20, at which point Wayland became the default user session. GNOME 3.24 will extend Wayland compatibility to Nvidia drivers. With GNOME 3.30, it is possible to run GNOME without X.Org Server, using only Wayland.
systemd
In May 2011 Lennart Poettering proposed systemd as a GNOME dependency. As systemd is available only on Linux, the proposal led to a discussion of possibly dropping support for other platforms in future GNOME releases. Since GNOME 3.2 multiseat support has only been available on systems using systemd. In November 2012 the GNOME release team concluded there will be no compile time dependency on systemd for basic functionality, like session tracking. For non-basic functionality, like power management, compile time dependency is possible. For example, there is no concept of systemd inhibitors in alternatives like consolekit. A package manager may want to ensure that the system is not turned off while the upgrade is taking place.
Application
Core Applications
GNOME Core Applications
There are a large number of GTK and Clutter-based programs written by various authors. Since the release of GNOME 3.0, The GNOME Project concentrates on developing a set of programs that accounts for the GNOME Core Applications. The commonalities of the GNOME Core Applications are the adherence to the current GNOME Human Interface Guidelines (HIG) as well as the tight integration with underlying GNOME layers like e.g. GVfs and also with one another e.g. GOA (gnome-online-accounts)settings and GNOME Files with Google Drive and GNOME Photos with Google Photos. Some programs are simply existing programs with a new name and revamped user interface, while others have been written from scratch.
Games
GNOME Games have the look and feel of the GNOME Core Applications and are released simultaneously with GNOME. All have been rewritten to conform to the current GNOME Human Interface Guidelines.
Development tools
Programmers have written software to provide development tools consistent with the GNOME desktop and to facilitate the development of GNOME software.
GNOME Builder is the new integrated development environment, Anjuta is the older one. Glade Interface Designer software constructs graphical interfaces using the graphical control elements in GTK. Devhelp is an API browser, Accerciser an accessibility explorer.
There are several debugging tools, including Nemiver, GtkInspector and Alleyoop, have also been provided to facilitate development of GNOME software.
Integration options for third-party development tools (e.g. NoFlo) also exist.
The libsoup library enables access to HTTP servers from GNOME applications.
BuildStream is a flexible and extensible framework for the modelling of build and CI pipelines in a declarative YAML format, written in Python. Its mascot is a Beaver, because beavers build things in a stream.

https://en.wikipedia.org/wiki/GNOME
That concludes that! It is everywhere though! Once again Thank you Wiki!
0 notes
Text
New Look Sabres: Midseason Thoughts

Happy New Year! The Buffalo Sabres game against the Florida Panthers tomorrow will be their 41st game. By my calculation that’s the halfway point of the season and I think my math skills are at least good enough for basic division. This landmark of the season had me thinking we ought to take a look at the season as whole here when we’re about halfway certain what it’s going to end up looking like. Yea, perhaps we can be a little more than halfway certain with our predictions at this point but just let me show off my basic math skills, ok? I initially started thinking about the grand scheme of things about this season back after the Sabres met the Leafs the first time at the start of December. True rivalry games like that always get me thinking. There is a lot more to digest about this season based on the first half than my most optimistic self would’ve thought in September. I remember predicting the Sabres would have a winning record in October like I was going out on a limb. The expectations clearly changed this season, early on two: like the first twenty odd something games it became clear the corner had finally been turned. There’s a lot to that and I will dive into some of the minutia of that in later thoughts but perhaps it’s wiser first to reflect. Before I started New Look Sabres I wrote hockey articles on and off for different outlets and even freelance like this. I have no writing degrees so my thoughts were encapsulated in slick declarative titles: 2013-2014 was the Dawn of the Tank, 2014-2015 was the War of the Tanks, 2015-2016 was the New Guard Rising, 2016-2017 was the lost season and 2017-2018 was… *shutters* … the trash season. Jack Eichel’s rookie year had its optimism as you can see but the seasons to follow showed the things wrong with the team needed fixing. Certainly not all those problems are fixed but what might this season be called? I feel that the first half of this season has already given us a pretty solid idea…
…2018-2019 is the Reclamation. The season the Sabres reclaimed not only relevance but the mantle of the minimum level of quality Sabres teams have had over the last forty nine years. Moreover, the Buffalo Sabres as a club reclaimed their fans: not just the diehards who look at draft rankings in January, the casual fans and the ones who just don’t want to be miserable watching hockey. The runner up name was the Found Money Season. That’s where my first thought starts. This team has turned a corner; they’re a playoff contender now. At least they acted like it in the first half. Expectations should remain there. Make the playoffs, please oh please make the playoffs; divisional or a more likely wildcard, just make it. Anything that happens beyond that is a gift; found money if you will. If the Sabres win a game there: excellent if they win a round, fantastic! If they get swept, okay whatever. I want to say this now not just to get ahead of crazy March and April sound bites but to remind us all not to sell the farm. The playoff race, the playoffs themselves and everything that comes before is a learning experience more than anything else. I would say some young guys on this team don’t know what the Stanley Cup playoffs are like but really it’s true with every member of the Sabres core including Jeff Skinner. Pominville is really your only guy who’s not a former Blue who can tell you about that. Bank points through the second half, make the playoffs and from there on out its whatever this season. No expectation past game 82 except learn. Learn what it means to be in the playoffs and play like it. The second half will be decisive if not for playoff positioning than simple team building. Not the roster building GMs do, no: Build Buffalo Sabres hockey. Learn it, and then teach us what it’s like. Playoffs are just proof of competitiveness, that’s all the Sabres need to prioritize right now on that front: growth in competitiveness.
They’ve found some kind of groove already this season but in the second half the Sabres need to lock down their style, their game, their groove and put it to the test in the playoffs against whoever they face. It seems cruel to use this phrase sometimes as a Sabres fan knowing what we’ve been through but we’re still in a building year. I am not going to be offended if Jason Botterill goes out and acquires a small piece or two but it better not be expensive and it better not be a rental. Reward these guys with a weapon that will be here a little while. Rental players you get for a playoff run or a season and a half rarely make the huge difference you want them to make. Reinforce the defense or shore up secondary scoring if you make a move. That’s how you’ll reward a Sabres team that turned it around this season. The Playoff window is just opening, the Stanley Cup window has not opened yet. Don’t buy a lot by selling futures when our focus is experience and growth as a team. So yes, reward them for what they’ve done with a cheaper move but don’t make the move that will be seen as demanding a deep run at the Cup. That rewarding the group is important in its own way. Maybe, although cheap wouldn’t be the word I use to describe it, that reward is signing Jeff Skinner since he wants to stay? Hmm.
