#Educational Requirements for Software Developers
Explore tagged Tumblr posts
Text
here’s my pro tip
everyone keeps pushing computer science without recognizing that the field is quickly becoming oversaturated. If you love CS, than sure, do that. But if you’re looking for a really marketable degree that will let you do CS but also leave the door open for other stem careers, then I highly recommend computer engineering or electrical engineering with a CS minor (optional - have an ee degree without a minor and I still work in software). You can still get a software job if you want, with the added bonus that a lot of CS people will think you’re a wizard for having a working knowledge of hardware. And as software jobs get harder to find and get, you can diversify and apply for hardware jobs. And the hardware jobs will be easier to get if you know how to code. Also, circuits are really fucking cool guys.
#Engineering#computer science#software development#electrical and computer engineering#stem education#jobs#employment#tech#for those who don’t know#computer engineering is a combination of electrical engineering and computer science degrees#So much so that at my school you aren’t even allowed to get a cs minor if you have ce major because they already overlap so much#That the cs minor is redundant#If you take a circuits class and hate it try ce instead of ee#ce usually requires less circuits#if you love circuits and the physics side do ee#But ce and ee will both let you work in both software and hardware even though ee is focused on hardware#And having both software and hardware skills is highly sought after#I got my software job because I was an electrical engineer#they specifically wanted someone to do software-hardware integration and that is a less common skill set
6 notes
·
View notes
Text
IETM for Beginners A Quick Guide to IETM Code and Pixels

IETM: Interactive Electronic Technical Manual
Training Aids to Defence Client
If you are a supplier of defence then along with the system/equipment you also need to provide Training Aids
(CBT) — Computer-Based Training
Charts and Bloups
Video Film
Training Work Modules
Manuals Hard Copies
IETM
Evolution of Documentation in Defence
Before — Hardcopies and PDFs in DVDs (Upto 2015)
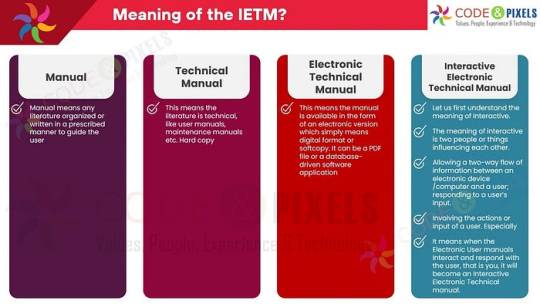
What is the meaning of the IETM?
Manual: Manual means any literature organized or written in a prescribed manner to guide the user.
TechnicalManual: This means the literature is technical, like user manuals, maintenance manuals etc. Hard copy
Electronic Technical Manual: This means the manual is available in the form of an electronic version which simply means digital format or softcopy. It can be a PDF file or a database-driven software application.
Interactive Electronic Technical Manual:
Let us first understand the meaning of Interactive. The meaning of interactive is two people or things influencing each other.
Allowing a two-way flow of information between an electronic device /computer and a user; responding to a user’s input.
Involving the actions or input of a user. Especially
It means when the Electronic User manuals Interact and respond with the user, that is you, it will become an Interactive Electronic Technical manual.
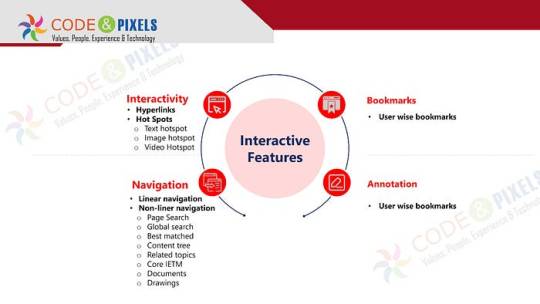
Interactive Features
Interactivity
Hyperlinks
Hot Spots
Text hotspot
Image hotspot
VideHotspot
Bookmarks
User wise bookmarks
Navigation
Linear navigation
Non-liner navigation
Page Search
Global search
Best matched
Content tree
Related topics
Core IETM
Documents
Drawings
Annotation
User wise bookmarks
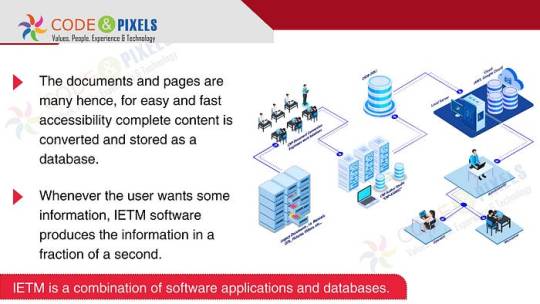
The documents and pages are many hence, for easy and fast accessibility complete content is converted and stored as a database.
Whenever the user wants some information, IETM software produces the information in a fraction of a second.
Use or Purpose of the IETM?
The purpose of the Manual is to give information related to the equipment to the end user for quick reference.
All the technicality is written in detail so that when an issue arises, the user can refer to the manual, as every time OEM or technical person or subject matter expert might not be available on the spot to resolve the issue.
If the manual has 10 pages users can refer easily.
But any system used by the defence will have multiple manuals and thousands of page counts and many times a user has to cross-refer between manuals, intra-manual and inter-manual to resolve the issue.
Referring to 10- 15 hard-copy or even soft-copy books simultaneously will be difficult and time-consuming.

