#Building Information Modeling Software
Explore tagged Tumblr posts
Text

Trovate le migliori soluzioni di Building Information Modeling per proprietari di edifici e gestori di immobili per prendere decisioni basate sui dati, ridurre i costi, migliorare le operazioni e mitigare i rischi. Tracciamo tutti i dati degli asset in un'unica interfaccia e forniamo soluzioni per una gestione a 360° dell'edificio durante il suo intero ciclo di vita.
0 notes
Text
Know how using Building Information Modeling (BIM) Software to accelerate the design process by maintaining constant communication and collaboration.
#Building Information Modeling Software#Building Information Modeling#BIM#Engineering Firms#BIM Software#BIM Software Development Company#Software Development Company#Software Development#BIM Software Development Services
0 notes
Text
Best BIM Tools in 2025 and Selecting the Right BIM Software

BIM is a comprehensive approach in the AEC realm, and its applications and tools hold a significant position. It is vital to choose the right BIM software for project requirements, coordination, and efficiency. Here’s a detailed, curated list of the best BIM software and key factors for selecting it.
#bim modeling services#3d bim services#mep shop drawings#building information modeling#interior visualization#clash detection#revit families creation#3d cad drawings#shop drawing services#bim company#top bim software#best bim tools
2 notes
·
View notes
Text

BIM Software Learning | BIM Certificate Programs- Aeczone Academy
#architecture#certificate in building information modelling#online bim certificate programs#learn bim online#bim classes#bim architecture course#bim certification courses#bim course with placement#bim modeling course#building information modeling course#bim engineer course#bim learning online#bim software learning
3 notes
·
View notes
Text
How Architectural Bim Services Streamline Building Design

Don’t you have any idea about how Architectural BIM Services USA made huge changes. Here you go. In this rapidly evolving architecture, engineering, and construction industry, there is a huge demand for promising work. Those who complete the project with precision, efficiency, and collaboration are always welcome.
#Architectural BIM Services USA#Bim Service Providers#Architectural Bim Services#Structural Bim Services#Mepf Bim Services#Infrastructure Landscape Mepf#4D Bim Software#5D Quantity Take-Off#Building Information Modelling 6D#7D Bim Asset Management Company#Point Cloud To Bim Conversion#Cad To Bim Modeling Services#Construction Documentation Checklist#Cobie Service India#Bim For Facility Management#Structural Precast Modelling#Revit Fabrication Service India#Bim Consulting Services India#Bim Implementation Service India#Bim Documentation Service#Bim Execution Planning Guide
0 notes
Text
BIM Software Solutions for Modern HVAC Applications
As the HVAC industry continues to evolve in 2025, Building Information Modeling (BIM) has become an indispensable tool for professionals seeking to optimize design, installation, and maintenance processes. For HVAC engineers, contractors, and technicians, selecting the right BIM software can significantly impact project efficiency and outcomes. Let’s explore the most effective BIM solutions for…
#3D modeling#augmented reality#Autodesk Revit#automation#Bentley AECOsim#BIM#BIM workflows#building information modeling#Building performance#building systems#clash detection#cloud collaboration#cooling loads#decision matrix#digital twin#duct design#energy analysis#Energy efficiency#fabrication documentation#Graphisoft ArchiCAD#heating loads#hvac#HVAC design software#HVAC engineering#interoperability#mechanical engineering#mechanical systems#MEP#MEP coordination#mixed reality
0 notes
Text
#revit bim software#bim software#building design#autocad#navisworks#tekla#bim software list#building information modeling services
0 notes
Text
Top 05 Future Trends in BIM Clash Detection Software

Clash detection is one of the most critical steps teams can take to identify and address potential design conflicts before construction begins. This proactive approach helps to prevent issues and avoid costly rework during the construction process.
While clash detection has been used for some time, it can be done manually by reviewing design drawings or using lightbox overlays. However, the introduction of Building Information Modeling (BIM) tools has significantly improved the ease and accuracy of this process.
As a result, BIM clash detection has become the standard practice in commercial construction, and it is implemented during the earliest stages of design and preconstruction.
Building Information Modeling (BIM) has become a cornerstone of modern construction practices, enabling architects, engineers, and contractors to collaborate more effectively. One of the most significant advancements within this realm is BIM clash detection software, which helps identify and resolve conflicts between various design elements before construction begins. As we look toward the future, several key trends are emerging that promise to enhance the capabilities and effectiveness of BIM clash detection software.
Learn more: https://blog.prototechsolutions.com/top-05-future-trends-in-bim-clash-detection-software/
#BIM Clash Detection Software#Clash Detection#Clash Detection Software#BIM Clash Detection#Navisworks#Autodesk#BIM#Building Information Modeling#Mechanical#Electrical#Plumbing
0 notes
Text
BIM -Building Information Modeling |Revolutionizing Construction
BIM, or Building Information Modeling, transforms construction and engineering projects by integrating data for planning, design, construction, and management. This comprehensive approach improves project visualization and coordination, making decision-making easier and reducing risks. In this blog, we’ll delve into the essential software components of BIM, including 3D modeling, data management,…
#applications of BIM#Benefits of BIM#BIM#BIM model#BIM objects#Building information modeling#construction#Future trends in BIM#what is bim software?
1 note
·
View note
Text

