#AWS Network Firewall
Explore tagged Tumblr posts
Text
AWS Network Firewall: Flow-Based Control Improves Security

AWS Network Firewall
Using AWS Network Firewall for Flow Management Improves Network Security
AWS Network Firewall manages stateful network firewalls and intrusion detection and prevention. It lets you apply security rules to VPC network traffic for better control. This blog article describes flow capture and flow flush, new AWS Network Firewall technologies that increase network visibility and security policy enforcement. While flow flush selectively terminates some or all flows, flow capture provides complete access into current network flows for monitoring and troubleshooting. These features help with network monitoring, troubleshooting, policy changes, and security circumstances that need isolating infected computers quickly.
Traffic flow is permanent if the firewall allows it. For compliance with your revised security needs, you may want to analyse and re-apply the new policy on existing flows after changing firewall rules, such as switching from a broader to a more targeted firewall policy.
This is especially beneficial in fast-paced security scenarios or dynamic cloud settings with changing security rules. These new features allow users better insight and control over this crucial firewall activity by natively recognising active flows and selectively flushing their connection data from the firewall's inspection engine. You may maintain network policy enforcement during scheduled security upgrades or security events by flushing dubious network traffic flows.
The AWS Network Firewall API and AWS Management Console offer these features.
Before AWS starts employing these new functionalities, let's examine some new terminology.
Terminology comprehension:
AWS Network Firewall's active flow is a monitored network connection with a uniquely identified source IP, destination IP, source port, destination port, and protocol. Flow capture and flush characteristics refer to active network flows as non-closed. This includes TCP sessions in the NEW or ESTABLISHED stage.
Flow filters match active network flows based on one or more parameters, such as source IP address, destination IP address, source port, destination port, or protocol. One flow filter matches several network flows that meet requirements.
This firewall function captures all active flows at a certain period using the supplied flow filter or filters. This functionality lets you see network traffic, security events, and flows before flushing. According to your flow filter(s), flow flush flushes a subset of active flows from the firewall flow table at a certain time. After flushing, packets are appraised as midstream flows based on stream exception criteria.
Summary: Flow capture and flush workflow
The open-source intrusion detection and prevention system Suricata is used by AWS Network Firewall for stateful inspection. When evaluating VPC traffic, the firewall stores detailed connection status data in a flow table. This means the firewall knows the full context of every network connection, not simply packets.
Depending on flow filter criteria like IP address, port, or protocol, you may need to flush flows to clear all active flows (during troubleshooting or maintenance) or selectively (during firewall rule updates, to flush long-running flows). Either flush flows directly using pre-specified filters or catch flows for examination before flushing. The firewall operation history lets you track and verify capture and flush actions.
Check out the flush and flow capture features:
These functions are accessible via console:
Enter the Amazon VPC console after login into AWS management.
Select Firewalls under Network Firewall in the navigation pane.
Firewalls: Select the firewall to collect or flush flows.
Firewall activities includes Configure flow capture and flush.
Capturing flow
Using full or partial 5-tuple filters to capture active flows is covered here. In the same VPC, AWS Network Firewall checks traffic on subnets 10.0.1.0/24 and 10.0.2.0/24. Find and flush active TCP port 80 traffic from 10.0.1.0/24 to 10.0.2.0/24.
Use the console to capture flow:
Select Configure Flow Capture to discover active flows. A new window appears.
Select Availability Zone.
The destination or source address must be entered.
Protocol (ICMP, TCP, UDP, IPv6-ICMP, or SCTP), Source Port, Destination Port, and Minimum Age of Flow are optional.
Select “Add filter.” Add up to 20 filters using entire or partial 5-tuple combinations.
Select “Start capture.”
Only one filter is needed to catch TCP port 80 traffic from subnet 10.0.1.0/24 to 10.0.2.0/24. Additional filters are shown to demonstrate filter choices. Specialised filters speed up operation.
After capture, the flow operation displays filter flows.
Flushing
Learn how to flush flows using a whole or partial 5-tuple in this section. Use the capture approach in the previous section to detect active flows before flushing. You may also specify new filters to flush certain active flows, starting a new flush operation.
Console-initiated flow flush:
Option 1: Record, erase
Select “Configure Flow.” Use the Configure flow capture process to cleanse flows that match the filters you previously defined.
Select Start flush in to flush.
Option 2: Direct flush
For firewall operations, choose “Set up flow flush”.
Set filter settings.
Start flushing.
You may inspect flushed flows after the flow flush using either option.
You can collect and flush flow to validate flushing again. Clients usually rejoin after flushing flows. The firewall's flow table and flow capture data reveal these retries. Minimum age can be used as a filter to reduce repeat flows in flow capture data.
For the stateful engine of your firewall, AWS Network Firewall flow logs show flushed flows. These entries show the flow's previous condition and the rationale field's flushed status.
Historical firewall operations
The Firewall operation history provides capture and flush actions from the preceding 12 hours using AZ-specific operation IDs. Any operation above 12 hours is immediately deleted. Click on a Flow operation ID to view capture or flush flow operation details.
What to know:
One flow capture or flush per AZ per firewall is allowed. If your firewall endpoints are in distinct AZs, you can capture or flush flows simultaneously.
Use Minimum age in Filter settings to identify or flush long-running flows. Only flows active for five minutes or longer are considered when the Minimum Age is 300 seconds.
The firewall policy's stream exception policy applies to packets that reach it after their flow state has been flushed. The reject stream exception policy is recommended for most applications.
Due to the distributed firewall technology, firewall hosts may perform flow capture and flush operations differently. The firewall distributes capture and flush actions instead than executing them in real time.
These traits support IPv4 and IPv6 flows.
For auditing, AWS CloudTrail logs flow capture and flush operations as management events.
In conclusion
This post showed you how to utilise flow capture and flush to detect and clear out existing flows and test your security configurations, including stream exception policies, as needed. These new features allow organisations to monitor network traffic, respond quickly to security problems, and apply updated security policies consistently to all active connections. These features are enabled by default for new and current clients and are free.
#technology#technews#govindhtech#news#technologynews#cloud computing#AWS Network Firewall#Network Firewall#Flow capture and flow flush#Flow capture#flow flush
0 notes
Text
Practice-scene 1