How to access the IETM ?
IETM is a web-based application like our bank software or any other web application. The graphic user interface will be provided to use IETM through which users can interact and get the desired data.
Like all other standard software, Unauthorized users cannot access the IETM. IETM is a Login - login-based application. Only users having valid Login credentials can access the software.
Based on the user log credentials data will be provided to the user.
IETM has 2 types of Users and one Administrator
Maintainer
Operator
If the operator logs in, the user gets all the content related to operator use, similarly if the maintainer logs in only maintenance-related content is visible for that user.
Ideally, all the content is available for both users, because the purpose of the IETM is to refer to the manual to fix the issue.
Administrators can create users who can see the user’s navigation and log-in history and interact with the users using user dashboards through Annotations.
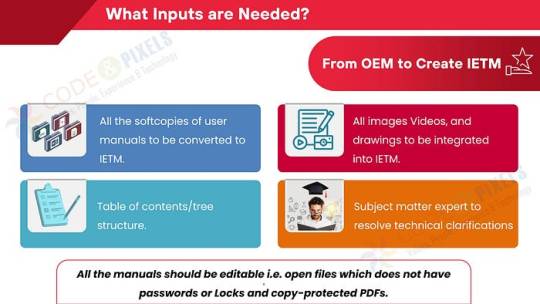
What Inputs are Needed? (From OEM to Create IETM)
All the softcopies of user manuals to be converted to IETM.
All images Videos, and drawings to be integrated into IETM.
Subject matter expert to resolve technical clarifications
Table of contents/tree structure.
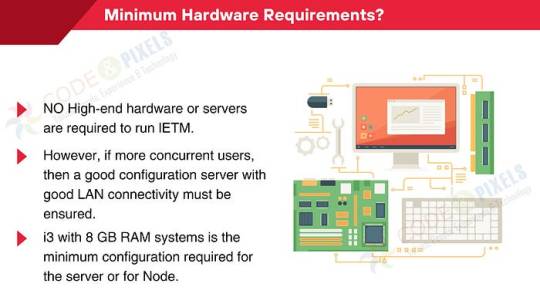
Minimum Hardware Requirements?
NO High-end hardware or servers are required to run IETM.
However, if more concurrent users, then a good configuration server with good LAN connectivity must be ensured.
i3 with 8 GB RAM systems is the minimum configuration required for the server or for Node.
Deliverables
BASED DB (Manuals are covered in the Database)
IETM VIEWER Software
User Manual and Installation Manual
Standards — compliance

Costing of IETM: (Interactive Electronic Technical Manual)
Level of IETM, is it Level 3 or Level 4
Cost will be based on the number of pages that are to be converted
The vendor calculates the cost per page. And a fixed cost of IETM viewer software
If you want to create IETM by yourself self then you also need to buy IETM authoring software.
What are these Levels?
Level — 1 is any PDF file
Level — 2 is a PDF file with hyperlinks from the table of contents to the body etc.
Level — 3 is an HTML application. More hyperlinks, simple search, a content tree having log a screen with a hardcoded username and password and supplied in the format of EXE so that Windows can easily open
Level — 4 is Software plus Content/manuals converted as Database

Regarding Level — 5, rest assured, till 2028 it will be Level — 4 only. As of now, there is nothing practically called Level — 5. Few are calling virtual reality and Augmented reality and Artificial intelligence Level — 5.
Pulling data from many user inputs and analyzing and giving results are done in Level — 5. IETM software cannot pull the data from various real-time points as No OEM will give the real-time information to third-party software directly. Yes, if the information is available offline, then that information can be imported into IETM and can be used as a reference.

