#Active Directory Domain Services
Link
As the world becomes increasingly digital, cyber threats continue to pose significant risks to businesses. Managed Service Providers (MSPs) play a critical role in protecting their clients from these threats by choosing the right cybersecurity solutions and implementing effective cybersecurity strategies. In this blog, we will explore the importance and risks of cyber threats for MSPs and their clients, the need for choosing the right cybersecurity tools and strategies for clients, and the steps to take in implementing cybersecurity strategies for SMB clients.
#Secured Remote Services#Managed IT services for small business#Managed It Services#Managed Services Dashboard#Active Directory Domain Services#Virtual Private Networking Services#ipsec vpn security#site-to-site vpn connection
0 notes
Text
Always On VPN Trusted Network Detection and Native Azure AD Join
Administrators deploying Microsoft Always On VPN are quickly learning that the native Azure Active Directory join (AADJ) model has significant advantages over the more traditional Hybrid Azure AD join (HAADJ) scenario. Native AADJ is much simpler to deploy and manage than HAADJ while still allowing full single sign-on (SSO) to on-premises resources for remote users. Intune even allows for the…
View On WordPress
#AAD#AADJ#Active Directory#AD#ADML#ADMX#Always On VPN#Azure#Azure Active Directory#Azure AD#Configuration Service Provider#CSP#Custom XML#Domain profile#endpoint manager#firewall#group policy#HAADJ#Hybrid Azure AD Join#InTune#management#Microsoft#Native Azure AD Join#network location server#NetworkListManager#NLS#OMA#OMA-URI#Public profile#Remote Access
0 notes
Text
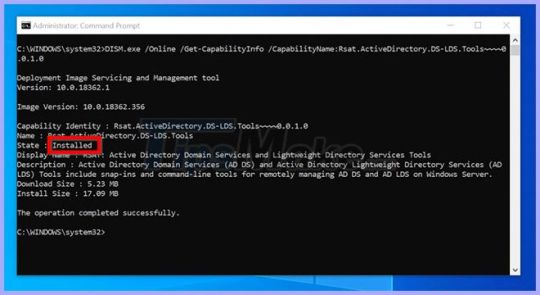
Enable active directory domain services windows 10

When the rubber hits the road, the choice boils down to which of the two you can set up quickly, given your current environment and your team's skill set.īut what happens when you choose AD, and you have a few CentOS servers, and you do not want to maintain a separate set of credentials for your Linux users? That overhead is entirely avoidable. Directory services such as FreeIPA are Linux-based and provide an excellent service for a Linux stable. This is one of the reasons for its ubiquity. In other words, it's going to be the automatic winner when your organization has many Windows systems. However, AD is a mature Windows-based service that comes incorporated with Windows Server systems. Other directory services include OpenLDAP and FreeIPA. AD is not the only directory service based on the x.500 standard, or that can be accessed using LDAP. LDAP is an open protocol for remotely accessing directory services over a connection-oriented medium such as TCP/IP. Basically, AD is a kind of distributed database, which is accessed remotely via the Lightweight Directory Access Protocol (LDAP). It saves time it saves emotions.Īt its heart, a directory service is just an organized way of itemizing all the resources in an organization while facilitating easy access to those resources. The bigger the organization, the greater the need for centralized management. That person's access to all resources is nullified on the spot. This directory can store staff phone numbers, email addresses, and can be extended to store other information. Using groups and organizational units, access to various resources can be tailored and maintained. The printers' authentication mechanism can be coupled with AD to achieve that. Members of staff can access the printers using the same set of credentials. Any account changes that need to be made are made once at the central database. Automatically, every user can access every workstation with that same set of credentials. Each computer system is also created as an object. With Active Directory, each user is uniquely created as an object in a central database, with a single set of credentials. This is where a directory service such as Active Directory thrives. I have not even spoken about managing access to the printers. Time that could be used for innovative tasks is now spent reinventing the wheel. I do not need to tell you the monotonous work that has to be repeated any time there's a change to the staffing or any workstations. Now, imagine two members of the staff resign. When a user changes his password for any reason, that user has to change the password on all computers he previously had access to, to keep things in sync. Imagine the workload on the end-user support team. The traditional way of working is to create local user accounts on each computer a user needs to access. Some have access to printing others don't.
Some employees run shifts while others work regular hours.
Imagine a collection of 40 computer systems and 70 users in a firm. Usually, the interaction is using one set of login credentials to log in to any workstation in the organization. For some of you reading this write-up, especially those who work in large institutions, you have interacted with AD before. It gives you the ability to manage users, passwords, resources such as computers, and dictate who has access to what. It is used by institutions and individuals the world over to centrally control access to resources belonging to the organization. Microsoft's Active Directory, more popularly known as AD, has held the lion's share of the market for enterprise access management for many years now.
Linux System Administration Skills Assessment.
Download Now: Basic Linux Commands Cheat Sheet.
Advanced Linux Commands Cheat Sheet for Developers.

0 notes
Text
Exploring the Depths: Active Directory Penetration Testing and the Enigma of Kerberos
Introduction
In the world of cybersecurity, staying one step ahead of potential threats is paramount. To safeguard an organization's sensitive information and network resources, it's crucial to regularly assess vulnerabilities and weaknesses. One potent approach is Active Directory (AD) penetration testing, which is an essential part of assessing and fortifying network security. This article delves into the intricacies of Active Directory penetration testing and the often elusive realm of Kerberos authentication.
Active Directory Penetration Testing: Unearthing Vulnerabilities
Active Directory, the cornerstone of identity management in Windows environments, serves as a centralized repository for user and system information, including authentication data. For cybercriminals, compromising AD can open the doors to a treasure trove of sensitive information. To counter this threat, organizations employ penetration testing to simulate real-world attacks and identify vulnerabilities.
Goals of Active Directory Penetration Testing
Identify Weak Passwords: One of the most common vulnerabilities is weak or easily guessable passwords. Penetration testers aim to uncover users with weak passwords and prompt them to strengthen their credentials.
Discover Misconfigured Permissions: Unauthorized access to resources can result from misconfigured permissions. Penetration testing assesses whether users have permissions that they shouldn't, potentially exposing sensitive data.
Locate Unpatched Systems: Outdated systems are susceptible to known vulnerabilities. Identifying and patching these systems is a critical goal of penetration testing.
Assess Kerberos Authentication: Active Directory relies heavily on Kerberos for secure authentication. Understanding Kerberos is essential for a thorough AD penetration test.
Kerberos: The Protector of Authentication
Kerberos, a network authentication protocol, plays a pivotal role in securing Active Directory environments. Named after the mythological three-headed dog guarding the gates of Hades, Kerberos acts as a guardian for network communication. Understanding how it works is vital for both defenders and attackers.
The Key Concepts of Kerberos
Authentication Tickets: In Kerberos, authentication occurs through tickets. A Ticket Granting Ticket (TGT) is obtained during initial authentication, and this TGT is used to request access to various resources without re-entering credentials.
Principle of Need to Know: Kerberos enforces the principle of "need to know." A user can access only the resources for which they have tickets, reducing the risk of unauthorized access.
Realms and Trust: In a multi-domain environment, Kerberos realms establish trust relationships between domains. Trust enables users from one domain to access resources in another.
Encryption: Kerberos relies on encryption to protect sensitive information, such as passwords and tickets. Encryption keys are generated dynamically during authentication.
Penetration Testing Kerberos: A Delicate Balancing Act
Penetration testing for Kerberos authentication involves a delicate balancing act between assessing security measures and not disrupting normal operations. Here are some critical aspects of Kerberos-focused penetration testing:
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak or vulnerable user accounts. Penetration testers attempt to retrieve Authentication Service (AS) tickets without the need for valid login credentials. This technique targets accounts with pre-authentication disabled, making them vulnerable to brute-force attacks.
