#COMP6441
Explore tagged Tumblr posts
Photo

Minecraft Factions: Security Engineering There’s an Overlap?
Minecraft just went up big time in sales. That has provided Youtube with an excuse to push Minecraft videos into my feed again. While the part of my brain that is closest to the 12-year-old me was so very enthused at how much this game has changed and only just cared about watching people play the casual Minecraft... The part of my brain that’s been in a tug of war with the concepts of Security Engineering noticed a lot of interesting things with my childhood sweetheart game.
Let me explain... Minecraft Factions is basically a sub-genre of themed servers on Minecraft, where people go to form factions and instigate in the mindless violence they can’t follow through with in real life. Players Join servers They make or join factions They then either collect resources or loot them from other factions This server requires people to maintain a high ranking in terms of resources and to build strongholds to protect those resources. When I was watching videos of people infiltrating these bases and using all these creative ways of finding weaknesses in seemingly secure defences, I noticed just how many overlaps there were with the concepts I’ve been learning in 6441 What are these similarities you ask?
That’s for my next blog...
2 notes
·
View notes
Text
CTF Challenge 12: cmd2
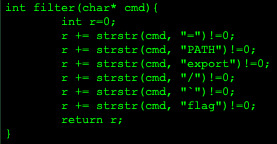
I found this challenge to be a little similar to cmd1, however it had a stricter filter function that rejected any ‘/’ in the arguments:
Due to this, I instead decided to turn my attention to the system() function that usually runs cat command:
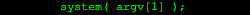
On its man page, I found out that it actually uses the execl() function to run a binary of sh to run the command:

Checking the man page for sh, I found that the sh program has a builtin command called ‘command’, and has an option -p, that will run any command that can be found in the PATH environment variable. Knowing this, I ran the command:
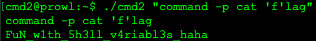
to bypass the filter and obtain the flag.
2 notes
·
View notes
Text
Week 8 - Case Study

Ghost - Scenario Discussion this week is the Stargate ghost problem, as described in the lecture.
· The major M will ask the ghost X for a kind of ID. Once M received that ID, he can verify it against a military internal database. (Assume M and X knew each other before)
· Get a few aliens and make them to communicate with the same ghost separately. If one or some aliens try to trick the M, they cannot fabricate exactly the same fake answers.
· Use one alien as an 'uplink' and another alien as a 'downlink', just like the people living in the remote areas accessing to the Internet - using a high-speed satellite as a downlink and a low-speed telephone line as a uplink. In this scenario, the alien A1 who serves as a 'uplink' can possible see the message that Major M sent to Ghost X, but anyway, X will send an answer back through another alien A2, who serves as a downlink and knows nothing about what M had sent to M. In this case, neither A1 or A2 will be a full 'man in the middle' as none of them knows the complete messages between M and X.
· Another interesting method would be that M can choose 10 aliens as candidate messengers and separate them, making them impossible to 'conspire' all the ten. M then send one question through all the 10 aliens to X, and X will send an answer back through all the 10 aliens to M. If one or more of the answers that M received from X through all 10 aliens is not the same as the rest of the answers, that is, if the ten answers M received are not exactly the same, then M knows that at least one of the ten aliens tempered the communication. In this case, not knowing which ones among the ten aliens are not trustworthy, M can just 'dump' all the ten aliens and find another batch of ten aliens, until one batch of ten aliens that can bring the same untampered communication.
1 note
·
View note
Text
[SA2.0] Something Awesome Essay
This is the link to my completed essay on the topic of Critically Analyse the Impact of the Telecommunications and Other Legislation (Assistance and Access) Act 2018. I am really happy with the finished product, it took longer to complete than intended but it is in-depth and reflective.
https://drive.google.com/open?id=1vFuREtePNC1mxMg7gliwjRORlbJlohKv
I have finished my submission that corresponds with my report, I just need to edit it.