My second thought I already touched on a little bit: it’s consistency. This Buffalo Sabres team is remarkably streaky and that’s fine when there’s enough wins in there to make it work but that’s not a habit of Stanley Cup teams. Consistently winning, or being damn close to it, requires not just one line action like we saw almost exclusively in December, but secondary scoring and a defensive core that contributes as well. Some of that you develop and call up in house but maybe, once again at a good price, you bring in a piece for the parts here that are not producing at all. My third point is a discussion of goaltending. The Carter Hutton-Linus Ullmark tandem has been top ten in this league in goals against and save percentage. Given where each of those guys is in their careers you expect a drop off at some point. That drop off has not come yet and any strategizing for it seems a little moot right now. That said, it would be good if Ullmark good get more starts in the second half. An 8-1-3 record in his 13 starts is safe enough a bet to trust him. Trust in him will build confidence and if he is the goalie of the future in Buffalo, which I truly believe he is, he needs that. Yea, he got pulled before the third in that one game, he’ll have his mistakes like any goalie does but I could not feel happier about the Sabres situation in net right now.
My fourth point: SIGN JEFF SKINNER! LOL, no that’s important but it’s not actually a midseason thought. No, I want to talk more generally about the season now; where we’ve been and where we’re going. The beginning of the season can really be thought of us as before and after Jeff Skinner got put on Eichel’s wing. After that 5-1 rout on the road against San Jose Phil Housley took a blender to the lineup and got some good results. Four wins came in the next eight games and then the next major phase of the Sabres season happened when everyone kicked into over gear and the ten game win streak hit. For three weeks the Sabres felt invincible beating teams like Tampa, Winnipeg and San Jose pulling in every Western New York Hockey fan that had since gotten tired of Sabres sorrows. The five game skid that followed the win streak wasn’t as bad as it felt and the wins came back although Buffalo is still in a post-win streak hangover from a standings perspective barely playing .500 hockey since the big one. From here on out the road map to the playoffs is simpler than seven years outside the playoffs might lead you to believe, at least until the end of January. It’s banking points, particularly in Western Canada before the bye week late in January, before suiting up for a stretch run in February and March that only sees two breaks of more than two days. The back half will be a crucible after the bye week and there will be teams, even ones not names Boston, Montreal or the Islanders, who will give you fits and make you work for that playoff berth we’ve all been dying for.
This blog is going to change a little bit in the second half of the season as well. Hopefully it won’t be a crucible to get through but I am making myself think harder for my comedic bits starting now. Instead of the burn book for all our reasons to hate divisional rivals in those games, each game against an Eastern Conference opponent will feature a bit on what facing them in the first round of the playoffs would mean. This will be understandably silly against some opponents like Ottawa and New Jersey but it should be fun. Some programming notes: seasons for this blog will revolve around the post season. The blog season ends when the Sabres are eliminated from contention for Lord Stanley’s Cup whether that be March *shutters* or early May. The blog season will formally end with a 2018-2019 Season retrospective followed by a break before the draft that may or may not see some kind of “Playoffs according to the Sabres” and or another Schedule breakdown depending on when that releases. If you care enough about the blog to read through that then thank you, I wish you had cared enough to drop me a comment or two going into this but I’m not bitter: it’s a super chill hockey blog, I don’t expect my writing here to attract deep thought. That said, deep thoughts appreciated.
Thanks for reading.
P.S. I want to signal boost the opinion that if the Sabres do not make the playoffs in 2019 then Phil Housley’s job should be at stake. A collapse great enough to ruin the 11 point lead on a playoff spot they had in November is already well in progress. Lots of hockey left but there’s the objective.
0 notes
Text
The 'Unix Way'
It probably shouldn't, but it routinely astonishes me how much we live on the Web. Even I find myself going entire boots without using anything but the Web browser. With such an emphasis on Web-based services, one can forget to appreciate the humble operating system.
That said, we neglect our OS at the risk of radically underutilizing the incredible tools that it enables our device to be.
Most of us only come into contact with one, or possibly both, of two families of operating systems: "House Windows" and "House Practically Everything Else." The latter is more commonly known as Unix.
Windows has made great strides in usability and security, but to me it can never come close to Unix and its progeny. Though more than 50 years old, Unix has a simplicity, elegance, and versatility that is unrivalled in any other breed of OS.
This column is my exegesis of the Unix elements I personally find most significant. Doctors of computer science will concede the immense difficulty of encapsulating just what makes Unix special. So I, as decidedly less learned, will certainly not be able to come close. My hope, though, is that expressing my admiration for Unix might spark your own.
The Root of the Family Tree
If you haven't heard of Unix, that's only because its descendants don't all have the same resemblance to it -- and definitely don't share a name. MacOS is a distant offshoot which, while arguably the least like its forebears, still embodies enough rudimentary Unix traits to trace a clear lineage.
The three main branches of BSD, notably FreeBSD, have hewn the closest to the Unix formula, and continue to form the backbone of some of the world's most important computing systems. A good chunk of the world's servers, computerized military hardware, and PlayStation consoles are all some type of BSD under the hood.
Finally, there's Linux. While it hasn't preserved its Unix heritage as purely as BSD, Linux is the most prolific and visible Unix torchbearer. A plurality, if not outright majority, of the world's servers are Linux. On top of that, almost all embedded devices run Linux, including Android mobile devices.
Where Did This Indispensable OS Come From?
To give as condensed a history lesson as possible, Unix was created by an assemblage of the finest minds in computer science at Bell Labs in 1970. In their task, they set themselves simple objectives. First, they wanted an OS that could smoothly run on whatever hardware they could find since, ironically, they had a hard time finding any computers to work with at Bell. They also wanted their OS to allow multiple users to log in and run programs concurrently without bumping into each other. Finally, they wanted the OS to be simple to administer and intuitively organized. After acquiring devices from the neighboring department, which had a surplus, the team eventually created Unix.