2. Pass-the-Ticket Attacks
Pass-the-Ticket attacks involve stealing Ticket Granting Tickets (TGTs) from compromised systems. Attackers can then use these stolen TGTs to gain unauthorized access to other network resources. Penetration testing assesses the organization's ability to detect and defend against such attacks.
3. Golden Ticket Attacks
Golden Ticket attacks involve forging TGTs, effectively granting attackers unlimited access to the domain. Penetration testers may attempt to create Golden Tickets to evaluate the AD's resilience against this advanced attack.
4. Silver Ticket Attacks
Silver Tickets are used for unauthorized access to specific services or resources. A penetration test may focus on creating Silver Tickets to assess the AD's ability to detect and prevent such attacks.
10 notes
·
View notes
Text
Why SEO Is More Than Just Keywords?

Search Engine Optimization (SEO) is a multifaceted strategy that extends far beyond merely incorporating keywords into content. While keywords remain a crucial element, a comprehensive SEO approach involves various factors to enhance a website's visibility and relevance to search engines. Here's why SEO is more than just keywords:
User Experience (UX): Google and other search engines prioritize user experience in their algorithms. A well-structured, easy-to-navigate website with relevant content contributes to a positive user experience. Factors like page loading speed, mobile responsiveness, and intuitive design all play a role in SEO. Prioritizing UX not only satisfies search engine algorithms but also improves the likelihood of user engagement.
Content Quality: Quality content is a cornerstone of effective SEO. Rather than focusing solely on keyword density, emphasis should be placed on providing valuable, informative, and engaging content. Content that addresses user queries solves problems, or offers insights is more likely to rank higher in search results.
Content Relevance: SEO success depends on creating content that aligns with user intent. Search engines aim to deliver results that best match what users are looking for. Understanding the context and intent behind search queries helps in creating content that resonates with the target audience, leading to improved rankings.
Backlinks and Authority:
Building a strong network of quality backlinks remains a crucial aspect of SEO. Backlinks from reputable websites signal to search engines that a site is trustworthy and authoritative. SEO strategies should include efforts to earn high-quality backlinks through content partnerships, outreach, and other legitimate means.
Technical SEO: Technical SEO focuses on the backend aspects of a website, ensuring that search engines can crawl and index content effectively. This includes optimizing website structure, improving page load times, fixing broken links, and creating an XML sitemap. Neglecting technical SEO can hinder a website's visibility in search results.
Local SEO: For businesses with a local presence, optimizing for local search is essential. This involves creating and optimizing Google My Business listings, obtaining online reviews, and ensuring accurate business information across directories. Local SEO strategies help businesses appear in local search results and on platforms like Google Maps.
User Intent and Semantic Search: Search engines increasingly focus on understanding user intent and context through semantic search. This means that SEO efforts should go beyond matching exact keyword phrases and consider the broader meaning behind queries. Creating content that answers questions comprehensively aligns with semantic search principles.
Social Signals: While the direct impact of social signals on SEO rankings is debated, a strong social media presence contributes to a brand's visibility and online reputation. Social media platforms can drive traffic to a website, increase brand awareness, and indirectly influence search engine rankings.
Regular Updates and Freshness: Search engines favor regularly updated content. Websites that consistently publish new, relevant content signal to search engines that they are active and authoritative in their respective domains. This dynamic approach to content creation helps maintain or improve search rankings over time.
Analytics and Data Analysis: SEO success relies on data-driven decision-making. Analyzing website performance through tools like Google Analytics provides insights into user behavior, popular content, and areas for improvement. Ongoing analysis allows for adjustments to SEO strategies based on real-time data.
Are you looking to get your SEO off the ground? If yes then it is best to connect with the experts providing the best SEO services in India.
In conclusion, while keywords are a fundamental element of SEO, a holistic approach is essential for long-term success. By prioritizing user experience, creating quality content, building authority, and addressing various technical aspects, websites can enhance their visibility and relevance in search engine results. SEO is a dynamic and evolving discipline that requires a multifaceted strategy to adapt to the ever-changing landscape of online search.
2 notes
·
View notes
Text
Azure’s Evolution: What Every IT Pro Should Know About Microsoft’s Cloud
IT professionals need to keep ahead of the curve in the ever changing world of technology today. The cloud has become an integral part of modern IT infrastructure, and one of the leading players in this domain is Microsoft Azure. Azure’s evolution over the years has been nothing short of remarkable, making it essential for IT pros to understand its journey and keep pace with its innovations. In this blog, we’ll take you on a journey through Azure’s transformation, exploring its history, service portfolio, global reach, security measures, and much more. By the end of this article, you’ll have a comprehensive understanding of what every IT pro should know about Microsoft’s cloud platform.
Historical Overview
Azure’s Humble Beginnings
Microsoft Azure was officially launched in February 2010 as “Windows Azure.” It began as a platform-as-a-service (PaaS) offering primarily focused on providing Windows-based cloud services.
The Azure Branding Shift
In 2014, Microsoft rebranded Windows Azure to Microsoft Azure to reflect its broader support for various operating systems, programming languages, and frameworks. This rebranding marked a significant shift in Azure’s identity and capabilities.
Key Milestones
Over the years, Azure has achieved numerous milestones, including the introduction of Azure Virtual Machines, Azure App Service, and the Azure Marketplace. These milestones have expanded its capabilities and made it a go-to choice for businesses of all sizes.
Expanding Service Portfolio
Azure’s service portfolio has grown exponentially since its inception. Today, it offers a vast array of services catering to diverse needs:
Compute Services: Azure provides a range of options, from virtual machines (VMs) to serverless computing with Azure Functions.
Data Services: Azure offers data storage solutions like Azure SQL Database, Cosmos DB, and Azure Data Lake Storage.
AI and Machine Learning: With Azure Machine Learning and Cognitive Services, IT pros can harness the power of AI for their applications.
IoT Solutions: Azure IoT Hub and IoT Central simplify the development and management of IoT solutions.
Azure Regions and Global Reach
Azure boasts an extensive network of data centers spread across the globe. This global presence offers several advantages:
Scalability: IT pros can easily scale their applications by deploying resources in multiple regions.
Redundancy: Azure’s global datacenter presence ensures high availability and data redundancy.
Data Sovereignty: Choosing the right Azure region is crucial for data compliance and sovereignty.
Integration and Hybrid Solutions
Azure’s integration capabilities are a boon for businesses with hybrid cloud needs. Azure Arc, for instance, allows you to manage on-premises, multi-cloud, and edge environments through a unified interface. Azure’s compatibility with other cloud providers simplifies multi-cloud management.
Security and Compliance
Azure has made significant strides in security and compliance. It offers features like Azure Security Center, Azure Active Directory, and extensive compliance certifications. IT pros can leverage these tools to meet stringent security and regulatory requirements.
Azure Marketplace and Third-Party Offerings
Azure Marketplace is a treasure trove of third-party solutions that complement Azure services. IT pros can explore a wide range of offerings, from monitoring tools to cybersecurity solutions, to enhance their Azure deployments.
Azure DevOps and Automation
Automation is key to efficiently managing Azure resources. Azure DevOps services and tools facilitate continuous integration and continuous delivery (CI/CD), ensuring faster and more reliable application deployments.
Monitoring and Management
Azure offers robust monitoring and management tools to help IT pros optimize resource usage, troubleshoot issues, and gain insights into their Azure deployments. Best practices for resource management can help reduce costs and improve performance.
