#ASP file handling
Explore tagged Tumblr posts
Text
What is .ASP (Active Server Pages)?
Learn everything about .ASP (Active Server Pages) in this complete guide. Discover its history, features, structure, how it works, syntax, objects, file handling, database connections, and real-world uses. Ideal for beginners and developers working with legacy systems. Understanding .ASP (Active Server Pages): A Complete Guide 1. Introduction to .ASP ASP, short for Active Server Pages, is a…
#.asp#Active Server Pages#ASP database connection#ASP error handling#ASP examples#ASP file handling#ASP form handling#ASP guide for beginners#ASP objects#ASP scripting#ASP security#ASP server execution#ASP tutorial#ASP vs ASP.NET#classic ASP#legacy ASP#Microsoft ASP#server-side scripting#VBScript in ASP#web development with ASP
0 notes
Text
Top 5 Accounting Errors Canadian Businesses Make - And How to Avoid Them

Canadian businesses face unique accounting challenges due to specific national standards and regulations. While accounting mistakes can happen to any organization, understanding and avoiding the most common errors can save businesses from costly consequences and regulatory issues.
Canadian accounting operates under distinct rules from its U.S. counterpart, following standards set by the Canadian Securities Administrators (CSA) and incorporating International Financial Reporting Standards (IFRS). Despite these robust frameworks, businesses continue to make several critical mistakes that can impact their financial health.
5 most common errors
Here are the five most common accounting errors Canadian businesses make and how to address them:
Mixing Personal and Business Finances
One of the most frequent mistakes, particularly among small business owners, is failing to separate personal and business accounts. This commingling of funds not only creates confusion during tax season but can also raise red flags during audits.
The solution is straightforward: maintain separate bank accounts and credit cards for business and personal use, and keep meticulous records of all business transactions.
2. Irregular Bookkeeping Practices
Many businesses fall into the trap of sporadic financial record-keeping. This inconsistency can lead to missing transactions, overlooked expenses, and inaccurate financial statements.
Implementing a regular bookkeeping schedule – whether daily, weekly, or monthly – ensures all financial activities are properly documented and tracked. Modern accounting software can significantly streamline this process.
3. Neglecting Bank Reconciliation
Failing to reconcile books with bank statements is a dangerous oversight that can mask errors or fraudulent activities. Regular reconciliation helps identify discrepancies, unauthorized transactions, or banking errors promptly.
Business owners should make it a priority to reconcile their accounts monthly, comparing every transaction in their books against their bank statements.
4. Missing Tax Deadlines and Compliance Requirements
Canadian businesses must navigate various tax obligations and filing deadlines throughout the year. Missing these deadlines can result in substantial penalties and interest charges. Creating a tax calendar marking all important dates and starting preparation well in advance can help avoid last-minute rushes and potential mistakes.
5. DIY Accounting Without Proper Expertise
While trying to save money by handling accounting in-house is understandable, a lack of expertise in Canadian accounting standards can lead to serious errors. These standards, including IFRS, Accounting Standards for Private Enterprises (ASPE), and Canadian Auditing Standards (CAS), require professional knowledge to navigate correctly.
Read Top 5 Accounting Errors Canadian Businesses Make to learn about these common errors in detail.
The Solution: Professional Support
To avoid these common pitfalls, businesses should consider working with qualified accounting professionals who understand Canadian accounting standards.
This doesn't necessarily mean hiring a full-time accountant – outsourcing to professional accounting services can be a cost-effective solution that provides expert guidance while ensuring compliance with all relevant regulations.
By addressing these common accounting errors proactively, Canadian businesses can maintain accurate financial records, ensure regulatory compliance, and make better-informed business decisions. Regular review of accounting practices, combined with professional support when needed, can help businesses maintain financial health and avoid costly mistakes in the long run.
Conclusion
Remember, good accounting isn't just about maintaining books – it's about creating a solid foundation for business growth and success while staying compliant with Canadian accounting standards and regulations. Contact us for a free consultation.
1 note
·
View note
Text
Securing ASP.NET Applications: Best Practices
With the increase in cyberattacks and vulnerabilities, securing web applications is more critical than ever, and ASP.NET is no exception. ASP.NET, a popular web application framework by Microsoft, requires diligent security measures to safeguard sensitive data and protect against common threats. In this article, we outline best practices for securing ASP NET applications, helping developers defend against attacks and ensure data integrity.

1. Enable HTTPS Everywhere
One of the most essential steps in securing any web application is enforcing HTTPS to ensure that all data exchanged between the client and server is encrypted. HTTPS protects against man-in-the-middle attacks and ensures data confidentiality.
2. Use Strong Authentication and Authorization
Proper authentication and authorization are critical to preventing unauthorized access to your application. ASP.NET provides tools like ASP.NET Identity for managing user authentication and role-based authorization.
Tips for Strong Authentication:
Use Multi-Factor Authentication (MFA) to add an extra layer of security, requiring methods such as SMS codes or authenticator apps.
Implement strong password policies (length, complexity, expiration).
Consider using OAuth or OpenID Connect for secure, third-party login options (Google, Microsoft, etc.).
3. Protect Against Cross-Site Scripting (XSS)
XSS attacks happen when malicious scripts are injected into web pages that are viewed by other users. To prevent XSS in ASP.NET, all user input should be validated and properly encoded.
Tips to Prevent XSS:
Use the AntiXSS library built into ASP.NET for safe encoding.
Validate and sanitize all user input—never trust incoming data.
Use a Content Security Policy (CSP) to restrict which types of content (e.g., scripts) can be loaded.
4. Prevent SQL Injection Attacks
SQL injection occurs when attackers manipulate input data to execute malicious SQL queries. This can be prevented by avoiding direct SQL queries with user input.
How to Prevent SQL Injection:
Use parameterized queries or stored procedures instead of concatenating SQL queries.
Leverage ORM tools (e.g., Entity Framework), which handle query parameterization and prevent SQL injection.
5. Use Anti-Forgery Tokens to Prevent CSRF Attacks
Cross-Site Request Forgery (CSRF) tricks users into unknowingly submitting requests to a web application. ASP.NET provides anti-forgery tokens to validate incoming requests and prevent CSRF attacks.
6. Secure Sensitive Data with Encryption
Sensitive data, such as passwords and personal information, should always be encrypted both in transit and at rest.
How to Encrypt Data in ASP.NET:
Use the Data Protection API (DPAPI) to encrypt cookies, tokens, and user data.
Encrypt sensitive configuration data (e.g., connection strings) in the web.config file.
7. Regularly Patch and Update Dependencies
Outdated libraries and frameworks often contain vulnerabilities that attackers can exploit. Keeping your environment updated is crucial.
Best Practices for Updates:
Use package managers (e.g., NuGet) to keep your libraries up to date.
Use tools like OWASP Dependency-Check or Snyk to monitor vulnerabilities in your dependencies.
8. Implement Logging and Monitoring
Detailed logging is essential for tracking suspicious activities and troubleshooting security issues.
Best Practices for Logging:
Log all authentication attempts (successful and failed) to detect potential brute force attacks.
Use a centralized logging system like Serilog, ELK Stack, or Azure Monitor.
Monitor critical security events such as multiple failed login attempts, permission changes, and access to sensitive data.
9. Use Dependency Injection for Security
In ASP.NET Core, Dependency Injection (DI) allows for loosely coupled services that can be injected where needed. This helps manage security services such as authentication and encryption more effectively.
10. Use Content Security Headers
Security headers such as X-Content-Type-Options, X-Frame-Options, and X-XSS-Protection help prevent attacks like content-type sniffing, clickjacking, and XSS.
Conclusion
Securing ASP.NET applications is a continuous and evolving process that requires attention to detail. By implementing these best practices—from enforcing HTTPS to using security headers—you can reduce the attack surface of your application and protect it from common threats. Keeping up with modern security trends and integrating security at every development stage ensures a robust and secure ASP.NET application.
Security is not a one-time effort—it’s a continuous commitment
To know more: https://www.inestweb.com/best-practices-for-securing-asp-net-applications/
0 notes
Text
Navigating Insurance Claims with Mobile Auto Window Repair Services in the Greater Toronto Area

Key Tips:
Understand your insurance policy coverage for auto glass repairs.
Document the damage and repair process thoroughly.
Communicate directly with your insurance to clarify claim procedures.
Choose a reputable mobile auto window repair service that collaborates with insurers.
Keep all receipts and documentation for your claim submission.
As a provider of comprehensive auto glass repair services, I often guide customers through the process of handling insurance claims for mobile auto window repair. In the bustling environment of the Greater Toronto Area, understanding how to efficiently manage these claims can save both time and money. This article delves into the crucial steps and considerations for seamlessly integrating insurance claims with your auto glass repair needs.
Understanding Your Coverage
Auto glass damage can be a common issue, especially in areas with high traffic like the Greater Toronto Area. It's vital to start by understanding what your insurance policy covers. Many policies cover windshield and auto glass repair, but specifics can vary widely.
Review your policy to see if glass damage is covered.
Determine whether your policy includes mobile repair services.
Check if you need to pay a deductible before service.
Documenting the Damage
When filing a claim, detailed documentation is your best ally. Take clear photos of the damage from multiple angles and note any circumstances that might have contributed to the damage.
Use a high-quality camera or smartphone to take pictures.
Include date and time stamps on all documentation.
Save all communication with your insurance company.
Choosing the Right Repair Service
Selecting a trusted mobile auto window repair service like Isho Auto Glass, which is familiar with working with insurance companies, can make the process smoother.
Look for services that offer direct billing to insurance.
Check reviews and testimonials for reliability and service quality.
Ensure the service is licensed and certified.
Direct Communication with Insurance
Keeping in direct contact with your insurance provider can prevent misunderstandings and expedite your claim.
Inform your insurer about the damage as soon as possible.
Discuss the repair service and ensure it is approved under your policy.
Confirm all forms and documentation required for the claim.
Managing Repair and Claim Together
Combining the repair appointment and the insurance claim can streamline the process, making it less time-consuming.
Schedule the repair in a manner that aligns with your insurance's approval.
Have the repair technician provide a detailed receipt that your insurer requires.
Ensure the repair service updates your insurance company directly if needed.
Legal Considerations
There are legal aspects to filing insurance claims for auto repairs in Ontario that you must be aware of to ensure compliance and proper claim handling.
Understand Ontario's regulations on auto insurance claims.
Be aware of your rights under insurance law.
Consult with a legal advisor if disputes arise.
Detailed Hypothetical Case
Imagine Sarah, a resident of Brampton, who discovered a significant crack in her car's windshield after a piece of debris struck it on the highway. Aware of her comprehensive insurance coverage, she contacted her provider to confirm the details and documented the damage. She chose Isho Auto Glass for the mobile repair because we collaborate directly with insurers and are known for our efficient service. After the repair, we provided Sarah with all the necessary documentation, which she submitted to her insurance, leading to a swift and favorable resolution of her claim.
How Isho Auto Glass Can Help
At Isho Auto Glass, we specialize in mobile auto window repairs across the Greater Toronto Area, making it convenient for our customers to get high-quality, insurance-approved services right at their doorstep. We handle all aspects of insurance claims, from providing detailed repair documentation to direct billing, ensuring that your experience is hassle-free.
FAQs on Handling Insurance Claims for Auto Glass Repair
What types of auto glass damages are typically covered by insurance in Ontario?
Most comprehensive insurance plans cover all types of auto glass damage, including chips, cracks, and shatters, but coverage specifics can vary.
Do I need to contact my insurance before getting a repair?
Yes, it's advisable to contact your insurer to understand your coverage details and ensure that the repair service is approved.
Can I choose any repair service for filing an insurance claim?
While you are generally free to choose your repair service, using an insurer-approved provider like Isho Auto Glass can streamline the process.
What should I do if my insurance claim for auto glass repair is denied?
Review the denial reasons, consult your policy, and discuss the matter with your insurer. Sometimes, providing additional documentation can resolve the issue.
How long does it take to process an insurance claim for auto glass damage?
The time can vary, but most claims are processed within a few days to a couple of weeks, depending on the complexity and the insurer's promptness.
#autowindowrepair#mobilewindshieldrepair#mobileautowindowrepair#camerarecalibration#windshieldchiprepaircost
0 notes
Text
5 Beneficial Tips About Outsourcing Data Input Services

Each business depends on its data to survive. It includes every aspect of the company and its operations. Companies are producing ever-increasing volumes of data as a result of the constantly changing market trends across all industries.
While data entering takes time, properly managed data simplifies information, conserves space, and provides instant access. Both big companies and small businesses can increase production and save costs through outsourcing.
What Is Data Input Services?
The data input service involves transferring various data from several sources into digital formats based on the needs of the business. This is how to handle data more effectively and securely in soft copies. Additionally, handling more paper documents—which is usually laborious work—will become less stressful. Data input services enable a company to make sure that its employees can easily access the data, which improves productivity.
For most businesses, data input is done on data formats such as spreadsheets, handwritten or scanned documents, audio or video, and other semi-core operations. The three applicable handles in data input are addition, modification, and deletion.
Why Outsourcing Data Input Services Is Important?
Those who are unfamiliar with this job tend to undervalue its significance, believing it to be of no value to a company. Although several online applications offer automated data input services, nothing can match the quality of work that an accomplished individual can produce.
You may be sure that skilled typists and programmers can handle these responsibilities if you outsource your data entry work to a reputable BPO service. These experts are less likely to make mistakes because they have years of expertise entering data.
When outsourcing data input services, many businesses also take cost reductions into account. For instance, recruiting teams from outside to perform data entry work is far less expensive than engaging teams from within to complete the same amount of work. Time and resources are also saved by outsourcing data entry tasks. There are fewer employees to assist with daily operations in startups and smaller companies. By assigning these laborious duties to an outside vendor, you can lessen their burden and free up time for other important endeavors.
Steps Follow In Data Input Services
The steps involved in data input services can vary depending on the specific requirements of the task and the technologies involved. However, here is a general outline of the steps commonly followed in data input services:
Assessment And Planning:
Recognize the precise data entry requirements, considering the volume, format, and kind of data. Establish project objectives, due dates, and standards of quality. Determine if the best action is to use automatic data capture, human data entry, or a combination of both.
Data Collection:
Collect the raw data from a variety of sources, such as forms, digital files, paper documents, photos, and other formats. Make sure that the information has been gathered and is prepared for processing.
Data Entry:
Assign skilled workers to precisely enter data into the computerized system. To reduce errors, use quality control or double-entry verification.
Quality Control:
Put strict quality control procedures in place to ensure that the data entered is accurate and comprehensive. Look for mistakes, discrepancies, or information that is missing. Make the necessary modifications or obtain more evidence to address any disparities.
Data Validation:
Check sure the submitted data complies with the specifications by comparing it to accepted guidelines or standards. Use validation tests to identify and correct any data that does not match the necessary formats or values.
Here Are 5 Useful Tips About Outsourcing Data Input Services For Business Growth
Outsourcing data input services can offer numerous benefits, but it's crucial to be aware of certain key aspects to make informed decisions. Here are five major things to know about outsourcing data input services:
Cost Efficiency:
The main goal of outsourcing data input for businesses is to cut expenses. For data entry activities, outsourcing is frequently more affordable than recruiting and onboarding internal employees. Recognize the pricing structures that outsourcing companies offer. It could depend on the amount of data handled, the difficulty of the tasks, or other elements. Select a model based on your requirements and available funds.
Data Security And Privacy:
Verify that the outsourcing company has strong security protocols in place to safeguard the privacy of your data. This is very important, particularly when handling confidential or private data. Check to see if the outsourced provider conforms with industry standards and any data protection laws. Obtain guarantees about data privacy and adherence to relevant laws and regulations, such as HIPAA, GDPR, and others.
Quality Control:
Clearly define your expectations for the quality and accuracy of data entry. Errors should be quickly detected and fixed with the implementation of quality control procedures. Keep lines of communication open with the outsourced company. Having regular updates and feedback systems in place can assist in guaranteeing that the data entry quality meets your requirements.
Technology And Infrastructure:
Examine the software and hardware that the outsourced provider uses. Data input services can be rendered much more accurately and efficiently by utilizing contemporary technology like OCR, automation, and artificial intelligence. Make sure the outsourcing partner's activities can be scaled to meet your needs. To accommodate variations in data volumes, this is important.
Risk Mitigation And Contingency Planning:
To reduce risks, the outsourcing contract's terms and conditions—including service level agreements, or SLAs—should be clearly defined. Indicate the consequences of non-compliance as well as the dispute resolution procedures. Talk about and comprehend the backup plans that the outsourcing provider has in place in case of unexpected events like system malfunctions, natural catastrophes, or other disruptions. Maintaining service continuity requires a strong business continuity plan.
Conclusion:
Remember to thoroughly research potential outsourcing partners, seek references, and possibly start with a smaller pilot project to assess the capabilities and compatibility of the service provider. Regularly review the outsourcing arrangement to ensure it continues to meet your evolving business needs. Source Of: https://latestbpoblog.blogspot.com/2024/02/5-beneficial-tips-about-outsourcing-data-input-services.html
#DataInput#DataInputCompanies#DataInputOutsourcing#DataInputServices#DataInputSpecialist#DataInputOperator
0 notes
Text
Safeguarding Your ASP.NET Web Applications: A Deep Dive Into Security Considerations
In the ever-evolving landscape of web development, ASP NET web application security is of paramount importance. Microsoft’s ASP NET framework, renowned for its power and flexibility, lays the groundwork for dynamic and feature-rich web applications. However, this power comes with the responsibility of addressing potential security vulnerabilities. This article delves into crucial security considerations developers must prioritize in ASP NET web application development.
Authentication and Authorization: Authentication and authorization form the bedrock of web application security. ASP NET supports various mechanisms, including forms-based authentication and identity providers like OAuth. Developers must judiciously choose and implement the appropriate authentication method based on the application’s requirements. Proper authorization controls ensure that only authenticated users with the appropriate permissions can access specific resources.