Towering skyscrapers stretched high into the clouds like pixelated monoliths. Roblox Industries, a gleaming beacon of creativity and order. Developers from across the grid flocked to work under its banner, crafting intricate worlds, fine-tuning security, and patching exploits before they could be used against them. At its helm sat Roblox himself—sharp-eyed, disciplined, and always three steps ahead. His mission? To build, protect, and expand his network, no matter the challenge.
Roblox sat at his desk, eyes fixed on the screen, his fingers dancing over the keyboard as he typed. He had deadlines to meet, bugs to fix, a whole system to maintain—no time for distractions.
Unfortunately, fate had other plans.
On the other side, lurking in the shadows, was Corp.666 Unlike its rival, who thrived in chaos, recruiting all the most notorious hackers, glitch exploiters, and black-hat coders that the underworld had to offer. Their leader, Guest666, ruled with a devilish grin and a mind built for destruction. He didn't create—he corrupted. Every firewall, every new update, every so-called "unbreakable" security measure from Roblox Industries was a game, an invitation to crack the code and slither through their very wires.
Guest666: Miss me?
Roblox exhaled sharply through his nose and closed the window. He wasn’t in the mood.
Guest666: Wow, rude. Is that any way to treat an old friend?
Close. Ignore. Keep working.
Guest666: Hellooo? Guest666: Knock knock~ Guest666: I’ll keep going.
Roblox sighed, minimizing the chat entirely. He typed out a command to block all incoming messages from 666.
[Error: User permissions restricted.]
"What the—"
Then the real chaos began. Messages flooded the screen, one after another, stacking on top of each other in an endless barrage.
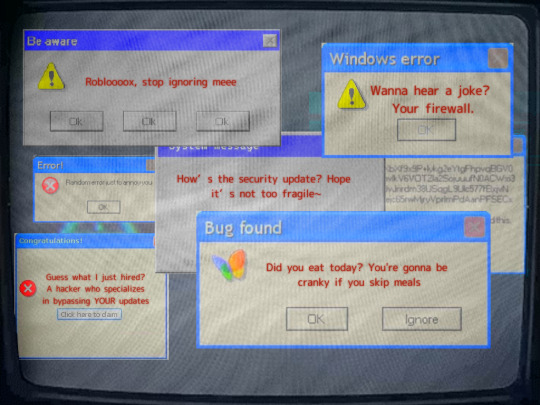
The screen flickered. The messages multiplied. The text turned red, distorting as if the very code itself was being rewritten.
Roblox clenched his jaw, his fingers moving to counter the intrusion. He opened his system diagnostics, started isolating the breach—
then a new window forced itself open.
A video call.
Guest666 sat on the other end, grinning wide, his red eyes glowing with delight. He rested his chin on his hand, tilting his head playfully. "Aww, you look so mad. I love it."
Roblox glared at him. "What do you want?"
666 stretched, yawning dramatically. "Oh, nothing much. Just wanted to see how my favorite rival is doing. You look stressed."
"You just flooded my entire system with garbage messages!"
"Aw, don’t be so sensitive." 666 smirked. "You should thank me—I’m testing your defenses for free."
Roblox took a deep breath, fingers already typing. "Fine. Let’s see how you like it."
A few keystrokes, a silent command—
Thus, Guest666’s screen began to glitch, his smug expression freezing mid-smirk. Then, his entire connection cut out.
Roblox leaned back in his chair, satisfied. "Idiot."
deep down, in the quiet corners of his mind, Roblox felt something strangely familiar in all this. It was routine now—the taunts, the teasing, the cat-and-mouse game they played through code. For every firewall he built, 666 found a way through. For every loophole Guest exploited, Roblox patched it before he could do real damage. ---------------
Roblox barely had a second to breathe after silencing 666's endless messages when the door to his office swung open without a knock.
"Hey there, sport!"
Builderman.
Roblox looked up, already dreading what was coming. The man strode in with the confidence of someone who owned the place—which, of course, he did. His suit was crisp, his smile unwavering, radiating that strange, corporate warmth that made it impossible to outright hate him.
"Got some fresh tasks for ya!" Builderman announced cheerily, slapping a thick folder onto Roblox’s already cluttered desk. "Nothing too crazy—just a couple hundred exploit reports, a few security patches, and, oh! A backlog of bug fixes from last month. You’re the best, buddy. Knew I could count on ya!"
Before Roblox could get a word in—before he could even blink—Builderman turned on his heel and strolled right back out. No pause, no waiting for a response, just pure, unshakable faith that Roblox would handle it.
Roblox stared at the folder. Then at the door. Then back at the folder.
A notification pinged on his screen.
Guest666: PFFFFTTT HAHAHAHAHA
7 notes
·
View notes
Text
A little ficlet for my DCA OC Bastion, who will not stop bullying me until I got this written out SOMEWHERE. And yes, this is partially inspired by/written in the setting of that Apartment Complex multi-OC dating game I posted about before ;3c
tldr: Bastion is a half-disembodied AI who uses it/they pronouns and, despite claiming that it doesn’t care at all about human values or companionship, seems to care an awful lot about YOU

“You have not eaten anything in exactly 6.3 hours.”
“I know, Bastion.”
“Your caloric intake has been below the recommended amount for the last three days,” the voice continues, echoing through the empty air of your room as if you hadn’t said anything at all. “You will eat something of your choosing within the next half-hour, or I will have to take measures in doing it for you.”
“I’m not hungry right now,” you mutter, trying to be quiet enough so that the quip wouldn’t be heard and you can continue your personal project in peace so—
“Why must you be combative about your own health?”
The words almost rumble through the air, echoing from the speakers dotting the corners of almost every single room and hallway of the building. You have to wonder what kind of mics are hooked up with them — or the nearly-microscopic security cameras — because even you barely heard yourself speak.
But before your mind can continue with the annoyed line of thoughts there is a sudden and abrupt grip on your shoulders that pull you back from the laptop and desk, chair wheels squeaking out from the sheer speed and force as Bastion’s tendril-like extensions snake out from the interface port somewhere near the room’s door leading into the hallway.
“Jesus fuck, Bastion I’m not—“
“You are eating,” the voice says, cold and firm, unwavering in a way that can only come from someone like it. It. Not him, it— though you know Bastion couldn’t find an atom of themself that truly cared how others regarded it anyway, but was always steadfast in referring to itself as ‘it’, and you had a feeling there was more nuance to the situation than that.
When you first met the AI construct, it had actually outlined all of the sole priorities that it had been ‘programmed to cared about’, and not one of them was ‘how humans regard my being’. Instead, you think that your health was near the top, followed by a laundry list of legal rules, regulations, and other things that came with Bastion taking on the role of being the apartment building’s literal internal network, firewall and pseudo-VPN.
Still, you’re not sure why YOU are a priority to the AI, and Bastion has not deigned the time to explain it to you either. It seems to rather avoid the topic with all the same stubbornness as you seem to avoid self-care.
“I will allow you the choice of food only once more, please designate something you have a preference for and I will obtain it.”
“God damn,” you murmur. “Just— cereal? I think I can stomach that right now.”
Around your waist and the chair both, the silver-smooth tendril squeezes for just a moment. Not a necessary motion, not in the slightest, but you can’t help but feel a sense of comfort in that little notion alone — a very human motion of affection that Bastion would otherwise deny if you’d brought it up to them.
“I will have a bowl of your favorite kind ready within the next five minutes. Are you able to walk to the kitchen?”
You think about it for a moment before nodding. It doesn’t need to hear your answer; Bastion is always watching.
“Good. I am satisfied with your answer.” Bastion’s tone is cold and calculated as always, nearly monotone from one word to the next, but you can hear something else lingering in the background.
The tendril lingers for a few moments more before finally— gently — letting you go.
“Please be in the kitchen in the next ten minutes,” the voice continues, and then, a brief flicker of humor as it adds, “…Or else the cereal will get soggy.”
#ficlet#writing#sfw#sfw writing#bastion oc#oc bastion#dca oc#fnaf dca oc#daycare attendant oc#the most non-DCA DCA OC i got#not originally inspired by AM but it…. kinda has the same vibes ngl#and ‘pseudo-disembodied’ basically means it has a body bc in this setting it legally HAS TO#but instead they have their body hidden somewhere and they just wanna be a system AI#Bastion likes it when things are very black/white UvU
8 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
re: constantine and technology, he's so bad at it that it's comical.
he didn't have a whole lot of exposure to its evolution outside of his friendship with quantum magic computer nerd ritchie simpson, and now he's old and it's everywhere and he doesn't fucking get it. he's awful with computers, the only washing machines that haven't broken on him are the ones at the laundromat, he got a smartphone once to look important but put a demon inside it to do shit For him (rip the vestibulian), he set up a website once and never looked at it again. makes him very cranky when everyone tells him to update his arsenal because he's tried, man, and it's hard.
on top of your basic old guy stuff, technology doesn't seem to like him, either. (certainly doesn't help that he has a habit of throwing, kicking, smacking, or smashing tech that doesn't work when he needs it to.) vending machines habitually break down around him, chip-and-pin machines at the shops throw up errors, and he has set off more than a few metal detectors just by being in proximity.
there's some argument that can be made about magic interfering with technology, two matrices that should never have intersected etc., but ritchie simpson is Right There combining the two with ease, and even if he's just a quantum theoretical genius, i do think that maguses in the modern age would have figured out ways to let the two meet/marry by now. so what it just comes down to is, either constantine is so bad at it that he breaks everything he touches, or technodemon ritchie is taking sweet, sweet revenge on him from hell. either is equally funny to me.
the majority of his begrudging flirtation with technology comes down to:
chunky dell laptop computer. he uses the same password for almost everything, and the few different ones are all written on a post-it note in a desk drawer. the one thing he's got going for him here is that ever since ritchie hacked his bank account, he's added a couple entangling magic firewalls that will set fire to a hard drive if you try to get in without the authentication invocation to disarm them.
cardboard box full of flip phones, busted smartphones, and sim cards. he breaks/loses so many phones that it's just easier to stock up ahead of time. the flip phones are easy, he buys them off ebay; the smartphones are more of a hunt-and-gather situation. he's not above rinsing out the odd phone repair store/apple store in times of great need, sorry to everyone who needed those things, though he does try to stick to high-end ones so there's a better chance that he's just temporarily denting some rich prick's wallet instead of actually inconveniencing people. he's got free and unlimited network coverage in london, thanks to his friendship with map, but that's highly dependent on whether or not map is pissed at him at the time.
walkman. they were invented while he was in ravenscar and he couldn't really stand listening to the tapes he had for a while after that (reminded him of the band and what happened), but cheryl got him the tenth anniversary model later for christmas and it was well-loved. he gave that one to gemma in 1991 when he was dying, and when he was healed, chas hunted down another one for his birthday.
5gb iPod that holds a hell of a lot more than that, thank you magic. lifted off an ex that was trying to kill him while he was in america, right when it had just come out.
unused e-reader. he was trying to be savvy and up-to-date, but the physical stuff just works for him better. he keeps meaning to give it to chas, but keeps forgetting it exists.
#me: today we are relaxing and queueing things for later#also me: nailing this to everyone's doors like martin luther's fuckin theses#also the number of times ritchie simpson's name came up in this lmao can you tell he's my favorite#but he's also Very entangled in constantine's tech history to be fair so it's acceptable this time#that gifset of him i reblogged earlier reminded me to post this#( headcanons. ) I'M JUST LIKE THE BASTARDS I'VE HATED ALL ME LIFE.
10 notes
·
View notes
Text
Navigating the Cloud: Unleashing the Potential of Amazon Web Services (AWS)
In the dynamic realm of technological progress, Amazon Web Services (AWS) stands as a beacon of innovation, offering unparalleled advantages for enterprises, startups, and individual developers. This article will delve into the compelling reasons behind the adoption of AWS and provide a strategic roadmap for harnessing its transformative capabilities.

