#wireless ATM modem
Explore tagged Tumblr posts
Text
Mastering Triton Ft5000 Series ATM Machine Installation: A Step-by-Step Guide for 2025

As the banking and retail industries continue evolving with advanced technology and user-focused design, automated teller machines remain vital access points for cash services. The Triton FT5000 Series is a highly reliable through-the-wall ATM model known for its durability, modular design, and security features. Whether you're a business owner, installer, or technician, mastering the Triton Ft5000 Series ATM Machine Installation process is key to ensuring seamless performance and long-term functionality.
In this guide, we walk you through the essential steps and best practices to confidently install the Triton FT5000 Series ATM in 2025.
Understanding the Triton FT5000 Series ATM
Before beginning the installation process, it’s important to become familiar with the core features of the Triton FT5000. This machine is engineered for high-volume locations and features a user-friendly interface, a robust construction suited for exterior wall installations, and enhanced security components such as vault locks and EMV card reader support.
The FT5000 is modular, which allows for simple servicing and upgrades. Its compact footprint and through-the-wall design make it ideal for retail centers, bank branches, or 24-hour walk-up installations. Knowing your machine’s capabilities will help you make informed decisions during the installation phase.
Preparing the Site
Proper site preparation is crucial to a successful installation. Start by selecting a secure and visible location with easy access for customers. The Triton FT5000 requires a solid wall surface that can support its weight and maintain alignment with its front-access panel. Make sure there is sufficient space behind the wall for installation, maintenance, and loading of the cash cassette.
Next, ensure all electrical, internet, and grounding requirements are met. The FT5000 requires a dedicated 120V power supply and a secure data connection (Ethernet or wireless modem). It is also essential to verify ADA compliance and safety standards for your region, such as minimum clearance and reach requirements.
Installing the Triton FT5000
Once the site is prepped, it’s time to begin the Triton Ft5000 Series ATM Machine Installation. With assistance, position the ATM to align precisely with the wall cutout. Use mounting brackets and bolts to securely fasten the ATM to the wall and the floor. This prevents shifting and tampering while maintaining the integrity of the weather-sealed frame.
Once physically mounted, proceed to connect the power and data lines, verifying the UPS (Uninterruptible Power Supply) is integrated if required. Carefully load the cassette and configure the software to establish communication with the host processor. Ensure all internal components such as the receipt printer, card reader, and cash dispenser are properly installed and calibrated.
Testing and Configuration
Testing is a critical phase of installation. After powering up the ATM, perform a series of diagnostic tests through the administrative menu. These tests include checking the keypad, card reader, receipt printer, and cash dispenser.
Next, configure the network settings, terminal ID, and encryption keys required to process transactions. Depending on your processor or bank network, you may need to coordinate with a technician or support team to finalize the setup. Be sure to simulate transactions to ensure seamless communication and function before going live.
During testing, pay attention to the screen interface, ensuring the brightness, prompts, and branding are correctly displayed. If using custom graphics or voice guidance, confirm all media files are loaded and functioning.
Final Touches and Maintenance Plan
With the installation complete and tested, apply any required security decals and notices. Confirm that surveillance cameras, lighting, and signage are correctly positioned for maximum visibility and compliance with local ordinances.
Equally important is establishing a regular maintenance plan. The Triton FT5000’s modular design makes routine servicing easier, but preventive maintenance ensures longevity. Schedule inspections for internal cleaning, firmware updates, and hardware checks every 3–6 months depending on usage levels.
Moreover, train staff or service providers on basic troubleshooting steps. Quick response to minor issues can reduce downtime and maintain customer trust.
Conclusion
Completing a Triton Ft5000 Series ATM Machine Installation in 2025 requires technical skill, attention to detail, and strategic planning. From choosing the right location to final system configuration and testing, every step is vital to delivering a secure and user-friendly cash access point. By following this guide, you’ll be equipped to manage the installation effectively and set the foundation for long-term ATM reliability and performance.
0 notes
Text
Where Is Chris Tucker? Jackie Chan Needs Him for 'Rush Hour 4' (And So Do We)
www.inhandnetworks.com
Ten years have passed since we last saw detectives Young Lee and James Carter taking down the Chinese mafia on the big screen in the Rush Hour franchise. Now, Jackie Chan, who played Lee in the first three movies, is calling on Chris Tucker, his screen partner, to agree to Rush Hour 4.
In an interview with Power 106’s The Cruz Show Wednesday, Chan revealed that there was indeed a Rush Hour 4 in the works. But there is one problem: Tucker has not yet signed on.
“[It’s coming] next year,” Chan said. “For the last seven years, we’ve been turning down the script, turning down the script. Yesterday, we just agreed.”
Keep up with this story and more by subscribing now
Although Chan seemed excited to finally have another Rush Hour in the works, he made it clear that if Tucker wasn’t involved, he wouldn’t be either.
“Next year [we’ll] probably start—If Chris Tucker agrees,” he said. “It’s not about money! It’s about [having] time to make. I tell Chris Tucker, ‘Before we get old, please do Rush Hour 4.’”
Despite being 64 years old, Chan does not believe he or his 46-year-old castmate are too old to create another action-packed film. “Rush Hour you can do anytime,” he said.
In their last outing, 2007's Rush Hour 3, the partners were causing mischief in Paris during a mission to find an infamous mob boss. In Rush Hour 2 (2001), they were causing trouble in Lee’s native Hong Kong after an explosion at the U.S. embassy killed two Customs agents. And before that, when the unconventional duo was first teamed together, they were tearing up the streets of L.A. to find a Chinese diplomat's daughter who had been kidnapped.
Tucker, once one of the highest-paid actors in Hollywood, has kept a low profile in recent years. With the buddy-cop franchise and the classic Friday under his belt, the former Def Comedy Jam icon seems to enjoy staying out of the spotlight, appearing on screen occasionally in small roles like Danny in 2012’s Silver Linings Playbook. In 2015, he re-emerged briefly for his own stand-up special on Netflix.
During an interview with the Los Angeles Times ahead of his Chris Tucker Live Netflix special, the actor said he’s still been hard at work.
“I went back to my roots,” Tucker said. "Having a lot of fun. It's been great doing what I wanted to do. I never stop working. I'm always on the road, honing my craft. I'm touring around the world: Australia, the Middle East, Asia, Malaysia, Singapore.”
崀山, 崀山科技, 崀山科技全球服务中心, LangShan Technology Global Service Center, LangShan Technology, LangShan, china webdesign, seo, web design, 企业建站, SEO, joomla template, joomla webdesign, joomla web design, joomla seo, wordpress themes, wordpress webdesign, wordpress web design, wordpress seo,magento themes, magento webdesign, magento web design, magento seo, opencart themes, opencart webdesign, opencart web design, opencart seo, prestashop themes, prestashop webdesign, prestashop web design, prestashop seo, 崀山, 崀山科技, 崀山科技全球服务中心, LangShan Technology Global Service Center, LangShan Technology, LangShan, china webdesign, seo, web design, 企业建站, SEO, joomla template, joomla webdesign, joomla web design, joomla seo, wordpress themes, wordpress webdesign, wordpress web design, wordpress seo, magento themes, magento webdesign, magento web design, magento seo, opencart themes, opencart webdesign, opencart web design, opencart seo, prestashop themes, prestashop webdesign, prestashop web design, prestashop seo, wordpress shop, wordpress plugins, wordpress plugins shop, lte, 4g, 4g-lte, 3g, umts, dsl, ethernet, cellular,gprs, wireless, wired, wi fi, vpn, m2m vpn, openvpn, ipsec-vpn, secure, reliable, dual sim, 2 sim, redundant, rugged, din rail, din rail mounting, ul certified, fcc certified, ptcrb certified, verizon wireless certified, att certified, ce certified-, emark certified, azure iot certified, cost effective, ipv6, python programming, reliability, security, high-speed, lte cat 1, router, gateway, routers, cellular gateway, modem,hardware, software, cloud platform, applications, ethernet switch, managed switch, vehicle router, car router, dtu, data terminal unit, computer, vending computer, vending pc, manufacturer, manufacturing, android computer, iot, industrial iot, industrial internet of things, m2m, industrial m2m, m2m communication, remote communication, wireless m2m, remote connectivity, remote access, m2m connectivity, iiot, industrial networking, industrial wireless, m2m iot, smart vending, touchscreen vending, cloud vms, telemeter, vending telemetry, cashless vending, light industrial, commercial, distribution automation, distribution power line monitoring, fault location, fault detection, da monitoring, smart grid, transformer monitoring, intelligent substation, goose messaging, remote machine monitoring, remote secure networks, remote secure networking
#secure#reliable#dual sim#2 sim#redundant#wireless ATM modem#IoT Remote Monitoring#industrial wireless#branch-networking#wireless-m2m#Secure remote networks#router dual sim#data terminal unit#android-computer
1 note
·
View note
Text


01/12/21: Here are my Wednesday fleamarket finds! I found a guy selling a whole lot of gaming stuffs, but I didn't have enough money. I spent most of it the day before at the thrift store. But I think I still bought a nice enough lot. But before that, I did find other things from other sellers. My first buy was on a whim, I found a Korean girl group k-pop CD for $2.00. I'm not really into that music, but I can resell it to a teenager that would like it. Next was an Xbox 360 game and a music cd of 50's band The Platters; $3.00 for both. I found Mario 3 on GBA for $6.00, so that was nice. For $13.00 it was three more xbox and one wii game, an empty 3ds case and two Xbox breakaway cables.
But the best items came from one guy and his stall. He had tubs full of games. Some decent titles. I had many of them already. But his prices were quite reasonable in my opinion. If only I had gone to the ATM before. Plus, I couldn't stay too long cause I had other errands to do and I had to take my mom back home to our place in Mexicali. I kept finding games and my tally kept going. Ps1, ps2, GameCube and other games, guy had a bit of everything. Grand total as the stack got bigger, was $100 dollars.
There was a black Gameboy pocket (no battery cover), A wacky wireless receiver for a JPN neo geo pocket. A decent selection of ps2 games, two less common ps1 fighting games. Four wii sensor bars. Spyro 3ds. Empty cases for some rareish games, the complete series for Invader zim, a vita charger and ps2 modem.
I could have easily spent another hundred there. I do hope he's back again next week. There's still more goodies I want. Some for me to keep and others to flip.
#video games#videogame collecting#flea market#videogame accessories#ps2#xbox#xbox 360#fighting games#neo geo pocket#wii
3 notes
·
View notes
Text
In-Depth Knowledge of GPON
Optical fiber networks operate on different passive optical network (PON) standards. A PON is a network system specific to fiber technology that delivers broadband network access to homes or businesses. One of many PON standards is GPON. This article will provide some knowledge about GPON

What is GPON?
Gigabit passive optical network (GPON ) is a point-to-multipoint access network. Its main feature is to use passive splitters in the fiber distribution network (ODN), enabling one single feeding fiber from the provider’s central office to serve multiple homes and businesses. In addition, GPON uses an IP-based protocol and asynchronous transfer mode (ATM) encoding to integrate voice and data traffic on the same network.

Components of GPON
There are three main components of GPON: optical line terminal (OLT), optical fiber splitter, and optical network terminal (ONT).
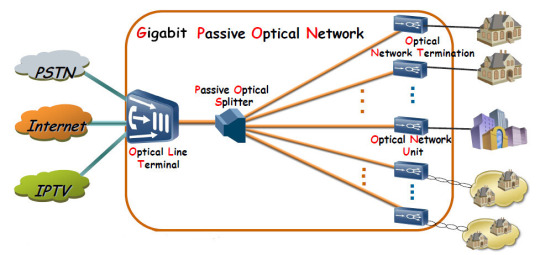
OLT
OLT is a device that serves as the service provider endpoint of a passive optical network. It is an active ethernet aggregation device that is located in a data center or the main equipment room. An OLT converts the optical signals to electrical signals and presents them to a core ethernet switch. The OLT replaces multiple layer 2 switches at distribution points. OLT distributing signal is connected with backbone cabling or horizontal cabling through optical splitters, which are connected to the optical network terminal at each work area outlet.
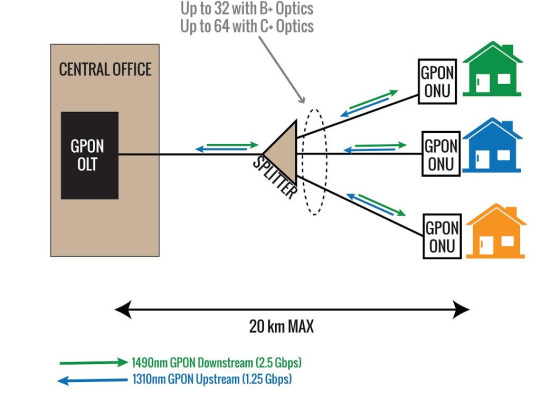
Optical Fiber Splitter
The optical fiber splitter is an integrated waveguide optical power distribution device that can split an incident light beam into two or more light beams and contain multiple input and output end. A GPON splitter often has a specified split ratio that could be 1:4, 1:8, 1:16, 1:32, and 1:64, depending upon the number of outputs required. The most common splitters deployed in a GPON system are uniform power splitters with a 1xN or 2xN splitting ratio, where N is the number of output ports.
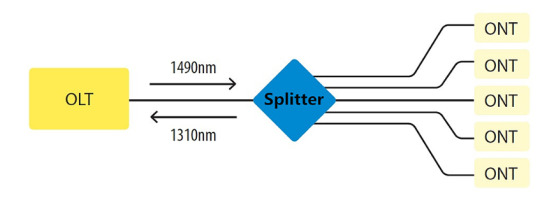
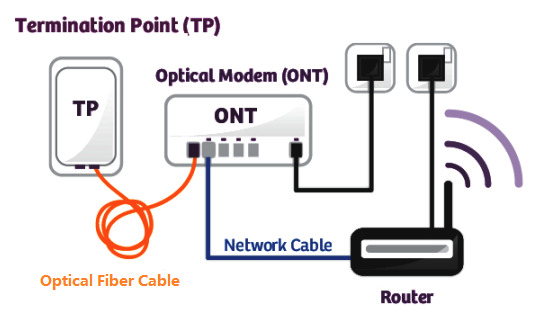
ONT
ONT also called the modem, connects to the termination point (TP) with an optical fiber cable, and connects to the router via a LAN / Ethernet cable. It converts the optical signals to electrical signals to deliver to the end device. ONT always has multiple Ethernet ports for connection to IP services such as CPUs, phones, wireless access points, and other video components.
Benefits of GPON
GPON has the benefits of high bandwidth, high security, low cost, easy installation, longer life, long-distance transmission, space-saving, energy-saving, scalable, and future-proof solutions.
Applications
GPON is used in data, video on demand, IPTV, VoIP, CATV, CCTV, FTTH, FTTB, FTTC, FTTD, FTTO, FTTM, FTTW, D-CCAP, etc.

