#BrowserSecurity
Text
Can the Anti-Detect Browser be Used for Web Crawling?

Anti-detection browsers can overcome the challenges of traditional web crawling methods. They offer a range of features that make it possible to perform data extraction tasks very efficiently.
1. Multi-account management
2. UA Masking
3. API Browser Automation
Any repetitive work can be done at VMLogin Antidetect Borwser through automation. You can use the Rest API within VMLogin, and other options include using a third-party automation builder, such as Browser Automation Studio, with automated web crawling for greater efficiency.
3-DAY Free Trial Now!
#virtualbrowser#dataprotection#incognito#searchsafely#virtualplatform#protection#software#webcrawler#automation#browsersecurity#shopify#ecommercetips#fretrial
1 note
·
View note
Text
Cyber Threats Q1 2024 revealed: Cat-Phishing, Living Off the Land, Fake Invoices

Cat-phishing, using a popular Microsoft file transfer tool to become a network parasite, and bogus invoicing were among the notable techniques cybercriminals deployed in Q1 2024, per @HP Wolf Security Report.
https://tinyurl.com/mpjd96xp
#cybersecurity#threats#phishing#malware#infosec#cybercrime#hacking#emailsecurity#netsec#dataprotection#ransomware#antivirus#cyberthreats#phishingattacks#scams#catphishing#asyncrat#bits#filehijacking#redirectattacks#fakeinvoices#securityawareness#threatintelligence#emailgateways#browsersecurity#mobilemalware
0 notes
Link
https://bit.ly/450kuxE - 🛡️ A recent cybersecurity analysis highlighted a surge in "Realst" infostealer malware attacks, specially targeting macOS devices. The malware, hidden within fake blockchain games, is designed to extract cryptocurrency wallet data and browser passwords. Notably, the campaign seems prepared for the upcoming macOS 14 Sonoma release. #CyberSecurity #MacOS #Malware #RealstInfostealer 🕹️ The distribution strategy of Realst involves numerous malicious websites advertising illegitimate blockchain games, each with associated social media accounts. Potential victims are directly contacted via social media, tricking them into installing the infostealer under the guise of a game. #CyberThreat #SocialEngineering 📦 Infostealer malware is primarily distributed through malicious .pkg installers containing a trio of harmful scripts. The scripts act as a Firefox infostealer, a password extractor, and an uninstaller. Surprisingly, the uninstaller was found to be non-malicious. #CyberAttack 🚀 Other versions of the Realst stealer come packaged within applications via .dmg disk images. Some malware samples were even code-signed with an Apple Developer ID, which has since been revoked. However, ad-hoc code-signed samples will continue to launch since their signatures cannot be remotely revoked. #AppleSecurity #CodeSigning 💻 From a behavior standpoint, Realst samples appear similar across variants and exfiltrate key user data. Targeted browsers include Firefox, Chrome, Opera, Brave, and Vivaldi, with Safari being notably absent. Also, the Telegram app seems to be on the hit list. #BrowserSecurity #DataExfiltration 🔍 Analysis identified 16 variants of Realst across 59 samples, classified into four major families (A, B, C, and D). Each variant utilizes unique tactics, but their main goal remains to steal users' data and credentials. About a third of the samples are prepped for macOS 14 Sonoma. #MalwareAnalysis 🚨 The efforts invested in the Realst campaign, the creation of fake game sites, and the use of social engineering indicate a serious threat targeting macOS users for data and crypto wallet theft. As blockchain games rise in popularity, users and security teams must exercise extreme caution when downloading and running such games.
#CyberSecurity#MacOS#Malware#RealstInfostealer#CyberThreat#SocialEngineering#CyberAttack#AppleSecurity#CodeSigning#BrowserSecurity#DataExfiltration#MalwareAnalysis#OnlineSafety#BlockchainGames#CryptoSecurity
0 notes
Text
SSL Certificate. Why You Need An SSL For WordPress
SSL Certificate. Why You Need An SSL For WordPress
SSL stands for Secure Socket Layer. An SSL certificate enables HTTPS encryption for your website and allows secure connection...
#ssl #websecurity #browsersecurity #googlessl #securesocketlayer
SSL stands for Secure Socket Layer. An SSL certificate enables HTTPS encryption for your website and allows secure connection and keeps your and customers data safe by ensuring that all data passing between you and a site is protected against man-in-the-middle attacks.
SSL certificate helps to prevent security breach on your website. This certificate works as digital documentation that verifies…

