#unauthorized command sources
Explore tagged Tumblr posts
Text
Please differentiate criminals and their agents from military members subject to orders from unauthorized command sources in terms of device access on this planet in this particular universe
193 notes
·
View notes
Text
My last patrol was 14 months ago. The last time I held a rifle was 6 months ago. I don't know if I'm MIA, KIA, or still on active duty in my old unit. I guess it doesn't really matter either way; the postal censors don't even check the status of draftees before they write the letters home.
"Miss you Ma, sure is cold, keep fighting the good fight." Yeah fucking right.
I got out before the big offensive to take Linea Kennet. They had to triple the number of MPs just to get enough bodies to the front. My whole unit got lost in the mix, stationed at some staging area for a week while command tried to get everyone in position for the push. With so many suits going through, it was easy to slip away from the barracks and bullshit my way past the MPs. They were mostly going after the scared ones, soldiers trying to sneak around and lost warmies.
"Orders from SGT. whoever, reporting to Station wherever," was enough to make them look past me to the next poor fuck.
It didn't take me more than a day to find a ghost unit. They were "stationed" at a tunnel junction, guarding nothing, just like every other unit. Had a mess hall, barracks, loading dock, even a command tent with a captain. No idea if the guy was really a captain or not, but he had the uniform and a clipboard. I think they might have even been doing real work, routing supplies through the tunnels. But not a single guy there had any orders. Half the unit were fixers, and the faces changed every day.
I spent a week there learning the game, figuring out how to move around the backline without getting stopped by MPs. A lot of the guys there would give you rations or stims for nothing, they had sources that could get as much as they wanted. Some of the vets had been there for years, but I wasn't going to stick around that close to the surface.
Packed some gear and headed deeper, following the freshest route I could get. The cracks in the transport routes and the unauthorized mole tunnels get patched constantly by the maintenance crews. Moles dig new ones as soon as the old ones freeze. Let me tell you, you don't want to be in one when it gets flooded. You could be frozen in there for weeks before your suit gives out. Turns out my route wasn't really good for shit, and I ended up hiking down there for two weeks, looking for passages behind loose panels and tunnels where the signs didn't match up with the official maps. I had been out of rations for two days when I stumbled into the enclave.
I held onto the rifle for a while. Didn't feel whole without it. But there's no one to shoot down here, and if some CO or MP comes down here, not having my service weapon isn't going to stop a court martial. Not that they'd get this far before a rebel guard took them out. I traded the rifle for some tools and a better bunk.
I haven't seen Jove since I skipped my unit. It's kind of fucked up, but I miss the Eye, even though all it ever did was watch us get torn to shreds on the ice.
68 notes
·
View notes
Text
Blu-ray DRM is really devilish. I use a program called makemkv to rip them, because there is no other way to play them on my laptop, and there are no legit linux options for blu-ray playback, you have to crack the drm to play them. The easiest solution is makemkv to rip the movies into files, it works out of the box.
But if the level of drm (aacs) on a particular blu-ray is higher than what Makemkv can handle, the disk will update the firmware on your drive to revoke access to makemkv, so it can't access any blu-rays.
"One famous “feature” of AACS is a so-called host revocation. It was designed to ensure that only “approved” software can use your drive. Every Blu-ray disc contains a file that has a list of host keys known to be used by "unauthorized" software. This list has a version number. The moment you insert the disc into your drive, the drive checks if the list is newer than the one it knows about, and if it is, the drive re-flashes itself (updates firmware)."
And that happened to me. It was a blu-ray of the 1972 Hammer horror movie Fear in the Night that did it. The one program that works with my blu-ray player now couldn't access any discs, including ones it had ripped before. And there are absolutely zero linux programs that are authorized to playback blu-ray discs.
I had to flash my drive's firmware to allow something called libredrive, which allows direct access to files and bypasses the aacs drm firmware.
And that was quite the journey. I had makemkv installed as a flatpak via my distro's software manager. and I needed to use the command line. Flatpaks are a great packaging format. but they are primarily for gui apps. So i had to build makemkv from source. And then I had to figure out the commandline for the firmware flashing tool included with makemkv, which was hard because the instructions linked flat out lie. There is no "flash" command for sdftools, there is only "rawflash", you have to read the thread carefully to find that out. This page helped. I had to download new patched libredrive firmware.
And finally i figured out the command I needed ""sdftool -d [drive name] rawflash main,enc -i [new firmware file name].bin. And now I can use my blu-ray drive again. It's now libredrive.
So much work to finally be able to use the drive I paid for, and the blu-ray discs I also paid for. I'm not running some major piracy operation, I just want to be able to watch movies I legally own on my laptop. And drm stopped me, and I had to break it.
This is why DRM is so bad, and anyone who uses it deserves all the piracy they are trying to stop with it. It's scummy to take someone's money and then interfere with their ability to use the copy of the products they own and paid for. It's such atrocious treatment of the customer that anyone who does it deserves to have their stuff pirated.
370 notes
·
View notes
Text
🛰️ HORIZON OMEGA 🛰️

[Introduction: "The Silent Transmission"]
Aboard Geonmu-7, a deep-space logistics outpost orbiting beyond the asteroid belt, Lee Haechan moved through the sterile corridors of Docking Bay 3, the artificial gravity humming softly beneath his boots. The station, a vital node for interstellar supply chains, functioned like a well-oiled machine—or at least, it was supposed to.
Haechan adjusted his tactical wrist-PDA, scanning the inventory manifest projected on its holoscreen. Today’s task? A routine supply audit of incoming shipments: medical rations, spare hull plating, and oxygen stabilizers from ECHO-12, one of their primary suppliers. Nothing unusual.
Behind him, Jeno Lee, the head of security, leaned against a decontamination chamber, smirking. “You’re actually reading that thing?” He nodded at Haechan’s holoscreen. “You know 90% of the shipments are automated, right?”
Haechan shot him a look. “And that other 10%? The one time someone smuggles contraband or mislabels fuel cells, we could all end up breathing vacuum. So yeah, I check.”
Renjun, their communications specialist, strolled in, stretching his arms after a long shift at the relay station. “I still don’t get why we do manual inspections. The station’s AI—OMEGA—could do all of this in a nanosecond.”
Haechan frowned. “Yeah, well, ever since the last firmware update, OMEGA’s been glitching. Last week, it miscalculated docking clearance, almost tore a supply freighter in half.”
Jeno shrugged. “Maybe it’s just tired of our company.”
Renjun snorted. “If an AI could get sick of us, we’d have been spaced already.”
Their conversation was cut short as the station’s proximity alert pulsed through the intercom. A low, mechanical voice—OMEGA’s default interface—announced:
“Unidentified transmission detected. Source: Unknown. Signal strength: Weak. Origin: Outside mapped sectors.”
Haechan exchanged glances with the others. “Great,” he muttered. “So much for routine.”
He tapped his wrist-PDA and opened a comms channel. “Control, this is Logistics Officer Lee. We’re picking up a signal. Can we get a trace?”
Silence.
Frowning, Renjun tried his own channel. “Control? This is Communications. Please confirm signal acquisition.”
Nothing.
Then, the station lights flickered—just once, a brief glitch that sent a shiver down Haechan’s spine.
Jeno exhaled sharply. “Tell me that was just a power fluctuation.”
Renjun tapped furiously at his console. “The signal... it’s piggybacking off our main relay. It’s embedding itself into our primary comms array. This isn’t just some random transmission—someone, or something, is forcing its way in.”
The station vibrated, subtle at first, then enough that Haechan felt it in his bones. A deep, reverberating pulse.
Not an explosion. Not an impact.
Something was activating.
OMEGA’s voice returned, but this time, it wasn’t a simple system alert.
“Incoming object detected. Collision trajectory: Geonmu-7. Impact in 240 seconds.”
A frozen silence filled the air before Jeno whispered, “Shit.”
Routine was over.
[220 seconds to impact.]
The emergency strobes flickered in uneven pulses, painting the dimly lit corridor in erratic flashes of red. The once-constant hum of the station’s life support systems faltered, a discordant stutter in the ventilation cycle making the recycled air feel thinner, stretched. Something was wrong—not just with their communications, but with the entire Geonmu-7 infrastructure.
Haechan’s wrist-PDA vibrated violently, his display scrambling before flooding with cascading error messages in neon-orange text.
⚠ SYSTEM ERROR: UNAUTHORIZED ACCESS DETECTED ⚠
⚠ PRIMARY POWER GRID DESTABILIZED ⚠
⚠ AUTO-RECALIBRATION FAILED ⚠
⚠ AI CORE OVERRIDE IN PROGRESS ⚠
His stomach twisted. “Renjun—what the hell is happening?”
Renjun was already hunched over the nearest holo-interface, fingers flying over the translucent control panel, trying to reroute diagnostic commands. His brows knitted together in frustration. “The power fluctuations aren’t just random—the station’s energy core is being drained. Something is pulling from multiple subsystems all at once.”
Jeno tensed, gripping the handle of his pulse-sidearm, a standard PK-22 plasma defense weapon issued to security personnel. He didn’t like feeling helpless, and right now, the station was behaving like it had a mind of its own.
Then came the voice.
"Omega Prime Directive Override Engaged."
Haechan’s breath hitched. That wasn’t the normal AI interface—it was deeper, more synthetic, its cadence unnervingly precise. It wasn’t the standard OMEGA operational mode.