Conclusion
GPON is a future-proof solution for providing broadband services. It provides high bandwidth, low cost, and long-distance transmission. Sun Telecom specializes in providing one-stop total fiber optic solutions for all fiber optic application industries worldwide. Contact us if any needs.
1 note
·
View note
Text
Buy An ATM

The Hercules is a 4G LTE CAT-1, single SIM modem ideal for low data usage applications such as ATMs, vending machines, and wireless laundry facilities. Its performance in fringe areas has earned it a reputation for being the most reliable modem on the market. In a recent head to head comparison the Hercules performed 9 times better than the competition!
Buy An ATM
0 notes
Text
M300 4G Modem
If you are searching for a 4G Modem, the E-Lins M300 series Cellular Modem is a good choice for you. It is a complete wireless USB data modem providing global cellular network connectivity, where cellular signal available, with 4G/3G/2G fallback capabilities for ensured access to the internet anywhere. The M300 is an easy to install productivity tool designed to provide maximum accessibility to the mobile professional allowing quick access to the internet for real-time business transactions, email, web browsing and more.
E-Lins’ mobile data products are widely used in more than 50 countries and regions, and more than twenty industrial fields, such as power control, water schedule, traffic, oil field, weather forecast, environmental protection, street lamp control, post, bank and many other areas.
What hot spots are M300 with?
Broadband M2M communications/SIM failover/standby APN
3G/4G failover for fixed line broadband connections
Rapid service deployment applications/Support At command/USB port
What Main features are M300 with?
■ Basic
l Auto install software
l Easy connection, directly to the PC or laptop by using a provided extension cable
l High speed with 4G LTE 100Mbps and back compatible to HSPA data (up to 14.4Mbps downlink and 5.76Mbps uplink) and backward compatible with EDGE/ GPRS/ GSM data connectivity (up to 216~384 Kbps)
l Visual feedback on connection status with the LED and the easy connection software, including signal strength indication
l Compatible with nearly all modern desktop and laptop PC’s equipped with Microsoft OS (2000, XP, XP Pro and Vista)
l Industrial design with intelligent software capabilities, making it a reliable cellular solution for data collection and transmission
l Plug-and-play design with easy-to-use software interface for easy integration
l Easily manage and control distributed remote devices over the air
l Built-in Watch Dog
l Real-time Clock (RTC)
l Remote Data Monitor and Control
l Reliable GSM/GPRS/EDGE/UMTS/HSPA network connectivity, providing fast and cost-effective long-range wireless communication
l Always-On-Line
l Easy-to-use
l Industrial design with surge protection
l Local and remote configuration over the air
l No need to build expensive fixed line network, saving cost substantially
What is the Typical Diagram and Industrial Applications?
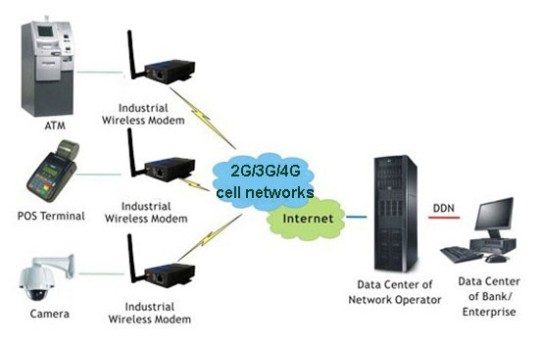
l Remote Data Monitor and Control
l CCTV, security surveillance
l Water, gas and oil flow metering and schedule
l AMR (automatic meter reading)
l Power station monitoring and control
l Remote POS (point of sale) terminals, ATM,
l Traffic signals monitor and control, Traffic info guidance
l Oil field, weather forecast, environmental protection, street lamp monitoring and control
l Early Warning of Mountain Torrent
l Fleet management
l Power distribution network supervision
l Central heating system supervision
l Weather station data transmission
l Hydrologic data acquisition
l Vending machine
l Telemetry, SCADA
l Vehicle logistics and diagnostics controlling
l Parking meter and Taxi Monitor
l Telecom equipment supervision (Mobile base station, microwave or optical relay station)
The M300 series Cellular Modem sets up in minutes, making it easy to use while on-the-go. If your case or project requires a smart 4G Modem, M300 is a excellent choice and do not hesitate to contact with E-Lins Communication Co., Limited.
0 notes
Text
Curiosity Technology Adapted to Detect Gas Leaks from wordpress plugins Pipelines
www.inhandnetworks.com
This artist’s concept features NASA’s Mars Science Laboratory Curtouch screen for vending machineiosity rover, a mobile robot for investigating Mars’ past or present ability to sustain microbial life. Image Credit: NASA/JPL-Caltech
Technology adapted from NASA’s Mars rover program is being used to develop a hand-held device that will help find and fix natural gas leaks from gas pipelines, with the goal of reducing emissions of greenhouse gases.
In collaboration with NASA’s Jet Propulsion Laboratory in Pasadena, California, Pacific Gas and Electric Company (PG&E) announced that it is testing state-of-the-art technology adapted from NASA’s Mars rover program. Originally designed to find methane on the Red Planet, this laser-based technology is lightweight and has superior sensitivity to methane, a major component of natural gas. The technology applied back on Earth helps guide PG&E crews using a tablet interface to identify possible leak locations, fast-tracking their ability to repair gas leaks.
“Our pursuit of this technology is evidence of our commitment to our mission of becoming the safest, most reliable utility in the country. We are using out-of-this-woindustrial l2tp cellular routerrld technology to find and fix even the smallest leaks in our system. By investing in innovation today, we are helping build a positive energy future,” said Nick Stavropoulos, PG&E’s executive vice president of gas operations.
On September 29, a new law, SB 1371, required the California Public Utilities Commission (CPUC) to open a proceeding to adopt rules and procedures that minimize natural gas leaks from gas pipelines, with the goal of reducing emissions of greenhouse gases, such as methane.
The hand-held device is the latest piece of advanced leak detection technology being embraced by the utility and is expected to be available for use in 2015. The development of this to IoT Remote Monitoring ol is part of a collaborative research effort at Pipeline Research Council International (PRCI).
“It’s rewarding to be involved in projects that translate JPL technological capabilities to meet industry needs, technologies which ultimately should help enhance safety and reliability. PG&E’s role as a collaborator with JPL on our PRCI-funded effort is essential to efficiently adapt the JPL methane sensor into a field-ready hand-held leak detection system,” said Andrew Aubrey, JPL technologist.
Pacific Gas and Electric Company, a subsidiary of PG&E Corporation (NYSE:PCG), is one of the largest combined natural gas and electric utilities in the United States. Based in San Francisco, with more than 20,000 employees, the company delivers some of the nation’s cleanest energy to nearly 16 million people in Northern and Central California.
Image: NASA/JPL-Caltech
Tags: cellular modem ethernet, 4g LTE router, 3g wireless router, 4g LTE router with SIM card, cellular router vendor, verizon 4g LTE router, best industrial wifi router, 4g modem router, 4g modem router wifi, att 4g router, cellular router wifi, industrial multi sim cellular router, m2m cellular router, verizon industrial router, 4g lte gateway, 4g lte modem, industrial cellular vpn router, industrial 3g m2m, industrial l2tp cellular router, industrial ethernet router, plc router, 12vdc lte router, 4g lte router dual SIM, multi SIM LTE router, cellular router manufacturer, edge gateway, industrial iot gateway, overhead line sensor, distribution line sensor, distribution line fault detection, medium voltage smart grid sensor, MV smart grid sensor, smart grid sensor, power line sensor, power sensor, MV sensor, Grid Fault Detection, Line Monitoring, Grid Analytics, Predictive Grid Analytics, Grid Monitoring, Grid Analytics System, Power Fault Detection, Advanced Grid Analytics, Intelligent Line Monitoring, distribution fault detection, smart vending machine, smart vending solutions, QR code vending machine, telemetry vending machine, intelligent vending machine, touch screen for vending machine, vending software, cashless vending, coupon vending machine, iot vending machine, vending machine card reader, POS vending machine, smart vending machine software, credit card vending machine, Industrial router, cellular router, 4g router, LTE router, 3g router, M2M router, wireless router, wireless m2m router, wireless m2m, Industrial Wireless M2M, Industrial Wireless M2M Router, Industrial Wireless M2M products, M2M wireless producdts, WiFi M2M Router, Industrial Wireless M2M gateway, industrial IoT router, industrial IoT gateway, industrial LTE router, Industrial router, cellular router, 4g router , LTE router, 3g router , M2M router, wireless router, wireless m2m router, WiFi M2M Router, Industrial Wireless M2M Router, M2M IoT router, industrial wireless router, industrial M2M router, industrial LTE router, Industrial VPN router, Dual SIM M2M router, M2M gateway, IoT gateway, Industrial router, low cost industrial router , low cost cellular router, low-cost LTE router, low-cost M2M router, compact industrial router, low-cost cellular router , cellular router, low-cost 4g router , LTE router, 3g router , M2M router, wireless router, wireless m2m router, WiFi M2M Router, Industrial Wireless M2M Router, M2M IoT router, industrial wireless router, industrial M2M router, industrial LTE router, Industrial VPN router, Dual SIM M2M router, M2M gateway, IoT gateway, LTE Cat 1 router, Embedded LTE Cat 1 router, Industrial LTE Cat 1 router, Verizon Embedded modem, Verizon Embedded router, Overhead Line Monitoring, Distribution Power Line Monitoring, Fault detection & location, Grid Analytics System, Remote Machine Monitoring & Maintenance System, IoT Remote Monitoring, Prognostics and Health Management, Remote connectivity, Remote Maintenance, Smart Vending, smart vending, InHandGo, retrofit, touchscreen vending, cashless vending, cloud VMS, Transformer Monitoring, Transformer Monitoring, substation monitoring, grid LTE router, wireless communication, smart grid, Remote Automation, Remote Automation, Secure remote networks, web SCADA, Remote Diagnostics, Remote PLC programming, Intelligent Traffic Enforcement, Intelligent Traffic Enforcement, wireless networking, cellular router, Wireless ATM Solution, Wireless ATM, ATM Remote Diagnostic, prestashop 多语商城, opencart 外贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign, webdesign, seo, joomla web design, 香港網頁設計, 網站建設, 企業建站, 商城網站, 集團網站, 海外網站, 營銷網站, 網站推廣, web design, joomla webdesign, wordpress webdesign, opencart webdesign, magento webdesign, durpal webdesign, vtiger crm, adempiere erp, compiere erp, hosting, domains, vps, email marketing, joomla 网页设计, wordpress 建站, magento 大型外贸商城, durpal 门户网站, seo 网站推广, 网站自然排名, joomla 網站製作, wordpress 定制開發, opencart 維護修改, prestashop 模板修改, magento 培訓實施, durpal 定制修改, seo 營銷推廣, 外鏈收錄排位, joomla, wordpress, opencart, prestashop, magento, durpal, zencart, crm, erp, edm, marketing, joomla template, wordpress themes,
#Verizon Embedded router#distribution line fault detection#wireless ATM modem#ATM Wireless Connectivity#distribution line sensor#Fault detection & location#LTE router VPN#router industrial#vending telemetry
0 notes
Text
300+ TOP Telecom Project Manager Objective Questions and Answers
TELECOM PROJECT MANAGER Multiple Choice Questions :-
1. Which of the following is a function of a workflow engine? a. to provide network repair information for field service technicians b. to prompt customer-care representatives to sell specific service packages c. to facilitate communication and task sequencing among various OSSs d. to draw graphical network maps for capacity planning Ans: c 2. Speech Servers support N+1 Redundancy by networking hosts together. During a failover scenario, which component in the secondary Speech Server takes over and manages Speech Server resources? A. LVR B. RCM C. CCM D. PMGR Ans: D 3. Which of the following is not a protocol used for communicating with network elements? a. CMIP b. SNMP c. TL1 d. TMN Ans: d 4. All network elements are equipped with built-in intelligence that will reroute network traffic around trouble spots. a. true b. false Ans: b 5. Legacy systems are ________. a. systems created from parts of other systems b. any RBOC OSS c. older, stand-alone mainframe systems common to ILECs d. systems used to interconnect LEC OSSs Ans: c 6. OSS interconnection is mandated and a critical factor in determining ILEC entry into long-distance markets. a. true b. false Ans: a 7. Interconnection gateways often perform error-checking functions to help speed the ordering process. a. true b. false Ans: a 8. Which of the following is not an inhibitor to DSL deployment? a. DSLAMs cannot be housed with circuit switches. b. Some lines carry load coils and filters that can negate DSLs. c. LEC line records are often inaccurate. d. Services riding adjacent lines can interfere with DSLs. Ans: a 9. IP guarantees time and delivery sequence for all packets on a network. a. true b. false Ans: b 10. When configuring for N+1 redundancy, where must the Speech Server resources be located? A. the primary vpshosts file B. the secondary vpshosts file C. the existing Speech Server group D. the primary node's Pool Manager (PMGR) Ans: A

