#week 3 of configuring a router...send help
Explore tagged Tumblr posts
Text
I finally understand why my job's network engineer lost all his hair and is always three seconds away from tearing out someone's liver.
4 notes
·
View notes
Text
The Future Is Now: Integrating Smart Tech with Solar Panel Installation in Chennai
Today’s homeowners want more than just low EB bills—they want control, automation, and intelligence. That’s why the new trend isn’t just solar… it’s solar-powered smart homes.
If you're considering solar panel installation in Chennai, now is the perfect time to upgrade your energy setup with smart home integration.
Here’s how to combine clean energy with cutting-edge tech—and future-proof your home.
🤖 1. Smart Inverters + Monitoring Apps
Forget manual checks. Today’s inverters:
Sync with your smartphone
Send live generation and usage data
Alert you to faults, shutdowns, or low output
Help you track ROI daily
Brands like Growatt, Enphase, and Solis are leading this space—installed by local experts like HelioStrom.
🏡 2. Power Your Smart Devices with Solar
A properly sized solar system can power:
Alexa-powered lights and fans
Smart ACs with scheduling & motion sensors
IoT devices like video doorbells, sensors, and smart locks
Wi-Fi routers, hubs, and backup systems
Now your automated home becomes a self-sufficient home.
⚡ 3. Auto-Sync with Battery Storage and Load Management
Using a hybrid inverter, you can:
Store excess solar in batteries
Auto-switch to stored power during outages
Prioritize loads (ex: fridge stays on, geyser stays off)
Schedule heavy usage (like EV charging) during peak sunlight
Your home knows when and how to use the sun—without lifting a finger.
🗣️ 4. Voice-Controlled Energy Tracking
Pair your solar system with voice assistants:
“Hey Google, how much solar did we generate today?” “Alexa, switch to battery mode.” “Siri, show energy savings this week.”
Perfect for tech-forward homes in Chennai’s smart villa communities.
📦 5. What You’ll Need
Wi-Fi enabled inverter
Optional home energy monitor (like Sense, Emporia)
Hybrid setup (if using battery)
Smart meter integration (optional with TANGEDCO)
HelioStrom helps configure these systems during solar setup—so you’re ready from Day 1.
🧠 6. Why This Matters in Chennai
Frequent outages in some areas = need for automation
Daytime loads (fans, ACs, pumps) match solar availability
Tech-savvy homeowners expect smart energy dashboards
Resale value of smart solar homes is rising rapidly
Final Word
Solar panel installation in Chennai doesn’t stop at panels. When you add smart tech, you gain full control, live analytics, and lifestyle automation.
Solar gives you power. Smart tech gives you intelligence.
Together? You get a home that saves, thinks, and adapts.
0 notes
Text


05/21/2020 (It's Gemini Season✨💕)
Hello to anyone seeing this post, I hope you are having a wonderful week, hope that those goals you are working hard come good and please, sleep well and drink water (eat well too) that will help a lot if you are dealing with anxiety<3 ✨💕 Sending all the good vibes✨💕
Hola a quienes vean este post, espero que tengan una semana maravillosa, espero que esas metas que están trabajando sean buenas y por favor, duerman bien y beban agua (también coman bien) que ayudarán mucho si tienen ansiedad. <3 ✨💕 Enviándoles todas las buenas vibraciones✨💕
Things i did today:
- An exposition about Psp(Personal software process)
- helped a friend with one of his hw.
-Ttrying again (while writing this post) with a Lab that didn't work yesterday about static router configuration (didn’t ping)
#software engineering#ingenieria de software#it#tech#studyblr#studyblr?#student#personal software process#im sure nobady search for this kinf of tags xD#Happy gemini season#Gemini#virtual classes
14 notes
·
View notes
Text
Monitoring using Sensu, StatsD, Graphite, Grafana & Slack.
At Airwoot, we are in the business of processing & mining real-time social media streams. It is critical for us to track heartbeat of our expansive distributed infrastructure and take timely action to avoid service disruptions.
With this blog post, we would like to share our work so far in creating an infrastructure watchdog and more. We started with following objectives:
Monitor everything under the radar and thereby learn how the system breath.
Use the monitoring framework to collect data and power an internal dashboard for identifying trends.
Alert anything that need attention to appropriate handlers (engineering and client servicing teams).
Let’s dive.
Monitoring Framework
Sensu
Sensu is a feature-packed distributed monitoring framework that executes health checks for applications/services and collects metrics across all connected Sensu clients, which then are relayed to a Sensu server. The checks’ results can be handled differently based on their severity levels. We choose Sensu out of the many monitoring tools available for the following reasons:
ability to write checks and handlers for check failures in any language.
large number of community plugins available and good documentation.
easy horizontal scaling by adding more clients and servers.
it acts as a “monitoring router” that publishes check requests and collects results across all Sensu clients. The results along with their context are directed to custom defined handlers for taking actions based on the criticality of results.
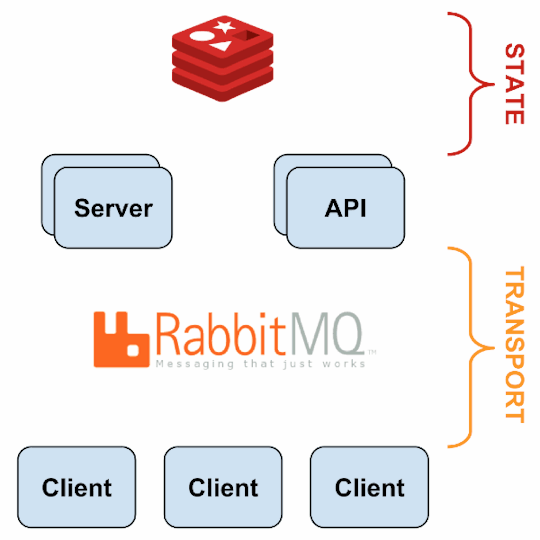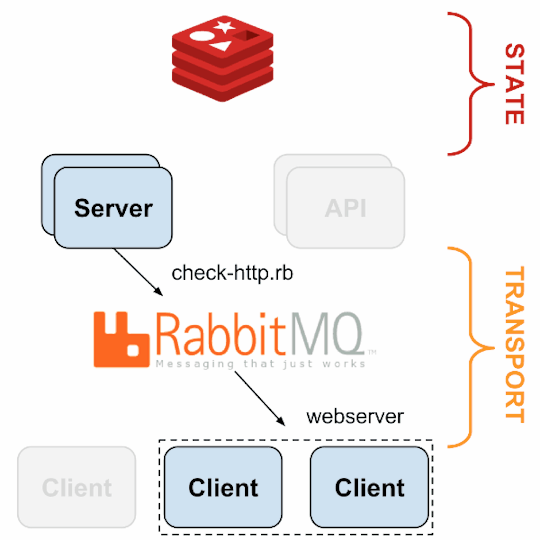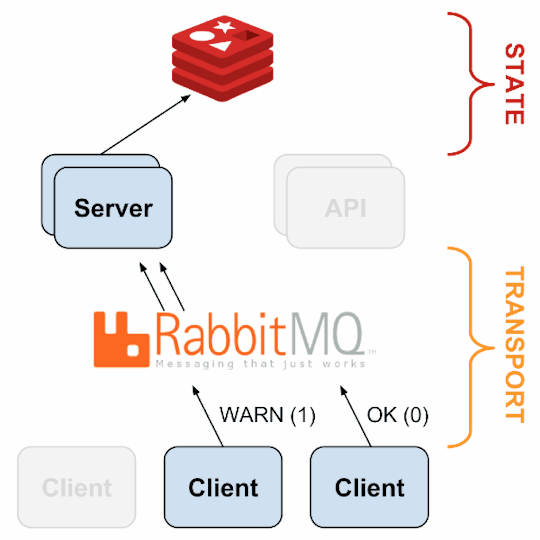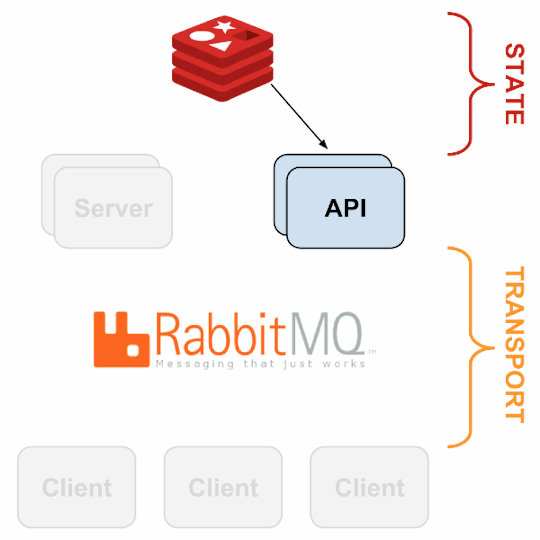
Source: Sensu Documentation - https://sensuapp.org
Sensu has three main components that are executed as daemon processes.
1. sensu-server runs on one or more machines in the cluster and acts as the command center for monitoring. It performs following actions:
schedules periodic checks on clients
aggregates the checks’ results and adds context to them to create events
events can be filtered and passed on to custom defined handlers for taking actions
2. sensu-client can subscribe to group(s) of checks defined on the sensu-server or can have their own standalone checks. sensu-client communicate with the server using the RabbitMQ.
3. sensu-api has a REST interface to Sensu’s data like connected clients, active events, and check results. It also has capabilities to resolve events, remove connected clients, and issue check requests.
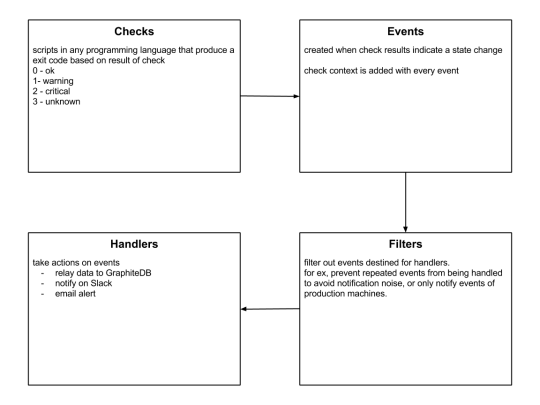
Sensu Entities
StatsD
StatsD is a push-based network daemon that allows a statsD client to collect custom metrics and export them to a collecting server. The catch here is that StatsD uses lightweight UDP protocol for relaying metrics to the metric store, so a slow metric receiver shall not affect application’s performance. We used the Python client for statsD to collect application level metrics.
There are three main data types in statsD:
1. Counters are simply time correlated count of events taking place per unit time. There are incr and decr methods for altering the value of a counter. We extensively used counters to track brand-wise documents from social channels like Twitter and Facebook. Here’s a code snippet for tracking mentions of a brand on it’s Twitter handle:
https://gist.github.com/tanaysoni/76a6de3d7ab3e52b2860
These mentions’ metrics can be displayed at arbitrary time aggregations. Here’s how we did in our Grafana dashboard.
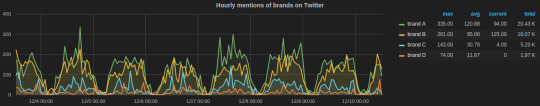
Grafana dashboard showing hourly brands’ mentions on Twitter calculated using StatsD counters.
2. Timers collect numbers times or anything that may be a number. StatsD servers then calculate the lower bound, upper bound, 90th percentile, and count of each timer for each period. We used timers to track the time in fetching social media conversation from Facebook and Twitter. Here’s the graph for the task that fetches comments on brands’ Facebook page:
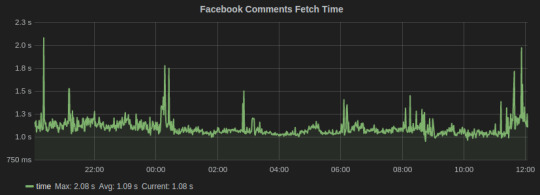
Facebook Comments
3. Gauges are a constant data type that are not subjected to averaging. They will retain their value until changed. We used gauges for computing the delays and queue lengths in our systems.
This is an excellent blog that explains these metrics in detail.
Graphite
Graphite is a database for storing numeric time series data. We use StatsD for collecting metrics, which are then stored in Graphite. There are three software components of Graphite:
1. carbon is a daemon that listens to the time series data. It has a cache that stores values in memory and subsequently flush them to disk at a regular interval. It has configuration files that define the storage schema and aggregation policies for the metrics. It tells whisper the frequency and the history of datapoints to store. We have configured carbon to store most our metrics in a frequency of 10 seconds and for a month’s time. Here’s an example config:
[storm_stats] # name of schema pattern = ^storm_stats.* # regex for matching metric names retentions = 10s:30d # frequency:history for retention
2. whisper is a database library for storing the metrics. The location of whisper files can be set from the carbon-conf file.
3. graphite webapp is the default web-based graphing library provided by graphite, but we used the more powerful Grafana dashboard.
New Relic
Infrastructure monitoring of all EC2 instances including memory, CPU, disks capacity and IO utilization. Many out-of-the-box solutions are available, so we decided not to reinvent the wheel. We have been using New Relic for a while now and it has worked perfectly(well almost!), so decided to stick with it.
New Relic has a quick step-wise guide for setting up. The problem we faced with New Relic is with their “Fullest Disk” alerts which are triggered when disk space of the fullest disk mounted on the machine being monitored is beyond alert thresholds. This fullest disk alert once open prevents alerts for the remaining disk from being triggered.
We solved this problem using Sensu disk check plugin which allows to select the disk(s) to be ignored from the check.
Supervisor
We run all the critical processes on Supervisor. It only has support for processes that are not daemonizing, i.e., they should not detach from the terminal from which they have been started. There are many process control features provided by Supervisor including restart on failures, alerts when set number of restart attempts fails, redirect output of processes to custom log directories, and autostart process on machine reboot.
We have instrumented a Sensu plugin that notifies on Slack if a process crashes. Here’s the code:
https://gist.github.com/tanaysoni/486ef4ad37ea97b98691
Monitoring of Services
Apache Kafka
The official monitoring doc is a good starting point for exploring metrics for monitoring Kafka. We use an open-source plugin released by Airbnb for sending the Kafka metrics to a StatsD server.
We have found the following metrics to be useful that we track,
Request Handler Idle Time, which tells us the average fraction of time request handler threads were idle. It lies in the range of 0-1, and should be ideally less than 0.3.
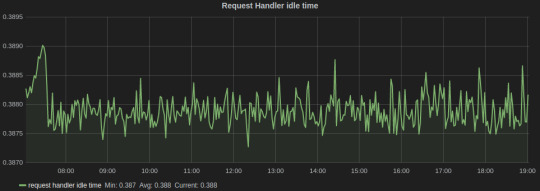
Grafana dash for Kafka
In the above graph, the legends Min, Avg, and Current are added by Grafana. The average value for the entire graph is just under 0.4, which tells us that it’s time to scale our Kafka cluster.
Data/Message Ingestion across all topics helps us to track and comprehend the load on the Kafka servers and how it varies with time.
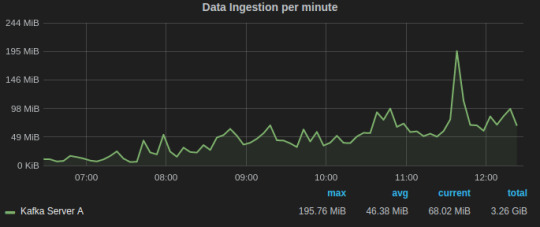
Grafana dash for Kafka request handler idle time
Alerts for Kafka
A Kafka instance runs Zookeeper and Kafka-Server processes. We run them through Supervisor which automatically restarts a process if it crashes and notifies on Slack via Sensu Supervisor check.
Apache Storm
We use Storm to process data that is consumed from Kafka clusters. The command center of our Storm clusters is the Storm UI, which is provided as a daemon process in the official Storm distribution. This blog is a good documentation for Storm UI.
We run all Storm process under Supervisor, which is instrumented with Sensu to alert Slack if any process is not in the running state.
There could be instances when all Storm daemons are running, but the topology might have crashed due to a code-level bug. For this scenario, we have written a Sensu plugin that parses the output of “./storm list” to check if given topology is deployed and activated.
