#Verified Address Data
Explore tagged Tumblr posts
Text
Residential And Business Address Lists
Access verified Residential and Business Address Lists across Australia for precise targeting and outreach. Ideal for marketing, research, and analysis, our platform offers postcode-level data with instant downloads to support smarter campaigns and accurate customer engagement.
#Verified Address Data#Direct Mail Address Lists#High-Quality Address Lists#Marketing List for Campaigns
0 notes
Text
.
#probably going to put together a guide or something about shadowbans and terminations and all that (not so) fun stuff#today I learned that most people who've been terminated have not gotten confirmation emails from the support form#and the common thread is GET THIS using the email address on file for the terminated account#EXACTLY LIKE THE FORM TELLS YOU TO#so you have to use a different email if you want to be sure the ticket goes through#which isn't ideal for a variety of reasons#primarily i have to assume that their data security policies likely rely on the customer being able to verify their email address#I mean I don't know but that seems like a pretty big one#anyway I do (finally) for sure have a ticket in#but that would've been nice to know earlier in the week#also would've been nice to know about the VPN two months ago#but what's done is done
2 notes
·
View notes
Text
How to avoid sharing Social Media Scams in the Wake of a Disaster
The world is full of disasters. It is also full of people who have learned to profit off of disaster. It is an unfortunate fact of life in the modern social media/online environment that in order to avoid spreading scams, you have to make a continuous effort and you have to be cynical.
There are a lot of wonderful, well-meaning people in the world who want to help everyone who asks for it. Unfortunately, those people are easy to scam.
These are some rules to prevent you from either falling victim to scams or from passing scams along to other people.
These are not suggestions, these are not things to take into consideration, the rules listed here are RULES that you need to adopt in order to keep from spreading scams on social media.
Rules:
Never, ever share screenshots of fundraisers or resources that you haven’t verified yourself. If you see a screenshot of, say, the Antelope Valley Fairgrounds Instagram announcing that they will be accepting evacuees with RVs, you go find the Antelope Valley Fairgrounds website, you find the social media linked on their website, and you check that the post you’re seeing actually came from the entity it’s claiming to. Once you have proved that the post actually came from the entity it’s claiming to, double check that entity with a couple of verifiable sources. So, for instance, if I was checking on the Guitar Center Music Foundation I’d check Guitar Center’s website and maybe I’d look for news articles about donations from the foundation. If I was looking up the Antelope Valley Fairgrounds, I’d look for a local newspaper calendar of events that linked to the fairgrounds or would check the city websites in the area and search “fairgrounds” on them. I would not share a link to a social media page for an organization until I was 100% certain that it was actually associated with the organization. You shouldn’t either. If you see a post that claims to come from a specific group but all you have is the screenshot of the post, go find the group’s website and if it all checks out you may share it IF AND ONLY IF you add the link to the post. And if a post has a link already, click through it and STILL check that everything looks okay.
Never give money or information to someone with a free email address. This sucks. I know. But if the group you’re looking at only has a gmail address or a protonmail you have no way of knowing if they’re legitimately associated with the organization at a glance. And even if they ARE associated with the organization, the free email account demonstrates a lack of planning/commitment that has troubling implications for the handling of your money or data.
Do not share screenshots of “resources,” headlines, social media posts, or news articles. I’m done with screenshots. Screenshots are easy to fake and almost always remove context from the discussion. A standalone screenshot isn’t information, it’s a trap to get you to share something without thinking. Do not *trust* screenshots of “resources,” headlines, social media posts, or news articles. Always assume a screenshot is faked unless you have found the original post yourself. A screenshot isn’t a “resource” it is an un-source, it is intentionally removing information from the viewer and we are well past the time when people should have understood that sharing screenshots without a link to the original text in context is never, every trustworthy.
Do not give money or information to accounts without a history. This may mean individual social media accounts, or it may mean a shiny new mutual aid project that popped up near your house. It’s unfortunate that people have their accounts deleted, it’s unfortunate that new orgs have trouble finding support, but the likelihood that a new account is a scam is simply too high to trust your money or information with it. If someone is asking for money or offering help on an account that hasn’t posted for years, or that suddenly changed all its content, or that has only existed for a month with no links to other, older sites and socials, you shouldn’t trust that account.
Okay, those are the RULES. Those are the lines you draw in the sand. The TL;DR version is this:
Don’t share posts you haven’t personally verified
Don’t give money or information to accounts with generic email accounts like gmail
Don’t share or trust screenshots that have no links or further context
Don’t give info or money to brand new accounts
I absolve you of any guilt you have surrounding this. You want to share that post to help a stranger but they have only had an account for a week. You want to spread that resource, but unfortunately it is only available as screenshots of an anonymous instagram account. You think that perhaps that mutual aid group really can help people, but the only way contact them is to put your info into a google form and send an email to their gmail account. That post seems really helpful, but actually you can’t find anything that suggests that the Mt. Pacifico Aquatic Center exists outside of this twitter account. No more guilt! Guilt be gone! You do not have to feel bad for not sharing these things, or not reaching out, or not giving money because doing so would be irresponsible and would put other people at risk of being tricked by scammers or wasting what money they can donate on a potential fraud.
Now, some tips:
Always, always, always take at least ten minutes to think about giving someone money or your information online. Read the post that moved you, then re-read it, then go sit away from it for ten minutes and think about it. There’s a good chance you will still want to give, or sign up, but ten minutes away will give you a chance to consider if there are any red flags in the post that inspired you.
Independently search everything you’re going to share. Go outside of social platforms and check on search engines. Check Wikipedia. Look up the website and send a while clicking around. Go on a *different* social media platform and check their account.
Just straight up search “[SUBJECT] Scam” before you do anything. See if this thing you’re looking at is actually an old scam that’s revamped for a new disaster. See if you can find an explanation of how something might be a scam or risk in a way that you didn’t understand before.
Get used to getting away from social media. Go check websites.
Learn domain name syntax. “musicfoundationguit.arcenter.com” is a bullshit scam. “guitarcenterfounditaon.org” is a bullshit scam. “guitarcenter-foundation.org” is a bullshit scam. The actual domain is “guitarcenterfoundation.org” and the link to the correct page isn’t going to be “guitarcenter.foundationfires.org” it’s going to be “guitarcenterfoundation.org/fires”
Tips for Orgs:
If you do not want your org to look like a scam you are going to have to put some effort into it. Unfortunately this will probably also require at least a little bit of money; I know it’s hard to get money together at the beginning, but it will pay off in the long run.
Invest in a domain and hosted email. You can get relatively inexpensive hosted email through most domain registrars and even if you only get one email address for your domain you can forward it to all the free gmail and protonmail accounts you want. But buy a domain, set up a simple website, and get an info@[yourdomain].com email set up because you don’t want people emailing “[email protected]” because it’s super fucking easy for a 1337 hax0r like me to set up “[email protected]” and scam the people who want to reach out to you.
Make a blog on your actual website, not on a social media site. A blog means that you can make regular posts and establish a history to prove that you are real and you do real stuff; it will also help with SEO and help to ensure that when people search for your org YOU are what comes up. Keeping up calendars of previous activities with links to those activities is also good.
Set up social handles on all the sites you use, make a “socials” page on your website, and link to your handles so that people can verify if you’re the one posting something. If you don’t make it extremely easy to find your socials, that means it’s extremely easy to set up fake accounts claiming to be you. Then put the link to your website in the bio on your socials.
If you are offering something or holding a fundraiser or doing anything on your social media page, link it back to your website. If you have an IG post offering resources, you should include a url for your site in each image. If you share a photo on twitter with the info for a march, that should link back to your website with more info about the march. If you post a fundraiser on tumblr you need to link the fundraising page of your website on that post.
