#Applocker bypass
Explore tagged Tumblr posts
Text
Secure Your Child's iPhone with the Best App Blocking Apps
In today's digital age, it has become increasingly important for parents to monitor and control their children's smartphone usage. With the widespread availability of various apps and online content, ensuring your child's safety and well-being can be a challenging task. Fortunately, there are several app blocking apps available that can help you manage and secure your child's iPhone. In this article, we will explore the best app blocking apps that provide effective parental control features, allowing you to create a safe digital environment for your child.
Introduction
In today's digital landscape, children have easy access to various apps on their iPhones. While this can be beneficial for educational and entertainment purposes, it also exposes them to potential risks. App blocking apps offer a practical solution by allowing parents to control and limit the apps their children can access, ensuring a safer online experience.
The Importance of App Blocking Apps
App blocking apps play a vital role in safeguarding your child's online activities. By utilizing these apps, you can prevent your child from accessing inappropriate or age-restricted content. Additionally, they enable you to establish healthy screen time limits, reducing the risk of excessive device usage and potential addiction. With app blocking apps, you can create a digital environment that promotes responsible smartphone usage.
Key Features to Look for in App Blocking Apps
When selecting an app blocking app for your child's iPhone, it's essential to consider the following key features:
User-Friendly Interface
Opt for an app blocking app that offers a simple and intuitive interface, allowing you to navigate and configure settings with ease. A user-friendly interface ensures that you can efficiently manage the app and customize restrictions according to your child's needs.
App Whitelisting and Blacklisting
Look for an app blocking app that provides the option to whitelist or blacklist specific applications. This feature allows you to selectively block or allow access to certain apps, ensuring that your child can only use apps that are safe and appropriate.
Time Management
Effective time management features enable you to set screen time limits for different apps or device usage as a whole. This functionality ensures that your child maintains a healthy balance between screen time and other activities, such as homework, physical exercise, and family interactions.
Web Filtering and Content Blocking
An ideal app blocking app should include web filtering capabilities to restrict access to inappropriate websites or content. This feature is crucial in protecting your child from encountering harmful or unsuitable material while browsing the internet.
Top App Blocking Apps for iPhone
Here are some of the best app blocking apps available for iPhone:
AppLock
AppLock offers robust app blocking and time management features, allowing you to lock specific apps and set time restrictions for individual apps or device usage. It also provides a secure and password-protected environment, ensuring that your child cannot bypass the restrictions.
Norton Family
Norton Family is a comprehensive parental control app that includes app blocking functionality. It allows you to monitor your child's app usage, block inappropriate content, and set time limits for different apps and device usage. Additionally, it provides real-time activity reports, giving you insights into your child's digital behavior.
Qustodio
Qustodio offers a wide range of parental control features, including app blocking and monitoring. It allows you to block or limit the usage of specific apps, set screen time limits, and monitor your child's online activity. Qustodio also provides detailed reports and alerts, keeping you informed about your child's smartphone usage.
OurPact
OurPact offers flexible app blocking and screen time management features. With its intuitive interface, you can easily block or grant access to apps, set schedules for app usage, and remotely manage your child's device from your own smartphone. OurPact also includes a location tracking feature, enhancing your child's safety.
Screen Time
Screen Time is a built-in app blocking and screen time management feature available on iPhones. It allows you to set app limits, schedule downtime, and block specific apps or categories altogether. While basic, Screen Time provides essential functionalities for controlling your child's app usage.
How to Choose the Right App Blocking App
When selecting the right app blocking app for your child's iPhone, consider factors such as ease of use, compatibility with your child's device, available features, and pricing. It is also recommended to read reviews and compare different options to make an informed decision.
Tips for Effective Usage of App Blocking Apps
To ensure the effective usage of app blocking apps, consider the following tips:
Communicate openly with your child about the reasons behind using app blocking apps.
Set clear rules and guidelines regarding app usage and screen time limits.
Regularly review and update the blocked and allowed apps based on your child's needs and maturity level.
Educate yourself about the latest apps and digital trends to stay informed and adapt your app blocking settings accordingly.
Read More: best parental control for iphone
Conclusion
In conclusion, securing your child's iPhone with app blocking apps is crucial for their online safety and well-being. By choosing the right app blocking app and implementing appropriate restrictions, you can create a safe digital environment that promotes responsible smartphone usage. Remember to communicate with your child, set clear boundaries, and regularly review and update the app blocking settings based on their needs. With the availability of effective app blocking apps, you can ensure peace of mind while your child explores the digital world.
FAQs
Q: Can I monitor my child's app usage remotely with app blocking apps?
A: Yes, many app blocking apps offer remote monitoring features that allow you to track your child's app usage and receive real-time activity reports.
Q: Can I customize the time restrictions for different apps?
A: Absolutely. App blocking apps provide the flexibility to set individual time restrictions for specific apps, ensuring a tailored approach to your child's smartphone usage.
Q: Are app blocking apps compatible with other devices besides iPhones?
A: Yes, while the focus of this article is on iPhone app blocking apps, many parental control solutions are available for other platforms such as Android and Windows.
Q: Will my child be able to bypass the app blocking restrictions?
A: Good app blocking apps offer secure and password-protected environments to prevent your child from bypassing the restrictions easily.
Q: How often should I review and update the app blocking settings?
A: It is recommended to regularly review and update the app blocking settings based on your child's needs, maturity level, and the evolving digital landscape.
