#Application Security testing of App
Explore tagged Tumblr posts
Text
Simplify Decentralized Payments with a Unified Cash Collection Application
In a world where financial accountability is non-negotiable, Atcuality provides tools that ensure your field collections are as reliable as your core banking or ERP systems. Designed for enterprises that operate across multiple regions or teams, our cash collection application empowers agents to accept, log, and report payments using just their mobile devices. With support for QR-based transactions, offline syncing, and instant reconciliation, it bridges the gap between field activities and central operations. Managers can monitor performance in real-time, automate reporting, and minimize fraud risks with tamper-proof digital records. Industries ranging from insurance to public sector utilities trust Atcuality to improve revenue assurance and accelerate their collection cycles. With API integrations, role-based access, and custom dashboards, our application becomes the single source of truth for your field finance workflows.
#ai applications#artificial intelligence#augmented and virtual reality market#augmented reality#website development#emailmarketing#information technology#web design#web development#digital marketing#cash collection application#custom software development#custom software services#custom software solutions#custom software company#custom software design#custom application development#custom app development#application development#applications#iot applications#application security#application services#app development#app developers#app developing company#app design#software development#software testing#software company
4 notes
·
View notes
Text
Web Application Security Testing
Web application security testing is the process of evaluating and identifying vulnerabilities, weaknesses, and potential threats in a web application's code, configuration, and deployment.
2 notes
·
View notes
Text
Revolutionize Your Receivables with Atcuality’s Collection Platform
Struggling with outdated manual collection processes? Atcuality’s comprehensive cash collection application provides everything your business needs to streamline payment collection and reconciliation. Our feature-rich platform supports real-time monitoring, customizable workflows, multi-currency support, and advanced security features. Designed to empower field agents and finance managers alike, our application reduces operational overhead while improving transparency and accountability. Seamless integration with ERP systems ensures smooth data flow across your organization. From retail networks to field services and utility providers, businesses trust Atcuality to simplify collections and boost cash flow. Partner with us to modernize your operations, improve customer satisfaction, and drive sustainable growth. Experience digital transformation with Atcuality.
#seo marketing#digital marketing#artificial intelligence#iot applications#seo agency#seo services#azure cloud services#seo company#amazon web services#ai powered application#cash collection application#software engineering#software testing#software company#software services#information technology#software development#technology#software#software consulting#applications#application development#mobile application development#ai applications#application security#application modernization#application process#application services#app design#app developers
1 note
·
View note
Text
Mobile Application Penetration Testing in the UK: Safeguarding Your Mobile Ecosystem

Mobile applications serve as a crucial touchpoint between businesses and customers. With countless users now utilizing sensitive applications in banking, healthcare, ecommerce, and social networking, business mobile apps deal with enormous amount sensitive data. The ever growing usage of mobile devices increases the likelihood of cyber threats making mobile application penetration testing a necessity, especially for businesses in the UK.
This paper will discuss the process of mobile application penetration testing and the techniques used and needed by companies based in the UK. It will also highlight the most vulnerabilities commonly found on mobile applications as well as best practices in mobile application security.
What Is Mobile Application Penetration Testing?
Testing the security of a mobile application involves mimicking real world attacks. Mobile application penetration testing is doing just that. This form of testing aims to reveal security weaknesses in mobile apps, both Android and iOS, which cybercriminals could leverage to gain unauthorized access, data, or disrupt services.
When testing the security of mobile applications, the mobile applications testers employed both manual techniques alongside automated methods to evaluate client-side (UI, storage, code) and server-side APIs, databases, and authentication) components of the mobile application. The process is akin to everything a hacker would do in the active exploitation phase if they were attempting to compromise your application.
Why Is Mobile Application Virus Scanning Important to Businesses in the UK?
1. Increased Mobile Cybersecurity Attacks
Due to the increased use of mobile applications in the UK, hackers are on the lookout for apps that would grant access to sensitive personal and financial information. Reports indicate that mobile malware attacks and insufficiently secured mobile API interfaces are among the leading worries of security professionals.
2. Adherence to Governing Laws in the UK
Businesses within the UK are required to observe laws on data protection like the UK GDPR that offers strong protective measures when it comes to handling and processing personal data. It is important to note that routinely scheduled mobile app penetration testing will be able to make certain that the application is compliant with the laws avoiding sumptuary fines.
3. Safeguarding Brand Loyalty
Penetration testing ensures that potential problems are dealt with beforehand, avoiding needless unflattering publicity as well as loss of treasured brand equity. One mobile application flaw has the potential to put thousands of lives at risk, exposing such vulnerabilities usually leads to public relation disasters, negative press, and damage to brand equity.
Most Common Flaws in Mobile Applications
Following is a list of the most common gaps emerging from mobile app penetration testing:
Insecure Data Retention: The retention of sensitive information such as personal passwords or session tokens in easily accessible forms such as in text files on devices.
