#Computer security service
Explore tagged Tumblr posts
Text


Website: http://triuneinfotech.com/
Address: 31886 Cotton Thorn Ct, Murrieta, CA 92563
Phone: +1 (951) 249-7775
Triune InfoTech has been providing expert IT support in Murrieta since 2013, helping businesses boost productivity and profitability through streamlined technology solutions. We offer reliable computer support, data recovery, cybersecurity, networking, consulting, and repair services—all under a simple flat-rate monthly plan. Our proactive service model ensures timely solutions, expert guidance, and predictable costs. As a trusted computer service provider, IT consultant, and tech support partner, we’re committed to helping your business thrive. Contact us today to get started!
#Computer service#Computer consultant#Data recovery service#Computer repair service#Computer security service#Computer networking service
1 note
·
View note
Text
Title: Business IT Service Corps
Description: Business IT Service Corps is built upon a foundation of dedication and expertise. Each team member has a minimum of 15 years of experience in information technology, and we are proud of the knowledge and insights we can bring.
Website URL: https://bitscorps.com/
Maps URL: https://maps.app.goo.gl/zUME3MYoZ5NTLHWP6
1 note
·
View note
Text
Secure and Scalable Cloud Server Management at Atcuality
For businesses seeking to enhance scalability and maintain top-tier security, Atcuality provides unparalleled cloud server management services. Our solutions cover all aspects of cloud server maintenance, including load balancing, patch management, data backups, and disaster recovery planning. Our experienced professionals work with cutting-edge tools to ensure that your servers are secure, efficient, and scalable to meet changing business needs. Whether you operate in e-commerce, finance, or technology, we tailor our services to align with your operational goals. With Atcuality as your trusted partner, you can focus on driving growth while we handle the technical complexities of cloud management.
#seo marketing#seo services#artificial intelligence#azure cloud services#seo agency#digital marketing#seo company#iot applications#ai powered application#amazon web services#ai applications#virtual reality#augmented reality agency#augmented human c4 621#augmented and virtual reality market#augmented intelligence#augmented reality#cloud security services#cloud computing#cloud services#cloud service provider#cloud server hosting#software#devops#information technology#cash collection application#task management#blockchain#web developing company#web development
2 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
obnoxious that I can't just use a computer to do the things I've always used computers to do, now I have to use two different computers including one with specialized hardware for interfacing with an entirely different network of interdevice communication. I don't wanna turn on goddamn mfa, and it's insufferable when I have to goddamn pull out another hundreds of dollars of tech just to be allowed to use your site's search (because you forbid it unauthenticated)
#on the one hand I get that having stronger security for authentication is nice.#on the other hand though. if you don't trust the individual with whom you have to authenticate for the service they have a monopoly over#then you have to fuckin sacrifice your operational security in the name of making some other individual feel better about their lax securit#which like. fine whatever dont do business with people you dont wanna do business with. except for like. fucking github#like you want the gpl'ed source code for the quake engine#youre gonna have to endure microsoft and github and a million petty tyrants who demand every bit of data just for fundamental functionality#ugh I don't know I have any coherent complaints I'm just whinging bc I had to use two computers for a task one computer can do
5 notes
·
View notes
Text
Positioned within the vibrant cityscape of Lubbock, Texas, Precision Managed IT stands as a beacon of technological prowess and reliability in the realm of outsourcing IT support. Our strategically located office embodies accessibility and expertise, catering to businesses seeking seamless and comprehensive IT solutions in this dynamic city.
Strategically situated within Lubbock's thriving business districts, our office serves as a central hub for businesses across diverse industries, from the healthcare sector near the medical facilities to the academic enterprises surrounding Texas Tech University. This strategic placement underscores our commitment to serving the varied tapestry of Lubbock's business community.
The physical space of Precision Managed IT is meticulously designed to exude professionalism and innovation. Boasting state-of-the-art infrastructure and a conducive workspace, our office cultivates an environment that fosters collaboration, trust, and ease for businesses seeking top-tier IT support services.
Beyond merely being a physical office, Precision Managed IT embodies a team of expert professionals deeply entrenched in the intricacies of the modern IT landscape. Each team member brings forth a wealth of technical knowledge, integrity, and proactive problem-solving skills to ensure that every client receives tailored, forward-thinking solutions to their IT needs.
Precision Managed IT isn't merely a service provider; it's a strategic partner invested in the success of the businesses we serve. We actively engage with our clients, forging strong partnerships aimed at elevating their technological infrastructure, optimizing operations, and ensuring seamless growth in an increasingly digital world.
Lubbock's dynamic business environment, educational institutions, and diverse industries align perfectly with Precision Managed IT's commitment to excellence and adaptability in the outsourcing IT support realm. We strive to remain at the forefront of technological advancements, empowering businesses to thrive amidst digital transformations and challenges.
In essence, Precision Managed IT represents more than just an IT support provider—it embodies trust, expertise, and efficiency in managing and optimizing technological infrastructure. Our presence in Lubbock signifies our unwavering dedication to simplifying IT complexities for businesses while upholding values of reliability, transparency, and a steadfast commitment to exceeding expectations.
Website: http://www.precisionmanagedit.com/lubbock-tx
Address: 5307 W Loop 289 Acc Rd, Lubbock, TX, 79414
Phone Number: +1 806-692-2884
Business Hours: Monday - Sunday : 07:00 AM - 07:00 PM
2 notes
·
View notes
Text
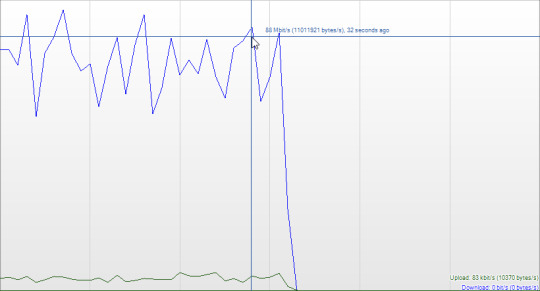
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
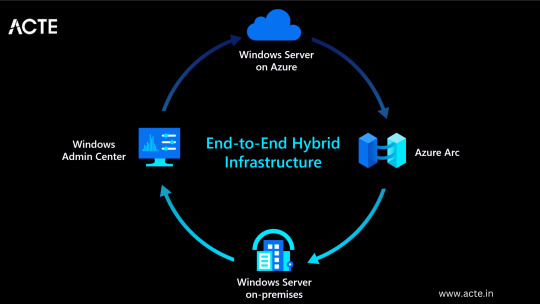
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Text
If anyone has taken their eyes off what's happening to federal workers in the US right now, here's some highlights that we're hearing from our comrades across the government who have not yet been fired:
In one building (hosting multiple agencies), the locks on the bathroom were changed so employees no longer have any access to a bathroom during the workday. People are peeing in trash cans.
Elsewhere, multiple agencies have reported that hand soap is no longer being supplied in the bathrooms.
Toilet paper supplies have not been adjusted to meet the needs of a vastly increased number of in-office employees.
Employee-owned coffee and coffee makers have been stolen or thrown away without notice (it was already illegal for taxpayer dollars to be spent on supplying federal employees with amenities like coffee, so many offices have coffee supplied by pooled employee funds).
Meanwhile, many offices don't even have potable drinking water (recurrent legionella outbreaks), so employees have to bring their own water from home.
Despite an explosion in the number of workers in offices, cleaning budgets have been slashed and many offices are not being cleaned regularly enough to remain sanitary. Pests like roaches and rats are a problem.
The firings continue, legal and illegal. Entire programs are being cut. Managers have no idea when they might lose staff. Employees are getting fired at 6pm on a weekend or finding out when they're unable to log into their computer or when they receive a shipping label in the mail to return their equipment.
Through all of this, the DOGE employees in federal workplaces are enjoying incredible and expensive luxury: AI-powered sleep pods, entire dormitories so they can live in federal buildings, nurseries for their children on site, free food and beverages, laundry services, and who knows what else. They have special security to restrict access to their areas of the buildings, including armed guards.
And I'm not just saying this to lament how bad it is for federal workers. I'm saying this because, as workers are reporting this to one another, the response is, inevitably: "This is illegal." "Yes, but who would I report it to? OPM? They're a DOGE puppet. OSHA? They've cut OSHA. The Inspectors General? Cut. The NLRB? Cut. My union? No longer recognized."
There is no one left to enforce these laws, so taking away access to basic sanitation is now effectively legal. They are doing this to federal workers, who historically have been some of the best-protected workers in the country. They are doing this specifically because it demonstrates to the public sector that it is now legal to do these things to their own workers.
17K notes
·
View notes
Text
Expert It Security Services in Sydney

Geek Seal provides trusted IT security services in Sydney, helping businesses protect their networks, data, and systems from cyber threats. Our expert team offers end-to-end cybersecurity solutions, including firewall setup, malware protection, risk assessment, and secure IT infrastructure. Whether you're a small business or a growing enterprise, Geek Seal ensures top-level IT security services in Sydney to keep your operations safe and compliant. Partner with us for reliable protection and peace of mind.
0 notes
Text
Secure Media Storage Services for Business Continuity

Intelics offers comprehensive MEDIA STORAGE SERVICES designed to safeguard your organization's critical data assets. Our solutions encompass secure tape media vaulting, rotation, transcription, and certified destruction services. With state-of-the-art facilities featuring fire-rated vaults, climate control, and 24/7 surveillance, we ensure the integrity and availability of your physical media. Trust Intelics to provide reliable, compliant, and efficient media storage solutions tailored to your business needs.
0 notes
Text
Come look at all the crazy methods no one has thought of until now.
#Cloud#Cloud computing#cloud security#cyber#cyber attack#cyber security#cyber threat#hackers#hacking#malware as a service
0 notes
Text
https://digimob.com.au/signs-of-malware-on-phone-or-laptop

#Phone Repair#Laptop Repair#Malware Detection#Mobile Security#Computer Security#Virus Removal#Tech Tips#Device Troubleshooting#Cyber Threats#Phone Performance Issues#Laptop Running Slow#Data Protection#Digimob Phone Repair#Device Malware Signs#Professional Repair Services
0 notes
Text
#cloud services#devops solutions#cloud computing#infrastructure automation#CI/CD pipeline#cloud and devops services#cloud migration#enterprise devops#cloud security#cloud-native development#cloud deployment services#continuous delivery#cloud consulting services#managed cloud services#devops consulting company#hybrid cloud solutions#cloud optimization#instep technologies
0 notes
Text
A Packing List of Apps to Download Before You Travel
So you can whip together a weekend bag or fit a fortnight’s worth of outfits into a rolling suitcase, but does your status as “packing guru” extend to your phone or tablet? Think of your device as a second carry-on, with its own packing list of apps that are essential for entertainment, getting around, safety and more. “Everyone talks about making the super app, the one place for everything you…
#Books and Literature#Computer Security#Computers and the Internet#Content Type: Service#Luggage and Packing#Mobile Applications#Museums#Passports#Transit Systems#Travel and Vacations
0 notes