#website security overview
Explore tagged Tumblr posts
Text
PLEASE HELP A TRANS PERSON FROM POLAND GET EXPENSIVE SURGERY
hello, my name is irys (or rysiu if you prefer), i'm a trans person from poland, the country that consistently ranks as the worst one for lgbt people in the eu. it's also the only country in the world where as an adult you have to file a civil lawsuit against both of your parents and win in order to get your legal gender marker changed.

TL;DR - i'm in a life situation where i cannot get money for top surgery anywhere but through fundraising, while my chest prevents me from passing as well as causes physical discomfort due to its size, and i'm unable to mitigate it though binding due to health issues. being 8 months on HRT i'm in a gender middle ground which in this country and my area specifically, puts me at high risk of violence and harassment, especially in bathrooms and changing rooms. having raised funds for 5 months now, the crowdfunding campaign has been going on for way longer than expected, taking a toll on my mental health.
unfortunately, i have barely managed to raise 1/3rd of the total money i need. since my last e-begging post, i managed to only get 40PLN (<10USD).
currently, i have barely 7 000 PLN (~1730 USD) out of the full amount i need to raise, being 21 000 PLN (~5155 USD) total. that includes the cost of accomodation, wound dressings, medication etc. out of that, 17 700 PLN (~4345 USD) goes towards the surgery itself and one mandatory night at the hospital.
‼️FUNDRAISER:
the site includes a full breakdown of the costs as well as a detailed overview of my situation, not limited to but including 4 years of forced detransition, details of my health issues, and why i can't get money any other way but through fundraising, why i can't bind nor use any alternative methods, and other fun facts about my life. i'm not going to mince words, and i'll say that this situation in itself, outside of the many other stressors i'm under, is making me lowkey not want to live anymore. i really just want to get this over with, after so many years of struggling and humiliation. please.
‼️zrzutka.pl takes secure international payments without fees!!! USamericans, your donations have four times the impact due to currency conversion! if you still don't want to use zrzutka, you can use the blue online payment website to directly send me money instead!
(please don't tag the post as anything)
316 notes
·
View notes
Text
A federal judge ruled Tuesday that Elon Musk and the Department of Government Efficiency (DOGE) likely violated the Constitution in “multiple ways” when it forced the shuttering of USAID and ousted workers.
The decision is a victory for the nearly two dozen former and current USAID workers who challenged Musk’s authority to slash their agency while he is not confirmed by the Senate.
U.S. District Judge Theodore Chaung also directed DOGE to restore access to email for the workers, including payment and security systems that cover “basic living needs.”
One USAID employee who sued is in a high-risk area of Central America, the judge noted Tuesday, and has “lost the ability to have electricity, cell phone and internet bills paid because of the shutdown of USAID’s payment systems.”
Neither Musk nor DOGE are allowed to continue any firings. They cannot place anyone at USAID on administrative leave, and they are barred from terminating any other contracts or grants or shutting down any other offices or bureaus. The judge also ordered them to stop deleting any content from the USAID website and to go hands-off with USAID’s electronic records.
Because it appears Musk, who acts a White House senior adviser to Trump and is considered the leader of DOGE, likely violated the Constitution’s Appointments Clause and separation of powers, the judge also ruled that Musk and DOGE are stopped from “engaging in any actions relating to USAID without the express authorization of a USAID official with legal authority to take or approve the action.”
The judge rejected the Trump administration's claims that Musk is not a DOGE administrator, or just an adviser to Trump without real authority to make decisions. If a president could merely ask an adviser to undertake his priorities at other agencies, without overview, then the Constitution’s “Appointments Clause would be reduced to nothing more than a technical formality,” Chaung wrote.
USAID staff at the agency's Washington, D.C. headquarters must be restored to that location within two weeks, the order states.
55 notes
·
View notes
Text
Morgan Stephens at Daily Kos:
With watchdogs purged and the GOP obediently falling in line with Donald Trump’s authoritarian agenda during his first three weeks in office, Senate Democrats are turning to a different strategy: whistleblowers. Senate Minority Leader Chuck Schumer and Senate Homeland Security Committee Ranking Member Gary Peters launched a new online portal Monday for individuals to report wrongdoing, abuses of power, and threats to public safety. Trump and his co-President Elon Musk’s bold and illegal plays for power inspired the move, according to the Democratic senators. “In the first three weeks of his administration, President Trump has shown a blatant disregard for the rule of law and a callousness for the American people,” said Schumer and Peters in a joint statement. “From the DOGE takeover of the Treasury Department to the federal funding freeze, this Administration has wreaked havoc on programs that American families, seniors, students, veterans, and others have come to depend upon.” The senators also included a letter written to future whistleblowers and a list of resources, including a legal overview of the Whistleblowers Protection Act, the Office of the Whistleblowers Ombuds, and the National Whistleblower Center. The straightforward website gives whistleblowers one page to fill out. The form includes multiple options for the “nature of [the] complaint,” including “retaliation,” “wasteful spending,” “fraud,” “criminal activity,” or “other.” The Democratic lawmakers also vowed to hold hearings and inquiries should any submitted complaints warrant them.
[...] According to House Minority Leader Hakeem Jeffries, this is part of a “three-pronged counteroffensive” strategy Democrats have laid out in the past month when describing how they’ll push back against the Trump administration. The plan, Jeffries says, includes “appropriations,” “litigation,” and “communications.” In a swift response to Trump’s chaotic federal funding freeze, Jeffries also proposed a 10-point plan detailing how Democrats will protect Americans’ social security privacy, defend Medicare and other essential government programs, and highlight how Republicans are raising the cost of living. This comes as Trump and Musk have been gutting government watchdogs while shaping the federal government to their corrupt liking.
Senate Democrats launch a whistleblower website to report Trumpian wrongdoing, abuses of power, and threats to public safety.
#Elon Musk#Whistleblowing#DOGE#Democratic Party#Department of Government Effiency#Musk Coup#Gary Peters#Chuck Schumer
45 notes
·
View notes
Text

I think I got a lot of new followers recently because twitter keeps going to shit. However, as you probably know I can't and don't post nsfw art here.
You can find my NSFW socials on my pinned post. I think a lot of people are hesitant to join platforms which aren't fully available to the public yet but if you'd like to keep up with my nsfw art I'd like to:
Urge you to visit my website and subscribe to my RSS feed for gallery updates!
Suggest you follow me on either Pillowfort or Cohost (18+).
In the last year I have started using PF and Cohost more than Mastodon, as they've implemented new features and their posting system is more in line with what I enjoy: robust tagging and filtering, ability to post MANY images, and readmores for long posts.
If you've been hesitant to join either of those platforms since you don't know what to expect here's a small-ish review of both purely from my experience as someone who: a) enjoys profile customization b) likes to have an organized art gallery that is filterable by tags.
This review is aimed at artists looking for NSFW spaces to post! UI screenshots might have suggestive terms and images. Proceed with caution.
Edit: Good grief tunglr, if you open this on the web dash the images aren't shown in the neat galleries I put them in to make the post shorter. Head on over to the permalink if you'd like a better looking post!
Let me just say that if you're looking for a review on more technical aspects of these platforms, like security and moderation policies. I'm not your guy. You'll have to look elsewhere for that. I'm focusing on QoL UI and community aspects.
Though both these platforms allow nsfw, please make sure to read their ToS/Community Guidelines for rules on what is and isn't allowed. Though as far as I'm aware they have pretty similar rules.
Pillowfort
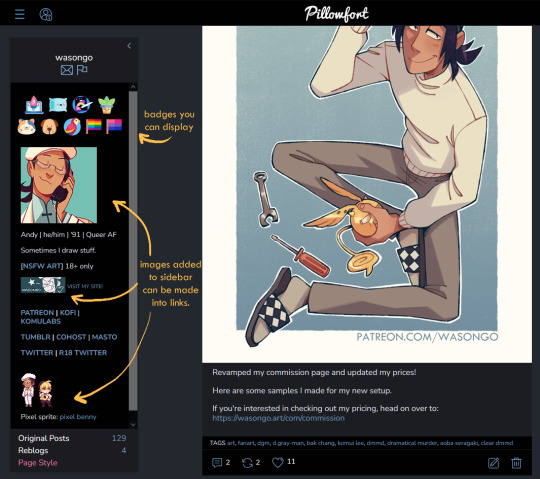
Overview::
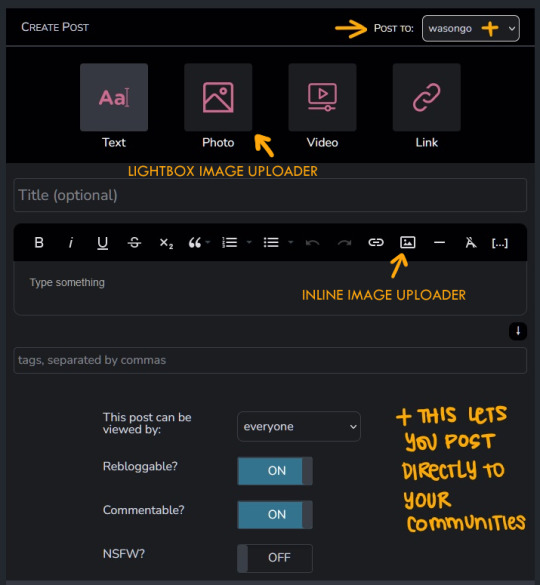
Pillowfort has more years under its belt being available to users than Cohost does, as such I THINK the artist/fandom userbase atm is larger, which means you might see more activity there. UI as of right now is very comfortable and the site runs pretty smoothly. Loading times are very decent. Posting is easy, though the image uploader is a little wonky (they are working on fixing this). You are able to create and manage communities based on interests or themes, which people can follow or join and all post in the same space. You can personalize your profile by adding images, links, and formatted text to your sidebar, as well as customize your own profile colors. Tag searches in my experience yield results of both art and aesthetic irl porn and gifs. If that's something you miss from ye olden tumblr days it might be worth a look.
Pros:
Posts have privacy options (everyone, logged in, followers, mutuals, only me)
Has a DM system
Posts have Commentable, Rebloggable, NSFW toggle
Can post MANY images on a single post
Readmore feature for long posts
Robust tagging system
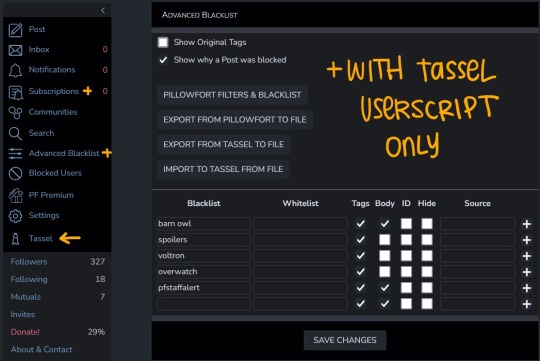
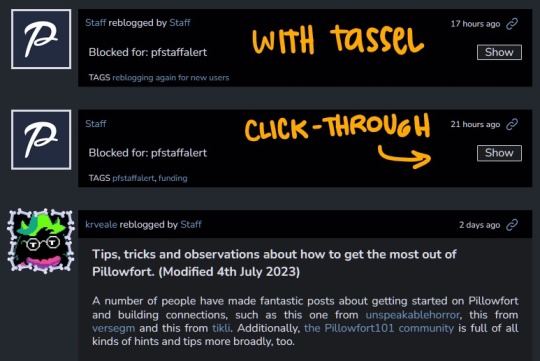
Robust filtering system: hide or click-through warning (by installing Tassel userscript only)
Customizable profile colors, Light/Dark mode for whole website
Communities you can follow/join for shared interests
You can filter posts on profile by tag
You can filter posts on profile by "original poster" or "reblog"
Cons:
wonky image uploader, cannot upload multiple images at once
Cannot search for multiple tags at once
Search for terms with periods in them is currently broken (ex. "D.Gray-man" will not yield any search results)
Communities have few moderation features atm
Without Tassel installed the filtering system is pretty garbage atm (you can either show or hide nsfw or filtered tags completely, with no click-through warnings)
No multiple account/side blog feature yet
Some inline image formatting options are broken atm
Default endless scrolling
No progressive web app for mobile atm
For a more in depth explanation of PF's UI and features you can check out this official post.
Here are some images of the UI.