Since, we do stream processing using Storm and Kafka, an important metric is Kafka consumer lag which tells how far is the consumer from the producers. It is essentially the queue length of tuples yet to be consumed by the Storm. There are also Sensu alerts on consumer lag that notifies on Slack if it goes beyond a threshold.
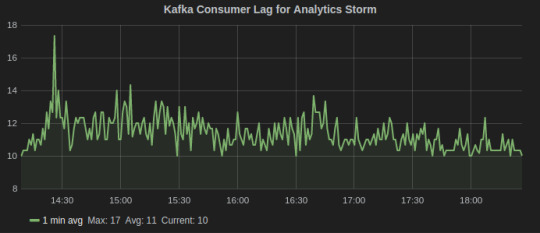
Consumer Lag metric for Kafka-Storm
Gunicorn
Gunicorn comes with a StatsD instrumentation that tracks all the metrics and sends to a StatsD client over UDP. Run Gunicorn with following command line arguments specifying the location of statsD server and an optional prefix to be added to the name of metrics.
gunicorn [ --statsd-prefix sentimentAPI.gunicorn_1] --statsd-host=localhost:8125
We used the following aggregations and transformations in Grafana for the Gunicorn dashboard:
Request status
series sum for all 2xx, 3xx, 4xx, and 5xx response codes
table of avg, current, and total legends help to summarize data for the given time interval
total count of exceptions in the given time range
response time average over one min window
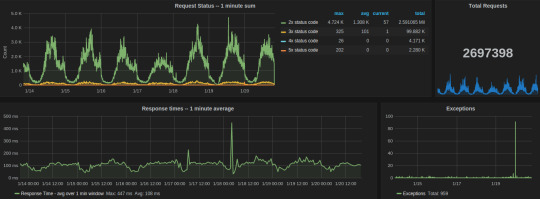
Celery dashboard of last week
MongoDB
MongoDB has in-built set of utilities for reporting real-time statistics on database activities. We leveraged them to built Sensu plugin that periodically parse output from them to sent to a graphite server. These Graphite metrics are graphed on our Grafana MongoDB dashboard.
The two most important utilities are mongostat and mongotop.
mongostat tracks the load on the servers based on database operations by type including insert, update, query, and delete.
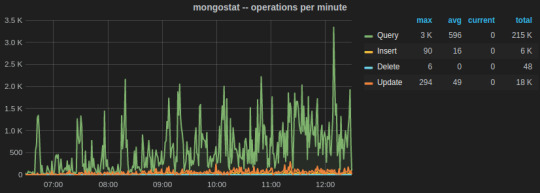
mongotop collect and reports real-time statistics on current read and write activity on a per collection basis. We wrote a Python script to send mongotop metrics to statsD client at an interval of 10 seconds.
https://gist.github.com/tanaysoni/780c4c68447cda8a0a38
Below is a Grafana dash of metrics for a collection graphed over a week time. The peaks and lows corresponds to the business hours, i.e., the reads from the collection were more during the business hours.
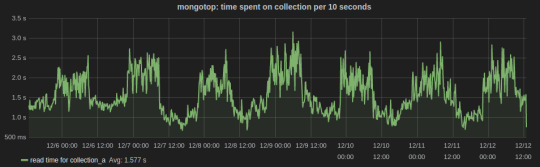
Sensu plugins for MongoDB monitoring
Sensu community has metrics and checks for MongoDB.
PostgreSQL
We are primarily tracking the number of connections including active, idle, and idle in transaction on PostgreSQL. For this, we created a Sensu plugin that runs periodically to fetch data from pg_stat table and output as Graphite metrics that are relayed by Sensu. Here’s the code:
https://gist.github.com/tanaysoni/30dabf820c500a58b860
PostgreSQL also provides built-in Postgres statistics collector, whose data can be relayed to a Graphite database using Postgres Sensu plugins.
Celery
Celery is an integral part of our system. Increase in the queue length beyond threshold is a critical state which the team should be informed of.
We have written a Sensu plugin which fetches the queue length of Celery every minute, which is then relayed to GraphiteDB by Sensu. If the queue length is above our warning thresholds, the team is notified on Slack.
Here’s how the Grafana dashboard for Celery looks like.
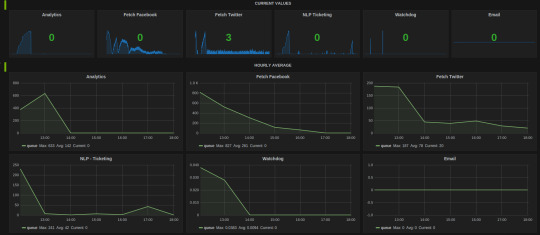
The hourly average summarization in Grafana smooths out the peaks(when bulk tasks get assigned by Celerybeat) to comprehend the load on the Celery cluster. It gives insight as to when to scale the Celery cluster to add more workers.
2 notes
·
View notes
Text
Best 5 Computer Inventory Software Solutions
What Does Computer Inventory Management Software Do?
Computer inventory management is the process of automatic discovery and tracking of computer assets in an organization throughout their life cycle. Computer inventory management software analyzes machines and devices on a network and generates flexible reports with information about the exact hardware and software configuration of each machine or device.
Computer inventory management software solutions target many different use-cases. Some computer inventory solutions are aimed at individual home users, conveniently displaying hardware and software specifications of Windows, macOS, and Linux desktop computers and laptops. Other computer inventory solutions are aimed at IT administrators who look after an entire network of machines and connected devices, helping them plan future hardware and software purchases and diagnose network issues.
Why Should I Use Computer Inventory Software?
Knowing exactly what computers you have, what’s their configuration, and where they are located can be useful for a number of reasons. Every year, businesses around the world waste huge sums of money on unnecessary hardware and software purchases that could have been easily avoided with careful planning supported by reports generated using a computer inventory system.
This affects even young and small companies and not just huge multinational corporations with bloated IT departments. The situation is worse now than ever before because employees are readily encouraged to bring their own devices to work, making it more difficult for the management to plan future purchases.
Many computer inventory software solutions support the tracking of software licenses, which is an invaluable feature for compliance with software license agreements and as a way to prepare for a software license audit.
Considering how complicated the current software license landscape can be, with a multitude of different software licensing models, having a software solution that can automatically send alerts when it detects a compliance issue can not only save a business a lot of time but also a lot of money.
What Are the Best Computer Inventory Software Solutions?
The number of excellent computer inventory software solutions that are available on the market is so large that it can be quite daunting to pick just one. To make things even more complicated, various computer inventory software solutions focus various use cases. We have carefully evaluated all the popular options and selected what we consider to be the top five best computer inventory software solutions currently available.
1. Network Inventory Advisor
Network Inventory Advisor is an all-in-one computer inventory software solution capable of generating flexible hardware and software reports that include Window-, macOS-, and Linux-based devices as well as other network and standalone equipment.
Network Inventory Advisor is agent-less and supports license aggregation, collection, and management for most major software products from more than 500 vendors, including Autodesk, Microsoft, Adobe, and others.
Network Inventory Advisor supports the management of multiple networks, which is perfect for MSPs as it allows them to use just a single installation of Network Inventory Advisor to manage multiple networks and switch between them with a click of a button. With Network Inventory Advisor, it’s possible to easily move, group, regroup and ungroup, reassign, and edit multiple nodes at the same time, and filtering down the network inventory is a matter of a few clicks, as well.
Network Inventory Advisor is priced fairly, with no hidden fees or limitations to worry about, and it’s just as suitable for small and mid-sized businesses as it is for large enterprises. A free trial version of Network Inventory Advisor is available on the official website, allowing anyone to test the software out at 25-node networks for up to 2 weeks.
2. Lansweeper
Lansweeper is a popular agent-less inventory management and software auditing tool with integrated reporting capabilities and automated software deployment. Lansweeper comes with an integrated help desk and IT service desk, making it possible to receive, analyze, and finalize help tickets from a single user interface.
The free version of Lansweeper is limited to only 100 assets and includes only a fraction of the functionality present in any of the three premium versions of the software.
3. Spiceworks IT Asset Management
Spiceworks IT Asset Management is an enterprise-grade computer inventory and network monitoring software system that handles everything from workstations and servers to routers and switches.
Spiceworks can track software licenses so you can stay in compliance, handling even cloud-based services. As an enterprise-grade solution, Spiceworks is less suitable for smaller businesses, who might feel overwhelmed by the sheer number of features the software offers.
4. Asset Panda
Asset Panda is a flexible computer inventory software solution with an intuitive user interface that makes asset tracking and management accessible to anyone. Asset Panda can handle any number of hardware and software assets, and it’s available both online and through a mobile application.
Asset Panda’s customer service is US-based, and anyone can test this popular computer inventory software solution for up to 14 days for free.
5. WinAudit
WinAudit is a simple computer inventory software utility for Windows computers. It’s free and can be distributed by anyone without any restrictions. The main purpose of WinAudit is to create a comprehensive report on a machine's configuration and save it as CSV, RTF,or HTML.
While WinAudit lacks many of the advanced auditing and network management features that make software solutions such as Network Inventory Advisor so popular among network administrators, it’s great for home users and small businesses who can get by with just the basics.
From: Best Computer Inventory Software
1 note
·
View note
Text
Kal1 Cnc Package
New Post has been published on https://autotraffixpro.app/allenmendezsr/kal1-cnc-package/
Kal1 Cnc Package
Buy Now
Don’t waste your hard-earned money following false CNC ‘experts’
Now you can do it easily using basic tools and low-cost components
Make sure your sound is turned on – Click to Play/Pause video
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
Click to get the complete Package NOW for just $194
I’m going to show you these simple secrets…
How to make your CNC router super rigid so it easily cuts aluminum without vibrating, flexing or chattering like crazy
How to choose the right materials, parts and components without wasting tons of money
How to avoid the need for expensive, hard to use machine tools like milling machines and lathes
Read on an I’ll give you my simple-to-follow strategies that avoid the worst and most expensive mistakes DIY CNC builders make.
Turn that CNC router you’ve always wanted into a reality.
You might be thinking that all this information is also available free on YouTube and forums like The CNC Zone.
But you’d be mistaken, because what I’m going to show you is nothing at all like that.
I’m going to tell you exactly what to avoid when building your CNC
And I’ll be giving you all right steps to follow to assure your CNC router build is a success.
I’ll be telling you about…
how to choose the best CNC router configurations and their strengths and weaknesses
which components are right for your build and which are overkill?
how you can start building your own super-rigid CNC router without wasting months and months researching, designing and test building your machine over and over.
I wasn’t always an expert in CNC Router Design, I was pushed into it by circumstances
Dave Field – KAL CNC Strategies
Professional Product Designer
Let me tell you about my own CRAZY CNC journey and how I came to design CNC machines…
It all started a few years ago when I’d approached by my friend Howard about investing in a product.. He liked my idea and had agreed to finance our venture.
Howard had asked me to cut a few aluminum machine parts for one of his clients.
It was a test of my maker abilities and I jumped at the chance.
All I would need was a small 3-axis CNC router to cut the parts and it needed to be rigid to cut aluminum.
I started to look for a suitable machine
I looked at buying a pre-built machine but I didn’t have the cash to buy a good quality one
None of the machines I could afford were rigid enough to cut aluminum.
I looked into sending the job to a machine shop, but their quotes were really high and the lead times were stupidly long for my small job
My only and best option was to build my own CNC Router
All I really needed was a rigid table-top machine because the parts weren’t huge so it made good sense for me to build my own CNC router in-house.
Plus, I really needed to have one in my shop.
I searched high and low for a good information on CNC Router Design
I started researching the best ways to design and build a CNC machine. But I found a huge amount of conflicting information and 10,000 different opinions existed. All the so-called EXPERTS were telling me something completely different.
I was expected to blindly accept what they were telling me, and just hope that it all turned out well.
It was a huge leap of faith, which made me really uncomfortable, but I needed to start producing parts quite quickly.
So, I made some wild educated guesses and got to work on my design.
Then my CNC Build Nightmare began
It took me about 4 weeks to complete my drawings and all the detailed parts list.
It had taken me much longer than I had estimated, because I had to design some parts over and over to get them to work.
Then I ordered all the expensive expert-recommended parts that I could afford, and started my build.
It took a lot of fiddling and back and forth to get the frame together so it was close to straight and level.
Too late, I discovered all those expensive components I had bought needed to be mounted really accurately too.
The mounting surfaces needed to be machined completely flat, which I couldn’t do.
I ended up buying a bunch of expensive tools to try get the mounting surfaces flat but never really managed to get them right.
Finally, after a lot of back and forth, I finished the mechanical build.
Things seemed to be coming along well and I started to wire the machine up.
Then, I hit the next hurdle…
I struggled to find a reliable wiring diagram anywhere. I looked everywhere but no two diagrams I found matched.
I had to design my own wiring diagrams from scratch.
It turned into a real nightmare to get it working and doubts about my abilities started creeping in.
To this day I’m not sure how I managed to get it to run properly. A lot of guessing and testing.
After a super stressful build, I was finally able set up and cut the first batch of parts.
My family hadn’t seen me for weeks!
Finally I started to cut parts…
But my expensive CNC machine wasn’t performing as expected!
When I took the first parts off the machine, I realized that things were really BAD! I knew I was in real trouble.
That beautiful machine I had bet my business future on was flexing, chattering and vibrating horribly when it cut the aluminum.
I tried different feeds and speeds but no matter what I did, it wasn’t rigid enough to cut the aluminum properly.
There was no simple fix, because of the complicated way I had designed the machine. I would need start all over again, and now I was out of time and really low on money.
So, with my back to the wall, I sent the job out to a machine shop.
A week later, they shipped the parts directly to Howard’s client. I had a bad feeling about rushing the machine shop.
I had no choice.
Then my worst fears came true!
Howard called me the next day and my heart just sank when I hear his voice. The machine shop really screwed up. All the tolerances were way off and none of the parts fit.
He backed out of our deal and I can’t blame him, I’d dropped the ball badly!
My reputation was in shreds. By blindly following the ‘experts’, I’d destroyed a good friendship and a promising business relationship.
My whole CNC build was a complete waste – I’d wasted all that money for nothing!
And all I had to show for all my work was a useless and expensive piece of scrap metal in the corner of my shop.
Worst of all is that I’d lost confidence in my abilities.
I crumpled-up my business plan and threw it in the trash and swore I’d never repeat the same stupid mistake again.
Then I locked up my shop and just walked away.
If I was going to live with myself, I only had one way out…
I had to solve the CNC design problem
I knew there just had to be an easy and simple way to approach the CNC problem. I just wasn’t going to let it beat me.
I quickly realized that I needed to trash all the bad ‘expert’ advice and go back to basics.
So I began researching all the machines tools I could find… and study how they were designed and what made them successful.
I looked at a bunch of simple old machine tools and even how WWII fighter planes and weapons were put together. I researched anything I thought would help clear the fog from all those so-called ‘experts’.
I searched for timeless techniques that had worked and produced so many simple and iconic mechanical designs that had served us well for so many years.
I searched for how mechanical designers did it in the times when resources, tooling and labor were really scarce, like during the War.
Those were times when people seem to really excel.
Then I discovered the perfect strategy…
One day I read about Mikhail Kalashnikov, an old Russian weapons designer.
During WWII, he’s the guy who designed the AK47 which is the simplest to build, most manufactured automatic weapon ever produced.
His design was revolutionary, it was super simple to manufacture using the unskilled workers and basic machine tools available to him.
Kalashnikov achieved his iconic design by ignoring all the wisdom of the weapon’s “experts” of the day.
It suddenly all CLICKED, and I knew I’d found a way.
And so I was inspired to developed what I now call my KAL Strategy™
The KAL Strategy™ is a set of simple guiding tips to follow when designing a CNC machine tool.
It’s a system I’ve tested and fine-tuned over time and I’m going to share it with you for free today.
The results have been phenomenal because the KAL Strategy™ simplifies the whole CNC design and build process a lot.
I never really wanted to be a CNC Expert, I was forced into it
I just wanted to build my own working CNC router like many of you people out there.
