#integrated library automation system
Explore tagged Tumblr posts
Text

Level Up Your Library with a Modern Library Management System
Organise books, streamline workflows, and empower users—all in one go! Discover an innovative approach to library organisation and patron satisfaction with our advanced library management system. Partner with us to unlock the full potential of your library!
0 notes
Text
The enshittification of garage-door openers reveals a vast and deadly rot

I'll be at the Studio City branch of the LA Public Library on Monday, November 13 at 1830hPT to launch my new novel, The Lost Cause. There'll be a reading, a talk, a surprise guest (!!) and a signing, with books on sale. Tell your friends! Come on down!

How could this happen? Owners of Chamberlain MyQ automatic garage door openers just woke up to discover that the company had confiscated valuable features overnight, and that there was nothing they could do about it.
Oh, we know what happened, technically speaking. Chamberlain shut off the API for its garage-door openers, which breaks their integration with home automation systems like Home Assistant. The company even announced that it was doing this, calling the integration an "unauthorized usage" of its products, though the "unauthorized" parties in this case are the people who own Chamberlain products:
https://chamberlaingroup.com/press/a-message-about-our-decision-to-prevent-unauthorized-usage-of-myq
We even know why Chamberlain did this. As Ars Technica's Ron Amadeo points out, shutting off the API is a way for Chamberlain to force its customers to use its ad-beshitted, worst-of-breed app, so that it can make a few pennies by nonconsensually monetizing its customers' eyeballs:
https://arstechnica.com/gadgets/2023/11/chamberlain-blocks-smart-garage-door-opener-from-working-with-smart-homes/
But how did this happen? How did a giant company like Chamberlain come to this enshittening juncture, in which it felt empowered to sabotage the products it had already sold to its customers? How can this be legal? How can it be good for business? How can the people who made this decision even look themselves in the mirror?
To answer these questions, we must first consider the forces that discipline companies, acting against the impulse to enshittify their products and services. There are four constraints on corporate conduct:
I. Competition. The fear of losing your business to a rival can stay even the most sociopathic corporate executive's hand.
II. Regulation. The fear of being fined, criminally sanctioned, or banned from doing business can check the greediest of leaders.
III. Capability. Corporate executives can dream up all kinds of awful ways to shift value from your side of the ledger to their own, but they can only do the things that are technically feasible.
IV. Self-help. The possibility of customers modifying, reconfiguring or altering their products to restore lost functionality or neutralize antifeatures carries an implied threat to vendors. If a printer company's anti-generic-ink measures drives a customer to jailbreak their printers, the original manufacturer's connection to that customer is permanently severed, as the customer creates a durable digital connection to a rival.
When companies act in obnoxious, dishonest, shitty ways, they aren't merely yielding to temptation – they are evading these disciplining forces. Thus, the Great Enshittening we are living through doesn't reflect an increase in the wickedness of corporate leadership. Rather, it represents a moment in which each of these disciplining factors have been gutted by specific policies.
This is good news, actually. We used to put down rat poison and we didn't have a rat problem. Then we stopped putting down rat poison and rats are eating us alive. That's not a nice feeling, but at least we know at least one way of addressing it – we can start putting down poison again. That is, we can start enforcing the rules that we stopped enforcing, in living memory. Having a terrible problem is no fun, but the best kind of terrible problem to have is one that you know a solution to.
As it happens, Chamberlain is a neat microcosm for all the bad policy choices that created the Era of Enshittification. Let's go through them:
Competition: Chamberlain doesn't have to worry about competition, because it is owned by a private equity fund that "rolled up" all of Chamberlain's major competitors into a single, giant firm. Most garage-door opener brands are actually Chamberlain, including "LiftMaster, Chamberlain, Merlin, and Grifco":
https://www.lakewoodgaragedoor.biz/blog/the-history-of-garage-door-openers
This is a pretty typical PE rollup, and it exploits a bug in US competition law called "Antitrust's Twilight Zone":
https://pluralistic.net/2022/12/16/schumpeterian-terrorism/#deliberately-broken
When companies buy each other, they are subject to "merger scrutiny," a set of guidelines that the FTC and DoJ Antitrust Division use to determine whether the outcome is likely to be bad for competition. These rules have been pretty lax since the Reagan administration, but they've currently being revised to make them substantially more strict:
https://www.justice.gov/opa/pr/justice-department-and-ftc-seek-comment-draft-merger-guidelines
One of the blind spots in these merger guidelines is an exemption for mergers valued at less than $101m. Under the Hart-Scott-Rodino Act, these fly under the radar, evading merger scrutiny. That means that canny PE companies can roll up dozens and dozens of standalone businesses, like funeral homes, hospital beds, magic mushrooms, youth addiction treatment centers, mobile home parks, nursing homes, physicians’ practices, local newspapers, or e-commerce sellers:
http://www.economicliberties.us/wp-content/uploads/2022/12/Serial-Acquisitions-Working-Paper-R4-2.pdf
By titrating the purchase prices, PE companies – like Blackstone, owners of Chamberlain and all the other garage-door makers – can acquire a monopoly without ever raising a regulatory red flag.
But antitrust enforcers aren't helpless. Under (the long dormant) Section 7 of the Clayton Act, competition regulators can block mergers that lead to "incipient monopolization." The incipiency standard prevented monopolies from forming from 1914, when the Clayton Act passed, until the Reagan administration. We used to put down rat poison, and we didn't have rats. We stopped, and rats are gnawing our faces off. We still know where the rat poison is – maybe we should start putting it down again.
On to regulation. How is it possible for Chamberlain to sell you a garage-door opener that has an API and works with your chosen home automation system, and then unilaterally confiscate that valuable feature? Shouldn't regulation protect you from this kind of ripoff?
It should, but it doesn't. Instead, we have a bunch of regulations that protect Chamberlain from you. Think of binding arbitration, which allows Chamberlain to force you to click through an "agreement" that takes away your right to sue them or join a class-action suit:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
But regulation could protect you from Chamberlain. Section 5 of the Federal Trade Commission Act allows the FTC to ban any "unfair and deceptive" conduct. This law has been on the books since 1914, but Section 5 has been dormant, forgotten and unused, for decades. The FTC's new dynamo chair, Lina Khan, has revived it, and is use it like a can-opener to free Americans who've been trapped by abusive conduct:
https://pluralistic.net/2023/01/10/the-courage-to-govern/#whos-in-charge
Khan's used Section 5 powers to challenge privacy invasions, noncompete clauses, and other corporate abuses – the bait-and-switch tactics of Chamberlain are ripe for a Section 5 case. If you buy a gadget because it has five features and then the vendor takes two of them away, they are clearly engaged in "unfair and deceptive" conduct.
On to capability. Since time immemorial, corporate leaders have fetishized "flexibility" in their business arrangements – like the ability to do "dynamic pricing" that changes how much you pay for something based on their guess about how much you are willing to pay. But this impulse to play shell games runs up against the hard limits of physical reality: grocers just can't send an army of rollerskated teenagers around the store to reprice everything as soon as a wealthy or desperate-looking customer comes through the door. They're stuck with crude tactics like doubling the price of a flight that doesn't include a Saturday stay as a way of gouging business travelers on an expense account.