Unveiling the Strengths of AWS:
1. Dynamic Scalability: AWS distinguishes itself with its dynamic scalability, empowering users to effortlessly adjust infrastructure based on demand. This adaptability ensures optimal performance without the burden of significant initial investments, making it an ideal solution for businesses with fluctuating workloads.
2. Cost-Efficient Flexibility: Operating on a pay-as-you-go model, AWS delivers cost-efficiency by eliminating the need for large upfront capital expenditures. This financial flexibility is a game-changer for startups and businesses navigating the challenges of variable workloads.
3. Comprehensive Service Portfolio: AWS offers a comprehensive suite of cloud services, spanning computing power, storage, databases, machine learning, and analytics. This expansive portfolio provides users with a versatile and integrated platform to address a myriad of application requirements.
4. Global Accessibility: With a distributed network of data centers, AWS ensures low-latency access on a global scale. This not only enhances user experience but also fortifies application reliability, positioning AWS as the preferred choice for businesses with an international footprint.
5. Security and Compliance Commitment: Security is at the forefront of AWS's priorities, offering robust features for identity and access management, encryption, and compliance with industry standards. This commitment instills confidence in users regarding the safeguarding of their critical data and applications.
6. Catalyst for Innovation and Agility: AWS empowers developers by providing services that allow a concentrated focus on application development rather than infrastructure management. This agility becomes a catalyst for innovation, enabling businesses to respond swiftly to evolving market dynamics.
7. Reliability and High Availability Assurance: The redundancy of data centers, automated backups, and failover capabilities contribute to the high reliability and availability of AWS services. This ensures uninterrupted access to applications even in the face of unforeseen challenges.
8. Ecosystem Synergy and Community Support: An extensive ecosystem with a diverse marketplace and an active community enhances the AWS experience. Third-party integrations, tools, and collaborative forums create a rich environment for users to explore and leverage.

