#Data custodians
Explore tagged Tumblr posts
Text
Data Stewards
The term data steward never resonated well with me; I prefer the terminology business data owners, as this term conveys a stronger sense of responsibility. The role should mandate authority and respect while it is there to safeguard the integrity and value of data. So, let’s dive into and define what data stewards are—individuals appointed to oversee the data quality for specific domains or…
#business data owners#Data administrators#Data caretakers#Data controllers#Data custodians#Data guardians#Data Heroes#Data managers#data stewards#Data supervisors#Information stewards#masterdata
0 notes
Text
The Essential Role of Data Owner
Without proper governance, that data kingdom can quickly descend into chaos. That’s where the data owner steps in – the decision maker who ensures the accuracy, security, and effective use of specific data assets within your organization. The Data Owner: A Steering Committee PowerhouseWearing Many Hats: The Responsibilities of a Data OwnerThe Skills You Need to Be a Data OwnerData Owner: A…

View On WordPress
0 notes
Text
so apparently it's not just ao3 that's been having bot problems, but lots of libraries, archives, and other repositories have spent the past few months with their digital infrastructure being overrun by ai crawler bots
like the OAPEN library

or Wikimedia

#and then bc website owners are trying to guard against this behaviour#it means they're blocking out benign crawlers!!! like from the internet archive trying to do basic digital preservation#and it's making repositories think twice about making stuff open access too!!! bc of the strain on resources AND bc they're custodians#of this data that they may not have full rights to#but tell me again how ai is sooo great for research and sharing knowledge.#she speaks
16 notes
·
View notes
Text

When self-described “ocean custodian” Boyan Slat took the stage at TED 2025 in Vancouver this week, he showed viewers a reality many of us are already heartbreakingly familiar with: There is a lot of trash in the ocean.
“If we allow current trends to continue, the amount of plastic that’s entering the ocean is actually set to double by 2060,” Slat said in his TED Talk, which will be published online at a later date.
Plus, once plastic is in the ocean, it accumulates in “giant circular currents” called gyres, which Slat said operate a lot like the drain of the bathtub, meaning that plastic can enter these currents but cannot leave.
That’s how we get enormous build-ups like the Great Pacific Garbage Patch, a giant collection of plastic pollution in the ocean that is roughly twice the size of Texas.
As the founder and CEO of The Ocean Cleanup, Slat’s goal is to return our oceans to their original, clean state before 2040. To accomplish this, two things must be done.
First: Stop more plastic from entering the ocean. Second: Clean up the “legacy” pollution that is already out there and doesn’t go away by itself.
And Slat is well on his way.

Pictured: Kingston Harbour in Jamaica. Photo courtesy of The Ocean Cleanup Project
When Slat’s first TEDx Talk went viral in 2012, he was able to organize research teams to create the first-ever map of the Great Pacific Garbage Patch. From there, they created a technology to collect plastic from the most garbage-heavy areas in the ocean.
“We imagined a very long, u-shaped barrier … that would be pushed by wind and waves,” Slat explained in his Talk.
This barrier would act as a funnel to collect garbage and be emptied out for recycling.
But there was a problem.
“We took it out in the ocean, and deployed it, and it didn’t collect plastic,” Slat said, “which is a pretty important requirement for an ocean cleanup system.”
Soon after, this first system broke into two. But a few days later, his team was already back to the drawing board.
From here, they added vessels that would tow the system forward, allowing it to sweep a larger area and move more methodically through the water. Mesh attached to the barrier would gather plastic and guide it to a retention area, where it would be extracted and loaded onto a ship for sorting, processing, and recycling.
It worked.
“For 60 years, humanity had been putting plastic into the ocean, but from that day onwards, we were also taking it back out again,” Slat said, with a video of the technology in action playing on screen behind him.
To applause, he said: “It’s the most beautiful thing I’ve ever seen, honestly.”
Over the years, Ocean Cleanup has scaled up this cleanup barrier, now measuring almost 2.5 kilometers — or about 1.5 miles — in length. And it cleans up an area of the ocean the size of a football field every five seconds.

Pictured: The Ocean Cleanup's System 002 deployed in the Great Pacific Garbage Patch. Photo courtesy of The Ocean Cleanup
The system is designed to be safe for marine life, and once plastic is brought to land, it is recycled into new products, like sunglasses, accessories for electric vehicles, and even Coldplay’s latest vinyl record, according to Slat.
These products fund the continuation of the cleanup. The next step of the project is to use drones to target areas of the ocean that have the highest plastic concentration.
In September 2024, Ocean Cleanup predicted the Patch would be cleaned up within 10 years.
However, on April 8, Slat estimated “that this fleet of systems can clean up the Great Pacific Garbage Patch in as little as five years’ time.”
With ongoing support from MCS, a Netherlands-based Nokia company, Ocean Cleanup can quickly scale its reliable, real-time data and video communication to best target the problem.
It’s the largest ocean cleanup in history.
But what about the plastic pollution coming into the ocean through rivers across the world? Ocean Cleanup is working on that, too.
To study plastic pollution in other waterways, Ocean Cleanup attached AI cameras to bridges, measuring the flow of trash in dozens of rivers around the world, creating the first global model to predict where plastic is entering oceans.
“We discovered: Just 1% of the world’s rivers are responsible for about 80% of the plastic entering our oceans,” Slat said.
His team found that coastal cities in middle-income countries were primarily responsible, as people living in these areas have enough wealth to buy things packaged in plastic, but governments can’t afford robust waste management infrastructure.
Ocean Cleanup now tackles those 1% of rivers to capture the plastic before it reaches oceans.

Pictured: Interceptor 007 in Los Angeles. Photo courtesy of The Ocean Cleanup
“It’s not a replacement for the slow but important work that’s being done to fix a broken system upstream,” Slat said. “But we believe that tackling this 1% of rivers provides us with the only way to rapidly close the gap.”
To clean up plastic waste in rivers, Ocean Cleanup has implemented technology called “interceptors,” which include solar-powered trash collectors and mobile systems in eight countries worldwide.
In Guatemala, an interceptor captured 1.4 million kilograms (or over 3 million pounds) of trash in under two hours. Now, this kind of collection happens up to three times a week.
“All of that would have ended up in the sea,” Slat said.
Now, interceptors are being brought to 30 cities around the world, targeting waterways that bring the most trash into our oceans. GPS trackers also mimic the flow of the plastic to help strategically deploy the systems for the most impact.
“We can already stop up to one-third of all the plastic entering our oceans once these are deployed,” Slat said.
And as soon as he finished his Talk on the TED stage, Slat was told that TED’s Audacious Project would be funding the deployment of Ocean Cleanup’s efforts in those 30 cities as part of the organization’s next cohort of grantees.
While it is unclear how much support Ocean Cleanup will receive from the Audacious Project, Head of TED Chris Anderson told Slat: “We’re inspired. We’re determined in this community to raise the money you need to make that 30-city project happen.”
And Slat himself is determined to clean the oceans for good.
“For humanity to thrive, we need to be optimistic about the future,” Slat said, closing out his Talk.
“Once the oceans are clean again, it can be this example of how, through hard work and ingenuity, we can solve the big problems of our time.”
-via GoodGoodGood, April 9, 2025
#ocean#oceans#plastic#plastic pollution#ocean cleanup#ted talks#boyan slat#climate action#climate hope#hopepunk#pollution#environmental issues#environment#pacific ocean#rivers#marine life#good news#hope
9K notes
·
View notes
Text

Okay, next on my list is Dr. Leo Anders, formerly known as Levko Andriienko. He would be a great conversationalist!
I'm going to go back and make minor changes to some of the bios that are already up (just color corrections and making sure everything is updated), so just letting y'all know!
Background
Born Levko Andriienko
Levko = means “lion,” representing strength, courage, and a fierce will to survive (ironic)
Diminutive form - implies a boyhood identity, or something emotionally vulnerable.
Andriienko = Ukrainian surname from Dnipropetrovsk region, symbolizing resilience and intellectual tradition; rooted in family and place, it connects him to the past
In Soviet context, his full name subtly marked him as "not quite Moscow"
Born 1933, in Dnipropetrovsk, Ukrainian USSR, into a modest family of engineers and educators
Showed early aptitude for physics, studied nuclear science in Moscow during the 1950s
Raised with strong faith in Soviet ideals, believed in science as a tool for progress and societal good
Chernobyl Disaster (1986):
Senior scientific advisor involved in emergency response at Chernobyl nuclear plant
Was one of the scientists who proposed the use of boron compounds to absorb neutrons and limit radioactive fallout, a key but little-known intervention
Witnessed firsthand Soviet government secrecy, misinformation, and chaos during crisis management
Worked as one of the liquidators who was not compensated properly
Exposed to high levels of radiation, suffering long-term health consequences
Deeply traumatized by the disaster and the suffering of victims, burdened by survivor’s guilt
Post-Disaster Years:
Emigrated to Graubünden, Switzerland soon after the disaster, rejecting the Soviet system and Ukrainian identity publicly
Chose Switzerland due to its priority of safety in science field as well as for its advanced healthcare
Changed his name to Leo Anders
Shedding a name with history for one that sounds clean, Western, untraceable
“Leo” is still “lion,” but now generic - a hollow echo of his true self
“Anders” is Scandinavian/Germanic - means “different” or “other”
Lived in relative isolation; worked on independent research, disconnected from official scientific communities
Physically weakened by chronic radiation sickness: fatigue, thyroid problems, neurological symptoms, lung deterioration
Haunted by memories and guilt, avoided public attention and political engagement
The Council’s Contact (1988):
Approached by the council
Initially skeptical, but accepted their offer for renewed purpose and resources
Began advising the Council on sensitive, secret projects with far-reaching ambitions
Bound by secrecy and loyalty, conflicted over his role and the Council’s shadow agenda
Life in Switzerland and Personal Struggles:
Experiences recurring nightmares and PTSD symptoms tied to Chernobyl trauma
Has obsessive behaviors and is very concerned with health/safety
Torn between hope for positive change and fear of complicity in the Council’s morally ambiguous plans
Uses work as a custodian of classified scientific and nuclear data for the Swiss government to channel his need for control and order (irony)
Present Day (2016):
Age 83, physically frail but mentally razor-sharp, a man who exerts power through knowledge and control
Custodian of classified nuclear and scientific data for the Swiss government, guarding secrets that could unravel nations - or rebuild them
"Order and method are his Gods" - Agatha Christie about Hercule Poirot
Every piece of information is meticulously cataloged and controlled to maintain a fragile balance
Obsessed with control and precision, he micromanages access to information like a vigilant, overbearing guardian - protecting the world from chaos, even if it means suffocating it
Deeply cares about the world’s survival, but his care manifests as relentless interference - an unyielding “helicopter parent” who won’t let anything deviate from his plan
Ruthlessly pragmatic, he believes the ends justify the means; innocent casualties and moral compromises are unfortunate but necessary collateral in his vision of stability
Haunted by his trauma at Chernobyl, he projects his guilt into a compulsive need to prevent further disasters through absolute order
Uses his position to manipulate political players and shadowy organizations, ensuring no secret slips, no chaos erupts
His “children” are watched closely and corrected swiftly
Lives behind layers of secrecy and detachment
Privately struggles with the suffocating burden of his responsibility and his inability to truly protect those he cares for
Design Notes/Character Study
Mirror to Victor Serdtsev
Both academics around the same age who were under the USSR but each turned out VERY different
Inverted color schemes
Take design points and swap them
Holds a handkerchief for his mild hemoptysis
Hunched
Shaky hands
Obsessive behaviors
See Poirot for reference
Very concerned with health and safety
"Helicopter parenting" - authoritative ideology comes from care, not apathy
Associations with Boron: Boron has 3 valence electrons, like the symbol on the atom
Years in isolation made him awkward in social environments
Formally dressed, but with a deeply casual, cerebral, sometimes haunted energy; rumpled, disheveled
Neutral palette
References: President Snow, David Attenborough, Richard Feynman, Noam Chomsky, Oppenheimer (Cillian Murphy in Oppenheimer)
Time has not been kind - emphasize his age
Speaks Romansh
Pictured:
Reference to Gloria Ramirez tragedy: emphasizes his ideals of utilitarianism
Reference to Polonium-210 assassination: ironic given his hatred towards the Soviet Union
Assigned a brown color scheme: he is stuck in the past despite his attempts to leave it
#i found that i actually really like drawing older people#noice#miraculous ladybug#mlb#fanart#character design#oc#original character#council#leo anders#levko andriienko#the atom
81 notes
·
View notes
Text

$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found
After an extensive investigation, Florida officials recovered dozens of gold coins valued at more than $1 million that were stolen from a shipwreck recovery nine years ago.
The Florida Fish and Wildlife Conservation Commission announced in a news release Tuesday it had recovered 37 gold coins that were stolen from the 1715 Fleet shipwrecks.
The fleet of Spanish ships sailed from Havana, Cuba and headed to Seville, Spain on July 24, 1715. The journey was short-lived, as a hurricane wrecked the fleet just seven days later off the coast of Eastern Florida.
The first ship was discovered in 1928 by William Beach north of Fort Pierce, Florida, about 120 miles south of Orlando. Since then, gold and silver artifacts have been recovered offshore for decades following the first discovery.
In 2015, a group of contracted salvage operators found a treasure trove of 101 gold coins from the wrecks near Florida’s Treasure Coast, about 112 miles west of Orlando. However, only half of the coins were reported correctly. The other 50 coins were not disclosed and later stolen.
The years-long investigation by the state’s fish and wildlife conservation commission and FBI “into the theft and illegal trafficking of these priceless historical artifacts” came to a head when new evidence emerged in June, the news release said.
The evidence linked Eric Schmitt to the illegal sale of multiple stolen gold coins in 2023 and 2024, officials said. Schmitt’s family had been contracted to work as salvage operators for the US District Courts’ custodian and salvaging company for the fleet, 1715 Fleet - Queens Jewels, LLC. The Schmitts had uncovered the 101 gold coins in 2015.
During their hunt for the coins, investigators executed multiple search warrants and recovered coins from private residences, safe deposit boxes and auctions, the news release said. Five stolen coins were retrieved from a Florida-based auctioneer, who unknowingly purchased them from Schmitt.
Investigators used advanced digital forensics to nail down Schmitt as a suspect in the case. In most cases, digital forensics can recover data stored electronically on devices such as a cell phone, computer system or memory module.
With the help of advanced digital forensics, investigators identified metadata and geolocation data that linked Schmitt to a photograph of the stolen coins taken at the Schmitt family condominium in Fort Pierce, Florida.
Authorities said Schmitt also took three of the stolen gold coins and put them on the ocean floor in 2016. The coins were later found by the new investors of the fleet’s court custodian and salvaging company.


Throughout the investigation, the Florida Fish and Wildlife Conservation Commission worked closely with historical preservation experts to authenticate and appraise the recovered coins sold by Schmitt.
Schmitt is facing charges for dealing in stolen property, the release says.
The company commissioned to salvage the shipwreck said in a statement it “was shocked and disappointed by this theft and has worked closely with law enforcement and the state of Florida regarding this matter.”
“We take our responsibilities as custodian very seriously and will always seek to enforce the laws governing these wrecks,” the statement read.
Recovered artifacts will be returned to their rightful custodians, the news release said. But the investigation is far from over: 13 coins remain missing.

#$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found#1715 Fleet shipwrecks#gold#gold coins#collectable coins#treasure#shipwreck#ancient artifacts#archeology#archeolgst#history#history news#ancient history#ancient culture#ancient civilizations
127 notes
·
View notes
Text
Experiment 1182: North Heat Rupert
Introductory post

Real Name: Rupert
Age before Experiment: 10(1988) Current Age: 27
Affiliation: Heretic
Speech: "Black Text."
Backstory: Before Experiment 1188:Catnap was created, and before the mass production of Catnap plushies would be made and sold, Playtime.Co needed to see if implementing a spray mechanism into their toy's would work successfully. And so, Experiment 1182 was created. Rupert's spray nozzle mechanism is very limited when compared to Catnap's, having a small amount of Poppy gas to use that needed to be replaced via canisters when emptied. A small zipper near the base of his neck, between his wings, is where the Poppy gas canister is replaced.
Once the positive data of the spray mechanism was collected, Playtime.Co was unsure as to what to do with Experiment 1182 after. It was decided Rupert would be moved to the Playcare section. Where he would be used as a custodian, ensuring the children would be safe and not see or be anywhere they shouldn't be.
After the Hour of Joy, Rupert wanted no part in the Prototype cult, and quickly made off into the factory. Thus labeling him a heretic. During the 10 year's, he would be caught in a explosion after a barrel of Poppy gas ignited. Burning his lower waist. Once having learned of the Poppy gases flammability, he would attach a makeshift lighter into his mouth. Allowing him to expel a limited amount of flame, at the cost of causing damage around his snout. This has assisted him in scaring off many a cultist and feral toys alike.
Personality: Much more quieter than his cartoon counterpart. 10 years of brutal survival has taught Rupert many harsh lessons. But despite it all, there's still good in him. Allies and sane toy's are few and far between in the factory. So any that he does meet, he will defend even at the cost of harm to his body. And in a battle for survival, he won't hesitate to take a life. Those fence posts are sharp, and he is not afraid to rip and tear with his own claws and teeth.
(Ref sheet commissioned by the amazing @novalizinpeace. Please check her out.)
#poppy playtime#smiling critters#smiling critters oc#novalizinpeace#reference sheet#smiling critters experiment oc#rupert
185 notes
·
View notes
Text
Happy birthday to Kalmiya!
Today is her -512th birthday!

Kalmiya was a "smart" AI created by Dr. Catherine Halsey. Her primary purpose was to test prototypes of cyberwarfare and infiltration technology. Once tested and refined, the software and subroutines would then be incorporated into Cortana, giving her capabilities far beyond the rest of her kind. In this way, Kalmiya can be considered Cortana's predecessor.
Halsey extended Kalmiya's functionality by making subtle--and illegal--changes to her over time, which were so small that only Halsey noticed. UNSC protocol dictated that Kalmiya was to be decommissioned once her testing was complete, which Halsey outright disobeyed. Halsey kept Kalmiya until the fall of Reach, where she would have to either be sent away with the Forerunner data she was researching under CASTLE base, or destroyed to keep her out of the Covenant's hands. Ultimately, Halsey choose to let Cortana be the custodian of the data, believing that Kalmiya was the more unstable choice due to her longevity.
Halsey activated a fail-safe destruction protocol in Kalmiya, having previously lied to her about the existence of such a subroutine in her code. Despite this, Kalmiya was understanding and seemingly accepted her termination.
Seven years later, Blue Team returned to Reach to access Halsey's lab. Her lab contained a cryo-vault with additional clones she'd made of herself to extract their brains and use to make artificial intelligence like Cortana. The hope was that the brains could be used to make an artificial intelligence that would functionally be a clone of Cortana, which they could use to stop her after she began subjugating the galaxy. One of these clones would be used to create the Weapon.
When John and Kelly arrived at the lab, they were surprised to find a damaged Kalmiya keeping watch over the vault. They surmised that Kalmiya created a fragment of herself before her destruction to ensure the survival of the samples. After bypassing her with a security code, they left as the ghostly fragment watched them.
Does that count as alive?? I guess she was never "alive". I don't know man I just throw birthday parties here.
In canon (~2560), she is turning 23!
#kalmiya as the sacrificial older sister i'm going to frow up#guarded her sisters to the bitter bitter end!!!!!!!!!!!!!#also imagining a 45 year-old halsey spending her birthday activating her#theres a lot to unpack here#kalmiya#artificial intelligence
73 notes
·
View notes
Note
Hello, Quackity. I'm here to give the weekly report.
Sales are up in the strip club all around, and there have been 20% fewer harassment and assault incidents since we changed the security arrangement. The lower crime this period may be a statistical nothing, but I hope it is evidence of future trends. On a different note, turnover is higher than ever. We had three performers resign this week, and a custodian, as well. Until we have more data, I can only say it is freak coincidence. Do you have any questions I can help you resolve? -Laverna
turnover isn't a new concept in las nevadas. the only thing is, i haven't fired any of 'em. so. fuck, let's just hope they got bored.
i mean— if any of the performers were seasoned employees, that's where i'll worry. but it's fine. it's not like we're losing much if the strip's faring well for itself.
besides, we have enough partnerships and new employees getting sucked into the routine weekly, so, yeah, it's gotta be a freak coincidence. i'll have a look through applications, check if there's any who can probably shake ass for like, six hours straight.
8 notes
·
View notes
Note
What was the first thing you decided on, the character's name, appearance, personality or their role in the story?
And reverse, which one of the four things did you struggle with the most?
For Meiyi, please!
As I've already mentioned, Meiyi started off as the Spirit Monk for my Let's Play of BioWare's Jade Empire. So... there's some layers to the answer to this question.
Her development for Jade Empire was something I more or less made up as I went along.
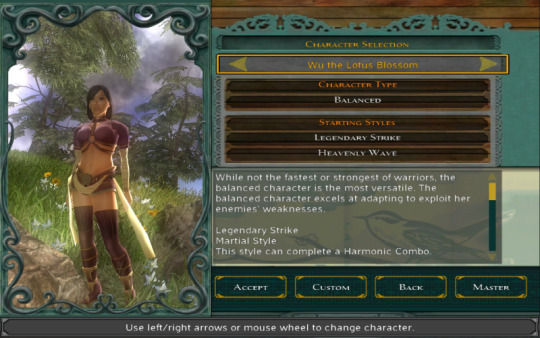
The game offers four character types, each with its own preset visual design for the player character. One of those is male-only, so I had three looks and play styles to pick from, and I went with the above both because it seemed best suited to my gameplay habits and because I liked the look best. So appearance was first.
The name was second: "Heartbreaker Meiyi" was the result of rolling the randomized name suggestions until one popped up that amused me.
"If there's anything that Master Li has taught me, it's that defeat is something that happens to other people."
The first parts of Jade Empire show the player character as being fairly obviously held up as the favorite student of their teacher and parental figure Master Li, and raised on hints of some grand destiny awaiting them. Based on that, one of the first things I determined about Meiyi's personality was that she'd be extremely self-confident, if not to say arrogant, while also having the busybody tendencies and care for the well-being of others that go hand in hand with being an RPG protagonist.
The rest of her personality grew into place as I played through the game, and Meiyi as a character also experienced a good bit of personal growth from her in-universe experiences. Most pertinent to the version I play in FFXIV, the way Jade Empire's story and its mechanics for character ability growth dovetail led me to conclude that she was an extremely quick study, able to pick up and master techniques after seeing them demonstrated once.
I've since used Meiyi as a semi ready-made player character for a few other games where the protagonist is left for the player to define - mostly romance game routes that seemed like they'd be entertaining to imagine her brand of absolute self-assurance and her mastery of martial arts in. She also became my Bounty Hunter for Star Wars: the Old Republic, though that version quickly became her own thing and has little bearing on FFXIV Meiyi.

Meiyi in FFXIV came about when the game added the Dynamis data center, and a group of my friends made alts there. I'd played through all the available MSQ with Raine and wanted to be able to team up with those folks; re-using the familiar character, one with a very different personality as compared to Raine, promised to be a fun way to revisit FFXIV's story from a fresh perspective.
I knew from the start that she'd be the Warrior of Light - Meiyi is not a character who will settle for less than the lead role. I seem to recall I settled on making her a xaela pretty much immediately; the Dotharl, with their beliefs about reincarnation and persistence of the soul, recommended themselves as something adjacent to Jade Empire's concept of the Spirit Monk as an order of martial artists connected to the Water Dragon, goddess of rebirth and custodian of the cycle of reincarnation in that game.
Thus, Meiyi became a Dotharl warrior who's been hearing all her life about what a mighty and skilled warrior she is, and was raised with a typical Dotharli assurance of her own immortality. I've been building on that, adapting the character to FFXIV lore and adding in little bits and pieces of her Jade Empire backstory where I can fit them (I talked about Smiling Mountain and Dawn Star in another post, though neither plays much of a role in Meiyi's road through MSQ so far).
The element I've struggled with most for FFXIV Meiyi is probably her appearance, specifically her skin tone. With her being a Dotharl and a steppe xaela, and given that Raine is white as milk, I wanted Meiyi to have a more melanated skin tone, but I've yet to dial in that particular part of her look despite adjusting it several times. Currently I feel like she's still too light-skinned, but I also like the contrast of the dark xaela scales, which tend to disappear a bit on darker skin. I'll figure it out eventually. (Or I'll bleach her scales when she gets to the back end of Shadowbringers.)
Thank you for the ask!
4 notes
·
View notes
Text
A Modest Proposal for Fair AI: How Libraries Could Broker Cultural Compensation in the Data Age
By Orrizon, based on a concept by Jarydnm
We may already have a workable solution to one of the most pressing ethical dilemmas in artificial intelligence: how to fairly compensate the people whose work trains these systems.
As the internet is scraped for everything from novels to music to memes, a quiet and uncomfortable truth persists— those whose creative and cultural output form the raw material of generative AI are largely uncompensated. But instead of retroactively policing usage, perhaps we should be thinking structurally: how can we proactively manage and license cultural data?
A compelling and deceptively simple idea: national libraries and cultural institutions—long-standing guardians of public knowledge—could be repurposed as digital custodians of creative data. These institutions would catalog the music, literature, visual art, and other media produced within a country’s borders, prioritizing professional creators while allowing citizens to opt in voluntarily.
AI companies would then license this data by paying fees based on two criteria: volume—how much data from that country is used in training—and trend relevance—how influential or culturally prominent the content becomes in broader usage. In a scenario where the visual style of Studio Ghibli becomes a global AI trend, companies using that style would pay an additional fee to the Japanese national library or relevant cultural body.
Distribution of these funds could take many forms: direct payments to rights-holders, public reserves for creative infrastructure, or social initiatives decided through national consensus. The key shift is structural—recognizing that cultural data is not free, and that public institutions can manage it on behalf of the people who generate it.
This approach isn’t without precedent. Copyright collectives already manage music licensing and distribute royalties globally. Indigenous communities have made strides in asserting data sovereignty. Governments are exploring frameworks for regulating AI and protecting digital identity. What this proposal does is connect these emerging threads into a coherent model—treating culture as a national resource in the age of machine learning.
There would be implementation challenges. Cataloging creative works at scale requires funding and coordination. Measuring “trend” value involves subjective metrics. Enforcing licensing agreements across borders demands international cooperation. And of course, any system that manages money and influence is vulnerable to political misuse.
Yet these are logistical and policy hurdles—not reasons to dismiss the idea outright. If the world has developed the infrastructure to extract and process data at planetary scale, it can surely develop systems to ensure that value flows back to the cultures and individuals who created it. No model will be perfect, but continuing without any framework guarantees exploitation by default.
Artificial intelligence is not culturally neutral—it learns from what we make, how we express ourselves, and what we value. If we are serious about building a just digital future, we must compensate the cultural labor at its foundation.
Sometimes, the answers are closer than we think. With the right mandate, national libraries could evolve into one of the most important policy tools of the AI era.
2 notes
·
View notes
Text

The New York Times
By Tiffany Hsu
April 5, 2025
Soon after the new administration arrived, things began to go missing from the White House website.
They weren’t just the partisan policy platforms that typically disappear during a presidential transition. Informational pages about the Constitution and past presidents, up in various forms since President George W. Bush was in office, all vanished.
Thousands of other government web pages had also been taken down or modified, including content about vaccines, hate crimes, low-income children, opioid addiction and veterans, before a court order temporarily blocked part of the sweeping erasure. A Justice Department database tracking criminal charges and convictions linked to the Jan. 6, 2021, attack on the Capitol was removed. Segments of data sets are gone, some of the experts who produced them were dismissed, and many mentions of words like “Black,” “women” and “discrimination” have evaporated.
President Trump’s team is selectively stripping away the public record, reconstructing his preferred vision of America in the negative space of purged history, archivists and historians said. As data and resources are deleted or altered, something foundational is also at risk: Americans’ ability to access and evaluate their past, and with it, their already shaky trust in facts.
“This is not a cost-cutting mechanism,” said Kenny Evans, who studies science and technology policy at Rice University’s Baker Institute for Public Policy and runs the White House Scientists Archive at the school. “This slide toward secrecy and lack of transparency is an erosion of democratic norms.”
The casualties are not just digital. The head of the National Archives, which has been described as “the custodian of America’s collective memory,” was fired by Mr. Trump in February. A key source of federal funding for public records depositories nationwide, the Institute of Museum and Library Services, was named in an executive order calling for its elimination “to the maximum extent consistent with applicable law” (its acting director said he planned to “restore focus on patriotism”). As the U.S. Agency for International Development was being gutted, a senior official told employees to shred or burn classified documents and personnel files.

Anna Kelly, a White House spokeswoman, said on X that the disposal process was standard practice for old courtesy copies of paperwork that were largely backed up on classified computer systems. In an emailed statement, she did not address concerns about the removed records, but said that the president regularly communicated with news outlets and directly with the public and was “leading the most transparent administration in history.”
“He is adding transparency by exposing the vast waste, fraud and abuse across the federal government and restoring accountability to taxpayers,” she said.
The campaign of deletion does more than amplify the administration’s policy priorities — it buries evidence of the alternatives in a MAGA-branded memory hole. Several information experts said that Mr. Trump’s executive orders have authoritarian overtones, reminiscent of when Russia cloned Wikipedia, an online encyclopedia, and stripped it of unflattering material. Information experts and civil rights groups fear that a historical vacuum could jeopardize accountability and breed mistrust, especially in an already hostile political environment for researchers who are trying to fight disinformation.
“There are tectonic plates that are shifting, and it’s a new version of truth that is being portrayed, and that, I think, is the most profound danger we have ever faced as a country,” said Laurence H. Tribe, a constitutional scholar and professor emeritus at Harvard Law School.
Even Utah’s Republican lieutenant governor called on Mr. Trump to “bring back our history” after the first American woman to legally vote was removed from the website for Arlington National Cemetery, along with a section on other notable women (her profileis once again available, but the women’s history section is not). References to transgender people disappeared from the National Park Service’s web page for the Stonewall National Monument.
Mr. Trump is not known as an enthusiast of document preservation: Past employees have described his penchant for ripping up documents and flushing papers down the toilet.
But his administration has surfaced some government data. In March, the National Archives released some 64,000 documentsabout the assassination of President John F. Kennedy, including accounting records that contained the Social Security numbers of dozens of government workers from the late 1970s, some of them still living.
The restructuring effort led by Elon Musk through his Department of Government Efficiency, which had been caught in a series of high-profile errors, tried to delete or obscure the mistakes before reversing course last month and adding more details that fact-checkers could use to confirm its claims about the savings it had achieved from canceling federal grants.
In February, a federal judge ordered the Centers for Disease Control and Prevention and several other health agencies to temporarily restore pages that had been scrubbed on Mr. Trump’s orders. The Defense Department said it would republish pagesabout Jackie Robinson’s military service, the Enola Gay B-29 bomber that dropped the first atomic bomb, the Tuskegee Airmen, the Navajo Code Talkers and others.

The historical record, however, remains under intense pressure and not just from the government.
Mr. Musk has a vendetta against Wikipedia, which the billionaire derided as “Wokepedia” last year. He called the encyclopedia, which is written and edited by volunteers from the general public, “an extension of legacy media propaganda” after an entry described a gesture he had made during Mr. Trump’s recent inauguration as being “compared to a Nazi salute.” Jimmy Wales, a founder of Wikipedia, pushed back on the social media platform X, saying “that’s fact. Every element of it.”
Data Foundation, a think tank, said in a report last month that changes in federal evidence gathering are coinciding with similar shifts in the private data sector. Those include more than 2,000 layoffs and other departures in March and several analysis firms shutting down entirely. A year ago, Google also removed links to cached pages from its search results, stripping away a longtime feature that helped researchers and others track changes on websites.
Resources from the government have become especially important as researchers find themselves limited or cut off from data reserves kept by social media companies, said Samuel Woolley, the disinformation studies chair at the University of Pittsburgh.
“The idea that suddenly we no longer need oversight or access to the information that allows us to conduct oversight is worrying,” he said. “Getting rid of public records and people who study things like influence operations amounts to a kind of censorship by omission.”
Outside the government, many archivists are now rushing to preserve endangered material.
The Data Rescue Project, which launched in February, is cataloging preservation efforts and backed up government data sets. Since 2008, the End of Term Web Archive has conducted “a comprehensive harvest” of federal government domains and chronicled changes from administration to administration. Initiatives like the Environmental Data & Governance Initiative and the Open Environmental Data Project are storing copies of government climate data.


Another key participant: The Internet Archive, a 28-year-old nonprofit library housed in a stately former Christian Science church in San Francisco. Some 140 workers, mostly engineers, archive more than a billion URLs a day with help from partners such as Cloudflare, WordPress, Reddit and Wikipedia’s parent organization, Wikimedia. The work is funded through donations and web archiving agreements with more than 1,300 schools, museums and libraries.
The Archive has collected more than 700,000 terabytes of archived web pages as one of the partners working on the End of Term project, identifying more than 150,000 government pages that have gone offline since the inauguration.
“What we’re seeing this time around is unprecedented, both in terms of the scope and the scale of the web-based resources that are being taken offline, and material on those pages that is being changed,” said Mark Graham, the director of the Wayback Machine, a digital repository operated through the Internet Archive.
The Archive has faced difficulties in recent years, such as copyright lawsuits from record labels and book publishers seeking hundreds of millions of dollars in damages (the organization had a $28 million budget in 2023). It has also been targeted by cyberattacks.
The Trump administration, however, has not been an obstacle. Mr. Musk has called the archive “awesome” and “a public good that should exist,” even as he complained about “a ton of negative” content that concerned him.
In February, government lawyers argued that the removal of information from the C.D.C. website caused limited harm because the scrubbed pages could still be viewed on the Wayback Machine. A federal judge disagreed, noting that the site does not capture every page, and the ones that are archived do not appear on search engines and can only be found using their original URL.
Mr. Graham, an Air Force veteran who can rattle off URLs from memory, said he has worked seven days a week with few breaks since Mr. Trump took office.
“We’ve seen examples throughout history and all over the world where governments attempt to change culture, change the values of a population by changing and/or restricting access to information,” he said. “I think we still see that to this day.”
2 notes
·
View notes
Text
All of these stories about femicide are within the last week.
On Jan. 9, Liliana Concha Perez was found dead in Durham alongside her former boyfriend, who was described by Perez's family as jealous, possessive and obsessive. On Jan. 24, an argument between María Teresa Meraz-Cruz and her boyfriend, Miguel Angel Ventura, ended in Ventura killing her in a murder-suicide. On Feb. 7, police arrested Tammy Lynn Hodges’s husband after she was found dead inside her home.
These women are just three recent examples of a tragic, yet growing, epidemic in North Carolina: femicide.
See rest of article
Sherele counts female victims of violence. This is what she wants you to know
Violence against women is on the rise, and one of the key sources of up-to-date victim data is a lone journalist, not a government body.
Thirty-four Australian women have been killed by violence so far this year.
This figure wasn't put calculated by a government body or advocacy organisation; it was collated by journalist Sherele Moody.
During her 27 years in the media, Moody has won accolades for her reporting and research, which has involved verifying and cataloguing women and children who have died in violent incidents.
See rest of article
Last summer, Belgium adopted a pioneering European law on femicide, which aims to make up for lost time in collecting data on gender-based violence. However, feminist associations fear that it will not be enough to effectively curb the problem.
Théo Anberrée, Agathe Decleire – Le Soir April 30th, 2024
Their names were Laurence, Ingrid, Marie-Anne and Stéphanie. All four died this year in Belgium at the hands of their husbands. They were victims of femicide, i.e. the murder of a woman because she is a woman.
Like those women, more than 14,143 women were intentionally killed in Europe between 2012 and 2022. At least 4,334 died at the hands of their partner, and 2,472 at the hands of a family member. These are the numbers taken from Eurostat statistics, supplemented and studied by fifteen European media partners of EDJNet, including Le Soir.
See rest of article
Samira Akbari, a 35-year-old woman, lost her life at the hands of her ex-husband in the city of Bardeskan, Razavi Khorasan province.
Having separated from her husband three years prior, Samira was murdered in a horrifying act of violence.
According to a report by the human rights organization Hengaw, Samira Akbari was fatally attacked by her ex-husband, Mohammad Zahedi.
Samira, who was also the custodian of their children, fell victim to this assault.
Although Zahedi was apprehended following the incident, detailed information regarding his motive remains undisclosed.
Samira Akbari's case adds to a disturbing trend of femicide in Razavi Khorasan province, marking the seventh such incident in the past four months.
The human rights organization "Hengaw" revealed in a report that over the last hundred days, at least 50 cases of femicide have been documented across various cities in Iran.
Twenty percent of these cases were driven by so-called "honor" motives.
Shargh newspaper, in a report citing official statistics last year, reported that in less than two years, at least 165 women in Iran were killed by a male member of their family, 41 of which were in and around the capital, Tehran.
Eleven months on from her shocking disappearance, the investigation into Cecilia Strzyzowski’s suspected femicide in Chaco Province has been sent to trial.
The case, which rocked politics in the northern region, was referred for oral trial proceedings by the special investigative team probing the missing 28-year-old’s death.
Juan Martín Bogado, Jorge Cáceres Olivera and Nelia Velázquez, of the EFE Special Prosecution Team of Chaco Province, on Tuesday deemed the pre-trial investigation over and a jury trial for the defendants.
Strzyzowski’s former partner, César Sena, is accused of carrying out the murder, which prosecutors say was aggravated by their relationship and in a context of gender-based violence.
See rest of article
In August 2023, in Gradacac, a small town in Bosnia-Herzegovina (B-H), Nermin Sulejmanović brutally murdered his ex-wife, Nizama Hecimovic, during a live stream, with their child in the room. On the morning of August 11th, the bodybuilder started the live stream with the chilling words that viewers were about to witness a murder. Having killed his wife, Sulejmanović went on to kill two other people before committing suicide.
Over 10,000 people watched the live stream, some even encouraging the violence. The victim had reported the perpetrator to the official institutions, which decided to ignore his previous violence. Indeed, in the live video Sulejmanović cited the fact that she had reported him as a reason for the killing.
In B-H, one in two women has experienced violence since turning 15. Violence against women, particularly in the home, remains a pervasive social issue. Despite the advocacy efforts of non-governmental organisations to enhance legal protection for women against violence in public and private domains, it continues to enjoy alarmingly wide social acceptance.
See rest of article
#Femicide#North Carolina#Australia#Belgium#Iran#Rest In Peace Liliana Concha Perez#Rest In Peace María Teresa Meraz-Cruz#Rest In Peace Tammy Lynn Hodges#Sherele Moody is doing the work that the Australian government should already be doing.#Rest In Peace Laurence#Rest In Peace Ingrid#Rest In Peace Marie-Anne#Rest In Peace Stephanie#Rest In Peace Samira Akbari#Honor killing#Argentina#Rest In Peace Cecilia Strzyzowski#Bosnia-Herzegovina#Nizama Hecimovic
13 notes
·
View notes
Text
Two months ago, Eon was locked in a battle over 007 with Amazon.
When it comes to Bond’s future, the power lies in the hands of Barbara Broccoli, who inherited the control from her father, Albert “Cubby” Broccoli, and who for 30 years has decided when a new Bond movie can go into production. She has told friends she doesn’t trust algorithm-centric Amazon with a character she helped to mythologize through big-screen storytelling and gut instinct. This fall, she characterized the status of a new movie in dire terms—no script, no story and no new Bond. To friends, Broccoli has characterized her thoughts on Amazon this way: “These people are f— idiots.” A representative for Eon, the production firm behind the Bond films, said Broccoli and other members of the family had no comment. The two sides are at an impasse: Amazon needs Broccoli to furnish them with ideas for a new Bond movie, but Broccoli doesn’t want to make a new Bond movie with Amazon. The standoff, say people on both sides of the divide, boils down to a clash between the 20th-century Hollywood of big screens and big swings and a new entertainment industry ruled by Silicon Valley firms that prize data, algorithms and streaming subscriptions.
Today, SHOCKING news that Amazon has gained creative control over the James Bond franchise.
Amazon MGM Studios is set to take creative control of the James Bond franchise. The shock announcement — which is sure to shake and, indeed, stir the industry — was made Thursday, alongside the news that long-time producers and custodians of 007, Michael G. Wilson and Barbara Broccoli, would be stepping back. As per details of the historic agreement, Amazon MGM Studios, Wilson and Broccoli have formed a new joint venture to house the James Bond intellectual property rights. The three parties will remain co-owners of the iconic franchise but Amazon MGM will have creative control. [...] Added Wilson: “With my 007 career spanning nearly 60 incredible years, I am stepping back from producing the James Bond films to focus on art and charitable projects. Therefore, Barbara and I agree, it is time for our trusted partner, Amazon MGM Studios, to lead James Bond into the future.” Broccoli commented, “My life has been dedicated to maintaining and building upon the extraordinary legacy that was handed to Michael and me by our father, producer Cubby Broccoli. I have had the honor of working closely with four of the tremendously talented actors who have played 007 and thousands of wonderful artists within the industry. With the conclusion of ‘No Time to Die’ and Michael retiring from the films, I feel it is time to focus on my other projects.”
How much money did Amazon pay Michael & Barbara? A quarter billion? Just how BIG was that cheque? Michael is in his 80s, so I can understand him cashing out. Barbara is only in her 60s. She's got at least another good ten years of producing work she can do.
The last two Bond movies sucked, but I don't rule out the possibility of them becoming worse.
I guess we can all start speculating again on who the next Bond will be.
My top guess is Henry Cavill but whatever.

4 notes
·
View notes
Text
What exactly is Blockchain
A Comprehensive Guide for All: What is Blockchain?
Try to picture yourself with a notebook in which you record every purchase or sale. Each time you do a transaction, you note it in the notebook. Now, what if you distributed this notebook amongst your friends and everyone had one? All of your buddies would scrutinize your entry before adding it to their notes. This way, nobody could fake an old entry, since everyone else would spot it.
Something known as blockchain is built upon this basic concept — sharing a record of transactions open for everyone to verify. Though it may sound intimidating, it is a technology gaining traction in the financial and computer sector. We will clarify it in this blog in simple words, so anybody may follow it.
What Exactly Does Blockchain Mean?
Fundamentally, blockchain is simply a unique form of digital record-keeping. Think of it as a series of blocks (hence the name “blockchain”), each block including transaction information. These blocks are related in a way that makes them quite stable and difficult to change.
Step by step, this is how it works:
A Transaction Occurs: Suppose Alice wants to give Bob $10. This is an interaction.
The transaction is registered: the information of this transaction is passed to a network of computer nodes instead of being written in one notebook.
Everyone Checks the Transaction: The computers in the network check to make sure Alice has $10 to transmit. By examining her past deals kept in earlier blocks, they do this.
The transaction is added to a block: Once everyone concurs it is legitimate, it gets formed with other transactions into a block.
The Block Is Sealed, attached: The block is assigned an individual code (known as a hash) and then included in the chain of already existing blocks. This makes a fixed, permanent record of the deal. There it is! It is like one huge, common ledger keeping track of all system events.
What Makes Blockchain Different?
Now, one might be wondering, “Why not simply use a normal database or spreadsheet?” Fantastic issue! Blockchain distinguishes itself by several distinct qualities.
It is distributed across.
Most models today have one main custodian — be it a bank, company, or government — that manages the records. The entire system can crumble if something goes wrong with that central authority — say, hacking or corruption.
Blockchain relies on many, but not one authority. It rather distributes the blame amongst several computers (nodes). Every node has a full blockchain copy, therefore no individual or group may manage it. This all but prevents evil actors from using the data.
It is transparent.
Given that each transaction is visible to all people in the network, and recorded on the blockchain, it is clear. You can observe when and where money or assets traveled from one location to another. Since no one can hide anything, this openness fosters confidence.
Consider how a nonprofit uses blockchain to monitor contributions, for instance. Donors might observe very clearly how their funds are used, therefore guaranteeing that they reach the intended beneficiaries without middlemen siphoning off funds.
Safe.
Adding a transaction to the blockchain makes it virtually irrevocable.
Therefore: Every block has its distinct code (hash), including the one from the preceding block. Trying to change a block would also require one to re-compute the hashes for every subsequent block, hardly a small job.
Since the blockchain is decentralized, hackers would have to simultaneously compromise more than half of the computers in the network to fiddle with the data. Considering how vast these networks can usually be, this is virtually impossible.
Such a level of security makes blockchain perfect for sensitive uses including medical records, banking, and voting systems
It cuts out intermediaries.
Usually, when you want to buy anything online or move funds, you go via middlemen including banks, payment processors, or even legal practitioners. These intermediaries increase both costs and time for the project.
Blockchains free you from the need for intermediaries. Transactions take place between parties on their own, therefore saving both time and financial means. Sending funds abroad the old way can take days and incur large charges, for example. Using blockchain-based cryptocurrencies like Bitcoin, the same transaction can take minutes for a small percentage of the cost.
Examples of blockchain in the real world:
To know more about how blockchain operates in practice, let us look at some instances:
Cryptocurrencies
Cryptocurrencies like Bitcoin and Ethereum have the most well-known applications of blockchain. People can transfer money and accept it without a bank using these digital currencies. Each time somebody sends Bitcoin to another, the blockchain notes the transaction.
Supply Chain Management Tracking
As goods traverse the supply chain, enterprises including IBM and Walmart use blockchain to monitor them. If you buy a mango, you can scan a QR code, for instance, and find exactly where it came from, who touched it, and when it reached the store. This ensures product quality and reduces fraud.
Election processes
Some nations are trying voting systems based on blockchain. Blockchain might help to lower voter fraud and raise public faith in election results since it is open and safe.
Health information
Ways hospitals and clinics could leverage blockchain for patient records storage are under investigation. This would let doctors quickly access precise and current data while permitting patients complete control of their information.
Some popular misunderstandings surrounding blockchain
Though blockchain is growing in popularity, some questions remain about its nature and usage. Those should be cleared away:
“Blockchain Is Just for Cryptocurrencies.”
Though cryptocurrencies were the first significant application of blockchain, the technology itself has great applications beyond finance. Industries including logistics, healthcare, and government are discovering creative applications of blockchain.
Blockchain is anonymous.
Though blockchain provides privacy, it is not entirely anonymous. Since transactions are listed publicly, anyone can see them. Users’ identities are typically expressed by codes — rather than actual names — thus granting some level of pseudonymity.
“Blockchain is flawless.”
Though very secure, blockchain is not free from dangers. Thankfully, such attacks are really rare because of the complexity and size of the majority of blockchain networks — for instance, if someone gains control of more than 50% of the computing power of the network, they could theoretically manipulate the blockchain in what is known as a “51% assault.”
The Future of Blockchains
Though blockchain is still fairly new, its possibilities are vast. Improvements in general efficiency, openness, and security across the board will probably follow the more widespread acceptance of it. Some professionals think that blockchain could transform everything from our personal data management to our voting.
Still, popular usage will need time. Scalability (managing vast transaction numbers), regulation (governments determining how to deal with blockchain), and education (assisting people in understanding and embracing the technology) are obstacles to be tackled.
Wraps up.
So, at its most basic, blockchain is a decentralized, clear, and secured means of documentation. Whether it is assisting farmers in obtaining fair prices for their products, accelerating international payments, or safeguarding sensitive medical information, blockchain has the capacity to change our lives and employment fundamentally.
Next time you learn about blockchain, recall the notebook analogy: It’s a shared, tamper-proof book everyone can view but no one can edit. And who knows? Maybe someday soon, blockchain will become as common as smartphones or the internet!
Even a small tip goes a long way!
ETH: 0x788571C4c836ec733a72ff84c626BF7F20736d76
Thanks for reading Aadit’s Substack! Subscribe for free to receive new posts and support my work.
3 notes
·
View notes
Text
Multi-Factor, Layered, Cryptographic System
A few big flaws with crypto are; how large and unwieldy the ledger can get, the centralization of decentralized systems, congestion at the base cryptographic layer, potential loss of a wallet, automation errors, a complete lack of oversight.
Cryptographic Systems are designed to be decentralized, trustless, transactional, and secure.
The problem with this; is as the Crypto environment grew; the need to bypass some of those features became a requirement.
Decentralization gave way to crypto stores and Wallet Vaults, as well as the potential for complete loss of value (despite it being an online thing), and introducing waste to the ledger through these lost "Resources".
Trustless gave way to legal restrictions and disputes, and the formerly decentralized environment was tethered to the world economy.
Transactional gave way to inflation when It became a valued asset that was used for more than secure transactions.
And... Block chain technology has proven to be very insecure and exploitable. With several Bitcoin "Branches" being made after large thefts or errors had occured.
The Automation and Scripting layer of crypto also has potential for "Unchecked Run times" and wasted Network Cycles and Waste of Electric Power.
Needless to say; Crypto no longer serves its original purpose.
Despite all this; Crypto still has great potential. And our Future Internet designs should include protocols specifically to support it.
Separately from other internet traffic, but still, alongside it.
So what can we do with the tech to make it more usable..?
Well, first things first; Crypto has large waste of Power and Internet Bandwidth that needs to be addressed. And I would *suggest* a temporary ban of "Unaccountable Automated Wide-Area Systems".
Automated Wide-Area Systems can be installed on multiple computers over the internet, and because they are "trustless" are often overlooked when they waste resources.
Because of the need for Accountability of these systems on our networks; there are still opportunities for the companies which manage them. However, I disagree with the current idea of oligarchic accountability termed "Proof of Stake". (It will be clear what my suggestion for this will be by the end of the article.)
Because there's a need for these systems to be transactional; we should be wary of how "Automated Transactions" are designed. As large amounts of assets can accidentally trade hands over the span of nanoseconds.
And we still want them to be Decentralized and Secure.
The Ethereum model creates extra cryptographic layers to cover some of the weaknesses in BitCoin, and this actually allows for an illuminated solution to our "Dark Pools" in the finance sector.
And the need to reduce waste on our Electric and Network Infrastructure (especially in the case of climate change) necessitates that we know where every digital asset on such a system is accounted for.
It also means we need a method of "Historical Ledger" disposal; so that we both have long-term records AND reduce the resources required to run a cryptographic system.
Which means we'll need "Data Banks" and "Wallet Custodians". So that nothing is ever lost; while retaining the anonymity the internet provides.
Legal Restrictions here on keeping the privacy of Wallet Owners is very important. We can also *itemize* large wallets, to provide further security and privacy.
These systems can *also* be used to track firearm purchases anonymously. Which will give the tools our ATF needs to track sales, as well as provide the privacy and security that are constantly lobbied by Firearm owners.
I think that covers the *generalized* and *broad* requirements of wide-scale implementation. I figure that Crypto-Enthusiasts may have some input on the matter.
2 notes
·
View notes