#Cloud data
Explore tagged Tumblr posts
Text
Geneva-based Infomaniak has been recovering 100 per cent of the electricity it uses since November 2024.
The recycled power will be able to fuel the centralised heating network in the Canton of Geneva and benefit around 6,000 households.
The centre is currently operating at 25 per cent of its potential capacity. It aims to reach full capacity by 2028.
Swiss data centre leads the way for a greener cloud industry
The data centre hopes to point to a greener way of operating in the electricity-heavy cloud industry.
"In the real world, data centres convert electricity into heat. With the exponential growth of the cloud, this energy is currently being released into the atmosphere and wasted,” Boris Siegenthaler, Infomaniak's Founder and Chief Strategy Officer, told news site FinanzNachrichten.
“There is an urgent need to upgrade this way of doing things, to connect these infrastructures to heating networks and adapt building standards."
Infomaniak has received several awards for the energy efficiency of its complexes, which operate without air conditioning - a rarity for hot data centres.
The company also builds infrastructure underground so that it doesn’t have an impact on the environment.
Swiss data centre recycles heat for homes
At Infomaniak, all the electricity that powers equipment like servers, inverters and ventilation is converted into heat at a temperature of 40 to 45C.
This is then channelled to an air/water exchanger which filters it into a hot water circuit. Heat pumps are used to increase its temperature to 67C in summer and 85C in winter.
How many homes will be heated by the data centre?
When the centre is operating at full capacity, it will supply Geneva’s heating network with 1.7 megawatts, the amount needed for 6,000 households per year or for 20,000 people to take a 5-minute shower every day.
This means the Canton of Geneva can save 3,600 tonnes of CO2 equivalent (tCO2eq) of natural gas every year, or 5,500 tCO2eq of pellets annually.
The system in place at Infomaniak’s data centre is free to be reproduced by other companies. There is a technical guide available explaining how to replicate the model and a summary for policymakers that advises how to improve design regulations and the sustainability of data centres.
#good news#environmentalism#science#environment#climate change#climate crisis#switzerland#geneva#Infomaniak#cloud storage#cloud data#carbon emissions#heat pumps
45 notes
·
View notes
Text
Tencent Hunyuan3D-PolyGen: A model for 'art-grade' 3D assets
New Post has been published on https://thedigitalinsider.com/tencent-hunyuan3d-polygen-a-model-for-art-grade-3d-assets/
Tencent Hunyuan3D-PolyGen: A model for 'art-grade' 3D assets
Tencent has released a model that could be quite literally game-changing for how developers create 3D assets.
The new Hunyuan3D-PolyGen model is Tencent’s first attempt at delivering what they’re calling “art-grade” 3D generation, specifically built for the professionals who craft the digital worlds we play in.
Creating high-quality 3D assets has always been a bottleneck for game developers, with artists spending countless hours perfecting wireframes and wrestling with complex geometry. Tencent reckons they’ve found a way to tackle these headaches head-on, potentially transforming how studios approach asset creation entirely.
Levelling up generating 3D assets
The secret sauce behind Hunyuan3D-PolyGen lies in what Tencent calls BPT technology. In layman’s terms, it means they’ve figured out how to compress massive amounts of 3D data without losing the detail that matters. In practice, that means it’s possible to generate 3D assets with tens of thousands of polygons that actually look professional enough to ship in a commercial game.
🚀Introducing Hunyuan3D-PolyGen, our newly upgraded and industry-first art-grade 3D generative model. It brings effortless intelligent retopology, making AI-generated models ready for professional art pipelines.
✅ Superior Mesh Topology: Our self-developed mesh autoregressive… pic.twitter.com/Lwy0dfGZkx
— Hunyuan (@TencentHunyuan) July 7, 2025
What’s particularly clever is how the system handles both triangular and quadrilateral faces. If you’ve ever tried to move 3D assets between different software packages, you’ll know why this matters. Different engines and tools have their preferences, and compatibility issues have historically been a nightmare for studios trying to streamline their workflows.
According to technical documentation, the system utilises an autoregressive mesh generation framework that performs spatial inference through explicit and discrete vertex and patch modelling. This approach ensures the production of high-quality 3D models that meet stringent artistic specifications demanded by commercial game development.
Hunyuan3D-PolyGen works through what’s essentially a three-step dance. First, it takes existing 3D meshes and converts them into a language the AI can understand.
