#Disable XML-RPC
Explore tagged Tumblr posts
Text
How to Secure Your WordPress Login Page from Hackers
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#cyber-security#cybersecurity#cybersecurity best practices#disable xml-rpc#firewall for wordpress#malware protection#protect wordpress website#secure wordpress hosting#secure wordpress login#secure wp-config file#security#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#web development#Website Builders#Wordpress#wordpress brute force protection#wordpress hosting security#wordpress password security#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes
Text
Enhance your WordPress website's security by disabling XML-RPC. Learn to secure your website with this step-by-step guide.
#disable xmlrpc in wordpress#wordpress xmlrpc disable#disable xml-rpc-api#disable xmlrpc#how to disable xml-rpc in wordpress
0 notes
Text
WP Hide and Security Enhancer PRO v7.1.7 WordPress Plugin
https://themesfores.com/product/wp-hide-and-security-enhancer-pro-plugin/ WP Hide and Security Enhancer PRO v7.1.7 Hide and increase Security for your WordPress website instance using smart techniques. No files are changed on your server. The plugin not only allows you to change the default URLs of your WordPress, but it hides/blocks defaults! All other similar plugins just change the slugs, but the defaults are still accessible, obviously revealing WordPress. WP Hide and Security Enhancer PRO Features: Custom Admin Url Block default admin Url Block any direct folder access to completely hide the structure Custom wp-login.php filename Block default wp-login.php Block default wp-signup.php Block XML-RPC API New XML-RPC path Adjustable theme URL New child Theme URL Change theme style filename Clean any headers for the theme style file Custom wp-include Block default wp-includes paths Block defalt wp-content Custom plugins URLs Individual plugin URL change Block default plugins paths New upload URL Block default upload URLs Remove WordPress version Meta Generator block Disable the emoji and required javascript code Remove pingback tag Remove we manifest Meta Remove rsd_link Meta Remove wpemoji Minify Html, css, JavaScript https://themesfores.com/product/wp-hide-and-security-enhancer-pro-plugin/ #SecurityPlugin #WordpressPlugins
0 notes
Text
How to Check If Your Website or Plugins Are Using XML-RPC

How to Check If Your Website or Plugins Are Using XML-RPC | https://tinyurl.com/2cmcveav | #Blogging #security #Wordpress #XMLRPC If you’re managing a WordPress site and want to know whether xmlrpc.php is being actively used by your site or plugins, you’ll need to perform some advanced steps. Disabling xmlrpc.php can improve security, but it’s essential to ensure that this won’t break any functionality. Here’s how you can determine if XML-RPC is in use on your site. Monitoring Server Logs for XML-RPC Requests One of the most direct ways to check if your site is using xmlrpc.php is by monitoring your server’s access logs. Steps to Monitor Server Logs What to Look For Using Plugins to Log XML-RPC Requests WordPress […] Read more... https://tinyurl.com/2cmcveav
0 notes
Text
How to Add Security through WordPress
WordPress itself provides several built-in security features, and you can further enhance security by utilizing various plugins and best wordpress hosting india. Here's how you can add security to your WordPress site:
Step 1: Update WordPress Core, Themes, and Plugins: - Keep your WordPress installation, themes, and plugins up to date to patch any known security vulnerabilities. Step 2: Use Secure Hosting: - Choose a reputable hosting provider that offers security features like firewalls, malware scanning, and regular backups. Step 3: Strong Admin Passwords: - Use strong, unique passwords for your WordPress admin accounts and encourage all users to do the same. Step 4: Limit Login Attempts: Install a plugin to limit the number of login attempts from a single IP address to protect against brute force attacks. Step 5: Two-Factor Authentication (2FA): - Implement 2FA for WordPress logins using plugins like Google Authenticator or Duo Two-Factor Authentication. Step 6: Secure wp-config.php: - Protect your wp-config.php file by moving it to a higher-level directory or adding code to your .htaccess file to restrict access. Step 7: Disable Directory Listing: - Prevent directory listing by adding Options -Indexes to your .htaccess file to hide directory contents. Step 8: Disable XML-RPC: - If you're not using XML-RPC functionality, disable it to prevent potential exploitation by attackers.

