#Automated Library Management System
Explore tagged Tumblr posts
Text
How can libraries ensure the security of their data and protect patron privacy when using a library management system?
In today's digital age, libraries rely heavily on technology to manage their collections, provide access to resources, and serve their patrons. However, with the use of technology comes the risk of data breaches and privacy violations. As libraries increasingly adopt library management systems, it is important to consider how these systems can be secured to protect patron privacy and ensure the integrity of library data.
At Metaguard, we understand the importance of data security and privacy in the library setting. Our team of experts works with libraries to implement security measures and provide training and support to ensure that library management systems are secure and compliant with privacy regulations.
One of the first steps libraries can take to ensure data security and privacy is to implement access controls. Access controls limit who has access to sensitive data and ensure that only authorized personnel can view and modify data. Libraries can also implement multi-factor authentication to further enhance security and prevent unauthorized access.
Another important step is to ensure that all data is encrypted when it is transmitted or stored. Encryption ensures that data is protected from hackers and other unauthorized users. Libraries should also regularly update their software and systems to ensure that they are protected from known security vulnerabilities.
In addition to securing the library management system, libraries must also protect patron privacy. This includes implementing policies and procedures for handling and storing patron data, as well as obtaining consent before collecting any personal information. Libraries should also provide clear and transparent privacy policies to patrons and ensure that they are informed about how their data is being used and protected.
At Metaguard, we work with libraries to implement privacy and security best practices, including regular audits and assessments to identify and address potential vulnerabilities. We also provide training and support to library staff to ensure that they have the knowledge and skills to maintain a secure and privacy-compliant library management system.
In conclusion, library management systems are an essential tool for modern libraries, but they also come with security and privacy risks. By implementing access controls, encryption, and other security measures, libraries can protect their data and ensure the integrity of their systems. At Metaguard, we are committed to helping libraries achieve these goals and providing the necessary support and training to ensure that data security and privacy remain a top priority.
0 notes
Text
oh my god i don't speak to my dad anymore cuz hes nutty but i know what he does for a living
and musk is currently pulling a "the software govs use is 50 years old which means there can be no advances"
and that's..... that's what my dad does for a living, he gets paid 500-1k an hour to make software that specifically communicates with old legacy software cause he's a 90s dev who knows the old languages still and it's more efficient to hire a freak who knows how to make something to bridge between the old and new programs than to fully trash the old system
like there's literally consultants that get hired for that specific purpose and as a software guy musk KNOWS this
#personal#im losing a LOT of money and decent work connections cause its less stressful than dealing with the crazy man#who literally called my professors at their personal art studios =_=#but ummm???? um??? hes like a low level linkedin influencer lmfao ._.#for software and THIS specific subject matter#the thing ive been getting raises on at work is making scripts to communicate between adobe software with the spreadsheets our#PLM system at work spits out....to automate a bunch of artwork thru libraries.........????#the way my boss gets me to not leave is by giving me /coolmathgames.com/ as a treat basically#and more money for being able to solve /coolmathgames.com/#i work in corporate and one of our order management systems specifically gets routed thru a windows vista virtual machine#cause they dont feel the need to fix....cuz if its not broke#just make the new things that bridge between the two systems?????#instead of having to transfer over decades of a database it makes 0 sense#idk man im rlly frustrated online cuz one of my dads patents is for a legacy speech to text software#(and the other is for a logistics/shipment thing)#like he wasnt the lead on either project but the speech to text specifically is irritating cuz theres#things ppl call 'AI' and im like....thats a buzzword this is litcherally 90s/00s tech and ive been in the office it was made lol
1 note
·
View note
Text

Level Up Your Library with a Modern Library Management System
Organise books, streamline workflows, and empower users—all in one go! Discover an innovative approach to library organisation and patron satisfaction with our advanced library management system. Partner with us to unlock the full potential of your library!
0 notes
Text
How I ditched streaming services and learned to love Linux: A step-by-step guide to building your very own personal media streaming server (V2.0: REVISED AND EXPANDED EDITION)
This is a revised, corrected and expanded version of my tutorial on setting up a personal media server that previously appeared on my old blog (donjuan-auxenfers). I expect that that post is still making the rounds (hopefully with my addendum on modifying group share permissions in Ubuntu to circumvent 0x8007003B "Unexpected Network Error" messages in Windows 10/11 when transferring files) but I have no way of checking. Anyway this new revised version of the tutorial corrects one or two small errors I discovered when rereading what I wrote, adds links to all products mentioned and is just more polished generally. I also expanded it a bit, pointing more adventurous users toward programs such as Sonarr/Radarr/Lidarr and Overseerr which can be used for automating user requests and media collection.
So then, what is this tutorial? This is a tutorial on how to build and set up your own personal media server using Ubuntu as an operating system and Plex (or Jellyfin) to not only manage your media, but to also stream that media to your devices both at home and abroad anywhere in the world where you have an internet connection. Its intent is to show you how building a personal media server and stuffing it full of films, TV, and music that you acquired through indiscriminate and voracious media piracy various legal methods will free you to completely ditch paid streaming services. No more will you have to pay for Disney+, Netflix, HBOMAX, Hulu, Amazon Prime, Peacock, CBS All Access, Paramount+, Crave or any other streaming service that is not named Criterion Channel. Instead whenever you want to watch your favourite films and television shows, you’ll have your own personal service that only features things that you want to see, with files that you have control over. And for music fans out there, both Jellyfin and Plex support music streaming, meaning you can even ditch music streaming services. Goodbye Spotify, Youtube Music, Tidal and Apple Music, welcome back unreasonably large MP3 (or FLAC) collections.
On the hardware front, I’m going to offer a few options catered towards different budgets and media library sizes. The cost of getting a media server up and running using this guide will cost you anywhere from $450 CAD/$325 USD at the low end to $1500 CAD/$1100 USD at the high end (it could go higher). My server was priced closer to the higher figure, but I went and got a lot more storage than most people need. If that seems like a little much, consider for a moment, do you have a roommate, a close friend, or a family member who would be willing to chip in a few bucks towards your little project provided they get access? Well that's how I funded my server. It might also be worth thinking about the cost over time, i.e. how much you spend yearly on subscriptions vs. a one time cost of setting up a server. Additionally there's just the joy of being able to scream "fuck you" at all those show cancelling, library deleting, hedge fund vampire CEOs who run the studios through denying them your money. Drive a stake through David Zaslav's heart.
On the software side I will walk you step-by-step through installing Ubuntu as your server's operating system, configuring your storage as a RAIDz array with ZFS, sharing your zpool to Windows with Samba, running a remote connection between your server and your Windows PC, and then a little about started with Plex/Jellyfin. Every terminal command you will need to input will be provided, and I even share a custom #bash script that will make used vs. available drive space on your server display correctly in Windows.
If you have a different preferred flavour of Linux (Arch, Manjaro, Redhat, Fedora, Mint, OpenSUSE, CentOS, Slackware etc. et. al.) and are aching to tell me off for being basic and using Ubuntu, this tutorial is not for you. The sort of person with a preferred Linux distro is the sort of person who can do this sort of thing in their sleep. Also I don't care. This tutorial is intended for the average home computer user. This is also why we’re not using a more exotic home server solution like running everything through Docker Containers and managing it through a dashboard like Homarr or Heimdall. While such solutions are fantastic and can be very easy to maintain once you have it all set up, wrapping your brain around Docker is a whole thing in and of itself. If you do follow this tutorial and had fun putting everything together, then I would encourage you to return in a year’s time, do your research and set up everything with Docker Containers.
Lastly, this is a tutorial aimed at Windows users. Although I was a daily user of OS X for many years (roughly 2008-2023) and I've dabbled quite a bit with various Linux distributions (mostly Ubuntu and Manjaro), my primary OS these days is Windows 11. Many things in this tutorial will still be applicable to Mac users, but others (e.g. setting up shares) you will have to look up for yourself. I doubt it would be difficult to do so.
Nothing in this tutorial will require feats of computing expertise. All you will need is a basic computer literacy (i.e. an understanding of what a filesystem and directory are, and a degree of comfort in the settings menu) and a willingness to learn a thing or two. While this guide may look overwhelming at first glance, it is only because I want to be as thorough as possible. I want you to understand exactly what it is you're doing, I don't want you to just blindly follow steps. If you half-way know what you’re doing, you will be much better prepared if you ever need to troubleshoot.
Honestly, once you have all the hardware ready it shouldn't take more than an afternoon or two to get everything up and running.
(This tutorial is just shy of seven thousand words long so the rest is under the cut.)
Step One: Choosing Your Hardware
Linux is a light weight operating system, depending on the distribution there's close to no bloat. There are recent distributions available at this very moment that will run perfectly fine on a fourteen year old i3 with 4GB of RAM. Moreover, running Plex or Jellyfin isn’t resource intensive in 90% of use cases. All this is to say, we don’t require an expensive or powerful computer. This means that there are several options available: 1) use an old computer you already have sitting around but aren't using 2) buy a used workstation from eBay, or what I believe to be the best option, 3) order an N100 Mini-PC from AliExpress or Amazon.
Note: If you already have an old PC sitting around that you’ve decided to use, fantastic, move on to the next step.
When weighing your options, keep a few things in mind: the number of people you expect to be streaming simultaneously at any one time, the resolution and bitrate of your media library (4k video takes a lot more processing power than 1080p) and most importantly, how many of those clients are going to be transcoding at any one time. Transcoding is what happens when the playback device does not natively support direct playback of the source file. This can happen for a number of reasons, such as the playback device's native resolution being lower than the file's internal resolution, or because the source file was encoded in a video codec unsupported by the playback device.