Unix was adopted initially, and vigorously so, by university computer science departments for research purposes. The University of Illinois at Champaign-Urbana and the University of California Berkeley led the charge, with the latter going so far as to develop its own brand of Unix called the Berkeley Software Distribution, or BSD.
Eventually, AT&T, Bell's successor, lost interest in Unix and jettisoned it in the early 90s. Shortly following this, BSD grew in popularity, and AT&T realized what a grave mistake it had made. After what is probably still the most protracted and aggressive tech industry legal battle of all time, the BSD developers won sole custody of the de facto main line of Unix. BSD has been Unix's elder statesmen ever since, and guards one of the purest living, widely available iterations of Unix.
Organizational Structure
My conception of Unix and its accompanying overall approach to computing is what I call the "Unix Way." It is the intersection of Unix structure and Unix philosophy.
To begin with the structural side of the equation, let's consider the filesystem. The design is a tree, with every file starting at the root and branching from there. It's just that the "tree" is inverted, with the root at the top. Every file has its proper relation to "/" (the forward slash notation called "root"). The whole of the system is contained in the directories found here. Within each directory, you can have a practically unlimited number of files or other directories, each of which can have an unlimited number of files and directories of its own, and so on.
More importantly, every directory under root has a specific purpose. I covered this a while back in a piece on the Filesystem Hierarchy Standard, so I won't rehash it all here. But to give a few illustrative examples, the /boot directory stores everything your system needs to boot up. The /bin, /sbin, and /usr directories retain all your system binaries (the things that run programs). Configuration files that can alter how system-owned programs work live in /etc. All your personal files such as documents and media go in /home (to be more accurate, in your user account's directory in /home). The kind of data that changes all the time, namely logs, gets filed under /var.
In this way, Unix really lives by the old adage "a place for everything, and everything in its place." This is exactly why it's very easy to find whatever you're looking for. Most of the time, you can follow the tree one directory at a time to get to exactly what you need, simply by picking the directory whose name seems like the most appropriate place for your file to be. If that doesn't work, you can run commands like 'find' to dig up exactly what you're looking for. This organizational scheme also keeps clutter to a minimum. Things that are out-of-place stand out, at which point they can be moved or deleted.
Everything Is a File
Another convention which lends utility through elegance is the fact that everything in Unix is a file. Instead of creating another distinct digital structure for things like hardware and processes, Unix thinks of all of these as files. They may not all be files as we commonly understand them, but they are files in the computer science sense of being groups of bits.
This uniformity means that you are free to use a variety of tools for dealing with anything on your system that needs it. Documents and media files are files. Obvious as that sounds, it means they are treated like individual objects that can be referred to by other programs, whether according to their content format, metadata, or raw bit makeup.
Devices are files in Unix, too. No matter what hardware you connect to your system, it gets classified as a block device or a stream device. Users almost never mess with these devices in their file form, but the computer needs a way of classifying these devices so it knows how to interact with them. In most cases, the system invokes some program for converting the device "file" into an immediately usable form.
Block devices represent blocks of data. While block devices aren't treated like "files" in their entirety, the system can read segments of the block device by requesting a block number. Stream devices, on the other hand, are "files" that present streams of information, meaning bits that are being created or sent constantly by some process. A good example is a keyboard: it sends a stream of data as keys are pressed.
Even processes are files. Every program that you run spawns one or more processes that persist as long as the program does. Processes regularly start other processes, but can all be tracked by their unique process ID (PID) and grouped by the user that owns them. By classifying processes as files, locating and manipulating them is straightforward. This is what makes reprioritizing selfish processes or killing unruly ones possible.
To stray a bit into the weeds, you can witness the power of construing everything as a file by running the 'lsof' command. Short for "list open files," 'lsof' enumerates all files currently in use which fit certain criteria. Example criteria include whether or not the files use system network connections, or which process owns them.
Virtues of Openness
The last element I want to point out (though certainly not the last that wins my admiration) is Unix's open computing standard. Most, if not all, of the leading Unix projects are open source, which means they are accessible. This has several key implications.
First, anyone can learn from it. In fact, Linux was born out of a desire to learn and experiment with Unix. Linus Torvalds wanted a copy of Minix to study and modify, but its developers did not want to hand out its source code. In response, Torvalds simply made his own Unix kernel, Linux. He later published the kernel on the Internet for anyone else who also wanted to play with Unix. Suffice it to say that there was some degree of interest in his work.
Second, Unix's openness means anyone can deploy it. If you have a project that requires a computer, Unix can power it; and being highly adaptable due to its architecture, this makes it great for practically any application, from tinkering to running a global business.
Third, anyone can extend it. Again, due to its open-source model, anyone can take a Unix OS and run with it. Users are free to fork their own versions, as happens routinely with Linux distributions. More commonly, users can easily build their own software that runs on any type of Unix system.
This portability is all the more valuable by virtue of Unix and its derivatives running on more hardware than any other OS type. Linux alone can run on essentially all desktop or laptop devices, essentially all embedded devices including mobile devices, all server devices, and even supercomputers.
So, I wouldn't say there's nothing Unix can't do, but you'd be hard-pressed to find it.
A School of Thought, and Class Is in Session
Considering the formidable undertaking that is writing an OS, most OS developers focus their work by defining a philosophy to underpin it. None has become so iconic and influential as the Unix philosophy. Its impact has reached beyond Unix to inspire generations of computer scientists and programmers.
There are multiple formulations of the Unix philosophy, so I will outline what I take as its core tenets.
In Unix, every tool should do one thing, but do that thing well. That sounds intuitive enough, but enough programs weren't (and still aren't) designed that way. What this precept means in practice is that each tool should be built to address only one narrow slice of computing tasks, but that it should also do so in a way that is simple to use and configurable enough to adapt to user preferences regarding that computing slice.
Once a few tools are built along these philosophical lines, users should be able to use them in combination to accomplish a lot (more on that in a sec). The "classic" Unix commands can do practically everything a fundamentally useful computer should be able to do.
With only a few dozen tools, users can:
Manage processes
Manipulate files and their contents irrespective of filetype
Configure hardware and networking devices
Manage installed software
Write and compile code into working binaries
Another central teaching of Unix philosophy is that tools should not assume or impose expectations for how users will use their outputs or outcomes. This concept seems abstract, but is intended to achieve the very pragmatic benefit of ensuring that tools can be chained together. This only amplifies what the potent basic Unix toolset is capable of.
