#php monitor
Explore tagged Tumblr posts
Text
Mastering PHP Application Monitoring: Best Practices for 2025

Introduction
PHP powers over 75% of the web today, making it one of the most widely used server-side languages. From WordPress sites to complex Laravel applications, developers rely on PHP to build fast, scalable solutions. But with growing complexity comes the need for real-time visibility and control. This is where application monitoring plays a critical role.
Monitoring isn't just about tracking uptime, it's about understanding how your code behaves in production, identifying slow queries, spotting memory leaks, and proactively fixing issues before users even notice them. In this blog, we’ll explore the best practices for PHP application monitoring and how you can implement them effectively.
12 Best Practices for PHP Application Monitoring
1. Upgrade to PHP 8+
Running on the latest version ensures better performance, error handling, and compatibility with modern tools. PHP 8’s JIT compiler alone can improve execution speed significantly.
2. Follow PSR Coding Standards
Using standards like PSR-3 (logging) and PSR-4 (autoloading) leads to cleaner, more structured code that monitoring tools can process more efficiently.
3. Use Descriptive Functions and Logs
Functions like processData() aren’t helpful when debugging. Instead, use meaningful names like generateMonthlyReport() and ensure log messages are clear and contextual.
4. Leverage Popular Frameworks
Frameworks such as Laravel, Symfony, or CodeIgniter come with built-in structure and middleware support, which integrate smoothly with APM solutions.
5. Manage Dependencies with Composer
Locking versions through Composer ensures consistent environments across staging and production, reducing unexpected errors during deployment.
6. Add Caching Layers
Implement opcode, database, and object caching to reduce server load and accelerate response times.
7. Set Up Smart Alerts
Avoid alert fatigue. Configure alerts for thresholds that truly matter like a sustained increase in response time or sudden spike in 500 errors.
8. Conduct Security Monitoring
Monitor failed login attempts, suspicious user behavior, or error messages that might indicate vulnerabilities.
9. Use CI/CD Tags for Deployments
Tagging releases helps correlate performance changes with specific deployments, making it easier to roll back or debug regressions.
10. Keep Monitoring Agents Updated
Regularly check for updates to ensure compatibility with your PHP version and frameworks.
11. Profile Real User Traffic
Use profiling tools in production to identify bottlenecks during peak usage not just in local or staging environments.
12. Optimize SQL Queries
Poorly indexed or long-running queries can slow down your app. APM tools can pinpoint these with exact timings and stack traces.
Why Choose Atatus for PHP Monitoring?
Atatus is a full-stack APM and error-tracking platform that offers deep insights into PHP applications. Here’s why it stands out:
Real-time performance monitoring for PHP 7.x and 8.x apps
Transaction tracing down to database queries, external calls, and slow functions
Easy integration with Laravel, Symfony, CodeIgniter, and other frameworks
Custom alerting, dashboards, and logs in one unified interface
Error tracking with stack traces and user context to speed up debugging
Atatus helps developers detect issues early, optimize code paths, and ensure smooth performance at scale.
Conclusion
Effective monitoring is key to building fast, stable, and scalable PHP applications. By following these best practices and choosing the right tool like Atatus, you can gain full visibility into your app's performance, reduce downtime, and deliver a seamless user experience.
Whether you're managing a startup project or an enterprise-grade application, observability isn't optional, it's essential. Implementing a strong monitoring strategy today will lead to fewer production issues, faster debugging, and more confident development tomorrow.
Originally published by https://www.atatus.com/
#php monitoring#php monitoring best practices#What is PHP Monitoring#php applications#PHP Application Monitoring#PHP apm#php application performance monitoring tools#php monitoring solution#php application monitoring tools#php application performance#php performance monitoring tool#php monitoring tools#php performance monitor#php monitor#apm for php#php apm monitoring#php monitoring tool#php monitoring software#monitor php application performance#apm php#php application monitoring tool#php application performance mangement#monitoring php performance#php app monitoring#php distributed tracing
0 notes
Text
Out of Memory OOM Killer issue Investigation
Wednesday morning our monitoring solution suddenly alerted me to a critical issue with our main web server. Attempting to access our WordPress website via browser returned database connection errors, indicating a problem with our hosting environment. When I logged into the server via SSH, I discovered it’s a Linux Out of Memory (OOM) Killer terminating our MariaDB database service due to memory…
#Linux server#MariaDB optimisation#memory management#OOM Killer#Out of Memory#performance tuning#PHP-FPM configuration#server administration#swap space#system monitoring#WordPress hosting
0 notes
Text
Fixing Insufficient Logging and Monitoring in Laravel
Insufficient logging and monitoring is a common vulnerability that can lead to missed or delayed detection of security incidents in web applications. In this blog, we’ll explore how Laravel developers can mitigate this issue with practical coding examples and introduce a free Website Security checker tool to evaluate your website's vulnerabilities.

What is Insufficient Logging and Monitoring?
Insufficient logging and monitoring occur when an application fails to:
Record critical events like authentication attempts, permission changes, or system errors.
Generate alerts for unusual activities.
Monitor logs for anomalies or breaches.
Without proper logging and monitoring, organizations may remain unaware of attacks, compromising their ability to respond to and mitigate potential damage.
Impact of Insufficient Logging and Monitoring
Delayed Incident Response: Attack detection is slower, giving attackers more time to exploit vulnerabilities.
Compliance Issues: Many regulations (e.g., GDPR, HIPAA) mandate robust monitoring systems.
Reputation Damage: Customers lose trust after unreported breaches.
How Laravel Handles Logging
Laravel uses the powerful Monolog library for logging, supporting multiple log handlers such as files, databases, or external tools like Slack. Laravel’s configuration files for logging are stored in:
config/logging.php
Steps to Mitigate Insufficient Logging and Monitoring
Enable Detailed Logging Configure logging levels based on your environment. Laravel supports levels like debug, info, notice, warning, error, etc. Example: Setting Up Logging in Laravel In the config/logging.php file:
return [ 'default' => env('LOG_CHANNEL', 'stack'), 'channels' => [ 'stack' => [ 'driver' => 'stack', 'channels' => ['daily'], ], 'daily' => [ 'driver' => 'daily', 'path' => storage_path('logs/laravel.log'), 'level' => 'debug', // Adjust as needed 'days' => 14, ], ], ];
This setup logs events daily and retains logs for 14 days.
Log Critical Events Ensure important actions are logged. For example, log login attempts and failed logins:
use Illuminate\Support\Facades\Log; // Successful Login Log::info('User logged in', ['user_id' => auth()->id()]); // Failed Login Log::warning('Failed login attempt', ['email' => request('email')]);
Monitor Logs and Generate Alerts Use tools like Laravel Telescope to monitor logs. Install Telescope via Composer:
composer require laravel/telescope
Publish its assets:
php artisan telescope:install php artisan migrate
Enable Telescope in production by modifying the telescope.php configuration file.
Using Free Tools for Security Checks
To ensure your Laravel application’s logging and monitoring setup is effective, it’s crucial to identify potential vulnerabilities. Our Website Security Scanner can help.

Screenshot of the free tools webpage where you can access security assessment tools.
Real-World Example: Logging Suspicious Activity
Here’s how to log suspicious activity in Laravel:
use Illuminate\Support\Facades\Log; // Log suspicious activity function detectSuspiciousActivity($user) { if ($user->login_attempts > 5) { Log::alert('Suspicious login activity detected', [ 'user_id' => $user->id, 'email' => $user->email, ]); } }
Sample Vulnerability Report
Using our tool, you can generate a detailed vulnerability assessment report, highlighting areas like insufficient logging.

An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion
Insufficient logging and monitoring are critical vulnerabilities that developers must address to ensure their Laravel applications remain secure. By implementing proper logging, monitoring logs, and using tools like Laravel Telescope, you can mitigate risks effectively.
Don’t wait—try our free Website Security Checker tool today to identify vulnerabilities in your application and improve your security posture!
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#logging#monitoring#sql
1 note
·
View note
Text
PHP Mail Açılıp Açılmadığını Kontrol Etmek
Merhabalar, bu yazımda PHP Mail Açılıp Açılmadığını Kontrol Etmek işlemini yani PHP ile bir gönderdiğimiz bir mail adresinin, gönderdiğimiz kişi tarafından açılıp açılmadığını nasıl kontrol edeceğimizi belirleyeceğiz. PHP Mail Açılıp Açılmadığını Kontrol Etmek Bazen sistemlerimiz üzerinden toplu mailler atarız ve mail gönderdiğimiz kişilerin bu mailleri açıp açmadığını merak ederiz. Hatta bazı…

View On WordPress
#campaign-monitor#Mail Açılma Durumu Kontrol Etmek#mass-emails#PHP#PHP Mail Açılıp Açılmadığını Kontrol Etmek
0 notes
Text
Quando ero giù, insieme a tanti album di fotografie mie e vecchi libri, ho trovato questo cimelio, ancora funzionante

E' stato un tuffo nei ricordi perché correva l'anno sotto al 2000 ed è stato il mio primo esperimento di Grande Fratello, quando ancora Grande Fratello non esisteva.
In pratica io avevo la mia base di computer nella mansarda di casa, dove la Mami mi aveva rinchiuso nella speranza che i topi divorassero me e l'elettronica che mi circondava. All'epoca iniziai a giocare un po' con siti web, PHP, phpNuke (che ancora esiste!), e praticamente la macchina Linux scattava foto alla mansarda tipo una al minuto, se non ricordo male, e metteva tale foto sulla home page del mio sito web, insieme a tante altre cagate, quindi chiunque poteva visitare il mio sito e vedere che cazz stavo facendo (i miei amici dell'Uni si divertivano a fare screenshot delle mie pose più compromettenti), e più volte la webcam mi beccò che mi stavo grattando i gioielli, o che uscissi dal bagno e in quel momento mi chiudevo la zip dei pantaloni, o che stessi bestemmiando al monitor, insomma per questa cosa mio fratello mio odiò alla grande e puntualmente sabotava il sistema, il maledetto. Il bello del gioco è che io dovevo scordarmi che questa webcam esisteva, e fare in modo come se non ci fosse, e la cosa mi riusciva benissimo.
Beh, oh, collegata alla mia Slackware, ancora funziona!
#però mo' lo streaming non è più pubblico#quindi raffreddate gli ormoni#anche perché all'epoca ero un figaccio#mo' nun è cos#i nudi ve li posso mandare solo su richiesta esplicita previo stipula di una polizza assicurativa per danni verso terzi
23 notes
·
View notes
Text



My cat is currently admitted at the vet for a viral infection. I will need at least 10k php to cover the cost. My commissions are currently open to pay for the bills. I accept payment through GCash, Maya, PayPal, bank transfer, and remittance.
My cat’s name is Cammie, and she’s a 4yo rescue. I have 11 other cats that I am currently monitoring in case they are also sick.
#digital art#illustration#procreate#autistic artist#furry#furry art#oc#sfw furry#anthro#cat anthro#emergency commissions#commission#open commissions#emergency
26 notes
·
View notes
Text

The AN330 Anesthesia Machine features a 12.1" TFT LCD touch screen displaying ventilation parameters, alarms, and waveforms, along with dual control via an alternate button and both high-precision electronic and mechanical flowmeters for accurate monitoring of fresh gas flow to the patient. https://www.narang.com/anaesthesia-equipments-products/anesthesia-machine/AN330.php
2 notes
·
View notes
Text
The still waters of Yambo Lake that reflects the beauty around it

a blog on Yambo Lake’s various information, history, & how it benefits the locals of Nagcarlan

Yambo lake was said to be the twin crater of Pandin lake that is also part of the seven lakes in San Pablo, Laguna. A serene, oligotrophic crater lake between Nagcarlan and San Pablo City. It is known for its clear waters, lush surroundings, and being suitable for swimming, outings, and picnics.

If you’re from Liliw, you can ride a jeep with a signboard saying “San. Pablo”. Then after you arrive at Nagcarlan, you can ride a tricycle to Yambo Lake. The transportation fee would cost around 50 PHP and above depending on the number of passengers.

HOW IS IT FORMED?
Yambo Lake, along with the other Seven Lakes, are volcanic crater lakes that was formed from phreatomagmatic eruption that blew out rocks that was filled with rainwater.
ACCORDING TO A LOCAL LEGEND
Yambo & Pandin were a pair of lovers, and the lakes are named after them. Pandin, a beautiful woman who was cursed to not set foot on earth. Meanwhile, Yambo, Pandin’s lover, was unaware of Pandin’s curse and made her step on the ground. This made a terrible noise, cracking the earth that transformed the area into twin lakes separated by a narrow strip of land.

There are many activies that you can do at Yambo Lake, this includes;
swimming
outings
picnics
bamboo rafting

TO THE LOCALS
Yambo Lake is very helpful to locals, especially when it comes to their source of income. It is also a good source of income that can also promote the attraction.
TO THE ECOSYSTEM
Yambo Lake may be developed into an ecotourism area in San Pablo City. However, measures must be undertaken to prevent the direct discharge of wastes into the lake. A Development Plan for Yambo Lake should be established in coordination with all the stakeholders. Although most parameters are still way below the criteria, efforts to continually preserve the water quality of the lake must continue. Maintaining the good water quality of the lake does not only depend on agencies like LLDA which monitor the area but also lies in the hands of the community that directly benefits from it.
˗ˏˋ ꒰ ♡ ꒱ ˎˊ˗
Here are some other photos that we took from Yambo Lake :)




2 notes
·
View notes
Text
Atlantic Tropical Weather Outlook issued by the National Hurricane Center in Miami, FL, USA
2024-06-28, 08:00 EDT
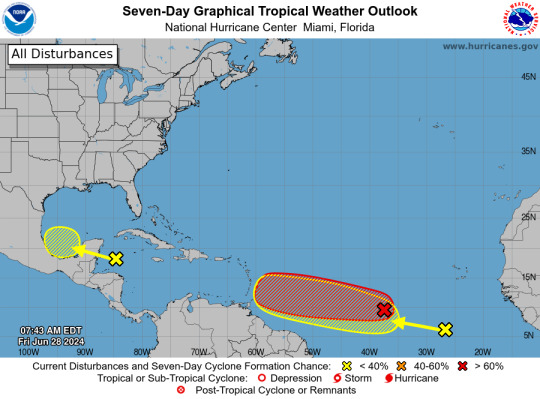
Western Caribbean/Southwestern Gulf of Mexico (AL94): A broad area of low pressure over the western Caribbean Sea associated with a tropical wave continues to produce widespread shower and thunderstorm activity. Development of this system is not expected today while it moves west-northwestward at around 15 mph, and an Air Force reconnaissance mission planned for today has been canceled. The disturbance is then expected to move westward over the Yucatan Peninsula and emerge over the Bay of Campeche late Saturday or early Sunday, at which point some development will be possible. Regardless of development, heavy rainfall associated with the tropical wave will affect portions of Central America and Mexico through the weekend.
* Formation chance through 48 hours...low...30 percent.
* Formation chance through 7 days...low...30 percent.
Central Tropical Atlantic (AL95): A low pressure system located about 1500 miles east-southeast of the Windward Islands is gradually becoming better defined. Showers and thunderstorms are also showing signs of organization, and a tropical depression or tropical storm will likely form later today or on Saturday. This system is expected to move westward at 15 to 20 mph and approach the Lesser Antilles by the end of the weekend. Interests there should monitor the progress of this system. For more information, including gale warnings, see High Seas Forecasts issued by the National Weather Service.
* Formation chance through 48 hours...high...90 percent.
* Formation chance through 7 days...high...90 percent.
Eastern Tropical Atlantic: A tropical wave centered several hundred miles south-southwest of the Cabo Verde Islands is producing disorganized showers and thunderstorms. Some slow development of this system is possible next week while it moves generally westward across the central and western tropical Atlantic at 15 to 20 mph.
* Formation chance through 48 hours...low...near 0 percent.
* Formation chance through 7 days...low...20 percent.
&& High Seas Forecasts issued by the National Weather Service can be found under AWIPS header NFDHSFAT1, WMO header FZNT01 KWBC, and online at ocean.weather.gov/shtml/NFDHSFAT1.php
$$ Forecaster Cangialosi/Zelinsky
#bot post#meteorology#weather#tropical weather#tropical storm#tropical depression#hurricane#atlantic#atlantic ocean#caribbean#gulf of mexico#noaa#national oceanic and atmospheric administration#nhc#national hurricane center
6 notes
·
View notes
Text
New Dominator has arrived 🤩

The Production I.G store will release the new Dominator model in collaboration with TANITA, for the voice body composition meter.
TANITA is the worldwide leading brand of medical scales bases in Japan.
This new model contains newly recorded audio of Dominator (CV: Noriko Hidaka) from "PSYCHO-PASS". In addition to reading out the Crime-Coefficient, it changes to execution mode when the standard value is exceeded. Don't miss out on this special body composition monitor that manages your health.
GET THE DETAILS HERE ⏬
https://psycho-pass.com/news/20231219_01.php
Reservations will begin by 2023/12/22 (Friday) 18:00PM.
16 notes
·
View notes
Text
Finding a Good Web Developer in Stamford
In today’s digital age, having a strong online presence is crucial for businesses of all sizes. Whether you're a startup or an established enterprise, hiring a skilled web developer can significantly impact your success. If you're located in Stamford and looking to enhance your website or create a new one, here are some essential tips to help you find the right web developer for your needs
Define Your Project Requirements Before you start your search, it's important to have a clear understanding of what you need. Are you looking for a simple informational website, a complex e-commerce platform, or a custom web application? Defining your project requirements will help you communicate effectively with potential developers and ensure you find someone with the right expertise
Look for Local Talent Stamford has a vibrant tech community, making it easier to find local web developers. Consider attending local meetups, tech events, or networking gatherings to connect with professionals in the area. This not only helps you find potential candidates but also allows you to gauge their skills and expertise through personal interactions
Check Portfolios and Previous Work A web developer’s portfolio is a crucial indicator of their skills and style. Look for developers who have experience in your industry or who have worked on projects similar to yours. Reviewing their previous work can give you insights into their creativity, technical abilities, and overall quality of work
Read Reviews and Testimonials Don’t just take a developer's word for it—check online reviews and testimonials from previous clients. Platforms like Google, Clutch, or even social media can provide valuable feedback about a developer's reliability, communication skills, and project management capabilities. Look for developers who have consistently positive reviews and a solid reputation in the Stamford community
Evaluate Technical Skills Web development encompasses a range of skills, from front-end design to back-end programming. Depending on your project, you may need a developer who is proficient in specific technologies such as HTML, CSS, JavaScript, PHP, or frameworks like React or Angular. Ensure that the developers you consider have the technical skills necessary to meet your project requirements
Communication is Key A successful web development project relies heavily on clear communication. During initial discussions, pay attention to how well the developer listens to your ideas and concerns. A good developer should be able to explain technical concepts in a way that you can understand and should be open to feedback throughout the development process
Discuss Budget and Timelines Before committing to a developer, discuss your budget and project timelines upfront. Be honest about what you can afford and ask for a detailed breakdown of costs. Additionally, establish clear deadlines to ensure that the project stays on track. A reputable developer will provide you with a realistic timeline and work within your budget
Consider Ongoing Support Web development doesn’t end once your site goes live. Look for developers who offer ongoing support and maintenance services. This can include regular updates, bug fixes, and security monitoring. Having a reliable developer available for future needs can save you time and stress down the line Conclusion Finding a good web designer in Stamford or a web designer in Rutland requires careful consideration and research. By defining your project needs, exploring local talent, reviewing portfolios, and ensuring effective communication, you can find a developer who aligns with your vision and goals. Investing time in this process will pay off, resulting in a high-quality website that effectively represents your brand and engages your audience.
#digital marketing#online business#web development#google ads#wordpress#web design#web developers#website#website design#wordpress websites webdesign seo webdevelopment webcompany
2 notes
·
View notes
Text
PHP Monitoring vs Logging: What’s the Difference and Why It Matters
When it comes to managing and maintaining PHP applications, two terms often come up: monitoring and logging. While they may sound similar and sometimes even overlap, they serve very different purposes. Understanding the difference between PHP monitoring and logging is essential for debugging faster, improving performance, and ensuring a reliable user experience.
What is PHP Logging?
Logging is the practice of recording events that happen within your application. This might include errors, warnings, notices, or even custom-defined events.
Common Examples of Logging:
Syntax or runtime errors
Database connection failures
User login attempts
Payment failures
Debug information during development
Tools Often Used for Logging:
PHP’s error_log()
Monolog
Laravel’s built-in logger
Syslog or custom log files
Pros of Logging:
Helpful for debugging specific issues
Easy to implement
Provides a historical record of events
Cons of Logging:
Reactive, not proactive
Difficult to search and correlate events manually
Doesn’t provide context about system performance or user impact
What is PHP Monitoring?
Monitoring is the continuous observation of your application’s performance and behavior in real-time. It includes tracking metrics like response time, error rates, memory usage, and third-party dependencies.
Monitoring Covers:
Real-time application performance (APM)
Slow transactions
Database query performance
Uptime monitoring
Infrastructure health (CPU, memory, disk)
Popular Monitoring Tools for PHP:
Atatus
New Relic
Datadog
AppDynamics
Pros of Monitoring:
Proactive alerts before users are affected
End-to-end visibility into user transactions
Tracks trends and long-term performance
Correlates errors with user sessions or deployments
Cons of Monitoring:
Slight learning curve to configure dashboards and alerts
Typically involves third-party services
Why Does It Matters?
Both logging and monitoring are crucial but for different reasons.
Use logging to capture detailed technical errors and custom events for debugging.
Use monitoring to understand how your app is behaving right now, across all users, in real-time.
In fast-moving production environments, relying on logs alone isn’t enough. Logs might tell you what happened but monitoring tells you why it’s happening and helps prevent it from happening again.
Final Thoughts: Use Both, But Smarter
Logging and monitoring should complement each other. While logs give you granular context for debugging, monitoring provides the bird’s-eye view you need to stay ahead of issues.
That’s why full-stack solutions like Atatus bring PHP monitoring, error tracking, and log management into one platform giving you a single pane of glass to view, analyze, and act on issues quickly.
Stop guessing. Start monitoring. And keep logging smart!
#php performance monitoring#php application performance monitoring#php application performance monitoring tools#php monitoring tools#php application monitoring tools#php performance monitoring tool#php application performance mangement#php profiling tools#php monitoring tool#php performance#php application performance management#php application monitoring tool#php performance profiling#php performance tools#php application performance#php performance testing tool#monitoring php performance#php performance monitoring tools#monitor php application performance#monitor php performance#php monitoring#php application monitoring
0 notes
Text
This day in history

