#the magnus database
Explore tagged Tumblr posts
Text
Database Additions for MAGP 09: Rolling With It
Released 7 Mar 2024 Episode written by Jonathan Sims & Alexander J Newall
Episode summary from The Magnus Database
SPOILERS BELOW CUT
CASE
CAT3RB3354-14101998-08032024 Dice (bone) -/- fate [Magnus Statement] Read by Chester
Parties mentioned: Carl Dice Owner Gary Magnus Institute
Locations mentioned: West Didsbury
Misc objects mentioned: Pair of dice
Other Parties Introduced
Nigel Dickerson
Other Locations Introduced
None
Other Misc Objects Introduced
Mr. Bonzo Saturdays on Six The Prank Tank
Connections/Item Relationships Found (New)
Nigel Dickerson and Mr. Bonzo
Voiced Characters
Norris Samama Khalid Celia Ripley Chester Lena Kelley Gwendolyn Bouchard Alice Dyer Teddy Vaughn
Database
The Magnus Database has been updated for this episode.
8 notes
·
View notes
Text
Broke: Archivist Sasha James would simply Girlboss her way past all the struggles Jonathan Sims faced
Woke: Sasha’s journey would be about the same as Jon’s
Bespoke: Sahsa would be even worse than Jon
#sasha james#Sasha tma#tma sasha#tma#the magnus archives#tma Au#archivist sasha#archivist!sasha#thearchives#the archivist#jonathan sims#but otherwise you cannot tell me that girl—Ms let me know just back into these databases illegally because I want to Know—Ms how she handle#micheal—has any kind of impulse control
851 notes
·
View notes
Text
hey did you guys know we have birthdays for sam, gerry and Someone In The Dyer Family That May Or May Not Be Alice
#ramblings with major#the magnus protocol#tmagp#tmagp arg#i forgot that database from the institute experiments in the arg had FULL BIRTHDAYS
66 notes
·
View notes
Text
Can I interest anyone in a database? Who am I kidding, you all want a database.
I'll try to keep this updated as much as possible, especially since this is the copy I've put into a different account that's not attached to my name. I'm currently through the basics of MAG and up to the current public episode of TMAGP. I'm still working on pulling descriptions and entities/artefacts/avatars from transcripts when I have the time, which isn't as often as I'd like, as a STEM uni student.
WARNING! This document for TMAGP will be updated every TUESDAY when the patreon episode is released. If you want to avoid spoilers, wait to read until Thursday for TMAGP
#the magnus protocol#tmagp#the magnus archives#tma#tmagp spoilers#the magnus protocol spoilers#the magnus protocol spoiler#magnus protocol#magpod#the magnus archives minor spoilers#magp#mag#the magnus archives database#the magnus protocol database#magpod analysis
134 notes
·
View notes
Note
i really don’t understand why gerryoliver isn’t a more popular ship
.
41 notes
·
View notes
Text
In a bit of a weird situation making The Database
I’m doing creepy monotonous (not really lol) data entry about people doing creepy monotonous data entry
Might put on a shirt and tie and make this a LARPing activity
8 notes
·
View notes
Text
Looking forward to a whole season of American football narrated by my good friends Jonathan Sims and Cecil Palmer. Coming to an ESPN near you any day now
#the normalcy of it all would make cecil’s life worth living and the databases of organized information might make jonathan cry#alas. tis but a shitpost. sigh#the magnus archives#welcome to night vale
2 notes
·
View notes
Text
guilty
unsure how i feel about the magnus protocol yet, but at the very least the new classification system for supernatural incidents seems interesting. they know their target audience (autistics who love inputting data into comprehensive spreadsheets).
919 notes
·
View notes
Text
Different Protocols explained
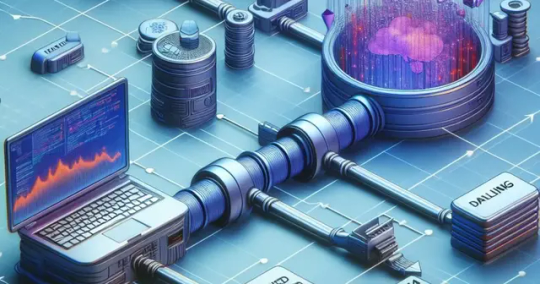
Ever wondered about the behind-the-scenes when you connect to a database, make an HTTP request, or check your Gmail? How does a server distinguish your legitimate device from an unauthorised interloper?
