#32-bit iOS devices
Explore tagged Tumblr posts
Text
ACCA DipIFR Remote Exam: Requirement, Set-up & Tips

In our previous blog, we discussed ACCA DipIFR exam utility interface & answer writing tips which will help students to get comfortable with CBE interface and to be familiar with the examination pattern and face it with confidence.
This blog is especially for the students who chose Remote examination session i.e., who would appear from home or office instead of centre-based examination. This blog will guide you about technical requirements of the allowed devices and necessary care to be taken before and during the remote examination session.
System Requirements:
Operating System
• Windows 11 and 10 (64-bit) – (excluding ‘S Mode’) • macOS 13 and above – (excluding beta versions)
Note: • Mac OS, starting with Mojave, now requires permission from the user to allow any hardware access to an application, which includes OnVUE (proctorapp). Candidates should be prompted to allow this application • Windows Operating Systems must pass Genuine Windows Validation.
Unsupported operating systems
• Windows 8/8.1, Windows 7, Windows XP, and Windows Vista • Linux/Unix and Chrome based Operating Systems
Firewall
• Corporate firewalls should be avoided as they often cause this delivery method to fail. • VPNs and proxies should not be used. • We recommend testing on a personal computer. Work computers generally have more restrictions that may prevent successful delivery.
RAM Required
Recommended Minimum RAM of 4 GB or more
Display
Minimum Resolution: 1024 x 768 in 16-bit col Recommended Resolution: 1920 x 1080 or higher in 32-bit color • If using an external monitor, you must close your laptop and use an external keyboard, mouse, and webcam. • Multiple monitors are forbidden. • Touch screens are strictly forbidden.
Webcam
• The webcam may be internal or external. It must be forward-facing and at eye level to ensure your head and shoulders are visible within the webcam. • The webcam must remain in front of you and cannot be placed at an angle. • Webcam filters are not allowed (for example, Apple’s ‘Reactions’). • Webcam must have a minimum resolution of 640x480 @ 10 fps.
Note: • Mobile phones are strictly prohibited as a webcam for exam delivery. • Mac OS users may need to allow OnVUE within their System Preferences: Security & Privacy: Privacy settings for camera & microphone.
Speakers and microphone
Speakers: • Speakers must be built-in or wired. • Bluetooth speakers or the use of headphones* as speakers are not allowed. Headphones: • Headphones and headsets are not allowed unless explicitly approved by your test sponsor. • If allowed, headphones must be wired – Bluetooth are not allowed.
Browser settings
Internet Cookies must be enabled.
Device
All tablets are strictly prohibited, unless they have a physical keyboard and meet the operating system requirements mentioned earlier.
Power
Make sure you are connected to a power source before starting your exam to avoid draining your battery during the exam.
Internet Browser
The newest versions of Microsoft Edge, Safari, Chrome, and Firefox, for web registrations or downloading the secure browser.
Internet Connection
• For better performance, a reliable and stable connection speed of 12 Mbps download and 3 Mbps upload required. • We recommend testing on a wired network as opposed to a wireless network. • If testing from home, ask others within the household to avoid internet use during your exam session.
We strongly recommend using equipment that meets or exceeds the Recommended Specifications. The minimum requirements will change periodically based on the needs of exam sponsors.
Mobile phone: You may have the option to use your mobile phone to complete the check-in process. The mobile must meet the following requirements:
• Android (11+, Chrome) or IOS (15+, Safari) operating systems • A functioning camera with a stable internet connection
A mobile phone is used only for completing admission steps and must not be used during the exam. After completing the check-in steps, please place the mobile phone where it is not accessible to you during the exam. As a reminder, phones are a prohibited item and should not be within your reach or visible to you while sitting in front of your computer.
Pre-exam requirements
Passing the Mandatory system test
• You MUST pass mandatory system test prior to your check-in for exam. • When taking the test, use same device and the same location you we’ll use on exam day. • Make sure your last test run is a pass, so that you are eligible for all post-exam options. • Go to Exam Planner & hit the Run System Test button.
Practice using the scratch pad
Remember, you cannot use scratch paper for remote exam session. So, it’s important to get used to using the scratch pad on the Practice Platform before your live exam.
Exam set-up
Your room setup
You will be under exam conditions and monitored by an invigilator throughout. Make sure below conditions are being followed: • A private and quite room with solid walls and doors. • No other person can be visible or heard for full duration of exam. • Use curtains or blinds to cover windows if anyone can be seen through them. • Switch all other unnecessary electrical equipment off. • Refer below images to have an idea about ideal exam environment.
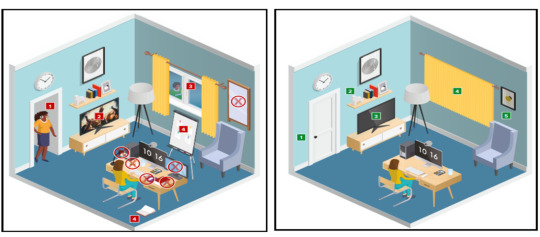
Prohibited Permitted
Your desk setup
Your desk must be setup in a way that meets the rules and regulations of the exam: • No scrap paper• Only one monitor • A glass/bottle of water with label removed permitted • No headphones / earbuds / earphones • No watches
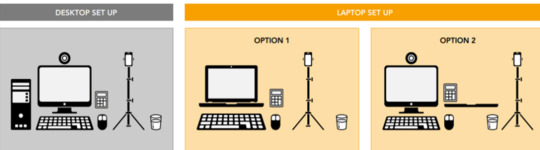
The check-in process
• Check in to your exam by going the exam planner and click launch exam button. • You can launch your exam 30 minutes prior your scheduled time. • If you are more than 15 minutes late you will miss your exam attempt and be marked as Absent.
Using your mobile phone:
• You may use your mobile phone during the check-in process – On-screen instruction will guide you.• You’ll be asked to take and upload photos of your exam environment, yourself and your ID. • Once completed this process place your mobile phone on silent and out of arm’s reach. • Do not use your mobile phone for any other purpose during exam (exception if invigilator calls you) • Taking photos of your screen or making calls during the exam is strictly prohibited.
Under exam conditions:
In addition to the desk/room requirements you should be aware that the following is also prohibited:
• Talking aloud during your exam. • People being audible outside your room. • Leaving the exam early – DO NOT end your exam early, you must stay supervised for the full-time duration.
Contacting the invigilator
• To start a chat with your invigilator, select the chat button. • Your invigilator will be with you as soon as they are available. • Unlikely they can assist you, but you should inform your invigilator if you are experiencing any technical difficulties. • You must inform your invigilator if you wish to use your permitted bathroom break.
Bathroom breaks
You can take one bathroom break during your exam of up to 5 minutes: • Notify your invigilator when you are leaving and returning from bathroom break. • You do not have to wait for the invigilator to give you their permission before taking your bathroom break. • The exam timing will continue to run – if you exceed 5 minutes your exam may be terminated.
Post-exam options: In the event of technical issue disrupting your exam, you may wish to use post-exam options which can be accessed on exam planner or under Contact Us on ACCA’s website.
Minimise the risk of the technical issue by: • Performing your equipment and connectivity test. • Accessing troubleshooting resources.
Using post exam options
To use rebook or withdrawal option you must have: • attempted to check-in your exam • experienced a technical issue impacting your ability to complete exam.
Additional withdrawal eligibility criteria
• The mandatory system test must be taken ahead of each exam session. • Student must have passed the mandatory system test in their last attempt prior to checking in for your exam.
Make sure that your device / other equipment’s are compatible as per the provided requirements and you are availed with the environment requisite for the exam purpose. Everyone should make sure to follow fair practices during exam to avoid any disqualification or disciplinary action.
We hope, this blog about ACCA DipIFR Remote Exam Requirement, Set-up & Tips shall assist in making the necessary arrangements.
Further, please watch video related to the remote examination on the below link: https://youtube.com/playlist?list=PLRYOefFr48S0apGK6f0kw0sX7fC6uSzsx&feature=shared
Best wishes from Team FinPro!