0 notes
Text
Sunday Roundup: 28th of May 2017
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "echo"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1ZZ5TM5SVRD2GHZ0KFG2"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "78d0ce00bb3ae0fc191ee006bde05194";
Sunday Round up for the week ending the 28th of May 2017:
Articles:
Interview with the Security Sleuth: https://www.teramind.co/blog/interview-security-sleuth
Critical Vulnerability in Samba from 3.5.0 onwards: https://isc.sans.edu/forums/diary/Critical+Vulnerability+in+Samba+from+350+onwards/22452/
Applocker Bypass via Registry Key Manipulation: https://www.contextis.com//resources/blog/applocker-bypass-registry-key-manipulation/
Beats and Bytes - Striking the Right Chord in Digital Forensics: https://digital-forensics.sans.org/blog/2017/05/22/beats-and-bytes-striking-the-right-chord-in-digital-forensics
The Man Who Made the Mistake of Trying to Help Wikileaks: https://motherboard.vice.com/en_us/article/jason-katz-wikileaks
Cameradar - An RTSP Surveillance Camera Access Multitool: http://www.kitploit.com/2017/05/cameradar-rtsp-surveillance-camera.html?utm_source=dlvr.it&utm_medium=facebook&m=1
Your Exploit is Mine: Automatic Shellcode Transplant for Remote Exploits: https://www.ieee-security.org/TC/SP2017/papers/579.pdf
Using Cloud Deployment to Jump-Start Application Security: https://www.sans.org/reading-room/whitepapers/analyst/cloud-deployment-jump-start-application-security-37805
Verify If A Photo Was Really Taken By A Suspected Camera - Camera Ballistics 2.0: https://www.forensicfocus.com/News/article/sid=2895/
Twitter:
"Classifying Illegal Activities On Tor Network Based On Web Textual Contents" #forensics #feedly https://t.co/EqrT3eVPIK
— The Security Sleuth (@Security_Sleuth) May 21, 2017
In 2017 only losers pay for VPN's #itrtg https://t.co/9mlZjwzDDS
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"“Yahoobleed” flaw leaked private e-mail attachments and credentials" #informationsecurity #feedly https://t.co/KkWYTKoN69
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"Spring Parade for Refreshed Android Marcher" #informationsecurity #feedly https://t.co/IQahxgESKo
— The Security Sleuth (@Security_Sleuth) May 22, 2017
"Breaking the iris scanner locking Samsung’s Galaxy S8 is laughably easy" #informationsecurity #feedly https://t.co/WgwWjiFNKL
— The Security Sleuth (@Security_Sleuth) May 23, 2017
"Beware! Subtitle Files Can Hack Your Computer While You're Enjoying Movies" #infosec #feedly https://t.co/AnLifPZF8O
— The Security Sleuth (@Security_Sleuth) May 23, 2017
"Subtitle Hack Leaves 200 Million Vulnerable to Remote Code Execution" #informationsecurity #feedly https://t.co/rw0aZuNABU
— The Security Sleuth (@Security_Sleuth) May 24, 2017
"Keybase Extension Brings End-to-End Encrypted Chat To Twitter, Reddit, GitHub" #informationsecurity #feedly https://t.co/dKHmOSdwFs
— The Security Sleuth (@Security_Sleuth) May 25, 2017
Read last weeks round up here
If you found some other interesting stuff this week feel free to leave a link to it in the comments section.
#Interview with me#Security Sleuth#Critical Samba Vulnerability#Applocker bypass#registry key manipulation#Beats and bytes#Digital Forensics#SANS#Man who tried to help wikileaks#Cameradar#RTSP surveillance Camera#Automatic shellcode transplant remote exploits#Cloud deployment#jump start application security#Camera Ballistics#whodunnit?#Classifying illegal activities#Tor#web textual contents#original post#In 2017 only losers pay for VPN's#Yahoobleed#leaked emails and credentials#Spring parade#refresher android marcher#Breaking the iris scanner#Galaxy S8#easy peasy#Subtiles hacked my PC#subtitles can hack your PC
1 note
·
View note
Text
youtube
1 note
·
View note
Text
ShellReset RAT Spread Through Macro-Based Documents Using AppLocker Bypass
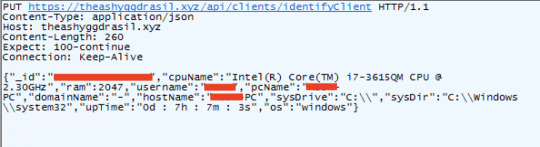
Source: https://www.zscaler.com/blogs/research/shellreset-rat-spread-through-macro-based-documents-using-applocker-bypass
2 notes
·
View notes
Text
Flexihub full

#FLEXIHUB FULL HOW TO#
#FLEXIHUB FULL INSTALL#
#FLEXIHUB FULL FOR ANDROID#
#FLEXIHUB FULL ANDROID#
Pros & Cons of All in One FRP Unlock toolĭespite being an extremely useful tool, even FRP unlocker all-in-one has its own share of pros and cons. Once the FRP lock is removed, you'll be able to unlock your smartphone without having to enter Google account credentials at all.
#FLEXIHUB FULL INSTALL#
Simply follow the on-screen instructions to install the right recovery package on your device and remove the FRP lock. Step 3: Now, check the radio button next to "Remove FRP" and click "Start". Step 2: Let the tool automatically detect your device or use the drop-down menu to select the device name and model.
#FLEXIHUB FULL ANDROID#
Step 1: Launch FRP unlocker all-in-one on your PC and connect your Android device using a USB cable. Once you have downloaded and installed the FRP unlocker tool on your PC, simply follow the below-mentioned instructions to bypass FRP verification on your smartphone. In a nutshell, FRP Unlocker all-in-one will be your one-stop solution to unlock an FRP-protected device.
#FLEXIHUB FULL HOW TO#
Moreover, you can use the software to remove Google account verification from different Android devices, irrespective of their brand, and model.įRP Unlocker All-In-One Tool: How to Unlock FRP Lock It doesn't matter which Windows version you're using, All-in-One FRP Unlocker is compatible with all PCs running on a Windows operating system. Simply click the Download button to get it. Below we've offered you the link to download the FRP unlock all in one tool. To bypass Google lock from your FRP-enabled device, you have to download the software on your PC/laptop. you can rely on this frp unlock all in one tool to bypass FRP lock easily. No matter what Android phones you are using, such as Samsung, Huawei, Xiaomi, Oppo, Vivo, Sony, Honor, etc. This tool runs on both Android and Windows operating systems and allows to enter download mode, fix software issue, remove FRP Lock and do a factory Reset. When it comes to the best FRP all in one tool, the first thing that comes to most Android users' minds is the All in One FRP Tools by Mobile Tech Channel. Part 1: FRP Unlocker All In One Tool freeload
#FLEXIHUB FULL FOR ANDROID#
Part 2: All In One FRP Unlock Better Alternative - 4uKey for Android.Part 1: FRP Unlocker All In One Tool freeload.Furthermore, we introduce a Samsung FRP one click tool to help Samsung users to bypass Google account verification after factory reset. If you're not familiar with such kind of FRP all in one tools, in this guide, we're going to share useful insight into the FRP unlock all-in-one and how you can use it to bypass FRP verification on your Android smartphone. As a professional tool that's designed to bypass FRP verification on almost every Android device, the FRP unlocker all-in-one tool has become the preferred choice of many Android users to unlock their Android device by bypassing the Google account verification. How to Bypass Factory Reset Protection AndroidĪn all-in-one FRP tool is one of the best solutions for someone who doesn't remember the Google account credentials and gets stuck on the FRP verification window.Albviral FRP Android 8 to Bypass FRP Lock.How to Use LG Google Account Bypass Tool.IObit Applock Face Lock & Fingerprint Lock Review.Does Screen Lock Bypass Pro Really Work.Fix Samsung Face Recognition Not Working.Fix Pixel 4/4XL Face Unlock Not Working.iMyFone LockWiper Review: How to Remove Android Screen Lock.How to Unlock Android Tablet without Password.Best 5 Methods to Remove Forgot Android PIN.How to Unlock LG Phone If Forgot Pattern.Get into Someone's Phone Without Knowing the Password.How to Unlock Android Phone Pattern Lock.How to Access Locked Android Phone from PC.Bypass Android Lock Screen without Google Account.Remove Forgotten Password from Android Phone.

0 notes
Text
AppLocker Bypass https://github.com/gtworek/PSBits/tree/master/AppLockerBypass
AppLocker Bypass https://github.com/gtworek/PSBits/tree/master/AppLockerBypass

PSBits/AppLockerBypass at master · gtworek/PSBits - GitHub Simple (relatively) things allowing you to dig a bit deeper than usual. - PSBits/AppLockerBypass at master · gtworek/PSBits
0 notes
Text
App Lock password
For some people, having a lock on their phone is not enough. They are also looking for an app to protect their personal information and social media accounts from being accessed by others. This blog post will provide you with the top 5 apps that can help you do this!
The last thing most of us want is our private messages or photos being shared with everyone. That's why we have locks on our phones and other devices to prevent unauthorized access to them. Some people, however, are still nervous about what might happen if they were ever in an accident or lost their device and someone else found it before they could remotely wipe it clean (or worse). To guard against these types of situations without locking your screen every time you walk away from your phone.
How do I unlock AppLock If settings are locked?
Are you getting locked out of your AppLock? We've all been there. But it's not the end of the world. All you need to do is get a little help from someone else who has access to their settings and can unlock them for you. If that person doesn't want to help, then start asking around! You're bound to find someone who will be willing to let you use their iPhone or iPad so that you can fix your own problem with App Lock settings being locked. Related post to click here.
1. Tap the lock icon in the upper right-hand corner of the screen
2. Enter your password to unlock AppLock settings
3. If you forgot your password, tap "Forgot Password" and enter your email address
4. Follow instructions on how to reset your password for future logins
5) After entering a new password, exit out of AppLock settings and try unlocking it again from home screen or app drawer
How can I open App Lock without password?
One of the most common problems people face when they lose their phone or someone steals it is all the apps that require a password before you can use them. One of those apps is App Lock, which only allows you to open it with your password. If you have forgotten your password and don't know how to get in, this blog post will show you how! Read on for more information.
The answer is not as easy as you might think. If you don't know the passcode, then there is no way to bypass the security without having your phone unlocked first. There are some ways to do this, but they require physical access to the device. If someone has stolen your phone and locked it with a passcode, they won't be able to unlock it either unless they happen to know what the code is already.
How can I open App Lock without my password?
It's a great way to keep nosy people from looking at your private information, but what do you do if you need to open it without the password? Luckily there are some ways that can help!