Step 9: Limit File Permissions: - Set appropriate file permissions for your WordPress files and directories to restrict unauthorized access. Step 10: WordPress Security Headers: - Implement security headers like Content Security Policy (CSP), X-Frame-Options, X-XSS-Protection, and others to enhance browser security. Step 11: WordPress Security Plugins: - Install reputable security plugins like Word fence, Sucuri Security, or themes Security to monitor and protect your site from various threats. Step 12: Regular Backups: - Set up regular backups of your WordPress site, including files and the database, and store them securely offsite. Step 13: WordPress Salts and Keys: - Update your WordPress salts and keys regularly to enhance encryption and protect against brute force attacks. Step 14: Disable File Editing: - Prevent file editing within the WordPress dashboard by adding define ('DISALLOW_FILE_EDIT', true); to your wp-config.php file. Step 15: Security Headers: - Add security headers to your site's HTTP responses to protect against various types of attacks. You can do this manually or by using a security plugin. Step 16: Monitor File Changes: - Install a plugin or set up alerts to monitor and notify you of any unauthorized changes to your WordPress files and cheap wordpress hosting india. Note: By implementing these security measures, you can significantly improve the security of your WordPress site and protect it from various threats. Additionally, staying informed about security best practices and regularly auditing your site's security can help you stay one step ahead of potential attackers.
0 notes
Link
0 notes
Text
Essential WordPress Security Tips to Protect Your Website
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack prevention#disable xml-rpc#firewall for wordpress#limit login attempts#malware protection#protect wordpress website#secure wordpress hosting#secure wp-config file#SSL encryption#two-factor authentication#wordpress backup plugins#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes
Text
How to disable XML-RPC in WordPress
How to disable XML-RPC in WordPress
In WordPress, XML-RPC has disabled by default for the longest period. This has disabled due to security issues. However, XML-RPC disables by default will change in WordPress 3.5. Hence, currently, XML-RPC will enable by default with a facility of the turnoff from the WordPress dashboard. So, this article explained to you how to disable XML-RPC in WordPress.
What is XML-RPC?
XML-RPC can explain…
View On WordPress
#Disable XML-RPC#disable XML-RPC with .htaccess#disable XML-RPC WordPress 3.5#XML RPC#XML-RPC WordPress
0 notes
Text
To disable automatic updates for the WordPress core, themes and plugins, you can follow these steps: Disable Automatic Updates for the WordPress Core: By default, WordPress automatically updates itself for minor releases (e.g., from 5.7 to 5.7.1). To disable this feature and prevent automatic updates for the core, you can add the following line of code to your wp-config.php file: phpCopy code define( 'WP_AUTO_UPDATE_CORE', false ); Place this code snippet just above the line that says "/* That's all, stop editing! Happy publishing. */". This will disable automatic updates for the WordPress core. Disable Automatic Updates for Themes and Plugins: To disable automatic updates for themes and plugins, you can utilize a plugin or add some code to your theme's functions.php file. Here's how: Option 1: Using a Plugin (Easy method): Install and activate the "Easy Updates Manager" plugin from the WordPress.org plugin repository. Go to the "Dashboard" menu in your WordPress admin area and click on "Updates Options." From there, you can configure the settings to disable automatic updates for themes and plugins. Option 2: Adding Code to Your Theme's functions.php file: Access your WordPress files using an FTP client or a file manager provided by your hosting provider. Navigate to the folder containing your currently active theme, usually located in wp-content/themes/. Locate the functions.php file for your active theme and edit it. Add the following code snippet at the end of the file: phpCopy code add_filter( 'auto_update_plugin', '__return_false' ); add_filter( 'auto_update_theme', '__return_false' ); This code will disable automatic updates for both plugins and themes. Remember to save the changes you made to the wp-config.php file or the functions.php file. With these modifications, your WordPress installation will no longer automatically update the core, themes, or plugins. Keep in mind that manually updating these components is crucial for maintaining security and stability, so be sure to regularly update them yourself. You might also like: XML-RPC Support in WordPress, Should I Disable XML-RPC in Wordpress Increase Maximum upload file size in Wordpress
0 notes
Text
WordPress Premium Plugin: Perfmatters Plugin v2.0.2 Free Download About Perfmatters Plugin v2.0.2 Perfmatters Plugin Free Download – Perfmatters is a very lightweight WordPress performance plugin. The main focus of this plugin is to reduce your page size and number of HTTP requests. It allows you to disable many unneeded features like emojis, XML-RPC, RSD Link, Shortlinks, RSS Feeds, and many o... https://bit.ly/3YL6PIr
#Plugins#perfmatters#perfmattersalternative#perfmattersbabiato#perfmatterscdn#perfmatterschangelog#perfmattersgpl#perfmattersnulled#perfmattersnulledfree#perfmattersplugin#perfmatterspluginchangelog#perfmattersplugindocumentation#perfmattersplugindownload#perfmatterspluginfreedownload#perfmatterspluginlatestversion#perfmatterspluginnulled#perfmatterspluginreviews#perfmattersreview#perfmattersscriptmanager#perfmatterssettings#perfmatterstutorial#perfmatterswordpress#perfmatterswordpressplugin#testwordpressperformance#wordpressperformanceplugin#wordpresspluginperformancetester#wordpresspluginspeedtest#wordpressspeedplugin#wpperfmatters
0 notes
Video
youtube
How To Disable WordPress XML RPC To Enhance Your Site Security? Easy Method Tutorial 🔒 https://www.youtube.com/watch?v=5ABRHVYVc5E 🛟🎯🎬 #Security #Disable #WordPress #XMLRPC
0 notes
Text
nmap cheat sheet PC L6W7?
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥 nmap Cheat Sheet. Built by Yuval (tisf) Nativ from See-Security's Hacking Defined Experts program. This nmap cheat sheet is uniting a few other cheat sheets. Nmap (network mapper), the god of port scanners used for network discovery and the basis for most security enumeration during the initial stages. Nmap is a free open source tool, employed to discover hosts and services on a computer network by sending packets and analyzing the. Common uses for Nmap include vulnerability discovery, system security auditing, and detecting cyber You can download a PDF version of Nmap Cheat Sheet. 9 Many network and system administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring server or service availability. Nmap uses raw IP packets in a novel way to determine the hosts available on the network, the services they offer application name and version , and the operating systems they are running and operating systems. Scan a single target. Scan multiple targets. Scan a list of targets. Scan a range of hosts. Scan an entire subnet. Scan random hosts. Excluding targets from a scan. Excluding targets using a list. Perform an aggressive scan. Scan an IPv6 target. Fragment packets. Specify a specific MTU. Use a decoy. Writing code in comment? Please use ide. Skip to content. Change Language. Related Articles. View Discussion. Improve Article. Save Article. Like Article. Last Updated : 05 Oct, Read Discuss. Previous Ethical Hacking Cheatsheet. Recommended Articles. Article Contributed By :. Easy Normal Medium Hard Expert. Load Comments. Please Login to comment What's New. We use cookies to ensure you have the best browsing experience on our website. Start Your Coding Journey Now! Login Register. Perform a ping scan only. ICMP Timestamp ping. ICMP address mask ping. Force reverse DNS resolution. Disable reverse DNS resolution. Alternative DNS lookup. Manually specify DNS servers. Create a host list. Idle zombie scan. Manually specify a source port. Append random data. Randomize target scan order. Spoof MAC Address. Send bad checksums. Operating system detection. Attempt to guess an unknown. Service version detection. Troubleshooting version scans. Perform a RPC scan. Save output to a text file. Save output to a xml file. Grepable output. Output all supported file types. Periodically display statistics. Execute individual scripts. Execute multiple scripts. Execute scripts by category. Execute multiple scripts categories. Troubleshoot scripts. Update the script database.
1 note
·
View note
Text
Experimenting with Cloudflare XML-RPC protections
Experimenting with Cloudflare XML-RPC protections
Looking for a way to further protect XML-RPC without letting it flap in the wind or fully disabling it. Up to now, everything that I’ve found online has been “suck it up” or “completely block it”. Got into Cloudflare this morning and fully blocked XML-RPC then tried to access my site using the WordPress app. Snagged some helpful data in the Cloudflare firewall logs then created a quick and dirty…
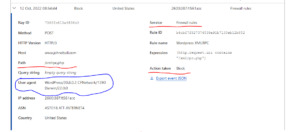
View On WordPress
0 notes
Text
The ultimate WordPress security guide 2020
The ultimate WordPress security guide 2020
WordPress security is a very important area for all WordPress website owners. More than 10,000 WordPress websites have become victims of hackers and malware per day around the globe. Hence website owners must give first priority to enhance the security in their WordPress websites.