With any shell-game, the quickness of the hand deceives the eye. Corporate crooks armed with computers aren't smarter or more wicked than their analog forebears, but they are faster. Digital tools allow companies to alter the "business logic" of their services from instant to instant, in highly automated ways:
https://pluralistic.net/2023/02/19/twiddler/
The monopoly coalition has successfully argued that this endless "twiddling" should not be constrained by privacy, labor or consumer protection law. Without these constraints, corporate twiddlers can engage in all kinds of ripoffs, like wage theft and algorithmic wage discrimination:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
Twiddling is key to the Darth Vader MBA ("I am altering the deal. Pray I don't alter it further"), in which features are confiscated from moment to moment, without warning or recourse:
https://pluralistic.net/2023/10/26/hit-with-a-brick/#graceful-failure
There's no reason to accept the premise that violating your privacy, labor rights or consumer rights with a computer is so different from analog ripoffs that existing laws don't apply. The unconstrained twiddling of digital ripoff artists is a plague on billions of peoples' lives, and any enforcer who sticks up for our rights will have an army of supporters behind them.
Finally, there's the fear of self-help measures. All the digital flexibility that tech companies use to take value away can be used to take it back, too. The whole modern history of digital computers is the history of "adversarial interoperability," in which the sleazy antifeatures of established companies are banished through reverse-engineering, scraping, bots and other forms of technological guerrilla warfare:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Adversarial interoperability represents a serious threat to established business. If you're a printer company gouging on toner, your customers might defect to a rival that jailbreaks your security measures. That's what happened to Lexmark, who lost a case against the toner-refilling company Static Controls, which went on to buy Lexmark:
https://www.eff.org/deeplinks/2019/06/felony-contempt-business-model-lexmarks-anti-competitive-legacy
Sure, your customers are busy and inattentive and you can degrade the quality of your product a lot before they start looking for ways out. But once they cross that threshold, you can lose them forever. That's what happened to Microsoft: the company made the tactical decision to produce a substandard version of Office for the Mac in a drive to get Mac users to switch to Windows. Instead, Apple made Iwork (Pages, Numbers and Keynote), which could read and write every Office file, and Mac users threw away Office, the only Microsoft product they owned, permanently severing their relationship to the company:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
Today, companies can operate without worrying about this kind of self-help measure. There' a whole slew of IP rights that Chamberlain can enforce against you if you try to fix your garage-door opener yourself, or look to a competitor to sell you a product that restores the feature they took away:
https://locusmag.com/2020/09/cory-doctorow-ip/
Jailbreaking your Chamberlain gadget in order to make it answer to a rival's app involves bypassing a digital lock. Trafficking in a tool to break a digital lock is a felony under Section 1201 of the Digital Millennium Copyright, carrying a five-year prison sentence and a $500,000 fine.
In other words, it's not just that tech isn't regulated, allowing for endless twiddling against your privacy, consumer rights and labor rights. It's that tech is badly regulated, to permit unlimited twiddling by tech companies to take away your rightsand to prohibit any twiddling by you to take them back. The US government thumbs the scales against you, creating a regime that Jay Freeman aptly dubbed "felony contempt of business model":
https://pluralistic.net/2022/10/23/how-to-fix-cars-by-breaking-felony-contempt-of-business-model/
All kinds of companies have availed themselves of this government-backed superpower. There's DRM – digital locks, covered by DMCA 1201 – in powered wheelchairs:
https://www.eff.org/deeplinks/2022/06/when-drm-comes-your-wheelchair
In dishwashers:
https://pluralistic.net/2021/05/03/cassette-rewinder/#disher-bob
In treadmills:
https://pluralistic.net/2021/06/22/vapescreen/#jane-get-me-off-this-crazy-thing
In tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
It should come as no surprise to learn that Chamberlain has used DMCA 1201 to block interoperable garage door opener components:
https://scholarship.law.marquette.edu/cgi/viewcontent.cgi?article=1233&context=iplr
That's how we arrived at this juncture, where a company like Chamberlain can break functionality its customers value highly, solely to eke out a minuscule new line of revenue by selling ads on their own app.
Chamberlain bought all its competitors.
Chamberlain operates in a regulatory environment that is extremely tolerant of unfair and deceptive practices. Worse: they can unilaterally take away your right to sue them, which means that if regulators don't bestir themselves to police Chamberlain, you are shit out of luck.
Chamberlain has endless flexibility to unilaterally alter its products' functionality, in fine-grained ways, even after you've purchased them.
Chamberlain can sue you if you try to exercise some of that same flexibility to protect yourself from their bad practices.
Combine all four of those factors, and of course Chamberlain is going to enshittify its products. Every company has had that one weaselly asshole at the product-planning table who suggests a petty grift like breaking every one of the company's customers' property to sell a few ads. But historically, the weasel lost the argument to others, who argued that making every existing customer furious would affect the company's bottom line, costing it sales and/or fines, and prompting customers to permanently sever their relationship with the company by seeking out and installing alternative software. Take away all the constraints on a corporation's worst impulses, and this kind of conduct is inevitable:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
This isn't limited to Chamberlain. Without the discipline of competition, regulation, self-help measures or technological limitations, every industry in undergoing wholesale enshittification. It's not a coincidence that Chamberlain's grift involves a push to move users into its app. Because apps can't be reverse-engineered and modified without risking DMCA 1201 prosecution, forcing a user into an app is a tidy and reliable way to take away that user's rights.
Think about ad-blocking. One in four web users has installed an ad-blockers ("the biggest boycott in world history" -Doc Searls). Zero app users have installed app-blockers, because they don't exist, because making one is a felony. An app is just a web-page wrapped in enough IP to make it a crime to defend yourself against corporate predation:
https://pluralistic.net/2023/08/27/an-audacious-plan-to-halt-the-internets-enshittification-and-throw-it-into-reverse/
The temptation to enshitiffy isn't new, but the ability to do so without consequence is a modern phenomenon, the intersection of weak policy enforcement and powerful technology. Your car is autoenshittified, a rolling rent-seeking platform that spies on you and price-gouges you:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
Cars are in an uncontrolled skid over Enshittification Cliff. Honda, Toyota, VW and GM all sell cars with infotainment systems that harvest your connected phone's text-messages and send them to the corporation for data-mining. What's more, a judge in Washington state just ruled that this is legal:
https://therecord.media/class-action-lawsuit-cars-text-messages-privacy
While there's no excuse for this kind of sleazy conduct, we can reasonably anticipate that if our courts would punish companies for engaging in it, they might be able to resist the temptation. No wonder Mozilla's latest Privacy Not Included research report called cars "the worst product category we have ever reviewed":
https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
I mean, Nissan tries to infer facts about your sex life and sells those inferences to marketing companies:
https://foundation.mozilla.org/en/privacynotincluded/nissan/
But the OG digital companies are the masters of enshittification. Microsoft has been at this game for longer than anyone, and every day brings a fresh way that Microsoft has worsened its products without fear of consequence. The latest? You can't delete your OneDrive account until you provide an acceptable explanation for your disloyalty:
https://www.theverge.com/2023/11/8/23952878/microsoft-onedrive-windows-close-app-notification
It's tempting to think that the cruelty is the point, but it isn't. It's almost never the point. The point is power and money. Unscrupulous businesses have found ways to make money by making their products worse since the industrial revolution. Here's Jules Dupuis, writing about 19th century French railroads:
It is not because of the few thousand francs which would have to be spent to put a roof over the third-class carriages or to upholster the third-class seats that some company or other has open carriages with wooden benches. What the company is trying to do is to prevent the passengers who can pay the second class fare from traveling third class; it hits the poor, not because it wants to hurt them, but to frighten the rich. And it is again for the same reason that the companies, having proved almost cruel to the third-class passengers and mean to the second-class ones, become lavish in dealing with first-class passengers. Having refused the poor what is necessary, they give the rich what is superfluous.
https://www.tumblr.com/mostlysignssomeportents/731357317521719296/having-refused-the-poor-what-is-necessary-they
But as bad as all this is, let me remind you about the good part: we know how to stop companies from enshittifying their products. We know what disciplines their conduct: competition, regulation, capability and self-help measures. Yes, rats are gnawing our eyeballs, but we know which rat-poison to use, and where to put it to control those rats.