#finproconsulting#diploma in ifrs#accounting#dipifrs#ifrs#ifrs online classes#finpro consulting#dipifr course#diplomainifrs#acca
0 notes
Text
Application Processor Market Size, Share, Trends, Growth and Competitor Analysis
Global Application Processor Market – Industry Trends and Forecast to 2028
Global Application Processor Market, By Core Type (Single-core, Dual-core, Quad-core, Hexa-core and Octa-core), Device Type (Mobile Phones, PC Tablets and E-readers, Smart Wearables, Automotive ADAS and Infotainment Devices), Industry (Consumer Electronics and Automotive), and Country (U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, Italy, U.K., France, Spain, Netherlands, Belgium, Switzerland, Turkey, Russia, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa) Industry Trends and Forecast to 2028.
Access Full 350 Pages PDF Report @
**Segments**
- **Type**: The application processor market can be segmented based on types such as 32-bit, 64-bit, and others. 32-bit application processors are widely used in smartphones, IoT devices, and automotive applications due to their cost-effectiveness and efficient performance. On the other hand, 64-bit application processors offer higher processing power and are prominently used in high-end smartphones, tablets, and laptops. The demand for 64-bit processors is increasing as devices require more computing power to run complex applications.
- **End-User**: Another crucial segmentation factor is the end-user industry, including consumer electronics, automotive, healthcare, industrial, and others. The consumer electronics sector dominates the application processor market, driven by the growing need for advanced processors in smartphones, smart TVs, wearables, and gaming consoles. The automotive industry is also adopting application processors to enable features like infotainment systems, advanced driver-assistance systems (ADAS), and in-vehicle networking.
- **Operating System**: Application processors are also segmented based on the operating system they support, such as Android, iOS, Windows, and others. Android-based application processors have a significant market share due to the popularity of Android OS in smartphones and tablets. iOS processors are specifically designed for Apple devices like iPhones and iPads, offering seamless integration with the iOS ecosystem. Processors supporting Windows OS are utilized in laptops, PCs, and hybrid devices, catering to a niche segment of users.
**Market Players**
- **Qualcomm Incorporated**: A leading player in the application processor market, Qualcomm offers a wide range of Snapdragon processors known for their superior performance, power efficiency, and 5G connectivity. Its processors power various smartphones, tablets, and IoT devices, making Qualcomm a dominant force in the market.
- **Apple Inc.**: Apple designs its own application processors, such as the A-series chips, to power iPhones, iPads, and other Apple devices. These processors are renowned for their high performance, optimized software-hardware integration, and enhanced security features, maintaining Apple's stronghold in the premium segment of the market.
- **Samsung Electronics Co., Ltd.**: Samsung develops Exynos application processors for its smartphones, tablets, and other consumer electronics products. The Exynos processors offer competitive performance, advanced graphics capabilities, and efficient power management, contributing to Samsung's market presence in the application processor segment.
- **MediaTek Inc.**: MediaTek is a key player offering a range of application processors for smartphones, smart TVs, smart home devices, and automotive applications. Its Dimensity series processors focus on delivering high performance, AI capabilities, and 5G connectivity at a competitive price point, catering to a wide range of devices and manufacturers.
The global application processor market is highly competitive and dynamic, driven by technological advancements, the demand for faster processing speeds, and the proliferation of connected devices across various industries.
https://www.databridgemarketresearch.com/reports/global-application-processor-marketThe application processor market is experiencing significant growth and transformation due to the increasing demand for faster and more efficient processing capabilities across various industries. One emerging trend in the market is the focus on AI integration within application processors to enable advanced functionalities such as natural language processing, image recognition, and predictive analytics. This trend is driven by the need for enhanced performance and intelligence in devices like smartphones, IoT products, and automotive systems.
Moreover, the development of 5G technology is shaping the application processor market landscape by offering higher data speeds, lower latency, and improved network capacity. Application processors with integrated 5G modems are becoming increasingly important in enabling seamless connectivity for smartphones, smart home devices, and industrial applications. The adoption of 5G technology is expected to drive the demand for more robust and power-efficient processors to support the demanding requirements of next-generation networks.
Another key aspect impacting the market is the growing emphasis on power efficiency and thermal management in application processors. As devices become more compact and power-hungry applications become prevalent, there is a need for processors that can deliver high performance while minimizing energy consumption and heat generation. Companies are investing in innovative technologies such as advanced cooling solutions, on-device AI processing, and heterogeneous computing architectures to address these challenges and enhance the overall user experience.
Furthermore, the shift towards edge computing is influencing the design and functionality of application processors. Edge computing allows data processing to occur closer to the source of data generation, enabling faster response times and reduced reliance on cloud services. Application processors with enhanced processing capabilities and AI acceleration are being deployed in edge computing devices such as smart cameras, industrial sensors, and autonomous vehicles to enable real-time decision-making and data analytics at the edge.
Overall, the application processor market is poised for continued growth and innovation driven by the rapid evolution of technology, increasing connectivity requirements, and the demand for smarter and more efficient devices across diverse industries. Companies that can effectively address the challenges of performance, power efficiency, and connectivity while meeting the evolving needs of end-users are likely to succeed in this competitive and dynamic market landscape.**Segments**
Global Application Processor Market, By Core Type (Single-core, Dual-core, Quad-core, Hexa-core, and Octa-core), Device Type (Mobile Phones, PC Tablets and E-readers, Smart Wearables, Automotive ADAS and Infotainment Devices), Industry (Consumer Electronics and Automotive), and Country (U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, Italy, U.K., France, Spain, Netherlands, Belgium, Switzerland, Turkey, Russia, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa) Industry Trends and Forecast to 2028.
The application processor market is witnessing significant advancements and transformations across different segments. The core type segmentation, including single-core, dual-core, quad-core, hexa-core, and octa-core processors, caters to varying performance needs in devices. Single-core processors are more common in basic devices, while hexa-core and octa-core processors are preferred for high-end smartphones and tablets requiring heavy multitasking capabilities. The device type segmentation highlights the diverse applications of application processors in mobile phones, PC tablets, smart wearables, automotive ADAS, and infotainment systems, showcasing the market's versatility across multiple industries.
Industry segmentation plays a vital role in determining the market landscape, with consumer electronics and automotive sectors driving significant demand for application processors. The prevalence of advanced processors in smartphones, smart TVs, and gaming consoles within the consumer electronics industry underscores the pivotal role of application processors in enhancing user experience and device functionalities. On the other hand, the automotive sector's adoption of application processors for infotainment systems, ADAS features, and in-vehicle networking signifies the increasing integration of technology in modern vehicles for a connected and intelligent driving experience.
Moreover, the country-wise segmentation sheds light on regional market dynamics, with countries like the U.S., China, India, Japan, and European nations being key players in the application processor market. The market trends and forecast provide valuable insights into the evolving landscape of application processors, emphasizing the need for continuous innovation and adaptation to stay competitive in the rapidly changing market scenario.
In this dynamic market environment, market players such as Qualcomm, Apple, Samsung, and MediaTek hold significant positions by offering advanced processors tailored to diverse end-user requirements. The competition among key players drives innovation and technological advancements in application processors, leading to improved performance, energy efficiency, and connectivity features. These companies are investing in AI integration, 5G technology, power efficiency solutions, and edge computing capabilities to meet the evolving demands of various industries and consumers.
The emerging trends in the application processor market, such as AI integration, 5G adoption, emphasis on power efficiency, and the shift towards edge computing, present new opportunities and challenges for market players to innovate and differentiate their offerings. The market's growth trajectory is fueled by the increasing need for faster processing speeds, enhanced intelligence in devices, and seamless connectivity solutions across industries. As technology continues to evolve, companies that can leverage these trends to deliver high-performance, efficient, and intelligent application processors are poised to thrive in the competitive market landscape.
Countries Studied:
North America (Argentina, Brazil, Canada, Chile, Colombia, Mexico, Peru, United States, Rest of Americas)
Europe (Austria, Belgium, Denmark, Finland, France, Germany, Italy, Netherlands, Norway, Poland, Russia, Spain, Sweden, Switzerland, United Kingdom, Rest of Europe)
Middle-East and Africa (Egypt, Israel, Qatar, Saudi Arabia, South Africa, United Arab Emirates, Rest of MEA)
Asia-Pacific (Australia, Bangladesh, China, India, Indonesia, Japan, Malaysia, Philippines, Singapore, South Korea, Sri Lanka, Thailand, Taiwan, Rest of Asia-Pacific)
Objectives of the Report
To carefully analyze and forecast the size of the Application Processor market by value and volume.