Charting the Course with AWS:
1. Establish an AWS Account: Embark on the AWS journey by creating an account on the AWS website. This foundational step serves as the gateway to accessing and managing the expansive suite of AWS services.
2. Strategic Region Selection: Choose AWS region(s) strategically, factoring in considerations like latency, compliance requirements, and the geographical location of the target audience. This decision profoundly impacts the performance and accessibility of deployed resources.
3. Tailored Service Selection: Customize AWS services to align precisely with the unique requirements of your applications. Common choices include Amazon EC2 for computing, Amazon S3 for storage, and Amazon RDS for databases.
4. Fortify Security Measures: Implement robust security measures by configuring identity and access management (IAM), establishing firewalls, encrypting data, and leveraging additional security features. This comprehensive approach ensures the protection of critical resources.
5. Seamless Application Deployment: Leverage AWS services to deploy applications seamlessly. Tasks include setting up virtual servers (EC2 instances), configuring databases, implementing load balancers, and establishing connections with various AWS services.
6. Continuous Optimization and Monitoring: Maintain a continuous optimization strategy for cost and performance. AWS monitoring tools, such as CloudWatch, provide insights into the health and performance of resources, facilitating efficient resource management.
7. Dynamic Scaling in Action: Harness the power of AWS scalability by adjusting resources based on demand. This can be achieved manually or through the automated capabilities of AWS Auto Scaling, ensuring applications can handle varying workloads effortlessly.
8. Exploration of Advanced Services: As organizational needs evolve, delve into advanced AWS services tailored to specific functionalities. AWS Lambda for serverless computing, AWS SageMaker for machine learning, and AWS Redshift for data analytics offer specialized solutions to enhance application capabilities.
Closing Thoughts: Empowering Success in the Cloud
In conclusion, Amazon Web Services transcends the definition of a mere cloud computing platform; it represents a transformative force. Whether you are navigating the startup landscape, steering an enterprise, or charting an individual developer's course, AWS provides a flexible and potent solution.
Success with AWS lies in a profound understanding of its advantages, strategic deployment of services, and a commitment to continuous optimization. The journey into the cloud with AWS is not just a technological transition; it is a roadmap to innovation, agility, and limitless possibilities. By unlocking the full potential of AWS, businesses and developers can confidently navigate the intricacies of the digital landscape and achieve unprecedented success.
2 notes
·
View notes
Text
This video is literally propaganda, of exactly the kind that you should expect to find on TikTok, and you just don't notice or care because it confirms things that you want to believe anyway. The app promotes videos like this, and suppresses those that are unfavorable to the Chinese state, because that is required of them under the Chinese censorship regime.
To claim that the US is "just as bad or worse" than China on things like worker protections and freedom of speech is profoundly ignorant. The person in that video does not know what they are talking about, and you should not be spreading this uncritically.
This much is true: - The US and Chinese governments both do some good things and many bad things. - The people in both countries have a lot in common, share many of the same struggles, and should push both governments to be better.
However, for nearly all the specific claims, it's dead wrong:
Mass surveillance (in China; in the US) Yes, the US has seen expansion of its surveillance apparatus and erosion of our right to privacy in recent years (especially since the Patriot Act), but China blows everyone else out of the water. They have an immense network of state-controlled CCTV—much of it incorporating computer vision and facial recognition—with the explicit goal of monitoring 100% of public space. They also impose controls on digital activity that make anonymous or private (encrypted) communication practically impossible.
Censorship (in China; in the US) This is just laughable. Efforts to gloss over the uglier parts of US history in some public school districts are reprehensible, but it does not compare to China's "Great Firewall" and nationwide suppression of certain kinds of speech. The fact that you can openly discuss this in news and social media is its own proof. Good journalism being difficult to monetize is a bigger problem, but it's not like it's made easier by additionally having to get government approval for everything you publish and risking imprisonment if you don't.
Freedom of Speech/"You're trying to ban this app right now" The issue with TikTok is not about speech; the same videos and comments can be uploaded anywhere else. But since you mention it, we should note that TikTok was never available in China—they have their own version of the app, Douyin, which complies with their digital censorship and surveillance laws. Because, again, those are far more strict than what we have in the US.
Human Rights Violations Abortion access is a genuine W for China, I'll give you that one. But holy shit do they have some awful things going on too. Honestly it's too depressing for me to dig too far into this, or the Native American and Uyghur situations. It's all terrible.
Working Conditions You cannot be serious with this. You know about sweatshops. Working conditions in China are generally bad. Their lowest minimum wage nationally is less than $1.50/hr. The US has the fifth highest median income worldwide. Get real.
Healthcare Universal healthcare is enviable, and the US really needs to stop artificially restricting its supply of doctors. There's so many factors here that I don't know if comparison is meaningful, but as one point in our defense, healthcare outcomes are still generally better in the US than in China. We spend more for it, but we also earn more to begin with.
Gun Control Yeah, this one is obviously an L for the US. Some people care more about gun ownership; I'm not one of them.
Homelessness (in China; in the US) Homelessness rates per capita seem pretty similar between the two countries, and both are working to address it with government programs, to varying degrees of success. There are people sleeping on streets and under bridges in China, and they have their own anti-homeless architecture, too.
Democracy/Authoritarianism Weird, the video didn't mention this one. You can probably guess why.
you have more in common with the average citizen in china than any us politician
19K notes
·
View notes
Text
Smart Cloud Management: The Key to Growth with Artzen Technologies
In today’s fast-paced digital world, businesses are shifting from traditional IT systems to smarter, more agile cloud infrastructure. As this shift accelerates, companies face increasing challenges around managing cloud resources efficiently. Enter Artzen Technologies—trusted names in smart cloud infrastructure management, helping businesses simplify operations, reduce costs, and unlock scalable growth.
This article explores how Artzen Technologies delivers intelligent cloud management solutions that empower businesses to thrive in a connected, data-driven world.
Why Cloud Infrastructure Management Matters
Cloud computing is no longer something extra—it’s something every business needs. Whether it’s a small startup or a big company, most businesses now use the cloud for storing data, working together, staying secure, and much more. But just moving to the cloud isn’t enough. The real challenge is learning how to manage the cloud the right way.
Without proper management, businesses face:
Unnecessary operational costs
Downtime and performance issues
Security vulnerabilities
Inefficient resource usage
That’s why cloud infrastructure management has become a key focus area—and why smart solutions from experienced IT partners like Artzen Technologies are more critical than ever.
What Is Smart Cloud Management?
Smart cloud management goes beyond basic monitoring. It’s a holistic, automated, and scalable approach to managing your entire cloud ecosystem—including compute power, storage, databases, networks, and security—using intelligent tools and strategies.
Key elements include:
Real-time monitoring of performance and usage
Cost optimization through intelligent resource allocation
Security and compliance management
Automation for updates, backups, and scaling
Centralized dashboards for full visibility and control
With smart cloud management, businesses can streamline their IT operations while maintaining flexibility and responsiveness.
Artzen Technologies: Your Partner in Cloud Excellence
Artzen Technologies is a top IT company from India that focuses on cloud services, software development, and helping businesses go digital. What makes Artzen special is its focus on customers—using strong technical skills to create custom solutions that fit each client’s exact needs.
Whether you're a growing startup or a large enterprise, Artzen Technologies ensures your cloud systems are:
Smartly managed
Secure and compliant
Optimized for growth
Here’s how Artzen Technologies delivers results through its cloud infrastructure services:
1. Custom Cloud Strategy Aligned with Business Goals
No two businesses are alike. Artzen starts by understanding your operations, goals, and pain points. Based on this, the team designs a custom cloud management strategy that fits your budget, performance requirements, and long-term vision.
From selecting the right cloud provider (AWS, Azure, Google Cloud) to designing multi-cloud or hybrid setups, Artzen helps you make decisions that drive real business value.
2. Scalable Infrastructure That Grows With You
Many companies struggle with scalability—either overpaying for unused resources or facing slowdowns during peak usage.
Artzen solves this by designing scalable cloud architectures that adapt in real time. Auto-scaling, load balancing, and containerization (using tools like Kubernetes and Docker) ensure that your cloud setup always matches your demand—no waste, no delays.
3. Enhanced Security and Data Protection
Security is a top concern for any cloud-based operation. Artzen Technologies implements best-in-class security practices to safeguard your data, systems, and users. This includes:
Data encryption at rest and in transit
Role-based access control (RBAC)
Firewall and intrusion detection
Regular security audits and compliance checks
Whether you handle financial data, customer records, or internal operations, Artzen ensures everything is protected by a secure cloud framework.
4. Cost Optimization and Resource Efficiency
It's easy to over-provision or forget about underused resources.
Artzen Technologies uses cloud monitoring tools and smart analytics to:
Identify idle resources
Recommend right-sizing options
Automate cost alerts
Track usage trends
The result? Lower cloud bills and higher ROI without compromising performance.
5. Real-Time Monitoring and Support
Artzen’s cloud solutions come with 24/7 monitoring and support, ensuring any issues are identified and resolved quickly. Using centralized dashboards, you get complete visibility into your infrastructure—CPU usage, memory, storage, traffic, and more.
And when things go wrong? Artzen’s expert team is ready with proactive support and fast response times to minimize downtime.
6. Automation and DevOps Integration
In the modern cloud world, automation is everything. Artzen Technologies incorporates Dev Ops practices and automation tools to:
Speed up deployments
Ensure consistency across environments
Automate backups and patches
Streamline CI/CD pipelines
This not only improves developer productivity but also reduces human error and makes scaling effortless.
Why Choose Artzen Technologies?
Experienced Team: Certified cloud architects and DevOps engineers Tailored Solutions: Custom strategies for your business goals Transparent Communication: No jargon, just clear guidance and results Focus on Growth: Your business success is their top priority
With Artzen Technologies, you don’t just get cloud management—you get a partner invested in your digital growth.
Final Thoughts
In a world where digital agility defines success, smart cloud infrastructure management is no longer optional. It’s a strategic necessity.
With Artzen Technologies as your cloud partner, you get the tools, expertise, and support needed to build a resilient, cost-effective, and scalable cloud ecosystem—one that grows with your business and adapts to change.
Source by
https://webdeveloperservicesinindia.blogspot.com/2025/05/smart-cloud-management-key-to-growth.html
0 notes
Text
Why a DevOps Cost Calculator Is Essential for Scalable DevOps in 2025

