#protecting your computer
Explore tagged Tumblr posts
Text
Okay, look, they talk to a Google rep in some of the video clips, but I give it a pass because this FREE course is a good baseline for personal internet safety that so many people just do not seem to have anymore. It's done in short video clip and article format (the videos average about a minute and a half). This is some super basic stuff like "What is PII and why you shouldn't put it on your twitter" and "what is a phishing scam?" Or "what is the difference between HTTP and HTTPS and why do you care?"
It's worrying to me how many people I meet or see online who just do not know even these absolute basic things, who are at constant risk of being scammed or hacked and losing everything. People who barely know how to turn their own computers on because corporations have made everything a proprietary app or exclusive hardware option that you must pay constant fees just to use. Especially young, somewhat isolated people who have never known a different world and don't realize they are being conditioned to be metaphorical prey animals in the digital landscape.
Anyway, this isn't the best internet safety course but it's free and easy to access. Gotta start somewhere.
Here's another short, easy, free online course about personal cyber security (GCFGlobal.org Introduction to Internet Safety)
Bonus videos:
youtube
(Jul 13, 2023, runtime 15:29)
"He didn't have anything to hide, he didn't do anything wrong, anything illegal, and yet he was still punished."
youtube
(Apr 20, 2023; runtime 9:24 minutes)
"At least 60% use their name or date of birth as a password, and that's something you should never do."
youtube
(March 4, 2020, runtime 11:18 minutes)
"Crossing the road safely is a basic life skill that every parent teaches their kids. I believe that cyber skills are the 21st century equivalent of road safety in the 20th century."
#you need to protect yourself#internet literacy#computer literacy#internet safety#privacy#online#password managers#security questions#identity theft#Facebook#browser safety#google#tesla#clearwater ai#people get arrested when google makes a mistake#lives are ruined because your Ring is spying on you#they aren't just stealing they are screwing you over#your alexa is not a woman it's a bug#planted by a supervillain who smirks at you#as they sell that info to your manager#oh you have nothing to hide?#then what's your credit card number?#listen I'm in a mood about this right now#Youtube
190 notes
·
View notes
Text
father. you are so annoying sometimes. get's a single hint of something not working anymore and immediately doomsday's it and tries to set on the path of replacement. man is single-handedly keeping consumerism alive.
#my mum's computer is working totally fine but it's 'vulnerable' and the security extentions 'wont work' so my dad says we need to ditch it#and he says that security extentions wont work at all and that it's better to have nothing in place to protect your computer#because hackers use that software to get into your computer#???#who tf is brainwashing my dad???
3 notes
·
View notes
Text
As someone who's maybe a little too quick to anthropomorphize any inanimate object I interact with, can I just say how glad I am that, thus far, computers mostly seem to talk in 'we' and 'you' terms instead of 'I' terms
#for clarification: I don't mean chatbots or alexa or AI-generated whatevers. They all seem to use 'I' quite comfortably#I'm talking about laptops that project messages like 'we're doing updates please don't turn off your computer'#and 'your antivirus protection has expired'#if my computer said shit like 'I'm updating give me a bit of time' and 'I have no antivirus :(' it would probably become a pet to me#not sure I can handle that tbh#computers
12 notes
·
View notes
Text

Chronicle of my experience trying to run Glaze/Nightshade that I really don't feel like resummarizing.
#zero's thoughts#“Use this tool to protect your shit” and the tool in question can't even run one some people's computers.#Vent post kinda#I'm just sick of... everything.
5 notes
·
View notes
Text
The burden of keeping training data free of copyrighted data-poisoned works should be on the company using it, not on the people just trying to protect their works.
#wrenfea.exe#i hate ai bros who cry that people should put warnings on their work that its poisoned#no YOU shouldntve have stolen their fucking creation#the warning is that you didn't get permission in the first place#you cant go into someones house steal a pie and then cry that it was full of shit#i mentioned this in my official public comment in a more...politically friendly way#i also said that peoples right to protect their work HAS to be protected#people cannot get sued for their work causing someones data to be fucked up#if they never explicitly agreed for their work to be used for that in the first place#and clicking yes on the terms of use doesnt count btw#if you want to scrape top results off of pixiv you shouldnt be surprised when your data gets fucked up#its your fault for not scrutinizing your dataset in the first place#ai#ai discourse#artifical intelligence#fuck ai#ai art#dall e ai#i studied ethics for computer scientists so im not just pulling this out of my ass
2 notes
·
View notes
Text
Stay safe, everyone!
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Microsoft Office, like many companies in recent months, has slyly turned on an “opt-out” feature that scrapes your Word and Excel documents to train its internal AI systems. This setting is turned on by default, and you have to manually uncheck a box in order to opt out.
If you are a writer who uses MS Word to write any proprietary content (blog posts, novels, or any work you intend to protect with copyright and/or sell), you’re going to want to turn this feature off immediately.How to Turn off Word’s AI Access To Your Content
I won’t beat around the bush. Microsoft Office doesn’t make it easy to opt out of this new AI privacy agreement, as the feature is hidden through a series of popup menus in your settings:On a Windows computer, follow these steps to turn off “Connected Experiences”:
File > Options > Trust Center > Trust Center Settings > Privacy Options > Privacy Settings > Optional Connected Experiences > Uncheck box: “Turn on optional connected experiences”
40K notes
·
View notes
Text
"oh but i'll lose my USB stick" secondary counter, how many people are actually using their files off their computer or phone? a backup shouldn't be a thing you carry round, it's a think you make once a month or so and leave in a safe place (preferably as far away from your main device as possible, like with a trusted friend) so that if your laptop is trashed or your flat burns down yours covered. It shouldn't be the thing you carry round with you to use your files, that's just your main drive! and general a backup drive should be a larger portable drive about the size of a phone not just a thumb drive. if you're working from the cloud every single day and it's not enforced by like an office job, you're wasting so much electricity uploading and downloading files! why open a file hosted in another country or state when you can easily open one hosted under your thumb?!
I am begging people to use LibreOffice and personal storage devices like hard drives or USB sticks instead of relying 100% on Google Docs. LibreOffice is free and open-source, it saves files to your own computer, and it lets you save as many different file types. You can write in it, format ebooks in it, and do everything you might possibly need to do as a writer.
"Oh, but I'll lose my USB stick--" Fine, back things up in whatever cloud you use as a form of extra protection, but you should also try your absolute damnedest to also put them on some form of storage that isn't a cloud.
I know it's not accessible to everyone, but if you at all have the ability, don't rely on shit that lives on other people's computers. Especially with everything going on with AI theft and aggressive censorship of adult media. If you don't store your files on your own personal computer that you have control over, your files aren't fully yours, and they're at the whims of whoever owns the cloud.
Learn where your files are stored and how to access them. Get into the habit of backing up your files to your own personal storage. Even if you're not up for intense tech research and you don't care about how the computer actually works, please stop letting your art live in corporate clouds.
#okay but now I feel the need to design a sort of gemini cloud#where your files get auto backed up to a friends computer at an arranged time#so it isn't a cloud it's just two computers#and it's protected so the backup can only be opened by the owner not the host#but you don't have some big company snooping in on your shit#god that'd be good
8K notes
·
View notes
Text
Volunteer Vacations: Making a Difference While Exploring the World
Volunteer travel, responsible tourism, ethical volunteering Where Adventure Meets PurposeNestled on the banks of the Zambezi River in Zambia’s Mosi-oa-Tunya National Park, Thorntree River Lodge offers more than a luxurious safari escape—it’s a gateway to ethical volunteer travel. Here, the thunder of Victoria Falls harmonizes with the quiet hum of community-driven change. Volunteer vacations,…

View On WordPress
#African Bush Camps Foundation’s impact dashboard). Community-Led: Projects should be requested and managed by locals#ask: How can my skills serve this community? The answer will guide you to a trip that’s as enriching for you as it is for Zambia. Pack your#built with tourism revenue . Sustainable Construction: Collaborate with local builders on infrastructure projects#exemplifies this ethos. Since 2006#guests can participate in: Wildlife Conservation: Assist rangers in rhino tracking and data collection#healthcare#leave your ego#like Maunga Village’s school renovations . 2. Aligning Skills with Community Needs Volunteer work thrives when skills meet necessity. At Tho#not in place of them. 4. Thorntree’s Model: Volunteer Through Experience While Thorntree doesn’t offer formal volunteer programs#or sharing cultural heritage. As you plan your journey#protecting rhinos#responsible tourism#school term schedules). Don’t: Engage in Orphanage Tourism: Many facilities exploit children for profit; instead#support family reunification programs . Take Over Jobs: Work with locals#supporting anti-poaching efforts in Mosi-oa-Tunya National Park . Education Initiatives: Teach English or computer skills at Maunga Village’#the foundation has channeled $10 from every guest’s stay into education#the thunder of Victoria Falls harmonizes with the quiet hum of community-driven change. Volunteer vacations#through the African Bush Camps Foundation#Volunteer travel#when done right
0 notes
Text
How to Protect Your Computer from Unauthorized Access?
Today, we live our lives online and on gadgets that are connected to the internet. We use the internet to do research, shop, bank, do assignments, play games, and connect with loved ones through social media. Because of this, our gadgets are filled with a
Continue reading How to Protect Your Computer from Unauthorized Access?
#Hackers#How To Prevent Unauthorized Computer Access#How To Protect Your Computer From Unauthorized Access#How To Save From Hacking#Methods For Preventing Unwanted Access To Your Computer#Protect Your Computer From Viruses
0 notes
Text
random person: [talks shit about langdon]
mel:
1. [is unamused/bothered/irked and it shows]

2. [leaves]

3. [strongly disagrees/makes factual and valid argument against]

4. [doubts the seriousness and proceeds to question the absurdity of the statement]

5. [thinks she must've heard wrong, surely]

6. [gets sad/hurt about it]

7. [ignores the complete and utter nonsense just spouted]

8. [hides]

9. [uses escapism to deal with the upsetting occurrence/dissociates]

10. [seeks comfort directly from the source]

ppl who love mel but hate langdon honestly baffle me. like?? even outside of all the shipping stuff he’s still her work bestie. her special little guy. her silly rabbit, even
#kingdon#if youre gonna 🤬🗯️ her soulmate to her face at least be aware shes proficient with a scalpel io drills 💉 and all sorts of ⚒️#such as defibrillators staple 🔫 needles and 🧵 ✂️ forceps intubation kits and the like#she can whirl her 🩺 about like a lasso or use it as a whip#she knows how to inflict maximum damage with bedpans 🌡️ 👅 depressors and the administration of carefully selected 💊#(she also can and will strap you to a 🛏️ and drain some of your 🩸 to calm you ⬇️ if need be do not test her)#mel believes people should 🤔💬 better before they 🗣️ ill of others and remember to always try to be respectful and polite#specially when it comes to the ones she holds dear to her and cares about the most#(i need to 👀 protective/💢😡 on behalf of another mel on the 🖥️ with my own two 👁️👁️ pitt gods 🥺🙏🏻 deliver)#just dont mess with her husky seriously even the most good tempered 🐶 owners can get 🤪🔪 about their mutts [source: me a 🐕 owner]#how can anyone seriously 🫤👎🏻 langdon? or any of the characters really. couldnt be me.#i 💓 them all so much. too much even. i should maybe chill a little.#and if one does indeed hate our local court jester how would one even enjoy his relationship no matter what kind with our beloved princess?#does. not. compute.#regardless theyre a 📦 deal already do not separate can only be sold as a pair et cetera#👩🏼⚕️🤝🏻🧑🏻⚕️#j’s thoughts
244 notes
·
View notes
Text

