#Cluster sampling comparison
Explore tagged Tumblr posts
Text
Cluster Sampling: Types, Advantages, Limitations, and Examples
Explore the various types, advantages, limitations, and real-world examples of cluster sampling in our informative blog. Learn how this sampling method can help researchers gather data efficiently and effectively for insightful analysis.
#Cluster sampling#Sampling techniques#Cluster sampling definition#Cluster sampling steps#Types of cluster sampling#Advantages of cluster sampling#Limitations of cluster sampling#Cluster sampling comparison#Cluster sampling examples#Cluster sampling applications#Cluster sampling process#Cluster sampling methodology#Cluster sampling in research#Cluster sampling in surveys#Cluster sampling in statistics#Cluster sampling design#Cluster sampling procedure#Cluster sampling considerations#Cluster sampling analysis#Cluster sampling benefits#Cluster sampling challenges#Cluster sampling vs other methods#Cluster sampling vs stratified sampling#Cluster sampling vs random sampling#Cluster sampling vs systematic sampling#Cluster sampling vs convenience sampling#Cluster sampling vs multistage sampling#Cluster sampling vs quota sampling#Cluster sampling vs snowball sampling#Cluster sampling steps explained
0 notes
Text



All currently active NeoBuilders.
Minecraft default skins in Ancient Ruins, reference picture at the end for comparison.
Don’t look too close at the faces, had to speedrun this so I could actually motivate myself to finish the entire lineup. Definitely not my best work. Clothing was a pain to figure out and I’ll definitely change some things in the future as I’m still not entirely happy with the general aesthetics of some sets. Zuri and Efe were the worst to figure out, their clothing styles were very modern in comparison to what I’m going for with Ancient Ruins so it took me a while.
But first of all, what is a NeoBuilder?
Lore entry Ahead, body horror warning, nothing too extreme I wouldn’t say, but the concept definitely isn’t the prettiest.
“NeoBuilder” describes a category of individuals that appear to be within the homo-genus (Artisan Family.).
The dissection of a deactivated individual showed (us) they are made of about 85% mechanical components, most of which consist of copper and iron. Organs however remain fully functional and can be traced back to Ancient Artisans in origin through DNA sampling. Blood vessels aswell as a large portion of their flesh has been replaced by machinery, activated regulated and moved through restricted soul energy coursing through their veins as blood would on a fully biological human.
The change of energy source makes them effectively immune to the green plague, which is transmitted through blood. In place of a heart they have a still unnamed chamber (Ch1), acting akin to a cockpit housing a freshly created soul, which is replaced by converting experience farmed in the previous lifecycle to the next, taking the raw energy and morphing it into a new soul. As souls are neither human nor animal but simply an energy cluster made of (if found post mortum) memories and life experience this can easily (and understandably) be transferred, even if the origin of the experience in question happens to be non-sentient. The experience is collected and stored within yet another unnamed organ replacing their left kidney (Ch2).
But do not be fooled, this process by no means makes them immortal. If the body is in critical shape it will resort to exporting the active soul and using the remaining soul energy still running through the machinery to activate the emergency program. In this state the body will do nothing but return to whatever point the machine has clocked as “safe” (this kind of reset happens when the person is resting for an extended period of time, as it marks said area as safe enough to stay vulnerable within.) and fix its injuries back to base point, excluding the bio-matter, as there no longer is any such material around. Through the expelling of the last soul, and slow process of developing a new one, the machine will power down there until the next energy burst. This means that even though the body itself remains alive, every life cycle houses a different person. If you see the same NeoBuilder twice it is therefore not guaranteed it will come with the same intention, as it might be a completely different soul speaking through the same form.
If the damage is too bad however, the NeoBuilder will shut down and cannot be reactivated unless one with actual knowledge of how to do so were to interfere. The how has been lost to history however, we blame the creature of despair and decay that shall not be named. It is different from deactivation, as it renders the body permanently dead. Many NeoBuilders have deactivated, we assume only 9 of the previous 30 remain.
We have no idea as to why these manmade humanoids were created, as the why has also been buried and lost to years of untouched unaddressed missing history.
Infact, their names are quite new, till about half a century ago, due to my own research if I may pat myself on the back, we had assumed them to be a strange strain of plague infested ancients, as they’d always remained distant to us and a dead specimen was a more than rare find. It is not a fully worked out name whatsoever, the “Builder” merely connecting them to the Artisan family, and the word “Neo”- as in “New” replacing the word “Ancient” we’ve been using to describe the other half of the family thus far, it is a placeholder by all means, but so is the latter.
Their nature would definitively make them more akin to bio-mechanical golems, however we chose to group them into the artisan family for the previously mentioned bio material, which matched identical to that of the mummified remains cave divers had found a few years back lodged between long forgotten pathways shut to time. Wasn’t a pretty sight when they showed me. One would think after a good few millennia they’d be nothing but a pile of ash and bones, but low oxygen levels within the closed off cave system made for some awfully good preservation, not pretty I dare say, I’m just glad nothing snapped at me during inspection as, perhaps in this case thankfully, the undead plague only infects the living; anything that doesn’t breathe and lacks running blood cannot fall victim to such a thing. But personal tangent aside, some interesting notes here:
- Despite the soul of the Neobuilder swapping with each lifecycle they generally keep the same base morals of the previous host.
- it seems Mother Earth isn’t very fond of them for whatever reason. The undead are very manageable if one isn’t around, but as soon as one chooses to stay in close vicinity it very quickly gets nearly impossible to maneuver, they’re like a magnet. It seems this is the reason they rarely last longer than 20 years within a single lifecycle.
- they’re actually quite cooperative, and many have learned our language. Though sorrowfully it appears they only store a single slot for their language, and forget all other information of a previously spoken one upon interaction (perhaps they were meant as a situational translation device?). I’ve attempted my best to reteach them, but I’m no linguist; I limit my research to history, with a limited understanding of biology. To figure out the mechanics alone I had to get a whole other villager to help my case.
- despite a large portion of their flesh being replaced by mechanical components an extra layer of the fat cells within the subcutis create an artificial layer of flesh like material dampening any slashes at the golem like form below.
More research to be added once I acquire more material to work with. This is a work in progress.
Understudied field, more research either classified information or unable to be attained due to both lack of examples and individuals willing enough to risk their lives acquiring such needless information. Ivan D. P. Retired shortly after writing his book discussing categorized biological information regarding the entities within our realm, which has since been removed from the market. The authors doctor title has been revoked due to a less than fortunate suspected alliance with the Illager cult on his end, so choose the information you’re willing to believe wisely, the villages dislike him for a reason.
We sincerely apologize but certain behaviors are to be taken seriously regarding the issues the cult on the outskirts has caused us in the past. Rumors have to be believed regarding individuals actively choosing to house away from the masses for whatever reason, to keep the general public safe.
Moving just out of sight to dedicate your life to dissecting humanoids on your dinner table is not normal behavior and was it not for his living position would hastily be investigated,
mumbling about how you hate our community doesn’t lessen our concerns, if you read this Ivan, it was not funny and it will never be, you know of the missing people concerns: if it happens again we’re sorry to inform you but you’ll no longer be welcome within this village.

#minecraft#minecraft lore#mineblr#minecraft au#minecraft theory#minecraft art#artists on tumblr#fanart#artwork#minecraft steve#steve minecraft#minecraft alex#minecraft efe#minecraft zuri#minecraft kai#minecraft makena#minecraft sunny#minecraft ari#minecraft noor#minecraft artist#minecraft villagers#the villagers don’t fw historians#I mean fair enough it’s kind of a pipeline in their case#try to talk about Minecraft without bringing up the ancient freaks challange level impossible#Minecraft Ancient Ruins#au#I’d love to talk about the seperate individuals and where they live and whatever but I kinda just wanted to yap about NeoBuilders (Players)#just ask if you have anything specific#lore dump#minecraft default skins
131 notes
·
View notes
Text
The Knights of Walpurgis: The Knights, Ascending
“Well then, Bella,” he hissed. “It’s just you and me now. It’s time for the real fun to begin. I wonder – just how long has it been since you’ve tasted your own medicine?” “Wha –” “Crucio!” Bellatrix, who had started to pick herself up from the ground, fell to her knees anew, screaming with the agony of his curse. He ended it quickly and crouched to lift her chin. “There. That wasn’t so bad, right Bella? Just a little taste, a little sample. Or would you like more?” “You’re nothing,” Bellatrix spat, wrenching herself away from his touch. “Your magic is paltry in comparison to what the Dark Lord can do. You may be able to block the Cruciatus, but to cast it you have to truly mean it!” “Oh, I meant it,” Tom said, stepping backwards and levelling his wand at her once more. “On the contrary, that was me holding back. If you’re so eager to see the depth of my power, I can certainly oblige you. Crucio!” Bellatrix shrieked as the full brunt of Tom’s curse hit her, knocking her backwards and onto the cobblestones where she writhed in agony. “There you go,” he purred. “Is that what you were looking for? I can provide even more, of course, but I’m afraid you might just lose your mind – what’s left of it, anyway.” He held her under the curse for several more seconds, allowing himself to wallow in the pleasure it engendered within him until her screams turned to sobs for mercy – mercy, please. Then, bending down low, he met Bellatrix dead in the eye. “Let it not be said that I cannot take pity upon those who oppose me,” he said, drinking in her terrified expression. “But now, I think, it’s time for a little cat and mouse. I do have to maintain an image of a perfectly normal Hogwarts student, even if it’s clear to all those who meet me that I am exceptional – extraordinary, even. So – I’m going to run, and you are going to chase me. Or do you no longer wish to kill me?” “You’re dead,” Bellatrix replied, wiping the sleeve of her robe across her mouth. Like rouge, it left a crimson smear across her cheek. “You’re dead, Riddle!” “Ah, that’s the spirit, Bella,” Tom smiled. “Do try and keep up. And Bella – remember my face.” He took off running in the same direction Harry had, instinctively following the tether that connected their souls. Something didn’t feel right, he realised, his mind clearing from the intensity of the fight. Harry was scared – terrified, even. He skidded to a halt as a small cluster of his Knights came into view: Fred, George, Luna, Pansy, and Longbottom. Fred was stretched out across the road, though his brother was helping him to sit up as Luna ran the tip of her wand over his back. Both Pansy and Longbottom looked fearful. “What is this?” Tom demanded. “Where is Harry, and why isn’t he with you?” “He went after Ron,” Luna said simply, pressing her wand into Fred’s side and eliciting a sharp wince from him. “A couple of Death Eaters dragged him off, so Harry went off to look for him.” “What?!” Tom shouted. “And none of you thought to go with him?! If you’re not going to keep him safe, what is the point of you?!”
10 notes
·
View notes
Text

Database Entry - [The Xiezhi]:
The Xiezhi are a humanoid long-life race that originated from the planet [???] in the Epsilon XII galaxy. They have several distinctive traits including antlers from the base of their ears and dense clusters of scales of varying shapes and colors. These scales can most visibly be seen along their hands, shoulders, upper back, outer ribs, and calves. The females have elongated canine teeth while the men have intricate antlers in comparison.
There is only one ability known about this race which is the innate ability to distinguish the truth from lies. Researchers have linked this trait to a section of the brain that most other species do not possess. Few studies have shown that one may disorient this ability by forming the falsities within metaphors or idioms. The Xiezhi are a very literal people which some allege is due to their unidentified connection with HooH, the Aeon of Equilibrium. This is a non-exhaustive list of abilities as there are no longer enough Xiezhi to provide an unbiased sample size.
As of the current year, more than fifty percent of the known population have been killed after a core-collapse supernova of the planet's local star ruptured the atmosphere. The remaining Xiezhi have since left [???] and the IPC has declared the planet inhabitable for any carbon based lifeforms.
#✿⇝ { hsr verse; } — ❝ the price of true equilibrium❞#// headcanons for this verse? more likely than you'd think#✿⇝ { Hsr verse; headcanons } — ❝ on the nature of impartiality ❞
6 notes
·
View notes
Text
Inhibition of EIF4E Downregulates VEGFA and CCND1 Expression to Suppress Ovarian Cancer Tumor Progression by Jing Wang in Journal of Clinical Case Reports Medical Images and Health Sciences
Abstract
This study investigates the role of EIF4E in ovarian cancer and its influence on the expression of VEGFA and CCND1. Differential expression analysis of VEGFA, CCND1, and EIF4E was conducted using SKOV3 cells in ovarian cancer patients and controls. Correlations between EIF4E and VEGFA/CCND1 were assessed, and three-dimensional cell culture experiments were performed. Comparisons of EIF4E, VEGFA, and CCND1 mRNA and protein expression between the EIF4E inhibitor 4EGI-1-treated group and controls were carried out through RT-PCR and Western blot. Our findings demonstrate elevated expression of EIF4E, VEGFA, and CCND1 in ovarian cancer patients, with positive correlations. The inhibition of EIF4E by 4EGI-1 led to decreased SKOV3 cell clustering and reduced mRNA and protein levels of VEGFA and CCND1. These results suggest that EIF4E plays a crucial role in ovarian cancer and its inhibition may modulate VEGFA and CCND1 expression, underscoring EIF4E as a potential therapeutic target for ovarian cancer treatment.
Keywords: Ovarian cancer; Eukaryotic translation initiation factor 4E; Vascular endothelial growth factor A; Cyclin D1
Introduction
Ovarian cancer ranks high among gynecological malignancies in terms of mortality, necessitating innovative therapeutic strategies [1]. Vascular endothelial growth factor (VEGF) plays a pivotal role in angiogenesis, influencing endothelial cell proliferation, migration, vascular permeability, and apoptosis regulation [2, 3]. While anti-VEGF therapies are prominent in malignancy treatment [4], the significance of cyclin D1 (CCND1) amplification in cancers, including ovarian, cannot be overlooked, as it disrupts the cell cycle, fostering tumorigenesis [5, 6]. Eukaryotic translation initiation factor 4E (EIF4E), central to translation initiation, correlates with poor prognoses in various cancers due to its dysregulated expression and activation, particularly in driving translation of growth-promoting genes like VEGF [7, 8]. Remarkably, elevated EIF4E protein levels have been observed in ovarian cancer tissue, suggesting a potential role in enhancing CCND1 translation, thereby facilitating cell cycle progression and proliferation [9]. Hence, a novel conjecture emerges: by modulating EIF4E expression, a dual impact on VEGF and CCND1 expression might be achieved. This approach introduces an innovative perspective to impede the onset and progression of ovarian cancer, distinct from existing literature, and potentially offering a unique therapeutic avenue.
Materials and Methods
Cell Culture
Human ovarian serous carcinoma cell line SKOV3 (obtained from the Cell Resource Center, Shanghai Institutes for Biological Sciences, Chinese Academy of Sciences) was cultured in DMEM medium containing 10% fetal bovine serum. Cells were maintained at 37°C with 5% CO2 in a cell culture incubator and subcultured every 2-3 days.
Three-Dimensional Spheroid Culture
SKOV3 cells were prepared as single-cell suspensions and adjusted to a concentration of 5×10^5 cells/mL. A volume of 0.5 mL of single-cell suspension was added to Corning Ultra-Low Attachment 24-well microplates and cultured at 37°C with 5% CO2 for 24 hours. Subsequently, 0.5 mL of culture medium or 0.5 mL of EIF4E inhibitor 4EGI-1 (Selleck, 40 μM) was added. After 48 hours, images were captured randomly from five different fields—upper, lower, left, right, and center—using an inverted phase-contrast microscope. The experiment was repeated three times.
GEPIA Online Analysis
The GEPIA online analysis tool (http://gepia.cancer-pku.cn/index.html) was utilized to assess the expression of VEGFA, CCND1, and EIF4E in ovarian cancer tumor samples from TCGA and normal samples from GTEx. Additionally, Pearson correlation coefficient analysis was employed to determine the correlation between VEGF and CCND1 with EIF4E.
RT-PCR
RT-PCR was employed to assess the mRNA expression levels of EIF4E, VEGF, and CCND1 in treatment and control group samples. Total RNA was extracted using the RNA extraction kit from Vazyme, followed by reverse transcription to obtain cDNA using their reverse transcription kit. Amplification was carried out using SYBR qPCR Master Mix as per the recommended conditions from Vazyme. GAPDH was used as an internal reference, and the primer sequences for PCR are shown in Table 1.
Amplification was carried out under the following conditions: an initial denaturation step at 95°C for 60 seconds, followed by cycling conditions of denaturation at 95°C for 10 seconds, annealing at 60°C for 30 seconds, repeated for a total of 40 cycles. Melting curves were determined under the corresponding conditions. Each sample was subjected to triplicate experiments. The reference gene GAPDH was used for normalization. The relative expression levels of the target genes were calculated using the 2-ΔΔCt method.
Western Blot
Western Blot technique was employed to assess the protein expression levels of EIF4E, VEGF, and CCND1 in the treatment and control groups. Initially, cell samples collected using RIPA lysis buffer were lysed, and the total protein concentration was determined using the BCA assay kit (Shanghai Biyuntian Biotechnology, Product No.: P0012S). Based on the detected concentration, 20 μg of total protein was loaded per well. Electrophoresis was carried out using 5% stacking gel and 10% separating gel. Subsequently, the following primary antibodies were used for immune reactions: rabbit anti-human polyclonal antibody against phospho-EIF4E (Beijing Boao Sen Biotechnology, Product No.: bs-2446R, dilution 1:1000), mouse anti-human monoclonal antibody against EIF4E (Wuhan Sanying Biotechnology, Product No.: 66655-1-Ig, dilution 1:5000), mouse anti-human monoclonal antibody against VEGFA (Wuhan Sanying Biotechnology, Product No.: 66828-1-Ig, dilution 1:1000), mouse anti-human monoclonal antibody against CCND1 (Wuhan Sanying Biotechnology, Product No.: 60186-1-Ig, dilution 1:5000), and mouse anti-human monoclonal antibody against GAPDH (Shanghai Biyuntian Biotechnology, Product No.: AF0006, dilution 1:1000). Subsequently, secondary antibodies conjugated with horseradish peroxidase (Shanghai Biyuntian Biotechnology, Product No.: A0216, dilution 1:1000) were used for immune reactions. Finally, super-sensitive ECL chemiluminescence reagent (Shanghai Biyuntian Biotechnology, Product No.: P0018S) was employed for visualization, and the ChemiDocTM Imaging System (Bio-Rad Laboratories, USA) was used for image analysis.
Statistical Analysis
GraphPad software was used for statistical analysis. Data were presented as (x ± s) and analyzed using the t-test for quantitative data. Pearson correlation analysis was performed for assessing correlations. A significance level of P < 0.05 was considered statistically significant.
Results
3D Cell Culture of SKOV3 Cells and Inhibitory Effect of 4EGI-1 on Aggregation
In this experiment, SKOV3 cells were subjected to 3D cell culture, and the impact of the EIF4E inhibitor 4EGI-1 on ovarian cancer cell aggregation was investigated. As depicted in Figure 1, compared to the control group (Figure 1A), the diameter of the SKOV3 cell spheres significantly decreased in the treatment group (Figure 1B) when exposed to 4EGI-1 under identical culture conditions. This observation indicates that inhibiting EIF4E expression effectively suppresses tumor aggregation.
Expression and Correlation Analysis of VEGFA, CCND1, and EIF4E in Ovarian Cancer Samples
To investigate the expression of VEGFA, CCND1, and EIF4E in ovarian cancer, we utilized the GEPIA online analysis tool and employed the Pearson correlation analysis method to compare expression differences between tumor and normal groups. As depicted in Figures 2A-C, the results indicate significantly elevated expression levels of VEGFA, CCND1, and EIF4E in the tumor group compared to the normal control group. Notably, the expression differences of VEGFA and CCND1 were statistically significant (p < 0.05). Furthermore, the correlation analysis revealed a positive correlation between VEGFA and CCND1 with EIF4E (Figures 2D-E), and this correlation exhibited significant statistical differences (p < 0.001). These findings suggest a potential pivotal role of VEGFA, CCND1, and EIF4E in the initiation and progression of ovarian cancer, indicating the presence of intricate interrelationships among them.
EIF4E, VEGFA, and CCND1 mRNA Expression in SKOV3 Cells
To investigate the function of EIF4E in SKOV3 cells, we conducted RT-PCR experiments comparing EIF4E inhibition group with the control group. As illustrated in Figure 3, treatment with 4EGI-1 significantly reduced EIF4E expression (0.58±0.09 vs. control, p < 0.01). Concurrently, mRNA expression of VEGFA (0.76±0.15 vs. control, p < 0.05) and CCND1 (0.81±0.11 vs. control, p < 0.05) also displayed a substantial decrease. These findings underscore the significant impact of EIF4E inhibition on the expression of VEGFA and CCND1, indicating statistically significant differences.
Protein Expression Profiles in SKOV3 Cells with EIF4E Inhibition and Control Group
Protein expression of EIF4E, VEGFA, and CCND1 was assessed using Western Blot in the 4EGI-1 treatment group and the control group. As presented in Figure 4, the expression of p-EIF4E was significantly lower in the 4EGI-1 treatment group compared to the control group (0.33±0.14 vs. control, p < 0.001). Simultaneously, the expression of VEGFA (0.53±0.18 vs. control, p < 0.01) and CCND1 (0.44±0.16 vs. control, p < 0.001) in the 4EGI-1 treatment group exhibited a marked reduction compared to the control group.
Discussion
EIF4E is a post-transcriptional modification factor that plays a pivotal role in protein synthesis. Recent studies have underscored its critical involvement in various cancers [10]. In the context of ovarian cancer research, elevated EIF4E expression has been observed in late-stage ovarian cancer tissues, with low EIF4E expression correlating to higher survival rates [9]. Suppression of EIF4E expression or function has been shown to inhibit ovarian cancer cell proliferation, invasion, and promote apoptosis. Various compounds and drugs that inhibit EIF4E have been identified, rendering them potential candidates for ovarian cancer treatment [11]. Based on the progressing understanding of EIF4E's role in ovarian cancer, inhibiting EIF4E has emerged as a novel therapeutic avenue for the disease. 4EGI-1, a cap-dependent translation small molecule inhibitor, has been suggested to disrupt the formation of the eIF4E complex [12]. In this study, our analysis of public databases revealed elevated EIF4E expression in ovarian cancer patients compared to normal controls. Furthermore, through treatment with 4EGI-1 in the SKOV3 ovarian cancer cell line, we observed a capacity for 4EGI-1 to inhibit SKOV3 cell spheroid formation. Concurrently, results from PCR and Western Blot analyses demonstrated effective EIF4E inhibition by 4EGI-1. Collectively, 4EGI-1 effectively suppresses EIF4E expression and may exert its effects on ovarian cancer therapy by modulating EIF4E.
Vascular Endothelial Growth Factor (VEGF) is a protein that stimulates angiogenesis and increases vascular permeability, playing a crucial role in tumor growth and metastasis [13]. In ovarian cancer, excessive release of VEGF by tumor cells leads to increased angiogenesis, forming a new vascular network to provide nutrients and oxygen to tumor cells. The formation of new blood vessels enables tumor growth, proliferation, and facilitates tumor cell dissemination into the bloodstream, contributing to distant metastasis [14]. As a significant member of the VEGF family, VEGFA has been extensively studied, and it has been reported that VEGFA expression is notably higher in ovarian cancer tumors [15], consistent with our public database analysis. Furthermore, elevated EIF4E levels have been associated with increased malignant tumor VEGF mRNA translation [16]. Through the use of the EIF4E inhibitor 4EGI-1 in ovarian cancer cell lines, we observed a downregulation in both mRNA and protein expression levels of VEGFA. This suggests that EIF4E inhibition might affect ovarian cancer cell angiogenesis capability through downregulation of VEGF expression.
Cyclin D1 (CCND1) is a cell cycle regulatory protein that participates in controlling cell entry into the S phase and the cell division process. In ovarian cancer, overexpression of CCND1 is associated with increased tumor proliferation activity and poor prognosis [17]. Elevated CCND1 levels promote cell cycle progression, leading to uncontrolled cell proliferation [18]. Additionally, CCND1 can activate cell cycle-related signaling pathways, promoting cancer cell growth and invasion capabilities [19]. Studies have shown that CCND1 gene expression is significantly higher in ovarian cancer tissues compared to normal ovarian tissues [20], potentially promoting proliferation and cell cycle progression through enhanced cyclin D1 translation [9]. Our public database analysis results confirm these observations. Furthermore, treatment with the EIF4E inhibitor 4EGI-1 in ovarian cancer cell lines resulted in varying degrees of downregulation in CCND1 mRNA and protein levels. This indicates that EIF4E inhibition might affect ovarian cancer cell proliferation and cell cycle progression through regulation of CCND1 expression.
In conclusion, overexpression of EIF4E appears to be closely associated with the clinical and pathological characteristics of ovarian cancer patients. In various tumors, EIF4E is significantly correlated with VEGF and cyclin D1, suggesting its role in the regulation of protein translation related to angiogenesis and growth [9, 21]. The correlation analysis results in our study further confirmed the positive correlation among EIF4E, VEGFA, and CCND1 in ovarian cancer. Simultaneous inhibition of EIF4E also led to downregulation of VEGFA and CCND1 expression, validating their interconnectedness. Thus, targeted therapy against EIF4E may prove to be an effective strategy for treating ovarian cancer. However, further research and clinical trials are necessary to assess the safety and efficacy of targeted EIF4E therapy, offering more effective treatment options for ovarian cancer patients.
Acknowledgments:
Funding: This study was supported by the Joint Project of Southwest Medical University and the Affiliated Traditional Chinese Medicine Hospital of Southwest Medical University (Grant No. 2020XYLH-043).
Conflict of Interest: The authors declare no conflicts of interest.
#Ovarian cancer#Eukaryotic translation initiation factor 4E#Vascular endothelial growth factor A#Cyclin D1#Review Article in Journal of Clinical Case Reports Medical Images and Health Sciences .#jcrmhs
2 notes
·
View notes
Text
in doing research about our disorders we have stumbled across something that has absolutely BLOWN OUR COLLECTIVE MIND and thus feel the need to share it with you all. the information here is about ADHD and DID, but mostly ADHD. we found the article through a website about DID but most of what we are talking about is about ADHD
coming from did-research.org's section on comorbid disorders, we read the paragraph:
There is a growing body of research showing that ADHD can be caused, exacerbated, or mimicked by childhood maltreatment. Although ADHD is known to be strongly heritable, there is evidence that genetic vulnerability interacts with an adverse family environment to increase the risk of ADHD (Laucht et al., 2007). Among those with childhood-diagnosed ADHD, the majority will not meet full ADHD criteria in adulthood, but childhood adversity increases the likelihood of continuing symptoms (Fuller-Thomson et al., 2015). Child maltreatment is strongly associated with symptoms also found in ADHD, including inattention, impulsivity, difficulties managing anger, extreme passivity, peer rejection, poor academic functioning, and cognitive delays (Briscoe-Smith & Hinshaw, 2006; Guendelman et al., 2016), and childhood physical abuse is so strongly associated with ADHD that some studies have found that ADHD is more likely to result from physical abuse than any other disorder, including PTSD (Sugaya et al., 2013). Most notably, ADHD symptoms are conceptualized as one of the clusters of symptoms associated with developmental trauma disorder, a proposed diagnosis meant to capture the extremely wide-reaching effects of severe childhood neglect and abuse (D’Andrea et al., 2012).
(bold font added by me to increase readability because tumblr's font is not very wall-of-text friendly)
AND THE PHRASE "Among those with childhood-diagnosed ADHD, the majority will not meet full ADHD criteria in adulthood" WAS SO FUNDAMENTALLY LIKE. PARADIGM SHIFTING. THAT WE LOOKED AT THE ARTICLE CITED AND IT ONLY GETS WORSE FOR OUR PAST PERCEPTION OF ADHD.
This is the article cited.
This is a paragraph from the abstract of the article, so not even the actual research conducted yet, just the background.
Research has begun to demonstrate a relationship between ADHD and adverse childhood experiences (ACEs), including physical abuse, sexual abuse, and witnessing parental domestic violence. Using the National Longitudinal Study of Adolescent Health, Ouyang, Fang, Mercy, Perou, and Grosse (2008) showed that adolescents with a history of childhood physical abuse had higher odds of self-reported symptoms of both inattentive and hyperactive subtypes of ADHD. Those with a history of sexual abuse also had significantly higher odds of the inattentive subtype, but not the hyperactive one. Another large study, this time using a representative sample of adult Canadians, found that those with a history of physical abuse had over six times higher odds of self-reporting a health professional diagnosis of ADHD (Fuller-Thomson, Mehta, & Valeo, 2014). Several smaller clinical studies have also linked ADHD to ACEs: Briscoe-Smith and Hinshaw (2006) found that a higher percentage of girls with ADHD reported any type of abuse than a matched comparison group. They also showed that most of the abuse occurred in the combination ADHD type as opposed to the inattentive type. Ford et al. (2000) revealed, among children and adolescents, that a history of physical or sexual maltreatment was associated with a diagnosis of ADHD. Finally, Biederman et al. (1995) found that children presenting with ADHD at a pediatric clinic disproportionately came from families who had experienced high levels of conflict.
(again, bold font added by me)
and i don't know enough about the categorization of developmental disorders and trauma disorders to really make this judgement but my brain semi-jokingly said "so when are we going to start classifying (adult) adhd as a trauma disorder" because like. the majority of people who i know that were diagnosed as kids violently hated being on medication and now don't use it, but every adult or late-teen-diagnosed person i know is endlessly grateful for medication. this is just personal experience, and i haven't made specific notes of it, but over half of my cousins (i have 30, so at least 15) have been diagnosed with adhd at some point or another, and they follow this pattern as well. the ones diagnosed past the age of like 16 or so have stayed on medication and we have talked about how much it has helped us, and the ones diagnosed as children look at us like we have three heads when we say we want to be on medication.
idk i just want to know you guys' thoughts! can be personal experience or professional knowledge, sorry that the second article is behind a paywall, i'm at university rn so i have access to it if you want me to like send you a pdf of it.
3 notes
·
View notes
Text
Statistics: Display and Shape



1 Categorical Variable: Class Make-up

Comparative Bar Charts
allows us to look at multiple groups of one categorical variable
can be a stacked bar graph or a clustered bar graph
One Quantitative Variable
A. Examining Quantitative Data
distribution = tells all possible values of a variable and how frequently they occur
Summarize distribution of a quantitative variable by telling shape, center, and spread.
Shape = tells which values tend to be more or less common.
Center = measure of what is typical in the distribution of quantitative variable.
Spread = measure of how much the distribution's values vary
B. Displays
Stemplot - advantage: most detail - disadvantage: impractical for large datasets
Histogram - advantage: works well for any size dataset - disadvantage: some detail lost
Dotplot - advantage: can show outliers - disadvantage: much detail lost

Stem Plot
quantitative data
combines the characteristics of a table and a graph
general steps: (1) Separate each observation into a stem (first part of number) and a leaf (remaining part of number) (2) Write the stems in a vertical column; draw a vertical line to the right of the stems. (3) Write each leaf in the row to the right of its stem; order leaves if desired.
Stem: 10's digit
Lead: 1's digit
5 I 3 = 53
Constructing Stem Plots


Comparative Stem Charts
used for comparison of two groups of 1 quantitative variable - ex. Compare exam scores from two classes.


Dot Plots
used for 1 quantitative variable
similar to a stem + leaf plot; each dot represents one value
Ex. An instructor has obtained the set of N=25 exam scores: 82, 75, 88, 93, 53, 84, 87, 58, 72, 94, 69, 84, 61, 91, 64, 87, 84, 70, 76, 89, 75, 80, 73, 78, 60

Histograms
Show possible values of a quantitative variable along the horizontal axis, with vertical bars showing the count, percentage, or proportion of values in certain interval ranges.
shows quantitative data ONLY
display of a grouped frequency distribution
adjacent bars touch each other
Divide the possible values into class intervals (equal width). - How many intervals? One rule is to calculate the square root of the sample size and round up. - Size of intervals? Divide range of data (max-min) by number of intervals desired and round up. - Pick intervals so each observation can only fall in exactly one interval (no overlap). maximum-minimum/number of intervals
Count how many observations fall in each interval (may change to proportion or percentages).
Draw representation distribution.
Ex. An instructor has obtained the set of N=25 exam scores:
82, 75, 88, 93, 53, 84, 87, 58, 72, 94, 69, 84, 61, 91, 64, 87, 84, 70, 76, 89, 75, 80, 73, 78, 60




Grouped frequency distribution histogram vs. stem plot.
The stem plot is placed on its side to demonstrate that the display gives the same information provided in the histogram.
Scatterplots
Used for displaying the relationship between two quantitative variables.
Ex. Compare students' exam 1 vs exam 2 scores.


Interpreting Histograms
When describing the distribution of a quantitative (interval or ratio) variable, we look for the overall pattern and for striking deviations from that pattern. We can describe the overall pattern of a histogram by its shape, center (central tendency) and spread (variability).

Shape of Distribution
A symmetric distribution has a balanced shape, showing that it is just as likely for the variable to take lower values as higher values.

A skewed distribution is lopsided:
skewed left: few values that are relatively low compared to the bulk of the data
skewed right: few values that are relatively high compared to the bulk of the data values


Outliers
Extreme values that fall outside the overall pattern.
may occur naturally
may occur due to error in recording
may occur due to measurement error
observational unit may be fundamentally different
After identifying potential outliers, investigate why they obtain unusual values.

More Specific Shapes
unimodal distribution: has one peak
bimodal distribution: has two peaks
uniform distribution: has no peaks, showing that all possible values are equally common
normal distribution: symmetric, unimodal, "bell-shaped" or "mound-shaped" pattern
2 notes
·
View notes
Text
Genetics
See also: Genetic history of Africa
Y DNA
Nilotic men in Kapoeta, South Sudan
A Y-chromosome study by Wood et al. (2005) tested various populations in Africa for paternal lineages, including 26 Maasai and 9 Luo from Kenya, and 9 Alur from the Democratic Republic of Congo. The signature Nilotic paternal marker Haplogroup A3b2 was observed in 27% of the Maasai, 22% of the Alur, and 11% of the Luo.[63]
Haplogroup B is another characteristically Nilotic paternal marker.[64] It was found in 22% of Luo samples, 8% of Maasai, and 50% of Nuer peoples.[63] The E1b1b haplogroup has been observed at overall frequencies around 11% among Nilo-Saharan-speaking groups in the Great Lakes area,[65] with this influence concentrated among the Maasai (50%).[63] This is indicative of substantial historic gene flow from Cushitic-speaking males into these Nilo-Saharan-speaking populations.[65] 67% of the Alur samples possessed the E2 haplogroup.[63]
The Y-DNA of populations in the Sudan region were studied, with various local Nilotic groups included for comparison. The signature Nilotic A and B clades were the most common paternal lineages amongst the Nilo-Saharan speakers, except those inhabiting western Sudan. There, a prominent North African influence was noted.[66]
Haplogroup A was observed amongst 62% of Dinka, 53.3% of Shilluk, 46.4% of Nuba, 33.3% of Nuer, 31.3% of Fur, and 18.8% of Masalit. Haplogroup B was found in 50% of Nuer, 26.7% of Shilluk, 23% of Dinka, 14.3% of Nuba, 3.1% of Fur, and 3.1% of Masalit. The E1b1b clade was also observed in 71.9% of the Masalit, 59.4% of the Fur, 39.3% of the Nuba, 20% of the Shilluk, 16.7% of the Nuer, and 15% of the Dinka.[66] Balemi (2018) found that a sample of 50 Nuer carried e1b1b-M78 (32%), A-M13 (28%), B-M60 (24%) and F-M89 (4%).
Solomon Balemi (2018) Genetic Study of LCT- Enhancer, Y chromosome and Mitochondrial DNA Variation in Some Ethnic Groups in Ethiopia.
The atypically high frequencies of the haplogroup in the Masalit was attributed to either a recent population bottleneck, which likely altered the community's original haplogroup diversity, or to geographical proximity to E1b1b's place of origin in North Africa. The clade "might have been brought to Sudan [...] after the progressive desertification of the Sahara around 6,000–8,000 years ago".[66] Similarly, Afro-Asiatic influence was seen in the Nilotic Datog of northern Tanzania, 43% of whom carried the M293 subclade of E1b1b.[67]
mtDNA
Pokot women trekking through the Kenya outback
Unlike the paternal DNA of Nilotes, the maternal lineages of Nilotes in general show low-to-negligible amounts of Afro-Asiatic and other extraneous influences. An mtDNA study examined the maternal ancestry of various Nilotic populations in Kenya, with Turkana, Samburu, Maasai, and Luo individuals sampled. The mtDNA of almost all of the tested Nilotes belonged to various sub-Saharan macro-haplogroup L subclades, including L0, L2, L3, L4, and L5. Low levels of maternal gene flow from North Africa and the Horn of Africa were observed in a few groups, mainly by the presence of mtDNA haplogroup M and haplogroup I lineages in about 12.5% of the Maasai and 7% of the Samburu samples, respectively.[68]
Autosomal DNA
The autosomal DNA of Nilotic peoples has been examined in a study on the genetic clusters of various populations in Africa. According to the researchers, Nilotes generally form their own African genetic cluster, although relatively most closely related to other Nilo-Saharan populations, more distantly followed by Afro-Asiatic speakers and Niger-Congo speakers. The authors also found that certain Nilotic populations in the eastern Great Lakes region, such as the Maasai, showed some additional Afro-Asiatic affinities due to repeated assimilation of Cushitic-speaking peoples over the past 5000 or so years.[69]Nyangatom people in Ethiopia
Overall, Nilotic people and other Nilo-Saharan groups are closely related to Afro-Asiatic speakers of North and East Africa. Both groups are inferred to have diverged from a common ancestor around 16,000 years ago. Nilotic people and other Nilo-Saharan groups are also closely related to Niger-Congo speakers of West and Central Africa. Both groups are inferred to have diverged from a common ancestor around 28,000 years ago, perhaps somewhere in the Sahel.[70] Most Nilotic peoples have predominant to exclusive West/East African ancestry, although some groups display varying degrees of West-Eurasian admixture, mostly mediated indirectly through pastoralists from the Horn of Africa.[71]
Admixture analysis
In 121 African populations, four African American populations, and 60 non-African populations, results indicated a high degree of mixed ancestry reflecting migration events. In East Africa, all population groups examined had elements of Nilotic, Cushitic and Bantu ancestry amongst others to varying degrees. By and large, genetic clusters were consistent with linguistic classification with notable exceptions including the Luo of Kenya. Despite being Nilo-Saharan speakers, the Luo cluster with the Niger-Kordofanian-speaking populations that surround them. This indicates a high degree of admixture occurred during the southward migration of southern Luo. Kalenjin groups and Maasai groups were found to have less Bantu ancestry, but significant Cushitic ancestry.[10]
Physiology
Cross-country world champion and record holder Lornah Kiplagat is one of many prominent Nilotic distance runners.
Physically, Nilotes are noted for their typically very dark skin color and lean, and occasionally tall bodies. They often possess exceptionally long limbs, particularly their distal segments (fore arms, lower legs).[72][73][74][75] Sudanese Nilotes are regarded as one of the tallest peoples in the world. Average values of 188.6 cm (6 ft 2.3 in) for height and 56.8 kg (125 lb; 8 st 13 lb) for weight were seen in a sample of Sudanese Shilluk.[76] Another sample of Sudanese Dinka had a stature/weight ratio of 181.9 cm (5 ft 11.6 in) and 58.0 kg (127.9 lb; 9 st 1.9 lb), with an extremely ectomorphic somatotype of 1.6–3.5–6.2.
In terms of facial features, the nasal profile most common amongst Nilotic populations is broad, with characteristically high index values ranging from 86.9 to 92.0. Lower nasal indices are often found amongst Nilotes who inhabit the more southerly Great Lakes region, such as the Maasai, which is attributed to genetic differences.[77]
Additionally, the Nilotic groups presently inhabiting the African Great Lakes region are sometimes smaller in stature than those residing in the Sudan region. Measurements of 172.0 cm (5 ft 7.7 in) and 53.6 kg (118 lb; 8 st 6 lb) were found in a sample of agricultural Turkana in northern Kenya, and of 174.9 cm (5 ft 8.9 in) and 53.0 kg (116.8 lb; 8 st 4.8 lb) in pastoral Turkana.[78] A height of 172.7 cm (5 ft 8.0 in) was seen for Maasai in southern Kenya, with an extreme trunk/leg length ratio of 47.7.[77]
Many Nilotic groups excel in long- and middle-distance running. This sporting prowess may be related to their exceptional running economy, a function of slim body morphology and very long, slender legs (particularly lower legs, i.e., calf muscles and ankles.).[79] For 404 elite Kenyan distance runners, 76% of the international-class respondents identified as part of the Kalenjin ethnic group and 79% spoke a Nilotic language.[80]
VEDETTE
0 notes
Text
Zomato India 1M+ Review Insights to Optimize Menu Pricing

Zomato India: Tracking 1M+ Reviews to Help Chains Improve Menu Pricing
Overview
In India’s rapidly evolving dining and food delivery market, customer reviews are more than feedback—they’re pricing intelligence.
With millions of active users, Zomato hosts detailed reviews across dine-in and delivery formats. These reviews often contain customer sentiment around price fairness, portion size, value for money, and competitive comparisons.
At Datazivot, we analyzed over 1 million Zomato reviews across 50 Indian cities to help mid-sized and national restaurant chains optimize menu pricing using review-driven intelligence.
Client Profile
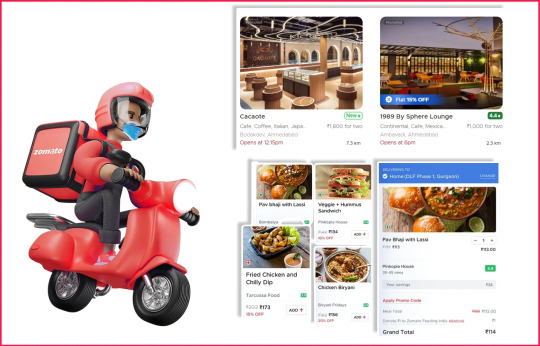
Industry: Casual Dining & Delivery-First Restaurant Chains
Platform Focus: Zomato India (dine-in + online delivery)
Review Volume Analyzed: 1,000,000+
Cities Covered: Mumbai, Delhi, Bengaluru, Hyderabad, Pune, Chennai, Ahmedabad, Lucknow, Kolkata, Jaipur, and more
Service Provided: Review scraping, NLP-based sentiment analysis, pricing sentiment clustering, competitor benchmarking
Objective

The restaurant chains wanted to:
Detect menu items priced “too high” based on review sentiment
Map value-perception gaps city-by-city
Adjust pricing for low-margin or over-priced SKUs
Understand if portion-size matched price expectations
Benchmark against nearby restaurants on price-to-value
What Datazivot Analyzed from Zomato Reviews

Sample Data Extracted by Datazivot

Key Findings from 1M+ Zomato Review Sentiment Analysis

Bengaluru & Chennai were more price-sensitive on single-item meals
Mumbai & Delhi had higher acceptance of premium pricing if portion justified
Tier-2 cities like Lucknow, Indore demanded better combo pricing
“Paneer Tikka,” “Pasta Alfredo,” “Biryani Half” frequently cited as overpriced
Sides like “Extra Mayo,” “Garlic Bread” seen as unjustified add-ons above ₹100
Most 2-star reviews included “small quantity,” “not filling,” or “barely enough”
Use Case

National Casual Dining Chain Improves Pricing Strategy :
Client: SpiceVault India (45-location casual Indian restaurant)
Challenge: Decline in customer ratings and profit margins after recent menu price hikes
What Datazivot Did:
Scraped 400,000 reviews across Zomato India
Isolated 8 dishes with consistent “overpriced” feedback across cities
Built “Pricing Sentiment Index” per SKU and region
Action Taken:
Reduced prices of 3 underperforming dishes by ₹20–₹40
Introduced new combo offers based on city-specific preferences
Added clearer portion size visuals to menu on Zomato listings
Results:
Average rating increased by 0.6 stars for top 5 affected SKUs
Price-related negative reviews dropped by 41%
18% increase in monthly orders from Tier-2 markets
Top Keywords Flagged for Pricing Issues

City-Level Pricing Benchmark Example: Biryani Dishes

Benefits Delivered by Datazivot’s Review-Based Pricing Analysis

Why Zomato Reviews Beat Traditional Price Testing

Conclusion
Don’t Guess Menu Prices - Listen to Your Customers
Your customers are already telling you what’s too expensive, what’s worth it, and what they’ll never reorder again.
With Datazivot, Zomato reviews become more than ratings—they become pricing intelligence tools.
Detect overpricing before churn
Refine pricing based on location and SKU sentiment
Improve value perception and boost orders
Strengthen profit margins without sacrificing trust
Want to Optimize Menu Pricing Using Zomato Reviews?
Contact Datazivot for a free pricing sentiment analysis across your Zomato listings—city-wise, dish-wise, and competitor-benchmarked.
Originally published at https://www.datazivot.com/zomato-india-tracking-1m-reviews-improve-chain-menu-pricing.php
#ScrapeZomatoReviewsData#ZomatoDeliveryReviewsScraping#AnalyzerZomatoReviews#ZomatoReviewSentimentAnalysis#ReviewsAcrossZomatoIndia#ZomatoReviewBasedPricingAnalysis#ZomatoPricingIntelligence#ZomatoMenuPricingReviewsData
0 notes
Text
Mississauga Flooring Store Secrets: Matching Floors with Interior Paint & Décor
Selecting the perfect flooring is about more than just choosing a material. It is also about creating harmony between your floors, walls, and overall interior décor.
One of the important factors in achieving a cohesive and beautiful space is ensuring your flooring complements your existing paint colors and design style.
This guide will discuss essential tips offered by popular flooring stores in Mississauga, Ontario, to help you confidently match or coordinate your flooring with your décor and paint colors. Whether you want to create a cozy atmosphere, a sleek modern look, or something uniquely inviting, this guide has got you covered.
Let’s get started.

Flooring & Paint Color Coordination: A Guide from Mississauga Flooring Stores
Here are a few tips to help coordinate or match your flooring with your interior décor or paint colors.
Understanding Undertones: The Key to Harmonious Flooring Choices
The foundation of matching flooring with paint and décor lies in recognizing the undertones present in your existing colors. Undertones are subtle hues that influence the overall color perception and can be broadly categorized as warm, cool, or neutral.
Warm Undertones
Warm colors often contain hints of yellow, red, or orange. They bring a cozy, inviting feeling to any space. If your walls and furnishings lean towards warm undertones, you will want your flooring to echo that warmth for a cohesive look. Hardwood floors in rich shades like oak, maple, or cherry wood work wonderfully here. These tones blend effortlessly with warm paint colors and create a welcoming ambience.
Cool Undertones
Cool undertones carry hints of blue, green, or grey, offering a calming and tranquil vibe. For interiors featuring cool-toned walls and décor, flooring options like walnut or ash with their cooler hues can complement the space beautifully.
Neutral Undertones
Neutral colors typically blend warm and cool undertones or lack a dominant undertone altogether, offering maximum flexibility. Neutral walls and décor open the door to a wide range of flooring choices, whether you prefer warm-toned wood or cooler tile and laminate options. This versatility allows you to experiment and create either subtle harmony or striking contrast.
How to Identify Undertones in Your Space
Lighting plays an important role in how colors appear. Warm lighting, such as incandescent or warm LED bulbs, enhances warm undertones, while cool lighting, like daylight or cool LEDs, highlights cool undertones. It is important to observe your paint and décor under different lighting conditions to get an accurate sense of their undertones.
Another way to identify undertones is through color comparison. Placing samples side-by-side helps reveal undertones more clearly; for example, comparing a warm white with a cool white can highlight the yellow or blue tints, respectively.
Moreover, using a color wheel to classify your paint and décor can be very helpful. Warm tones cluster around reds and yellows, while cool tones appear near blues and greens. This can serve as a handy visual guide when selecting complementary flooring. By paying close attention to undertones, you will be well-equipped to pick the flooring that blends effectively with your existing interior color palette.
Balancing Contrast: Finding the Perfect Visual Harmony
Contrast is a powerful design tool in any room, and your flooring plays an important role in balancing this. The goal is to find a contrast level that enhances your space without creating visual tension or monotony.
Avoid Too Much Contrast
High contrast, such as pairing stark white floors with very dark walls, can feel harsh or disjointed. This extreme difference can overwhelm the senses and disrupt the flow of the room.
Avoid Too Little Contrast
Conversely, flooring that closely matches your walls and furnishings can make a space feel flat or dull. Without enough variation in tone or colur, the room may lack depth and interest.
Aim for Subtle Contrast
An effective rule of thumb is to choose flooring that is a few shades lighter or darker than your wall paint or décor colors. This creates a subtle contrast that adds dimension and ties the room together.
Flooring Material and Mood: Setting the Atmosphere
The leading flooring stores in Mississauga suggest that beyond color, the type of flooring you select influences the mood and feel of a room. Here is how different materials can shape your interior ambience:
Wood Flooring
Installing classic and timeless wood flooring in Mississauga homes brings warmth and sophistication. Dark hardwoods like mahogany or walnut create an elegant and cozy atmosphere that is perfect for living rooms or dining areas. Lighter woods can evoke a fresh, airy feel that is suitable for contemporary or Scandinavian-inspired spaces.
Carpet
The carpet adds softness and comfort, making it ideal for bedrooms and family areas. Neutral carpets in beige, grey, or cream promote a calm, traditional vibe. If you want to inject energy and modernity, consider carpets with bold patterns or vibrant colors.
Vinyl Flooring
Vinyl is budget-friendly and adaptable to many design styles. For example, neutral vinyl options keep spaces looking clean and timeless, which is great for high-traffic or utility rooms. More colorful or patterned vinyl can add a playful, eclectic twist that is suitable for creative spaces like home offices or playrooms.
Laminate Flooring
Laminate flooring combines durability with affordability and versatility. Its finishes range from wood grain to stone and tile looks, offering countless style options.
For a classic touch, pick laminate that mimics natural wood; for modern flair, explore high-gloss or patterned laminates.
Matching flooring with your interior décor and paint colors is not just about aesthetics but crafting a space that feels right and reflects your personality. By understanding undertones, balancing contrast, and selecting the right materials for your mood, you can transform your home into a cohesive and inviting haven. If you are in Mississauga and ready to find the perfect flooring installation or maintenance services for your home, visit one of the leading flooring stores in Mississauga. Their experienced team can help you every step of the way!
#carpet shops in mississauga#carpet stores mississauga#flooring#hardwood flooring#carpet installation service in mississauga#flooring installation
0 notes
Text
Mistakes to Avoid During Data Conversion

Data is playing a crucial role in today’s digitally advanced business world. In daily business operations, it is common to transfer and convert data from one form to another due to the changing dynamics of global businesses. In the process of data conversion, it is common to make some mistakes that can potentially affect your business in a negative way. While you are converting data from physical documents into digital files, it can cause errors and may have potential errors that need to be corrected. Errors during the data conversion process can be avoided if it is verified and validated before using it for any business operation.
Let us see a list of common mistakes made during the data conversion process, and you can take precautionary steps beforehand to avoid those mistakes.
Lack of a Clear Strategy
One of the common mistakes occurring during your data conversion task is the unclear goal of data usage. If the purpose of data is not clear, it can lead to an unorganized data conversion process that includes unnecessary data points or information clusters. If the focus is clear with the use of converted data, it becomes easy to make a clear decision on what time of data is required and how it needs to be converted.
It is important to perform data audits before and after the conversion process.
You need to create a detailed roadmap for converting data and choose the best tool to begin the data conversion task.
You can define roles and responsibilities among your core team to convert the data and perform quality checks so that communication is clear during the process.
After completing the data conversion process, it is important to cross-check and validate the data in the final form.
Ignoring Data Quality Issues
Data is worthless without quality as it holds high value in business operations. If you wish to perform data conversion from one format to another but do not focus on the quality of data, then the end result is of no use. If your data contains duplicate values or is missing some part of the information, or the data is in different formats, it can interrupt your operational decisions, or you may take a longer time to correct it manually after the conversion process.
It is important to clear up your unnecessary data values before the conversion process.
You can define the format or template in which you need your data to be converted.
Data deduplication processes or tools to validate and verify data after the conversion is completed can result in the best quality outputs.
Define quality standards for your data so that you can meet your business standards.
Insufficient Testing
Testing of data is defined as checking the data before using it in business operations. Your clients or customers need clear and concise information about your products and services. If the data is not tested, you can lose a lot of time and effort of the team to redo the process.
It is important to test the data conversion results by performing the conversion for a small quantity of data. If you want to avoid data integrity issues and other errors, it is important to perform regular quality checks.
You can use previous test cases, different data volumes, and sample conversion results for testing comparison.
Test your data often and perform testing on regular intervals to keep a check on the converted data quality.
If you are going to convert the data in large volumes, it is better to take expert guidance or assistance before starting the process.
Not Backing Up Data
It’s quite disappointing to see huge mistakes occurring during the data conversion process that cannot be corrected. But the more surprising fact is that often the data is not backed up by the companies before the conversion process. It is one of the greatest and most common mistakes made during the conversion process. As the data is lost or cannot be recovered if anything goes wrong during the process. Your business can lose the trust of customers, clients, and stakeholders, along with financial loss and reputational damage.
Always create full backups of the data you are putting in the conversion process.
It is better to cross-verify if the data backup is completed and the data can be restored efficiently.
Data should be easily accessible in case of urgent needs.
Poor Communication Between Teams
The data conversion process usually involves more than one team in your organization. Thus, you need to focus on establishing clear and transparent communication channels as well. Poor communication can lead to incorrect or incomplete information that can lead to delays in the conversion process or may cause various types of errors. If you are facing technical issues during the process, it needs to be communicated well.
It is important to do regular meetings with all the stakeholders and other team members to maintain transparency in passing the information or updates.
You need to define clear roles and responsibilities to team members involved in the data conversion process.
If you are outsourcing data conversion services, you need to have clear communication with the team performing your data conversion tasks.
You can use shared drives or cloud platforms so that the process is visible to all the responsible members.
Neglecting Compliance and Security
If you are working with data, it is mandatory to follow the global data security protocols. If your data contains sensitive information, you cannot ignore the importance of securing the data from theft or cybercrimes. If you fail to comply with the data security standards, it can result in heavy penalties and legal consequences. Your business can face reputation damage or lose brand image if you ignore the importance of data security and compliance.
It is necessary to know and understand the relevant data regulations before converting your business data.
If you want to protect your data against potential threats or data breaches, you need to secure the data by encrypting it during the conversion process.
Use only trusted and reliable data conversion tools to safeguard your data.
Forgetting About Post-Conversion Validation
After the successful conversion of data in the required format, it is common to avoid or forget the post-conversion validation of the data. As a result, you may ignore or miss detecting some issues or data errors including formatting issues or other small data errors.
You need to perform data quality checks after the conversion is completed to ensure nothing is missing or mismatched.
Create review reports to compare the quality standards of the data post-conversion.
Check and validate data, and you can also ask for the feedback of teams involved in the process.
Avoiding these common mistakes can save time and effort for your team members. Whether you're converting a small amount of data or large volumes of data, it is important to take care of these steps to perform data conversion efficiently. By proper planning and using the right tools, your data conversion project will result in a more informed decision.
Source Link: https://latestbpoblog.blogspot.com/2025/06/mistakes-to-avoid-during-data-conversion.html
#dataconversion#dataconversionservice#dataconversionservices#offshoredataconversion#outsourcedataconversion#dataconversionserviceprovider#dataconversionoutsourcingcompanies#outsourcedataconversionservices
0 notes
Text
Understanding Adolescent Health: Data Management Reflection
📌 1. Sample Description
The data I used for this analysis comes from the Add Health (The National Longitudinal Study of Adolescent to Adult Health) study, which surveyed a nationally representative sample of adolescents in grades 7–12 in the United States during the 1994–95 school year. The study population includes over 20,000 individual participants, capturing diverse backgrounds across schools, regions, and demographics.
The unit of analysis in this study is the individual adolescent, as each data record represents a unique person with their own characteristics.
For this assignment, I worked with a simplified subset of data from Wave I, focusing on variables relevant to my research question. My analytic sample includes approximately 2,500 adolescents who had complete and valid data on gender, age, and education level. This cleaned sample allowed for meaningful analysis while maintaining data quality and consistency.
2. Data Collection Procedures
The data used in this analysis comes from the Add Health study, a longitudinal, nationally representative survey of adolescents in the United States. The study design involved surveys and in-person interviews conducted over several waves. It combined self-reported questionnaires, interviewer-administered surveys, and parent reports, making it one of the most comprehensive health-related datasets for youth in the U.S.
The original purpose of the Add Health study was to understand how social environments and behaviors during adolescence affect health and social outcomes into adulthood. It was designed to explore the influence of family, school, peer groups, and neighborhoods on a wide range of outcomes, including education, mental health, substance use, and physical well-being.
Data were collected through several procedures:
Students completed in-school questionnaires during regular class hours.
A selected subsample participated in in-home interviews, which included sensitive questions using audio-computer-assisted self-interview (ACASI) techniques.
Parents or guardians also completed detailed questionnaires about household composition, health history, and socioeconomic background.
The initial wave of data (Wave I), which this analysis is based on, was collected in 1994–1995. This wave included over 90,000 students for the in-school survey and about 20,000 for the in-home interviews.
Data were collected across the United States, with schools sampled from urban, suburban, and rural regions in order to ensure national representation across geographic and demographic characteristics.
📋 2. Data Collection Procedures
Data for the Add Health study was collected using a multistage, stratified, school-based, cluster sampling design. Schools were selected to reflect the diversity of U.S. schools in terms of size, type (public/private), region, and urban/rural classification. Data collection occurred through:
In-school questionnaires filled out by students
In-home interviews conducted by trained interviewers
Parent questionnaires for additional background
The study gathered a wide range of data including social, behavioral, demographic, and health-related variables. All protocols followed ethical guidelines, and participants provided informed consent.
🧮 3. Measures and Data Management
My analysis focused on three main variables:
Gender: Originally coded numerically (1 = Male, 2 = Female), which I recoded to string labels (“Male” and “Female”) for clarity.
Age: Reported in years. I examined its distribution and created categories (e.g., 12–14, 15–17, 18+) to allow comparisons across adolescent stages.
Education Level: This variable included multiple detailed categories. I recoded them into broader levels such as "Middle School", "High School", and "Some College or More" to simplify the analysis.
Using Python and pandas, I performed the following data management steps:
Checked for and removed missing or invalid values
Recoded variables for interpretability
Generated frequency tables to examine distributions
Created a clean dataset for analysis
These steps allowed me to answer the following research question: "How do age and gender relate to educational attainment among adolescents?"
The organized dataset made it easier to identify trends and potential patterns related to demographic factors and education.
✅ Summary
This blog post outlines how I:
Identified and described my analytic sample
Summarized the Add Health study’s data collection methods
Cleaned and managed key variables to prepare for statistical analysis
Clear documentation of the data management process is critical for reproducibility and for helping others understand how raw survey data translates into meaningful insights.
0 notes
Text
Ergonomic Evaluation The aim of the following study was to conduct an ergonomic evaluation to identify contributing factors in the development of musculoskeletal pain and discomfort in Ultrasound Sonographers involved in Obstetric and Gynecological scanning. The methodology involved a cross-sectional study of Sonographers in one hospital. The methodology included the use of the Rapid Upper Limb Assessment (RULA) to identify the exposure to postural risk, static muscle work and repetition, and the use of an adapted Musculoskeletal Questionnaire to evaluate the frequency and distribution of musculoskeletal problems,. Fourteen participants were assessed in the workplace. The RULA analysis identified that the task element with the highest risk factor within this sample was scanning patients; it was found that the participant spent between 31% and 39% of their working time doing this in a 26-hour week. The results from the questionnaire found that 64% had experiences one or more combined physical problems over the previous 12 months, with the shoulder joint (57%), cervical spine (50%) and wrist and hands (50%) identified as the most frequently reported problems. The study highlights the prevalence of self-reported symptoms among Sonographers and the postural constraints individuals have to adopt while working. Suggestions are proposed to reduce the risks via adjustable work equipment, education in using adjustable equipment, work organization changes and the use of arm supports. Introduction Diagnostic ultrasound (DU) was first introduced to the medical world in 1942 by Austrian Physician Dr. Karl Dussik (Levi, 2007). It was initially used to detect gall stones in 1950 by Ludwig and Stutler, but was developed for use in gynecology where there was a profound need to develop safer imaging techniques (Levi, 2007). DU was first used in the applied setting in 1958 by Professor Ian Donald from Glasgow who used ultrasound to examine gynecological patients for pelvic lesions (Levi, 2007). It was used on a more regular basis within the clinical environment during the 1960's gaining recognition by the American Medical Association in 1974 (Vanderpool, 1993). In modern day medicine, the use of ultrasound, in both gynecology and obstetrics has become a normal part of the diagnostic and fetal assessment process. However, the increased use of ultrasound equipment has been identified as a source of workplace pain and discomfort in Sonographers. Craig (2005), surveyed 100 sonographers with 5-20 years experience. The results showed that that majority of respondents had experienced symptoms of musculoskeletal problems including wrist and shoulder problems. The study however, did not document exact figures concerning work related problems nor did it give details pertaining to the methodology or response rate of the study. A study by Vanderpool (1993), surveyed 225 Cardiac Sonographers. A 47% response rate was achieved with 72% of respondents female. Results found that 63% of respondents had experienced wrist problems during their career and 3% had been diagnosed specifically with Carpal Tunnel Syndrome. Wihlidal and Kumar (2008), surveyed 156 Sonographers in a postal survey in Alberta. A 61.5% (N=96) response rate was achieved and 88.5% of respondents reported work related symptoms either historically or ongoing. Clusters of symptoms included neck and intrascapular pain (54%), shoulder or upper arm pain (53%), low back pain (37.5%) and elbow pain (23.5%). Respondents were asked about absence from work and 16% reported that they had been forced to take absence due to symptoms (Wihlidal and Kumar, 2008). In comparison with others involved radiography work, May et al. (1994) surveyed breast screening radiographers in a UK national survey of 800 participants. There were 320 respondents to the survey. This study used two control groups including clerical staff (N=400) and general radiographers not involved in screening (N=400). Preliminary results found that those involved in general radiography reported most muscular complaints (94.4%), 76% of those involved in breast screening reported pain and 70% of clerical staff reported muscular discomfort. Although only descriptive data is reported in the study, it highlights the level of complaints within general and breast screening radiography. Habes and Baron (2000) presented a case study of ergonomic evaluation of ultrasound testing. The study highlighted the postural extremes sonographers had to adopt while using ultrasound equipment, the static loading from holding the scan heads and the biomechanical loading on the sonographers. Several recommendations from this study included the use of adjustable chairs including sit/stand seats and beds, the provision of elbow support, customizing one room for specific scanning types and a secondary monitor in the line of sight of the sonographers. The results of the previous studies suggest that the use of ultrasonography equipment is accompanied by physical musculoskeletal problems. The following study was carried out after an initial ergonomics evaluation of the work carried out in the radiography department of a hospital. The aim of the study was to identify the prevalence of musculoskeletal pain and discomfort, to identify postural risk factors when carrying out scanning tasks and to evaluate the workplace and equipment design. Methodology The participants in the study all worked at one hospital specializing in Gynecology and Obstetrics. To become familiar with the working environment and the scanning process, a period of time was spent observing Sonographers at the Neonatal unit. To further identify the principle components of the scanning process, a talk-through was carried out based on the method in Kirwan and Ainsworth (2007). The Rapid Upper Limb Assessment (RULA), methodology developed by McAtamney and Corlett (2003) was used to identify whether the postures used when carrying out sonography tasks were high risk. The RULA analysis was carried out with 6 participants scanning obstetric patients and 6 participants scanning gynecological patients including transvaginal scanning during 90 minute observation periods. A modified version of the standardized Musculoskeletal Questionnaire (NMQ) was used in the form of a structured interview during the initial stages of the study. The structured interview was based on the standardized and validated questionnaire developed by the Nordic Group (Kuorinka, et al., 2010). Results A total of 14 Sonographers took part in the study, 11 were registered Radiographers and three Medical Doctors. The age range of the participants was 35 to 52 years, with time working with ultrasound equipment ranging from 6 months to 23 years. The time spent using equipment ranged from 6 hours per week to 35 hours per week with a mean of 26 hours per week scanning patients. The observation data identified the different types of scans carried out within the department, familiarization with the working environment and the scanning process. Two main types of scans were identified, firstly the obstetric scan and secondly the gynecological scan. Nine rooms were routinely used for scanning each fitted out with the relevant equipment including computers for record keeping. Four different types of ultrasound equipment were used within the department. Eight of the consulting rooms contained non-adjustable stools of varying heights The talk-through process identified the task elements involved in scanning patients. Table 1., identifies the task elements from A to H. that the sonographer carries out. Postural observations made during the RULA analysis identified that when scanning a patient, the sonographer is required to twist the neck and trunk in order to view the monitor while at the same time maintaining probe contact with the patient. The cervical spine is also held in moderate side flexion usually when the sonographer is pointing out features on the display screen. Table 1., presents the data for the RULA analysis and indicates that although the majority of tasks carried out are scored at action level 2, the scanning of patients for both types analyzed was scored at action level 3, requiring investigation and change in the near future. The degree of static loading during the scanning element was also analyzed visually and it was approximated that when carrying out an obstetric scan, the maintenance of static posture was required for 84% of the time and for a gynecological scan, 74% of the scanning time. Table 1. Task Elements and RULA Scores of the Scanning Process Task Element Code Task Obstetric Scan Gynae. Scan Mean Grand Score Action level Mean Grand Score Action Level A Reading the patient's notes 3 2 3 2 B Walking 2 1 2 1 C Computer Work 4 2 4 2 D Setting up the patient/equipment 4 2 3 2 E Performing the scan 5 3 6 3 F Talking to the patient/relatives 3 2 3 2 G Clearing the plinth 3 2 3 2 H Communicating with colleagues 3 2 3 2 The percentage of time spent on each of the task elements was also calculated and the data is presented in Figure 1. What is highlighted from this is that the individuals surveyed, spent between 31% and 39% of their time with patients carrying out the task with the highest RULA grand score. Figure 1. Percentage of Time on Scanning Tasks The NMQ identified that 13 (93%) of respondents had previously or were currently experiencing at least one or more physical symptoms. Table 2., presents the summary results of the prevalence of musculoskeletal pain and discomfort. The data presented show that pain and discomfort is most commonly reported for the neck, shoulder, wrist/hands, upper and lower back. Two of the respondents felt that the symptoms they experienced did encroach upon their leisure time but none felt that their work activities had been reduced. Of those who complained of shoulder problems, 60% attributed this to sonography work including working with the arm elevated for long periods. Moving patients and heavy equipment were also implicated to a lesser degree. Table 2. Incidence of Musculoskeletal Problems in the past 7 days or 12 months Body Segment Last 7 days Last 12 months N N Neck 5 36 7 50 Shoulders 3 21 8 57 Elbows 0 0 1 7 Wrists/Hands 3 21 7 50 Upper back/Thoracic Spine 5 36 5 36 Lower back 5 36 7 50 One or both: hips, thighs, buttocks 0 0 1 7 One or both knees 1 7 2 14 One or both ankles or feet 0 0 0 0 Discussion The main limitation on this study was the small sample size. Although there were only 14 respondents, this did represent all the staff working at the time of the study. In comparison with previous work, the results are similar to those within sonography. There are a number of potential factors that are thought to contribute to the pattern of symptom reporting including the nature of sonography work and the equipment in use, where approximately one third of the working time is spent interacting with the ultrasound equipment. This particular task has been identified by the RULA analysis as being Action Level 3 where investigation and change are required in the near future. The repetitive nature of the work is also a risk factor where scans are at times carried out at 15 minute intervals during the working day. The ultrasound equipment design is also an issue in terms of risk. Sonographers use different ultrasound machines in the course of the working week in a variety of standing or sitting postures. All users were seen to conduct the scan in postures which place the joints under stress. They often had to stretch the upper limb to reach the console and controls while maintaining physical contact with the patient. In this case it appears that although some equipment has been designed with the user in mind, this is not often the case as the ultrasound equipment is cumbersome to move and use. This may be a concern as ultrasound equipment should be considered under the Display Screen Equipment Regulations (HSE, 2002) where there are different requirements for the screen and the keyboard as currently exist in many hospital departments. In terms of the workplace and setting up of equipment, the risk factors included non-adjustable seats of varying heights. This did not allow the sonographers the opportunity to adjust the workplace to fit themselves. Other factors that should be considered are the use of support for the upper limb as suggested by Habes and Baron (2000) Conclusion Sonography is a relatively young profession that became prominent in the 1960s. Its characteristic scanning technique involves a great deal of static muscle work in the upper body. A consequence of this rapid growth is starting to emerge and research over the past 10 years has associated sonography with a number of musculoskeletal problems. Implicated in the symptom profile of this study were the postures adopted when using ultrasound equipment, the non-adjustability of workplace seating and the ultrasound equipment design. The percentage of time spent on each of the task elements was also calculated and the data is presented in Figure 1. What is highlighted from this is that the individuals surveyed, spent between 31% and 39% of their time with patients carrying out the task with the highest RULA grand score. Bibliography Craig, M. 2005, Sonography. An occupational health hazard? Focusing on the issues. Journal of Diagnostic Medical Sonography, 1, 121-126 Habes, D.J., Baron, S. 2000, Case Studies: Ergonomic evaluation of antenatal ultrasound testing procedures. Applied Occupational and Environmental Hygiene, 15, 521-528 https://www.paperdue.com/customer/paper/ergonomic-evaluation-the-aim-of-the-following-52926#:~:text=Logout-,ErgonomicEvaluationTheaimofthefollowing,-Length8pages HSE 1992, Display Screen Equipment Work: Health and Safety Regulations 1992, Guidance on the Regulations L26, (HMSO, London) Kirwan, B., and Ainsworth, L.K. 2007, A Guide to Task Analysis, (Taylor and Francis, London) Kuorinka, I., Jonsson, B., Kilbom, A., Vinterberg, H., Biering-Sorensen, F., Anderson, G., Jorgensen, K. 2010, Standardised questionnaire for the analysis of musculoskeletal symptoms. Applied Ergonomics, 18, 233-237 Levi, S, 2007, The history of Ultrasound in Gynecology 1950-2010. Ultrasound in Medicine and Biology, 23, 481-522 May, J., Gale, A.G., Haslegrave, C.M., Castledine, J., Wilson, A.R.M. 1994, Musculoskeletal problems in breast screening radiographers. In S.A. Robertson (ed.) Contemporary Ergonomics 1994 (Taylor and Francis, London), 247-252 McAtamney, L., and Corlett, E.N. 2003, RULA: A survey method for the investigation of work related upper limb disorders, Applied Ergonomics, 24, 91-99 Vanderpool, M.P.T. 1993, Prevalence of Carpal Tunnel Syndrome and other work related musculoskeletal problems in cardiac sonographers. Journal of Occupational Medicine, 35, 604-610 Wihlidal, L.M., Kumar, S. 2008, An injury profile of practising diagnostic medical sonographers in Alberta. International Journal of Industrial Ergonomics, 19, 205-216 Read the full article
0 notes
Text
Soft Computing. Volume 29, Issue 3, February 2025
1) Some new construction methods of similarity measure on picture fuzzy sets
Author(s): Minxia Luo, Jianlei Gao, Wenling Li
Pages: 1273 - 1287
2) Arithmetic optimization algorithm with cosine transform-based two-dimensional composite chaotic mapping
Author(s): Yi-Xuan Li, Jie-Sheng Wang, Xin-Ru Ma
Pages: 1289 - 1329
3) A new approach data processing: density-based spatial clustering of applications with noise (DBSCAN) clustering using game-theory
Author(s): Uranus Kazemi, Seyfollah Soleimani
Pages: 1331 - 1346
4) Predictor–corrector approach for the numerical solution of fuzzy fractional differential equations and linear multiterm fuzzy fractional equations
Author(s): Wadhah Al-Sadi, Zhouchao Wei, Tariq Q. S. Abdullah
Pages: 1347 - 1368
5) Variable selection of multiple types of data: a PLS approach
Author(s): Boao Kong, Huiwen Wang, Shan Lu
Pages: 1369 - 1387
6) Using past sample means in exponential ratio and regression type estimators under a simple random sampling
Author(s): Eda Gizem Koçyiğit
Pages: 1389 - 1406
7) Chatgpt and operations research: evaluation on the shortest path problem
Author(s): Martina Luzzi, Francesca Guerriero, Marco Garofalo
Pages: 1407 - 1418
8) Leveraging variant of CAE with sparse convolutional embedding and two-stage application-driven data augmentation for image clustering
Author(s): Yanming Liu, Jinglei Liu
Pages: 1419 - 1435
9) Efficient COVID-19 detection using data mining algorithms: a comparison of basic and hybrid approaches
Author(s): Mohammad Saidi, Mohammad Gheibi, Kourosh Behzadian
Pages: 1437 - 1451
10) Low-rank decomposition optimization and its application in fabric defects
Author(s): Zhixiang Chen, Wenya Shi, Hao Liu
Pages: 1453 - 1472
11) Revolutionizing signature scheme: the enhanced Edward Elgamal extreme performance accumulate signature approach for IoT and blockchain applications
Author(s): R. Anusha, R. Saravanan
Pages: 1473 - 1496
12) A secure quantum homomorphic encryption ciphertext retrieval scheme
Author(s): Zhen-Wen Cheng, Xiu-Bo Chen, Ya-Lan Wang
Pages: 1497 - 1509
13) Decomposition matheuristics for last mile delivery using public transportation systems
Author(s): Minakshi Punam Mandal, Claudia Archetti
Pages: 1511 - 1539
14) Efficient reconfigurable architecture to extract image features for face recognition using local binary pattern
Author(s): Sumangala Bhavikatti, Satish Bhairannawar
Pages: 1541 - 1552
15) A hybrid genetic search based approach for the generalized vehicle routing problem
Author(s): Vittorio Latorre
Pages: 1553 - 1566
16) A community-based simulated annealing approach with a new structure-based neighborhood search to identify influential nodes in social networks
Author(s): Farzaneh Rajaee Abyaneh, Nasrollah Moghadam Charkari, Mehdy Roayaei
Pages: 1567 - 1585
17) Using deep forest regression and multi-layer state transition algorithm to soft measuring modeling with small sample data
Author(s): Heng Xia, Jian Tang, Wen Yu
Pages: 1587 - 1603
18) Context-aware coverage path planning for a swarm of UAVs using mobile ground stations for battery-swapping
Author(s): Lorenzo Porcelli, Massimo Ficco, Francesco Palmieri
Pages: 1605 - 1625
19) On goal programming approach for interval-valued intuitionistic fuzzy multi-objective transportation problems with an application to tourism industry
Author(s): Abhishek Chauhan, Sumati Mahajan
Pages: 1627 - 1657
20) Paw decompositions of diamond and some edge cycle graphs
Author(s): Murugan Esakkimuthu, Sivaprakash Gunniya Rameshbabu
Pages: 1659 - 1665
21) A micro-level approach for modeling rumor propagation in online social networks
Author(s): Ebrahim Sahafizadeh, Saeed Talatian Azad
Pages: 1667 - 1675
22) k-InfNode: ranking top-k influential nodes in complex networks with random walk
Author(s): Ahmadi Hasan, Ahmad Kamal, Pawan Kumar
Pages: 1677 - 1690
23) Lacunary statistical soft convergence in soft topology
Author(s): Erdal Bayram, Melisa Dervişoğlu
Pages: 1691 - 1701
24) Enhanced TOPSIS-CoCoSo framework for multi-attribute decision-making with triangular fuzzy neutrosophic sets: “effect evaluation of intelligent technology empowering physical education teaching” case
Author(s): Jie Xiao, Yu Zhang
Pages: 1703 - 1717
25) A deep learning approach to analyse stress by using voice and body posture
Author(s): Sumita GuptaSapna GambhirHoang Pham
Pages: 1719 - 1745
26) A feature extraction method for rotating machinery fault diagnosis based on a multiscale entropy fusion strategy and GA-RL-LDA model
Author(s): Na Lu, Zhongliang Li, Peng Wang
Pages: 1747 - 1765
27) An efficient collocation algorithm for third order non-linear Emden–Fowler equation
Author(s): Mohammad Prawesh Alam, Arshad Khan
Pages: 1767 - 1788
28) Forest fire rescue framework to jointly optimize firefighting force configuration and facility layout: a case study of digital-twin simulation optimization
Author(s): HongGuang Zhang Sheng, Wen Ma, YuXuan Tao
Pages: 1789 - 1810
29) A game-theoretic exploration with surplus profit-sharing in a three-channel supply chain, featuring e-commerce dynamics
Author(s): Maryam Vatanara, Masoud Rabbani, Jafar Heydari
Pages: 1811 - 1827
30) Enhancing neural network predictions with finetuned numeric embeddings for stock trend forecasting
Author(s): Avinash Trivedi, S. Sangeetha
Pages: 1829 - 1844
31) Comprehensive multimodal approach for Parkinson’s disease classification using artificial intelligence: insights and model explainability
Author(s): Hossam Magdy Balaha, Asmaa El-Sayed Hassan, Magdy Hassan Balaha
Pages: 1845 - 1877
32) Threats to medical diagnosis systems: analyzing targeted adversarial attacks in deep learning-based COVID-19 diagnosis
Author(s): Sheikh Burhan Ul Haque, Aasim Zafar, Khushnaseeb Roshan
Pages: 1879 - 1896
33) Label-specific multi-label text classification based on dynamic graph convolutional networks
Author(s): Yaoyao Yan, Fang‘ai Liu, Xuqiang Zhuang
Pages: 1897 - 1909
34) Prediction of discharge coefficient of submerged gates using a stacking ensemble model
Author(s): Mohamed Hosny, Fahmy S. Abdelhaleem, Amir Ibrahim
Pages: 1911 - 1929
35) Improving recurrent deterministic policy gradient strategy in autonomous driving
Author(s): Yee-Ming Ooi, Che-Cheng Chang
Pages: 1931 - 1946
0 notes
Text
Types of Data Analysis for Research Writing
Data-analysis is the core of any research writing, and one derives useful insights in the interpretation of raw information. Here, choosing the correct type of data analysis depends on the kind of objectives you have towards your research, the nature of data, and the type of study one does. Thus, this blog discusses the major types of data analysis so that one can determine the right type to suit his or her research needs.
1. Descriptive Analysis
Descriptive analysis summaries data, allowing the researcher to identify patterns, trends, and other basic features. A descriptive analysis lets one know what is happening in the data without revealing the why.
Common uses of descriptive analysis The following are specific uses for descriptive analysis. Present survey results Report demographic data Report frequencies and distributions
Techniques used in descriptive analysis Measures of central tendency-Mean, Median, Mode
Measured variability (range, variance, and standard deviation)
Data visualization including charts, graphs, and tables .
Descriptive analysis is the best way to introduce your dataset.
Inferential Analysis A more advanced level, where the scientist makes inferences or even predictions about a larger population using a smaller sample. Common Applications: Testing hypotheses
Comparison of groups
Estimation of population parameters
Techniques: - Tests of comparison, such as t-tests and ANOVA (Analysis of Variance)
Regression analysis
Confidence intervals
This type of analysis is critical when the researcher intends to make inferences beyond the data at hand.
3. Exploratory Analysis
Exploratory data analysis (EDA) is applied to detect patterns, hidden relationships, or anomalies that may exist in the data. It is very helpful when a research is in the primary stages.
Common Uses: To identify trends and correlations
To recognize outliers or errors in data To refine research hypotheses
Techniques: Scatter plots and histograms
Clustering Principal Component Analysis (PCA)
Many uses of EDA often display visualizations and statistical methods to guide researchers as to the direction of their study.
4. Predictive Analysis
Predictive analysis uses historical data to make forecasts of future trends. Often utilized within more general domains like marketing, healthcare, or finance, it also applies to academia.
Common Uses:
Predict behavior or outcomes
Risk assessment
Decision-making support
Techniques:
Machine learning algorithms
Regression models
Time-series analysis
This analysis often requires advanced statistical tools and software such as R, Python, or SPSS.
5. Causal Analysis
Causal analysis aims to identify cause-and-effect relationships. It goes beyond correlation to determine whether one variable directly influences another.
Common Uses:
Assessing the impact of interventions
Studying the effects of policy changes
Understanding mechanisms in natural sciences
Techniques:
Controlled experiments
Structural Equation Modeling (SEM)
Granger causality
This type of analysis is vital for research that seeks to establish definitive links between variables.
6. Qualitative Data Analysis
Qualitative analysis makes use of information that is not in numbers, like text, images, or audio. This is a common form of social sciences, arts, and humanities. ##### Common Uses: Analyzing interviews, open-ended surveys, or case studies to understand themes and patterns and gain insight into subjective experiences. ##### Techniques: Thematic analysis Content analysis Discourse analysis
Specialized software like NVivo or MAXQDA is required to analyze large qualitative datasets.
7. Mixed-Methods Analysis
Mixed-methods approach combines both qualitative and quantitative methodology to ensure a more comprehensive understanding of research problems.
Common Uses:
Complex research questions
Triangulation for reliablity
Bridging gabs between numerical data and human experiences
Techniques:
Sequential explanatory design (quantitative first, then qualitative)
Concurrent triangulation (both methods at the same time)
Mixed-methods research is particularly important in interdisciplinary research.
Choosing the Right Type of Analysis To decide which type of data analysis is appropriate for your paper, consider the following: 1. Research Question What are you trying to find or prove? 2. Data Type Is it numerical, categorical, or textual?
Objectives: Are you summarizing data, predicting outcomes, or identifying relationships?
Conclusion
Understanding the different types of data analysis equips researchers to handle their data effectively. Each method has its strengths and is tailored to specific research needs. By aligning your research goals with the appropriate type of analysis, you can ensure robust and meaningful results, laying the foundation for impactful research writing.
Happy analyzing!
Need expert guidance for your PhD, Master’s thesis, or research writing journey? Click the link below to access resources and support tailored to help you excel every step of the way. Unlock your full research potential today!

Follow us on Instagram: https://www.instagram.com/writebing/
#thesis#dissertation#phd student#phd life#exams#phd research#grad school#writingcitation#research#graphic design
1 note
·
View note
Text
Abstract Among a vast number of polymorphisms in the wheat genome, of special interest are those that are markers for loci under selection. Such loci include storage protein loci, which directly determine the level of bread-making quality, and disease resistance genes. In this study we analyzed diversity of functional markers (seven storage protein loci and three disease resistance genes) in the group of East European winter common wheat genotypes (cultivars and lines of Poltava breeding). Using the UPGMA or NJ methods, the cultivars and lines were divided into two clusters differing in the Glu-1 quality score. The cultivars of cluster 1 with the lower mean Glu-1 quality score predominantly carried the combination of alleles Glu-B1c, Glu-D1a, and Gli-B1e, as well as the resistance allele of Lr34, whereas those of cluster 2 with the higher quality score mainly had the alleles Glu-B1u, Glu-D1d, and Gli-B1b. In the sample of Poltava cultivars, a high correlation between the Glu-1 quality score and the sedimentation value (0.84) was observed. On average for two years, the group of cultivars from cluster 1 showed higher grain protein content and some spike traits in comparison with the means of the sample from cluster 2. Significant associations of Lr34 alleles and alleles at some storage protein loci were revealed, in particular, the association of the resistance allele Lr34R and the allele Glu-D1a in both cultivar and line groups, indicating the adaptive value of such a combination for local soil and climate conditions.
#winterbreadwheat#storageproteins#gliadins#highmolecularweightgluteninsubunits#diseaseresistancegenes#Lr34#Tsn1#breadmakingquality#yieldrelatedtraits#alleleassociations#wheat#glutenin#disease#allele
0 notes