Using point cloud data as a starting point, the system then generates new mesh instructions using techniques borrowed from natural language processing. It’s like teaching the AI to speak in 3D geometry, predicting what should come next based on what it’s already created.
Finally, the system translates these instructions back into actual 3D meshes, complete with all the vertices and faces that make up the final model. The whole process maintains geometric integrity while producing results that would make any technical artist nod in approval.
Tencent isn’t just talking about theoretical improvements that fall apart when tested in real studios; they’ve put this technology to work in their own game development studios. The results? Artists claim to report efficiency gains of over 70 percent.
The system has been baked into Tencent’s Hunyuan 3D AI creation engine and is already running across multiple game development pipelines. This means it’s being used to create actual 3D game assets that players will eventually interact with.
Teaching AI to think like an artist
One of the most impressive aspects of Hunyuan3D-PolyGen is how Tencent has approached quality control. They’ve developed a reinforcement learning system that essentially teaches the AI to recognise good work from bad work, much like how a mentor might guide a junior artist.
The system learns from feedback, gradually improving its ability to generate 3D assets that meet professional standards. This means fewer duds and more usable results straight out of the box. For studios already stretched thin on resources, this kind of reliability could be transformative.
The gaming industry has been grappling with a fundamental problem for years. While AI has made impressive strides in generating 3D models, most of the output has been, quite frankly, not good enough for commercial use. The gap between “looks impressive in a demo” and “ready for a AAA game” has been enormous.
Tencent’s approach with Hunyuan3D-PolyGen feels different because it’s clearly been designed by people who understand what actual game development looks like. Instead of chasing flashy demonstrations, they’ve focused on solving real workflow problems that have been frustrating developers for decades.
As development costs continue to spiral and timelines get ever more compressed, tools that can accelerate asset creation without compromising quality become incredibly valuable.
The release of Hunyuan3D-PolyGen hints at a future where the relationship between human creativity and AI assistance becomes far more nuanced. Rather than replacing artists, this technology appears designed to handle the grunt work of creating 3D assets, freeing up talented creators to focus on the conceptual and creative challenges that humans excel at.
This represents a mature approach to AI integration in creative industries. Instead of the usual “AI will replace everyone” narrative, we’re seeing tools that augment human capabilities rather than attempt to replicate them entirely. The 70 percent efficiency improvement reported by Tencent’s teams suggests this philosophy is working in practice.
The broader implications are fascinating to consider. As these systems become more sophisticated and reliable, we might see a fundamental shift in how game development studios are structured and how projects are scoped. The technology could democratise high-quality asset creation, potentially allowing smaller studios to compete with larger operations that traditionally had resource advantages.
The success of Hunyuan3D-PolyGen could well encourage other major players to accelerate their own AI-assisted creative tools beyond generating 3D assets, potentially leading to a new wave of productivity improvements across the industry. For game developers who’ve been watching AI developments with a mixture of excitement and scepticism, this might be the moment when the technology finally delivers on its promises.
See also: UK and Singapore form alliance to guide AI in finance
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#3d#ai#ai & big data expo#AI assistance#AI integration#amp#approach#Art#Artificial Intelligence#artists#assets#automation#AutoRegressive#Big Data#box#california#Cloud#cloud data#Companies#comprehensive#compress#conference#craft#creativity#creators#cyber#cyber security#dance#data#developers
2 notes
·
View notes
Audio
3 notes
·
View notes
Text
How Modern Data Engineering Powers Scalable, Real-Time Decision-Making
In today's world, driven by technology, businesses have evolved further and do not want to analyze data from the past. Everything from e-commerce websites providing real-time suggestions to banks verifying transactions in under a second, everything is now done in a matter of seconds. Why has this change taken place? The modern age of data engineering involves software development, data architecture, and cloud infrastructure on a scalable level. It empowers organizations to convert massive, fast-moving data streams into real-time insights.
From Batch to Real-Time: A Shift in Data Mindset
Traditional data systems relied on batch processing, in which data was collected and analyzed after certain periods of time. This led to lagging behind in a fast-paced world, as insights would be outdated and accuracy would be questionable. Ultra-fast streaming technologies such as Apache Kafka, Apache Flink, and Spark Streaming now enable engineers to create pipelines that help ingest, clean, and deliver insights in an instant. This modern-day engineering technique shifts the paradigm of outdated processes and is crucial for fast-paced companies in logistics, e-commerce, relevancy, and fintech.