For starters, try going into settings and changing the automatic lock setting. This will set how long before the phone locks itself after inactivity. If this doesn't work, try rebooting or resetting your device altogether. Finally, if all else fails contact customer service for assistance with opening up App Lock!
What other tips would recommend for opening up App Lock without my password? Share them below in the comments section!
How do I disable App Lock?
Well, Read on. It's actually very easy! The first step is to tap "Settings" and then scroll down until you see “App lock” in the list of settings that are displayed. You'll need your phone password or fingerprint for this part! Once you unlock the setting, just tap "disable." If you're not sure what this does, it stops anyone from locking apps behind a passcode or fingerprint security system. That means people can access anything they want without having to enter any passwords! So if someone has their hands on your phone and tries unlocking an app with a code, they won't be able to do so because there is no code anymore.
How can I change my app lock password?
People who are looking for a way to change their app lock password should read this blog post. I will show you how to do it on both Android and iPhone devices. If you have an iPhone, go to Settings > Face ID & Passcode or Touch ID & Passcode. It's the same settings menu as your regular pass code but with the "Face" or "Touch" part in front of it. For Android users, head over to Settings > Lock Screen Preferences and scroll down until you see Password/PIN/Patterns followed by App Locks. You'll need to find the app that needs its password changed before clicking on Change Password and following the prompts from there! There are also ways where you can use either fingerprint scanning or facial.
How do I find out what my password is?
So, you've forgotten your password and now you can't log back in to your account? Don't worry! This post will show you how to find out what it is.
The key thing is that if this is the first time forgetting your password, then you should be able to remember it by doing a little bit of detective work.
First, see if there's any passwords saved on the computer or phone and login with one of those. If not, try using words from old messages or emails as they may include some keywords which could help unlock the mystery of the forgotten password. The last idea I have for finding out what your password might be: go through all past periods where you used a different email address and see.
Conclusion:
App Lock is a great way to keep your app data secure and private. With our help, you can stay safe from hackers who want their hands on all of your personal information by giving them nothing but an unbreakable password for the rest of time! If this sounds like something that will work well with you, just download the free version now. We promise it's worth every penny.
0 notes
Text
Best App Lockers in iPhone to Secure Apps
Secure Apps In some cases, fundamental security options such as adding a passcode or enabling Touch ID is not only adequate for your iPhone. Fortunately, there is little chance of security flaws in Apple as its software is up-to-date. Apple creates some built-in security and privacy protection into its devices. Rather than waiting for hackers and attackers to come for you, you should protect your iOS devices when you ponder that it isn’t enough to lock the screen by adding a password. Your protection can be breached if your password is known by someone else.

Here are some mobile security applications that will bolster your security:
AppLocker
This feature was introduced in iOS 6, and it has generated effective results as well. It offers a solution for individuals who desire to secure more than their pre-installed phone apps. Even you can employ the Touch ID as a passcode replacement. When you don’t realize secure enough by only inclusion of passcode to protect your apps, then the fingerprints can be handy as an ideal substitute. You should keep in mind that this app is reliable for Mobile Substrate.
2. BioLockdown
Apple’s iPhone 5s was the first which introduced Touch ID in 2013. It permits you to unlock your iOS devices with the help of the fingerprint sensor. Additionally, it can lock applications, settings, and switches on your iOS devices with the help of Touch ID. Similar to AppLocker, you can employ your fingerprints to keep safe any apps on your iPhone. Without the use of fingerprint, the apps will be remaining locked. No one can remove it or intrude with the “app locker” itself.
3. iProtect
It consists of similar tools as earlier mentioned two app lockers. It offers an important feature regarding locking applications like securing and keeping safe your apps, contact lists, images, and more.
4. BioProtect
It provides a multitude of features inclusive of locking your apps. You can check anyone from switching off your iOS device or altering the setting panes without your consent. With the more incidence of Password bypass techniques and hacking attack, it is indispensable to keep safe and lock your iOS applications in order to keep all the private and critical data secure and safe. We expect that these aforesaid app lockers will assist you to protect your passcode and your apps ultimately.
Graccey Leio is a self-professed security expert; she has been making the people aware of the security threats. Her passion is to write about Cybersecurity, cryptography, malware, social engineering, internet and new media. She writes for Norton security products at norton.com/setup.
Source:https://us-notron.com/best-app-lockers-in-iphone-to-secure-apps/
0 notes
Link
Today i will show you some of the great android hidden tricks which is realated to how to open password app lock, how to take a long screenshot, how to remove background from image, how to check whatsapp read reciepts is turn or not and how to copy text on photo.
#how to bypass app lock#how to take a screenshot#how to copy text on photo#how to remove photo background#how to hack password applock#how to take a long screenshot#how to check read reciepts off
0 notes
Text
تحميل تطبيق Security-Master-Premium-5.1.4.apk لتنظيف و حماية هاتفك الاندرويد
Security Master - Antivirus, VPN, AppLock, Booster v5.1.4 Premium
تمت ترقية CM Security الأصلي إلى Security Master وإعادة تعريف نطاق أمان الهاتف: لا يحمي فقط هاتف Android الخاص بك ولكن أيضًا خصوصيتك.