InformationValidation: Attackers often target user inputs to exploit vulnerabilities. ASP NET developers must validate and sanitize all user inputs to prevent injection attacks, such as SQL injection and Cross-Site Scripting (XSS). Techniques like parameterized queries and encoding user inputs before rendering them on the client side significantly mitigate these risks.
Secure Data Transmission: Secure communication is imperative to protect sensitive data during transit. Utilizing HTTPS (SSL/TLS) encrypts data exchanged between the client and the server, preventing eavesdropping and man-in-the-middle attacks. Developers should enforce HTTPS for the entire application and configure secure communication protocols to enhance data integrity and confidentiality.
Cross-Site Request Forgery (CSRF) Protection: CSRF attacks exploit a web application’s trust in a user’s browser. ASP NET provides built-in mechanisms, such as anti-forgery tokens, to protect against CSRF attacks. Developers should incorporate these measures to validate the origin of requests and ensure that actions initiated within the application are legitimate.
Session Security: Sessions are crucial for maintaining user state, but insecure session management can expose sensitive information. Secure session handling practices, including unique session identifiers, session timeout mechanisms, and a secure repository of session data, are essential. Regularly rotating session identifiers add an extra layer of protection against session hijacking.
Error Handling and Logging: Effective error handling is vital for security and user experience. Carefully crafted error messages aid developers in identifying and resolving issues, while generic error messages presented to users prevent the disclosure of sensitive information. Proper logging mechanisms are equally important for tracking and analyzing security incidents for ASP NET web applications.
Secure File Uploads: File uploads can be a potential avenue for malicious activities. Developers must implement strict controls, including validating file types, restricting file sizes, and storing uploads securely. Utilizing content-disposition headers prevents browsers from rendering uploaded files as executable scripts.
Code Access Security: ASP NET incorporates Code Access Security (CAS) to control permissions granted to web applications. Developers should leverage CAS to restrict actions, ensuring applications operate within defined security boundaries. This granular control helps mitigate the impact of potential security breaches by limiting the scope of compromised components.
Regular Security Audits and Updates: The security landscape evolves, and regular security audits are crucial for identifying and addressing potential weaknesses. Staying informed about Microsoft’s security updates and promptly applying patches protects the application from known vulnerabilities.
In ASP NET web application development, security considerations are non-negotiable. Adhering to best practices in authentication, input validation, secure data transmission, and other key areas fortifies applications against potential threats. Establishing a robust security posture is not just a development best practice but a fundamental aspect of safeguarding user data and maintaining trust in an interconnected digital world. As technology evolves, so must our commitment to creating web applications prioritizing security without compromising functionality and user experience. Selecting an ASP.NET development company in India ensures a potent blend of technical expertise, cost-effectiveness, and skilled developers, making it a compelling choice for secure and innovative web solutions.
1 note
·
View note
Text
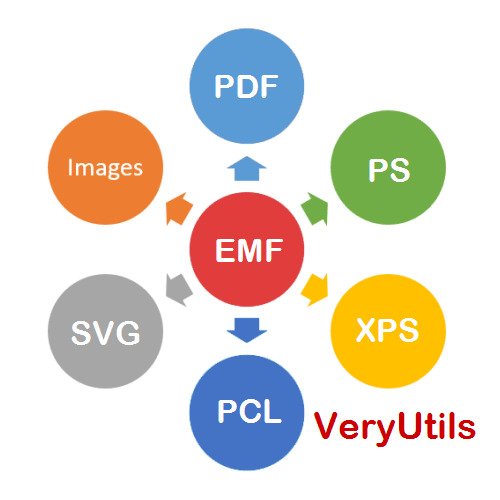
VeryUtils EMF to Vector Converter Command Line Software can be used to convert from EMF and WMF Metafile files to PDF, Postscript, EPS, SVG, SWF, XPS, HPGL, PCL, TIFF, JPG, BMP, PNG, GIF, etc. formats.
VeryUtils EMF to Vector Converter Command Line Software can be used to convert from EMF and WMF Metafile files to PDF, Postscript, EPS, SVG, SWF, XPS, HPGL, PCL, TIFF, JPG, BMP, PNG, GIF, etc. formats.
Are you tired of struggling with incompatible file formats and the loss of vector and text information during conversions? Look no further! VeryUtils EMF to Vector Converter (EMF2Vector) is your comprehensive solution for converting enhanced metafiles (EMF) and Windows metafiles (WMF) into a wide array of vector and raster formats while preserving their original quality. Let's dive deep into the features and benefits of this versatile software.
Transforming enhanced metafiles (EMF) and Windows metafiles (WMF) into an array of vector formats while preserving their core vector and textual attributes, VeryUtils EMF to Vector Converter (EMF2Vector) is your solution. With the ability to convert EMF and WMF files into formats like PDF, WMF, EMF, PS (Postscript), EPS, SVG, SWF, XPS, HPGL, and PCL, this software opens doors to seamless vector compatibility.
But it doesn't stop there. VeryUtils EMF to Vector Converter (EMF2Vector) is not limited to vector formats alone. It gracefully transitions EMF and WMF files into raster image formats, including BMP, GIF, JPEG, PNG, TGA, PCX, PNM, RAS, PBM, and TIFF, to cater to a broader spectrum of graphic needs.
EMF2Vector doesn't just cater to individual conversions; it's a versatile tool for batch conversions as well. Whether you prefer a user-friendly interface or the efficiency of batch mode, it can efficiently handle large volumes of EMF and WMF files in real-time. What's more, it's accessible through COM objects, DLL libraries, or Command Line, ensuring seamless integration into various programming and scripting languages such as Visual Basic, C/C++, Delphi, ASP, PHP, C#, .NET, and more. Whether you're processing files consecutively or simultaneously, EMF2Vector has your back.
✅ Effortless Format Conversion
EMF2Vector takes the hassle out of file conversion. It effortlessly converts EMF and WMF files into an impressive list of vector formats, including:
Output Vector formats: •PDF: Adobe Acrobat PDF format •PS: Postscript format •EPS: Adobe Encapsulated PostScript •WMF: Windows Metafile •EMF: Microsoft Enhanced Metafile (32-bit) •SVG: Scalable Vector Graphics •SWF: Macromedia Flash File Format •XPS: Microsoft XML Paper Specification •HPGL: HP-GL plotter language •PCL: HP Page Control Language, Printer Command Language Format (PCL)
✅ But that's not all! EMF2Vector can also convert EMF and WMF files into popular raster image formats, such as:
Output Raster image formats: •JPEG: Joint Photographic Experts Group JFIF format •TIFF: Tagged Image File Format •BMP: Microsoft Windows bitmap •GIF: CompuServe Graphics Interchange Format •PNG: Portable Network Graphics •PCX: ZSoft IBM PC Paintbrush file •TGA: Truevision Targa image •PNM: Portable anymap •RAS: SUN Raster Format •PBM: Portable bitmap format (black and white) •And more!
No matter your desired output format, EMF2Vector has you covered.
✅ Seamless Batch Conversion
VeryUtils EMF to Vector Converter (EMF2Vector) is designed to handle both individual file conversions and large-scale batch processing. Its intuitive user interface allows you to convert files with ease. Plus, the software can run in batch mode, enabling you to process substantial volumes of EMF and WMF files in real-time. Whether you're a casual user or a power user dealing with extensive data, EMF2Vector adapts to your needs.
✅ Developer-Friendly Integration
Developers, rejoice! EMF2Vector is available as an easily integrated COM object, DLL Library, or Command Line tool. This means you can access the converter via your preferred programming or scripting languages, including Visual Basic, C/C++, Delphi, ASP, PHP, C#, .NET, and more. You have the flexibility to perform file conversions consecutively or simultaneously, adding efficiency to your workflow.
✅ Industry-Standard Output Formats
EMF2Vector converts EMF and WMF files to a range of industry-standard formats. By retaining the vector nature of the graphics, you gain a competitive edge when importing these files into your publishing system. Whether you're in CAD architecture, business diagramming, GIS cartography, chart and graph creation, scientific plotting, or vector artwork, EMF2Vector empowers you to deliver superior results.
✅ Licensing Options
Choose the licensing model that suits your needs: •Server License: Licensed per Production Server, perfect for integration into ASP, PHP, C#, .NET, and other server-side applications. •Developer License: Licensed per Developer with Royalty-Free Runtime Desktop Distribution, allowing installation on any number of servers or computers.