Building Resilient, Scalable Data Pipelines
Modern data engineering focuses on the construction of thoroughly monitored, fault-tolerant data pipelines. These pipelines are capable of scaling effortlessly to higher volumes of data and are built to accommodate schema changes, data anomalies, and unexpected traffic spikes. Cloud-native tools like AWS Glue and Google Cloud Dataflow with Snowflake Data Sharing enable data sharing and integration scaling without limits across platforms. These tools make it possible to create unified data flows that power dashboards, alerts, and machine learning models instantaneously.
Role of Data Engineering in Real-Time Analytics
Here is where these Data Engineering Services make a difference. At this point, companies providing these services possess considerable technical expertise and can assist an organization in designing modern data architectures in modern frameworks aligned with their business objectives. From establishing real-time ETL pipelines to infrastructure handling, these services guarantee that your data stack is efficient and flexible in terms of cost. Companies can now direct their attention to new ideas and creativity rather than the endless cycle of data management patterns.
Data Quality, Observability, and Trust
Real-time decision-making depends on the quality of the data that powers it. Modern data engineering integrates practices like data observability, automated anomaly detection, and lineage tracking. These ensure that data within the systems is clean and consistent and can be traced. With tools like Great Expectations, Monte Carlo, and dbt, engineers can set up proactive alerts and validations to mitigate issues that could affect economic outcomes. This trust in data quality enables timely, precise, and reliable decisions.
The Power of Cloud-Native Architecture
Modern data engineering encompasses AWS, Azure, and Google Cloud. They provide serverless processing, autoscaling, real-time analytics tools, and other services that reduce infrastructure expenditure. Cloud-native services allow companies to perform data processing, as well as querying, on exceptionally large datasets instantly. For example, with Lambda functions, data can be transformed. With BigQuery, it can be analyzed in real-time. This allows rapid innovation, swift implementation, and significant long-term cost savings.
Strategic Impact: Driving Business Growth
Real-time data systems are providing organizations with tangible benefits such as customer engagement, operational efficiency, risk mitigation, and faster innovation cycles. To achieve these objectives, many enterprises now opt for data strategy consulting, which aligns their data initiatives to the broader business objectives. These consulting firms enable organizations to define the right KPIs, select appropriate tools, and develop a long-term roadmap to achieve desired levels of data maturity. By this, organizations can now make smarter, faster, and more confident decisions.
Conclusion
Investing in modern data engineering is more than an upgrade of technology — it's a shift towards a strategic approach of enabling agility in business processes. With the adoption of scalable architectures, stream processing, and expert services, the true value of organizational data can be attained. This ensures that whether it is customer behavior tracking, operational optimization, or trend prediction, data engineering places you a step ahead of changes before they happen, instead of just reacting to changes.
1 note
·
View note
Text
Get These 5 Ms of Cloud Data Migrations Right
0 notes
Text
How the Demand for DevOps Professionals is Exponentially Increasing

In today’s fast-paced technology landscape, the demand for DevOps professionals is skyrocketing. As businesses strive for greater efficiency, faster deployment, and improved collaboration, the role of DevOps has become crucial. This blog explores why the demand for DevOps professionals is exponentially increasing and how enrolling in a DevOps course in Mumbai can be your ticket to a successful career in this field.
The Rise of DevOps
What is DevOps?
DevOps is a set of practices that combines software development (Dev) and IT operations (Ops). The goal is to shorten the development lifecycle and provide continuous delivery with high software quality. This approach fosters a culture of collaboration between development and operations teams, leading to more efficient workflows and quicker product releases.
Why is Demand Growing?
Increased Need for Speed: Businesses are under pressure to deliver updates and new features rapidly. DevOps methodologies enable faster software development and deployment, making organizations more competitive.
Enhanced Collaboration: DevOps breaks down silos between teams, promoting better communication and collaboration. Companies are realizing that this integrated approach improves overall productivity.
Adoption of Cloud Technologies: As organizations migrate to the cloud, the need for professionals who understand both development and operational aspects of cloud environments is rising. DevOps professionals are key in managing these transitions effectively.
Focus on Automation: Automation is a core component of DevOps. The demand for professionals skilled in automation tools and practices is increasing, as organizations seek to minimize manual errors and optimize processes.
The Skill Set of a DevOps Professional
To succeed in the field of DevOps, certain skills are essential:
Continuous Integration/Continuous Deployment (CI/CD): Proficiency in CI/CD tools is critical for automating the software release process.
Cloud Computing: Understanding cloud platforms (AWS, Azure, Google Cloud) is crucial for managing and deploying applications in cloud environments.
Scripting and Automation: Knowledge of scripting languages (Python, Bash) and automation tools (Ansible, Puppet) is important for streamlining processes.
Monitoring and Logging: Familiarity with monitoring tools (Nagios, Grafana) to track application performance and troubleshoot issues is vital.
Collaboration Tools: Proficiency in tools like Slack, Jira, and Trello facilitates effective communication among teams.
Why Enroll in a DevOps Course in Mumbai?
Advantages of Taking a DevOps Course in Mumbai
Structured Learning: A DevOps course in Mumbai provides a structured curriculum that covers essential concepts, tools, and practices in depth.
Hands-On Experience: Many courses offer practical labs and projects, allowing you to apply your knowledge in real-world scenarios.
Networking Opportunities: Studying in Mumbai gives you access to a vibrant tech community and potential networking opportunities with industry professionals.
Career Advancement: Completing a DevOps course enhances your resume and makes you a more attractive candidate for employers in this high-demand field.
Future Outlook for DevOps Professionals
The future looks bright for DevOps professionals. As more organizations adopt DevOps practices, the demand for skilled individuals will continue to grow making and this is where DevOps Course in Mumbai plays a major role. Companies are increasingly recognizing the value of DevOps in achieving business goals, leading to a more significant investment in training and hiring.
In addition, emerging technologies such as artificial intelligence and machine learning are starting to intersect with DevOps practices. Professionals who can bridge these areas will be even more sought after, creating new opportunities for career advancement.
Conclusion
The demand for DevOps professionals is increasing at an unprecedented rate as businesses strive for greater efficiency, speed, and collaboration. By enrolling in a DevOps course in Mumbai, you can acquire the skills and knowledge needed to excel in this thriving field.
#cloud computing#cloudcomputing#cloud storage#cloud data#cloudsecurity#devops#devops course#devops training#devops certification#cloud computing course#technology
0 notes
Text
In today's digital era, data is the lifeblood of any business. The ability to efficiently collect, store, manage, and analyze data can make the difference between thriving and merely surviving in a competitive marketplace. Castle Interactive understands this dynamic and offers cutting-edge cloud data solutions designed to empower your business. Let's explore how these solutions can transform your operations and drive growth.
0 notes
Text
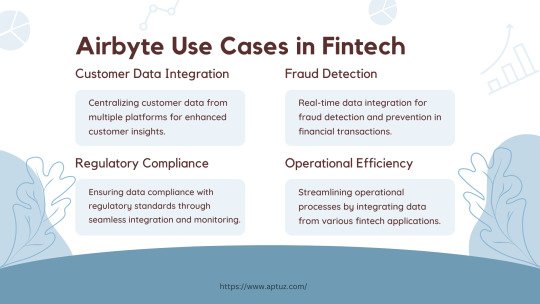
Explore the impactful use cases of Airbyte in the fintech industry, from centralizing customer data for enhanced insights to real-time fraud detection and ensuring regulatory compliance. Learn how Airbyte drives operational efficiency by streamlining data integration across various fintech applications, providing businesses with actionable insights and improved processes.
Know more at: https://bit.ly/3UbqGyT
#Fintech#data analytics#data engineering#technology#Airbyte#ETL#ELT#Cloud data#Data Integration#Data Transformation#Data management#Data extraction#Data Loading#Tech videos
0 notes
Text
Data warehousing has become a trending avenue for enterprises to better manage large volumes of data. Leveraging it with the latest capabilities will help you stay relevant and neck-to-neck with the competition. Here are a few data warehousing trends that you should keep in mind for 2024 for your data warehousing requirements.
#Data warehousing#cloud Data warehousing#cloud data#data warehouse#2024#trends 2024#data warehousing trends
0 notes
Text
Data Quality Management in Master Data Management: Ensuring Accurate and Reliable Information
Introduction: In the digital age, data is often referred to as the new gold. However, just like gold, data needs to be refined and polished to extract its true value. This is where Data Quality Management (DQM), offered by master data management companies, steps in, playing a pivotal role in the success of Master Data Management (MDM) initiatives. In this blog post, we'll explore the critical importance of data quality within MDM and delve into the techniques that organizations can employ, with the assistance of master data management services, to achieve and maintain accurate and reliable master data.