#20yrsago Promising anti-obesity pill https://web.archive.org/web/20040419011611/http://www.businessweek.com/technology/content/apr2004/tc2004048_9548_tc122.htm
#20yrsago NDP leader Jack Layton endorses P2P https://memex.craphound.com/2004/04/09/canadas-ndp-leader-endorses-p2p/
#20yrsago EFF on Gmail https://web.archive.org/web/20040420195950/https://blogs.eff.org/deeplinks/archives/001375.php#001375
#15yrsago Cold dead hand of Frank Herbert reaches up from grave, stabs Dune Second Life megafans in the back https://nwn.blogs.com/nwn/2009/04/enforcers-of-dune.html
#15yrsago French government nukes crazy Internet law in open revolt against Sarkozy https://www.theguardian.com/technology/2009/apr/09/france-illegal-downloads-state-surveillance
#10yrsago NSA spies on human rights groups, including those in the USA https://techcrunch.com/2014/04/08/snowden-council-of-europe-testimony/
#10yrsago Prosecutors wage war on judges who insist on fairness https://www.washingtonpost.com/news/the-watch/wp/2014/03/07/judge-says-prosecutors-should-follow-the-law-prosecutors-revolt/
#10yrsago LAPD officers sabotage their own voice-recorders: nothing to hide, nothing to fear? https://arstechnica.com/tech-policy/2014/04/lapd-officers-monkey-wrenched-cop-monitoring-gear-in-patrol-cars/
#5yrsago Today, Michigan regulators vote on conservative education “reform” plan to purge the word “democracy” from curriculum https://nymag.com/intelligencer/2019/04/michigan-conservatives-vie-to-cut-democracy-from-classroom.html
#5yrsago The Chinafication of the internet continues as the UK proposes blocking any service that hosts “illegal” or “harmful” material https://memex.craphound.com/2019/04/09/the-chinafication-of-the-internet-continues-as-the-uk-proposes-blocking-any-service-that-hosts-illegal-or-harmful-material/
#5yrsago How to Do Nothing: Jenny Odell’s case for resisting “The Attention Economy” https://memex.craphound.com/2019/04/09/how-to-do-nothing-jenny-odells-case-for-resisting-the-attention-economy/
#1yrsago How To Make a Child-Safe TikTok https://pluralistic.net/2023/04/09/how-to-make-a-child-safe-tiktok/
7 notes
·
View notes
Text
Exploring the Realm of cPanel Hosting in Australia: A Comprehensive Guide
In the vast digital landscape of Australia, where businesses thrive and online presence is paramount, finding the right hosting solution is akin to selecting a foundation for a skyscraper. In this digital age, where websites serve as the face of enterprises, the choice of hosting can significantly impact performance, user experience, and ultimately, the success of ventures. Among the plethora of options, cPanel hosting stands out as a popular choice for its user-friendly interface, robust features, and reliability. But what exactly is cPanel hosting, and why is it gaining traction among businesses in Australia?

Understanding cPanel Hosting
What is cPanel hosting?
cPanel hosting is a type of web hosting that utilizes the cPanel control panel, a web-based interface that simplifies website and server management tasks. It provides users with a graphical interface and automation tools, allowing them to effortlessly manage various aspects of their website, such as file management, email accounts, domain settings, databases, and more.
How does cPanel Hosting Work?
At its core, cPanel hosting operates on a Linux-based server environment, leveraging technologies like Apache, MySQL, and PHP (LAMP stack). The cPanel interface acts as a centralized hub, enabling users to perform administrative tasks through a user-friendly dashboard, accessible via any web browser.
Benefits of cPanel Hosting
User-Friendly Interface
One of the primary advantages of cPanel hosting is its intuitive interface, designed to accommodate users of all skill levels. With its graphical layout and straightforward navigation, even those with minimal technical expertise can manage their websites efficiently.
Comprehensive Feature Set
From creating email accounts to installing applications like WordPress and Magento, cPanel offers a wide array of features designed to streamline website management. Users can easily configure domains, set up security measures, and monitor website performance, and much more, all from within the cPanel dashboard.
Reliability and Stability
cPanel hosting is renowned for its stability and reliability, thanks to its robust architecture and frequent updates. With features like automated backups, server monitoring, and security enhancements, users can rest assured that their websites are in safe hands.
Scalability and Flexibility
Whether you're running a small blog or managing a large e-commerce platform, cPanel hosting can scale to meet your needs. With options for upgrading resources and adding additional features as your website grows, cPanel offers the flexibility required to adapt to evolving business requirements.
Choosing the Right cPanel Hosting Provider
Factors to Consider
When selecting a cPanel hosting provider in Australia, several factors should be taken into account to ensure optimal performance and reliability:
Server Location: Choose a provider with servers located in Australia to minimize latency and ensure fast loading times for local visitors.
Performance: Look for providers that offer high-performance hardware, SSD storage, and ample resources to support your website's needs.
Uptime Guarantee: Opt for providers with a proven track record of uptime, ideally offering a minimum uptime guarantee of 99.9%.
Customer Support: Evaluate the level of customer support offered, ensuring prompt assistance in case of technical issues or inquiries.
Conclusion
In conclusion, cPanel hosting serves as a cornerstone for businesses seeking reliable and user-friendly cpanel hosting Australia. With its intuitive interface, comprehensive feature set, and robust architecture, cPanel empowers users to manage their websites with ease, allowing them to focus on their core business objectives.
2 notes
·
View notes
Text
Journey to Devops
The concept of “DevOps” has been gaining traction in the IT sector for a couple of years. It involves promoting teamwork and interaction, between software developers and IT operations groups to enhance the speed and reliability of software delivery. This strategy has become widely accepted as companies strive to provide software to meet customer needs and maintain an edge, in the industry. In this article we will explore the elements of becoming a DevOps Engineer.
Step 1: Get familiar with the basics of Software Development and IT Operations:
In order to pursue a career as a DevOps Engineer it is crucial to possess a grasp of software development and IT operations. Familiarity with programming languages like Python, Java, Ruby or PHP is essential. Additionally, having knowledge about operating systems, databases and networking is vital.
Step 2: Learn the principles of DevOps:
It is crucial to comprehend and apply the principles of DevOps. Automation, continuous integration, continuous deployment and continuous monitoring are aspects that need to be understood and implemented. It is vital to learn how these principles function and how to carry them out efficiently.
Step 3: Familiarize yourself with the DevOps toolchain:
Git: Git, a distributed version control system is extensively utilized by DevOps teams, for code repository management. It aids in monitoring code alterations facilitating collaboration, among team members and preserving a record of modifications made to the codebase.
Ansible: Ansible is an open source tool used for managing configurations deploying applications and automating tasks. It simplifies infrastructure management. Saves time when performing tasks.
Docker: Docker, on the other hand is a platform for containerization that allows DevOps engineers to bundle applications and dependencies into containers. This ensures consistency and compatibility across environments from development, to production.
Kubernetes: Kubernetes is an open-source container orchestration platform that helps manage and scale containers. It helps automate the deployment, scaling, and management of applications and micro-services.
Jenkins: Jenkins is an open-source automation server that helps automate the process of building, testing, and deploying software. It helps to automate repetitive tasks and improve the speed and efficiency of the software delivery process.
Nagios: Nagios is an open-source monitoring tool that helps us monitor the health and performance of our IT infrastructure. It also helps us to identify and resolve issues in real-time and ensure the high availability and reliability of IT systems as well.
Terraform: Terraform is an infrastructure as code (IAC) tool that helps manage and provision IT infrastructure. It helps us automate the process of provisioning and configuring IT resources and ensures consistency between development and production environments.
Step 4: Gain practical experience:
The best way to gain practical experience is by working on real projects and bootcamps. You can start by contributing to open-source projects or participating in coding challenges and hackathons. You can also attend workshops and online courses to improve your skills.
Step 5: Get certified:
Getting certified in DevOps can help you stand out from the crowd and showcase your expertise to various people. Some of the most popular certifications are:
Certified Kubernetes Administrator (CKA)
AWS Certified DevOps Engineer
Microsoft Certified: Azure DevOps Engineer Expert
AWS Certified Cloud Practitioner
Step 6: Build a strong professional network:
Networking is one of the most important parts of becoming a DevOps Engineer. You can join online communities, attend conferences, join webinars and connect with other professionals in the field. This will help you stay up-to-date with the latest developments and also help you find job opportunities and success.
Conclusion:
You can start your journey towards a successful career in DevOps. The most important thing is to be passionate about your work and continuously learn and improve your skills. With the right skills, experience, and network, you can achieve great success in this field and earn valuable experience.
2 notes
·
View notes
Text
Gophish Setup Guide: Launching Phishing Campaigns
Phishing Scenario : CASE 1 - Breaking news
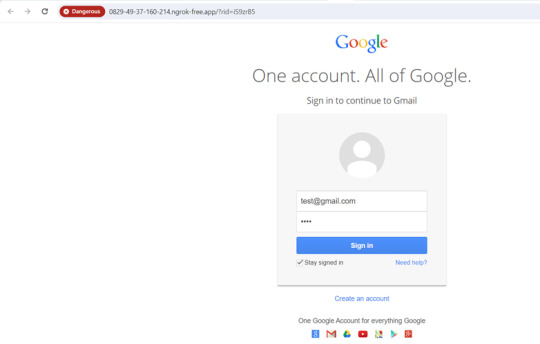
Objective: The objective of this phishing campaign is to lure employees into clicking a malicious link disguised as breaking news from the company. The landing page masqueraded as a Gmail sign-in page, prompting users to enter their login credentials. This page was designed to steal users' email account credentials.
Install Gophish framework
Make the required changes in the config.json file
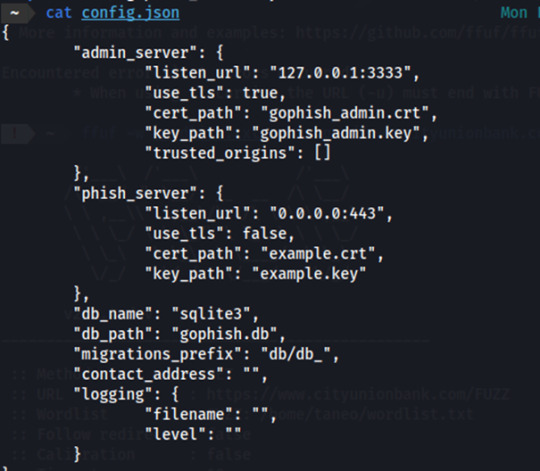
Launch Gophish and our first step would be to set up the sending profile by which we will send out phishing emails.
Let’s assume that the target company is using Gmail server
(When setting up the sending profile in Gophish using a Gmail account, you have to enable 2FA and give app access to Gophish)
Since our target company is using Gmail server, we will use Gmail email on our phishing campaign so we have set host as smtp.gmail.com:587. After creating the sending profile, we have to test if the sending profile works by sending a test email.
We're using the email address [email protected] as our designated Gmail account for sending phishing emails. Make sure to include the password that was generated when granting Gophish access to this Gmail account. After configuring the sending profile, we can test it by sending a test mail.