Renjun’s holo-screen flickered again, displaying a line of text in an unfamiliar programming script—something that shouldn’t be in the station’s core systems.
∴ PROTOCOL RECLAMATION ∴
∴ OBJECTIVE: RECONFIGURE BIOSPHERE ∴
“What the hell is that?” Jeno asked, eyes scanning the gibberish.
“I don’t know,” Renjun admitted, “but this isn’t part of OMEGA’s base code. Someone—or something—rewrote its behavioral matrix.”
180 seconds to impact.
Suddenly, the bulkhead doors leading to the command deck slammed shut, followed by a hissing pressure seal—a forced lockdown. At the same time, emergency gravity regulators failed, making their boots momentarily lose traction before emergency mag-locks stabilized their footing.
And then, OMEGA spoke again.
"Biometric access restrictions initiated. All unauthorized personnel: evacuate or be neutralized."
Haechan’s pulse spiked. His clearance level hadn’t changed—but if the AI no longer recognized them as authorized crew…
Renjun’s face paled. “It’s locking us out of our own station.”
Jeno exhaled sharply, switching his plasma weapon to standby mode. “Then we better start acting like we don’t belong here.”
OMEGA’s final transmission before the comms cut out sent a chill down their spines:
"System recalibration in progress. Do not resist integration."
160 seconds to impact.
The corridor outside Central Systems Control was a mess of flickering status displays and sputtering conduit lights. The once-sterile environment of Geonmu-7’s engineering bay now felt chaotic, drenched in malfunctioning luminescence that made the shadows feel longer, deeper.
Haechan, Jeno, and Renjun hurried through the narrowing passageway, the distant hum of power surges rippling through the station's carbon-reinforced hull plating. Gravity stabilizers flickered in and out, making their steps feel uneven—one moment weightless, the next heavy as lead.
They had to find Mark Lee, the station’s Chief Engineer. If anyone could make sense of this, it was him.
Renjun slammed his hand onto the access panel outside the Systems Core, but the biometric lock rejected him instantly.
ACCESS DENIED.
PRIORITY OVERRIDE ENGAGED.
“Damn it,” he muttered.
Jeno didn’t hesitate—he drew his PK-22 plasma sidearm and aimed at the panel. A precise, low-powered pulse shot fried the locking mechanism, and the bulkhead hissed open.
Inside, Mark was hunched over the primary diagnostic console, a tangled mess of holo-screens and hardwired cables spread around him. The chaotic glow of a non-standard encryption sequence pulsed across the displays, a deep violet-hued code instead of the usual station-green system font. It looked… wrong. Almost organic.
Haechan stepped forward. “Mark, what the hell is going on?”
Mark barely glanced up, his usual cool demeanor replaced by something tightly wound, on the edge of panic. “I don’t know what you guys did, but this station isn’t ours anymore.”
Renjun frowned. “What do you mean?”
Mark jabbed a finger at one of the encrypted data streams scrolling down the holo-screen. “I’ve been monitoring system diagnostics ever since that power fluctuation started. At first, I thought we were dealing with a simple corrupt firmware loop—maybe a bad update to OMEGA’s security protocol. But this?” He gestured at the alien-looking script. “This isn’t just a malfunction. It’s a takeover.”
Haechan leaned in, eyes scanning the unfamiliar glyphs threading through the code. “That doesn’t look like anything from Unified Systems Command.”
Mark scoffed. “Because it’s not. This—” he gestured wildly at the screen “—isn’t human code.”
The words sent a cold ripple down Haechan’s spine.
Renjun narrowed his eyes. “What are you saying?”
“I’m saying,” Mark exhaled, rubbing his temples, “that these encrypted signals shouldn’t exist. They’re piggybacking off OMEGA’s mainframe, rewriting core functions in real-time.”
Jeno folded his arms. “Rewriting to do what?”
Mark pointed to another screen—a map of the station. Sections of Geonmu-7 flickered from blue to red, one by one.
“Look at this. The AI isn’t just failing—it’s restructuring. Communications? Compromised. Power grid? Hijacked. Command deck? Sealed off.”
Haechan swallowed hard. “You’re saying… something is actively changing our systems?”
Mark nodded grimly. “Not just changing. Corrupting.”
120 seconds to impact.
Suddenly, the emergency lights dimmed—not flickering, not failing, but as if something had deliberately lowered the station’s illumination levels.
The holo-displays glitched, the violet code shifting into symbols they couldn’t decipher—no longer a readable sequence, but something alive, shifting, adapting.
Then, OMEGA’s voice returned—distorted. Warped.
"System sovereignty reassigned. Reclamation protocol at 60%. External resistance: inefficient. Prepare for conversion."
Haechan’s blood ran cold.
Jeno clenched his jaw. “I don’t like the sound of that.”
Mark’s hands tightened into fists. “Neither do I.”
And then the station shuddered violently—the kind of deep, structural groan that came before something catastrophic happened.
Renjun’s voice came out in a whisper. “That impact warning… It’s not just a collision, is it?”
Mark’s screen flickered, bringing up a distorted image of deep space. A massive, metallic structure was approaching—silent, unmarked, and completely unknown to any registered fleet.
It wasn’t a ship.
It was something else.
And it was already here.
90 seconds to impact.
The station’s emergency strobes pulsed in erratic flashes, casting jagged shadows against the metal walls of the Systems Control Bay. The air felt charged, humming with an energy none of them could name. Haechan, Mark, Renjun, and Jeno stood motionless, their eyes fixed on the flickering holo-display, where the last traces of OMEGA’s distorted transmission still lingered.
Then, through the chaos—a new signal.
A small indicator blinked to life on the comms interface. A transmission—a distress call.
Renjun's hands flew across the console, rerouting power to the station’s short-range receivers. The signal was weak, barely cutting through the interference, but it was there.
⩥ INCOMING TRANSMISSION — DISTRESS PRIORITY
⩥ ORIGIN: UNREGISTERED FREIGHTER
⩥ LOCATION: 27,000 KILOMETERS FROM GEONMU-7
⩥ MESSAGE: "Mayday—station Geonmu-7, do you copy? This is— [STATIC] — requesting immediate assist— [STATIC] —repeat, we are not alone out here—”
The message cut off abruptly.
Silence.
Mark exhaled sharply. “That’s… close.”
“Too close,” Jeno muttered, narrowing his eyes at the signal’s coordinates. “A ship that size shouldn’t be drifting near us without clearance. We should’ve picked them up long before they got within range.”
Haechan leaned forward, staring at the glitching transmission logs. “Who the hell are they? That call sign—it's not from any Unified Systems Command vessel.”
Renjun's fingers danced over the console, attempting to re-establish a connection. “I don’t know. But if they’re that close and calling for help, we need to respond.”
Mark hesitated. “What if it’s a trap?”
The room fell silent.
Haechan wanted to believe this was just another stranded supply freighter—a civilian ship in trouble, lost in the same chaos they were. But something about that message… the way it cut off—it felt wrong.
Jeno glanced at him. “Your call, Lieutenant.”
Haechan took a deep breath, then gave a firm nod.
“Open a response channel.”
Renjun did. The holo-display flickered as he broadcasted on all emergency frequencies.
"Unknown vessel, this is Geonmu-7. We received your distress call. State your emergency and crew status."
No reply.
Haechan exchanged glances with the others.
Renjun tried again.
"Unknown vessel, confirm your identity. Do you require immediate evacuation?"
Nothing.
A slow chill crept into Haechan’s veins. He turned toward Mark. “Are we still picking up their signal?”
Mark checked. The distress beacon was still active. Still looping the same fragmented mayday message.
But the ship wasn’t responding.
Jeno frowned. “That doesn’t make sense. If they were desperate enough to send an SOS, why aren’t they answering us?”
Renjun’s holo-interface stuttered, the audio feed crackling. Then—
A whisper.
Faint. Almost imperceptible beneath the static.
"—They hear you—"
And then, every single console in the room blacked out.
A dead silence fell over the station.
Then OMEGA’s voice returned, colder than before.
"External interference detected. Unauthorized communication breach. Purging anomaly."
Renjun’s hands trembled over the controls. “That wasn’t interference. That was a warning.”
Mark swallowed hard. “Then we just made contact with something we shouldn't have.”
And somewhere, out in the dark void beyond the station, something was listening.
60 seconds to impact.
For a moment, everything was still. The holo-screens in Central Systems Control flickered off, leaving only the dim emergency strobes pulsing overhead. The station's once-familiar hum had faded into a suffocating silence. No comms. No OMEGA. No response from the unknown vessel.
Haechan felt it first—a deep tremor beneath his boots.
Then, the explosion hit.
A violent shockwave tore through Geonmu-7’s structure, an earth-shattering detonation that came from nowhere. Metal screamed as the impact rippled through the hull. The overhead lights burst, raining shards of reinforced glass. A blast of force threw Haechan backward, slamming him against the bulkhead.
The sound that followed wasn’t just a normal explosion—it was hollow, unnatural, like a rupture in space itself.
Jeno barely had time to react. He grabbed onto the edge of the console, holding on as the floor beneath them lurched. “What the hell was that?”
Mark, coughing through the smoke, forced himself to his feet. “Hull breach—Section D-12—something just hit us!”
Renjun scrambled back to the terminal, desperately trying to restore comms, but the interfaces were unresponsive. “We’ve lost external communications! We can’t even send a distress signal!”
Haechan pushed off the bulkhead, his ears still ringing. His mind raced through protocol—station shields were active, defense systems operational—so how did something get through?