In today’s fast-paced digital economy, organizations are under constant pressure to deliver software faster, better, and more reliably. DevOps—a blend of development and operations—is the go-to strategy for achieving that agility. But how do you budget for DevOps in a way that’s transparent and scalable? That’s where a DevOps cost calculator becomes indispensable.
Whether you’re launching a new product or optimizing an existing delivery pipeline, knowing the projected cost of your DevOps strategy helps you avoid budget overruns. The DevOps cost calculator allows organizations to model expected costs and compare various deployment scenarios. This ensures you're not only speeding up your software delivery but also doing so in a financially sustainable manner.
Understanding the Role of a DevOps Cost Calculator
A DevOps cost calculator is a tool that helps organizations estimate the financial resources needed for implementing DevOps strategies. It accounts for factors like infrastructure, tools, personnel, automation, and maintenance. By using a calculator, decision-makers can simulate various team sizes, toolchains, cloud costs, and operational scopes to forecast expenses.
For those wondering How to hire DevOps Developers, a calculator also provides insights into the costs associated with in-house vs. outsourced talent. This becomes particularly helpful when deciding on hiring models and managing DevOps at scale.
Why Accurate Cost Estimation Matters in DevOps
DevOps is not a one-size-fits-all approach. Every organization has unique needs depending on team size, application complexity, cloud usage, and automation levels. A DevOps cost calculator provides a customized overview of these factors, making it easier to allocate resources wisely.
Budget estimation also improves stakeholder communication. When teams can present a detailed cost analysis using a DevOps cost calculator, they’re more likely to secure approvals and avoid mid-project financial surprises. This clarity enhances trust and fosters smoother implementation across departments, especially when engaging with a custom software development company for end-to-end delivery.
Core Components in a DevOps Cost Calculator
When using a DevOps cost calculator, you’ll typically input the following:
Team composition: Number of developers, operations engineers, and QA testers.
Tooling and automation: CI/CD platforms, monitoring tools, container services.
Infrastructure: Cloud usage (AWS, Azure, GCP), servers, network configurations.
Security & compliance: Firewalls, encryption tools, compliance frameworks.
Training & support: Onboarding costs, certifications, support staff.
Many calculators also allow advanced forecasting for integrations, scaling, and high availability architecture—all key considerations from an SDLC complete guide perspective.
Who Should Use a DevOps Cost Calculator?
A DevOps cost calculator isn’t just for financial teams. It’s a powerful tool for:
CTOs and CIOs planning strategic DevOps initiatives.
Project managers tasked with budgeting DevOps pipelines.
Startups wanting to scale infrastructure without waste.
Enterprise architects validating large-scale deployments.
If you're asking yourself, Why Should You Hire DevOps Developers?, the calculator can clarify the cost benefits of building a DevOps team, highlighting potential ROI and trade-offs between in-house and external experts.
Benefits of Using a DevOps Cost Calculator
Using a DevOps cost calculator yields several key advantages:
Budget predictability: Avoid cost overruns by estimating before deployment.
Decision-making clarity: Compare tools, hiring models, and infrastructures.
Better vendor selection: Aligns your needs with what vendors can offer.
Team alignment: Keeps everyone on the same page with clear financial targets.
Partnering with a skilled DevOps app development company further enhances these benefits by helping interpret the calculator's output into actionable strategies. These experts understand how to balance cost with performance, reliability, and compliance.
Common Mistakes to Avoid When Using a DevOps Cost Calculator
While a DevOps cost calculator is a powerful tool, it’s only effective when used correctly. Common pitfalls include:
Underestimating ongoing costs such as monitoring, backups, and security.
Ignoring training and onboarding expenses.
Assuming static resource usage, especially in cloud-native environments.
Overlooking license fees for third-party tools.
To get the most accurate estimates, ensure your data is current and comprehensive. Collaboration with a custom software development company or DevOps consultant can help fine-tune your inputs for precision.
Comparing DevOps Scenarios with a Cost Calculator
One of the most valuable features of a DevOps cost calculator is the ability to simulate different implementation paths. For instance, you can compare:
On-premises vs. cloud deployments
Manual testing vs. automated testing
Container-based vs. serverless architecture
In-house vs. outsourced DevOps engineers
These simulations are critical for long-term planning and strategic decisions. Incorporating the insights from an SDLC complete guide into these scenarios helps align technical choices with business goals.
Integrating Cost Estimation into Your DevOps Strategy
Rather than treating cost estimation as an isolated task, make it a central part of your DevOps planning. Use a DevOps cost calculator during the initial planning stages and update it regularly as project needs evolve.
This not only ensures ongoing cost control but also promotes accountability. Plus, having a consistent financial overview supports better discussions with investors, clients, and stakeholders who want to see clear, data-backed reasoning for your DevOps roadmap.
Consulting with a DevOps app development company at this stage can turn your cost analysis into a competitive advantage, ensuring every dollar spent translates into agility, speed, and resilience.
Conclusion: The DevOps Cost Calculator as a Strategic Tool
In 2025, digital success will be defined by how fast and efficiently companies can build and deploy software. A DevOps cost calculator empowers businesses to make that happen without financial guesswork. From cost modeling and team planning to scaling strategies and vendor negotiations, this tool is indispensable for any forward-thinking organization.
Whether you're wondering How to hire DevOps Developers, planning a new CI/CD pipeline, or evaluating your current infrastructure, don’t proceed without first leveraging a DevOps cost calculator. It’s more than just a budgeting tool—it’s a roadmap for scalable, cost-effective DevOps success.
0 notes
Text
CCNA Certification: Why It Matters for Networking Professionals

In the ever-evolving field of IT, staying updated with the right certifications can determine how fast and how far a professional can grow. One such globally recognized credential is the CCNA (Cisco Certified Network Associate) certification. If you're wondering what is CCNA, it's a foundational certification offered by Cisco that validates a networking professional’s skills in installing, configuring, and troubleshooting networks.
Understanding the Scope of CCNA
The CCNA certification is not just a badge; it's proof of your hands-on ability to work with Cisco networking equipment and technologies. It covers key concepts like:
IP addressing and subnetting
Routing and switching fundamentals
LAN/WAN technologies
Network security basics
Wireless networking
Automation and programmability
With the increasing demand for secure, scalable, and stable networks, professionals who understand these core areas are always in high demand.
Why CCNA Still Holds Relevance in 2025
Despite the rise of advanced certifications and cloud platforms, CCNA remains incredibly relevant. Here’s why:
1. Strong Foundation for a Networking Career
CCNA lays the groundwork for all other Cisco certifications and many non-Cisco ones too. It’s the first step into a world filled with routers, switches, firewalls, and cloud-connected infrastructure.
2. Industry Recognition
Cisco is a leader in the networking world. When employers see CCNA on your resume, they instantly recognize your capability to handle network-related tasks and challenges.
3. Global Validity
Whether you're applying for a job in your local city or overseas, CCNA is accepted worldwide. This opens doors to international career opportunities.
How CCNA Enhances Practical Networking Skills
CCNA isn’t just theory; it emphasizes practical knowledge. During your training or preparation, you will:
Set up real or virtual routers and switches
Create and troubleshoot networks
Configure routing protocols like OSPF
Implement Access Control Lists (ACLs)
Understand how NAT and DHCP work
This hands-on learning builds confidence and prepares you for on-the-job challenges.
Security Awareness with CCNA
One of the newer components of CCNA is its focus on network security. In an age where cyber threats are growing rapidly, understanding basic security principles like firewalls, password policies, and encryption is vital. CCNA introduces these topics to help you build networks that are not only functional but also secure.
The Role of CCNA in Cloud and Hybrid Networks
As businesses move to cloud-based infrastructure, network professionals are expected to understand how traditional networking integrates with platforms like AWS, Microsoft Azure, and Google Cloud. CCNA now touches on cloud and virtualization concepts, helping professionals bridge the gap between on-premises and cloud environments.
Who Should Get CCNA Certified?
Fresh graduates looking to enter the IT industry
Working professionals wanting to upskill or shift to networking
Support engineers aiming for network admin roles
System administrators managing on-premise and cloud-based networks
Freelancers and consultants offering network setup services
Even if you don’t work directly in networking, CCNA gives you a better understanding of how IT infrastructure works, making you more effective in any tech role.
Career Opportunities After CCNA
After earning your CCNA, many career paths open up:
Network Support Engineer
Network Administrator
Technical Support Engineer
System Engineer
Security Analyst (entry-level)
Junior Network Consultant
Once you gain some experience, you can move on to more specialized roles or pursue higher certifications like CCNP (Cisco Certified Network Professional).
Tips to Prepare for CCNA Certification
Understand the exam syllabus thoroughly
Use Cisco’s official study materials and labs
Practice using Packet Tracer or GNS3
Join online forums and study groups
Take practice tests to assess your progress
A consistent study schedule, combined with hands-on lab practice, is the best way to prepare effectively.
Final Thoughts
In the fast-paced world of IT, certifications like CCNA help professionals stay relevant, knowledgeable, and competitive. It’s more than just a credential; it’s a gateway into the networking domain with practical skills that can shape your entire career.
Whether you’re starting out or aiming to climb the career ladder, investing your time in learning what is CCNA and pursuing the certification can be one of the smartest moves you make. It validates your expertise, enhances your confidence, and connects you with global career opportunities in networking.
#CCNA#CiscoCertification#NetworkingProfessionals#NetworkEngineer#LearnNetworking#TechCareer#ITCertification#CybersecurityBasics#NetworkingSkills#CareerInTech#CCNA2025#NetworkSecurit
0 notes
Text
Amazon Route 53 Resolver DNS Firewall prevents DNS threats

Amazon Route 53 DNS Firewall Advanced
Amazon Route 53 Resolver DNS Firewall protects against advanced DNS assaults.
Millions of applications simply connect users to their regular digital services using DNS queries. These queries connect with the internet's address book by transforming domain names like amazon.com into IP addresses computers need to route traffic. Amazon VPC DNS presents unique security risks and opportunities. DNS resolution can be used to manage network traffic before it starts. Second, the Amazon Route 53 Resolver, which runs separately from your internet gateway, routes DNS queries in your VPC to bypass other network security protections.
Start with standard domain lists to permit or prevent DNS resolution of specific domains, Amazon Route 53 Resolver DNS Firewall secures DNS traffic to handle this issue. AWS Managed Domain Lists automatically ban hazardous sites detected by Amazon Threat Intelligence and its trusted security partners. This method is successful against known dangers, but savvy thieves are increasingly using non-blocklist tactics.
Instead of static lists, Amazon Route 53 Resolver DNS Firewall Advanced provides intelligent protection. These advanced programs monitor DNS queries for suspicious tendencies like a security researcher. Even when the service finds unidentifiable domains, query duration, entropy, and frequency can indicate malicious activity. DNS tunnelling and domain generation algorithms (DGAs), which bad actors use to build covert communication channels or link malware to their command centres, are detected and stopped by this method.
Knowing DGA and DNS tunnelling risks
As mentioned, the Route 53 Resolver provides a service-managed internet access path separate from your VPC internet gateway. While DNS tunnelling allows DNS resolution, it can also be used to exploit its architecture. Let's explore these methods' operation and challenges.
DNS tunnelling utilises the DNS system's essential functionality by asking domain name questions and getting answers from the authoritative nameserver. Tunnelling encrypts DNS requests and answers instead of resolving domain names. A tunnelling exploit can use secretdata123.attacker.com, which contains encoded data, instead of just asking for example.com's IP address? Thus, DNS can be used for two-way command and control. DNS tunnelling must be identified and disabled to avoid data exfiltration and C2 connections.
DNS security is threatened by DGAs. Instead of utilising a set, predictable domain name that can be quickly halted, DGAs use mathematical techniques to produce many alternative domain names for C2 traffic. For instance, a DGA may generate mn9qrs.com tomorrow and xkt7py.com today. Effective blocklists are difficult to maintain since domains seem random and change constantly. DGA-generated domains are too rapid for typical threat intelligence feeds that find and block problematic sites.
DNS Firewall Advanced works how?
Route 53 Resolver DNS Firewall Advanced analyses domain names using several parameters to identify trustworthy and suspicious domains. Legitimate domain names, for instance, include real words and patterns to make them easier to remember and enter. However, DGA and tunnelling domains often feature weird patterns or random character sequences.
Route 53 Fix DNS Firewall Advanced analyses domain usage trends to provide insight. It learns what authentic domain names look like by monitoring the most resolved domains on the internet and AWS domain resolution trends. Using real-world training data helps establish domain name attributes. DNS Firewall Advanced analyses these patterns to DNS tunnelling and domain creation methods to identify suspicious behaviour.
Domain names are checked in several ways by the service:
Domain name structure and division
Use of letter and number patterns
How much the domain resembles natural language
Common words, not random characters
By analysing queries in real time and processing them in milliseconds, the service provides strong security without slowing your apps.
Route 53 Resolver DNS Firewall Advanced's configurable protection levels let you choose how aggressively to discover and address suspicious domains using confidence thresholds:
High confidence: Focussing on the biggest threats decreases false positives. It works well in production environments when blocking legitimate traffic is inconvenient.
Medium confidence: Protects most settings well.
Low confidence: The maximum detection level but may need adjustment to prevent false positives. High-security settings or preliminary traffic pattern monitoring benefit from this setup.
Mix these confidence levels with block or alert actions to create a security approach that meets your needs.
Observability
Route 53 Resolver query logging lets you see DNS requests from resources linked to your VPCs for security and compliance. Query logging can record the domain name, record type, response code, and originating VPC and instance for every DNS request. With the Route 53 Resolver DNS Firewall, query logging lets you monitor blocked queries and alter security rules to match your DNS traffic patterns.
Security Hub connection
Security Hub gives you an overview of your AWS security against industry standards and best practices. Security Hub collects security data from AWS accounts, services, and supported third-party products to identify the biggest security threats. These warnings will appear without further settings because it enables discoveries from both the Amazon: Route 53 Resolver DNS Firewall – AWS List and Advanced list. You only need to enable Amazon: Route 53 Resolver DNS Firewall – Custom List findings when using custom domain lists in rule groups.
In conclusion
Amazon Route 53 Resolver DNS Firewall Advanced protects businesses from complicated DNS-based attacks. The Route 53 Resolver bypasses security groups, NACLs, and the AWS Network Firewall while processing DNS queries, leaving many installations insecure. DNS tunnelling and DGA-based vulnerabilities exploit this blind spot, while Route 53 Resolver DNS Firewall Advanced employs anomaly detection and real-time pattern analysis to fight against them.
The AWS console was used to build up the service using the CloudFormation template and proposed rules that balance high-confidence threats and warnings. You saw how Security Hub integration centralises security findings and how query recording provides DNS traffic information. These features can protect your infrastructure from complicated DNS-based threats that standard domain blocklists cannot identify, improving cloud security and operational efficiency.
#AmazonRoute53ResolverDNSFirewall#AmazonRoute53Resolver#DNSFirewall#Route53Resolver#domaingenerationalgorithms#DNStunnelling#technology#technews#technologynews#news#govindhtech
0 notes
Text
What is Foundation Service in Cloud Computing?
Ever wonder what powers all those apps, websites, and smart services we use every day? The answer lies in the foundation services of cloud computing—the essential building blocks that make the cloud work like magic behind the scenes. ✨
Whether you're a curious learner or a professional looking to get certified, understanding these foundational services is key. That’s why the Certified Cloud Computing Foundation (CCF Certification) offered by GSDC is gaining global attention 🌍.
Let’s break it down in plain English 👇
🧱 What Are Foundation Services in Cloud Computing?
Foundation services in cloud computing are the core infrastructure and platform services that allow applications and software to run seamlessly in the cloud. Think of them as the plumbing and electricity of your cloud “house.”
These services usually include:
Compute (Virtual machines and containers)
Storage (Cloud databases, object storage)
Networking (Virtual networks, firewalls, load balancers)
Security and Identity (User access, encryption, monitoring)
Automation tools (APIs, orchestration services)
These aren’t fancy extras—they’re the foundation. And mastering them starts with the right cloud foundation course.
🎓 Why Start with a Cloud Foundation Certification?
If you're new to cloud computing, diving straight into specialized areas can be overwhelming. That’s where a cloud computing foundation certification comes in.
The CCF course offered by GSDC simplifies the complex world of cloud into understandable concepts. You’ll learn how cloud foundation services work together to support everything from mobile apps to large enterprise platforms.
Here’s what the cloud computing certification covers:
✅ Basics of IaaS, PaaS, SaaS ✅ Deployment models (Public, Private, Hybrid) ✅ Cloud infrastructure and virtualization ✅ Security and cost optimization ✅ Real-world applications of cloud services
🌐 Who Should Consider the CCF Certification?
Whether you're an IT beginner, business analyst, or digital transformation leader—this certification in cloud computing is for you.
It’s perfect if you:
Want to start a career in cloud
Need to manage cloud-based projects
Want to speak confidently with IT teams
Plan to move into more advanced AWS, Azure, or GCP paths
The CCF certification has no prerequisites and is globally recognized. ✅
📈 How Foundation Services Support Career Growth
With a CAGR of over 16% in the global cloud computing market, the demand for cloud talent is booming. 🌍💼
By earning a cloud foundation certification, you’re proving your understanding of the most crucial components of the cloud. That makes you a valuable asset for:
👨💻 Cloud Support Roles 📊 Business Analysis 📦 SaaS and App Development 📁 IT Infrastructure Management 🔒 Cloud Security Operations
The cloud computing foundation gives you the tools to grow in any of these areas—and beyond.
If you've ever asked yourself, "What is foundation service in cloud computing?", now you know: it’s everything your digital world runs on. 🌐
And if you're ready to understand it deeper—and build a cloud-focused career—there’s no better way to start than with the CCF course. The cloud computing foundation certification from GSDC gives you the edge you need in today’s fast-paced, cloud-first job market.
Get certified, get cloud-smart, and get ahead! ☁️🔥
#CloudComputingCertification #CCFCertification #CloudFoundationCourse #CertificationInCloudComputing #CloudSkillsReady #DigitalTransformation #LearnCloudToday #FutureInTech #CloudComputingFoundation