I've seen a number of people worried and concerned about this language on Ao3s current "agree to these terms of service" page. The short version is:
Don't worry. This isn't anything bad. Checking that box just means you forgive them for being US American.
Long version: This text makes perfect sense if you're familiar with the issues around GDPR and in particular the uncertainty about Privacy Shield and SCCs after Schrems II. But I suspect most people aren't, so let's get into it, with the caveat that this is a Eurocentric (and in particular EU centric) view of this.
The basic outline is that Europeans in the EU have a right to privacy under the EU's General Data Protection Regulation (GDPR), an EU directive (let's simplify things and call it an EU law) that regulates how various entities, including companies and the government, may acquire, store and process data about you.
The list of what counts as data about you is enormous. It includes things like your name and birthday, but also your email address, your computers IP address, user names, whatever. If an advertiser could want it, it's on the list.
The general rule is that they can't, unless you give explicit permission, or it's for one of a number of enumerated reasons (not all of which are as clear as would be desirable, but that's another topic). You have a right to request a copy of the data, you have a right to force them to delete their data and so on. It's not quite on the level of constitutional rights, but it is a pretty big deal.
In contrast, the US, home of most of the world's internet companies, has no such right at a federal level. If someone has your data, it is fundamentally theirs. American police, FBI, CIA and so on also have far more rights to request your data than the ones in Europe.
So how can an American website provide services to persons in the EU? Well… Honestly, there's an argument to be made that they can't.
US websites can promise in their terms and conditions that they will keep your data as safe as a European site would. In fact, they have to, unless they start specifically excluding Europeans. The EU even provides Standard Contract Clauses (SCCs) that they can use for this.
However, e.g. Facebook's T&Cs can't bind the US government. Facebook can't promise that it'll keep your data as secure as it is in the EU even if they wanted to (which they absolutely don't), because the US government can get to it easily, and EU citizens can't even sue the US government over it.
Despite the importance that US companies have in Europe, this is not a theoretical concern at all. There have been two successive international agreements between the US and the EU about this, and both were struck down by the EU court as being in violation of EU law, in the Schrems I and Schrems II decisions (named after Max Schrems, an Austrian privacy activist who sued in both cases).
A third international agreement is currently being prepared, and in the meantime the previous agreement (known as "Privacy Shield") remains tentatively in place. The problem is that the US government does not want to offer EU citizens equivalent protection as they have under EU law; they don't even want to offer US citizens these protections. They just love spying on foreigners too much. The previous agreements tried to hide that under flowery language, but couldn't actually solve it. It's unclear and in my opinion unlikely that they'll manage to get a version that survives judicial review this time. Max Schrems is waiting.
So what is a site like Ao3 to do? They're arguably not part of the problem, Max Schrems keeps suing Meta, not the OTW, but they are subject to the rules because they process stuff like your email address.
Their solution is this checkbox. You agree that they can process your data even though they're in the US, and they can't guarantee you that the US government won't spy on you in ways that would be illegal for the government of e.g. Belgium. Is that legal under EU law? …probably as legal as fan fiction in general, I suppose, which is to say let's hope nobody sues to try and find out.
But what's important is that nothing changed, just the language. Ao3 has always stored your user name and email address on servers in the US, subject to whatever the FBI, CIA, NSA and FRA may want to do it. They're just making it more clear now.
10K notes
·
View notes
Text
If any one of my posts is to break containment, make it this one.
Before January 2025, download your favorite fics, especially those with smut or queer content.
If Project 2025 goes into effect (which it very likely will now that we have three red branches of government in the US), they may attempt to restrict the use/sharing of media on sites like ao3.
This particularly applies to fics with smut or any type of queer content, because the official Project 2025 document states, "Pornography, manifested today in the omnipresent propagation of transgender ideology and sexualization of children, for instance... has no claim to First Amendment protection... Pornography should be outlawed."
Now, I don't expect ao3 to disappear or go anywhere without a fight, but it's best to be on the safe side these days.
To download your favorite fics:
Go to archiveofourown.org and open the fic you want to download.
At the top right corner, to the right of the 'subscribe' button, is a button that says 'download'. Click it.
A drop-down menu will give you the option to choose the format of your download. Choose your preferred format (.epub and .pdf are my personal favorites -- .epub lets you open a fic in the apple books app and .pdf is compatible with like every device and program out there).
When you click the button for your preferred format, a pop-up window appears confirming your choices. The title of the document will default to the title of the fic, so be aware of that and consider changing conspicuous titles to something ignorable, especially if you share the computer.
You're done! Now do this with all your favorite fics!
Stay safe out there, your favorite characters are rooting for you <3
#us politics#kamala harris#donald trump#project 2025#2024 elections#election 2024#hellection day#november 5th#spn#supernatural#destiel#destiel confession#fanfic#fanfiction#ao3#ao3 fanfic#archive of our own#fanfic writing#writers on tumblr#writeblr#fandom#whump#my post
9K notes
·
View notes
Text
When gas disappears… we invent fire.
In Gaza, where war stole everything from us — even our gas cylinders — we refused to freeze or give up.








With nothing but scrap metal, old car oil, and computer fans, people here built handmade burners to cook, boil water, and survive.
We turned trash into life. We turned despair into invention. This is how we fight for existence every single day.
We don't just survive — we create.🔥🛠️���
Reblog. Raise awareness. Let the world see our resilience.

As for me… I’m Kareman, a mother in Gaza.
I’m doing my best to protect and care for my son, Hammoud, in the middle of this war.
Thanks to a kind friend’s donation, I was able to bring a little light into my child’s life — food, warmth, and a smile.
The photo below is my son smiling next to the food we managed to buy.