But I realized, by stupidly throwing away a great business opportunity, that nothing was going to change for me until I worked out a fool-proof, reliable way to prevent it all happening again.
We have a lot in common. As makers and designers, we all face similar day-to-day problems. We just want to get on producing the things we’ve designed.
The only difference is that I’ve managed to work out a simple solution to the CNC problem.
And that’s why you’re here reading this now…
First, you need to understand what the real problem with DIY CNC’s is… …And it’s much bigger than you may think.
Building a own reliable CNC router shouldn’t be difficult…
When I started, I had no idea that it could be so incredible difficult for me to build a professional CNC machine.
I didn’t understand why there are so many badly performing DIY CNC machines exist out there.
Just look at all the failed machines on YouTube and you’ll know what I mean.
You’re going to be surprised because the problem is NOT what you think it is. And to be clear, it’s NOT because you don’t have the right building skills.
We once knew how to do it simply, why not now?
We created so many leading iconic designs that performed beautifully.
But, we left the tracks…
Back in the 1950s our factories were changing over from producing weapons for WWII. The War years were exceptional times, people needed to be enterprising just to survive.
There was no time to make things over-complicated, because lives depended on doing things quickly and simply.
But somewhere along the way, we started to believe that we couldn’t get it done by ourselves. We started to believe that anything of quality had to be designed by engineers and made in a factory.
All the information you’ve needed to build a quality CNC on a budget is nowhere to be found!
It’s not your fault, and here’s the reason why…
There are just no in-depth, simple-to-follow, step-by-step guides available that cut through all the BS and the smoke and mirrors.
Everyone’s trying to sell you overkill components you don’t need
The CNC industry intentionally puts out a lot of marketing misinformation.
They’e not going to tell you that you can achieve similar professional results without using the most expensive components.
They don’t tell you that less-expensive parts can perform well if used correctly. The trick is to know how to use them.
So many builders spend a fortune and end up with a massively over-spec’d, complicated machines that are difficult to build without access to expensive machine tools.
No one is showing you the way through.
Everyone’s trying to sell over-priced and weak CNC kits
Most of these kits have frames built from light aluminum sections to save on shipping costs, and they use cheap and junky linear drive components to save money.
They’re toys and not useable as serious machine tools.
The KAL Strategy helps you avoid a CNC build nightmare
Building a pro-quality CNC router is not for everyone.
It’s for dedicated makers who aren’t afraid to put in the hard work to get a reliable professional result
By following the KAL Strategy™ CNC Cheat Sheet you’ll be avoiding the DIY CNC builders’ worst nightmare, which is having to tear it all apart and start over.
If you are confident of your skills and are prepared to put in hard work, then the KAL Strategy™ – CNC Cheat Sheet is a really useful guide to getting on the right track to designing your own DIY CNC Router.
Once you research and draw up your design and then work out each part, you’ll be able to move ahead with confidence.
You can design your own CNC router, but it takes time and a lot of trial and error
But there’s a MUCH Simpler Way!
You DON’T have to go through those long hours to researching, designing and drawing up to get professional results
Because I’ve put it ALL together for you in one comprehensive package…
You can now skip ALL the trial and error and uncertainty of the CNC design process and start building your CNC right after you read this article.
You can have a professionally designed and tested CNC machine design complete with all plans and drawings and step by step instructions that you need!
There’s now NO need for you to waste your time duplicate all my efforts and reinventing the wheel.
Because I’ve already done all the research, design and drawing for you...
Introducing the KAL1 CNC Package
Everything I’ve learned on my long CNC journey has culminated in this professional CNC router design.
All the methods developed in the KAL Strategy™ have been incorporated into this one of a kind, original CNC machine design.
All the plans and information you willneed to build your own professional level CNC machine are included in the KAL1 CNC package.
The KAL1 CNC Router is unmatched
The KAL1 CNC Router has been specially designed to be super-rigid.
It can easily cut hard metals like aluminum and brass cleanly, and without fuss!
This is why the KAL1 CNC is so UNIQUE…
It’s designed to be a super-rigid and heavy duty CNC router:
It can easily cut hard metals like aluminum and brass!
It’s designed to be inexpensive to build:
KAL1 leverages all the design principles of the KAL Strategy™ to achieve professional results using inexpensive materials and easily available mechanical components.
It’s designed as a compact table-top CNC that doesn’t waste space:
If you don’t have a whole lot of space in your workshop, then the KAL1 is perfect for you.
It’s a compact, heavy-duty, 3-axis CNC router with a useable cutting envelope of 17.75” x 17.75” x 4” (45 cm x 45 cm x 10 cm)
It comes as a complete package with plans and step-by-step instructions:
The KAL1 CNC Package comes complete with all the information and drawings you’ll need to start building your own CNC router.
It’s designed to be incredibly simple to build:
You can easily build the KAL1 CNC with common tools found in most home workshops.
NO exotic and expensive machine tools like milling machines or lathes are required.
It’s designed to looks super-professional, it doesn’t look home-built
People will have a hard time believing it wasn’t built in a factory. That’s because it is designed by a professional product designer.
The KAL1 requires only basic DIY skills to build
Even if you’ve never built anything like it, the KAL1 CNC Package takes all that into account.
Only basic DIY building skills are required to build it.
The KAL1 CNC Package explains the complete build process in depth with simple-to-understand, step-by-step illustrations.
So, you can easily build your KAL1 CNC at an easy comfortable pace.
The KAL1 is a serious machine for serious builders
It takes dedication to build but KAL1 delivers big results
KAL1 CNC isn’t one of those under-structured, thrown-together CNC kits.
It’s a comprehensive, step-by-step guide to building a heavy-duty CNC router based on the KAL Strategy™.
It’s designed for builders and makers who need a professional quality, super-rigid CNC router with superior performance.
So what exactly is the KAL1 CNC Router?
What sets it apart from other desktop CNC routers?
– The KAL1 CNC is super-simple to build, heavy duty and it’s a real budget option…
– KAL1 CNC is one of the easiest to build, tabletop DIY CNC routers.
– It’s designed to be super-rigid so it can easily cut aluminum and other hard materials.
– It’s also one of the least expensive ways to get a heavy-duty, pro-level CNC router into your shop.
All the best machine tool designs are uncomplicated and have super simple manufacturing processes.
The simpler the machine design – the better the machine.
And that’s exactly what you get with the KAL1 CNC Package
Is the KAL1 right for you?
If you’re looking for an easy bolt-together, hobby CNC router to engrave plywood pictures of your cat, then the KAL1 CNC Package is definitely not for you!
If that’s what you’re looking for, close your browser right now, because then the KAL1 CNC Package is not right for you.
So who is the KAL 1 CNC meant for?
It’s for those of you who are ready to stop looking for that easy miracle-in-a-box, silver-bullet CNC Router solution.
It’s for those who are ready to put in the real work that’s needed to build your own super-rigid, professional CNC router.
It’s for makers who are looking for a serious CNC machine to take their skills up a notch.
There are NO shortcuts to getting professional quality in a CNC router. There are NO easy push-button solutions.
But, if you’re looking for a pro quality CNC to serve you well in your shop, and you’re prepeared to put in the solid work…
…then, KAL1 CNC is as easy as it gets!
So if you’re looking for…
A complete start-to-finish CNC router build package with plans in feet and inches and metric measurements
A pro-quality CNC router with a super rigid steel frame that can easily cut aluminum
A complete set of step-by-step assembly drawings with in-depth instructions
A CNC router that’s super-simple to build using easily available components…
…then you are in exactly the right place.
Here’s what you’ll get in with KAL1 Package…
You get the 126-page eBook with 9 in-depth chapters covering the complete KAL1 CNC build from start to finish.
It’s in easy to read PDF format so you can read it on your computer, tablet or phone or print out the drawings.
The eBook contains ALL the easy-to-follow drawings, instructions and files you’ll need to quickly and successfully complete your KAL1 CNC build.
Chapter 1 – Design/Build Approach
Here we go over all the design choices we made when designing the KAL1 CNC.
We go into detail about the different CNC frames
We explain the different linear-motion and drive system types and advantages.
We explain the CNC control box contents and the CNC control software.
Chapter 2 – Machine View Drawings
This chapter has all the assembled machine views so you have a complete detailed reference as you build your KAL1 CNC
Chapter 3 – Fabrication Drawings
This chapter contains all the detailed drawings needed to fabricate each of the parts of your machine.
Every dimension, hole and weld are clearly called out in inches and mm on each of the drawings with full, easy-to-follow notes.
Chapter 4 – Assembly Drawings
This chapter guides you step-by-step through the 28 assembly stages from start to finish.
You’re shown exactly how to assemble each component in simple-to-follow 3D exploded views.
You’re taken through the assembly process for each of the 28 assembly stages, step-by-step…
Nothing is missed out and everything, the placement of every screw and nut is illustrated in complete
Chapters 5 & 6 – Frame Assembly Drawings
These chapters contain the complete set of drawings you’ll need to assemble your CNC router’s steel frame.
There’s a chapter containing all the information for each of the 2 different frame options.
Chapters 7 to 9 – Final Stages
These chapters take you through the final stages of your CNC build.
In these chapters we cover the CNC Control Box layout and how to route all the control and signal wiring in detail.
You also get the Structural Analysis Studies showing how well the steel frame performs under cutting loads.
Plus, with your package you’ll get…
The electronic DXF CAD files of all the CNC mounting plates so you can print them as templates or even cut them on a friend’s CNC router.
A digital file of the official KAL1 logo to give your CNC machine that professional touch.
So, you can see, with your package you’ll have everything you need to start building your own professional quality KAL1 CNC router just minutes after you download the package
And the best part of the KAL1 Package is…
How quick it is to get started
That the KAL1 CNC is really simple to build
How having the package cuts out long months of researching and second guessing
How beautiful and professional the completed KAL1 CNC looks.
Right now, you’re probably curious how much the KAL1 CNC Package is.
You may be thinking that this complete package would cost you over $500.
The good news is, that’s not the case.
When you buy the KAL1 Package today:
You’ll be avoiding those weeks and months of wasted time researching, drawing up and testing your own designs.
You’ll be able to start your CNC build without delays. There are NO unknowns and the path ahead for your CNC build is clearly mapped with NO surprises
All the engineering heavy lifting has already been done for you so you can really enjoy the stress-free building process
So, if you need a super-rigid CNC Router, that performs professionally and easily cuts through aluminum, and you need to build it on a limited budget.
And you need complete step-by-step drawings and instructions in one professionally designed package…
…then the KAL1 Package is right for you
When I first started putting together the package, I decided that a fair retail price would be $297.
But, I’ve changed my mind and I’ll tell you about that in a moment….
To complete your CNC build, you’re going to need to have…
An accurate Bill of Materials (or BOM)
There’s really no way around it, because you’ll be completely lost without it.
Now, you won’t have to do all that work because I’ll be giving you the complete detailed KAL1 BOM as a free bonus!
The KAL1 BOM lists ALL the materials, parts and components with quantities, purchase links and pricing.
You’ll easily be able to order products online by simply clicking on hyper-links next to the products
The BOM by itself is worth $50
Having this pre-made BOM will save you huge amounts of time…
Adding the BOM in, brings the total value of the KAL1 package to $347
Of course, you could just follow the information in the KAL Strategy™ CNC Cheat Sheet to guide your CNC design.
And if you carefully follow all the tips I gave you, it’s possible you may be able to come up with your own working design.
But remember, it could take many long nights and weeks to finish the drawings.
You’ll still need to test each of the designs and make sure they work.
If you choose to go it alone, it could end up costing you 5x or 10x more than the investment you’ll make today.
And that’s NOT what I want for you, because I’ve already been there.
I want get my design out there into the maker community because it’ll end up helping a lot of makers who are just starting out. They need to move up to the next level just like I did.
The only way I’m going to be able to help is to make the KAL1 CNC Package more affordable.
And that’s why I’m discounting the price…
That’s why it’s not going to cost you $347……
It’s not even going to cost you $247……
In just a couple of minutes you can have the full KAL1 CNC Package + Bonuses.
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
Click to get the complete Package NOW for just $194
Here’s my NO RISK promise to you…
I’m so confident that the KAL1 CNC Package is going to work for you, that I’m going to give you a triple, money back guarantee.
If you don’t feel that the KAL1 CNC Package delivers for you in 60 days, I’ll give you your all money back!
For whatever reason, if there’s anything you don’t like about KAL1 CNC Package, I’ll give you your all your money back, NO questions asked!
Even if your neighbor’s dog barks too loud, or your morning coffee gets cold, any reason whatsoever, I’ll give you 100% of your money back
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
Click to get the complete Package NOW for just $194
If all of that hasn’t got you so excited that you click the Buy Button.
I was going to tell you about this bonus on the sales landing page but guess what?
I’m going to tell you what it is right now.
The KAL1 CNC Wiring Diagram
The wiring diagram eliminates all your wiring guesswork and testing headaches.
…and I’m going to include it free with your purchase today…
You won’t find this wiring diagram anywhere, on the internet or in any library.
The KAL1CNC Wiring Diagram took weeks of design and testing to perfect.
I could easily sell it for $50 as a standalone product but, you’re getting it included today as a free bonus.
It’s included free with your KAL1 package!
You get the full electrical wiring diagram showing you exactly how to wire up the KAL1 CNC.
It fully details exactly how to wire the whole machine, including all the limit switches, stepper motors, spindle control and the complete CNC control box.
So, join other successful Makers now!
You’ll be joining the thousands of makers and builders using CNC routers in their shops every day to produce incredible and unique products. They’re making drones, electric guitars, auto and bike parts, signage and thousands of other incredible things.
Their inventions are becoming reality.
Here are just a few of the many amazing things you could make with your KAL1 CNC. The sky’s the limit!
So click on the Buy Button below and moments from now, you’ll be taken to the Buy Page to get your package.
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
Click to get the complete Package NOW for just $194
Here’s how you’ll check out…
When you click on the Buy Button here’s what you’re going to see. You’re going to be taken to our secure Clickbank checkout page. It’s going to look something like this:
You’ll know you’re in the right place when you see the KAL1 CNC Package image:
Notice, our checkout handled via Clickbank and is 100% Secure:
Also, you’ll see your no-risk 60-Day Money Back Guarantee on the Clickbank order screen:
And when you click the Pay Now button:
You’ll then be taken to the Order Confirmation screen.
Simply click on the link and your download will start.
In just a couple of minutes you’ll have the full KAL1 CNC Package on your computer.
The KAL1 CNC Package is in .PDF format and can be read with Adobe Acrobat Reader which is a free download, and other similar programs.
To download your digital files, you will find a link to the KAL1 Download page on the Table of Contents of your eBook.
Without a detailed set of plans and full assembly instructions your CNC Router build can take many, many extra weeks or months to design, draw up and test.
And that’s NOT including the time to choose and search for all the hundreds of parts and components.
And then you’ll still have to research, test and design a complete working wiring diagram.
You could spend hours just staring at a blank piece of paper wondering where you should start.
This is what you’ll be receiving today…
With your purchase you’ll get…
The complete KAL1 CNC Package which includes all the 9 chapters we covered earlier.
You’ll also get the detailed KAL1 BOM listing all the materials part, fasteners and electronic parts, everything you’ll need.
Plus, you’ll get the original .XLS spreadsheet file of the KAL1 BOM so if you ever need to revise it, you can.
You also get the set of fabrication drawings covering each part you will build for your KAL1 CNC
Plus, you get the step-by-step assembly drawings with the easy-to-follow 3d exploded views with written instructions.
Inside we explain how to correctly align the X, Y and Z axes to assure your CNC performs accurately
Plus, you get the detailed design and layout for all the components inside CNC control box.
We show you how to lay out the control boards and power supplies and how to route the wiring so you avoid electrical interference
Plus, included as a bonus is the complete KAL1 CNC Wiring Diagram so there’s no wiring guesswork.
It shows you how to correctly wire and ground every electric and electronic component to avoid any disruptive ground loop problems
Plus, you get DXF CAD files for all the mounting plates, so you can print out full-scale drilling templates or even cut and drill those parts on a CNC router if you choose to
The moment you download your KAL1 CNC Package today, all of this will be yours.
It’s taken us a lot of time, effort and expertise to put this package together.