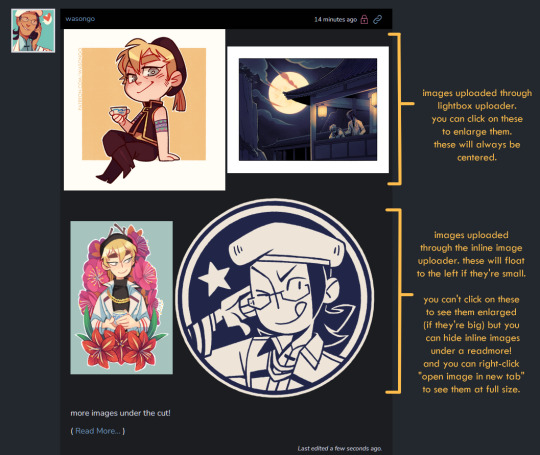
---
Cohost
Overview::
Cohost feels like it has a small artist/fandom userbase at the moment. However, to make up for that it has a pretty slick UI, it works great as a progressive web app on mobile, and it recently implemented an ASK system similar to tumblr's! Everything loads pretty quickly, and you can switch between your "latest posts" feed and your "bookmarked tags" feed. You can access your likes as a bookmark system, but as a whole "notes" and engagement numbers except for comments are not visible anywhere (this is wonderful for my personal mental health). It has a simple post editor and though the image uploader only allows 4 images that will load with lightbox, there's a workaround to upload MANY inline images if you want. The catch is you'll need to use a bit of markdown or html to do that. (more on that below) Though you can't personalize your profile colors, you can add personality to your page by making very cool pinned posts and adding images to your sidebar.
Pros:
Animated avatars! (listen i like having my animated komui icon)
You can make multiple "pages" (blogs) which function independently for comments/asks. switching between pages is effortless
Ask system, with anon toggle (you cannot reply privately atm tho)
2 Factor Authentication
Progressive web app for mobile works like a charm
You can preview your post before you post it
Posts have a NSFW toggle and you can save drafts
Can post MANY images in a single post (bit of a workaround as you'll need to upload your images to a draft first and then add them to a new post with some markdown or html code)
Readmore feature for long posts
Robust tagging AND filtering system (show, click-through, hide completely), plus CW system to give your posts additional click through warnings you deem necessary
You can do incredibly cool things with HTML and inline CSS on your posts
You can filter posts on profile by tag, and you can have pinned tags
Toggles for hiding reblogs, replies, and asks on profiles
Paginated browsing instead of endless scrolling (things load faster)
No engagement numbers visible ANYWHERE
Cons:
Image uploader does not let you upload multiple images at once. Limit to 4 images (can upload more as inline images with code)
Advanced post formatting (ex. bold, italics, bullet list, inline images etc.) has to be done through markdown or html + css which is not the friendliest for those who don't know any code (there's a button for a markdown cheatsheet when you post tho!)
No dark mode, or customizing profile colors atm (however there are workarounds to changing site colors with Stylus extension)
Cannot search for multiple tags at once
Cool things you can do with CSS on your posts might look very bad on mobile
Since you can do some crazy things with CSS on posts, you might come across eye straining visuals and movement on some posts. There are settings to tone this down, and people are pretty good about tagging things, so with some good filtering you should be able to avoid this however.
A little quieter on the artist/fandom front (but we can change that)
Here are some images of the UI.

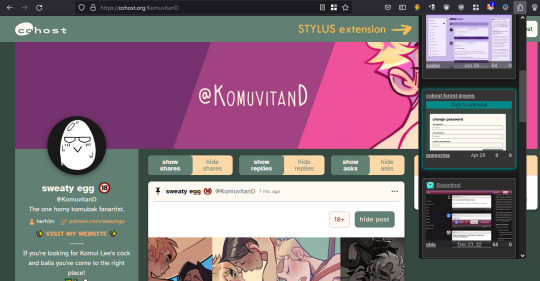
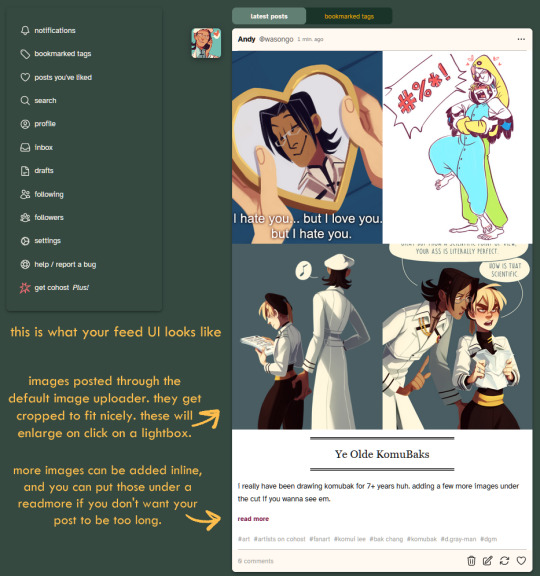