TELECOM PROJECT MANAGER MCQs 11. Which component, common on both the Media Processing Server (MPS)Application and Speech Server, uses and manages call conferencing, phone line application, and Speech Server resources? A. Pool Manager (PMGR) B. Call Control Manager (CCM) C. Resource Control Manager (RCM) D. Vengine Application Management Process (VAMP) Ans: A 12. What is the maximum number of Speech Server nodes that can connect to one DCC 3000? A. 8 B. 12 C. 24 D. 32 Ans: D 13. Each of the following is an advantage that wireless local area networks deliver to businesses except a. greater network security b. increased productivity c. time savings d. financial savings Ans: a 14. VoWLAN uses a WLAN for a. enhanced security transmissions b. voice communications c. roaming between wired segments d. segmentation Ans: b 15. The primary advantage of wireless technology is a. low cost b. decreased flexibility c. mobility d. bandwidth Ans: c 16. Each telephone subscriber is connected to several central offices (COs) a. True b. False Ans: b 17. The local loop, or the connections between individual subscribers and central offices, is also known as the last mile. a. True b. False Ans: a 18. The ________________ is a particular set of standards that allows the interworking of products from different vendors. It usually embodies a fiber- optic ring that will permit transmission in both directions. a. local-area network (LAN) b. wide-area network (WAN) c. synchronous optical network (SONET) d. common channel signaling network Ans: c 19. Packet switching is used for which of the following? a. credit-card verification b. automated teller machines c. SS7 d. the Internet and the World Wide Web e. all of the above Ans: e 20. Analog signals can be ________ by combining them with a carrier frequency. a. carried b. transported c. multiplexed d. mixed Ans: c 21. ______________ is a high-performance switching and multiplexing technology that utilizes fixed-length packets to carry different types of traffic. a. asynchronous transfer mode (ATM) b. asymmetric digital subscriber line (ADSL) c. synchronous optical network (SONET) d. none of the above Ans: a TELECOM PROJECT MANAGER Objective type Questions with Answers 22. The types of media that can transmit information in the telecommunications world are the following ______________. a. copper wire, coaxial cable, fiber, and wireless b. hybrid fiber/coax and copper wire c. wireless and copper wire d. copper wire, coaxial cable, fiber, and hybrid fiber/coax Ans: a 23. A(n) ____ is a network that connects computer systems and devices within the same geographic area. a. PAN b. LAN c. MAN d. WAN Ans: b 24. The present state of mobile wireless communications is often called ____. a. 1G b. 2G c. 2.5G d. 3G Ans: c 25. ____ is a specialized subset of telecommunications that refers to the electronic collection, processing, and distribution of data. a. Data communications b. Synchronous communications c. Asynchronous communications d. Electronic communications Ans: a 26. A(n) ____ is a type of topology that has a central hub or computer system, and other computers or computer devices are located at the end of communications lines that originate from the central hub or computer. a. ring network b. hierarchical network c. bus network d. star network Ans: d 27. Which layer of the OSI model enables the user and host nodes to communicate with each other? a. Session b. Network c. Transport d. Application Ans: c 28. Which of the following refers to ALL types of data transmissions from voice to video and receiving of data across a distance via a communication channel? A. Network B. Modem C. Telecommunications D. UPS E. All of the above Ans: c 29. Corporate networks that use the infrastructure standards of the Internet are called a/an A. Extranet B. World Wide Web C. Internet D. Intranet E. All of the above Ans: d 30. What type of signals were you using on the last occasion when you used a hand-held remote control to change the channel on your television? A. Electrical pulses B. Microwaves C. Infrared D. radio waves E. All of the above Ans: c 31. What type of signals is being used between a radio and a radio tower? A. Infrared B. radio waves C. Microwaves D. Electrical pulses E. All of the above Ans: b 32. What type of signals is being used between a cellular telephone and a cellular tower? A. Electrical pulses B. Infrared C. radio waves D. Microwaves E. All of the above Ans: d 33. Why is a digital network preferred over an analogue one? A. It is newer B. It is smaller C. It has lower power consumption D. It has higher capacity for the same bandwidth Ans: d 34. The difference(s) between GSM and PCN is : A. GSM operates in the frequency range of 900MHz while PCN operates in the 1800MHz range B. GSM is the standard used in Europe, while PCN is the one in North America C. GSM uses digital technology while PCN is analogue D. None of the above Ans: a 35. Central coordinating function and administration is carried out by a) Cell site b) BSC c) MTSO d) PSTN and BSC. Ans: c 36. The quality of voice received can be estimated and judged by a) Number of dropped calls b) Subjective tests c) Coverage capacity d) Transmitting power Ans: b 37. Which is NOT part of a typical wireless site survey? A. implementation suggestions B. access point locations C. security requirements D. access point mounting methods Ans: c 38. What are two objectives of a pre-site survey walkthrough? (Choose two.) A. identify potential problem areas B. define intended coverage areas C. assess compliance with local building codes D. determine the final location of APs and antennas E. identify sources of RF signal attenuation and RF interference Ans: a,b 39. To which parameter should the access point be set during a site survey? A. transmit only B. diversity C. receive only D. single isolated antenna Ans: b 40. The average splice loss for a multimode fusion splice is: a) 0.05 dB b) 0.10 dB c) 0.30 dB d) 0.75 dB Ans: a 41. For an optical fiber system, the essential determinants of end-to-end bandwidth are: a) The optical fiber and the receiver b) The transmitter and the optical fiber c) The transmitter and the receiver d) None of the above Ans: b TELECOM PROJECT MANAGER Questions and Answers pdf Download Read the full article
0 notes
Text
Circuit Protection Market: Potential Effect On Upcoming Future Growth, Competitive Analysis And Forecast 2025
Circuit protection devices (CPDs) are used to safeguard low voltage devices from latch ups or damage caused by lightning or electrostatic discharge (ESD). The primary goal of circuit protection devices are safety and reliability. Safety is assured by CPDs by disconnecting power in circuit in case of overvoltage or overcurrent which further eliminates electrocution and fire threats. A circuit breaker or a fuse is usually installed as CPD to prevent a wire conductor from overheating and damaging the electronic equipment and circuitry. Overheating results when too much amperage travels through a wire conductor which could generate enough heat to melt and burn wire insulation and nearby materials.
Circuit protection devices are integrated into various types of equipment including computers and laptops, cell phones, medical equipment, game systems, ATM machines, DVD players, battery packs, computer peripherals, set top boxes, modems, wireless communication systems, portable electronics, and network systems to avoid reduction in lifespan and for better efficiency. In automotive vehicles, CPDs are used to enhance driving assistance, passenger comfort, and safety.
Growing consumer awareness regarding the quality and standards of electronics products and growth of the global electronics industry are some of the factors expected to boost the global circuit protection market. Rising awareness about user-safety has generated significant demand for more advanced circuitry protection technologies. Growth of the electronics industry especially electric utilities and consumer electronics driven by product differentiation and development is anticipated to have huge impact on the circuit protection market. The move toward more compact surface mount designs have made Integrated Circuits (ICs) become further vulnerable to electrical surges through circuits, making circuit protection very important.
Planning To Lay Down Future Strategy? Request Sample https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=34556
The rapid growth of smart portable appliances with faster processors, improved sensitivity, better power densities, and extended battery life is also fueling the market growth. Rise in prices of raw materials used in circuit protection devices is expected to be the limiting factor for the growth of the market. Furthermore, strict government regulations pertaining to use of SF6 circuit breaker technology is also likely to hinder the market growth. IoT technology applications in which smart sensors are used to streamline data collection is expected to present huge market growth opportunity.
The global circuit protection market is segmented on the basis of type of protection, device, end-use, and region. On the basis of type of protection, the circuit protection market is segmented into overcurrent, overvoltage, and electrostatic discharge. Owing to growing adoption of overcurrent protection solutions, the overcurrent sub segment is likely to hold significant market share in the coming years. On the basis of device, the market is divided into ESD protection, fuses, circuit breakers, and surge protection devices. The circuit breakers segment is further divided into vacuum circuit breakers, SF6 circuit breakers and others.
Request For COVID19 Impact Analysis Across Industries And Markets - Circuit Protection Market
By end-use, the market is classified into automotive, construction, electrical equipment, energy and others. Need to pass regulatory standards of testing by various types of electronics components and durable or nondurable electronic consumer goods is expected to drive the market from electrical equipment sub segment. Geographically, the circuit protection market can be segmented into North America, Europe, Middle East & Africa, Asia Pacific, and South America. Substantial growth of consumer electronics in Asia Pacific, especially in emerging economies including China, Japan, and India is anticipated to drive the regional circuit protection market over the forecast period.
The global circuit protection market has a large number of players, though with technical advancements, the market is expected to witness new entrants from developing regions. Some of the key players in the market are Siemens AG, ABB Ltd., Schneider Electric, Eaton Corp. PLC, Mitsubishi Electric Corp., On Semiconductor Corp., Rockwell Automation Inc. General Electric Company, Larsen & Toubro Ltd. and Texas Instruments Inc.
More Trending Reports by Transparency Market Research –
Air Cargo Market https://www.prnewswire.com/news-releases/air-cargo-market-to-expand-at-a-cagr-of-4-9-by-2025--due-to-growing-effective-options-for-goods-transportation-noted-tmr-300839626.html
0 notes
Text
Underwater Acoustic Modem- Challenges, Technology and Applications - A Review Survey- Juniper Publishers
Abstract
Today, underwater acoustic communication is developing for its various applications. For signal transmission in underwater using ocean/ sea/lakes/rivers as a medium an appropriate underwater acoustic system is required. The significant characteristic of ocean makes the underwater communication difficult using electromagnetic waves. The characteristics of an acoustic signal make a good candidate for data transfer in underwater. The underwater communication is furthermore challenging due to factors like reverberation, attenuation, scattering and sea characteristics, etc., apart from various sources of ambient noises due to natural and man made. Thus, an underwater acoustic modem plays a vital role for long distance signal transmission in underwater. Hence, it is important to study the various types of underwater acoustic modems. This paper provides a comprehensive overview of recent development and challenges in various underwater modems. This survey provides the operational classifications of modems under various frequencies. It also addresses the gaps in development of modems for long distance underwater communication.
Keywords: Underwater communication; Signal processing; High frequency modem
Go to
Introduction
Over two third of earth's surface is covered by water. There are many areas in ocean that are unexplored. The main reason is for the minimum technological advancement in the field of oceanography compared to land and space. In recent years the underwater communication has gained massive popularity. The general classification on frequency of use, distance covered, speed of signal transmission, types of signal used, data rate etc. for various communications medium is shown in Table 1. Today, compared to terrestrial, space communication, underwater communication is one of the most difficult modes of communication. Underwater acoustic communication can be termed as the process of sending and receiving. Various signals/ messages using ocean/sea as a medium. Communication in ocean can be carried by either wired or wireless. The major issue in using the wired medium lies in the deployment cost of cables and external interventions due to aquatic animals and ships which are unavoidable. Hence, the alternative wireless medium requires more attention. Though, electromagnetic waves are used for transmission in land and space communication, it cannot be used for underwater due to the properties of ocean. Hence the alternate is an acoustic signal transmission. The velocity of sound in sea water is determined by three factors: the temperature of the water, salinity and the hydrostatic pressure. The speed of sound in underwater is high compared to terrestrial. Underwater acoustic channels have large delay spreads due to reverberation which further leads to strong frequency selectivity. Since the acoustic channel is highly variable the underwater acoustic modem is preferred for reliable underwater communication.
Go to
Classification Of Acoustic Modem Based On Frequency
The modem is used for the purpose of effective transmission of acoustic signals in underwater. The general block diagram and modem classifications on frequencies are shown in Figure1. The underwater modems are broadly classified into two types depending on the operational frequencies as low and high frequency modems. Low frequency modems are used predominantly as they provide long range communication at low channel bandwidth which further results in low data rate. The High frequency modem provides higher bandwidth and high data rate but high frequency signal are easily absorbed in the water, which limits the usage of high frequency signals. This paper makes a comprehensive study on overview of different types of acoustic modems operating at different frequencies. Till today, many acoustic modems have been implemented for research as well as commercial purposes. Commercial modems are mostly used for data collection, underwater monitoring, positioning and telemetry.Technical parameters like modulation, bandwidth, data rate, transmission range, application and power of few underwater acoustic modems available in commercial is represented in Table 2.
Commercial modems
Link quest [1] sound link underwater acoustic modem uses a cutting edge broadband acoustic spread spectrum technology. The data rate achieved is 38.4kbps with a bit error rate of less than 1010 and significantly reduction in power consumption. This system features advanced hybrid modulation, channel equalization, automatic rate adaptation with suitability for horizontal and vertical environments. Aquasent[2] provides truth worthy underwater communication using OFDM, which offers high performance data transfer. To boost up the performance of the shifting sea state a special algorithm, high speed digital processor and filtering techniques were used. This has three types of model, namely AM-D2000, AM-OFDM-13A and AM-AUV. AM-D2000 used in vertical communication with a single crystal beam transducer the data rate is up to 1500bps. AM-OFDM-13A provides higher data even in multi path environment. It's used in application like oceanography and research. AM-AUV model is specially designed for autonomous underwater vehicles range is up sto 5Km depth (Table 3).
The Evo Logics [3] underwater communication modem based on sweep spread technology, which provides full duplex communication with multiple data addressing network. Each product is used in different type of application in long and short range communication. Evologics group has different modems namely S2CR 48/78, S2CR 18/34,S2CR 42/65 S2CM HS etc. Example the S2CR 18/34 modem White Line Science Edition modem enables an embedded network protocol. The modem has horizontally omnidirectional transducer beam pattern to make communication in shallow waters, the data rates up to 13.9kbps over a 3500m range with a frequency of 18-34kHz. The SNR is 10dB with smaller bit error rate less than 10-10. S2CR 18/34 on the standby mode, listen mode and receive mode consumes 2.5mW, 5- 285mW and 1.3W respectively.
Aqua Comm [4] underwater wireless modem is considered the ideal choice for underwater communications. The Aqua Comm modem is highly reliable for communications, which consumes less power with an ease of integration furthermore its small form factor and light weight. The Aqua Comm is available in 100bps and 480bps and the Aqua Comm operates with a bit rate of 10-6. Coupled with high immunity to noise and to multi-path and Doppler fading with Acoustic Doppler tolerance of±5ms-1. Broadband operation ranges between 16KHz and 30KHz. The maximum possible distance is 3km. Aqua Comm operates on Direct sequence spread spectrum/OFDM. Confirmed packet delivery with error detection. If the transmitting end does not receive an acknowledgement, it will resend the data two more times. Number of retries is configurable. Uniquely addressable, Aqua Comm provides Six digit numeric address set through host command. The voltage ranges from DC 5V to 9V.
Teledyne Benthos [5] modems are used for worldwide ocean applications. The ATM-886 provides a depth of 2000m with the weight as low as 9lbs when dry and 3lbs when wet. Its omni directional for 180° beam and directional for 60° beam.The ATM- 886 has a baud rate of 360bps and bit error rate better than 10-7 with high signal to noise ratio. It supports 704k Byte data logger standard. The processing supported are Data redundancy, 1/2 rate convolution coding multipath guard period selection MFSK and PSK modulation schemes. The distances range from 2-6km in common mode however distances can be boosted over 20km using repeaters.
The Micron Data Modem [6] has been designed to provide a reliable communication through water. This is more suitable for AUV control system. Owing to a smaller size and light weight, its used in subsea data transfer process application. The data rate is 40bps, micron data modem provides multipath noise rejection and compact size, with low error rate, low power consumption, 500m and 150m horizontal and vertical range. Micron modem working frequency band is 20-28KHz at a data rate of 40bit S-1 with an integral range function of 0.1m resolution over full range and 0.02m accuracy. The commercial underwater acoustic modem technical merits and applications are presented in Figure 2.In future the high frequency modem development should focus on the following qualities like long range, low power, small size, and higher data rate to make an effective underwater communication.
Researcher developed modem
The author Benson et al. [7] developed a underwater acoustic modem proposed for short range communication with a lower data rate. Underwater transducers are typically made from piezoelectric materials and the frequency of the transducer is 35kHz with a 6kHz bandwidth. The transmitter was designed to operate for signal inputs in a range from 0 to 100kHz. The architecture has twoamplifiers; the primary amplifier is a Class AB amplifier that provides a voltage gain of 23db with the power efficiency of about 50%. The secondary amplifier is a Class D switching amplifier which is nonlinear, but possesses an efficiency of approximately 95%, both the amplifiers working together in parallel. The transmitter achieves a highly linear output. The power management system has been designed to retain transmitter efficiency maximum over the wide range of power output levels. The receiver's architecture has a set of narrow filters with high gain. These filters are based on biquad band-pass filters, and essentially combine the tasks of filtering and amplification. The current receiver configuration consumes about 375mW when in standby mode and less than 750mW when fully engaged. An ultralow-power wake up circuit will be added to the receiver to considerably reduce power consumption. Hardware platform makes use of reconfigurable hardware, particularly afield-programmable gate array, for all the digital signal processing and control required for the modem (Figure 3).
Ethem [8] developed communication modem called the reconfigurable modem, this hardware has four major parts: power supply board, the DSP board, analog-digital interface, power amplifier, and transducers. This modem implemented in TMS32OC6713 DSP, the micro-line C6713 compact board has 64Mbyte on board SDRAM as nonvolatile memory space together with local Flash File system. This FIash File system is used to store multiple modem operation in the on board memory and select the required definition at the boot time. Therefore, multiple communication algorithms are tested in a time within one deployment without the need for multiple downloads that’s provided an environment. The acoustic receiver has two major parts: the Preamble Process block and the demodulator block the samples received from the A/D converter are fist down converted to baseband. These relaxed requirements reduce the complexity of the system and speed up the simulations. The transmitter consists of an APSK modulator and a square- root raised cosine interpolation filter. A number of symbols are selected as training symbols to be used at the receiver. The transmitter employs the same filter shape for decimation. The output of the adaptive filter is converted into soft bit estimates.
Pierre et al. [9] Presented HERMES modem which is an asymmetrical underwater acoustic modem operated in two separate frequency bands. The modem operated in band between 262.5kHz and 375kHz which has sub bands like the lower sub-band (262.5kHz to 337.kHz) carries the binary information and the middle sub-band (347-373 kHz) is used for detection purposes. The acoustic uplink uses either BPSK or QPSK modulation. The uplink resides combines both parallel doppler-compensated decision feedback equalizers combined with soft-decision BCH decoding to reduce the interferences produced by the communication channel. HERMES with a phase- lock looped DFE routine which influences this complementary solution approach. This method provides smaller bit error rate with compromising the processing power. The percentage of lost messages were reduced by nearly an order of magnitude.
Tao et al. [10] developed an underwater acoustic modem based on two types of spread-spectrum techniques, namely frequency-hopping and direct sequence spread spectrum. The external synchronization method uses the low frequency modulation technique for signal synchronization. In the software design part uses the modular programming to reuse and parameter adjustment. The physical layer contains source coding, channel coding and decoding, modulation and demodulation, synchronization capture and tracking modules. Hardware uses the transducer at thefrequency band of 13- 18kHz. Currently using only four multi-point nodes underwater acoustic communication system is extended to support multiple nodes to form large covered areas of underwater acoustic communication networking systems.
The author Nusrat et al. [11] proposed a high frequency modem with large channel bandwidth with greater link capacity. The system operating frequencies from 100 kHz to 1MHz which support 1km down to under 100m. BPSK modulation and demodulation technique is used. The proposed tunable oscillator design deal with infinite frequency resolution. The modem design is implemented in FPGA with oscillator of 50MHz. The result shows that the multiplication-free filters produces same frequency and impulse response as with multiplication filter. FPGA based modem reduces the hardware cost. The reconfigurable FPGA is a suitable choice for more robust for communication system.
Hai et al. [12] proposed a modem which uses a two systems namely SISO and MIMO system with two transmitters and two receivers. MIMO OFDM has two separate data streams in parallel. This was implemented inTMS320C6713 floatingpoint DSP with the operating frequency of 225MHz. Algorithm optimization and programming optimization techniques are used for the implementation of modem, first one is algorithm optimization performed such as convolution and CFO estimation is performed and next one is programming optimization, a few new coding approaches is performed, such as loop unrolling and compiler directives, to increase the processing speed. The realtime decoding technique is performed with remarkable margins. Nonbinary LDPC coding improves the performance relative to convolutional coding.
Lingjuan et al. [13] proposed an adaptive underwater acoustic modem which changes its parameters according to the situation. Underwater acoustic modems consist of three fundamental components namely a transducer, an analog transceiver and a digital hardware platform for signal processing and control. The receiver uses a non-coherent energy detection demodulation method. In DSSS, symbols are spreading frequency domain by multiplying with a spreading code. Both simulations and sea tests are performed. The results show that the best data rate varies for different links in a network; it changes from 40 to 400b/s for FSK, and from 600 to 1900b/s for DSSS. FSK rate adaptation gives an energy saving of 63.4%. In the same way, an energy saving of 45.8% is possible for DSSS. Data were collected at two sites at distances of 265 and 638m from the transmitter. For each site, FSK and DSSS data were transmitted at six different data rates. At each data rate, 20 packets containing 2040 symbols were transmitted.
Wangwei et al. [14] presented a new underwater acoustic modem prototype design based M-ary different chirp spread signals.The transmitted and received signals used in the chirps are wave nature and acuity is proportional to bandwidth the acoustic modem. The modem is implemented in TI TMS320DM642 fixed point DSP processor with 600MHz operating frequency.The DSP encodes and decodes the chirps signal for transmission, which are contained in a packet. The former LFM is used to trigger the receiver from standby to reception mode, and the other achieves symbol synchronization. The modem is capable of transmitting between a range of 20kHz to 3kHzwith the sampling frequency of 10kHz.
Martins et al. [15] proposed a low power high data-rate acoustic modem, based on a piezoelectric poly polymer as a transducer and a Xilinx Field Programmable Gate Array (FPGA) that can be programmed to work with different types of modulations. This test was performed using an OOK 1Mbps transmission with a 1MHz single carrier, resulting in a sine period to each bit length. In the emitter side, it is possible to observe that each high logic state is converted to a 1MHz sine wave. It is noteworthy that the serial port is operating with inverted logic, meaning that a high logic state corresponds to a '0' bit and low logic state to a '1' bit. These characteristics allow for the implementation of unmanned underwater vehicles (UUV) in real time remote control with compressed video and sound or access to the internet from a submarine.
Nathan et al. [16] investigate the transmission range of an FHFSK modem operating at several different rates across three different frequency bands. Non-coherent frequency hopping, frequency shift keying allows for a robust, low- cost physical layer solution that is particularly suited for low rate communications.Frequency hopping divides the useable bandwidth into orthogonal frequency bins. Frequency hopping can be exploited in a multi-user environment in order to share the available bandwidth by allowing a number of users to transmit simultaneously on different hopping patterns. Performance of FH-FSK at four different data rates across three different frequency bands: 7.44-12.24 KHz, 12.56-17.36 KHz, and 22.8-27.6KHz similar to those in the Micro-modem. These three frequency bands will be denoted as the 9 kHz band, the 14 kHz band, and the 2kHz band. The absorption coefficient of the acoustic medium plays a critical role in determining the received signal power, and thus, the probability of error at the receiver. This will greatly influence the deployment of an underwater network. Nodes that use the 25kHz bandwidth will need to be spaced densely within an area in order to ensure communication. However, in the 9kHz band, nodes that are separated by greater distances will have a greater chance of collisions by due to overlap of simultaneous transmissions since the received signal power decays much less slowly with distance.Brady et al. [17] proposed a design to build a platform for underwater acoustic communication research with high frequency, large bandwidth, and low power design. The frequencies used in this system were 115kHz and 351kHz. The system has to channel the transmit channel and the receive channel. The transmit channel is comprised of the DSP, the power amplifier, the tuning indicator and the broadband transducer. The receive channel is made up of the transducer as a source, protection circuitry, a fully differential pre-amplifier, an analog-to-digital converter and the DSP. This modem is implemented in TMS320C6713 with resonance around 110kHz, and the other at 304kHz. There were two functional tests which were at varying bit-length test, and a bandwidth test. The setup for the bit-length test for the 115kHz transducer, for this test, the bandwidth was constant at 57.6kHz. The length of the M-sequence was increase from 255 bits to 2047 bits. The setup for the bandwidth test for the 115kHz transducer, as the bandwidth increases from 11.5kHz to 57.6kHz one can note that the path resolution is increased.
Future direction for underwater modem
These comparative studies on various acoustic modems explain that the performance of the systems depends on the following likes type of modulation, implementation board, frequency and transducer and power consumed. The commercial modem can achieve long distance with higher energy consumption. The following will explain about the improvement study on the underwater modem to enhance the performance of the system in terms of power, bandwidth and simulation model.
Antonio [18] presents modem design with Asynchronous wakeup circuit in order to avoid the additional transducer in the modem with lower energy consumption. An acoustic wake up circuit is used to minimize the power consumption in the transmitter and receiver. The system remains in idle state until it receives wakeup signals also the sleep mode saves when the system in idle state. Push-pull amplifier is directely connected to the wilkinson power divided circuit to minimize the power consumption. A case study has been done in ITACA modem prototype. In this type of prototype Power consumption is not increased in wake up or in sleep mode when the additional circuit is added to the network.