In actual practice, this allows the output of one command to be the input of another. Remember that I said that everything is a file? Program outputs are no exception. So, any command that would normally require a file can alternatively take the "file" that is the previous command's output.
Lastly, to highlight a lesser-known aspect of Unix, it privileges text handling and manipulation. The reason for this is simple enough: text is what humans understand. It is therefore what we want computational results delivered in.
Fundamentally, all computers truly do is transform some text into different text (by way of binary so that it can make sense of the text). Unix tools, then, should let users edit, substitute, format, and reorient text with no fuss whatsoever. At the same time, Unix text tools should never deny the user granular control.
In observing the foregoing dogmas, text manipulation is divided into separate tools. These include the likes of 'awk', 'sed', 'grep', 'sort', 'tr', 'uniq', and a host of others. Here, too, each is formidable on its own, but immensely powerful in concert.
True Power Comes From Within
Regardless of how fascinating you may find them, it is understandable if these architectural and ideological distinctions seem abstruse. But whether or not you use your computer in a way that is congruent with these ideals, the people who designed your computer's OS and applications definitely did. These developers, and the pioneers before them, used the mighty tools of Unix to craft the computing experience you enjoy every day.
Nor are these implements relegated to some digital workbench in Silicon Valley. All of them are there -- sitting on your system anytime you want to access them -- and you may have more occasion to use them than you think. The majority of problems you could want your computer to solve aren't new, so there are usually old tools that already solve them. If you find yourself performing a repetitive task on a computer, there is probably a tool that accomplishes this for you, and it probably owes its existence to Unix.
In my time writing about technology, I have covered some of these tools, and I will likely cover yet more in time. Until then, if you have found the "Unix Way" as compelling as I have, I encourage you to seek out knowledge of it for yourself. The Internet has no shortage of this, I assure you. That's where I got it.
0 notes
Text
Microsoft DOESN'T CARE - WAN Show Aug 16, 2019
Mac or PC, whichever one you personally prefer. You have to admit that there are advantages to the other side. Let me think about it. You simply cannot run, say, Final Cut Pro or Logic Pro on Windows and, at the same time, gaming on Mac OS Sox only there were some way that you could run both of them at near full speed simultaneously on the same PC. Oh, what's that there. I guess there is so behind me and Anthony is a machine that we call the indecision ater. It can be a Mac, it can be a PC and through some software magic it can actually be both of them at the same time as you can see right here so uh. What do you say guys? Should we walk you through how we did it and take it for a spin? I think so after this message from our sponsor Vertigo's PL 4500 RGB LED upgrade kit. Wirelessly connects to your PC and features tons of color customization options, including audio and visual sync, and more check them out at the link in the video description, [ Music ]. If you've seen any of our videos involving hackintosh virtual machines, you'll probably have some idea where we're going with this. If not, here's the twenty second version using Red, Hat's, KVM hypervisor many modern computers can actually have their resources like CPU cores system memory or even graphics cards, divide it up and then allocate it to multiple users or workloads. Using this technology you can even install two operating systems on the same computer that exists completely independently of each other, as we've done in the past. So for today's project, then we've got something really really cool for you guys. So we've taken an AMD reisen. 930. 900. X12 core processor and then what we've done is: we've split those 12 cores straight down the middle between two virtual machines that will run Windows on one side and Mac OS on the other for graphics, we've gone with an RT X, 20 atti for our windows box And a Radeon 7 for our Mac, then we've passed those graphics cards through to their respective VMs, this method of assigning our GPUs results in relatively little lost performance. So the main challenge we ran into for this project. While there were many firsts and videos, legendary code, 43 error, Nvidia, obviously doesn't like consumers running their GeForce GPUs in a VM just go out and buy a Quadro. Combating some weird stuttering in Windows was the next issue that we had to fix and we fixed that by switching to message. Signaled interrupts instead of traditional electrical line based interrupts like you'd, normally get in a processor these days or ever really and finally, getting the mac OS catalina beta to use the drivers that Apple included for virtualized storage. That last one in particular, is prop really exciting, because Apple has never supported it in the past, make sure you're subscribed, because I'm already working on convincing Linus here to let me work on a video on Mac virtualization. Once we get the Mac Pro in yeah. We'Re definitely gonna be doing that. Anywho, where things take a bit of a turn today, is how we're going to interact with our Frankenstein machine. So in the past, if you wanted to use multiple computers, you'd either have to use a hardware switcher and conveniently also call KVM multiple monitors or in the case of the LGU d 79 that we used once before. You would have to be content with 1080p quadrants of a single 16 by 9 4k display. Today. We have something quite special. This display from Phillips is the 499 p, 9 H and it's a 1440p super ultra wide display, with a double wide 32 by 9 aspect ratio, which means that what we're effectively looking at here is a bezel free single display setup where we've got the equivalent of 2 27 inch monitors side by side with no bezel in between them, so we can completely seamlessly interact with both of our VMs. How do you do that? You might be asking well well so did you do that? Yeah? This energy is still kind of trying to work out the kinks of their 2.0 release. So I decided to use a different piece of software, just kind of switched things I'll call share mouse, which has some, unfortunately, agro marketing, but hey if it works, it works and for the most part, although there are some glitches like you can see my Mac OS Cursor is actually still kind of ghosted over here there you go and you can see kind of the header of my windows cursor. For the most part it actually does work. We can move the cursor seamlessly from one of our displays over to the other, as if the imaginary line down the middle didn't exist, in fact, actually we could probably do some really cool stuff. Like pretend that the whole thing is one machine, so I actually don't know how to switch the wallpaper on a Mac, but I'm gonna go ahead and do this one nice, it's an abomination, isn't it beautiful? Oh, I like this too LTTE store.com by a water bottle. Ok, then, so we're good. Essentially, what we've got here is to rise in 5:30 600 systems, but on one machine, we're running Mac OS and, on the other, one we're running Windows with seamless Mouse movement between them, which means, if I wanted to. I could browse the Internet over here in Safari and then potentially use an Apple Magic Trackpad for gesture control. While I fire up, let's say game, like shadow of the Tomb Raider over on the other side. Wait am I just running in a circle right now? Yes, so I'm like okay, I'm bored of playing video games or whatever and I go over - and I browse the forum. Then I'm just like oh yeah, you know what I'm gonna go back to playing video games, freakin nuts yeah and you can set up a keyboard shortcut to switch automatically, so you don't need to Creole tap. We just haven't set that up yet so, let's say game play, isn't your number one priority, maybe you're a content creator like a youtuber or a twitch streamer and that's