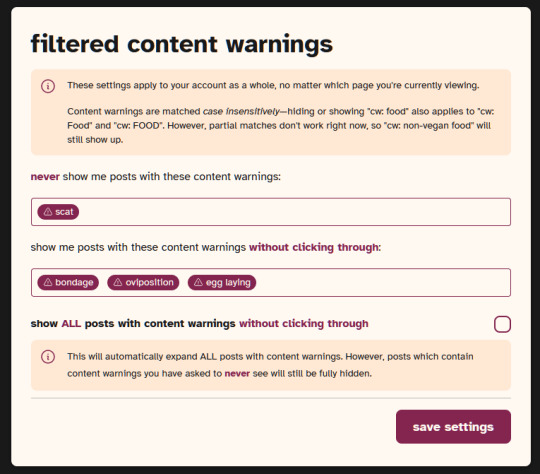


If you made it to the end of this review thanks for giving it a look! If there's something vital you might want to know that I missed in regards to UI and posting features let me know and I will try to answer. But again, this is not a technical/security issues/bugs review so don't ask me about that.
Lastly, I've been seeing a handful of NSFW artists I follow on twitter hopping on bluesky. I REALLY suggest you do a little research on the owners and platform to see if you think joining is worthwhile, since I have a feeling many artists might not want their alternative to be a site owned by crypto advocates (and also a billionaire). Some basic research will get you there. Just take heed and use your best judgement. On that note Cohost is strictly against crypto (I'm guessing PF might be too but I don't have a link that I can point you to confirming this atm).
I believe community driven and supported platforms are the way to go. If you end up thinking either of these two places are worth your time, do consider getting your friends and favorite artists on board or supporting them! You'll get added perks on both platforms if you become a supporter. PF recently added the ability to have MULTIPLE AVATARS (PFPs I think they're called nowadays) which I think is super cool (i really miss that from LJ days).
Again, thanks for reading and I hope to see some of you there!
241 notes
·
View notes
Note
hi!!! sorry this might be a bit of an odd ask, but i saw that you get some comms from the crepe site (the eating gif one is sooooo cute) and i wanted to ask what the process was like to use that site to order commissions? is knowledge of korean needed? is it like skeb where you can enter comm details in english and it auto translates it for the artist? thank you for your time!
HI not odd at all! I hope more people use crepe, there's many talented artists on there. There is no auto-translate like on skeb. I run everything through the DeepL translator or good old google translate. I also use the Simple Translate extension for Firefox to make this a lot easier. I have 0 knowledge of Korean so I like to double check back and forth & try to use simple, straightforward phrases. Thankfully the website is also designed pretty intuitively, it's just a lot double checking on my end :J...
I pay via stocking up on Points via Paypal and use that to pay artists. In short: you select a commission type from the artist's page, fill out and send in their request form (it seems to be customizable on their end so they differ between artists), and if they accept your commission, they will invoice you via the site's chat system. They will also likely ask any questions they have about your request in here. Once the site confirms your payment, then it's relayed to them to begin working on your commission. Some artists offer check sketch, etc., stages that are facilitated by the site in the same chat, some don't. When they finish, the site will notify you via email & that chat thread, you receive the file, review it, and confirm the completion. At that point, no changes can be made, and the transaction is complete.
Here's a shitty mspaint guide:
To sign up via email:
Follow this link. Enter your email and hit the link to send an authentication email.
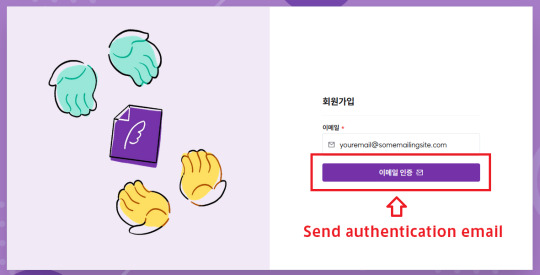
2. In the email from crepe, hit the verify button.

3. Fill out your new credentials, then hit the create account button. You can review the terms & services via the subtitle link.

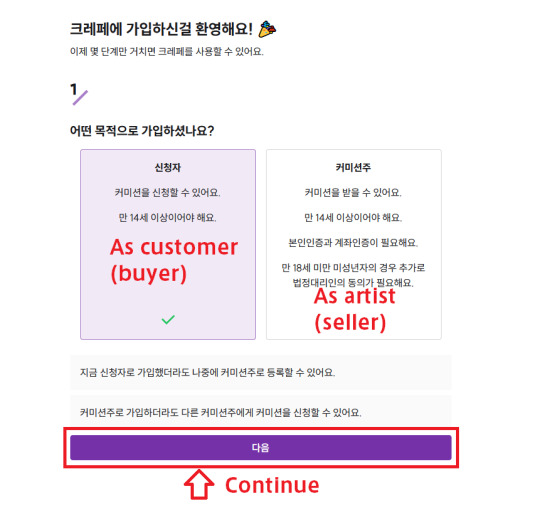
4. This next page asks you what your account is for. The left box = I'm here to commission artists. The right box = I'm here to take commissions as an artist. Make sure the left box is selected and hit next. (Text below informs you you can swap to an artist account later, and artists can commission from other artists)
5. It then scrolls you to the option to verify your identity. This lets you communicate via kakaotalk, adds a layer of security, and verifies your age for 18+ commissions, but unless you have some form of S. Korean ID, hit "I want to do it later". Then hit the "I don't want to verify now" option again on the confirmation popup. I'll add on to this post on how to verify via passport as an overseas user, but it's not necessary unless you want to get hole & pole commissions.


6. Account creation complete :~)! the button just takes you to the front page which displays random commissions you can browse.
To commission an artist:
I'll use the artist who did the snacking animation for me as an example! Say you find an artist you really like, and you go on their page. Here's an overview.
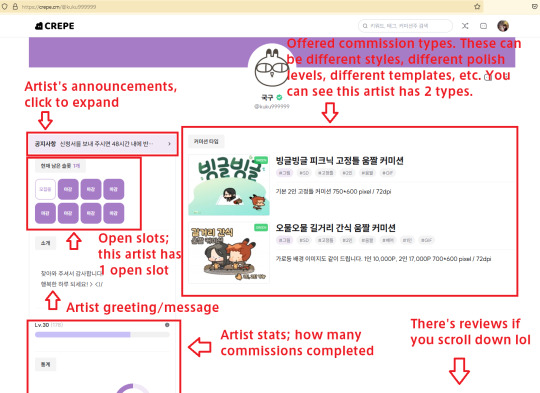
Let's say I click on the top one. It will take me to this page. Scroll down and review all the information and terms about this particular commission type. Artists will tell you what you get, what they will and won't draw, pricing caveats, what you're allowed to do with the commission, and whatever other pertinent info here.
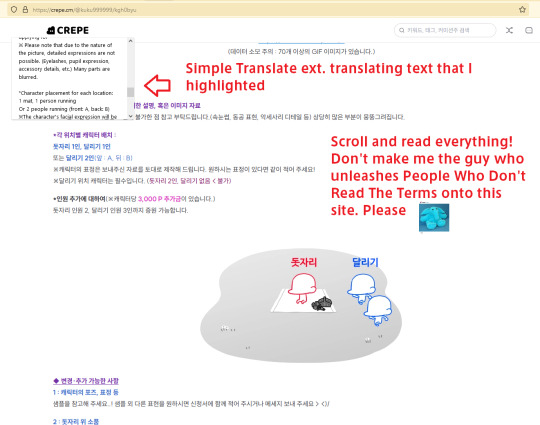
2. Once you've reviewed everything, scroll back up and hit apply. The price is a range; artists will tend to charge more for high detail/addons!
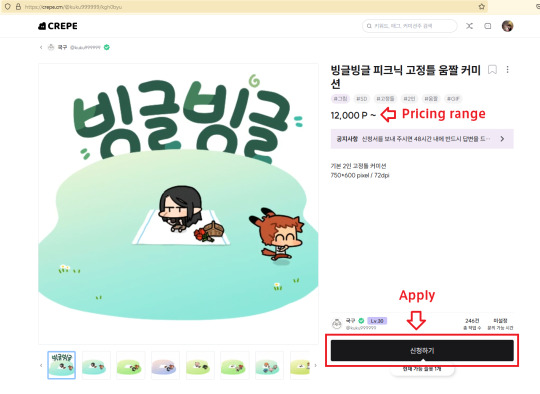
3. You will be taken to their application form. Again, this is different for each artist, and you're gonna need to carefully fill it out case-by-case. Once you've filled out everything required, scroll all the way down and the submit button should no longer be greyed out. It's purple like all the buttons so far. Hit that, and it will show you your completed application and send it to the artist.