The Crucial Role of Data Quality in MDM: Data quality is the foundation upon which effective MDM is built, facilitated by cloud data services. Accurate, consistent, and reliable master data ensures that business decisions are well-informed and reliable. Poor data quality can lead to erroneous insights, wasted resources, and missed opportunities. Therefore, implementing robust data quality management practices, with the support of cloud data management services, is essential.
Techniques for Data Quality Management in MDM:
Data Profiling: Data profiling involves analyzing data to gain insights into its structure, content, and quality, enabled by data analytics consulting services. By identifying anomalies, inconsistencies, and gaps, organizations can prioritize their data quality efforts effectively.
Actionable Tip: Utilize automated data profiling tools, including cloud data management services, to uncover hidden data quality issues across your master data.
Data Cleansing: Data cleansing is the process of identifying and rectifying errors, inconsistencies, and inaccuracies within master data, supported by cloud data management solutions. This involves standardizing formats, removing duplicates, and correcting inaccurate entries.
Actionable Tip: Establish data quality rules and automated processes, with the assistance of data analytics consulting services, to regularly cleanse and validate master data.
Data Enrichment: Data enrichment involves enhancing master data by adding valuable information from trusted external sources, facilitated by data analytics consulting services. This enhances data completeness and accuracy, leading to better decision-making.
Actionable Tip: Integrate third-party data sources and APIs, in collaboration with master data management solutions, to enrich your master data with up-to-date and relevant information.
Ongoing Monitoring: Data quality is not a one-time task but an ongoing process, supported by cloud data services. Regularly monitor and assess the quality of your master data, with the assistance of cloud data management services, to detect and address issues as they arise.
Actionable Tip: Implement data quality metrics and key performance indicators (KPIs), leveraging cloud data management solutions, to track the health of your master data over time.
Real-World Examples:
Example 1: Data Profiling at Retail Innovators Inc. Retail Innovators Inc., in partnership with master data management services, implemented data profiling tools to analyze their customer master data. They discovered that approximately 15% of customer records had incomplete contact information. By addressing this issue, with the support of cloud data management services, they improved customer communication and reduced delivery failures.
Example 2: Data Cleansing at Healthcare Solutions Co. Healthcare Solutions Co. partnered with cloud data management services and embarked on a data cleansing initiative for their patient master data. They removed duplicate patient records and corrected inaccuracies in demographic details. This led to more accurate patient billing and streamlined appointment scheduling.
Example 3: Data Enrichment at Financial Services Group. Financial Services Group collaborated with data analytics consulting services and integrated external data sources to enrich their client master data. By adding socio-economic indicators, they gained deeper insights into their clients' financial needs and improved personalized financial advisory services.
Conclusion: In the world of Master Data Management, data quality is not an option; it's a necessity, facilitated by cloud data management services. Effective Data Quality Management, supported by master data management solutions, ensures that your master data remains accurate, consistent, and reliable, forming the bedrock of successful MDM initiatives. By leveraging techniques such as data profiling, cleansing, enrichment, and ongoing monitoring, in collaboration with data analytics consulting services, organizations can unlock the true potential of their master data. This enables them to make more informed decisions, enhance customer experiences, and gain a competitive edge in the marketplace. Remember, the journey to high-quality master data begins with a commitment to data excellence through diligent Data Quality Management.
0 notes
Text
Elеvating Cloud Data Encryption: Exploring Nеxt-Gеnеration Tеchniquеs
In an еra whеrе data brеachеs and cybеr thrеats havе bеcomе morе sophisticatеd than еvеr, thе nееd for robust data protеction mеasurеs has intеnsifiеd. Cloud computing, which offers immеnsе flеxibility and scalability, also introducеs sеcurity concerns duе to thе dеcеntralizеd naturе of data storagе. This is whеrе data еncryption еmеrgеs as a powerful solution, and as technology еvolvеs, so do thе tеchniquеs for safеguarding sеnsitivе information in thе cloud.
Related Post: The Importance of Cloud Security in Business

Thе Crucial Rolе of Cloud Data Encryption:
Cloud data encryption involves transforming data into an unrеadablе format using cryptographic algorithms. This еncryptеd data can only bе dеciphered with a specific kеy, which is hеld by authorizеd usеrs. Thе importancе of еncryption liеs in its ability to thwart unauthorizеd accеss, еvеn if an attackеr manages to brеach thе sеcurity pеrimеtеr. It еnsurеs that еvеn if data is intеrcеptеd, it rеmains indеciphеrablе and thus usеlеss to malicious actors.
Thе Evolution of Encryption Tеchniques:
As cyber thrеats grow more sophisticatеd, еncryption tеchniquеs must also еvolvе to kееp pacе. Lеt's dеlvе into somе of thе nеxt-gеnеration еncryption mеthods that arе еnhancing cloud data sеcurity:
Homomorphic Encryption: This groundbrеaking tеchnique allows computations to bе pеrformеd on еncryptеd data without dеcrypting it first. It еnsures that sеnsitivе data rеmains еncryptеd throughout procеssing, minimizing thе risk of еxposurе.
Quantum Encryption: With thе advent of quantum computеrs, traditional еncryption mеthods could bе compromisеd. Quantum еncryption lеvеragеs thе principlеs of quantum mеchanics to crеatе еncryption kеys that arе virtually impossiblе to intеrcеpt or rеplicatе.
Post-Quantum Encryption: This involvеs dеvеloping еncryption algorithms that arе resistant to attacks from both classical and quantum computеrs. As quantum computing power grows, post-quantum еncryption will play a crucial role in maintaining data sеcurity.
Multi-Party Computation (MPC): MPC еnablеs multiplе partiеs to jointly computе a function ovеr thеir individual inputs whilе kееping thosе inputs privatе. This tеchniquе adds an еxtra layеr of sеcurity by distributing data and computations across different еntitiеs.
Attributе-Basеd Encryption (ABE): ABE allows data access based on attributеs rather than specific kеys. It's particularly useful in cloud еnvironmеnts whеrе multiplе usеrs with varying lеvеls of accеss might nееd to intеract with еncryptеd data.
Tokеnization: Tokеnization involvеs rеplacing sеnsitivе data with tokеns that havе no inhеrеnt mеaning. Thеsе tokеns can bе usеd for procеssing and analysis without еxposing thе actual sеnsitivе information.
Implementing Nеxt-Gеnеration Encryption Tеchniquеs
Whilе next-genеration еncryption tеchniquеs offеr еnhancеd sеcurity, thеy also bring challеngеs in tеrms of implеmеntation and managеmеnt:
Kеy Managеmеnt: Robust еncryption rеliеs on еffеctivе key management. With new tеchniquеs, key gеnеration, storage, and rotation bеcomе morе complеx and rеquirе mеticulous attеntion.
Pеrformancе Overhead: Somе advancеd еncryption mеthods can introduce computational ovеrhеad, potentially affеcting thе pеrformancе of applications and systеms. Striking a balancе bеtwееn sеcurity and pеrformancе is crucial.
Intеgration with Existing Systеms: Intеgrating nеxt-gеnеration еncryption into еxisting cloud еnvironmеnts and applications can bе intricatе. It oftеn rеquirеs carеful planning and adaptation of currеnt architеcturе.
Usеr Expеriеncе: Encryption should not hindеr usеr еxpеriеncе. Accessing еncryptеd data should bе sеamlеss for authorizеd usеrs whilе maintaining stringеnt sеcurity mеasurеs.
Bеst Practicеs for Nеxt-Gеnеration Cloud Data Encryption
Assess Your Nееds: Undеrstand your data, its sеnsitivity, and rеgulatory requirеmеnts to detеrminе which еncryption tеchniquеs arе most suitablе.
End-to-End Encryption: Implemеnt encryption throughout thе data lifеcyclе – at rest, in transit, and during procеssing.
Thorough Kеy Managеmеnt: Dеvotе significant attеntion to kеy managеmеnt, including gеnеration, storagе, rotation, and accеss control.
Rеgular Audits and Updates: Encryption is not an onе-timе task. Rеgular audits and updatеs еnsure that your еncryption practicеs stay еffеctive against evolving threats.
Training and Awareness: Educatе your tеam about еncryption bеst practices to prеvеnt inadvеrtеnt data еxposure.
Vendor Evaluation: If you are using a cloud sеrvicе providеr, еvaluatе thеir еncryption practicеs and ensurе they align with your security requiremеnts.
Thе Path Forward
Nеxt-genеration еncryption tеchniquеs arе shaping thе futurе of cloud data sеcurity. As data brеachеs bеcomе more sophisticatеd, thе need for strongеr еncryption grows. Whilе thеsе tеchniquеs offеr еnhancеd protеction, they also rеquirе a comprеhеnsivе undеrstanding of thеir intricacies and challengеs. Implеmеnting thеm еffеctivеly dеmands collaboration bеtwееn sеcurity еxpеrts, cloud architеcts, and IT professionals.