kind of more of your jam. So what you could do, then, is capture some gameplay with shadow play or OBS and then port that directly over to the Mac by dragging and dropping and there you can use that if you're more comfortable with it check this out. So I just grabbed the clip that I recorded right now, while you're talking dragged it over the middle line and loop there. It is, let's see what the back looks like boom nice just like that now doesn't copy that quickly: we're limited to about 20 megabytes. A second, so there's probably some work. The developer could do on that, but hey the footage is there now. One thing I did want to mention is that we didn't manage to login to the App Store. We think it might be something to do with our copy of Final Cut Pro being on my consumer register at Apple account and this being a developer only OS, because it's still the preview but hey. The point is, if you're comfortable, editing in Final Cut Pro, you can create your content on Windows and then you can edit it together on the Mac, and then you could log into YouTube on Windows, and you can upload it from Windows. If you wanted to pretty cool best of all, if you want, you can select just one of the VMS for full productivity, with the press of a button and another button and another button and another button, this they told us it was gonna, be just like One button to switch yeah yeah. They said that they could actually set it up to just switch by a single button. But as far as I can tell no, but it does have a KVM and that is the keyboard, video mouse rendition of KBM, so ready hat. So, what's cool about that at the very least, is that if you want to use just one set of peripherals for both of your OSS, you can by plugging in through the monitor right? Let me just switch inputs here. Obviously, I could change it to full resolution, but yeah as we can see it's being a little bit dumb and also our Mac needs to be unplugged and replugged. Sometimes, in order to pick up this yeah, that's just Apple things. I think. Okay, it's a little janky, but what's cool about our setup here is that it doesn't even have to be Windows and Mac OS. It'S just that, thanks to the Mac OS catallena beta Mac OS now supports not just virtualized storage like Anthony mentioned before that allowed us to take our single PCIe gen 4. So like this high performance, 2 terabyte SSD and split it up, but it even supports other verdi, o devices. Now so we can get access to near native speeds over the network as well. Like imagine what it would be like to take a machine like this and be able to split something like the upcoming 16 core Raisa 939 50 X, I mean, even without all the PCI Express Lanes and memory bandwidth that you could get from something like a thread. Ripper you'd be compromising very little janky NASA side with a dual setup like this, so I mean. Maybe we should come back to this concept when that launches, make sure you guys are subscribed and stay tuned, because if nothing else we'll definitely be checking out virtualization on the upcoming Mac Pro yeah and by that time I think that there's a lot more, that I Could do to smooth out the experience overall like having a virtualized 9p shared drive between the two OSS that lets it basically become a network drive that native speeds, but that's all we have time for today. So if you haven't seen it already check out our previous Mac, virtualization videos, we'll have them linked below pulse way, is a real-time, remote monitoring and management software that helps you fix problems on the go you can send commands from routerhosting any mobile device and the software is Compatible with Windows, Mac and Linux pulse way, single app gives you remote desktop functionality, so you can get access to real-time status system resources. You can see logged in users, you can monitor network performance, you can manage Continue windows updates and more, in fact, the sky's the limit, because you can create and deploy your own custom scripts to automate your IT tasks so try it for free at pulse wacom or through Our link in the video description hi thanks for watching
youtube
0 notes
Text
Devry Comp 129 all weeks discussions, Quizzes, course project and final exam
Follow Below Link to Download File
https://homeworklance.com/downloads/devry-comp-129-all-weeks-discussions-quizzes-course-project-and-final-exam/
We also Do 100% Original and Plagiarism Free Assignment / Homework and Essay
Email us for original and Plagiarism Free Work At ( [email protected] ) or order us at (https://homeworklance.com/custom-order/ )
Devry Comp 129 Week 1 Discussion
Discussion 1
In this discussion, we will look at the basics of both hardware and operating systems. To begin this discussion, let’s first define the difference between hardware and software. What is hardware? What is software? What are the purposes of hardware and software?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Discussion 2
In this discussion, we will look at power supplies and form factors. What is the purpose of a power supply? What is a form factor? How do power supplies and form factors relate to one another?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry Comp 129 Week 2 Discussion
Discussion 1
Take some time this week to open up your computer (or better yet, an old junky one), and take a look inside (be sure to unplug your machine and not to touch any of the components—look but don’t touch). Based on your readings, what kind of motherboard is being used? What form factor? How did you know?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Discussion 2
What is a CPU? What is the purpose of the CPU?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry Comp129 Week 3 Discussion
Discussion 1
Describe the Windows operating system. Discuss some of your favorite Windows features.
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts
Discussion 2
Have you ever had a problem with your Windows operating system? What happened, and what was the result?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry Comp129 Week 4 Discussion
Discussion 1
Identify and discuss some peripherals that ordinary desktop PC users would normally use. Discuss how they work and their purposes.
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Discussion 2
Discuss backup strategies and devices that you can use with your PC at home or in the workplace. How does the device connect? What standards does it use?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry COMP129 Week 5 Discussion
Discussion 1
What are the basic components required to set up a network? How do you add a PC to a network?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Discussion 2
What is one of your favorite applications that utilizes the Internet? Discuss what happens behind the scenes in the network that enables your PC to implement that application.
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry COMP 129 Week 6 Discussion
Discussion 1
What are some of the basic precautions a computer owner or network administrator can take to help make the computing environment secure? What are some of the basic security threats that a user or administrator might have to face?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Discussion 2
What is Linux? When would you use it? How does it differ from Windows? Are there different versions of Linux?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry COMP 129 Week 7 Discussion
Discussion 1
What is troubleshooting? How can you find the cause(s) of the problem quickly when you have limited experience? Why is it important to keep a computer healthy?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
discussion 2
We have studied the CLI for both Windows and Linux. The real power in using commands comes with scripting. What are some repetitive tasks you can think of that could be done more easily with a well-written script?
Avoid using the Respond button at the top of the discussion. Help keep the discussion organized by responding only to other posts.
Devry COMP 129 All Weeks quizzes
week 1
1. Question : (TCO 2) Why is having the correct device driver so important?
Question 2. Question : (TCO 2) What is the maximum transfer rate for a USB 2.0 port?