Future Trends and Innovations
As the technology landscape continues to evolve, Azure remains at the forefront of innovation. Keep an eye on trends like edge computing and quantum computing, as Azure is likely to play a significant role in these domains.
Training and Certification
To excel in your IT career, consider pursuing Azure certifications. ACTE Institute offers a range of certifications, such as the Microsoft Azure course to validate your expertise in Azure technologies.

In conclusion, Azure’s evolution is a testament to Microsoft’s commitment to cloud innovation. As an IT professional, understanding Azure’s history, service offerings, global reach, security measures, and future trends is paramount. Azure’s versatility and comprehensive toolset make it a top choice for organizations worldwide. By staying informed and adapting to Azure’s evolving landscape, IT pros can remain at the forefront of cloud technology, delivering value to their organizations and clients in an ever-changing digital world. Embrace Azure’s evolution, and empower yourself for a successful future in the cloud.
#microsoft azure#tech#education#cloud services#azure devops#information technology#automation#innovation
2 notes
·
View notes
Text
Do you want your website to rank in Google?

It's no secret that ranking in Google can be a major boon for businesses. After all, being one of the first results that come up when someone searches for a particular product or service can mean increased traffic and, as a result, more customers. But how do you go about ensuring that your website ranks highly in Google? There are a number of things you can do to improve your website's ranking on Google. One is to make sure that your website is mobile-friendly, as more and more people are using their smartphones and other mobile devices to search the internet. Another is to use relevant keywords throughout your website, including in the titles and descriptions of your pages. Finally, you need to make sure that your website is updated regularly with fresh content. By following these tips, you can improve your chances of ranking highly on Google and driving more traffic to your website.
Role of Off-Page SEO for Websites Why is a monthly link-building service necessary?
How many backlinks are needed for website rank?
Why do Off-Page SEO for a Website?
Role of Off-Page SEO for Websites.
Off-Page SEO is critical for any website that wants to rank in Google. Here are five ways Off Page SEO can help your website rank:
1. Quality backlinks: One of the most important ranking factors for Google is the number and quality of backlinks pointing to your website. Quality backlinks come from websites that are respected and popular, and they show Google that your website is also respected and popular.
2. Social media signals: Another important ranking factor for Google is social media signals. If people are talking about your website on social media, that’s a good sign that it’s popular and relevant.
3. Directory listings: Directory listings can help your website rank in Google by increasing its visibility. When people search for websites like yours, your website will be more likely to show up if it’s listed in directories.
4. press mentions: If your website is mentioned in the press, that’s a good sign that it’s popular and relevant. Google takes notice of press mentions and often ranks websites higher if they’re mentioned in the press.
5. user-generated content: User-generated content, such as reviews and testimonials, can help your website rank in Google. This is because Google sees user-generated content as a sign of trustworthiness and popularity.
Why is a monthly link-building service necessary?
A monthly link-building service is necessary in order to rank in Google for several reasons. First, Google ranks websites based on the number and quality of inbound links. In order to get inbound links, you need to actively pursue link-building opportunities. Second, a monthly link-building service can help you keep track of your link-building progress and ensure that you are consistently building links. Third, a monthly link-building service can help you find new opportunities for link-building that you may not have otherwise found. Fourth, a monthly link-building service can help you build relationships with other webmasters and bloggers, which can lead to more inbound links. Finally, a monthly link-building service can help you save time by doing the link-building for you.
How many backlinks are needed for website rank?
The answer to how many backlinks are needed for website rank is far from black and white. The number of backlinks needed to rank in Google depends on a number of factors, including the quality and relevancy of the backlinks, the age and authority of the linking domain, the number of links on the linking page, and the anchor text used. In general, however, it is safe to say that the more high-quality backlinks you have, the higher your website will rank in Google. This is because backlinks are one of the main ways Google determines the quality and relevancy of a website. If you are serious about ranking in Google, then you need to focus on building high-quality backlinks from authoritative domains. This can be done through guest blogging, directory submissions, or by reaching out to other website owners and asking for a link. Remember, however, that quality is more important than quantity when it comes to backlinks. It is better to have a few high-quality backlinks than a large number of low-quality links. If you are struggling to build backlinks, then there are a number of link-building services that can help you. These services will help you to build high-quality backlinks from authoritative domains. Finally, remember that even if you have a large number of high-quality backlinks, there is no guarantee that you will rank in Google. This is because there are a number of other factors that Google takes into account when determining the ranking of a website. However, if you focus on building high-quality backlinks, then you will give yourself the best chance of ranking in Google.
Why do Off-Page SEO for a Website?
Off-page SEO includes all of the activity that takes place outside of your website that can impact your ranking on search engine results pages (SERPs). While on-page SEO looks at the factors on your website that can affect your ranking, off-page SEO looks at the factors that are external to your website. There are many different factors that can contribute to your off-page SEO. One of the most important is link building. When other websites link to yours, it tells search engines that your site is a valuable resource. The more high-quality links you have, the higher your site will rank. Social media is also an important factor in off-page SEO. Search engines take into account the popularity of your content on social media when they are determining your ranking. If your content is shared a lot on social media, it is a good sign that you have valuable, relevant content, and your site will be more likely to rank higher. Another important factor in off-page SEO is the overall authority of your website. If your website is seen as an authority on a certain topic, it will be more likely to rank higher. There are a number of different ways to build authority, such as publishing high-quality content, getting links from other authority websites, and being quoted in the news. Off-page SEO is a complex and ever-changing process, but it is an important part of making sure your website is visible to potential customers. By taking into account the different factors that can impact your ranking, you can put your website in the best possible position to be seen by those who are looking for what you have to offer.
Overall, it is clear that ranking in Google is a desired goal for many website owners. However, it is also important to keep in mind that there is no guarantee that your website will rank in Google, no matter how much effort you put into it. In the end, it is up to Google's algorithms to decide where your website will rank.
Please visit here https://www.fiverr.com/m_rafique073/monthly-hq-link-building-backlinks-and-off-page-seo-service for details.
5 notes
·
View notes
Text

Do you need OFF Page #SEO Services?
OFF-Page SEO Benefits:
Off-page SEO helps build a website's recognition and domain authority. Without it, your site will continually rank below other websites that already have a more substantial lead. While links are not the only off-page signals that Google's algorithm applies to rank a site, it is perhaps the most vital of the lot.
OFF Page SEO importance :
Off-page SEO helps build a website's recognition and domain authority. Without it, your site will continually rank below other websites that already have a more substantial lead. While links are not the only off-page signals that Google's algorithm applies to rank a site, it is perhaps the most vital of the lot.
Here are My OFF Page SEO Activities:
→ High-Quality Backlinks
→ Classified Advertising
→ Profile Creation Submission
→ Quality Article Posting
→ PDF Sharing
→ Social Bookmarking Submission
→ Image Sharing Submission
→ Local Business Listing
→ Directory Submission
#off page seo#local seo#seo#content marketing#digital marketing services#company#seo company#backlinks#local seo agency#fiverr#freelance#digitalmarketing#freelancing#digital marketing agency#local seo services#link building#seo marketing
2 notes
·
View notes
Text
Real-World Applications of RHCSA and RHCE Skills
The Red Hat Certified System Administrator (RHCSA) and Red Hat Certified Engineer (RHCE) certifications are highly regarded in the IT industry. These certifications validate an individual's skills in managing and automating Red Hat Enterprise Linux environments. However, the value of these certifications extends beyond just passing exams; the skills acquired are directly applicable to various real-world scenarios in the IT domain. Let's explore some of the practical applications of RHCSA and RHCE skills.
1. Server Management and Maintenance
RHCSA:
User and Group Management: Creating, modifying, and managing user accounts and groups. This is crucial for maintaining security and organization within a server environment.