Unraveling the Mystery of Protocols
In the world of computer networks, a protocol is like a set of rules or guidelines that dictate the way data is sent and received across a network. These protocols are crucial for ensuring that various hardware and software elements involved in data communication work together seamlessly, despite their different backgrounds.
Consider these examples: HTTP, Simple Mail Transfer Protocol (SMTP), Redis Serialization Protocol (RESP), Post Office Protocol 3 (POP3), Internet Message Access Protocol (IMAP), and more.
Diving into the OSI Model
The OSI model plays a pivotal role in classifying these diverse networking protocols into a well-defined structure.
Why focus on the OSI model? This model is vital as it breaks down network communication into seven distinct layers, with each layer assigned specific responsibilities. Importantly, each layer depends on the ones below it to handle the more fundamental aspects of communication.
Take the Application Layer (Layer 7), for example. It doesn't get bogged down with the nuances of data transport - that's the job of the Transport Layer (Layer 4), where you find protocols like TLS ensuring secure data transmission. This layered approach lets each protocol operate effectively within its domain, without the need to delve into the complexities of the underlying layers.
Before diving deeper into the workings of protocols in contexts like email or database communication, let's start with something more straightforward and accessible: HTTP.
Hyper Text Transfer Protocol (HTTP): A Peek into Simplicity

Now, let's decode the story revealed by a Wireshark snippet. It unfolds the tale of TCP communication initiation between the client and server, the data transfer process, and the conclusion of communication after data exchange.

Why does this warning appear? It's because HTTP is susceptible to eavesdropping, replay attacks, data theft, and various security risks. It lacks the encryption and protection mechanisms necessary to ensure secure data transmission.
Hypertext Transfer Protocol Secure (HTTPS): Fortifying Web Communication HTTPS (HyperText Transfer Protocol Secure) is an extension of HTTP. It is HTTPS, an extension of HTTP, stands as a more secure alternative. It enhances security by employing SSL/TLS (Secure Socket Layer/Transport Layer Security) to encrypt data during transit.

The journey of HTTPS begins much like HTTP, with the same TCP-based communication initiation between the client and server. However, the crucial divergence occurs afterward, where HTTPS introduces the TLS handshake.
TLS: Safeguarding Data for All Protocols TLS, or Transport Layer Security, stands as a protector of data for various protocols, ensuring encryption and decryption of data. To understand why TLS is a vital component in data security, let's delve into how it operates.
In the image presented earlier, we witnessed the process of communication secured by TLS:
Initiation and Cipher Negotiation: The TLS handshake commences when the client sends a "client hello" message, specifying its TLS version, supported cipher suites, and a client-generated random byte string. In response, the server issues its "server hello" message, containing its SSL certificate, chosen cipher suite, and a server-generated random byte string.
Authentication and Key Exchange: Next, the client authenticates the server, utilizing its SSL certificate and a certificate authority. Subsequently, the client sends a premaster secret, encrypted with the server's public key, which the server decrypts using its private key.
Completion and Secure Communication: Both parties collaborate to generate session keys, relying on the client's random data, server's random data, and the premaster secret. This process ensures that both ends compute identical session keys. Following this, they exchange "finished" messages, encrypted with the session keys, thereby establishing a secure, encrypted session.In essence, TLS serves as the bedrock of security for various protocols by facilitating encryption and decryption processes. Its robust handshake procedure ensures the establishment of secure encrypted sessions, providing a shield for sensitive data during transmission.

Certainly, let's shift our focus to the importance of encryption keys in various protocols and explore how different protocols, including SMTP, address the need for security.
Now that we've established the concept of secure communication through session keys, it's essential to recognise that not all protocols follow the same approach of "use TLS and be happy." Each protocol has unique requirements and considerations when it comes to security.
Take, for example, email services like "gomailer" that use SMTP (Simple Mail Transfer Protocol). SMTP follows a specific sequence of steps before engaging in TLS encryption. It's important to understand that:
SMTP doesn't immediately jump into TLS for security; instead, it initiates communication and checks if the client is capable of communicating via the protocol. If the conditions are met, it proceeds with TLS to ensure secure data transfer.

SMTP: Tailoring TLS Security for Email Communication SMTP serves as the protocol that defines the structure of email messages and the process of transferring these messages between servers, ultimately reaching the recipient's email server. An interesting aspect of SMTP is that the conversation initiates from the server side, which differs from most protocols where communication typically starts at the client side. In SMTP, the server first checks if the client is capable of communicating via the protocol and then proceeds to establish a TLS-encrypted connection.
This reveals a crucial insight: While security is paramount in data transmission, SMTP allows for a flexible approach to when and how security measures are applied. It empowers the sender to choose when to introduce TLS security during the communication process, adapting to the specific requirements of email transfer. In essence, SMTP demonstrates that TLS can be implemented at different stages of communication based on the use-case and security preferences.
MongoDB: TLS Encryption in Database Communication MongoDB the very popular database uses a some complex protocol to transfer data When you establish a connection between your program and a MongoDB database, a TLS (Transport Layer Security) connection is established to ensure data security. This TLS-encrypted connection becomes the conduit for sharing data.
MongoDB takes a unique approach to data sharing. Instead of transmitting data in plain text like HTTP, MongoDB uses BSON (Binary JSON) as its data format. BSON is a binary representation of JSON (JavaScript Object Notation). To transmit data over the network, this BSON data is further encoded into data packets.
This combination of TLS encryption and BSON data format allows MongoDB to securely and efficiently share data between applications and the database server.

Redis, which utilizes the RESP (REdis Serialization Protocol), offers users the flexibility of choosing whether to implement TLS (Transport Layer Security). But why is this choice available, and why doesn't Redis employ security measures by default, as many other applications do? One significant factor is performance optimization.
In high-performance environments where Redis is frequently deployed, minimizing latency is a critical concern. The necessity for TLS largely hinges on the specific security requirements of the application. For instance, if Redis is primarily utilized for caching public data that isn't sensitive, the demand for TLS encryption may be minimal.
So, how does RESP handle data when TLS is enabled? When TLS is activated in Redis, it introduces an additional layer of security. Data packets, including those containing RESP-formatted messages, are encrypted by the client before transmission over the network. Upon receipt, the server decrypts these packets. Notably, this encryption and decryption process is transparent to the RESP protocol itself. RESP continues to operate seamlessly, just as it does without TLS, but the data remains protected throughout transmission, striking a balance between security and performance.

In PostgreSQL (often referred to as PgSQL), specific packets play a pivotal role as they typically contain the actual data or commands sent to the PostgreSQL database server. These packets can encompass a variety of elements, including SQL commands, query results, or database control messages. It's worth noting that certain packets bear distinctive symbols to denote their direction in data communication—">" signifies a packet as a request from the client to the server, while "<R" indicates a response from the server to the client.
Much like Redis, PgSQL also employs symbols to illustrate the direction of data flow, featuring elements like CommandComplete and ReadyForQuery.
Furthermore, similar to Redis, PgSQL offers the option of TLS security as an add-on.So one thing is for sure, these protocols are secure, but are they secure enough to safe?That doesn't seem to be the case.
Securing Data in Protocols: TLS and Its Application
In this discussion, we explored how various protocols implement security, with a focus on TLS (Transport Layer Security). SMTP tailors security for email communication by initiating TLS at specific stages. MongoDB uses TLS to encrypt data transmission, while Redis offers optional TLS due to performance considerations. Similarly, PgSQL employs TLS for added security. However, despite these security measures, the effectiveness of TLS can be challenged by Man-In-The-Middle attacks, emphasising the ongoing need for vigilance in protocol security.
0 notes
Text
what i think oiar employees listen to at work:
alice - welcome to nightvale
sam - white noise or r&b playlists
gwen - malevolent
colin - death metal
lena - the scp foundation database
celia - the magnus archives
#this post sponsored by my genuine headcanons as well as my need to include that meta punchline at the end#tmagp#the magnus protocol#tmagp headcanons#tmagp shitpost#alice dyer#samama khalid#gwen bouchard#colin becher#lena kelley#celia ripley
2K notes
·
View notes
Text
Database Additions for MAGP 04: Taking Notes
Released 1 Feb 2024 Episode written by Cole Weavers Edited by Jonathan Sims & Alexander J Newall
Episode summary from The Magnus Database
SPOILERS BELOW CUT
CASE
CAT3C7494-19111831-29012024 Collection (blood) -/- musical [letter] Read by Augustus
Parties mentioned: Trinket Merchant Oliver Bardwell Royal Court Orchestra Violinist Violinist's Nephew
Locations mentioned: Alnwick Abbey Mannheim School
Misc objects mentioned: Violin
Other Parties Introduced
Klaus Starkwall
Other Locations Introduced
None
Other Misc Objects Introduced
Emailed video of Lena and Klaus San Pedro Square Massacre The Protocol
Connections/Item Relationships Found (New)
Uncategorized tech strangeness at the OIAR The Protocol and information surrounding it San Pedro Square Massacre and information surrounding it Lena Kelley and information surrounding her
Voiced Characters
Alice Dyer Samama Khalid Gwendolyn Bouchard Augustus Lena Kelley Klaus
Database
The Magnus Database has been updated for this episode.
8 notes
·
View notes
Text
OHHH, I just thought of something.
It's been bugging me that Norris, Chester, and Augustus started speaking around a year ago, and I've been wondering about the significance of that timing. At first I thought maybe it was some consequence of whatever RedCanary stumbled into at the Magnus Institute, because that was a bit over a year and a half ago--we know from the case numbering system that the episodes are taking place in the present day (episode 2 was taking place on Jan 18 2024; note for my fellow US folks that the dates are the UK standard with day first, not month). And from the dates on the forum posts, RedCanary's series of unfortunate events was in April 2022.
BUT based on their case numbers, which give the date the case's events happened even if that's not said in the episode, all the incidents Sam has looked at so far were from mid 2022. They're not perfectly grouped together; the dolls and Arthur and RedCanary were all April through May 2022, while Daria's therapy appointment was September--that last one's a bit of a jump, but it could have happened depending on how cases are being allotted among the various workers. But they're all close enough that it's a plausible assumption, I think, that FR3-D1 is generally finding these things roughly as they're posted and then adding them into people's queues for review. This would mean they're at a current backlog of around a year and a half. (Looking at you, Gwen...)
If that's the case, and if the OIAR's workers have been maintaining a roughly constant rate, then around a year ago they would probably have been reviewing a lot of cases that FR3-D1 found in early to mid-2021. Which means they'd have been opening files that have been sitting in their database untouched since that time.
MAG200 aired on March 25, 2021.
Whether Chester and Norris are a Ushanka'd JMart, or something resulting purely from Annabelle Caine's manipulation of their voices, or something else entirely... l don't know. But I am betting that they didn't start as part of the system, like Colin thinks they did. I think there was some direct consequence of MAG200's events which led to them being embedded in a post that FR3-D1 scraped up, and that they simply weren't activated and "let loose" until some unknowing office worker clicked on their file.
#apologies if someone else has said all this already! I haven't seen it in the tags but I could well have missed it.#the magnus protocol#the magnus protocol spoilers#tmagp#tmagp speculation#tmagp spoilers#tma spoilers#pondering magpods
1K notes
·
View notes
Text
“I Need Your Support to Continue My Studies and Build My Future from Gaza🍉🍉

My name is Mahmoud Naeem Abu Hatab, from Gaza.
I am a university student majoring in Software and Databases at Al-Azhar University. Since the beginning of my academic journey, I have been passionate about User Experience (UX) and User Interface (UI) design, as well as website development. These fields inspire me, and I dream of advancing my skills and building a professional career in them.
Unfortunately, during the recent war, I lost my laptop, which was essential for both my studies and work. I was forced to flee my home and relocate to southern Gaza due to the difficult circumstances. Despite my efforts to replace my laptop, the financial situation has made it impossible to afford a new one.

Without a laptop, continuing my studies or seeking job opportunities in programming and design has become extremely challenging. This directly affects my academic progress and future career.
Today, I am reaching out to ask for your support to help me purchase a new laptop. Having a laptop would allow me to resume my studies and work on programming and design projects that are crucial for improving my skills. It is a vital step towards completing my education and pursuing my dream of becoming a professional in programming and UX/UI design.
I know that the situation in Gaza is difficult, but I believe education is the only path to building a better future for myself and my family. If you are able to contribute any amount to help me get a new laptop, it would be a real opportunity for me to get back on track academically and professionally.
I am determined to keep learning and working despite the challenges, but I need your support to achieve this goal. Every donation or act of help, no matter how small, will make a significant difference in my life.
If you’d like to support me, you can donate through:
GoFundMe
OR
USDT
If you can assist in any way, please don’t hesitate to reach out to me.
Thank you for your support and kindness! 🌿
@gaza-evacuation-funds @appsa @nabulsi27 @palestinegenocide @orblesbian @palebluebutler @pallasisme @fallahifag-deactivated20240722 @vakarians-babe @sayruq @ @plomegranate @riding-with-the-wild-hunt @queerstudiesnatural @tamamita @apollos-boyfriend @riding-with-the-wild-hunt @queerstudiesnatural @palestinegenocide @sar-soor @akajustmerry @annoyingloudmicrowavecultist @feluka @marnosc @flower-tea-fairies @flower-tea-fairies @tsaricides @tsaricides @belleandsaintsebastian @ear-motif @brutaliakent @raelyn-dreams @troythecatfish @4ft10tvlandfangirl @90-ghost @paper-mario-wiki @nabulsi @prisonhannibal @beepiesheepie @walcutt @schoolhater98 @commissions4aid-international @sar-soor @zigcarnivorous@tododeku-or-bust@turtletoria @brutaliakhoa @flower-tea-fairies @schoolhater @baby-girl-aaron-dessner @sayruq @omiteo777 @malcriada @neptunerings @bat-luun @kaneverse @nightowlssleep @staretes @friendshapedplant @soon-palestine @aria-ashryver @heritageposts @magnus-rhymes-with-swagness-blog @khangerinedreams @kordeliiius @mazzikah @feluka @dlxxv-vetted-donations @girlinafairytale @a-shade-of-blue @vakarians-babe @babygoatsandfriends @self-hating-zionist @mangocheesecakes @dlxxv-vetted-donations @gazaboovintage @gazavetters @wellwaterhysteria @sar-soor @applebunch @irhabiya @sayruq @xxx-sparkydemon-xxx @junglejim4322 @reptilianspecies @dr-lapdance @tamamita @cantsayidont @fairweathermyth @dear-indies @eruthiawenluin @katealot @lenasai @stalinistqueens @ayeshjourney @gaza-evacuation-funda @el-shab-hussein @irhabiya @nabulsi @ibtisams @dlxxv-vetted-donations @tododeku @a-shade-of-blue @gaza-relief-fund @catnapdreams @northgazaupdates @buttercuparry @stuckinapril
#voic of gaza#gaza#free palestine#palestine#free gaza#save gaza#save palestine#help gaza#help palestine#programming#studying#uxdesign#ui ux design#uidesign#ui#ux#user interface#user experience#figma#xd#web design#web development#web developers#mobile design#html#css#js#javascript#java#front end development
296 notes
·
View notes
Text
Sam fumbled Gwen’s Bonzo reveal… but he’d been primed to do so
I suspect that there's going to be a LOT of conversation around Sam after this episode, and since this episode was so good that I couldn't think of a meme or shitpost, I decided I'd throw my hat into the ring and do some character analysis instead. CW: Spoilers for The Magnus Protocol episode 18, "Solo Work" under the cut.
Episode 18 finally gave us the Sam and Gwen interaction I (and I think a lot of others) have been so desperate to finally see, and boy oh boy do I have Thoughts… none of which are new per se, but Sam’s reaction to Gwen dropping the Bonzo Bomb seems to have reinforced the way I’ve been reading (and projecting in fanfiction oops) Sam, his personality, and his motivations.
Out of everyone new we’ve been introduced to so far, Sam has by far gotten the most explicit development and conversation around his personality. Even before episode 1, folks who participated in the ARG got a preview of our favorite baby shrimp’s personality through access to the child database spreadsheet that was, presumably, used to document the results of the experiments run on children participating in The Magnus Institute’s “gifted and talented program.” From this spreadsheet, we can gather that Baby Sam is logical, empathetic, works towards the benefit of others (prosocial), and fair… but also a rule follower and highly willing to follow the lead of an authority figure, even if it is in conflict with his personal views. The picture this information paints is an interesting one, but when taken in a vacuum leaves us with an impression of Sam as someone who is kind but lacking in backbone.
This idea of Sam as “kind but lacking in backbone” is further reinforced in canon, as Alice of multiple occasions rags on him for being “noodly” and “ickle fawn” and a “baby shrimp,” all seeming to highlight that Sam has the sort of helplessness about him typically ascribed to sopping wet kittens and baby birds. And I think that if we view Sam’s outburst when Gwen brings up Bonzo through this lens alone, it’s going to seem WAY out of character for him and a downright cruel response.
Now while I do believe that Sam is empathetic and fair and, sometimes, a little helpless, I’ve been inclined to believe from early on that much of Sam’s affable self-deprecation is a way to cover or soften what can be, at times, a tendency to be hard-headed, temperamental, a little manipulative, and petty (and I’m totally not just saying that as a people-pleaser-and-gifted-kid-in-recovery who has been projecting hard on Sam since Day 1). And it’s this second batch of personality traits, the ones that make Sam so real and interesting to me, that I think set up the disaster of a conversation between Sam and Gwen.
We have definitely seen hints of Sam’s hard-headedness and manipulative leanings in previous episodes: it comes out most often around Alice, showing his stubbornness in the form of refusing to give up his lines of questioning and curiosity about what is happening in the cases and at the OIAR; and revealing his willingness to manipulate a situation the form of subtly redirecting Alice’s focus away from prying into his crush on Celia and during the mocha incident (I have, of course, already explored Sam’s manipulative tendencies in my totally comprehensive shitpost).
And we’ve even been shown at times before episode 18 where Sam can be petty, his buzzed insistence that Alice try and keep things “professional” at work after his date with Celia being at the top of the list. The case headers filed for “Putting Down Roots” and “Pet Project” also suggest to me Sam’s ability to be stubborn and petty: in both instances, Alice and Gwen suggest a different classification than the one that Sam ultimately files. In the case of Gwen in “Pet Project,” she’s dismissive of him when he tries to ask if she’s all right.

While there’s no way to know for sure, I interpret this interaction as part of the reason why Sam ultimately disregarded Gwen’s suggestion for how to file the case—she shut him down and shut him out, and the petty part of his heart couldn’t resist ignoring her recommendation out of spite. This scene also begins to lay the foundations for Sam and Gwen’s interactions in episode 18 and, I suspect, the rest of the season.
So with all of this in mind, let’s look at episode 18. When Gwen emerges from Lena’s office, Alice has just finished shutting Sam down, again. Throughout most of this season, Sam has been desperate for some validation that the cases they are listening to are real, that whatever happened to him at The Magnus Institute was real, and that him pursuing this line of questioning and wanting to find answers isn’t a waste of his time. Alice has, of course, been not-so-gently nudging him away from this line of thinking for most of the season, while Gwen has been icing him out about it up until this point. Just about the only one who has given his questioning any air has been Celia who is, conveniently, not there. Even after Alice has her very own supernatural experience that is reaffirmed in the case Sam receives, she strongly pushes back on his idea that they should investigate and pursue this further. He understands why she doesn’t want to learn more, but it’s clear that he’s still frustrated at the end of the conversation.
Enter Gwen. Here, for the first time, it seems like she’s opening up about what is going on at the OIAR, and Sam is immediately hooked, even dropping his softer and sympathetic side when Alice tries to redirect with one of her classic barbs.

After being shut down time and time again, Sam is so eager for confirmation that there is more to all of this than meets the eye. And then Gwen says the B-word, and Sam loses it.

Sam is laughing here, but honestly? I think he’s angry, and his reaction is one of complete disbelief that Gwen would set him up like this just to, in his mind, take the piss out of him. He thinks that, at best, Gwen is having a breakdown and he’s once again being shut out or, at worst, Gwen is making a joke at his expense. Now, he’s used to being the butt of a joke thanks to being friends with Alice, but despite that we’ve never heard him call her an asshole the way he does Gwen. Temperamental and petty, turning around his hurt and anger over being stonewalled again and again to lash out at Gwen with his joke.
And honestly, can you blame him? (I can’t.)
Of course this wasn’t the ideal reaction. I have been waiting for Sam and Gwen to have a serious heart-to-heart about what’s going on forever, and Sam pretty much blew that chance without even realizing it. And I would be surprised if we get an apology out of him anytime soon, not only because this interaction is likely to push Gwen away from wanting to even be around Sam, but also because he’s not going to believe that Gwen wasn’t making fun of him or that Gwen isn’t having a delusional breakdown until he sees Mr. Bonzo with his own two eyes.
I also think this conversation would have gone very differently had Celia been there instead of Alice. Sam’s slew of psychological testing suggests he’s willing to follow the leader, and in this case he doesn’t seem immune to Alice’s general dismissiveness of Gwen. He may have even been primed to lash out at Gwen in this moment because Alice is constantly ragging on her; chameleon-like, he’ll take on the shade of the strongest personality when he’s on uncertain or dangerous footing. It’s almost a guarantee that Celia would have taken Gwen seriously, not only because she’s likely from or connected to the TMA-verse of horrors, but also because it was Celia who received the first Mr. Bonzo case. And had Celia been there to temper the disbelief, Sam would have absolutely been ready to hear Gwen out in full. I honestly cannot wait for Celia to be back in office; she’s going to walk in to these new, rancid office vibes like Troy from Community walking into the whole room on fire while casually carrying the pizza.
So, what do I think this means for the rest of the season? Well, the title of this episode seems telling: Solo Work. Gwen and Sam’s respective desires for their experiences to be validated and their goals to be taken seriously paired with the seeming dismissiveness of those around them are going to push them along their separate paths, dangerously alone. And I suspect that it is only going to be Celia or, more likely, an encounter with Bonzo, that is going to put them back on the same path—if it happens at all. Good luck, babes!
#The Magnus Protocol#tmagp#tmagp theory#tmagp spoilers#The Magnus Protocol spoilers#tmagp ep 18#tmagp solo work#samama khalid#Sam Khalid#gwen bouchard#the magnus institute#character analysis#sam khalid character analysis#Teal's TMAGP takes
476 notes
·
View notes
Text
Summarizing @MalkPs Amir,/ Yusuf's family
EDit,, current account @malak-za
this Tumblr is wasbeing run by a child not much more than 12. (edit:latest link is too a sibling's) Please help and donate
"’m trying to raise $500 for my grandpa’s treatment and to support my siblings."

t is verified by @/el-shab-hussein (sheet no. 209).


This thread has been copied below the cut with interruptions and dead links removed
Donation incentives
@/a-shade-of-blue is running a raffle for those who donate to vetted campaigns, with necklaces as a prize
Flowerpawarts has compiled a list of similar artists providing incentives for vetted I and many other artists have donation commissions open or will give you stuff in exchange for donating! i've bought from most of these artists: dan and phil phriendship bracelets $5 not including shipping varied friendship bracelets $5 for premade bracelets, $10 for custom chibi donation commissions $5+ fic commissions $ varies more fic commissions ~$10 cartoonist co-op artist database (offering MANY different things from stickers to zines! you can usually reach out to these artists individually)
if you can't donate anything, please share!
magnus-rhymes-with-swagnessdonors can get postcards or owl trinkets!
Hi, my name is Amir and I’ve lived through three wars — in 2014, 2021, and 2023. Each time, my family lost everything, and somehow we always started over. But this time… after the last war, we couldn’t start over. We’ve lost too much. It feels impossible.
I created this account because I want to try — to do anything I can — to help my family survive. Even though I’m just a kid, I won’t give up.
If you see this, please don’t scroll past. A share can go a long way. Even $1 can bring a little hope.
💔 Please, I’m begging you… don’t look away 💔
My siblings are trapped. The borders are closed. There is no escape, no safety, no peace.
We’re surrounded by fear, hunger, and the sound of loss. I was holding on to the hope of evacuating them — but now, that hope is gone.
I feel helpless… but I can’t give up. Not when they’re still breathing, still fighting to survive.
Please, I’m asking from the depths of my heart: don’t leave them alone. They are cold. They are hungry. They are children of war who did nothing to deserve this.
Your share might reach someone who can help. Your donation might be the reason they wake up tomorrow.
Please… be the reason.
I apologize for the double tag today, but please know that I wouldn’t do this if you weren’t needed. Contact me DM if you wish to be removed.
malkps
9h
Hey, I really need your help right now. I’m trying to raise $500 for my grandpa’s treatment and to support my siblings. Anything you can give would mean the world to me. And if you could share this with your friends, that would be amazing. Thanks so much for being there for me.
@spicy-apple-pie @strangeauthor @virdigrishammer @laurajameskinney @beetledrink @unpeeled-human @catmask @neechees @uncouth-thespian-ghost @maelstroms-blog @approximately-63-crying-cats @funnyname34 @hiveswap @tamamita @tigersharrrk @yakiattaki
malkps
7h
My grandpa is sick, and my brothers are in Gaza under heavy hardship. Please, a reblog could really help us. Thank you from my heart. 💔🙏
#emergency#gaza gfm#vetted#time sensitive#help this brave child#help this family#gaza family#urgent#please help#mutual aid
114 notes
·
View notes
Note
The way experiment baby alec rotates in my brain.... the possibilities.....
Hell hound alec,, mermaid alec, cannibal alec..... maybe some dnd bloodhunter type shit... damn
@queensaryn and I actually have a really fucked up idea/headcanon that I haven't worked on yet but that Robert Lightwood is actually sterile and when Valentine helps them with a 'special fertility treatment' but he really just does IVF with his own sperm.
So like, he does not have Maryse's consent and she doesn't know that Alec or Izzy are his and they only find out something is wrong when she and robert try to have another kid and go to the doctors of Idris who are like 'oh no this guys sterile' and maryse is like 'what injury did that' and they're 'oh no. we can tell by his system that he's always been sterile.' and then maryse has to have her kids run through the database because whose are they? like at this point Maryse's is just relieved they're fully shadowhunter with what she remembers hearing about Jonathon later. (who she thinks is dead and doesn't bring up).
They find out the they're Valentine's and the Clave basically is like 'wait... if you didn't know. what if he did this to other people?' and DNA check all kids born during the time Valentine was active (even before he started the circle) just to be safe. it's how they discover Jace is a herondale and that some other fucky shit has happened.
but also Alec on learning who his bio-sperm is immediately does a ritual that basically is destroying his own sire's legacy. like he creates a blood-oath that is basically he will kill Valentine on site.
the clave is all: okay with the evidence before us we don't know that Valentine is dead anymore. so if you see him try to capture him.
Alec: if I see him i'll try to remember to bring you a piece of his corpse. i'm a mama's boy even if she's not the best mom and he violated her consent and I am going to take it out of his hide. he is not my father.
the clave unable to argue since legally he's allowed to do this: ... well at least we don't have to worry about another uprising?
the clave: surely valentine's children won't be downworlders extremists as well? is this something we need to worry about?
Izzy growing up with Alec teaching her to hate everything Circle because it hurt their mom and fucked them over: screw shadowhunter politics. i'm going to live my best life and fuck a bunch of downworlders until my name becomes synonymous with a good time in the downworld. ha! take that Valentine. hows the legacy the kids you made created? is this what you wanted???
Everyone in the Clave: thank Raziel that Alec Trueblood is slightly more normal than his sister and just wants to tear apart his father and is known for killing and sometimes eating other nephilim (aka circle members).
Alec coming out as a consort to a Dominion King: excuse me. I may only fuck ONE downworlder but I do so in style. and I have the best taste.
Magnus and Alec bonding over hating their fathers and their father's hurting their mothers.
Magnus to Valentine: yes I am fucking your oldest. what are you going to do about it. nothing because he wants to kill you
-
but also experiment!Alec is amazing in so many different contexts and I really do enjoy using it because the timeline fits and it makes sense. I doubt Valentine experimented first on his own kid and while maryse wouldn't have been willing, Valentine knows how to lie very convincing. she wouldn't know they were anything but normal medical checks.
so it does make sense that Alec could have been experimented on and its very fun to play with the different things he could be or become.
especially if Alec develops them over time and its a steep learning curve.
thank you for dropping by the asks! this is very fun to talk about
<3 lumine
*mermaid Alec where alec haunts lake lynn until Magnus is called in. mermaid Alec where Magnus is lured to the beach on the waves of a sad song of yearning
i could go so many places
54 notes
·
View notes