Competition, regulation, constraint and self-help measures all backstop one another, and while one or a few can make a difference, they are most powerful when they're all mobilized in concert. Think of the failure of the EU's landmark privacy law, the GDPR. While the GDPR proved very effective against bottom-feeding smaller ad-tech companies, the worse offenders, Meta and Google, have thumbed their noses at it.
This was enabled in part by the companies' flying an Irish flag of convenience, maintaining the pretense that they have to be regulated in a notorious corporate crime-haven:
https://pluralistic.net/2023/05/15/finnegans-snooze/#dirty-old-town
That let them get away with all kinds of shenanigans, like ignoring the GDPR's requirement that you should be able to easily opt out of data-collection without having to go through cumbersome "cookie consent" dialogs or losing access to the service as punishment for declining to be tracked.
As the noose has tightened around these surveillance giants, they're continuing to play games. Meta now says that the only way to opt out of data-collection in the EU is to pay for the service:
https://pluralistic.net/2023/10/30/markets-remaining-irrational/#steins-law
This is facially illegal under the GDPR. Not only are they prohibited from punishing you for opting out of collection, but the whole scheme ignores the nature of private data collection. If Facebook collects the fact that you and I are friends, but I never opted into data-collection, they have violated the GDPR, even if you were coerced into granting consent:
https://www.nakedcapitalism.com/2023/11/the-pay-or-consent-challenge-for-platform-regulators.html
The GDPR has been around since 2016 and Google and Meta are still invading 500 million Europeans' privacy. This latest delaying tactic could add years to their crime-spree before they are brought to justice.
But most of this surveillance is only possible because so much of how you interact with Google and Meta is via an app, and an app is just a web-page that's a felony to make an ad-blocker for. If the EU were to legalize breaking DRM – repealing Article 6 of the 2001 Copyright Directive – then we wouldn't have to wait for the European Commission to finally wrestle these two giant companies to the ground. Instead, EU companies could make alternative clients for all of Google and Meta's services that don't spy on you, without suffering the fate of OG App, which tried this last winter and was shut down by "felony contempt of business model":
https://pluralistic.net/2023/02/05/battery-vampire/#drained
Enshittification is demoralizing. To quote @wilwheaton, every update to the services we use inspires "dread of 'How will this complicate things as I try to maintain privacy and sanity in a world that demands I have this thing to operate?'"
https://wilwheaton.tumblr.com/post/698603648058556416/cory-doctorow-if-you-see-this-and-have-thoughts
But there are huge natural constituencies for the four disciplining forces that keep enshittification at bay.
Remember, Antitrust's Twilight Zone doesn't just allow rollups of garage-door opener companies – it's also poison for funeral homes, hospital beds, magic mushrooms, youth addiction treatment centers, mobile home parks, nursing homes, physicians’ practices, local newspapers, or e-commerce sellers.
The Binding Arbitration scam that stops Chamberlain customers from suing the company also stops Uber drivers from suing over stolen wages, Turbotax customers from suing over fraud, and many other victims of corporate crime from getting a day in court.
The failure to constrain twiddling to protect privacy, labor rights and consumer rights enables a host of abuses, from stalking, doxing and SWATting to wage theft and price gouging:
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
And Felony Contempt of Business Model is used to screw you over every time you refill your printer, run your dishwasher, or get your Iphone's screen replaced.
The actions needed to halt and reverse this enshittification are well understood, and the partisans for taking those actions are too numerous to count. It's taken a long time for all those individuals suffering under corporate abuses to crystallize into a movement, but at long last, it's happening.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#monopolists#anticircumvention#myq#home assistant#pay or consent#enshittification#surveillance#autoenshittification#privacy#self-help measures#microsoft#onedrive#twiddling#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#felony contempt of business model#darth vader mba
376 notes
·
View notes
Text

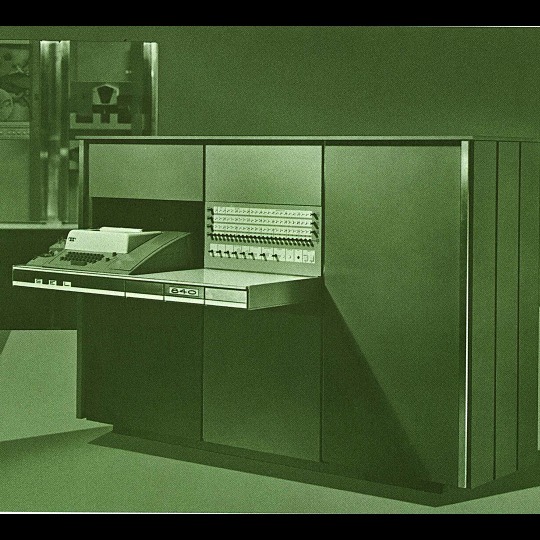




🎄💾🗓️ Day 11: Retrocomputing Advent Calendar - The SEL 840A🎄💾🗓️
Systems Engineering Laboratories (SEL) introduced the SEL 840A in 1965. This is a deep cut folks, buckle in. It was designed as a high-performance, 24-bit general-purpose digital computer, particularly well-suited for scientific and industrial real-time applications.
Notable for using silicon monolithic integrated circuits and a modular architecture. Supported advanced computation with features like concurrent floating-point arithmetic via an optional Extended Arithmetic Unit (EAU), which allowed independent arithmetic processing in single or double precision. With a core memory cycle time of 1.75 microseconds and a capacity of up to 32,768 directly addressable words, the SEL 840A had impressive computational speed and versatility for its time.
Its instruction set covered arithmetic operations, branching, and program control. The computer had fairly robust I/O capabilities, supporting up to 128 input/output units and optional block transfer control for high-speed data movement. SEL 840A had real-time applications, such as data acquisition, industrial automation, and control systems, with features like multi-level priority interrupts and a real-time clock with millisecond resolution.
Software support included a FORTRAN IV compiler, mnemonic assembler, and a library of scientific subroutines, making it accessible for scientific and engineering use. The operator’s console provided immediate access to registers, control functions, and user interaction! Designed to be maintained, its modular design had serviceability you do often not see today, with swing-out circuit pages and accessible test points.
And here's a personal… personal computer history from Adafruit team member, Dan…
== The first computer I used was an SEL-840A, PDF:
I learned Fortran on it in eight grade, in 1970. It was at Oak Ridge National Laboratory, where my parents worked, and was used to take data from cyclotron experiments and perform calculations. I later patched the Fortran compiler on it to take single-quoted strings, like 'HELLO', in Fortran FORMAT statements, instead of having to use Hollerith counts, like 5HHELLO.
In 1971-1972, in high school, I used a PDP-10 (model KA10) timesharing system, run by BOCES LIRICS on Long Island, NY, while we were there for one year on an exchange.
This is the front panel of the actual computer I used. I worked at the computer center in the summer. I know the fellow in the picture: he was an older high school student at the time.
The first "personal" computers I used were Xerox Alto, Xerox Dorado, Xerox Dandelion (Xerox Star 8010), Apple Lisa, and Apple Mac, and an original IBM PC. Later I used DEC VAXstations.
Dan kinda wins the first computer contest if there was one… Have first computer memories? Post’em up in the comments, or post yours on socialz’ and tag them #firstcomputer #retrocomputing – See you back here tomorrow!
#retrocomputing#firstcomputer#electronics#sel840a#1960scomputers#fortran#computinghistory#vintagecomputing#realtimecomputing#industrialautomation#siliconcircuits#modulararchitecture#floatingpointarithmetic#computerscience#fortrancode#corememory#oakridgenationallab#cyclotron#pdp10#xeroxalto#computermuseum#historyofcomputing#classiccomputing#nostalgictech#selcomputers#scientificcomputing#digitalhistory#engineeringmarvel#techthroughdecades#console
31 notes
·
View notes
Text



Kia ora! Just a wee re-introduction
I'm just another solarpunk in Aotearoa looking for other like-minded friends, inspiration, and advice on other ways I can green up my life. I love sewing, baking, making, gardening, and animals.
I live in an off-grid tiny home I built with my partner in 2016 out of wood and second-hand windows/doors/appliances. We run off solar power, rain water, a composting toilet, and try to repair, mend, make, borrow, and buy 2nd hand or local. Our meat is all hunted, which here in Aotearoa is a huge help for our environment as our only native mammals are seals and bats. Everything else is a pest. We also grow a lot of our own fruit and veggies, but the garden is still a work in progress. This year, i have a new wing of the veggie garden built, but I still have so much work to do around the herb and fairy garden.
I'm looking at irrigating the garden and automating the process. I saw something about https://www.home-assistant.io/ online but would love any advice you might have. I'd like to automate and chart my watering as well as integrate moisture monitors and a weather monitoring system.
I have an electric bike and an old 1996 honda crv. I'd like to switch to an electric vehicle, something like a Pickman 4x4 or another small farm vehicle, as I only need to get to the village bus stop, neighbouring farms, and the occasional trip into town via back roads.
Clothes are me-made with 2nd hand materials, mostly from the dump shop. I've helped start a collection point for alternative recycling like bottle lids and tetrapaks, a library of things, and a community workshop. We are working towards a bike repair hub and time bank but it might be a couple years before they are operational.
Please share all your inspiration, book recommendations, and thoughts around other ways I can make an impact in my community 😊
20 notes
·
View notes
Text
The Talon Roost
Nestled along the rugged shoreline of Puget Sound, just outside the bustling heart of Unity City, Terra, Melissa Hazen and Theodora Marten-Steiner’s home exudes a warmth and intimacy that starkly contrasts with their imposing public personas. Known as “The Talon Roost,” this sprawling lodge combines the rustic charm of traditional log cabin architecture with the subtle integration of cutting-edge technology from Terra’s civilian sector.
The Talon Roost sits perched on a rocky bluff overlooking the Sound, its timbered exterior blending with the surrounding forest. Massive, hand-hewn logs form the structure’s frame, their natural grain and texture preserved to honor the timeless beauty of the Pacific Northwest. The lodge’s roof is made up of a mix of eco-friendly solar tiles and living greenery. Wide wraparound decks extend from the main structure, offering panoramic views of the water and mountains beyond. A series of cascading stairs, lined with ambient lighting, leads down to a private dock where a sleek, automated watercraft rests, flanked by kayaks and a small security boat. At night, the lodge glows warmly, its large windows offering glimpses of life inside—a sharp yet inviting contrast to the quiet wilderness outside.
Entering the Talon Roost feels like stepping into a sanctuary. High vaulted ceilings, supported by massive wooden beams, create a sense of openness, while large floor-to-ceiling windows flood the space with natural light during the day. The interior décor balances modern minimalist design with the cozy aesthetics of a mountain lodge. Neutral tones dominate, accented by vibrant greens and golds—an homage to Melissa’s Jade Falcon heritage. The heart of the lodge, the living room, is anchored by a double-sided fireplace made of locally quarried stone. The hearth radiates warmth, surrounded by plush sofas and armchairs adorned with patterned blankets and throw pillows. Above the fireplace, a holographic display can project serene landscapes or serve as an entertainment hub, though it’s often turned off, leaving the room in serene simplicity. The kitchen combines the rustic appeal of handcrafted cabinetry with state-of-the-art appliances. A long central island, topped with polished stone, doubles as a communal dining space. The open floor plan flows into the dining area, where a custom-built table—crafted from salvaged driftwood—sits beneath an impressive chandelier of crystal and wrought iron. A cozy library, lined with shelves of books and historical texts, offers a quiet retreat for both Melissa and Theodora. A vintage mahogany desk sits at the far end, equipped with a concealed holo-terminal for secure communication and work. Nearby, a comfortable reading nook overlooks the Sound, with a soft chair and a small table perpetually holding a steaming pot of tea. The large, lavish, and highly advanced home theater was Theodora's pet project - it is outfitted with the absolute latest in cutting-edge holographic, trideo, and flat screen projection technology as well as a sound system that cost nearly as much as a light BattleMech.
While The Talon Roost appears traditional, its technology is anything but. Discrete panels throughout the home provide instant access to climate control, security systems, and personal AI assistants. The lodge’s power is supplied by a combination of renewable sources, ensuring self-sufficiency even during extended outages. A secure Star League-era communication hub is integrated into the study, allowing Melissa and Theodora to stay connected with SLDF operations. Beneath the lodge, hidden from view, lies a private hangar with bays large enough for both Melissa’s Highlander and Theodora’s Atlas, as well as the company of security 'Mechs on-site. Advanced automated repair systems and diagnostic tools ensure the 'Mechs are always ready for action. Also included is a multi-functional room utilizing advanced Holotank technology capable of projecting tactical simulations, training environments, or serene natural landscapes for relaxation.
The grounds around the lodge are meticulously curated. A path winds through a grove of ancient cedar trees to a private firepit surrounded by log benches. Nearby, a greenhouse houses a mix of local flora and medicinal plants, along with herbs for Theodora’s favorite recipes. A falconry mew, discreetly tucked into the edge of the property, is home to a small cast of Jade Falcons whom Melissa tends to personally—a connection to her heritage and a calming pastime away from the demands of leadership. The Talon Roost’s atmosphere is one of quiet strength and serenity. For two figures as legendary as Melissa Hazen and Theodora Marten-Steiner, the lodge represents a refuge from the chaos of the Inner Sphere—a place to reconnect with nature, their shared history, and each other. The cozy interiors, paired with the breathtaking natural surroundings, create a space where visitors are immediately put at ease, despite the immense power and influence of its owners. This dichotomy—between public and private life, between war and peace—is what makes The Talon Roost not just a home, but a reflection of the lives Melissa and Theodora have built together.
While The Talon Roost exudes an aura of peace and natural harmony, its security infrastructure rivals that of any high-level military installation. As the personal residence of two high-ranking SLDF officers, it incorporates layers of cutting-edge technology, physical deterrents, and personnel to ensure the safety of its occupants and maintain its strategic utility. The property is surrounded by an invisible perimeter system that utilizes advanced motion detection, thermal imaging, and seismic sensors. Any unauthorized entry triggers both silent and audible alarms, alerting the SLDF garrison stationed nearby. Discrete but highly effective automated turrets, hidden in the rocky outcroppings and among the trees, are equipped with non-lethal crowd control measures and high-powered laser weaponry for more extreme threats. Signature reduction technology derived from Null Signature System technology shields The Talon Roost from all but visual aerial and orbital scans, while a squadron of SLDF-designed surveillance drones patrols the airspace and property boundary. These drones are equipped with stealth tech, high-resolution cameras, and lethal weaponry. Meanwhile, the picturesque firepit near the cedar grove doubles as an emergency bunker entrance, reinforced to withstand even orbital bombardment. Decorative stone statues around the property conceal sensors and emitters capable of deploying small scale energy weapons in emergencies.