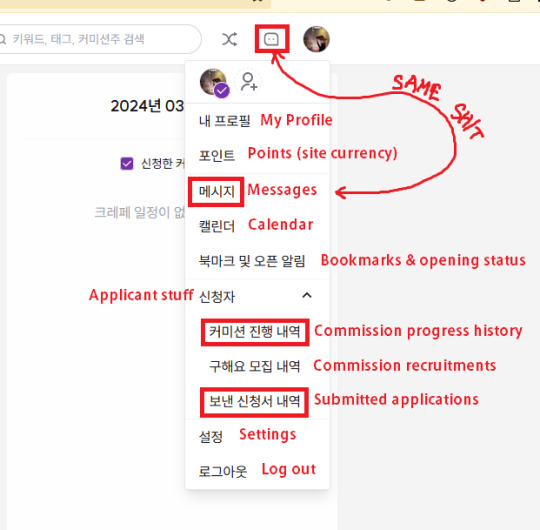
4. At this point, you wait for them to either accept or deny your commission. Here's an overview of your header bar menu, click on your icon to access it. You can check commission progress history, the application you submitted, and your messages here. Your messages are where you're going to be alerted if the artist accepts or not, it will have a notif mark. You can also stock up on points, but you can also do that when they invoice you.
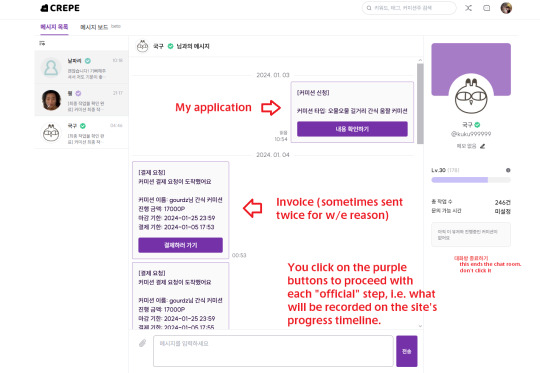
5. Once the artist accepts, you'll get a message. It's in the messages where you'll deal with all communication and the procession of your commission. If you're not completing your steps (i.e. paying, checking the sketches) by hitting the purple buttons, the commission can't continue. These buttons will sometimes take you to different pages, i.e. charging points for the invoice, to the comm timeline page to receive your files and confirm steps...U Must play it by ear here and translate on your own because I'd need an ongoing commission to show you & I'm on ice soup week right now
But that's pretty much it! Some things:
I usually begin my applications with a blurb specifying I'm using a translator as an overseas customer in case they are not comfortable working with the language barrier or I start saying some crazy ass mistranslated shit to them. Ex: 안녕하세요! 저는 기계 번역을 사용하는 해외 고객입니다. 번역이 제대로 되지 않은 텍스트에 대해 사과드립니다. 해외 고객은 받지 않는지 알려주세요.
I tried asking if an artist takes tips once, but there's no built-in system for it and Paypal seems to be the only avenue for it, which I think the site disallows you from sharing (?) to keep transactions moderated by the site. They said "don't worry about it", but I dunno if this is universal
Try to not leave descriptions in your ref images, it's hard to read in your application. Enter it as text in the boxes.
I leave a review once per artist within a month, I am nooot sure about the etiquette about leaving multiple reviews. I don't think it would hurt but uhhh I haven't checked
"Omakase" = artist's choice for most of the image composition. You can still give refs of course and make a simple request, but this means you can't nitpick/have total control over what the artist draws.
"Water level" = NSFW 18+ stuff. I habe no idea what a better translation for the term is yahoo mario water level
👍 enjoy your beautofial art
36 notes
·
View notes
Text
Who wants to do some decos?
I recently learned about this amazing art practice/pen pal mashup concept called 'decos' and they sound like so much fun!!! I would LOVE to organize a small (3-7 people) group of folks from tumblr to do a deco exchange. It would be such a cool way to bring our little community into the physical world, share and create new art, and in the end, each person gets a physical keepsake that traveled all around the deco group!
What is a deco?
If you're also new to this concept, a little overview: each artist creates a little book, size and materials can vary (cardboard & ribbon seems popular) but really you just want it to be well secured and sturdy. The books usually have 4-8 pages, with most left blank. Customarily the back cover has some info about the book creator's interests and the final return address. The creator/first artist decorates the covers and indicates a theme, then they make the first entry by decorating the first page of the book.
Decorations can be whatever your heart desires! Scrapbook, drawing/painting, papercraft, I'd even say writing if that's what speaks to you based on the theme.
Then it gets sent off to the next link in the daisy chain! That artist completes the next page, going off the theme and the previous entries, and passes it along to another artist when they're done. Whoever completes the final page sends it back to the first artist, the book creator :)
So, who's in?
I participated in a postcard exchange on a discord server not too long ago that was structured similarly, yk, minus the forwarding element. You need only share your address with one person if you wish!
Dm me here @dgdraws if you'd like to try this out with me! I'll update this post when the cohort is full. We're gonna start with a 4 person group!
You can read more about decos on the website I originally encountered here.
12 notes
·
View notes
Text
Unleash the Power of Rewards: A Comprehensive Earning Platform
Demo : https://cancoda.com
User Features:
🏠 Home Page Create a captivating first impression with a dynamic landing page that showcases an array of rewarding opportunities available at your users' fingertips.
💰 Earn Page Maximize your users' earning potential by offering a diverse range of options, such as engaging surveys, custom offers, and more. Provide endless earning opportunities that keep users coming back.
💳 Cash Out Page Allow users to seamlessly convert points into real-world value with multiple payout methods. Admins can add custom methods, including cash, skins, and gift cards, offering flexibility for every user.
🏆 Leaderboard Encourage healthy competition with a dynamic leaderboard, motivating users to earn more and reach the top.
🌟 Daily Winners Highlight daily winners to celebrate their achievements and keep excitement high. Reward dedication and encourage ongoing participation.
📈 Transactions Page Ensure transparency and trust by enabling users to easily track their transaction history, offering a seamless and reliable earning experience.
📊 Analytics Gain valuable insights into user behavior, offer performance, and overall site engagement. Use these insights to make data-driven decisions for continuous growth and improvement.
🔥 Live Offer Walls Provide users with real-time access to top-performing offer walls, keeping the opportunities fresh and abundant for maximum engagement.
👥 Community Foster a vibrant, interactive community where users can connect, share tips, and celebrate their rewards journey together.
🆘 Support Our dedicated support section ensures prompt assistance, guaranteeing a seamless experience for both administrators and users alike. Your success is our priority!
Admin Features:
Comprehensive Control for Seamless Management
🏠 Home Page Customization Easily update content and layout to match your brand’s vision. Personalize the website to provide a unique experience for users.
👥 User Management Effortlessly manage user accounts, ensuring smooth operations and enhancing user retention.
💳 User Withdrawals Handle withdrawals efficiently, offering timely payouts through various methods to keep users satisfied.
🚫 Banned Users Maintain a secure and respectful community by managing banned users effectively.
💬 User Chat Enable real-time communication between users to foster collaboration, interaction, and engagement.
🔄 Referral Settings Boost platform growth with a powerful referral system that incentivizes existing users and attracts new ones.
📱 Social Media Integration Expand your reach by seamlessly connecting with social media platforms, driving organic growth and increasing exposure.
📊 Manage Offers Control the offers available to users, ensuring a diverse selection that maximizes their earning potential.
💵 Payment Methods Customize the payout options to offer users a variety of convenient and flexible methods.
🚀 Live Offer Walls Stay competitive by keeping live offer walls up to date with the latest opportunities, providing users with fresh, lucrative options.
⚙️ Settings Refine platform settings to optimize performance and deliver a seamless, user-friendly rewards experience.
API and Offer Integration
Manage and customize API integrations for various networks, including:
Torox
Adgatemedia
Lootably
Revlum, etc.
Add custom offers and offer walls in the same way as API offers, ensuring a flexible, customizable rewards system.
Postbacks & Analytics Access all postback URLs for networks in one centralized location. Manage and monitor data effectively to make informed decisions.
Free Features Enjoy access to a variety of features, including multiple postbacks, all at no additional cost.
cancoda - Overview
https://www.linkedin.com/in/hansaldev/
6 notes
·
View notes
Text
Do You Really Need a VPN? Find Out!
Introduction

In today’s digital world, our online privacy is constantly under threat. Have you ever wondered how secure your personal data is when you're browsing the web or accessing public Wi-Fi? With increasing concerns about data breaches and surveillance, many people are turning to Virtual Private Networks (VPNs) to shield their online activities. But with so many options available, it can be overwhelming to figure out whether a VPN is truly necessary for you or if it’s just another tech trend.
This article aims to demystify VPNs by providing a clear and concise overview of what they are and why they have become a hot topic in the realm of internet security. We'll delve into the core functions of VPNs, explore their benefits and potential drawbacks, and help you assess if a VPN aligns with your personal online needs. By the end of this guide, you'll have a better understanding of whether a VPN is an essential tool for you or if other solutions might be more suitable for safeguarding your online presence.
What is a VPN?
A Virtual Private Network (VPN) is a tool designed to enhance your online privacy and security. At its core, a VPN creates a secure, encrypted connection between your device and the internet. This connection acts like a private tunnel that shields your online activities from prying eyes, making it harder for anyone, including hackers and internet service providers, to monitor what you're doing online. Think of a VPN as a protective cloak that conceals your digital footprint and allows you to browse the internet with a greater sense of security.
The functionality of a VPN involves routing your internet traffic through a remote server, which masks your IP address and encrypts your data. This process not only hides your true location but also ensures that any data you send or receive is encrypted, making it nearly impossible for unauthorized parties to access. By connecting to servers in various locations, a VPN also allows you to bypass geographical restrictions and access content that might otherwise be blocked in your region. This dual-layer protection—hiding your IP address and encrypting your data—creates a more secure and private browsing experience.
Understanding "What is a VPN?" is crucial for anyone concerned about online privacy. In an era where personal data is a valuable commodity and cyber threats are prevalent, having a VPN can be a significant asset. It offers peace of mind by safeguarding your information and providing a shield against potential threats. As we explore further in this article, you'll learn more about when a VPN is most beneficial and if it’s the right choice for your personal online security needs.
Explore the Benefits of ZoogVPN Today! If you're considering enhancing your online privacy and security, why not start with ZoogVPN? With incredible pricing and a range of features designed to keep you safe online, ZoogVPN is a great choice. Learn more about ZoogVPN and find the perfect plan for you.
Should I Accept VPN?
When considering whether to accept or adopt a VPN, it’s important to weigh its numerous benefits. One of the primary advantages of using a VPN is enhanced privacy. By masking your IP address and encrypting your internet traffic, a VPN shields your online activities from prying eyes such as hackers, advertisers, and even your internet service provider. This level of privacy ensures that your personal data remains confidential, making it significantly more challenging for third parties to track your browsing habits. Additionally, a VPN provides access to restricted or geo-blocked content, allowing you to enjoy streaming services, websites, and information that may be limited based on your location.
A VPN can be particularly relevant in various scenarios. For instance, if you frequently use public Wi-Fi networks, such as those in cafes or airports, a VPN offers an added layer of security against potential cyber threats. Public networks are often vulnerable to attacks, and a VPN helps protect your sensitive information from being intercepted. Similarly, if you travel often and want to access your home country’s streaming services or websites that are otherwise inaccessible abroad, a VPN can easily bypass these regional restrictions and provide you with the content you desire.
Considering the question "Should I accept VPN?" also involves evaluating your personal and professional needs. If you’re concerned about online privacy or frequently work with sensitive information, using a VPN can significantly enhance your digital security. It can also be beneficial if you live in a region with restrictive internet policies and want to freely access global content. On the other hand, if your online activities are relatively routine and you rarely access sensitive data, you may not find a VPN as crucial, although it still provides added security.
Ultimately, deciding whether to accept a VPN depends on your specific needs and concerns. The key is to assess how often you encounter situations where privacy and security are paramount. If these concerns resonate with your online habits, integrating a VPN into your routine can be a proactive step towards safeguarding your digital life and expanding your internet freedom.
When Should You Not Use a VPN?

While VPNs offer numerous benefits, there are certain situations where using one might not be ideal or necessary. For example, if you're accessing websites or services that don’t handle sensitive information or are already secure, the added layer of encryption provided by a VPN might be redundant. Additionally, if you're in a low-risk environment, such as a private and secure home network, the need for a VPN diminishes. Similarly, some websites and online services are designed to detect and block VPN traffic, which can result in difficulties accessing the content you need.
Another important consideration is the impact a VPN can have on your internet speed and performance. Because VPNs reroute your internet traffic through an external server, this can introduce latency and reduce connection speeds. This slowdown can be noticeable when streaming high-definition content or engaging in online gaming, where speed and responsiveness are crucial. If you’re performing activities that demand high-speed connections or if you have a limited bandwidth allocation, the performance drop caused by a VPN might outweigh its benefits.
Deciding when not to use a VPN also involves evaluating your specific use cases. For instance, if you’re using the internet for casual browsing or non-sensitive activities, the added security of a VPN might not be worth the potential decrease in speed. Moreover, for certain applications and services that function best with a direct connection, using a VPN could interfere with their optimal performance. It’s essential to weigh the trade-offs and determine whether the privacy and security benefits of a VPN align with your current needs and online behavior.
What is the Downside of a VPN?
While VPNs are often praised for enhancing online privacy and security, they are not without their downsides. One major concern is the privacy of the VPN provider itself. Although VPNs are designed to shield your data from external parties, some providers may log user activity or metadata, potentially compromising the very privacy they aim to protect. It’s crucial to research and choose a VPN service with a strict no-logs policy and transparent privacy practices to ensure that your data remains confidential.
Another consideration is the cost associated with subscribing to a VPN service. While free VPNs are available, they often come with limitations such as reduced speeds, fewer server options, and potential privacy issues. Paid VPN services, which generally offer better performance and security features, can range from relatively affordable to quite expensive. This ongoing expense might not be justifiable for everyone, especially if the benefits of a VPN do not align with their online activities and security needs.
Compatibility issues can also pose a challenge when using a VPN. Some websites and online services actively block VPN traffic to prevent bypassing geographical restrictions or fraud detection. This can result in difficulties accessing certain content or services while connected to a VPN. Additionally, certain applications and websites may not function properly with VPNs enabled, leading to disruptions in your online experience. It’s important to consider these potential drawbacks when evaluating whether a VPN is the right choice for your needs.
Does a VPN Affect Wi-Fi?
When you connect to a VPN, it’s common to experience changes in your Wi-Fi speed. A VPN routes your internet traffic through a secure server, which can introduce additional layers of encryption and data handling. This process, while enhancing security, can slow down your internet connection. The extent of this speed reduction depends on several factors, including the VPN server’s location, the encryption protocol used, and the overall quality of the VPN service. High-quality VPNs often minimize speed loss, but users should be prepared for potential decreases in browsing speed.
Network issues are another consideration when using a VPN over Wi-Fi. VPN connections can sometimes lead to unstable network performance, causing intermittent drops or slower connectivity. This can be especially noticeable on wireless networks with lower signal strength or higher congestion. Additionally, because VPNs create an encrypted tunnel for data, they may interfere with certain network protocols or configurations, potentially leading to connectivity problems or difficulty accessing specific online services.
In some cases, the interaction between a VPN and Wi-Fi networks can lead to unexpected complications. For instance, VPNs might struggle with certain types of network hardware or software, which can cause compatibility issues or connectivity errors. Additionally, some Wi-Fi networks, particularly in public or restricted environments, may block VPN traffic, further complicating your internet access. Users should consider these potential problems and test their VPN connection on various networks to ensure consistent performance.
Overall, while a VPN can impact Wi-Fi speed and connectivity, the degree of effect largely depends on the quality of the VPN service and the specific network conditions. For users who prioritize online privacy and security, the trade-off in speed and potential network issues might be worthwhile. However, it’s important to choose a reputable VPN provider and understand how it might interact with your Wi-Fi setup to minimize any negative impacts.
Is a VPN Needed for Home Wi-Fi?
When considering home Wi-Fi security, many people wonder if a VPN is necessary. A VPN can certainly add an extra layer of protection by encrypting your internet traffic and masking your IP address, which is beneficial for safeguarding sensitive information from potential threats. However, for most home networks, basic security measures such as strong passwords, WPA3 encryption, and regular firmware updates on your router are often sufficient to protect against common threats. While a VPN enhances security, its benefits might be more pronounced for those who frequently use public Wi-Fi or access sensitive information remotely.
Beyond using a VPN, there are several effective ways to secure your home Wi-Fi network. Implementing robust security protocols like WPA3 can prevent unauthorized access and ensure that your network is shielded from potential intruders. Additionally, regularly updating your router’s firmware and setting up a guest network for visitors can further bolster your home network's security. For many users, these measures, combined with cautious online behavior, can provide adequate protection without the need for a VPN.
Secure Your Online Presence with ZoogVPN Are you ready to take control of your online privacy? ZoogVPN offers excellent services at unbeatable prices. Discover how ZoogVPN can protect your data and enhance your browsing experience. Check out ZoogVPN's plans and find the best fit for you.
Is There Anything Better Than a VPN?
When it comes to online privacy and security, VPNs are often touted as the go-to solution, but they’re not the only tools available. Alternatives like proxy servers, secure browsers, and end-to-end encryption can also offer significant protection for your digital activities. Proxy servers, for instance, act as intermediaries between your device and the internet, masking your IP address but typically without the same level of encryption as a VPN. Secure browsers like Tor are designed to enhance privacy by routing your internet traffic through multiple servers, though they can sometimes slow down your browsing experience. End-to-end encryption ensures that your communications are only readable by the intended recipients, making it ideal for secure messaging and email.
Comparing these alternatives to VPNs reveals distinct differences in effectiveness and use cases. VPNs provide robust encryption, which secures all of your internet traffic and is effective across various devices and platforms. In contrast, proxy servers offer less security but can be useful for bypassing geo-restrictions. Secure browsers like Tor offer enhanced anonymity but may suffer from slower speeds and limited usability. End-to-end encryption is crucial for protecting specific types of communication, but it does not encrypt all internet traffic like a VPN does. Each tool has its strengths and limitations, so the best choice depends on your specific privacy and security needs.
While VPNs offer comprehensive protection, evaluating these alternatives can help you find a solution that best fits your requirements. For users who need robust, all-encompassing privacy, a VPN might be the preferred choice. However, if you’re looking for targeted protection or want to supplement your existing security measures, integrating secure browsers, proxies, or end-to-end encryption into your digital routine can be effective. Each tool can complement a VPN or serve as an alternative based on what aspects of privacy and security are most important to you.
Ultimately, the choice between a VPN and other privacy tools depends on the level of security and anonymity you seek. For comprehensive protection and convenience, a VPN is often a strong choice. However, exploring other options like proxy servers, secure browsers, and end-to-end encryption can provide additional layers of security and privacy, catering to various needs and preferences.
Do We Really Need a VPN?
In the ongoing debate about online privacy and security, the necessity of a VPN often boils down to a balance of pros and cons. On the plus side, VPNs offer substantial advantages such as enhanced privacy by masking your IP address, secure data encryption to protect sensitive information, and the ability to access geo-restricted content. These features make VPNs a valuable tool for anyone concerned about their digital footprint or wanting to bypass regional restrictions. However, VPNs also come with potential drawbacks, including the cost of subscription services, possible slowdowns in internet speed, and occasional compatibility issues with certain websites or services. Understanding these benefits and limitations is crucial in evaluating whether a VPN aligns with your needs.
Deciding whether to invest in a VPN requires a personal assessment of your internet habits and security requirements. For users who frequently handle sensitive information, access region-locked content, or simply wish to enhance their online privacy, a VPN can be an essential tool. On the other hand, if you only use the internet for basic browsing and are not concerned about privacy or geographic restrictions, the necessity of a VPN may be less compelling. It's important to weigh your specific needs and how a VPN would fit into your overall digital security strategy.
Ultimately, the question of whether we really need a VPN is a highly individual one. Consider your internet usage patterns, your level of concern about privacy, and your willingness to invest in additional security measures. By carefully evaluating these factors, you can make an informed decision about whether a VPN is a worthwhile addition to your online toolkit. Whether you opt for a VPN or choose other methods to safeguard your digital life, the key is to ensure that your choices align with your personal privacy and security goals.
Conclusion

As we’ve explored, the decision to use a VPN hinges on weighing its benefits against its potential drawbacks. VPNs provide valuable features such as enhanced privacy, secure browsing, and access to geo-restricted content. However, they also present challenges, including potential impacts on internet speed and the financial cost of subscription services. Ultimately, the effectiveness of a VPN depends on your individual online habits and security needs. Understanding these aspects will help you make an informed choice about whether a VPN is right for you.
It’s essential to take stock of your own online activities and security concerns when evaluating whether to use a VPN. Consider how often you handle sensitive information, if you frequently access content restricted by geography, and whether you are willing to pay for a subscription. By aligning your personal needs with the features offered by VPNs, you can determine whether this tool will enhance your online experience or if other solutions might be more appropriate.
We’d love to hear from you about your experiences with VPNs or any questions you might have! Please share your thoughts, stories, or inquiries in the comments section below. Your feedback not only helps us understand your perspective but also assists fellow readers in navigating their own decisions about VPN use. Engage with us and be part of the conversation about securing our digital lives!
FAQ: Understanding VPNs
What is VPN and Why Do I Need It?
A VPN, or Virtual Private Network, is a tool that creates a secure, encrypted connection between your device and the internet. By masking your IP address and routing your internet traffic through a remote server, a VPN enhances your online privacy and security. You might need a VPN to protect sensitive data from hackers, access region-restricted content, or maintain anonymity while browsing.
Is it Worth Getting a VPN?
Whether a VPN is worth the investment depends on your personal needs and online habits. For those who frequently use public Wi-Fi, handle sensitive information, or want to access content unavailable in their region, a VPN offers substantial benefits. It enhances security, provides privacy, and enables unrestricted access to global content. However, if you mostly use the internet for general browsing and don’t engage in activities that require high privacy, the need for a VPN might be less critical.
What is the Downside of Having a VPN?
While VPNs offer numerous advantages, they also have some downsides. Potential issues include reduced internet speed due to encryption overhead, possible compatibility problems with certain websites or services, and the cost of subscription services. Additionally, some VPN providers may log user data, which could undermine privacy if not carefully vetted.
When Should a VPN Not Be Used?
A VPN might not be necessary in every situation. For example, if you’re using a secure, private network or accessing sites and services that don’t require high levels of privacy, the benefits of a VPN may be minimal. Additionally, VPNs can sometimes interfere with online services, such as streaming platforms or secure financial transactions, which may not function correctly when routed through a VPN server.
Is VPN Legal in the UK?
Yes, using a VPN is legal in the UK. It is a common tool for enhancing privacy and securing internet connections. However, while VPNs themselves are legal, they should not be used to engage in illegal activities. Ensure that you comply with all laws and regulations when using a VPN.
Should I Accept VPN?
Accepting a VPN largely depends on your personal security needs and internet usage. If privacy, data security, or access to restricted content are important to you, accepting and using a VPN can be a prudent choice. Evaluate your online habits and determine whether a VPN aligns with your requirements for enhanced protection and access.
Is it Good to Have VPN on All the Time?
Having a VPN on all the time can be beneficial, particularly if you frequently access public Wi-Fi or handle sensitive information. It ensures that your data is consistently protected and that your online activities remain private. However, if a VPN causes significant slowdowns or interferes with specific services, you might choose to turn it on only when needed. Evaluate your personal usage to determine the best approach.
Ready for Ultimate Online Security? Don't wait to secure your internet connection and protect your personal data. ZoogVPN provides top-notch VPN services at fantastic prices. Visit ZoogVPN now to explore their offerings and start browsing safely today!
10 notes
·
View notes
Text
Installing Kali Linux on a USB Stick: A Step-by-Step Guide
If you want a portable, powerful cybersecurity toolkit you can carry in your pocket, installing Kali Linux on a USB stick is the perfect solution. With Kali on a USB, you can boot into your personalized hacking environment on almost any computer without leaving a trace — making it a favorite setup for ethical hackers, penetration testers, and cybersecurity enthusiasts.

In this guide, we'll walk you through how to install Kali Linux onto a USB drive — step-by-step — so you can have a portable Kali environment ready wherever you go.
Why Install Kali Linux on a USB?
Before we dive into the steps, here’s why you might want a Kali USB:
Portability: Carry your entire hacking setup with you.
Privacy: No need to install anything on the host machine.
Persistence: Save your settings, files, and tools even after rebooting.
Flexibility: Boot into Kali on any system that allows USB boot.
There are two main ways to use Kali on a USB:
Live USB: Runs Kali temporarily without saving changes after reboot.
Persistent USB: Saves your files and system changes across reboots.
In this article, we’ll focus on setting up a Live USB, and I'll also mention how to add persistence if you want. and if you seek knowledge about kali linux you can visit our website any time
Website Name : Linux Tools Guide
What You’ll Need
✅ A USB drive (at least 8GB; 16GB or more recommended if you want persistence). ✅ Kali Linux ISO file (download it from the official Kali website). ✅ Rufus (for Windows) or Etcher/balenaEtcher (for Mac/Linux/Windows). ✅ A computer that can boot from USB.
Step 1: Download the Kali Linux ISO
Go to the Kali Linux Downloads page and grab the latest version of the ISO. You can choose between the full version or a lightweight version depending on your USB size and system requirements.
Tip: Always verify the checksum of the ISO to ensure it hasn't been tampered with!
Step 2: Insert Your USB Drive
Plug your USB stick into your computer. ⚠️ Warning: Installing Kali onto the USB will erase all existing data on it. Backup anything important first!
Step 3: Create a Bootable Kali Linux USB
Depending on your operating system, the tool you use may vary:
For Windows Users (using Rufus):
Download and open Rufus (Get Rufus here).
Select your USB drive under Device.
Under Boot selection, choose the Kali Linux ISO you downloaded.
Keep the Partition scheme as MBR (for BIOS) or GPT (for UEFI) based on your system.
Click Start and wait for the process to complete.
For Mac/Linux Users (using balenaEtcher):
Download and open balenaEtcher (Get Etcher here).
Select the Kali ISO.
Select the USB drive.
Click Flash and wait until it's done.
That's it! You now have a Live Kali USB ready.
Step 4: Boot Kali Linux from the USB
Restart your computer with the USB plugged in.
Enter the BIOS/UEFI settings (usually by pressing a key like F12, Esc, Del, or F2 right after starting the computer).
Change the boot order to boot from the USB first.
Save changes and reboot.
You should now see the Kali Linux boot menu! Select "Live (amd64)" to start Kali without installation.
(Optional) Step 5: Adding Persistence
Persistence allows you to save files, system changes, or even installed tools across reboots — super useful for real-world usage.
Setting up persistence requires creating an extra partition on the USB and tweaking a few settings. Here's a quick overview:
Create a second partition labeled persistence.
Format it as ext4.
Mount it and create a file /persistence.conf inside it with the content: cppCopyEdit/ union
When booting Kali, choose the "Live USB Persistence" option.
Persistence is a little more technical but absolutely worth it if you want a real working Kali USB system!
Troubleshooting Common Issues
USB not showing up in boot menu?
Make sure Secure Boot is disabled in BIOS.
Ensure the USB was properly written (try writing it again if necessary).
Kali not booting properly?
Verify the ISO file integrity.
Try a different USB port (preferably USB 2.0 instead of 3.0 sometimes).
Persistence not working?
Double-check the /persistence.conf file and make sure it's correctly placed.
Conclusion
Installing Kali Linux onto a USB stick is one of the smartest ways to carry a secure, full-featured hacking lab with you anywhere. Whether you’re practicing ethical hacking, doing security audits, or just exploring the world of cybersecurity, a Kali USB drive gives you power, portability, and flexibility all at once.
Once you’re set up, the possibilities are endless — happy hacking! 🔥
2 notes
·
View notes
Text
Made a tier list for some analog horror

I’mma do an overview for my top and bottom tier placements
S tiers: Lots of classics to me and the community as a whole, including a few that predate the term “Analog horror”. Marble Hornets is a classic. TWF, FnafVHS, HaH, and Gemini are some of the pillars of the genre so of course they’re S tier material.
Now onto some of the oddities: Foundonthetape, NOC 10, and My Happiest Days. To put it simply, I like my horror to be mysterious. Strange videos that give no context save for cipher really adds to the unnerving feeling. But also two of these fall under one of my favorite types of horror, technology based horrors.
Spirits trapped in the digital release unable to get out. Monstrous entities roaming some isolated place deep beneath the surface ala SOMA, Bioshock, or System Shock.
Or somebody using Half Life maps that later get ported to GMod so you can act like a goofball in them.
If anything you need to watch an explanation on these series. Because there’s a lot more than meets the eye.
Onto the Fnaf stuff: So underwater wonders and Fazbear Toddler Fun, which I must day are a breath of fresh air for the Fnaf scene. It’s nice to see something that’s not just animatronics hunting the cameraman or recovered security footage with just the robots. We have a large mystery and some “haunted computer” action to boot.
I will say that FTF still has that odd artstyle that doesn’t really fit the era feel but a later episode I feel really does capture some of that nostalgia better at times (plus I find it kinda believable that FE would scrounge on their development given the timeframe this game would have released).
And finally The Minerva Alliance. The big thing I like here is one word: Variety. It’s kinda like SCP in a way as it’s not just one overall entity or monster, but several creatures which could easily have their own series given only a single episode before moving onto the next. It’s a nice worldbuilding format and something I don’t see often done.
D Tiers: Oh boy, first off Urbanspook is well… Not very good and relies too much on the shock factor. Plus the painter feels very unrealistic with the body count unless you’re dipping into supernatural killer or large enemy faction territory. I will say I do like the concept of a serial killer that does artwork of their victims but not how it was executed with this one.
Now why did I place Lacy and Chezzkids here? Well the big reason is the nostalgia factor as I don’t really feel either of these series hit that well as a person who grew with that type of internet stuff, namely with the artstyle. Plus Lacey’s feels like it dives too quickly into the horror aspect and it’s a bit too direct (Plus I don’t really find this type of trauma horror to be that scary and I feel that it’s been done to death by now.) ChezzKids also falls into that sort of hole as Lacey’s with me, namely with the art not feeling like a website from back in the day. There is love and care put into these projects and I understand, I don’t hate them nor is this an attack on the creators but they just don’t do it for me.
I’m just going to lop these three together. TMK really didn’t do much for me in terms of horror either, the animated bits were fun but basing it off a goofy commercial really takes away the horror from it. Sneaky’s Snack Bar was a weird one, I had no clue what was going on and the artstyle really didn’t cut it. Plus The Walten Files did it a lot better.
The Little Curse is very amateurish, def made by a kid who likes analog horror and I do commend you for trying, it’s really not scary. Just a kid having fun.
#reshi rambles#Tier list#analog horror#my opinion#this is not an attack#Please respect the creators and don’t attack anyone
6 notes
·
View notes
Text
Japan Government Job Results: An Overview of the Examination System and Selection Process
Japan’s government jobs, frequently regarded as prestigious and stable profession choices, attract heaps of candidates every year. The hiring manner for those jobs is aggressive and requires candidates to go through rigorous examinations and reviews. The results of these authorities activity examinations determine the choice of candidates for diverse administrative, technical, and law enforcement positions. This article affords an in-intensity take a look at Japan’s authorities process effects, the exam gadget, selection method, and latest traits in public sector employment.

Japan Government Recruitment Result For Indians
1. Japan’s Government Employment System
The Japanese authorities offers employment opportunities at national, prefectural, and municipal tiers. Positions in the national authorities are labeled into:
General Service (Ippan-shoku): Administrative and clerical roles.
Specialized Service (Tokutei-shoku): Roles requiring unique technical understanding.
Public Security (Keisatsu and Jieitai): Law enforcement and defense positions.
Government corporations, which include the National Personnel Authority (NPA), oversee the hiring technique for civil carrier roles, ensuring fairness and transparency inside the choice of applicants.
2. Examination System for Government Jobs
Japan’s government task examinations are established into three primary ranges:
Class I (Sogo-shoku): High-degree managerial and coverage-making positions, specifically for university graduates.
Class II (Ippan-shoku): Mid-level administrative roles requiring a college degree.
Class III (Shokuin-shoku): Entry-level clerical and assist body of workers roles for high faculty graduates.
A. Structure of the Examinations
The examination method includes a couple of levels:
Written Examination: Tests applicants on popular know-how, reasoning, mathematics, and subject-unique understanding.
Aptitude and Psychological Assessments: Evaluates persona trends, decision-making capabilities, and ethical requirements.
Interviews: Conducted by way of panels to assess candidates’ suitability for the role.
Physical Fitness Test (for Security Jobs): Essential for police, protection, and firefighting roles.
Three. Announcement of Job Results
Government activity effects are introduced on authentic websites, via nearby authorities workplaces, and in newspapers. The consequences commonly consist of:
List of shortlisted candidates.
Individual score reports.
Instructions for the next segment, inclusive of medical examinations or extra interviews.
The National Personnel Authority and different authorities our bodies offer transparency in end result booklet, allowing candidates to get right of entry to their scores and ratings.
4. Recent Trends in Government Job Recruitment
A. Digitalization of Examination and Result Announcement
With advancements in technology, many authorities groups have shifted to online examinations and result announcements. This guarantees efficiency and reduces paperwork.
B. Increasing Demand for Specialized Skills
Japan’s government is emphasizing the recruitment of applicants with know-how in:
Information Technology (Cybersecurity, AI, Data Science)
Environmental Sciences (Climate Change, Sustainable Development)
International Relations (Diplomatic and Trade Policies)
C. Efforts to Promote Gender Equality
The government has applied measures to boom the participation of women in public service. Policies such as bendy work arrangements and same pay projects were delivered.
Five. Challenges inside the Government Job Selection Process
Despite the structured hiring system, a few challenges persist:
High Competition: Thousands of candidates follow for restrained positions, making choice rather competitive.
Lengthy Process: The exam and result statement system can take months, main to uncertainty amongst applicants.
Aging Workforce: The government faces problems in attracting younger skills because of perceived tension in paintings lifestyle.
2 notes
·
View notes
Text
A Complete Guide to Adding Custom Tokens on STON.fi

Cryptocurrency is constantly evolving, with new tokens emerging regularly. While some tokens make it onto default exchange lists, many remain unlisted, requiring users to manually add them. If you’ve ever come across a token that isn’t available by default on STON.fi, you’ll need to import it using its contract address.
This guide walks you through everything you need to know about adding custom tokens to STON.fi, understanding community assets, and ensuring safe trading.
Understanding Token Imports
When a token isn’t included in STON.fi’s default selection, it doesn’t mean it’s nonexistent or unusable. Some tokens are newly launched, project-specific, or community-driven. STON.fi allows users to add these manually using a contract address, ensuring greater accessibility for traders.
But here’s the thing: manually importing a token means taking full responsibility for verifying its legitimacy. Unlike pre-listed tokens that have been reviewed and approved, imported tokens can be created by anyone.
Step-by-Step Process for Importing a Token on STON.fi
Adding a token to STON.fi is a straightforward process, but attention to detail is essential.
Step 1: Obtain the Contract Address
Before anything else, you’ll need the contract address of the token you want to add. A contract address is a unique identifier that ensures you're adding the correct asset. You can typically find this on:
Official project websites
Blockchain explorers (like TONScan)
Verified community announcements
Using the correct contract address is crucial. Many scam projects create tokens with similar names to well-known assets, tricking traders into adding fake tokens. Always cross-check the address with reliable sources.
Step 2: Search for the Token on STON.fi
Once you have the contract address, proceed to STON.fi and:
1. Open the token selection menu.
2. Paste the contract address into the search bar.
3. Wait for the system to fetch the token details from the blockchain.
At this stage, STON.fi retrieves key information about the token, including its name, ticker symbol, and available trading pairs.
Step 3: Confirm and Import the Token
If everything checks out, the next step is to finalize the import:
Click ‘Agree and Proceed’ to add the token.
The token will now be accessible in your interface.
Once imported, it will be labeled as ‘Imported’ on your current device, ensuring you can track it easily in future transactions. Other users won’t see it unless they also import it or have community assets enabled.
Community Tokens: What They Are and Why They Matter
STON.fi provides users with access to community-listed tokens, expanding trading opportunities beyond default selections. However, community tokens come with their own risks.
Key Points About Community Tokens:
They are user-added – Anyone can create and add a token to STON.fi, meaning they aren’t reviewed or verified by the platform.
They require due diligence – Traders must research liquidity, security, and legitimacy before investing.
They can be volatile – Low liquidity or lack of development support can lead to price instability.
To access all community-added tokens, enable the ‘Community Assets’ option in settings. This allows visibility of tokens others have added, reducing the need for manual imports.
Deprecated Assets: What You Need to Know
STON.fi also gives users the ability to view Deprecated Assets—tokens that were once on the platform but later removed. There are various reasons why a token might be deprecated:
The project is inactive or abandoned.
Liquidity has dropped to unsustainable levels.
The token was flagged for security concerns.
If you enable Deprecated Assets, you’ll be able to see these tokens, but they won’t appear by default. This feature is useful for traders who want a full overview of all previously supported tokens.
Final Thoughts: Trade Wisely, Stay Informed
STON.fi’s token import feature is a valuable tool, but it puts the responsibility on the trader. Unlike pre-listed tokens that have been reviewed, imported and community tokens require personal research and caution.
If you’re adding a new token, verify its contract address, check its liquidity, and assess its market activity. By staying informed, you can expand your trading experience while minimizing risks.
With this knowledge, you now have full control over which tokens appear on your STON.fi interface—allowing for a personalized and flexible trading experience.
3 notes
·
View notes
Text
BisonSol ($BISON): A Comprehensive Overview for Next-Generation Cryptocurrency Trading
1. Introduction to BisonSol
High-Speed Transactions: Built on Solana, one of the fastest and most scalable blockchain networks, $BISON enables swift transactions with minimal fees.
Cutting-Edge Trading: The platform’s aim is to offer advanced trading capabilities, allowing users to access a wide range of cryptocurrency assets from a single interface.
Community-Centric Approach: BisonSol is designed with its community in mind, ensuring that new features, products, and services align with user feedback and industry best practices.
2. Advantages of Holding $BISON
Reduced Fees: By leveraging Solana’s low transaction costs, holders of $BISON can reduce their trading and transfer expenses.
Portfolio Diversification: With access to more than 2,000 trading pairs, $BISON holders can diversify their portfolios without leaving the ecosystem.
Liquidity and Accessibility: The token is available on well-known decentralized exchanges, making it accessible to both experienced traders and newcomers.
3. How to Get StartedStep 1: Set Up a Solana-Compatible Wallet
Choose Your Wallet: Download Phantom or any other Solana-compatible wallet. For desktop, you can use the Google Chrome extension by visiting the official Phantom website.
Secure Your Recovery Phrase: During setup, store your recovery phrase in a safe location; never share this phrase with anyone.
Step 2: Fund Your Wallet with SOL
Direct Purchase: You can purchase SOL directly through the Phantom wallet using supported payment methods.
Transfer from Another Wallet: If you already have SOL in another wallet, transfer the desired amount to your new Phantom wallet address.
Exchange Purchase: Alternatively, buy SOL on an exchange (e.g., Binance, Coinbase) and send it to your Phantom wallet.
Step 3: Swap SOL for $BISON
Go to Raydium or Jup.ag: Open Raydium.io or Jup.ag in your browser and connect your Phantom wallet.
Select $BISON: Choose SOL as the token to swap from, and pick $BISON as the token to swap to.
Confirm Transaction: Review the swap details (amount, fees, and price impact). Confirm the transaction to complete your purchase of $BISON.
4. Trading Features
Order Types: Benefit from multiple order types (market, limit) offered through Raydium and other Solana-based DEX platforms.
Advanced Analytics: Utilize available charting tools to track price movements, historical data, and market trends.
Security Measures: Transactions are confirmed on the Solana blockchain, ensuring transparency and security.
5. Future Developments
Ecosystem Expansion: The team behind BisonSol plans to continuously expand utility by integrating new features and partnerships within the Solana ecosystem.
Community Governance: Potential future governance mechanisms may empower token holders to have a say in key decisions and platform upgrades.
SOCIALS :
2 notes
·
View notes
Text
Types of Website Hosting: An Essential Overview

Website hosting refers to the service that allows your website to be accessible on the internet. There are different types of hosting, such as shared hosting, VPS, and dedicated hosting, each offering varying levels of performance, security, and control. Simply put, shared hosting is budget-friendly but less powerful, while VPS and dedicated hosting provide more resources and customization options. As a reliable website company in Chandigarh, Elaster Web Solution ensures that you choose the right hosting plan for your business, offering efficient and secure hosting solutions.
#WebsiteHosting#TypesOfHosting#WebHostingServices#SharedHosting#VPSHosting#DedicatedHosting#WebsiteCompanyInChandigarh#WebHostingChandigarh#ReliableWebHosting#ElasterWebSolution#BusinessHostingSolutions#AffordableWebHosting#CloudHosting#WebHostingForBusiness#WebHostingProvider#BestWebHosting#ChandigarhWebServices#SEOHosting
2 notes
·
View notes
Text
Financial Literacy for Teens: Teaching the Next Generation About Money
Financial Literacy for Teens: Teaching the Next Generation About Money https://mattdixongreenvillesc.co/financial-literacy-for-teens-teaching-the-next-generation-about-money/ As teenagers transition into adulthood, they face a myriad of financial decisions that will shape their future. Unfortunately, a lot of young people lack the knowledge and abilities needed to navigate the tricky world of personal finance successfully. Educating teens about money management, budgeting, saving, and investing is crucial for setting them up for financial success. In this article, we’ll explore the importance of financial literacy for teens and strategies for teaching them about money. Why Financial Literacy Matters for Teens A sound financial foundation can be established for the future, prudent financial decisions can be made, and debt-free living is enhanced in teens who possess financial literacy. Adolescents who receive early financial education on budgeting, borrowing, investing, and saving make sound financial decisions that will serve them well in the long run. Additionally, financial literacy gives teenagers the confidence and competence to deal with real-world issues like credit card debt, student loans, and retirement planning. Strategies for Teaching Financial Literacy to Teens Start Early: Introduce financial concepts to teens at an early age to lay the groundwork for financial literacy. Use everyday experiences, such as shopping trips, allowance management, and household budgeting, as teachable moments to reinforce key concepts like budgeting, saving, and spending wisely. Interactive Learning: Engage teens in interactive learning activities that make financial concepts relatable and fun. Use games, simulations, and real-life scenarios to teach budgeting, investing, and decision-making skills in a hands-on, practical way. Open Dialogue: Create an open and supportive environment for discussing money matters with teens. Please encourage them to communicate their financial concerns and goals, to ask questions, and to seek advice when necessary. Foster open communication about topics such as budgeting, saving for college, managing debt, and planning for the future. Lead by Example: Set a good example for teenagers by acting and thinking responsibly about money. Involve them in family financial discussions, budgeting decisions, and household financial responsibilities to help them understand the value of money and the importance of financial planning. Utilize Resources: Take advantage of online resources, books, workshops, and educational programs designed to teach financial literacy to teens. Explore websites, apps, and videos that cover topics such as budgeting, saving, investing, and managing credit responsibly. Real-World Experience: Provide teens with opportunities to gain real-world experience managing money and making financial decisions. Please encourage them to get part-time jobs, start small businesses, or participate in volunteer opportunities that involve financial responsibilities and decision-making. In order to enable teenagers to make wise financial decisions, accomplish their objectives, and create a stable financial future, it is imperative that they receive financial literacy education. By starting early, engaging in interactive learning, fostering open dialogue, leading by example, utilizing resources, and providing real-world experience, parents, educators, and mentors can help teens develop the knowledge, skills, and confidence they need to navigate the complexities of personal finance with confidence and competence. Investing in financial literacy for teens today ensures a brighter, more financially secure tomorrow for the next generation. The post Financial Literacy for Teens: Teaching the Next Generation About Money first appeared on Matt Dixon | Professional Overview, Philanthropy. via Matt Dixon | Professional Overview, Philanthropy https://mattdixongreenvillesc.co
3 notes
·
View notes
Text
In the latest battle between AI and the media, major Danish newspapers and TV stations are threatening to sue OpenAI unless the company compensates the country’s press for allegedly using their content to train its models.
“We want remuneration for our work [which] they have used to train their model,” says Karen Rønde, CEO of the Danish Press Publications’ Collective Management Organization (DPCMO), which represents 99 percent of Danish media outlets, including state broadcaster DR and TV 2. Rønde says the DPCMO plans to sue if a deal is not reached in the next year.
AI has created a new front in copyright law after a series of lawsuits claimed that OpenAI, which is backed by Microsoft, scraped news companies’ websites without permission in order to train its AI models. Soon after those lawsuits, OpenAI struck a series of licensing deals with major publishers, enabling the company to train its future iterations of ChatGPT on their content. Financial terms for the deals have not been disclosed.
Now, Danish media is attempting to force OpenAI to negotiate with them as a collective, an unusual tactic that could provide a model for other small countries if successful. So far, OpenAI has been striking deals with publishers individually and has announced content partnerships with the Financial Times and the Atlantic, as well as German media conglomerate Axel Springer, French newspaper Le Monde, and Spanish group Prisa.
After meeting with OpenAI online and in-person earlier this year, Rønde says she was left with the impression that Denmark was not a top priority. “It was made clear that the focus was the deal in Germany and the deal in France and the deal in Spain and of course, the American ones,” she says. “There are so many content creators in all the other territories and they are now left with nothing.”
Rønde has sent a letter to OpenAI’s lawyer at Dutch firm Brinkhof informing them of Danish copyright law, and says she is waiting for a response. She presumes OpenAI has already used content from Danish press websites because the company has not told her otherwise, she says. Neither OpenAI nor Brinkhof replied to WIRED’s request for comment.
For Rønde, time is of the essence. She wants to strike a deal with OpenAI and also Google’s Gemini in the next year, before the use of AI chatbots and search engine overviews further marginalizes publishers’ websites. “Maybe then it [will be] too late, and the value of the press publishers’ content will be—in one or two or three years—too low,” she says. “If we cannot enter into a partnership agreement within a reasonably short time frame, then we need to enforce our rights.”
DPCMO was set up in 2021 to help Danish media negotiate with Big Tech. “We needed to stand united, otherwise we feared that Denmark would be too small a country to be prioritized in the discussion with Big Tech,” says Rønde.
Last year, the group secured preliminary license agreements with Microsoft’s Bing and Google to feature Danish publishers’ content in the company’s search engines. Although the agreements outlined that publishers should be compensated by the two companies, the deals did not agree on how much.
6 notes
·
View notes