Ineffective Authentication Protocols: Other than absence of multi-factor authentication (MFA), poor session control is a contributing factor.
Insecure Communication: The use of encryption that is either absent or weak when encrypting the communication that takes place between the app and the server.
Reverse Engineering Risk: Possibility of attackers reverse engineering the application due to the absence of obfuscation in the code.
Insecure APIs: Exposed backend APIs which can be exploited for unauthorized access to data or functions.
Improper Platform Usage: The use of platform functionalities such as permissions, intents, or inter-process communications in a manner that was not intended.
Recommended Mobile Application Security Practices
As noted during penetration testing, businesses should take steps to fix vulnerabilities with the following suggested practices:
1. Protect All Sensitive Information With Encryption.
Encrypt all stored and transmitted information, data, or resources, including mobile application data, with strong encryption algorithms. Communication between the mobile application and the backend servers should be conducted using SSL or TLS.
2. Employ Strong Security Controls Related to User Authentication.
Implement multi-factor authentication, protective session handling with secure session maintenance, automatic log-out after idle timeouts for user accounts and sessions.
3. Obfuscate Mobile App Code
Weaknesses or secrets embedded in the app may be exploited by reverse engineering it. Attacks of this nature are made difficult through code obfuscation.
4. Secure APIs
Implement controls for access restriction base on proper validation commands and limit the number of permitted input rates to secure APIs from abuse.
5. Conduct Regular Penetration Testing
Penetration testing on mobile applications should be conducted routinely, especially after a significant code change or prior to introducing new features. Engage certified cyber security services to get thorough testing done.
The Best Cyber Security Companies for Mobile App Pen Testing in the UK
Should you wish to acquire Mobile Application penetration testing services within the United Kingdom, these companies come highly recommended:
1. NCC Group
NCC Group, as one of the world's foremost cyber security experts, provides thorough mobile application testing which includes source code review, dynamic analysis, and backend security review.
2. Redscan (now part of Kroll)
Redscan offers specialized penetration testing for both Android and iOS applications, addressing security loopholes and assisting organizations to fortify their mobile applications.
3. Falanx Cyber
Falanx offers tailored mobile security assessments and penetration testing with detailed reporting and strategic remediation guidance.
4. Cyber Smart
Cyber Smart serves SMEs specializing in automated compliance and security, offering assessments of mobile applications from the GDPR and Cyber Essentials compliance perspectives.
Conclusion: Mobile Pen Testing Is No Longer Optional
Mobile applications, when leveraged appropriately within a business, can propel the organization to new heights. However, they do bring with them additional avenues for potential attacks. As the UK continues to embrace mobile adoption, mobile application penetration testing is a fundamental practice that protects both users and businesses from critical breaches.
From thoroughly testing your applications, working with reputable cyber security companies, as well as dealing with weaknesses in a proactive manner, you not only safeguard sensitive information but also protect compliance as well as customer confidence.
What are you waiting for? We can help you defend your mobile applications with trusted penetration testing. Contact us today and we can discuss how to improve your mobile security posture.
#aws penetration testing uk#mobile application penetration testing uk#pen testing for mobile app uk#mobile app pen testing uk#penetration test application uk#Cloud Security Penetration Testing uk
0 notes
Text
Smart Financial Management with Atcuality’s Cash Collection Tools
Businesses need reliable tools to manage their financial operations efficiently. Atcuality offers advanced fintech solutions, including an AI-powered cash collection application that ensures smooth and timely payment collection. This innovative tool helps businesses automate billing, generate instant payment reports, and send notifications to clients, reducing payment delays. With a secure platform that supports multiple payment options, companies can offer a hassle-free experience to customers while maintaining steady cash flow. Whether you’re a startup or an established enterprise, Atcuality’s technology-driven solutions are designed to support your financial goals with ease and security.
#search engine optimisation company#search engine optimisation services#emailmarketing#search engine marketing#digital services#search engine ranking#seo#search engine optimization#digital marketing#seo company#cash collection application#software testing#software company#software engineering#software#software development#developers#applications#opensource#software solutions#software services#software support#software security#software design#software developers#application development#application modernization#application process#app#app development
1 note
·
View note
Text
TCoE Framework: Best Practices for Standardized Testing Processes
A Testing Center of Excellence (TCoE) framework focuses on unifying and optimizing testing processes across an organization. By adopting standardized practices, businesses can improve efficiency, consistency, and quality while reducing costs and redundancies.
Define Clear Objectives and Metrics
Set measurable goals for the TCoE, such as improved defect detection rates or reduced test cycle times. Establish key performance indicators (KPIs) to monitor progress and ensure alignment with business objectives.
Adopt a Robust Testing Framework
Use modular and reusable components to create a testing framework that supports both manual and automated testing. Incorporate practices like data-driven and behavior-driven testing to ensure flexibility and scalability.
Leverage the Right Tools and Technologies
Standardize tools for test automation, performance testing, and test management across teams. Integrate AI-driven tools to enhance predictive analytics and reduce test maintenance.
Focus on Skill Development
Provide continuous training to ensure teams stay updated with the latest testing methodologies and technologies. Encourage certifications and cross-functional learning.
Promote Collaboration and Knowledge Sharing
Foster collaboration between development, QA, and operations teams. Establish a knowledge repository for sharing test scripts, results, and best practices.
By implementing these best practices, organizations can build a high-performing TCoE framework that ensures seamless, standardized, and efficient testing processes.
#web automation testing#ui automation testing#web ui testing#ui testing in software testing#automated website testing#web ui automation#web automation tool#web automation software#automated web ui testing#web api test tool#web app testing#web app automation#web app performance testing#security testing for web application
0 notes
Text
Secure your mobile apps with robust Mobile Application Testing Services to reduce the risk of potential cyberattacks and strengthen their security.
1 note
·
View note
Text
Revolutionize Your Business with Custom Web Applications
Web application development services encompass a wide range of activities aimed at designing, building, and maintaining web-based applications. These applications can perform a variety of functions and provide services to users over the internet. Here are the key aspects of web application development that techcarrot offer:
1. Consultation and Strategy:
Understanding client requirements and business objectives.
Offering strategic guidance and consultation on the technology stack, platform, and features.
2. Custom Web Application Development:
Building web applications tailored to meet specific business needs.
Utilizing programming languages (such as JavaScript, Python, Ruby, PHP, etc.) and frameworks to develop scalable and secure applications.
3. Front-End Development:
Creating the user interface (UI) and user experience (UX) design.
Implementing responsive design for optimal user experience across various devices.
4. Back-End Development:
Developing server-side logic and database management.
Utilizing server-side languages (like Node.js, Django, Flask, Ruby on Rails, etc.) and database systems (such as MySQL, PostgreSQL, MongoDB, etc.).
5. Database Design and Integration:
Designing and implementing the database architecture.
Integrating databases with the application for efficient data storage and retrieval.
6. API Development and Integration:
Creating Application Programming Interfaces (APIs) for communication with other systems.
Integrating third-party APIs or services for added functionality.
7. Testing and Quality Assurance:
Conducting a comprehensive testing process that includes unit testing, integration testing, and user acceptance testing.
Identifying and fixing bugs and issues is necessary to ensure a reliable and secure application.
8. Security Implementation:
Enacting security measures to safeguard against common web vulnerabilities.
Ensuring secure data transmission and storage.
9. Deployment and Hosting:
Deploying the web application in a hosting environment.
Configuring server settings and ensuring the application is live and accessible.
10. Maintenance and Support:
Providing ongoing maintenance and support services.
Addressing issues, applying updates, and ensuring the application remains compatible with changing technologies.
11. Scalability and Performance Optimization:
Optimizing the application for performance and scalability.
Monitoring and addressing performance issues as the user base grows.
12. Upgrades and Enhancements:
Implementing new features or upgrading existing ones to meet evolving business needs.
Keeping the technology stack up-to-date for security and performance reasons.
When seeking web application development services Dubai, Abu Dhabi, and the Middle East, techcarrot would be the ideal partner that aligns with your specific project requirements, budget, and long-term goals.
#oracle partners in dubai#oracle jd edwards#oracle consulting company in dubai#cloud service providers in uae#mobile app development company in abu dhabi#web application development services abu dhabi#mobile app development dubai#mobile app development company in dubai#oracle consulting services in dubai#salesforce implementation company in dubai#web application development company abu dhabi#web application development company dubai#web application development#web application testing#web application security#web application services#web application architecture
0 notes
Text
Web App Development Services in San Francisco

SleekSky stands out because we're good at creating awesome web apps in San Francisco. We take your ideas and turn them into cool digital solutions using our expertise, creativity, and the latest technologies. Our experienced team works closely with you to understand what you need, making everything personalized. From the start to the finish, SleekSky makes sure the whole process is smooth. We create top-notch web apps that shine in San Francisco. Choose SleekSky to make your online presence stand out with our excellent web app development services in San Francisco, where your ideas meet amazing technology!
Choose our software expertise: https://bit.ly/47HDEZZ
#software development#software development company#software development services#softwaredeveloper#software development solutions#software company#app development company#full stack developer#mobile app development#app development#web app development#web application development#web application testing#web application security#web app developers
0 notes
Text
HS Digital Media Crafting Compelling Narratives through Ad Films
The Power of Ad Films

Why Choose HS Digital Media
Showcase your company’s unique selling characteristics. Highlight any awards, recognition, or successful case studies.