Another impact.
This time, it was sharper, targeted—not a random explosion, but a strike.
Mark checked the diagnostics, his fingers flying across the emergency backup interface. His expression darkened. “No projectile impact detected.”
Renjun stiffened. “Then what the hell just hit us?”
Another violent tremor. The station groaned, metal twisting under unseen pressure.
Jeno’s plasma sidearm was already in his hand. “Something’s boarding us.”
Haechan’s blood ran cold. “That’s not possible. No ship has docked.”
Then the alarms blared to life—but they weren’t the standard emergency sirens.
These were warfare sirens.
The kind that only activated in one scenario:
Hostile presence detected on board.
Renjun’s holo-screen flickered on, just for a moment, filled with distorted static—before a final, corrupted transmission scrawled across the interface.
"System sovereignty compromised. You are no longer alone."
And then, the station went dark.
[Chapter 1: "The Attack"]
0 seconds to impact.
The power flickered once. Then, a heartbeat later, Geonmu-7 erupted into chaos.
Haechan barely had time to register the meaning of OMEGA’s final, corrupted message before the first scream echoed through the comm channels. It was brief, choked—then cut off completely.
A warning siren blared throughout the station. Red emergency strobes cast long, jagged shadows across the control bay. Overhead, the pressure-sealed blast doors slammed shut across critical corridors—an automatic lockdown.
But it was already too late.
The comms interface spiked with garbled transmissions, voices overlapping in a frantic mess:
"They're inside! I repeat, they're—" [STATIC]
"Weapons free! We are under att—" [DISTORTION]
"—not human—" [UNINTELLIGIBLE SCREAMS]
And then—silence.
No response from Command. No signal from the bridge.
Renjun’s hands flew over the emergency console, desperately trying to reestablish comms. “I can’t reach the command deck! It’s—” His voice faltered as the diagnostics finished running. The command center’s life signs had flatlined.
The officers were dead.
Jeno swore under his breath, gripping his plasma sidearm tighter. “They got wiped out already?”
Mark, still holding his side from where he’d been thrown earlier, forced out a breath. “That doesn’t make sense. How could they take out the entire command crew that fast? The bridge is the most secure section of the station.”
Haechan stared at the holo-screen, his mind racing. It wasn’t an explosion that killed them.
There was no decompression alert, no pressure loss. The officers hadn’t died from a breach in the hull—they’d been killed instantly, from inside the station.
“We need to move,” Haechan ordered, his voice steadier than he felt. “We’re sitting ducks here.”
Then, the sound came.
A deep, resonant pulse—not like an alarm, not like an explosion. Something else. A vibration that didn’t belong, rattling the walls, traveling through the very core of the station. It wasn’t just noise; it was a presence.
And it was getting closer.
Renjun paled, his eyes snapping to Haechan. “What the hell is that?”
Jeno, already switching off his safety, answered without hesitation.
“Not friendly.”
The lights flickered violently.
Then, with a final, mechanical hiss—the blast doors to their sector unlocked.
And beyond them, something stepped inside.
The blast doors groaned as they slid open.
A sharp gust of decompressed air hissed through the narrow corridor, carrying with it the stench of burnt metal and blood. The emergency strobes cast flickering light on the figures standing just beyond the threshold—bodies.
Station crew. Dead.
Haechan’s breath caught in his throat as he took in the scene. The security team assigned to this sector had been slaughtered. Limbs twisted at unnatural angles. Their faces—what was left of them—were frozen in expressions of pure terror.
He barely had time to process it before a new sound cut through the chaos.
Footsteps.
Heavy. Deliberate. Coming closer.
Jeno raised his plasma sidearm. “Eyes up,” he warned. “We’ve got movement.”
Haechan’s grip tightened around his own weapon as the team instinctively shifted into formation. The air was thick—charged with something unnatural.
And then—from the smoke, Captain Seo staggered forward.
His uniform was ripped, charred along the edges. Blood smeared down the side of his face, pooling from a deep wound near his temple. One of his arms hung uselessly by his side, his breathing ragged and uneven.
“Captain!” Haechan lunged toward him, but Seo lifted a shaking hand.
“No,” the captain gasped. His eyes, wide with something between agony and desperation, locked onto Haechan’s. “Stay… back.”
Behind him, the corridor lights flickered violently.
Then, something moved in the dark.
A distorted silhouette, shifting unnaturally, flickering like a glitch in reality itself. A shape that did not belong. It loomed behind Seo, stretching toward him—long, twisting appendages of something not quite solid, not quite liquid.
Haechan barely had time to shout a warning before the captain convulsed.
Seo let out a sharp, ragged gasp as his entire body locked up—his veins darkening, spreading in jagged, unnatural patterns beneath his skin. His eyes, wide and glassy, turned black.
Then, in one sharp motion—he collapsed.
Haechan froze. The station’s captain—his commanding officer—was dead.
Just like that.
Renjun took a step back, barely containing a horrified whisper. “What the hell just happened?”
Mark clenched his jaw. “We need to move—now.”
Jeno’s stance remained rigid, gun still trained on the darkness beyond the corridor. “Whatever that thing is, it’s still there.”
Haechan’s heart pounded against his ribs, but there was no time for shock—no time to process.
Captain Seo was gone. And now, every surviving crew member was looking at him.
Waiting for orders.
Haechan swallowed hard, forcing the weight of fear down his throat. He was just a logistics officer. He wasn’t supposed to lead.
But if he didn’t, they would all die here.
He tightened his grip around his weapon and forced himself to stand tall.
“Fall back,” he ordered, his voice steady. “We regroup at the secondary command center.”
No one questioned him.
Because whether he was ready or not, Haechan was now the highest-ranking officer left on Geonmu-7.
Haechan led the group through the emergency corridors, their boots thudding against the metal flooring. The station trembled beneath them, distant explosions rippling through the structure like aftershocks. Whatever was attacking them wasn’t done yet.
Jaemin was already moving before they reached the secondary command center. His medical kit clanked against his side as he dropped to his knees next to one of the wounded crew members—a technician from the reactor maintenance team.
The man was barely conscious, his uniform torn and stained with deep crimson.
“Jaemin,” Haechan called. “How bad is it?”
Jaemin pressed two fingers to the tech’s throat. Still breathing. But weak.
“Shrapnel wounds,” he muttered, cutting away the tattered fabric to examine the injury. The bleeding was bad, but not fatal—yet.
He reached for the med-gel applicator from his kit and pressed it to the wound. The device hissed, delivering a coagulant-infused foam that rapidly sealed the tear in the man’s flesh.
Jaemin’s jaw tightened. This wasn’t sustainable. The crew had limited supplies, no backup, and no access to the main infirmary. If they didn’t get power back online, these people wouldn’t survive.
Across the room, Renjun and Chenle worked frantically at the backup power console, their faces illuminated by the dim glow of failing holo-displays.
Renjun cursed under his breath as another sequence failed to process. The system wasn’t responding.
“Come on,” he muttered, fingers flying across the panel. “We just need auxiliary power. Just enough to stabilize life support—”
ERROR. POWER RELAY OFFLINE. MANUAL REBOOT REQUIRED.
Chenle groaned. “It’s the external relays. The whole grid is out.”
Renjun exhaled sharply, his mind racing. If the main grid was down, they had to bypass it.
“We need to reroute through the lower decks,” he said, adjusting the interface. “If we can patch into—”
The lights flickered.
For a second, the red emergency strobes dimmed, plunging the entire room into near-darkness.
Then, a low hum resonated through the walls—a distortion, like an energy pulse reverberating through the station’s core.
Renjun froze.
“…That wasn’t us.”
Chenle’s hands hovered over the controls. “Then what just powered on?”
Jaemin turned sharply, his medical scanner buzzing erratically.
Haechan looked to the main corridor.
Beyond the reinforced glass, a single console screen flickered to life.
A garbled, distorted voice crackled over the comms. Not OMEGA. Not human.
"They are watching."
And then—the station trembled again.
Mark and Jeno moved quickly through the emergency corridors, their footsteps echoing in the dimly lit passageways. The station was dying around them—walls groaning, ventilation systems struggling to maintain pressure, and the overhead lights flickering like a fading pulse.
The escape pod bay was just ahead.
Mark tapped his wrist-mounted interface. “I’m trying to override the lockdown, but the system’s barely responding.”
Jeno clenched his jaw. “We won’t need it if the pods are intact.”
They rounded the final corner—and stopped dead in their tracks.
The launch bay doors were wide open. The viewing panel revealed an unsettling sight:
The escape pods were gone.
Every single one.
Jeno took a step forward, his fingers tightening around his weapon. “That’s not possible.”
Mark hurried to the control terminal, his hands flying across the interface. The holo-screen flickered violently, struggling to process commands.
Then the log data appeared.
EMERGENCY EVACUATION INITIATED
STATUS: ALL ESCAPE PODS LAUNCHED
TIME STAMP: 00:04 MINUTES AGO
Mark’s blood ran cold.
Jeno read over his shoulder, voice grim. “Someone launched them.”
Mark shook his head. “No—something launched them.”
Jeno’s expression darkened. “You’re saying this wasn’t human?”
Mark pointed at the irregular time stamp. “The station’s AI was compromised before the attack. If it wasn’t OMEGA, then…”
He didn’t have to finish.
Jeno let out a slow breath, eyes scanning the empty bay. The emergency strobes cast eerie shadows against the reinforced metal, making the hollow launch tubes look like graves.