It easily has a retail value of $347
So, take advantage of this great offer today and get the complete KAL1 CNC Package + Bonuses for an incredibly low price
At this point you have choices to make:
First, you can keep on going it on your own and maybe take 6 months or a year to finish your CNC router build. In fact, you may NEVER get around to building a reliable, working CNC machine.
The second thing you can do is to follow the strategies I gave you in the KAL Strategy CNC Cheat Sheet above. You can use that information to design and eventually build your own CNC router.
Do you really want to go it alone?
Asset 1450 You’ll still need to design and draw up every part for your CNC router and make sure they all to work together perfectly in the end.
Asset 1450 You’ll still have to work out the best way to assemble your CNC machine, to align the components and be sure it will be rigid enough
Asset 1450 And then you’ll still need to spend time choosing and finding parts and creating your own detailed BOM
Asset 1450 And you’ll need to work out a working CNC control box layout and choose the power supplies and the electronic control components
Asset 1450 Then you’ll need to design a working wiring diagram for the control box and how to connect it to the CNC router
Asset 1450 And you still won’t be assured that your steel frame is rigid enough unless you simulate the engineering in a computer engineering program
So make the smart decision
Choose to take advantage of this great offer today!
Click to get the complete Package NOW for just $194
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
If haven’t taken action yet and you’re still reading this, there can only be ONE reason
It’s can’t be price – you know you can afford this and it can’t be the quality of the package…
We’ve shown you that it contains everything you’ll need to easily build your KAL1 CNC
It must be that you still have questions that I’ve missed.
I’ll go through a few in the FAQ below.
You have a full 100% Money Back, 60-Day Guarantee for any reason, no questions asked. There is absolutely NO risk to you.
The KAL1 CNC Package takes into account ALL skill levels and has especially been designed to be forgiving and easy to build. You will just need basic tools and DIY skills.
It all depends on the time you have to put in to it. If you go at it full time and have all the parts and materials pre-ordered, it could be as short as a few days.
The tools required are really basic and there’s a complete list in Chapter 1 of the package.
Any number of things. You can make signage, drone parts, electric guitar bodies, car parts, prototypes, you can even engrave and cut stone with the right cutting bits. The possibilities are endless.
The CNC control software is run on a PC computer and only needs a really basic system. In addition, you will need a CAD CAM program to create your cutting tool paths. I like Autodesk Fusion 360 for which is currently offered free to startups and hobbyists.
The KAL1 BOM included in the package has links to Amazon, eBay and other online suppliers. You can get up to date pricing for parts by clicking the links.
I recommend Linux CNC as I mentioned earlier. It’s downloadable free as a package with the Linux OS and that’s all you’ll need to run the CNC machine.
The KAL1 DIY CNC is specially designed to cut hard materials but it can easily cut wood and plastic. There are bits or end mills designed for the different material types.
Yes, I’ve surveyed what’s available on the market at the time of publication. Kit CNC’s of similar size and capacity sell for 3 or 4 times what the KAL1DIY CNC costs to build and factory-built machines will cost you upwards of 3 to 4 times.
The KAL1 CNC is your best budget CNC router option if you’re looking to build a reliable and serious machine.
There are no comparable CNC packages that I know of on the market.
Everything points to the KAL1 CNC Package being the best available option
So click on the Buy Button below and get started on your own incredible CNC journey in just minutes!
Click to get the complete Package NOW for just $194
One time payment. No hidden charges. (I reserve the right to end this introductory price at anytime without warning)
Click to get the complete Package NOW for just $194
Thanks for taking the time to read about the KAL1
Wishing you the best on your CNC journeys,
Dave Field – KAL CNC Strategies
Professional Product Designer
ClickBank is the retailer of products on this site. CLICKBANK® is a registered trademark of Click Sales Inc., a Delaware corporation located at 1444 S. Entertainment Ave., Suite 410 Boise, ID 83709, USA and used by permission. ClickBank’s role as retailer does not constitute an endorsement, approval or review of these products or any claim, statement or opinion used in promotion of these products.
©2019 KAL CNC Stategies 2019 – Dave Field
0 notes
Link
DarknetA Darknet is an overlay network that can only be accessed with specific software, configurations, or authorization, often using non-standard communications protocols and ports.The Dark Net, Deep Net or The Hidden Internet are anonymous that means you will not be able to know the website owner or to who the website belongs too, Over the usual Internet,A non-indexed website owner or website developer can be tracked by doing some Internet searches or wondering to different sites. However, web pages on the Dark Net or say Dark Web are using the TOR (The Onion Router) network and the foundation of the TOR is to include numerous nodes, so the source is not traceable.
The Deep Web and the DarknetMost people are confused about what exactly the Darknet is. Firstly, the Darknet is sometimes confused with the Deep Web. 'Deep Web' refers to all parts of the Internet which cannot be indexed by search engines, and so can't be found through Google, Bing, Yahoo, and so forth. Experts believe that this Deep Web is hundreds of times larger than the 'surface Web' (i.e., the internet you can easily get to from Google).Birth of the DarknetOctober 29, 1969Charley Kline, a student at the University of California, Los Angeles, types out the first message between computers connected by ARPANET, the Internet progenitor developed by the Pentagon’s Defense Advanced Research Projects Agency.Darknets were able to receive data from ARPANET but had addresses that did not appear in the network lists and would not answer pings or other inquiries.Just a few years later, a number of isolated, secretive networks begin to appear alongside ARPANET. Some eventually become known as "Darknets." Birth of The Onion RouterSeptember 20, 2002Researchers at the U.S. Naval Research Laboratory release an early version of Tor ("The Onion Router"), which conceals the location and IP address of users who download the software. Originally designed to protect the identity of American operatives and dissidents in repressive countries like China, Tor also has another natural constituency: denizens of the darknet.As of 2015 "The Darknet" is often used interchangeably with the dark web due to the quantity of hidden services on Tor's darknet. The term is often used inaccurately and interchangeably with the deep web search due to Tor's history as a platform that could not be search indexed. Mixing uses of both of these terms has been described as inaccurate, with some commentators recommending the terms be used in distinct fashions. Currency of the darknetBitcoin...Bitcoin plays an important role throughout the Darknet. Since staying anonymous is key, Bitcoin is the only currency you can pay with there. Unlike the “normal” web almost every other website has the “Bitcoin accepted” sign displayed on it. Because of Bitcoin’s pseudo-anonymous nature, it’s the perfect currency to power such an ecosystem.on January 3, 2009 A man calling himself Satoshi Nakamoto "mines" the first Bitcoin, a form of untraceable cryptocurrency. Unlike previous digital currencies that failed because there was nothing to prevent users from literally copying their money, Bitcoin makes use of an innovative public accounting ledger that prevents double spending. Unsurprisingly, the cryptocurrency is an instant hit in the darknet, its anonymity making it a perfect tool for money laundering and criminal activity.1 Bitcoin equals 468.53 US Dollar as of 28/may/2016The Uses of DarknetDarknets in general may be used for various reasons, such as:To better protect the privacy rights of citizens from targeted and mass surveillanceProtecting dissidents from political reprisalWhistleblowing and news leaksComputer crime (hacking, file corruption etc.)Sale of restricted goods on Darknet marketsFile sharing (porography, confidential files, illegal or counterfeit software etc.) Access the DarknetAll darknets network require specific software installed or network configurations made to access themTo access the hidden web you need two things – for starter The Onion Browser (also known as TOR Browser) that can access dot onion pages and a search engine or web page that can help you to search the dark web.Recently there are many websites that are known as the deep web directories. Since they are hidden and are unable to search due to the reason that they are not listed correctly. Most of the links on such directories do not guide you where the link will lead to.Here is some software used to access the darknet1) Tor the most popular instance of a darknetSo what is Tor?Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.The Tor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet. Tor's users employ this network by connecting through a series of virtual tunnels rather than making a direct connection, thus allowing both organizations and individuals to share information over public networks without compromising their privacy. Along the same line, Tor is an effective censorship circumvention tool, allowing its users to reach otherwise blocked destinations or content. Tor can also be used as a building block for software developers to create new communication tools with built-in privacy features.What is Tor?Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.Other Popular Deep Web TechnologiesI2P – This is an anonymity network which you may find slightly more techie to install and get running, but once you do there are some great tools and apps, including one to make it easier for you to set up your own hidden blog.FAI (Free Anonymous Internet) – Based on blockchain technology, this network allows for the anonymous publishing and browsing of content and has a social network style homepage that lets you follow other users, share content with your followers, and tip the creators of content you like. FreeNet – One of the older and most highly regarded systems,FreeNet combines deep web with DarkNet. This means that you can maintain a list of trusted peers and either connect to them only, or connect to them in preference to less trusted peers. As far as I know, this gives the highest level of privacy and security of any system, but does require a little more effort to make the most of.ZeroNet – Based on torrent technology in combination with Bitcoin encryption, this is a new system which is not well developed but which I think holds promise for the future.Is this safe to browse the Dark Net?All safety depends on you. What you are looking for? You can create a private chat room where you can talk with your friends, or you can also hire a person for the wet job(for the wrong work). It could be a journalist for exchanging of intelligence documentation, or someone selling illegal drugs. There are also websites that sell unlicensed weapons.If you are willing to analyze the types of sites that are accessible on the darknet, then a majority of web sites usually belongs to the Gangsters. Why, due to the fact that it gives you full anonymity. You will find some forum where people will be talking about suicides, murders and the odd things they did. And If you have a week heart than don’t even think to search that!How to stay anonymous when surfing the DarknetIn order to access the Tor network you have to remain anonymous, this is not a request, it’s a prerequisite. This is done through a special web browser called, surprisingly enough, TOR. TOR stands for “The Onion Router”, it got its name from the fact that in order to reveal the core user of the browser you’ll have to peel a lot of layers off just like an onion.You can use TOR to surf the pedestrian web (the everyday Internet you know ) anonymously, or you can use it to access the Darknet.Here’s the deal:When you access the pedestrian Internet , you are directly communicating with websites. But when you’re accessing a website through TOR it’s like asking another user to ask another user to ask another user to fetch the webpage information for you. This is of course a over simplified explanation but the general idea is that communications bounce around a lot of different computers and it makes it very difficult to track who is actually viewing a website, sending an email or conducting any other action.It also makes the Internet connection extremely slow, but for now here’s what you need to know about TOR:It’s a free to download browser, The browser is built on top of the Firefox browser’s open source code so it’s pretty intuitive. Once you download and launch it it will connect you to the TOR network and you’re good to go.TOR network was initially created by the US military to communicate anonymously. They still dump government files – not open to the general public – on the Darknet. Since the federal and other governments are themselves using the Darknet, they do not consider it feasible to order TOR to shut it down.Additional security – using VPNAlthough no one knows your identity when using TOR, some people like to add an additional layer of protection and connect to TOR through a Virtual Private Network (VPN). The reason is, that even though you’re anonymous, you can still be identified as using TOR for “something”.Important security steps when using the DarknetTurn off running scripts in the TOR options (click the button just before the address bar). This is because most of the sites in Darknet are criminal in nature. If you land on one, they might want to trace you down. And scripts created using JavaScript can be dangerous if they manage to store something on your computer.Think twice before you click any link as you do not know who operates the website and where any of these links lead to. Use only known directories to reach authenticated destinations.DO NOT DOWNLOAD ANYTHING TO YOUR COMPUTER. No BitTorrents and no downloads as they may give away your actual IP when storing things to your computer.This is not for youIn all likelihood, you’ll never need to venture into the Deep Web. The Surface Web contains all the services and tools the average person could ever want. You won’t find any streaming video services or social networks or corporate websites you will feel like you are using the internet on 1990 .months ago few social networks start to appear on the darknet but it's not yet that large and its not for your daily life ! it's a darknet social network ! can you imagine a social network that was made only for mafia men !The Darknet is fraught with bogeymen just waiting for you to let down your guard.you will be an easy target on the darknet for those who are waiting to catch the new victim ! don't be the victim everyone is looking for !But if you ever do need the sanctity of secure communications and true anonymitya level of protection that the Surface Web simply can’t provide then rest easy.Everyone has a voice in the Darknet, down in the depths where even Google’s spiders fear to crawl.This post was written for educational purposes only. If you wish to use the Darknet, do it at your own discretion and at your own risk. Make sure to be aware of any consequences that may follow.
0 notes
Text
Best 5 Computer Inventory Software Solutions
What Does Computer Inventory Management Software Do?
Computer inventory management is the process of automatic discovery and tracking of computer assets in an organization throughout their life cycle. Computer inventory management software analyzes machines and devices on a network and generates flexible reports with information about the exact hardware and software configuration of each machine or device.
Computer inventory management software solutions target many different use-cases. Some computer inventory solutions are aimed at individual home users, conveniently displaying hardware and software specifications of Windows, macOS, and Linux desktop computers and laptops. Other computer inventory solutions are aimed at IT administrators who look after an entire network of machines and connected devices, helping them plan future hardware and software purchases and diagnose network issues.
Why Should I Use Computer Inventory Software?
Knowing exactly what computers you have, what’s their configuration, and where they are located can be useful for a number of reasons. Every year, businesses around the world waste huge sums of money on unnecessary hardware and software purchases that could have been easily avoided with careful planning supported by reports generated using a computer inventory system.
This affects even young and small companies and not just huge multinational corporations with bloated IT departments. The situation is worse now than ever before because employees are readily encouraged to bring their own devices to work, making it more difficult for the management to plan future purchases.
Many computer inventory software solutions support the tracking of software licenses, which is an invaluable feature for compliance with software license agreements and as a way to prepare for a software license audit.
Considering how complicated the current software license landscape can be, with a multitude of different software licensing models, having a software solution that can automatically send alerts when it detects a compliance issue can not only save a business a lot of time but also a lot of money.
What Are the Best Computer Inventory Software Solutions?
The number of excellent computer inventory software solutions that are available on the market is so large that it can be quite daunting to pick just one. To make things even more complicated, various computer inventory software solutions focus various use cases. We have carefully evaluated all the popular options and selected what we consider to be the top five best computer inventory software solutions currently available.
1.Network Inventory Advisor
Network Inventory Advisor is an all-in-one computer inventory software solution capable of generating flexible hardware and software reports that include Window-, macOS-, and Linux-based devices as well as other network and standalone equipment.
Network Inventory Advisor is agent-less and supports license aggregation, collection, and management for most major software products from more than 500 vendors, including Autodesk, Microsoft, Adobe, and others.
Network Inventory Advisor supports the management of multiple networks, which is perfect for MSPs as it allows them to use just a single installation of Network Inventory Advisor to manage multiple networks and switch between them with a click of a button. With Network Inventory Advisor, it’s possible to easily move, group, regroup and ungroup, reassign, and edit multiple nodes at the same time, and filtering down the network inventory is a matter of a few clicks, as well.
Network Inventory Advisor is priced fairly, with no hidden fees or limitations to worry about, and it’s just as suitable for small and mid-sized businesses as it is for large enterprises. A free trial version of Network Inventory Advisor is available on the official website, allowing anyone to test the software out at 25-node networks for up to 2 weeks.
2. Lansweeper
Lansweeper is a popular agent-less inventory management and software auditing tool with integrated reporting capabilities and automated software deployment. Lansweeper comes with an integrated help desk and IT service desk, making it possible to receive, analyze, and finalize help tickets from a single user interface.
The free version of Lansweeper is limited to only 100 assets and includes only a fraction of the functionality present in any of the three premium versions of the software.
3.Spiceworks IT Asset Management
Spiceworks IT Asset Management is an enterprise-grade computer inventory and network monitoring software system that handles everything from workstations and servers to routers and switches.
Spiceworks can track software licenses so you can stay in compliance, handling even cloud-based services. As an enterprise-grade solution, Spiceworks is less suitable for smaller businesses, who might feel overwhelmed by the sheer number of features the software offers.
4.Asset Panda
Asset Panda is a flexible computer inventory software solution with an intuitive user interface that makes asset tracking and management accessible to anyone. Asset Panda can handle any number of hardware and software assets, and it’s available both online and through a mobile application.
Asset Panda’s customer service is US-based, and anyone can test this popular computer inventory software solution for up to 14 days for free.