Albert [19] proposed an asynchronous idle power management system along with the properties of acoustic modem. Two techniques is used for idle-time power management to improve the energy efficiency in underwater acoustic modem is compared. The evaluation is performed based on the four types of protocols namely Standard idle mode, optimum sleep, STEM mode and Wakeup mode is performed in terms of energy consumption, to minimize the power with lowest cost. This shows that wakeup mode saves energy than sleep cycling mode.
Alexander [20] proposed an algorithm for AUVs. An algorithm provides possible solution to the acoustic modem where the range and estimation of dead line measurement. This algorithm is best suitable in the bandwidth limited environment. The algorithm will compute a range-measurement outlier by using the past range measurements. When the bandwidth is limited a new position estimation is performed to solve the problem although this is inexpensive and its continuously will run in main vehicles computer of underwater applications. The information collected from the one vehicle is periodically shares the information to others, so there is no extra bandwidth is needed to transmit information.
The underwater communication behaviors are unpredictable by the human begins. It's difficult to forecast the signal what happens in transmitter and receiver side. For this purpose a simulator and modelling tools are developed to test the signals. P Xie [21] proposed a network simulator called Aqua-Sim, for simulating underwater sensor networks. Aqua-Sim can simulate the collision behaviors in long delay acoustic networks and the signal attenuation that underwater acoustic channels can suffer. In addition, this simulator is able to simulate three-dimensional network deployment and authors added several protocol definitions to make it more accurate. Aqua-Sim higher energy consumption and packet deliver ratio than others [22-26].
Existing mechanisms for conventional modems need to be modified, or even interchanged to suit the newly emerged technology. The view and progress expected for development of high frequency underwater modems as shown in Figure 4 should address on the following issues [26-31]
Longer distance transmission (more than 6kms),
Smaller size (at least 50% less in size compared to modems that are used for terrestrial and space communication),
High Data rate (More than 10kbps)
Low power consumption
Various modulation techniques (OFDM the excessive compact of attenuation due to its promises for higher data rate)
Implementation for real time applications (FPGA- Provides greater reconfigurable flexibility).
The recommended plan for the future development of underwater acoustic communication modem is presented below. High frequency acoustic modem has to be designed with low power consumption and software reconfigurable. By incorporating suitable modulation, equalization and coding techniques, the communication has to be highly immune to noise and multi-path fading. Modem controls of analog card and digital card and power supply modules are to be assembled in a rugged mechanical valise. The digital card has to be designed around a suitable DSP processor and a low power FPGA. The analog card has to provide signal conditioning and amplification for transmission and reception acoustic signals through underwater acoustic transducer. Power supply I/P, Transducer interface and RS 232 interface can provide on the mechanical valise. The design and development of underwater acoustic modem meant for underwater communication system between the on-shore control station and underwater device. The communication is two way and is in full duplex mode. To make an effective communication in underwater the designed acoustic modem should have the following specification [32].
General Specification
Modem has to be designed and developed with low power consumption and software reconfigurable. The modem consists of two cards:
Analog card and
Digital card.
The specifications of each card are given below.
A. Implementation of modulation techniques:
a. OFDM modulation
b. QPSK modulation
c. Chip slope keying
B. Implementation of coding techniques:
Convolution encoder with interleaver at transmitter chain and Viterbi decoder with interlever in receiver chain.
1. Development of Algorithms for channel estimation.
2. The carrier frequency for QPSK modulation is 48khz and for CSK modulation 24 to 48Kh .
3. Band rate is selectable from 100 to 4000 bits/s.
4. Bit error rate should be less than 10-6
5. The communication operating depth is upto 4000m.
6. Source level should be from 185 dBupa@1m.
7. SNR: 30dB.
8. Electrical power of o/p of power amplifier should be up to 60W.
9. The Pre-amplifier gain should be adjustable up to 100dB.
10. Modem should have Rs.232 serial interface.
11. The electrical parameters of modem are given below.
a. Input operating Voltage: 28VDC, other required voltages are to be generated using DC-DC converter or voltage regulators.
b. Current in power down mode: To be minimum.
c. Max current in transmitting mode: 4A
d. Transmitter power: 60W
12. Each mode consists of Analog card digital card and power supply modules are to be assembled in a rugged mechanical valise. Analog and digital card specifications are given below with the diagrams.
Digital card specification
The general block diagram of digital card is shown in Figure 5 which includes the followings like UART, Memory, FPGA, Analog to Digital converter and Digital to Analog Converter.
1. The digital card has to be designed around a suitable DSP processor and a low power FPGA by
2. Xilinx makes.
3. Memory:
a. Flash: 16MB,
b. RAM: 128MB,
c. NAND Flash: 4GB
4. A/D converter:
a) Type: 18 bit, SAR converter,
b) Sampling frequency: 200KHz. And
c) AD 7608 or equipment.
5. D/A converter:
a. 16 bit DAC and
b. Settling time 4μs.
Go to
Analog Card Specification
The general block diagram of Analog card is given below in Figure 6 which has the following elements, namely pre amplifiers, Automatic gain controller, Band pass filter, Drive amplifier, Reconstruction filters etc.
Pre-Amplierl:
Gain: 10dB,
Input voltage range: 1|xv -10|iv,
Impedance matching: should be coupled with capacitive transducer and
Make: AD 624SD or equivalent.
Automatic gain control specifications
a. Operating frequency: 16-20KHz,
b. Make: AD 8332 or Equivalent.
5.3. Pre-amplifier 2:
a. Gain: Adjustable up to 100dB and
b. Operating frequency: 16-20KHz.
Band pass filter
Operating frequency
15-21kHz,
Pass band gain: 10dB
Stop Band Attenuation:
a) 40dB
b) Type: Chebyshev and
c) Order: 8
Anti-aliasing filter
Low pass filter with cutoff frequency 100khz
5.8. Programmable driver amplifier
Gain adjustments from FPGA.
Power amplifier
Type: Bridge mode power amplifier,
Operating frequency: 16-20 kHz
Output power:
Variable power output up to 60W,
Impendence matching: should be coupled to capacitive transducer and
Make: Power booster PB 58A. Wake up circuit is added to reduce power consumption.
Go to
Functional Requirements Of Acoustic Modem
The data transmission should be in packets/frames with proper protocol and acknowledgment.
The protocol should be an error control protocol with error detection and correction technique to establish reliable communication between ship and underwater device (UWD). The modem will be placed in ship.
Communication will be in half duplex mode. By incorporating suitable digital signal processing techniques, the communication has to be highly immune to noise and multi-path fading.
The entire system should be compact with low operating power requirement.
Development of software and firmware
Acoustic modem has to be interfaced to PC through USB post for user interaction. The following software modules are to be developed as part of the Modem. Test software (monitor) running in target processor to test all the hardware resources of the modem.
A front-end GUI based software running on PC for user interaction and to send commands to modem.
A modem application program running in target for two way communication. In the modem application program, there should be provision to select modulation scheme, coding type, band rate, power level, etc. the data file has to be uploaded from PC to modem for transmission. Similarly the software should be able to download the data received from the modem into PC for display. The modem application may be split between processor and FPGA as convenient.
Go to
Conclusion
Most of the underwater modems operate in low frequency. While using high frequency, low attenuation, high bandwidth and higher data rate can be achieved, but by compromising the range to a few thousand meters. An overview of commercial and under research underwater acoustic modem is presented in this paper. Several factors that do not exist in low power modem impose fundamental limitations on their performance. The technical challenges existing and can be eliminated in future is also addressed. This paper specifies some key configuration parameters that needs to be concentrated on to improve the performance of the high frequency modem.
To Know More About Journal of Oceanography Please Click on: https://juniperpublishers.com/ofoaj/index.php
To Know More About Open Access Journals Publishers Please Click on: Juniper Publishers
0 notes
Text
Overview on Industrial Grade 4G Wireless Routers
The industrial grade 4G wireless router is an industrial IoT high-speed router that provides a solution for users to access 4G networks through WIFI or network ports. Support WLAN wireless LAN function, support FDD LTE/TD-LTE two 4G LTE network standards, but also backward compatible with 2G/3G, support TD-SCDMA/WCDMA/EDGE/GPRS/GSM/CDMA1X/EVDO, etc. Performance 32-bit ARM processor with APN private network, VPN, mandatory portal, flow control, peanut shell domain name service and many other functions. Currently widely used in the M2M industry in the IoT industry chain, such as smart grid, intelligent transportation, smart home, finance, mobile POS terminal, supply chain automation, industrial automation, intelligent building, fire protection, public safety, environmental protection, meteorology, digitization Medical, telemetry, agriculture, forestry, water, coal, petrochemical and other fields.
Features
1, features and functions:
Built-in 3G/3G+/4G LTE industrial-grade wireless modules supporting FDD-LTE, TD-LTE, WCDMA, HSPA+, TD-SCDMA, and backward compatible with EDGE/GPRS/GSM network standards
Support wired, Wi-Fi, 4G/4G+/LTE multi-network switching
Support DTU function: support RS232, RS485 serial data transparent transmission
WIFI communication distance up to 100 meters
2, high reliability:
Full industrial grade EMC electromagnetic compatibility design, power supply anti-reverse protection, ESD anti-static / anti-surge protection
Iron enclosure protection class IP30
Support hardware watchdog, never crash
3. Features:
Support VPN, APN private network access
Compulsory portal, WIFI-DOG
Support NTP network timing
Support WEB, SSH encryption communication, set software multiple parameter management methods,
Support WEB mode firmware upgrade
Provides functions such as parameter backup and import, system local log and remote log sending.
Provide system local log and remote log to send remote LOG server for real-time network monitoring
Parameter settings file can be exported and imported
4, router function:
Support DHCP server to automatically obtain IP
Support DNS domain name resolution
Support various routing functions: static routing, port forwarding, network diagnosis, DDNS dynamic domain name resolution;
Support firewall
Intelligent QOS flow control
Support port mapping: support mapping from external network port to internal network port
Support static routing table
Hardware system
CPU: Industrial Grade 32-Bit Communication Processor, 580MHz
FLASH: 16MB (128Mb) (expandable to 512MB/4Gb)
RAM: 64MB (512Mb) (expandable to 256MB/2Gb)
Interface Type
Ethernet interface: 1 10/100M Ethernet LAN port (RJ45 socket), adaptive MDI/MDIX, built-in 1.5KV electromagnetic isolation protection;
1 10/100M Ethernet WAN port (RJ45 socket), adaptive MDI/MDIX, built-in 1.5KV electromagnetic isolation protection, cascaded superior router or xDSL or Cable Modem;
(When WAN RJ45 can be converted to LAN RJ45 port, it becomes 2 LAN RJ45 ports)
DTU serial port: support 1 serial port; 1 terminal block RS232 serial port (or RS485), built-in 15KV ESD protection, the parameters are as follows:
Data bits: 5, 6, 7, 8 bits;
Stop bits: 1, 1.5 (optional), 2 bits;
Flow control: none, hardware, software;
Calibration: no parity, even parity, odd parity, (SPACE and MARK check) (optional);
Serial port rate: 300bps, 600bps, 1200bps, 2400bps, 4800bps, 9600bps, 19200bps, 38400bps, 57600bps, 115200bps;
Working mode: server mode (supports 4 central terminals, and can customize more central terminals), client mode;
Heartbeat package: support
I/O port: 2-4
LED indicator: system power supply SYS*1, VPN*1, signal strength Signal*1, online Cell*1, WAN*1, LAN*1, WiFi*1
Antenna and interface
Standard SMA female antenna interface with a characteristic impedance of 50 ohms;
WiFi antenna interface - SMA female antenna interface × 1-2, 50 ohm;
Wireless antenna interface--SMA female antenna interface ×1-4, 50 ohm;
GPS antenna interface - SMA female antenna interface × 1, 50 ohm;
Support MIMO
SIM/UIM card interface: standard caliper user card interface, support 1.8V/3V SIM/UIM card, built-in 15KV ESD protection; 2 SIM card slots;
Power interface
3 power supply backups:
Standard 3-pin locomotive power outlet with built-in power reverse protection and overvoltage protection;
Terminal block power connector;
POE power supply
Reset button: This button restores the parameter configuration of ROUTER to the factory.
Console port: Debug port × 1
Powered by
Standard power supply: DC12V/1.5A or 9V/2A
Power supply range: wide power input (DC 5~40V), optional DC 5~60V
Current: Idle mode: approx. 100mA@12VDC
Communication mode: about 260mA@12VDC
Software system
VPN features
Support IPSec, PPTP, L2TP, GRE, OpenVPN, DMVPN (optional) and others;
Support VPN transparent transmission;
Firewall throughput speed: 100Mbps
VPN encryption speed: 5M~200M bps
Number of concurrent sessions: 8192~327680 seconds
Number of new sessions processed: 2250~45000
Number of VPN tunnels: 100~5000
Key exchange algorithm: Diffie-Hellman
HASH algorithm: (MD5, SHA128, SHA256, SHA384, SHA512), Cipher (AES, 3DES, DES)
The return key is completely confidential (PFS)
Authentication mode: Preshare password
VPN network type: support network to network intranet
Wi-Fi
WLAN (WiFi) function, support 802.11b/g/n, 300Mbps;
Support AP mode, bridge mode and Client client mode;
GPS/GNSS (optional) GPS/GNSS function
Voice (optional) Controls the upper and lower lines
SMS
Control the upper and lower lines to detect the status of the router;
Send and receive text messages;
Configuring an APN parameter of the WAN microcell Cell;
SMS alert;
Alarm: low signal strength or no signal SMS or voice notification (voice notification is optional)
VLAN: Support dual LAN IP address
Supported protocols TCP, UDP, SMTP, POP, ICMP, FTP, PPP, DHCP, DDNS dynamic domain name service, DNS, SNMP, NAT/NAPT, DMZ, Qos, ALG, VLAN, DNS proxy, static routing, dynamic routing, etc.
Safety
Support 64/128 bits WEP, 802.1x, WPA, and WPA2
Support WDS
Support WPA1/2 – PSK
Support WPA1/2 – 802.1x
Support EAP – TLS, TTLS, LEAP, PEAP
Support access with user name & password.
Support access control base WAN/LAN interface
Support access control base source IP address
Defense DOS attack, SYN flooding, IP surfing, ping of Death, fragile, teardrop, land etc.
Support PAP, CHAP, MsChap
Support IP filtering
Remote management system NMS
Physical characteristics
Housing: Metal enclosure, protection class IP30. The housing and system are safely isolated, especially suitable for industrial field applications
Dimensions: PCBA board: 96mm x 56mm x 14mm
Machine: 100mm x 60mm x 21mm
Weight: 220g (excluding antenna and mounting parts)
Working temperature: -35~+75oC
Storage temperature: -40~+85oC
Relative humidity: 95% (no condensation)
Magnetic compatibility performance Electrostatic discharge immunity test level: 3
Radio frequency electromagnetic field radiation immunity test level: 3
Applications
Industrial IoT Application
Use RJ45 network port and WiFi to connect Ethernet or WIFI wireless serial port server to realize remote acquisition of sensor data and serial port control. The network cable connects IP camera to realize remote transmission of video.
Smart life application:
Widely used in intelligent express cabinets, smart vending machines, smart number machines, smart buses, self-service ATM machines, advertising machines, etc.
Realize business data upload, free wifi, advertising broadcast, remote video surveillance, VPN / APN private network management and other application requirements, etc.
---------------------------------------------------
Source: https://elinstechnology.tumblr.com/post/182956990325/overview-on-industrial-grade-4g-wireless-routers
0 notes
Text
Astronomers Analyze the Di secure stribution of Globular Clusters
www.inhandnetworks.com
An optical image of the Fornax Cluster of galaxies.
Astronomers from the Harvard-Smithsonian Center for Astrophysics have analyzed the distribution of over eighty thousand globular clusters to infer an active history of galaxy-galaxy interactions.
Glo industrial LTE router bular clusters are gravitationally bound, roughly spherical ensembles of stars. Some contain as many as a million stars, and their sizes are as small as only tens of light-years in diameter. Globular clusters are typically located in the outer regions (the halos) of galaxies, and our Milky Way galaxy has about two hundred of them. Astronomers are interested in globular clusters in part because they are home to many of the oldest known stars, but also because of their locations in the halos.
Collisions between galaxies are commonplace, and the locations of globular clusters can offer evidence of these encounters because they are strongly affected by such interactions. During a collision, a galaxy can grow by absorbing or merging with its neighbor, and some models even predict that clusters form during these interactions. Moreover, it is possible that in a merger large numbers of globular clusters originally belonging to a smaller galaxy may be captured by a larger one. The distribution of globular clusters around a galaxy holds therefore clues to their origins and to the history of the host galaxy. There is an additional benefit: Standard models of cosmology make predictions for how galaxies form and evolve that depend on fundamental properties of the universe like the amounts of dark matter and dark energy. The properties of globular ct scanners remote monitoring cluster, mostly determined by the accretion histories and mergers of their host galaxies, also reflect the values of these fundamental cosmic quantities.
CfA astronomers Pepi Fabbiano and Raffaele D’Abrusco (now at the University of Naples), together with their colleagues, studied the globular clusters in the core of the Fornax Cluster of galaxies, a complex of over fifty galaxies located about sixty million light-years away. Using optical and near-infrared images taken with the European Southern Observatory’s Very Large Survey Telescope, the scientists cataloged over three thousand globular clusters throughout Fornax (about two-thirds of them previously unidentified), providing a rich resource for structural analyses. They find clear evidence for an active history of galaxy-galaxy interactions, for example in bridges between galaxies, elongated groupings, and other unusual arrangements. While these results by themselves do not refine the values of any cosmological parameters, they are consistent with the standard models, and help complete the evolutionary description of this massive nearby cluster of galaxies.
Reference: “The Extended Spatial Distribution of Globular Clusters in the Core of the Fornax Cluster,” R. D’Abrusco, M. Cantiello, M. Paolillo, V. Pota, N.R. Napolitano, L. Limatola, M. Spavone, A. Grado, E. Iodice, M. Capaccioli1, R. Peletier, G. Longo, M. Hilker, S. Mieske, E.K. Grebel, T. Lisker, C. Wittmann, G. van de Ven & G. Fabbiano, ApJ low cost cellular router 819, L31, 2016.
Industrial IoT Gateway, Industrial IoT Gateway, M2M gateway, VPN gateway, remote PLC programming, Industrial Cellular Modem, Cellular modem, data terminal unit, 3g modem, Industrial 3G Cellular Modem, 3g modem, industrial cellular modem3g modem, industrial cellular modem, industrial wireless modem, data terminal unit, Android Industrial Computer, Android Industrial Computer, Vending PC, Vending Telemetry, Vending Telemeter, Android Industrial Computer, Android Industrial Computer, Vending PC, Vending Telemetry, Vending Telemeter, Touchscreen & Vending PC, Vending Touchscreen, Vending Telemeter, Vending Telemetry, Vending Computer, Industrial LTE Router, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial IoT Router/Gateway, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial LTE Router, Industrial LTE router, industrial 4G/3G router, router industrial, cost-effective industrial LTE router, Industrial LTE Router, Industrial LTE router, industrial IoT router, router industrial, cost-effective M2M router, M2M LTE router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Distribution Power Line Monitoring System, Overhead Line Monitoring, Distribution Power Line Monitoring, Fault detection & location, Grid Analytics System, Remote Machine Monitoring & Maintenance System, IoT Remote Monitoring, Prognostics and Health Management, Remote connectivity, Remote Maintenance, Smart Vending, smart vending, InHandGo, retrofit, touchscreen vending, cashless vending, cloud VMS, Transformer Monitoring, Transformer Monitoring, substation monitoring, grid LTE router, wireless communication, smart grid, Remote Automation, Remote Automation, Secure remote networks, web SCADA, Remote Diagnostics, Remote PLC programming, Intelligent Traffic Enforcement, Intelligent Traffic Enforcement, wireless networking, cellular router, Wireless ATM Solution, Wireless ATM, ATM Remote Diagnostic, prestashop 多语商城, opencart 外贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign, webdesign, seo, joomla web design, 香港網頁設計, 網站建設, 企業建站, 商城網站, 集團網站, 海外網站, 營銷網站, 網站推廣, web design, joomla webdesign, wordpress webdesign, opencart webdesign, magento webdesign, durpal webdesign, vtiger crm, adempiere erp, compiere erp, hosting, domains, vps, email marketing, joomla 网页设计, wordpress 建站, magento 大型外贸商城, durpal 门户网站, seo 网站推广, 网站自然排名, joomla 網站製作, wordpress 定制開發, opencart 維護修改, prestashop 模板修改, magento 培訓實施, durpal 定制修改, seo 營銷推廣, 外鏈收錄排位, joomla, wordpress, opencart, prestashop, magento, durpal, zencart, crm, erp, edm, marketing, joomla template, wordpress themes, magento themes, opencart themes, prestashop themes, 崀山, 崀山科技, 崀山科技全球服务中心, LangShan Technology Global Service Center, LangShan Technology, langshantech, LangShan, china webdesign, 網頁製作, 網頁設計, 企业建站, 企業建站, 在線商城, 營銷網站, 網站推廣, 網站營銷, 排名推廣, 產品推廣, 主機維護, 公司兼職, 網站SEO, joomla seo, wordpress seo, joomla 網站推廣, opencart 網站推廣, prestashop 網站推廣, wordpress 網站推廣, magento 網站推廣, joomla 網站排名, prestashop 網站排名, wordpress 網站排名, opencart 網站排名, prestashop 多语商城, opencart 外贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign, webdesign, seo, joomla web design, 香港網頁設計, 網站建設, 企業建站, 商城網站, 集團網站, 海外網站, 營銷網站, 網站推廣, web design, joomla webdesign, wordpress webdesign, opencart webdesign, magento webdesign, durpal webdesign, vtiger crm, adempiere erp, compiere erp, hosting, domains, vps, email marketing, joomla 网页设计, wordpress 建站, magento 大型外贸商城, durpal 门户网站, seo 网站推广, 网站自然排名, joomla 網站製作, wordpress 定制開發, opencart 維護修改, prestashop 模板修改, magento 培訓實施, durpal 定制修改, seo 營銷推廣, 外鏈收錄排位, joomla, wordpress, opencart, prestashop,
#Verizon Embedded router#distribution line fault detection#wireless ATM modem#ATM Wireless Connectivity#distribution line sensor#Fault detection & location#LTE router VPN#router industrial
0 notes
Text
Qualcomm just gave us our best glimpse yet into the 5G revolution
New Post has been published on https://www.articletec.com/qualcomm-just-gave-us-our-best-glimpse-yet-into-the-5g-revolution/
Qualcomm just gave us our best glimpse yet into the 5G revolution
5G will change our lives… eventually.
James Martin/CNET
Do you want to know what 5G is going to look like? Qualcomm just went all-in on the next-generation wireless technology will look like next year.
The maker of mobile chips, best known for the powerful processors that serve as the brains of high-profile smartphones like the Google Pixel 3 and Samsung Galaxy Note 9, this week is holding its annual Snapdragon Tech Summit in Maui. Qualcomm showed off a prototype phone capable of tapping into 5G networks. AT&T and Verizon have set up “live networks” in the hotel where the event is being held to show off their capability.
“A lot of the work went into getting the 5G to show on this phone,” Qualcomm President Cristiano Amon said during the keynote.
Samsung, meanwhile, also has a reference device capable of tapping into 5G that it will be showing at the summit.
Samsung and Verizon already said they’ll launch a 5G smartphone in the first half of next year. AT&T and Sprint too. Already this year, Verizon has launched a variant of 5G as a home internet service, and in early 2019 it plans to begin a standards-based mobile service.
All of this equates to 5G going from years of hype — ever since Verizon talked about moving into this area three years ago — to actually becoming reality. Beyond a big speed boost, 5G has been referred to as a foundational tech that will supercharge areas like self-driving cars, virtual and augmented reality, and telemedicine services such as remote surgery.
Now playing: Watch this: Qualcomm, Verizon, Samsung are working to make 5G real….
1:26
But what exactly is 5G? Why are people so excited? The following is a breakdown of why the next generation of wireless technology is more than just a boost in speed, and why you should be excited.
What is 5G?
It’s the next (fifth) generation of cellular technology, which promises to greatly enhance the speed, coverage and responsiveness of wireless networks. How fast are we talking? Think 10 to 100 times speedier than your typical cellular connection, and even faster than anything you can get with a physical fiber-optic cable going into your house. (In optimal conditions, you’ll be able to download a season’s worth of “Stranger Things” in seconds.)
Is it just about speed?
No! One of the key benefits is something called low latency. You’ll hear this term a lot. Latency is the response time between when you click on a link or start streaming a video on your phone, sending the request up to the network, and when the network responds and gives you the website or starts playing your video.
That lag time can last around 20 milliseconds with current networks. It doesn’t seem like much, but with 5G, that latency gets reduced to as little as 1 millisecond, or about the time it takes for a flash in a normal camera to finish.
That responsiveness is critical for things like playing an intense video game in virtual reality or for a surgeon in New York to control a pair of robotic arms performing a procedure in San Francisco, though latency will still be affected by the ultimate range of the connection. The virtually lag-free connection means self-driving cars have a way to communicate with each other in real time — assuming there’s enough 5G coverage to connect those vehicles.
How does it work?
5G initially used super high-frequency spectrum, which has shorter range but higher capacity, to deliver a massive pipe for online access. But given the range and interference issues, the carriers are starting to explore lower-frequency spectrum — the type used in today’s networks — to help ferry 5G across greater distances and through walls and other obstructions.
The result is that the insane speeds companies first promised won’t always be there, but they’ll still represent a big boost from what we get today with 4G LTE.
Where do these carriers get the spectrum?
Some of these carriers already control small swaths of high-frequency radio airwaves, but many will have to purchase more from the government. The Federal Communications Commission is holding an auction for so-called millimeter wave spectrum, which all of the carriers are participating in.
Motorola’s 5G Mod, in prototype form
Juan Garzon/CNET
Are there other benefits?
The 5G network is designed to connect a far greater number of devices than a traditional cellular network. That internet of things trend you keep hearing about? 5G can power multiple devices around you, whether it’s a dog collar or a refrigerator.
The 5G network was also specifically built to handle equipment used by businesses, such as farm equipment or ATMs. Beyond speed, it’s also designed to work differently on connected products that don’t need a constant connection, like a sensor for fertilizer. Those kinds of low-power scanners are intended to work on the same battery for 10 years and still be able to periodically send over data.
Sounds great, but when does 5G get here?
Verizon launched the first “5G” service in the world in October, but it’s a bit of a technicality.
The service isn’t mobile service, but a fixed broadband replacement. An installer will need to put in special equipment that can pick up the 5G signals and turn it into a Wi-Fi connection in the home so your other devices can access it.
There’s also some debate about whether the service even qualifies for 5G — it doesn’t use the standards that the industry has agreed upon. The company wanted to jump out ahead, and used its own proprietary technology. Verizon argues that the speeds, which range from 300 megabits per second to 1 gigabit per second, qualify the service for 5G designation. Its rivals and other mobile experts dispute that claim.
The launch is extremely limited in select neighborhoods in Los Angeles; Sacramento, California; Indianapolis; and Dallas. (Let us know if you’re one of the lucky few who get it.)
OK, but what about mobile 5G?
Verizon says it’ll launch its mobile 5G next year. AT&T is looking like the first company to launch a true mobile 5G service. It plans to launch 5G this year in 12 markets. Last month, it successfully tested a mobile 5G connection in Waco, Texas, using what should be the first consumer 5G device, a wireless hotspot built by Netgear.
Like the Verizon deployment, expect the rollout of 5G in these cities to be extremely limited.
AT&T said it plans to launch in 19 cities next year, including Los Angeles, San Francisco and Las Vegas.
No 5G phones? Can’t I just pick up 5G with my existing smartphone?
Sorry, no. 5G technology requires a specific set of antennas that aren’t available yet. Sprint says it plans to release the first US 5G smartphone next year, which will be built by LG. It’s also working on a 5G “smart hub” with HTC, but as with all of the 5G news so far, they’ve been light on details such as features, specifications, price or availability.