✅ Key Features for EMF and WMF to Vector Conversion
VeryUtils EMF to Vector Converter (EMF2Vector) stands out with its exceptional features: •Standalone Software: No need for Adobe Acrobat or Adobe Reader; EMF2Vector is a self-sufficient solution. •Multilingual Support: Available in a wide range of languages, including English, French, German, Italian, Chinese Simplified, Chinese Traditional, Czech, Danish, Dutch, Japanese, Korean, Norwegian, Polish, Portuguese, Russian, Spanish, Swedish, Thai, and more. •Direct Integration: Easily import converted graphics files directly into your target applications. •Optimized for Various Fields: Ideal for CAD architecture, business diagrams, GIS cartography maps, charts and graphs, scientific plots, vector artwork, and beyond. •Font Preservation: Convert embedded fonts into Polylines within the vector graphics formats. •Versatile Output: Convert EMF and WMF files into various vector graphics and raster image formats. •Batch Processing: Seamlessly integrate high-volume batch conversion into your server-based applications or workflow. •Customization Options: Specify width, height, X resolution, Y resolution, color depth, rotation options, and more for your image format conversions. •Unicode Support: Preserve Unicode characters during EMF and WMF conversion. •Platform Compatibility: Compatible with Windows platforms, including Win98, ME, NT, 2000, XP, 2003, Vista, 7, 10, 11 and later systems, support both 32bit and 64bit systems. •Automated Viewing: View created files automatically.
✅ Special Features for EMF and WMF to PDF Conversion
VeryUtils EMF to Vector Converter (EMF2Vector) offers a host of advanced features when converting EMF and WMF files to PDF: •Direct PDF Conversion: Convert EMF & WMF to PDF directly, without relying on any printer driver products. •Compact PDFs: Produce PDF files with the smallest possible file size. •Batch PDF Creation: In batch conversion, merge multiple document files into a single PDF or convert each document file into its own PDF. •Password Protection: Secure your PDF files with 40 or 128-bit encryption, including "owner password" and "user password" protection options. •Document Metadata: Set document title, subject, author, and keywords for enhanced PDF organization. •Wildcard Support: Utilize wildcard characters (e.g., *.emf, *.wmf) for versatile file selection. •Command Line Efficiency: Execute batch and unattended operations using the command line interface. •Text Searchability: Ensure that produced PDF documents are fully text-searchable in Adobe Reader. •Dynamic PDF Conversion: Integrate EMF and WMF to PDF conversion into web-based applications for real-time dynamic conversion. •PDF Manipulation: Merge multiple PDF files into a single PDF, merge from a text file listing filenames, append or insert EMF and WMF files into existing PDFs, burst multi-page PDFs into single-page PDFs, and insert bookmarks into PDF files.
✅ Experience the Power of EMF to Vector Conversion
Unlock the full potential of your EMF and WMF files with VeryUtils EMF to Vector Converter (EMF2Vector). Whether you're a designer, developer, or professional working across diverse fields, this software provides the flexibility, efficiency, and quality you need for seamless file conversion. Say goodbye to compatibility issues and hello to a world of possibilities.
Try EMF2Vector today and discover how easy it is to transform your EMF and WMF files into versatile vector and raster formats!
✅ Custom Development Service
Discover the power of customization with our VeryUtils EMF to Vector Converter Command Line software custom development service. We understand that every organization has unique needs, and that's why we offer tailored solutions to meet your specific requirements. Whether you need additional features, specialized integrations, or unique functionalities, we have the expertise to modify our software to align perfectly with your objectives. With our custom development service, you can harness the full potential of VeryUtils EMF to Vector Converter, ensuring it becomes an invaluable asset that seamlessly integrates into your workflows and delivers precisely the results you envision. Let us transform our software to suit your needs, empowering you with a powerful tool that caters to your unique demands and accelerates your productivity.
If you are interested in purchasing this software or developing a customized software based on it, please do not hesitate to contact us.
We look forward to the opportunity of working with you and providing developer assistance if required.
0 notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
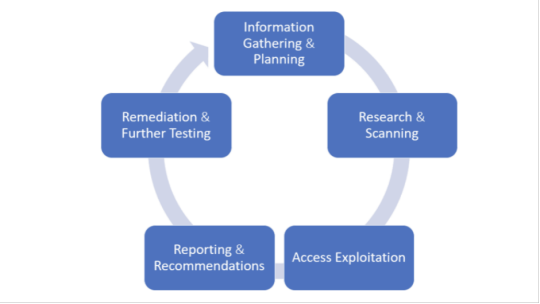
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
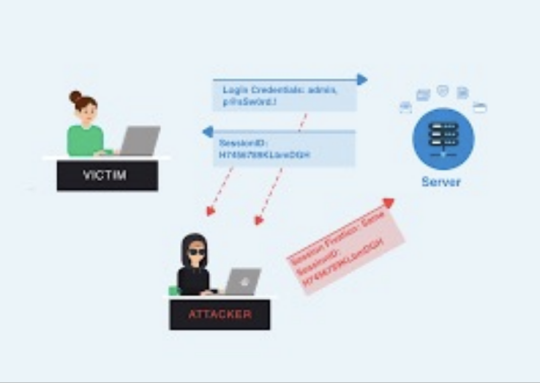
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Computer Support
Feeling overwhelmed after a computer problem is completely natural. But it should be fixed right away. Our technicians bring the right tools, certifications, experience and computer support to the table in order to correctly diagnose and repair any problem you may be suffering from. We are Monmouth Computer and we have been in business since 2004. We also happen to specialize in personalized computer repair services in your community.

Wondering what the top three most common computer problems we see are? Check them out:
1. Sluggish performance can often be fixed with a memory upgrade. If your computer is failing to perform like it used to, let our pros upgrade your computer’s memory (RAM) to increase speed and performance.
2. Hard drive failures are a common problem to face. If your hard drive has suffered a catastrophic failure, call Monmouth Computer Associates. We are here to help you quickly so we can back up your data and install or upgrade your hard drive. This will regain your device’s peak performance.
3. Slow systems are another culprit. Monmouth Computer Associates can perform a network assessment to identify performance issues related to workstation storage, memory, and older operating systems that can decrease speed.
So, if you’re experiencing a computer crash, broken laptop screen, blue screen, data corruption, or general malfunction, Monmouth Computer Associates is your go-to resource for comprehensive computer support.
Ready to learn more? Contact Monmouth Computer Associates for fast service, affordable prices and attention to detail at 732-963-1707 today.

Why Panic? Call Us!
When your computer gets you in a tizzy and won’t do what you need it to, first, don’t panic, just call us. Rest easy knowing we can repair any desktop computer, workstation, server, networking equipment and more. Trust us, chances are good that we can get you back to normal again after a frustrating computer glitch, failure or other issue.
Any of these problems happening to you at the moment?
· Virus or spyware infections
· Frequent freezing and/or blue screens
· A slow running computer
· Error messages
· A system that fails to turn on
· Internet access that’s frequently down
· Repeated pop-ups
If so, call Monmouth Computer Associates before the problem spirals out of your control and you make things worse by tinkering with it.
Let the pros handle the following computer support:
· Data recovery – Recover lost documents and files from any storage media
· Maintenance – System maintenance and optimization
· Security – Virus and spyware removal and clean-up
· Performance – Speed up slow systems

Let’s break those down even further into specific problems our clients contend with on a regular basis:
1. Memory Upgrade Installations
2. Virus and Spyware Clean-Up and Recovery
3. Laptop Motherboard Repair
4. Windows Server Error Messages
5. Malware and Spyware Removal
6. BSOD "Blue Screen of Death"
7. Clicking Hard Drive
8. Windows Blue Screen
9. Replace Video Card
10. Data Recovery From Damaged Laptop
11. Exchange Server Data Corruption
12. Desktop PC Motherboard Replacement
13. Windows Operating System Will Not Boot
14. POST Boot Error Messages
15. IIS Web Server Not Running
16. PHP Installation/Configuration on IIS
17. Workstation PC Data Migration
18. Email Server Rejecting Messages
19. Windows Troubleshooting
20. Data Recovery From Server Hard Drives
21. Network Data Migration
22. ASP Web Site Not Operational
23. CD/DVD Drive Will Not Read Discs
24. Improper Shutdown Caused Blue Screen

Computer support services: it’s just what we do. We know how important a seamless office or home computer system is to your productivity. Computer malfunctions and service disruptions can prevent you from running your business or being productive at home. We will be there for you in your time of need.
Make the call to Monmouth Computer Associates for any insanely frustrating computer issue you may have.
Contact Monmouth Computer
To find out how our computer repair or support services can help you, contact us, Monmouth Computer Associates is your trusted destination for local emergency service 24x7.
1 note
·
View note
Text
Aries March Navigium Isidis

By shirleytwofeathers
When Egypt became part of the Roman Empire, Greek merchants brought the worship of Isis from Alexandria to Rome and invoked Her as inventor of the sail, patron of navigation, and ruler of the waves.
Possibly the most well known Isiac festival of the Roman world was the Navigium Isidis, celebrated on the 5th of March. As part of the festivities, a a festive carnival procession was performed in honour of Isis, and the Vessel of Isis, laden with offerings of precious spices and milk libations, is launched.
Here is a colorful and detailed eye-witness account of the procession and the ceremony:
Soon the sun of gold arose and sent the clouds of thick night flying; and lo, a crowd of people replenished the streets, filing in triumphal religious procession. It seemed to me that the whole world, independent of my own high spirits, was happy. The dusky clouds were routed; and the heavens shone with clear sheer splendour of their native light.