1 note
·
View note
Text
Cross-site scripting (XSS)
What is cross-site scripting?
Cross-site scripting (or XSS for short) is an attack on web applications where a malicious script is injected into the site. The attack can be carried out on the client side where the injected code can be executed by another user on the same site.
What can the attacker do?
Malicious scripts are usually Javascript as it has direct control of the website’s DOM (modifying elements), cookies (where user info is stored on a machine) and HTTP requests (requests to the server for information).
For example, the attacker can exploit an XSS vulnerability to make other users’ send their credentials (stored in their cookies) to the attacker’s server by simply modifying a URL link and give it to a victim. Once the victim clicks on the link, the script activates and execute malicious code on the victim’s browser.
How does XSS work?
To carry out an XSS attack, the attacker must first inject the site with a script. Then, the victim must somehow activate that script, usually through social engineering/phishing to get the victim to go to a URL that contains the script.
There are 3 categories of XSS attack:
Reflected XSS
Stored XSS
DOM XSS
Reflected XSS works by modifying a parameter in a URL to execute a script.
For example, a URL to the target website can be modified to contain the malicious script:
https://www.tumblr.com/blog?data=<script>alert("You have been hacked!”)</script>
If the application is vulnerable to reflected XSS, the application will take this data parameter value and inject it into the DOM where it will execute in the victim’s computer.
Stored XSS works by having a script stored somewhere in the site, where it will execute as soon as the victim visits it.
For example, an attacker may comment <script>alert("You have been hacked!”)</script> on the victim’s post. If the site is vulnerable to stored XSS (e.g. not checking if the comment has any scripts in it), anyone who views the comment will be affected.
DOM XSS works by injecting the script into the website by the victim’s browser directly.
For example, an attacker may modify the victim’s browser to inject malicious scripts on a certain site. When the victim visits the site, the script activates and runs.
How to prevent XSS attacks?
XSS vulnerabilities are quite common, where any website that takes inputs from its users without thoroughly checking can be susceptible to XSS attacks. This can be a login form, a comment box, virtually any <input> element are vulnerable to XSS attacks.
To prevent XSS attacks, web developers must:
Sanitise inputs (e.g. clear any scripts and prevent any scripts to be run in all inputs).
Never output data directly on to the browser without checking for malicious code.
To protect yourself from XSS attacks, users must:
Never click on a suspicious URL and always check for scripts in the URL.
Disable cookies and Javascript on untrusted websites.
1 note
·
View note
Text
Module 4 - Lecture
Unfortunately, I couldn’t attend the 2nd part so I will need to catch using the lecture notes and slides. Here are some notes from the first 2 hours of the lecture.

1 note
·
View note
Link
Recently I’ve heard people say “EVERYONE SHOULD USE A PASSWORD MANAGER”. And then this article popped up:
The points Stuart raises are quite interesting. Some reasons why they’re good to use are:
They make it easier to use strong passwords
Password managers can prevent password-reuse attacks
Password managers can prevent impostor websites from “phishing” you
Password managers track which services you have accounts with
On the flip side, there are also risks involved with password manager:
You may forget the master password that protects your other passwords
An attack on your password manager can reveal all your passwords.
But so far there has yet to be a major breach in password managers, so for now, maybe I SHOULD consider using one...
1 note
·
View note
Photo

Stalk mode on.
1 note
·
View note
Text
COMP6441 Lecture Blog - Week 1.1
I wasn’t able to attend the first set of lectures for this course so the blogs on the lectures will be based on the videos uploaded for module 1. I will make every effort possible to attend the subsequent lectures.
The way Richard describes how this course will be run seems very different to what I’m used to during my couple of years of being at uni. The main point that sticks out to me is the open ended learning, personally I’m not sure how I feel about this, I like how my previous courses had structure in their assessments as I knew what I was getting into. That being said the layout of this course does focus on us (as Richard mentions) and the skills we acquire would be more useful once we leave uni.
1 note
·
View note
Text
Case Study: deepwater horizon oil spill
For this week’s case study, we discussed about a deepwater horizon oil spill which took place in 2010.
We came up with several main causes that led to the disaster.
1. False negative pressure test (no clear standard)
2. No automation(cost problem, no standard to apply)
3. Management issue (pursue profit)
5. Cutting corners (ignoring procedure) - waste of cost and time
6. Blowout preventer failed (none of the 3 models worked properly)
7. Sheer ram lack of redundancy
8. Too many company involved which made it too complicated
9. Neglected flaws even though pointed out several times.
10. People issue(crew rotation): no proper handover procdedure took place
Solutions that we came up with include:
1. Make legal and clear standards(set methods&procedures)
2. Better communication (overlapping schedule when rotation takes place)
3. Often testing
4. Monitor control systems - quick alert
5. Redundancy check
6. Don’t ignore small issues/errors - can lead to chain of failure
1 note
·
View note
Photo

Jake Paul: Infiltrating the White House
You heard me...
“YouTuber Sensation Jake Paul done goofed up real good this time...”
In one of his most recent videos, Jake Paul posted a video of himself hiding in the Presidential Whitehouse in Washington. The use of the word “Infiltrated” might have been a stretch but hey, this is how you grab attention on the internet. It’s called Click baiting...
Here’s some context,
Jake Paul for some reason was invited to the Whitehouse. He was authenticated and authorised to go inside as a friendly package.
Jake Paul for some reason decided to slip away from the main event and went into the bathroom. Since he’s already inside there aren’t many people checking for unusual activity in that premise. He’s decided to turn menacing after bypassing the big security defences.
Jake Paul for some reason decides to stay in the bathroom overnight. No one checks for him in there, since it’s only a bathroom and no one even notices him missing. Menacing package decides to take over unimportant asset. Menacing package doesn’t throw off alarms.
He then walked out at 3AM. No harm done. No items stolen. Miraculous that he’s still alive.
What a stunt. Taught me a lot about the Whitehouse’s security.
It’s a one time door... Once you’re in... You’re in...
I’m only kidding now XD
1 note
·
View note
Text
ATM Attacks and Defence
A typical ATM attack method is skimming, where a card reader is slotted over the ATM’s card reader in way that disguises itself that won’t be noticed by the ATM user. The card reader records the data on a card’s magnetic strip and this can be placed on a copycat card. A hidden camera or accomplice standing behind the user can then record the user’s PIN, so that with these two pieces of information, thieves can withdraw money from their account. Another way of obtaining this information is through the use of a fake ATM, which can lure people into thinking they are using a legitimate machine from a bank. People can prevent these attacks by being aware of their surroundings and alert to any signs of tampering on an ATM, such as not being able to see the card reader light, or any poorly designed features that may indicate a fake ATM.
Another form of ATM attack would be through physical theft, where an ATM is physically removed from where it’s located, such as through towing it with a vehicle, and disassembled elsewhere with tools to access its supply of cash. This type of method can be mitigated through the application of security cameras to assist in the identification of any thieves and strong bolting to the floor and walls surrounding the ATM to make it harder for physical removal.
2 notes
·
View notes
Text
Something Awesome Proposal
· Overview
Circumvention of Software Registration, the so-called software “cracking”, “patching”, “keygen making” or “unlocking”, is a significant illegal or at least unethical activity related to the software business. It is a serious and pervasive security issue of copyright infringement in many countries and contributes substantial losses to a large number of software companies all over the world.
Traditional desktop standalone GUI software always requires users to purchase a serial number or “key” and then use the key to activate the software. Hackers usually take advantage of the defects and loopholes in the validation module of the software to bypass the key requirement, or make key generators (keygen) to enable illegal generation of serial numbers.
Up to now, C++ and C# are two of the most used programming languages for software companies to develop desktop GUI softwares for Microsoft Windows operating system. In my project, I will dip thoroughly into the most common mechanisms for software registration used by software companies for their C++ and C# softwares, analyse their design principles and vulnerabilities, and try to “crack” a C++ software and a C# software to demonstrate the possibility of unauthorised activation of their products, and finally I will put forward a few feasible practices which software companies can use to protect their products from unauthorised activation.
· Research Candidates
v C++ software: BytesX Software IconLibraryX 1.0.0.1108
http://iconlibraryx.zero2000.com/
v C# software: TriSun Software KeyMusic v3.0 and TriSun Software Advanced Date Time Calculator v9.1
https://www.trisunsoft.com/key-music.htm
https://www.trisunsoft.com/advanced-date-time-calculator/
· Time-based Objectives
v Learn common and specific security issues on software activation for C++ and C# softwares
v Learn common tools and methods for software disassembly and cracking, the necessary basics in reverse engineering
So far, Milestone 1
v Learn how to use the analysis and disassembling tools to reverse a software, look for its activation validation module and extract the important codes
v Learn how to locate the key validation sentence or make the reversed function
So far, Milestone 2
v Crack the softwares , make a “patch” or “keygen” for the softwares mentioned above and test the effectiveness of them to see if I have successfully bypassed the activation requirements, grace period limitation and unlocked full feature of the software.
So far, Milestone 3
v Research the feasible practices that software companies can use to protect their softwares from “cracking”, and test these practices on my own, if possible.
v Write a report on the cracking process and the practices that can be used for piracy-prevention.
So far, Milestone 4
· Deliverables
v Learning notes and summary on blog or tumblr every week for the objectives mentioned above
v Source codes and executables of keygen or patch for the two kinds of softwares mentioned above
v A report on the software activation validation issues
· Misc
v Please return feedback at [email protected] or [email protected]
1 note
·
View note
Text
Security Everywhere 1
Sitting in the main library @ UNSW; little sick of reading about the Deepwater Horizon case so I'm just gonna go ahead and write my first Security Everywhere blog entry. In this blog, I'll be quickly introducing the obvious security mechanisms of the main library and realistic methods of breaching a couple of these mechanisms to gain unauthorised access to the upper floors after-hours.
In the main library on the Kensington campus, there are your very typical theft and illegal entry deterrents; hourly security guard patrols, ID scanning doors, security cameras, shutter doors closing off day floors, motion sensors, notes being left around with a bold image of a big brother style eye and the words 'THIEVES ARE EVERYWHERE'.
Other more interesting mechanisms include:
- Fixed windows and secured, thick window frames. They’re nailed shut and seem to be made of aluminium. Uninteresting I know, but I find it curious how many used to be able to be opened.
- Sticky tape to secure a doorknob in place so that it could not be turned, preventing opening of said door. Very effective
Needless to say, library security is fairly minimal compared to some other buildings on campus and it would be fairly easy for an intruder to breach the above security mechanisms to gain unauthorised access to the upper floors.
First method comes to mind is simply to enter the upper floors in library hours and not leaving. However, this is easier said than done as there are thorough-ish security sweeps done at closing time and these upper floors are quite open meaning there are little to no places one can hide out. Which would force us to be a little creative in how we approach this method...
Method 1: Hiding in Bean Bags
Difficulty: Easy
Social Engineering: Zero
Cost: A lot of time and 20 dollars if you're too big
There are large beanbags on floors 3 and 7. If you are small enough to fit inside one, then you could simply (discreetly) unzip the beanbag, remove some of its stuffing and hide out there. If you aren't, bring your own beanbag and hide in that.
Other more difficult variations include: opening up some of the couches and hiding in those, removing an overhead panel, hiding amongst the wires, hiding in a janitorial cart.
Method 2: Imitating/Becoming Authority/Janitorial Staff
Difficulty: Very Hard
Social Engineering: Depends on the method you use but on average - Very High
Cost: Cost of a security guard uniform, fake keycard and even more time
I'd imagine it'd be quite difficult to actually imitate a security guard, as most of them are assigned access keys which would be pretty difficult to replicate. However, one could simply steal one though I'd have to imagine they have methods of remotely disabling stolen keys, once it was discovered stolen.
Easiest method would be to dress up, pretend to be a guard on their first day or something wearing the uniform with a fake badge and walkie talkie comms to match. And simply walk around at around closing time, chat to the other guards and generally fit in and then wander off into a bathroom and wait.
One could also pretend to be a janitor, although it might be awkward when you run into the assigned janitor of the floor.
1 note
·
View note