5.WinAudit
WinAudit is a simple computer inventory software utility for Windows computers. It’s free and can be distributed by anyone without any restrictions. The main purpose of WinAudit is to create a comprehensive report on a machine's configuration and save it as CSV, RTF,or HTML.
While WinAudit lacks many of the advanced auditing and network management features that make software solutions such as Network Inventory Advisor so popular among network administrators, it’s great for home users and small businesses who can get by with just the basics.
Source: https://www.network-inventory-advisor.com/best-computer-inventory-software.html
0 notes
Text
What is the open packet optical switch, Voyager?
Modern web-scale data centers are thirsty for bandwidth. Popular applications such as video and virtual reality are increasing in demand, causing data centers to require higher and higher bandwidths — both within data centers and between data centers. In this blog post, we will briefly discuss the current challenges in the optics space as well as some of the key technical aspects of the Voyager’s DWDM transponders. In part two of this series, we will cover why Voyager is a unique, powerful and robust solution.
The challenges to accommodate longer distances
Within a data center, organizations are adding higher and higher bandwidth ports and connections to accommodate the need for more bandwidth. However, connections that accommodate longer distances between data centers may be limited and expensive. Therefore, a critical requirement for businesses with this challenge is how to support longer distance spans at higher bandwidths over a small amount of fiber pairs.
The optical industry solves the bandwidth problem using Dense Wave Division Multiplexing (DWDM). DWDM allows many separate connections on one fiber pair by sending them over different wavelengths. Although the wavelengths are sent on the same physical fiber, they act as “ships in the night” and don’t interact with each other, similar to VLANs on a trunk. Each wavelength can transport very high speeds (hundreds of Gigabits per second) over very long distances. While this is an incredible feat, today’s DWDM systems are typically closed and expensive. The transponders (which I’ll be explaining in more detail below) are generally the most expensive part of the closed DWDM network.
Announcing Voyager early access
Back in November, we announced the partnership between Cumulus and the open packet DWDM platform Facebook brought to the Telecom Infra Project (TIP), called Voyager, bringing the first open packet optical product to the industry. In just a few weeks, Voyager will officially be available for early access, and we’ll be rolling out a variety of resources for you to get to know the solution in more detail. Voyager is a Broadcom Tomahawk-based switch, similar to Facebook’s Wedge 100, but with added DWDM ports that can connect to another switch tens, hundreds or thousands of kilometers away by adding transponders.
By running Cumulus Linux, Voyager brings all the functionality of Cumulus with it, including BGP, EVPN, OSPF, Layer 2, native network automation and advanced monitoring — right to the optical world in just 1RU. We have also added typical DWDM transponder features, such as configuring power, wavelength, FEC, speed and performance monitoring. And of course, being Cumulus Linux, it’s extremely cost effective too. Finally, integrating L1/L2 and L3 all on Linux may enable you to reduce the number of nodes in the network and unify the entire data center from the hosts to the switches and even to the optical devices!
What is a DWDM transponder?
For reference, a typical active DWDM network is depicted below. Depending upon the use case, all elements below are not required for Voyager deployment. For example, Voyager can also be deployed over dark fiber with no ROADMs.
Voyager is the transponder (TPDR) in the below scenario and is also a Layer2/3 switch with all the functionality of a Broadcom Tomahawk switch with Cumulus Linux.
The transponder lives primarily at the edge of the DWDM network (with some exceptions, like when back-to-back transponders are used as a regenerator) and has a port to connect to a switch or router and a port to connect to the DWDM line system facing the remote end. In some cases, such as Voyager, the transponder could be located within a switch or router (i.e. the same box does switching, routing and transponding).
A muxponder is similar to a transponder, only it also performs time division multiplexing (TDM) over a pre-specified wavelength. For example, with a muxponder, you can send ten 10GigE links over a single 100G wavelength. Voyager will support this functionality as well.
What does a transponder do?
A transponder performs an optical-electrical-optical conversion and is primarily responsible for three tasks:
Converting the “grey” wavelength (850nm, 1310nm or 1550nm) to a pre-specified C-band wavelength and back
Encapsulating/decapsulating the ethernet frame into a layer 1 OTN or OTN-like frame and providing performance monitoring and forward error correction (FEC)
Modulating, transmitting, receiving, demodulating and controlling signal power
After the wavelength leaves the transponders line side port, it is typically multiplexed with other wavelengths and travels through the network over single mode fiber. Any wavelength could be dropped off or added at any site with a ROADM. At the remote end, the signal is de-multiplexed before being handed back to the transponder. The transponder provides performance monitoring, fixes any transmission errors and decapsulates the OTN frame before handing the ethernet frame back to a switch or router or an upper layer.
Voyager combines the transponder with L2/L3 — doing the “ethernet handoff” internally to Voyager itself.
What is a C-band wavelength?
The ITU-T divides the fiber optic communication spectrum (part of the infrared section of the full electromagnetic spectrum) into 6 bands: O, E, S, C, L and U. The attenuation across a single mode fiber optic cable is lowest (0.20-0.25dB/km) at the C-band (or conventional band), so it is primarily used for DWDM communications. Also, low cost Erbium Doped Fiber Amplifiers (EDFAs) help boost signals operating at this range. Voyager will support transmitting/receiving on the C-band.
The C-band wavelength spectrum used by Voyager is shown below:
The Voyager line port can be tuned to use a pre-specified C-band wavelength. It will support tuning at 50GHz spacing and flex spacing at 12.5GHz increments. The channels are fixed and determined at every 12.5GHz or 50GHz along the spectrum, identified by ITU-T G.694.1. With flex grid, they can be chosen by the operator at every 12.5GHz, with the operator being careful not to let the channels sidebands overlap. The sidebands can be different depending on the speed and modulation type of the channel.
What is an OTN or OTN-like frame?
An Optical Transport Network (OTN) frame (or the like) is used with DWDM. An ethernet frame is run inside it for this application.
It looks similar to the following:
As you can see, an OTN frame (which is in the electrical domain) consists of three overhead layers and they are analogous to SONET Line, Section and Path overheads:
Optical Transport Unit (OTU): Between optical network elements
Optical Data Unit (ODU): Network level
Optical Path Unit (OPU): Responsible for end-to-end
It also offers Forward Error Correction (FEC) and OAM&P (performance monitoring) capabilities within the overheads. Using amplifiers (specifically EDFAs) in a network can increase noise, thereby reducing signal quality and creating potential errors. FEC is used to correct the errors.
Several FEC algorithms exist in the industry today. Generally, the Soft Decision (SD) FECs can correct more errors than Hard Decision FECs, so the optical network can push longer distances at faster speeds with an SD-FEC. Voyager will run an SD-FEC.
Performance monitoring consists of reporting and keeping track of when there are errors in the network. For example, it keeps track of the pre-FEC bit error rate (BER), which is how many errors the FEC had to correct to be able to deliver a clean frame up to the higher layers. All of these characteristics can tell an operator if the network has issues, such as a degrading amplifier.
What is modulation and transmitting?
A transponder/muxponder is also responsible for modulating the signal and transmitting the signal at the appropriate power level. Transmitting at too little power won’t drive very far, and transmitting at too much power can distort the signal. Voyager will be able to effectively transmit up to +2.5dBm.
Different modulations are typically used with different bit rates. For example, lower bit rates at or below 10Gbps may use on-off keying (OOK). OOK is a simple modulation method that turns light on to signify a binary “1” and turns light off to signify a binary “0”. In this scenario, the bit rate and the symbol (baud) rate (signals through the fiber) are the same. Phase Shift Keying (PSK) uses the same idea, but instead of changing the power of the signal, it changes its phase to denote a binary “0” or “1”.
As we get to higher and higher bit rates, we want to keep the baud rate low to minimize distortions while increasing the bit rate we send. This leads to more complex modulation types, such as QPSK (Quadrature Phase Shift Keying) and 8 & 16 QAM (Quadrature Amplitude Modulation). QPSK transmits 2 bits per baud, 8 QAM transmits 3 bits per baud and 16 QAM transmits 4 bits per baud. Additionally, when we modulate 2 orthogonal polarizations separately (sometimes called Dual Polarization or Polarization Division Multiplexing), we double the throughput. Voyager will support QPSK with 100Gbps, 8QAM with 150Gbps, and 16QAM with 200Gbps with PDM.
As more and more bits per symbol are transmitted, more symbols are needed to represent the different bit patterns. The symbols are then represented closer together and thus more difficult to distinguish from each other. Therefore, the signal needs to be “cleaner” and have less noise in order to read it effectively. This leads to shorter supported distances and the need for more complex FEC algorithms, such as SD-FEC.
Of course, a transponder also receives and demodulates the signal on the remote end.
What now?
At this point, you hopefully understand the basic technical challenges and needs with DWDM. This blog post covered the technical aspects of a transponder within Voyager. In part two, we will cover the question “Why Voyager?” and discuss Voyager functionality and use cases in greater detail. We couldn’t be more excited to be releasing Voyager for early access in just a few weeks, along with several supporting resources. If you’re dying to check it out in more detail in the meantime, visit Adva’s website, as they will be supporting and selling the product with Cumulus Linux, or contact TIP. Stay Tuned for more!
The post What is the open packet optical switch, Voyager? appeared first on Cumulus Networks Blog.
What is the open packet optical switch, Voyager? published first on https://wdmsh.tumblr.com/
0 notes
Text
Best 5 Computer Inventory Software Solutions
What Does Computer Inventory Management Software Do?
Computer inventory management is the process of automatic discovery and tracking of computer assets in an organization throughout their life cycle. Computer inventory management software analyzes machines and devices on a network and generates flexible reports with information about the exact hardware and software configuration of each machine or device.
Computer inventory management software solutions target many different use-cases. Some computer inventory solutions are aimed at individual home users, conveniently displaying hardware and software specifications of Windows, macOS, and Linux desktop computers and laptops. Other computer inventory solutions are aimed at IT administrators who look after an entire network of machines and connected devices, helping them plan future hardware and software purchases and diagnose network issues.
Why Should I Use Computer Inventory Software?
Knowing exactly what computers you have, what’s their configuration, and where they are located can be useful for a number of reasons. Every year, businesses around the world waste huge sums of money on unnecessary hardware and software purchases that could have been easily avoided with careful planning supported by reports generated using a computer inventory system.
This affects even young and small companies and not just huge multinational corporations with bloated IT departments. The situation is worse now than ever before because employees are readily encouraged to bring their own devices to work, making it more difficult for the management to plan future purchases.
Many computer inventory software solutions support the tracking of software licenses, which is an invaluable feature for compliance with software license agreements and as a way to prepare for a software license audit.
Considering how complicated the current software license landscape can be, with a multitude of different software licensing models, having a software solution that can automatically send alerts when it detects a compliance issue can not only save a business a lot of time but also a lot of money.
What Are the Best Computer Inventory Software Solutions?
The number of excellent computer inventory software solutions that are available on the market is so large that it can be quite daunting to pick just one. To make things even more complicated, various computer inventory software solutions focus various use cases. We have carefully evaluated all the popular options and selected what we consider to be the top five best computer inventory software solutions currently available.
1. Network Inventory Advisor
Network Inventory Advisor is an all-in-one computer inventory software solutioncapable of generating flexible hardware and software reports that include Window-, macOS-, and Linux-baseddevices as well as other network and standalone equipment. Network Inventory Advisor is agent-less and supports license aggregation, collection, and management for most major software products from more than 500 vendors, including Autodesk, Microsoft, Adobe, and others.
Network Inventory Advisor supports the management of multiple networks, which is perfect for MSPs as it allows them to use just a single installation of Network Inventory Advisor to manage multiple networks and switch between them with a click of a button. With Network Inventory Advisor, it’s possible to easily move, group, regroup and ungroup, reassign, and edit multiple nodes at the same time, and filtering down the network inventory is a matter of a few clicks, as well.
Network Inventory Advisor is priced fairly, with no hidden fees or limitations to worry about, and it’s just as suitable for small and mid-sized businesses as it is for large enterprises. A free trial version of Network Inventory Advisor is available on the official website, allowing anyone to test the software out at 25-node networks for up to 2 weeks.
2. Lansweeper
Lansweeper is a popular agent-less inventory management and software auditing tool with integrated reporting capabilities and automated software deployment. Lansweeper comes with an integrated help desk and IT service desk, making it possible to receive, analyze, and finalize help tickets from a single user interface. The free version of Lansweeper is limited to only 100 assets and includes only a fraction of the functionality present in any of the three premium versions of the software.
3. Spiceworks IT Asset Management
Spiceworks IT Asset Management is an enterprise-grade computer inventory and network monitoring software system that handles everything from workstations and servers to routers and switches. Spiceworks can track software licenses so you can stay in compliance, handling even cloud-based services. As an enterprise-grade solution, Spiceworks is less suitable for smaller businesses, who might feel overwhelmed by the sheer number of features the software offers.
4. Asset Panda
Asset Panda is a flexible computer inventory software solution with an intuitive user interface that makes asset tracking and management accessible to anyone. Asset Panda can handle any number of hardware and software assets, and it’s available both online and through a mobile application. Asset Panda’s customer service is US-based, and anyone can test this popular computer inventory software solution for up to 14 days for free.
5. WinAudit
WinAudit is a simple computer inventory software utility for Windows computers. It’s free and can be distributed by anyone without any restrictions. The main purpose of WinAudit is to create a comprehensive report on a machine's configuration and save it as CSV, RTF,or HTML. While WinAudit lacks many of the advanced auditing an network management features that make software solutions such as Network Inventory Advisor so popular among network administrators, it’s great for home users and small businesses who can get by with just the basics.
Source: https://www.network-inventory-advisor.com/best-computer-inventory-software.html
0 notes
Text
been preyed among mob.
Jun 12, 2017
a relaxing dream in which I visited my artist friends in Tianjin art college. at first I dreamt with BianQiong, my Tibet painter friend, and his friend. they live in dorm like a family. then shifted to a house near door and some of those students there working and chatting. I using English with a friend from my hometown neighbor county, who is humble and treated me well even I visited BianQiong in vacation but then the moment didn't paid him enough attentions but kindness felt. he sometimes mixed with my impression on another guy in the art college who also attracted me with his abled attitude. we chatted in English but my English seemingly not fluent enough and sometimes the students there in the house perceived it. its a peaceful dream and I without any pressure but enjoy staying. last 2 weeks I too busy to blog. my son's nexus 6 lost due to forgot to fetch after sport, likely accompanied by his sinful intrusive mom, a really small woman and poor gifted junior teacher. but next day she registered the lost on local stadium administrative and it even returned intact. I even disappointed by my son's loose management and bad memories, but ready to accept the misfortune. my son really glad to regain his nexus, he hummed upstairs when I waiting him in Sunday visit. last week I under heavy government sponsored hacking, detained my downloading windows 10 creator edition iso. I also tried to rebuild router os after disastrous intrusion. I failed times and times to make configurations backup. later I gave up backup now that if I left most of router profile default then will be less shortage of ram and lagging response. we also elated with new auto-connecting script and localized vpn server script, a byproduct huge finding during googling our problems. it fix our pains on ass of vpn connection which frequented by PRC surveillance and problematic. its really a great achievement saves. even most of the weeks busy and fruitful, PRC surveillance turns freakier now. my facing dorm moved in some young beast with stylish pig tail on his head, staying all day indoor babbled. most night when I went to toilet and back, their door left opener and room in dark, just remind me their capable of surveillance, poisoning, and stealth. that sometimes made me unease, but I know who is more unbalanced and revengeful. I put my fate in holy bliss. let thieves trying rob me in day time and in shadows. CCP and PRC literally makes everyone poorer day by day, minute by minute. its a burning fire heap that destroys any surplus in Chinese society. God, bring me sooner my Royal China. bring me my Crowned Queen from Japan, Asoh Yukiko, for better management of my life, of my Empire of China from my heroic ancestor. bring us surprise in this month salary day.
May 28, 2017
dreamt in a journey and next day we will return. I designed a multimedia and have to change some text in it. I tried many ways then found have to install then hack text string, one for title, one for calculation result. then in a class there are some guests. a black child played with my son and slammed my son's face. I angry with my son and urged him to slam back. then the black dad join the war and forced me to pay more attention and compensation. that's likely concerns about my son's English tutor his sinful mom arranged under a black man's lecture in her college, Qiqihar Univ, where she still felt romantic or fantasy. yesterday google alphago, AI powered chess rebot, beat all human Chinese go players. back to bed, dream continue about the lost. I saw some collegians lived around, like QRRS dorm stuffed by young blue-collar workers. I tried asking if they saw my suitcase. no one listened in their games. one of them likely my once QRRS colleague in tech department, Chen Ziming, who left QRRS for better career prospective decade ago, later told me alone that I too risky to put my baggage outside of door and packed valued items inside. I should pay for my careless. its a long morning and my late dream echos turbulent wind outside of window. last night my stomach painful midnight and I had to get up to shit twice to relieve the uncomfort. the dorm canteen's operator, the husband of the woman, turned hostile to me. the marching team in dusk around QRRS square also hated me, just like I didn't appreciate their noisy boombox and coarse taste of music, too. young workers esp close neighbored in the dorm long time grudged with me, trying all means to upset me, to hurt me. the dangers in mop sometimes put me in chill. but I have nothing but mission. coming lunar dragon boat holiday let me so lonely, like the Chinese girl Yang shuping lectured in her graduation ceremony in US aroused so many blind hates in sinking PRC young dogs, exactly her plain true thankful emotion toward American years educated her. dog PRC hated anything out of its humility. they turning China more and more mirror of bankrupted MidEast, purest poverty, now that they never care anything in the world out of their mouths, or their teeths' tearing and grinding, world of mere prey. God, dad, bring me sooner my vested Empire from my grand ancestor, for harmony Chinese family and life. bring me soone my Crowned Queen from Japan, Asoh Yukiko, for sanity of nowadays Chinese society. bring me more offspring for future 1109 years my new Empire of China reset for span timespace. grant us a merry holiday, esp woz's last children holiday coming less than a week.
May 22, 2017
dreamt at my hometown with my old family who all catering a new baby whose centered likely my son. lots of relatives jammed in the bedroom once my old parents prepared for their first next generation's wedding, my 2nd brother's. I held the infant and sending him sleep but in a blink I only holding blanket while the baby missing. then on the edge of bed and edge of the entrance of the room, on uneven stone or plastic teeth of a plate the infant sleeping. his head left on bare rugged without clothes cushion but thank God its OK. we carefully shift him to new infant bed. my 2nd elder brother's wife, their first son, my 3rd elder sister esp helpful in caring relatives crowd. the infant under so many attentions that I felt he must be my newly born son. in second view during a break I thought he might be my brother's 2nd son's first son. the nephew married a neighbor village girl then soon divorced. he now rumored dislikes woman and kept single, that's his mother claimed about her own son in front of me in our latest hometown tour. I think he more likes his grandpa than his elder brother, who had 3 children now, and merits belongs to be our family members but not a clue in his mom who bold and shameless feminism, like generous, honest, integrity, kind, etc. I told him my appreciation in once QQ chat session decade ago when he still a boy. today is Monday morning. I again in chill felt boring and napped. yesterday I bought my son small fishes and shrimps from an elder amateur vendor who is lonely and hopeless aside the road where I went alone to buy fruits. I intended to do him a favor but he refused aid. so I bought his all he charged ¥15, a small heap small fishes and a small heap of shrimps. I left him a peach and 2 CNY extra and fled to evade the elder's defying. I told my son how small fishes with small hot pepper can be delicious for in my teenage my 2nd elder brother quite sometimes bring home the food material after his school, ie. he caught fishes in pond or rice fields after school hours. it left me life long appetite. I really hope my son find the delicacy but so far I unable to contact him on the phone about the dish the grandma loathed to prepare with before I left in Sunday dusk. I also bought my son extra fruits, including litchi and mango, peach, for my son loathed to let me buy fruits after showered in public bathroom. I feed him with litchi and mango before left him alone in his android games. we really enjoyed the fruits. on Wednesday I will fetch his birthday cake ordered online, and celebrate his 13 birthday together ( woz 12 birthday reported here). God dad, I recently felt more solider to accept de facto that my offspring limits to one son. I trust Holy arrangement and humble of my son's mother family, her insanity. God dad, grant me more children in my prime time. bring me sooner my Crowned Queen from Japan, Asoh Yukiko. link our nations, our blood bond on new land that shared among us. bring more laugh and companions in my life in family forever hospitable and bright. BTW, these days media reveals misery of pangolins which extincting after sinful PRC Chinese insane appetite, God, dad, pl save the adorable animal, which is key to remain rampant ants lair everywhere those years under control. let's bee and pangolin forever happily enjoy the planet as we do. God dad, pl!
May 21, 2017
dreamt with ample details after migrated into US. an elder Chinese woman with her spouse contacted me for rent her house or living matters in America. yesterday I happily dispatched salary and sliced it into feeding small bills due monthly, ie. laundry, groupon for salon, spa, dining out. woz's birthday celebration also booked. local debtee received partial return. God dad, grant me next month reserves for my hosting plan renewal on godaddy. this week also somewhat busy. I napped on Monday morning after found jobless and exhausted after joys of reunited son the day before. Tuesday morning I restored, found I can add feedback form onto my google sites. then I launched to learn google form, component of Gsuite, to enrich my website's interactivity. my long time afraid of form and script in microsoft office suite cured by google form's easy to use. in an hour I built up my survey for my google sites and published, inc checkbox, multi-choice, rate, scale, dropdown, pictures etc lots of elements of interactive. google form's response analysis amazingly rich, in pie chart, bar chart, and lots of charts that's easy understanding while informative first impression. Friday I rebuilt my portable os on a retired ssd, after failed to fix ubuntu's lingering error. this time I made the bootable images more cleaner and handier. in woz's monthly visit my dorm, I demonstrated him my websites' new element, survey. and we enjoyed snack routinely, and hot water washing feet powered by dorm's heater just recovered from broke down. dorm canteen loaned me ¥100, but God knows how we satisfied in our companion and companion of hard times. God dad, my living so far designated to deal with a salary ¥3000/month, how real during hopes and joys in dealing with the only source of income. God dad, how I endear my life within this tiny time space here and now on the planet and before climate disaster, while we stride into big chances never seen holy grants. bring me sooner my Crowned Queen from Japan, Asoh Yukiko, and my vested Empire of China, and our future new land of north and water peculiar cold sweet. grant my cyberspace startup booming in business and influential of public mind. thx for my new summer pants with mobile pockets my nephew offered free weeks ago in my hard time.
LOFTER:riveryog, 旎宫嘉坊 http://ift.tt/2shIQDW
0 notes
Text
threats of robbing in poverty infused PRC by CCP dog.
Jun 12, 2017
a relaxing dream in which I visited my artist friends in Tianjin art college. at first I dreamt with BianQiong, my Tibet painter friend, and his friend. they live in dorm like a family. then shifted to a house near door and some of those students there working and chatting. I using English with a friend from my hometown neighbor county, who is humble and treated me well even I visited BianQiong in vacation but then the moment didn't paid him enough attentions but kindness felt. he sometimes mixed with my impression on another guy in the art college who also attracted me with his abled attitude. we chatted in English but my English seemingly not fluent enough and sometimes the students there in the house perceived it. its a peaceful dream and I without any pressure but enjoy staying. last 2 weeks I too busy to blog. my son's nexus 6 lost due to forgot to fetch after sport, likely accompanied by his sinful intrusive mom, a really small woman and poor gifted junior teacher. but next day she registered the lost on local stadium administrative and it even returned intact. I even disappointed by my son's loose management and bad memories, but ready to accept the misfortune. my son really glad to regain his nexus, he hummed upstairs when I waiting him in Sunday visit. last week I under heavy government sponsored hacking, detained my downloading windows 10 creator edition iso. I also tried to rebuild router os after disastrous intrusion. I failed times and times to make configurations backup. later I gave up backup now that if I left most of router profile default then will be less shortage of ram and lagging response. we also elated with new auto-connecting script and localized vpn server script, a byproduct huge finding during googling our problems. it fix our pains on ass of vpn connection which frequented by PRC surveillance and problematic. its really a great achievement saves. even most of the weeks busy and fruitful, PRC surveillance turns freakier now. my facing dorm moved in some young beast with stylish pig tail on his head, staying all day indoor babbled. most night when I went to toilet and back, their door left opener and room in dark, just remind me their capable of surveillance, poisoning, and stealth. that sometimes made me unease, but I know who is more unbalanced and revengeful. I put my fate in holy bliss. let thieves trying rob me in day time and in shadows. CCP and PRC literally makes everyone poorer day by day, minute by minute. its a burning fire heap that destroys any surplus in Chinese society. God, bring me sooner my Royal China. bring me my Crowned Queen from Japan, Asoh Yukiko, for better management of my life, of my Empire of China from my heroic ancestor. bring us surprise in this month salary day.
May 28, 2017
dreamt in a journey and next day we will return. I designed a multimedia and have to change some text in it. I tried many ways then found have to install then hack text string, one for title, one for calculation result. then in a class there are some guests. a black child played with my son and slammed my son's face. I angry with my son and urged him to slam back. then the black dad join the war and forced me to pay more attention and compensation. that's likely concerns about my son's English tutor his sinful mom arranged under a black man's lecture in her college, Qiqihar Univ, where she still felt romantic or fantasy. yesterday google alphago, AI powered chess rebot, beat all human Chinese go players. back to bed, dream continue about the lost. I saw some collegians lived around, like QRRS dorm stuffed by young blue-collar workers. I tried asking if they saw my suitcase. no one listened in their games. one of them likely my once QRRS colleague in tech department, Chen Ziming, who left QRRS for better career prospective decade ago, later told me alone that I too risky to put my baggage outside of door and packed valued items inside. I should pay for my careless. its a long morning and my late dream echos turbulent wind outside of window. last night my stomach painful midnight and I had to get up to shit twice to relieve the uncomfort. the dorm canteen's operator, the husband of the woman, turned hostile to me. the marching team in dusk around QRRS square also hated me, just like I didn't appreciate their noisy boombox and coarse taste of music, too. young workers esp close neighbored in the dorm long time grudged with me, trying all means to upset me, to hurt me. the dangers in mop sometimes put me in chill. but I have nothing but mission. coming lunar dragon boat holiday let me so lonely, like the Chinese girl Yang shuping lectured in her graduation ceremony in US aroused so many blind hates in sinking PRC young dogs, exactly her plain true thankful emotion toward American years educated her. dog PRC hated anything out of its humility. they turning China more and more mirror of bankrupted MidEast, purest poverty, now that they never care anything in the world out of their mouths, or their teeths' tearing and grinding, world of mere prey. God, dad, bring me sooner my vested Empire from my grand ancestor, for harmony Chinese family and life. bring me soone my Crowned Queen from Japan, Asoh Yukiko, for sanity of nowadays Chinese society. bring me more offspring for future 1109 years my new Empire of China reset for span timespace. grant us a merry holiday, esp woz's last children holiday coming less than a week.
May 22, 2017
dreamt at my hometown with my old family who all catering a new baby whose centered likely my son. lots of relatives jammed in the bedroom once my old parents prepared for their first next generation's wedding, my 2nd brother's. I held the infant and sending him sleep but in a blink I only holding blanket while the baby missing. then on the edge of bed and edge of the entrance of the room, on uneven stone or plastic teeth of a plate the infant sleeping. his head left on bare rugged without clothes cushion but thank God its OK. we carefully shift him to new infant bed. my 2nd elder brother's wife, their first son, my 3rd elder sister esp helpful in caring relatives crowd. the infant under so many attentions that I felt he must be my newly born son. in second view during a break I thought he might be my brother's 2nd son's first son. the nephew married a neighbor village girl then soon divorced. he now rumored dislikes woman and kept single, that's his mother claimed about her own son in front of me in our latest hometown tour. I think he more likes his grandpa than his elder brother, who had 3 children now, and merits belongs to be our family members but not a clue in his mom who bold and shameless feminism, like generous, honest, integrity, kind, etc. I told him my appreciation in once QQ chat session decade ago when he still a boy. today is Monday morning. I again in chill felt boring and napped. yesterday I bought my son small fishes and shrimps from an elder amateur vendor who is lonely and hopeless aside the road where I went alone to buy fruits. I intended to do him a favor but he refused aid. so I bought his all he charged ¥15, a small heap small fishes and a small heap of shrimps. I left him a peach and 2 CNY extra and fled to evade the elder's defying. I told my son how small fishes with small hot pepper can be delicious for in my teenage my 2nd elder brother quite sometimes bring home the food material after his school, ie. he caught fishes in pond or rice fields after school hours. it left me life long appetite. I really hope my son find the delicacy but so far I unable to contact him on the phone about the dish the grandma loathed to prepare with before I left in Sunday dusk. I also bought my son extra fruits, including litchi and mango, peach, for my son loathed to let me buy fruits after showered in public bathroom. I feed him with litchi and mango before left him alone in his android games. we really enjoyed the fruits. on Wednesday I will fetch his birthday cake ordered online, and celebrate his 13 birthday together ( woz 12 birthday reported here). God dad, I recently felt more solider to accept de facto that my offspring limits to one son. I trust Holy arrangement and humble of my son's mother family, her insanity. God dad, grant me more children in my prime time. bring me sooner my Crowned Queen from Japan, Asoh Yukiko. link our nations, our blood bond on new land that shared among us. bring more laugh and companions in my life in family forever hospitable and bright. BTW, these days media reveals misery of pangolins which extincting after sinful PRC Chinese insane appetite, God, dad, pl save the adorable animal, which is key to remain rampant ants lair everywhere those years under control. let's bee and pangolin forever happily enjoy the planet as we do. God dad, pl!
May 21, 2017
dreamt with ample details after migrated into US. an elder Chinese woman with her spouse contacted me for rent her house or living matters in America. yesterday I happily dispatched salary and sliced it into feeding small bills due monthly, ie. laundry, groupon for salon, spa, dining out. woz's birthday celebration also booked. local debtee received partial return. God dad, grant me next month reserves for my hosting plan renewal on godaddy. this week also somewhat busy. I napped on Monday morning after found jobless and exhausted after joys of reunited son the day before. Tuesday morning I restored, found I can add feedback form onto my google sites. then I launched to learn google form, component of Gsuite, to enrich my website's interactivity. my long time afraid of form and script in microsoft office suite cured by google form's easy to use. in an hour I built up my survey for my google sites and published, inc checkbox, multi-choice, rate, scale, dropdown, pictures etc lots of elements of interactive. google form's response analysis amazingly rich, in pie chart, bar chart, and lots of charts that's easy understanding while informative first impression. Friday I rebuilt my portable os on a retired ssd, after failed to fix ubuntu's lingering error. this time I made the bootable images more cleaner and handier. in woz's monthly visit my dorm, I demonstrated him my websites' new element, survey. and we enjoyed snack routinely, and hot water washing feet powered by dorm's heater just recovered from broke down. dorm canteen loaned me ¥100, but God knows how we satisfied in our companion and companion of hard times. God dad, my living so far designated to deal with a salary ¥3000/month, how real during hopes and joys in dealing with the only source of income. God dad, how I endear my life within this tiny time space here and now on the planet and before climate disaster, while we stride into big chances never seen holy grants. bring me sooner my Crowned Queen from Japan, Asoh Yukiko, and my vested Empire of China, and our future new land of north and water peculiar cold sweet. grant my cyberspace startup booming in business and influential of public mind. thx for my new summer pants with mobile pockets my nephew offered free weeks ago in my hard time.
via Blogger http://ift.tt/2s4MQ8o
0 notes
Text
New Post has been published on Globeinfrom
New Post has been published on https://globeinform.com/defensive-mac-addresses-from-stalkers-is-hard-and-android-fails-miserably-at-it/
Defensive MAC addresses from stalkers is hard and Android fails miserably at it
In early 2015, architects of Google’s Android mobile working device delivered a brand new feature that was meant to curtail the actual time tracking of smartphones as their customers traversed retail shops, metropolis streets, and just about anywhere else. A recently posted research paper observed that the degree stays lacking at the giant majority of Android telephones and is easily defeated by the notably small number of devices that do support it.
