#cyberthreats
Text
#cyberjapan#cybercity#cyberpunk#cyberthreats#animes#best anime#anime girl#anime cosplay#anime art#art#cyberart#memes#fails#funny animals#anime memes#bts#wtf#amor
47 notes
·
View notes
Text

What these African deities have to say about cybercrime is crazy!😂
Enjoyed the post? Then don't let your laughter be encrypted! Like, and follow for more heavenly humor.

#funny#funny memes#funny post#satire#haha#funny shit#just for fun#hilarious#just for laughs#just for you#african gods#african gods react#africa#humor#cyberthreats#cyber criminals#cybersecurity#Ethiopia#Zimbabwe#Maldives#Kenya#Uganda#Angola#Morocco#nigeria#for you page
4 notes
·
View notes
Text
Hacker Breach Exposes 23andMe’s Customers’ Data

Genetic Testing Giant Confirms Massive Security Compromise
A staggering breach has rattled the foundations of 23andMe, the renowned genetic testing company, as it confirms unauthorized access to nearly seven million user profiles. A spokesperson disclosed to CNN on Tuesday that the breach encompassed sensitive details such as ancestry reports, zip codes, and birth years, significantly impacting a subset of the company’s extensive user base.
The Scale of the Breach
The unsettling revelation came to light through a filing to the Securities and Exchange Commission (SEC) on Friday, where 23andMe indicated that approximately 0.1% of its user accounts, approximately 14,000 profiles, fell victim to the cyber intrusion. However, subsequent investigations unveiled a more substantial impact, with hackers infiltrating around 5.5 million profiles employing the company’s DNA Relatives feature.
Extent of Compromised Information
Notably, hackers also managed to access a subset of family tree data linked to 1.4 million DNA Relatives profiles, raising concerns about the depth and breadth of compromised personal information. Engadget, a prominent tech news outlet, initially shed light on the broader implications of this extensive security breach.
23andMe faces data breach: Over 7 million users exposed to hackers
youtube
Ongoing Cybersecurity Woes
This incident adds 23andMe to the roster of major U.S. corporations grappling with severe cybersecurity breaches affecting a larger populace than initially acknowledged. Just recently, Okta, an identity management firm, acknowledged a data breach impacting all users within its customer support system, a figure significantly higher than initially reported.
Modus Operandi: Credential Stuffing
The method of intrusion employed by the hackers has been identified as ‘credential stuffing.’ Leveraging old usernames and passwords obtained from other platforms, this rudimentary yet effective technique facilitated unauthorized access to numerous 23andMe customer accounts.
Company’s Response and Measures Taken
In response to the breach, 23andMe embarked on a comprehensive investigation aided by third-party forensic experts. Despite declining to disclose the perpetrators, the company is diligently notifying affected customers, complying with legal obligations.
A statement posted on the company’s website outlined measures to bolster data protection, mandating password resets for existing customers and implementing two-step verification for both new and existing users.
As concerns over data security and privacy amplify, this breach underscores the pressing need for stringent measures to safeguard sensitive personal information in an increasingly digitized world.
The ramifications of such a breach extend far beyond the compromised data itself. Users are now grappling with potential identity theft, privacy infringement, and the misuse of their genetic information. This breach has reignited conversations about the ethical responsibilities of companies dealing with highly personal data and the imperative to fortify cybersecurity protocols.
In the wake of this breach, regulatory bodies and lawmakers are likely to intensify their scrutiny of companies handling sensitive user data, potentially leading to stricter compliance standards and regulations aimed at fortifying cybersecurity measures and protecting consumer privacy.
As 23andMe continues its damage control and endeavors to rebuild trust, the cybersecurity landscape faces renewed challenges, emphasizing the criticality of proactive measures to thwart malicious cyber threats and safeguard user information from similar breaches in the future.
Curious to learn more? Explore our articles on Enterprise Wired
#DataBreach#Cybersecurity#PrivacyConcerns#23andMeHack#SecurityAlert#DigitalPrivacy#CyberThreats#Youtube
2 notes
·
View notes
Text
CYBER SECURITY: WHAT IS IT AND WHAT YOU NEED TO KNOW?

Cyber Security is a protection offered to an automated information system in order to attain the applicable objectives of preserving the integrity, availability and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications). To read more visit: https://www.rangtech.com/blog/cybersecurity/cyber-security-what-is-it-and-what-you-need-to-know
3 notes
·
View notes
Video
New Tracking Trojan Made For Fake Uses
#cyber security#cyberattack#ethical hacking#kali linux#trending#crypto#cyberthreats#hacking#ethical hacker#safety
46 notes
·
View notes
Text
I'm laughing so hard at this🤣🤣🤣
7 notes
·
View notes
Text
The Dangers of TikTok: A Deep Dive into the Technical Concerns
TikTok, a social media platform owned by ByteDance, a Beijing-based company, has taken the world by storm. Its short-form video content has attracted millions of users, particularly among the younger generation. However, as with any technology, it comes with its own set of risks and concerns. This blog post will delve into the technical dangers associated with TikTok, including data privacy,…

