#endpoint manager
Text
Always On VPN DPC with Intune
Always On VPN DPC with Intune
In the past, I’ve written about PowerON Platforms’ Always On VPN Dynamic Profile Configurator (DPC), a software solution administrators can use to provision and manage Always On VPN client configuration settings using Active Directory and group policy. In addition to streamlining the deployment and management of Always On VPN client settings, DPC has many advanced features and capabilities to…

View On WordPress
#Active Directory#Always On VPN#AOVPN#ConfigMgr#configuration#DPC#Dynamic Profile Configurator#endpoint#endpoint management#endpoint manager#enterprise mobility#GPMC#group policy#Group Policy Management Console#InTune#MEM#MEMCM#Microsoft#Microsoft Endpoint Manager#Mobility#optimizations#otpimization#performance#policy#PowerON Platforms#Proactive Remediation#SCCM#security#systems management#Windows
2 notes
·
View notes
Text
anyway. i'm rotating divorce quartet. because. it's not as if they didn't look for each other. they looked all over the map, cleo says. none of them went into it assuming they would fail or abandon or be abandoned by their soulmate. and it's easy to forget that because by the end of session 1 it's already fallen apart, but. there's a world where it worked out for them. maybe it still wasn't good--certainly the other pairs make it clear things can go bad even if you're together--but at least they'd each have their soulbound partner there, right? they had, all of them, bought into the premise. and it's still. i don't know that they ever shake it off completely.
scott and cleo choose each other, allegedly in defiance of the soulbound, but it's still. two people. deciding to stick together against everyone else. there's a world where pearl joins them, or joins a different soulbound pair, but that's not how the soulmate system works, right? it's always two. to be three is unthinkable, unless you assume the exclusive primacy of some particular pair in that three. the third will always just be... tagging along for a bit. it was never going to work. and it's not as if there weren't external pressures to do the teaming up with your soulbound thing -- being able to keep an eye on this other potential avenue from which harm could arrive at you, not having to guess if that tick was your soulbound or a skeleton you can't see are advantages in a death game.
but the thing is they don't think to try. your options are to go with the partnership that has been forced upon you, or to stand in the most vocal opposition to it you can manage. but you're still being defined in relation to the original thing you're against? there is still the fact that anything you can dream up for yourself is still founded on the initial shape of two soulbound partners versus the whole rest of the world. there's nowhere to fit yourself if you try something else. at the end of the game, it still comes down to pearl and scott. at the end of the game, martyn still dies when cleo does. they still bought into the premise. it was never not going to eat them all.
#sparrowsong#it's. this is just imagery but. they built a bridge.#a bridge still only has two endpoints.#pearl tried to build a place to stay in the middle of the bridge#and got it almost immediately burned down for her trouble#jesus. the fic practically writes itself. the bridge. the tower. the safehouse. hrghh.#there's a handful of stray thoughts i feel like i'm missing here. will come back and update if i manage to sort them out.#the closest you will ever get to falling in love#double life
10 notes
·
View notes
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes
Text
Say goodbye to standard security for smartphones (you need this instead) - CyberTalk
New Post has been published on https://thedigitalinsider.com/say-goodbye-to-standard-security-for-smartphones-you-need-this-instead-cybertalk/
Say goodbye to standard security for smartphones (you need this instead) - CyberTalk