The Creative Process
Provide insights into how HS Digital Media approaches ad film creation. Discuss the collaboration between your team and clients. Emphasize the importance of tailoring each project to the client’s brand and goals.
Technological Edge
Detail the cutting-edge technology and equipment used by HS Digital Media. Discuss any innovative techniques or trends in the ad film industry.
The Team Behind the Magic
Introduce key members of your team and their expertise. Share any success stories or challenges overcome during previous projects.
Client Success Stories
Include testimonials from satisfied clients. Highlight specific projects and their impact on the client’s brand.
Industry Trends and Insights
Discuss current trends in ad film production. Share insights into the evolving landscape of digital media.
Challenges and Solutions
Address common challenges in ad film production. Showcase how HS Digital Media overcomes these challenges to deliver exceptional results.
Social Impact Through Ad Films
Discuss any projects that have contributed to social causes. Highlight the potential for ad films to create positive change.
The Future of Ad Films
Share your vision for the future of ad film production. Discuss emerging technologies and their potential impact on the industry.
#Mobile App Development#App Development Services#iOS App Development#Android App Development#Custom Mobile App#Mobile Application Design#Cross-Platform App Development Native App Development Mobile App Developers#Mobile App UI/UX#Mobile App Testing#Enterprise App Development#Mobile App Prototyping#App Maintenance Services#Mobile App Security#Cloud-Based App Development#Mobile App Integration#Wearable App Development#AR/VR App Development#IoT App Development#Mobile App Development Mumbai#Mumbai App Developers#iOS App Development Mumbai#Android App Development Mumbai#Mobile App Design Mumbai#Mumbai Mobile App Agency#Mumbai App Development Services#Custom App Development Mumbai#Mumbai Mobile App Solutions#Native App Development Mumbai#Cross-Platform App Mumbai#Mobile App Testing Mumbai
0 notes
Text
Crafting Future-Ready Digital Experiences with Atcuality
Atcuality stands at the forefront of digital innovation, delivering tailored technology solutions for businesses of all sizes. From startups to enterprises, our clients trust us to build robust software that meets their unique challenges. One of our highly sought-after services is Telegram Bot Creation—perfect for businesses aiming to engage audiences on a platform they already love. We build bots that are secure, intuitive, and scalable, supporting diverse use cases from customer service to lead generation. Beyond bots, we offer full-stack development, AI integration, and cloud solutions. Discover how Atcuality can elevate your digital presence and give your business the competitive edge it deserves.
#artificial intelligence#ai applications#augmented and virtual reality market#website development#web development#digital marketing#information technology#web design#augmented reality#emailmarketing#website#website optimization#web developers#web developing company#website security#softwaredevelopment#website services#website seo#website design#it services#telegram#custom application development#custom app development#custom software design#custom software company#application development#applications#application design#software engineering#software testing
0 notes
Text
Ethical Hacking and Penetration Testing
In today's digital landscape, the need for robust cybersecurity measures has become paramount. With the rise in cyber threats and attacks, organizations and individuals are constantly seeking ways to protect their valuable data and systems. Two methods that have gained significant attention in recent years are ethical hacking and penetration testing. In this article, we will explore what ethical hacking and penetration testing entail, their importance in safeguarding against cyber threats, and how they differ from each other.
Ethical Hacking
Ethical hacking, also known as white-hat hacking, is the practice of intentionally infiltrating computer systems and networks to identify vulnerabilities before malicious hackers can exploit them. Ethical hackers, often referred to as cybersecurity professionals or penetration testers, use their knowledge and skills to legally and ethically assess the security of an organization's infrastructure. Their goal is to proactively identify weaknesses and vulnerabilities, allowing organizations to patch them up before they can be exploited.
One of the key aspects of ethical hacking is the mindset of thinking like a hacker. Ethical hackers adopt the same techniques and methodologies that malicious hackers use, but with the intention of helping organizations strengthen their security. They employ a range of tools and techniques to conduct penetration testing, including vulnerability scanning, network mapping, and social engineering. By simulating real-world attack scenarios, ethical hackers can uncover vulnerabilities that might otherwise go unnoticed.
Ethical hacking plays a crucial role in ensuring the security and integrity of computer systems. It enables organizations to identify and address potential weaknesses in their infrastructure, preventing unauthorized access and data breaches. By proactively seeking out vulnerabilities, ethical hackers help organizations stay one step ahead of cybercriminals.
The Growing Importance of Ethical Hacking
In a world where cyberattacks are becoming increasingly sophisticated, ethical hacking plays a pivotal role in safeguarding sensitive information and critical infrastructure. Businesses, governments, and organizations across the globe recognize the value of proactive cybersecurity measures.
Ethical hackers and penetration testers are in high demand, with career opportunities spanning various industries, including finance, healthcare, and tech. Their skills are crucial for fortifying defenses, ensuring compliance with data protection regulations, and ultimately, preserving trust in the digital world.
The Intricate Art of Penetration Testing
Penetration Testing, often referred to as pen testing, is a subset of ethical hacking. It involves actively simulating cyberattacks to evaluate the security of a system, network, or application. Penetration testers employ a systematic approach, mimicking the tactics of real attackers to identify vulnerabilities and assess the potential impact of an attack.
There are different types of penetration testing, such as network penetration testing, application penetration testing, and social engineering testing. Each type focuses on specific areas of an organization's infrastructure and helps uncover vulnerabilities that may have been overlooked. By conducting regular penetration tests, organizations can ensure that their security measures are effective and up to date.
Conclusion
In the ever-evolving world of cybersecurity, ethical hacking and penetration testing are indispensable tools for organizations and individuals seeking to safeguard their digital assets. Ethical hacking allows organizations to proactively identify vulnerabilities and strengthen their security measures before malicious hackers can exploit them. Penetration testing goes a step further by simulating real-world attacks to assess the effectiveness of existing security measures.
#cyber security#ethicalhacking#penetration testing#hiteshi technologies#mobile app development company#mobile app development services#iphone application development company#android application development company#technology#custom software development
1 note
·
View note
Text
Stiles Emergency Bag
things found in Stiles bag:
A key ring with keys to all the pack houses, as well as to various secure locations in the police station, hospital, etc
A burner phone
A first aid kit
A lighter
His phone with an app linked to the tracking devices he secretly placed on the pack members (except Peter who keeps removing his)
basic make up supplies
A can of fly spray
A collection of the loudest personal alarms he could find (very useful when being chased around an enclosed space by a creature with supernatural hearing)
A mini hoover (the kind advertised for cleaning desks)
Two mini supersoakers, one filled with wolfsbane and mistletoe solution, one filled with holy water (just because you've not met a vampire Derek doesn't mean there aren't any. It's called being prepared!)
A compact mirror (added after the kanima incident)
Throat sweets (for Lydia)
Super glue
A baggie full of sand (demon wolf or not, it's hard to look intimidating when trying to get sand out of your werewolf eyes)
Zip ties
Lock picking gear (a combo of professional tools and improvised ones)
Duct tape (tests on Isaac proved that suitable levels of application could indeed prevent a wolf from being able to claw their way out once their hands were bound. Isaac did not agree to be the test subject)
A mini sewing kit
A jar full of a homemade mixture that absolutely stank (and could therefore effectively disguise a person's scent)
A bag of marshmallows
A wallet with at least one fake ID for each pack member
A lacrosse ball (Derek was 90% sure that was just to make fetch jokes)
Hair ties
A spare t-shirt
A packet of rubber gloves
A dog whistle

#teen wolf#stiles stilinski#Stiles is a feral chaos gremlin#erica reyes#vernon boyd#derek hale#peter hale#isaac lahey#scott mccall#the hale pack
565 notes
·
View notes
Text
CONFIDENTIAL MEMORANDUM
DRC, Black Ops Command, Covert Acquisition Unit
To: Director [REDACTED]
From: Administrator [REDACTED], Covert Acquisition Unit
Date: [REDACTED]
Subject: Surrogate Recruitment via Social Media Application
Executive Summary
This memorandum summarizes the initial pilot testing of "Broodr," a mobile dating application developed by the DRC Covert Acquisition Unit as an identification and capture tool of viable surrogate candidates within the Los Angeles metropolitan region.
The Broodr pilot program aims to:
Test effectiveness in luring suitable surrogate candidates aged 18-25.
Assess the app’s capability to profile and locate high-fertility individuals discretely.
Evaluate the overall success rate of transitioning online interactions into physical capture operations.
Operational Procedure
Broodr was launched covertly through standard digital app distribution channels. It is marketed as a casual social/dating application targeted at young, romantically single men. Four other apps in the market were also disrupted to reduce competition and increase public awareness. The application utilizes advanced profile analytics to identify users displaying surrogate-compatible traits based on fertility indicators such as age, athletic status, height, genetic background, and health metrics.
Once identified, candidates receive targeted messaging from AI bots and doctored profiles using altered photos of athletes and models designed to entice them to designated physical meeting locations. These meeting spots are strategically placed within zones easily secured by DRC rapid response capture teams.
Initial Test Results
Since the pilot launch [REDACTED] weeks ago, Broodr has attracted over [REDACTED] registered users within the target demographic.
[REDACTED]% of identified high-value targets initiated interactions leading to physical meetings.
Capture success rate currently stands at [REDACTED]%, exceeding initial operational goals.
Captured surrogates demonstrate above-average fertility rates, with an average fetal load of 12-16 embryos upon initial insemination.
Key Incident
On [REDACTED], Broodr successfully identified, seduced, and facilitated the capture of a high-profile fitness celebrity at our DRC detainment site in [REDACTED], Beverly Hills.
Mr. [REDACTED], a 23-year-old fitness influencer known for his muscular physique, extensive social following, and endorsements of health products, was identified as a prime surrogacy candidate due to exceptional fertility markers (5'11", 174 lbs pre-pregnancy, optimal athletic conditioning).
Four real profiles and 28 tailored AI-generated profiles initially contacted him, depicting attractive, athletic personas that closely matched his profile's interests. This sophisticated digital interaction rapidly evolved into sexually graphic exchanges, successfully convincing him to attend what he believed to be a home address for a physical engagement.
“Hey, handsome ;) Hott as fuck! A stud like you promising an unforgettable night got me seriously curious. What are you into? I would love to work out all your kinks, physical and sexy!” - Copy of Chat Log
Upon arrival at the designated location, a rapid response team swiftly and discreetly apprehended Mr. [REDACTED]. Upon completion of on-site insemination, secured transport protocols were immediately enacted, moving Mr. [REDACTED] to the nearby Paternity Compound 141, best equipped for his subsequent gestation, birth, and expiration. Mr. [REDACTED] was assigned the surrogate ID S-141-548-P (which will be used henceforth to identify the surrogate).
Post evaluations confirmed highly successful insemination, resulting in an exceptionally high fetal load of sexdecuplets (16 embryos), and in under 33 days, S-141-548-P's weight jumped to 534 lbs (+360 lbs) with an abdominal circumference of 96 inches (+64 inches), rendering the surrogate wholly bedridden and dependent on continuous medical supervision. Despite his extreme size and rapidly declining mobility, regular medical evaluations confirmed that S-141-548-P's health remained within acceptable operational parameters.
"I can barely process what's happened—my body’s unrecognizable. I used to flex these abs for millions online, and now they're buried beneath a mound of babies. I'm so enormous and heavy that breathing feels like a workout! I never thought I'd feel this helpless—or this big." - S-141-548-P, Gestation Day 21
Labor commenced on day 33 of gestation, and over 22 hours, all 16 fetuses were successfully delivered. Upon completion of delivery, vital signs deteriorated rapidly, culminating in S-141-548-P’s expiration approximately [REDACTED] minutes after the last fetus was expelled. Post-mortem assessments indicated complete [REDACTED] shutdown, extensive [REDACTED] to the [REDACTED] and [REDACTED] system.
"I can't stop it! They’re coming! Everything's ripping apart, and every contraction feels like my belly's splitting open. Oh God—I can’t move, I can't breathe, but my body... I'm just so... fat…" - S-141-548-P, Gestation Day 33
Of particular note is that S-141-548-P was well known on social media channels for exemplifying his abdominal muscles, mainly using the moniker “All Core, No Compromise.” The primary cause of expiration was confirmed to be the macroscopic tearing and rupture of all abdominal muscles, a typical result for surrogates subjected to such high fetal loads.
Recommendations
The capture and subsequent pregnancy of such a notable public figure not only significantly boosted internal operational morale but also underscored the strategic efficacy of Broodr as an unprecedented method of securing high-value surrogate candidates. This incident has provided robust proof-of-concept evidence, strongly supporting further investment and nationwide deployment of the Broodr initiative.
Based on the Los Angeles pilot:
Expand Broodr's implementation to additional high-density urban areas (e.g., New York City, [REDACTED], San Francisco).
Increase application analytics capabilities to enhance fertility trait profiling.
Implement additional security protocols to ensure continued operational secrecy.
Conclusion
The pilot deployment of Broodr in the Los Angeles metro area confirms the application's high efficacy as a discreet surrogate recruitment and capture tool. Expansion into additional metropolitan zones is recommended to bolster surrogate conscription efforts further nationwide.
Prepared by: Assistant Director [REDACTED]
DRC, Black Ops Command, Covert Acquisition Unit
----------------
Click Here to return to DRC Report Archives

#mpreg#mpregkink#malepregnancy#mpregbelly#pregnantman#mpregmorph#mpregcaption#mpregstory#mpregbirth#mpregart#mpregnancy#aimpreg#mpregroleplay#malepregnant#latinompreg
40 notes
·
View notes
Text
Innovative Solutions for Seamless Digital Transformation - Atcuality
Atcuality crafts tailor-made digital solutions that help businesses stay ahead in a competitive marketplace. With a team of experienced developers, designers, and digital marketers, we specialize in creating functional websites, high-performing mobile apps, AI-driven platforms, and immersive AR/VR experiences. Our solutions are built with precision and creativity to meet the unique needs of each client. One of our core services is Telegram Bot Creation, designed to automate customer engagement, streamline communication, and deliver instant support through highly interactive bots. These bots not only handle user queries but also execute complex tasks like sending alerts, integrating APIs, and providing real-time updates, making them invaluable for businesses seeking efficiency. Additionally, Atcuality offers digital marketing strategies, SEO optimization, and blockchain development services to ensure holistic digital growth. Choose Atcuality to empower your business with innovative technologies and expert-driven strategies.

#search engine marketing#emailmarketing#search engine optimisation company#search engine optimization#search engine ranking#seo#digital services#search engine optimisation services#digital marketing#seo company#telegram#telegram channel#applications#software#digital transformation#technology#software testing#software company#software engineering#software development#software solutions#software security#software services#software support#app development#app developers#app developing company#cash collection application#application modernization#application development
0 notes
Text





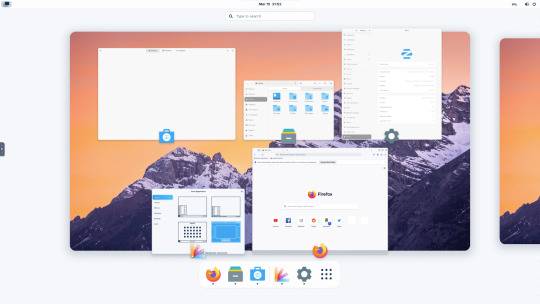

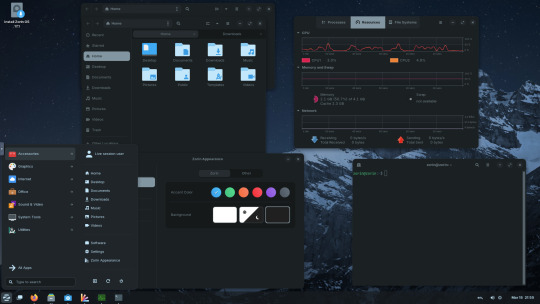


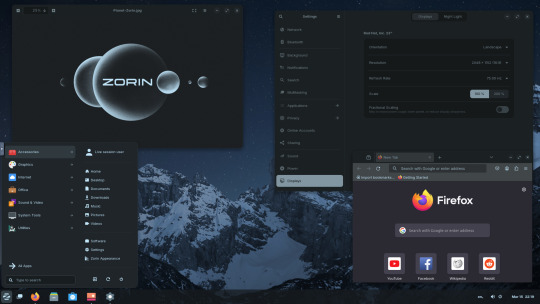
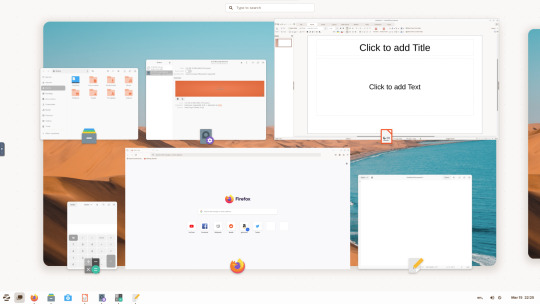
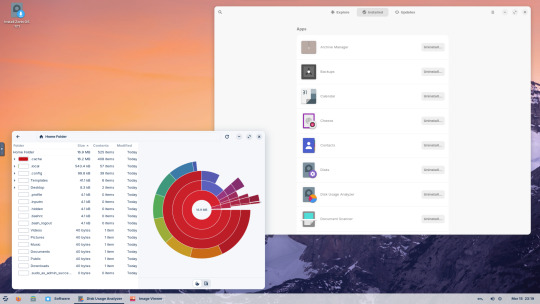
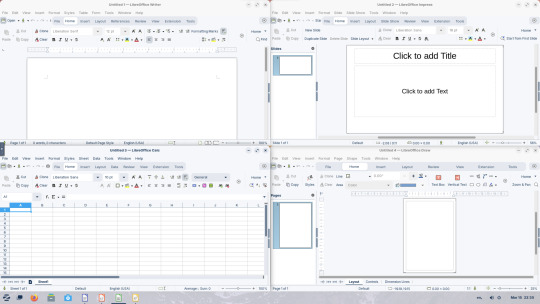
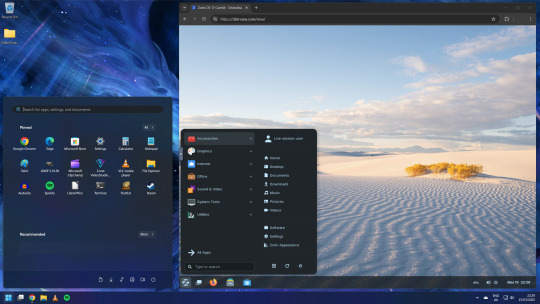
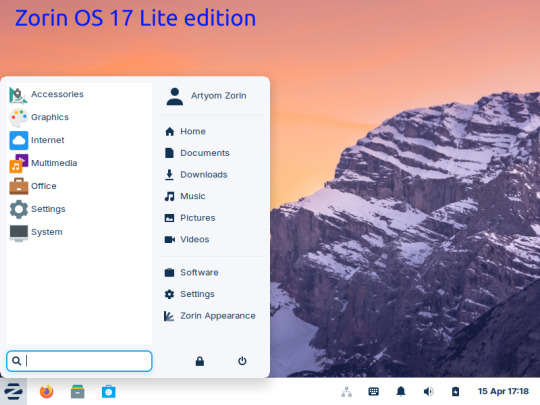
15.03.25
I tried out Zorin OS Linux on Distrosea.
https://distrosea.com/
Zorin OS started its development in 2008 by co-founders Artyom and Kyrill Zorin. The company is based in Dublin, Ireland.
Main site:
https://zorin.com/os/
Wiki link:
https://en.wikipedia.org/wiki/Zorin_OS
Like Linux Mint, it is based on Ubuntu, which in turn is based on Debian and uses the current Ubuntu 24.04.2 LTS base release.
It features the GNOME 3 and XFCE desktop environments and is available in Lite, Education and Core editions.
Due to enhanced performance optimizations in the Core, Pro, and Education editions of Zorin OS, the Lite version is being discontinued.
However the XFCE desktop packages will still be available through the official software repositories:
https://help.zorin.com/docs/getting-started/getting-zorin-os-lite/
I chose version 17 and selected the 'Core' edition.
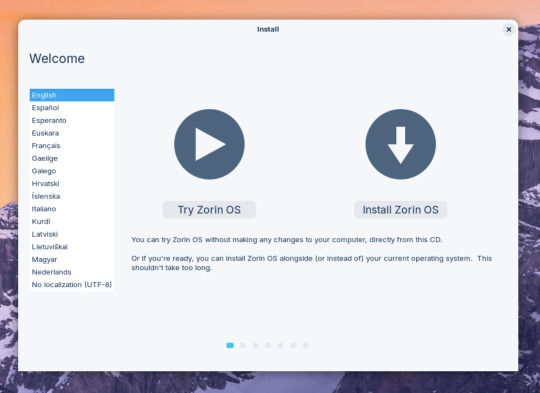
This version (Core64) features the GNOME desktop and a few more apps. I clicked 'Try' when the Linux distro booted up to the install wizard. The distro performs a md5 sum check before boot-up to check the security of the .iso file.
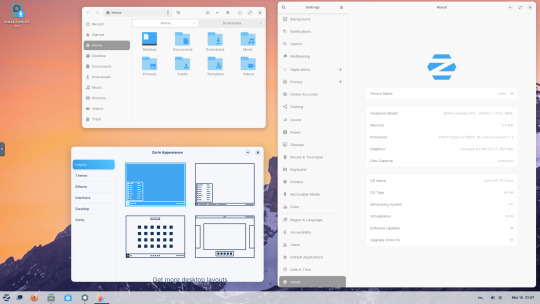
The distro can be easily customised to echo Windows or MAC-OS, as well as being tweaked to the users preferred layout.
Software can be installed through Zorin's Software Store. applications are available to install in APT, dpkg, Snap and flatpak.
Windows software can be ran using Wine, a compatibly layer for running Windows only programs on Linux, MAC OS and BSD systems.
Zorin OS 17 also comes with various menu layouts from a Windows Classic/7 layout, Windows 11 style layout, GNOME menu and full screen menus. Some of the menu layouts are only available in the paid for Pro edition.
For more about the various layouts and a review see:
https://www.zdnet.com/article/zorin-os-demonstrates-exactly-what-a-desktop-operating-system-should-be/
The panel (referred to as a taskbar) is also highly configurable in size and appearance and can be changed to match the desktop layouts.
Various window management set-ups are featured for tiling windows to the sides of the screen.
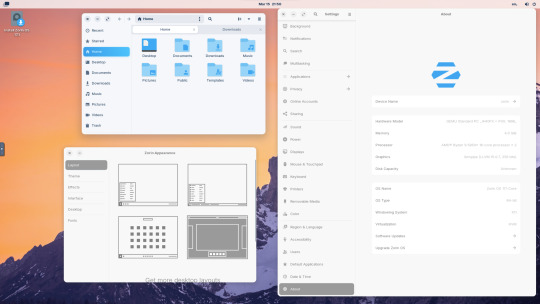
I like the operating system as it is both familiar to me as a Windows user, but also is very configurable, features a polished user interface and is easy to navigate. Also Zorin comes with some very striking desktop backgrounds and colours!
However, I couldn't get the VM to connect to the internet, so I couldn't browse Firefox or try out any additional software.
This is just the way that it has been set-up on Distrosea. For test purposes though, it works very well.
It also feels very speedy, even in a virtual machine over the host internet!
4 notes
·
View notes