أكثر من مجرد برنامج مكا��حة فيروسات بسيط للأندرويد ، تم تصميم Security Master مع ميزة أكثر قوة ، بما في ذلك:
★ التشخيص الذكي
- برنامج مكافحة الفيروسات غير المرغوب فيه
لبرنامج مكافحة الفيروسات غير المرغوب فيه Phone Cooler ★ SafeConnect VPN
- وكيل VPN آمن سريع
★ أمان Wi-Fi - فحص شبكات Wi-Fi من أجل التهديدات
★ إنذار ضد السرقة - حماية هاتفك من السرقة عن طريق إصدار صوت ناقوس الخطر
★ أمان الرسائل - إخفاء إشعارات المعاينة
★ قفل - قفل التطبيقات وحمايتها بكلمة مرور
★ ★ الدخيل صورة شخصية - التقاط الدخيل باستخدام هاتفك
الميزات الرئيسية:
التشخيص الذكي
Antivirus - Security السيطرة على مضاد الفيروسات المجاني لنظام Android للحفاظ على هاتفك والخصوصية في مأمن من الفيروسات والبرامج الضارة مع # 1 مكافحة الفيروسات المحرك.
Junk Clean - مسح وإزالة الملفات غير المرغوب فيها بذكاء بما في ذلك ذاكرة التخزين المؤقت للنظام والتطبيقات بنقرة واحدة فقط.
Phone Boost Battery Saver و CPU Cooler - قم بإزالة تطبيقات الخلفية التي تستهلك ارتفاعًا في الذاكرة وتستنزف البطارية.
تقوم ميزة SafeConnect VPN
Bypass بجدران الحماية والوصول بحرية إلى المواقع الحساسة بمشاهدة مقاطع الفيديو غير المتوفرة في بلدك بشكل مجهول دون أن يتم تعقبك.
إخفاء عنوان IP وتطبيق الموقع الظاهري حماية الأنشطة الخاصة بك على الإنترنت لمنع تسرب المعلومات المصرفية عبر الإنترنت خاصة الرسائل وسجل التصفح.
أمن Wi-Fi
يقوم Security Master باكتشاف وتحديد سرعة شبكة اختبار شبكة Wi-Fi الاحتيالية وحماية أمان الهاتف عبر الإنترنت.
إنذار
مضاد للسرقة يقوم جهاز إنذار مضاد للسرقة بحماية هاتفك من السرقة من خلال إصدار إنذار عند قيام شخص ما بتحريك هاتفك.
أمان
الرسائل Message Security يخفي معاينة الإشعارات في الوقت المناسب لحماية خصوصيتك. يجمع كل إشعارات الدردشة في واحد ويجعلها أسهل في القراءة والإدارة.
يقوم AppLock
Lock Bluetooth & Wi-Fi بتبديل صور التطبيقات أو أي بيانات خاصة برمز PIN أو بصمة.
مع Security Master برنامج مكافحة فيروسات مجاني لنظام Android يحمي هاتفك من الفيروسات والبرامج الضارة. حافظ على خصوصيتك آمنة مع Applock SafeConnect VPN Wi-Fi Security والمزيد من الميزات.
Security Master - مكافحة الفيروسات ، VPN ، AppLock ، ما الجديد في v5.1.4 (Premium
- مميزات PREMIUM
الائتمانية غير المقفلة Apkmos
نحن نعمل دائمًا على تحسين أداء Master Security وتجربة المستخدم.
بسببك ، نحن نتحسن.
- حماية ليس فقط هاتف Android الخاص بك ولكن أيضًا خصوصيتك عبر الإنترنت
- محرك مسح ومضاد فيروسات أكثر قوة
- تحسين سرعة المنتج وأدائه
- إصلاح بعض الأخطاء المعروفة
التحميل من هنا
source https://www.tetbekat.com/2019/11/security-master-premium-514apk.html
0 notes
Text
Original Post from Rapid7 Author: Matthew Kienow
On the correct list
AppLocker and Software Restriction Policies control the applications and files that users are able to run on Windows Operating Systems. These two protections have been available to the blue team for years. AppLocker is supported on Windows 7 and above, and Software Restriction Policies is supported on Windows XP and above. Encountering either during an engagement could slow you down; however, look no further than the evasion modules for assistance. Nick Tyrer contributed two new AppLocker and Software Restriction Policies evasion modules that leverage different bypass vectors discovered by Casey Smith (@subTee). First, the evasion/windows/applocker_evasion_presentationhost evasion module uses the Microsoft signed binary PresentationHost.exe in order to execute the payload. Second, the evasion/windows/applocker_evasion_regasm_regsvcs evasion module uses the Microsoft signed binaries RegAsm.exe or RegSvcs.exe in order to execute the payload. Both evasions should work as long as .NET version 3.5 or above is installed and the binaries are not explicitly blocked.
New modules (2)
Applocker Evasion – Windows Presentation Foundation Host by Casey Smith and Nick Tyrer
Applocker Evasion – Microsoft .NET Assembly Registration Utility by Casey Smith and Nick Tyrer
Bugs fixed
PR #12343 by egypt fixes a payload generation issue when formatting payload buffers as powershell byte arrays. These changes also add comments describing how the payload was configured.
PR #12239 by Clément Notin fixes the search path separator to use the client’s path separator instead of a fixed slash character.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.47…5.0.49
Full diff 5.0.47…5.0.49
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Matthew Kienow Metasploit Wrap-Up Original Post from Rapid7 Author: Matthew Kienow On the correct list AppLocker and Software Restriction Policies control the applications and files that users are able to run on Windows Operating Systems.
0 notes
Text
0 notes
Text
Finished Reading: AppLocker Bypass – MSXSL
https://ift.tt/2ttovKc via Read it Later (February 24, 2018 at 07:55PM )
0 notes
Photo

10 best gallery vault apps for Android! Sometimes you just want to keep prying eyes away from your stuff. We understand. There are a variety of ways to do it too. Applocks provide a quick, if somewhat ineffective, means of privacy. There are also special vault apps that store files and hide files from other apps. Of course, there are also OEM solutions as well. Whatever you choose to go with should keep out snoopy roommates or kids. However, a tech savvy individual can bypass these without too much effort. It’s not the end of the world, but more of a heads up that these aren’t infinitely secure. These only provide short term privacy benefits. In any case, here are the best gallery vault apps for Android! More privacy apps here! 10 best applocks and privacy lock apps for Android The applock is perhaps the most rudimentary of security apps. The way it works is that it will lock up your other apps from prying eyes. That way you don't have to worry about someone … 10 best privacy apps for Android Privacy is a big deal these days. Facebook is all over the place with Congress and the whole Cambridge Analytica thing. People are more aware of their privacy (or lack thereof) than ever before. So … AppLock by DoMobile Lab Price: Free / Varies DOWNLOAD ON GOOGLE PLAY AppLock by DoMobile Lab is one of the most popular applocks for Android. It basically turns any app into a vault app. It has a variety of security measures. For instance, you can hide it from the app drawer. Additionally, it locks down your gallery, cloud storage apps, file explorer app, or any other app that might access your files. This should work well for snooping individuals or kids. There are a few ways to pay for this one. You can use the app for free with ads, though, if you prefer. It's pretty decent for what it does. DOWNLOAD ON GOOGLE PLAY AppLock - Fingerprint Unlock Price: Free DOWNLOAD ON GOOGLE PLAY Cheetah Mobile has a lot of really terrible apps. This isn't one of them. This applock works like most applocks do. It lets you lock up apps tight so that others can't see them. It features fingerprint support and you can lock things like Bluetooth settings as well. There are also themes if you're into that. This is actually a decent, free, and very basic applock. It is very unlike Cheetah Mobile, actually. It works best with older versions of Android as users have reported some issues with it on Android Oreo. It's completely free with no ads or in-app purchases as far as we could tell. DOWNLOAD ON GOOGLE PLAY Gallery Vault Price: Free / Up to $14.99 DOWNLOAD ON GOOGLE PLAY Gallery Vault is one of the most popular vault apps for Android. It's a standalone app that hides files. You import files and the app hides them from all of your other apps. This makes it good for hiding whatever photo and video content you want. The app also features a privacy browser, limited fingerprint scanner support (apparently only Samsung devices), break-in alerts, and file encryption. Of course, if something happens, the app may delete all of your photos, but that's the risk you run sometimes. We're not sure it's worth the $14.99 price tag, but the free version has most of the features anyway. DOWNLOAD ON GOOGLE PLAY Hide Something Price: Free / $1.99 DOWNLOAD ON GOOGLE PLAY Hide Something is one of the cleanest gallery vault apps we've seen. It also works well enough as a vault app. You can share files directly from third party apps to this in order to hide them. Additionally, it features Google Drive support for hidden backups. That's kind of neat, actually. Some other features include GIF support, a fake vault mode, fingerprint support, and more. It also doesn't show up in the recent apps menu. It's cheap, it looks good, and it has the more common features. That works for us! DOWNLOAD ON GOOGLE PLAY LockMyPix Price: Free / Up to $2.99 DOWNLOAD ON GOOGLE PLAY LockMyPix is another decent gallery vault app. It has a lot of desirable features, including complete offline support, a fake login, AES encryption, fingerprint scanner support, and SD card support. You can even open a fake vault if you want to. That is potentially useful if someone is forcing you to open the app for them. We found the occasional report of backups not functioning all that well. Otherwise, this app actually seems rock solid. It's also relatively inexpensive. DOWNLOAD ON GOOGLE PLAY Maybe try these too! 5 best private messenger apps for Android! People care more about their privacy now than ever before. Facebook is dropping the ball with privacy, companies engage in data collection almost constantly, and it's difficult to know who to trust. New products come … 15 best antivirus apps and best anti-malware apps for Android! Antivirus Android apps remain one of the most popular types of applications on Android. Generally, you don't need an antivirus app if you play it safe, only download apps from the Play Store, and keep … Norton App Lock Price: Free DOWNLOAD ON GOOGLE PLAY Norton App Lock is another surprisingly good applock from a typically not-so-great developer. This one has all of the common features. It also includes a few different passcode options, support for multiple apps, and it takes photos of people trying to break the applock. Other app locks have more features. However, this one does the basics and it's surprisingly light for a Norton app. It's also entirely free with no in-app purchases or ads. Of course, it has the same caveats as other applocks. People can get around it with enough time. DOWNLOAD ON GOOGLE PLAY Calculator Gallery Vault by Kohinoor Apps Price: Free / $2.99 DOWNLOAD ON GOOGLE PLAY Calculator Gallery Vault is one of a few apps in this very weird genre of vault apps. It disguises itself as a calculator app. You use the number pad to enter a password to access the vault. It's a unique and fun idea and there are a surprising number of apps that pretend to be a calculator. In terms of features, this one includes a fake password to show fake content if needed, a hidden incognito browser, and a few others. It's also one of the few that supports things other than photos and videos such as music, documents, contacts, and other files. It's not perfect, but it usually gets the job done. DOWNLOAD ON GOOGLE PLAY SpSoft AppLock Price: Free / Up to $4.99 DOWNLOAD ON GOOGLE PLAY SpSoft AppLock is another popular and dependable applock. It has all of the usual features, including a function to record intruders, fingerprint support, a fake lock, support for 31 languages, and more. This one also includes support for different passwords for each app it locks and it has remote lock functionality as well. That gives it an extra step above most other applocks. We found the occasional report of a bug, but most people seem to like this one a lot. It's also relatively inexpensive. DOWNLOAD ON GOOGLE PLAY OEM specific locking features Price: Free DOWNLOAD ON GOOGLE PLAY OEMs add a lot of extra features to their devices over stock Android. Occasionally, that includes an app lock or a privacy vault of some sort. Samsung's Secure Folder feature (in the security and lock screen settings) is an excellent example. These apps have an advantage over third party apps because they are system-level. They can't be uninstalled, they're built right into the OEM version of Android, and that all makes it much harder to crack than an uninstallable app. If a lock screen isn't enough, we definitely recommend looking at OEM specific locking features before going with a third party app. Trust us, it's better. DOWNLOAD ON GOOGLE PLAY Or just use a really good lock screen Price: Free DOWNLOAD ON GOOGLE PLAY Here's the thing, folks. If people are in your phone, your security can only be so good. We really only recommend applocks and vault apps to people with kids because thieves can get around them with enough time. A good lock screen with a good pattern/PIN/fingerprint lock will do more to protect your device than any app on this list. If you're worried about extra protection in case of theft, we actually recommend Find My Phone apps that can remotely wipe your device like Google's option. Set up a good lock screen and we have a list of Find My Phone apps just below! DOWNLOAD ON GOOGLE PLAY Thank you for reading! 5 best find my phone apps and other find my phone methods too! Losing your smartphone is one of the most frightening experiences in the modern age. You have your contact information, your personal information, your personal pictures, and possibly even financial data on there. It's a treasure … 10 best security apps for Android that aren’t antivirus apps When you Google Search the term security apps, you get a ton of antivirus and anti-malware app listings. Unfortunately, that's a very narrow view of what's out there. There are tons of apps that can … If we missed any great gallery vault apps for Android, tell us about them in the comments! You can also click here to check out our latest Android app and game lists! , via Android Authority http://bit.ly/2HAXzxI
0 notes
Link
0 notes
Photo

Several Pentesting Tools and Techniques Used by Information Security Experts
Technology is pulsing all around you, and in the short amount of time that you are hosted in this network that you must try to understand its inner workings. Fortunately or unfortunately, most network and system administrators are persons of habit. All you have to do is listen for long enough, and more often than not it will yield some of those juicy findings, information security experts say.
Regardless of any discussion beforehand, a penetration test has a competitive feel from both sides. Consulting pentesters want their flag, and administrators want their clean bill of health to show that they are resilient to cyber-attack; something akin to a game of flag football. The difference here is that in flag football, both teams are familiar with the tools used to play the game.
It goes without saying that a pentester’s job is to simulate a legitimate threat to effectively determine your organization’s risk, but how can remediation happen without at least some familiarity? Sun Tzu once said, “If you know neither the enemy nor yourself, you will succumb in every battle.”
In order to truly secure our networks, any administrator with cybersecurity duties will need to not only understand what they themselves have, but also step into the shoes of the opposite side.
This article’s intention is to focus on the ‘why’ and not completely the ‘how’. There are countless videos and tutorials out there to explain how to use the tools, and much more information than can be laid out in one blog post. Additionally, I acknowledge that other testers out there may have an alternate opinion on these tools, and which are the most useful. This list is not conclusive. With that being said, let’s get into the list.
Responder
This tool, in the information security expert opinion, makes the absolute top of the list. When an auditor comes in and talks about “least functionality”, this is what comes immediately to mind. If you are a pentester, Responder is likely the first tool you will start running as soon as you get your Linux distro-of-choice connected to the network and kick off the internal penetration test. The tool functions by listening for and poisoning responses from the following protocols:
Link-Local Multicast Name Resolution (LLMNR)
NetBIOS Name Service (NBT-NS)
Web Proxy Auto-Discovery (WPAD)
There is more to Responder, but I will only focus on these three protocols for this article.
NBT-NS is a remnant of the past; a protocol which has been left enabled by Microsoft for legacy/compatibility reasons to allow applications which relied on NetBIOS to operate over TCP/IP networks. LLMNR is a protocol designed similarly to DNS, and relies on multicast and peer-to-peer communications for name resolution. It came from the Vista era, and we all know nothing good came from that time-frame. You probably don’t even use either of these. Attackers know this, and use it to their advantage.
WPAD on the other hand serves a very real and noticeable purpose on the network. Most enterprise networks use a proxy auto-config (PAC) file to control how hosts get out to the Internet, and WPAD makes that relatively easy. The machines broadcast out into the network looking for a WPAD file, and receive the PAC which is given. This is where the poisoning happens.
The information security professionals are aware that most protocols which rely on any form of broadcasting and multicasting are ripe for exploitation.
PowerShell Empire
Before, pentesters typically relied on Command and Control (C2) infrastructure where the agent first had to reside on-disk, which naturally would get uploaded to Virus Total upon public release and be included in the next morning’s antivirus definitions. The time spent evading detection was a seemingly never-ending cat-and-mouse game.
It was as if the collective unconscious of pentesters everywhere came to the realization that the most powerful tool at their disposal was already present on most modern workstations around the world. A framework had to be built, and the Empire team made it so.
The focus on pentesting frameworks and attack tools has undoubtedly shifted towards PowerShell for exploitation and post-exploitation.
It means that some of the security controls you have put in place may be easily bypassed. File-less agents (including malware) can be deployed by PowerShell and exist in memory without ever touching your hard disk or by connecting a USB. A write-up mentioned at the end of this post elaborates much further into this topic. Existing in memory makes antivirus whose core function is scanning disk significantly less effective.
Fortunately, information security researchers say, that the best mitigation here is something you may already have access to , Microsoft’s Applocker. Granted, white listing can take some time to stand up properly and likely requires executive sign-off, but it is the direction endpoint security is heading. This is a good opportunity to get ahead of the curve.
When it comes to mitigation; the execution policy restrictions in PowerShell are trivial to bypass.
Hashcat with Wordlists
This combo right here is an absolute staple. Cracking hashes and recovering passwords is pretty straightforward of a topic at a high level.
Hashcat is a GPU-focused powerhouse of a hash cracker which supports a huge variety of formats, typically used in conjunction with hashes captured by Responder. In addition to Hashcat, a USB hard drive with several gigs of wordlists is a must. On every pentest that the information security analysts have been on, time had to be allocated appropriately to maximize results, and provide the most value to the client.
Sysadmins, think about your baseline policies and configurations. Typically it is best practice to align with an industry standard, such as the infamous DISA STIG, as closely as possible. Baselines such as DISA STIG support numerous operating systems and software, and contain some key configurations to help you prevent against offline password cracking and replay attacks. This includes enforcing NIST recommended password policies, non-default authentication enhancements, and much more. DISA even does the courtesy of providing you with pre-built Group Policy templates that can be imported and custom-tailored to your organization’s needs, which cuts out much of the work of importing the settings.
Web Penetration Testing Tools
It is important to note that a web penetration testing tool is not the same as a vulnerability scanner.
Web-focused tools absolutely have scanning capabilities to them, and focus on the application layer of a website versus the service or protocol level. Granted, vulnerability scanners (Nessus, Nexpose, Retina, etc) do have web application scanning capabilities, though I have observed that it is best to keep the two separate.
Many organizations nowadays build in-house web apps, intranet sites, and reporting systems in the form of web applications. Typically that since the site is internal it does not need to be run through the security code review process, and gets published out for all personnel to see and use.
The surface area of most websites leaves a lot of room for play to find something especially compromising. Some of the major issues are:
Stored Cross-site Scripting (XSS).
SQL Injection.
Authentication bypass.
Directory traversal abuse.
Unrestricted file upload.
If you administer an organization that builds or maintains any internal web applications, think about whether or not that code is being reviewed frequently. Code reuse becomes an issue where source code is imported from unknown origins, and any security flaws or potentially malicious functions come with it. Furthermore, the “Always Be Shipping” methodology which has overtaken software development as of late puts all of the emphasis on getting functional code despite the fact that flaws may exist.
Acquaint yourself with OWASP, whose entire focus is on secure application development. Get familiar with the development team’s Software Development Lifecycle (SDLC) and see if security testing is a part of it. OWASP has some tips to help you make recommendations.
Understand the two methodologies for testing applications, including:
Static Application Security Testing (SAST). The application’s source code is available for analysis.
Dynamic Application Security Testing (DAST). Analyzes the application while in an operational state.
Additionally you will want to take the time to consider your web applications as separate from typical vulnerability scans. Tools (open and closed source) exist out there, including Burp Suite Pro, OWASP Zed Attack Proxy (ZAP), Acunetix, or Trustwave, with scanning functionality that will crawl and simulate attacks against your web applications. Scan your web apps at least quarterly.
Arpspoof and Wireshark
Arpspoof is a tool that allows you to insert yourself between a target and its gateway, and Wireshark allows you to capture packets from an interface for analysis. You redirect the traffic from an arbitrary target, such as an employee’s workstation during a pentest, and snoop on it.
Likely the first theoretical attack presented to those in cybersecurity, the infamous Man-in-the-Middle (MitM) attack is still effective on modern networks, information security researchers said. Considering most of the world still leans on IPv4 for internal networking, and the way that the Address Resolution Protocol (ARP) has been designed, a traditional MitM attack is still quite relevant.
According to information security researcher, many falsely assume that because communications occur inside their own networks, they are safe from being snooped on by an adversary and therefore do not have to take the performance hit of encrypting all communications in their own subnets. Granted, your network is an enclave of sorts from the wild west of the Internet, and an attacker would first have to get into your network to stand between communications.
Now, let’s assume that a workstation is compromised by an attacker in another country using a RAT equipped with tools that allow a MitM to take place. Alternately, consider the insider threat.
The information security experts said that the best tactics of defense are: encrypt your communications. Never assume communications inside your network are safe just because there is a gateway device separating you from the Internet.
Keep your VLAN segments carefully tailored, and protect your network from unauthenticated devices. Implementing a Network Access Control (NAC) system is something you may want to add to your security roadmap in the near future or implementing 802.1X on your network may be a good idea. Shut down those unused ports, and think about sticky MACs if you are on a budget.
0 notes