0 notes
Text
Cloud Consulting Services and Implementation Solutions

In the digital age, cloud computing has become a crucial element for industry-wide innovation, efficiency, and scalability. As businesses continue to transition from traditional IT infrastructure to the cloud, professional guidance and reliable execution are more crucial than ever. Cloud consulting services and implementation solutions can assist organizations in effectively implementing, optimizing, and managing cloud infrastructures. Whether you're looking into cloud adoption for the first time or want to make the most of your present infrastructure, professional consultation and implementation services assist ensure a smooth, secure, and cost-effective transfer.
What Are Cloud Consulting Services?
Businesses can create a thorough plan for cloud adoption with the aid of cloud consulting services. This entails assessing the existing IT infrastructure, determining which workloads are appropriate for the cloud, picking the best cloud platform (such as AWS, Microsoft Azure, or Google Cloud), and developing a deployment and management roadmap.
Core Areas of Cloud Consulting:
Assessing the readiness of an organization's systems and apps for migration is known as cloud readiness assessment.
Strategic Planning: Developing a tailored cloud strategy in line with corporate objectives.
Cost analysis and optimization: projecting costs and figuring out how to cut back on cloud spending.
Platform Selection: Assisting companies in selecting the best private, public, or hybrid cloud solution.
Planning for security and compliance: Making sure cloud solutions adhere to data protection guidelines and industry regulations.
What Are Cloud Implementation Solutions?
Cloud implementation services concentrate on carrying out the plan after a strategy has been established. This covers data migration, infrastructure configuration, application integration, and change management throughout the company.
Key Aspects of Implementation:
Cloud migration is the process of transferring workloads, data, and apps from on-premises systems to the cloud.
Infrastructure setup includes creating and implementing storage, databases, networking, and virtual machine configurations.
Rewriting or optimizing applications to utilize cloud-native features is known as application modernization.
Integration of Automation and DevOps: Using tools to automate deployments and optimize development processes.
Continuous Support and Maintenance: After implementation, offering security updates, performance optimization, and monitoring.
Benefits of Cloud Consulting and Implementation

There are numerous important advantages to working with a seasoned cloud service provider:
1. Quicker Implementation
Professional consultants expedite cloud environment design and deployment, minimizing downtime and guaranteeing on-time delivery.
2. Lower Expenses
Waste can be eliminated, resource usage can be optimized, and infrastructure costs can be decreased with a customized cloud strategy.
3. Enhanced Capability to Scale
Cloud solutions are ideal for expanding companies or workloads that change over time because they enable businesses to scale resources up or down in response to demand.
4. Strengthened Security
Strong security measures, such as firewalls, access controls, encryption, and compliance frameworks, are implemented by cloud professionals.
5. Expertise Access
Engaging with seasoned consultants gives internal teams access to best practices and cutting-edge knowledge that they might not have.
Cloud Models and Deployment Options
Cloud consultancy can help businesses choose the optimal deployment and service model:
Public Cloud: Ideal for companies seeking cost-effectiveness and scalability without having to worry about infrastructure ownership.
Private Cloud: Perfect for companies that want specific configurations for security or compliance.
Hybrid cloud, which blends the benefits of public and private clouds, allows data and apps to move freely between environments.
Multicloud: Increases redundancy and avoids vendor lock-in by utilizing services from many cloud providers.
Use Cases Across Industries
Cloud computing is transforming industries such as
Healthcare: safe patient data management, telemedicine, and AI diagnoses.
Finance: Real-time transaction processing, fraud detection, and mobile banking.
Retail: Scalable eCommerce platforms, inventory management, and customer analytics.
Manufacturing: predictive maintenance, IoT integration, and supply chain visibility.
Conclusion
Cloud migration is not merely a fad it is a strategic necessity in the cutthroat business world of today. Businesses can successfully and smoothly make this transition with the aid of cloud deployment solutions and consulting services. Businesses may maximize cloud technology, cut expenses, and lower risks by enlisting professional help.
A reliable cloud consulting partner can assist you in reaching your objectives in a secure, effective, and calculated manner, regardless of whether you're preparing your first cloud migration or improving an existing architecture. Source: https://silverspaceinc.com/cloud-consulting-services/
0 notes
Text
Affordable Cybersecurity Solutions Provider in Noida for End-to-End IT Security and Threat Detection Services: Wish Geek Techserve
In today's hyper-connected world, where businesses rely heavily on digital platforms and data, cybersecurity is no longer optional—it's essential. With rising threats like ransomware, phishing, and data breaches, securing IT infrastructure is critical for business continuity. That’s where Wish Geeks Techserve, the best cybersecurity solutions provider in Noida, steps in to protect and empower businesses with advanced security frameworks.
As a top-rated name among Cybersecurity Services India, we provide proactive, real-time, and scalable security services designed to protect your digital ecosystem from evolving cyber threats.
Why Cybersecurity Is Mission-Critical for Modern Businesses
No matter the size of your business, a single vulnerability can lead to data theft, financial loss, or reputational damage. With the increasing complexity of attacks, relying on outdated security practices can be a costly mistake.
Key reasons to invest in enterprise-grade cybersecurity:
Rising volume of cyberattacks targeting businesses across industries
Increased remote work and cloud dependence leading to new vulnerabilities
Regulatory requirements like GDPR and ISO for data compliance
Cost of downtime due to ransomware or DDoS attacks
Demand for customer trust and brand reputation
Wish Geeks Techserve provides IT Security Services in India to secure networks, endpoints, and sensitive business data.
About Wish Geeks Techserve
Wish Geeks Techserve is a premier Cybersecurity Solutions Provider in India, offering a wide range of digital protection services to enterprises, startups, and government agencies. From penetration testing to network monitoring, we deliver custom cybersecurity strategies backed by the latest tools and expertise.
Our Cybersecurity Service Offerings
We believe security should be holistic, continuous, and business-aligned. Our solutions are designed to cover every aspect of your IT infrastructure.
Network Security Services
We safeguard your internal and external networks through firewalls, intrusion detection systems (IDS), and real-time monitoring.
Endpoint Protection
Protect laptops, desktops, and mobile devices from malware, ransomware, and unauthorized access with advanced endpoint security tools.
Vulnerability Assessment & Penetration Testing (VAPT)
Regular scanning and ethical hacking simulations to identify and fix security loopholes before attackers exploit them.
Data Protection and Encryption
We use advanced encryption protocols to secure sensitive data during storage, transit, and processing.
Cloud Security Solutions
Secure your cloud infrastructure on platforms like AWS, Azure, and Google Cloud with compliance-ready controls.
Security Audits and Compliance
We help you stay compliant with industry standards (ISO 27001, GDPR, PCI-DSS) through regular audits and policy management.
Incident Response & Recovery
In case of a breach, our experts provide immediate containment, root cause analysis, and disaster recovery support.
Why We’re the Best Cybersecurity Company in India
We’re more than a service provider—we’re your security partner in a rapidly changing threat landscape.
Key reasons to choose Wish Geeks Techserve:
Experienced Cybersecurity Experts with global certifications (CEH, CISSP, CISA)
Customized Security Plans tailored to business size, industry, and infrastructure
24/7 Threat Monitoring and real-time response capabilities
Affordable Packages without compromising on protection or performance
Latest Tools and Technologies including SIEM, SOC, EDR, and UTM solutions
Transparent Reporting and regular performance dashboards
Industries We Secure
As a trusted Cybersecurity Solutions Provider in Noida, we work across various industries:
E-commerce and Retail
BFSI (Banking, Financial Services, Insurance)
Healthcare and Pharmaceuticals
IT and SaaS Companies
Manufacturing and Supply Chain
Government and Public Sector
Whether it’s an SME in Noida or an MNC with global offices, our network security services in India are scalable and tailored.
What’s Included in Our Cybersecurity Packages?
Wish Geeks Techserve offers modular and customizable cybersecurity plans that can include:
Threat detection and log analysis
Email security and spam filtering
Malware and ransomware defense
VPN configuration and access control
Security training for employees
Policy development and documentation
Regular patch management and updates
Connect with Wish Geeks Techserve Today
Protect your business from today’s most sophisticated cyber threats with India’s most reliable security partner. Whether you need basic protection or an enterprise-level cybersecurity framework, Wish Geeks Techserve delivers with precision, expertise, and integrity.
Final Thoughts
In an age where data breaches and ransomware are on the rise, cybersecurity is your first and last line of defense. At Wish Geeks Techserve, we provide end-to-end IT security services in India—from prevention and detection to response and recovery.
Don’t wait for a cyberattack to take action. Choose the best cybersecurity company in India and protect your digital future with confidence.
#Cybersecurity Services India#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
0 notes
Text
Elastic Load Balancer: تعادلساز بار در دنیای هاستینگ و سرورها
در دنیای امروز که هاستینگ ابری (Cloud Hosting)، مقیاسپذیری سرورها، بالانس ترافیک وبسایتها، سرویسهای ابری و امنیت زیرساخت شبکهای از مهمترین دغدغههای کسبوکارهای آنلاین هستند، استفاده از Elastic Load Balancer (یا به اختصار ELB) به یک ضرورت تبدیل شده است. اگر یک وبسایت یا اپلیکیشن دارید که روزانه با هزاران یا میلیونها درخواست سر و کار دارد، باید یاد بگیرید چطور از ELB برای مدیریت بهتر منابع خود بهره ببرید.

ELB چیست و چرا به آن نیاز داریم؟
Elastic Load Balancer یک سرویس ارائهشده توسط آمازون (AWS) و برخی دیگر از شرکتهای بزرگ ابری است که وظیفهاش توزیع هوشمندانهی ترافیک میان چند سرور است. بهعبارت سادهتر، وقتی چند کاربر همزمان وارد سایت یا اپلیکیشن شما میشوند، ELB بهصورت خودکار تصمیم میگیرد که این ترافیک بین چه سرورهایی تقسیم شود تا فشار روی یک سرور خاص زیاد نشود.
انواع Elastic Load Balancer
آمازون سه نوع اصلی از ELB ارائه میدهد که هر کدام کاربرد خاص خود را دارند: 1. Classic Load Balancer (CLB) مناسب برای پروژههای سنتی و اپلیکیشنهایی که از پروتکلهای پایهای مانند HTTP و TCP استفاده میکنند. 2. Application Load Balancer (ALB) مناسب برای برنامههای مدرن و مبتنی بر HTTP/HTTPS با قابلیتهایی مثل مسیریابی بر اساس محتوای URL، لایه هفتم (Application Layer). 3. Network Load Balancer (NLB) برای سرویسهایی که نیاز به پرفورمنس بالا و تاخیر کم دارند. در لایهی چهارم شبکه (TCP) کار میکند.
مزایای استفاده از ELB
- مقیاسپذیری بالا بدون نیاز به مداخلهی انسانی - افزایش در دسترس بودن سرویسها - امنیت بیشتر با استفاده از گواهیهای SSL/TLS - مسیریابی هوشمندانه ترافیک به سالمترین سرور - ادغام کامل با سرویسهای مانیتورینگ و لاگینگ مثل CloudWatch

مقیاسپذیری سرورها
موارد استفادهی ELB در هاستینگ
در صنعت هاستینگ، بهویژه وقتی بحث دربارهی هاستهای ابری یا اختصاصی پیش میآید، ELB نقش کلیدی ایفا میکند. شرکتهایی که خدمات هاست ابری مقیاسپذیر ارائه میدهند، معمولاً از Load Balancer استفاده میکنند تا بار ترافیکی بین ماشینهای مجازی یا کانتینرهای مختلف تقسیم شود. این باعث میشود کاربران نهایی تجربهی سریعتر و پایدارتری داشته باشند.
ارتباط ELB با امنیت و مانیتورینگ
Elastic Load Balancer میتواند در کنار WAF (Web Application Firewall) استفاده شود و جلوی حملات رایج مثل DDoS و SQL Injection را بگیرد. همچنین بهکمک CloudWatch یا دیگر ابزارهای مانیتورینگ، میتوان وضعیت سلامت هر سرور را لحظهای بررسی کرد.

امنیت زیرساخت
نقش وان سرور در ارائهی سرویسهای مرتبط با ELB
وان سرور بهعنوان یکی از ارائهدهندگان پیشرو در خدمات زیرساخت و هاستینگ، امکان راهاندازی سرور ابری با قابلیت Load Balancer را در اختیار کاربران خود قرار میدهد. اگر قصد دارید وبسایت یا اپلیکیشن خود را بر روی چند سرور بهصورت موازی اجرا کنید و از مزایای توزیع ترافیک بهره ببرید میتوانید از خدمات وان سرور استفاده کنید.
نتیجهگیری
Elastic Load Balancer فقط یک ابزار نیست؛ بلکه ستون فقرات زیرساختهای مقیاسپذیر و پایدار امروزیست. اگر دنبال سرعت بالا، دسترسی دائمی، امنیت بیشتر و کارایی بالاتر هستید، بدون شک ELB یکی از مؤثرترین راهکارهای شما خواهد بود. Read the full article
#ALB#CLB#CloudHosting#CloudWatch#Infrastructuresecurity#NLB#Serversscalability#SSL#TLS#امنیتزیرساخت#مقیاسپذیریسرورها
0 notes
Text
Cloud Data Security Market Size, Share, Industry Outlook & Forecast to 2032

The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
The global cloud data security market is undergoing a transformative shift as organizations accelerate digital transformation and embrace hybrid cloud architectures. As cyber threats become increasingly sophisticated, enterprises are investing in cloud-native security solutions to safeguard sensitive data and ensure regulatory compliance. With the expansion of remote work, the demand for scalable and agile data protection strategies has intensified, propelling growth across industries such as banking, healthcare, and retail.
Cloud Data Security Market Poised for Strategic Advancements Rapid innovations in artificial intelligence, machine learning, and encryption technologies are fueling a new era in cloud data security. Enterprises are transitioning from traditional perimeter-based defenses to dynamic, identity-centric models that offer greater resilience and adaptability. This evolution is supported by the proliferation of multi-cloud environments, which require robust security frameworks capable of managing complex data flows and access points without compromising performance or user experience.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Market Analysis
The cloud data security market is characterized by a highly competitive landscape featuring both established cybersecurity providers and emerging startups. Strategic alliances, mergers, and acquisitions are shaping the trajectory of the market, as companies seek to integrate advanced security features such as automated threat detection, behavioral analytics, and zero-trust architecture. The increasing stringency of global data protection laws is compelling organizations to invest in compliance-driven security solutions tailored to regional regulatory frameworks.
As businesses adopt Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS) models, cloud security is no longer an optional component but a critical enabler of trust and operational continuity. The integration of DevSecOps practices further emphasizes security as a core part of the software development lifecycle, fostering a proactive rather than reactive security posture.
Market Trends
Surge in demand for cloud-native security solutions to secure hybrid and multi-cloud infrastructures
Rising adoption of Zero Trust security frameworks for identity and access management
Growth in AI- and ML-powered threat detection and automated response mechanisms
Emphasis on data sovereignty and localized cloud security compliance measures
Expansion of DevSecOps practices integrating security at every stage of development
Increased focus on Secure Access Service Edge (SASE) to unify networking and security
Rapid evolution of encryption standards for data-at-rest, in-transit, and in-use
Greater investment in secure collaboration tools for remote workforce protection
Market Scope
The scope of the cloud data security market extends across a wide array of sectors including finance, healthcare, IT, telecommunications, manufacturing, and government. Enterprises are seeking end-to-end encryption, secure access control, and continuous monitoring solutions that align with their digital maturity. As cloud adoption reaches new heights, vendors are scaling offerings to support diverse workloads, APIs, and third-party integrations. The market also encompasses cloud security posture management (CSPM), data loss prevention (DLP), and cloud access security broker (CASB) technologies, collectively fortifying organizational resilience in an increasingly hostile cyber landscape.
Market Forecast
Over the forecast period, the cloud data security market is expected to maintain robust momentum, driven by technological innovations and the global push toward data-centric digital ecosystems. Cloud security will increasingly become embedded within broader digital transformation strategies, with providers focusing on intuitive, automated, and scalable platforms. Organizations will continue prioritizing investments in user behavior analytics, micro-segmentation, and unified threat management to preempt breaches and maintain trust. With the convergence of networking and security under cloud-native frameworks, the market is poised to evolve beyond traditional paradigms into a new standard of digital trust infrastructure.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The future of cloud data security is not just about protecting data—it’s about enabling digital confidence in a rapidly evolving business landscape. As enterprises redefine their digital blueprints, security leaders are called to align protection with innovation, ensuring that cloud adoption drives growth without compromising integrity. This dynamic market offers not only challenges but also immense opportunities for vendors and enterprises ready to invest in resilient, intelligent, and future-forward security architectures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes