#Android Google
Explore tagged Tumblr posts
Text
Critical PSA for anyone with Android devices!
I got the following email this morning:


Basically Google is rolling out the ability to track you via your android devices even when you're offline and you have to manually opt out of it. Many android devices no longer come with a wired headphone jack, so if you have Bluetooth headphones or a keyboard or anything, your location will be tracked and stored by your device unless you opt out of this.
I tried using the link they gave me in the email to opt out of it, but it didn't really seem to do anything. So I looked up how to opt out and found the following steps, which worked for my phone:
Opting out from the Find My Device network is as simple as tapping a toggle in your phone's settings. 1. On your Android device, go to Settings. 2. Tap the Google setting. 3. Tap the Find My Device setting. 4. Tap the toggle to off next to "Use Find My Device." 5. Confirm with pin, pattern, or biometrics. That's it. Your device is no longer participating in the Find My Device network. To rejoin, just flip the toggle back on.
Please reblog to spread awareness. My husband has the same phone as me and he didn't get any emails about this.
23K notes
·
View notes
Text
When it comes to green tones these two Live Wallpapers are my current favorites, both, illustration and how parallax works on these /ᐠ o ˕ oマ🍀🍃₊˚⊹♡ …these will work on Android devices only. Download LINK! ^_^
517 notes
·
View notes
Text
Google’s new phones can’t stop phoning home

On OCTOBER 23 at 7PM, I'll be in DECATUR, presenting my novel THE BEZZLE at EAGLE EYE BOOKS.

One of the most brazen lies of Big Tech is that people like commercial surveillance, a fact you can verify for yourself by simply observing how many people end up using products that spy on them. If they didn't like spying, they wouldn't opt into being spied on.
This lie has spread to the law enforcement and national security agencies, who treasure Big Tech's surveillance as an off-the-books trove of warrantless data that no court would ever permit them to gather on their own. Back in 2017, I found myself at SXSW, debating an FBI agent who was defending the Bureau's gigantic facial recognition database, which, he claimed, contained the faces of virtually every American:
https://www.theguardian.com/culture/2017/mar/11/sxsw-facial-recognition-biometrics-surveillance-panel
The agent insisted that the FBI had acquired all those faces through legitimate means, by accessing public sources of people's faces. In other words, we'd all opted in to FBI facial recognition surveillance. "Sure," I said, "to opt out, just don't have a face."
This pathology is endemic to neoliberal thinking, which insists that all our political matters can be reduced to economic ones, specifically, the kind of economic questions that can be mathematically modeled and empirically tested. It would be great if all our thorniest problems could be solved like mathematical equations.
Unfortunately, there are key elements of these systems that can't be reliably quantified and turned into mathematical operators, especially power. The fact that someone did something tells you nothing about whether they chose to do so – to understand whether someone was coerced or made a free choice, you have to consider the power relationships involved.
Conservatives hate this idea. They want to live in a neat world of "revealed preferences," where the fact that you're working in a job where you're regularly exposed to carcinogens, or that you've stayed with a spouse who beats the shit out of you, or that you're homeless, or that you're addicted to Oxy, is a matter of choice. Monopolies exist because we all love the monopolist's product best, not because they've got monopoly power. Jobs that pay starvation wages exist because people want to work full time for so little money that they need food-stamps just to survive. Intervening in any of these situations is "woke paternalism," where the government thinks it knows better than you and intervenes to take away your right to consume unsafe products, get maimed at work, or have your jaw broken by your husband.
Which is why neoliberals insist that politics should be reduced to economics, and that economics should be carried out as if power didn't exist:
https://pluralistic.net/2024/10/05/farrago/#jeffty-is-five
Nowhere is this stupid trick more visible than in the surveillance fight. For example, Google claims that it tracks your location because you asked it to, by using Google products that make use of your location without clicking an opt out button.
In reality, Google has the power to simply ignore your preferences about location tracking. In 2021, the Arizona Attorney General's privacy case against Google yielded a bunch of internal memos, including memos from Google's senior product manager for location services Jen Chai complaining that she had turned off location tracking in three places and was still being tracked:
https://pluralistic.net/2021/06/01/you-are-here/#goog
Multiple googlers complained about this: they'd gone through dozens of preference screens, hunting for "don't track my location" checkboxes, and still they found that they were being tracked. These were people who worked under Chai on the location services team. If the head of that team, and her subordinates, couldn't figure out how to opt out of location tracking, what chance did you have?
Despite all this, I've found myself continuing to use stock Google Pixel phones running stock Google Android. There were three reasons for this:
First and most importantly: security. While I worry about Google tracking me, I am as worried (or more) about foreign governments, random hackers, and dedicated attackers gaining access to my phone. Google's appetite for my personal data knows no bounds, but at least the company is serious about patching defects in the Pixel line.
Second: coercion. There are a lot of apps that I need to run – to pay for parking, say, or to access my credit union or control my rooftop solar – that either won't run on jailbroken Android phones or require constant tweaking to keep running.
Finally: time. I already have the equivalent of three full time jobs and struggle every day to complete my essential tasks, including managing complex health issues and being there for my family. The time I take out of my schedule to actively manage a de-Googled Android would come at the expense of either my professional or personal life.
And despite Google's enshittificatory impulses, the Pixels are reliably high-quality, robust phones that get the hell out of the way and let me do my job. The Pixels are Google's flagship electronic products, and the company acts like it.
Until now.
A new report from Cybernews reveals just how much data the next generation Pixel 9 phones collect and transmit to Google, without any user intervention, and in defiance of the owner's express preferences to the contrary:
https://cybernews.com/security/google-pixel-9-phone-beams-data-and-awaits-commands/
The Pixel 9 phones home every 15 minutes, even when it's not in use, sharing "location, email address, phone number, network status, and other telemetry." Additionally, every 40 minutes, the new Pixels transmit "firmware version, whether connected to WiFi or using mobile data, the SIM card Carrier, and the user’s email address." Even further, even if you've never opened Google Photos, the phone contacts Google Photos’ Face Grouping API at regular intervals. Another process periodically contacts Google's Voice Search servers, even if you never use Voice Search, transmitting "the number of times the device was restarted, the time elapsed since powering on, and a list of apps installed on the device, including the sideloaded ones."
All of this is without any consent. Or rather, without any consent beyond the "revealed preference" of just buying a phone from Google ("to opt out, don't have a face").
What's more, the Cybernews report probably undercounts the amount of passive surveillance the Pixel 9 undertakes. To monitor their testbench phone, Cybernews had to root it and install Magisk, a monitoring tool. In order to do that, they had to disable the AI features that Google touts as the centerpiece of Pixel 9. AI is, of course, notoriously data-hungry and privacy invasive, and all the above represents the data collection the Pixel 9 undertakes without any of its AI nonsense.
It just gets worse. The Pixel 9 also routinely connects to a "CloudDPC" server run by Google. Normally, this is a server that an enterprise customer would connect its employees' devices to, allowing the company to push updates to employees' phones without any action on their part. But Google has designed the Pixel 9 so that privately owned phones do the same thing with Google, allowing for zero-click, no-notification software changes on devices that you own.
This is the kind of measure that works well, but fails badly. It assumes that the risk of Pixel owners failing to download a patch outweighs the risk of a Google insider pushing out a malicious update. Why would Google do that? Well, perhaps a rogue employee wants to spy on his ex-girlfriend:
https://www.wired.com/2010/09/google-spy/
Or maybe a Google executive wins an internal power struggle and decrees that Google's products should be made shittier so you need to take more steps to solve your problems, which generates more chances to serve ads:
https://pluralistic.net/2024/04/24/naming-names/#prabhakar-raghavan
Or maybe Google capitulates to an authoritarian government who orders them to install a malicious update to facilitate a campaign of oppressive spying and control:
https://en.wikipedia.org/wiki/Dragonfly_(search_engine)
Indeed, merely by installing a feature that can be abused this way, Google encourages bad actors to abuse it. It's a lot harder for a government or an asshole executive to demand a malicious downgrade of a Google product if users have to accept that downgrade before it takes effect. By removing that choice, Google has greased the skids for malicious downgrades, from both internal and external sources.
Google will insist that these anti-features – both the spying and the permissionless updating – are essential, that it's literally impossible to imagine building a phone that doesn't do these things. This is one of Big Tech's stupidest gambits. It's the same ruse that Zuck deploys when he says that it's impossible to chat with a friend or plan a potluck dinner without letting Facebook spy on you. It's Tim Cook's insistence that there's no way to have a safe, easy to use, secure computing environment without giving Apple a veto over what software you can run and who can fix your device – and that this veto must come with a 30% rake from every dollar you spend on your phone.
The thing is, we know it's possible to separate these things, because they used to be separate. Facebook used to sell itself as the privacy-forward alternative to Myspace, where they would never spy on you (not coincidentally, this is also the best period in Facebook's history, from a user perspective):
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3247362
And we know it's possible to make a Pixel that doesn't do all this nonsense because Google makes other Pixel phones that don't do all this nonsense, like the Pixel 8 that's in my pocket as I type these words.
This doesn't stop Big Tech from gaslighting* us and insisting that demanding a Pixel that doesn't phone home four times an hour is like demanding water that isn't wet.
*pronounced "jass-lighting"
Even before I read this report, I was thinking about what I would do when I broke my current phone (I'm a klutz and I travel a lot, so my gadgets break pretty frequently). Google's latest OS updates have already crammed a bunch of AI bullshit into my Pixel 8 (and Google puts the "invoke AI bullshit" button in the spot where the "do something useful" button used to be, meaning I accidentally pull up the AI bullshit screen several times/day).
Assuming no catastrophic phone disasters, I've got a little while before my next phone, but I reckon when it's time to upgrade, I'll be switching to a phone from the @[email protected]. Calyx is an incredible, privacy-focused nonprofit whose founder, Nicholas Merrill, was the first person to successfully resist one of the Patriot Act's "sneek-and-peek" warrants, spending 11 years defending his users' privacy from secret – and, ultimately, unconstitutional – surveillance:
https://www.eff.org/deeplinks/2013/03/depth-judge-illstons-remarkable-order-striking-down-nsl-statute
Merrill and Calyx have tapped into various obscure corners of US wireless spectrum licenses that require major carriers to give ultra-cheap access to nonprofits, allowing them to offer unlimited, surveillance-free, Net Neutrality respecting wireless data packages:
https://memex.craphound.com/2016/09/22/i-have-found-a-secret-tunnel-that-runs-underneath-the-phone-companies-and-emerges-in-paradise/
I've been a very happy Calyx user in years gone by, but ultimately, I slipped into the default of using stock Pixel handsets with Google's Fi service.
But even as I've grown increasingly uncomfortable with the direction of Google's Android and Pixel programs, I've grown increasingly impressed with Calyx's offerings. The company has graduated from selling mobile hotspots with unlimited data SIMs to selling jailbroken, de-Googled Pixel phones that have all the hardware reliability of a Pixel, coupled with an alternative app suite and your choice of a Calyx SIM and/or a Calyx hotspot:
https://calyxinstitute.org/
Every time I see what Calyx is up to, I think, dammit, it's really time to de-Google my phone. With the Pixel 9 descending to new depths of enshittification, that decision just got a lot easier. When my current phone croaks, I'll be talking to Calyx.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/08/water-thats-not-wet/#pixelated

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#google#android#pixel#privacy#pixel 9#locational privacy#back doors#checkhov's gun#cybernews#gaslighting
541 notes
·
View notes
Text

#androids who google#press X to retain innocence#X!#connor is a cinnamon roll#with a kill count 😐#detroit become meme#connor detroit become human#connor dbh#dbh connor#dbh#connor rk800#dbh rk800#connor anderson#detroit connor#connor’s instructions#connor army#dbh edits#detroit become human memes#detroit become human rk800
154 notes
·
View notes
Text


My partner asked me to draw evil Wheatley
#Wheatley#glados#chell portal#portal 2#mathes0nart#giving him this cool tech android villain design is so cool and awesome#but what if he dressed like an evil oil baron#what if he googled ‘smart handsome guy’ and raided glados’s private butch collection to dress the part#I can’t emphasize how much I love this man and how it’s so important to me that he’s so stupid#dumbass rep
501 notes
·
View notes
Text

76 notes
·
View notes
Text
why does so much robotfucking hornyposting on this site revolve around opening up a computer/robot/android and rooting around in its internal wiring WHILE IT'S ON? do yall not value your fingers? at least integrate proper lockout/tagout procedure into your fantasies. and then there's the issue where letting someone literally open you up and stick their hands in your organs carries a pretty high risk of straight up dying, especially if that person's only medical/technical qualification is being horny about it. that's like letting a grindr hookup with a surgery fetish but no medical education whatsoever perform an appendectomy on you
#being an android and seeing the person doing maintenance on you checking the manual mid-repair#would be like seeing your dentist google “how to fill cavity” while he has a drill in your mouth
109 notes
·
View notes
Text
ANDROID USERS
Check your Installed Apps for an app called ‘Android System SafetyCore’ (Settings > Installed Apps). If it is there, IT HAS BEEN SHADOW-INSTALLED WITHOUT NOTIFICATION OR CONSENT AND LOOKS AT YOUR PICTURES. < as well as this it has also been reported that it drains battery
DELETE IT IMMEDIATELY, IT IS SPYWARE!!
https://play.google.com/store/apps/details?id=com.google.android.safetycore <- it wont show up in searches so use this link!
i just uninstalled it from my phone

#viro talks#viro said/drew a thing#tumblr#tumblr news#important#spyware#bloatware#android#google#google bullshit#dashboard#tumblr dashboard#help i really dont know what to tag this with#destiel news channel#destiel news
56 notes
·
View notes
Text
A federal judge on Wednesday indicated he will order major changes in Google’s Android app store to punish the company for engineering a system that a jury declared an illegal monopoly that has hurt millions of consumers and app developers. Over the course of a three-hour hearing in San Francisco, U.S. District Judge James Donato made it clear that the forthcoming shake-up he is contemplating will probably include a mandate requiring Google’s Play Store for Android phones offer consumers a choice to download alternative app stores Donato has been weighing how to punish the Google since last December when a jury declared the Play Store a monopoly following a four-week trial. The verdict centered on Google’s nearly exclusive control over distribution of apps designed for Android phones and the billing systems for the digital commerce occurring within them — a system that generates billions of dollars in annual revenue for the company.
111 notes
·
View notes
Text
Android’s Emoji Kitchen is unhinged. Like, thanks Google.
How in the world have I ever lived without this emotion??
324 notes
·
View notes
Note
why u flagged as nsfw
are you on the android app because if so that would be why
#google forced them to do some really dumb shit to stay on the play store#so the android app is a bit of a mess right now#answered
23 notes
·
View notes
Text


428 notes
·
View notes
Text
New Live Wallpaper for April! Blossoming Colors🌸It will work on Android phones only ^_^ ( MP4 version for iOS coming soon! ) Download LINK!
259 notes
·
View notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Text
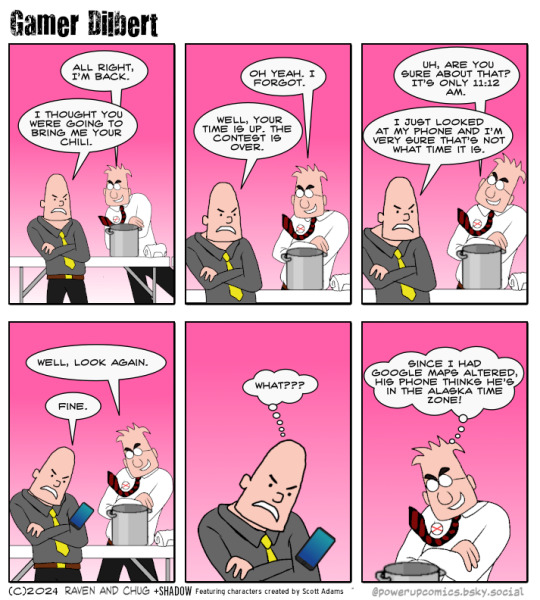
#Gamer Dilbert#Powerup Comics#Dilbert#CEO#Chili Contest#Google Maps#I don't think the android clock is actually set by google maps but this is a heightened reality#Webcomics#comics
50 notes
·
View notes
Text
Android expertek!
Tudja valaki, hogy lehet kigyomlálni a google RCS üzenetküldöjét és visszaszerezni a normál SMS üzenteket Android alatt?
Egy darabig csak ajánlgatta magát, de most már simán felülírta a normál appot.
Ezzel a szarral

lötték fejbe a normálmessages appot:

32 notes
·
View notes