Building Smarter with BIM Technology
Building Information Modeling Companies like us, Modulus Consulting, are revolutionizing the AEC industry. We are renowned for our commitment to quality, precision, and client satisfaction. As one of the Top BIM Service Companies, we provide comprehensive solutions tailored to your specific needs, pushing the boundaries of what's possible with 3D modeling technology.
#BIM 360 Model Coordination#Building Information Modeling Services#Top Bim Service Companies#3D BIM Modeling#3D BIM Modelling Services DC#Reality Capture Software#AEC BIM Services
0 notes
Text
Building Information Modeling (BIM) Market Size, Share, Statistics and Industry Growth Analysis Report by Offering (Software, Services), Deployment (Cloud, On-Premise), Project Lifecycle (Preconstruction), Application (Buildings, Industrial), End User (AEC Professionals) and Region - Global Forecast to 2028
0 notes
Text

UTwin è all'avanguardia come fornitore di tecnologie per la modellazione Building Infromation Modeling (BIM) degli edifici, con l'obiettivo di assistere i proprietari immobiliari in una gestione dei dati più intelligente e collaborativa. Le nostre soluzioni si rivolgono a una clientela globale, con una forte presenza in Italia, Europa e nell'area MENA.
0 notes
Text
Exploring the Diverse Landscape of BIM Software in Construction: A Comprehensive Guide
Introduction: In the ever-evolving field of construction, Building Information Modeling (BIM) has emerged as a transformative technology that revolutionizes the way buildings are designed, constructed, and managed. BIM software plays a pivotal role in enhancing collaboration, improving efficiency, and minimizing errors throughout the construction process. This article delves into the various…
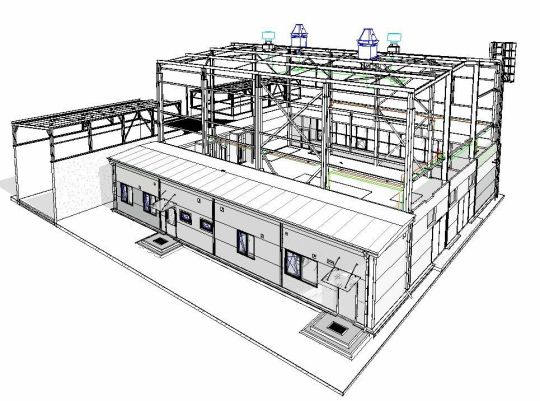
View On WordPress
#architectural design software#as-built documentation#BIM model accuracy#BIM software#Building Information Modeling#collaboration platforms#construction industry advancements#construction management software#construction project efficiency#Construction Technology#cost estimation tools#facility maintenance optimization#facility management solutions#laser scanning technology#LiDAR applications#MEP systems modeling#point cloud integration#project stakeholders collaboration#real-time coordination#structural engineering tools#sustainable building practices
0 notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Text
The Four Horsemen of the Digital Apocalypse
Blockchain. Artificial Intelligence. Internet of Things. Big Data.
Do these terms sound familiar? You have probably been hearing some or all of them non stop for years. "They are the future. You don't want to be left behind, do you?"
While these topics, particularly crypto and AI, have been the subject of tech hype bubbles and inescapable on social media, there is actually something deeper and weirder going on if you scratch below the surface.
I am getting ready to apply for my PhD in financial technology, and in the academic business studies literature (Which is barely a science, but sometimes in academia you need to wade into the trash can.) any discussion of digital transformation or the process by which companies adopt IT seem to have a very specific idea about the future of technology, and it's always the same list, that list being, blockchain, AI, IoT, and Big Data. Sometimes the list changes with additions and substitutions, like the metaverse, advanced robotics, or gene editing, but there is this pervasive idea that the future of technology is fixed, and the list includes tech that goes from questionable to outright fraudulent, so where is this pervasive idea in the academic literature that has been bleeding into the wider culture coming from? What the hell is going on?
The answer is, it all comes from one guy. That guy is Klaus Schwab, the head of the World Economic Forum. Now there are a lot of conspiracies about the WEF and I don't really care about them, but the basic facts are it is a think tank that lobbies for sustainable capitalist agendas, and they famously hold a meeting every year where billionaires get together and talk about how bad they feel that they are destroying the planet and promise to do better. I am not here to pass judgement on the WEF. I don't buy into any of the conspiracies, there are plenty of real reasons to criticize them, and I am not going into that.
Basically, Schwab wrote a book titled the Fourth Industrial Revolution. In his model, the first three so-called industrial revolutions are:
1. The industrial revolution we all know about. Factories and mass production basically didn't exist before this. Using steam and water power allowed the transition from hand production to mass production, and accelerated the shift towards capitalism.
2. Electrification, allowing for light and machines for more efficient production lines. Phones for instant long distance communication. It allowed for much faster transfer of information and speed of production in factories.
3. Computing. The Space Age. Computing was introduced for industrial applications in the 50s, meaning previously problems that needed a specific machine engineered to solve them could now be solved in software by writing code, and certain problems would have been too big to solve without computing. Legend has it, Turing convinced the UK government to fund the building of the first computer by promising it could run chemical simulations to improve plastic production. Later, the introduction of home computing and the internet drastically affecting people's lives and their ability to access information.