File Permissions and ACLs: Setting appropriate permissions and access control lists to protect sensitive data and ensure users have the necessary access to perform their jobs.
Service Management: Starting, stopping, enabling, and disabling services using systemctl. This is essential for maintaining the uptime and performance of services.
RHCE:
Advanced System Monitoring: Using tools like top, htop, vmstat, and iotop to monitor system performance and diagnose issues.
Network Management: Configuring and troubleshooting network interfaces, firewalls, and SELinux settings to secure and optimize network communications.
2. Automating System Administration Tasks
RHCSA:
Shell Scripting: Writing basic scripts to automate repetitive tasks, such as backups, user creation, and log rotation.
Cron Jobs: Scheduling routine tasks to run automatically at specified times, ensuring consistent system maintenance without manual intervention.
RHCE:
Ansible Automation: Utilizing Ansible for configuration management and automation. Creating playbooks to automate complex multi-tier deployments and configurations.
Automating Deployments: Streamlining the process of deploying applications and services using automated scripts and configuration management tools.
3. System Security and Compliance
RHCSA:
Security Enhancements: Implementing basic security measures such as configuring firewalls with firewalld, and managing SELinux to enforce security policies.
Auditing and Logging: Setting up and maintaining system logs to monitor and audit system activities for compliance and troubleshooting purposes.
RHCE:
Advanced Security Configurations: Applying more sophisticated security measures such as configuring advanced SELinux policies, managing TLS/SSL certificates for secure communications, and implementing secure SSH practices.
System Auditing and Reporting: Using tools like auditd to create detailed security audits and reports, ensuring systems comply with security policies and standards.
4. Troubleshooting and Problem Solving
RHCSA:
Basic Troubleshooting: Using commands like journalctl, dmesg, and systemctl to diagnose and resolve common issues related to system performance, boot processes, and service failures.
Disk Management: Managing storage with LVM (Logical Volume Management) and understanding disk usage with tools like df and du.
RHCE:
Advanced Troubleshooting: Diagnosing complex issues involving network services, storage systems, and application performance. Using advanced tools and techniques to pinpoint and resolve problems.
System Recovery: Implementing disaster recovery plans, including restoring from backups, repairing boot issues, and recovering corrupted file systems.
5. Managing Enterprise Environments
RHCSA:
Package Management: Installing, updating, and managing software packages using yum or dnf, ensuring that systems have the necessary software and updates.
Network Configuration: Setting up and managing basic network configurations, including IP addresses, DNS settings, and hostname configurations.
RHCE:
Centralized Authentication: Setting up and managing centralized authentication services such as LDAP, Kerberos, and integrating with Active Directory.
Clustering and High Availability: Configuring and managing Red Hat High Availability Clustering to ensure critical services are always available.
6. DevOps and Continuous Integration/Continuous Deployment (CI/CD)
RHCSA:
Version Control Systems: Basic knowledge of version control systems like Git, which is fundamental for managing code and configuration files.
Containerization: Introduction to containerization concepts using tools like Docker.
RHCE:
CI/CD Pipelines: Setting up and managing CI/CD pipelines using tools like Jenkins, GitLab CI, or Red Hat OpenShift, enabling automated testing, integration, and deployment of applications.
Advanced Container Management: Managing and orchestrating containers using Kubernetes and Red Hat OpenShift, ensuring scalable and reliable deployment of containerized applications.
Conclusion
The skills acquired through RHCSA and RHCE certifications are not just theoretical but have direct, practical applications in the real world. Whether it's managing and securing servers, automating administrative tasks, or setting up robust enterprise environments, these certifications equip IT professionals with the knowledge and tools necessary to excel in their careers. By applying these skills, professionals can ensure efficient, secure, and high-performing IT operations, ultimately driving organizational success.
For more details click www.qcsdclabs.com
#redhatcourses#information technology#containerorchestration#kubernetes#docker#linux#container#qcsdclabs#rhcsa#rhce#devops#ansibleautomation
0 notes
Text
Hidden Wiki
Exploring The Depths Of Web: An Insight Into The Hidden Wiki Uses
The Hidden Wiki, often referred to as the dark web's "unofficial Wikipedia," holds a unique position in the online landscape.

Unlike its namesake, it's not a curated encyclopedia but a directory listing websites accessible only through the Tor network.
Understanding the purposes for which people use the Hidden Wiki requires acknowledging both its potential benefits and inherent risks.
1. Gateway To The Dark Web:
The Hidden Wiki serves as a portal to the dark web, providing access to a myriad of hidden services and websites that are inaccessible through traditional means.
For those curious enough to venture into this murky domain, the Hidden Wiki offers a tantalizing glimpse into a world shrouded in secrecy.
2. Anonymity And Privacy:
One of the primary draws of the Hidden Wiki is its emphasis on anonymity and privacy. By utilizing tools such as the Tor browser, users can navigate the dark web without fear of surveillance or censorship, allowing for unrestricted access to information and resources.
4. Drugs:
While much of the content found on the Hidden Wiki is benign, there are also areas that delve into controversial and potentially harmful topics.
From tutorials on bomb-making to guides on drug use, users must exercise caution and discretion when exploring these darker corners of the dark web.
5. Information And Resources:
In addition to its more nefarious offerings, the Hidden Wiki also provides a wealth of information and resources on a variety of subjects.
From guides on internet privacy and security to tutorials on software and programming, users can find a wide range of valuable resources hidden within its depths.
6. Scam Awareness:
One of the inherent risks of exploring the dark web is the prevalence of scams and fraudulent activities.
To help users navigate this treacherous terrain, the Hidden Wiki often includes lists of known scams and fraudulent websites, allowing users to avoid falling victim to exploitation.
7. Educational Opportunities:
While the dark web may be notorious for its illicit activities, it also offers educational opportunities for those willing to explore its depths.
From learning about encryption and cybersecurity to gaining insights into the inner workings of the underground economy, the Hidden Wiki provides a unique window into the darker side of the internet.
8. Access To Censored Information:
The Hidden Wiki can link users to content restricted in their countries, like political dissident blogs or alternative news sources.
This fosters free speech and empowers individuals seeking information beyond government control. Journalists and researchers might also use the Hidden Wiki to access sensitive materials for investigative purposes.
9. Acquiring Niche Resources
Another use is acquiring niche resources. The platform can connect users with academic papers or software unavailable on the clear web (surface web). For instance, researchers might find unpublished data sets or specialists could locate rare software versions.

Conclusion:
The Hidden Wiki occupies a complex and controversial space. While it offers a gateway to censored information, educational opportunities, and even niche resources, it also presents a significant risk of encountering scams, illegal activities, and harmful content.
Ultimately, the decision of whether or not to delve into the dark web through The Hidden Wiki rests with the user, who must carefully weigh the potential benefits against the inherent dangers.
It's crucial to remember that the Hidden Wiki itself doesn't host this illegal content; it merely acts as a directory.
0 notes
Text
Cài đặt Active Directory Domain Services trên Windows Server 2022
Active Directory Domain Services (AD DS) là một phần không thể thiếu của hệ thống mạng doanh nghiệp, cung cấp một cơ sở dữ liệu chung cho việc quản lý và tổ chức người dùng, máy tính và các tài nguyên khác trên mạng. Trên nền tảng của Windows Server 2022, việc cài đặt AD DS là một bước quan trọng trong quá trình xây dựng và duy trì một môi trường domain đáng tin cậy và hiệu quả.
Trong bài viết này, chúng tôi sẽ hướng dẫn chi tiết về cách cài đặt AD DS trên Windows Server 2022, giúp bạn hiểu rõ hơn về công nghệ quan trọng này và áp dụng nó vào hệ thống mạng của mình một cách dễ dàng và hiệu quả.
I. Tổng quan
1. Windows Server 2022
Windows Server 2022 là phiên bản mới nhất của hệ điều hành máy chủ của Microsoft, tập trung vào tính ổn định, bảo mật và hiệu suất. Nó cung cấp các tính năng tiên tiến như hỗ trợ container, ảo hóa và tích hợp dịch vụ đám mây, đồng thời cải thiện bảo mật và quản lý. Windows Server 2022 linh hoạt trong việc triển khai trên nhiều môi trường khác nhau, từ máy chủ vật lý đến môi trường ảo hóa và đám mây, là nền tảng lý tưởng cho các ứng dụng và dịch vụ kinh doanh hiện đại.
2. Active Directory Domain Services là gì?
AD DS hay còn được biết đến là Active Directory Domain Services là một dịch vụ của hệ điều hành Windows Server, được sử dụng để quản lý và tổ chức tài nguyên mạng trong một môi trường domain. AD DS sẽ cho phép các tổ chức tổ chức và quản lý người dùng, máy tính, nhóm và các tài nguyên khác trên mạng nội bộ một cách dễ dàng và hiệu quả. Bằng cách cung cấp một cơ sở dữ liệu chung và một cách thức đơn giản để quản lý người dùng và tài nguyên, AD DS giúp tăng cường sự hiệu quả và bảo mật trong quản lý hệ thống mạng.
3. Vai trò của Active Directory Domain Services
Giả sử có một công ty với hàng trăm nhân viên, nhiều phòng ban và có cơ sở hạ tầng Windows Server với Active Directory được triển khai. Đây là cách thư mục này phát huy vai trò của nó:
Quản lý người dùng: Quản trị viên CNTT có thể tạo và quản lý tài khoản người dùng của từng nhân viên bằng Active Directory. Khi các tài khoản này được tạo, chúng có thể thêm và quản lý tên tài khoản người dùng, loại tài khoản, mật khẩu và các chi tiết tương tự khác.
Kiểm soát truy cập và bảo mật: Active Directory cung cấp nhiều tính năng bảo mật mà quản trị viên có thể sử dụng để cải thiện bảo mật tổng thể của hệ thống. Điều này bao gồm triển khai xác thực hai yếu tố, thực thi mật khẩu và ngăn truy cập trái phép vào dữ liệu nhạy cảm.
Quản lý tài nguyên: Quản trị viên có thể quản lý quyền truy cập vào tài nguyên mạng như máy in, thư mục dùng chung và thiết bị mạng. Họ có thể làm cho các thiết bị này có thể truy cập được đối với những người dùng hoặc nhóm cụ thể, cũng như sửa đổi các quyền để kiểm soát quyền truy cập vào thông tin nhạy cảm.
4. Thành phần của Active Directory Domain Services
Trong một môi trường AD DS, các thành phần cơ bản bao gồm:
Domain: Là một phân vùng bảo mật trên mạng, nơi chứa thông tin về người dùng, máy tính và các đối tượng khác.
Domain Controller: Là máy chủ chứa cơ sở dữ liệu AD DS và quản lý tất cả các tài nguyên trong domain.
User Accounts: Được sử dụng để xác định và quản lý quyền truy cập của người dùng vào các tài nguyên trong domain.
Group Policies: Là các chính sách bảo mật và cấu hình được áp dụng cho người dùng và máy tính trong domain.
II. Hướng dẫn cài đặt AD DS trên Windows Server 2022
1. Chuẩn bị trước
Để có thể triển khai được AD DS, bạn cần phải chuẩn bị những thứ sau:
Một máy tính hoặc máy chủ đáp ứng đủ các yêu cầu về cấu hình như: CPU, RAM, Bộ nhớ,... để cài đặt Windows Server 2022.
Xác định được tên miền và cấu trúc tổ chức của domain.
2. Triển khai AD DS
2.1. Thiết lập máy Windows Server
Đối với máy được chọn làm Domain Controller, sau khi thực hiện cài đặt xong, các bạn tiến hành đổi tên thiết bị từ tên mặc định sang tên ngắn gọn, dễ phân biệt. Nếu bạn chưa biết cách để đổi tên thiết bị, bạn có thể xem hướng dẫn dưới đây.
- Các bạn ấn tổ hợp phím Windows + R để mở hộp thoại Run, sau đó các bạn nhập vào ‘sysdm.cpl’ như sau để mở hộp thoại System Properties.
- Tiếp đó, khi hộp thoại System Properties hiện ra, các bạn chọn “Change” để tiến hành thay đổi tên cho máy tính.
- Khi hộp thoại Computer Name hiện ra, các bạn thực hiện đổi tên cho thiết bị như ý muốn của mình, sau đó bấm OK để lưu. Tiếp đến, các bạn chọn Apply và OK để hoàn tất quá trình. Sau khi đổi tên xong, thiết bị sẽ yêu cầu khởi động lại, các bạn chọn OK để khởi động lại là hoàn tất quá trình đổi tên.
Vì chúng ta sẽ cấu hình máy tính này làm AD DS nên chúng ta sẽ cần thiết lập IP tĩnh. Các bạn có thể thực hiện cấu hình IP tĩnh trên Windows Server bằng cách vào Start → Search → View Network Connections. Click phải chuột vào card mạng mà máy đang sử dụng và chọn Properties.
- Tiếp đến, chúng ta chọn vào mục Internet Protocol Version 4 và chọn Properties
- Cuối cùng, bạn thực hiện thiết lập IPv4 tĩnh cho thiết bị của mình, sau đó bấm OK để lưu và thoát. Việc thay đổi IP sẽ chỉ yêu cầu khởi động lại kết nối mạng mà không yêu cầu bạn phải khởi động lại thiết bị.
2.2. Cài đặt AD DS cho Windows Server
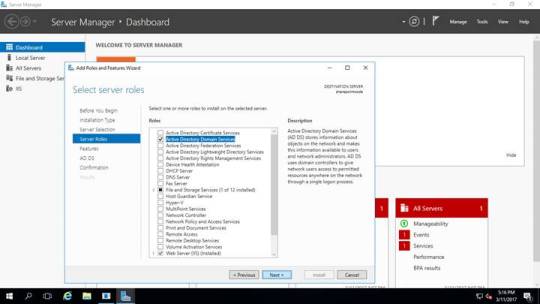
Các bạn truy cập vào Server Manager, sau đó chọn “Add roles and features” để thêm mới vai trò cho Server.
Khi bảng hiển thị cách cài đặt hiện ra, các bạn chọn như sau:
Tiếp đến là mục chọn Server để cài đặt
Sau khi chọn vai trò, chúng ta chọn các đặc trưng muốn cài đặt, cái này chúng ta nên để mặc định và chỉ bấm Next
Sau đó tiếp tục bấm Next cho đến mục Confirmation
Đến mục Confirmation, chúng ta chọn tự động khởi động lại, sau đó cài đặt.
Vậy là chúng ta đã hoàn tất cài đặt AD DS trên máy Windows Server.
III. Tổng Kết
Trong bài viết này, chúng ta đã tìm hiểu được về Active Directory Domain Services và biết được cách cài đặt AD DS trên Windows Server 2022. Bằng cách tuân thủ các bước và hướng dẫn trên, bạn có thể triển khai và quản lý một môi trường domain trên hệ điều hành Windows Server 2022 một cách hiệu quả. Nếu gặp phải vướng mắc cần được giải đáp, hãy liên hệ với chúng tôi để được hỗ trợ sớm nhất nhé. Chúc bạn thành công!
Nguồn: https://suncloud.vn/active-directory-domain-services

0 notes
Text
Unlock the Power of AI Tools: A Comprehensive Guide

In today's digital landscape, artificial intelligence (AI) tools are transforming industries and revolutionizing how businesses operate. From streamlining workflows to enhancing creativity, AI tools offer unparalleled capabilities that empower individuals and organizations to achieve more. This comprehensive guide explores the diverse applications and benefits of AI tools, equipping you with the knowledge to unlock their full potential.
Understanding AI Tools: A Game-Changing Technology
Artificial intelligence encompasses a wide range of technologies that simulate human intelligence to perform tasks traditionally requiring human intelligence. AI tools leverage machine learning, natural language processing, computer vision, and other advanced techniques to automate processes, generate insights, and drive innovation across various domains.
Key Features of AI Tools:
Automation: AI tools automate repetitive tasks, improving efficiency and reducing manual workload.
Data Analysis: AI tools analyze large datasets to uncover patterns, trends, and actionable insights.
Natural Language Processing (NLP): AI-powered NLP tools process and understand human language, enabling applications such as chatbots and language translation.
Computer Vision: AI tools with computer vision capabilities interpret and analyze visual content, enabling applications like image recognition and object detection.
Applications of AI Tools Across Industries
AI tools have diverse applications across industries, revolutionizing business operations, customer experiences, and product development:
1. Healthcare:
AI-powered diagnostic tools assist healthcare professionals in disease detection, medical imaging analysis, and personalized treatment recommendations.
2. Finance:
AI tools optimize financial processes, including fraud detection, risk assessment, algorithmic trading, and customer service automation.
3. Marketing and Advertising:
AI tools enhance marketing campaigns by analyzing consumer behavior, personalizing content, optimizing ad placements, and predicting market trends.
4. Manufacturing:
AI-driven robotics and predictive maintenance improve manufacturing efficiency, quality control, supply chain management, and inventory optimization.
5. Creative Industries:
AI tools aid in content creation, graphic design, music composition, and video editing, fostering creativity and innovation.
Harnessing the Power of AI Tools: Best Practices
To leverage AI tools effectively and maximize their impact, consider the following best practices:
1. Identify Business Needs:
Define specific business challenges or opportunities that AI tools can address, such as process automation, data analysis, or customer engagement.
2. Research AI Solutions:
Explore available AI tools and platforms that align with your business goals, considering factors like scalability, compatibility, and ease of integration.
3. Pilot Projects:
Start with small-scale pilot projects to evaluate AI tools' effectiveness and gather insights before implementing broader initiatives.
4. Train Employees:
Provide training and upskilling programs to empower employees with the knowledge and skills required to use AI tools effectively.
Submitting Your AI Tool to RightAITools
To expand the reach of your AI tool and connect with a broader audience, consider submitting it to RightAITools, a leading AI tool directory website. RightAITools categorizes AI tools across various domains, enabling users to discover, evaluate, and adopt innovative solutions. By registering your tool on RightAITools, you gain visibility among AI enthusiasts, researchers, and businesses actively seeking AI solutions.
The Future of AI Tools: Innovation and Growth
Looking ahead, AI tools will continue to evolve, driving innovation and shaping the future of technology. Advances in AI ethics, explainability, and democratization will expand access to AI tools while addressing ethical concerns and promoting responsible AI development.
In conclusion, AI tools represent a transformative technology that empowers businesses and individuals to unlock new possibilities, streamline processes, and drive innovation. By understanding their capabilities, exploring applications across industries, and adopting best practices, you can harness the power of AI tools to achieve strategic objectives, enhance productivity, and thrive in the era of digital transformation. Unlock the potential of AI tools and embark on a journey of innovation and growth!
0 notes
Text
Enhancing Your Law Firm's Visibility through Effective Directory and Citation Management

Enhancing Your Law Firm's Visibility through Effective Directory and Citation Management
For law firms, the accuracy of online directories and citations plays a critical role in establishing trust and boosting local SEO. A strategic approach to managing these resources can significantly influence your firm’s online visibility and client acquisition.
Understanding the Impact of Directory Listings
Online directories are more than just digital phone books; they are platforms where potential clients make critical decisions. Proper management of these listings ensures that when a potential client searches for legal services, your firm appears credible, professional, and ready to serve.
- Choosing the right directories for law firms, focusing on those that prospective clients trust.
- Ensuring consistency across all platforms to reinforce your firm's professional image.
Case Study: The Digital Transformation of Baxter & Associates
Baxter & Associates, a seasoned real estate law firm, faced challenges with inconsistent listings across various online directories. This inconsistency led to confusion among potential clients and a noticeable drop in inquiries. The firm decided to overhaul their online presence, beginning with a comprehensive audit of all existing listings.
They updated outdated information, standardized their firm’s details, and actively managed reviews. By also engaging in local SEO practices, they enhanced their visibility in local search results. Six months later, Baxter & Associates not only saw a 40% increase in website traffic but also a significant improvement in client engagement and retention rates.
Optimizing Google My Business for Maximum Impact
Your Google My Business (GMB) (more recently renamed as Google Business Profile) profile is often the first point of contact between your law firm and potential clients. An optimized GMB listing can dramatically enhance your local SEO and drive more traffic to your website.
- Regularly updating business information such as hours, services, and location to keep potential clients informed.
- Encouraging satisfied clients to leave positive reviews, boosting your firm's credibility and attractivity.
Addressing SEO and the Importance of Accurate Citations
Citations, which are mentions of your business across the web, play a vital role in your SEO strategy. Accurate citations build domain authority and help your firm rank higher in search results.
- Audit and correct any discrepancies in how your firm’s name, address, and phone number appear online.
- Strategically increase citations on reputable legal and business websites to enhance your firm's online authority.
Frequently Asked Questions (FAQ)
Why is directory and citation management important for law firms?
Effective management ensures your firm is accurately represented online, enhancing your credibility and improving your SEO, which attracts more clients.
How often should law firms update their directory listings?
Law firms should review and update their listings at least bi-annually to ensure all information is current and reflects any changes in services or contact details.
To further refine your firm’s directory and citation strategy, access our comprehensive Ultimate Lawyer Digital Marketing Checklist.
References:
1. Moz:
2. Search Engine Journal:
Read the full article
0 notes
Text
You will get Customized monthly local SEO services designed for success in the UAE.
In today's digital world, having a strong online presence is Important for businesses to succeed, especially in the competitive market of the United Arab Emirates (UAE). One of the most effective ways to enhance your visibility and reach your target audience is through Search Engine Optimization (SEO). However, SEO is not a one-time task; it requires consistent effort and adaptation to stay ahead of the curve.
What are Customized Monthly Local SEO Services?
Customized monthly local SEO services are Greate strategies designed to improve a business's online visibility and rankings specifically within a local market, such as the UAE. These services encompass a range of techniques aimed at optimizing a website to appear prominently in search engine results pages (SERPs) when users search for relevant keywords related to the business's products or services.
Why are They Important?
In a country as diverse and digitally connected as the UAE, consumers rely heavily on search engines like Google to find local businesses and services. Without a strong presence in local search results, businesses risk being overshadowed by competitors and missing out on valuable opportunities to attract customers.
Customized monthly local SEO services offer several benefits:
Targeted Reach: By focusing on local keywords and geographic modifiers, businesses can connect with potential customers who are actively seeking their products or services in the UAE.
2. Increased Visibility: By optimizing various aspects of a website, such as on-page content, meta tags, and business listings, businesses can improve their chances of appearing at the top of local search results, thereby increasing visibility and attracting more organic traffic.