Presently the vanguard of the grand procession came in view. It was composed of a number of people in fancy dress of their own choosing; a man wearing a soldier’s sword-belt; another dressed as a huntsman, a thick cloak caught up to his waist with hunting knife and javelin; another who wore gilt sandals, a wig, a silk dress and expensive jewellery and pretended to be a woman.
Then a man with heavy boots, shield, helmet and sword, looking as though he had walked straight out of the gladiators’ school; a pretended magistrate with purple robe and rods of office; a philosopher with cloak, staff, clogs and billy-goat beard; a bird catcher, carrying lime and a long reed; a fisherman with another long reed and a fish hook.
Oh, yes, and a tame she-bear, dressed like a woman, carried in a sedan chair; and an ape in a straw hat and a saffron-coloured Phrygian cloak with a gold cup grasped in its paws – a caricature of Jupiter’s beautiful cup-bearer Ganymede.
Finally an ass with wings glued to its shoulders and a doddering old man seated on its rump; you would have laughed like anything at that pair, supposed to be Pegasus and Bellerophon. These fancy-dress comedians kept running in and out of the crowd, and behind them came the procession proper.
At the head walked women crowned with flowers, who pulled more flowers out of the folds of their beautiful white dresses and scattered them along the road; their joy in the Savouriness appeared in every gesture.
Next came women with polished mirrors tied to the backs of their heads, which gave all who followed them the illusion of coming to meet the Goddess, rather than marching before her.
Next, a party of women with ivory combs in their hands who made a pantomime of combing the Goddess’s royal hair, and another party with bottles of perfume who sprinkled the road with balsam and other precious perfumes; and behind these a mixed company of women and men who addressed the Goddess as “Daughter of the Stars” and propitiated her by carrying every sort of light – lamps, torches, wax-candles and so forth.
Next came musicians with pipes and flutes, followed by a party of carefully chosen choir-boys singing a hymn in which an inspired poet had explained the origin of the procession.
The temple pipers of the great god Serapis were there too, playing their religious anthem on pipes with slanting mouth-pieces and tubes curving around their right ears; also a number of beadles and whiffers crying: “Make way there, way for the Goddess!”
Then followed a great crowd of the Goddess’s initiates, men and women of all classes and every age, their pure white linen clothes shining brightly. The women wore their hair tied up in glossy coils under gauze head-dresses; the men’s heads were completely shaven, representing the Goddess’s bright earthly stars, and they carried rattles of brass, silver and even gold, which kept up a shrill and ceaseless tinkling.
The leading priests, also clothed in white linen drawn tight across their breasts and hanging down to their feet, carried the oracular emblems of the deity. The High Priest held a bright lamp, which was not at all like the lamps we use at night banquets; it was a golden boat-shaped affair with a tall tongue of flame mounting from a hole in the centre.
The second priest held an auxiliaria, or sacrificial pot, in each of his hands – the name refers to the Goddess’s providence in helping her devotees. The third priest carried a miniature palm-tree with gold leaves, also the serpent wand of Mercury. The fourth carried the model of a left hand with the fingers stretched out, which is an emblem of justice because the left hand, with its natural slowness and lack of any craft or subtlety, seems more impartial than the right. He also held a golden vessel, rounded in the shape of a woman’s breast, from the nipple of which a thin stream of milk fell to the ground. The fifth carried a winnowing fan woven with golden rods, not osiers. Then came a man, not one of the five, carrying a wine-jar.
Next in the procession followed those deities that deigned to walk on human feet. Here was the frightening messenger of the gods of Heaven, and of the gods of the dead: Anubis with a face black on one side, golden on the other, walking erect and holding his herald’s wand in one hand, and in the other a green palm branch. Behind, danced a man carrying on his shoulders, seated upright, the statue of a cow, representing the Goddess as the fruitful Mother of us all.
Then along came a priest with a box containing the secret implements of her wonderful cult. Another fortunate priest had an ancient emblem of her godhead hidden in the lap of his robe; this was not make in the shape of any beast, wild or tame, or any bird or human being, but the exquisite beauty of its workmanship no less than the originality of its design called for admiration and awe.
It was a symbol of the sublime and ineffable mysteries of the Goddess, which are never to be divulged a small vessel of burnished gold, upon which Egyptian hieroglyphics were thickly crowded with a rounded bottom, a long spout, and a generously curving handle along which sprawled an asp, raising his head and displaying its scaly, wrinkled, puffed-out throat…
Meanwhile the pageant moved slowly on and we approached the sea shore… There the divine emblems were arranged in due order and there with solemn prayers the chaste lipped priest consecrated and dedicated to the Goddess a beautifully built ship, with Egyptian hieroglyphics painted over the entire hull; but first he carefully purified it with a lighted torch, an egg and sulphur. The sail was shining white linen, inscribed in large letters with the prayer for the Goddess’s protection of shipping during the new sailing season.
The long fir mast with its shining head was now stepped, and we admired the gilded prow shaped like the neck of Isis’s sacred goose, and the long, highly-polished keel cut from a solid trunk of citrus-wood. Then all present, both priesthood and laity, began zealously stowing aboard winnowing-fans heaped with aromatics and other votive offerings and poured an abundant stream of milk into the sea as a libation.
When the ship was loaded with generous gifts and prayers for good fortune, they cut the anchor cables and she slipped across the bay with a serene breeze behind her that seemed to have sprung up for her sake alone. When she stood so far out to sea that we could no longer keep her in view, the priests took up the sacred emblems again and started happily back towards the temple, in the same orderly procession as before.
On our arrival the High Priest and the priests who carried the oracular emblems were admitted into the Goddess’s sanctuary with other initiates and restored them to their proper places. Then one of them, known as the Doctor of Divinity, presided at the gate of the sanctuary over a meeting of the Shrine-bearers, as the highest order of the priests of Isis are called. He went up into a high pulpit with a book and read out a Latin blessing upon “our liege lord, the Emperor, and upon the Senate, and upon the Order of Knights, and upon the Commons of Rome, and upon all sailors and all ships who owe obedience to the aforesaid powers.”
Then he uttered the traditional Greek formula, “Ploeaphesia”, meaning that vessels were now permitted to sail, to which the people responded with a great cheer and dispersed happily to their homes, taking all kinds of decorations with them; such as olive boughs, scent shrubs and garlands of flowers, but first kissing the feet of a silver statue of the Goddess that stood on the temple steps.
From: The Golden Ass
https://shirleytwofeathers.com/The_Blog/pagancalendar/category/march/page/4/
3 notes
·
View notes
Text
VeryUtils Metafile (EMF, WMF) to PDF Converter Command Line
VeryUtils Metafile (EMF, WMF) to PDF Converter Command Line can be used to convert EMF, WMF, and RTF files into Adobe PDF files. The graphic file (EMF, WMF) to PDF converter can convert enhanced metafile files and rich text format (RTF) to PDF while preserving vector and text information. This results in small PDF files that can be printed at high resolution, making the conversion of graphic files (EMF, WMF) to PDF superior to other solutions that convert embedded graphic files into bitmaps. The graphic file (EMF, WMF) to PDF supports common PDF features, including compression and 128-bit encryption, and it is the first command-line application that allows embedding font subsets to reduce file size.

In the realm of document and image conversion, having a reliable tool at your disposal is essential. VeryUtils Metafile (EMF, WMF) to PDF Converter Command Line emerges as the go-to solution for efficiently converting EMF, WMF, and RTF files into Adobe PDF format.
✅ Preserving Vector and Text Information VeryUtils Metafile (EMF, WMF) to PDF Converter is designed to excel in preserving the vector and text information within your files. This means that when converting enhanced metafiles and Rich Text Format (RTF) files to PDF, it maintains the integrity of your documents. Unlike other solutions that convert embedded metafiles into less flexible bitmaps, this tool ensures that your resulting PDF files remain sharp and clear. This preservation of vector and text information results in smaller PDF file sizes that can be printed at high resolutions, setting it apart from other conversion methods.
✅ Independence from Virtual PDF Printers One key advantage of VeryUtils Metafile (EMF, WMF) to PDF Converter is its complete independence from virtual PDF printers. Unlike solutions that rely on such printers, this converter operates without dependencies, resulting in faster and more efficient file conversions. By removing the need for virtual printers, it eliminates potential compatibility issues, providing a seamless and hassle-free conversion experience.
✅ Batch Conversion and Document Combination This powerful tool not only simplifies the conversion of individual EMF, WMF, and RTF files to PDF format but also offers the ability to combine multiple documents into a single PDF file. Whether you need to convert tables, fonts, colors, styles, or other document elements, VeryUtils Metafile (EMF, WMF) to PDF Converter handles the task seamlessly. This batch processing feature streamlines your workflow, saving you time and effort in managing multiple files.
✅ Developer-Friendly Integration Metafile to PDF Converter is designed with developers in mind, offering multiple integration options. It provides an easily integrated COM object, DLL library, and command-line interface, enabling developers to access the converter using programming or scripting languages like Visual Basic, C/C++, Delphi, ASP, PHP, C#, and .NET. Whether you need to perform file conversions consecutively or simultaneously, this tool provides the flexibility and functionality required for your specific needs.
✅ Licensing Options Users have the flexibility to choose between two licensing options based on their usage scenarios:
Server License: Ideal for production servers, this license allows seamless integration into ASP, PHP, C#, .NET, and other server-side applications.
Developer License: With a developer license, you gain royalty-free runtime desktop distribution, enabling you to run the converter on any number of servers or computers. This option suits developers and organizations with diverse conversion requirements.
✅ Key Features Summarized • Standalone software, no Adobe Acrobat or Reader dependency. • No reliance on printer driver products. • Supports high-volume batch conversion for efficient processing. • Achieves the smallest PDF file sizes during conversion. • Provides password protection with 40 or 128-bit encryption. • Customizable document title, subject, author, and keywords. • Supports wildcard characters for file selection. • Offers command-line versions for batch and unattended operations. • Creates fully text-searchable PDF documents in Adobe Reader. • Suitable for web-based applications for real-time RTF, WMF, EMF to PDF conversion. • Facilitates merging of multiple PDF files into a single document. • Compatible with various Windows platforms.
✅ Image to PDF Conversion Utility In addition to its capabilities with metafiles and RTF files, Metafile to PDF Converter Command Line includes a robust image to PDF conversion utility. This utility supports various image formats such as TIFF, JPG, JPEG, PNG, GIF, PCD, PSD, TGA, BMP, DCX, PIC, EMF, WMF, and more. It offers features like automatic despeckling, skew correction, and efficient compression processing, optimizing space usage in resulting PDF files. You can generate bookmarks, specify resolutions, and merge multiple image files into a single PDF file, making it a comprehensive solution for image conversion needs.
✅ Supported Conversions VeryUtils Metafile (EMF, WMF) to PDF Converter Command Line supports a wide range of conversions, including: • EMF and WMF to PDF, PS (Postscript), TIF, TIFF, JPG, JPEG, GIF, PNG, BMP, WMF, EMF, PCX, TGA, JP2, PNM • RTF to PDF, PS (Postscript), TIF, TIFF, JPG, JPEG, GIF, PNG, BMP, WMF, EMF, PCX, TGA, JP2, PNM • TIFF, JPG, JPEG, PNG, GIF, PCD, PSD, TGA, BMP, DCX, PIC, EMF, WMF, and more image formats to PDF
VeryUtils Metafile (EMF, WMF) to PDF Converter Command Line is your ultimate solution for hassle-free and efficient file conversion. Its versatility, developer-friendly features, and support for batch processing make it a valuable tool for businesses and individuals alike. Whether you need to convert a single file or manage large volumes of data, this converter ensures that the vector and text information in your documents remain intact for high-quality PDF output. Don't miss the opportunity to explore the possibilities of this powerful conversion tool.
✅ Custom Development Service If you are interested in purchasing this software or developing a customized solution based on it, do not hesitate to contact us through the provided link. We look forward to working with you and providing developer assistance as needed.
0 notes
Text
Benefits of Outsourcing Mortgage Form Processing Work
The mortgage industry has witnessed variations with some of the prevalent changes pertinent to a price war, various regulations that added penalty risks for non-compliance and further evolved with the increase in loan demand. But this ever-changing latitude of mortgage determined lenders to identify ground-breaking solutions in order to satisfy inconsistent demand predominant in the market. This varying trend has been possible with the proper integration of technology, capabilities, transformation and lending functions. These combinations of factors may hamper banks and mortgage companies to work on the core competencies, making them viable to engage with BPO companies who are qualified enough to address these issues.
These services are not restricted to banks and mortgage but various other organizations like Insurance organizations, Educational Institutes and Libraries, Legal Companies, Educational Institutes and Libraries, Logistics Companies and Retailers need these services as they deal with different varieties of forms for instance Vouchers, Invoices, Insurance Papers, Medical Claims, Purchase Orders, Financial and Legal Documents, Tax statements and many more. This necessitates streamlined network for easy retrieval facilities and structured form processing services suitable for business size and business profile. With a lot of paperwork subjected with a legal letter, loan applications and loan forms which makes it necessary to manage tasks quickly and accurately.
The main objective of mortgage form processing outsourcing is to assist banks and mortgage companies to come through in this competitive landscape to manage more loan case, lowest cost per loan and maintain a loyal customer base. But there are some more advantages which further postulate to outsource mortgage form processing work:
Benefits can be Leveraged by Small Enterprises as Well One of the myths that people come across that outsourcing can only be benefitted by larger companies. But smaller community banks and lending companies are subjected to risk and can leverage the benefits of outsourcing mortgage form processing work.
Big banks and mortgage companies have access to knowledge of mortgage standards and regulations that ensure compliance. But outsourcing the task enhances flexibility in order to handle technology-related changes, lower infrastructure cost, overhead requirements, and integrated automated system with utmost accuracy.
Faster Turnaround By incorporating the potential of professional forms processing services with advanced technology, customized solutions are provided irrespective whether in a structured database form or in document management systems. We believe that the mortgage industry operates in a cyclical nature to contour operations efficiently. It encourages streamlining results to enhance efficiency and improve accuracy which enables companies not only to close the loan faster but correspond to the demand, handling cases efficiently by controlling the cost per loan.
Prioritize Customer Satisfaction BPOs recruit the best of the talent where they are competent to extract valuable data from every sort of form irrespective of whether structured or unstructured, scan paper documents, digitize and index them as per the preference of file format. They outline the best possible strategy to streamline business processes, accelerate loan processing, increase productivity and trigger customer satisfaction at the end of the day.
Simplify Complex Tasks They constitute skilled manpower that can convert huge volumes of hardcopy, image-based forms into electronic formats. They are talented to capture information from a multilingual form with regular updating of legible data. They possess customized software for a highly structured and massive volumes of data that ensure faster delivery with the highest possible quality irrespective of the project size.
It begins with the downloading of forms from client site, loading into customized software, a new database is created, data entered with utmost accuracy, regular quality check-up and delivering the output in a desirable format. These intricacies are out of question for a regular organization where these tasks are considered to be non- core processes.
Integrate Advanced Technology This domain is invaded by OCR/ICR technologies in order to extend customized exports, achieved and back-up in addition to the retrieval facilities. It looks for personnel expertise in HTML, ASP, CGI, PHP, and JSP formats of form processing to deliver in various formats inclusive of CSV, ASCII and database files through CGI scripts.
Impenetrable Infrastructure Most of the BPOs follow robust Information Security Management where data security and confidentiality have strictly adhered. With a strictly safe environment that verbalizes minimal errors with a maximum accuracy of data. They understand that even the smallest error can cause a significant loss for the company. Their services are designed in such a way that affirms the International standards by implementing a stringent privacy policy.
Cover Wide Range of Services BPOs services comprise of underwriting, close documents review, loan modifications, and payoffs. Other services include online data updating on customized forms, connecting to a customer’s database securely over VPN and regular updating through various interfaces. These services are accomplished with high-tech security measures. They have separate certified systems teams that make sure that the project is executed with the utmost efficiency.
A Reliable Partner Any organization looks for greater proficiency, faster processing, and tailor-made solutions, lower human resource cost which can only be extended by any reliable partner. These factors are satisfied by outsourcing mortgage form processing service provider where their services are available 24*7, prioritize 100% customer satisfaction where quality and accuracy are kept at the forefront.
They handle operational shortcomings, extend substantial savings with a competitive advantage which leaves the staff of the organization to focus on the expertise they possess, manage on core activities maintaining the level of services and strategize meticulously to improve the company’s bottom line.
1 note
·
View note
Text
Get an Outstanding Ajax Assignment Help
To decide the overall grades of a college student assignments play a very important role. The students who can secure the top grades have in-depth knowledge of the subject. But most students find it difficult to score well on their programming assignments.
The students who are learning the AJAX programming language face a lot of difficulties in preparing their AJAX assignments and that is why they seek Ajax assignment help. My Academic Helps is the one-stop solution for the students in this case. We have employed the best AJAX programming professionals who are highly experienced in this field. So, you can expect to have the best quality AJAX assignment help from us within your budget. Our experts have in-depth knowledge of programming. You may just let us know your AJAX programming assignment requirements and our assignment experts will provide you with the best possible AJAX assignment solution after understanding your requirements properly. You may also request our experts to prepare your AJAX assignment at the ultimate moment. We will try our best to assist you by providing you with last-minute AJAX assignment assistance.
What is AJAX?
The full form of AJAX is Asynchronous JavaScript and XML. This popular web development concept is utilized in the front end for communications back end. A lot of popular websites like Amazon, Facebook, and Instagram use AJAX for providing the best possible user experience and simplifying the activities of their websites.
Request our professionals for AJAX assignment assistance
The students who are facing difficulties in writing their AJAX assignments may ask our experts for help without any hesitation. We provide simple and easily understandable AJAX assignment solutions to students. We always provide the best quality content at affordable prices. All our experts are highly experienced in composing any type of AJAX assignment. We are working 24×7 to finish your work before the due date. We use the latest programming techniques to compose our AJAX assignments.