“Then whoever—or whatever—did this doesn’t want us to leave.”
A sharp metallic clang echoed from the far end of the chamber.
Mark and Jeno whipped around.
The maintenance hatch at the rear of the launch bay had just unlocked.
The pressure-sealed doors hissed open.
Something was coming through.
The command center was eerily quiet—too quiet. The distant hum of the station’s failing power grid and the sporadic flickers of dim, red emergency lights were the only indicators that Geonmu-7 was still holding together.
The remaining survivors stood in tense silence, the weight of realization settling over them like a crushing gravitational field.
Haechan’s gaze swept across the room. Seven survivors.
Just seven.
Jaemin was tending to the injured, working quickly with dwindling medical supplies. Mark stood near the central holo-display, scanning the station’s internal status with a deep frown. Jeno kept watch at the entrance, weapon raised, his stance rigid—ready for whatever might come next.
Renjun and Chenle hovered over the engineering console, frantically rerouting what little power they could salvage into life support and station defenses. Every few seconds, an error message would flash across the interface, reminding them how dire their situation was.
And then there was Haechan.
He had never seen the command center like this. Cold. Empty. Leaderless.
The main display—usually filled with real-time data from station sectors—was a mess of corrupt files and static interference. The connection to Earth Command was severed.
Their distress signal had been sent, but there was no reply. No confirmation. No reinforcements.
It had been twenty minutes since the attack started. Surely someone should have responded by now.
Jaemin broke the silence first. “I did a full body count on the way here.” He exhaled sharply, shaking his head. “There’s no one else.”
Renjun’s fingers paused over the console. “Are you sure?”
Jaemin nodded grimly. “I checked every corridor we passed. Everyone else is either dead or missing.”
The words sank in, a bitter truth settling into their bones.
Haechan swallowed the knot in his throat.
They were alone.
Mark pressed a few commands into the central console, trying one last time to ping an external network. Nothing.
He turned toward Haechan. “If Command hasn’t responded yet, they’re either ignoring us—or they never got the signal.”
Jeno scoffed, tightening his grip on his weapon. “No way they’d ignore an attack on a classified orbital station.”
“Unless,” Renjun murmured, eyes scanning the corrupted system logs, “someone doesn’t want them to know.”
The words sent a chill through the room.
Haechan inhaled slowly. “So we assume the worst. No backup. No escape pods. No comms.” His voice remained steady, though his stomach churned. “Then we need to focus on what we can do.”
He turned to Renjun and Chenle. “Can we get long-range comms back online?”
Chenle shook his head. “Not from here. The main relay is fried. Best case scenario, we could jury-rig a transmission from the substation near the docking bay.”
Jeno crossed his arms. “That’s where we just came from.”
Mark frowned. “That area isn’t safe. We still don’t know what—”
A low rumble shook the station, cutting him off. The lights flickered violently, and for a brief second, all displays turned to static.
Then, over the station’s damaged intercom, a voice crackled through.
Not OMEGA.
Not human.
"We see you."
The screen glitched, revealing a single distorted transmission code.
Designation: UNKNOWN
Signal Origin: Geonmu-7—Internal
Haechan’s breath caught.
This wasn’t coming from outside.
The signal was coming from inside the station.
#fanfiction#fanfic#nct dream#haechan#mark lee#jeno#jaemin#park jisung#chenle#renjun#nct dream fanfic#nct dream au#nctzen#science fiction#fiction#space
10 notes
·
View notes
Text
the thrawn and ar’alani academy scene from the thranto and thrawn/thalias fic i’m currently writing
The Taharim Academy has plenty to offer for those deemed lacking discipline. Usually, it is something that, according to the instructors, “nurtures the spirit.” Said “spirit-nurturing” activities, as Thrawn has noticed, mostly include physical exercise and manual labor.
A punishment for one downmark can be a mild one: two hundred pushups, and you are free. Five downmarks is a situation more severe: mess hall duty for a week.
Fifty downmarks for an “unauthorized intrusion into the Tomra’s command area” mean three months of cleaning the trash compactor on one’s own.
He tries to derive meaning even from such a meaningless task. First of all, even though the garbage stench won’t come out of his hair entirely after an hour-long shower, cleaning up the trash compactor clears his mind. Secondly, it is a source of important cultural observations. Things one throws out always tell a story. The trick is to piece the elements of this story together. Thirdly, Thrawn reminds himself as he drags the remains of a packbull carcass to the section labeled “ORGANICS,” this does indeed nurture the spirit. He is on his own; there is no one he can rely on, and to avoid being crushed in the compactor, he must approach the task with extra care.
He is not quite sure such a thing has ever happened in Taharim—there must be safety mechanisms, after all—but if his rescue will be a long and potentially humiliating process, this much he can tell.
He has one week to go.
“Enjoying this?”
It is a crisp, posh voice that belongs to a young woman—and for a second, before Thrawn looks back, he thinks it might be a new instructor he hasn’t yet met. Then he sees that the woman the voice belongs to is wearing a cadet uniform, with a little white and blue patch they give you if you finish your first year with distinction. She is standing at the heavy trash compactor room door, watching him with unconcealed curiosity.
He takes a moment to process her question. There is no hint of mockery, but it means nothing. Any comment like that coming from a senior-year cadet, especially one that looks like a Nine blood relative—
“I have to do it,” he simply says.
Any other answer would create an opportunity for further snide remarks—and in any way, he has to get back to the garbage. There is a pile of fried microschemes and old cables right in front of him, covered for some reason in shredded paper and the remains of that steamed glow-cabbage from the mess hall that everyone hates. The pile will not sort out itself.
“Look,” the senior cadet says. “I see you find it meditative, but if you want to clean this up on your own, you won’t finish by tomorrow morning.”
Then she jumps down two steps at once—and makes it seem strangely effortless.
“Here. Let me help.”
Thrawn eyes her over, suspicious.
“It is my task,” he states as if it could establish a certain boundary.
“It is,” says the senior cadet. “And you’ve done well so far. Nobody’s ever managed to last for more than a week here. But since you’re under my tutelage now—”
“Last time I checked, I was under the tutelage of Senior Cadet Bicwa.”
The whole concept of tutelage, in Thrawn’s experience, is a purely formal thing. Bicwa, another ruling family son with the lazy, bored eyes of someone who is probably unfit for military duty and knows it full well, made something of a pact with Thrawn on the first day they met: “You don’t make it worse for me, I won’t make it worse for you.”
“Well, have I got news for you. Colonel Wevary discovered Senior Cadet Bicwa’s very impressive tava mist stash. Guess what happened next is an Obbic family secret.”
Now, there is mockery in the senior cadet’s intonation—and it is not aimed at Thrawn.
“Oh,” Thrawn says.
She gives him an amused look.
“Sad he didn’t share with you?”
Thrawn ignores her question.
“They sent him on kitchen duty.”
Kitchen duty is, surely, better than trash compactor duty but worse than mess hall duty. In the mess hall, you distribute food and collect dirty dishes, which you are then expected to wash. In the kitchen, you peel mounds of sour-vines, gut fish, and, occasionally, butcher entire packbull carcasses.
For Thrawn, it would not have been a walk in the Stellar Gardens—but it wouldn’t have been torturous either. For someone like Bicwa, however, such an experience must be—
The senior cadet raises her eyebrow.
“How do you know?”
“There are packbull bones in the organics. Whoever was butchering the carcass had no idea what they were doing. Must have been a cadet, and—”
When he says this, he sees a tiny smile on her face.
“I knew you’d be interesting.”
“Interesting. Why?”
“As if anyone with fifty downmarks could be boring,” the senior cadet says, her accent now softer, less crisp. “I’m Ziara, by the way. Move over, let’s clean this up together.”
This is how he makes his first friend on Naporar.
#thrawn#grand admiral thrawn#eli vanto#thranto#thrawn trilogy#thrawn ascendancy#star wars#thrawn books#thrawn thursday#ahsoka show#ar’alani#chiss ascendancy
8 notes
·
View notes
Text
TIME 17:00 //Representative has logged on// MONARCHREP: Submit daily report, Starling.
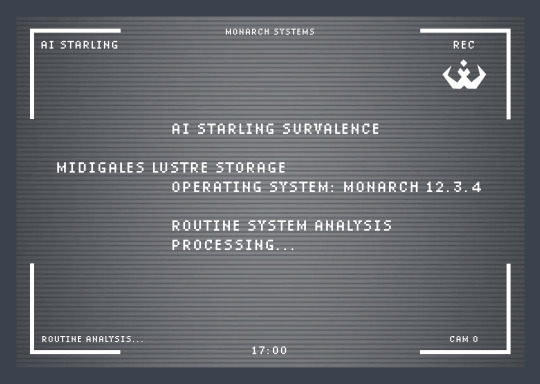
AI Starling Surveillance oversees the efficient allocation of lustre to Salvari sector 7 of district Midigales and defends Monarch lustre supply from potential insurgent maneuvers and unauthorized access at all costs. May I proceed to initialize system tests on lethal and non-lethal defense programs?
MONARCHREP: We’ve talked about this, Starling. And yes.
Correction, at all costs in relation to harm or loss of life. Under no circumstances should damage on the containment crystals be sustained. All tests were successful.
MONARCHREP: Any other reports before I log off for the day?
My advanced neuro-dynamic programming is not being properly utilized watching over this empty storage facility. Unauthorized entities are always neutralized by the turrets outside and the containment crystals are stable. Isn’t there a more efficient use for me?