3. Enhanced User Experience: SEO isn't just about keywords; it's also about creating a seamless and user-friendly experience for website visitors. Customized monthly local SEO services often involve optimizing website speed, mobile responsiveness, and overall usability, which can lead to higher engagement and conversions.
4. Long-Term Growth: Unlike traditional advertising methods that require ongoing investment, the effects of SEO can compound over time, resulting in sustainable growth and a higher return on investment (ROI) for businesses in the UAE.
What Do Customized Monthly Local SEO Services Include?
Every business is unique, so customized monthly local SEO services are tailored to meet the specific needs and goals of each client. However, typical components of these services may include:
Keyword Research: Identifying the most relevant and high-traffic keywords related to the business's products or services and its target market in the UAE.
2. On-Page Optimization: Optimizing website content, meta tags, headers, and images to align with target keywords and improve search engine visibility.
3. Local Business Listings: Creating or optimizing business profiles on local directories, review sites, and mapping services to improve local search rankings and increase online visibility.
4. Content Creation: Developing high-quality, informative, and engaging content that resonates with the target audience and addresses their needs and pain points.
5. Link Building: Acquiring back-links from reputable websites and local sources to improve domain authority and credibility in the eyes of search engines.
6. Performance Monitoring: Tracking key metrics such as website traffic, keyword rankings, and conversion rates to measure the effectiveness of the SEO strategy and make data-driven adjustments as needed.
Conclusion:
In conclusion, customized monthly local SEO services offer businesses in the UAE a strategic improve their online visibility, attracting more qualified leads, and ultimately driving growth and success in the digital landscape. By partnering with experienced SEO professionals who understand the unique challenges and opportunities of the local market, businesses can stay ahead of the competition and achieve their marketing objectives with confidence.
#google ranking#keywords research#seo strategy#content optimization#digital marketing#Local SEO#UAE#Online Visibility#Local Search#Grow With SEO#Digital Success#Customized Services
0 notes
Text
what is vpn and dns
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn and dns
Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a powerful tool for ensuring online privacy, security, and freedom. Essentially, a VPN creates a secure and encrypted connection between your device and the internet, allowing you to browse the web anonymously and securely.
One of the primary functions of a VPN is to encrypt your internet traffic, making it unreadable to hackers, government agencies, or internet service providers (ISPs). This encryption ensures that your sensitive information, such as passwords, credit card details, and personal data, remains protected from prying eyes.
Moreover, VPNs enable users to mask their IP addresses. Your IP address is like your digital fingerprint, revealing your location and online activities. By connecting to a VPN server in a different location, you can effectively hide your real IP address and browse the web as if you were in another country. This feature not only enhances your privacy but also allows you to bypass geo-restrictions and access content that may be blocked or censored in your region.
In addition to privacy and security benefits, VPNs can also enhance your online experience by providing faster and more reliable internet connections, especially when accessing websites or streaming services that may be throttled or restricted by your ISP.
However, it's essential to choose a reputable VPN provider that prioritizes user privacy and does not log your online activities. Additionally, while VPNs offer robust protection, they are not foolproof, and users should still practice good internet hygiene, such as avoiding suspicious websites and using strong, unique passwords.
Overall, a VPN is an indispensable tool for anyone looking to safeguard their online privacy, bypass censorship, and enjoy a more secure internet experience.
Domain Name System (DNS)
The Domain Name System (DNS) is the backbone of the internet, serving as a directory that translates human-readable domain names into IP addresses. This system enables users to access websites and other online services using easy-to-remember names like "example.com" instead of complex strings of numbers.
DNS works like a phone book for the internet. When you type a domain name into your web browser, such as "www.google.com," your computer sends a request to a DNS server to resolve that name into the corresponding IP address, such as "172.217.9.196." This process allows your device to locate the server hosting the website you want to visit.
DNS operates in a hierarchical structure, with multiple levels of servers responsible for different parts of the domain name space. At the top of the hierarchy are the root DNS servers, which store information about the top-level domains (TLDs) like .com, .org, .net, and country-code TLDs like .uk or .jp. Below the root servers are the authoritative name servers, which store information about specific domain names and their corresponding IP addresses.
One of the key benefits of DNS is its ability to cache information, which helps to improve the efficiency of web browsing and reduce the load on DNS servers. When a DNS server resolves a domain name, it stores the result in its cache for a certain period of time, known as the Time to Live (TTL). This allows subsequent requests for the same domain name to be resolved more quickly, without the need to query upstream servers.
Overall, DNS plays a vital role in enabling the smooth functioning of the internet, ensuring that users can easily navigate to their desired online destinations with minimal hassle.
VPN Encryption
Title: Understanding VPN Encryption: Securing Your Online Activities
In today's digitally connected world, ensuring the security and privacy of our online activities is paramount. With the increasing prevalence of cyber threats and surveillance, utilizing tools like Virtual Private Networks (VPNs) has become essential. At the heart of VPNs lies encryption, a crucial mechanism that safeguards our data from prying eyes.
VPN encryption works by encoding the data transmitted between your device and the VPN server. This process involves scrambling the information in such a way that only authorized parties with the decryption key can decipher it. By doing so, VPN encryption shields your online communications, making them incomprehensible to anyone attempting to intercept them.
There are various encryption protocols employed by VPN services, each offering different levels of security and performance. Some of the most common protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP. These protocols utilize sophisticated encryption algorithms such as AES (Advanced Encryption Standard) with key lengths ranging from 128 to 256 bits, ensuring robust protection against cyber threats.
The strength of VPN encryption depends on factors such as the protocol used, the length of the encryption key, and the integrity of the VPN provider. Opting for reputable VPN services that prioritize security and employ stringent encryption standards is crucial for maximum protection.
Beyond safeguarding sensitive information such as passwords, financial details, and personal conversations, VPN encryption also serves as a shield against censorship and geo-restrictions. By masking your IP address and encrypting your internet traffic, VPNs enable users to bypass geographical blocks and access restricted content while preserving anonymity.
In conclusion, VPN encryption is a fundamental component of online security, offering a layer of defense against cyber threats and intrusion. By encrypting your internet traffic, VPNs empower you to browse the web with confidence, knowing that your data remains private and secure.
DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, is a malicious attack that exploits the Domain Name System (DNS) to redirect internet traffic to fraudulent websites. By manipulating the DNS server's cache, attackers can trick users into visiting fake websites that resemble legitimate ones, leading to sensitive information theft, financial scams, and malware installation.
The most common method of DNS spoofing involves the attacker intercepting DNS queries and replacing valid IP addresses with malicious ones. This way, when a user tries to access a specific website, they are unknowingly redirected to a bogus site controlled by the attacker. For example, a user typing "www.example.com" in their browser may be directed to a deceptive website designed to steal login credentials or distribute harmful software.
To protect against DNS spoofing, users and organizations can implement several security measures. Using DNSSEC (Domain Name System Security Extensions) can help verify the authenticity of DNS responses, mitigating the risk of spoofed data. Additionally, regularly updating and patching DNS servers can patch vulnerabilities that attackers may exploit to poison caches.
It is crucial for users to be vigilant when browsing the internet and to look out for signs of DNS spoofing, such as unexpected website redirects, SSL certificate errors, and unfamiliar login prompts. By staying informed about potential threats and implementing robust security practices, individuals and businesses can safeguard themselves against the dangers of DNS spoofing and maintain a secure online presence.
VPN Protocols
VPN protocols are the backbone of secure internet communication, ensuring that data transmitted between your device and the VPN server remains private and encrypted. These protocols dictate how data is transmitted and encrypted, providing varying levels of security, speed, and compatibility. Here are some of the most common VPN protocols:
OpenVPN: Known for its versatility and strong security features, OpenVPN is widely used across different platforms. It utilizes OpenSSL encryption and supports various authentication methods, making it a popular choice for both personal and corporate VPNs.