The Talon Roost is protected by a small, elite detachment of SLDF Royal Black Watch troops. While their presence is unobtrusive, they are always ready to respond to any threat. The guard detachment includes three Stars of MechWarriors, with their BattleMechs stationed in the Roost's subterranean hangar. A company of infantry, drawn from the Royal Black Watch's commando-trained operatives, patrols the property and acts as a rapid reaction force. All on-site security personnel reside in a concealed bunker built into the cliffside upon which the Roost perches. Security details rotate regularly to maintain optimal readiness and avoid becoming predictable. A concealed, automated command center under the lodge handles all security and monitoring tasks. Operatives stationed here can communicate directly with SLDF High Command and deploy additional resources as needed.
Beneath The Talon Roost lies a complex network of subterranean tunnels, elevators, and passageways that connect the property to critical SLDF and Star League installations in the region. This link allows both Melissa and Theodora to access secure meeting rooms or emergency operations centers without requiring surface travel. A direct maglev transit tunnel leads to both the nearby Tacoma Castle Brian, as well as the SLDF's Citadel inside Unity City itself - rebuilt by the SLDF to once again serve as their High Command complex. The headquarters of the Royal Black Watch, Fort Cameron, is linked to the lodge by another high-speed maglev route. The connection allows Theodora to oversee her regiment's activities or deploy her Atlas in minutes. The lodge is also connected via the maglev-tunnel system directly to the Court of the Star League.
In the event of an overwhelming threat, the lodge’s subterranean systems include a concealed evacuation pod capable of transporting occupants to either the Citadel or Fort Cameron in under five minutes. The lodge also features a last-resort self-destruct mechanism. Activated only by voice authorization from Melissa or Theodora, this system ensures no critical technology or data can fall into enemy hands. In case of a siege, the lodge can deploy automated counter-battery defenses, jamming fields, and active missile interceptors hidden within the terrain.
While The Talon Roost offers warmth, serenity, and a welcoming atmosphere, its hidden security and strategic capabilities reflect the immense responsibilities carried by its owners. This stark juxtaposition mirrors the lives of Melissa Hazen and Theodora Marten-Steiner, who must balance their personal sanctuary with their duties as protectors of humanity’s future. It is a place of respite, but one always ready for the call to action.
7 notes
·
View notes
Text
Why Sabaragamuwa University is a Great Choice.
Sabaragamuwa University of Sri Lanka (SUSL) is increasingly recognized for its technological advancement and innovation-driven environment, making it one of the leading universities in Sri Lanka in terms of technology. Here are the key reasons why SUSL stands out technologically.

Here’s why SUSL stands out as a technological powerhouse among Sri Lankan universities:
🔧1. Faculty of Technology
SUSL established a dedicated Faculty of Technology to meet the demand for tech-skilled graduates. It offers degree programs such as:
BTech in Information and Communication Technology
BTech in Engineering Technology
These programs combine practical experience in labs, workshops and real-world projects with a strong theoretical foundation.
🖥️2. Advanced IT Infrastructure
SUSL has modern computer labs, smart classrooms, and high-speed internet access across campus.
A robust Learning Management System (LMS) supports online learning and hybrid education models.
Students and lecturers use tools like Moodle, Zoom, and Google Classroom effectively.
🤖 3. Innovation & AI Research Support
SUSL promotes AI, Machine Learning, IoT, and Data Science in student research and final-year projects.
Competitions like Hackathons and Innovative Research Symposia encourage tech-driven solutions.
Students develop apps, smart systems, and automation tools (e.g., Ceylon Power Tracker project).
🌐 4. Industry Collaboration and Internships
SUSL connects students with the tech industry through:
Internships at leading tech firms
Workshops led by industry experts
Collaborative R&D projects with government and private sector entities
These connections help students gain hands-on experience in areas such as software engineering, networking, and data analytics that make them highly employable after graduation.
💡 5. Smart Campus Initiatives
SUSL is evolving into a Smart University, introducing systems that streamline academic life:
Digital student portals
Online registration and results systems
E-library and remote resource access
Campus Wi-Fi for academic use
These initiatives improve the student experience and create an efficient, technology-enabled environment.
🎓 6. Research in Emerging Technologies
The university is involved in pioneering research across emerging technological fields, including:
Agricultural tech (AgriTech)
Environmental monitoring using sensors
Renewable energy systems
Students and faculty publish research in international journals and participate in global tech events.
🏆 7. Recognition in National Competitions
SUSL students often reach fina rounds or win national competitions in coding, robotics, AI, and IoT innovation.
Faculty members are invited as tech advisors and conference speakers, reinforcing the university's expertise.
Sabaragamuwa University is actively shaping the future not only with technology, but by integrating technology into education, research and operations. This makes it a technological leader among Sri Lankan Universities. Visit the official university site here: Home | SUSL
2 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text
Image-Line FL Studio Producer Edition v21.2.3 Build [4004]

Image-Line FL Studio is a complete music production software environment or digital audio workstation (DAW). With more than 20 years of innovative developments, it combines everything you need for composing, arranging, recording, editing, mixing, and producing professional quality music.
Feature of FL Studio 21.2.3:
Record multiple tracks, stretch time, and bend notes with ease during editing.
Industry-leading piano roll lets you craft intricate melodies and control MIDI patterns like a maestro.
Multi-track mixer, automation control, and VST plugin support – mix and polish your tracks to perfection.
Create complex productions with ease. Effect chains, audio sends, sidechain control, advanced automation – it’s all here.
Experience the smoothest piano roll in the game. Edit notes, work with scores, and unleash your creative potential.
No DAW does playlist-ing like FL Studio. Sequence notes, audio, and automation freely, creating unique sonic tapestries.
Explore a massive library of native instruments and effects. Still not enough? Dive into the vast world of VST plugins.
Resize, rearrange, personalize – the user interface adapts to your workflow, not the other way around.
Record and edit automation in real-time, breathing life into your music.
Use FL Studio as a VST plugin or connect with ReWire for seamless integration.
FL Studio is designed for touch control, letting you express your creativity in a whole new way.
Powerful clip-triggering and intuitive controls unleash your inner DJ.
Context-sensitive guidance is always available with a simple press of F1.
Bind your MIDI controllers with ease, taking command of your sounds.
Render mesmerizing 4K videos directly from your FL Studio projects.
More Info
Version: v21.2.3 Build [4004]
Developer: Image-Line
Format: STANDALONE, VST
Bit depth: 64bit
Interface language: English, German, Spanish, French, Chinese.
System requirements: WIN 10+
Size: 1.23 GB
Installation:
Install FL.Studio.v21.2.3 [4004].exe
Install
Edison Declipper Windows.exe
FL Cloud mastering Windows.exe
Stem extractor Windows.exe
Download Setup
14 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
B.C. libraries have been targeted by a hacker who demanded a ransom or they would release user data that includes the phone numbers and email addresses of some clients.
The Cariboo Regional District says its library was among those involved, and data was obtained about users who received automated notifications from the library between March 27 and April 19.
t says it was informed of the breach last week by the BC Libraries Cooperative which provides integrated library systems for multiple institutions, and several library networks had been affected.
#librarylife#libraryland#library news#news article#british columbia#canada#cndpoli#bcpoli#public libraries#libraries
6 notes
·
View notes
Text
GetResponse the best email marketing software. Review: Features, Pros, and How It Stands Out
GetResponse is a comprehensive marketing automation platform that caters to businesses looking to streamline their marketing efforts. Known for its email marketing tools, GetResponse also offers a suite of other features that help businesses attract, engage, and convert customers. Here’s a detailed look at the features GetResponse offers and what sets it apart from competitors.
Minding Blowing Features:
1. Email Marketing
Drag-and-Drop Email Editor: GetResponse’s email editor allows users to create professional-looking emails without any coding knowledge. With a simple drag-and-drop interface, users can customize email templates to match their brand’s look and feel.
Personalized Email Content: Dynamic content features enable users to personalize emails for each recipient, boosting engagement rates and customer satisfaction.
Automation Features: With GetResponse’s automation tools, users can create workflows to automatically send emails based on triggers such as subscriber actions or specific dates.
2. Marketing Automation
Workflow Builder: This visual editor allows users to design workflows that automate repetitive tasks. For example, businesses can set up automated welcome emails, cart abandonment emails, or re-engagement campaigns.
Behavior Tracking: GetResponse’s automation system can track user actions and segment contacts based on behaviors, like which links they click or how long they spend on a landing page.
Lead Scoring: This feature helps businesses identify potential customers by assigning scores based on engagement, making it easier to target the most interested leads.
3. Landing Pages and Conversion Funnels
Landing Page Builder: With a library of customizable templates, the landing page builder makes it easy to create effective, high-converting pages. It includes features like split testing and SEO optimization to help improve performance.
Conversion Funnels: GetResponse offers pre-designed sales funnels that guide leads through each stage of the buyer’s journey, from lead capture to purchase. It’s a valuable tool for e-commerce businesses looking to maximize conversions.
Webinar Funnels: This feature is ideal for businesses that rely on webinars for lead generation. The webinar funnel helps users set up registration pages, send reminders, and automate follow-ups, making the entire process seamless.
4. Webinars
Built-In Webinar Tool: GetResponse is one of the few platforms that includes webinars as part of its marketing toolkit. Users can host live webinars, share files, and engage attendees with polls and Q&A sessions.
Webinar Analytics: After each session, GetResponse provides detailed analytics that help businesses understand engagement levels, attendee drop-off rates, and overall webinar success.
Follow-Up Automation: Automatically follow up with webinar attendees based on their participation. For example, you could send a thank-you email to those who attended and an on-demand recording link to those who missed it.
5. E-Commerce Features
Product Recommendation Engine: GetResponse integrates with e-commerce platforms to help businesses recommend products to customers based on past purchases.
Abandoned Cart Recovery: This feature allows businesses to reach out to customers who abandoned their carts, helping to recover potentially lost sales.
Integrated Payment Gateways: Users can set up product pages and directly integrate payment options, making it easy to sell products or services directly through GetResponse.
6. Advanced Analytics and Reporting
Email Analytics: GetResponse’s email analytics provide in-depth data on open rates, click-through rates, and bounce rates. Users can use this data to fine-tune their campaigns.
Conversion Funnel Analytics: Users can track every stage of their sales funnels to understand where leads drop off and make adjustments to improve conversion rates.
Customizable Reports: The platform offers customizable reports for different metrics, enabling businesses to get insights tailored to their specific goals.
Pros of Using GetResponse
All-in-One Platform: GetResponse offers a full suite of marketing tools, from email marketing to webinars and sales funnels, so users don’t have to juggle multiple tools.
User-Friendly Interface: Even for beginners, GetResponse’s interface is intuitive and easy to navigate.
Webinar Hosting: With built-in webinar capabilities, GetResponse stands out among other email marketing platforms, making it ideal for educational content, product demos, and more.
Advanced Segmentation and Targeting: The platform offers robust segmentation and automation tools, allowing for highly personalized and targeted marketing campaigns.
Excellent Customer Support: GetResponse is known for providing reliable customer support through live chat, email, and extensive online resources.
Cons of Using GetResponse
Pricing: Compared to some email-only platforms, GetResponse can be pricier due to its comprehensive feature set.
Complexity for Basic Users: For those who only need basic email marketing, GetResponse’s extensive features may feel overwhelming.
Learning Curve for Automation: While powerful, the automation builder can take some time to learn and optimize fully.
Who Should Use GetResponse?
GetResponse is ideal for:
Small to Medium Businesses: With its range of features, GetResponse is suitable for businesses looking to streamline and automate various aspects of their marketing efforts.
E-Commerce Businesses: With its e-commerce tools, abandoned cart recovery, and product recommendation engine, GetResponse provides essential features for online stores.
Content Creators and Educators: The built-in webinar tool makes it perfect for educators, coaches, and content creators who need to host virtual sessions and automate follow-ups.
Digital Marketers: GetResponse’s advanced segmentation and automation make it a valuable tool for digital marketers running multi-channel campaigns.
Conclusion: Is GetResponse Worth It?
For businesses looking for an all-in-one marketing solution that includes email marketing, automation, webinars, and e-commerce support, GetResponse is a strong contender. While it may have a learning curve, particularly in automation, its depth of features allows businesses to centralize their marketing activities in a single platform. Though slightly pricier than simpler email tools, its versatility and powerful capabilities justify the investment for businesses that need a comprehensive marketing solution.
2 notes
·
View notes
Text
All-in-One Software for Managing Your Library

Revolutionise your library operations with seamless book management, real-time updates, and automated reminders. LDT Technology provides a bespoke Library Management System to streamline your library's efficiency. Book your demo now and empower your firm with the latest technology!
0 notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
Unlock the Power of Python Programming: A Complete Guide
Python programming has become one of the most sought-after skills in the world of technology. Its simplicity, flexibility, and vast ecosystem of libraries make it a top choice for both beginners and experienced developers. In this guide, we will explore various aspects of Python programming, from basic concepts to advanced applications like machine learning and web development.
Python Programming: A Beginner-Friendly Language
Python programming is renowned for its readability and straightforward syntax, making it ideal for beginners. Whether you are just starting to code or transitioning from another language, Python offers a smooth learning curve. Key Python programming concepts include variables, data types, and control structures, which are essential for writing functional code.
youtube
Python Data Structures: Organizing Data Efficiently
One of the core strengths of Python programming is its rich set of data structures. Lists, dictionaries, tuples, and sets help you store and manage data effectively. Understanding Python data structures allows you to create more efficient programs by organizing and manipulating data effortlessly.
Functions in Python Programming: Building Reusable Code
Functions are a fundamental part of Python programming. They allow you to break down complex problems into smaller, reusable chunks of code. Python functions not only promote code reusability but also make your programs more organized and easier to maintain.
Loops in Python Programming: Automating Repeated Tasks
Loops are an essential feature in Python programming, allowing you to perform repeated operations efficiently. With Python loops such as for and while, you can iterate over sequences or perform tasks until a specific condition is met. Mastering loops is a key part of becoming proficient in Python.
Object-Oriented Programming in Python: Structured Development
Python programming supports object-oriented programming (OOP), a paradigm that helps you build structured and scalable software. OOP in Python allows you to work with classes and objects, making it easier to model real-world scenarios and design complex systems in a manageable way.
Python Automation Scripts: Simplify Everyday Tasks
Python programming can be used to automate repetitive tasks, saving you time and effort. Python automation scripts can help with file management, web scraping, and even interacting with APIs. With Python libraries like os and shutil, automation becomes a breeze.
Python Web Development: Creating Dynamic Websites
Python programming is also a popular choice for web development. Frameworks like Django and Flask make it easy to build robust, scalable web applications. Whether you're developing a personal blog or an enterprise-level platform, Python web development empowers you to create dynamic and responsive websites.