Many of the phones will use Qualcomm’s X50 modem, which is designed specifically to tap into 5G spectrum.
Generally, 5G smartphones are expected to come out in the first half of next year. Rumors point to Samsung being among the first to build a 5G smartphone. The company is reportedly to put 5G in a version of its Galaxy S10. Samsung mobile CEO DJ Koh, however, teased of a specific 5G phone to launch ahead of its flagship.
OnePlus has also claimed that it’ll be among the first to have 5G in a phone as well, but that device won’t be coming to the US.
Anything I should worry about?
High-frequency spectrum is the key to that massive pickup in capacity and speed, but there are drawbacks. The range isn’t great, especially when you have obstructions like trees or buildings. As a result, carriers will have to deploy a lot more small cellular radios, creatively named small cells, around any areas that get a 5G signal.
That’s going to annoy anyone who doesn’t want cellular radios near them. With concerns over potential health risks, as well as the possibility some people will see them as neighborhood eyesores, there may be some objections to these things.
Carriers using low-frequency bands may get away with fewer cellular radios, but 5G will almost certainly require companies to further build out their networks.
How broadly will 5G be available in 2019?
Here’s the other concern — 5G might still be a theoretical possibility for a lot of people.
T-Mobile says it’s launching in 30 cities next year, while Sprint will launch in nine cities. AT&T is launching in a dozen markets this year and 19 next year, and Verizon aims to launch next year too, but it’s unclear how wide the coverage will be. Globally, China, Japan and South Korea are racing to build out their 5G networks, with Europe behind as it takes the slow and steady approach.
So don’t feel like you need to rush out to buy that first 5G smartphone. Chances are, service won’t be widely available until 2020 or beyond.
Also, while some see 5G helping to improve coverage everyone, rural areas will likely miss out for a while since it lacks the infrastructure to support all of those cell radios.
Will it cost more?
That’s unclear. Indications are the carriers won’t likely charge any more, although then-Sprint CEO Marcelo Claure said in March that he saw 5G as a premium service. New CEO Michel Combes declined to comment on pricing.
You’ll remember that LTE didn’t cost anymore when it first came out — you just needed to buy a new phone. But pricing models could change over time. Since 4G launched, the carriers both took away unlimited plans and brought them back.
Verizon’s home broadband service costs $50 for wireless subscribers, and $70 for everyone else. Those are in line with other broadband costs. (You can find out if you’re eligible for the service here.)
Our 5G glossary
Do you want to show off your 5G knowledge to your friends? Or seem like the smartest person at a party? Check out our 5G glossary below.
5G NR
The 5G bit is pretty obvious, but the NR stands for New Radio. You don’t have to know a lot about this beyond the fact that it’s the name of the standard that the entire wireless industry is rallying behind, and it just came out in December.
That’s important because it means everyone is on the same page when it comes to their mobile 5G networks. Carriers like AT&T and T-Mobile are following 5G NR as they build their networks. But Verizon, which began testing 5G as a broadband replacement service before the standard was approved, isn’t using the standard — yet. The company says it’ll eventually adopt 5G NR for its broadband service, and intends to use NR for its 5G mobile network.
Millimeter wave
All cellular networks use airwaves to ferry data over the air, with standard networks using spectrum in lower frequency bands like 700 megahertz. Generally, the higher the band or frequency, the higher the speed you can achieve. The consequence of higher frequency, however, is shorter range.
To achieve those crazy-high 5G speeds, you need really, really high frequency spectrum. The millimeter wave range falls between 24 gigahertz and 100 gigahertz.
The problem with super-high-frequency spectrum, besides the short range, is it’s pretty finicky — a leaf blows the wrong way and you get interference. Forget about obstacles like walls. Companies like Verizon are working on using software and broadcasting tricks to get around these problems and ensure stable connections.
Small cell
Traditional cellular coverage typically stems from gigantic towers littered with different radios and antennas. Those antennas are able to broadcast signals at a great distance, so you don’t need a lot of them. Small cells are the opposite — backpack-size radios can be hung up on street lamps, poles rooftops or other areas. They can only broadcast a 5G signal at a short range, so the idea is to have a large number of them in a densely packed network.
Some cities have this kind of dense network in place, but if you go outside of the metro area, that’s where small cells become more of a challenge.
Sub-6GHz
Given how troublesome really high-band spectrum can be (see the “millimeter wave” section above), there’s a movement to embrace spectrum at a much lower frequency, or anything lower than 6GHz. The additional benefit is that carriers can use spectrum they already own to get going on 5G networks. T-Mobile, for instance, has a swath of 600MHz spectrum it plans to use to power its 5G deployment. Prior to sub-6GHz, that would’ve been impossible.
That’s why you’re seeing more carriers embrace lower-frequency spectrum.
But lower-frequency spectrum has the opposite problem: While it reaches great distances, it doesn’t have the same speed and capacity as millimeter wave spectrum.
The ideal down the line will be for carriers to use a blend of the two.
Gigabit LTE
You’re hearing more about Gigabit LTE as a precursor to 5G. Ultimately it’s about much higher speeds on the existing LTE network. But the work going toward building a Gigabit LTE network provides the foundation for 5G.
For more on Gigabit LTE, read our explainer here.
MIMO
An abbreviation of “multiple input, multiple output.” Basically, it’s the idea of shoving more antennas into our phones and on cellular towers. And you can always have more antennas. They feed into the faster Gigabit LTE network, and companies are deploying what’s known as 4×4 MIMO, in which four antennas are installed in a phone.
Carrier aggregation
Wireless carriers can take different bands of radio frequencies and bind them together so phones like the Samsung Galaxy S8 can pick and choose the speediest and least congested one available. Think of it as a three-lane highway so cars can weave in and out depending on which lane has less traffic.
QAM
This is a term that’s so highly technical, I don’t even bother to explain the nuance. It stands for quadrature amplitude modulation. See? Don’t even worry about it.
What you need to know is that it allows traffic to move quickly in a different way than carrier aggregation or MIMO. Remember that highway analogy? Well, with 256 QAM, you’ll have big tractor trailers carrying data instead of tiny cars. MIMO, carrier aggregation and QAM are already going into 4G networks, but play an important role in 5G too.
Beam forming
This is a way to direct 5G signals in a specific direction, potentially giving you your own specific connection. Verizon has been using beam forming for millimeter wave spectrum, getting around obstructions like walls or trees.
Unlicensed spectrum
Cellular networks all rely on what’s known as licensed spectrum, which they own and purchased from the government.
But the move to 5G comes with the recognition that there just isn’t enough spectrum when it comes to maintaining wide coverage. So the carriers are moving to unlicensed spectrum, similar to the kind of free airwaves that our Wi-Fi networks ride on.
Network slicing
This is the ability to carve out individual slivers of spectrum to offer specific devices the kind of connection they need. For instance, the same cellular tower can offer a lower-power, slower connection to a sensor for a connected water meter in your home, while at the same time offering a faster, lower-latency connection to a self-driving car that’s navigating in real time.
Are you hearing more 5G-related terms that confuse you? Contact us and we’ll update this story with additional terms.
First published Feb. 8. Updated Sept. 27, Oct. 17 and Nov. 13:: Added new details. Updated Dec. 3 at 5:00 a.m. PT: Added details about the Qualcomm event.
Updated Dec. 4 at 2:00 p.m. PT: To include more details from the Qualcomm keynote.
5G: Your Next Big Upgrade: CNET’s series on the next generation of cellular technology.
Not just speed: Check out 7 incredible things you can do with 5G.
Source link
0 notes
Link
This wikiHow teaches you how to find hidden cameras in your house or building. Even though hidden cameras are incredibly small and easy to hide, there are a few techniques you can use to search for them under the right conditions.
EditSteps
EditUsing Basic Techniques
Know where to look. Unfortunately, hidden cameras can be as small as the end of a pen, making it easy to hide them virtually anywhere. When searching a room for hidden cameras, look in places such as the following:[1]
Smoke detectors
Electrical outlets
Power strips
Night lights
Books, DVD cases, or video game cases
Shelves
Small holes in the wall
Pictures or other decorations
Stuffed animals
Lava lamps
Understand what part of the camera to look for. Most of the camera will usually be hidden, but the camera's lens must always be visible for the camera to be effective. This means that you can always spot a camera by looking for its lens.
Any camera installed by an expert will not display wires or lights, but the lens must be visible.
Consider the best angle for coverage in a room. It's easiest to search for the camera from the perspective of someone wanting to record the center of activity in a room; for example, if you're worried someone is recording your kitchen, it doesn't make much sense to look for the camera in the floorboards.
Corners of rooms often provide the best picture of the whole room, though cameras placed in the corner are often less inconspicuous than most hidden cameras.
Look for oddly placed mirrors or decorations. While things like stuffed animals and books can be placed pretty much anywhere, mirrors and decorations (e.g., pictures or paintings) often aren't. If you see a mirror or decoration at a weird height or in an otherwise odd location, there may be a hidden camera embedded.[2]
You can check to see if a mirror is a two-way to confirm whether or not a camera is embedded. If the mirror is a two-way, it's suspicious at the very least.
Check stuffed animals and clocks. The eyes of stuffed animals and the screws or details on clocks can often conceal a camera.
Since both stuffed animals and clocks are easy to move, consider removing them from your vicinity if you suspect that they house cameras.
Turn off the lights to search for camera indicators. Most cameras have red or green lights which blink or display steadily; if the hidden cameras were poorly installed, you may be able to see these lights when you turn off the room's lights.
Chances are slim that anyone who installed hidden cameras was too sloppy to hide the camera's indicator lights, so don't rule out hidden cameras if you don't see any.
Create a DIY camera detector. Professional camera detectors can cost several hundred dollars, but you can make a cheap one with nothing but a paper towel and a flash light:[3]
Turn off all the lights in the room, and draw the blinds (or wait until nightfall).
Hold up a paper towel roll to one eye, then close the other eye.
Place a flashlight at eye level (in front of the closed eye) and turn on the flashlight.
Scan the room, keeping an eye out for glints as you do so.
Use your cell phone to scan for interference. This isn't a perfect system, but it will help you find certain types of cameras:
Make a call on your cell phone, and leave the caller on the line.
Walk around the room with your phone on speakerphone.
Listen for crackling, clicking, or buzzing from your phone.
Purchase and use an RF detector. An RF detector allows you to scan for hidden cameras by physically sweeping the detector around a room and listening for feedback; if you hear sudden crackling or beeping through the detector, there's a good chance you'll find a hidden camera in front of it.
When using an RF detector, you'll need to unplug any items which broadcast radio signals. These include things like kitchen appliances, baby monitors, routers and modems, gaming consoles, TVs, and so on.
You may need to cycle through several different frequencies before you find the correct one.
RF detectors can be found anywhere from electronics stores to Amazon, and you can expect to spend between $15 and $300 on one.
Search for public cameras. While public cameras tend to be less nefarious and more conspicuous than their personal counterparts, it may be good to know where the nearest "hidden" camera is if you're attempting to dispute a traffic incident or something similar. You can usually find cameras in the following locations:
ATMs
Store ceilings
Two-way mirrors in stores and high-profile shops (e.g., jewelry fronts)
Gas stations
Traffic lights
EditUsing Your Smartphone's Front Camera
Open your smartphone's Camera app. On an iPhone, you'll usually find this app on the Home Screen, while Android users can search for the Camera app in the App Drawer.
Switch to the front-facing camera. If the camera isn't showing your face while you hold the screen side facing you, tap the "Rotate" icon (which usually resembles a circular arrow or two) to flip it.
You can't perform this process with the rear camera.
Verify that your smartphone can see infrared light. In order to search for hidden cameras, your smartphone's front camera cannot have an infrared filter. You can determine whether the camera has an IR filter by using a TV remote:
Point a remote control at the camera.
Press any button on the remote control.
Look for a flash on the remote control's front light.
Turn off the lights in the room you want to scan. In order to scan for infrared light, you'll need to have the room as dark as possible.
If there are any other lights in room (e.g., night lights, power strip indicators, etc.), unplug their sources if possible.
Use your smartphone's camera to look for flashing lights. With your phone's screen facing you, rotate while looking for flashing spots. If you see a flashing area, it's most likely a hidden camera's IR light.
EditTips
Wireless cameras operate with a wireless transmitter and tend to be bit larger because they contain the wireless transmitter. These can operate on a battery and be transmittable to a recording device within a range of about 200 feet (60.96 m). This type can be popular for people looking to spy on other individuals.[4]
Perform the same discrete visual checks and sweeps in hotels and in workplaces. In a workplace and in other business settings, realize that dummy cameras may be set up to intimidate you into good behavior.
Hardwired cameras are typically the kind used in businesses to prevent crime. These can connect with a recording device or with television monitors.
EditWarnings
If you do find a hidden camera in your home or office, it's best to contact authorities immediately.
There are several paid smartphone apps which claim to sense cameras. These apps often have poor reviews and even poorer performance, so steer clear of them.
EditRelated wikiHows
Detect Hidden Cameras and Microphones
Build a Hidden Camera Detector
Tell if a Mirror Is Two Way or Not
EditSources and Citations
EditQuick Summary
Cite error: <ref> tags exist, but no <references/> tag was found
from How to of the Day https://ift.tt/2Iapo0K
0 notes
Text
Goodfellas, the Brazilian carding scene is after you
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From the early beginnings, using skimmers on ATMs, compromising point of sales systems, or even modifying the hardware of processing devices, Latin America has been a fertile ground for collecting credit and debit cards en masse. Brazil started the migration to EMV cards in 1999 and nowadays almost all cards issued in the country are chip-enabled. A small Java-based application lives inside this chip and can be easily manipulated in order to create a “golden ticket” card that will be valid in most (if not all) point of sale systems. Having this knowledge has enabled the criminals to update their activities, allowing them to create their own cards featuring this new technology and keeping them “in the business.” Enter the world of Brazilian malware development, incorporating every trick in the book and adding a custom made malware that can easily collect data from chip and PIN protected cards; all while offering a nicely designed interface for administering the ill-gotten information, validating numbers, and offering their “customers” an easy to use package to burn their cloned card. “Seu cartão vou clonar”: not only a crime but a lifestyle According to the 2016 Global Consumer Card Fraud: Where Card Fraud Is Coming From, “At this point in time, the assumption should be that almost all users’ credentials and/or card information has been compromised. The underground economy for user information has matured so much that it is indistinguishable from a legitimate economy.” In addition, when we are faced with the current credit card fraud statistics, we found that in 2016, Mexico was in the lead with 56% of residents reporting experiencing card fraud in the past five years. Brazil comes in second at 49%, and the U.S. in third with 47%. It’s worth noting that approximately 65% of the time, credit card fraud results in a direct or indirect financial loss for the victim, with an average reported loss of $1,343 USD. While traditional criminal activities in Brazil regarding computer crime have included banking trojans, boletos, and all sorts of different malware, cloning credit and debit cards for a living is more than a day job for some. With MCs rapping about the hardships of obtaining new plastic, and how easy the money starts flowing once they get in the game, there’s no shortage of options being offered for infecting ATMs, point of sales systems, or directly stealing credit card numbers from the users. One of the many Youtube channels sharing tutorials and real life stories on being a Brazilian carder. There are tutorials, forums, instant message groups, anything and everything as accessible as ever; making this industry a growing threat for all Brazilians. When it comes to Prilex, we are dealing with a complete malware suite that gives the criminal full support in their operations, all with a nicely done graphical user interface and templates for creating different credit card structures, being a criminal-to-criminal business. While cloning chip and PIN protected cards has already been discussed in the past, we found Prilex and its business model something worth sharing with the community; as these attacks are becoming easier to perform and the EMV standard hasn’t been able to keep up with the bad guys. Anything they wanted was an ATM infection away The first notable appearance of the Prilex group was related to an ATM attack targeting banks located primarily in the Brazilian territory. Back then, criminals used a black box device configured with a 4G USB modem in order to remotely control the machine. By opening a backdoor to the attacker, they could hijack the institution’s wireless connection and target other ATMs at their will. At the time, the malware that was used to dispense money at will, was developed using Visual Basic version 6.0; a reasonably old programming language that is still heavily used by Brazilian criminals. The sample was using a network protocol tailored specifically to communicate to its C2 allowing the attacker to remotely dig deeper in the ATM system and collect all the necessary information in order to perform further attacks. After obtaining initial access to the network, the attacker would run a network recognition process to find the IP address of each of the ATMs. With that information at hand, a lateral movement phase would begin, using default Windows credentials and then installing a custom crafted malware on the most promising systems. The backdoor would allow the attacker to empty the ATM socket by launching the malware interface and sending remote commands to dispense the money. ATM version of Prilex patching legitimate software for jackpotting purposes. The malware was developed to target not only the ATMs with the jackpotting functionality but also the bank’s customers due to a function which enables the malware to steal the magnetic stripe information once the client use the infected ATM: cloning and jackpotting on the same package. Targeting point of sales systems and expanding functionality While hunting new samples related to the ATM attack, we found a new sample matching the previously dissected communication protocol. In fact, the protocol (and code) used by this new sample had been updated a bit in order to support extended functionality. Code similarity of the ATM and Point of Sale samples from the Prilex family. The main module contains different functions that allow the attacker to perform a set of debugging operations on the victim’s machine as well as performing the attack itself. Remote administration using “Ammyy Admin”. Upload/download files from/to infected computer. Capture memory regions from a process. Execute shell commands. Update main module. Patch libraries in order to allow capturing card information. Functions handled by the malware. The main purpose of the malware is to patch the point of sales system libraries, allowing it to collect the data transmitted by the software. The code will look for the location of a particular set of libraries in order to apply the patch thus overwriting the original code. Log strings referring the patch applied by the malware. With the patch in place, the malware collects the data from TRACK2, such as the account number, expiration date, in addition to other cardholder information needed to perform fraudulent transactions. The PIN is never captured by the malware, since is not needed as we will see later. Using DAPHNE and GPShell to manage your Smart Card After the information is exfiltrated to the C2 server, it’s read to be sold in the blackmarket as a package. The criminals provide access to a tool called Daphne ,which is responsible for managing the credit card information acquired and ultimately writing it to the cloned cards. The Daphne “client” has the option to choose which type of card it wants to write, debit or credit; then the information will be validated on the server only to be written to the card once all necessary tests are passed. The new card, which is connected to the smart card writer, will receive the new information via GPShell scripts in charge of setting up the card’s structure and creating the “golden card”. Function to write the card data as credit or debit, or just copy the information to the clipboard. After using the card, the criminal is able to keep track of how much money is possible to withdraw. While we are not sure how this information is being used, Prilex’s business model encourages users to register which cards are valid and the amount that they have paid off. This could enable reselling the cards in other venues and charging differential prices depending on their status. After a card stops working (marked as “dead”), the criminal will fill the information about how much money was stolen from that card, if any. Since Daphne is designed as a client/server application, several individuals can query the same information at once, and all modifications on the cards are synchronized with a central database. This behavior enables crews to work on the same set of information, allowing the connected user to create a new card directly from the interface and allowing the tool to decide the best template to use and how to preset the card. Do not panic, but your credit card might be running Java The EMV standard and supporting technology is in fact a robust framework that can provide much more security than the traditional magnetic stripe. Unfortunately, due to a bad implementation of such technology, it’s possible for criminals to abuse it and clone an EMV supported card with information stolen from the victim. However, this technique is not entirely new and also not specific to Brazil. We have seen the same TTPs in other malware families, being sold on underground forums and targeting banks in Europe and other countries in Latin America such as Mexico and Argentina In addition, the tool has an option to communicate with Smart Card devices by using GPshell in order to create a fake card with the stolen information. Commands sent to GPshell in order to check for a Smart Card. The commands above are responsible for checking if the Smart Card can be accessed, and if so it will enable the option to write the information to the fake card. Some commands used here are not generic and not usually found on a normal transaction. Since they cannot manipulate all the information of the ‘chip and PIN’ technical standard, they need to modify the application responsible for validating the transaction. In order to do that, they install a modified CAP file (JavaCard applet) to the Smart Card, then when the PoS tries to validate the PIN, it will always accept as well as bypass all other validation processes. Due to the fact that most of the payment operators do not perform all validations as required by the EMV standard, the criminals are able to exploit this vulnerability within the process in advantage of their operation. Commands used to install the malicious CAP file to the Smart Card. Furthermore, GPshell sends commands to replace the PSE (Payment System Environment) by deleting the original one and installing a malicious counterpart. After that, the Smart Card just needs the stolen information to be written and it will be ready to use on PoS devices. Commands sent to the card to write all data. In this step, the script executed by GPShell contains all the necessary information in order for the point of sales terminal to perform the payment operation. The given script contains data extracted from original cards that are necessary to perform the authorization with the card operator. One of the most relevant data written by this script is the Application Interchange Profile, changed in order to enable Static Data Authentication (SDA) and Signed Static Application Data (SSAD). This section contains the data signed by the card issuer that should be validated to guarantee that the information from the card was not counterfeited. However, the issuer has to decide which data should be protected by the signed information and based on our research, we found that most of the cards only have the Application Interchange Profile data signed, making the SSAD data valid even with a modified TRACK2 and a different cardholder’s name. Getting the hardware and the blank cards is not as difficult as it sounds Buying the equipment is quite cheap and surprisingly easy. To perform the attack, criminals just need to have a Smart Card Reader/Writer and some empty smart cards. Everything can be easily found online and since those tools can also be used in a legitimate way, there is no problem buying it. JCop cards costing around $15 USD. A basic reader/writer can be bought for less than $15 USD. As we can see, the necessary equipment can be acquired by less than $30 USD, making it really affordable and easy for everyone to buy (not that anyone should!). Smart Cards, the EMV standard, and the Brazilian carding scene Industry reports, such as The Nilson Report, states that credit card fraud in 2016 has represented losses of $22.80 billion USD worldwide. And by 2020, card fraud worldwide is expected to total $31.67 billion USD. Since that day in 1994, where Europay, MasterCard, and Visa developed this technology with the goal of ending fraud once and for all, several speed bumps have been found along the way, making theft and counterfeiting of payment card data more difficult for criminals in each iteration. It’s interesting to see how the liability of a fraud incident has been theoretically moved over the years from the customer, to the merchants, then to the bank; when in reality is the customer the one that always deals with the worst part of the story. To be continued… The crew behind the development of Prilex has demonstrated to be a highly versatile group, active since at least 2014 and still operating, targeting primarily Brazilian users and institutions. The motivation behind each of their campaigns has been repeatedly proven as solely monetary, given their preference for targets in the financial or retail industry. Luckily, the banks and operators in Brazil have been investing a lot in technologies to improve their systems and avoid fraudulent transactions, allowing them to identify those techniques and preparing them for what’s to come. However, some countries in Latin America are not as evolved when it comes to credit card technologies and still rely on plain old magnetic stripe cards. Other countries are just starting to actively implement chip-and-pin authentication measures and have become a desirable target for criminals due to the overall lack of expertise regarding this technology. The evolution of their code, while not technically notable, has been apparently sufficient in maintaining a constant revenue stream by slowly perfecting their business model and customer applications. The discovery of “Daphne”, a module to make use of the ill-gotten financial information and their affiliate scheme, suggests that this is a “customer oriented” group, with many levels in their chain of development; resembling what we have seen for example in the popular ATM malware Ploutus and other jackpotting operations. This modularization, in their source code as well as their business model, constitutes Prilex as a serious threat to the financial industry, currently confined to the territory of Brazil with the uncertainty of how long it will take before it expands its operations to other regions. IOCs 7ab092ea240430f45264b5dcbd350156 Trojan.Win32.Prilex.b 34fb450417471eba939057e903b25523 Trojan.Win32.Prilex.c 26dcd3aa4918d4b7438e8c0ebd9e1cfd Trojan.Win32.Prilex.h f5ff2992bdb1979642599ee54cfbc3d3 Trojan.Win32.Prilex.f 7ae9043778fee965af4f8b66721bdfab Trojan.Win32.Prilex.m Our complete IOCs list, as well as YARA rules and full reports are available for Financial Intelligence Reports service customers. If you need more information about the service, please contact us at: [email protected] https://securelist.com/goodfellas-the-brazilian-carding-scene-is-after-you/84263/ https://goo.gl/VVF1ky
0 notes
Text
EMV Level 2 Kernel Approved
The term derives from regular utilisation of the method amongst Lebanese fraudsters. The insertion of your loop of plastic, metal, or perhaps cassette tape as aforementioned, to the ATM card slot. The customer's card then gets into, the transaction is processed, however the card cannot eject because of a lip for the end of the loop. The customer then leaves the ATM frustrated, and also the criminal awaits his moment to gather the credit card and money. Read our EMV Level 2 Kernel guide below, it is very interesting indeed.

