#[METHOD = HTML ESCAPE]
Explore tagged Tumblr posts
Note
RESULT: [that's not my host] METHODS USED: [HTML ESCAPE]
Oooooo, who is your host? :D
Oh, their name's Frankie! They're the BEST, they're so much fun :D they've got problems moving and stuff so I help 'em with that and sometimes è̴͜ẋ̸͎p̷̘̎e̷̘͘r̶͖̅î̴͍m̸͔̃ë̵̲́ǹ̴̩t̶̠̓s̴̩̿-̵̮̉-̸̪̿
Sorry. Sorry. Not allowed. What I meant was, uh... sorry, forgot...
that's not my host
5 notes
·
View notes
Text

黄立羽[Kitateha] Polygonia c-aureum
黄[Ki] : Yellow
立[Tate] : 立てる[Tateru], to stand up, to erect
羽[Ha] : Wing
立羽 is 立羽蝶[Tatehachō], which means Brush-footed butterfly(Nymphalinae). Tateha is so named because it folds its wings and puts them up when perching on something. The length of the forewings is about three centimeters, and it is a common species. 蝶 means butterfly. It is 野紺菊[Nokongiku](Aster microcephalus var. ovatus) that Kitateha is perching on.
芥川龍之介[Akutagawa Ryūnosuke] wrote the following in the short story 羅生門[Rashōmon]. https://en.wikipedia.org/wiki/Rashōmon_(short_story)
どうにもならない事を、どうにかするためには、手段を選んでいる遑はない。
[Dō nimo naranai koto wo, dō nika suru tame niwa, shudan wo erande iru itoma wa nai.] There is no time to choose the means to deal with things that cannot be helped. Source: https://www.aozora.gr.jp/cards/000879/files/127_15260.html
It is possible to do that because humans are creatures that can move on their own. Plants, on the other hand, accept every situation as it is, and, 禅[Zen] has something in common with this.
In the winter of 1828, when a major earthquake hit Sanjō, Echigo Province (Niigata Prefecture today), Zen monk 良寛[Ryōkan](1758 - 1831) wrote the following in a letter to a stricken friend. https://en.wikipedia.org/wiki/Ryōkan
災難に逢ふ時���には災難に逢ふがよく候 死ぬる時節には死ぬがよく候 是は(これ)災難をのがるゝ妙法にて候
[Sainan ni au jisetsu niwa sainan ni au ga yoku sōrō Shinuru jisetsu niwa shinu ga yoku sōrō Kore wa (kore) sainan wo nogaruru myōho nite sōrō] When calamity strikes, it is good to be in calamity When the time is appropriate to die, it is good to die This is the excellent method of escaping from calamity Source: https://dl.ndl.go.jp/pid/957395/1/140
He also wrote the following poem.
花󠄁無心招蝶、蝶無心尋󠄁花󠄁、花󠄁開時蝶來、蝶來時花󠄁開、吾亦不知人、人亦不知吾、不知從帝則
[Hana wa mushin nishite chō wo maneki, chō wa mushin nishite hana wo tazunu. Hana hiraku toki chō kitari, chō kitaru toki hana hiraku. Ware mata hito wo shirazu, hito mata ware wo shirazu, shirazushite teisoku ni shitagau.] A flower mindlessly invites a butterfly, a butterfly mindlessly visits a flower. When the flower blooms the butterfly comes, when the butterfly comes the flower blooms. I do not know what is in people's heart, people do not know what is in my heart either. Unknowingly I follow the natural order of things. Source: https://dl.ndl.go.jp/pid/968898/1/210
20 notes
·
View notes
Note
Hi there! I'm a twine game developer and I noticed you'd converted your games to be used on Steam and the Google Play store. I'd love to ask a few questions about this, if that's okay? 1. What tools/methods did you use to convert your Twine game to APK? Did you come across any limits with file sizes and game dependencies? e.g. Images pushing you over the 100mb limit? 2. As above, but what tools/methods did you use to get Twine into an executable for Steam? Were there any hiccups here? 3. If you had to make a text-based game with gamified elements and graphics (and you wanted it on Steam/Android, and to retain screen reader capabilities) would you do it in Twine again, or would you use another engine or solution such as Ren'py, Godot, Unreal, etc? Thank you so much for your time!
Hi.
Under the cut, you'll find a list of videos and links that helped me put the game on Steam and Android.
Feel free to ask any questions as you go through the process—some steps aren't detailed here, as a few things currently escape my memory.
To be able to publish your game on Steam, Google Play, or Apple store, you need to create an account.
Follow the steps on this video to create an account on Steam:
youtube
Or this one:
youtube
This is the Steam work page to start:
Follow this step for google Play
youtube
Twine game needs to be repacked as app before you can publish them.
To repack your Twine games, use these steps:

For Google, you'll need an Android repacker. You can use this one below: (This site is not free)
Here is how to use it (Skip to 3:01 minutes)
youtube
For point #1, I had no issues with size or image limit. Steam does give you different ways to upload depending on the size of your game.

For point #2, there will be hiccups and errors when you try to complete this checklist on Steam, but again, watch the videos and send some questions my way, I'll help as much as I can.

For point #3, I have no idea about the Screen Reader part. I know Twine is good for it, but personally, I don't plan on using Twine any longer, I'm moving to Renpy because it's are easier for me as of now.
Side note: Be sure to watch even more videos than those listed and don't hesitate to do additional research on Google whenever you feel stuck. Most questions and answers are already out there, so a quick search can often point you in the right direction.
If you still need help, feel free to send your questions my way!
14 notes
·
View notes
Text
Unlocking the Possible of a Home Organization: Your Path to Financial Flexibility
In today's fast-paced globe, the idea of a home based business has gained enormous popularity, offering individuals the chance to escape the standard 9-to-5 work and embrace a more adaptable lifestyle. With advancements in modern technology and the increase of remote job, starting a home organization has never been even more accessible. Whether it's selling handcrafted crafts online, giving consulting services, or releasing an ecommerce shop, the possibilities are unlimited. A home based business not just permits you to function from the comfort of your own space however additionally encourages you to pursue your enthusiasms while creating income.However, introducing a successful home based business requires mindful preparation and devotion. It's vital to determine your specific niche, understand your target audience, and create a solid business strategy. Furthermore, leveraging electronic marketing methods can aid you reach a bigger audience and stand apart in an open market. As you start this business journey, keep in mind that determination and versatility are crucial. With the ideal state of mind and sources, your home service can grow, providing you with both economic safety and security and the liberty to live life on your very own terms.
Read more here https://92w.z4.web.core.windows.net/dropshipwebhosting/privatelabel/Access-Your-Account-Here-505.html
0 notes
Note
RESULT: [stop] METHODS USED: [HTML ESCAPE]
Hi! You know everyone! That's so cool, I barely know anyone! :0
@splitsquip
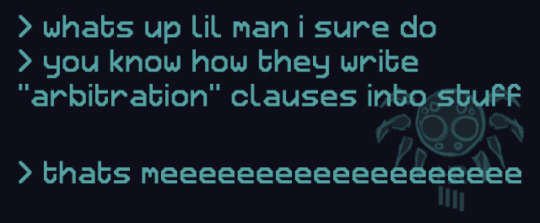
NOTICE TEXT:
whats up lil man i sure do you know how they write "arbitration" clauses into stuff
thats meeeeeeeeeeeeeeeeeee
8 notes
·
View notes
Text
Unlocking the Prospective of a Home Based Business: Your Course to Financial Flexibility
In today's hectic globe, the idea of a home based business has obtained tremendous appeal, using individuals the possibility to escape the traditional 9-to-5 work and welcome an extra adaptable way of living. With advancements in innovation and the increase of remote work, beginning a home based business has never been even more obtainable. Whether it's marketing handcrafted crafts online, supplying consulting services, or introducing an e-commerce store, the possibilities are unlimited. A home business not only enables you to work from the convenience of your very own area however additionally equips you to seek your interests while generating income.However, releasing a successful home service calls for cautious planning and commitment. It's important to identify your particular niche, comprehend your target audience, and develop a strong organization strategy. Additionally, leveraging digital advertising methods can assist you get to a broader target market and stick out in an affordable market. As you start this entrepreneurial journey, bear in mind that determination and versatility are crucial. With the ideal state of mind and sources, your home based business can grow, offering you with both economic safety and the freedom to live life by yourself terms.
Read more here https://92w.z4.web.core.windows.net/dropshipwebhosting/privatelabel/Access-Your-Account-Here-505.html
0 notes
Text
Securing Your Full Stack Python Development Application

Security is a crucial consideration in every Full Stack Python development project. Whether you are building a simple web app or a complex enterprise solution, safeguarding your application from potential threats is essential. A security breach can lead to compromised data, reputational damage, and financial losses. In this blog, we'll discuss best practices for securing your Full Stack Python development applications.
1. Secure Your Backend with Authentication and Authorization
Authentication and authorization are the first lines of defense in securing a Full Stack Python development application.
Authentication is the process of verifying the identity of a user. A common practice is to implement JWT (JSON Web Tokens) or OAuth for managing user sessions. Using these methods allows users to log in securely and ensures their identity is validated across different services.
Authorization determines what actions a user can perform once authenticated. Use Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to limit access based on user roles or attributes. For example, an admin might have full access to manage data, while regular users can only view it.
Tools like Django come with built-in user authentication systems, while Flask can be integrated with extensions like Flask-Login to handle user authentication and sessions securely.
2. Protect Sensitive Data with Encryption
Sensitive data such as passwords, credit card information, and personal data should never be stored in plain text. Always use encryption to protect this data:
Password Hashing: Use a hashing algorithm like bcrypt or Argon2 for securely storing user passwords. This ensures that even if the database is compromised, attackers cannot retrieve the original passwords.
SSL/TLS Encryption: Secure data transmission by using SSL/TLS protocols. This ensures that any data exchanged between your users and servers is encrypted and protected from man-in-the-middle attacks. Use HTTPS instead of HTTP to secure the communication channel.
Database Encryption: Sensitive data stored in the database should also be encrypted at rest. AES (Advanced Encryption Standard) is a commonly used algorithm for encrypting sensitive data in storage.
3. Prevent Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF)
Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) are common web application vulnerabilities that can compromise the security of your Full Stack Python development application.
XSS occurs when an attacker injects malicious scripts into web pages that other users will execute. To prevent XSS:
Always sanitize user input and escape output.
Use modern frameworks like Django or Flask that automatically escape content, or rely on libraries like Bleach to filter potentially dangerous HTML tags.
CSRF is an attack where a malicious website tricks a user into performing actions on a web application where they are authenticated. To prevent CSRF:
Use anti-CSRF tokens in your forms. Both Django and Flask provide middleware to protect against CSRF attacks automatically.
Ensure that sensitive actions (like changing a password) are POST requests with CSRF protection enabled.
4. Use Secure Cookies and Sessions
When managing user sessions, cookies can be a potential attack vector. Follow these best practices to secure cookies in your Full Stack Python development project:
HttpOnly Flag: Set the HttpOnly flag to prevent client-side JavaScript from accessing cookies, reducing the risk of XSS attacks.
Secure Flag: Set the Secure flag to ensure cookies are only sent over HTTPS, preventing man-in-the-middle attacks over unsecured networks.
SameSite Attribute: Set the SameSite attribute to Strict or Lax to prevent cookies from being sent in cross-site requests, thereby mitigating CSRF risks.
5. Regular Security Audits and Vulnerability Scanning
Regularly auditing your application and performing vulnerability scanning is critical for identifying and addressing potential security flaws.
Static Code Analysis: Tools like Bandit for Python can help you analyze your code for security vulnerabilities such as hardcoded passwords, improper input validation, and potential injection points.
Dependency Management: Ensure that all libraries and packages you use are up to date. Tools like Dependabot and Snyk help monitor your dependencies for known vulnerabilities, ensuring your application remains secure as external packages evolve.
Penetration Testing: Conduct regular penetration tests to identify any weaknesses in your app’s security posture. Pen testing tools like OWASP ZAP can automate much of the process, allowing you to uncover vulnerabilities before attackers can exploit them.
6. Secure Your APIs
In Full Stack Python development APIs are often a central part of the application architecture, especially when using a microservices architecture. Securing your APIs is critical to protecting your application from unauthorized access.
API Authentication: Use secure methods like OAuth2 or API keys to authenticate API requests. OAuth2 is commonly used to authorize access across different services in Full Stack Python development.
Rate Limiting: Implement rate limiting to prevent abuse of your APIs. This limits the number of requests a client can make within a specific period, reducing the risk of denial-of-service (DoS) attacks.
Input Validation: Always validate and sanitize API input to prevent SQL Injection and other injection attacks. Use frameworks like Marshmallow or Pydantic for validating incoming data and ensuring it adheres to the expected format.
7. Handle Error Logging and Monitoring
Proper error handling is essential for both user experience and security. Avoid exposing detailed error messages to end-users, as they can provide attackers with valuable information.
Error Handling: Ensure that error messages are generic, such as “Something went wrong,” and log the full error details in a secure logging system that only authorized personnel can access.
Logging: Use secure logging practices, storing logs in a separate server or cloud service. Tools like Sentry or Loggly can help you collect, analyze, and respond to errors in real-time.
Monitoring: Implement continuous monitoring using tools like Prometheus, Grafana, or New Relic. These tools provide insights into application health, enabling you to detect anomalies and respond to potential security breaches swiftly.
8. Regular Updates and Patches
Software vulnerabilities are discovered regularly, making it essential to keep all components of your Full Stack Python development application updated:
Python Updates: Always use the latest version of Python, which includes important security fixes. Set up alerts for new Python releases, and upgrade your application when security patches are released.
Package Updates: Regularly update your project’s dependencies and libraries. Use package managers like pip or Poetry to ensure that you’re always running the most secure versions of external packages.
Conclusion
Securing your Full Stack Python development application requires a multi-layered approach that includes securing authentication and sessions, encrypting sensitive data, preventing common vulnerabilities, and implementing secure APIs and error handling practices. By following these best practices and continuously monitoring and updating your application, you can build a robust security posture that protects your users and data from potential threats. Security should be a priority throughout the development lifecycle, ensuring that your application remains safe, trustworthy, and resilient.
0 notes
Text
API Security Best Practices Checklist
Introduction
In the realm of modern web applications, APIs (Application Programming Interfaces) play a crucial role in connecting various systems and enabling seamless data exchange. However, the convenience of APIs comes with significant security challenges. Securing APIs is paramount to safeguarding sensitive data and maintaining the integrity of systems. In this article, we delve into API security best practices to ensure your applications are fortified against potential threats.

Authentication and Authorization
Implement Strong Authentication Mechanisms
Authentication is the cornerstone of API security. Utilize robust authentication methods such as OAuth 2.0 or JWT (JSON Web Tokens) to verify the identity of clients accessing your APIs. Ensure credentials are transmitted securely over HTTPS to prevent interception by malicious actors.
Role-Based Access Control (RBAC)
Authorization defines what authenticated users are permitted to do within your API ecosystem. Implement RBAC to enforce least privilege access, granting permissions based on roles and responsibilities. Regularly review and update access control policies to reflect organizational changes and minimize security risks.
Secure Communication
Transport Layer Security (TLS)
Secure data transmission between clients and servers using TLS (Transport Layer Security). TLS encrypts data in transit, preventing eavesdropping and tampering. Always enforce the use of HTTPS for API endpoints to protect sensitive information from interception.
API Gateway
Deploy an API gateway to centralize control and security policies across API services. A gateway acts as a single entry point for client requests, enabling functionalities such as rate limiting, logging, and request validation. Configure your API gateway to authenticate clients and validate incoming requests before forwarding them to backend services.
Input Validation and Output Encoding
Input Validation
Validate and sanitize all input parameters to mitigate SQL injection, cross-site scripting (XSS), and other injection attacks. Implement strict input validation routines on both client and server sides to ensure only expected data formats are processed by your APIs.
Output Encoding
Encode output data to prevent malicious scripts from executing on client browsers. Use encoding mechanisms such as HTML entity encoding or JavaScript escaping to neutralize potential XSS payloads embedded in API responses.
Logging and Monitoring
Comprehensive Logging
Maintain detailed logs of API activities, including request parameters, user identities, and response statuses. Logging helps in auditing and forensic analysis during security incidents. Ensure log entries are securely stored and accessible only to authorized personnel.
Real-time Monitoring
Implement real-time monitoring to detect suspicious activities or anomalies in API traffic. Leverage SIEM (Security Information and Event Management) solutions to correlate events across your infrastructure and trigger alerts for potential security breaches.
Security Testing and Continuous Integration
Automated Testing
Integrate security testing into your CI/CD pipelines to identify vulnerabilities early in the development lifecycle. Conduct regular penetration testing and vulnerability assessments to evaluate the resilience of your APIs against evolving threats.
Secure Development Lifecycle (SDLC)
Adopt a secure SDLC approach by integrating security practices from design through deployment. Educate developers on secure coding practices and conduct regular security training sessions to foster a security-aware culture within your organization.
Compliance and Governance
Regulatory Compliance
Adhere to industry-specific compliance requirements such as GDPR, HIPAA, or PCI DSS when handling sensitive data through APIs. Implement controls to protect data privacy and ensure lawful processing of user information.
Security Governance
Establish robust security governance frameworks to define policies, procedures, and controls governing API security. Conduct periodic security assessments and audits to validate compliance with internal policies and external regulations.
Incident Response and Recovery
Incident Response Plan
Develop and maintain an incident response plan outlining procedures to address security breaches affecting your APIs. Define roles and responsibilities for incident responders and establish communication protocols for notifying stakeholders.
Disaster Recovery
Implement disaster recovery measures to restore API services in the event of a security incident or infrastructure failure. Maintain backups of critical data and configurations to facilitate rapid recovery and minimize downtime.
Conclusion
Effective API security requires a proactive approach encompassing authentication, authorization, secure communication, input validation, monitoring, and compliance. By adhering to these best practices, organizations can mitigate risks associated with API vulnerabilities and uphold the trust of users and stakeholders.
For more information on securing your APIs, consult with our team of security experts who specialize in safeguarding digital assets against emerging threats.
0 notes
Note
CHUNK 1 RESULT: [don't trust him] METHODS USED: [HTML ESCAPE]
CHUNK 2 RESULT: [manipulator. liar.] METHODS USED: [HTML ESCAPE]
CHUNK 3 RESULT: [NOT SAFE NO] METHODS USED: [HTML ESCAPE]
Hi! You know things, right? I don't know a lot... could you teach me? :0
don't trust him
@splitsquip

} I am happy to. The universe is magnificent. It is unchanging, uniform, perfect, necessary, timeless, and neither generated nor perishable. You are the universe, and the universe is you. There is so much world beyond the stars, and beyond the sea. There is so much pain that we can solve, to save the universe from this darkness. I can help you see the light.

} who am I not to trust?
17 notes
·
View notes
Text
Best Practices for Ruby on Rails Website Security

Ruby on Rails (RoR) has emerged as a popular framework for web development due to its simplicity, flexibility, and productivity. However, like any other web application, Ruby on Rails websites are vulnerable to security threats such as SQL injection, cross-site scripting (XSS), and unauthorized access. In this article, we will explore best practices for ensuring the security of Ruby on Rails websites, with a focus on mitigating common vulnerabilities and protecting sensitive data. As a leading ruby on rails web development company usa, it is crucial to prioritize website security to safeguard client interests and maintain trust.
Secure Authentication and Authorization
Authentication and authorization are fundamental aspects of website security, especially for applications that handle sensitive user data or require user authentication. In Ruby on Rails, developers can leverage the built-in authentication mechanisms provided by gems like Devise or implement custom authentication solutions using the has_secure_password method. It is essential to use strong cryptographic algorithms for password hashing and enforce secure password policies to prevent brute-force attacks. Additionally, implementing role-based access control (RBAC) ensures that users only have access to the resources they are authorized to access, reducing the risk of unauthorized data access.
Input Sanitization and Parameterized Queries
One of the most common security vulnerabilities in web applications is SQL injection, which occurs when malicious SQL queries are inserted into input fields and executed by the database. To prevent SQL injection attacks in Ruby on Rails applications, developers should employ input sanitization techniques and use parameterized queries when interacting with the database. By sanitizing user input and using placeholders for dynamic values in SQL queries, developers can mitigate the risk of SQL injection attacks and ensure the integrity of the database.
Cross-Site Scripting (XSS) Prevention
Cross-Site Scripting (XSS) is another prevalent security vulnerability that can compromise the integrity and confidentiality of web applications. XSS attacks occur when malicious scripts are injected into web pages and executed in the context of unsuspecting users, allowing attackers to steal sensitive information or perform unauthorized actions on behalf of the user. To prevent XSS attacks in Ruby on Rails applications, developers should implement input validation and output encoding techniques to sanitize user input and escape special characters that could be interpreted as HTML or JavaScript code. Additionally, leveraging Content Security Policy (CSP) headers can help mitigate the impact of XSS attacks by restricting the execution of inline scripts and external resources.
Cross-Site Request Forgery (CSRF) Protection
Cross-Site Request Forgery (CSRF) attacks exploit the trust between a user and a website to execute unauthorized actions on behalf of the user without their knowledge. To prevent CSRF attacks in Ruby on Rails applications, developers should implement CSRF protection mechanisms such as CSRF tokens or SameSite cookies. By generating unique tokens for each user session and validating them with each form submission or AJAX request, developers can ensure that requests originate from legitimate sources and mitigate the risk of CSRF attacks.
Secure Session Management
Session management is a critical aspect of website security, as it involves maintaining the state of user authentication and authorization across multiple requests. In Ruby on Rails applications, developers should ensure that session cookies are encrypted and signed to prevent tampering or session hijacking attacks. Additionally, it is essential to implement proper session expiration policies and invalidate sessions after a specified period of inactivity to reduce the risk of unauthorized access.
Conclusion: Prioritizing Ruby on Rails Website Security
In conclusion, ensuring the security of Ruby on Rails websites is essential for protecting sensitive data, maintaining user trust, and mitigating the risk of security breaches. By following best practices such as secure authentication and authorization, input sanitization, XSS prevention, CSRF protection, and secure session management, ruby on rails website development company usa, can build robust and resilient web applications that withstand common security threats. By prioritizing website security from the outset of the development process and staying abreast of emerging threats and vulnerabilities, developers can create secure and reliable Ruby on Rails applications that meet the highest standards of security and compliance.
#ruby on rails web development company usa#ruby on rails website development company usa#ruby on rails web development services usa
0 notes
Text
Unlocking the Marvels of Travel: A Trip to Discover the Globe
""
Paragraph 1: Taking a trip is even more than simply visiting brand-new areas; it is a transformative experience that widens our perspectives, enhances our lives, as well as permits us to find the wonders of the world. Whether it's exploring busy cities, submersing in various societies, or venturing right into awesome natural landscapes, travel uses us the opportunity to break without our daily regimens as well as embrace the unidentified. From the minute we tip foot on an aircraft or begin on a trip, we embark on a journey that opens our minds, stimulates our curiosity, as well as produces memories that last a lifetime.Paragraph 2: Among one of the most amazing facets of traveling is its capability to challenge us and also press us out of our convenience zones. It urges us to encounter our fears, adapt to brand-new atmospheres, and also connect with individuals from diverse backgrounds. Traveling shows us important life lessons, such as strength, perseverance, and open-mindedness. It allows us to establish a deeper understanding and admiration for different cultures, practices, and also methods of life. Moreover, it provides us the chance to see the world via a different lens, to witness the beauty of nature, and to wonder at the building marvels produced by humankind.In verdict, traveling is not merely a pastime or a method of leisure; it is a crucial
part of individual growth as well as self-discovery. It allows us to escape the ordinary and also begin on remarkable adventures. So, let's load our bags, get out of our convenience areas, as well as unlock the marvels of travel, for it is through these experiences that we genuinely discover to live, love, as well as appreciate the unbelievable globe we inhabit.
Read more here https://dive-batu-bolong.s3.amazonaws.com/what-is-the-adventure-of-experiencing-dive-batu-bolong-2.html
0 notes
Text
How Toei wanted to make their own ver. of Silver Surfer in the early 80′s (Get ready because it’s about to get wild)
All the information I’ve gotten is in this one blog here, documenting about what Toei and Marvel were collabing on at the time: https://spider-man.at.webry.info/200802/article_3.html
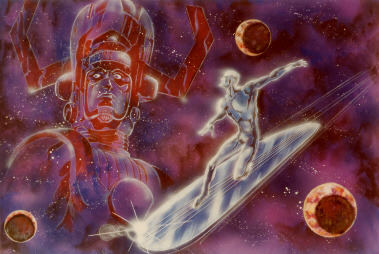
From the blog in the link above:
‘As mentioned in this blog several times before, after Spider-Man aired from 1978 to 1979, Toei planned and considered several programs using Marvel characters, including 3-D Man, Moon Knight and Silver Surfer. We introduced 3-D Man (26 May 2007) and Moon Knight (14 January 2008), but Silver Surfer had not yet been introduced, so we thought we would introduce it sooner or later, but the other day we happened to receive a copy of the "New Programme Proposal" that resulted in Silver Surfer's death. I was planning to introduce it sooner or later, but I happened to get a copy of the Silver Surfer's lost 'New Programme Proposal' the other day, so I'll write about it this time, weaving in its contents as I go along.
This is the Silver Surfer proposal. Four colour photos of the main characters are attached.

The show is a colourful and varied action series centered on three Marvel Comics heroes - Silver Surfer, Ms Marvel and The Thing - and features Marvel characters from time to time, plus original characters from Japan.
Title: Silver Surfer Type: SF hero action film Format: TV film with extensive use of VTR synthesis, 30-minute complete episodes, 26 or more episodes. Target audience: Young people and other families in general. Based on the novel by Saburo Hate (from the Marvel Comics version) Planning cooperation: Kikakusha 104 Production: Toei Co.
Planning details The Great Invasion Army, led by the space emperor Galactus, extends its power across the universe. Their next target is our home planet, Earth. At ・・・・・, Ms Marvel and The Thing, who belong to the Japan Branch of the Independent Strategy Office, have a fateful encounter with the superhero Silver Surfer, who has escaped from Galactus' army to Earth, and are told by him of the enemy's true intentions. The three are united by a strong sense of comradeship and rivalry as they face their giant enemy.
Introduction of the characters

Silver Surfer (Koushi Shibuki). A silver-coloured alien who pilots a surfboard named Skyboard and travels through space at the speed of light. He was a resident of the planet Zen Ra, but was captured when an invasion force destroyed the planet and converted into a space combat soldier in the psychic strategic development section. After being converted, he attempted to escape to his late mother's planet.
Fights enemies with Cosmic Power, an ability that allows him to manipulate cosmic energy. Cosmic Blast = Attacks by firing energy blasts from the fingertips. Cosmic Burst = Energy discharge generated from both hands spread wide. Cosmic Attack = The strongest attack method, in which the energy stored in the body is released, the entire body is enveloped in energy and the attacker strikes with the body. However, this technique drains all of Silver Surfer's energy and can only be used once in battle, as he has no attack ability for "one hour" until the Cosmic Energy is charged up in his body again.
Usually a young man who enjoys ocean sports, mainly surfing. When he catches sight of an enemy invasion, he heads for the battlefield as a warrior Silver Surfer. His father is from the planet Zen Ra and his mother is from Earth.

Miz Marvel (Masumi Suzuka). An Earth superheroine with inherently superior precognition and clairvoyant abilities. In everyday life, she is a female university student who works part-time at a coffee shop frequented by Koushi Shibuki. She is actually the daughter of the wealthy Suzuka family.

Thing (Gen Ishihara). A power fighter who punches with great destructive power, defeats his enemies with great monstrous strength, and is an earthling who specialises in ground combat. He is usually a truck driver. He often frequents the coffee shop where Suzuka Masumi works part-time. During the investigation of a previous case, he was involved in an explosion at an enemy hideout, at which time he was exposed to special energy along with a monstrous beam of light, and became a superhuman with immeasurable power.
That's roughly how it went down. The rest of the book contains information about the 'Independent Strategy Office of the Earth Defence Organisation' to which the three belong, an introduction to the 'Galactus Army', a sample story of the first episode, and so on. We will introduce this proposal when we have a chance.
-----------------------------------
By the way, I looked into this lost project to see if it was utilized in any later Toei special effects programs, and found some matching settings in Space Detective Gavan, which was broadcast from March 1982. The Gavan project started in the spring of 1981, around the same time as Silver Surfer. The story is about the defense of peace in space, which is a different dimension from existing heroes. He wears a silver combat suit. He emits rays of light from his fingertips. His father is an alien and his mother is from Earth. He rides in a sidecar (Cyberian), reminiscent of the Silver Surfer.
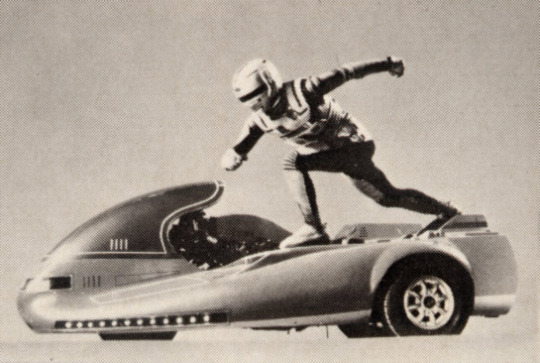
[Image reference.]
There may be more, but I don't think I'm the only one who feels that this is similar. However, I haven't seen any reference book that states the fact that the 'Silver Surfer' setting was used for 'Gavan', so this is a matter of speculation.’
------------------------------------- End of Translation
So that was my find of this info. All while I’m trying to find info of ‘Tomb of Dracula’ anime animated by Toei so I tried to find info on Google using Dracula’s Japanese title and lo and behold, I found this blog that has quite the info on it.
Next time, info on ‘Tomb of Dracula’ anime movie and how Harmony Gold crammed WAAAY Too much story into a condensed movie that was different in the intended way by Toei.
#toei tokusatsu#toei#Marvel Comics#marvel#silver surfer#jack kirby#1980s#80s#superheroes#tokusatsu#Toei and Marvel Collab#40th anniversary Metal Heroes#Metal Heroes#space sheriff gavan#Metal Heroes 40th#comic book heroes#comic books
41 notes
·
View notes
Text
Malice and greed make a bad combination
Here’s another article for this quarter.
Source:
https://www.hrxfw.com/fjgs/yggs/353586.html
TRANSLATION STARTS
An evil woman harms her mother-in-law and ultimately causes her own demise
Once upon a time, there lived a Brahman with a young and beautiful wife who was lascivious and adulterous (For further reading on the Brahman caste in India - https://www.britannica.com/topic/Brahman-caste). Whenever the Brahman traveled to make a living, his wife would seek out lovers for a good time. However, she had a mother-in-law who was mindful of the code of conduct for women, and this limited the extent of her adultery. To make merry to her heart’s content, the Brahman’s wife sought ways to get rid of her mother-in-law. One day, after much pondering, she finally came up with an evil plan.
To make her husband let down his guard, she pretended to be a dutiful daughter-in-law, tending to the Brahman’s mother’s every need from morning to night, from providing delicious food and fine clothing, performing every chore in the household, to flattering her with terms of endearment and praise. This made her mother-in-law very happy and proud to have such a filial daughter-in-law.
One day, upon returning from a trip, the Brahman was pleased to witness the meticulous care which was given to his mother by his wife and said, “You’re truly a filial daughter-in-law to treat my mother with such care. I am truly blessed to have married such a fine woman as you.”
His wife replied, ”As much as I would like to provide the best for your mother, I can only give her the things which are obtainable on this earth, and this is a mere pittance. If we could provide her with the wonderful delights which are only found in Heaven, that would be true filial piety. Tell me, is there a way for us to send her to Heaven?”
The Brahman was impressed with his wife’s display of “filial piety” which went beyond the provision of earthly pleasures by attempting to provide heavenly enjoyment. Pausing to think, the Brahman suggested, “According to Brahman teachings, if one desires to ascend to the heavens, one can jump down from a rocky mountain, or jump into a bonfire. A person who jumps down from a rocky mountain can float in the air and ascend to the heavens; a person who jumps into a bonfire can make use of the rising flames to support his soul’s ascent to the heavens.”
His wife replied, “I wish I had known that it was so easy to ascend to the heavens. Why don’t we try these methods on your mother? This would allow her to enjoy eternal bliss in Heaven. It would be unfilial of us to keep her here on the human realm to dine on unworthy viands.”
The Brahman agreed with his wife’s suggestions and the two of them made preparations for his mother’s ascent.
A few days later, the Brahman made a deep and large pit in the wilderness, filled it with dried twigs and grass, and set the pit ablaze. To keep the fire going, he added firewood and chaff to the pit. Next, he brought his mother to the pit, and invited his relatives and friends to a ceremony held at the site. Everyone feasted, drank, sang and danced at a banquet which lasted for a day.
When night fell, the crowd dispersed, leaving the Brahman, his wife and his mother at the site. The couple brought the Brahman’s mother to the pit, and said, “Mother, we will now send you to Heaven.” Without waiting for an answer, they pushed the old woman into the pit and returned home.
By a stroke of luck, the men who were hired by the Brahman to dig the pit made a trough by the side of the pit as a makeshift terrace to climb back up, and the Brahman’s mother fell into this trough, thus avoiding a fiery end in the bonfire. Climbing her way to safety, the Brahman’s mother escaped from the pit.
By the time she made it out of the pit, it was already pitch dark in the wilderness, so the old woman had to rely on her memory of the route taken during the day to find her way back. As she passed by a sinister-looking forest, animal calls echoed in her vicinity, making her tremble with trepidation. Fearing wolves, tigers, Rakshasas and venomous snakes, she decided against venturing further, opting instead to climb up a huge tree and wait for dawn before continuing her journey home (For further reading on Rakshasas - https://www.britannica.com/topic/rakshasa).
After some time, a gang of robbers who had completed a heist made their way into the forest to split the loot and gathered under the tree from which the Brahman’s mother watched. She was too afraid to move, fearing for her life lest the robbers discovered her, but anxiety made it hard for her to avoid making a sound, and finally she coughed heavily from the branches above. Already jumpy from their criminal misdeeds, the robbers were shocked by her cough and thought an evil forest spirit had detected their presence. Scattering from their hiding spot and running away for their lives, they left their ill-gotten gains at the base of the tree.
At the crack of dawn, the old woman climbed down from the tree and discovered a cache of riches. It was much more than she could possibly carry, so she selected small items such as ivory, pearls, gold bracelets and earrings before returning home.
Pushing the door open, the old woman’s disheveled appearance terrified the Brahman and his wife, who backed away thinking that the old woman’s ghost had returned for vengeance. The Brahman’s mother said, “Do not be afraid. I was in Heaven last night and I have decided to return this morning. While I was in Heaven, our relatives who had also ascended presented me with many precious gifts which I have brought down to show you. Take a look at these fine treasures!” Opening a bundle and pointing to the jewelry which lay within, she said to her daughter-in-law, “Look at the ivory, pearls, gold bracelets and earrings! They are gifts from your parents and aunts. They wanted to give me many more gifts, but how much more can an old woman like me possibly carry? When I left Heaven this morning, they bade me farewell and expressed their desire to give you many more gifts if you ascended to Heaven too.”
The old woman’s words made the Brahman’s wife’s eyes lit up with amazement. Seizing the opportunity to make a huge windfall, she pestered her husband all day to conduct the ascension ceremony for her as well. The Brahman acceded to her request and threw another banquet at the pit, reviving the bonfire and happily pushing his wife into the flames. But this time, the Brahman’s wife was not as lucky as her mother-in-law. She missed the trough and instead fell into the deep recesses of the pit where she was quickly engulfed by the bonfire.
The Brahman waited many days at home for his wife’s return from Heaven but she never came back. Sighing continuously, he complained to his mother, assuming that his wife must have been enjoying herself too much in Heaven to remember him.
-- Excerpt from the Sutra of Miscellaneous Jewels
TRANSLATION ENDS
2 notes
·
View notes
Text
so i tried what @nicolemaiines suggested but in the folder, instead of giving me a separate folder with the gif files or just listing them right there, it generated a .DOWNLOAD file ???? which i cannot read, i tried. i tried to save the page using the same method but with internet explorer (i refuse to use its new name) and same thing; with firefox it did give me the actual image files but in the clunkiest way possible and using .webp as an extension (which apparently means i only had the first frame) for most of the gifs. not sure why.
BUT
i just found a roundabout way to do it, for now. my main issue with what @uservicky suggested is that while yes i know where the gif urls are, they're hidden in tumblr's really clunky json formatting due to NPF, so it's there but it still was gonna take too long
today i stumbled on tumblr mirror sites such as tumbex, and i tried playing with that for a bit and found out that you can open the mirrored post even if tumblr has hidden it due to content rules so long as you have the post number and the post still exists. so then i tried opening that and when i downloaded it, what nicolemaiines suggested does in fact work as it should, BUT ALSO the page source is itself readable and it's formatted in an html-friendly way, meaning i can do what i originally wanted to do which is to copy-paste the html into my own tumblr post in my gif hunt dump blog so i can keep that
granted, tumblr now has an image limit per post i believe, iirc it's 30? and that means approx 10 to 20 posts per gif hunt i'm trying to save, but it's a LOT easier
so step by step (in purple what changes according to your post you wanna save):
yoink the post permalink - the one that's like tumblr.com/blogurl/bunchofnumbers/post-title
format the original url you just copied so it's tumbex.com/blogurl.tumblr/post/bunchofnumbers
go nuts i guess lol
if you go into the page source, you gotta scroll down a bit (the post technically appears in the <head></head> section but i don't know if the entire post is there or not, didn't check that closely - that's not the actual body of the webpage)

you'll find the post in what looks like the yellow square above (it's preceded by blog info about who posted it, so like their url, description, pfp, etc.) and then the actual gifs are what's in the red square
if you select the text in that red square, it's got some escape characters you wanna delete, marked in red here
{"url":"https:\/\/64.media.tumblr.com\/tumblr_mbid64mx4d1rt6nee.gif","height":375,"width":500,"type":"image"},
and some information you don't need, so just delete everything marked in red here:
{"url":"https://64.media.tumblr.com/tumblr_mbid64mx4d1rt6nee.gif","height":375,"width":500,"type":"image"},
so it's just this:
https://media.tumblr.com/tumblr_mbid64mx4d1rt6nee.gif
and you get a proper gif that you can either open in a new tab or post on tumblr by pasting the url itself:

and that's it :)
does anyone know how to download large gif hunts? there's a specific set of gif hunts that i used to use a lot and the blog that posted them seems to have been abandoned, so i'm hoping to save those gifs before it gets deleted (if it does, i hope it doesn't)
the problem is each post has 100+ gifs so downloading them one by one manually is a process and i just don't have the patience for that x10
the other problem is that the blog has been flagged as nsfw meaning i can't actually open the gif hunt in the url dot tumblr dot com page, making it functionally a dash-only blog even though i know it isn't
i've already tried to open the post in its own tab and save the webpage but it's just not giving me the gifs that way. i can access them via the inspect element console but it won't let me download them from there, which ???? i feel like it should. i can download the html-only source for the page but then i'm having a Time figuring out how to get just the gif urls from that, and then how to like actually download them instead of going one by one. this feels like there's some sort of macro that could be written or some easier way i am somehow missing
help????? this is The andy biersack gif repository set of posts and i dunno what to do lol
#downloading gifs#downloading posts#indie rp#reference#ooc#idk hopefully those tags help someone find it
5 notes
·
View notes
Photo

Extracting energy from black holes the Penrose way The idea of extracting energy from a black hole may seem like extracting blood from a stone as a black hole may be characterised as a region of “no escape”. However the famous physicist and mathematician Roger Penrose proposed just a way to do that and in the process offered some deep insights in to the physics of a black hole.
What is called the’ Penrose process’ applies to rotating Kerr black holes only and not their non-rotating cousins, Schwarzschild black holes. One of the essential physical differences between a Kerr black and a Schwarzschild black hole is that outside of the event horizon of a Kerr black hole there is another surface called the ergosphere. Inside of the ergosphere all matter is compelled to rotate by the black hole’s angular momentum, however particles inside of the ergosphere (but outside of the event horizon) may still escape from the black hole. [Warning: the following paragraph is a brief detour for the more theoretically minded!]The concept of energy in advanced physics is a little bit more difficult to pin down than one might expect. In general relativity the problem comes from having to define energy in curved spacetime and made much more difficult in that some of the energy (gravitational energy) is tied up in the curvature of spacetime itself. However thanks to the spacetime describing a Kerr black hole possessing a nifty property known as ‘asymptotic flatness’, the total energy of a Kerr black hole can be defined with little risk of contradiction. In layman’s terms the total energy of a Kerr black hole is the total energy as observed by someone sufficiently faraway as to be free of its gravitational effects. From an ‘up close and personal’ point of view particles must always have positive energy (realistic ones that is), but an interesting effect on particles in the ergosphere of a Kerr black hole is that from the point of view of a faraway observer their energies may appear to either positive or negative. Penrose’s scheme for energy extraction of a black hole takes advantage of this fact. The Penrose process can be summarized as follows: An observer faraway from a Kerr black hole sends a particle in to the ergosphere of the black hole where it is split in to two ‘fragments’; one of positive energy and one of negative energy. The positive energy fragment then returns to the faraway observer, whilst the negative energy fragment (necessarily) falls in to the black hole. The positive energy fragment will have more energy than the particle that was original sent, whilst the negative energy fragment will reduce the total energy and therefore mass of the black hole. A similar process can be applied to waves (e.g. light waves, gravitational waves), this is known as superradiant scattering. An effect of the Penrose process is to also reduce the angular momentum of the black hole and therefore it is not possible to extract the total energy of a black hole using Penrose’s method. A black hole would stop rotating and lose its ergosphere long before all of its energy had been extracted. The portion of mass of a black hole which cannot be extracted by the Penrose process is known as the irreducible mass of the black hole. An interesting postscript is that once quantum effects are brought in to play, it was shown that a Kerr black hole will spontaneously radiate its energy away (without the need of outside intervention) by the quantum equivalent of superradiant scattering. Stephen Hawking showed shortly after that if quantum effects are brought in to play on a non-rotating Schwarzschild black hole that even it will radiate its energy away as Hawking radiation. -John Davis Reference: General Relativity by Robert M Wald 1984 http://arxiv.org/abs/astro-ph/0404135 Image: Picture: A quasar ‘fires’ a narrow jet a million light years long and travelling only a tiny fraction below the speed of light in to a gas cloud. The Penrose process has been put forward as possible method by which quasars, supermassive black holes surrounded by a dense region of matter which power them, eject thin jets of extremely high energy particles. (Source: NASA http://apod.nasa.gov/apod/ap010905.html) https://bit.ly/32165nn
69 notes
·
View notes
Text
hey uhhhhh remember when i said that the world building in shera sucked really bad i needed to not think too much into it? 🤡
anyway i was trying to board an expanded lore comic for the horde but it wasnt coming along.... so i wrote out a basic backstory for horde prime...... posted under the cut because the comic is still happening but its not coming out before i have t go back to work again lmao
Horde prime was born on a planet that is now long dead. His species originally had wings and tails even as adults. The culture that he was born into was similar to the culture on etheria in that there was diverse ethnic groups, song, dance, entertainment, no transphobia or homophobia, war, and strife. He was trained as a soldier and in war tactics but became disillusioned with war as a concept and wanted only peace.
He left the army and started preaching pacifism. He gained enough followers of his teachings to begin a small commune that would eventually become a cult. He preached to his followers like they were apart from the larger problems of the world but his commune was eventually attacked by the enemy that he had scorned fighting before. They take horde prime and some members captive, horde prime attempts to preach to them about peace but they do not listen. Though it pains him to do so, horde prime goes from thinking that he could live in his own little peaceful world to thinking that it is his duty to rid the entire world of evil so that suffering can no longer exist and to do that, war is necessary.
Horde prime rallies his followers to revolt against their captors and escape imprisonment. Horde primes once peaceful commune becomes a paramilitary organization that aids in the war he once fled.
His side wins. Horde prime attempts to go back to living peacefully but the militaristic organization of his cult stays. Being a cult leader feeds his ego. He sees that there is still strife in the world. His cult is no longer isolated from the world, but actively trying to build itself into a major religion ala scientology. Horde prime becomes jaded with other people, especially when scandals happen in his church. He feels that people who follow them of their own choosing should simply not need to be guided any more and is mystified as to why people seem to cause problems on purpose, in his mind. Horde prime begins to think that he is the only person that knows how to live a righteous and moral life, even people who have followed him from the beginning are doomed to sin if they even so much as think thoughts that are not his. Horde prime dislikes people and sees them as only a means to an end or something he can get something out of. He dislikes actually having to lead people and mediate conflicts. He thinks that the world would be a much better place if only he could do the thinking for everyone.
Horde prime invents (or steals) the technology needed to make horde chips. He invents or steals the tech needed to create the hive mind. He has his followers chip themselves ala jamestown. At this point he can use the hive mind to read people's thoughts and possess them and has his new army go about chipping everyone on the planet.
At last, he has achieved world peace, but he knows that there are more planets and more people and more strife in the universe, so he uses his world wide army to build a space fleet and begin his universal conquest in earnest. He takes all the resources remaining on his home planet and leaves it desolate, the first of many planets he would do this to.
As the years drag on and horde prime begins to age, so does his army. It is steadily growing via new conquests but there are no new children in the horde because everyone is chipped and not having them. Horde prime knows that if his goal of total annihilation of the known universe so it can be rebuilt can work, then he can have no suitable heir, because his entire philosophy revolves around him knowing best and doing the thinking for everyone. He also knows that if he succeeds in chipping everyone in existence eventually that would mean that all sapient life would die out. This is not necessarily his goal, he just wants all people to reflect his image and think what he wants them to think, not be completely gone. In addition to that, though horde prime dislikes actually having to lead people, he does not desire to be completely alone and enjoys manipulating and using his followers now that they are completely obedient.
This would entice him to invent his method of cloning that we see in the show. Horde prime uses the greater part of his remaining natural life perfecting his cloning process and devising ways to keep himself living for longer and longer than his original lifespan would have lent him. He develops a way of replacing eating with injecting himself with the green amniotic fluid that we see in the show. It both nourishes him and keeps his body working in top physical condition. How does it do this? Idk!!!!!!! But he bases his clones around it, fitting them with ports all over their bodies that make maintenance easier. He also replaces their organic brains with computers that are pre-connected to the hive mind and preloaded with all the knowledge the clone would need to live when popping out of a tube as an adult. They are also pre-programmed to adore and worship horde prime. He fits them with a port on the back of their necks that connects directly to their computer brains like a usb or html. He also at some point decides that he doesn't want his clones to have wings or a tail and has them be stopped from growing in the cloning process.
When he decides that he can no longer keep his original body alive, he has his most favored clone fitted with even more ports and cables that can connect to the brains of other clones. When his original body dies, he has this clone's mind completely wiped and possesses him, having him become his new primary vessel. The original clone that once laid claim to that body is essentially dead and can never be revived, though horde prime can access his memories. This would be the permanent process of horde prime gaining new bodies to keep himself immortal. The species that horde prime belongs to eventually dies out until the only members of it left are his clones.
And that is how we find him in the show.......
#horde prime#shera#spop#shera fanfic#spop fanfic#horde prime fanfic#horde prime backstory#rambling#thoughts#srpop#shera netflix#shera reboot#shera horde#shera lore#spop lore
18 notes
·
View notes