That's fine, I will give him that. To me, they all represent changes in the means of production and the flow of information, but the Fourth Industrial revolution, Schwab argues, is how the technology of the 21st century is going to revolutionize business and capitalism, the way the first three did before. The technology in question being AI, Blockchain, IoT, and Big Data analytics. Buzzword, Buzzword, Buzzword.
The kicker though? Schwab based the Fourth Industrial revolution on a series of meetings he had, and did not construct it with any academic rigor or evidence. The meetings were with "numerous conversations I have had with business, government and civil society leaders, as well as technology pioneers and young people." (P.10 of the book) Despite apparently having two phds so presumably being capable of research, it seems like he just had a bunch of meetings where the techbros of the mid 2010s fed him a bunch of buzzwords, and got overly excited and wrote a book about it. And now, a generation of academics and researchers have uncritically taken that book as read, filled the business studies academic literature with the idea that these technologies are inevitably the future, and now that is permeating into the wider business ecosystem.
There are plenty of criticisms out there about the fourth industrial revolution as an idea, but I will just give the simplest one that I thought immediately as soon as I heard about the idea. How are any of the technologies listed in the fourth industrial revolution categorically different from computing? Are they actually changing the means of production and flow of information to a comparable degree to the previous revolutions, to such an extent as to be considered a new revolution entirely? The previous so called industrial revolutions were all huge paradigm shifts, and I do not see how a few new weird, questionable, and unreliable applications of computing count as a new paradigm shift.
What benefits will these new technologies actually bring? Who will they benefit? Do the researchers know? Does Schwab know? Does anyone know? I certainly don't, and despite reading a bunch of papers that are treating it as the inevitable future, I have not seen them offering any explanation.
There are plenty of other criticisms, and I found a nice summary from ICT Works here, it is a revolutionary view of history, an elite view of history, is based in great man theory, and most importantly, the fourth industrial revolution is a self fulfilling prophecy. One rich asshole wrote a book about some tech he got excited about, and now a generation are trying to build the world around it. The future is not fixed, we do not need to accept these technologies, and I have to believe a better technological world is possible instead of this capitalist infinite growth tech economy as big tech reckons with its midlife crisis, and how to make the internet sustainable as Apple, Google, Microsoft, Amazon, and Facebook, the most monopolistic and despotic tech companies in the world, are running out of new innovations and new markets to monopolize. The reason the big five are jumping on the fourth industrial revolution buzzwords as hard as they are is because they have run out of real, tangible innovations, and therefore run out of potential to grow.
#ai#artificial intelligence#blockchain#cryptocurrency#fourth industrial revolution#tech#technology#enshittification#anti ai#ai bullshit#world economic forum
32 notes
·
View notes
Text
putting aside the ethics of 'A.I' videos in their creation/usage/waste/economics, just on a purely technical level one thing i find interesting is no matter if the result looks photorealistic or like 3d CGI- it's all technically 2d image generation.
unless specifically used as an add on in a software for 3d rendering, of course, pretty much every ai video you see online is 2d art. the space rendered is a single plane, think of it like doing a digital painting on a single layer. the depth/perspective is an illusion that is frame by frame being rendered to the best ability of prediction based on data it has been fed.
obviously videos of 3d models in animation are a 2d file. like a pixar movie. but in video games you do have a fully rendered 3d character in a 3d rendered space, that's why glitches that clip through environments are so funny. it's efficient to have stock animations and interaction conditions programmed onto rigged dolls and sets.
by contrast if you were to use a generative ai in a similar context it would be real time animating a series of illustrations. of sounds and scenarios. the complexity required for narrative consistency and the human desire to fuck up restrictions hits up against a much more randomised set of programming. how would it deal with continuity of setting and personality? obviously chatbots already exist but as the fortnight darth vader debacle recently shows there are limits to slapping a skin on a stock chatbot rather than building one custom.
i just think that there's so many problems that come from trying to make an everything generator that don't exist in the mediums it is trying to usurp because those mediums have a built in problem solving process that is inherent to the tools and techniques that make them up.
but also also, very funny to see algorithmic 2D pixel generation being slapped with every label "this photo, this video, this 3d render" like it is at best description cgi, let's call it what it is.
but i could of course be wrong in my understanding of this technology, so feel free to correct me if you have better info, but my basic understanding of this tech is: binary code organised by -> human programming code to create -> computer software code that -> intakes information from data sets to output -> pixels and audio waveforms
9 notes
·
View notes