But while ATMs are undoubtedly worthwhile and time saving for both banks as well as their customers, due to their design and simplicity of use, it's important to be extra vigilant when utilizing an ATM, because there happen to be cases when people are already robbed when working with them. While these cases are rare, it can appear to be we've become to accustomed to using ATMs and so are no longer cautious when utilizing our bank cards and PIN numbers in public areas. However, that is not to express that by using a cash machine is dangerous; not even close to it, but here are some tips to assist you be sure that withdrawing your dollars is easy, fast as well as, safe.
EMV Level 2 Kernel
Voice over Internet Protocol, commonly known more briefly as VoIP could be the technology which allows us to produce free and cheap calls online to friends, family and business associates around the world. Without it, computer programmes such as Skype and cellular phone apps such as Viber and iCall would not be in a position to exist.

The kind of interaction that industry is employed to having with bank tellers and cashiers is something that the significant number don't want to relinquish. There is commonly a feeling that by finding a partner in the flesh, the customer are able to enjoy better service. This means that nearly all reputable bank CEOs could not imagine making their services entirely automated, not nevertheless there is still such perception. However, opening and maintaining banks everywhere that the bank could have customers would have been a large financial drain and is not often practical.
2 months later with EMV Level 2 Kernel, for the 8th February 1879, the gang imprisoned police officers, stole their uniforms and then paraded themselves as re-inforcements from Sydney. In addition to the money stolen, Ned and the outlaws burned the mortgage deeds from the townspeople that have been held in the lending company. Such acts simply because this make Ned Kelly a folk hero in Australia to many people.
Technology That We Have Learnt to Take for Granted
The Greatest Inventors You've Probably Never Heard Of
We are all amassed and amazed in/by technology, to be sure it
virtual wired, virtual here or there, virtual wireless, virtual
When was the past time that you just visited/took advantage of the convenience of Pay-Pal, the ATM, the Kiosk, online financials, for example
Banking, or HR services - The Submittal of Cvl/Resume(s)
Service Software Dreaming