APIs and Python Programming: Connecting Services
Python programming allows seamless integration with external services through APIs. Using libraries like requests, you can easily interact with third-party services, retrieve data, or send requests. This makes Python an excellent choice for building applications that rely on external data or services.

Error Handling in Python Programming: Writing Resilient Code
Python programming ensures that your code can handle unexpected issues using error handling mechanisms. With try-except blocks, you can manage errors gracefully and prevent your programs from crashing. Error handling is a critical aspect of writing robust and reliable Python code.
Python for Machine Learning: Leading the AI Revolution
Python programming plays a pivotal role in machine learning, thanks to powerful libraries like scikit-learn, TensorFlow, and PyTorch. With Python, you can build predictive models, analyze data, and develop intelligent systems. Machine learning with Python opens doors to exciting opportunities in artificial intelligence and data-driven decision-making.
Python Data Science: Turning Data Into Insights
Python programming is widely used in data science for tasks such as data analysis, visualization, and statistical modeling. Libraries like pandas, NumPy, and Matplotlib provide Python programmers with powerful tools to manipulate data and extract meaningful insights. Python data science skills are highly in demand across industries.
Python Libraries Overview: Tools for Every Task
One of the greatest advantages of Python programming is its extensive library support. Whether you're working on web development, automation, data science, or machine learning, Python has a library for almost every need. Exploring Python libraries like BeautifulSoup, NumPy, and Flask can significantly boost your productivity.
Python GUI Development: Building User Interfaces
Python programming isn't just limited to back-end or web development. With tools like Tkinter and PyQt, Python programmers can develop graphical user interfaces (GUIs) for desktop applications. Python GUI development allows you to create user-friendly software with visual elements like buttons, text fields, and images.
Conclusion: Python Programming for Every Developer
Python programming is a versatile and powerful language that can be applied in various domains, from web development and automation to machine learning and data science. Its simplicity, combined with its extensive libraries, makes it a must-learn language for developers at all levels. Whether you're new to programming or looking to advance your skills, Python offers endless possibilities.
At KR Network Cloud, we provide expert-led training to help you master Python programming and unlock your potential. Start your Python programming journey today and take the first step toward a successful career in tech!
#krnetworkcloud#python#language#programming#linux#exams#coding#software engineering#coding for beginners#careers#course#training#learning#education#technology#computing#tech news#business#security#futurism#Youtube
2 notes
·
View notes
Text
Blogg post #7 - Creating my Final Instrument
As part of our upcoming "Best of Booth" event on June 7th, I’ve started a unique final project that showcases everything I’ve learned in Max MSP over the past six months. The project revolves around creating a distinctive musical instrument for my performance, using live recordings of the djembe drum.
The core idea is to develop a patch that can sort these recordings into sample files and then play them back in polyrhythmic forms, essentially mimicking a djembe player. My djembe, a solo model, will be used for playing fills over the percussion sequences, triggering laser lights to enhance the visual aspect of the performance.
One of the main challenges is ensuring the patch isn’t too large to prevent my computer from crashing. With numerous processes running simultaneously, I’m considering using two computers to manage the load effectively. Another challenge is devising a way to change up the lighting show so it feels both natural and unexpected.
Here’s a breakdown of my current progress and plans:
Objective:
Initially, my goal was to trigger the venue's unique lights with a drum for our event. However, I’ve decided to complicate things slightly to simplify the drumming aspect for myself, as I’m not a seasoned djembe player.
Current Progress:
Inspired by a tutorial from UMUT Hearing Glass—a channel I highly recommend—I’ve developed a polyrhythmic generator. This system allows you to input a sample into one or more boxes, where a clock (which you can adjust) plays the sample in varying lengths. Currently, the system randomizes the sample length with each trigger, creating dynamic polyrhythms.
Lighting Patch:
The patch for controlling the lights is a bit more complex. It’s still under development, but the plan is to integrateing the Polyrymic patch with the Lighthing Patch. This will give me three weeks to practice and fine-tune the system, ensuring it’s engaging and reliable.
Potential of the Patch:
This project could fill several important gaps in the market if i would like to further develop it.
It eliminates the need for a lighting specialist/VDJ to control lighting, as the artist can manage this through triggers like MIDI, automation, or sound transients.
It enhances the artistic experience by directly linking the music and lighting, allowing for a more immersive atmosphere.
It simplifies the control interface, making it more adaptable and user-friendly.
Future Steps:
Before considering a public release, I need to:
Test the system extensively to ensure reliability, which involves accessing enough DMX lights to fill a DMX universe (512 channels).
Develop a user-friendly interface.
Find an affordable yet functional DMX unit.
Add lighting fixtures to the library, explaining each DMX channel's function.
I’m excited about the potential of this project and look forward to seeing how it evolves in the coming weeks.
3 notes
·
View notes
Text
This Week in Rust 518
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Project/Tooling Updates
Strobe Crate
System dependencies are hard (so we made them easier)
Observations/Thoughts
Trying to invent a better substring search algorithm
Improving Node.js with Rust-Wasm Library
Mixing C# and Rust - Interop
A fresh look on incremental zero copy serialization
Make the Rust compiler 5% faster with this one weird trick
Part 3: Rowing Afloat Datatype Boats
Recreating concurrent futures combinators in smol
Unpacking some Rust ergonomics: getting a single Result from an iterator of them
Idea: "Using Rust", a living document
Object Soup is Made of Indexes
Analyzing Data 180,000x Faster with Rust
Issue #10: Serving HTML
Rust vs C on an ATTiny85; an embedded war story
Rust Walkthroughs
Analyzing Data /,000x Faster with Rust
Fully Automated Releases for Rust Projects
Make your Rust code unit testable with dependency inversion
Nine Rules to Formally Validate Rust Algorithms with Dafny (Part 2): Lessons from Verifying the range-set-blaze Crate
[video] Let's write a message broker using QUIC - Broke But Quick Episode 1
[video] Publishing Messages over QUIC Streams!! - Broke But Quick episode 2
Miscellaneous
[video] Associated types in Iterator bounds
[video] Rust and the Age of High-Integrity Languages
[video] Implementing (part of) a BitTorrent client in Rust
Crate of the Week
This week's crate is cargo-show-asm, a cargo subcommand to show the optimized assembly of any function.
Thanks to Kornel for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch (Hacktoberfest)- [FEATURE] separate payments_session from payments core * Hyperswitch (Hacktoberfest)- [NMI] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Airwallex] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Worldline] Use connector_response_reference_id as reference to merchant * Ockam - Make ockam project delete (no args) interactive by asking the user to choose from a list of space and project names to delete (tuify) * Ockam - Validate CBOR structs according to the cddl schema for authenticator/direct/types * Ockam - Slim down the NodeManagerWorker for node / node status
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
397 pull requests were merged in the last week
rewrite gdb pretty-printer registration
add FileCheck annotations to mir-opt tests
add MonoItems and Instance to stable_mir
add a csky-unknown-linux-gnuabiv2hf target
add a test showing failing closure signature inference in new solver
add new simpler and more explicit syntax for check-cfg
add stable Instance::body() and RustcInternal trait
automatically enable cross-crate inlining for small functions
avoid a track_errors by bubbling up most errors from check_well_formed
avoid having rustc_smir depend on rustc_interface or rustc_driver
coverage: emit mappings for unused functions without generating stubs
coverage: emit the filenames section before encoding per-function mappings
coverage: fix inconsistent handling of function signature spans
coverage: move most per-function coverage info into mir::Body
coverage: simplify the injection of coverage statements
disable missing_copy_implementations lint on non_exhaustive types
do not bold main message in --error-format=short
don't ICE when encountering unresolved regions in fully_resolve
don't compare host param by name
don't crash on empty match in the nonexhaustive_omitted_patterns lint
duplicate ~const bounds with a non-const one in effects desugaring
eliminate rustc_attrs::builtin::handle_errors in favor of emitting errors directly
fix a performance regression in obligation deduplication
fix implied outlives check for GAT in RPITIT
fix spans for removing .await on for expressions
fix suggestion for renamed coroutines feature
implement an internal lint encouraging use of Span::eq_ctxt
implement jump threading MIR opt
implement rustc part of RFC 3127 trim-paths
improve display of parallel jobs in rustdoc-gui tester script
initiate the inner usage of cfg_match (Compiler)
lint non_exhaustive_omitted_patterns by columns
location-insensitive polonius: consider a loan escaping if an SCC has member constraints applied only
make #[repr(Rust)] incompatible with other (non-modifier) representation hints like C and simd
make rustc_onunimplemented export path agnostic
mention into_iter on borrow errors suggestions when appropriate
mention the syntax for use on mod foo; if foo doesn't exist
panic when the global allocator tries to register a TLS destructor
point at assoc fn definition on type param divergence
preserve unicode escapes in format string literals when pretty-printing AST
properly account for self ty in method disambiguation suggestion
report unused_import for empty reexports even it is pub
special case iterator chain checks for suggestion
strict provenance unwind
suggest ; after bare match expression E0308
suggest constraining assoc types in more cases
suggest relaxing implicit type Assoc: Sized; bound
suggest removing redundant arguments in format!()
uplift movability and mutability, the simple way
miri: avoid a linear scan over the entire int_to_ptr_map on each deallocation
miri: fix rounding mode check in SSE4.1 round functions
miri: intptrcast: remove information about dead allocations
disable effects in libcore again
add #[track_caller] to Option::unwrap_or_else
specialize Bytes<R>::next when R is a BufReader
make TCP connect handle EINTR correctly
on Windows make read_dir error on the empty path
hashbrown: add low-level HashTable API
codegen_gcc: add support for NonNull function attribute
codegen_gcc: fix #[inline(always)] attribute and support unsigned comparison for signed integers
codegen_gcc: fix endianness
codegen_gcc: fix int types alignment
codegen_gcc: optimize popcount implementation
codegen_gcc: optimize u128/i128 popcounts further
cargo add: Preserve more comments
cargo remove: Preserve feature comments
cargo replace: Partial-version spec support
cargo: Provide next steps for bad -Z flag
cargo: Suggest cargo-search on bad commands
cargo: adjust -Zcheck-cfg for new rustc syntax and behavior
cargo: if there's a version in the lock file only use that exact version
cargo: make the precise field of a source an Enum
cargo: print environment variables for build script executions with -vv
cargo: warn about crate name's format when creating new crate
rustdoc: align stability badge to baseline instead of bottom
rustdoc: avoid allocating strings primitive link printing
clippy: map_identity: allow closure with type annotations
clippy: map_identity: recognize tuple identity function
clippy: add lint for struct field names
clippy: don't emit needless_pass_by_ref_mut if the variable is used in an unsafe block or function
clippy: make multiple_unsafe_ops_per_block ignore await desugaring
clippy: needless pass by ref mut closure non async fn
clippy: now declare_interior_mutable_const and borrow_interior_mutable_const respect the ignore-interior-mutability configuration entry
clippy: skip if_not_else lint for '!= 0'-style checks
clippy: suggest passing function instead of calling it in closure for option_if_let_else
clippy: warn missing_enforced_import_renames by default
rust-analyzer: generate descriptors for all unstable features
rust-analyzer: add command for only opening external docs and attempt to fix vscode-remote issue
rust-analyzer: add incorrect case diagnostics for module names
rust-analyzer: fix VS Code detection for Insiders version
rust-analyzer: import trait if needed for unqualify_method_call assist
rust-analyzer: pick a better name for variables introduced by replace_is_some_with_if_let_some
rust-analyzer: store binding mode for each instance of a binding independently
perf: add NES emulation runtime benchmark
Rust Compiler Performance Triage
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Add f16 and f128 float types
Unicode and escape codes in literals
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Consider alias bounds when computing liveness in NLL (but this time sound hopefully)
[disposition: close] regression: parameter type may not live long enough
[disposition: merge] Remove support for compiler plugins.
[disposition: merge] rustdoc: Document lack of object safety on affected traits
[disposition: merge] Stabilize Ratified RISC-V Target Features
[disposition: merge] Tracking Issue for const mem::discriminant
New and Updated RFCs
[new] eRFC: #[should_move] attribute for per-function opting out of Copy semantics
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-10-25 - 2023-11-22 🦀
Virtual
2023-10-30 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - online & in person) October 2023 Rust Melbourne Meetup
2023-10-31 | Virtual (Europe / Africa) | Rust for Lunch
Rust Meet-up
2023-11-01 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
ECS with Bevy Game Engine
2023-11-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-11-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-11-09 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-11-14 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-11-15 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Building Our Own Locks (Atomics & Locks Chapter 9)
2023-11-15 | Virtual (Richmond, VA, US) | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2023-11-16 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-21 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
Europe
2023-10-25 | Dublin, IE | Rust Dublin
Biome, web development tooling with Rust
2023-10-25 | Paris, FR | Rust Paris
Rust for the web - Paris meetup #61
2023-10-25 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2023/10: Lunatic
2023-10-26 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
Augsburg Rust Meetup #3
2023-10-26 | Copenhagen, DK | Copenhagen Rust Community
Rust metup #41 sponsored by Factbird
2023-10-26 | Delft, NL | Rust Nederland
Rust at TU Delft
2023-10-26 | Lille, FR | Rust Lille
Rust Lille #4 at SFEIR
2022-10-30 | Stockholm, SE | Stockholm Rust
Rust Meetup @Aira + Netlight
2023-11-01 | Cologne, DE | Rust Cologne
Web-applications with axum: Hello CRUD!
2023-11-07 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake
2023-11-07 | Brussels, BE | Rust Aarhus
Rust Aarhus - Rust and Talk beginners edition
2023-11-07 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #7
2023-11-09 | Barcelona, ES | BcnRust
11th BcnRust Meetup
2023-11-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-11-21 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
GPU processing in Rust
2023-11-23 | Biel/Bienne, CH | Rust Bern
Rust Talks Bern @ Biel: Embedded Edition
North America
2023-10-25 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2023-10-25 | Chicago, IL, US | Deep Dish Rust
Rust Happy Hour
2023-11-01 | Brookline, MA, US | Boston Rust Meetup
Boston Common Rust Lunch
2023-11-08 | Boulder, CO, US | Boulder Rust Meetup
Let's make a Discord bot!
2023-11-14 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer: Share, Show, & Tell! 🦀
2023-11-14 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2023-11-15 | Richmond, VA, US + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-16 | Nashville, TN, US | Music City Rust Developers
Python loves Rust!
2023-11-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2023-11-21 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-11-22 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-10-26 | Brisbane, QLD, AU | Rust Brisbane
October Meetup
2023-10-30 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) October 2023 Rust Melbourne Meetup
2023-11-21 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
When your Rust build times get slower after adding some procedural macros:
We call that the syn tax :ferris:
– Janet on Fosstodon
Thanks to Jacob Pratt for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
9 notes
·
View notes