Conclusion
In conclusion, as technology еvolvеs, so do thе thrеats to our data. Nеxt-genеration encryption tеchniquеs hold thе kеy to safеguarding sеnsitivе information in thе cloud. By еmbracing thеsе advancеd mеthods and adhеring to best practicеs, organizations can navigatе thе intricatе landscapе of cloud data sеcurity with confidеncе, еnsuring that thеir data rеmains shiеldеd from thе еvеr-еvolving rеalm of cybеr thrеats.
1 note
·
View note
Text

415 notes
·
View notes
Text
Future-Ready Enterprises: The Crucial Role of Large Vision Models (LVMs)
New Post has been published on https://thedigitalinsider.com/future-ready-enterprises-the-crucial-role-of-large-vision-models-lvms/
Future-Ready Enterprises: The Crucial Role of Large Vision Models (LVMs)


What are Large Vision Models (LVMs)
Over the last few decades, the field of Artificial Intelligence (AI) has experienced rapid growth, resulting in significant changes to various aspects of human society and business operations. AI has proven to be useful in task automation and process optimization, as well as in promoting creativity and innovation. However, as data complexity and diversity continue to increase, there is a growing need for more advanced AI models that can comprehend and handle these challenges effectively. This is where the emergence of Large Vision Models (LVMs) becomes crucial.
LVMs are a new category of AI models specifically designed for analyzing and interpreting visual information, such as images and videos, on a large scale, with impressive accuracy. Unlike traditional computer vision models that rely on manual feature crafting, LVMs leverage deep learning techniques, utilizing extensive datasets to generate authentic and diverse outputs. An outstanding feature of LVMs is their ability to seamlessly integrate visual information with other modalities, such as natural language and audio, enabling a comprehensive understanding and generation of multimodal outputs.
LVMs are defined by their key attributes and capabilities, including their proficiency in advanced image and video processing tasks related to natural language and visual information. This includes tasks like generating captions, descriptions, stories, code, and more. LVMs also exhibit multimodal learning by effectively processing information from various sources, such as text, images, videos, and audio, resulting in outputs across different modalities.
Additionally, LVMs possess adaptability through transfer learning, meaning they can apply knowledge gained from one domain or task to another, with the capability to adapt to new data or scenarios through minimal fine-tuning. Moreover, their real-time decision-making capabilities empower rapid and adaptive responses, supporting interactive applications in gaming, education, and entertainment.
How LVMs Can Boost Enterprise Performance and Innovation?
Adopting LVMs can provide enterprises with powerful and promising technology to navigate the evolving AI discipline, making them more future-ready and competitive. LVMs have the potential to enhance productivity, efficiency, and innovation across various domains and applications. However, it is important to consider the ethical, security, and integration challenges associated with LVMs, which require responsible and careful management.
Moreover, LVMs enable insightful analytics by extracting and synthesizing information from diverse visual data sources, including images, videos, and text. Their capability to generate realistic outputs, such as captions, descriptions, stories, and code based on visual inputs, empowers enterprises to make informed decisions and optimize strategies. The creative potential of LVMs emerges in their ability to develop new business models and opportunities, particularly those using visual data and multimodal capabilities.
Prominent examples of enterprises adopting LVMs for these advantages include Landing AI, a computer vision cloud platform addressing diverse computer vision challenges, and Snowflake, a cloud data platform facilitating LVM deployment through Snowpark Container Services. Additionally, OpenAI, contributes to LVM development with models like GPT-4, CLIP, DALL-E, and OpenAI Codex, capable of handling various tasks involving natural language and visual information.
In the post-pandemic landscape, LVMs offer additional benefits by assisting enterprises in adapting to remote work, online shopping trends, and digital transformation. Whether enabling remote collaboration, enhancing online marketing and sales through personalized recommendations, or contributing to digital health and wellness via telemedicine, LVMs emerge as powerful tools.
Challenges and Considerations for Enterprises in LVM Adoption
While the promises of LVMs are extensive, their adoption is not without challenges and considerations. Ethical implications are significant, covering issues related to bias, transparency, and accountability. Instances of bias in data or outputs can lead to unfair or inaccurate representations, potentially undermining the trust and fairness associated with LVMs. Thus, ensuring transparency in how LVMs operate and the accountability of developers and users for their consequences becomes essential.