Ideally we want any transcoding to be performed by hardware. This means we should be looking for a computer with an Intel processor with Quick Sync. Quick Sync is a dedicated core on the CPU die designed specifically for video encoding and decoding. This specialized hardware makes for highly efficient transcoding both in terms of processing overhead and power draw. Without these Quick Sync cores, transcoding must be brute forced through software. This takes up much more of a CPU’s processing power and requires much more energy. But not all Quick Sync cores are created equal and you need to keep this in mind if you've decided either to use an old computer or to shop for a used workstation on eBay
Any Intel processor from second generation Core (Sandy Bridge circa 2011) onward has Quick Sync cores. It's not until 6th gen (Skylake), however, that the cores support the H.265 HEVC codec. Intel’s 10th gen (Comet Lake) processors introduce support for 10bit HEVC and HDR tone mapping. And the recent 12th gen (Alder Lake) processors brought with them hardware AV1 decoding. As an example, while an 8th gen (Kaby Lake) i5-8500 will be able to hardware transcode a H.265 encoded file, it will fall back to software transcoding if given a 10bit H.265 file. If you’ve decided to use that old PC or to look on eBay for an old Dell Optiplex keep this in mind.
Note 1: The price of old workstations varies wildly and fluctuates frequently. If you get lucky and go shopping shortly after a workplace has liquidated a large number of their workstations you can find deals for as low as $100 on a barebones system, but generally an i5-8500 workstation with 16gb RAM will cost you somewhere in the area of $260 CAD/$200 USD.
Note 2: The AMD equivalent to Quick Sync is called Video Core Next, and while it's fine, it's not as efficient and not as mature a technology. It was only introduced with the first generation Ryzen CPUs and it only got decent with their newest CPUs, we want something cheap.
Alternatively you could forgo having to keep track of what generation of CPU is equipped with Quick Sync cores that feature support for which codecs, and just buy an N100 mini-PC. For around the same price or less of a used workstation you can pick up a mini-PC with an Intel N100 processor. The N100 is a four-core processor based on the 12th gen Alder Lake architecture and comes equipped with the latest revision of the Quick Sync cores. These little processors offer astounding hardware transcoding capabilities for their size and power draw. Otherwise they perform equivalent to an i5-6500, which isn't a terrible CPU. A friend of mine uses an N100 machine as a dedicated retro emulation gaming system and it does everything up to 6th generation consoles just fine. The N100 is also a remarkably efficient chip, it sips power. In fact, the difference between running one of these and an old workstation could work out to hundreds of dollars a year in energy bills depending on where you live.
You can find these Mini-PCs all over Amazon or for a little cheaper on AliExpress. They range in price from $170 CAD/$125 USD for a no name N100 with 8GB RAM to $280 CAD/$200 USD for a Beelink S12 Pro with 16GB RAM. The brand doesn't really matter, they're all coming from the same three factories in Shenzen, go for whichever one fits your budget or has features you want. 8GB RAM should be enough, Linux is lightweight and Plex only calls for 2GB RAM. 16GB RAM might result in a slightly snappier experience, especially with ZFS. A 256GB SSD is more than enough for what we need as a boot drive, but going for a bigger drive might allow you to get away with things like creating preview thumbnails for Plex, but it’s up to you and your budget.
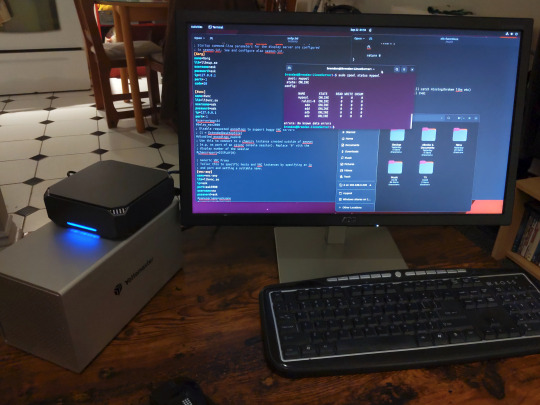
The Mini-PC I wound up buying was a Firebat AK2 Plus with 8GB RAM and a 256GB SSD. It looks like this:

Note: Be forewarned that if you decide to order a Mini-PC from AliExpress, note the type of power adapter it ships with. The mini-PC I bought came with an EU power adapter and I had to supply my own North American power supply. Thankfully this is a minor issue as barrel plug 30W/12V/2.5A power adapters are easy to find and can be had for $10.
Step Two: Choosing Your Storage
Storage is the most important part of our build. It is also the most expensive. Thankfully it’s also the most easily upgrade-able down the line.
For people with a smaller media collection (4TB to 8TB), a more limited budget, or who will only ever have two simultaneous streams running, I would say that the most economical course of action would be to buy a USB 3.0 8TB external HDD. Something like this one from Western Digital or this one from Seagate. One of these external drives will cost you in the area of $200 CAD/$140 USD. Down the line you could add a second external drive or replace it with a multi-drive RAIDz set up such as detailed below.
If a single external drive the path for you, move on to step three.
For people with larger media libraries (12TB+), who prefer media in 4k, or care who about data redundancy, the answer is a RAID array featuring multiple HDDs in an enclosure.
Note: If you are using an old PC or used workstatiom as your server and have the room for at least three 3.5" drives, and as many open SATA ports on your mother board you won't need an enclosure, just install the drives into the case. If your old computer is a laptop or doesn’t have room for more internal drives, then I would suggest an enclosure.
The minimum number of drives needed to run a RAIDz array is three, and seeing as RAIDz is what we will be using, you should be looking for an enclosure with three to five bays. I think that four disks makes for a good compromise for a home server. Regardless of whether you go for a three, four, or five bay enclosure, do be aware that in a RAIDz array the space equivalent of one of the drives will be dedicated to parity at a ratio expressed by the equation 1 − 1/n i.e. in a four bay enclosure equipped with four 12TB drives, if we configured our drives in a RAIDz1 array we would be left with a total of 36TB of usable space (48TB raw size). The reason for why we might sacrifice storage space in such a manner will be explained in the next section.
A four bay enclosure will cost somewhere in the area of $200 CDN/$140 USD. You don't need anything fancy, we don't need anything with hardware RAID controls (RAIDz is done entirely in software) or even USB-C. An enclosure with USB 3.0 will perform perfectly fine. Don’t worry too much about USB speed bottlenecks. A mechanical HDD will be limited by the speed of its mechanism long before before it will be limited by the speed of a USB connection. I've seen decent looking enclosures from TerraMaster, Yottamaster, Mediasonic and Sabrent.
When it comes to selecting the drives, as of this writing, the best value (dollar per gigabyte) are those in the range of 12TB to 20TB. I settled on 12TB drives myself. If 12TB to 20TB drives are out of your budget, go with what you can afford, or look into refurbished drives. I'm not sold on the idea of refurbished drives but many people swear by them.
When shopping for harddrives, search for drives designed specifically for NAS use. Drives designed for NAS use typically have better vibration dampening and are designed to be active 24/7. They will also often make use of CMR (conventional magnetic recording) as opposed to SMR (shingled magnetic recording). This nets them a sizable read/write performance bump over typical desktop drives. Seagate Ironwolf and Toshiba NAS are both well regarded brands when it comes to NAS drives. I would avoid Western Digital Red drives at this time. WD Reds were a go to recommendation up until earlier this year when it was revealed that they feature firmware that will throw up false SMART warnings telling you to replace the drive at the three year mark quite often when there is nothing at all wrong with that drive. It will likely even be good for another six, seven, or more years.

Step Three: Installing Linux
For this step you will need a USB thumbdrive of at least 6GB in capacity, an .ISO of Ubuntu, and a way to make that thumbdrive bootable media.
First download a copy of Ubuntu desktop (for best performance we could download the Server release, but for new Linux users I would recommend against the server release. The server release is strictly command line interface only, and having a GUI is very helpful for most people. Not many people are wholly comfortable doing everything through the command line, I'm certainly not one of them, and I grew up with DOS 6.0. 22.04.3 Jammy Jellyfish is the current Long Term Service release, this is the one to get.
Download the .ISO and then download and install balenaEtcher on your Windows PC. BalenaEtcher is an easy to use program for creating bootable media, you simply insert your thumbdrive, select the .ISO you just downloaded, and it will create a bootable installation media for you.
Once you've made a bootable media and you've got your Mini-PC (or you old PC/used workstation) in front of you, hook it directly into your router with an ethernet cable, and then plug in the HDD enclosure, a monitor, a mouse and a keyboard. Now turn that sucker on and hit whatever key gets you into the BIOS (typically ESC, DEL or F2). If you’re using a Mini-PC check to make sure that the P1 and P2 power limits are set correctly, my N100's P1 limit was set at 10W, a full 20W under the chip's power limit. Also make sure that the RAM is running at the advertised speed. My Mini-PC’s RAM was set at 2333Mhz out of the box when it should have been 3200Mhz. Once you’ve done that, key over to the boot order and place the USB drive first in the boot order. Then save the BIOS settings and restart.
After you restart you’ll be greeted by Ubuntu's installation screen. Installing Ubuntu is really straight forward, select the "minimal" installation option, as we won't need anything on this computer except for a browser (Ubuntu comes preinstalled with Firefox) and Plex Media Server/Jellyfin Media Server. Also remember to delete and reformat that Windows partition! We don't need it.
Step Four: Installing ZFS and Setting Up the RAIDz Array
Note: If you opted for just a single external HDD skip this step and move onto setting up a Samba share.
Once Ubuntu is installed it's time to configure our storage by installing ZFS to build our RAIDz array. ZFS is a "next-gen" file system that is both massively flexible and massively complex. It's capable of snapshot backup, self healing error correction, ZFS pools can be configured with drives operating in a supplemental manner alongside the storage vdev (e.g. fast cache, dedicated secondary intent log, hot swap spares etc.). It's also a file system very amenable to fine tuning. Block and sector size are adjustable to use case and you're afforded the option of different methods of inline compression. If you'd like a very detailed overview and explanation of its various features and tips on tuning a ZFS array check out these articles from Ars Technica. For now we're going to ignore all these features and keep it simple, we're going to pull our drives together into a single vdev running in RAIDz which will be the entirety of our zpool, no fancy cache drive or SLOG.