What topics do we cover?
Our AJAX programming experts are capable enough to provide you with a solution for every problem you face and that is why you do not need to bother about the AJAX assignment topics. We cover almost all AJAX assignment topics to better assistance to the students in writing their AJAX assignments:
File handling
AJAX PHP
JSON
Error Handling
Functions, variables, loops, and switches
Cookies
AJAX ASP
AJAX Database
Advanced Filters
User Interface Design for AJAX
XML, XML parsers
XML data in AJAX
Callback function
AJAX Gold Framework
Advanced Ajax Transports and JSON
Advanced Ajax to the Server
Site and Application Architecture with AJAX
Whitespace interpretation
Developing an AJAX Library
Why do the learners want to avail of our AJAX assignment assistance?
There are only a few students who are capable enough to write a well-structured and perfect AJAX assignment because they do not have either adequate knowledge or time. That is why students prefer to hire AJAX programmers from My Academic Helps. We also provide Java assignment help in Australia. Students generally prefer to have our services for the following reasons:
A team of qualified programmers:
We have employed the best AJAX programming experts to provide you with a premium-quality AJAX assignment solution. All our experts hold Masters or Ph.D. degrees in computer science.
Affordable prices:
Students who are afraid of taking assignment help due to their low budget feel free to avail of our services because all our services are available at reasonable prices.
Secure payment options:
We have safe and secure payment methods.
100% plagiarism free:
All our content is plagiarism-free.
Unlimited revisions for free:
You may ask our experts to revise your assignment unlimited times. We do not claim any extra charges for that.
You may also ask our experts for literature review assignment help. To avail of our services you just have to drop us an email mentioning your requirements. So, place your order with us right now.
0 notes
Text
How To Choose A Search Engine Optimization Company
Search Engine Optimization Philosophy
This Is potentially the most essential element when deciding which firm to utilize to boost your internet business or business identity. Implementing a search engine optimization or positioning firm that only uses ethical search engine optimization methods or even"white hat" techniques will make certain you minimize the possible danger of being lost, eliminated, penalized, deleted, or banished in the various search engines. Nobody likes waking glassy eyed to the unfortunate fact of becoming"Google sacked" for bending or breaking the search engines' implicit rules or explicit terms of service.
Search Engine Optimization Methodology / Specific Expertise
Can your expert SEO Company only optimize static websites constructed in basic HTML? An upstanding SEO company will have experience working with websites in all the common programming languages and technologies, PHP, ASP, ASPX, HTML, Cold Fusion, Flash etc..
Does your SEO Company have experience optimizing both static and dynamic websites? Can your SEO Company optimize using various e-commerce packages and interfaces such as Monster Commerce, Yahoo Stores, OS Commerce, Storefront.net, Volusion?
Depth Of Optimization / Piecemeal Services
The most basic search engine optimization companies around don't actually perform search engine optimization at all- they are merely submission services which either manually or automatically submit your site to various search engines or directories. Submission companies are typically very inexpensive since no actual coding, linking, or content development takes place on your actual website. Typical pricing runs around $19.95 to $399 per month for these submission type services.
A mid level optimization company gets their hands more firmly on the marketing handle by editing code, analyzing keywords, building links, and adjusting / writing fresh content for your site. They also may do a pinch of off-site optimization, such as press releases, article submissions, and blog writing. Typically, firms of this middle level range charge between $399 and $850 per month.
The highest level search engine placement firm performs the duties described for mid level optimization companies, but also is responsible for conversion tracking and analysis. The emphasis on off-site optimization is also much greater and time consuming. This means that high level optimization firms are essentially responsible for discovering what is working and what is not working throughout the entire customer experience - from initial search through conversion. More man hours per month also means a higher fee that search engine firms must charge to cover their costs. The usual pricing range for these firms' are 850.00 all the way around $10,000 a month, but normally, you are going to be considering fees over the $1,000 per month range.
A piecemeal marketing firm is one that Treats different pieces of an optimization effort as different entities. By way of instance, an optimization provider might charge different fees exclusively for"linking" or"content construction." This piecemeal approach can be damaging. Successful optimization is the synergy of numerous attempts on multiple fronts, sometimes simultaneous, and at times in series. Piecing together different facets of an optimization effort generally reaps poorer outcomes than a thorough plan.
System Of Evaluation / Reporting
The Vast majority of search engine optimisation businesses cringe at the idea of enabling their customers to rate their job. A search engine optimisation firm does the reverse. There are four tools we advocate using in tandem to assess an internet search engine optimization firm's work / functionality.
1. Actual Time Statistics / Conversion Analysis Software
Being Able to determine visitors conversions and gains in real time may be useful window in assessing the way your SEO Firm is doing. Possessing the ability to find out who's coming to your website, from what search engines they're coming from, and also the specific keyword phrase used within the search query is a vital tool.
2. Positioning or Visibility Reports
Being Emailed bi-weekly placement reports about the special keywords that you are interested in rank highly for could be incredibly helpful. A presence percentage, that's the proportion of people which are discovering you for key words which are important to your company - to the Major Search Engines - Google, Yahoo, AOL, and MSN can also be significant. Ensure that your company does not overdue the automatic search engine inquiries but the search engines might consider this spamming their databases.
3. Alexa Rating:
You May download the Alexa Toolbar right now from alexa.com. This provides you a good review of the overall traffic trend throughout the previous 3 months for your site compared to other existing websites. In case you've got a brand-new site, chances are you won't even possess an alexa score or observable data in any way. The alexa score additionally shows you, generally speaking, how your site stacks up- visitors wise- compared to your opponents or business affiliates. The lower your alexa score the more visitors your website is generating compared to other websites in the alexa universe. Please be aware, if your website has an alexa score of"1" this does not mean that you would be the most visited website on the net - it probably means you're running a Yahoo Store- in this circumstance, it's identifying Yahoo's general visitors, rather than your personal website. A general tool in this way may provide you a fast general impression of visitors growth and tendencies. Be cautious though, the amounts are generalities (like the tv Nielsen Ratings) rather than absolute figures.
4. Google PageRank
You can download the Google Toolbar right now by visiting google.toolbar.com. Click the options tab and then wait for the"display PageRank" step. You'll have the ability to learn how Google is evaluation the significance of your website on a scale of 0-10. As an optimization firm proceeds with your effort you may check occasionally to determine how the amount is increasing. The normal site might observe a PageRank growth of one or two points within the duration of an optimization effort. Remember it is a lot easier to boost your PageRank in the ends of this spectrum. Since you approach higher PageRanks it gets more difficult to your score to balloon.
Due Diligence: Corporate Goals / Industry And Keyword Research
How Does the SEO Company you're considering perform its up-front legwork regarding your company, business and company objectives? Can they ask questions about:
What your company goals (both short and long Word ) are, your business, your competitors. What key words are now working for you? What PPC (Pay Per Click) phrases are effective? What PPC engines (Adwords, Overture, MSN/Live) are now powerful? How your website is made? Is your website static or dynamic?
What applications does your SEO Firm use to execute its own key word research?
How about Wordtracker, WebCEO, or Keyword Elite? What about the fundamental Overture keyword suggestion tool or the generic Google keyword suggestion tool provided by Adwords. Can they use a mix of the fundamental tools? What about proprietary key word investigation methodology? Do they've dedicated tools which were developed in house, or with a third party?
Customer to Account Manager Ratio
Not many SEO Firms prefer to market their customer to account supervisor ratio. This is actually the ratio representing the amount of customers that every account manager manages at any particular time. The lower the number of customers each account supervisor helps, chances are the greater the service and also the greater the amount of personal attention. We advocate a search engine optimization accounts supervisor supports significantly less than thirty customers at any particular time.
Man-Hours Per Month
The Amount of person hours per Month your SEO manufacturing department really dedicates to your company is essential. It's more than clever to request a time period allotment quote before starting an optimization effort. Everything you expect to get and what's actually delivered ought to be appropriate in line.
Business Structure and Size
Can Your SEO Company include a notebook computer with your account manager working from his cellar sitting with a salivating golden retriever? Is your SEO firm a bureaucratic nightmare which compels you to complete trouble tickets if you require help immediately?
Your Ethical search engine optimisation firm ought to be somewhere inside the sweet spot of not too little rather than overly big. You need individual focus, but you'd also like to understand there's more than 1 head, calculating your next company moves.
Direction
Does your Ethical search engine optimisation firm have a good management team? Can they have a management staff in any respect? Are the companies you're considering privately held or publicly traded? Is the owner of the optimisation firm an absentee landlord or a energetic member of the SEO community? It's not from the question to request the curriculum vitae or resume of all the forces which are, in actuality, it makes great sense if you're entrusting this business with not just your company but your own livelihood. In the end, SEO professionals don't have any board certification which you may count on in order to look at their history.

Standing / Importance
Has Your SEO Company received multiple complaints through the Better Business Bureau? Assess the better business bureau reports and see whether there are unresolved complaints. From time to time customers could file complaints, but we think it's the timely handling of those inquiries that are even more significant when thinking about an optimization company to utilize.
Past Results / Company SEO Rankings
Each SEO Company Must have detailed reports concerning previous client successes. The reports must include specifics regarding optimization objectives and timelines. Reporting on previous clients should additionally focus between and within multiple businesses. You need to always know about a foundation point - in which a specific customer started out before the optimization firm commencing an SEO effort. Is your SEO company itself doing badly at the search engines? A reduced Google PageRank (under a 5) could be a sign your SEO company has not existed for so long as you might like.
References / Company Shelf Life
Each SEO firm Should have strong references across fields and industries in the business to consumer businesses in addition to business to business arenas. Applicants ought to stem from not just the previous six months, but if arise from years before your introduction together with the business. If your SEO company performs good work, customers must be around for many years to sing their praises.
Prices / Pricing Structure / Up front Fees
Prices Should be in agreement with the support that the business is supplying - a la the"Consistent Value Proposition" educated at Yale School of Management. A $49.00 per month effort run by a credit card company that doesn't specialize in search engine optimization may not be the best option for an in-depth or higher level optimization effort. An SEO firm should also just offer costing when they have a very clear comprehension of your organization, goals, and the job entailed. Blanketed price structures may result in frustration, unrealized expectations, and finally collapse. Additionally fret if your optimisation company demands a whole six month payment up front so as to simply"get started."
The Perfect optimization provider charges an up front charge and yearly recurring fee that's commensurate with the services which are actually being done. A premium excellent optimization company that operates on your website using 30-60 man-hours a month can't possibly charge a $49.00 each half an hour to execute its services.
Redundancy
A Nasty case of the bird flu strikes your unsuspecting accounts supervisor right where it counts! Is it true that your optimization firm have the capacity to easily transition the present condition of your effort to a different skilled optimization pro? Each SEO firm needs to have a system where knowledge concerning existing accounts are readily deducted from 1 person to another. If there will be a tragedy seeing your accounts supervisor, you need to feel comfortable your company continues to flourish whatever the conditions.
Quality Control
Each SEO company needs to have Someone overseeing your account supervisor to make certain every last"I" is dotted and each"t" is crossed. Your account supervisor ought to be accountable for the achievement of your effort, but an additional pair of eyes may sometimes be required to include yet another variable weighing on your side of succeeding.
Promises / Results Timeline
We have heard SEO Companies guarantee first page listings in Google for aggressive phrases in 48-Hours. If your SEO sales agent is overzealous and unrealistic, it ought to be an indication that this is probably a company to steer clear from. Gaining search engine listings might be hard fought, a time-consuming struggle that comes from diligent work and smart preparation.
Production Staff Quality
The production team should Be split between account managers and technical production technicians. Account managers would be the heart of an advertising effort management and execution. Account managers need to have the ability to execute each the real coding, linking, and articles structure for every single customer. As an advertising effort grows and increases in sophistication, they ought to have the ability to call upon their service staff or manufacturing department to finish technical work orders for every customer. The more technical every member of the manufacturing section, the more effective they'll be at finishing their job (thank Henry Ford with this).
Location / Proximity
When you telephone your Account supervisor or SEO firm would you hear some curious two beeps Prior to being joined to an individual functioning without air conditioning overseas? Not a fantastic sign. It Is Very Important That you employ a search Engine placement company whose sales force works in tandem with its own Manufacturing department. There should be no disparity between what you Were offered and what was actually delivered. The SEO genius working in your own Consideration needs to be in a position to understand your company, business, and Company goals fast, with no overseas static jamming up communications.To get more detail click https://www.bestseo.sg/seo-expert-singapore/
1 note
·
View note
Text
What is ASP.NET and Why do we need it?
Intro
.Net is a framework that helps developers create web applications and web services that use forms and web technology. It is used to develop desktops and server-based applications. There are a number of programming languages that can be used with .NET, but VB.NET and C# tend to be the most popular among them. It is widely used to build many applications for the Web, phones, desktops, etc. Now that we have an idea about .NET, let us come to the main subject of this article: ASP. NET.
ASP.NET is one of the .NET frameworks. It was developed by Microsoft and is an open-source software that is preceded by the ASP(Active Page Server). The software is used to create dynamic websites and web pages for all types of businesses.
It is built on Common Language Runtime(CLR) that allows a programmer to execute the code using any .NET language. It uses HTML commands to set a browser-to-server bilateral communication.
Components of ASP.NET
The following are the components of ASP. NET-
Razor
It is the standard markup syntax that allows us to embed server code in the web pages. We can perform logical tasks on the view page and we can create expressions, loops, and variables in it.
Authentication
It is the process of getting credentials from the users and using them to identify those users. It also supports customized authentication which means that you can just set the authentication mode for the application to none and then write your own code to perform it.
Caching
A cache merely saves the data outcome created by a page in the memory and this kept result (cache) will be useful for us (users) later. Three principal types of caching exist- page caching, segment caching, and information caching.
State Management
This is about the recognition of the condition of a program at its existing moment. ASP.NET has the ability to write extra codes that is necessary for carrying a transaction initiated by the user from one web page to another in HTTP which is a stateless protocol.
Editor extensions
They assist a developer in the development of Web applications and webpages which includes features such as syntax highlighting and code completion along with others.
Features of ASP.NET
Cross Platform and Container Support- It supports platforms such as Windows, mac OS, and Linux which enables easy deployment and immediate running of ASP.NET applications on these platforms.
Asynchronous Programming Pattern
These blueprints are embraced by all the .Net framework classes, external libraries, and structures. The factor that makes ASP.NET swifter than other frameworks is attributable to the utilization of asynchronous designs in kestrel frameworks.
Web sockets
They are used to compose web-based customer-server programs. These offer back-and-forth correspondence between the browser.
Globalization and Localization
Localization is important for the application to be used globally. ASP.NET can easily localize dates, numbers, and text in the application. It also enables customization of the application for many languages via resource files.
Filters
ASP.NET allows the implementation of functionality that can be applied to “an entire controller or action without modifying the action itself”. They specify caching, error handling, authorization, or any other custom logic you want to implement.
High performance
The introduction of ASP.NET Core and the Kestrel web server has named ASP.NET one of the fastest web application frameworks available. Kestrel web server was redesigned to benefit from asynchronous programming models making it much more lightweight and fast.
Why is ASP.NET suitable for web app development?
ASP.NET is the standard tool for web application development. It is cost-effective and fast allowing developers to solve complex challenges. It is a subset of .NET, and it provides a consistent, and scalable environment for the development of robust web applications.
ASP.NET is easy to use especially if you are relatively new to the development industry. Developers with less coding knowledge can build web applications using this tool.
Performance is an integral part of any web development tool. ASP.NET gives you a smooth performance with little to no crashes or slow down. It provides enhanced and advanced tools which result in the optimization of codes increasing the quality of performance.
ASP.NET is an open-source framework that allows developers to modify, review or contribute to the code as per their needs. It also allows them to add new features and components to the codes available. Aside from this, a huge community of experts and developers have the platform to share their ideas, and answers, and provide guidance to budding developers and creators.
ASP.NET development has fiercely maintained security features which makes it reliable to be used in large firms, government agencies, and other high agencies. The framework provides enhanced application security that has Windows configuration and confirmation. ASP.NET has come up with Manage code and CLR, delivering security options like code access security and role-based control.
Outro
ASP.NET is the “next generation platform” of Microsoft ASP. It is used to build both large and small web applications. It not only offers many updated and new features for the developers but also high-tech performance and security features making it ideal for cooperate and government agencies. It gives you full control over your web application.
1 note
·
View note
Text
Describe Node.js. A cross-platform, open-source server environment called Node.js can be used with Windows, Linux, Unix, macOS, and other operating systems. Node.js is a back-end runtime environment for JavaScript that executes JavaScript code outside of a web browser using the V8 JavaScript Engine. An open source server environment is Node.js. Free to use Node.js Numerous platforms support Node.js (Windows, Linux, Unix, Mac OS X, etc.) JavaScript is used by Node.js on the server. Why use Node.js? Asynchronous programming is used by Node.js. Opening a file on the server and sending the content to the client is a regular activity for a web server. Way a file request is handled by PHP or ASP: Sends the task to the file system on the computer. The file system opens and reads the file while you wait. Gives the client its stuff back. Able to handle the upcoming request.
The way Node.js responds to a file request
Sends the task to the file system on the computer. Able to handle the upcoming request. The server sends the content to the client after the file system has opened and read the file. Node.js does away with the waiting and just moves on to the subsequent request. Single-threaded, non-blocking, asynchronous programming, which uses little memory, is supported by Node.js.
How Effective Is Node.js? Node.js has the ability to create, open, read, write, remove, and close files on a server and can provide dynamic page content. Node.js may gather data using forms. In your database, Node.js can add, delete, and edit data.
BEST NODE JS TRAINING INSTITUTE IN NOIDA.

0 notes