Like all -enabled devices, smartphones are continuously scanning their environment for available access points, and with every probe, they send a MAC—short for media get entry to control—address associated with the handset. All through a maximum of the history of, the free alternate of MAC addresses did not pose much threat to privateness. That everyone changed with the advent of cellular computing. All at once MAC addresses left a never-ending collection of virtual footprints that revealed a dizzying array of records approximately our comings and goings, including what time we left the bar final night, how many times we have been there inside the beyond month, the time we depart for work every day, and the course we take to get there.
Ultimately, engineers at Apple and Google realized the ability for abuse and took a movement. Their answer became to rotate through a series of often converting pseudo-random addresses whilst casually probing near-through get admission to factors. That way, devices that logged MAC addresses would not be capable of correlated probes to a unique tool. Best while a telephone absolutely related to a community wouldn’t it display the particular MAC address it turned into tied to. Apple introduced MAC address randomization in June 2014, with the discharge of iOS 8. A few months later, Google’s Android running device delivered experimental guide for the measure. Full implementation went live in March 2015 and is presently available in model five.0 through the modern-day 7.1; the one’s versions account for about -thirds of the Android consumer base.
Newly posted studies, however, has observed Android’s MAC randomization to be in large part absent. Of the more or less 960,000 Android gadgets that have been scanned over a two-12 months duration, fewer than 60,000 of them—and really possibly as few as 30,000 of them—randomized their addresses, even when walking OS versions that supported the characteristic. (The researchers recognize Most effective that they obtained approximately 60,000 randomized MAC addresses from Android phones. They presume that during at least some instances, or extra of the randomized addresses belonged to the equal smartphone.) Equally alarming, of the six percentage of Android telephones the researchers saw presenting randomization, surely they all periodically dispatched out probes the use of their particular MAC address, a flaw that in large part rendered the degree vain. The Simplest model researchers located to do randomization efficaciously become the Cat S60. In sharp contrast, really all the iOS devices observed through the researchers furnished study randomization.
Wi-findingWireless Your MAC cope with On Stressed out And Wi-fi community Playing cards
The answer To The Media access manipulate Question
During the last few weeks I’ve received quite Some e-mails approximately Ethernet Cards, both Stressed out and Wireless, and more mainly, approximately Media get right of entry to manage (MAC) addresses. I think the main reason I have acquired so many questions about Ethernet Playing cards and MAC addresses is people looking to cozy their home Wireless networks and their desire to use MAC cope with filtering. This sort of filtering in Wi-fi networks may be configured to allow or deny unique computer systems to apply or connect to the Wi-fi network, based totally on the MAC cope with.
My first notion changed into to write down a piece of writing pretty much MAC addresses and Wireless Ethernet. After thinking about it I determined to extend on this and move over a few specific facts approximately Ethernet Cards and verbal exchange.
Specific Ways Of Wi-findingWireless Your MAC address And greater
There are numerous Approaches of WiWireless your Ethernet and communications protocol statistics. Many Ethernet card manufacturers have proprietary software that can screen this data however they work in another way relying on the manufacturer. So we can use the Home windows 2000 and XP “config” application for the reason that this is to be had in most of the people of Windows running Systems.
Wi-first, go to “start” -> “run” and type “cmd” without the fees. Then hit the enter key. On the command line type “config /all”, again without the fees. in reality, just typing config without the /all will work however will Simplest offer you with abbreviated records concerning your network Playing cards. An example of what you might see by means of typing the “config /all” command is beneath with every object commented in green lettering:
Fault Tolerant And Notably Availability Computer Systems
There are numerous Ways of Wi-fi your Ethernet and communications protocol facts. Many Ethernet card manufacturer’s have proprietary software that could display this records however they paintings in another way depending on the producer. So we will use the Windows 2000 and XP “config” software due to the fact that that is available in the majority of Windows working Systems.
And here we have the MAC cope with. The MAC cope with is a forty-eight bit hexadecimal code and is think to be a totally precise cope with. It is 48 bits due to the fact every number or letter in hexadecimal represents 8 bits. Hexadecimal numbers variety from zero,1,2,three,4,5,6,7,eight,nine,A,B,C,D,E, F. There are 6 alpha-numeric codes for this reason 6*eight=forty eight(bits). The primary 3 codes pick out the producer of the card and the ultimate codes are used to create a completely unique range. Theoretically there must by no means be a card with identical MAC address on a local community. but, there are Some exceptions. There are software gear that will let you change this code. In fact, this is a step a few hackers take to attack different Systems on a nearby network. I say nearby network due to the fact MAC addresses aren’t routable among network segments. with the aid of spoofing this cope with, you can impersonate every other gadget at the local community. Site visitors that turned into bound for the intended target can be redirected to the hacker’s machine. that is the deal with you would also use to populate a MAC cope with, or physical cope with desk when setting up your Wireless get entry to factor to help MAC cope with filtering.
DHCP Enabled. . . . . . . . . . . : Sure
DHCP, or the Dynamic Host manage Protocol, if enabled way your computer systems IP deal with is being furnished by using a DHCP server on you community. The DHCP server can be your Wi-fi access factor, cable/DSL router, cable modem, or a server for your community. also, if a DHCP server isn’t enabled to your network, your computers operating machine will automobile generate a random IP address inside a certain predefined variety. This means you could network a set of Systems together without having to manually assign the IP settings.
IP deal with. . . . . . . . . . . . : 192.168.zero.117
This parameter affords you together with your current IP address. The cope with indexed above is what is referred to as a “private” cope with. There are sure instructions of IP addresses which have been set aside for personal use. This means on your inner, neighborhood, or personal network at domestic or workplace. Those addresses aren’t, or ought to not, be routable at the Net. The Net routes what are known as “legitimate” IP addresses. Your cable/DSL router or cable modem has a legitimate IP deal with assigned to its “outside” network interface. The outside interface can be your smartphone line or cable Television cable.
Subnet Mask . . . . . . . . . . . : 255.255.255.0
The Subnet Masks is a unique variety, or in a few experience, clear out, that breaks down your IP address, in this situation personal IP address, into positive groups. IP addresses and Subnet Mask can be a complex count and might take an entire article to go over.
Default Gateway . . . . . . . . . : 192.168.0.254
The default gateway, the IP addresses indexed above, is the IP address of the device as a way to direction your request, which includes while you try and browse a internet site, to the Internet. It’s far a bit more complicated than that even though as gateways or routers can direction Traffic to diverse One of a kind networks, even other personal networks. At your property or small workplace, this gateway maximum possibly is your cable/DSL modem or router.
DHCP Server . . . . . . . . . . . : 192.168.zero.49
The DHCP server, don’t forget we talked a bit approximately this above, is the tool that assigns your Pc an IP address and different data. DHCP servers can assign all kinds of statistics such as; Default Gateway, Area Call Servers (DNS), IP address, Subnet Mask, Time Server, and lots greater.
DNS Servers . . . . . . . . . . . : 192.168.0.49, sixty-four.one zero five.197.58
DNS Servers are internal or external servers that remedy Fully Qualified Domains (FQDN), which includes http://www.Defendingthenet.Com , to IP addresses. this is executed due to the fact computer systems don’t sincerely transmit your requests the use of the Domain Call, they use the IP address assigned to the FQDN. For most home or small workplace customers, the number one DNS server is the IP address of your cable/DSL router. Your cable/DSL router than queries an external DNS server on the Net to carry out the real resolution of the FQDN to IP address. The address 192.168.zero.forty-nine is an inner personal device on my network while the sixty four.105.197.fifty-eight is an outside public Internet DNS server and is gift simply in case my router has problem appearing the DNS decision duties.
0 notes
Text
95% off #The Python 3 Bible™ | Go from Beginner to Advanced in Python – $10
Python – Complete Guide to learning how to program. Go from Beginner to Advanced level in Python with coding exercises!
All Levels, – 8 hours, 73 lectures
Average rating 4.1/5 (4.1 (173 ratings) Instead of using a simple lifetime average, Udemy calculates a course’s star rating by considering a number of different factors such as the number of ratings, the age of ratings, and the likelihood of fraudulent ratings.)
Course requirements:
Should be willing to learn and treat this as a full course – please take notes and put lessons into practice for maximum benefit. Only the very basic computer skills are needed Access to a computer with internet connection.
Course description:
========================= TESTIMONIALS =========================
“Everything is explained perfectly!” – Mouheb
“Great Teacher. I like his teaching style, step by step approach, easy to follow him. Lectures is very engaging. Well structured and organized course content” – Faisal
“Overall, this is a very high quality course. Taking the course has *shown* me what is possible even before I thought of searching for it.” – Kevin
“Great course overall! I started off as a complete beginner and feel much more confident about coding with Python” – Frank S
“Great set of Python Tutorials. The instructor walks you through the classes and materials in an easy to understand manor. A++” – Mirko
“Just did my first program very early on, which was exciting” – Chloe
===============================================================
If you want to learn Python to advance your skills, then this is the course for you!
If you have no previous knowledge or experience in Python, you will like that the course begins with Python basics. Even if you have some experience in programming in Python, this course can help you learn some new information you had missed before. Each section of the course is linked to the previous one in terms of utilizing what was already learned and each topic is supplied with lots of examples which will help students in their process of learning. Upon the completion of this course, you should be able to write programs that have real-life applications.
What I think is the best about this course is that you can search questions others have had, post your own questions, and get answers to challenges you are currently facing in learning and using Python. You get paid Python expert technical support in this course here to answer every single question you ask!
If you have any suggestions on topics that have not been covered, you can send them via private message. I will do my best to cover them as soon as possible.
Thank you for reading this. I hope to see you in the course soon and I hope you will enjoy your time learning as much as I have!
Full details Go from Beginner to Advanced in Python Programming by learning all of the basics to Object Orientated Programming. Gain general knowledge in regard to Python programming language Write scripts for general productivity tasks Read and comprehend Python code Gain knowledge in regard to general programming concepts
Full details For people who are new to Python For Programming Beginners Anyone who has always wanted to learn Python For people looking to transition from another language to Python This is not intended for advanced Python Programmers People of any age, gender or country but must understand Business English No prior programming knowledge is needed.
Full details
Reviews:
“Right off the bat, although the title seems to suggest that this a beginner class, frankly, intermediate would be more appropriate.. Sure, some of the beginning is a rehash, but most of this tutorial is ‘eye’s glazed over”. One glaring error the author makes is the HORRIBLE ASSUMPTION that everybody runs Windows10. To get the downloaded Python and Sublime TExt programs to run, he correctly points out that the path statement to the location of these programs must be added to the enviormental variable. Now, in Win 10 it is fairly easy, but not in 7 as most people have. In fact, with his instructions, you will damage your machine, although not seriously as i did. Mainly, it’s not being able to use cmd line functions unless you put them back in. Putting in a new path statement in 7 is quite different than it is in 10. The Author chooses a teaching style that is stating a bunch of facts without proving or explaining them. A great analogy is saying 2+2 = 5 and The sky is green. One would expect him explain himself or hope that some of his hired guns would answer questions in the Q & A section.. Unfortunately, they were there in the beginning but fled after a week. I CANNOT recommend this course to a beginner, because of what I wrote above, and you will lost interest because of the lack of explanations of his dictates.. But since you paid for it, keep it for future reference for when you have a more grounded understanding of the basics As for why I gave it 1 ½ stars? I stuck with 1 star but one of his hired guns is the very attractive Sadeta Kulevic but she seems to be a little English challenged. Several times, someone would post a question and her response was ” I don’t understand your question” Myself, I have issues with the concept of indentation of code lines. Could never get that explained properly. Ms Kulevic, I noticed was studying Computer Networking and since I am a network guy, I know that subnetting is one of the harder concepts to grasp and be able to do in your brain in 45 seconds or less. I offered to trade that knowledge for some more guidance on the indentation issue, but it never got anywhere Good luck” (Mikey B Barrett)
“because of there isn’t subtitle because my mother language isn’t English and i find hard to hear what the teacher say the second reason is the teacher don’t reply all of questions” (Abdelaziz Said Abdelaziz)
“Great set of Python Tutorials. The instructor walks you through the classes and materials in an easy to understand manor. A++” (Mirko Cukich)
About Instructor:
Ermin Kreponic Suppoman ®
Strongly motivated young IT expert, Linux enthusiast with a passion for troubleshooting network related problems. With an exceptional eye for details and a sense of urgency when it comes down to problem solving. Skills – Advanced knowledge of Linux command line – Installation, configuration and maintenance of servers that run under Unix/Linux type operating systems To name a few: DNS, TFTP, FTP, SSH, APACHE, SMTP, VSFTP and some others – Troubleshooting a wide range of network related problems. Meaning, digging deep for packets on any given network. Using one of my favourite tools for capturing and filtering packets on the network, Wireshark, and resolving end-user issues – Good understanding of Cisco routers and IOS operating system – Configuration and implementation of Linux firewall namely Iptables – Supervision and filtration of network traffic – Tightening down security and pen testing networks for possible vulnerabilities – Good knowledge of network gear brands and their strengths or weaknesses – Preforming system back up – Fair knowledge of Bash scripting – equipment installation, upgrades, patches, and configuration. Personal note: I do not sleep much, but that is not only because I work hard, rather instead it is because I enjoy this line of work, it is extremely rewarding in every way that matters
Why are 40,000+ Students enrolled in my 19 courses? 1) I am proof my strategies work with 500,000+ fans online and a daily reach of 1,000,000 people. 2) I teach Masterclass Courses on Facebook Ads, YouTube, Instagram, Google Ads, Twitter & Udemy. 3) My courses are interactive live tutorials – no boring slideshows! You can copy and paste my exact systems. ► Don’t delay, every second could be costing you money! ◄ I’ve achieved a number 1 app on the iOS app store, and top selling Udemy courses, using Online Marketing. Learn how to grow your fanbase on Facebook using my Facebook Ads & Facebook Marketing Course: 10+ hours of HD video. Learn to build a fast-growing, popular and revenue generating YouTube business with The Complete YouTube Courses with your own videos and without filming: 14+ hours of HD classes. Learn how to create a high-growth, traffic and revenue generating Instagram account with The Complete Instagram Domination Course. If you want to learn how to market your business and products online, enrol in my courses today!
Instructor Other Courses:
JavaScript from Beginner to Advanced Ermin Kreponic, IT Expert (5) $10 $195 YouTube SEO Secret: How I got 40,000 subscribers in 2 weeks! Suppoman ®, Your Superhero On Udemy! Teaches 19 Courses to 40k students (7) $10 $195 C# From Beginner to Advanced Udemy Marketing: Boost Sales & SEO with YouTube – Unofficial Learn Angular 2 from Beginner to Advanced Facebook Live: Attract 100,000+ Page fans with Viral Streams …………………………………………………………… Ermin Kreponic Suppoman ® coupons Development course coupon Udemy Development course coupon Programming Languages course coupon Udemy Programming Languages course coupon The Python 3 Bible™ | Go from Beginner to Advanced in Python The Python 3 Bible™ | Go from Beginner to Advanced in Python course coupon The Python 3 Bible™ | Go from Beginner to Advanced in Python coupon coupons
The post 95% off #The Python 3 Bible™ | Go from Beginner to Advanced in Python – $10 appeared first on Udemy Cupón/ Udemy Coupon/.
from Udemy Cupón/ Udemy Coupon/ http://coursetag.com/udemy/coupon/95-off-the-python-3-bible-go-from-beginner-to-advanced-in-python-10/ from Course Tag https://coursetagcom.tumblr.com/post/155755939748
0 notes
Link
Jun 12, 2017
a relaxing dream in which I visited my artist friends in Tianjin art college. at first I dreamt with BianQiong, my Tibet painter friend, and his friend. they live in dorm like a family. then shifted to a house near door and some of those students there working and chatting. I using English with a friend from my hometown neighbor county, who is humble and treated me well even I visited BianQiong in vacation but then the moment didn't paid him enough attentions but kindness felt. he sometimes mixed with my impression on another guy in the art college who also attracted me with his abled attitude. we chatted in English but my English seemingly not fluent enough and sometimes the students there in the house perceived it. its a peaceful dream and I without any pressure but enjoy staying. last 2 weeks I too busy to blog. my son's nexus 6 lost due to forgot to fetch after sport, likely accompanied by his sinful intrusive mom, a really small woman and poor gifted junior teacher. but next day she registered the lost on local stadium administrative and it even returned intact. I even disappointed by my son's loose management and bad memories, but ready to accept the misfortune. my son really glad to regain his nexus, he hummed upstairs when I waiting him in Sunday visit. last week I under heavy government sponsored hacking, detained my downloading windows 10 creator edition iso. I also tried to rebuild router os after disastrous intrusion. I failed times and times to make configurations backup. later I gave up backup now that if I left most of router profile default then will be less shortage of ram and lagging response. we also elated with new auto-connecting script and localized vpn server script, a byproduct huge finding during googling our problems. it fix our pains on ass of vpn connection which frequented by PRC surveillance and problematic. its really a great achievement saves. even most of the weeks busy and fruitful, PRC surveillance turns freakier now. my facing dorm moved in some young beast with stylish pig tail on his head, staying all day indoor babbled. most night when I went to toilet and back, their door left opener and room in dark, just remind me their capable of surveillance, poisoning, and stealth. that sometimes made me unease, but I know who is more unbalanced and revengeful. I put my fate in holy bliss. let thieves trying rob me in day time and in shadows. CCP and PRC literally makes everyone poorer day by day, minute by minute. its a burning fire heap that destroys any surplus in Chinese society. God, bring me sooner my Royal China. bring me my Crowned Queen from Japan, Asoh Yukiko, for better management of my life, of my Empire of China from my heroic ancestor. bring us surprise in this month salary day.