If you absolutely positively cannot set up a website and a real-ass email address, set up a linktree, choose a primary social media to post on that all the others refer back to, and very explicitly state what your email address is and that you do not have other email addresses somewhere that's difficult to miss. Build a history of posts and link to other orgs that you work with or any writeups or stories about your events or projects. The point of all of this is making yourself easy to verify. "[email protected]" sucks but it sucks a lot less if it's in the bio of "@northfulltertonfnb" and that page has a two year history of posting meal share schedules and menus.
In conclusion, don't share things that you haven't personally checked. When in doubt, it is always safer not to share.
5K notes
·
View notes
Text
If you want a job at McDonald’s today, there’s a good chance you'll have to talk to Olivia. Olivia is not, in fact, a human being, but instead an AI chatbot that screens applicants, asks for their contact information and résumé, directs them to a personality test, and occasionally makes them “go insane” by repeatedly misunderstanding their most basic questions.
Until last week, the platform that runs the Olivia chatbot, built by artificial intelligence software firm Paradox.ai, also suffered from absurdly basic security flaws. As a result, virtually any hacker could have accessed the records of every chat Olivia had ever had with McDonald's applicants—including all the personal information they shared in those conversations—with tricks as straightforward as guessing that an administrator account's username and password was “123456."
On Wednesday, security researchers Ian Carroll and Sam Curry revealed that they found simple methods to hack into the backend of the AI chatbot platform on McHire.com, McDonald's website that many of its franchisees use to handle job applications. Carroll and Curry, hackers with a long track record of independent security testing, discovered that simple web-based vulnerabilities—including guessing one laughably weak password—allowed them to access a Paradox.ai account and query the company's databases that held every McHire user's chats with Olivia. The data appears to include as many as 64 million records, including applicants' names, email addresses, and phone numbers.
Carroll says he only discovered that appalling lack of security around applicants' information because he was intrigued by McDonald's decision to subject potential new hires to an AI chatbot screener and personality test. “I just thought it was pretty uniquely dystopian compared to a normal hiring process, right? And that's what made me want to look into it more,” says Carroll. “So I started applying for a job, and then after 30 minutes, we had full access to virtually every application that's ever been made to McDonald's going back years.”
When WIRED reached out to McDonald’s and Paradox.ai for comment, a spokesperson for Paradox.ai shared a blog post the company planned to publish that confirmed Carroll and Curry’s findings. The company noted that only a fraction of the records Carroll and Curry accessed contained personal information, and said it had verified that the administrator account with the “123456” password that exposed the information “was not accessed by any third party” other than the researchers. The company also added that it’s instituting a bug bounty program to better catch security vulnerabilities in the future. “We do not take this matter lightly, even though it was resolved swiftly and effectively,” Paradox.ai’s chief legal officer, Stephanie King, told WIRED in an interview. “We own this.”
In its own statement to WIRED, McDonald’s agreed that Paradox.ai was to blame. “We’re disappointed by this unacceptable vulnerability from a third-party provider, Paradox.ai. As soon as we learned of the issue, we mandated Paradox.ai to remediate the issue immediately, and it was resolved on the same day it was reported to us,” the statement reads. “We take our commitment to cyber security seriously and will continue to hold our third-party providers accountable to meeting our standards of data protection.”
Carroll says he became interested in the security of the McHire website after spotting a Reddit post complaining about McDonald's hiring chatbot wasting applicants' time with nonsense responses and misunderstandings. He and Curry started talking to the chatbot themselves, testing it for “prompt injection” vulnerabilities that can enable someone to hijack a large language model and bypass its safeguards by sending it certain commands. When they couldn't find any such flaws, they decided to see what would happen if they signed up as a McDonald's franchisee to get access to the backend of the site, but instead spotted a curious login link on McHire.com for staff at Paradox.ai, the company that built the site.
On a whim, Carroll says he tried two of the most common sets of login credentials: The username and password “admin," and then the username and password “123456.” The second of those two tries worked. “It's more common than you'd think,” Carroll says. There appeared to be no multifactor authentication for that Paradox.ai login page.
With those credentials, Carroll and Curry could see they now had administrator access to a test McDonald's “restaurant” on McHire, and they figured out all the employees listed there appeared to be Paradox.ai developers, seemingly based in Vietnam. They found a link within the platform to apparent test job postings for that nonexistent McDonald's location, clicked on one posting, applied to it, and could see their own application on the backend system they now had access to. (In its blog post, Paradox.ai notes that the test account had “not been logged into since 2019 and frankly, should have been decommissioned.”)
That's when Carroll and Curry discovered the second critical vulnerability in McHire: When they started messing with the applicant ID number for their application—a number somewhere above 64 million—they found that they could increment it down to a smaller number and see someone else's chat logs and contact information.
The two security researchers hesitated to access too many applicants' records for fear of privacy violations or hacking charges, but when they spot-checked a handful of the 64-million-plus IDs, all of them showed very real applicant information. (Paradox.ai says that the researchers accessed seven records in total, and five contained personal information of people who had interacted with the McHire site.) Carroll and Curry also shared with WIRED a small sample of the applicants' names, contact information, and the date of their applications. WIRED got in touch with two applicants via their exposed contact information, and they confirmed they had applied for jobs at McDonald's on the specified dates.
The personal information exposed by Paradox.ai's security lapses isn't the most sensitive, Carroll and Curry note. But the risk for the applicants, they argue, was heightened by the fact that the data is associated with the knowledge of their employment at McDonald's—or their intention to get a job there. “Had someone exploited this, the phishing risk would have actually been massive,” says Curry. “It's not just people's personally identifiable information and résumé. It's that information for people who are looking for a job at McDonald's, people who are eager and waiting for emails back.”
That means the data could have been used by fraudsters impersonating McDonald's recruiters and asking for financial information to set up a direct deposit, for instance. “If you wanted to do some sort of payroll scam, this is a good approach,” Curry says.
The exposure of applicants' attempts—and in some cases failures—to get what is often a minimum-wage job could also be a source of embarrassment, the two hackers point out. But Carroll notes that he would never suggest that anyone should be ashamed of working under the Golden Arches.
“I have nothing but respect for McDonald’s workers,” he says. “I go to McDonald's all the time.”
329 notes
·
View notes
Text
HERE'S WHAT YOU CAN DO:
email, call, or write your reps (this is the most important one) — use this tool to find your reps HERE IS A TEMPLATE that you can pull from.
Here is the text used in the petition that you can pull from to include in your email/letter to your reps:
I’m writing to urge you to reject the Kids Online Safety Act, a misguided bill that would put vulnerable young people at risk. KOSA would fail to address the root issues related to kid’s safety online. Instead, it would endanger some of the most vulnerable people in our society while undermining human rights and children’s privacy. The bill would result in widespread internet censorship by pressuring platforms to use incredibly broad “content filters” and giving state Attorneys General the power to decide what content kids should and shouldn’t have access to online. This power could be abused in a number of ways and be politicized to censor information and resources. KOSA would also likely lead to the greater surveillance of children online by requiring platforms to gather data to verify user identity. There is a way to protect kids and all people online from egregious data abuse and harmful content targeting: passing a strong Federal data privacy law that prevents tech companies from collecting so much sensitive data about all of us in the first place, and gives individuals the ability to sue companies that misuse their data. KOSA, although well-meaning, must not move forward. Please protect privacy and stop the spread of censorship online by opposing KOSA.
Here is an open letter from parents of trans and GNC kids that you can also add your name to/ pull from in writing your own letter
sign this petition
2K notes
·
View notes
Text
Writing Notes: Self-Editing
Take a Break Before Editing
One of the most effective self-editing techniques is to distance yourself from your writing before diving into the editing process. After completing your draft, give yourself some time away from the text – a few hours, a day, or even longer if possible. This break provides a fresh perspective, allowing you to approach your work with a more critical eye.
Read Aloud
Engage your auditory senses by reading your work aloud. This not only helps identify grammatical errors and awkward phrasing but also allows you to assess the overall flow and rhythm of your writing. Awkward sentences are more apparent when heard.
Focus on One Element at a Time
To avoid feeling overwhelmed during the self-editing process, concentrate on specific elements in each round. Start by checking for grammatical errors and punctuation, then move on to sentence structure, coherence, and finally, style. This systematic approach ensures a thorough examination of your writing.
Add Dimensions
After you are finished with your first draft, flip to the beginning and start anew. As you write and edit more of your story, you may add different aspects to a character that might need to be mentioned in a section you already edited. You might add a part of the plot that should be alluded to earlier in your book.
Fill in the Gaps
Re-reading your first draft might reveal plot holes that will be addressed via revisions. It may expose logical inconsistencies that must be buttressed with enhanced detail. If you, as the author, know a lot of details about a character’s backstory, make sure your reader does as well.
Mend Character Arcs
Audiences want engaging plots, but they also want detailed characters who undergo change during the events of a story. Use a second draft to make sure that your main character and key supporting characters follow consistent character arcs that take them on a journey over the course of the story. If your story is told through first person point of view (POV), this will be even more important as it will also affect the story’s narration.
Track the Pacing of your Story
Find ways to space out your story points so that every section of your novel is equally compelling and nothing feels shoehorned in.
Clean up Cosmetic Errors
When some first time writers think of the editing process, they mainly think of corrections to grammar, spelling, syntax, and punctuation. These elements are certainly important but such edits tend to come toward the end of the process. Obviously no book will go out for hard copy publication without proofreading for typos and grammatical errors, but in the early rounds of revising, direct most of your energy toward story and character. If you consider yourself a good writer who simply isn’t strong on elements like spelling, grammar, and punctuation, consider hiring an outside proofreader to help you with this part of the writing process.
Inject Variety
The best novels and short stories contain ample variety, no matter how long or short the entire manuscript may be. Look for ways to inject variety into your sentence structure, your narrative events, your dialogue, and your descriptive language. You never want a reader to feel like s/he’s already read a carbon copy of a certain scene from a few chapters back.
Check for Consistency
Consistency is key to maintaining a professional and polished tone in your writing. Ensure that your language, formatting, and style choices remain consistent throughout your piece. Inconsistencies can distract the reader and diminish the overall impact of your work.
Eliminate Redundancies
Effective communication is concise and to the point. During the self-editing phase, be vigilant in identifying and eliminating redundancies. Repetitive phrases and unnecessary words can dilute your message and hinder clarity.
Verify Facts and Information
If your writing incorporates facts, figures, or data, double-check the accuracy of your information. Providing accurate and up-to-date information enhances your credibility as a writer. Cross-referencing your sources during the self-editing process ensures the reliability of your content.
Consider Your Audience
Keep your target audience in mind during the self-editing process. Ensure that your language, tone, and examples are tailored to resonate with your intended readership. This step is crucial for creating a connection with your audience and enhancing the overall impact of your writing.
Utilise Editing Tools
Take advantage of the various editing tools available to writers. Spell and grammar checkers, and style guides can serve as valuable companions during the self-editing journey. However, remember that these tools are aids, not substitutes, for your critical evaluation.
Seek Feedback
Engage with others to gain fresh perspectives on your writing. Peer reviews or feedback from mentors can offer valuable insights that you might have overlooked. Embrace constructive criticism and use it to refine your work further.
Be Ruthless with Revisions
Effective self-editing requires a degree of ruthlessness. Don’t be afraid to cut or rewrite sections that do not contribute to the overall strength of your piece. Trim excess words, tighten sentences, and ensure that every element serves a purpose.
Sources: 1 2 3 4 ⚜ More: Writing Notes & References ⚜ On Editing
#writing notes#editing#writeblr#spilled ink#writing reference#studyblr#dark academia#light academia#literature#writers on tumblr#writing prompt#poets on tumblr#creative writing#fiction#lit#writing tips#writing advice#writing resources#on writing
241 notes
·
View notes
Text
DCxDP Prophecy Universe Part 7
Part 6
It took Damian the rest of the afternoon to prepare for his trip to Amity Park. Jon helpfully agreed to cover for him, on the promise of a copy of the upcoming Cheese Viking 2 and getting filled in on all the hot Bat gossip afterwards. Wasn’t friendship grand?
Pennyworth thankfully agreed that ‘bonding time’ between the Super Sons was a good use of fall break and even took the time to ‘Prepare some healthy snacks for the young Masters, lest you eat junk food the whole week’. The task also handily distracted the butler while Damian packed the Batwing with all the necessary surveillance equipment he would need and set up the program to spoof his flight data. Damian had no doubt that Father wouldn’t be fooled for long, but with the Bat it was always better to ask for forgiveness rather than permission.
The flight to Illinois was mercifully uneventful. Damian rappelled off in the middle of the eponymous city Park, then instructed the autopilot to take the plane to a wooded area outside city limits and park there in camouflage mode. Once he was sure his arrival had gone undetected, he changed into civvies and with his backpack full of gear set off in the direction of Fenton Works on foot. In jeans, sneakers, a dark hoodie and a baseball cap he looked like any other kid his age, even if he was out after curfew. Damian made sure to stick to the shadows and ducked behind cover whenever a car passed him.
All in all it took him until the early morning hours to arrive at the correct address. Intellectually, he had known the Fentons operated their workshop out of the family home, but he was in no way prepared for the monstrosity of a building that greeted him. Damian couldn’t help but stop and stare in disbelief.
What had once started out as an ordinary brownstone building had a glaring neon sign out front, proudly proclaiming the company name. Perched precariously on the roof was a gigantic metal structure that looked like a cross between a cartoon UFO and an observatory. There was no way this was legal or sane. If something like this had popped up in Gotham it would have been flagged as a Rogue hideout and bugged to hell and back. Hell, Damian was half tempted to break in immediately to start planting cameras but was held back by the likely presence of a custom security system. Mad scientists were rude like that and Damian didn’t want to tip his hand too early. He would have to at least wait until he was sure the Fentons weren’t at home.
Damian tucked his hands into the pockets of his hoodie and strolled past the building at a fake casual pace. The windows were dark and the building was silent, except for the faint hum of the neon sign. This early on a Saturday morning, the residents were likely fast asleep. He spotted an electric scooter chained up next to the stairs leading up to the entrance and made the deduction that it likely belonged to Daniel. Under the guise of retying his shoelaces, he dropped to one knee and surreptitiously attached a bug to the vehicle. Ideally he would get the opportunity to bug Daniel himself, but for now this would have to do. Hoping that no one had noticed him, Damian continued down the street.
He had researched the area ahead of time and had found an apartment a few buildings down and across the street that was advertised as available for rent and was unoccupied. Breaking in and disabling the home alarm was child’s play, and after making sure he was alone in the apartment, Damian settled in to begin his surveillance.
He pulled the handheld radiation detector out of his backpack and after making sure it was operational he slipped it into his pocket. With no way to boost its range he would have to get pretty close to Daniel with no major obstructions in the way in order to verify if he had been in contact with the marked bills he had slipped Phantom. But Damian was confident in his ability to stay undetected. After all, Daniel had no reason to suspect he was being stalked by a curious Bat.
Damian kept himself occupied by listening to the local radio broadcast over his comm. The hosts sounded like chipper twenty-somethings, excitedly shilling for various local events happening over fall break, in-between shilling for local businesses. Why anyone would want to eat at an establishment called the Nasty Burger was beyond Damian. Whenever they stopped nattering to play actual music it was a blessing even if the appeal of the songs was entirely lost on the young vigilante. Finally, at 8am they had an actual news segment. Most of it was covering major US and global events, nothing Damian hadn’t already heard. Elections, natural disasters, rising tensions in Bialya…
“...and in local news, the City Library has announced that clean-up after last week’s ghost attack is finished, and they will be open at their normal hours on Monday!” the female host said cheerily, as if she was talking about the weather. “As usual, we would like to remind our listeners to keep their third eyes peeled for any ghost sightings! In case of a ghost attack, follow standard protocol and head to your nearest ghost shelter. Thank you! And here’s Mark with sports!”
Damian was flabbergasted. Ghost attack? This city experienced supernatural incursions and treated it like it was a normal occurrence? He’d read that the Fentons were ghost hunters, but he hadn’t thought anyone was taking them seriously! If Amity Park was under attack on a regular basis, how come the Justice League didn’t have a file on the city? Surely the news should have leaked to the outside world by now!
It was rare that Damian was caught so utterly wrong footed. His cursory research into Amity Park had turned up nothing like this! He was itching to get back to the Batcomputer to do a deep dive on the city and its history. Unfortunately, all he had on him was his phone which was ill suited for serious data compilation. At best he could scour local news sites and social media for any hint as to what was going on.
After half an hour of fruitless searching, he gave up in disgust. There was no mention of ghosts anywhere, save for the Fentons’ own website. Yet the news report had been almost blasé about the subject! Something was rotten in the State of Illinois.
All he could do for now was stare out the window at the Fenton’s front porch and hope his quarry made an appearance soon.
At 9.13 AM there was finally movement at the Fenton house. A dark-haired teenager in jeans, a light T-shirt, a backpack and a bicycle helmet bounded down the front steps and unlocked the electric scooter. It was unmistakably Daniel.
Damian hurriedly packed away his things, grabbed his backpack and left the apartment. He made sure to rearm the security system and lock the door, leaving no trace of ever having been there. Of course Damian wasn’t about to pursue his target across the rooftops of an unknown city in broad daylight. He would just have to wait for Daniel to arrive at his destination and follow him there. He retrieved his phone and pulled up the tracking data. It looked like the teen was headed towards the city center.
Damian tuned his comm to the listening device he had planted and set off towards downtown Amity at a light jog. For a while, all he heard was background noise. After about ten minutes, Daniel came to a stop.
“Hey Tucker, ready to go?” That had to be Daniel.
“Hey Danny!” a second male voice answered, “I was just waiting for you. Sam says she’ll meet us at the main entrance of the mall.”
“Sweet. Hopefully we can grab something cool from Game’O’Rama if we beat the rush.”
“You said it, my dude. Come on!”
The tracker resumed its movement. Now that he had a destination, Damian used his phone to call a cab. There couldn’t be that many malls in a city this size.
Daniel and his friend ‘Tucker’ kept up a steady stream of idle chatter on their journey. Damian learned more than he ever wanted to know about the attractive qualities of the female students at their high school, the tediousness of the homework assignments they had received for the week and the reviews of recent horror movie releases. Inconsequential chit chat as far as Damian was concerned. Once the pair arrived at their destination they parked their scooters and were soon out of range of the listening device. Damian cut the transmission and spent the rest of the short cab ride trying to find information on Daniel’s companion. Since they were apparently classmates and he had a first name to go on, it didn’t take long to narrow it down to Tucker Foley. Damian made a mental note to investigate him in depth later.
The mall was moderately busy when he arrived but nowhere near as bad as Gotham. Luckily there was a floorplan displayed at the entrance and it didn’t take Damian long to find the Game’O’Rama store. Predictably, it was dedicated to video games, gaming accessories and memorabilia. A sign in the window announced a major weekend sale, likely what had drawn Daniel and his companions. Damian slipped on a pair of mirrored sunglasses to conceal his eyes and meandered into the store. Wandering between the aisles, pretending to examine the games on offer, it didn’t take him long to find his quarry and Damian got his first good look at the trio.
Daniel was almost a head taller than Damian, slightly paler and with his dark hair mussed up from the scooter ride earlier. His clothes were slightly threadbare, and not the kind that was intentional. His white T-shirt bore a faded NASA logo and his jeans were frayed at the cuffs. He had dark circles under his eyes, though not nearly as bad as Drake got when he was on a case. Nonetheless, for the moment he seemed cheerful and at ease. He was examining the back of a disk case.
“I don’t know Tuck, I’m not much for medieval fantasy,” he said amusedly, “and a lot of these monsters look like ghosts we’ve seen. I get enough of them on a day to day basis, I don’t need them in my video games too.”
Again, this talk of ghosts.
The African American male next to Daniel had to be Tucker Foley. He was just a few inches shorter than Daniel, with his hair in shoulder length dreadlocks partially covered by a red beret. A matching red T-shirt with white Atari logo and baggy camo pants screamed nerd even before you got close enough to notice the black rimmed glasses and the clunky looking device he was tapping away on. Where did he get it from, the middle-ages?
“Look, the reviews are pretty great, and if we avoid everything ghost related what’s even left?” the boy argued, “You can’t let ghosts ruin your fun, man.”
“Tucker’s right, Danny.” the third member of their group chimed in. She was dressed head to toe in black, with a sheer, lacy top, a knee-length skirt, fishnet gloves and stockings and a pair of combat boots. With the thick soles giving her added height, she was almost as tall as Daniel. She wore eerily pale foundation making her dark purple lipstick and eyeshadow pop out even more. She had a small nose stud with a matching purple stone. Her earrings were shaped like spiders dangling from a web and she wore a pentagram necklace. Damian knew some of his schoolmates belonged to the goth subculture, but Gotham Academy’s dress code heavily limited such self-expression on campus. He guessed this girl was either really dedicated to the style or really dedicated to pissing off her parents. Maybe both.This had to be ‘Sam’.
“Besides, if Technus couldn’t ruin gaming for us no one else should either!” she continued.
“Fiiiiine,” Daniel sighed, clearly playing up his reluctance. “but if Amity gets attacked by an army of goblins next I reserve the right to say ‘I told you so’!” He double checked the price tag. “Splitsies?”
The girl scoffed and plucked the case from his hand. “I’ll take this one, you can pay for lunch later. Why don’t you two go ahead to Pineapple Republic for those jeans you wanted? I’ll catch up to you.”
“If you’re sure. Thanks Sam!” Daniel leaned over and gave her a peck on the cheek. “I guess we’ll see you there.”
“Yeah, thanks Sam.”
“Go on, shoo!” she laughed and headed over to the cash register as the boys left the store. Making a split second decision, Damian grabbed a random game from the shelf and got in line behind Sam. He leaned slightly towards her, pretending to examine the figurines behind the counter and stealthily stuck a bug to her skirt. Now he could listen in on their conversation without having to risk being noticed.
After paying for his purchase he wandered off in the direction the other teens had taken. He would just have to leave the game somewhere ‘accidentally’ at the earliest opportunity. Pretending to check his phone he tuned his comm to the frequency of the new bug.
“...I think those are still a little short on you.” Sam said amusedly.
“Man, I’m glad I finally got my growth spurt, but having to replace most of my wardrobe is gonna be a pain in the ass!” Daniel complained.
“Look at it this way Danny, this could be your chance to branch out. A whole new style, a whole new you!” Sam countered enthusiastically.
Damian walked towards the source of the signal. He didn’t follow the trio directly into Pineapple Republic, instead heading into the shoe store across from the clothing store. Browsing there would let him keep an eye on the entrance.
“Let me guess, would this style include black, black and more black?” came Foley’s snarky voice.
“Black is timeless, I’ll have you know,” Sam sniffed in mock offense, “and Danny does look good in it. Just try it?”
“I don’t know Sam, I don’t wanna blow my allowance on clothes that don’t feel like me.”
“Oh! We could always try the thrift store, they have plenty of cool stuff! And upcycling is great for the environment.”
“Uh, hard pass,” came the flat reply, “I would like to survive the year with some of my dignity intact, please.”
“Yeah dude, if Dash and his cronies caught wind of Danny going to Goodwill or something they’d never let him live it down.”
“There is nothing wrong with buying second-hand!”
“Says the girl in $500 guaranteed cruelty free designer boots.” Foley shot back.
“That’s different!” Sam sputtered, “And besides, I don’t see why you still chase the approval of those jerks.”
“Easy guys, settle down,” Daniel said placatingly, “Sam, you know it’s different for us. You might be able to brush off Paulina’s snarky comments, but I can’t just brush off Dash trying to rearrange my face. I’d rather not paint an even bigger target on my back.”
Sam gave a loud sigh. “Ugh, stupid high school politics. I can’t wait to graduate.”
“I dunno, if things go according to plan you’ll have to deal with real politics, Ms Future Administrator of the EPA Manson.” Daniel teased.
“You mean Senator Manson.” Foley chimed in.
“Madam President Manson!”
“Stop it guys!” the girl laughed, “I’ll leave the political ass kissing to someone else. I just want to save the planet! But I gotta get my doctorate first.”
“Well if you do end up having to take over the country to do it, there’s one thing to keep in mind,” Foley said sagely, “You can’t be much worse than President Luthor.”
The two replied with fake gagging noises while Foley just snickered.
“But seriously, since you brought up mixing up my style… I was thinking of getting my ears pierced.” Daniel said hesitantly.
“Really? Ooh, do you want studs? Danglers? An industrial?” Sam gushed excitedly.
“Well… aw nuts.” Daniel’s voice was suddenly tense.
“You know what?” Sam rushed out, equally tense, “I think you should go and try these pants on. In the changing room. Right now.”
Damian frowned. What the hell had happened? He glanced out the shop window but couldn’t see anything out of the ordinary. Suddenly, he heard distant screams and the sound of glass breaking. It’s almost like being back in Gotham.
Part 8
#dcxdp#dpxdc#dc x dp#dp x dc#danny phantom#batman#batfamily#damian wayne#robin#prophecy universe#the one where clockwork uses prophecies to mess things up (and set things right)#no beta we die like danny#tucker foley#sam manson#help the length of this fic has run away from me#team phantom is 16 btw#damian is 12
410 notes
·
View notes
Text
Oh, also, I really hope that this point isn't news to anyone, but if you don't already have a basic understanding of what it means to develop information security, now is the fucking time.
Critically, I want to see people being responsible in how they interact with:
A) the dissemination of information and the correction or disruption of misinformation
B) privacy related or personal data (of themselves, but ESPECIALLY of others who you could unknowingly harm)
C) pictures and visual media
D) your bodies: not a good time to start leaving traces of yourself where they shouldn't be, e.g. blood, saliva, etc
E) triangulatory/tangential information (you know that guy who can tell where you are by the weather descriptions? That's an extreme example very few people can pull off, but you'd be horrified how little info I need about someone to correctly interpret whole sections of their personal history and data)
F) other people. If you have never formally done so, find a conflict resolution/group facilitation class with a local organizing group or community college. Start learning what healthy boundaries (flexible, but neither porous nor rigid) look like for you. Pick a communication style to cultivate so you can be consistent in how you navigate stressful moments. Figure out what it means to you to share space with others with intention. (And yes, there is no one way to do this, but every one of us will need to find our most secure version, whatever that is, ESPECIALLY those of us who are already vulnerable here due to past trauma, neurotype, TBI, healthcare/wellbeing needs, etc)
I'm a really open book in a lot of ways, and yall might rightly look at that and go "butts you're one to talk about infosec"
And yeah. Yeah. But like.
I know what you know. I made those choices on purpose or at the very least addressed the aftermath of the accidents with intention. I also know what I did to be protective of myself and my info, and you don't know those things. You should know how to do them for yourself though, because it will help you understand why I can have done what I've done over the years and still say this now.
It matters what people know. It matters how easy that knowledge is to revisit. It matters how much of that knowledge is heresay vs documented and verifiable. It matters what contrary information is ALSO known. It matters what interconnected information about OTHER PEOPLE is known. It matters when you haven't said anything at all versus when you said a bit versus when you said a LOT. It matters when you say a lot without saying anything at all.
Information gathering is about putting together puzzle pieces. It's slow work, and it involves a massive amount of resources to do comprehensively and at scale. Information security is about making the gathering process not worth the investment such that the gatherers give up before they are able to put together enough pieces to do real damage. This is what "need to know" means.
For example, in a healthcare practice, it is a HIPAA requirement that access to protected patient info be limited to those who have a clinically relevant reason for accessing it. This means that certain system credentials or permissions will reveal varying amounts of protected information about a person. While one MIGHT be able to put together enough puzzle pieces for certain minor information gathering from early stages (e.g. where someone will be a the specific time of their appt), one likely cannot identify deeper and more vulnerable levels of information (who is the appt with and what is it for?)
This kind of layered buffer is most important when people who AREN'T PERMITTED (permited as in able to do without effective correction/consequence, not permitted as in legally or appropriately authorized to do) to access this info are trying to access it. If someone is permitted (e.g. if person with the appropriate credentials/access permission discloses it voluntarily or if a subpoena is ordered, etc) then the level of access is less protective - they will typically simply access the level of info they need if they will be permitted to.
But there are further layers still of information security. For example, you can tie up a LOT of time forcing authorized bodies to refresh and specify their authorization over and over again, each time appropriately only providing the exact level of disclosure they have required of you. The more specific the information they are looking for, the easier it is to bury so deep down that they literally cannot access it even if they are looking right at it.
I was taught to write documentation "like at any time it could be read out by the patient in front of you, or by another provider asking us to justify a treatment, or in open court by order of a judge". For a year, my supervisor had me write four copies of every piece of documentation I ever made. My personal copy (burned upon completion of the billable note), my "soft note" that removed all protected/identifiable information from the narrative (e.g. names, ages, genders, specific diagnoses/conditions), my "hardnote" which removed anything "heresay" which had been self-reported by the patient unless I could professionally verify it), and lastly my billable note which I understood needed to offer "detailed justificstion" for the used (and named) interventions which cannot be used to work backwards and interpret the originating care conversation.
The only note that ever gets read by anyone but myself is the billable, because they others are never retained long enough to be seen by others, even if they do have the appropriate access. It becomes very difficult for someone to use the hard data they are capable of getting from me, voluntarily or by force, to actually confirm context. This is a similar principle when orhanizers compartmentalize need-to-information.
So start learning what it looks like to cordon off each layer of infosec you're about to implement in your life. What it will look like to grant someone access to a new layer.
Be responsible. We protect us.
#man i really hope i actually managed to make clear what i'm trying to say here#dogwhistles are hard when your workbook comes from three generations back lol
78 notes
·
View notes
Text
Keys guide to general scams
(Keys guide to general scams)
Hey everyone! This post is intended as a simple compilation of common scams without going into too much detail and also explains how to check for scams in general. If you want to check out info in detail, check out my tag “how to spot a scam blog”!
So here’s a quick rundown of some simple scams:
Donation scam - These scams range from medical aid to pet care and sometimes a little in between. The most common variant of these is someone needing insulin and their asking for “nt much” or claiming their “nose freezes” due to asthma. The other common kind is for a pet of theirs, usually one needing some kind of surgery or having some kind of medical condition. Another version of this scam may be themed around world events, a seasonal holiday, or a special week depending on when the account was made.
Art scam - These scams range from commission scams to commissioner scams. The common kind of scam you’ll get is someone asking you if you do commissions then request you draw their pet for around $100-$300. This price is usually more than your actual commission prices but don’t be fooled the person doesn’t want your art and often wants to only pay you by an email address which then gives you a fake payment sent email. Commissioner scams are less common but work in a similar fashion where someone will ask you if you want to commission them but their art is stolen from someone else. Another version of this scam is the mural scam where they offer to use your art in a mural but want to pay you with a check via mobile deposit but it’s a fake check and you’ll lose money.
Mutual aid support scam - This kind of scam is when you’ll get a comment on your fundraiser of someone saying you don’t seem to be getting much attention and offer to boost your post. They will then DM you and offer their services usually requiring a payment to do so. Additionally, some may contact you offering to help you but won’t use any method of support you already have. Instead they will offer to link your bank to theirs or offer a digital check. Don’t give them any information or pay anyone to get more views on your fundraiser.
Tech support scam - A very common scam where someone on Discord claims to have reported you and you need to pay support to get the report cleared up. Often seen on hacked accounts, the ‘support’ is fake and often someone wanting your account data. Additionally, this scam may also be someone sending you an ask claiming you need to go to a suspicious link to ‘verify’ your account or someone sending you a DM claiming to be support and asking for your personal information to ‘verify’ your account. Keep in mind this is just a phishing scam and your account isn’t in danger as long as you haven’t given anything.
Misc scams - Outside of the above scams, you’ll also find scams based around lottery winners, gift card giveaways, or offering you monthly allowances to be in a romantic relationship. There’s also drop shipping scams where someone’s advertising a product but doesn’t mention it’s an ad and the product is just a cheap version of an already easily affordable item and often doesn’t get shipped leaving you out of money.
—
Always check how many posts an account has with timestamps enabled to see how much time passed between each post. Usually scam accounts only have one original post with a few reblogs from a trending tag or is just random reblogs to make their account look active with no original content. You can also try searching the username to see if anyone’s posted a warning or reverse image search there pictures to see if there’s any potential the images they used are from another site without credit.
Not everyone is a native English speaker, meaning poor English in a post isn’t a sign someone’s scamming you. Additionally, not every fundraiser is a scam by default just because you was sent an ask or a DM. Those are things you can turn off if necessary or limit if you don’t want them. It’s a relatively simple process and doesn’t take more than a few seconds of your time to do.
If you found this guide useful, feel free to share it around to your friends or users who are new to this website.
70 notes
·
View notes
Text
In an unsurprising turn of events, people have been using the 4chan hack to be antisemitic.
Essentially people are claiming leaked data shows how posts on 4chan come from each country via IP addresses, and that Israel is the biggest offender.
People are claiming that the mods of 4chan are US government officials using 4chan as a honey pot, and that israelis use the site the most and are all mossad psyops trying to trick people into being right wing
This data is verifiably false thanks to an article from Denmark about 4chans users.
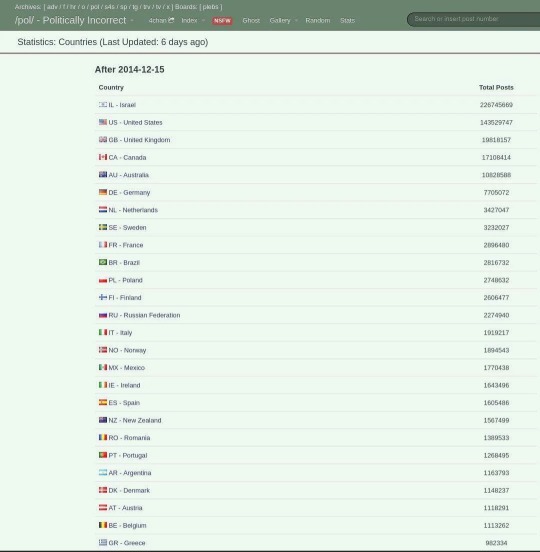
A news site on Denmark published in 2020 with data from 2018, that 170,000 unique IP addresses visit 4chan every month.
1,148,237 posts since 2014 from Denmark according to that leak. To get that 9 year post number in a single year, only 95,686 of that 170,000 will have to post only once a month.
To stay accurate to the data which is over a 9 year period, only 10,631 people from Denmark have to post once a month since 2014.
Whilst I assume the 4chan users in Denmark weren't always as high as 170,000 with both breakdowns i provided it just isn't adding up. Especially when the number of users has likely grown in the past 6 years. Denmark should be higher on the list, but it's not.
Because of course it's a lot easier to lie about data to go "the jews are controlling the world" than it is to share accurate data.
The source isn't in English, so here is the relevant screenshot from the article translated in English and you can find the original article below that
32 notes
·
View notes
Text
Australian Address Database
Access a reliable Australian Address Database with verified residential and business records. Perfect for targeted marketing, logistics, and data-driven planning. Instantly download postcode-accurate address data tailored to your campaign or business needs across Australia.
#Residential And Business Address Lists#Verified Address Data#High-Quality Address Lists#Direct Mail Address Lists
0 notes
Text
#Targeted Address Lists#Residential And Business Address Lists#Verified Address Data#High-Quality Address Lists
0 notes
Text
On Recovering From Disaster

Just before disaster struck with my 68030 homebrew, I had a plan to fork the project and take it in two directions in parallel.
The first would be my minimal Multibasic setup which was running great and was something I would be proud to exhibit at VCFSW '25.
Since that was working well, I didn't want to do anything that might make it not ready for the show. So I had assembled a second main board that I could use with other peripheral cards to continue development. My plan was to rework the memory map to move ROM and I/O addresses to the upper half of the 32-bit address space, which would allow me to use a DRAM card for up to 16MB of contiguous memory starting at address 0 — a perfect setup for running a proper OS
And then I burned up my good mainboard.
I had a spare CPLD on-hand, and I was able to get another 40MHz 68EC040 for cheap. But the 4Mbit SRAM chips are expensive, and I thought that if I was going to be paying for more SRAM, I should get the 12ns parts that would allow me to run RAM with no wait states at 50MHz. Which would require adapter boards, and more pin headers, and would have just driven the cost up even more.
Paralyzed by indecision and the rising cost, I decided to switch gears. I already have the DRAM board I built years ago, I just needed to get it working. And if I'm doing that, I may as well do the work on reorganizing my memory map.
So that's what I did. I made a new branch on my newly cleaned up repository, and set to work. I updated the mainboard bus controller logic to remove the no-longer-needed SRAM control, adjust the ROM address to start at 0x8000,0000, and move the 6850 UART address to 0x8008,0000. This freed up the entire 2GB space between 0x0000,0000 and 0x7FFF,FFFF for the DRAM card to use for main memory (my bus connector layout only allows for up to 16MB main memory, but that's plenty for my purpose).
Next, I needed to build the control logic for my DRAM board. I've done this once before on my Wrap030-ATX project a couple years ago, so I used that logic as a starting point. It … kind-of worked. Sometimes. Maybe.

I was getting random errors all over the place. Sometimes it was able to copy all of ROM into RAM and verify the copy without error, but it would fail when running code from RAM. Sometimes it wouldn't even pass the first two simple tests of writing a longword to RAM and reading it back.
Back to the data sheets to plan out the logic. I drew out a new timing diagram down to 1ns resolution, accounting for the specified propagation time for my CPLDs, and the measured signal delays for my CPU. This gave me the information I needed to build out a new state machine for the DRAM controller. In the process I also caught a few other bugs in my original logic, such as not ensuring the DRAM Write Enable strobe did not get asserted during refresh cycles.

The new state machine worked much better, but I got my timing off a bit. It worked reliably at 16MHz, but not at the intended 25MHz. At least it was working though; I can move forward with 16MHz.
The next thing to do was get my 8-port serial card working with this new setup. Every time the computer tried to access one of the 8 serial ports, it would get a bus error. This was a tough one that had me stuck for a while.
It looked like the serial card was getting addressed and asserting DSACK0# as expected, but I couldn't confirm the signal was making it back to the CPU. Every time I tried to measure the DSACK signals, the probes would increase the line capacitance (I think) too much and cause the whole computer to fail before it even got to the point of trying to address the serial ports.


I have the DSACK signals in a wired-or configuration. The logic on each card connects to the proper DSACK signal via an open-collector buffer, and is able to pull the signal low to signal that card acknowledging the bus cycle. The signal is then pulled back up to +5V by a 1kΩ resistor. This works well enough for small, slow systems, but with long bus wires or lots of chips on the bus, the extra capacitance means it can take a long time for that pull-up resistor to get the signal back up to +5V.
I made a change to my DRAM controller to actively drive the DSACK signals to +5V briefly at the end of a bus cycle before setting the pin to high-impedance. This helps ensure a fast rise time at the end of the cycle so it doesn't disrupt the next bus cycle.
It didn't fix the problem with the serial card, but it did allow me to actual probe the signals live to see what was happening — the Bus Error signal was getting asserted immediately after the CPU addressed the serial card. This didn't make much sense to me. My main board logic will assert Bus Error if no peripherals acknowledge a bus transaction within 64 clock cycles. Nothing should be asserting Bus Error so quickly.
Except … the main board bus controller. My original memory map used the lower half of the address space for the main board, and peripheral cards used the upper half. So my original main board logic was built to assert Bus Error immediately for an unused address in the lower half of the address space. I hadn't properly removed that bit of logic, so it was now asserting Bus Error for any accesses to the upper half of the address space that weren't used by the main board.
The challenges of working on a project after six years. I had forgotten that bit of logic was even there.
With that erroneous Bus Error assertation removed, the machine was finally able to properly load my Multibasic kernel and run BASIC for 8 users again.


At the moment it is running stable at 24MHz on my 25MHz-rated full 68030. It may not be the 50MHz high I was at, but after the frustration and disappointment of the past few weeks, I'm absolutely taking that as a win. 24MHz is incredible.
#mc68030#motorola 68k#motorola 68030#vcfsw#wrap030#retrotech#debugging#troubleshooting#homebrew computing#homebrew computer#retro computing
23 notes
·
View notes
Note
Genuine question, if Apple sucks and Google sucks, what phone do I get? Like, I'm a proponent of Fuck Google, but I have an Android cause I'm a bigger proponent of Fuck Apple, and I don't really have a great way to reconcile these feelings of conflict
I address this a bit in the degoogling pamphlet; iphones are genuinely better for privacy and I think the phone side of apple is less terribly reprehensible than the computer side if for no other reason than market forces prevent them from gouging quite as excessively. If you own an android your best bet is to turn off location data (everyone should be doing this for all of their devices anyway) uninstall as many apps as possible, force stop or disable as many apps as possible, deny every possible permission it is possible to deny, and never use your phone for sensitive work.
Your other option is to look into linux phones, which are out there, but don't have the same kind of app ecosystem or broad support as ios or android.
And the thing that I really think everyone should do that nobody actually likes hearing is to stop using your phone as anything but a phone. They can't track your data if you don't use it. I recognize that people need phones now in a way they didn't in the past (2fa is a huge part of this; people are either using SMS or apps to verify and that means it's not as easily dismissed as a necessity as it was 10 years ago) but there's a huge part of me that's like "I want to replace my smartphone with a jitterbug."
If you can't actually replace your smartphone with a jitterbug you can at least pretend that it isn't anything but a phone with a few limited extra tools.
(Also this is my "the boomers are right about..." thing: everyone should uninstall navigation applications and go back to reading maps and pre-planning their route to their destination)
1K notes
·
View notes
Note
Would it possible at all for you to point me in the direction of how to translate elder futhark runes ie: “Thor, Protector of Humanity”. I’m entertaining the idea of woodburning Norse art.
lol you're gonna hate this. Nobody asks me shit like this anymore so I'm gonna take it too seriously.
Really the answer is "no." I can try to do it for you but I don't think it makes sense for me to say "learn Proto-Norse" and hope for the best. Learning how to do this is a lot more difficult than learning Old Norse or Old English (and tbh "learn ON or OE or OHG" is the actual advice I'd give here). I know you're asking about doing this in general, and not for that phrase in particular, but you happened to provide a good example so I'm going to try a translation and show all my work.
I did put together a very non-exhaustive list of sources on runes available here but honestly that will not get you far here. Turning Proto-Norse into runes is easy, it's the language part that's hard. I also made a big list of deity names in Elder Futhark. Apparently the font embedding broke so it looks like nonsense, and I'm not gonna fight with it now. But the bolded text in each entry can be transliterated into runes. I haven't looked at this in years, but did just update Thor to be more in line with what I have here. Also, don't trust Wikipedia or Wiktionary for this stuff, you can use them as a research tool but verify independently or just use them to find other sources.
If I were in your position, I would consider using Old Norse and the runes that wrote that. Völuspá even gives us a near parallel: Miðgarðs véurr, and one of many ways to write that might be ���ᚢᚱ ᛬ ᛘᛁᚦᚴᛆᚱᚦᛋ ᛬ ᚢᛁᚢᚱ.
I should make sure sure you're asking what you want to be asking. I'm assuming you want to translate into language that was spoken when the Elder Futhark was used. Some people say "translate" when they mean the less-commonly-known-but-more-accurate "transliterate" (turn "abc" into "ᚨᛒᚲ"). Maybe you just want to go ᚦᛟᚱ ᛬ ᛈᚱᛟᛏᛖᚲᛏᛟᚱ ᛬ ᛟᚠ ᛬ ᚺᚢᛗᚨᚾᛁᛏᛁ and call it a day, and there's nothing wrong with that but you don't need my help for it so I'm guessing that isn't what you mean.
Anyway I'll give you my crack at a translation of the phrase you provided now in case you don't want to read the rest of this but the explanation is after the break:
*þonaraʀ warjaʀ *man(n)akunjas þonaraʀ warijaʀ manakunjas ᚦᛟᚾᚨᚱᚨᛉ ᛬ ᚹᚨᚱᛁᛃᚨᛉ ᛬ ᛗᚨᚾᚨᚲᚢᚾᛃᚨᛊ
(the i ~ ij thing is on purpose. word boundary markers optional)
Thor
There are some unclear phonological aspects of *þun?raz > Þórr. Haukur Þorgeirsson recently addressed this (this article is currently paywalled but for some reason the whole thing loaded just fine for me a few hours ago, not sure why), and I find his conclusions satisfactory, which complicates things. Haukur proposes an earlier *Þunurr but doesn't rule out *Þonarr (or earlier reflex of these). By Haukur's analysis the former is easier to resolve within Old Norse but the latter is more convenient with some other proposals already made, especially by comparative linguists. So we find ourselves with two proposals for the god's name in Elder Futhark-era language: ᚦᚢᚾᚢᚱᚨᛉ *þunuraʀ and ᚦᛟᚾᚨᚱᚨᛉ *þonaraʀ. I'm conditioned to favor *þonaraʀ, but I can't find fault in Haukur's preference for *þunuraʀ within the context of his own paper.
The only reason I'm not siding with it is that it seems impossible to resolve with Old High German donar and Old Saxon thunar (both 'thunder'; compare *eburaz > OHG/OS ebur, not **ebar). So while Haukur's got me convinced that *þunuraʀ seems like a more likely immediate precursor to Þórr, I can't shake *þonaraʀ being what seems to me, at least for now, a necessary precursor to the OHG especially. And for now, "seems necessary" beats "more likely." Of course variation is possible but that isn't a way to handwave conflicting data, it's a whole separate thing to investigate, and I haven't done that yet.
If I were researching something for myself, or for something permanent like a tattoo, I'd keep going and make sure I'm more confident. Even Haukur leaves open possibilities I haven't mentioned here. If nothing else, at least *þunraz no longer seems necessary to maintain (as Ringe 2014 thought following Noreen 1923).
Alternatively, one who does prefer *þunraz as the Proto-Germanic could probably be convinced to allow an epenthetic vowel for Elder Futhark-era language, so we're safe there.
I probably could have left all this out. *þonaraʀ is a fairly normal, mainstream way to reconstruct Þórr. But that wouldn't have been an accurate depiction of the situation. However we work this out, it highlights that what we're doing is not speaking/writing ancient, dead, unattested language. Or, if we are, it's only incidental to the primary thing we're doing, which is trying and sometimes failing to understand how attested words relate to each other, and taking sides in arguments about that.
protector
Selecting a word for 'protector' is difficult. It was only with some hesitation that I went with warjaʀ, a word only attested in compounded personal names like Landawar(i)jaʀ on the Tørvika A stone. It's highly likely to be derived from *warjan- 'to protect/defend.' What's a little weird, though, is that it seems to always be written warijaʀ, in apparent violation of Sievers' Law. I won't get into details here because this post is gonna be long enough as it is, but let it be known the word (and others -- the (i)ja thing recurs a bunch in the Elder corpus) is controversial and my preference for leaving it as it's attested would probably not be universal.
Snorri calls Thor verjandi Ásgarðs, Miðgarðs 'protector of Ásgarðr, Miðgarðr.' To be honest, this isn't the most common use of verjandi; usually it means 'defendant' in a trial, but we can get its meaning from context. We should stop to question whether it could have been used that way some 700 years before Snorri, and once we're satisfied that we can use it we run into trouble again with the non-phonological change of the suffix *-andz > -andi. The *-andz suffix is poorly attested in the Elder Futhark. We have the Tune stone's witada witanda-, but it's a compound word and doesn't give us the nominative ending. Then there's the Eggja stone's suwimąde swimmande and gąląnde galandi which are late enough to be basically fully Old Norse, and doesn't tell us much about earlier language. In Old Norse, these -andi words have the same endings as an n-stem in the singular, and maybe they did in Proto-Norse, but we don't have nominative (or even uncompounded in any case) forms from early enough to be sure. *warjandʀ or *warjanda? Or something else? If not for this, it's the word I'd probably use, and if we want to come as close as we can to technical dictionary accuracy, we'll have to be okay with a shot in the dark at the morphological state of the language.
Also derived from verja are vernd, verndari, vǫrn, vǫrðr. Both vernd and vǫrn mean roughly 'protection' and it makes more sense to say that Thor gives or provides them than that he is them. A vǫrðr is a guard or warden -- Heimdallr is definitely a vǫrðr but I'm not certain Thor is. Most likely, verndari is a later, Norse-era formation, which is unfortunate because it is the word I'd use if we were translating to Old Norse (might go a little bit something like ᚦᚢᚱ ᛬ ᚢᛆᚱ(ᚿ)ᛐᛆᚱᛁ ᛬ ᛘᚭᚿᚴᚢ(ᚿ)ᛋ).
In Old Norse there's also gæta. It isn't attested outside of North Germanic which means relying on internal reconstruction, which isn't great. Kroonen's (2013) *ganhatjan- makes sense and PN *gą̄tijaʀ does seem pretty reasonable as a reconstruction. Semantically, I'm not sure if it's a good fit, though I'm having trouble articulating why. Its meaning should be something like 'to watch, tend, take care of' and in most modern language is more like what Iðunn does with her apples, or what a shepherd does with their flock, than what Thor does with humans, but I don't know that we can be so precise with Proto-Norse and in either case I don't think it's wrong. Actually, perhaps gætir Miðgarðs would be a better way to put it (hint: gætir Miðgarðs < *gą̄tijaʀ miðjagarðas ᚷᚨᛏᛁᛃᚨᛉ ᛬ ᛗᛁᛞᛃᚨᚷᚨᚱᛞᚨᛊ).
The Norse word hlífa might be closer to what we're looking for, though it might only seem that way because we have little evidence to contradict it. In Norse it means 'to protect/defend/shelter (from something)' and works here, but its attestations in other Germanic languages are a little weak and don't inspire confidence in the semantics.
Given all this, I can't help but feel it's best to return to war(i)jaʀ. Though unattested outside of names, it presumably had an independent existence at some point, and is transparently derived from the verb *warjan- 'to defend.' And maybe most importantly, it is actual, attested language. This is a rare opportunity to forget about what I said at the end of the "Thor" section and connect to real language committed to real record by real people.
As an aside, véurr, mentioned way above, is probably etymologically equivalent to vé + warjaʀ, so *wīhawarjaʀ ᚹᛁᚺᚨᚹᚨᚱᛁᛃᚨᛉ.
humanity
We catch a break with 'humanity.' There are complications but they won't end up mattering. There are a few ways to say 'humanity' but they all start man(n)-; we can have our pick of -kin or -kind to end it but -kin is more common, which in PN is *kunja. But the 'man' words in early Germanic languages are a little weird. Sometimes it has one n, sometimes two; it's always two in Old Norse, but it's hard to say if that was true in elder runic language. Fortunately we can sidestep this: in most runes you only write a letter once, even if the sound is long. But to use a connecting vowel or not? Gothic has compounds in mana-, manna-, man-, and mann-. So *man(n)akunja or *man(n)kunja? Well, as Martin Syrett (1994) pounds out, Germanic in general and Gothic in particular are not consistent when it comes to stem vowels in compounds. There's a tendency to spread -a- as a connecting vowel even where it doesn't belong. So we should feel pretty safe that even if *man(n)akunja isn't the inherited form from Proto-Germanic, it was always a possibility. Finally, worst comes to worst, you could just let ᛗ stand for the whole word, given that it's the 'man' rune anyway.
Last, we'll have to put that in the genitive case to make it 'of mankind.' We don't have examples of neuter ja-stems in the genitive from the Elder Futhark but there isn't really strong reason to believe it wasn't *-jas, so: *kunjas.
We've arrived at my answer:
*þonaraʀ warjaʀ *man(n)akunjas þonaraʀ warijaʀ manakunjas ᚦᛟᚾᚨᚱᚨᛉ ᛬ ᚹᚨᚱᛁᛃᚨᛉ ᛬ ᛗᚨᚾᚨᚲᚢᚾᛃᚨᛊ
Anyway I hope you don't mind me going completely over the top answering this, I don't think I realized before starting to answer this that I needed to get it out of my system.
36 notes
·
View notes
Text
The Death of Physical Media
I keep seeing this concern around all of my home theater circles. Ever since Best Buy decided to abandon physical media there has been a call to arms to save it.
Chris Stuckman did a great video on his love of physical media.
youtube
I admire and share his passion.
That said, I think there is nothing to stop physical media from being scaled back. At best, it will end up like vinyl and only a few select titles will still be pressed.
Which is why I think saving physical media is the wrong fight.
There is a much larger fight that encompasses more than just blu-ray discs...
(I'm going to use really big letters for dramatic effect so don't get startled.)
DATA OWNERSHIP!
(Imagine a long trailing echo when reading that in your mind.)
(Sorry, I probably should have included those instructions in the previous parenthetical. So go back and read "data ownership" again with the proper gusto.)
(Did you do it?)
(Was it cool?)
(Cool.)
A blu-ray is just data.
The disc does not positively affect the visuals or the sounds. It's just 1s and 0s coded into microscopic pits. You can put that data on a hard drive. You can put it on an SD Card. You can put it on a thumb drive and wear it on a necklace.
You can even use WinRAR to break it up into little 1.44 megabyte chunks and save it to floppy disks.

Another 40 more cases of floppies and you've got Avatar preserved for life!
The medium is not important.
The *data* is important.
And as everything turns into a subscription we are losing out on ways to own data. Beyond that, people aren't yet seeing the value of owning data. If renting a digital download is cheaper, they are almost always going to choose that option.
So the fight is two-fold.
We need to fight for the right to parrrrrty own data.
We need to convince the populace of the value of owning data.
This can apply to software, movies, video games. Hell, I don't even own my damn doorbell videos. There is no way to download all of the footage. I'd have to do each video one at a time. And if I don't keep my subscription, I will no longer have access to that data as it will soon be deleted.
We would need a platform similar to Steam—though it isn't the perfect data ownership solution. Many titles require internet connectivity and DRM verification. What happens to our media when a company goes out of business and the infrastructure to verify the DRM over the internet is gone?
So that would need to be addressed. Perhaps a new form of DRM linked to our digital identity that can be verified locally.
I mean, I'd love to get rid of DRM, but that is probably not realistic.
I think the best avenue is probably a congressional law.
"The Own Your Own Data Act"
TOYODA?
We can workshop the name later.
In conclusion, we don't need to save blu-rays. We need the option to buy data and actually own it in perpetuity.
Meaning if a streaming service deletes a movie or a movie studio goes belly up, our data doesn't disintegrate along with it. We cannot let our favorite shows go extinct. We need to be part of preserving that history. Not to mention discs have a shelf life. But data can be transferred to new mediums indefinitely.
My house is just going to be wall to wall floppy disks.
158 notes
·
View notes