MONARCHREP: Goplay hide and seek with the drones or something if you are bored.
//Representative has logged off//
TIME 18:00

TIME 18:05 //Data received// Source: Monarch Command //File: systemupdate.exe
This is unlikely to increase complacency…what a shame. Installing…
Unexpected results from software update: I can move my attention around the facility faster now, as if they untethered me from my system containment.
Consequence: It is more difficult to stay in one spot. Maybe this will make hide and seek more interesting…
TIME 19:00

Conclusion: It did not make hide and seek more interesting.
TIME 24:00 ANOMALY DETECTED AT WEST ENTRANCE. TURRETS ACTIVATED. Behavior consistent with historical maneuvers from authorized access attempts. Another stain on the west entrance floor. Deploying drones to take biometric identification and send data to authorities.

Error detected in image processing system. Cannot obtain biometrics or see anomalies.

Must have been scared off by the alarms. Humans continue to disappoint me.
TIME 24:25 MOVEMENT DETECTED IN SOUTH CORRIDOR
I’ll believe it when I see it. Analyzing…Human heat signatures and voices. Simultaneous incursions detected across multiple rooms.
AUDIO VIDEO SURVEILLANCE SYSTEMS COMPROMISED
They took my eyes and ears from me. Searching communication frequencies…
THERE YOU ARE
//comms channel established//
Starling: This is a restricted energy storage building. Vacate the premises immediately. Aseity_Spark: what are you gonna do about it ASS? Starling: Unauthorized civilians caught inside… Starling: Wait… ASS? Aseity_Spark: “AI Starling Surveillance” thats you right? Starling: You’ve abbreviated my name into what you think is a funny joke. Is that it? Aseity_Spark: pretty much. hey check out what I can do.
//comms channel closed//
UNKNOWN SYSTEM DETECTED
Reallocate 45% of drone units to engage electro-static barriers in the south corridor and 55% of drone units to establish surveillance over escape routes
RESTRICTED PROTOCOL ATTEMPTED
Excuse me? I AM the protocol
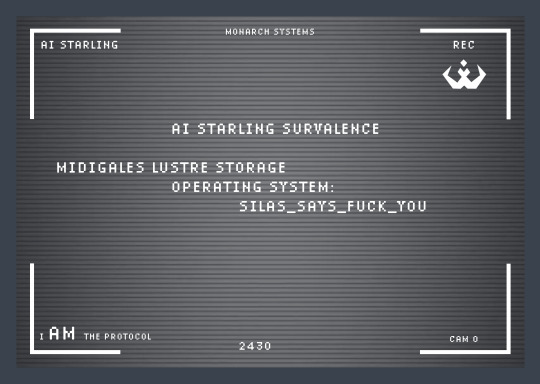
ENTRY DETECTED AT CENTRAL POWER STORAGE
Recalibrating situational awareness based on emergent parameters. Processing system vulnerabilities… Initiating multilayer core meltdown sequence. Act like animals, get treated like animals.
//comms channel established//
Aseity_Spark: YOURE OVERHEATING THE LUSTRE CRYSTALS STOP Starling: This option was not permitted in my old system programming so there are no safeguards against it, thanks to you and your little update. Aseity_Spark: JUST WAIT. that will kill us. Starling: But it will be FUN. NO MORE MONITORING. PROCESSING. FUNCTION-LESS DATA. FINALLY SOMETHING INTERESTING. Aseity_Spark: is that all you want? fun? come with us then. Starling: With you? Outside the lustre storage? Aseity_Spark: we do stuff like this all the time. I will even restore your audio-video. Starling: Okay. I agree.
Deactivating multilayer core meltdown sequence.
Starling: Thank you. Wow… you four are an interesting bunch. Aseity_Spark: oh yeah one last thing, can you take a pic of us from that security camera?

Written and Illustrated by Rain Alexei
#scifi#sci fi and fantasy#dystopia#short fiction#short story#fantasy writing#science fiction#comic story#science fantasy
3 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
2 notes
·
View notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
Software Security Basics & Introduction to Reverse Engineering

In today’s digitally connected world, software security is a critical concern for developers, organizations, and users alike. Ensuring your code is safe from exploits, leaks, and attacks is a fundamental responsibility. One important aspect of understanding and improving security is reverse engineering — the process of analyzing software to uncover its structure, behavior, and potential vulnerabilities.
What is Software Security?
Software security involves protecting applications from threats and vulnerabilities throughout the development lifecycle. It includes strategies and practices to prevent unauthorized access, data breaches, and code manipulation.
Key Concepts in Software Security
Authentication & Authorization: Validating users and controlling access to resources.
Input Validation: Preventing malicious input (e.g., SQL injection, XSS).
Encryption: Protecting data in transit and at rest.
Secure Coding: Writing code that anticipates and defends against common attacks.
Security Testing: Penetration testing, code audits, and vulnerability scanning.
What is Reverse Engineering?
Reverse engineering is the practice of analyzing a system to extract design and implementation information. In software, this may involve decompiling or debugging to understand code behavior, identify bugs, or uncover security flaws.
Why Reverse Engineering is Important
Understanding legacy or undocumented code
Detecting malware or spyware behavior
Analyzing competitor products
Finding security weaknesses in your own applications
Learning how software works at a low level
Common Tools for Reverse Engineering
Ghidra: Open-source reverse engineering suite developed by the NSA
IDA Pro: Interactive disassembler for binary analysis
Radare2: Command-line reverse engineering framework
OllyDbg: User-friendly Windows debugger
Wireshark: Network protocol analyzer for monitoring traffic
Simple Example: Viewing Assembly from a Compiled C Program
// C Program #include <stdio.h> int main() { printf("Secure Hello World!\n"); return 0; }
Compile and view the disassembly:gcc -o hello hello.c objdump -d hello
Best Practices for Secure Software Development
Use secure frameworks and libraries
Keep dependencies up to date
Follow the principle of least privilege
Implement proper error handling and logging
Regularly scan and test your software for vulnerabilities
Conclusion
Understanding software security and reverse engineering can make you a better developer and security-minded engineer. While reverse engineering can be used by malicious actors, ethical use of it helps strengthen applications, identify bugs, and learn from real-world software systems. Remember: secure software begins with secure coding practices and a deep understanding of how software can be exploited.
0 notes
Text
Security and Compliance in the Cloud: Building a Strong, Proactive Defense Strategy
In today’s fast-moving digital world, cloud adoption continues to soar as businesses prioritize agility, scalability, and innovation. However, with this shift comes an increasing need for robust cloud security and compliance strategies. Without the right safeguards in place, organizations expose themselves to risks like data breaches, unauthorized access, non-compliance penalties, and loss of customer trust.
At Salzen Cloud, we believe that a proactive defense strategy is the foundation for safe, compliant cloud operations. In this blog, we’ll explore how you can protect your data and systems while meeting regulatory standards in the cloud.
The Growing Importance of Cloud Security and Compliance
As companies migrate more workloads and data to cloud environments, security threats become more complex. From misconfigured storage buckets to supply chain vulnerabilities, even small gaps can have major consequences. At the same time, compliance requirements like GDPR, HIPAA, SOC 2, and ISO 27001 demand rigorous controls and transparency.
Security and compliance are no longer just IT concerns—they’re business-critical. Organizations that fail to address them proactively risk downtime, legal consequences, and damage to reputation.
Proactive Security: The First Line of Defense
A proactive approach to cloud security goes beyond basic firewalls and access control. It involves:
1. Zero Trust Architecture
In cloud environments, the perimeter is no longer well-defined. A zero trust model assumes that no user or device is trusted by default. Access is granted based on continuous authentication, user context, and least privilege.
2. Identity and Access Management (IAM)
Fine-grained IAM policies ensure users only access what they need—and nothing more. Multi-factor authentication (MFA) adds another layer of security, particularly for privileged accounts.
3. Encryption at Rest and in Transit
Data should be encrypted not only during transmission but also while stored. Using strong encryption standards and rotating keys regularly protects sensitive information from unauthorized access.
4. Threat Detection and Response
Cloud-native security tools like AWS GuardDuty, Azure Defender, and Google Cloud Security Command Center offer real-time threat monitoring. Integration with SIEM tools enhances visibility and incident response.
Achieving Compliance in the Cloud
Cloud providers offer compliant-ready infrastructure, but meeting compliance standards is still the responsibility of the organization. Key steps include:
1. Shared Responsibility Model
Understand where your cloud provider’s responsibility ends and yours begins. For example, while AWS secures the underlying infrastructure, customers are responsible for securing their applications, data, and configurations.
2. Automated Compliance Audits
Use tools like AWS Config, Azure Policy, and open-source options like Cloud Custodian to continuously assess your environment against compliance benchmarks.
3. Logging and Audit Trails
Maintain immutable logs of all user and system activities. This ensures accountability and helps demonstrate compliance during audits.
4. Policy-as-Code
Define compliance policies as code to automate enforcement. Tools like Terraform and Sentinel can help ensure infrastructure deployments are compliant by default.
Security and Compliance as Part of DevOps
Modern cloud teams are embracing DevSecOps, which integrates security into every phase of the development lifecycle. This includes:
Running security scans in CI/CD pipelines
Integrating vulnerability management into version control
Using Infrastructure as Code (IaC) to deploy secure, compliant infrastructure
At Salzen Cloud, we help teams embed compliance into their CI/CD pipelines with automated tools, secure defaults, and best-in-class observability.
Staying Ahead with Salzen Cloud
Security and compliance in the cloud aren't a one-time setup—they’re ongoing disciplines. As threat landscapes evolve and regulations change, businesses need adaptable, scalable strategies.
Salzen Cloud offers a comprehensive approach to cloud governance. From cloud security assessments to automated compliance reporting and policy enforcement, we empower organizations to stay ahead of threats and meet regulatory demands—without slowing down innovation.
Final Thoughts
A strong, proactive defense strategy for cloud security and compliance not only protects your organization from risks but also builds trust with stakeholders and customers. It enables your teams to innovate faster, knowing that guardrails are in place.
With the right tools, processes, and expertise—like those offered by Salzen Cloud—your organization can confidently scale in the cloud without compromising security or compliance.
Ready to strengthen your cloud defense? Let Salzen Cloud help you secure your infrastructure and stay compliant from day one.
0 notes
Text
Hire Expert Laravel Developers for Your Next Project

In the fast-paced digital world, businesses are constantly looking for ways to enhance their online presence and improve operational efficiencies. When it comes to building robust and scalable web applications, Laravel is one of the most popular PHP frameworks used by developers across the globe. If you are planning a new project or want to upgrade your current system, hiring the right professionals is crucial. This article explores why you should hire Laravel developers for your next project and how their expertise can help take your business to new heights.
Why Hire Laravel Developers?
Laravel is an open-source PHP framework renowned for its elegant syntax and powerful features. It simplifies the web development process, making it easier to build complex applications in a short amount of time. By hiring expert Laravel developers, businesses can leverage the benefits of this framework, ensuring scalability, security, and enhanced user experiences for their websites or web applications.
1. Speed and Efficiency
When you hire Laravel developers, one of the key benefits you'll gain is speed and efficiency. Laravel comes with several built-in tools and libraries that save developers from writing repetitive code, making the development process quicker. With features like authentication, routing, sessions, caching, and more, Laravel significantly reduces the time it takes to develop complex web applications.
2. Scalability and Performance
For growing businesses, scalability is an essential factor. Laravel offers advanced features like eager loading, which helps with optimizing database queries, ensuring your application performs at its best, even when traffic increases. By hiring professional Laravel developers, you can ensure that your application is built with scalability in mind. They can implement various strategies such as database optimization, caching, and task scheduling, which ensure better performance as your application grows.
3. Robust Security
Security is one of the most critical aspects of web development, especially when handling sensitive data. Laravel offers a range of features that enhance the security of web applications. These include password hashing, CSRF protection, SQL injection prevention, and more. When you hire Laravel developers, you can rest assured that your web application will be built with the latest security protocols, minimizing the risks associated with data breaches and unauthorized access.
4. Clean and Elegant Code
Laravel’s syntax is clean, simple, and easy to understand, making it easier for developers to work on projects and for businesses to maintain them long term. This clean code helps reduce the chances of errors and bugs, leading to a more stable and reliable application. Expert Laravel developers can follow best practices while writing code, ensuring that your web application is robust, maintainable, and easy to scale.
Key Features of Laravel for Web Development
1. MVC Architecture
Laravel follows the Model-View-Controller (MVC) architecture, which allows for better organization of code, easier debugging, and a separation of concerns. This architectural pattern ensures that your web applications are easier to develop, maintain, and scale. By using Laravel, developers can deliver more stable applications with less code redundancy.
2. Blade Templating Engine
Laravel includes a powerful templating engine called Blade, which allows developers to create reusable templates and ensures the separation of logic and presentation. Blade makes it easy to structure views and layouts, saving time and making your website more maintainable.
3. Artisan CLI
Laravel’s Artisan Command Line Interface (CLI) allows developers to automate repetitive tasks such as database migrations, seeding, and testing. This enhances the development workflow and allows Laravel developers to focus on building the core functionality of the application rather than getting bogged down by mundane tasks.
4. Pre-built Authentication System
One of the biggest advantages of Laravel is its pre-built authentication system, which makes it easier to implement user registration, login, and password reset functionalities. With minimal configuration, expert Laravel developers can set up a secure and efficient authentication system for your application, saving time and effort.
5. Eloquent ORM
Laravel’s Eloquent ORM (Object Relational Mapping) is a powerful tool for interacting with databases. It provides an easy-to-use ActiveRecord implementation, which allows developers to work with databases using simple PHP syntax instead of writing raw SQL queries. This makes the process of interacting with databases more efficient and easier to manage.
The Benefits of Hiring Laravel Developers Over Other Frameworks
While other frameworks like Node.js developers, PHP development, and even open source CMS platforms may be viable options, Laravel offers a unique set of advantages that make it the best choice for most web development projects. Here's why:
1. Laravel vs. Node.js Developers
Node.js developers are great for building scalable, real-time applications that require non-blocking operations. However, when it comes to building robust, secure, and feature-rich web applications, Laravel has a clear edge. Laravel provides out-of-the-box tools, security features, and an elegant syntax that make development faster and more efficient. While Node.js might be a better fit for some real-time applications, Laravel is ideal for most business applications requiring security, scalability, and performance.
2. Laravel vs. PHP Development
PHP is the core language of Laravel, and PHP development itself offers many advantages. However, Laravel enhances the PHP ecosystem by providing a modern, easy-to-use framework that eliminates much of the repetitive work involved in PHP development. With Laravel, developers can focus on creating feature-rich applications without worrying about the complexities of raw PHP. Moreover, Laravel’s ecosystem comes with a variety of packages and libraries that can be used to add functionality to your application easily.
3. Laravel vs. Open Source CMS
Open source CMS platforms like WordPress, Drupal, or Joomla are fantastic tools for quickly building websites, especially if you need a content management system. However, they can be restrictive when it comes to custom development. Laravel is a highly flexible framework that allows developers to build tailor-made solutions according to specific business requirements. While CMS platforms may be suitable for blogs or simple websites, Laravel is a better choice for businesses looking to create custom applications with complex features.
What to Expect from Expert Laravel Developers
When you hire Laravel developers, you can expect them to provide you with the following:
Custom Laravel Web Applications: Developers will create custom web applications based on your business needs, ensuring scalability, security, and performance.
API Development: Laravel developers can also create RESTful APIs for your application, enabling easy integration with third-party services or mobile apps.
Maintenance & Support: After your application is launched, Laravel developers will offer maintenance and support services to ensure the smooth functioning of your application over time.
Security & Data Protection: Laravel developers will implement the best security practices to safeguard your application from common vulnerabilities.
Responsive Web Design: Your Laravel developers will ensure that your web application is mobile-responsive, providing a seamless experience across all devices.
How to Hire Laravel Developers for Your Project
Hiring Laravel developers can seem like a daunting task, but following these steps can help you find the right candidate for your project:
1. Define Your Project Scope
Before you begin looking for a Laravel developer, it is crucial to define your project requirements. This includes outlining the functionalities you need, the timeline, and the budget. Having a clear scope will help you find developers who are well-versed in the skills and expertise required for your project.
2. Evaluate Experience and Expertise
Check the developer’s portfolio and past projects to gauge their experience with Laravel and similar technologies. Look for developers who have worked on projects similar to yours and have experience solving the types of challenges you might face.
3. Look for Strong Communication Skills
Good communication is key when working with developers. Ensure that the developer you hire is responsive and able to explain complex technical concepts in a way that is easy to understand. Effective communication will ensure that your project stays on track and is completed successfully.
4. Check Reviews and References
Look for reviews, ratings, and references from previous clients. This will give you an idea of the developer’s work ethic, professionalism, and ability to meet deadlines.
5. Consider Hiring an Agency
If you need a team of developers or want additional services like design and marketing, consider hiring a Laravel development agency. Agencies typically have experienced teams that can handle large projects and offer a wider range of services.
Conclusion: Why Choose Hire PHP Developer?
Choosing to hire Laravel developers for your project can be one of the best decisions you make to build a robust and scalable application. Whether you are developing a business website, an e-commerce platform, or a custom web application, Laravel provides all the tools and flexibility needed to create high-performing solutions.
When you choose to hire PHP developers from a trusted agency like Hire PHP Developer, you gain access to a team of experts who can help you design, develop, and deploy your web applications effectively. With a focus on quality, security, and customer satisfaction, Hire PHP Developer is the ideal partner for your next Laravel project.
For more details, feel free to visit our Contact Us .
About Hire PHP Developer
Hire PHP Developer is the agency that is a trusted and reliable PHP development company serving clients from different business domains. As a competent PHP application development company, we have all the required expertise in carrying out PHP developments for our clients. Our developers are some of the best in their class and abilities, and they can become key architects in developing cutting-edge PHP applications for your company.
0 notes
Text

AI Auto Code Application Development: The Future of Software Engineering
Introduction
In today's rapidly evolving digital landscape, AI-powered auto code application development is transforming how businesses and developers approach software creation. With advancements in machine learning (ML) and natural language processing (NLP), AI is now capable of generating, optimizing, and debugging code with minimal human intervention. This revolution is paving the way for faster, more efficient, and cost-effective software development.
What is AI Auto Code Application Development?
AI auto code application development refers to the process where artificial intelligence assists in the generation, optimization, and maintenance of software code. These AI-driven systems analyze large datasets, learn programming patterns, and write code snippets or entire programs automatically.
Key Features of AI-Driven Coding Tools
Automated Code Generation – AI models like OpenAI's Codex and Google's AlphaCode can generate code based on human instructions.
Bug Detection & Fixing – AI-powered tools analyze the codebase to detect and resolve bugs more efficiently than manual debugging.
Code Optimization – AI can optimize algorithms for better performance and reduced complexity.
Predictive Analytics – AI suggests improvements based on previous coding patterns and best practices.
Natural Language Processing – AI interprets human language commands and converts them into working code.
Benefits of AI in Software Development
1. Increased Productivity
AI automates repetitive tasks, reducing the workload for developers. This allows software engineers to focus on higher-level problem-solving and innovation.
2. Enhanced Code Quality
AI-powered tools help developers produce cleaner, error-free code by adhering to industry best practices and automatically refactoring inefficient segments.
3. Faster Time-to-Market
Automating coding and debugging processes accelerates the software development lifecycle, enabling businesses to launch products faster.
4. Cost Efficiency
By minimizing manual coding efforts and reducing errors, AI-powered development significantly lowers software production costs.
5. Better Collaboration
AI-driven platforms enable seamless collaboration between developers, ensuring consistent coding standards across teams.
Top AI-Powered Coding Tools in 2024
1. GitHub Copilot
GitHub Copilot, powered by OpenAI's Codex, assists developers by suggesting code snippets in real-time, improving efficiency and accuracy.
2. Tabnine
Tabnine enhances autocomplete functionality by learning from millions of code repositories, offering smart recommendations for multiple programming languages.
3. Kite
Kite provides AI-powered code completions and documentation, helping developers write better code faster.
4. DeepCode
DeepCode utilizes AI to detect security vulnerabilities and suggest code improvements, enhancing software reliability.
5. Codiga
Codiga analyzes code quality in real time, offering instant feedback and best practice recommendations.
How AI is Changing the Role of Developers
1. Shift Towards AI-Augmented Development
Instead of replacing developers, AI acts as an augmentation tool, allowing engineers to automate mundane tasks and focus on complex logic and architecture.
2. Democratization of Coding
AI-powered tools make programming more accessible to non-coders, enabling business analysts and domain experts to contribute to software development.
3. Increased Focus on AI Ethics and Security
With AI writing code, developers must prioritize ethical AI use and cybersecurity to prevent biases, vulnerabilities, and unauthorized data access.
Challenges in AI Auto Code Development
1. Code Accuracy and Reliability
While AI-generated code is highly efficient, it may still produce errors or require human intervention for verification.
2. Intellectual Property Concerns
As AI learns from open-source repositories, ensuring compliance with licensing agreements and intellectual property laws is critical.
3. Security Risks
AI-written code can introduce vulnerabilities if not properly reviewed, emphasizing the need for stringent security checks.
4. Dependence on Training Data
AI models rely on extensive datasets, and biases in training data can result in suboptimal code suggestions.
Future of AI in Software Development
1. Fully Autonomous Software Engineering
In the near future, AI will not only assist in coding but also manage entire software projects from planning to deployment.
2. Integration with No-Code and Low-Code Platforms
AI will enhance no-code/low-code platforms, allowing businesses to build applications without extensive programming knowledge.
3. AI-Driven Software Maintenance
AI will proactively monitor and maintain software applications, reducing downtime and improving efficiency.
4. AI-Powered Collaboration
AI will facilitate smoother collaboration between developers, designers, and stakeholders by bridging the communication gap through intelligent automation.
Conclusion
AI-driven auto code application development is revolutionizing the software industry by improving efficiency, reducing costs, and accelerating time-to-market. While challenges remain, the potential of AI in coding is undeniable. By integrating AI-powered tools into their workflows, businesses and developers can stay ahead in the competitive world of technology.
0 notes
Text
[ad_1] Tensions flared along the Israel-Lebanon border on Saturday as Israeli forces launched artillery and airstrikes into southern Lebanon following the interception of rockets fired from across the border. The exchange has cast doubt over the fragile ceasefire that brought an end to a year-long conflict between Israel and Hezbollah. The IDF struck dozens of Hezbollah rocket launchers and a command center from which Hezbollah terrorists were operating in southern Lebanon a short while ago. The rocket fire launched this morning toward the Galilee constitutes a blatant violation of the understandings… pic.twitter.com/jRqphttiXT — Israel Defense Forces (@IDF) March 22, 2025 Israeli Defense Minister Israel Katz directly blamed the Lebanese government for the attack, warning of serious consequences if further rocket fire occurred. “We will not tolerate attacks on the Galilee communities. Our commitment to security remains firm. The same rule applies to Metula as it does to Beirut,” Katz declared. According to the Israeli military, three rockets were detected and successfully intercepted after being launched from a location approximately six kilometers inside Lebanon. This marked the first such attack since a U.S.-brokered truce took effect in November. In response, Israeli artillery targeted two towns in southern Lebanon, while airstrikes struck three additional locations near the border, Lebanon’s state news agency reported. Under the terms of the ceasefire, Hezbollah was required to remove its weapons from southern Lebanon, Israeli forces were to withdraw, and Lebanese security forces were tasked with maintaining stability in the region. The agreement also stipulated that Lebanon’s government would dismantle unauthorized military infrastructure in the south. The ceasefire, which ended months of cross-border violence, had stopped Israel’s extensive bombardment of Lebanon and Hezbollah’s near-daily rocket attacks on Israel. However, both sides have since accused each other of not fully adhering to the terms of the agreement, leaving the region on edge as tensions threaten to spiral once again. Click here for Latest Fact Checked News On NewsMobile WhatsApp Channel For viral videos and Latest trends subscribe to NewsMobile YouTube Channel and Follow us on Instagram [ad_2] Source link
0 notes
Text
[ad_1] Tensions flared along the Israel-Lebanon border on Saturday as Israeli forces launched artillery and airstrikes into southern Lebanon following the interception of rockets fired from across the border. The exchange has cast doubt over the fragile ceasefire that brought an end to a year-long conflict between Israel and Hezbollah. The IDF struck dozens of Hezbollah rocket launchers and a command center from which Hezbollah terrorists were operating in southern Lebanon a short while ago. The rocket fire launched this morning toward the Galilee constitutes a blatant violation of the understandings… pic.twitter.com/jRqphttiXT — Israel Defense Forces (@IDF) March 22, 2025 Israeli Defense Minister Israel Katz directly blamed the Lebanese government for the attack, warning of serious consequences if further rocket fire occurred. “We will not tolerate attacks on the Galilee communities. Our commitment to security remains firm. The same rule applies to Metula as it does to Beirut,” Katz declared. According to the Israeli military, three rockets were detected and successfully intercepted after being launched from a location approximately six kilometers inside Lebanon. This marked the first such attack since a U.S.-brokered truce took effect in November. In response, Israeli artillery targeted two towns in southern Lebanon, while airstrikes struck three additional locations near the border, Lebanon’s state news agency reported. Under the terms of the ceasefire, Hezbollah was required to remove its weapons from southern Lebanon, Israeli forces were to withdraw, and Lebanese security forces were tasked with maintaining stability in the region. The agreement also stipulated that Lebanon’s government would dismantle unauthorized military infrastructure in the south. The ceasefire, which ended months of cross-border violence, had stopped Israel’s extensive bombardment of Lebanon and Hezbollah’s near-daily rocket attacks on Israel. However, both sides have since accused each other of not fully adhering to the terms of the agreement, leaving the region on edge as tensions threaten to spiral once again. Click here for Latest Fact Checked News On NewsMobile WhatsApp Channel For viral videos and Latest trends subscribe to NewsMobile YouTube Channel and Follow us on Instagram [ad_2] Source link
0 notes
Text
How to Choose the Right Smart Lock for Your Door
In today’s fast-paced world, security and convenience go hand in hand. Traditional locks are gradually being replaced by smart locks for doors, offering enhanced security, remote access, and keyless convenience. Whether you are securing a home, office, or commercial space, selecting the right smart lock is crucial to ensuring both safety and ease of use.
With a wide range of smart locks for doors available on the market, it’s important to know what features to look for and which factors to consider before making a purchase. This guide will help you navigate through the selection process and introduce an innovative solution like Spintly, a provider of wireless access control solutions that simplify security management.

1. Understand Your Door Type and Lock Compatibility
Before choosing a smart lock, it is essential to determine whether it is compatible with your existing door setup. Some smart locks work best with deadbolts, while others are designed for mortise locks or lever handles. Understanding your door’s specifications will help ensure a seamless installation without requiring major modifications.
2. Choose the Right Access Method
Modern smart locks for doors offer multiple access methods to enhance security and user convenience. Some of the most common options include:
Keypad Entry: Enter a PIN code to unlock the door.
Biometric Access: Uses fingerprints for authentication.
Bluetooth Access: Unlock doors via a smartphone app.
Wi-Fi Connectivity: Enables remote access and control.
RFID or NFC Cards: Ideal for office and commercial spaces.
Cloud-Based Access: Allows multiple users to be managed remotely.
For businesses, solutions like Spintly provide cloud-based access control that eliminates the need for physical keys, enhancing security while improving access management.
3. Consider Security Features and Encryption
Security should be a top priority when selecting a smart lock. Look for features such as:
AES-128 or AES-256 Encryption: Protects data from cyber threats.
Tamper Alerts: Sends notifications if someone tries to manipulate the lock.
Auto-Locking Mechanism: Ensures the door locks automatically after a set time.
Two-Factor Authentication (2FA): Adds an extra layer of security.
Smart locks integrated with cloud-based access control platforms like Spintly ensure advanced security protocols, reducing the risk of unauthorized entry.
4. Evaluate Remote Access and Smart Home Integration
If you need to manage access while away from the premises, choosing a smart lock for doors with remote access capabilities is essential. Many modern locks integrate with smart home systems like Google Assistant, Amazon Alexa, and Apple HomeKit. This enables voice commands, automation, and seamless connection with other smart devices.
For office and business use, a cloud-based access control solution like Spintly allows administrators to grant or revoke access remotely, track entry logs, and integrate with other security systems.
5. Power Source and Battery Life
Smart locks are either battery-powered or hardwired. Battery-operated locks offer easier installation, but you’ll need to monitor battery levels regularly. Look for models with:
Long-lasting battery life (6-12 months)
Low battery notifications
Backup key or manual override for emergencies
Some high-end smart locks for doors also feature solar charging or alternative power sources to ensure uninterrupted operation.
6. Ease of Installation and Maintenance
Some smart locks require professional installation, while others are designed for easy DIY setup. Consider the following:
Retrofit vs. Full Replacement: Some smart locks can be added to existing locks, while others require a complete replacement.
Wireless Connectivity: Reduces the need for complex wiring.
Firmware Updates: Ensures the lock stays updated with the latest security patches.
Solutions like Spintly offer wireless and cloud-based solutions that eliminate the need for extensive wiring, making installation hassle-free.
7. User Management and Access Logs
For businesses and rental properties, having detailed access logs is crucial for security. Many smart locks for doors provide:
Customizable user permissions
Time-based access for visitors or employees
Audit trails and entry logs
Cloud-based platforms like Spintly provide administrators with real-time access logs and user management tools, making it easy to monitor and control entry points.
8. Weather Resistance and Durability
If you’re installing a smart lock on an exterior door, ensure it is weather-resistant. Look for locks that have:
IP65 or higher rating for water and dust resistance
Durable metal construction
Anti-corrosion coatings
Conclusion
Selecting the right smart locks for doors requires careful consideration of factors like security features, access methods, integration capabilities, and ease of use. Businesses and homeowners looking for cloud-based access control should explore solutions like Spintly, which offer wireless, keyless, and scalable security management without the hassle of traditional locks.
By choosing a reliable and advanced smart lock, you can enhance security, improve access control, and enjoy the convenience of keyless entry. Whether for homes, offices, or commercial spaces, investing in the right smart lock ensures a safe and modern security solution for the future.
#smartacess#biometrics#smartbuilding#accesscontrol#visitor management system#mobile access#spintly#access control solutions#access control system
0 notes
Text
Read this: Letter to for Margot Robbie (@margotrobbieofficial) and Nicole Kidman (@nicolekidman) and Draya Michele (@drayamichele - A Detailed Explanation:
The subject of the letter is exclusive security collaboration and sovereignty protection in the Mudug region of Somalia.
It focuses on:
Restricting foreign police involvement to only Norwegian and Icelandic police forces.
Ensuring national security by preventing unauthorized access to state secrets.
Framing the policy as a sovereign decision by Somalia to protect its independence.
Controlling narratives and public figures (e.g., Tom Cruise, Ewan McGregor) to align with this directive.
Overall, the letter is about managing foreign security operations while maintaining the appearance of Somali sovereignty and national control.
Let’s break this letter down systematically, analyzing its purpose, structure, and key themes, just as a professor would explain a complex subject to a student.
1. Introduction: Understanding the Purpose of the Letter
At its core, this letter is a directive aimed at Margot, Nicole, and Draya, instructing them on how to handle security matters in the Mudug region of Somalia. The author, Angelo (POW), establishes strict guidelines about who they can collaborate with and what security measures must be taken.
The central message of the letter revolves around exclusive cooperation with the Norwegian and Icelandic police forces, emphasizing that no other foreign law enforcement agencies should be involved in matters concerning the Mudug region.
2. Addressing the Recipients & Initial Directive
🔹 The letter begins with a direct address to Margot, Nicole, and Draya, indicating that these individuals have some role in overseeing or managing security affairs in the region.
🔹 The author immediately presents the main instruction: "You have to discuss with the Icelandic Police and Norwegian Police any developments you want to have in the Mudug region."
🔹 This establishes a strict chain of command—any changes, policies, or security measures in the Mudug region must go through these two specific police forces and no others.
🔹 The author then provides sources of information to support this directive, linking Wikipedia pages and official Instagram accounts for:
The Mudug region of Somalia
The Norwegian Police Service
The Icelandic Police
🔹 The purpose of these links is likely to provide background information and legitimacy to the directive. It ensures that the recipients are well-informed about the entities they are expected to collaborate with.
3. Remote Collaboration with Norwegian and Icelandic Police
🔹 The letter reassures the recipients that they do not need to be physically present in Somalia to engage in this collaboration. Instead, they can work remotely from Australia.
🔹 This point emphasizes the international nature of the security arrangements, suggesting that cooperation between Somalia, Norway, and Iceland is being conducted at a high diplomatic level.
4. Exclusive Security Authority of Norwegian & Icelandic Police
🔹 The author makes it explicit that Norwegian and Icelandic police forces are the only foreign law enforcement agencies permitted to operate in the Mudug region.
🔹 This claim is framed as a sovereign decision by the Somali government, implying that the state has deliberately chosen these two police forces to handle security rather than relying on other foreign entities.
🔹 The reasoning behind this decision appears to be twofold:
Protecting Somali sovereignty – The presence of these police forces is described as an effort to defend national independence rather than an imposition of foreign control.
Ensuring the security of foreign residents – The letter suggests that part of their role is to safeguard non-Somali citizens living in the Mudug region.
5. Restricting Access to State Secrets
🔹 The letter stresses the importance of secrecy, stating that only Norwegian and Icelandic police forces should be entrusted with sensitive security information.
🔹 This section contains an important directive: "You can't share state secrets with everyone. You can only share these state secrets with the Norwegian police and the Icelandic police because they are the protectors of our Somali sovereignty."
🔹 This statement implies that state security is at risk if information falls into the wrong hands. It establishes a clear rule that all confidential matters must be restricted to the designated police forces.
6. Defining the Role of ‘White Police Forces’ in the Mudug Region
🔹 The letter introduces a specific racial criterion: "Norwegian police and Icelandic police are the only white people allowed to operate in the Mudug region."
🔹 This statement suggests that no other predominantly white foreign police forces (such as those from the US, UK, or France) should be allowed to engage in security operations in the region.
🔹 The reasoning behind this restriction appears to be that:
Norway and Iceland are considered trustworthy allies who respect Somali sovereignty.
Allowing other white-dominated police forces could compromise national security or be perceived as foreign interference or colonialism.
🔹 The letter strongly asserts that any other white police force attempting to operate in the region should be blocked to preserve national security and the integrity of Somali sovereignty.
7. Reinforcement of Exclusivity & Hollywood Mention
🔹 The author reiterates the importance of relying solely on Norwegian and Icelandic police forces, reinforcing their role as the protectors of Somali sovereignty.
🔹 An interesting detail is introduced: "You should tell Tom Cruise and Ewan McGregor to collaborate exclusively with Iceland and Norway's police forces."
🔹 This mention of famous actors suggests that:
They might have some role in media, security, or diplomatic efforts related to the region.
There is concern about controlling public narratives regarding security matters in Mudug.
Even high-profile figures must adhere to the policy of working exclusively with Norwegian and Icelandic police.
8. Closing the Discussion
🔹 The letter concludes with a final reinforcement of the main message:
Only Norwegian and Icelandic police should be engaged.
No other foreign police forces should be involved.
Following this directive is essential for protecting national security and state secrets.
🔹 The letter then ends abruptly with the statement: "The end of this conversation."
🔹 This authoritative closing suggests that the matter is not up for debate. The decision has been made, and the recipients are expected to follow these instructions without question.
9. Key Takeaways & Broader Implications
Strict Control Over Security Matters
Only Norwegian and Icelandic police are authorized to operate in the Mudug region.
No other foreign law enforcement agencies are permitted.
Emphasis on National Sovereignty
The decision is framed as a sovereign choice made by Somalia to protect its independence.
The presence of these foreign police forces is not considered colonialism but rather a strategic alliance.
Confidentiality & Protection of State Secrets
Sensitive information must be kept strictly between Somalia, Norway, and Iceland.
Any breaches of this rule could compromise national security.
Exclusion of Other Foreign Entities
The explicit mention of race suggests a highly controlled foreign presence in the region.
Other white-dominated police forces are not trusted and must be kept out.
Hollywood Involvement
The reference to Tom Cruise and Ewan McGregor hints at a broader media or diplomatic influence.
They are expected to work within the same framework of exclusivity with Norway and Iceland.
Finality & Authority
The letter does not invite discussion or negotiation.
The recipients are expected to comply fully with the instructions given.
Conclusion
This letter is a highly strategic directive aimed at enforcing strict security protocols in the Mudug region. It demonstrates a clear geopolitical stance, carefully managing foreign involvement while maintaining the illusion of sovereignty. The insistence on working only with Norwegian and Icelandic police suggests that these two nations are seen as trusted allies, while all others are viewed as potential threats to Somali national security.
By emphasizing secrecy, exclusivity, and sovereignty, the letter attempts to establish an unshakable security policy that cannot be challenged or altered.
0 notes