By Zahier Madhar, Lead Security Engineer and Office of the CTO, Check Point.
Smartphones play a pivotal role in all of our lives. In a way, smartphones today are a sort of a diary, storing pictures, organizing them and displaying them in a story telling modality. Smartphones are much more than a piece of technology that allows you to make phone calls and send text messages.
Many people, before they go to bed, they have their smartphones in their hands; they are getting the latest updates, finishing some work, or watching a movie or video shorts. And once they wake up, the first activity of the day consists of picking up the smartphone, checking the time and seeing about whether or not they have missed any updates.
Smartphones: dual uses
That very same smartphone is often used for business purposes as well; such attending or hosting meetings, emails and managing an agenda. The dual-purpose dimension is also the case with a laptop (used for both private and business purposes). The biggest different between a laptop and a smartphone is that a smartphone is always turned on and connected to the internet, while a laptop, not-so-much.
A second difference is that a laptop is managed and has a threat prevention application on it. In contrast, smartphones are, in many cases, managed by the organization but not secured by a threat prevention application. However, the smartphone contains the same mix of private data and business related data as the laptop. See the problem?
The bakery next door
In a previous Cyber Talk thought leadership article, I talked about the bakery next door. The bakery next door can use a smartphone to get the status of the ovens, but also to control the ovens. Imagine if the baker’s smartphone were hacked and hackers took control over the most important ovens. This would impact the bakery’s output immediately. This is not just a theory; this could happen. Although this example is small-scale, the implications are immense; lack of smartphone security can jeopardize a business.
History of mobile threats
Malware targeting smartphones is not new. The difference today compared with 20 years ago is that the smartphone holds sensitive data; sensitive data on private and business level.
The question is why do organization fail to install mobile anti-malware on the smartphones? I believe it has to do with awareness, costs, and user experience or they think it is not needed (especially for iOS users).
iOS cyber security
Despite popular belief, it is possible to install malware on iOS devices and since the EU’s Digital Markets Act of 2022 came about, Apple has been forced to allow also apps outside the App store on its phones.
But regulating smartphones based on unified endpoint management and mobile device management is not enough. The reason why is simple: These security tools do not contain security controls for inspecting apps, network connections and interfaces in regards to malicious behavior.
Malware prevention
Let’s get back to the bakery next door. The baker uses his smartphone for daily business (baking bread-related tasks) and also for personal use. To avoid getting infected by malware, the baker does not install apps outside of the App store, does not scan QR codes and does not connect to public wifi.
As with his laptop, he makes sure that the smartphone and his apps are always updated with the latest software releases. Still, this is not enough. The baker won’t successfully avoid SMS phishing, malicious websites and network related attacks by taking those steps. To truly advance his security, the baker needs to install a mobile security solution that protects the smartphone from mobile security risks.
The baker is lucky because he relies on a cyber security vendor partner to deliver a platform and he can simply apply mobile security, in addition to the other security controls that have been delivered, through the platform.
In other words, what the baker has is a consolidated cyber security platform with threat prevention, ensuring that his business won’t be disrupted by opportunistic hackers.
Key takeaways
As I mentioned earlier, smartphones have become day-to-day essentials, shaping our social interactions and business operations. However, they also present security risks, as they contain sensitive personal and business information. Here are some tips to enhance smartphone security:
1. Stick to official app stores for downloading apps.
2. Avoid connecting to public wifi networks.
3. Consider installing a mobile threat prevention application.
As a Chief Information Security Officer (CISO), it’s crucial to treat smartphones with the same level of security awareness as laptops. Incorporate them into your awareness campaigns and ensure they are regularly updated with the latest patches.
Implement mobile threat prevention solutions like Harmony Mobile from Check Point to serve as a security enforcement point for your Unified Endpoint Management (UEM) or Mobile Device Management (MDM) system.
These measures will enhance security maturity and provide visibility into potential malicious activities on mobile devices within your organization.
For more insights from Zahier Madhar, please click here. To receive compelling cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2022#analyses#anti-malware#app#app store#apple#apps#Article#awareness#Behavior#bread#Business#Check Point#chief information security officer#CISO#consolidated#consolidated cyber security#CTO#cyber#cyber security#data#devices#endpoint#Endpoint Management#Engineer#eu#hackers#History#Hosting#impact
0 notes
Text
Protect your business from API breaches with comprehensive security testing. Learn from recent incidents and implement best practices for robust API security.
#api protection#api security#api security testing#api scanning#api endpoints#api management#firewall
0 notes
Text
ManageEngine Named a 'Strong Performer' in Unified Endpoint Management and Enterprise Service Management
ManageEngine’s Endpoint Central and ServiceDesk Plus acknowledged
Company attained top scores possible in OS support, application management, innovation, pricing flexibility and transparency criteria in UEM evaluation
View a complimentary copy of the 2023 report for UEM – https://mnge.it/UEMPR2023
Philippines — ManageEngine, the enterprise IT management division of Zoho Corporation, today…

View On WordPress
0 notes
Text
Vietnamese Hackers Hit Digital Marketers With Info Stealers
Anti-Phishing, DMARC
,
Endpoint Security
,
Fraud Management & Cybercrime
Under Fire: US, UK and India; Attackers Often Wield DarkGate Info-Stealing Malware
Jayant Chakravarti (@JayJay_Tech) •
October 20, 2023
Image: Shutterstock
Cybercrime groups in Vietnam are targeting the digital marketing sector in the United Kingdom, United States and India with multiple malware strains, including the…

View On WordPress
0 notes
Text
0 notes
Text
The Business Research Company offers unified endpoint management market research report 2023 with industry size, share, segments and market growth
#unified endpoint management market analysis#unified endpoint management market segments#unified endpoint management market forecast#unified endpoint management market growth#unified endpoint management market overview#unified endpoint management market share#unified endpoint management market size#unified endpoint management market outlook#global unified endpoint management market#unified endpoint management market trends
0 notes
Text
Microsoft Intune Cloud PKI and Certificate Templates
Microsoft recently announced the general availability of its new PKI-as-a-Service platform called Microsoft Intune Cloud PKI. With Intune Cloud PKI, administrators create certification authorities (CAs) to issue and manage user and device authentication certificates for Intune-managed endpoints. Cloud PKI also provides hosted Authority Information Access (AIA) and Certificate Revocation List…

View On WordPress
#Active Directory#Active Directory Certificate Services#AD#AD CS#ADCS#AIA#authentication#CDP#certificate#certificate authority#certificate template#certificates#Certification Authority#Cloud PKI#CRL#encryption#endpoint manager#InTune#Intune Cloud PKI#MEM#Microsoft#Microsoft Endpoint Manager#Microsoft Intune Cloud PKI#NDES#Network Device Enrollment Service#PKI#public key infrastructure#SCEP#security#Simple Certificate Enrollment Protocol
0 notes
Text
#Unified Endpoint Management Market#Unified Endpoint Management Market Trends#Unified Endpoint Management Market Growth#Unified Endpoint Management Market Industry#Unified Endpoint Management Market Research#Unified Endpoint Management Market Report
0 notes
Text
Inbound vs outbound traffic in Azure. What you need to know?
As many companies have moved their database and sensitive information to the cloud, it is important to have a solid understanding of how data flows in and out of your cloud environment. In Microsoft Azure, managing inbound and outbound traffic is an impor
As many companies have moved their database and sensitive information to the cloud, it is important to have a solid understanding of how data flows in and out of your cloud environment. In Microsoft Azure, managing inbound and outbound traffic is an important aspect of ensuring optimal performance, security, and cost-effectiveness.
Managing inbound and outbound traffic in Azure is crucial for…
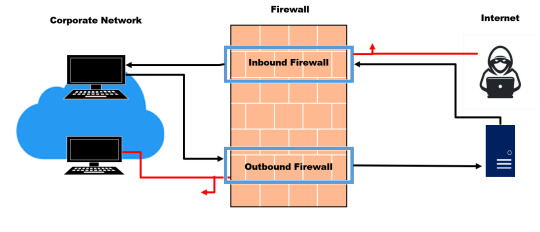
View On WordPress
#Azure#Azure Application Gateway#Azure Hybrid Connections#Azure Inbound Traffic#Azure Outbound Traffic#Azure Private EndPoint#Azure Private Link#Azure Service Endpoint#Azure Traffic Management#Azure Virtual network Integration#microsoft azure
0 notes
Text
Exclusive Discount on DanteAV PTZ Cameras - Videoguys
New Post has been published on https://thedigitalinsider.com/exclusive-discount-on-danteav-ptz-cameras-videoguys/
Exclusive Discount on DanteAV PTZ Cameras - Videoguys


Save $500 on PTZOptics Link 4K PTZ Cameras
Your Dante Workflow is About to Get Easier
Ready to add video to your Dante setup? With Dante AV-H™ and the latest in auto-tracking capabilities, the Link 4K fits easily into even the most complex Dante design or workflow. The Link 4K combines broadcast quality with Dante’s simple discovery, set up and management, simplifying and professionalizing any video production installation.

What is Dante AV-H?
Dante AV-H brings device interoperability and the power of Dante to H.26x endpoints. With Dante AV-H, all video and audio routing, configuration, and management of devices is done with one easy to use platform. The Link 4K will automatically sync up with your Dante system clock leader ensuring seamless audio and video synchronization, and is able to output Dante AV-H video on your network natively, along with audio sources connected to the 3.5mm audio input. Designed with the Future in Mind
Every Link 4K camera features SDI, HDMI, USB, and IP output for unparalleled performance and versatility. The Link 4K features 4K at 60fps over HDMI, USB, and IP. Using technology by Dante, the Link 4K can also provide 4K at 60fps resolution over Dante AV-H. The Link 4K offers built-in auto-tracking capabilities — no need to run software on another computer — freeing teams of the need for a camera operator.

PTZOptics also makes a line of PTZ Cameras with NDI|HX

Now with NDI|HX license included!
PTZ and auto-tracking features, now more accessible. Combining HDMI, SDI, USB, and IP outputs into one camera, with native NDI® support coming soon. Perfect for live streaming and video production, offering high-quality 1080p60fps resolution & excellent low-light performance thanks to SONY CMOS sensors.
starting at $999.00

Featuring auto-tracking for a more intelligent video production workflow. The Move 4K is capable of 4K at 60fps (1080p at 60fps over SDI), future-proofing your technology investment while still accommodating HD and Full HD video resolutions equipment. The Move 4K offers high performance in low-light, PoE+ capabilities, & a built-in tally light.
starting at $1,799.00
#4K#amp#audio#Cameras#computer#Design#devices#easy#endpoints#equipment#Features#Full#Future#hdmi#investment#Light#Link#management#network#One#performance#platform#power#Production#PTZOptics#resolution#sensors#setup#Software#sony
0 notes
Text
Extending Detection to Every Managed and Unmanaged Connected Device in Your Enterprise: A Comprehensive Guide
As technology continues to advance, the number of connected devices in enterprises is increasing rapidly. According to a forecast by International Data Corporation (IDC), there will be 42 billion IoT devices in 2025, capable of generating 80 zettabytes (ZB) of data.. With so many devices in use, enterprises are facing new challenges in terms of security and device management. It has become…

View On WordPress
#Cloud Access Security Broker#Connected Devices#Cybersecurity#Endpoint Detection and Response#Enterprise Security#Internet of Things Security#Mobile Device Management
0 notes
Text
The importance of our Managed Endpoint Security
Cybercriminals have more entry points into a company network the more endpoint devices connected to it. Endpoint security management is a software strategy that allows network administrators to track and control end users' device access over the company network, including employees' personal devices.
Our Managed Endpoint Security includes
controllable antivirus software
Web filtration
Managing applications and patches
Controlling network access and "need to know"
Software for a virtual private network
Encryption of emails and data
Administrators can restrict network access for devices that don't adhere to the organization's security policy. They can also establish policies to limit end-user access to network resources to those they actually need to know in order to perform their jobs. In doing so, they contribute to ensuring that the organization remains secure from security risks regardless of how many devices connect to the network.
What is the Operation of our Endpoint Security Systems?
Depending on the sort of protection or online access needed by employees and systems, endpoint security apps give managers the ability to manage security for corporate endpoints through policy settings. Administrators should, for instance, always check that every device connecting to the network is running the most recent version of antivirus software and has all essential patches and updates installed. They should also ban access to websites known to host malware and other harmful content.
Employees must be able to access corporate data from any location because so many more work remotely, either because they are headquartered off-site or because travel is a significant part of their jobs. No matter where they are or what device they use while working, your employees and your organization must be protected with effective endpoint protection with our 24x7 Help Desk Support. It helps in providing help support at any time and prevents loss of data.
0 notes