This article will aid to website owners to equip their website with advance WordPress security tips. As a website…
View On WordPress
#Change WordPress Database Prefix#Cloudflare#Disable directory indexing and browsing#disable file edit#Disable PHP file execution#Disable XML-RPC#Enable web application Firewall#Limit login attempts#SSL#Sucuri firewall#two-factor authentication#use strong password#WAF#Website security#WordPress hosting#wordpress security#WordPress security plugin#WordPress update
0 notes
Text
WordPress has built-in support for XML-RPC, allowing you to interact with your WordPress site remotely using XML-RPC requests. XML-RPC support in WordPress enables you to perform various actions such as publishing posts, managing comments, updating settings, and more, using XML-RPC client applications or libraries. [tie_index]Verify XML-RPC support in WordPress[/tie_index] [padding top="0" bottom="0" right="5%" left="5%"] Verify or enable XML-RPC support in WordPress By default, XML-RPC support is enabled in WordPress installations. However, if you need to verify or enable XML-RPC support, you can follow these steps: Log in to your WordPress admin dashboard. Navigate to the "Settings" menu and click on "Writing." Scroll down to the "Remote Publishing" section. Ensure that the "XML-RPC" checkbox is checked. If it is not checked, click on it to enable XML-RPC support. Click the "Save Changes" button to apply the settings. [tie_index]What can I do with XML-RPC Support[/tie_index] [padding top="0" bottom="0" right="5%" left="5%"] What can I do with XML-RPC Support Once XML-RPC support is enabled, you can use XML-RPC client applications or libraries to interact with your WordPress site. These clients can make XML-RPC requests to perform various actions. For example: Publishing a post: You can use an XML-RPC client to send a request to the wp.newPost method, which allows you to create and publish a new post on your WordPress site. Managing comments: The wp.getComments method enables you to retrieve comments from your site, while wp.newComment allows you to post new comments. Updating settings: With XML-RPC, you can modify various WordPress settings using methods like wp.getOptions and wp.setOptions. It's important to note that XML-RPC has some security implications, as it allows remote access to your WordPress site. To ensure the security of your site, you should always use strong passwords, keep your WordPress installation up to date, and consider using plugins or server configurations that add additional security layers to XML-RPC functionality. In recent years, the popularity of the WordPress REST API has increased, and it provides a more modern and flexible way to interact with WordPress sites. It's recommended to explore the REST API if you're looking for more advanced and flexible remote communication with your WordPress site. [tie_index]Should I disable XML-RPC in WordPress[/tie_index] [padding top="0" bottom="0" right="5%" left="5%"] Should I disable XML-RPC in WordPress? The decision to disable XML-RPC in WordPress depends on your specific needs and security considerations. Here are some factors to consider when deciding whether to disable XML-RPC: Security: XML-RPC has been a target for certain types of attacks in the past. By disabling XML-RPC, you reduce the potential attack surface and mitigate the risk of specific XML-RPC-related vulnerabilities. If you don't use XML-RPC or have alternative means of remote communication, disabling it can be a security precaution. Functionality: XML-RPC is used by some plugins, themes, and third-party applications to interact with your WordPress site. Disabling XML-RPC may break compatibility with these tools and limit certain functionality. If you rely on XML-RPC for specific purposes, disabling it may not be feasible. Legacy support: Older or less frequently updated applications may still rely on XML-RPC for remote communication. If you need to maintain compatibility with such applications, disabling XML-RPC might not be ideal. Alternative APIs: WordPress now has the REST API, which provides a more modern and flexible way to interact with your site. If you have migrated to using the REST API or plan to do so, disabling XML-RPC may not have a significant impact on your workflow. [tie_index]How to disable XML-RPC in WordPress[/tie_index] [padding top="0" bottom="0" right="5%" left="5%"]
How to disable XML-RPC in WordPress: If you decide to disable XML-RPC in WordPress, you can do so by using one of the following methods: Plugins: Several WordPress security plugins offer options to disable XML-RPC. Look for reputable security plugins and check their features to see if XML-RPC disabling is included. We advise you to use Disable XML-RPC-API plugin. The plugin works out of the box and will immediately deactivate XML-RPC. navigate to XML-RPC Security » XML-RPC Settings to configure the plugin. For example, you can allow certain users to access XML-RPC by whitelisting their IP addresses. Code snippets (Recommended): To disable XML-RPC in WordPress using a code snippet, you can add the following code to your theme's functions.php file or create a custom plugin: phpCopy code // Disable XML-RPC add_filter('xmlrpc_enabled', '__return_false'); This code uses the xmlrpc_enabled filter to return false, effectively disabling XML-RPC functionality in WordPress. .htaccess rules (Advanced): To disable XML-RPC in WordPress using .htaccess rules, you can add the following code to your .htaccess file in the root directory of your WordPress installation: apacheconfCopy code # Disable XML-RPC Order Deny,Allow Deny from all Always keep your WordPress installation and plugins up to date, use strong passwords, and follow other security best practices to ensure the overall security of your website.
0 notes