View On WordPress
1 note
·
View note
Photo
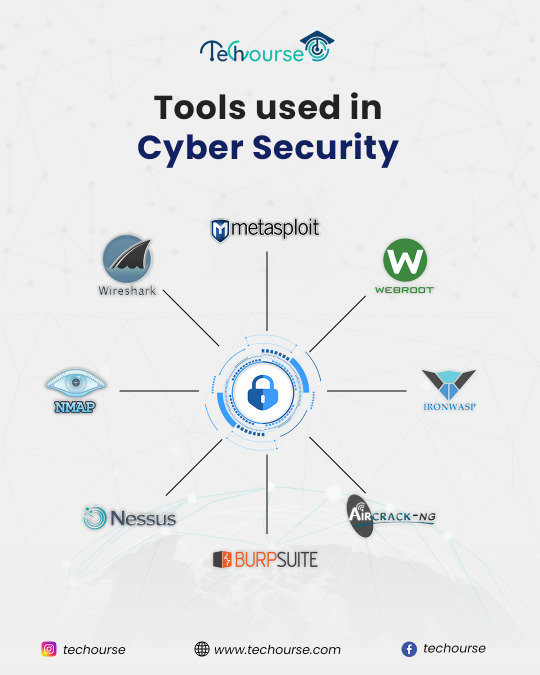
Here is the list of best tools used in Cyber Security. Choose the right tool from this list and protect you business from Cyber Threats. Get more insights only at Techourse.
3 notes
·
View notes
Text
#ThreatIntelligence#ThreatIntelligenceAnalyst#CertifiedThreatIntelligenceAnalyst#CyberThreatIntelligence#Cybersecurity#Cyberattack#Cybersec#Cyberthreat#Cyberthreats#Cybercrime#edtech#technology#teaching
2 notes
·
View notes
Text
How AI is Revolutionizing B2B SaaS: Driving Growth, Saving Time, and Boosting Your Bottom Line
In today's fiercely competitive B2B (business-to-business) SaaS (software-as-a-service) landscape, companies must find an edge to stand out, accelerate growth, and thrive. Artificial intelligence (AI) is rapidly emerging as a catalyst for transforming how B2B SaaS businesses operate, from customer acquisition to product development.
In this article, we'll explore how AI streamlines…

View On WordPress
#artificialintelligence#cloudsoftware#cloudtechnology#customerfirst#cybersecurity#cyberthreats#devops#devopsteams#digitalidentity#digitalsolutions#ITexpert#leadership#LoginRadius#password#postcovid#productinnovation#softwaredevelopers#techexpert#technologynews#tip
0 notes
Text

youtube
#cyberpunk#cyberthreats#cyberculture#cyborg#cybercore#bomb rush cyberfunk#cyberpunk 2077#animes#anime girl#best anime#mechanicaldesign#the mechanisms#mecha art#anime 90s#90s anime#90s aesthetic#funny animals#anime memes#memes#fails#bts#anime#anime cosplay#btsv#jajajaja#fyp#fypシ#fypage#tumblr fyp#bad art
23 notes
·
View notes
Text
The Evolution of Cyber Security in Computer Science & Engineering: A Journey Through Dayanandasagar College of Engineering
Cybersecurity has undergone a remarkable evolution within the realm of Computer Science & Engineering. Dayanandasagar College of Engineering has played a pivotal role in nurturing this evolution. From basic firewalls to sophisticated machine learning algorithms, the landscape has transformed. As technology advances, so do cyber threats, necessitating constant innovation and vigilance. At Dayanandasagar College of Engineering, students are equipped with cutting-edge tools and knowledge to tackle modern cyber challenges.
#Cybersecurity#ComputerScience#Engineering#DayanandasagarCollegeOfEngineering#Innovation#CyberThreats#Technology.
0 notes
Text
How to Protect Your Business from Cyber Attacks
Ensuring the security of your business from cyber attacks is crucial in the digital age. These attacks have the potential to cause significant damage to your data, disrupt your business operations, and result in financial losses. Regardless of your business’s size, it’s vital to take proactive steps to protect yourself. Here are some simple strategies you can adopt to strengthen your business’s…
View On WordPress
0 notes
Text
Top 5 Cloud Security Threats and How to Combat Them

Stay ahead of emerging cyber threats in the cloud computing landscape. This insightful article unveils the top 5 cloud security threats businesses face.
Read More. https://www.sify.com/security/top-5-cloud-security-threats-and-how-to-combat-them/
#CloudSecurityThreats#Cybersecurity#DataProtection#CloudComputing#Cyberthreats#Cloud#DataBreach#Malware
0 notes
Text
Malware Explained Part 1: Understanding the Malicious
Dive into the world of malware in this first part of a series! In this video, I'll be sharing my views on what malware is, how it works, and the different types you might encounter. Whether you're a tech wiz or just starting out, this video will equip you with the knowledge to stay safe online. Stay tuned for Part 2 where we'll discuss how to protect yourself from malware attacks!
To learn more do check out Cybersecurity courses.
#Cybersecurity#ethicalhacking#InfoSec (Information Security)#DigitalDefense#CyberThreats#DataSecurity#OnlineSafety#SecurityAwareness#CyberHygiene#Cybercrime#Phishing#Ransomware#Spyware#Adware#Virus#Worm#Botnet#ZeroDayAttack#MalwareAnalysis#CyberSecurityBasics#StaySafeOnline#ProtectYourData#CyberSecurityTrends#EthicalHacking#VulnerabilityManagement
1 note
·
View note