To estimate the market shares of major segments of the Application Processor
To showcase the development of the Application Processor market in different parts of the world.
To analyze and study micro-markets in terms of their contributions to the Application Processor market, their prospects, and individual growth trends.
To offer precise and useful details about factors affecting the growth of the Application Processor
To provide a meticulous assessment of crucial business strategies used by leading companies operating in the Application Processor market, which include research and development, collaborations, agreements, partnerships, acquisitions, mergers, new developments, and product launches.
Key questions answered
How feasible is Application Processor Market for long-term investment?
What are influencing factors driving the demand for Application Processor near future?
What is the impact analysis of various factors in the Global Application Processor market growth?
What are the recent trends in the regional market and how successful they are?
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America
Browse Trending Reports:
Led Lighting Market Nutraceutical Excipients Market Workflow Orchestration Market Fluoropolymer Coating Market Hybrid Memory Cube Hmc High Bandwidth Memory Hbm Market Wearable Sensors Market Managed Security Services Market Texture Paint Market 3d Optical Metrology Market Data Mining Tools Market Digital Inks Market Benzene Market Corporate Learning Management System Market Cerebrospinal Fluid Csf Management Market Document Management Software Market Clinical Trial Supplies Market Dementia Alzheimer Disease Market Breast Cancer Liquid Biopsy Market Silicone Adhesives Market Aluminum Caps And Closures Market Polyvinylidene Fluoride Market Reactive Diluents Market Data Center Accelerator Market Silicon Anode Battery Market 24d Printing Medical Devices Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]
0 notes
Text
0 notes
Text
what is forticlient vpn used for
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is forticlient vpn used for
FortiClient VPN features
FortiClient VPN is a robust software solution designed to provide secure remote access to corporate networks for employees working from remote locations. One of the key features of FortiClient VPN is its advanced encryption protocols, ensuring that all data transmitted between the user's device and the corporate network is fully protected from potential threats and cyberattacks.
Another notable feature of FortiClient VPN is its split tunneling capability, which allows users to route only specific traffic through the VPN connection while directing other traffic through their regular internet connection. This feature not only helps optimize network performance but also enables users to access local resources securely while connected to the corporate network.
Additionally, FortiClient VPN offers multi-factor authentication options, adding an extra layer of security to the remote access process by requiring users to provide additional forms of verification before gaining access to the network. This helps prevent unauthorized access and enhances overall network security.
Furthermore, FortiClient VPN includes robust endpoint security features, such as antivirus and anti-malware protection, web filtering, and application control, helping ensure that users' devices are protected from potential threats while connected to the corporate network.
In conclusion, FortiClient VPN offers a comprehensive set of features designed to provide secure and reliable remote access to corporate networks. With advanced encryption protocols, split tunneling capabilities, multi-factor authentication, and endpoint security features, FortiClient VPN is a valuable tool for organizations looking to enhance their network security and enable secure remote access for their employees.
FortiClient VPN compatibility
FortiClient VPN is a robust and versatile VPN solution that offers compatibility across various platforms and devices, ensuring seamless connectivity and security for users. Whether you're using a Windows, macOS, iOS, or Android device, FortiClient VPN is designed to work efficiently across all major operating systems.
For Windows users, FortiClient VPN offers compatibility with Windows 7, 8, and 10, providing a user-friendly interface and advanced security features to safeguard your online activities. With support for both 32-bit and 64-bit architectures, FortiClient VPN ensures compatibility with a wide range of Windows devices, from desktops to laptops.
Mac users can also benefit from FortiClient VPN's compatibility with macOS, including the latest versions such as macOS Catalina and Big Sur. Whether you're accessing the VPN from your MacBook or iMac, FortiClient VPN delivers reliable performance and robust security features to protect your data and privacy.
Mobile users are not left behind, as FortiClient VPN offers compatibility with both iOS and Android devices. Whether you're using an iPhone, iPad, or Android smartphone or tablet, you can enjoy secure and encrypted connections with FortiClient VPN, whether you're browsing the web, accessing corporate networks, or streaming content.
In addition to its broad compatibility across platforms, FortiClient VPN also integrates seamlessly with Fortinet's suite of security solutions, providing comprehensive protection against cyber threats and ensuring a consistent user experience across your network infrastructure.
Overall, FortiClient VPN's compatibility with a wide range of platforms and devices makes it a versatile and reliable choice for individuals and organizations seeking secure and reliable VPN connectivity. Whether you're working from home, traveling, or accessing sensitive information on the go, FortiClient VPN has you covered.
FortiClient VPN security protocols
FortiClient VPN is a robust solution for ensuring secure and private communication over the internet. One of its key features lies in its array of security protocols designed to safeguard data transmission.
One of the most widely used protocols within FortiClient VPN is the OpenVPN protocol. OpenVPN is renowned for its strong security measures, including encryption through OpenSSL and support for various authentication methods. Its open-source nature also means it undergoes continuous scrutiny and improvement by the security community.
Another prominent protocol offered by FortiClient VPN is the Secure Socket Tunneling Protocol (SSTP). Developed by Microsoft, SSTP operates seamlessly across firewalls and proxy servers, making it an excellent choice for ensuring connectivity in diverse network environments. Its integration with the Windows operating system adds an extra layer of convenience for users.
For users prioritizing speed without compromising security, the Internet Key Exchange version 2 (IKEv2) protocol is an ideal option. Known for its efficiency in reconnecting after network disruptions, IKEv2 provides strong encryption and authentication, making it a preferred choice for mobile devices and remote workers.
Additionally, FortiClient VPN supports the Transport Layer Security (TLS) protocol, which ensures data integrity and confidentiality during transmission. TLS, the successor to the Secure Sockets Layer (SSL), is widely used in securing web communications and offers robust encryption algorithms for safeguarding sensitive information.
In conclusion, FortiClient VPN offers a comprehensive suite of security protocols, including OpenVPN, SSTP, IKEv2, and TLS, to ensure users can enjoy a secure and private browsing experience. By leveraging these protocols, users can mitigate risks associated with unauthorized access and data breaches, thereby fostering a safe and secure digital environment.
FortiClient VPN setup guide
FortiClient VPN Setup Guide
FortiClient is a comprehensive cybersecurity solution that includes a VPN client for secure remote access to your network. Setting up the FortiClient VPN is relatively easy but requires attention to detail to ensure a secure connection. Follow these steps to set up FortiClient VPN on your device:
Download and Install FortiClient: Visit the official Fortinet website to download the FortiClient VPN software suitable for your operating system. Once downloaded, run the installation file and follow the on-screen instructions to complete the installation process.
Launch FortiClient: After installation, launch the FortiClient application on your device.
Add VPN Configuration: Click on the "Remote Access" tab in the FortiClient console. Then, click on "Configure VPN" and select "Add a new connection."
Enter Connection Details: Enter the connection details provided by your network administrator, including the VPN server's IP address or domain name, your username, and password.
Select Authentication Method: Choose the appropriate authentication method, such as username and password or a certificate, based on your network's security settings.
Connect to VPN: Save the connection settings and click on "Connect" to establish a connection to the VPN server securely.
Verify Connection: Once connected, verify that your device has successfully connected to the VPN by checking the FortiClient console for the connection status.
By following these steps, you can easily set up FortiClient VPN on your device and enjoy secure remote access to your organization's network. Remember to disconnect from the VPN when not in use to ensure network security.
FortiClient VPN troubleshooting
FortiClient VPN Troubleshooting: Tips to Resolve Connectivity Issues
FortiClient VPN offers a secure way to connect to your network remotely, but like any technology, it can encounter issues that hinder its functionality. Here are some common troubleshooting tips to help resolve connectivity issues:
Check Network Connectivity: Ensure that your device has a stable internet connection. Sometimes, the issue might not be with the VPN itself but with your network connection.
Verify VPN Configuration: Double-check your VPN configuration settings, including server address, authentication credentials, and encryption settings. Incorrect configurations can prevent successful connections.
Update FortiClient Software: Ensure that you are using the latest version of the FortiClient software. Updates often include bug fixes and performance improvements that can resolve connectivity issues.