#ietm#software#technology#ietm developement#ietm code and pixels ietm hyderabad#ietm software#elearning#code and pixels#ietm level iv#codeandpixels#ietm level 4 software requirements#technical documentation#ietm document#ietm documentation#interactive electronic technical manual#Ietm Service Providers#Ietm Software Designers of India#Software Development Company#Elearning Solutions Company#E Learning Content Development Company#Online Education#Digital Education#Digital Content#Software Development Solutions#Elearning#Ietm Developers#Econtent Development#Elearning Solutions Providers#Econtent Developers#Econtent
3 notes
·
View notes
Text
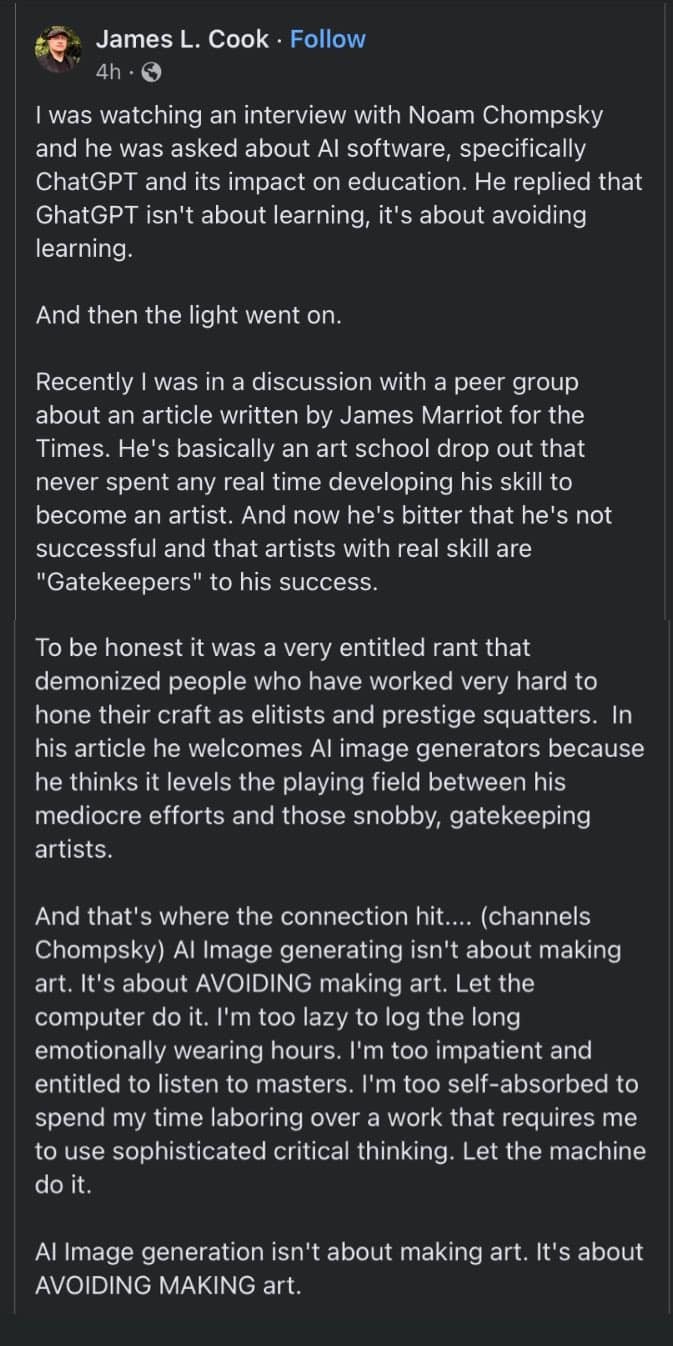
Image description from the notes by @summery-captain:
"A post by James L. Cook, reading: "I was watching an interview with Noam Chompsky and he was asked about AI software, specifically Chat GPT and its impact on education. He replied that Chat GPT isn't about learning, it's about avoiding learning.
And then the light went on.
Recently I was in discussion with a peer group about an article written by James Marriot for the Times. He's basically an art school drop out that never spent any real time developing his skill to become an artist. And now he's bitter that he's not successful and that artists with real skill are 'gatekeepers' to his success.
To be honest it was a very entitled rant that demonized people who have worked very hard to hone their craft as elitists and prestige squatters. In his article he welcomes AI generators because he thinks it levels the playing field between his mediocre efforts and those snobby, gatekeeping artists.
And that's where the connection hit... (channels Chompsky) AI image generating isn't about making art. It is about AVOIDING making art. Let the computer do it. I'm too lazy to log the long emotionally wearing hours. I'm too impatient to listen to masters. I'm too self-absorbed to spend my time laboring over a work that requires me to use sophisticated critical thinking. Let the machine do it.
AI imagine generation isn't about making art. It's about AVOIDING MAKING art." End of imagine description
59K notes
·
View notes
Text
There is an incredibly talented developer I’ve worked with for the last few years who is an absolute font of technical knowledge. They know just about every coding language and pick up literally anything software-related at the drop of a hat. This individual is indispensable to their team. To replace them, their expertise, and their work ethic, would require hiring at least three people.
And today, this developer turned in their resignation notice. Not because they’re unhappy with their job, or pay, or coworkers. They love their job!
But because they no longer feel safe in the US. Because they’re trans.
Already, they can no longer receive medically necessary treatment in their home state and they fear that moving to a different state would merely prolong the inevitable. So they found a new job in a different country that has accepted them and all their skills with delighted, open arms, and the promise that they will be able to continue their life without fear.
And listen, a person should not have to display indispensable talents for us to care that they are being forced out of their home country. A person’s usefulness is not the most important thing about them. But in this case, we are actively losing a highly educated, intelligent, and genuinely good person from our workforce because people with shit for brains needed a villain and they decided trans folks were the ideal target.
No point to this. Just anger.
As you were.
565 notes
·
View notes
Text