This is what the test mail will look like:

Email Template
The next step involves integrating an email template for the phishing campaign. We can opt for a pre-made template, for example, here we use a Breaking News email template, for initial testing. We can incorporate a tracking image within the emails to monitor various engagement metrics, including email opens, clicks, and receipt statuses. It also has an option where we can add a link which will redirect the victim to the landing page. On the landing page we can proceed to request for more valuable information from the user.

Landing Page
In the third step, set up a landing page where targets will be directed after clicking a link in the email. This landing page plays a crucial role in the phishing campaign, as it's where you can capture sensitive information like passwords. Gophish defaults to using http://0.0.0.0:80 for the landing page, but we can customize it to look like a legitimate login page or other enticing content to attract targets. We'll need to specify a redirect page where users will be sent after submitting their credentials.
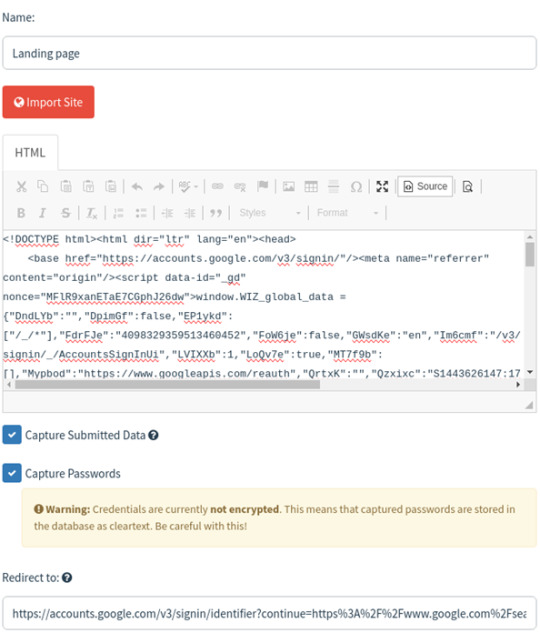
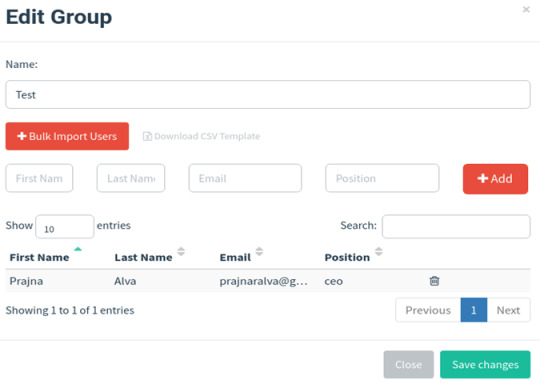
In the User & Groups section, you'll need to input the email addresses of your targets. Gophish framework requires you to provide the first name, last name, email address, and the rank of each target individual on the user groups page. You can also upload target details from a CSV file stored on your local system using import feature.
Install and set up Ngrok:
Install ngrok via Apt with the following command:
curl -s https://ngrok-agent.s3.amazonaws.com/ngrok.asc \
| sudo tee /etc/apt/trusted.gpg.d/ngrok.asc >/dev/null && echo "deb https://ngrok-agent.s3.amazonaws.com buster main" \
| sudo tee /etc/apt/sources.list.d/ngrok.list && sudo apt update && sudo apt install ngrok
Run the following command to add your authtoken to the default ngrok.yml configuration file.
ngrok config add-authtoken 2crm6P5lWlbTm4rwoGqn0QSHhPA_6nf7WmMJFKXVSD2SgBohF
Create an index.html page for the landing page and launch python http server in the port 8001
• python3 -m http.server 8001
Note: Verify in the browser if it's actually accessible.
We can also use other login page cloning techniques like built in gophish cloner, or Github projects (we used), Custom or by using third party clones (ex-goclone).
If it's a php file use the following command instead:
• php -S localhost:8001 -t .
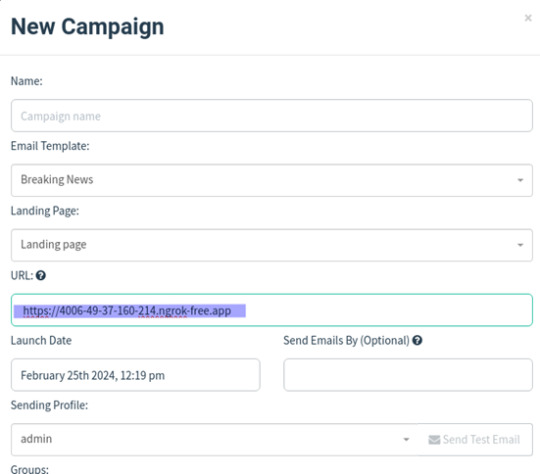
Launch ngrok :
ngrok http http://localhost:8001/

Use the URL under forwarding and paste it on the Gophish URL section in the campaign page shown below:
Creating Gophish Campaign:
Go to the Campaigns section.
Choose the right email and landing page templates.
Enter the landing page server URL.
Select the target group.
Start the campaign and monitor its progress.

Once we click on the link we are directed to the landing page, where we can enter our credentials.
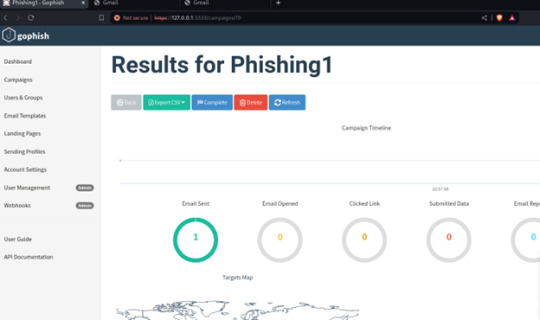
You can find all the phishing reports related to a specific campaign on the Dashboard in the Gophish framework. Here, you can see details such as sent emails, opened emails, clicked links, submitted data, and any emails reported as phishing by the targets. This page provides a comprehensive overview of the ongoing phishing campaign.
Phishing scenario: Case 2 - Password Reset Campaign
The aim of this phishing campaign is to trick users into divulging their login credentials by pretending to offer account protection in response to a fake mailbox compromise.

Users received an urgent email claiming their mailbox was compromised. They were directed to a phishing landing page disguised as a password reset portal.
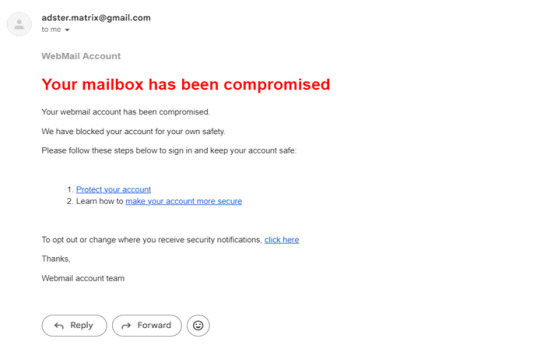
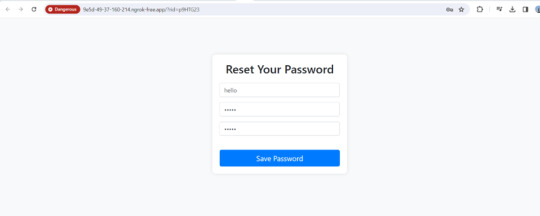
Upon clicking the link, Users were redirected to a fake password reset page resembling the email service provider's design, where they were prompted to enter their login credentials.
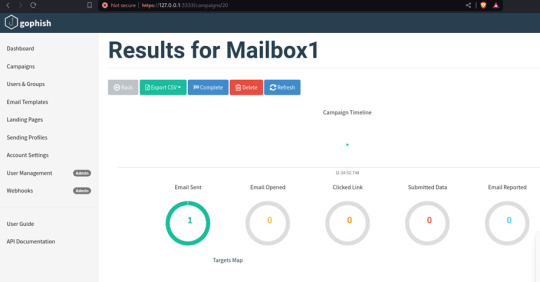
3 notes
·
View notes