Question 3. Question : (TCO 2) What is the primary purpose of the power supply?
Question 4. Question : (TCO 2) What atmospheric condition
can increase the potential for static electricity?
Question 5. Question : (TCO 2) A _____ is required
before software from the BIOS is executed.
Question 6. Question : (TCO 2) Which unit would you recommend for the help desk people who sit at a computer for a 24/7 operation where help must be provided at all times?
Question 7. Question : (TCO 1) Refer to the provided figure. What type of cable would have this symbol?
Question 8. Question : (TCO 1) Jane decides to restart her computer by pressing the Ctrl+Alt+Delete combination keys. This procedure
is called a _____.
Question 9. Question : (TCO 1) Why is it best not to start cleaning a computer by using compressed
air?
Question 10. Question : (TCO 11) After a problem is solved, a technician must _____ findings, actions, and outcomes.
Devry Comp129 Week 2 Quiz
1. Question : (TCO 3) Major microprocessor manufacturers are _____.
Question 2. Question : (TCO 3) What does quad core mean in relation of processors?
Question 3. Question : (TCO 3) An engineering professor teaches CAS at the university. Which expansion slot would be best for the graphics card in the professor’s computer?
Question 4. Question : (TCO 3) Most motherboards use _____ for RAM.
Question 5. Question : (TCO 3) Double-sided memory _____.
Question 6. Question : (TCO 3) Dual channeling _____.
Question 7. Question : (TCO 3) Where are mini PCIe cards normally installed?
Question 8. Question : (TCO 2) Which of the following will most likely contain SO-DIMM memory?
Question 9. Question : (TCO 2) A physical problem with a memory chip will often cause a(n) _____ error.
Question 10. Question : (TCO 11) Bill and John are overloaded. They have to install more than 50 access points. Joni hears their frustration and offers to help. This is an example of _____.
Devry Comp129 Week 3 Quiz
1. Question : (TCO 4) Linux has a variety of _____ that provide the basic functionality that you are used to when working with an operating system, such as the cp command for copying files, the mvcommand for moving files, the vi editor for editing a text file, and so on.
Student Answer: DOS commands
utilities
batch files
GUI tools
Instructor Explanation: TestOut Linux+ Section 0.1.3
Points Received: 4 of 4
Comments:
Question 2. Question : (TCO 4) What is a home screen on a mobile device?
Student Answer: Where you have to be to see what applications are currently running
Where the physical volume control is normally located
Where photo files are stored
Where app icons are found
Instructor Explanation: Schmidt, Chapter 11
Points Received: 4 of 4
Comments:
Question 3. Question : (TCO 4) Consider the following directory structure from the C: drive root directory.
2014_Term (directory)
CompRepair (subdirectory)
Opsys (subdirectory)
Cisco8 (subdirectory)
VOIP (subdirectory)
If the prompt is C:2014_Term> and you wanted to move into theCisco8
subdirectory, what
command do you type?
Student Answer: CD Cisco8
CD..
CD Cisco8
CD C:Cisco8
Instructor Explanation: Schmidt, Chapter 11
Points Received: 0 of 4
Comments:
Question 4. Question : (TCO 4) List three items commonly found in a dialog box.
Student Answer: Properties, Close button, Font button
OK button,
Cancel button, Make new file button
Help button, Close button, OK button
Help button, Close button, Restart button
Instructor Explanation: Schmidt, Chapter 11
Points Received: 4 of 4
Comments:
Question 5. Question : (TCO 4) Which tool can you use to view, but not modify, hardware and configuration information for your computer?
Student Answer: The System applet in Control Panel
Msinfo32
Msconfig.exe
Event Viewer
Instructor Explanation: TestOut PC Pro Section 9
Points Received: 4 of 4
Comments:
Question 6. Question : (TCO 4) Who is given credit for the GNU initiative?
Student Answer: Richard Stallman
Bill Gates
Linus Torvald
All of the above
Instructor Explanation: TestOut Linux+ Section 0.1.3
Points Received: 4 of 4
Comments:
Question 7. Question : (TCO 4) Which user type was available
in Windows XP but is not available
for Windows Vista and 7?
Student Answer: Guest
Administrator
Standard User
Power User
Instructor Explanation: Schmidt, Chapter 12
Points Received: 4 of 4
Comments:
Question 8. Question : (TCO 4) What Windows 7 feature speeds up file searches?
Student Answer: Shadow Copy
Indexing
Sharing
ReadyBoost
Instructor Explanation: Schmidt, Chapter 12
Points Received: 4 of 4
Comments:
Question 9. Question : (TCO 4) What is the default location for 64-bit application files in Windows 7?
Student Answer: The Windows folder
The Program Files folder
The SysWOW64 folder
The System64 folder
Instructor Explanation: Schmidt, Chapter 12
Points Received: 4 of 4
Comments:
Question 10. Question : (TCO 11) Learning the next-generation features of the most recent . october#”>smartphones is an example of _____.
Student Answer: OS maintenance
staying current with technology
leveraging documentation
working out a solution
Instructor Explanation: Schmidt, Chapter 11
Points Received: 4 of 4
Comments:
* Times are displayed in (GMT-07:00) Mountain Time (US & Canada)
week 4
Devry CoMP129 Week 4 Quiz Latest 2015 October
1. Question : (TCO 5) A laptop normally has an _____ type of hard drive installed.
Student Answer: internal SCSI
external SCSI
external SATA
internal SATA
Instructor Explanation: Schmidt, Chapter 7
Points Received: 4 of 4
Comments:
Question 2. Question : (TCO 6) Why is backing up data to a different partition on the same hard drive not a good idea?
Student Answer: The data perform at a slower rate.
Other users who have rights to save files can retrieve the backup, install to a different computer or drive, and potentially see others’ data.
If the drive fails, both the data and the backup are potentially unusable.
The backup takes longer.
Instructor Explanation: Schmidt, Chapter 7
Points Received: 4 of 4
Comments:
Question 3. Question : (TCO 6) Which backup type would back up all the user’s data and set the archive bit for each file?
Student Answer: Comprehensive
Full
Differential
Incremental
Instructor Explanation: Schmidt, Chapter 7
Points Received: 4 of 4
Comments:
Question 4. Question : (TCO 5) Which optical medium has the greatest storage capacity?