At my last job, we sold lots of hobbyist electronics stuff, including microcontrollers.
This turned out to be a little more complicated than selling, like, light bulbs. Oh how I yearned for the simplicity of a product you could plug in and have work.
Background: A microcontroller is the smallest useful computer. An ATtiny10 has a kilobyte of program memory. If you buy a thousand at a time, they cost 44 cents each.

As you'd imagine, the smallest computer has not great specs. The RAM is 32 bytes. Not gigabytes, not megabytes, not kilobytes. Individual bytes. Microcontrollers have the absolute minimum amount of hardware needed to accomplish their task, and nothing more.
This includes programming the thing. Any given MCU is programmed once, at the start of its life, and then spends the next 30 years blinking an LED on a refrigerator. Since they aren’t meant to be reflashed in the field, and modern PCs no longer expose the fast, bit-bangable ports hobbyists once used, MCUs usually need a third-party programming tool.
But you could just use that tool to install a bootloader, which then listens for a magic number on the serial bus. Then you can reprogram the chip as many times as you want without the expensive programming hardware.
There is an immediate bifurcation here. Only hobbyists will use the bootloader version. With 1024 bytes of program memory, there is, even more than usual, nothing to spare.

Consumer electronics development is a funny gig. It, more than many other businesses, requires you to be good at everything. A startup making the next Furby requires a rare omniexpertise. Your company has to write software, design hardware, create a production plan, craft a marketing scheme, and still do the boring logistics tasks of putting products in boxes and mailing them out. If you want to turn a profit, you do this the absolute minimum number of people. Ideally, one.
Proving out a brand new product requires cutting corners. You make the prototype using off the shelf hobbyist electronics. You make the next ten units with the same stuff, because there's no point in rewriting the entire codebase just for low rate initial production. You use the legacy code for the next thousand units because you're desperately busy putting out a hundred fires and hiring dozens of people to handle the tsunami of new customers. For the next ten thousand customers...

Rather by accident, my former employer found itself fulfilling the needs of the missing middle. We were an official distributor of PICAXE chips for North America. Our target market was schools, but as a sideline, we sold individual PICAXE chips, which were literally PIC chips flashed with a bootloader and a BASIC interpreter at a 200% markup. As a gag, we offered volume discounts on the chips up to a thousand units. Shortly after, we found ourselves filling multi-thousand unit orders.
We had blundered into a market niche too stupid for anyone else to fill. Our customers were tiny companies who sold prototypes hacked together from dev boards. And every time I cashed a ten thousand dollar check from these guys, I was consumed with guilt. We were selling to willing buyers at the current fair market price, but they shouldn't have been buying these products at all! Since they were using bootloaders, they had to hand program each chip individually, all while PIC would sell you programmed chips at the volume we were selling them for just ten cents extra per unit! We shouldn't have been involved at all!
But they were stuck. Translating a program from the soft and cuddly memory-managed education-oriented languages to the hardcore embedded byte counting low level languages was a rather esoteric skill. If everyone in-house is just barely keeping their heads above water responding to customer emails, and there's no budget to spend $50,000 on a consultant to rewrite your program, what do you do? Well, you keep buying hobbyist chips, that's what you do.
And I talked to these guys. All the time! They were real, functional, profitable businesses, who were giving thousands of dollars to us for no real reason. And the worst thing. The worst thing was... they didn't really care? Once every few months they would talk to their chip guy, who would make vague noises about "bootloaders" and "programming services", while they were busy solving actual problems. (How to more accurately detect deer using a trail camera with 44 cents of onboard compute) What I considered the scandal of the century was barely even perceived by my customers.
In the end my employer was killed by the pandemic, and my customers seamlessly switched to buying overpriced chips straight from the source. The end! No moral.
360 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Text
Pick a Card: Career Guidance




Top Left to Right--> Pile 1, Pile 2
Bottom Left to Right--> Pile 3. Pile 4
If You Liked This Reading Sign up to TheObsidianPages777 Newsletter
+Free E-Guides on New Moon Manifestation and Gem Stone for Life Path
================================================================================================
Pile 1
Current Situation: The Chariot
You are determined and focused on your career goals, moving forward with purpose and direction. There's a sense of control and determination driving your actions.
Challenges: Five of Wands
You may be facing competition or conflict in your workplace. There could be differing opinions and struggles that make it hard to progress smoothly.
Advice: Strength
Rely on your inner strength and patience to navigate through challenges. Maintain self-control and approach conflicts with compassion and understanding. Your resilience will lead you to success.
Ideal Careers:
Leadership Roles: Positions such as a manager, director, or CEO, where determination and leadership are crucial.
Entrepreneur: Running your own business where you can harness your drive and overcome competition.
Project Management: Roles that require strong organizational skills and the ability to navigate conflicts and challenges.
Military or Law Enforcement: Careers that require discipline, determination, and the ability to handle conflict and stress.
Athletics or Coaching: Where physical and mental strength, as well as resilience, are important.
================================================================================================
Pile 2
Current Situation: The Hierophant
Your career path is currently influenced by traditional structures and conventional methods. You may be working within an established system or organization.
Challenges: Seven of Cups
There may be confusion or too many options available, making it difficult to choose the right path. Avoid getting lost in illusions or wishful thinking.
Advice: The Hermit
Take time for introspection and seek inner guidance. Reflect on your true goals and values before making decisions. Solitude and self-reflection will provide clarity.
Ideal Careers:
Education: Teacher, professor, or academic advisor, where traditional knowledge and guidance are valued.
Religious or Spiritual Leader: Priest, minister, or spiritual counselor, providing guidance within established belief systems.
Legal Profession: Lawyer, judge, or paralegal, working within the structures of the legal system.
Research and Academia: Careers that involve deep study and reflection, such as a researcher or academic.
Counseling or Therapy: Roles that require introspection and helping others find clarity, such as a therapist or counselor.
================================================================================================
Pile 3
Current Situation: Ace of Pentacles
A new opportunity or beginning in your career is emerging. This could be a job offer, a new project, or a chance to start something new with strong potential for growth.
Challenges: The Devil
Be wary of falling into negative patterns or becoming too attached to material success. Avoid temptations that could lead to unethical behavior or burnout.
Advice: Page of Swords
Approach new opportunities with curiosity and a willingness to learn. Stay vigilant and gather information before making decisions. Be clear and honest in your communication.
Ideal Careers:
Finance: Banker, financial advisor, or investment analyst, where new opportunities for growth are abundant.
Real Estate: Real estate agent or property manager, involving new ventures and potential for substantial growth.
Technology: IT specialist, software developer, or tech entrepreneur, where continuous learning and vigilance are key.
Journalism: Reporter, editor, or content creator, focusing on gathering and disseminating information.
Consulting: Business consultant or analyst, providing strategic advice and insights to businesses.
================================================================================================
Pile 4
Current Situation: Three of Cups
Collaboration and teamwork are currently significant in your career. You may be part of a supportive group or network, enjoying camaraderie and shared goals.
Challenges: Four of Pentacles
There could be a tendency to hold on too tightly to security or resources, leading to stagnation. Fear of change or loss may be preventing growth.
Advice: The Star
Stay hopeful and keep a positive outlook. Trust in the universe and your vision for the future. This is a time for healing, inspiration, and aligning with your true purpose.
Ideal Careers:
Event Planning: Event coordinator or wedding planner, where collaboration and teamwork are essential.
Human Resources: HR manager or recruiter, fostering a positive and collaborative workplace environment.
Creative Arts: Artist, musician, or performer, involving collaboration and shared creative goals.
Non-Profit or Community Work: Community organizer, social worker, or NGO worker, focusing on collective well-being and humanitarian goals.
Healthcare: Nurse, doctor, or therapist, providing care and support with a focus on healing and hope.
If You Liked This Reading Sign up to TheObsidianPages777 Newsletter
+Free E-Guides on New Moon Manifestation and Gem Stone for Life Path
#pick a card#pick a pile#pick a photo#pick one#tarot community#tarot reading#tarot#tarot cards#tarotblr#pick a picture#pick a reading
317 notes
·
View notes
Text
A Programming Hook
Object-Oriented Programming's strength is Modularity; and just about everything coded today follows the OOP design. Except Python and JavaScript--sometimes.
So I've coined a term "Hook"; not to be confused with a fishing-line-hook, or the literary tool where you write the most interesting part of your whole story into the first sentence.
A [Hook] in this regard is a [Space for Something]{to go} like a nook or a closet. You don't know *what* might go into that nook or closet; you just know there are *things* with which are properly displayed or stored in a Nook or in a Closet.
And this is the same concept.
There's a *whole* lot of features that we'd might *wish* to add to a coding project, yet time and funding constraints, oftentimes, makes it hard to include every feature one might want.
In this vein; we add space for the features we might want to add *after* we finish all the important bits.
This is very important in [Software Engineering], because there will be a time in a project where you make it to an important feature that you cannot implement *without* having had re-written the *whole* thing.
And so, you want options available when that inevitably comes to pass.
Now. I developed this whole making [Training Simulations] in the [Air Force] and when I tell you; one day somebody asked me to do something that may have added several weeks to the development time.
They asked "How long will this take to [fix]?" To which I responded; "I'm not sure. I think I remember adding some hooks that would make this easy, and it could be done tonight. But as it wasn't a requirement *at the time* this may take 2-4 weeks to implement if I have to rework it from scratch."
To which, they were very upset with my best time "4 hours, or the end of shift, whichever comes first" or "several weeks, because that would put us behind schedule."
"I'll get back to you at the end of day Chief!"
Non-developers, Maintenance Professionals like myself *actually* who're used to every little thing being documented and not *created on the fly* were rather upset with those timelines.
And I had already been reprimanded several times based on my timeline predictions.
Which uh. Were accurate. They just weren't particularly accurate *for me* whom'st {is/was} a very well educated developer... In a sea of maintainers who have not studied the code as I have done.
My timelines were usually off at this stage *because* I was getting my understanding of how the coders (who were also rather green) and the (maintainers become coders) would be able to understand the timelines.
I have to make clear; I was, in-fact, doing *my* job to the best of my ability, and even better than *your{my supervisor's}* ability despite them being very concerned about my time estimates being [too long].
Communication isn't bad on my side... Even when I appear to be bad at communicating.
One of these days I will not be so defensive! Yet the Anti-Trans sentiment remains, so will the SALT!
Anyway; these particular [Hooks] were contextual triggers. Things that would/should be called at certain times during certain steps in the simulation.
Custom CallBack functions mostly.
And these particular callbacks were rather complex for a simple one-function call event.
Luckily for my OCD brain; I had stopped to asked the question about this exact feature they wanted to add *now* that they had been worried about adding earlier, until the customer made it a [Need to have].
I had asked the question, at that time; "What happens if *this* particular feature *becomes* a Necessary addition."
Because my [awesome predictive abilities] were spot on about what they need that particular simulation to accomplish.
Luckily I had been stumbling through various frameworks and implementations of the Squadrons Honorable Historical Developments. (Part of the job was updating and modernizing old Adobe Flash 2.0 projects) And had stumbled across a few implementations of these features *both* before it was necessary *and* after it seems to have taken a week to tack on at the end.
And that's when I started adding the concept of "Hooks" to my personal development checklist. Everytime you ask yourself; "How might this feature be used outside this implementation" or "What happens if I need to add something *somewhere* that might break Modularity" is an opportunity to add in hooks.
"Can I go back, and reuse this feature to make my job easier in the future?"
Or you know; Object-Oriented Design (And Modularity) in a nutshell.
19 notes
·
View notes
Text
Enter the FujoVerse™