IKEv2/IPsec: Offering excellent performance and stability, Internet Key Exchange version 2 (IKEv2) with IPsec provides robust security and seamless switching between networks, making it ideal for mobile devices. It's known for its ability to quickly re-establish connections in case of network disruptions.
L2TP/IPsec: Layer 2 Tunneling Protocol (L2TP) with IPsec combines the best of both worlds by providing the tunneling capabilities of L2TP and the security features of IPsec. While it's widely supported across different platforms, it's not as secure as some other protocols due to potential vulnerabilities.
SSTP: Secure Socket Tunneling Protocol (SSTP) is developed by Microsoft and provides high levels of security by leveraging SSL/TLS encryption. It's commonly used on Windows operating systems and offers excellent performance, especially in areas with restricted internet access.
WireGuard: A newer addition to the VPN protocol landscape, WireGuard is praised for its simplicity, speed, and modern cryptographic design. It aims to be leaner and more efficient than traditional protocols while maintaining high levels of security.
When choosing a VPN protocol, consider factors such as security, speed, and compatibility with your devices and network requirements. Ultimately, the best protocol for you will depend on your specific needs and priorities.
0 notes
Text
does vpn change hosts fole
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn change hosts fole
How VPN affects hosts file
A VPN (Virtual Private Network) can have a significant impact on the hosts file of a computer or device. The hosts file is a local text file used by the operating system to map hostnames to IP addresses. It is commonly used to override DNS (Domain Name System) settings and block access to certain websites by redirecting their hostname to a different IP address, such as localhost (127.0.0.1).
When a VPN is activated, it reroutes all internet traffic through its servers, encrypting the data and masking the user's IP address. This means that DNS queries are also routed through the VPN's DNS servers, rather than the ones provided by the user's ISP (Internet Service Provider).
As a result, the hosts file entries may not function as expected when a VPN is active. For example, if a user has added entries to block certain websites by redirecting their hostname to localhost, these entries may be bypassed when the VPN is enabled because the DNS resolution is handled by the VPN's servers, which may not honor the entries in the hosts file.
Additionally, some VPN services modify the hosts file as part of their functionality. They may add their own entries to the hosts file to redirect certain domains through the VPN tunnel or to prevent access to known malicious websites.
Users should be aware of how VPNs can affect their hosts file and adjust their configurations accordingly. This may involve updating the hosts file to include entries that work with the VPN's DNS servers or using alternative methods to achieve the desired website blocking or redirection behavior.
Changing hosts file using VPN
Changing the hosts file using a VPN is a useful technique for modifying the way your computer resolves domain names, even while connected to a VPN server. The hosts file is a local file on your computer that maps hostnames to IP addresses, bypassing the need for a DNS server lookup. By editing the hosts file, you can override the default DNS resolution for specific domain names.
When using a VPN, your internet traffic is encrypted and routed through a remote server, which can sometimes affect how your computer resolves domain names. If you encounter issues accessing certain websites or services while connected to a VPN, modifying the hosts file can be a workaround to access them directly through their IP addresses.
To change the hosts file while using a VPN, you first need to locate the hosts file on your operating system (located in different directories depending on whether you are using Windows, macOS, or Linux). Then, you can add entries to map domain names to specific IP addresses, effectively bypassing the DNS lookup process.
It is essential to note that making changes to the hosts file should be done with caution, as incorrect entries can potentially break connectivity to websites. Always make backups of the original hosts file before making any modifications.
In conclusion, changing the hosts file using a VPN can be a handy trick to overcome DNS resolution issues while ensuring secure and private internet browsing. Just remember to handle the hosts file with care to prevent any unintended consequences on your system.
VPN impact on hosts file
A VPN, or Virtual Private Network, serves as a secure tunnel between your device and the internet. It encrypts your internet traffic, providing anonymity and enhancing security. One aspect of using a VPN that often goes unnoticed is its impact on the hosts file of your device.
The hosts file is a local file on your device that maps hostnames to IP addresses. It is commonly used to block access to malicious websites or to redirect specific URLs. When you connect to a VPN, it creates a virtual network interface on your device and routes all your internet traffic through this interface. This means that all DNS resolutions are also routed through the VPN network.
As a result, the hosts file on your device may not function as expected when connected to a VPN. Any entries in the hosts file that redirect or block certain websites may be bypassed when using a VPN, as the DNS resolution is controlled by the VPN server.
It is essential to be aware of this impact when using a VPN, especially if you rely on the hosts file for specific website redirections or blocking malicious domains. In such cases, additional measures may be required to achieve the desired outcome while using a VPN.
In conclusion, while VPNs are powerful tools for enhancing online security and privacy, their impact on the hosts file should be considered to ensure that your device functions as intended while connected to a VPN. Be mindful of this interaction to make informed decisions regarding your online activities and security measures.
Hosts file manipulation with VPN
Manipulating the hosts file alongside a VPN can be a strategic move for users seeking enhanced control over their internet browsing experience. The hosts file, a plain text file stored on a computer, associates IP addresses with domain names, effectively acting as a local DNS resolver. By editing this file, users can override DNS settings and direct specific domain names to different IP addresses.
When combined with a VPN (Virtual Private Network), hosts file manipulation can further bolster privacy and security measures. A VPN encrypts internet traffic and routes it through a remote server, masking the user's IP address and location. By editing the hosts file to block certain domains or redirect them to local addresses, users can enhance their anonymity and protect against unwanted tracking or malicious sites.
For instance, users may choose to block advertisements or tracking domains by redirecting them to localhost (127.0.0.1) in the hosts file. This prevents connections to these domains at the system level, bypassing the need for browser extensions or plugins. Additionally, users can redirect domains associated with known malware or phishing sites, adding an extra layer of defense against cyber threats.
However, it's essential to exercise caution when manipulating the hosts file, as incorrect modifications can disrupt internet connectivity or lead to unintended consequences. Users should always make backups of the original hosts file and double-check their changes to avoid potential issues.
In conclusion, combining hosts file manipulation with a VPN offers users greater control over their online privacy and security. By redirecting or blocking specific domains, individuals can customize their browsing experience while safeguarding against threats and intrusive tracking mechanisms.
Modifying hosts file with VPN
Modifying the hosts file with a VPN can be a useful technique for both privacy-conscious users and those seeking to bypass certain restrictions. The hosts file, a local text file on your computer, maps hostnames to IP addresses, essentially acting as a local DNS resolver. By modifying this file, users can direct their computer to specific IP addresses for certain domain names, effectively overriding the DNS lookup process.
When combined with a VPN (Virtual Private Network), modifying the hosts file can enhance privacy and security. VPNs encrypt internet traffic and route it through remote servers, masking the user's IP address and encrypting data transmissions. By editing the hosts file to block connections to tracking or malicious domains, users can add an extra layer of protection against intrusive tracking and potential security threats.
Moreover, modifying the hosts file with a VPN can help bypass certain restrictions imposed by ISPs (Internet Service Providers) or governments. For example, users in countries with internet censorship may use this method to access blocked websites by redirecting DNS requests through VPN servers located in regions with unrestricted access.
However, it's essential to proceed with caution when modifying the hosts file, as incorrect entries can disrupt internet connectivity or lead to unintended consequences. Users should make backups of the original hosts file and exercise care when editing it.
In conclusion, combining the modification of the hosts file with a VPN can offer increased privacy, security, and the ability to bypass certain restrictions. Nonetheless, users should approach this technique with care and ensure they understand the potential implications of their modifications.
0 notes