Student Answer: Compact disc
Dual-layer, single-sided DVD
Single-layer, single-sided Blu-ray disc
Dual-layer, double-sided DVD
Instructor Explanation: TestOut PC Pro A+, Section 5.6
Points Received: 4 of 4
Comments:
Question 5. Question : (TCO 5) For internal optical drives, what is the most common type of internal interface found today?
Student Answer: SCSI
IDE
USB
Firewire
Instructor Explanation: Schmidt, Chapter 8
Points Received: 4 of 4
Comments:
Question 6. Question : (TCO 6) What term is used to describe the number of samples a sound card takes to create the reproduction of the original sound?
Student Answer: Analog-to-digital conversion rate
Power rating
Frequency response
Signal to noise ratio
Instructor Explanation: Schmidt, Chapter 8
Points Received: 4 of 4
Comments:
Question 7. Question : (TCO 5) What Android app could be used to see saved photos?
Student Answer: Settings
Gallery
Photos
Video
Instructor Explanation: Schmidt, Chapter 8
Points Received: 4 of 4
Comments:
Question 8. Question : (TCO 5) What happens when you press the Fn key along
with a function key on a laptop computer?
Student Answer: You allow the computer
to be placed in one of four power modes, which helps with video troubleshooting.
You allow the computer
to be placed in diagnostic
mode, which is especially useful when troubleshooting video problems.
You get additional features depending
on the key you press.
You refresh the monitor.
Instructor Explanation: Schmidt, Chapter 9
Points Received: 4 of 4
Comments:
Question 9. Question : (TCO 6) A user wants to expand his normal Windows 7 desktop work area across two monitors.
What would be the best solution for this user?
Student Answer: Use an integrated VGA port and a DVI port on an adapter.
Install a video card with two ports if two ports are not available on the motherboard.
Use a KVM switch.
Use a video splitter.
Instructor Explanation: Schmidt, Chapter 9
Points Received: 4 of 4
Comments:
Question 10. Question : (TCO 11) What should you do when speaking on the phone with a customer who is very upset and yelling at you?
Student Answer: Stay calm but raise your voice level a little to show the importance and professionalism of your technical question.
Ask the caller whether you can put him or her on hold while he or she calms down.
Hang up on the caller.
Speak to the customer using a calm, professional tone.
Instructor Explanation: Schmidt, Chapter 7
Points Received: 4 of 4
Comments:
Devry Comp129 Week 6 Quiz
1. Question : (TCO 8) The protocols used to encrypt account names and passwords are called authentication protocols. The protocol used for Windows is _____.
Student Answer: Kerberos
Crypto IP Encapsulation (CIPE)
Internet Protocol Security (IPsec)
Secure Sockets Layer (SSL)
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 2. Question : (TCO 9) A(n) _____ is about the size of a credit card, but thicker.
Student Answer: ExpressCard
CardBus card
PCI card
PC Card
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 3. Question : (TCO 8) A worm _____.
Student Answer: is a program that can replicate by attaching itself to another program
can spread copies of itself throughout a network without a host program
does not need a host program to work; It pretends to be a legitimate program
is dormant code added to software and triggered by a predetermined event
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 4. Question : (TCO 8) _____ prove(s) that individuals are who they say they are.
Student Answer: Authentication
Authorization
A background process
BIOS settings
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 5. Question : (TCO 8) The largest security risk for stealing confidential data comes from ____.
Student Answer: Russian or Chinese hackers
college students studying hacking
employees leaving passwords in full view
disgruntled employees
Instructor Explanation: Week 6 Online Lecture
Points Received: 0 of 4
Comments:
Question 6. Question : (TCO 8) Which security method would be best to use if extremely sensitive government information were stored on a hard drive that will no longer be used?
Student Answer: Buy 1/0 rewrite software.
Drill holes in the platters and smash the pieces with a hammer.
Hold a magnet over each platter.
Repartition the hard drive into multiple partitions using different file systems.
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 7. Question : (TCO 8) The protocols used to encrypt account names and passwords are called _____ protocols.
Student Answer: user service
encryption
authentication
authorization
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 8. Question : (TCO 4) Which Linux command shows you what the current directory is?
Student Answer: more
pwd
dir
ls
Instructor Explanation: TestOut Linux+, Section 1.1
Points Received: 4 of 4
Comments:
Question 9. Question : (TCO 9) What is SSID broadcasting?
Student Answer: The method the access point uses to reach all wireless NICs with a single message
A means for the access point to send the wireless encryption keys to all wireless NICs for network access
The access point constantly sending the name of the wireless network into the air
The access method used for 802.11 a, b, g, and n wireless networks
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 10. Question : (TCO 11) Trust between you and your customer begins with _____.
Student Answer: never lying.
good communications skills
a new customer discount
professionalism.
Instructor Explanation: Schmidt, Chapter 15
Points Received: 0 of 4
Devry Comp129 Week 6 Quiz
1. Question : (TCO 8) The protocols used to encrypt account names and passwords are called authentication protocols. The protocol used for Windows is _____.
Student Answer: Kerberos
Crypto IP Encapsulation (CIPE)
Internet Protocol Security (IPsec)
Secure Sockets Layer (SSL)
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 2. Question : (TCO 9) A(n) _____ is about the size of a credit card, but thicker.
Student Answer: ExpressCard
CardBus card
PCI card
PC Card
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 3. Question : (TCO 8) A worm _____.
Student Answer: is a program that can replicate by attaching itself to another program
can spread copies of itself throughout a network without a host program
does not need a host program to work; It pretends to be a legitimate program
is dormant code added to software and triggered by a predetermined event
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 4. Question : (TCO 8) _____ prove(s) that individuals are who they say they are.
Student Answer: Authentication
Authorization
A background process
BIOS settings
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 5. Question : (TCO 8) The largest security risk for stealing confidential data comes from ____.
Student Answer: Russian or Chinese hackers
college students studying hacking
employees leaving passwords in full view
disgruntled employees
Instructor Explanation: Week 6 Online Lecture
Points Received: 0 of 4
Comments:
Question 6. Question : (TCO 8) Which security method would be best to use if extremely sensitive government information were stored on a hard drive that will no longer be used?
Student Answer: Buy 1/0 rewrite software.
Drill holes in the platters and smash the pieces with a hammer.
Hold a magnet over each platter.
Repartition the hard drive into multiple partitions using different file systems.
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 7. Question : (TCO 8) The protocols used to encrypt account names and passwords are called _____ protocols.
Student Answer: user service
encryption
authentication
authorization
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 8. Question : (TCO 4) Which Linux command shows you what the current directory is?
Student Answer: more
pwd
dir
ls
Instructor Explanation: TestOut Linux+, Section 1.1
Points Received: 4 of 4
Comments:
Question 9. Question : (TCO 9) What is SSID broadcasting?
Student Answer: The method the access point uses to reach all wireless NICs with a single message
A means for the access point to send the wireless encryption keys to all wireless NICs for network access
The access point constantly sending the name of the wireless network into the air
The access method used for 802.11 a, b, g, and n wireless networks
Instructor Explanation: Schmidt, Chapter 15
Points Received: 4 of 4
Comments:
Question 10. Question : (TCO 11) Trust between you and your customer begins with _____.
Student Answer: never lying.
good communications skills
a new customer discount
professionalism.
Instructor Explanation: Schmidt, Chapter 15
Points Received: 0 of 4
Comments:
week 7
(TCO 4) You have been asked to temporarily fill in for a Linux administrator who has just been fired. This administrator was known to take a lax view of security and it is suspected that passwords are still kept in the /etc/passwd file. When viewing that file, which entry below would indicate that the passwords are there?
kolson:85yxir:430:0:Back Door:/root:/bin/bash
badams:x:341:52:Brent Adams:/users/badams:/bin/bash
dclifford:x:689:306:non secure user:/root:
tmurphy:x:100:100:/users/tmurphy:/bin/bash
Question 2. Question :
(TCO 11) Mitch Miller wants to use his optical drive to play a Moody Blues CD. When he inserts the disc and closes the drive tray, the drive turns, but he does not hear any music. What type of problem would a technician say this is?
The technician would say that it is a hardware problem.
The technician would say that it is a software problem.
The technician would say that it is an error of the user.
The technician would not be able to draw a conclusion from the description given.
Question 3. Question :
(TCO 10) In which troubleshooting step do you complete a help-desk ticket by typing the solution and closing the ticket?
Document findings, actions, and outcomes.
Identify the problem.
Verify full system functionality and, if applicable, implement preventive measures.
Establish a plan of action to resolve the problem and implement the solution.
Question 4. Question :
(TCO 10) The audio beeps heard during the boot process are caused by the _____.
RAM
processor
CMOS
BIOS
Question 5. Question :
(TCO 10) Hardware errors are often obvious _____.
during POST
during printing
when saving a file
during RAM access
Question 6. Question :
(TCO 10) What component is most likely to be included in an audio and video editing PC design?
RAID
Powerful GPU
Multiple processors
Video capture card
Question 7. Question :
(TCO 10) Which of the following would most likely be a design consideration for a gaming PC rather than a computer used for virtualization?
NAS
High amount of RAM
Multiple fast, large-capacity hard drives
Additional system cooling
Question 8. Question :
(TCO 10) Debbie keeps getting an error each time she tries to save her worksheet in AJAX ABC accounting software to the thumb drive. She then saves an Excel spreadsheet she was working on to the thumb drive and it too produces the error. A good next step would be to _____.
save the file to a different drive.
open the computer case to see whether the thumb drive is connected properly.
replace the hard drive.
Question 9. Question :
(TCO 10) Which statement is true regarding mobile design?
. Netbooks are low cost and lightweight.
Netbooks are typically lighter than tablets.
Laptops usually have less storage capability than tablets or smartphones.
Question 10. Question :
(TCO 10) An internal keyboard is generally connected to the laptop’s system board using a _____.
USB connector
ribbon cable
PS/2 port
mini-molex connector
Course Project: Due in Week 7 (Begin in Week 1)
Objectives
.equella.ecollege.com/file/fe25679a-cc25-4079-a28b-289fa1484619/19/COMP129_CH_CourseProject.html#top”>Back to Top
BUILDING A PERFECT PC!
The COMP129 project is designed to help you apply what you are learning each week using current hardware and software options to build a PC that meets a specific purpose. Although your Final Project is due in Week 7, you will begin working in Week 1 and continue adding components to your computer in each week of the class. Start by selecting the purpose of your computer and a budget. Then you can work each week to select components for your PC based on what you are learning in your class activities. Download the project deliverable template and create a spreadsheet in Week 1. (Remember, you will be turning in these two files in Week 7.) Build on these during the term as you work on building your perfect PC.
Guidelines
Plan to build your perfect PC. (Remember, you are to select each part of the computer. No kits are allowed. No prebuilt computing devices are allowed. This project is designed to help you apply what you are learning each week using current hardware and software options.) Use the lab project template to turn in your project questions. Attach an Excel spreadsheet that includes the major components, specifications, parts, vendors, pricing, and total cost as outlined below. (You can add additional rows and columns to the Excel template if you want to add more than the minimum in your completed computer build).
Plan the purpose of your computer. (Remember, Chapter 10 in your textbook will give you some ideas on what you might select as a purpose.)
Preplan a price range and try to stick to it. (Were you able to stick to your budget? Why or why not?)
List all major components in your spreadsheet template. (Include at least the motherboard, processor power, memory, drives, and monitor size. Add to this list as needed).
Determine all necessary parts to buy. (Include at least the case, expansion cards, NIC, and keyboard. Add to this list as needed.)
Include OS and software.
Update an Excel spreadsheet with all specifications and parts.
Price parts from two locations. You may use brick-and-mortar stores in your area, such as TigerDirect, and online sellers, such as.newegg.com/”>newegg.comor.tigerdirect.com/”>http://www.tigerdirect.com/. You can do all of your .comparison shopping online, if you desire. (You will be adding in the prices from these two locations as separate columns in your spreadsheet. See Item 8 below.)
Update your spreadsheet with the seller’s name, prices, and totals. (Make sure you add the vendor, price, and total for all the items you select, as well as the total for the computer as a whole.)
Write a 4–5-paragraph report on your learning and experiences in completing this project. Make sure to include an introduction, two to three paragraphs about the project, and a conclusion for full credit on this part of the assignment. Remember, this portion of the project is worth 10 points, so make sure you are thorough and complete in your essay.
0 notes