Firewall and Antivirus Settings: Adjust firewall and antivirus settings to allow FortiClient VPN traffic. Sometimes, these security measures can block VPN connections, leading to connectivity problems.
Restart FortiClient Service: Restarting the FortiClient service or the entire application can sometimes resolve temporary glitches or conflicts that affect VPN connectivity.
Check for IP Address Conflicts: Ensure that there are no IP address conflicts on your network. Conflicting IP addresses can disrupt VPN connections.
Try Different Servers: If you are unable to connect to a specific VPN server, try connecting to a different server location. Sometimes, servers may be temporarily unavailable or experiencing issues.
Contact Support: If you have exhausted all troubleshooting steps and still cannot resolve the issue, contact Fortinet support for further assistance. They can provide advanced troubleshooting and guidance specific to your situation.
By following these troubleshooting tips, you can quickly diagnose and resolve connectivity issues with FortiClient VPN, ensuring a smooth and secure remote access experience.
0 notes
Text
do i want 32 or 64 bit vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i want 32 or 64 bit vpn
32-bit VPN advantages
A 32-bit VPN offers several advantages in terms of security, efficiency, and compatibility. One of the primary benefits of using a 32-bit VPN is the enhanced security it provides for transmitting sensitive data over networks. With stronger encryption protocols and secure tunneling techniques, a 32-bit VPN ensures that your online activities remain private and secure from potential cyber threats.
Additionally, a 32-bit VPN offers improved efficiency by optimizing network performance and reducing latency. By utilizing a 32-bit architecture, the VPN can process data packets more rapidly, resulting in faster connection speeds and smoother browsing experiences. This enhanced efficiency is especially beneficial for users who engage in activities that require high data transfer rates, such as streaming videos or online gaming.
Moreover, a 32-bit VPN is compatible with a wide range of devices and operating systems, making it versatile and user-friendly. Whether you are using a Windows PC, an Android smartphone, or an iOS device, a 32-bit VPN can be easily installed and configured to protect your online privacy across multiple platforms.
In conclusion, the advantages of using a 32-bit VPN are clear – from robust security features to improved efficiency and broad compatibility. By choosing a 32-bit VPN for your online activities, you can enjoy a safer, faster, and more seamless browsing experience while ensuring your data remains secure and inaccessible to unauthorized third parties.
64-bit VPN benefits
Title: Exploring the Benefits of 64-bit VPN Technology
In the realm of digital privacy and security, Virtual Private Networks (VPNs) play a crucial role in safeguarding sensitive data and ensuring anonymity online. With the advent of 64-bit VPN technology, users can enjoy a myriad of benefits that enhance their online experience and bolster their cybersecurity efforts.
One of the primary advantages of 64-bit VPNs is enhanced performance and efficiency. By leveraging the power of 64-bit architecture, these VPNs can handle larger amounts of data and execute operations more swiftly compared to their 32-bit counterparts. This results in faster connection speeds and smoother browsing experiences for users, especially when streaming HD content or engaging in bandwidth-intensive activities.
Moreover, 64-bit VPNs offer improved security features, making them more resilient against cyber threats and vulnerabilities. With stronger encryption algorithms and advanced protocols, such as OpenVPN and IKEv2/IPsec, these VPNs provide an extra layer of protection against hackers, malicious actors, and surveillance efforts. This is particularly crucial for individuals and organizations that deal with sensitive information and need to safeguard their online communications and transactions.
Additionally, 64-bit VPNs enable greater compatibility with modern computing systems and software applications. As more devices and operating systems transition to 64-bit architecture, having a VPN that is optimized for these platforms ensures seamless integration and optimal performance across various devices and environments.
In conclusion, the adoption of 64-bit VPN technology represents a significant advancement in the field of cybersecurity and online privacy. With its enhanced performance, robust security features, and broader compatibility, 64-bit VPNs empower users to navigate the digital landscape with confidence, knowing that their data and identity are safeguarded against potential threats.
Compatibility with 32-bit systems
Compatibility with 32-bit systems remains a relevant topic in the digital landscape as technology progresses towards 64-bit architecture. Many software developers and manufacturers continue to ensure that their products are compatible with 32-bit systems due to the large number of users still utilizing these older platforms.
In computing, the terms 32-bit and 64-bit refer to the way a computer's processor handles information. 32-bit systems can only manage a certain amount of data at once, whereas 64-bit systems can handle larger amounts of data more efficiently. Despite the advantages of 64-bit systems, the transition from 32-bit to 64-bit has been slow for many users and organizations due to compatibility issues and cost factors.
To address these concerns, software developers often create versions of their products that are compatible with both 32-bit and 64-bit systems. This ensures that users with older devices or operating systems can still access and utilize the software without any issues.
While the industry continues to shift towards 64-bit technology, the consideration for compatibility with 32-bit systems remains crucial. By supporting both architectures, software developers can cater to a wider audience and provide a seamless experience for users regardless of their system specifications.
In conclusion, compatibility with 32-bit systems is an important aspect of software development that ensures inclusivity and accessibility for all users. As technology evolves, maintaining support for older systems helps bridge the gap between legacy technology and modern advancements.
Performance of 64-bit VPN
The emergence of 64-bit VPNs has brought about a significant shift in the realm of online privacy and security. These VPNs leverage the processing power and memory capabilities of 64-bit systems to enhance their performance, offering users a more robust and seamless experience.
One of the key advantages of 64-bit VPNs lies in their ability to handle larger amounts of data more efficiently. With a wider memory address space, these VPNs can process and transmit data at faster speeds, making them ideal for bandwidth-intensive tasks such as streaming high-definition video or downloading large files.
Additionally, 64-bit VPNs often boast improved encryption algorithms, further enhancing the security of users' online activities. By leveraging advanced cryptographic techniques, these VPNs can ensure that data remains protected from prying eyes, safeguarding sensitive information from potential threats.
Moreover, the compatibility of 64-bit VPNs with modern operating systems and hardware platforms allows for seamless integration into existing infrastructure. Whether on desktops, laptops, or mobile devices, users can enjoy the benefits of enhanced performance and security without encountering compatibility issues.
Furthermore, the scalability of 64-bit VPNs makes them well-suited for businesses and organizations of all sizes. Whether catering to a handful of employees or serving a global clientele, these VPNs can adapt to meet the growing demands of a dynamic digital landscape.
In conclusion, the performance of 64-bit VPNs represents a significant advancement in the field of online privacy and security. By harnessing the power of 64-bit systems, these VPNs offer users enhanced speed, security, and compatibility, making them an invaluable tool for safeguarding sensitive data and ensuring a seamless online experience.
System requirements for 32 vs 64-bit VPN
When choosing a virtual private network (VPN) for your online activities, it's essential to consider the system requirements, particularly whether they are compatible with a 32-bit or 64-bit operating system. Understanding the differences between the two can help you make an informed decision on which VPN to use.
A 32-bit VPN client is designed to work on a 32-bit operating system, while a 64-bit VPN client is optimized for a 64-bit operating system. The primary difference between the two lies in the amount of memory they can access. A 32-bit system can only address up to 4 gigabytes of RAM, limiting the processing power and performance of the VPN client. In contrast, a 64-bit system can handle large amounts of memory, allowing for more efficient multitasking and faster data encryption.
Before choosing a VPN, it's crucial to check the system requirements to ensure compatibility with your operating system. Most modern VPN providers offer clients that are compatible with both 32-bit and 64-bit systems, giving users the flexibility to select the appropriate version for their devices. Additionally, some VPNs may have specific hardware requirements, such as a minimum processor speed or available storage space, which should also be considered before installation.
In conclusion, understanding the system requirements for 32-bit vs 64-bit VPN clients is vital for optimal performance and security. By choosing a VPN that is compatible with your operating system and hardware specifications, you can enjoy a seamless and protected online experience.
0 notes
Text
does avast pro come with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does avast pro come with vpn
Avast Pro VPN features
Avast Pro VPN offers a comprehensive suite of features to ensure your online privacy and security. Here are some of the key features that set it apart:
Secure Encryption: Avast Pro VPN employs bank-grade encryption to safeguard your internet connection. This encryption ensures that your data remains private and secure from prying eyes, whether you're browsing at home or using public Wi-Fi networks.
Wide Server Network: With servers located in numerous countries around the world, Avast Pro VPN allows you to bypass geographical restrictions and access content that may be blocked in your region. Whether you're traveling abroad or simply want to stream geo-restricted content, Avast Pro VPN has you covered.
Anonymous Browsing: Avast Pro VPN masks your IP address and encrypts your internet traffic, making it virtually impossible for third parties to track your online activities. This anonymity not only protects your privacy but also helps prevent targeted advertising and tracking.
Kill Switch: In the event of a VPN connection drop, Avast Pro VPN's kill switch feature automatically blocks all internet traffic to ensure that your data remains secure. This feature is especially crucial when accessing sensitive information or conducting online transactions.
Multi-Device Support: Avast Pro VPN allows you to protect multiple devices simultaneously, including computers, smartphones, and tablets. This flexibility ensures that your entire digital ecosystem remains shielded from potential threats.
Easy-to-Use Interface: Avast Pro VPN boasts a user-friendly interface that makes it simple to connect to servers and customize your VPN settings. Whether you're a tech-savvy user or a novice, you'll find Avast Pro VPN intuitive and easy to navigate.
In conclusion, Avast Pro VPN offers a robust set of features designed to protect your online privacy and security. From secure encryption to anonymous browsing and beyond, Avast Pro VPN is an essential tool for anyone looking to safeguard their digital footprint.
Avast Pro VPN compatibility
Avast Pro VPN is a powerful tool that prioritizes security and privacy for its users. When it comes to compatibility, Avast Pro VPN is designed to work seamlessly across a wide range of platforms and devices.
For Windows users, Avast Pro VPN can be easily installed on Windows 7, 8, and 10 operating systems. The user-friendly interface allows for quick installation and setup, ensuring a hassle-free experience for Windows users. Additionally, the VPN is compatible with both 32-bit and 64-bit versions of Windows.
Mac users can also benefit from Avast Pro VPN, as it is fully compatible with macOS systems. Whether you are using an older version such as macOS X El Capitan or the latest macOS Catalina, Avast Pro VPN works reliably to protect your online activities.
Furthermore, Avast Pro VPN offers compatibility with Android and iOS devices. By downloading the Avast VPN app from Google Play Store or Apple App Store, users can secure their internet connections on their smartphones and tablets. This enables users to stay protected while on the go and accessing public Wi-Fi networks.
In conclusion, Avast Pro VPN excels in compatibility by supporting a wide range of devices and operating systems. Whether you are using a Windows PC, Mac, Android, or iOS device, Avast Pro VPN ensures that your online activities remain secure and private across all platforms.
Avast Pro VPN subscription options
Avast Pro VPN offers various subscription options to cater to the diverse needs of its users. Whether you are an individual looking to secure your online activities or a business aiming to safeguard your sensitive data, Avast Pro VPN has got you covered.
One of the subscription options available is the monthly plan, which provides users with flexibility and the freedom to use the VPN service on a month-to-month basis. This option is perfect for users who may not require a VPN year-round but want to ensure their online privacy and security when needed.
For those looking to make a more long-term commitment, Avast Pro VPN also offers an annual subscription plan. By opting for the yearly plan, users can enjoy cost savings compared to the monthly option, making it a budget-friendly choice for individuals and businesses alike.
Additionally, Avast Pro VPN provides a multi-device subscription option, allowing users to protect multiple devices under one account. This is ideal for users who have multiple devices that need VPN protection, such as laptops, smartphones, and tablets.
With Avast Pro VPN's subscription options, users can enjoy unrestricted access to the internet while maintaining their privacy and anonymity. Whether you opt for the monthly, annual, or multi-device plan, Avast Pro VPN ensures a secure and seamless online experience for all its users.
Avast Pro VPN pricing
Avast Pro VPN offers flexible pricing plans tailored to meet the diverse needs of users seeking enhanced online privacy and security. With its range of subscription options, Avast ensures that individuals and businesses can find a plan that aligns with their requirements and budgetary constraints.
The pricing structure of Avast Pro VPN is transparent and straightforward, making it easy for users to understand the value they receive for their investment. Users can choose between monthly, yearly, or biennial subscription plans, each offering distinct advantages in terms of cost-effectiveness and commitment flexibility.
For those who prefer the convenience of short-term commitments, the monthly plan provides the flexibility to use the VPN on a pay-as-you-go basis, ideal for occasional users or those who require temporary protection for specific online activities.
For individuals and businesses seeking long-term protection and cost savings, the yearly and biennial plans offer significant discounts compared to the monthly option. These plans provide uninterrupted access to Avast Pro VPN's comprehensive features and benefits, including unlimited bandwidth, secure encryption, and access to a vast network of servers worldwide.
Moreover, Avast frequently offers promotional discounts and special offers, allowing users to enjoy even greater savings on their VPN subscription. By keeping an eye out for these promotions, users can maximize the value they receive from Avast Pro VPN without compromising on quality or security.
In conclusion, Avast Pro VPN pricing is designed to accommodate the diverse needs of users while delivering exceptional value and peace of mind. Whether opting for a short-term commitment or a long-term investment, users can trust Avast Pro VPN to deliver reliable, affordable, and robust protection for their online activities.
Avast Pro VPN benefits
Avast Pro VPN offers numerous benefits for users looking to enhance their online privacy and security. By using Avast Pro VPN, individuals can encrypt their internet connection, ensuring that their online activities remain private and protected from potential cyber threats.
One of the key advantages of Avast Pro VPN is the ability to access geo-restricted content. Users can bypass regional restrictions and censorship by connecting to servers in different countries, allowing them to enjoy unrestricted access to their favorite websites and streaming services.
Furthermore, Avast Pro VPN helps users stay anonymous online by masking their IP address and encrypting their internet traffic. This not only protects users from hackers and cybercriminals but also prevents government agencies, internet service providers, and advertisers from tracking their online activities.
In addition to enhancing online privacy and security, Avast Pro VPN also allows users to browse the internet more securely, especially when using public Wi-Fi networks. By encrypting data transmitted over public networks, Avast Pro VPN helps prevent sensitive information such as passwords, emails, and financial details from being intercepted by malicious actors.
Overall, Avast Pro VPN is a powerful tool for individuals looking to safeguard their online activities and data. With its advanced encryption technology, seamless user experience, and ability to bypass geo-restrictions, Avast Pro VPN provides a comprehensive solution for internet privacy and security.
0 notes
Text
BLIIoT| BL205 OPC UA Distributed IO Module in Industrial Automation
Introduction
In industrial automation, OPC UA Distributed I/O Modules can be used to connect sensors, actuators, and controllers to a unified network. This enables data acquisition, device control, and monitoring, which improves production efficiency and quality.

Features
OPC UA Distributed I/O Modules allow for the remote I/O devices to communicate with each other over the network using the OPC UA protocol. This eliminates the need for additional wiring and reduces installation costs.
With OPC UA Distributed I/O Modules, data from multiple devices can be collected, processed, and analyzed in real-time. This allows for automated responses to changing conditions or events. For example, if a sensor detects a temperature increase, the system can automatically adjust the cooling system to prevent damage or shutdown.
Additionally, OPC UA Distributed I/O Modules allow for secure communication between devices and systems. OPC UA provides a secure and reliable communication protocol that ensures data is transmitted without interference or manipulation.
Product
BL205 controller is a data acquisition and control system based on a powerful 32-bit microprocessor design with Linux operating system, supports OPC UA protocol for quick access to on-site PLC, SCADA, and ERP systems.
The I/O system supports programmable logic control, edge computing, and customized applications, it is widely applicable to a variety of IIoT and industrial automation solutions.
The BL205 I/O system consists of 3 parts: Controller, I/O modules and terminal module.
0 notes
Text
Complete Pack of Audio Interface for Music Production
Music production opens up an entirely different world for those interested in producing music, podcasts, or live streaming; having the right tools is essential for turning creative visions into musical reality. A complete pack of music production equipment brings together a high-quality microphone, professional headphones, and an audio interface. All these together provide you with a comprehensive setup that caters to every aspect of your recording and mixing needs.
Yamaha’s Studio Audio Interface Pack is everything you need to begin recording at home. It includes a free version of Cubase and is really simple and quick to set up. The UR22C contains all the necessary components to get you started if you're an ambitious producer who doesn't necessarily want to break the bank.

Recording Pack To Produce Excellent Recordings
Yamaha has been the leader in instruments for music production. The Steinberg UR22C Recording Pack is a pack of three devices anybody would require for making music. It comes with a USB 3.1 Audio Interface, Condenser Microphone, and Headphones.
The entire bundle for recording podcasts, interviews, or high-quality music and live streaming audio is the UR22C Recording Pack. With the accompanying ST-M01 microphone and ST-H01 headphones, you'll have everything you need to record in amazing 32-bit/192kHz quality. The small, sturdy UR22C audio interface boasts all the connections and features you need.
The UR22C Audio Interface Pack brings you a set of quality products that gives you amazing sound quality in a remarkably compact, tough, and versatile package for composing and recording anywhere. It gives you:
32-bit/192 kHz audio resolution
Class-A D-PRE mic preamps
Superspeed USB 3.1 with USB-C
Latency-free monitoring with DSP effects
iOS ready via CC Mode
If you are looking for a complete package of the best professional audio interface for recording high-quality music, The UR22C is the ideal package you require to record podcasts or interviews and also for live streaming audio.

Components Of The UR22C Audio Interface Pack Together with the bundled ST-M01 microphone and ST-H01 headphones, the small and sturdy UR22C audio interface has all the ports and features required to record in amazing 32-bit/192kHz quality. With this, you'll be well-equipped to create excellent recordings. You can record and mix anywhere you have fast, dependable connectivity to desktops or iOS devices. You can even listen while recording utilizing latency-free monitoring with DSP effects.
What Makes Yamaha Audio Interface a worthy investment?
With everything you need, start recording your music.
Everything you need to record and produce your tracks in amazing 32-bit/192 kHz quality is included in the UR22C Recording Pack. With the microphone and instrument inputs, MIDI inputs, and outputs on the small, durable UR22C digital audio interface, every instrument or voice may be captured in high definition. You may record and mix anywhere you have fast, dependable connectivity to desktops or iOS devices. You can even listen while recording utilizing latency-free monitoring with DSP effects. It's the perfect recording set, complete with an XLR cable, headphones, Cubase AI recording software, and a premium condenser microphone.

With a whole kit, create ASMR productions or podcasts.
Create podcasts to share your ideas, inspiration, news, and thoughts with the world. You can also record your thoughts to audio files for download or distribution, or you can publish them to any social platform. With this fantastic portable production suite of the best audio interface, you can record to a computer or iOS device from anywhere. Additionally, the bundled high-quality microphone, D-PRE mic preamps, and 32-bit/192 kHz recording quality allow you to capture every stimulating sound in the finest detail if you wish to join the expanding community of ASMR audio creators.
Publish your message live to attract more followers.
Reaching out to new and existing audiences through streaming is highly recommended, and the UR22C Recording Pack offers the perfect setup for going live on the internet. Whether you're streaming music, talks, game instructions, or any other type of performance, the Loopback feature makes it simple to do so. Additionally, the studio condenser microphone that comes with the device and the flexible, high-quality inputs ensure that your audience will hear everything in crystal clear clarity. Buy audio interface from Yamaha online music store.
#audio interfaces#best audio interface#best professional audio interface#studio audio interface#digital audio interface
0 notes
Text
Extremely Silent JPG Exploit ( NEW )

Hack within seconds.
Works on windows 32×64 bit , Linux , Android, iOS, Unix, device.
The exploit allows you to convert EXE, apk, jar, to .JPG file its coded 100% from scratch and used by private methods to assure a great stability and long lasting FUD time. You are able to attach it to all email providers and now a days everyone uses Internet so it gives a huge chance of success.
HACK ANY Windows, Linux , Android, iOS, Unix, device EASILY WITH THIS PRIVATE SILENT JPG EXPLOIT.
PACKAGE Content :
Ultra Hd Videos & Pdf For step By step Traning.
3 years Free Blackhat Dedicated Server.
1 year free blackhat team supports 24×7.
free Live Support Life time.
0 notes
Text
👉 Kasa 2K QHD Security Camera ✅ Pan/Tilt, Starlight Sensor for Color Night Vision, Motion Detection for Baby & Pet Monitor

Kasa 2K QHD Security Camera Pan/Tilt, Starlight Sensor for Color Night Vision, Motion Detection for Baby & Pet Monitor, 2-Way Audio, Cloud & SD Card Storage, Works with Alexa & Google Home (KC410S)
-22% Less $34.99
List Price: $44.99
👉 Recommended Uses For Product: Pet Monitoring, Baby Monitoring, Indoor Security
👉 Brand: Kasa Smart
👉 Model Name: KC410S
👉 Connectivity Technology: Wi-Fi
👉 Special Feature: Night Vision, Motion Sensor
CLICK HERE TO GET INSTANT ACCESS NOW >>
About this item
✅ Person/Motion/Sound Detection in Real-Time. Day or Night: With cutting-edge AI algorithms, KC410S can detect people, motion and sound to notify on your smart phone even at night with the night vision (30 ft. away in the dark). Customize up to 4 activity zones around areas which are important to make most use of cameras for home security as a baby monitor, pet camera or nanny cam. Controller Type: Google Assistant; Amazon Alexa. Connectivity protocol: Wi-Fi. Power source type: Corded Electric. Operating Temperature : 0°C~40°C (32°F~104°F). Adapter Input : 100-240 VAC, 50/60 Hz, 0.2 A. Adapter Output : 5.0 VDC, 1.0 A.. Compatible devices : Tablet, Smartphone. Power source : Corded Electric.
✅ Secure Your Videos Locally or with AWS Cloud: As an indoor security camera, KC410S continuously records and stores footage or video clips on a local MicroSD card up to 256 GB (MicroSD card not included). Premium cloud storage options are available with industry-standard 128-bit AES end-to-end encryption on AWS.
✅ Enjoy a Smarter Home with Smart Actions: Set your lights to turn on when your camera detects motion with Kasa Smart Actions. Smart Actions allows you to create interactions between your Kasa camera and other Kasa devices to make your life simpler. No need to check your Kasa Spot Pan Tilt throughout the day. Get automatic alerts when it detects motion or sound.
✅ Voice Control: For additional ease of use, pair the Kasa wireless camera with Alexa echo or Google assistant. Use a simple voice command to ask Alexa or Google Assistant to view your live camera feed on compatible Alexa or Google devices. System Requirements iOS 10+, Android 5.0+
CLICK HERE TO GET INSTANT ACCESS NOW >>
#QHDSecurityCamera#QHDSecurityCameraReview#QHDSecurityCameraReviews#QHDSecurityCameraBrand#QHDSecurityCameraGoodorBad#QHDSecurityCameraAmazon#QHDSecurityCameraFeatures#QHDSecurityCameraPrice#QHDSecurityCameraInboxing#HowtobuyQHDSecurityCamera#HowtogetQHDSecurityCamera#QHDSecurityCameraWalkthrough#QHDSecurityCameraWorks#marketing#amazon#onlinemarketing#amazondeals#amazonprime#amazonfinds#usa
0 notes
Text
GF and Microchip announce production of Microchip’s 28nm SuperFlash embedded flash memory solution

【Lansheng Technology News】GF and Microchip Technology Inc. and its subsidiary Silicon Storage Technology® announced today that the SST ESF3 third-generation embedded SuperFlash technology NVM solution using the GF 28SLPe process will be put into production soon.
GF has set a new industry benchmark in implementing SST's widely deployed ESF3 SuperFlash technology. This implementation has the following features and advantages:
Lowest cost 28nm HKMG ESF3 solution with only 10 additional masks, including true 5V IO CMOS devices
SST ESF3 bit cell size is less than 0.05 square microns, very competitive
Operating temperature rating −40°C to 125°C
Read access time is 25 ns, programming time is 10 us, and erase time is 4 ms
Endurance over 100,000 program/erase cycles
Does not affect the design process (EG process) using qualified IP of the GF 28SLPe platform
Ready-made macros from 4 Mb to 32 Mb available immediately
Custom macro design support available from SST or GF
As the level of edge intelligence continues to increase, the use cases for embedded flash memory have also exploded. Embedded memory for secure code storage, OTA updates and enhanced functionality is on the rise in a wide range of applications in home and industrial IoT and smart mobile devices. Meeting these needs requires innovative platforms.
“GF is proud to partner with SST to develop, qualify and bring into production this impressive embedded NVM solution on our powerful 28SLPe platform,” said Mike Hogan, chief business unit officer at GF. “GF’s customers are discovering "This solution combines high performance, outstanding reliability, IP availability and cost-effectiveness, making it ideal for advanced MCUs, complex smart cards, and IoT chips for consumer and industrial products."
Mark Reiten, Vice President of Microchip’s Licensing Business Unit and SST said: “SST has worked closely with GF over the past decade to integrate and productize SST’s industry-standard ESF1 and ESF3 embedded flash technologies into GF’s 130nm BCD, 55nm, 40nm and current 28nm process platforms. We admire GLOBALFOUNDRIES for its leadership in offering the broadest range of embedded NVM solutions and look forward to our close partnership leading to more breakthroughs over the next decade."
Lansheng Technology Limited, which is a spot stock distributor of many well-known brands, we have price advantage of the first-hand spot channel, and have technical supports.
Our main brands: STMicroelectronics, Toshiba, Microchip, Vishay, Marvell, ON Semiconductor, AOS, DIODES, Murata, Samsung, Hyundai/Hynix, Xilinx, Micron, Infinone, Texas Instruments, ADI, Maxim Integrated, NXP, etc
To learn more about our products, services, and capabilities, please visit our website at http://www.lanshengic.com
0 notes
Text
SSD Capacities: Accessing the Potential

Real-world workloads enable huge SSD capacities and efficient data granularity
Large SSDs (30TB+) present new challenges. Two important ones are:
High-density NAND, like QLC (quad-level cell NAND that stores 4 bits of data per cell), enables large SSDs but presents more challenges than TLC.
SSD capacity growth requires local DRAM memory growth for maps that have traditional 1:1000 DRAM to Storage Capacity ratios.
We cannot sustain the 1:1000 ratio. Do we need it? Why not 1:4000? Or 1:8000? They would cut DRAM demand by 4 or 8. What’s stopping us?
This blog examines this approach and proposes a solution for large-capacity SSDs
First, why must DRAM and NAND capacity be 1:1000? The SSD must map system logical block addresses (LBA) to NAND pages and keep a live copy of them to know where to write or read data. Since LBAs are 4KB and map addresses are 32 bits (4 bytes), we need one 4-byte entry per 4KB LBA, hence the 1:1000 ratio. We’ll stick to this ratio because it simplifies the reasoning and won’t change the outcome. Very large capacities would need more.
Once map entry per LBA is the best granularity because it allows the system to write at the lowest level. 4KB random writes are used to benchmark SSD write performance and endurance.
Long-term, this may not work. What about one map entry every four LBAs? 8, 16, 32+ LBAs? One map entry every 4 LBAs (i.e., 16KB) may save DRAM space, but what happens when the system wants to write 4KB? Since the entry is every 16KB, the SSD must read the 16KB page, modify the 4KB to be written, and write back the entire 16KB page. This would affect performance (“read 16KB, modify 4KB, write back 4KB”, rather than just “write 4KB”) and endurance (system writes 4KB but SSD writes 16KB to NAND), reducing SSD life by a factor of 4.
It’s concerning when this happens on QLC technology, which has a harder endurance profile. For QLC, endurance is essential!
Common wisdom holds that changing the map granularity (or Indirection Unit, or “IU”) would severely reduce SSD life (endurance).
All of the above is true, but do systems write 4KB data? And how often? One can buy a system to run FIO with 4KB RW profile, but most people don’t. They buy them for databases, file systems, object stores, and applications. Does anyone use 4KB Writes?
We measured it. We measured how many 4KB writes are issued and how they contribute to Write Amplification, i.e., extra writes that reduce device life, on a set of application benchmarks from TPC-H (data analytics) to YCSB (cloud operations), running on various databases (Microsoft SQL Server, RocksDB, Apache Cassandra), File Systems (EXT4, XFS), and, in some cases, entire software defined storage solutions like Red Hat Ceph Storage
Before discussing the analysis, we must discuss why write size matters when endurance is at stake.
Write 16K to modify 4K creates a 4x Write Amplification Factor for a 4KB write. What about an 8K write? If in the same IU, “write 16K to modify 8K” = WAF=2. A bit better. If we write 16K? It may not contribute to WAF because one “writes 16K to modify 16KB”. Just small writes contribute to WAF.
Writes may not be aligned, so there is always a misalignment that contributes to WAF but decreases rapidly with size.
The chart below shows this trend:
Large writes barely affect WAF. 256KB may have no effect (WAF=1x) if aligned or low (WAF=1.06x) if misaligned. Much better than 4KB writes’ 4x!
To calculate WAF contribution, we must profile all SSD writes and align them within an IU. Bigger is better. The system was instrumented to trace IOs for several benchmarks. After 20 min, we post-process samples (100–300 million per benchmark) to check size, IU alignment, and add every IO contribution to WAF.
The table below shows how many IOs each size bucket holds:
As shown, most writes fit in the 4–8KB (bad) or 256KB+ (good) buckets.
If we apply the above WAF chart to all misaligned IOs, the “Worst case” column shows most WAF is 1.x, a few 2.x, and very rarely 3.x. Better than 4x but not enough to make it viable.
IOs are not always misaligned. Why would they? Why would modern file systems misalign structures at such small scales? They don’t.
We measured and post-processed each benchmark’s 100+ million IOs to compare them to a 16KB IU. Last column “Measured” WAF shows the result. WAF >=1.05x, so one can grow the IU size by 400%, make large SSD using QLC NAND and existing, smaller DRAM technologies at a life cost of >5%, not 400%! These results are amazing.
The argument may be that many 4KB and 8KB writes contribute 400% or 200% to WAF. Given the small but numerous IO contributions, shouldn’t the aggregated WAF be much higher? Though many, they are small and carry a small payload, minimising their volume impact. A 4KB write and a 256KB write are both considered single writes in the above table, but the latter carries 64x the data.
Adjusting the above table for IO Volume (i.e., each IO size and data moved) rather than IO count yields the following representation:
The colour grading for more intense IOs is now skewed to the right, indicating that large IOs move a lot of data and have a small WAF contribution.
Finally, not all SSD workloads are suitable for this approach. For instance, the metadata portion of a Ceph storage node does very little IO, causing high WAF=2.35x. Metadata is unsuitable for large IU drives. The combined WAF is minimally affected if we mix data and metadata in Ceph (a common approach with NVMe SSDs), as data is larger than metadata.
Moving to 16K IU works in apps and most benchmarks, according to our testing. The industry must be convinced to stop benchmarking SSDs with 4K RW and FIO, which is unrealistic and harmful to evolution.
0 notes
Text
Movesense Medical Sensor wireless ECG monitor provides customizable measurements for remote healthcare monitoring

Movesense Medical Sensor wireless ECG monitor provides customizable measurements for remote healthcare monitoring. Oslo Norway, Aug 31, 2023 - The Movesense Medical sensor employs Nordic’s nRF52832 SoC to transmit medical data to the user’s smartphone using Bluetooth LE. Finnish medical device manufacturer Movesense has launched a compact and lightweight wearable wireless ECG monitor (electrocardiogram) sensor for remote patient monitoring and telehealth applications. The ‘Movesense Medical’ sensor is registered as a Class IIa device under the European Union (EU) Medical Device Regulation (MDR), and is designed for use by remote healthcare providers, medical device manufacturers and integrators, hospitals, or by companies developing their own commercialized medical device.
Wealth of sensor data
Movesense Medical provides wireless ECG monitor, heart rate (HR), heart rate variability (HRV), and movement data via the integrated nine-axis inertial measurement unit (IMU). It employs Nordic Semiconductor’s nRF52832 SoC to supervise the Movesense firmware stack and record the sensor data using its powerful 64 MHz, 32-bit Arm® Cortex® M4 processor with floating point unit (FPU). This data is then transmitted via Bluetooth® LE wireless connectivity to the wearer’s smartphone. Battery life optimization is crucial to this application, to ensure the wearer’s medical data is collected and transmitted with no gaps Jussi Kaasinen, Movesense “Movesense Medical sensor is a ready-to-go solution for medtech innovators as it can be integrated into existing health applications or used to develop new wearable health solutions that improve patient outcome and save costs,” says Jussi Kaasinen, CEO and Founder at Movesense. “It also enables health operators and researchers running clinical trials the ability to access medically certified raw data.” The Movesense Showcase app (available for iOS) can be used to test hardware functionality including ECG registration at various sampling rates, HR and HRV recording, and sensor signal collection at various dynamic ranges. The app source code and sample apps are also available to developers to use as a starting point for their own projects and to accelerate product development.
Ultra low power operation
Using a CR2025 coin cell battery, the Movesense Medical sensor can function for up to seven days – assuming continuous real time ECG streaming at a 256 Hz sample rate. Depending on the use case and amount of data being transmitted, the device can function for up to several weeks before the battery needs to be replaced. The ultra low power consumption is thanks in part to the nRF52832 SoC, which has been engineered to minimize power consumption with features such as the 2.4 GHz radio’s 5.5 mA peak RX/TX currents and a fully-automatic power management system. “Battery life optimization is crucial to this application, to ensure the wearer’s medical data is collected and transmitted with no gaps,” says Kaasinen. “The ultra low power characteristics of the Nordic SoC helped make this possible. We also selected the chip due to the wide range of available hardware building blocks, and the generous 256/512 KB Flash memory and 32/64 KB RAM. “In addition, Nordic provided us with access to excellent technical information, reference designs and brilliant application engineers.” Movesense Medical is a Bluetooth equipped and class IIa medically certified ECG and motion sensor. Also a perfect tool for developing and running your own medical applications related to measuring ECG, heart rate, heart rate variability (HRV) and movement. Movesense Medical is intended to be used as a measuring device, together with a host device or an application. Note: attaching accessories, such as Chest straps and ECG wet gel elegtrode patches, are sold separately.
Technical Highlights Movesense Medical Sensor wireless ECG monitor
- Single channel ECG, Heart rate, R-R intervals - 9-axis movement sensor: 3 x accelerometer, 3 x gyroscope, 3 x magnetometer - Configurable sample rates - In-built memory for logging data - Bluetooth® Low Energy (BLE) - Software tools for developing applications that run on the sensor - Wireless firmware update with BLE - Water (IP68) and shock proof construction, suitable for medical, health and sports applications - Based on Suunto design and development - Developed, designed and manufactured in Finland - Suitable for ECG and movement signal registration in oxygen rich environment, such as hyperbaric chambers - User replaceable battery (CR2025 coin cell) - Battery life optimization options through software. - Weight 9.4 g/0.33 oz. with battery, diameter 36.6 mm/1.44 in, body thickness 8 mm/0.32 in Read the full article
0 notes
Text
Gacha Nox MOD APK Download Latest Version [32-bit, 64-bit] Android, iOS, PC, Chromebook
Gacha Nox APK is a modified version of the Gacha Club with more Added Features and items for Gacha Fans. Gacha Nox is Free to Play with lot of different battle mods. Gacha Nox MOD APK for 32-bits and 64-bits allows you to Personalize your Characters the way you want and you can customize your Anime with decorations, accessories, various clothes, Shoes, Height, Hair Color, Skin and more.

Gacha Nox is a Role Playing Mobile and PC Game developed by Gacha. You can Unleash your creativity and design characters with unique styles and also you can share your Gacha Experience with your friends. You can Download Gacha Nox for Android 32-bit, Android 64-bit devices. You can Also Play Gacha Nox in Chromebook and PC as well.
Gacha Nox Features
Gacha Nox APK has wide range of features including it allow players to collect Virtual Charactres, Compete in battles and explore different worlds.
Virtual Charactres
Battle
Customization
Social Features
Gacha Play Gameplay is quite Simple and addictive. Gacha Players can collect Virtual Characters and use them to compete in battle, complete missions and explore worlds. Based on Your unique strategies, you can Win the Battles. The Interesting Part is you can Customize your Characters and make it feel unique and special with so many customization Options. The Social Feature makes it more interesting as users can connect with other players across the world, join guilds and participate in various events.
Gacha Nox APK for Android >> Click Here (64 Bit)
Gacha Nox APK for Android >> Click Here (32 Bit)
Gacha Nox APK for PC >> Click Here
gacha nox android, gacha nox apk download android, gacha nox install, gacha nox download, gacha nox outfit ideas, gacha nox mod combo, gacha nox mod apk download, gacha nox apk mod 1.0 download for android latest version 2023, gacha nova apk mod download latest for android, descargar gacha nox mod apk download
gacha nox android 32-bit gacha nox android 32-bit.apk download gacha nox android 64-bit.apk file gacha nox android 64-bit.apk 173 mb gacha nox chromebook gacha nox for pc gacha nox for ios gacha nox for samsung, oppo, apple ipad and more devices.
9 notes
·
View notes
Text
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
iBypasser Ramdisk Tool V2.7 iCloud Bypass Windows Tool
iBypasser Ramdisk Tool is a powerful application designed to bypass iCloud activation on iOS devices running iOS 11-15 without the need for jailbreaking. It provides various functionalities to disable the passcode, back up files, disable the iCloud account by opening the menu, and retrieve the Apple ID and phone number associated with the device. Additionally, it offers the capability to disable the “Hello” screen using the MEID/GSM signal. Please note that bypassing iCloud activation is not endorsed by Apple and may violate their terms of service.
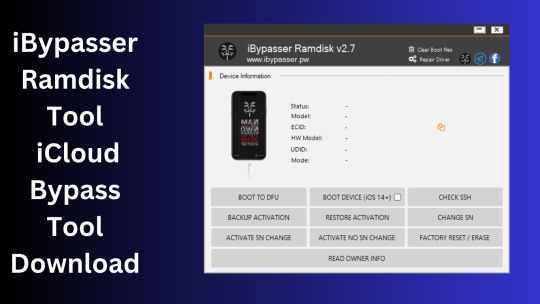
What is iBypasser Ramdisk Tool V2.7?
The iBypasser Ramdisk Tool V2.7 software program was created especially to get around the iCloud activation lock on the iOS device. Customers may use it to give a speedy fix if they find themselves locked out of their devices and unable to access all of the features on their iPhones, iPads, or iPods.
Features iBypasser Ramdisk tool:
Boot Device for iOS 15. x and earlier
Verify SSH
Restore/Backup Activation
Alter SN
Switch on the Hello Device
Go To Owner Info
iOS 15+ (DFU) Data Erasure
Remove Boot File
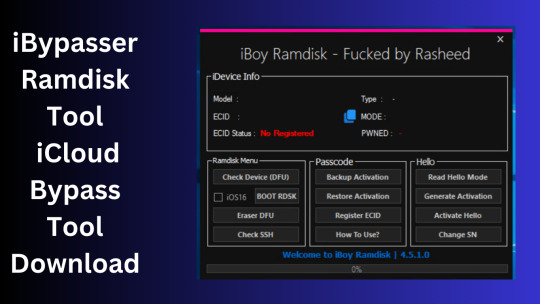
Changelog!!!
Update: iBypasser Ramdisk AIO v2.0
Resolving boot problems.
DFU Helper was added.
Driver problems were resolved.
Performance augmentation.
How To Use?
You will initially need to register the device’s ECID.
Your MAC notebook should have iBypasser RAMDISK installed. Next, unzip it.
Start your RAMDISK tool after that. then adhere to the directions below.
Enter DFU mode on the iPhone. When you successfully connect your device to DFU mode, the iBypasser RAMDISK Tool will provide you with further alternatives. Activate, Backup Files, Open SSH, Open Proxy, etc.
To open the proxy, type one and press the Enter key. Start SSH by pressing 2; then press 3 to access the backup files.
You may examine the data you successfully backed up on your device in the backup directory.
Second, flash your device with the 3u Tool or iTunes.
Connect your device to DFU mode once you’ve finished flashing it.
Open the proxy after switching the device to DFU mode Type 1. Press 4 again to turn on your gadget.
Readme:
Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1, and Windows 10 (32-bit and 64-bit) are all fully compatible with the program.
Create a Backup: If you want to try the tool described above, create a backup of the personal information stored on the Android smartphone or tablet you intend to utilize. Considering that flashing any recovery or firmware has the potential to harm the device.
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
Click Her
5 notes
·
View notes