May 28, 2017
dreamt in a journey and next day we will return. I designed a multimedia and have to change some text in it. I tried many ways then found have to install then hack text string, one for title, one for calculation result. then in a class there are some guests. a black child played with my son and slammed my son's face. I angry with my son and urged him to slam back. then the black dad join the war and forced me to pay more attention and compensation. that's likely concerns about my son's English tutor his sinful mom arranged under a black man's lecture in her college, Qiqihar Univ, where she still felt romantic or fantasy. yesterday google alphago, AI powered chess rebot, beat all human Chinese go players. back to bed, dream continue about the lost. I saw some collegians lived around, like QRRS dorm stuffed by young blue-collar workers. I tried asking if they saw my suitcase. no one listened in their games. one of them likely my once QRRS colleague in tech department, Chen Ziming, who left QRRS for better career prospective decade ago, later told me alone that I too risky to put my baggage outside of door and packed valued items inside. I should pay for my careless. its a long morning and my late dream echos turbulent wind outside of window. last night my stomach painful midnight and I had to get up to shit twice to relieve the uncomfort. the dorm canteen's operator, the husband of the woman, turned hostile to me. the marching team in dusk around QRRS square also hated me, just like I didn't appreciate their noisy boombox and coarse taste of music, too. young workers esp close neighbored in the dorm long time grudged with me, trying all means to upset me, to hurt me. the dangers in mop sometimes put me in chill. but I have nothing but mission. coming lunar dragon boat holiday let me so lonely, like the Chinese girl Yang shuping lectured in her graduation ceremony in US aroused so many blind hates in sinking PRC young dogs, exactly her plain true thankful emotion toward American years educated her. dog PRC hated anything out of its humility. they turning China more and more mirror of bankrupted MidEast, purest poverty, now that they never care anything in the world out of their mouths, or their teeths' tearing and grinding, world of mere prey. God, dad, bring me sooner my vested Empire from my grand ancestor, for harmony Chinese family and life. bring me soone my Crowned Queen from Japan, Asoh Yukiko, for sanity of nowadays Chinese society. bring me more offspring for future 1109 years my new Empire of China reset for span timespace. grant us a merry holiday, esp woz's last children holiday coming less than a week.
May 22, 2017
dreamt at my hometown with my old family who all catering a new baby whose centered likely my son. lots of relatives jammed in the bedroom once my old parents prepared for their first next generation's wedding, my 2nd brother's. I held the infant and sending him sleep but in a blink I only holding blanket while the baby missing. then on the edge of bed and edge of the entrance of the room, on uneven stone or plastic teeth of a plate the infant sleeping. his head left on bare rugged without clothes cushion but thank God its OK. we carefully shift him to new infant bed. my 2nd elder brother's wife, their first son, my 3rd elder sister esp helpful in caring relatives crowd. the infant under so many attentions that I felt he must be my newly born son. in second view during a break I thought he might be my brother's 2nd son's first son. the nephew married a neighbor village girl then soon divorced. he now rumored dislikes woman and kept single, that's his mother claimed about her own son in front of me in our latest hometown tour. I think he more likes his grandpa than his elder brother, who had 3 children now, and merits belongs to be our family members but not a clue in his mom who bold and shameless feminism, like generous, honest, integrity, kind, etc. I told him my appreciation in once QQ chat session decade ago when he still a boy. today is Monday morning. I again in chill felt boring and napped. yesterday I bought my son small fishes and shrimps from an elder amateur vendor who is lonely and hopeless aside the road where I went alone to buy fruits. I intended to do him a favor but he refused aid. so I bought his all he charged ¥15, a small heap small fishes and a small heap of shrimps. I left him a peach and 2 CNY extra and fled to evade the elder's defying. I told my son how small fishes with small hot pepper can be delicious for in my teenage my 2nd elder brother quite sometimes bring home the food material after his school, ie. he caught fishes in pond or rice fields after school hours. it left me life long appetite. I really hope my son find the delicacy but so far I unable to contact him on the phone about the dish the grandma loathed to prepare with before I left in Sunday dusk. I also bought my son extra fruits, including litchi and mango, peach, for my son loathed to let me buy fruits after showered in public bathroom. I feed him with litchi and mango before left him alone in his android games. we really enjoyed the fruits. on Wednesday I will fetch his birthday cake ordered online, and celebrate his 13 birthday together ( woz 12 birthday reported here). God dad, I recently felt more solider to accept de facto that my offspring limits to one son. I trust Holy arrangement and humble of my son's mother family, her insanity. God dad, grant me more children in my prime time. bring me sooner my Crowned Queen from Japan, Asoh Yukiko. link our nations, our blood bond on new land that shared among us. bring more laugh and companions in my life in family forever hospitable and bright. BTW, these days media reveals misery of pangolins which extincting after sinful PRC Chinese insane appetite, God, dad, pl save the adorable animal, which is key to remain rampant ants lair everywhere those years under control. let's bee and pangolin forever happily enjoy the planet as we do. God dad, pl!
May 21, 2017
dreamt with ample details after migrated into US. an elder Chinese woman with her spouse contacted me for rent her house or living matters in America. yesterday I happily dispatched salary and sliced it into feeding small bills due monthly, ie. laundry, groupon for salon, spa, dining out. woz's birthday celebration also booked. local debtee received partial return. God dad, grant me next month reserves for my hosting plan renewal on godaddy. this week also somewhat busy. I napped on Monday morning after found jobless and exhausted after joys of reunited son the day before. Tuesday morning I restored, found I can add feedback form onto my google sites. then I launched to learn google form, component of Gsuite, to enrich my website's interactivity. my long time afraid of form and script in microsoft office suite cured by google form's easy to use. in an hour I built up my survey for my google sites and published, inc checkbox, multi-choice, rate, scale, dropdown, pictures etc lots of elements of interactive. google form's response analysis amazingly rich, in pie chart, bar chart, and lots of charts that's easy understanding while informative first impression. Friday I rebuilt my portable os on a retired ssd, after failed to fix ubuntu's lingering error. this time I made the bootable images more cleaner and handier. in woz's monthly visit my dorm, I demonstrated him my websites' new element, survey. and we enjoyed snack routinely, and hot water washing feet powered by dorm's heater just recovered from broke down. dorm canteen loaned me ¥100, but God knows how we satisfied in our companion and companion of hard times. God dad, my living so far designated to deal with a salary ¥3000/month, how real during hopes and joys in dealing with the only source of income. God dad, how I endear my life within this tiny time space here and now on the planet and before climate disaster, while we stride into big chances never seen holy grants. bring me sooner my Crowned Queen from Japan, Asoh Yukiko, and my vested Empire of China, and our future new land of north and water peculiar cold sweet. grant my cyberspace startup booming in business and influential of public mind. thx for my new summer pants with mobile pockets my nephew offered free weeks ago in my hard time.
0 notes
Text
sync with woz's new school term.
Feb 27, 2017
dreamt 2 or 3 my privileged senior middle school alumni, Zhu Zehua, who's technical subjects usually score quite high, and some others long time no see. we corporate and compete to produce rebellion weapons. we also compete intelligently. we passed my hometown dam, spring well with crowd among which we escape enemy's hunting. this week a bit sad. gay in neighbor dorm room desperate stalks me. surveillances my usage of toilet and follows to shit and leave it unflushed. the sickened soul pretends coughing for quite some time and he should dies in illness. my son's mom, the small bitch also tried her best to challenge me. they mimic my son's monthly cinema day and invited her mom to go cinema the night before my gathering day with my son. all her knowledge is outdated and poor quality but still she day by day gathering pupils at her house for tuition. one of her girl friend whose father lent me camera when my son given birth at hospital found some old photos of my son in the hospital agrees to send me those precious photos but now hold back by the bitch, son's mom, for a bargain. my son yesterday irritated me and I had to give him a lesson. we previously agreed that our new broadband was a bliss holy and we should make good usage. but on Sunday when I went to see him, he even didn't power on broadband router in his house, but just reading paper book of rephrased Chinese classic, A Dream of RED Mansions. I went mad with his ignorance. I show brutal violent threat and scorned him for near half hour in cause of his failing VPN and system update. I didn't mean hurts but remind him his work, his future indispensable with high tech including internet, while his mom and his grandma actually not equipped it, for their cheap work mainly related with primitive tools. my son show resolve when we went for lunch and shower, even after I bought him extra fruits. on way returning to my dorm, I pray God to let it the hard time for us to defeat, to slaughter our enemies by hand and will. I beg Holy rewards us thicker after the adversity and allow us to stick out of the dark curtain and smile. in the night I felt guilty upon my son, and boring and sad for shopping online. I bought my son a spring trousers with cellphone pocket. I also ordered myself one but run out of money. so I entreated my kid brother to pay. but the contemptible man enlist my phone number into his blacklist to evade confrontation with me. God, let me remember the revengeful shame sinful people insult us, the glorious One. bring me sooner my Royal China to sustain the eastern Asia. bring me sooner Asoh Yukiko, my Crowned Queen from Japan for peace among our heritage, our once more glory cover half pacific ocean. grant us memories of retaliation.
Feb 16, 2017
the day before yesterday I worked overnight. then yesterday I felt inspiration in ladies fulfilled my heart. I admire them so much, and sympathetic to their pleasure seeking and concerns while none of them lives in my life in past decade. in the night I dreamt first played with kids. then among a kindergarten, I with my men with shotguns played with kids crossword puzzle. we shoot to answer. then I likely a royal captain of firearm brigade, operated them in war field where fire distance matters. after wake up I wonder the small figure in dream is Napoleon, who relentless with war fire till saw his own failure and death after challenge Russian, the iced land. I saw relentless love attempts for his concerned, esp women in his life, in prescribed relief of embrace of death against doomed premature failure. I felt dizzy after morning alarm. even breakfast in canteen is satisfying, I still trying finding nap after settle here my workload. last afternoon bankcomm clearance crew buzzed in, show their interest to interview. there is nothing new in their probation. they impotently demanded me return at once my credit debt of ¥10000 while It clearly out of possibility in my situation, in which recent 3 months steadily returning, ¥2000 paid every salary day. in the mid after found their only aim is to intimidate me, I claimed they incapable to negotiate with me, for there is nothing valuable or granting policy in their holding card, so I arbitrarily quit the conversation. my work space just resumed, I enjoyed my favorite Chinese podcasts, and Amazon prime video in the rest of the day. God dad, last Monday after my ICBC monthly credit statement revealed ¥700 left under account, I immediately renew zhone 19th domain, billingzhu.com for my 2nd son, to its longest life span, 5 years for ¥511. dad God, there is only one thing unfinished in 2016 as annual, woz's 12 domains renewal. grant us financial freedom to do the job. bring me sooner my Royal China to sustain my offspring. bring Asoh Yukiko, my Crowned Queen from Japan, to home my new family. bring 2017 new monument for ever growing mission to revitalize eastern Asia, for the grace and persistent commitment of Chinese and Japanese for thousand years forged in Ming Dynasty under my ancestor's title, Zhu's. thx dad God, for the snowing night yesterday and this morning so quiet in sober.
Feb 10, 2017
dreamt of complicated time space pair. after 2 busy days at dorm, heat gathered in central China gradually melt. my nose ran water a lot, and shit softly, too. last night I perceived erotic dream drove by full sperms, but in fact I didn't wet last night. rather, in dream I got insight of time-space tangle. I saw a dynasty broke down and lots of strange behaviors, like soldier don't know who to obey, court women don't know how to survive in riot era. I saw my Nankai alumni went class while I drift wild. I saw when time dissolves, events in space can be floating around, losing their sequence. the result and the cause in different time location can't be replaced, otherwise there will be forecast, in time travel paradox. these days hard economy again pestered me. I only gain a much shrinked ¥3000 in 2016 as year end bonus from QRRS, my once and long time employer, comparing near ¥7000 in 2015. a policy gain, aid for poor staff, ¥1000 offered to me by labor union. I handed over to dorm canteen at once, and next day I had to borrow ¥200 again for living expense. now I have debt ¥1000 to local contacts, and my anual renewal of zhone domains yet complete. ¥2000 will do the job like a breeze. then again every month I will fight for dinning out twice a week with my son woz for gathering, and my pills will add another ¥100. in the 3rd hometown flight tour, I almost broke up with my kid brother who contempts me and cheats me into endless waiting his aid. now my salary, at its best around ¥3000, barely afford our lifestyle including credit debt penalty. but, God, how I lucky in such failing economy maintaining such a small burden of investment! and watch the grand produce of my endeavour and willful. God, dad, I see so many affirmatives in holy message. please firmly attach me onto faith of Christian. bring me sooner my Royal China to fasten the falling treasure. bring me Asoh Yukiko to put together the Empire dream and stipulation. grant me financial independence to safeguard our startup so strong online.
Jan 31, 2017
the night before yesterday I gave my son a lesson, for he too open and vulnerable upon cheap offers. this night I felt blessed when we ready to sleep. I first dreamt in art college saw many students and computers running a software likely robohelp or tin?in. its a series tools including 3d modeling, illustration, and presentation. in dream I felt glad to fetch my pastime skill and sharpen them. I felt that would more or less let me more energetic. then in my hometown village, facing neighbor village there are 2 modern office malls where once rice field. many small companies rent space there and share introduction multimedia, project management or progress report online there. I still dwelling on the robohelp and thought about app as service, or the functions of presentation. I tried hard to sync our data or put our running data into the app. the detail of program very lengthy in dream, even cross the intervene of getting up to pee. 2 days ago I finally got informed that our train ticket booked, after more than 60000 times bidding online by our travel agency, ctrip.com. so last unease resolved and we really needn't hurry, just as holy affirmed. my son once repulsive upon my teasing infant of my nephew's, a 16 month old boy, after I told him why I glad to help infant with empowering them with full heart support, he forgave me and I thankful for his considerate. his willful pal, the grandson of my 2nd elder sister, also quit hijacking my son with all flattery. I also openly talked about fault of my 2nd elder sister whose family less attractive and colder in heart, with her husband and daughter-in-law. the daughter-in-law is a slim tall woman with adorable configure and I tried to help her when she loathe to chores. I hope they don't pitfall like some of my relatives. after all, we are family from my passed grand father, God in heaven now. this is a sunny morning with clouds. hopeful it will more shiny later. God, dad, bring me sooner my Royal China to home my offspring, to guest my concerned. bring me financial independence to liberate some of my relatives trapped in wrong idea and habit. grant me adequate fund to renew our domains, the last task unfilled upon new year 2017.
LOFTER:riveryog, 旎宫嘉坊 http://ift.tt/2m0DCJP
0 notes