View On WordPress
4 notes
·
View notes
Text
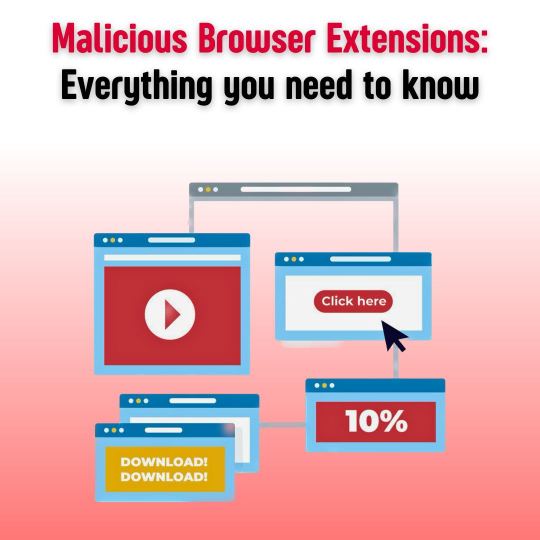
Malicious Browser Extensions: Everything You Need to Know 💡
In today's digital age, web browsers have become an integral part of our daily lives, enabling us to access a vast array of online resources. However, the convenience and functionality provided by browser extensions can come with risks. Malicious browser extensions, in particular, pose a significant threat to users' privacy and online security. In this article, we will explore what malicious browser extensions are, how they work, the dangers they present, and crucial steps to detect, remove, and avoid them.
Read on 👉 https://www.valevpn.com/post/malicious-browser-extensions-everything-you-need-to-know
MaliciousBrowserExtensions #BrowserSecurity #PrivacyThreats #OnlineSecurity #DigitalSafety #BrowserExtensions #CyberThreats #MalwareProtection #DetectMaliciousExtensions #RemoveMaliciousExtensions #OnlinePrivacy #BrowserHijacking #AdInjection #DataCollection #CyberSecurity #BrowsingSafety #ExtensionSecurity #WebBrowsers #ProtectYourself #InternetSafety #SafeBrowsing
0 notes
Photo
START TO EARN BY DOWNLOADING & INSTALLING BRAVE BROWSER.
Download Brave Here to earn: https://brave.com/aco859
Earn 1,000$ and up per month with this Browser. WORK AT HOME.
Convert the tokens you earned into a currency of your choosing.
Expand your Business.
Earn by viewing private ads.
Advertise/monetize your website and social media accounts.
Get a reward while using this Browser and support your favorite content creators.
Experience unparalleled privacy and security.
#websiteowner#entreprenuerlife#make money online#earnonline#bitcoin cash#moneymagic#ad blocker tools#contentcreator#ads#browsersecurity
2 notes
·
View notes
Text
Is AdBlocker Helpful To Install On your Browser?

AdBlockers are software or browser extensions designed for laptops, desktops and even smartphones to block out flashy ads and help you browse website content without interruption from ads. There are concerns that hackers are buying advertising space on the website to install malicious software.
0 notes
Text
ProctorDIY is the world’s first Do-It-Yourself proctoring platform. Through the use of a computer web camera, ProctorDIY conducts ID Verification, automated Facial ID Confirmation and Browser Security, ProctorDIY empowers instructors to monitor their own students, dramatically reducing student privacy and student data security risks.
0 notes
Photo

Private, protected surfing for your whole gadgets with #BrowserSecurity #DealOfTheDay #encryption #hidemyass https://t.co/m3B6O0ntHu http://twitter.com/iandroideu1/status/1252220610777714694
Private, protected surfing for your whole gadgets with #BrowserSecurity #DealOfTheDay #encryption #hidemyass https://t.co/m3B6O0ntHu
— iAndroid.eu (@iandroideu1) April 20, 2020
0 notes
Link
Armorfly is a secure browser that offers maximum privacy and security. You can lock your secrets away and enjoy a comfortable browsing experience with all-round protection. With the help of its video detection function, Armorfly browser makes various online videos downloadable. Furthermore, Armorfly is on private mode permanently, all data sent and received via the app will be cleaned upon exiting the app.
0 notes
Text
How to Secure Multiple Amazon Accounts Against Associations?

Most Amazon sellers currently use cross-border browsers such as the VMLogin fingerprint browser. The convenience of this kind of browser is that sellers can use only one device to operate multiple Amazon accounts, and will not be associated.
1. Customized to modify the browser fingerprint to simulate different login environments;
2. Simulate IP addresses in any region of the world, ensuring that the IP address of each Amazon account is independent, anonymous, and stable;
3. The virtual browser environments created within VMLogin are independent and separate.
The above points ensure that multiple Amazon accounts can be logged into the same computer and that each account runs independently of the other, and cannot be associated with each other.

VMLogin free trial for new users: https://www.vmlogin.us
#amazon#amazonwebservices#amazonfba#amazonseller#amazonads#amazonbusiness#multilogin#antidetect#antidetection#antidetectbrowser#browsersecurity#browser#security#ecommerce#undetectable#detection#antitrack#anonymous#stable#virtualbrowser
0 notes
Text
Browser-Based Phishing Attacks Soar 198% in Second Half of '23

Attacks on browsers by phishing actors ballooned during the second half of 2023, increasing 198% over the first six months of the year, according to a report by a browser security company.
https://jpmellojr.blogspot.com/2024/01/browser-based-phishing-attacks-soar-198.html
0 notes
Link
https://bit.ly/3I1cN1a - 🎥 Malicious Actors Exploit Super Mario Bros. Popularity: Cyber attackers are utilizing the hype around the box office hit, Super Mario Bros., to spread a Trojan virus. Researchers from ReasonLabs have found multiple malicious files downloaded to users' devices, disguised as the trending movie. #Cybersecurity #SuperMarioBros #Malware 💻 Trojan Virus Mechanism: The Trojan virus installs a browser extension that manipulates the user's search function. This allows cyber criminals to gain monetary benefits or access sensitive data. Such tactics have been used before by these attackers, capitalizing on popular films and software. #CyberCrime #BrowserHijacking ⚠️ Browser Hijacking: The malicious software changes users' browser settings without consent. It alters the homepage, default search engine, and may install unwanted applications. The objective? To redirect users to different search engines, display unwanted ads, and profit the attacker. #OnlinePrivacy #DataProtection 🔍 How It Operates: This malicious extension gains control over the web search functions by assigning itself numerous sensitive browser permissions. It replaces primary browser DLLs, controlling the default search bar and injecting its own DLL. It's not bound by Google Chrome Web Store's security restrictions, making it harder to remove. #CyberThreats #BrowserSecurity 🌍 Global Impact: This Trojan virus has been detected over 150,000 times by ReasonLabs researchers. However, the actual number of victims worldwide is estimated to be in the millions. Affected users are seeking help on various online platforms such as Microsoft Answers, Bleeping Computer, Reddit, and Google Support. #GlobalCyberThreat #InternetSafety 📚 Protecting Yourself: The best defense against such attacks is a combination of robust security tools and cyber education. By using services like RAV Endpoint protection, a DNS filter, VPN, and EDR, users can significantly reduce their vulnerability. However, security companies and antivirus providers must prioritize educating users on safe browsing practices.
#Cybersecurity#SuperMarioBros#Malware#CyberCrime#BrowserHijacking#OnlinePrivacy#DataProtection#CyberThreats#BrowserSecurity#GlobalCyberThreat#InternetSafety#CyberEducation#OnlineSafety
0 notes
Photo

Hackers Using Google Analytics to Bypass Web Security and Steal Credit Cards | MrHacker.Co #browsersecurity #contentsecuritypolicy #cybersecurity #databreach #digitalskimmer #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

Watch Out! Adrozek Malware Hijacking Chrome, Firefox, Edge, Yandex Browsers #adware #browserhacking #browsersecurity #edgebrowser #googlechrome #malware #searchengine #yandexbrowser #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo
Update Google Chrome Browser to Patch New Critical Security Flaws | TheHackerNews.Co #browsersecurity #browservulnerability #chromebrowser #googlechrome #hackingcomputers #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes