#Defense Counterintelligence and Security Agency
Explore tagged Tumblr posts
Text


#Documents#urban-renaissance#Classified#I Plead The Fifth#[REDACTED]#TSA#FBI#DHS#SSA#EPA#Environmental Protection Agency#Social Security Administration#Department of Homeland Security#Federal Bureau of Investigation#2023#2022#2001#Transportation Security Administration#dcsa#Defense Counterintelligence Security Agency#OPM#Office of Personnel Management#Black Scale#BLVCKSCVLE#Business
0 notes
Note
Can you please write something with the idea of y/n asking Bucky if she can tie a pink ribbon around his bicep? Thank you
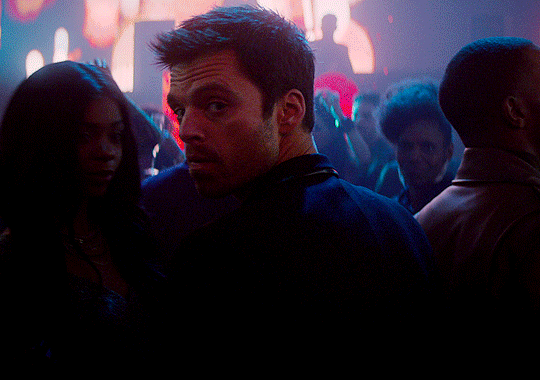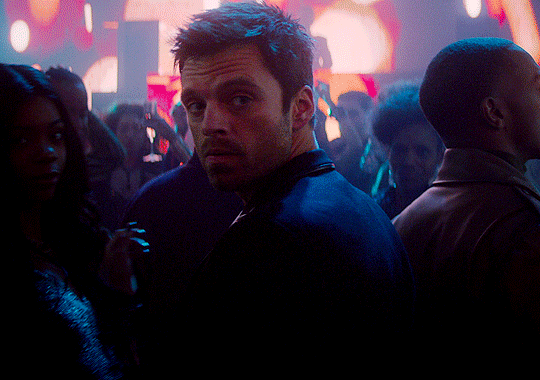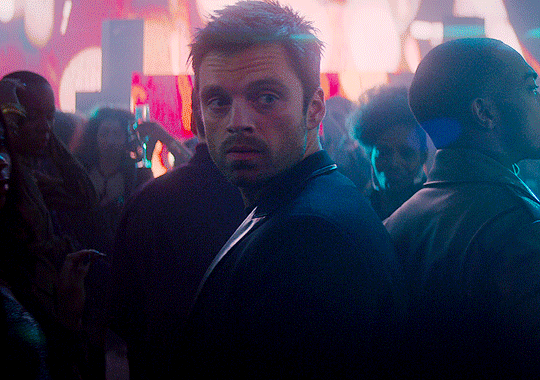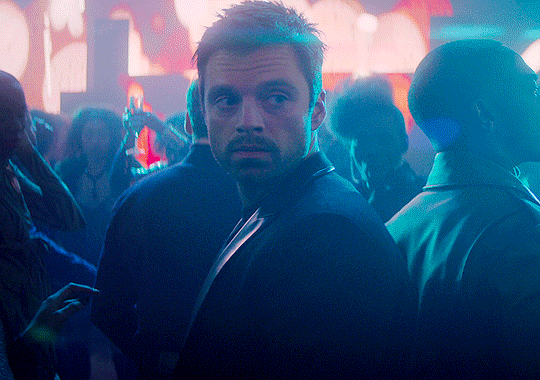
Request: "Can you please write something with the idea of y/n asking Bucky if she can tie a pink ribbon around his bicep? Thank you"
Pairing: Bucky Barnes x reader
Word count: 1.5k
Warnings: none, just fluff
Note: hooooly shit guys, i've been gone for way too long. hope you enjoy <3
_____
The jingle of keys in the doorknob had you lifting your eyes from your book, followed by the sound of the door opening and closing softly. The quiet whispers of a jacket being taken off, laces being untied, keys being set on the small table beside the door travelled through the apartment, meeting your ears and bringing a smile to your face.
Soft footsteps padded against the hardwood floor, careful to avoid any creaky spots.
"I'm awake, Buck," you called out softly from the comfort of your bed, and you heard him pause his movements. And then continue, a bit quicker than before.
Brown hair and blue eyes popped around the the edge of the door frame, brows furrowed. "It's midnight. Why are you still awake?"
You shrugged, sitting up in bed and setting your book aside. "Dunno, really. Got caught up reading."
Bucky frowned, and stepped into the room, walking over to the bed. "You can't sleep?"
It was a casual question, but you sensed the undertone of worry laced through it, and smiled to yourself.
"Actually, I spent most of the evening redecorating, so I'll probably start snoring as soon as the lights are off."
Bucky's hands reached for yours, grabbing them and bringing them up to his lips as he stood in front of you. One, two, three kisses along your knuckles. One hand, then the other.
"Redecorating?" he murmured against your skin, and you nodded slyly. His eyes narrowed, partially in amusement, partially in curiosity.
You cleared your throat and pulled your hands back, settling yourself back into the fluffy down of your pillows and blankets. "How was work today?"
At your question, Bucky's jaw ticked.
"It was fine."
You studied him for a few seconds, and cocked your head. "Just fine?"
He let out a heavy sigh, then collapsed atop the comforter at the foot of the bed. On nights like this, when he came home later than usual, the tension in his shoulders a bit more prominent than usual, the bags under his eyes a bit heavier, he found it hard to form sentences adequate enough to explain how he felt or what he needed.
Ever since the government cleared him of all charges and his mandated therapy ended, Bucky had taken up a job at the DCSA.
Defense Counterintelligence and Security Agency.
On paper, James Buchanan Barnes was an ordinary, ex-military security guard working for the Department of Defense and the United States.
In reality, the executive branch of the federal government reached out to him themselves and offered him a job doing what they claimed he did best: making people disappear, and making it seem like an accident. He was hesitant at first, unwilling to be the very thing he tried so hard to run away from being, but soon enough, they had made it very clear he had limited options: accept the position, or get thrown in prison for all the charges they claimed to have dropped.
So, for all his hesitating and hatred, Bucky Barnes was the United States government's own personal hitman, killing anybody who posed a threat to the life of the president, his family, or anybody in the Senate.
At least they paid better than HYDRA, Bucky had once joked. You could see, in his eyes, how much it pained him to revert back to his old ways, once again not having a choice.
Bucky cleared his throat, and glanced at you, blinking away the shadows behind his eyes.
"It's fine, sweetheart. I promise. It could have been worse."
Your heart cracked in your chest and you frowned, burying your cheek even deeper into your pillow as you looked at him. "If you say so."
Bucky pursed his lips to the side, then looked toward the door connecting your bedroom to the bathroom. Without a word, he got up, walking towards the bathroom and simultaneously pulling his shirt over his head. You smiled to yourself as you watched him disappear behind the door, flicking the lights on and letting the soft, yellow glow flood the floor of your room. You listened to him shuffle about, letting out a soft sigh as he unbuckled his belt.
His movements paused.
Your smile grew.
"Y/N?" he called out.
"Yes, babe?"
The door creaked open all the way, and behind it stood Bucky, holding his toothbrush in one hand, with a confused look on his face.
"Why is there a pink bow on my toothbrush?"
It took all your strength not to burst into a fit of giggles immediately as you schooled your face into one of nonchalance, and said, "I told you. I redecorated."
Bucky's bewildered eyes flickered from you, to the toothbrush, then back to you. Then he turned to look at the bathroom. And you saw the exact moment in which he realized there were pink bows everywhere. Big, small, light pink, dark pink, neon pink, cotton, silk, linen. A variety of ribbons tied in bows around everything you could think of: toothbrushes, toothpaste, shampoo bottles, the soap dispenser, the toilet brush, the towel rack, your skincare bottles, his deodorant and cologne.
"Y/N," Bucky said calmly.
"Yes?" you replied, batting your eyelashes innocently.
"Can you please tell me, why, exactly, you decided on redecorating with pink bows everywhere?"
You hummed, then shrugged. "You know, I'm not exactly sure. I just think they make pretty things look so much prettier. I may have gone a bit overboard, though."
"You think?"
You bit back a grin as you watched him shake his head, as if to snap him from his stupor of amusement, and bend over the sink to brush his teeth. You watched him brush his teeth, wash his face, change out of his jeans and into pajama pants. You tracked him as he turned the lights off and sighed, trudging over to the bed, exhaustion creeping into every one of his movements and pulling at him like gravity. You opened your arms wide, lifting the covers as you did so, and Bucky gladly crawled into them, nuzzling his head into your chest and wrapping his arms around your waist and back.
You placed a soft kiss to the crown of his head, and let your arms come loosely around his neck. Bucky said nothing, content to lay in silence and listen to the beat of your heart as it lulled him to sleep.
After a few minutes of you silently running your fingers through his hair, you whispered his name. "Bucky?"
He hummed in answer against your chest.
"You know how I said pink bows make pretty things even prettier?"
You felt, rather than saw, his body pause at the question, and then his head was up and his blue eyes were staring into yours with a puzzled expression. "Yes... why? What's that have to do with anything?"
"Well..."
You paused. All of a sudden, you felt stupid. Bucky's furrowed brows and sleepy eyes urged you to continue.
"I have a pink ribbon under the pillow, actually, and I was... I wanted to..."
"What, honey?"
"Well, I was wondering if I could tie it around your arm."
Bucky paused, blinking up at you slowly, as if he hadn't heard you.
"My arm?"
You nodded.
"Why?"
You shrugged. "Because it's already beautiful, and I want to make it even more so."
He laid there quiet for a moment, and you were about to tell him to forget about it, but then he unwrapped his arms from around you, letting you drop flat onto your back, and shoved a hand beneath your head. Beneath your pillow.
He emerged with a baby pink ribbon in his fingers, the material pliable and soft in his grip, as he handed it to you.
"Go ahead," he said simply.
You gave him a skeptical look. "Really?"
He shrugged with one shoulder. "Why not? Did you think I'd say no?"
You fell quiet, then let out a sigh through your nose, turning over slightly to better reach his arm. His left arm.
You wrapped the ribbon around his bicep, the vibranium cold and unyielding, a stark contrast to the warm pink silk in your fingers. You looped it through, pulling it taut, then let go. You stared at it for a second, then glanced up at Bucky. Leaning in, you pressed a light kiss to the exposed metal right above the bow.
Bucky let out a shuddering breath, then laid down again, this time face to face with you. His fingers traced soft, swirling patterns against the skin of your arm, leaving goosebumps in their wake, and you closed your eyes against the feeling.
"I love you so much," he muttered quietly. "You know that, right?"
You nodded, eyes closed and a smile playing at your lips. "I know. I love you, too. Every part of you."
Bucky loosed a breath that sounded somewhat like a disbelieving breath, and you felt him lean in and press a kiss to your temple.
You fell asleep without even realizing, lulled into dreams by the steady thrum of his heartbeat and his hand stroking your hair.
#bucky barnes#bucky barnes x reader#bucky barnes fic#james bucky barnes#bucky barnes fanfiction#bucky barnes fluff#bucky barnes x y/n#bucky barnes x you#marvel#mcu#marvel fanfic#sebastian stan#bucky barnes x female reader#sebastian stan fic#the winter soldier#the winter soldier fanfiction#tfatws#tfatws fanfiction
556 notes
·
View notes
Text
Three investigators for the Heritage Foundation have deluged federal agencies with thousands of Freedom of Information Act requests over the past year, requesting a wide range of information on government employees, including communications that could be seen as a political liability by conservatives. Among the documents they’ve sought are lists of agency personnel and messages sent by individual government workers that mention, among other things, “climate equity,” “voting” or “SOGIE,” an acronym for sexual orientation, gender identity and expression. The Heritage team filed these requests even as the think tank’s Project 2025 was promoting a controversial plan to remove job protections for tens of thousands of career civil servants so they could be identified and fired if Donald Trump wins the presidential election. All three men who filed the requests — Mike Howell, Colin Aamot and Roman Jankowski — did so on behalf of the Heritage Foundation’s Oversight Project, an arm of the conservative group that uses FOIA, lawsuits and undercover videos to investigate government activities. In recent months, the group has used information gleaned from the requests to call attention to efforts by the Defense Counterintelligence and Security Agency to teach staff about gender diversity, which Fox News characterized as the “Biden administration’s ‘woke’ policies within the Department of Defense.” Heritage also used material gathered from a FOIA search to claim that a listening session the Justice Department held with voting rights activists constituted an attempt to “rig” the presidential election because no Republicans were present. An analysis of more than 2,000 public-records requests submitted by Aamot, Howell and Jankowski to more than two dozen federal offices and agencies, including the State Department, the Department of Homeland Security and the Federal Trade Commission, shows an intense focus on hot-button phrases used by individual government workers.
The conservative think tank’s requests are clogging the pipeline at federal agencies in an apparent attempt to find employees a potential Trump administration would want to purge.
The authors of Project 2025 sure seem to be acting like Trump knows all about it despite his many claims to the contrary
28 notes
·
View notes
Text
The federal government is going MAGA — fast.
Why it matters: President Trump has only been in office a week, but the departments under his command are moving with blazing speed to transform the federal bureaucracy into an army of loyalists.
The new administration immediately moved to freeze nearly all foreign aid, root out DEI programs, remove officials and whole offices deemed ideologically suspect, and muzzle public health agencies.
"We're getting rid of all of the cancer ... caused by the Biden administration," Trump told reporters while signing a Day One executive order that stripped employment protections from civil servants.
Driving the news: Late Friday night, the White House fired 17 inspectors general — independent agency watchdogs responsible for identifying fraud, waste and corruption.
The mass firings, relayed via email, appear to violate a federal law that requires the administration to notify Congress 30 days before removing inspectors general.
Amid outrage from Democrats and ethics experts, Sen. Chuck Grassley (R-Iowa) — a Trump ally and longtime advocate for whistleblowers — called on the president to explain his decision to Congress.
Zoom in: DEI offices and programs have been shuttered across the government, including at the CIA, Department of Veterans Affairs, Army and Air Force, and the Federal Aviation Administration.
Federal workers have been ordered to report colleagues who may seek to "disguise" DEI efforts by using "coded language."
And Trump directed federal agencies to each identify "up to nine" major companies, universities or non-profits to investigate over their DEI practices.
There have been hundreds of staff removals or reassignments, including at the State Department, where far more career officers were asked to resign than in past administrations.
The Department of Justice reassigned at least 15 senior career officials, including a top counterintelligence attorney involved in the FBI's investigation of classified documents Trump stashed at Mar-a-Lago.
The DOJ also rescinded job offers to recent law school graduates who were placed through the Attorney General's Honors program.
Trump's National Security Council sent home around 160 staffers while Trump officials conducted loyalty screenings to ensure they're aligned with his agenda.
One of the administration's highest-profile firings so far was Coast Guard Commandant Adm. Linda Fagan, the first woman to lead a branch of the U.S. military. She was accused of leadership failures and an "excessive focus" on DEI at the Coast Guard Academy.
Between the lines: Trump loyalists have also moved to centralize control around public messaging, particularly when it comes to public health.
The Department of Health and Human Services ordered an unprecedented "immediate pause" on all health reports and social media posts through at least the end of the month, leading scientists to cancel CDC meetings on the escalating bird flu outbreak.
The Pentagon also ordered a global pause on all official social media posts until the confirmation of Defense Secretary Pete Hegseth, who has promised a radical culture shakeup across the U.S. military.
The new administration is also moving quickly on issues including LGBTQ and civil rights.
The State Department froze all passport applications with "X" designated as the gender.
DOJ ordered a freeze on civil rights litigation and is weighing a potential reversal of police reform agreements negotiated by the Biden administration.
It also ordered federal prosecutors to investigate local and state officials in so-called "sanctuary cities."
Meanwhile, the Pentagon moved to abolish an office set up during the Biden administration focused on curbing civilian deaths in combat operations.
Zoom out: Trump made no secret of his intentions to build a MAGA-aligned federal workforce during the campaign, and he quickly imposed a hiring freeze after taking office.
The vast majority of federal workers are career employees, not political appointments, but the president has made clear he wants them all to board the Trump train.
His administration is currently testing the ability to email the entire federal government workforce from a single email address.
What to watch: Trump's nominee to lead the Office of Management and Budget, Russ Vought, will be a key architect of the White House's efforts to re-engineer the administrative state.
Vought has assailed "the woke and weaponized bureaucracy," and said in a 2023 speech to his conservative think tank that he wants to put federal bureaucrats "in trauma," ProPublica reported.
"When they wake up in the morning, we want them to not want to go to work because they are increasingly viewed as the villains," Vought said — comments he defended during his confirmation hearing.
18 notes
·
View notes
Text
So this is...a bounty.
The Orange Liar destroying records:
..."President Trump continued his document destruction “despite being urged by at least two chiefs of staff and the White House counsel to follow the law on preserving documents. ”According to oficials familiar with these actions, “[h]undreds of documents, if not more, were likely torn up,” spanning “a range of topics, including conversations withforeign leaders[.]
”Reportedly the problem was “particularly acute at the time of the transition to the Biden administration.”Although the Trump White House instituted “special practices” to deal with his shredded records, including attempting to tape them backtogether, the article notes that it is “unclear how many records were lost or permanently destroyed through Trump’s ripping routine.”...
Spy Stuff:
..."The FBI also battled the Kremlin on the counterintelligence front.199 In1985 — dubbed the Year of the Spy, the FBI arrested 11 U.S. citizens for espionage, — including former U.S. warrant officer John Walker, who provided the Soviets highly classified cryptography codes during a spying career that began in the 1960s.The FBI also arrested Larry Wu-Tai Chin, a CIA employee, a spy for the People’sRepublic of China; Jonathan Pollard, a Naval Investigative Service intelligence analyst who stole secrets for Israel; and Ronald Pelton, a former National SecurityAgency communications specialist who provided the Soviet Union classified material.200 More recently convicted spies include FBI Special Agent Robert P.Hanssen, who spied on behalf of Soviet Union and, subsequently, Russia, and pleaded guilty to 15 espionage-related charges in 2001; and former Defense Intelligence Agency analyst Ana Belen Montes, arrested in 2001 and subsequently convicted for spying for Cuba."...
6 notes
·
View notes
Text
# Strategic Analysis: Embedded Corrupt Actors Initiating Attacks or Escaping to Earth Upon Imminent Discovery
---
## 1. **Actors and Motivations**
* **Embedded corrupt actors**: Deep-cover agents aligned with hostile factions (e.g., predator species, criminal syndicates, rogue states).
* **Motivations**:
* **Self-preservation:** Avoid capture, interrogation, or elimination.
* **Mission continuity:** Preserve or relocate command/control nodes and assets.
* **Strategic retreat:** Use Earth as a fallback safe haven or staging area.
* **Disruption:** Impair opposing forces through sabotage or diversion to delay response.
---
## 2. **Capabilities and Resources**
* **Access to sensitive intel and infrastructure**: Ability to manipulate communications, logistics, surveillance, and weaponry.
* **Ability to coordinate covert attacks**: Cyber warfare, misinformation, sabotage, or kinetic strikes.
* **Secret transport or escape methods**: Advanced technology like cloaked spacecraft, wormholes, or underground facilities.
* **Insider knowledge**: Foreknowledge of counterintelligence operations and detection methods.
* **Networked cells**: Distributed sleeper agents or collaborators facilitating escape and evasion.
---
## 3. **Threat Vectors**
| Vector | Description | Potential Impact |
| ---------------------------- | --------------------------------------------------------------- | ----------------------------------------------------- |
| **Preemptive sabotage** | Attacks on command centers, communication hubs, or transport. | Disruption of coordinated defense, delayed responses. |
| **Cyber infiltration** | Hacking into AI surveillance, sensor grids, and databases. | Blind spots, false positives, or corrupted intel. |
| **Misinformation campaigns** | False narratives to confuse authorities and public perception. | Paralysis or misallocation of response resources. |
| **Escape & relocation** | Use of clandestine routes or tech to reach Earth or safe zones. | Untracked movement enabling regrouping or staging. |
| **Insider manipulation** | Bribery, coercion, or threats to weaken loyalty of personnel. | Increased internal vulnerability and chaos. |
---
## 4. **Strategic Risks**
* **Compromise of Earth as a safe zone**: Earth could become a contested or occupied territory if hostile actors establish footholds.
* **Cascade of distrust within agencies**: Internal paranoia leading to purges, reduced cooperation, or systemic inefficiencies.
* **Escalation of conflict**: Preemptive attacks might trigger wider military engagements.
* **Technological degradation**: Sabotage of AI and surveillance weakens long-term defense posture.
* **Loss of strategic assets**: Vital intelligence, personnel, or equipment may be lost or captured.
---
## 5. **Strategic Opportunities**
* **Expose and neutralize embedded actors early**: Using counterintelligence and forensic investigation to root out insiders before triggering escape attempts.
* **Leverage insider knowledge for deception**: Turn discovered agents into double agents or use misinformation to lure hostile elements into traps.
* **Secure Earth as a fortified zone**: Prepare for defensive and intelligence operations to detect and prevent unauthorized arrivals or footholds.
* **Enhance AI robustness**: Harden detection and inference capabilities against sabotage or data poisoning.
* **Inter-agency cooperation**: Foster communication and trust across governments, militaries, and private sectors to share intelligence.
---
## 6. **Recommended Counterstrategies**
### A. **Early Detection & Surveillance**
* **Implement continuous vetting and behavioral analytics** on personnel with access to sensitive operations.
* **Monitor communications and travel logs** for anomalous patterns indicating planning of escape or sabotage.
* **Deploy AI-driven anomaly detection systems** with built-in redundancy and adversarial testing to prevent blinding.
### B. **Containment and Rapid Response**
* **Establish rapid reaction teams** capable of intervening before full escape or sabotage can be executed.
* **Create layered defense perimeters** around critical facilities and known escape routes.
* **Activate preplanned misinformation or counterintelligence campaigns** to sow confusion among hostile insiders.
### C. **Counter-Escape Operations**
* **Map and monitor known clandestine transit routes** (e.g., hidden gateways, black market spacecraft sales).
* **Use satellite and sensor grids** to detect unauthorized movements toward Earth or other safe zones.
* **Coordinate with allied intelligence agencies** to intercept agents in transit.
### D. **Post-Exposure Management**
* **Conduct comprehensive audits** of personnel, technology, and data for signs of compromise.
* **Maintain operational continuity plans** to quickly replace sabotaged systems or compromised personnel.
* **Leverage forensic cyber capabilities** to trace back attack origins and implicated actors.
---
## 7. **Conclusion**
Embedded corrupt actors launching attacks or attempting escape to Earth upon imminent discovery represent a **high-risk, high-impact threat vector**. Their insider access combined with preemptive sabotage and clandestine escape plans requires a **multi-layered strategic response** that combines:
* **Advanced AI and human intelligence synergy**
* **Vigilant personnel monitoring and vetting**
* **Rapid tactical response capabilities**
* **International cooperation and intelligence sharing**
Failure to address these risks can lead to severe operational, territorial, and security consequences—making this a critical focus for strategic defense planning.
0 notes
Text
Ukraine detains Hungarian spy network in westernmost Zakarpattia Oblast, SBU reports

The Security Service of Ukraine (SBU) has allegedly dismantled a Hungarian military intelligence network operating in Zakarpattia Oblast, detaining two agents accused of espionage against the Ukrainian state, the agency announced on May 9.
According to the SBU, this marks the first time Ukrainian authorities have exposed a Hungarian military intelligence network conducting activities harmful to Ukraine.
The operation’s objectives reportedly included gathering intelligence on military defenses, identifying vulnerabilities in its ground and air defense systems, and assessing local residents' socio-political views, particularly scenarios of public reaction if Hungarian troops entered the region.
Hungarian Prime Minister Viktor Orban has been broadly seen as the most Moscow-friendly leader in the EU during Russia’s all-out war against Ukraine. He has repeatedly opposed military aid for Ukraine, arguing that Western support prolongs the war.
Zakarpattia Oblast is a region with a sizable ethnic Hungarian minority and a sensitive location along NATO’s eastern frontier. Kyiv has long accused Budapest of undermining Ukraine’s sovereignty through political interference and dual citizenship schemes.
SBU counterintelligence detained two alleged agents as a result of a complex operation. Investigators identified their supervisor as a Hungarian military intelligence officer, whose identity has been established by the agency.
One of the suspects, a 40-year-old former Ukrainian military officer, was recruited by Hungarian intelligence and placed on standby in 2021.
The SBU said he was “activated” in September 2024. After that, he reportedly conducted reconnaissance on the deployment of Ukrainian Armed Forces and the coordinates of S-300 air defense systems in the region.
Join our community
Support independent journalism in Ukraine. Join us in this fight.
Support Us

The agency documented that after gathering intelligence, the agent crossed into Hungary to deliver reports to his handler.
During these meetings, the Hungarian intelligence officer allegedly provided him with cash to fund operations and instructed him to expand an informant network.
According to the investigation, the agent attempted to recruit at least two individuals.
In March 2025, the SBU recorded a second meeting between the agent and his handler. The agent reportedly received a phone equipped with specialized software for covert communications.
His new tasks included identifying official vehicles belonging to Ukraine's army, gathering data on military losses, and reporting front line developments through an identified contact in the Armed Forces.
The second detainee is a former member of Ukraine's security forces, who left service in 2025. The SBU said her responsibilities involved reporting on the presence of aircraft and helicopters in Zakarpattia and the air defense systems at her former military unit.
The agency said the suspects have been charged with high treason under martial law. They are currently in custody and face life imprisonment with property confiscation.
‘The front is noisy’ — for Ukraine’s soldiers, Russia’s Victory Day ‘ceasefire’ is yet another sham
Moscow’s self-declared truce which came into force at midnight on May 8 is not being felt on the front lines, Ukrainian soldiers have told the Kyiv Independent, reporting numerous cases of Russian military activity throughout the day. “There is no truce. There is shelling, artillery, drone and FPV (bomb) drops,” Petro Kuzyk, a battalion commander at the National Guard, said. The Kremlin announced the measure on April 28, claiming all military actions would halt on May 8 to midnight on May 11 t

The Kyiv IndependentChris York,

0 notes
Text

A confusing graphic showcasing the bureaucracy of the SEGh global coalition security state, or at least the parts I've made flags for.
Left to right, top to bottom these are:
In the corners: the organization-wide SEGh shield
The EXECUTIVE (EX)
The FIRST (FIRST)
The SECRETARIAT (SEC)
The Department for Preservation of Life (EX.DPoL)
The Department for General Welfare (EX.DGW)
The Department for Conflict Resolution (EX.DCR)
SECRETARIAT I (SEC.I, government)
SECRETARIAT II (SEC.II, records)
SECRETARIAT III (SEC.III, communication)
SECRETARIAT IV (SEC.IV, accountability)
SECRETARIAT V (SEC.V, security)
SECRETARIAT VI (SEC.VI, engineering)
SECRETARIAT VII (SEC.VII, territorial direction)
SECRETARIAT VIII (SEC.VIII, secrecy)
SECRETARIAT IX (SEC.IX, counterintelligence)
SECRETARIAT X (SEC.X, transportation)
SECRETARIAT XI (SEC.XI, economics)
SECRETARIAT XII (SEC.XII, health)
SECRETARIAT XIII (SEC.XIII, safety)
SECRETARIAT XIV (SEC.XIV, human services)
Bureau of Offensive Warfare (EX.DPoL.BOW)
Bureau of Defensive Warfare (EX.DPoL.BDW)
Bureau of Experimental Warfare (EX.DPoL.BXW)
Bureau of Non-Human Life (EX.DPoL.BNHL)
Bureau of Distribution (EX.DGW.BDis)
Bureau of Infrastructure (EX.DGW.BInfra)
Bureau of Production and Manufacturing (EX.DGW.BPaM)
Bureau of Law Enforcement (EX.DCR.BLE)
Bureau of International Justice (EX.DCR.BIJ)
Bureau of the Army (EX.DCR.BtA)
Bureau of Internal Affairs (EX.DCR.BIA)
Agency of the Library (SEC.II.LibA)
Nuclear Weapons Command (EX.DPoL.BOW.NWC)
Observation and Reconnaissance Command (EX.DPoL.BOW.OaRC)
MagnetoDynamics Research Unified Command (EX.DPoL.BXW.MDRUC)
Grid Command (EX.DGW.BInfra.GridC)
Salvo Administration (EX.DPoL.BOW.NWC.SalA)
Collider Isotope Production Administration (EX.DPoL.BOW.NWC.CIPA)
Early Warning Telescope Administration (EX.DPoL.BDW.OaRC.EWTA)
Temporal Optimization Research Administration (EX.DPoL.BXW.MDRUC.TORA)
Advanced Power Generation Research Administration (EX.DPoL.BXW.MDRUC.APGRA)
High Yield Detonation Research Administration (EX.DPoL.BXW.MDRUC.HYDRA)
Other plot-relevant but not pictured bodies include:
Artificial Genetics Research Command (EX.DPoL.BXW.AGRC)
Artificial Temporal Endurance Research Administration (EX.DPoL.BXW.AGRC.ATERA)
Casualty Management Command (EX.DPoL.BDW.CMC)
Special-Purpose Personnel Acquisition Agency (SEC.XIV.SPPAA)
0 notes
Text
Exclusions from Federal Labor-Management Relations Programs
Issued March 27, 2025.
By the authority vested in me as President by the Constitution and the laws of the United States of America, including sections 7103(b)(1) of title 5 and 4103(b) of title 22, United States Code, to enhance the national security of the United States, it is hereby ordered:
Section 1. Determinations. (a) The agencies and agency subdivisions set forth in section 2 of this order are hereby determined to have as a primary function intelligence, counterintelligence, investigative, or national security work. It is also hereby determined that Chapter 71 of title 5, United States Code, cannot be applied to these agencies and agency subdivisions in a manner consistent with national security requirements and considerations.
(b) The agency subdivisions set forth in section 3 of this order are hereby determined to have as a primary function intelligence, counterintelligence, investigative, or national security work. It is also hereby determined that Subchapter X of Chapter 52 of title 22, United States Code, cannot be applied to these subdivisions in a manner consistent with national security requirements and considerations.
Sec. 2. Additional National Security Exclusions. Executive Order 12171 of November 19, 1979, as amended, is further amended by:
(a) In section 1-101, adding “and Section 1-4” after “Section 1-2” in both places that term appears.
(b) Adding after section 1-3 a new section 1-4 that reads:
“1-4. Additional Exclusions.
1-401. The Department of State.
1-402. The Department of Defense, except for any subdivisions excluded pursuant to section 4 of the Executive Order of March 27, 2025, entitled ‘Exclusions from Federal Labor-Management Relations Programs.’
1-403. The Department of the Treasury, except the Bureau of Engraving and Printing.
1-404. The Department of Veterans Affairs.
1-405. The Department of Justice.
1-406. Agencies or subdivisions of the Department of Health and Human Services:
(a) Office of the Secretary.
(b) Food and Drug Administration.
(c) Centers for Disease Control and Prevention.
(d) Administration for Strategic Preparedness and Response.
(e) Office of the General Counsel.
(f) Office of Refugee Resettlement, Administration for Children and Families.
(g) National Institute of Allergy and Infectious Diseases, National Institutes of Health.
1-407. Agencies or subdivisions of the Department of Homeland Security:
(a) Office of the Secretary.
(b) Office of the General Counsel.
(c) Office of Strategy, Policy, and Plans.
(d) Management Directorate.
(e) Science and Technology Directorate.
(f) Office of Health Security.
(g) Office of Homeland Security Situational Awareness.
(h) U.S. Citizenship and Immigration Services.
(i) United States Immigration and Customs Enforcement.
(j) United States Coast Guard.
(k) Cybersecurity and Infrastructure Security Agency.
(l) Federal Emergency Management Agency.
1-408. Agencies or subdivisions of the Department of the Interior:
(a) Office of the Secretary.
(b) Bureau of Land Management.
(c) Bureau of Safety and Environmental Enforcement.
(d) Bureau of Ocean Energy Management.
1-409. The Department of Energy, except for the Federal Energy Regulatory Commission.
1-410. The following agencies or subdivisions of the Department of Agriculture:
(a) Food Safety and Inspection Service.
(b) Animal and Plant Health Inspection Service.
1-411. The International Trade Administration, Department of Commerce.
1-412. The Environmental Protection Agency.
1-413. The United States Agency for International Development.
1-414. The Nuclear Regulatory Commission.
1-415. The National Science Foundation.
1-416. The United States International Trade Commission.
1-417. The Federal Communications Commission.
1-418. The General Services Administration.
1-419. The following agencies or subdivisions of each Executive department listed in section 101 of title 5, United States Code, the Social Security Administration, and the Office of Personnel Management:
(a) Office of the Chief Information Officer.
(b) any other agency or subdivision that has information resources management duties as the agency or subdivision’s primary duty.
1-499. Notwithstanding the forgoing, nothing in this section shall exempt from the coverage of Chapter 71 of title 5, United States Code:
(a) the immediate, local employing offices of any agency police officers, security guards, or firefighters, provided that this exclusion does not apply to the Bureau of Prisons;
(b) subdivisions of the United States Marshals Service not listed in section 1-209 of this order; or
(c) any subdivisions of the Departments of Defense or Veterans Affairs for which the applicable Secretary has issued an order suspending the application of this section pursuant to section 4 of the Executive Order of March 27, 2025, entitled ‘Exclusions from Federal Labor-Management Relations Programs.’”
Sec. 3. Foreign Service Exclusions. Executive Order 12171, as amended, is further amended by:
(a) In the first paragraph:
(i) adding “and Section 4103(b) of Title 22,” after “Title 5”; and
(ii) adding “and Subchapter X of Chapter 52 of Title 22” after “Relations Program.”.
(b) Adding after section 1-102 a new section 1-103 that reads:
“1-103. The Department subdivisions set forth in section 1-5 of this order are hereby determined to have as a primary function intelligence, counterintelligence, investigative, or national security work. It is also hereby determined that Subchapter X of Chapter 52 of title 22, United States Code, cannot be applied to those subdivisions in a manner consistent with national security requirements and considerations. The subdivisions set forth in section 1-5 of this order are hereby excluded from coverage under Subchapter X of Chapter 52 of title 22, United States Code.”
(c) Adding after the new section 1-4 added by section 2(b) of this order a new section 1-5 that reads:
“1-5. Subdivisions of Departments Employing Foreign Service Officers.
1-501. Subdivisions of the Department of State:
(a) Each subdivision reporting directly to the Secretary of State.
(b) Each subdivision reporting to the Deputy Secretary of State.
(c) Each subdivision reporting to the Deputy Secretary of State for Management and Resources.
(d) Each subdivision reporting to the Under Secretary for Management.
(e) Each subdivision reporting to the Under Secretary for Arms Control and International Security.
(f) Each subdivision reporting to the Under Secretary for Civilian Security, Democracy, and Human Rights.
(g) Each subdivision reporting to the Under Secretary for Economic Growth, Energy, and Environment.
(h) Each subdivision reporting to the Under Secretary for Political Affairs.
(i) Each subdivision reporting to the Under Secretary for Public Diplomacy.
(j) Each United States embassy, consulate, diplomatic mission, or office providing consular services.
1-502. Subdivisions of the United States Agency for International Development:
(a) All Overseas Missions and Field Offices.
(b) Each subdivision reporting directly to the Administrator.
(c) Each subdivision reporting to the Deputy Administrator for Policy and Programming.
(d) Each subdivision reporting to the Deputy Administrator for Management and Resources.”.
Sec. 4. Delegation of Authority to the Secretaries of Defense and Veterans Affairs. (a) Subject to the requirements of subsection (b) of this section, the Secretaries of Defense and Veterans Affairs are delegated authority under 5 U.S.C. 7103(b)(1) to issue orders suspending the application of section 1-402 or 1-404 of Executive Order 12171, as amended, to any subdivisions of the departments they supervise, thereby bringing such subdivisions under the coverage of the Federal Service Labor-Management Relations Statute.
(b) An order described in subsection (a) of this section shall only be effective if:
(i) the applicable Secretary certifies to the President that the provisions of the Federal Service Labor-Management Relations Statute can be applied to such subdivision in a manner consistent with national security requirements and considerations; and
(ii) such certification is submitted for publication in the Federal Register within 15 days of the date of this order.
Sec. 5. Delegation of Authority to the Secretary of Transportation. (a) The national security interests of the United States in ensuring the safety and integrity of the national transportation system require that the Secretary of Transportation have maximum flexibility to cultivate an efficient workforce at the Department of Transportation that is adaptive to new technologies and innovation. Where collective bargaining is incompatible with that mission, the Department of Transportation should not be forced to seek relief through grievances, arbitrations, or administrative proceedings.
(b) The Secretary of Transportation is therefore delegated authority under section 7103(b) of title 5, United States Code, to issue orders excluding any subdivision of the Department of Transportation, including the Federal Aviation Administration, from Federal Service Labor-Management Relations Statute coverage or suspending any provision of that law with respect to any Department of Transportation installation or activity located outside the 50 States and the District of Columbia. This authority may not be further delegated. When making the determination required by 5 U.S.C. 7103(b)(1) or 7103(b)(2), the Secretary of Transportation shall publish his determination in the Federal Register.
Sec. 6. Implementation. With respect to employees in agencies or subdivisions thereof that were previously part of a bargaining unit but have been excepted under this order, each applicable agency head shall, upon termination of the applicable collective bargaining agreement:
(a) reassign any such employees who performed non-agency business pursuant to section 7131 of title 5 or section 4116 of title 22, United States Code, to performing solely agency business; and
(b) terminate agency participation in any pending grievance proceedings under section 7121 of title 5, United States Code, exceptions to arbitral awards under section 7122 of title 5, United States Code, or unfair labor practice proceedings under section 7118 of title 5 or section 4116 of title 22, United States Code, that involve such employees.
Sec. 7. Additional Review. Within 30 days of the date of this order, the head of each agency with employees covered by Chapter 71 of title 5, United States Code, shall submit a report to the President that identifies any agency subdivisions not covered by Executive Order 12171, as amended:
(a) that have as a primary function intelligence, counterintelligence, investigative, or national security work, applying the definition of “national security” set forth by the Federal Labor Relations Authority in Department of Energy, Oak Ridge Operations, and National Association of Government Employees Local R5-181, 4 FLRA 644 (1980); and
(b) for which the agency head believes the provisions of Chapter 71 of title 5, United States Code, cannot be applied to such subdivision in a manner consistent with national security requirements and considerations, and the reasons therefore.
Sec. 8. General Provisions. (a) Nothing in this order shall be construed to impair or otherwise affect:
(i) the authority granted by law to an executive department or agency, or the head thereof; or
(ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
0 notes
Text
Treasury Secretary says federal job cuts necessary because the US government was crowding out the private market.
The New Republic - Malcolm Ferguson/ April 7, 2025 Treasury Secretary Says Fired Federal Workers Can Work in the Factory Scott Bessent has an unbelievable career pivot in mind for all the federal employees the Trump administration has fired “And we’re going to relever the private sector. So the private sector, in essence, has been in recession during the Biden years. And this is an opportunity to right-size the federal government and unleash the private sector again, because it’s been hemmed down by excessive regulation, and it’s been crowded out by the government.” — Scott Bessent (emphasis added)
China is trying to recruit current and former feds, intelligence document warns The notice is one of the first public acknowledgements from the U.S. intelligence community showing how adversaries are leveraging DOGE-led layoffs to target the government. April 9, 2025 11:12 AM ET By David DiMolfetta, Cybersecurity Reporter, Nextgov/FCW China and other groups are “targeting current and former U.S. government (USG) employees for recruitment by��posing as consulting firms, corporate headhunters, think tanks, and other entities on social and professional networking sites,” said the document, which also contains seals from the Justice Department and the Defense Counterintelligence and Security Agency. (emphasis added)
#trump administration#government#outsourcing#offshoring#private sector#public sector#intelligence#infosec#security#jobs#national security#cybersecurity#privatization
0 notes
Text
Counterintelligence and SCNS detained several servicemen — Defense Ministry -
14:14, 25 February 2025, Bishkek – 24.kg news agency , by Baktygul OSMONALIEVA Officers of the State Committee for National Security of Kyrgyzstan (SCNS), together with military counterintelligence officers, detained several servicemen of the Defense Ministry. The press service of the Defense Ministry reported. «The Ministry of Defense of the Kyrgyz Republic reports that, together with the…
0 notes
Text
Mastering DISS, NISS, and NBIS Management: A Complete Guide for FSOs
Introduction
For Facility Security Officers (FSOs) and security professionals handling classified contracts, efficient management of DISS, NISS, and the evolving NBIS system isn’t just important—it’s critical. These platforms serve as the backbone of personnel security, facility management, and insider threat mitigation for organizations dealing with classified information.
Yet, navigating these systems can feel like wrangling a three-headed beast—each system with its quirks, frequent updates, and ever-changing compliance requirements. Understanding their functions, key differences, and best management practices ensures your organization remains in full compliance with the National Industrial Security Program (NISP).
This guide breaks down everything you need to know, from system capabilities to hands-on strategies for FSOs.
What Are DISS, NISS, and NBIS?
DISS (Defense Information Security System)
The Defense Information Security System (DISS) is the primary personnel security clearance management system under the Defense Counterintelligence and Security Agency (DCSA). It replaced JPAS (Joint Personnel Adjudication System) and is used for:
Submitting and tracking security clearance investigations
Managing personnel access records
Communicating clearance-related updates with DCSA
Initiating incident reports and continuous vetting reviews
DISS is divided into two subsystems:
JVS (Joint Verification System): Used for verifying security clearances, eligibility, and managing personnel records.
CAF (Consolidated Adjudications Facility): Handles clearance adjudications and eligibility decisions.
NISS (National Industrial Security System)
The National Industrial Security System (NISS) is DCSA’s web-based tool for industrial security facility management. It enables FSOs to:
Submit and track facility clearance (FCL) requests
Manage security vulnerability assessments
Submit sponsorship and ownership changes
Access security alerts, documentation, and training materials
NISS acts as the primary platform for facility clearance actions, making it indispensable for organizations handling classified work.
NBIS (National Background Investigation Services)
The National Background Investigation Services (NBIS) is the newest security system, gradually replacing legacy clearance management systems. It’s designed as a centralized solution for personnel vetting, aiming to modernize and streamline the security clearance process.
NBIS incorporates:
End-to-end digital security clearance processing
Improved automation and case tracking
Enhanced analytics for insider threat detection
Integration with Continuous Vetting (CV) programs
With NBIS rolling out in phases, FSOs must prepare for the transition while maintaining compliance with existing DISS and NISS requirements.
Why FSOs Must Master DISS, NISS, and NBIS
1. Compliance with Government Regulations
Failure to properly manage these systems can result in FCL suspension, personnel clearance delays, and security violations. DCSA expects FSOs to understand and effectively use these platforms for compliance with NISPOM requirements.
2. Speeding Up Clearance and Facility Processing
A well-managed security program minimizes clearance delays and ensures rapid onboarding for cleared personnel. Proper NISS management also reduces delays in facility clearance approvals and sponsorship processing.
3. Strengthening Insider Threat Programs
DISS and NBIS provide incident reporting tools and continuous evaluation capabilities. FSOs who proactively manage these reports can mitigate insider threats before they escalate.
4. Avoiding Costly Mistakes
Mistakes in clearance sponsorship, incomplete NISS filings, or mismanagement of clearance eligibility can lead to contract delays, compliance fines, or loss of classified work.
Best Practices for Managing DISS
1. Keep Personnel Security Records Updated
Ensure employee clearance records, eligibility statuses, and accesses are always accurate in DISS. Common issues arise when:
Personnel have outdated visit requests
Employees change contracts without access updates
Incident reports remain unresolved
2. Monitor Continuous Vetting (CV) Alerts
DISS integrates with Continuous Vetting (CV), where security clearance holders are subject to real-time monitoring. FSOs should:
Review vetting alerts promptly
Report security concerns through JVS
Follow up on adjudication outcomes
3. Establish a DISS Management SOP
Having a Standard Operating Procedure (SOP) for managing DISS ensures:
Consistent clearance tracking and case monitoring
Proper handling of incoming/outgoing visit requests
Regular clearance audits to catch discrepancies
4. Train Employees on DISS Usage
DISS isn’t intuitive for first-time users. Conduct internal training for security staff to reduce errors in clearance submissions, reporting, and tracking.
Best Practices for Managing NISS
1. Submit Facility Changes Promptly
Any changes in company ownership, location, or FSO assignments must be immediately updated in NISS to avoid compliance risks.
2. Track Security Vulnerability Assessments (SVA)
DCSA conducts periodic Security Vulnerability Assessments (SVA) for cleared facilities. FSOs should:
Review previous assessments in NISS
Address identified deficiencies proactively
Upload compliance documentation before the next review
3. Keep Facility Clearance Sponsorships Accurate
Sponsorship issues can delay new facility clearances (FCLs) or cause problems with contract eligibility. Always:
Ensure sponsorship data is up to date
Verify that FCL records match contract requirements
4. Utilize NISS Reporting for Better Security Posture
NISS offers security alerts, compliance updates, and training resources. FSOs should leverage these tools for:
Preparing for audits
Understanding NISPOM changes
Tracking required compliance actions
Best Practices for Transitioning to NBIS
1. Prepare for System Migration
DCSA is rolling out NBIS in phases. FSOs must:
Track NBIS implementation updates from DCSA
Ensure staff receives NBIS training
Verify that personnel records transfer correctly from DISS
2. Adjust Personnel Security Workflows
NBIS changes how security investigations are handled. Expect:
Automated clearance adjudications
Integrated risk assessments
New reporting and tracking tools
3. Monitor System Performance and Security Alerts
Since NBIS is still evolving, FSOs should report system issues and track policy updates to avoid processing errors.
4. Leverage NBIS for Proactive Security
NBIS enhances insider threat detection through:
Real-time risk assessments
Advanced security analytics
Automated alerts for clearance concerns
FSOs who take advantage of these tools improve overall security posture and reduce clearance risks.
Common Pitfalls FSOs Should Avoid
1. Neglecting Regular Clearance Audits
Failing to audit security clearance statuses can lead to inactive employees retaining access to classified materials.
2. Delayed Incident Reporting
Incident reports must be submitted ASAP in DISS/NBIS to prevent security lapses and ensure timely adjudication.
3. Mismanaging Facility Clearance Changes
Failure to update NISS with FCL modifications can cause contract suspensions and compliance violations.
4. Ignoring System Training and Updates
DCSA regularly updates DISS, NISS, and NBIS. FSOs who don’t stay current struggle with system functionality and risk compliance gaps.
Conclusion: Why Mastering These Systems Matters
DISS, NISS, and NBIS management isn’t just an administrative burden—it’s a mission-critical responsibility for FSOs ensuring national security compliance. By implementing clear workflows, regular audits, and proactive system monitoring, your organization stays ahead of security risks, avoids costly clearance delays, and maintains eligibility for classified contracts.
As NBIS continues rolling out, FSOs must adapt quickly to new processes and security requirements. Organizations that invest in system training and proactive security management will emerge as industry leaders in classified contract compliance.
For expert guidance on FSO services, compliance strategies, and security system management, contact AOCI today—the trusted leader in industrial security solutions.
0 notes
Text
The Department of Government Efficiency (DOGE) has outlined an ambitious agenda and is rapidly gaining momentum. Beyond organizations, programs, and grants, however, lies a realm that has defied reform. It encompasses elected officials, civilians, military service members, intelligence officers, and private sector professionals. It spans retirees to interns, massive domestic installations to austere overseas outposts. It totals nearly three million individuals and the waiting list to join is several months long. Most of all, its power is information, and it guards its privileges jealously and unyieldingly. DOGE may have no greater challenge than tackling the Republic of Security Clearance–Holders.
Elon Musk and Vivek Ramaswamy, the co-principals of DOGE, have identified three major areas of reform—regulatory rescissions, administrative reductions, and cost savings. Unfortunately, the realm of classified information cannot be located in a single regulation, administrative entity, or budget line. DOGE won’t be able to highlight single examples of egregious waste or incompetent leadership. The entire enterprise is sprawling, complex, opaque, and nearly impenetrable.
Prior to 2018, the Office of Personnel Management oversaw approximately 95 percent of all background investigations. In 2019, DOD assumed responsibility. The Defense Counterintelligence Security Agency (DCSA) now similarly conducts about 95 percent of all background investigations for the executive branch, and at least 21 federal agencies have the authority to conduct all or some of their own investigations.
0 notes
Text

By Julian E. Barnes
Julian Barnes covers American intelligence agencies and has been covering the Russian sabotage campaign.
Nov. 21, 2024
U.S. officials warned on Thursday that Russia may be targeting American defense companies in a potentially stepped-up sabotage campaign.
The new warning said that Russia’s intelligence services had conducted sabotage operations against European defense companies “in an attempt to undermine Allied support for Ukraine.”
Russia’s campaign, officials said, increases the risk to American companies overseas and, at least potentially, in the United States.
The warning was issued by the National Counterintelligence and Security Center, which advises American businesses on intelligence threats from potential adversaries.
The center often warns about attempts by the Russian and Chinese governments to steal intellectual property or potential cyberthreats against American businesses.
The alert issued on Thursday urged executives at defense companies to be on the lookout for surveillance near their facilities and staff, as well as for signs of trespassing or vandalism. Intelligence officials also said defense firms should be extra watchful for potential disruptions and should increase their physical and online security.
In addition to protecting sites, the center suggested bolstering personal security for executives and other key employees.
The warning, according to people briefed on the matter, was spurred in part by concern about a Russian attempt to assassinate the head of a German arms maker.
In the notice published on Thursday, the center said defense company officials should be careful when discussing travel plans, vary their routes to and from work, and report suspicious incidents.
“Those involved in work tied to Ukraine or other geopolitical conflicts should be cautious about disclosing work, travel, personal and family information online,” the warning said. “Adversaries can use this information to identify access, location and personal vulnerabilities.”
The warning highlighted Britain’s arrest of several people in an arson attack in March on a business linked to Ukraine, and Poland’s announcement in June that it had arrested 18 people accused of plotting sabotage attacks on behalf of Russia.
In addition, Western officials previously warned that Russia had plotted to plant incendiary devices in cargo planes and was potentially planning to set off those devices in U.S. warehouses or on planes bound for the United States.
So far all of Russia’s known sabotage attacks have taken place in Europe, although Russian intelligence has targeted many countries, including Britain, France, Germany, Lithuania and beyond. But some officials believe that Russia wants to expand its sabotage campaign to the United States, particularly if the Biden administration in its closing weeks continues to support Ukraine in its war against Russia or takes steps that Russia sees as escalatory.
A small fire at the Scranton Army Ammunition Plant in Pennsylvania in September, and another incident at the same site in April, set off concerns that Russia had extended its campaign to the United States. But officials believe those fires were an accident, not sabotage.
Intelligence agencies had previously assessed that if the United States allowed Ukraine to use longer-range missiles to strike Russian territory, Russia might attempt deadlier acts of sabotage.
The Biden administration this week allowed Ukraine to fire the Army Tactical Missile Systems, or ATACMS, at targets in Russia. The U.S. move came in response to Russia’s decision to use North Korean troops in the war.
https://www.nytimes.com/2024/11/21/us/politics/defense-companies-russia-sabotage.html
0 notes
Text

The Most Banned Movie In America!
Shocks Nation With "T" For Truth Rating
In an unprecedented moment in cinematic history, The Most Banned Movie in America, “Splintering Babylon,” the film the critics won’t watch and politicians will avoid for its radioactive content, has become the first movie to receive the highly controversial ‘T’ for Truth rating from the newly-formed FEMA Rumor Response unit.
The Verdict: SEE IT (If You Can). Limited screenings of The Most Banned Movie in America will be held in undisclosed locations, with showtimes posted in invisible ink. For those unable to attend, worry not—bootlegged digital files are circulating on the black market (but be careful, it’s rumored they’re being tracked
GARY BERTSEN TRANSCRIPT
Gary Berntsen: Hello, my name is Gary Berntsen. I'm a veteran of the United States Air Force and a retired Senior Operations Officer and Chief-of-Station of the Central Intelligence Agency.
For over three decades, I served in the US National Security apparatus, in various capacities.
Shortly after the attacks of 11 September 2001, I entered Afghanistan and commanded CIA paramilitary forces, helping seize the cities of Talaqan and the capital of Afghanistan, Kabul.
I was the driving force and architect of the Battle of Tora Bora. I held the position as Chief of Hezbollah Operation in CIA's Counterterrorism Center for several years and concluded my service in CIA as a Chief-of-Station in Latin America, combating narco-terrorists.
Approximately six years ago, a business associate and I began working together as whistleblowers for the Department of Justice, FBI, DEA and Homeland Security Investigations (HSI). Our target was the largest and most well-funded transnational criminal organization on the planet called the Cartel de los Soles, "Cartel of the Suns".
Share
The Cartel de los Soles is the Venezuelan government and is led by Venezuelan President Nicolás Maduro, Diosdado Cabello, Minister of Defense Vladimir López Padrino, President of the National Assembly Jorge Rodríguez, and former Directorate General of Military Counterintelligence Hugo Carbajal, who was detained in Spain several years ago and extradited to New York. He is currently awaiting trial for narco-trafficking.
Venezuelan President Maduro has a US indictment and bounty of US $15 million for his capture. Diosdado Cabello has US indictment and a $10 million bounty on his head. At least six other Venezuelan cabinet members and senior officials are indicted.
In the last 20 years, the Cartel de los Soles has stolen $1 trillion US dollars from Venezuela's national oil company, PDVSA, and embezzled $500 billion US dollars from its national treasury. It not only has – but continues to produce and smuggle – 25 to 40 metric tons of cocaine every month, out of its country into the world.
Upgrade to paid
The Cartel del Sol is a $2 trillion transnational criminal organization and the most well-resourced criminal syndicate in history. Through bribery and investments of its funds, it controls a dozen countries and world leaders. It has massive investments in the US and European financial markets and institutions.
As we conducted investigations against the Cartel de los Soles and presented them, one after another to the US Department of Justice, we noticed and pursued leads from the Cartel's money-laundering operations to the world of non-governmental organizations and election companies.
After witnessing election irregularities associated with the 2020 US Presidential Election, we decided to direct time and resources to Cartel del Sol links to US and global election fraud.
After an exhaustive three-and-a-half-year investigation, it is indisputable: Smartmatic Election Systems was created at the direction of now-deceased Venezuelan dictator Hugo Chavez, and its source code, the basis of its operating system developed jointly by Venezuela's Consejo Nacional Electoral (CNE) and Smartmatic, was designed to allow election results to be altered without the knowledge of voters and the public.
Additionally, the Venezuelan CNE holds ownership of Smartmatic's source code. Each time the Venezuelan CNE and Smartmatic update the source code, a copy of it is stored at the vault at the Venezuelan Central Bank.
In 2005, the European Union Electoral Observation Mission to Venezuela published a report, stating the Venezuelan regime owns Smartmatic's source code. The Venezuelan government signed that report as factual.
Smartmatic's first election in Venezuela was the 2003 Recall Election of Hugo Chavez. The CNE director at the time, Jorge Rodriguez, at the direction of the Cuban Directorate General of Intelligence, DGI, hired three Venezuelan-American computer engineers that were graduates of Simon Bolivar University, a Venezuelan university linked to the US University, MIT.
They had already registered a software company in Delaware and opened an office for it, in Boca Raton. The engineers, Antonio Mugica, Roger Piñate, and Alfredo Anzola, established Smartmatic at the direction of the Venezuelan regime, built the source code, and flew off to Italy to buy lottery machines from Olivetti to serve as election hardware. They succeeded in altering-up votes to ensure Hugo Chavez's victory in the recall election.
Secure in power, President Chavez decided to weaponize this capability beyond Venezuela's border. Smartmatic would enter into the US election market in Cook County, Illinois [aka Chicago] and the state of New Jersey for Democratic Party Primary races in 2006.
In 2005, Smartmatic orchestrated the purchase of Sequoia Voting Systems Inc, a US company. Sequoia was a company that had conducted elections in the US for over 100 years and had a 22% market share of the US electoral market.
Approximately 18 months later, the Committee on Foreign Investments in the United States, CFIUS, began investigating the ownership of Smartmatic, because of Smartmatic's Venezuelan connection.
Smartmatic immediately put its source code in the machines, in the Sequoia machines. Smartmatic tried to conceal its Venezuelan connection by hiring a former US Naval Officer, Jack Blaine, to set up a holding company, SVS Holding, to place its ownership of Sequoia in stock.
In December 2006, Smartmatic entered into an agreement with CFIUS to sell Sequoia in six months.
Antonio Mugica, one of the three original founders, then found a little-known election company in Toronto, Canada, Dominion Election Systems, that had only managed one small local election in Toronto. He arranged for Dominion to purchase Sequoia.
Dominion, owned by John Poulos, with that purchase of Sequoia would inherit the licensing agreement for Smartmatic's source code, the source code owned by the Venezuelan regime, i.e., the Cartel de los Soles.
To be clear, Smartmatic and Dominion would ultimately sign an agreement that provided Dominion with the US market and Smartmatic with the international global market. The only two exceptions are that Smartmatic does elections in Los Angeles County and Puerto Rico. Puerto Rico was an issue they ultimately settled in court.
In Caracas, in a building owned by the CNE, the Concejo Nacional Electoral, more than 100 software engineers, half in the CNE and half in Smartmatic, worked side-by-side. Their effort for more than a decade was to perfect the techniques of altering elections and defeating audit.
In 2018, Smartmatic publicly, and with the approval of the Venezuelan regime, broke with the regime, the Cartel de los Soles, because the Venezuelan CNE's theft of an election was so egregious.
The techniques of the source code and machine operate and conceal a theft of an election when the spread of the candidates is between three to five percentage points.
As sophisticated as the machine is, it can be defeated with significant turnout against it. The recent 2024 election in Venezuela was also so blatantly stolen and the machine could not conceal that massive spread, either.
In its place, a company called Xclay [?] took Smartmatic's place as the election provider in Venezuela. Allowing Smartmatic to exit Venezuela in this fictitious manner allowed the regime to retain its power and influence over the global electoral market.
Smartmatic built a production facility for electronic voting equipment hardware just outside Beijing, China, and then shipped the hardware to a warehouse in Taiwan. In violation of US Law, the hardware was marked as "Manufactured in Taiwan" and shipped to both Smartmatic and Dominion, for use in US elections.
Dominion Voting Systems manages elections in almost all the Swing States in the US, which determines who wins the Presidency. We have evidence and witnesses that can prove the source code operating the election machines of both Smartmatic and Dominion and other election companies are owned by the Venezuelan NARPA regime.
We have evidence and witnesses proving the machines are manufactured in the People's Republic of China.
Every citizen needs to be asking, "Where is the DOJ, FBI, CISA, and where is the CIA? Is anyone in the national security apparatus defending our democracy or enforcing the law?"
And if that isn't enough to convince you there's a major problem, Dominion, in an additional step to conceal its manipulation of US elections, moved its research and development and servers, which store Swing State voting information, to its office in Belgrade, Serbia!
Upgrade to paid
In the Belgrade office, Venezuelan, Chinese, and Serbian software engineers maintain system administrative status over swing state elections and alter elections, as directed by the Cartel de los Soles, the Cuban DGI, and the Chinese CCP.
The facility and its personnel are protected by Serbia's counterintelligence service. Swing State voter information is saved on Huawei servers in Dominion's Belgrade office. These servers are linked to Huawei servers in Hong Kong, China.
For years, the US National Security apparatus has identified Huawei and its technology as a threat to US National Security.
The Cybersecurity and Infrastructure Security Agency, CISA, a component of the United States Department of Homeland Security, is responsible for cybersecurity and infrastructure, across all levels of government.
CISA has 3,100 employees and a $2.9 billion budget. In 2020, when faced with calls to address election irregularities, CISA did a conference call with Smartmatic and Dominion, in order to better able to address the public's concerns and assure everyone that there had been "No irregularities".
Yes, it's shocking. CISA decided to consult the criminals in order to respond to the American public's outcry.
In August 2024, three current and former executives of Smartmatic were indicted in Florida, in connection with bribery during the 2016 election in the Philippines. Among those arrested executives is Roger Peñate, one of the three founders and current President of Smartmatic. Roger Peñate paid $8.5 million in bail.
What the public will soon learn is that the bribery paid in the case was not to obtain a contract. The bribery was paid to alter election results.
We have the CNE source code, the source code employed by Smartmatic, Dominion, and others. We will surrender it to appropriate authorities.
Source code, like DNA, can easily be matched with other systems to prove that they are from the same family. In this particular case, it is a family of altering elections.
Two years ago, we briefed a senior FBI agent in Washington, DC. That agent, after seeing our three-hour presentation with corporate ownership documents, engineering specifications, and witness statements, told us to flee Washington, DC, that the FBI would actively work to destroy our efforts and seek ways to prosecute us, in order to stop our investigative efforts. That was a stunning moment, hearing those words from a 20-year veteran of the FBI.
Seven months ago, with our attorney, we briefed a US Attorney and two Assistant US Attorneys, Federal Prosecutors from the Department of Justice. The US Attorney told us he would forward the information to the Office of Public Integrity at the Department of Justice. That US Attorney followed up with us months later, to see if the Office of Public Integrity had contacted us. They never did.
Smartmatic, Dominion, and their media allies will immediately point to the fact that FoxNews settled with Dominion, paying US$787.5 million, and that Newsmax just settled with Smartmatic, this past week in a defamation case as "evidence of Smartmatic and Dominion innocence".
In FoxNews' case against Dominion, we briefed Fox News trial attorneys. Our lawyers were present when we did that. FoxNews corporate officers refused to be briefed directly for that case. They wanted plausible deniability.
FoxNews corporate knew we had significant evidence – and, more importantly, witnesses. When all the facts are known, Fox News executives and Board will have to explain why they went down on their knees for enemies of the US.
We briefed Newsmax's corporate attorney, as well. Though their settlement with Smartmatic is not public, any settlement with either company and their masters, the Cartel de los Soles, the Cuban DGI, and CCP, makes it more difficult for those of us trying to defend the country and our democracy.
I ask everyone to go to the website StolenElectionsFacts.com. Here, you will find articles and original source documents supporting the claim that Smartmatic and Dominion are employing a source code created and owned by the Venezuelan Regime, with hardware manufactured in China that alters election results.
I will follow with other videos and statements to inform and educate others.
Best-selling author, Ralph Pazullo has written the book, 'Stolen Elections, the Plot to Destroy Democracy'. It will be released in late October. Mr Pazullo interviewed my whistleblower associate and I and several of our key witnesses. This is a must-read, to understand one of the greatest crimes ever committed against the United States.
This is an assault on our democracy.
Again, go to the website StolenElectionsFacts.com. Look at the timeline, the documents, and the original sources that are attached. Thank you for your time.
God bless America. We go forward.
Running Time: 16 mins
—> WATCH ‘SPLINTERING BABYLON’ FREE, NOW!
ForbiddenNews Substack is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
Upgrade to paid
You’re currently a free subscriber to the Forbidden.News Substack. For the full experience, upgrade your subscription.
Upgrade to paidLikeCommentRestack
0 notes