That smile is a rare treasure in the middle of fear, displacement, and hunger.😭🫶❤️
If you’re reading this, please… don’t let this be the last smile I see on his face.🙏
Support us — donation link is in my bio.
My campaing vetted by/ @90-ghost here
@gaza-evacuation-funds here (6)
Donate here
Or through PayPal
Your kindness makes hope possible.
From a mother who is still trying
#artists on tumblr#disco elysium#911 abc#all eyes on palestine#space#zendaya#free gaza#free palestine#gaza#free gaza 🇵🇸#gaza genocide#gaza strip#gazaunderattack#free palestine 🇵🇸#palestine fundraiser#mini palm scales#van palmer#save palestine#i stand with palestine
4K notes
·
View notes
Text
Another approach is to use Git. No, seriously, I know it's like a programmer thing, but it works for all text files and can technically work for xml based files like Word also.
If you're not confident on using a command prompt, check out Github Desktop. Contrary to the name you don't have to put repositories it makes online (and if you do they don't have to be public).
Git is helpful because all those versions of files don't remain visible in one folder, you always just see the most recent version. Past versions exist in the commit history, and you can. Roll back to specific versions, branch off from them, all that good stuff.
REMEMBER: WHEN YOU'RE WORKING ON A PIECE OF WRITING, NEVER DELETE ANYTHING
Ok, so you have a big paper due in July. You make a folder for the project called "Big Paper." You get to work, and save a file titled "PaperTopic.doc" in that folder.
You go back to your draft the next day. DO NOT simply open "PaperTopic.doc" and start editing/adding/revising. You are going to make a folder titled "Paper Versions." You are going to make a copy of "PaperTopic.doc." You are going to move it into the "Paper Versions" Folder.
Then you are going to go back to the original "PaperTopic.doc," and rename it "PaperTopic 5.14.24.doc." And you're going to repeat this EVERY DAY that you work on this project. Soon the "Paper Versions" will look like this:
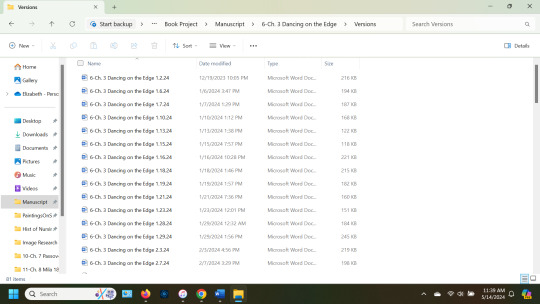
I post about this every 6 months or so, and I will continue to do so; because one day, it WILL save your ass. You're welcome.
Also, back it up to an external hard drive at least once a week.
#writing#writers#creative writing#also please please make backups!!!#they dont have to be in a cloud service#but if you want the peace of mind of cloud stuff without them spying on you consider putting your backups on cloud platforms in password#protected zip files. those are encrypted so Google or whoever wont be able to peek at them#i personally use a free tier Oracle Cloud server as my “house fire” level backup but ik thats not practical for most#remember that backups living on the same device arent really backups at all#since your whole hard drive could fail#and a bad power surge could take out all the drives in your computer#stay safe yall!
2K notes
·
View notes
Text
Critical Windows Update: Apply Patch Now to Prevent Black Basta Ransomware
#Time is running out for Windows users to secure their systems against the notorious Black Basta ransomware. Microsoft has released a critica#as failure to install it could leave your PC vulnerable to sophisticated ransomware threats.#The Critical Windows Update#Microsoft has issued an urgent call to all Windows users to apply a crucial security patch aimed at thwarting the Black Basta ransomware. T#your system remains susceptible to attacks that could encrypt your data and demand a ransom for its release.#Understanding Black Basta Ransomware#Black Basta is a highly dangerous form of ransomware that encrypts files on the victim’s computer#rendering them inaccessible until a ransom is paid. Often#even paying the ransom does not guarantee the recovery of the encrypted files. The threat posed by Black Basta is severe#making it imperative for users to protect their systems immediately.#Why This Update is Crucial#The update released by Microsoft is designed to close a vulnerability that Black Basta exploits to infiltrate systems. Cybersecurity expert#emphasizing the need for users to act quickly. Applying this patch is not just a recommendation—it’s a necessity to safeguard your personal#How to Apply the Update#Applying the Windows update is straightforward:#Open the Settings menu on your Windows PC.#Navigate to Update & Security.#Click on Windows Update.#Select Check for updates.#Once the update appears#click Download and install.#Ensuring your system is up-to-date with the latest security patches is a vital step in protecting against ransomware attacks.#Potential Consequences of Ignoring the Update#Failure to apply this critical update could result in severe consequences. If Black Basta ransomware infiltrates your system#you could lose access to valuable data#suffer financial loss#and face significant disruptions to both personal and business operations. The cost of recovery and the potential damage to your reputation#Real Stories#Real Risks#Think about all the important files on your computer—photos
0 notes