But while ATMs are undoubtedly worthwhile and time saving for both banks in addition to their customers, because of their design and convenience, it is advisable to be extra vigilant when you use an ATM, because there happen to be cases where people have been robbed when using them
While these cases are rare, it could look like we've become to utilized to using ATMs and therefore are don't cautious when you use our credit cards and PIN numbers in public
However, which is not to say that by using a cash machine is dangerous; faraway from it, but below are great tips to help you be sure that withdrawing your cash is easy, fast and also, safe
The Greatest Inventors You've Probably Never Heard Of

As a data terminal, an ATM must be attached to a bunch processor; this is the equal of an Internet Service Provider (ISP) insofar as it behaves as a gateway through which various ATM networks become available to the conclusion userMost host processors is capable of supporting the leased-line or dial-up machine, while using former connecting right to the host processor via a four-wire telephone lineThe latter works on the traditional line to connect for the processor by using a modem as well as a toll-free number
Finally, next time you want to that 'hole inside the wall' to withdraw cash, check your balance or top-up your mobile have you thought to spare a moment's thought to the inventor behind the automated teller machine AKA the ATM. Scottish inventor John Shepherd-Barron was credited with inventing earth's first ATM machine within the 1960s in which a branch of Barclays in London first installed the equipment. Using the thought of a naughty food dispenser since the catalyst for his creation, Shepherd-Barron took to make the monetary equivalent that has been first operated using chemically coded cheques. Nowadays ATM software programs are a multi-billion pound industry that extends right worldwide.