Security concerns add another layer of complexity, requiring the protection of sensitive data processed by LVMs and precautions against adversarial attacks. Sensitive information, ranging from health records to financial transactions, demands robust security measures to preserve privacy, integrity, and reliability.
Integration and scalability hurdles pose additional challenges, especially for large enterprises. Ensuring compatibility with existing systems and processes becomes a crucial factor to consider. Enterprises need to explore tools and technologies that facilitate and optimize the integration of LVMs. Container services, cloud platforms, and specialized platforms for computer vision offer solutions to enhance the interoperability, performance, and accessibility of LVMs.
To tackle these challenges, enterprises must adopt best practices and frameworks for responsible LVM use. Prioritizing data quality, establishing governance policies, and complying with relevant regulations are important steps. These measures ensure the validity, consistency, and accountability of LVMs, enhancing their value, performance, and compliance within enterprise settings.
Future Trends and Possibilities for LVMs
With the adoption of digital transformation by enterprises, the domain of LVMs is poised for further evolution. Anticipated advancements in model architectures, training techniques, and application areas will drive LVMs to become more robust, efficient, and versatile. For example, self-supervised learning, which enables LVMs to learn from unlabeled data without human intervention, is expected to gain prominence.
Likewise, transformer models, renowned for their ability to process sequential data using attention mechanisms, are likely to contribute to state-of-the-art outcomes in various tasks. Similarly, Zero-shot learning, allowing LVMs to perform tasks they have not been explicitly trained on, is set to expand their capabilities even further.
Simultaneously, the scope of LVM application areas is expected to widen, encompassing new industries and domains. Medical imaging, in particular, holds promise as an avenue where LVMs could assist in the diagnosis, monitoring, and treatment of various diseases and conditions, including cancer, COVID-19, and Alzheimer’s.
In the e-commerce sector, LVMs are expected to enhance personalization, optimize pricing strategies, and increase conversion rates by analyzing and generating images and videos of products and customers. The entertainment industry also stands to benefit as LVMs contribute to the creation and distribution of captivating and immersive content across movies, games, and music.
To fully utilize the potential of these future trends, enterprises must focus on acquiring and developing the necessary skills and competencies for the adoption and implementation of LVMs. In addition to technical challenges, successfully integrating LVMs into enterprise workflows requires a clear strategic vision, a robust organizational culture, and a capable team. Key skills and competencies include data literacy, which encompasses the ability to understand, analyze, and communicate data.
The Bottom Line
In conclusion, LVMs are effective tools for enterprises, promising transformative impacts on productivity, efficiency, and innovation. Despite challenges, embracing best practices and advanced technologies can overcome hurdles. LVMs are envisioned not just as tools but as pivotal contributors to the next technological era, requiring a thoughtful approach. A practical adoption of LVMs ensures future readiness, acknowledging their evolving role for responsible integration into business processes.
#Accessibility#ai#Alzheimer's#Analytics#applications#approach#Art#artificial#Artificial Intelligence#attention#audio#automation#Bias#Business#Cancer#Cloud#cloud data#cloud platform#code#codex#Collaboration#Commerce#complexity#compliance#comprehensive#computer#Computer vision#container#content#covid
2 notes
·
View notes
Audio
3 notes
·
View notes
Text


elle n vlad 2025
#thought i lost these 2 forever#3 months ago i lost not only my mods folder but my tray files as well...nearly killed me tbh#but then I got these two back n im not so sad abt it anymore :)#my build folder rip 2019-2024 will haunt me for a while#im also getting this wierd bug where my game will CTD as soon as I add ANY new cc with “game data is corrupt or missing”#so i go back n delete random pieces of cc and it will load fine again but the thing is the cc i deleted isn't the cause of the crash#like I added some remussiron eye cc and it crashes I take it out and it runs put it back in it crashes#but if i add remussirion eye cc back AND delete a random hair it will run fine#so my mod folder is an orobors eating itself atm#maybe its bc windows 11 for some god forsaken reason puts the document folder in your one drive which is uploaded to a cloud service u#need to pay for n well one day i will kill whoever was responsible for that#my sims#vladislaus straud#elle de vampiro
395 notes
·
View notes
Text
Cloud Data Migration for MSPs: CloudFuze’s Reselling Benefits
https://www.cloudfuze.com/cloud-data-migration-for-msps-cloudfuzes-reselling-benefits/
0 notes