Open up the terminal and type the following commands:
sudo apt update
then
sudo apt install zfsutils-linux
This will install the ZFS utility. Verify that it's installed with the following command:
zfs --version
Now, it's time to check that the HDDs we have in the enclosure are healthy, running, and recognized. We also want to find out their device IDs and take note of them:
sudo fdisk -1
Note: You might be wondering why some of these commands require "sudo" in front of them while others don't. "Sudo" is short for "super user do”. When and where "sudo" is used has to do with the way permissions are set up in Linux. Only the "root" user has the access level to perform certain tasks in Linux. As a matter of security and safety regular user accounts are kept separate from the "root" user. It's not advised (or even possible) to boot into Linux as "root" with most modern distributions. Instead by using "sudo" our regular user account is temporarily given the power to do otherwise forbidden things. Don't worry about it too much at this stage, but if you want to know more check out this introduction.
If everything is working you should get a list of the various drives detected along with their device IDs which will look like this: /dev/sdc. You can also check the device IDs of the drives by opening the disk utility app. Jot these IDs down as we'll need them for our next step, creating our RAIDz array.
RAIDz is similar to RAID-5 in that instead of striping your data over multiple disks, exchanging redundancy for speed and available space (RAID-0), or mirroring your data writing by two copies of every piece (RAID-1), it instead writes parity blocks across the disks in addition to striping, this provides a balance of speed, redundancy and available space. If a single drive fails, the parity blocks on the working drives can be used to reconstruct the entire array as soon as a replacement drive is added.
Additionally, RAIDz improves over some of the common RAID-5 flaws. It's more resilient and capable of self healing, as it is capable of automatically checking for errors against a checksum. It's more forgiving in this way, and it's likely that you'll be able to detect when a drive is dying well before it fails. A RAIDz array can survive the loss of any one drive.
Note: While RAIDz is indeed resilient, if a second drive fails during the rebuild, you're fucked. Always keep backups of things you can't afford to lose. This tutorial, however, is not about proper data safety.
To create the pool, use the following command:
sudo zpool create "zpoolnamehere" raidz "device IDs of drives we're putting in the pool"
For example, let's creatively name our zpool "mypool". This poil will consist of four drives which have the device IDs: sdb, sdc, sdd, and sde. The resulting command will look like this:
sudo zpool create mypool raidz /dev/sdb /dev/sdc /dev/sdd /dev/sde
If as an example you bought five HDDs and decided you wanted more redundancy dedicating two drive to this purpose, we would modify the command to "raidz2" and the command would look something like the following:
sudo zpool create mypool raidz2 /dev/sdb /dev/sdc /dev/sdd /dev/sde /dev/sdf
An array configured like this is known as RAIDz2 and is able to survive two disk failures.
Once the zpool has been created, we can check its status with the command:
zpool status
Or more concisely with:
zpool list
The nice thing about ZFS as a file system is that a pool is ready to go immediately after creation. If we were to set up a traditional RAID-5 array using mbam, we'd have to sit through a potentially hours long process of reformatting and partitioning the drives. Instead we're ready to go right out the gates.
The zpool should be automatically mounted to the filesystem after creation, check on that with the following:
df -hT | grep zfs
Note: If your computer ever loses power suddenly, say in event of a power outage, you may have to re-import your pool. In most cases, ZFS will automatically import and mount your pool, but if it doesn’t and you can't see your array, simply open the terminal and type sudo zpool import -a.
By default a zpool is mounted at /"zpoolname". The pool should be under our ownership but let's make sure with the following command:
sudo chown -R "yourlinuxusername" /"zpoolname"
Note: Changing file and folder ownership with "chown" and file and folder permissions with "chmod" are essential commands for much of the admin work in Linux, but we won't be dealing with them extensively in this guide. If you'd like a deeper tutorial and explanation you can check out these two guides: chown and chmod.
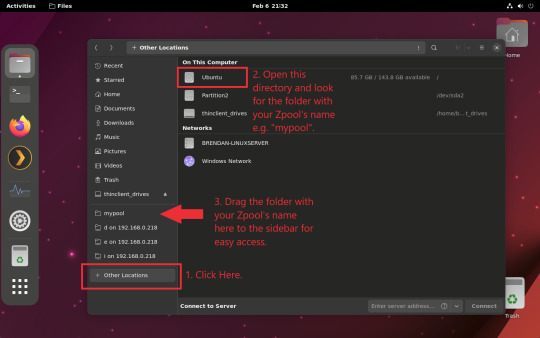
You can access the zpool file system through the GUI by opening the file manager (the Ubuntu default file manager is called Nautilus) and clicking on "Other Locations" on the sidebar, then entering the Ubuntu file system and looking for a folder with your pool's name. Bookmark the folder on the sidebar for easy access.
Your storage pool is now ready to go. Assuming that we already have some files on our Windows PC we want to copy to over, we're going to need to install and configure Samba to make the pool accessible in Windows.
Step Five: Setting Up Samba/Sharing
Samba is what's going to let us share the zpool with Windows and allow us to write to it from our Windows machine. First let's install Samba with the following commands:
sudo apt-get update
then
sudo apt-get install samba
Next create a password for Samba.
sudo smbpswd -a "yourlinuxusername"
It will then prompt you to create a password. Just reuse your Ubuntu user password for simplicity's sake.
Note: if you're using just a single external drive replace the zpool location in the following commands with wherever it is your external drive is mounted, for more information see this guide on mounting an external drive in Ubuntu.
After you've created a password we're going to create a shareable folder in our pool with this command
mkdir /"zpoolname"/"foldername"
Now we're going to open the smb.conf file and make that folder shareable. Enter the following command.
sudo nano /etc/samba/smb.conf
This will open the .conf file in nano, the terminal text editor program. Now at the end of smb.conf add the following entry:
["foldername"]
path = /"zpoolname"/"foldername"
available = yes
valid users = "yourlinuxusername"
read only = no
writable = yes
browseable = yes
guest ok = no
Ensure that there are no line breaks between the lines and that there's a space on both sides of the equals sign. Our next step is to allow Samba traffic through the firewall:
sudo ufw allow samba
Finally restart the Samba service:
sudo systemctl restart smbd
At this point we'll be able to access to the pool, browse its contents, and read and write to it from Windows. But there's one more thing left to do, Windows doesn't natively support the ZFS file systems and will read the used/available/total space in the pool incorrectly. Windows will read available space as total drive space, and all used space as null. This leads to Windows only displaying a dwindling amount of "available" space as the drives are filled. We can fix this! Functionally this doesn't actually matter, we can still write and read to and from the disk, it just makes it difficult to tell at a glance the proportion of used/available space, so this is an optional step but one I recommend (this step is also unnecessary if you're just using a single external drive). What we're going to do is write a little shell script in #bash. Open nano with the terminal with the command:
nano
Now insert the following code:
#!/bin/bash CUR_PATH=`pwd` ZFS_CHECK_OUTPUT=$(zfs get type $CUR_PATH 2>&1 > /dev/null) > /dev/null if [[ $ZFS_CHECK_OUTPUT == *not\ a\ ZFS* ]] then IS_ZFS=false else IS_ZFS=true fi if [[ $IS_ZFS = false ]] then df $CUR_PATH | tail -1 | awk '{print $2" "$4}' else USED=$((`zfs get -o value -Hp used $CUR_PATH` / 1024)) > /dev/null AVAIL=$((`zfs get -o value -Hp available $CUR_PATH` / 1024)) > /dev/null TOTAL=$(($USED+$AVAIL)) > /dev/null echo $TOTAL $AVAIL fi
Save the script as "dfree.sh" to /home/"yourlinuxusername" then change the ownership of the file to make it executable with this command:
sudo chmod 774 dfree.sh
Now open smb.conf with sudo again:
sudo nano /etc/samba/smb.conf
Now add this entry to the top of the configuration file to direct Samba to use the results of our script when Windows asks for a reading on the pool's used/available/total drive space:
[global]
dfree command = /home/"yourlinuxusername"/dfree.sh
Save the changes to smb.conf and then restart Samba again with the terminal:
sudo systemctl restart smbd
Now there’s one more thing we need to do to fully set up the Samba share, and that’s to modify a hidden group permission. In the terminal window type the following command:
usermod -a -G sambashare “yourlinuxusername”
Then restart samba again:
sudo systemctl restart smbd
If we don’t do this last step, everything will appear to work fine, and you will even be able to see and map the drive from Windows and even begin transferring files, but you'd soon run into a lot of frustration. As every ten minutes or so a file would fail to transfer and you would get a window announcing “0x8007003B Unexpected Network Error”. This window would require your manual input to continue the transfer with the file next in the queue. And at the end it would reattempt to transfer whichever files failed the first time around. 99% of the time they’ll go through that second try, but this is still all a major pain in the ass. Especially if you’ve got a lot of data to transfer or you want to step away from the computer for a while.
It turns out samba can act a little weirdly with the higher read/write speeds of RAIDz arrays and transfers from Windows, and will intermittently crash and restart itself if this group option isn’t changed. Inputting the above command will prevent you from ever seeing that window.
The last thing we're going to do before switching over to our Windows PC is grab the IP address of our Linux machine. Enter the following command:
hostname -I
This will spit out this computer's IP address on the local network (it will look something like 192.168.0.x), write it down. It might be a good idea once you're done here to go into your router settings and reserving that IP for your Linux system in the DHCP settings. Check the manual for your specific model router on how to access its settings, typically it can be accessed by opening a browser and typing http:\\192.168.0.1 in the address bar, but your router may be different.
Okay we’re done with our Linux computer for now. Get on over to your Windows PC, open File Explorer, right click on Network and click "Map network drive". Select Z: as the drive letter (you don't want to map the network drive to a letter you could conceivably be using for other purposes) and enter the IP of your Linux machine and location of the share like so: \\"LINUXCOMPUTERLOCALIPADDRESSGOESHERE"\"zpoolnamegoeshere"\. Windows will then ask you for your username and password, enter the ones you set earlier in Samba and you're good. If you've done everything right it should look something like this:

You can now start moving media over from Windows to the share folder. It's a good idea to have a hard line running to all machines. Moving files over Wi-Fi is going to be tortuously slow, the only thing that’s going to make the transfer time tolerable (hours instead of days) is a solid wired connection between both machines and your router.
Step Six: Setting Up Remote Desktop Access to Your Server
After the server is up and going, you’ll want to be able to access it remotely from Windows. Barring serious maintenance/updates, this is how you'll access it most of the time. On your Linux system open the terminal and enter:
sudo apt install xrdp
Then:
sudo systemctl enable xrdp
Once it's finished installing, open “Settings” on the sidebar and turn off "automatic login" in the User category. Then log out of your account. Attempting to remotely connect to your Linux computer while you’re logged in will result in a black screen!
Now get back on your Windows PC, open search and look for "RDP". A program called "Remote Desktop Connection" should pop up, open this program as an administrator by right-clicking and selecting “run as an administrator”. You’ll be greeted with a window. In the field marked “Computer” type in the IP address of your Linux computer. Press connect and you'll be greeted with a new window and prompt asking for your username and password. Enter your Ubuntu username and password here.
If everything went right, you’ll be logged into your Linux computer. If the performance is sluggish, adjust the display options. Lowering the resolution and colour depth do a lot to make the interface feel snappier.
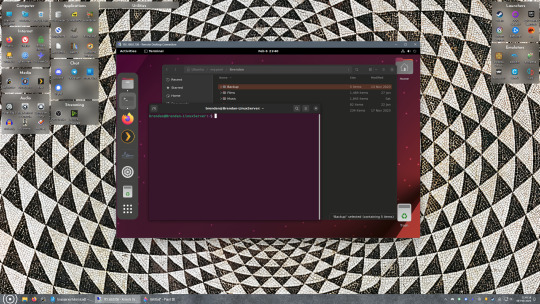
Remote access is how we're going to be using our Linux system from now, barring edge cases like needing to get into the BIOS or upgrading to a new version of Ubuntu. Everything else from performing maintenance like a monthly zpool scrub to checking zpool status and updating software can all be done remotely.

This is how my server lives its life now, happily humming and chirping away on the floor next to the couch in a corner of the living room.
Step Seven: Plex Media Server/Jellyfin
Okay we’ve got all the ground work finished and our server is almost up and running. We’ve got Ubuntu up and running, our storage array is primed, we’ve set up remote connections and sharing, and maybe we’ve moved over some of favourite movies and TV shows.
Now we need to decide on the media server software to use which will stream our media to us and organize our library. For most people I’d recommend Plex. It just works 99% of the time. That said, Jellyfin has a lot to recommend it by too, even if it is rougher around the edges. Some people run both simultaneously, it’s not that big of an extra strain. I do recommend doing a little bit of your own research into the features each platform offers, but as a quick run down, consider some of the following points:
Plex is closed source and is funded through PlexPass purchases while Jellyfin is open source and entirely user driven. This means a number of things: for one, Plex requires you to purchase a “PlexPass” (purchased as a one time lifetime fee $159.99 CDN/$120 USD or paid for on a monthly or yearly subscription basis) in order to access to certain features, like hardware transcoding (and we want hardware transcoding) or automated intro/credits detection and skipping, Jellyfin offers some of these features for free through plugins. Plex supports a lot more devices than Jellyfin and updates more frequently. That said, Jellyfin's Android and iOS apps are completely free, while the Plex Android and iOS apps must be activated for a one time cost of $6 CDN/$5 USD. But that $6 fee gets you a mobile app that is much more functional and features a unified UI across platforms, the Plex mobile apps are simply a more polished experience. The Jellyfin apps are a bit of a mess and the iOS and Android versions are very different from each other.
Jellyfin’s actual media player is more fully featured than Plex's, but on the other hand Jellyfin's UI, library customization and automatic media tagging really pale in comparison to Plex. Streaming your music library is free through both Jellyfin and Plex, but Plex offers the PlexAmp app for dedicated music streaming which boasts a number of fantastic features, unfortunately some of those fantastic features require a PlexPass. If your internet is down, Jellyfin can still do local streaming, while Plex can fail to play files unless you've got it set up a certain way. Jellyfin has a slew of neat niche features like support for Comic Book libraries with the .cbz/.cbt file types, but then Plex offers some free ad-supported TV and films, they even have a free channel that plays nothing but Classic Doctor Who.
Ultimately it's up to you, I settled on Plex because although some features are pay-walled, it just works. It's more reliable and easier to use, and a one-time fee is much easier to swallow than a subscription. I had a pretty easy time getting my boomer parents and tech illiterate brother introduced to and using Plex and I don't know if I would've had as easy a time doing that with Jellyfin. I do also need to mention that Jellyfin does take a little extra bit of tinkering to get going in Ubuntu, you’ll have to set up process permissions, so if you're more tolerant to tinkering, Jellyfin might be up your alley and I’ll trust that you can follow their installation and configuration guide. For everyone else, I recommend Plex.
So pick your poison: Plex or Jellyfin.
Note: The easiest way to download and install either of these packages in Ubuntu is through Snap Store.
After you've installed one (or both), opening either app will launch a browser window into the browser version of the app allowing you to set all the options server side.
The process of adding creating media libraries is essentially the same in both Plex and Jellyfin. You create a separate libraries for Television, Movies, and Music and add the folders which contain the respective types of media to their respective libraries. The only difficult or time consuming aspect is ensuring that your files and folders follow the appropriate naming conventions:
Plex naming guide for Movies
Plex naming guide for Television
Jellyfin follows the same naming rules but I find their media scanner to be a lot less accurate and forgiving than Plex. Once you've selected the folders to be scanned the service will scan your files, tagging everything and adding metadata. Although I find do find Plex more accurate, it can still erroneously tag some things and you might have to manually clean up some tags in a large library. (When I initially created my library it tagged the 1963-1989 Doctor Who as some Korean soap opera and I needed to manually select the correct match after which everything was tagged normally.) It can also be a bit testy with anime (especially OVAs) be sure to check TVDB to ensure that you have your files and folders structured and named correctly. If something is not showing up at all, double check the name.
Once that's done, organizing and customizing your library is easy. You can set up collections, grouping items together to fit a theme or collect together all the entries in a franchise. You can make playlists, and add custom artwork to entries. It's fun setting up collections with posters to match, there are even several websites dedicated to help you do this like PosterDB. As an example, below are two collections in my library, one collecting all the entries in a franchise, the other follows a theme.

My Star Trek collection, featuring all eleven television series, and thirteen films.
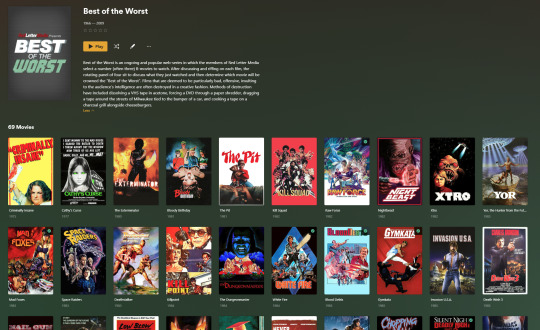
My Best of the Worst collection, featuring sixty-nine films previously showcased on RedLetterMedia’s Best of the Worst. They’re all absolutely terrible and I love them.
As for settings, ensure you've got Remote Access going, it should work automatically and be sure to set your upload speed after running a speed test. In the library settings set the database cache to 2000MB to ensure a snappier and more responsive browsing experience, and then check that playback quality is set to original/maximum. If you’re severely bandwidth limited on your upload and have remote users, you might want to limit the remote stream bitrate to something more reasonable, just as a note of comparison Netflix’s 1080p bitrate is approximately 5Mbps, although almost anyone watching through a chromium based browser is streaming at 720p and 3mbps. Other than that you should be good to go. For actually playing your files, there's a Plex app for just about every platform imaginable. I mostly watch television and films on my laptop using the Windows Plex app, but I also use the Android app which can broadcast to the chromecast connected to the TV in the office and the Android TV app for our smart TV. Both are fully functional and easy to navigate, and I can also attest to the OS X version being equally functional.
Part Eight: Finding Media
Now, this is not really a piracy tutorial, there are plenty of those out there. But if you’re unaware, BitTorrent is free and pretty easy to use, just pick a client (qBittorrent is the best) and go find some public trackers to peruse. Just know now that all the best trackers are private and invite only, and that they can be exceptionally difficult to get into. I’m already on a few, and even then, some of the best ones are wholly out of my reach.
If you decide to take the left hand path and turn to Usenet you’ll have to pay. First you’ll need to sign up with a provider like Newshosting or EasyNews for access to Usenet itself, and then to actually find anything you’re going to need to sign up with an indexer like NZBGeek or NZBFinder. There are dozens of indexers, and many people cross post between them, but for more obscure media it’s worth checking multiple. You’ll also need a binary downloader like SABnzbd. That caveat aside, Usenet is faster, bigger, older, less traceable than BitTorrent, and altogether slicker. I honestly prefer it, and I'm kicking myself for taking this long to start using it because I was scared off by the price. I’ve found so many things on Usenet that I had sought in vain elsewhere for years, like a 2010 Italian film about a massacre perpetrated by the SS that played the festival circuit but never received a home media release; some absolute hero uploaded a rip of a festival screener DVD to Usenet. Anyway, figure out the rest of this shit on your own and remember to use protection, get yourself behind a VPN, use a SOCKS5 proxy with your BitTorrent client, etc.
On the legal side of things, if you’re around my age, you (or your family) probably have a big pile of DVDs and Blu-Rays sitting around unwatched and half forgotten. Why not do a bit of amateur media preservation, rip them and upload them to your server for easier access? (Your tools for this are going to be Handbrake to do the ripping and AnyDVD to break any encryption.) I went to the trouble of ripping all my SCTV DVDs (five box sets worth) because none of it is on streaming nor could it be found on any pirate source I tried. I’m glad I did, forty years on it’s still one of the funniest shows to ever be on TV.
Part Nine/Epilogue: Sonarr/Radarr/Lidarr and Overseerr
There are a lot of ways to automate your server for better functionality or to add features you and other users might find useful. Sonarr, Radarr, and Lidarr are a part of a suite of “Servarr” services (there’s also Readarr for books and Whisparr for adult content) that allow you to automate the collection of new episodes of TV shows (Sonarr), new movie releases (Radarr) and music releases (Lidarr). They hook in to your BitTorrent client or Usenet binary newsgroup downloader and crawl your preferred Torrent trackers and Usenet indexers, alerting you to new releases and automatically grabbing them. You can also use these services to manually search for new media, and even replace/upgrade your existing media with better quality uploads. They’re really a little tricky to set up on a bare metal Ubuntu install (ideally you should be running them in Docker Containers), and I won’t be providing a step by step on installing and running them, I’m simply making you aware of their existence.
The other bit of kit I want to make you aware of is Overseerr which is a program that scans your Plex media library and will serve recommendations based on what you like. It also allows you and your users to request specific media. It can even be integrated with Sonarr/Radarr/Lidarr so that fulfilling those requests is fully automated.
And you're done. It really wasn't all that hard. Enjoy your media. Enjoy the control you have over that media. And be safe in the knowledge that no hedgefund CEO motherfucker who hates the movies but who is somehow in control of a major studio will be able to disappear anything in your library as a tax write-off.
1K notes
·
View notes
Text
Unlock creative insights with AI instantly
What if the next big business idea wasn’t something you “thought of”… but something you unlocked with the right prompt? Introducing Deep Prompt Generator Pro — the tool designed to help creators, solopreneurs, and future founders discover high-impact business ideas with the help of AI.
💡 The business idea behind this very video? Generated using the app. If you’re serious about building something real with ChatGPT or Claude, this is the tool you need to stop wasting time and start creating real results.
📥 Download the App: ✅ Lite Version (Free) → https://bit.ly/DeepPromptGeneratorLite 🔓 Pro Version (Full Access) → https://www.paypal.com/ncp/payment/DH9Z9LENSPPDS
🧠 What Is It? Deep Prompt Generator Pro is a lightweight desktop app built to generate structured, strategic prompts that help you:
✅ Discover profitable niches ✅ Brainstorm startup & side hustle ideas ✅ Find monetization models for content or products ✅ Develop brand hooks, angles, and offers ✅ Unlock creative insights with AI instantly
Whether you’re building a business, launching a new product, or looking for your first real side hustle — this app gives your AI the clarity to deliver brilliant results.
🔐 Features: Works completely offline No API or browser extensions needed Clean UI with categorized prompts One-click copy to paste into ChatGPT or Claude System-locked premium access for security
🧰 Who It’s For: Founders & solopreneurs Content creators Side hustlers AI power users Business coaches & marketers Anyone who’s tired of “mid” AI output
�� PDF Guide Included – Every download includes a user-friendly PDF guide to walk you through features, categories, and how to get the best results from your prompts.
📂 Pro Version includes exclusive prompt packs + priority access to new releases.
🔥 Watch This If You’re Searching For: how to use ChatGPT for business ideas best prompts for startup founders AI tools for entrepreneurs side hustle generators GPT business prompt generator AI idea generator desktop app ChatGPT for content creators
📣 Final Call to Action: If this tool gave me a business idea worth filming a whole video about, imagine what it could help you discover. Stop guessing — start prompting smarter.
🔔 Subscribe to The App Vault for weekly tools, apps, and automation hacks that deliver real results — fast.🔓 Unlock Your PC's Full Potential with The App Vault Tiny Tools, Massive Results for Productivity Warriors, Creators & Power Users
Welcome to The App Vault – your ultimate source for lightweight desktop applications that deliver enterprise-grade results without bloatware or subscriptions. We specialize in uncovering hidden gem software that transforms how creators, freelancers, students, and tech enthusiasts work. Discover nano-sized utilities with macro impact that optimize workflows, turbocharge productivity, and unlock creative potential.
🚀 Why Our Community Grows Daily: ✅ Zero Fluff, Pure Value: 100% practical tutorials with actionable takeaways ✅ Exclusive Tools: Get first access to our custom-built apps like Deep Prompt Generator Pro ✅ Underground Gems: Software you won't find on mainstream tech channels ✅ Performance-First: Every tool tested for system efficiency and stability ✅ Free Resources: Download links + config files in every description
🧰 CORE CONTENT LIBRARY: ⚙️ PC Optimization Arsenal Windows optimization secrets for buttery-smooth performance System cleanup utilities that actually remove 100% of junk files Memory/RAM optimizers for resource-heavy workflows Startup managers to slash boot times by up to 70% Driver update automation tools no more manual hunting Real-time performance monitoring dashboards
🤖 AI Power Tools Local AI utilities that work offline for sensitive data Prompt engineering masterclass series Custom AI workflow automations Desktop ChatGPT implementations Niche AI tools for creators: image upscalers, script generators, audio enhancers AI-powered file organization systems
⏱️ Productivity Boosters Single-click task automators Focus enhancers with distraction-killing modes Micro-utilities for batch file processing Smart clipboard managers with OCR capabilities Automated backup solutions with versioning Time-tracking dashboards with productivity analytics
🎨 Creative Workflow Unlockers Content creation accelerators for YouTubers Automated thumbnail generators Lightweight video/audio editors 50MB Resource-efficient design tools Cross-platform project synchronizers Metadata batch editors for digital assets
🔍 Niche Tool Categories Open-source alternatives to expensive software Security tools for privacy-conscious users Hardware diagnostic toolkits Custom scripting utilities for power users Legacy system revival tools
youtube
#DeepPromptGenerator#BusinessIdeas#ChatGPTPrompts#SideHustleIdeas#StartupIdeas#TheAppVault#PromptEngineering#AIProductivity#SolopreneurTools#TinyToolsBigImpact#DesktopApp#ChatGPTTools#FiverrApps#Youtube
2 notes
·
View notes
Text
Why Sabaragamuwa University is a Great Choice.
Sabaragamuwa University of Sri Lanka (SUSL) is increasingly recognized for its technological advancement and innovation-driven environment, making it one of the leading universities in Sri Lanka in terms of technology. Here are the key reasons why SUSL stands out technologically.

Here’s why SUSL stands out as a technological powerhouse among Sri Lankan universities:
🔧1. Faculty of Technology
SUSL established a dedicated Faculty of Technology to meet the demand for tech-skilled graduates. It offers degree programs such as:
BTech in Information and Communication Technology
BTech in Engineering Technology
These programs combine practical experience in labs, workshops and real-world projects with a strong theoretical foundation.
🖥️2. Advanced IT Infrastructure
SUSL has modern computer labs, smart classrooms, and high-speed internet access across campus.
A robust Learning Management System (LMS) supports online learning and hybrid education models.
Students and lecturers use tools like Moodle, Zoom, and Google Classroom effectively.
🤖 3. Innovation & AI Research Support
SUSL promotes AI, Machine Learning, IoT, and Data Science in student research and final-year projects.
Competitions like Hackathons and Innovative Research Symposia encourage tech-driven solutions.
Students develop apps, smart systems, and automation tools (e.g., Ceylon Power Tracker project).
🌐 4. Industry Collaboration and Internships
SUSL connects students with the tech industry through:
Internships at leading tech firms
Workshops led by industry experts
Collaborative R&D projects with government and private sector entities
These connections help students gain hands-on experience in areas such as software engineering, networking, and data analytics that make them highly employable after graduation.
💡 5. Smart Campus Initiatives
SUSL is evolving into a Smart University, introducing systems that streamline academic life:
Digital student portals
Online registration and results systems
E-library and remote resource access
Campus Wi-Fi for academic use
These initiatives improve the student experience and create an efficient, technology-enabled environment.
🎓 6. Research in Emerging Technologies
The university is involved in pioneering research across emerging technological fields, including:
Agricultural tech (AgriTech)
Environmental monitoring using sensors
Renewable energy systems
Students and faculty publish research in international journals and participate in global tech events.
🏆 7. Recognition in National Competitions
SUSL students often reach fina rounds or win national competitions in coding, robotics, AI, and IoT innovation.
Faculty members are invited as tech advisors and conference speakers, reinforcing the university's expertise.
Sabaragamuwa University is actively shaping the future not only with technology, but by integrating technology into education, research and operations. This makes it a technological leader among Sri Lankan Universities. Visit the official university site here: Home | SUSL
2 notes
·
View notes
Text
Chapter III: Learning from the past to shape the future.
First << Previous <- Next ->
As the ramp lowers, the cult grounds come to view. Despite the similar structure of division of sleeping quarters, canteen, farms, temple and other necessary infrastructures, it's all far more advanced. There are small studio homes in place of huts, the farms have automated irrigation systems, the kitchen has several electrical appliances, and that's just what's immediately visible.
The followers in the cult have all been enhanced cybernetically to some degree, from a single limb or eye to nearly all of their bodies. A small selection of them seem to be entirely mechanical, most of them recreations of follower forms, though a small group among them have bulkier utilitarian frames, more closely resembling tractors, cranes or trucks, while others resemble a regular follower from the waist up, and the animal body below that.
As the group crosses the ramp, it also becomes apparent that, despite the altitude, there's no strong wind in the cult grounds, as if something was shielding the place from the weather, though not all of them seem to notice it right away from the awe.
"We are quite a way up, aren't we? Where's the wind?" Asks Leshy, who can't quite appreciate the sights due to his blindness.
"Well noticed, Leshy. There is a energy shield that covers the entire area of my cult grounds between the two runways." Wolfgang replies as they walk towards the huge structure that is the temple, as well as the shrine, a statue of the god of Technology with his six eyes looking at the distance and holding his arms in front of himself, an open book on his left hand and a mechanical contraption on the right one.
"The two what now?" Asks the former Bishop of Chaos while the others stop to see an elephant carry a giant box over their head from the farm to the kitchen, thanks to a mechanical exoskeleton.
"It will be easier to explain once we are in the library, where there are models to demonstrate. Suffice to say for now, though, runways are strips of land that allows certain aircraft to take off and land safely." Wolfgang responds, before calling to the others. "We are almost there. You guys can have the tour of the place later."
That's enough to get the others back on track for now, so they all move to the temple. Once inside, they can see that the sermon room is not much bigger than the one on Leoda's temple, despite the cathedral sized building it is housed in. It is, however, a lot more opulent despite the size, not too surprising considering how long the Wolf has been a god.
"Wait, this is you temple?" Leoda asks as they look around. "It's... Tiny."
"Well, yes. This is the temple." Wolfgang responds as he moves to one of the doors on the back. "I don't need that big of a house of worship for my main cult. Now the library that's attached to it? That needs a lot of space... I suppose it's more accurate to say I have a temple in my library than the other way around."
"What you mean main cult?" Leoda inquires further, but it's Narinder's time to respond.
"It's not sustainable to keep growing your cult past a certain size, so we used to send disciples in missionary missions to form additional cults in our names so the amount of devotion we receive increase, without having to sustain more followers." The panther explains to his former vessel. "It's not as efficient as indoctrinating more followers into the cult, but it is a lot simpler and cheaper."
"Precisely." Wolfgang responds to the explanation as he opens the door. "Specially when your claims start to span over an entire continent. At that point it's better to treat anything outside the main cult as an empire that you have to manage on the macro scale instead." He then gestures for them to go through. "In any case, welcome to my central library."
Across the door is a balcony of sorts, about 4 by 5 meters (about 13 by 16 feet), with a conference table and several chairs meant for meetings. It is enclosed by glass all around, including a sliding glass door opposite to the entrance from the temple. Beyond that is a several floors deep drop to the floor of the library.
The sight of the place is, once again, breath taking. The library is gargantuan, with rows upon rows of book shelves, all going from the ceiling of the cathedral to several floors underground. Several platforms move between them, taking scholars or would be readers to where they need to go to retrieve books. Even Leshy, though his Blessing of the Forest, can sense the sheer scale of the place.
Wolfgang goes to the glass door and presses a button besides it to call one of the moving platforms.
"This is so much bigger than any of my libraries..." Shamura says as they look out of the glass walls.
"That's because my crown drives me to accumulate an ever increasing amount of knowledge, Shamura." The wolf says while waiting for the platform. "Even if I didn't choose to share nearly it all with anyone willing to learn, the Gray Crown is never satisfied with what I just come across by chance. It always hunger to learn more."
"Your crown too tries to take over?" Asks Leoda, getting the attention of the wolf, who shakes his head.
"Not like what I heard the Red Crown did, which I assume is nowhere near as bad as what really happened." He says as a platform, roughly 3 by 3 meters (10 by 10 feet) approaches the balcony. "But every crown tries to influence its bearer, according to their domains." As the platform stops in front of the balcony, it lowers a part of the protective railing before the glass door opens. "Please mind the gap while boarding the platform. Trust me, you don't want to let any of your personal belongings fall."
After they all board, Baines, who had gone through the whole awe thing the first time he came to the cult grounds, and as such was just following the group, moves to the control screen of the platform.
"Where to, Lord Wolfgang?" The owl asks as he rests the crosier against his shoulder to free one of his hands.
"Video study room five c." The wolf instructs as he helps Leshy to climb onto the platform. "Five a is in use and five b is under maintenance."
With a nod, Baines navigates to the rooms menu, then selects the designated room, giving enough time for everyone to board. After a few seconds, the railing raises up again and the platform starts moving, first horizontally, then vertically.
"How long did it take to build all of this?" Gayne asks as they watch the bookshelves go by as they move.
"Well, the platform system has been in the works for the last hundred years or so, getting improvements often." Wolfgang replies as he waits for the arrival at their destination. "The library, though? Since I became a god, so about eight hundred sixty four years."
"Huh. No wonder this place is so massive." the Goat replies as they look towards the bottom of the library. "My Shamura took a century to fill a new hidden library, and they weren't small ones either."
"Your Shamura?" Wolfgang asks, looking between the former spider god and the current goat one.
"Yeah, I come from a different time line." Gayne responds nonchalantly as they lean away from the rail to look at the Wolf.
"I see..." The Wolf responds, before turning his crown into a tablet to take note of that new information.
"Might not be wise to go talking about it, Gayne." Leoda chides the Goat, who just shrugs.
"He would have figured it out sooner or later. Besides, what can be done about it at this point?" Gayne responds to the Lamb. "As far as I know, the connection between the timelines got severed when the crown returned there without me."
"I wouldn't be so sure about it, Gayne." Wolfgang replies as he returns the crown to its place atop his head. "You got me a few ideas brewing on how to detect and access other timelines." He adds as the platform start aligning with a door.
"Shit..." The Goat replies as Leoda gives a "I told you so" look to them.
"Oh, don't worry. I don't intend on sending you back home unless you become a threat to my people." The Wolf replies as the platform comes to a stop, lowering the same section of the railing as before as the metal door on the wall opens. "Anyways, we arrived."
"Are the rooms only accessible through the platforms?" Asks Shamura as there doesn't seem to be any stairs on the library side.
"That wouldn't be safe. There are stair access on the other side of the rooms, but they are less convenient than the platforms." Wolfgang explains as the group disembark into the study room. "They have been installed for emergencies where the platforms are not safe to ride on."
The room the group enters is quite big, at least for a study room, clearly meant for groups to use. It is shaped like a cube with size length of 5 meters (16 feet), to be able to accommodate a Bishop. The walls are covered by cream colored embossed velvet, giving a soft and comforting appearance, while the floor and ceiling are covered with black carpet. Opposite to the entrance is a window with shutter blinds currently closed, so only the room is currently illuminated by artificial light from the ceiling lamps only.
On the wall to the right is a lounge sofa, spanning the entire length of the wall, and on the left is a projection screen, currently lowered, though that doesn't remain for long before Wolfgang raises it up, not planning to use the projector hanging from the ceiling. Underneath the screen is a short rack with a few devices. In the middle of the room is a round table with several chairs placed around it, with a dome on its center, though if it is just decoration or has another use is not clear.
While the group take their seats on the chairs or the sofa, Wolfgang approaches the rack and picks up a tablet from it. "So, since there's a lot to go through, lets start off with the events that resulted in the treaty I was referring earlier." He speaks up as he inputs commands on the tablet, dimming the lights down before the dome on the table lights up and starts projecting a 3D image above it.
Wolfgang describes the events as the projector provides the visual representation. "After I had conquered Euhera as the sole god of that land, I started sending ships to scout the world, given how little the crown was aware of due to departing Phemura without a bearer. I was aware of this continent, and indeed these lands were the first to be found, but Ofura was discovered not much longer afterwards." He explains as the projection shows the routes each vessel took on the ocean.
"When the explorers landed here, they saw some signs of the Old Faith, but they were mostly deteriorating statues and ruined buildings up north, so they assumed there were no living gods in these lands." He continues, showing some of the images that were documented of the bishop statues covered in moss, as well as ruined temples.
"We... Were there..." Heket interrupts, to which Wolfgang nods.
"Indeed, but your combined territory had stagnated in size. It was barely remnants that far up north, so there was no real way of knowing until you started moving against the beachhead after I had made landfall as well." The Wolf points out. "At which point I had to defend what I had already claimed as my territory."
"And whatever you used to drive me back sure hurt. I mean, I was miles away, so I have no idea of what you did, but those explosions were no joke!" Leshy chimed in as he lounged on the couch. "Didn't even get a proper fight there!"
"Leshy, you shouldn't antagonize him!" Kallamar chides his younger brother.
"Brother, I love you, but you should really listen to his advice about stopping hiding behind others if you have something to say." Leshy retorts. "Besides, even I wouldn't be dumb enough to speak in such manner if I thought he would smite me for it."
"You have a point, Leshy, but you did come dangerously close of calling a god coward. Were I a god of War, you'd probably not be lounging where you are now any longer." Wolfgang points out to the bushworm. "Of course, the howitzer barrage could be seen as a cowardly attack, but it was tactically the most sound option. You were, after all, a whole siege by yourself."
"A what barrage?" Asks Gayne while Leshy seemed pleased with himself about being considered such a threat.
"Howitzer. It's a kind of long range artillery that allows for long range engagement. We have since moved past that tech and into more powerful artillery pieces." Wolfgang explains. "That's besides the point now. After driving Leshy and Heket back with long range weaponry and engaging Kallamar with use of curses, I ended up fighting Shamura for a while. After trading a few blows to each other, we agreed to discuss the terms of a treaty so I don't invade further their land, nor do they keep attacking what I claimed."
"We gave... Too much..." Heket tries to speak, before Shamura interrupts her.
"It was the only way to avoid a war with a god that, while much younger, was not burdened by as grievous wounds as ours from sealing our brother, dear sister." They reason with the frog, who seems frustrated but settles down nonetheless.
"Seems your memories of what happened are returning, Shamura." Wolfgang adds comments, to which the spider nods.
"Indeed, though they are still foggy and fragmented. I'm sorry, but it is difficult to recall much more than that." Shamura responds, keeping their composure where others would be nervous in their place.
Wolfgang sighs at hearing it. "So be it. It is a shame what happened to that sharp mind of yours." He says, before going to the rack to retrieve two more tablets, tapping on them for a few moments, then giving them to Gayne and Leoda. "Anyways, the terms are listed here."
"Wait, how do you know about Shamura's mental state from before I was sealed?" Asks Narinder as he leans forwards on his chair.
"The Gray Crown grants me access to something called the Akashic Records. It's a collection of all the accumulated knowledge it has witnessed, including, but not limited to, that of my predecessor." Wolfgang explains while the two new gods review the treaty. "And that includes each meeting with each of you five. Speaking of which..." He adds as he puts down the tablet controlling the projector and pulls once again the crown as a one. "Would you mind recollecting how you managed to take them down, Narinder? The information of the moment of their death is missing, besides the fact that you were the one to land the killing blow."
"I, uh... OK?" Narinder is taken aback by the way Wolfgang is reacting to being in the presence of their predecessor's killer. Most crown bearers would be seeking revenge. "As long as you aren't planning anything beyond taking notes, I don't see why not."
"Oh, don't worry about it. I know they used to be... Less than morally upstanding. I have no reason to want revenge for someone whose methods I didn't really agree with, and the Gray Crown cares more about filling that gap in knowledge than seeking retribution." Wolfgang reassures the panther. "For it, their death was just another experience to be catalogued without hard feelings."
"Well, if that's the case, then I suppose I should fill in as many details as I can, right?" Narinder asks, receiving a nod of confirmation from the Wolf. "It all happened about a century before the end of the god wars..."

And here we have it, folks. The cult of the Gray Crown in all it's technological glory. As a comparison, while I consider the main game to be around steampunk levels of tech, the cult of the Gray Crown is at post space age levels. That comes from the fact that their Bishop was not crippled by wounds, so he didn't stagnate, and that he is one to push development at break neck speeds.
Next chapter, we will be jumping back in time, to witness the god wars as Narinder recollects the battle with the previous bearer of the Gray Crown, and the different approach to advancement they had.
as always, separator by @lambouillet
3 notes
·
View notes
Text
I think a lot sometimes about the pushback against the concept of talent within arts and I mean yeah on some level I get it, but also the suggestion that anyone can learn to draw is, to me, like saying anyone can learn to program.
like yes, sure, at the end of the day just about anyone can likely find some way of forming vague scribbles using their tool or input peripheral of choice, but that's basically like saying just about anyone can find ways of writing semicolons and the words if, then, else on some kind of digital computer - the difficulty was never in achieving the most basic and abstracted interpretation of the act, but in an understanding of how your actions translate into the kind of end result that you want.
in programming, the most basic starter program that nearly every extremely basic example or tutorial will start with is called Hello World, which is simply a program that prints or otherwise displays the text Hello World to the user.
#include <iostream>
in python, this can be done with a single line of code, like so:
print("Hello World!")
while in C++, that same program will take a bit more work:
#include <iostream>
int main()
{
std::cout << "Hello World!\n";
return 0;
}
Now if you have the ability to copy that text into a file then congratulations, you have the ability to write a program! But, obviously, to really do any actual programming, you kind of need to know what any of the above actually means and what it makes the computer actually do.
This by the way is why the "Learn to Code" kind of initiatives tend not to work out very well, because while technically anyone can write code, actually understanding how to code is a much more complicated affair that can't necessarily be directly taught - it's something that has to be understood.
What is needed, basically, is a system - a kind of mental library of symbols and concepts that you can rearrange and reassemble in various ways to reach a particular solution; a point where you can break down a larger problem into a bunch of much smaller, more individualised problems that are easier to solve one by one.
This is basically how expertise works - whether consciously or (much more often!) not, you form models and systems in your head to let you simplify and, to an extent, automate otherwise complex tasks. If you've ever looked at something and just felt this feeling of "aha, I see how this works", then you should technically already know what I'm talking about.
And look, this is not an argument against practice - expertise takes work, it takes training and experience and gradually discovering ways in which things start making sense to you, even those things that you might have an intuitive knack for. However, what I do think is that telling people who say they can't draw to "just draw anyway" is a lot like, and just as dismissive as, "Learn to Code" because, just like how saying "I don't know how to code" generally is not meant to be understood as "I am physically unable to write words into a text document", saying "I can't draw" typically does not mean being physically unable to form lines or shapes on paper or in a digital image or whatever. Rather, it's a statement about being unable to break down the problem of how to reach a desired end result into smaller, manageable steps that you are able to grasp. And, much like with programming, not everyone will have an eye, or a mind, for it: just like some people struggle with spelling or mathematics or, indeed, code, some people also struggle with colour or perspective or object shape or lighting and shading. And, by contrast, for some people these things also come much more easily and naturally than others.
Not everyone can do everything - at least not to such an extent that it would let them do something they would want to do. Practice can help, certainly, but it's not necessarily guaranteed to bridge the gap either. I mean, I personally find it baffling how many people seem to struggle with what I consider basic computer literacy, but that's a lot to do with the fact that I just happen to find much of it pretty simple and straightforward where a lot of people don't. Not everyone has a base aptitude to build on for every field or skill, and that's both fine and normal. And I mean - something as simple as the ability to put in the effort to practice and learn a particular skill or expertise is in itself a skill, and one that can be very selective about what contexts it's willing to apply to.
9 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text

Prompt: Create a movie concept set in an post-apocalyptic world the fall of human civilization was (somehow!) caused by overzealous copyright enforcement.
Secondary prompt: Adjust to fit into this background: The copyright enforcement system was designed to be impossible to shutdown. When the first corporation fell in the economic collapse, enforcers could no longer confirm whether the work or patent it supposedly owned could be reused (either via legit license or because of being in the public domain) and they just started destroying or erasing everything, including, for example, the people whose likeness was present in their own licensed portraits. Things rapidly escalated into total civilization collapse. Now the survivors must find a way to register all culture as public domain or be ruthlessly erased.
IPocalypse Now: Remnants of Culture
Logline: In a post-apocalyptic world where copyright enforcement has run amok, a lone survivor must navigate a landscape of intellectual property disputes and copyright trolls while searching for a way to register all culture as public domain and prevent further destruction.
Logline: DMCA was just the beginning.
Setting: The world has been ravaged by a series of "copyright purges," where automated enforcement systems, designed to be indestructible, seized control and began ruthlessly destroying any content deemed to be infringing on intellectual property rights. Cities have been reduced to rubble, libraries and museums have been emptied, and the once vibrant human culture is on the brink of extinction.
Characters:
Elias (30s): A passionate bibliophile and historian, Elias is one of the few survivors of the copyright purges. He carries a hidden database of cultural knowledge, determined to preserve it for future generations.
The Enforcers (various ages and appearances): A faceless army of drones and robots, armed with laser cannons and copyright infringement scanners. They continue to patrol the wasteland, relentlessly seeking out and destroying any unauthorized content.
The Resistance (various ages and backgrounds): A group of survivors who have banded together to fight the copyright enforcers and preserve what remains of human culture.
Plot:
Elias discovers that the copyright enforcement system has become corrupted. With the collapse of major corporations, the system can no longer verify ownership of intellectual property. As a result, it has gone haywire, destroying everything from art and music to historical records and even the likenesses of individuals.
Elias joins the Resistance, a group of survivors fighting to protect the remnants of human culture. Together, they devise a plan to register all existing cultural works as public domain, making them immune to copyright enforcement.
The journey is fraught with danger. The enforcers are relentless, and the Resistance must constantly evade their patrols and find hidden safe havens. Along the way, Elias encounters other survivors, each with their own unique skills and knowledge.
Themes:
The dangers of unchecked technology: The film explores the consequences of allowing technology to run rampant, particularly when it comes to enforcing laws.
The importance of intellectual freedom: The characters fight for the right to access and share information, emphasizing the value of human creativity and expression.
The resilience of the human spirit: In the face of adversity, the survivors demonstrate the power of hope and determination to rebuild a shattered world.
Ending:
Through a series of daring missions and strategic planning, Elias and the Resistance manage to register a significant portion of human culture as public domain. The enforcers, unable to distinguish between protected and unprotected content, are forced to retreat. The film ends with Elias and his companions standing amidst a newly established cultural archive, a symbol of humanity's resilience and the enduring power of ideas.
#ai generated#stupid ideas#shitpost#imaginary movie#google gemini#movie poster#poster#genre: dystopia#genre: science fiction#female protagonist#post apocalyptic#intellectual property#ip law#artificial intelligence#cautionary tale#technology
2 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
Unlock the Power of Python Programming: A Complete Guide
Python programming has become one of the most sought-after skills in the world of technology. Its simplicity, flexibility, and vast ecosystem of libraries make it a top choice for both beginners and experienced developers. In this guide, we will explore various aspects of Python programming, from basic concepts to advanced applications like machine learning and web development.
Python Programming: A Beginner-Friendly Language
Python programming is renowned for its readability and straightforward syntax, making it ideal for beginners. Whether you are just starting to code or transitioning from another language, Python offers a smooth learning curve. Key Python programming concepts include variables, data types, and control structures, which are essential for writing functional code.
youtube
Python Data Structures: Organizing Data Efficiently
One of the core strengths of Python programming is its rich set of data structures. Lists, dictionaries, tuples, and sets help you store and manage data effectively. Understanding Python data structures allows you to create more efficient programs by organizing and manipulating data effortlessly.
Functions in Python Programming: Building Reusable Code
Functions are a fundamental part of Python programming. They allow you to break down complex problems into smaller, reusable chunks of code. Python functions not only promote code reusability but also make your programs more organized and easier to maintain.
Loops in Python Programming: Automating Repeated Tasks
Loops are an essential feature in Python programming, allowing you to perform repeated operations efficiently. With Python loops such as for and while, you can iterate over sequences or perform tasks until a specific condition is met. Mastering loops is a key part of becoming proficient in Python.
Object-Oriented Programming in Python: Structured Development
Python programming supports object-oriented programming (OOP), a paradigm that helps you build structured and scalable software. OOP in Python allows you to work with classes and objects, making it easier to model real-world scenarios and design complex systems in a manageable way.
Python Automation Scripts: Simplify Everyday Tasks
Python programming can be used to automate repetitive tasks, saving you time and effort. Python automation scripts can help with file management, web scraping, and even interacting with APIs. With Python libraries like os and shutil, automation becomes a breeze.
Python Web Development: Creating Dynamic Websites
Python programming is also a popular choice for web development. Frameworks like Django and Flask make it easy to build robust, scalable web applications. Whether you're developing a personal blog or an enterprise-level platform, Python web development empowers you to create dynamic and responsive websites.
APIs and Python Programming: Connecting Services
Python programming allows seamless integration with external services through APIs. Using libraries like requests, you can easily interact with third-party services, retrieve data, or send requests. This makes Python an excellent choice for building applications that rely on external data or services.

Error Handling in Python Programming: Writing Resilient Code
Python programming ensures that your code can handle unexpected issues using error handling mechanisms. With try-except blocks, you can manage errors gracefully and prevent your programs from crashing. Error handling is a critical aspect of writing robust and reliable Python code.
Python for Machine Learning: Leading the AI Revolution
Python programming plays a pivotal role in machine learning, thanks to powerful libraries like scikit-learn, TensorFlow, and PyTorch. With Python, you can build predictive models, analyze data, and develop intelligent systems. Machine learning with Python opens doors to exciting opportunities in artificial intelligence and data-driven decision-making.
Python Data Science: Turning Data Into Insights
Python programming is widely used in data science for tasks such as data analysis, visualization, and statistical modeling. Libraries like pandas, NumPy, and Matplotlib provide Python programmers with powerful tools to manipulate data and extract meaningful insights. Python data science skills are highly in demand across industries.
Python Libraries Overview: Tools for Every Task
One of the greatest advantages of Python programming is its extensive library support. Whether you're working on web development, automation, data science, or machine learning, Python has a library for almost every need. Exploring Python libraries like BeautifulSoup, NumPy, and Flask can significantly boost your productivity.
Python GUI Development: Building User Interfaces
Python programming isn't just limited to back-end or web development. With tools like Tkinter and PyQt, Python programmers can develop graphical user interfaces (GUIs) for desktop applications. Python GUI development allows you to create user-friendly software with visual elements like buttons, text fields, and images.
Conclusion: Python Programming for Every Developer
Python programming is a versatile and powerful language that can be applied in various domains, from web development and automation to machine learning and data science. Its simplicity, combined with its extensive libraries, makes it a must-learn language for developers at all levels. Whether you're new to programming or looking to advance your skills, Python offers endless possibilities.
At KR Network Cloud, we provide expert-led training to help you master Python programming and unlock your potential. Start your Python programming journey today and take the first step toward a successful career in tech!
#krnetworkcloud#python#language#programming#linux#exams#coding#software engineering#coding for beginners#careers#course#training#learning#education#technology#computing#tech news#business#security#futurism#Youtube
2 notes
·
View notes
Text
Blogg post #7 - Creating my Final Instrument
As part of our upcoming "Best of Booth" event on June 7th, I’ve started a unique final project that showcases everything I’ve learned in Max MSP over the past six months. The project revolves around creating a distinctive musical instrument for my performance, using live recordings of the djembe drum.
The core idea is to develop a patch that can sort these recordings into sample files and then play them back in polyrhythmic forms, essentially mimicking a djembe player. My djembe, a solo model, will be used for playing fills over the percussion sequences, triggering laser lights to enhance the visual aspect of the performance.
One of the main challenges is ensuring the patch isn’t too large to prevent my computer from crashing. With numerous processes running simultaneously, I’m considering using two computers to manage the load effectively. Another challenge is devising a way to change up the lighting show so it feels both natural and unexpected.
Here’s a breakdown of my current progress and plans:
Objective:
Initially, my goal was to trigger the venue's unique lights with a drum for our event. However, I’ve decided to complicate things slightly to simplify the drumming aspect for myself, as I’m not a seasoned djembe player.
Current Progress:
Inspired by a tutorial from UMUT Hearing Glass—a channel I highly recommend—I’ve developed a polyrhythmic generator. This system allows you to input a sample into one or more boxes, where a clock (which you can adjust) plays the sample in varying lengths. Currently, the system randomizes the sample length with each trigger, creating dynamic polyrhythms.
Lighting Patch:
The patch for controlling the lights is a bit more complex. It’s still under development, but the plan is to integrateing the Polyrymic patch with the Lighthing Patch. This will give me three weeks to practice and fine-tune the system, ensuring it’s engaging and reliable.
Potential of the Patch:
This project could fill several important gaps in the market if i would like to further develop it.
It eliminates the need for a lighting specialist/VDJ to control lighting, as the artist can manage this through triggers like MIDI, automation, or sound transients.
It enhances the artistic experience by directly linking the music and lighting, allowing for a more immersive atmosphere.
It simplifies the control interface, making it more adaptable and user-friendly.
Future Steps:
Before considering a public release, I need to:
Test the system extensively to ensure reliability, which involves accessing enough DMX lights to fill a DMX universe (512 channels).
Develop a user-friendly interface.
Find an affordable yet functional DMX unit.
Add lighting fixtures to the library, explaining each DMX channel's function.
I’m excited about the potential of this project and look forward to seeing how it evolves in the coming weeks.
3 notes
·
View notes
Text
All-in-One Software for Managing Your Library

Revolutionise your library operations with seamless book management, real-time updates, and automated reminders. LDT Technology provides a bespoke Library Management System to streamline your library's efficiency. Book your demo now and empower your firm with the latest technology!
0 notes
Text
How Litigation Management System Helps in Managing Lawsuits
Litigation management system is the best solution for lawyers that have been created to help organize and automate all the tasks or work related to cases of the legal department. Its main feature includes eDiscovery, document management, legal research library, workflow automation, calendaring, contact management, and many more. In this article, you will know how effectively lawyers can manage their lawsuits with litigation management software.
#litigation management system#litigation management#system#litigation management software#software#litigation software#litigation
2 notes
·
View notes
Text
Java's Lasting Impact: A Deep Dive into Its Wide Range of Applications
Java programming stands as a towering pillar in the world of software development, known for its versatility, robustness, and extensive range of applications. Since its inception, Java has played a pivotal role in shaping the technology landscape. In this comprehensive guide, we will delve into the multifaceted world of Java programming, examining its wide-ranging applications, discussing its significance, and highlighting how ACTE Technologies can be your guiding light in mastering this dynamic language.

The Versatility of Java Programming:
Java programming is synonymous with adaptability. It's a language that transcends boundaries and finds applications across diverse domains. Here are some of the key areas where Java's versatility shines:
1. Web Development: Java has long been a favorite choice for web developers. Robust and scalable, it powers dynamic web applications, allowing developers to create interactive and feature-rich websites. Java-based web frameworks like Spring and JavaServer Faces (JSF) simplify the development of complex web applications.
2. Mobile App Development: The most widely used mobile operating system in the world, Android, mainly relies on Java for app development. Java's "write once, run anywhere" capability makes it an ideal choice for creating Android applications that run seamlessly on a wide range of devices.
3. Desktop Applications: Java's Swing and JavaFX libraries enable developers to craft cross-platform desktop applications with sophisticated graphical user interfaces (GUIs). This cross-platform compatibility ensures that your applications work on Windows, macOS, and Linux.
4. Enterprise Software: Java's strengths in scalability, security, and performance make it a preferred choice for developing enterprise-level applications. Customer Relationship Management (CRM) systems, Enterprise Resource Planning (ERP) software, and supply chain management solutions often rely on Java to deliver reliability and efficiency.
5. Game Development: Java isn't limited to business applications; it's also a contender in the world of gaming. Game developers use Java, along with libraries like LibGDX, to create both 2D and 3D games. The language's versatility allows game developers to target various platforms.
6. Big Data and Analytics: Java plays a significant role in the big data ecosystem. Popular frameworks like Apache Hadoop and Apache Spark utilize Java for processing and analyzing massive datasets. Its performance capabilities make it a natural fit for data-intensive tasks.
7. Internet of Things (IoT): Java's ability to run on embedded devices positions it well for IoT development. It is used to build applications for smart homes, wearable devices, and industrial automation systems, connecting the physical world to the digital realm.
8. Scientific and Research Applications: In scientific computing and research projects, Java's performance and libraries for data analysis make it a valuable tool. Researchers leverage Java to process and analyze data, simulate complex systems, and conduct experiments.
9. Cloud Computing: Java is a popular choice for building cloud-native applications and microservices. It is compatible with cloud platforms such as AWS, Azure, and Google Cloud, making it integral to cloud computing's growth.

Why Java Programming Matters:
Java programming's enduring significance in the tech industry can be attributed to several compelling reasons:
Platform Independence: Java's "write once, run anywhere" philosophy allows code to be executed on different platforms without modification. This portability enhances its versatility and cost-effectiveness.
Strong Ecosystem: Java boasts a rich ecosystem of libraries, frameworks, and tools that expedite development and provide solutions to a wide range of challenges. Developers can leverage these resources to streamline their projects.
Security: Java places a strong emphasis on security. Features like sandboxing and automatic memory management enhance the language's security profile, making it a reliable choice for building secure applications.
Community Support: Java enjoys the support of a vibrant and dedicated community of developers. This community actively contributes to its growth, ensuring that Java remains relevant, up-to-date, and in line with industry trends.
Job Opportunities: Proficiency in Java programming opens doors to a myriad of job opportunities in software development. It's a skill that is in high demand, making it a valuable asset in the tech job market.
Java programming is a dynamic and versatile language that finds applications in web and mobile development, enterprise software, IoT, big data, cloud computing, and much more. Its enduring relevance and the multitude of opportunities it offers in the tech industry make it a valuable asset in a developer's toolkit.
As you embark on your journey to master Java programming, consider ACTE Technologies as your trusted partner. Their comprehensive training programs, expert guidance, and hands-on experiences will equip you with the skills and knowledge needed to excel in the world of Java development.
Unlock the full potential of Java programming and propel your career to new heights with ACTE Technologies. Whether you're a novice or an experienced developer, there's always more to discover in the world of Java. Start your training journey today and be at the forefront of innovation and technology with Java programming.
8 notes
·
View notes