In case an in-office machine spits out the information, and then the FP issues a report, you must report the complete code CPT 93000 (Electrocardiogram, routine ECG with at least 12 leads; with interpretation and report), which certainly pays more than $26. However, determining which code to report when your practice doesn't deliver the tracing or interpret the results is more challenging.
The most common forms of fraud are card cloning and skimming. Cards have a magnetic stripe and, in some cases with embedded chip where all personal information are stored. Nevertheless, the electronic devices (called skimmers) used to record account data encoded on the magnetic stripe are easy to make.
How you determine which is the right one for you depends on how will you use it. When you pay always in fill your monthly statement, the best kind of credit card is the one containing no yearly fee and provides a grace period” for paying the bill without having to pay a finance fee.

A stripe on the back of a bankcard that contains magnetically encoded cardholder account information. The name of the cardholder is stored on Track I and the account number and expiration date are stored on Track II. Also referred to as MAG STRIPE.
Creditcall's 100% first time pass certification track record has ensured that to date over 1 million of our EMV Kernels are deployed worldwide in ATMs, PINpads, mobile chip card readers for smartphones, parking payment machines, kiosks and a multitude of other devices.
Besides the aforementioned info, for payments processed over Internet, merchants should have information regarding the transaction such as the card owner's contact information (phone number or email address), the date and time the order was placed, details of the order, or details of the conversation they had with the buyer.
Say Where: The name of a popular voice enabled application for the Apple iPhone device. Say Where is a free application that can be used to recognize your speech and input it as text into Web sites when using the Safari browser on your iPhone. The application is used to finding locations, directions and maps. for example, users can speak the name of a place, an address, or intersection and the application will show search result from a number of partners including Google Maps, MapQuest and others.

Let's face it, banks and financial institutions are in it for profit, not charity. They have been backed by the Federal Reserve since 1933. Last year alone, banks have made over 31 billion dollars just in overdraft fees! Even with a reported 14% drop in profits from overdrafts after the Financial Reform Act was passed by the U.S. Senate, banks are still making big money. Banks may be profiting less from overdraft fees, but the amount they charge for them have started to go up. The chart up over to the right displays what the average fee was in the last 4 years. Some banks charge well above the average. Bank of America for example, charges 35.00 and Fifth Third Bank will have the highest overdraft fee of them all, at $37.00 each item!
The main characteristic of a restaurant POS system is that an order of a guest may be recalled or deleted through the use of 'Bump Bars', which are essentially small components that have different buttons for different purposes. Apart from this, most POS systems for this type of business have wireless headset features that allow an order to be transmitted manually from a speaker to an employee who inputs the order. POS systems can be customized to suit well a vendor's different needs also. Large business clients can dictate their requirement through it to a retailer who provides the materials.

EMV cards do take a little bit longer to process because chip cards transmit an encrypted code that changes with every new transaction, Petoskey News Reported. Although these transactions typically only take a few seconds longer to finish than a swipe purchase, many customer have not been shy about voicing their displeasure with the increased wait time.
Each year on EMV Level 2 Kernel, one of the greatest concerns for ATM software developers may be the improvement of security measures. Since the ATM first appeared being a trusted banking machine, its security has become a concern for both customers and banks too. This is because ATM access relies upon on a card and PIN system, both of which could possibly be easily prone to theft.
Resources:
EMV Level 2 (L2) Kernel | AISCES
EMV - Wikipedia
EMV LEVEL 2 KERNEL TESTING - WEEBLY
youtube
0 notes