Starting 2024's content creation journey with a bang, it's time to outline the principles behind the FujoVerse™: an ambitious (but realistic) plan to turn the web back into a place of fun, joy, and connection, where people build and nurture their own communities and software. (You can also read the article on my blog)
The Journey
As those who follow my journey with @bobaboard or read my quarterly newsletter (linked in the article) know, the used-to-be-called BobaVerse™ is a collection of projects I've been working on since 2020 while pondering an important question: how do we "fix" the modern social web?

Obviously the joyless landscape that is the web of today is not something a single person can fix. Still, I loved and owed the internet too much to see it wither.
After countless hours of work, I found 3 pillars to work on: community, software ownership and technical education.
Jump in after the cut to learn more about how it all comes together!
Community
Community is where I started from, with good reason! While social networks might trick us into thinking of them as communities, they lack the characteristics that researchers identify as the necessary base for "true community": group identity, shared norms, and mutual concern.
Today, I'm even more convinced community is a fundamental piece of reclaiming the web as a place of joy. It's alienating, disempowering, and incredibly lonely to be surrounded by countless people without feeling true connection with most of them (or worse, feeling real danger).

Software Ownership and Collaboration
As I worked with niche communities "software ownership" also became increasingly important to me: if we cannot expect mainstream tech companies to cater to communities at the margins, it follows that these communities must be able to build and shape their own software themselves.
Plenty of people have already discussed how this challenge goes beyond the tech. Among many, "collaboration" is another sticking point for me: effective collaboration requires trust and psychological safety, both of which are in short supply these days (community helps here too, but it's still hard).

Education (Technical and Beyond)
As I worked more and more with volunteers and other collaborators, however, another important piece of the puzzle showed itself: the dire state of educational material for non-professional web developers. How can people change the web if they cannot learn how to *build* the web?
(And yes, learning HTML and CSS is absolutely important and REAL web development. But to collaborate on modern software you need so much more. Even further, people *yearn* for more, and struggle to find it. They want that power, and we should give it to them.)
Once again, technical aspects aren't the only ones that matter. Any large-scale effort needs many skills that society doesn't equip us with. If we want to change how the web looks, we must teach, teach, TEACH! If you've seen me put so much effort into streaming, this is why :)
And obviously, while I don't go into them in this article, open source software and decentralized protocols are core to "this whole thing".

The Future
All of this said, while I've been working on this for a few years, I've struggled to find the support I need to continue this work. To this end, this year I'm doing something I'm not used to: producing content, gaining visibility, and putting my work in front of the eyes of people that want to fight for the future of the web.
This has been a hard choice: producing content is hard and takes energy and focus away from all I've been doing. Still, I'm committed to doing what it takes, and (luckily) content and teaching go hand in hand. But the more each single person helps, the less I need to push for wide reach.
If you want to help (and read the behind the scenes of all I've been working on before everyone else), you can subscribe to my Patreon or to my self-hosted attempt at an alternative.

I deeply believe that in the long term all that we're building will result in self-sustaining projects that will carry this mission forward. After all, I'm building them together with people who understand the needs of the web in a way that no mainstream company can replicate.
Until we get there, every little bit of help (be it monetary support, boosting posts, pitching us to your friends, or kind words of encouragement and support) truly matters.
In exchange, I look forward to sharing more of the knowledge and insights I've accrued with you all :)

And once again, to read or share this post from the original blog, you can find it here.
#bobaboard#fujoguide#freedom of the web#decentralized protocols#community#social networks#the great content creationing of 2024
88 notes
·
View notes
Text
Blog Post #2 - Week 3 (due 2/6)
Cyberfeminism, Technology, and Digital Inequality
Does cyberfeminism help fight gender and racial inequality online, or does it sometimes reinforce these inequalities?
Cyberfeminism aims to create online spaces for gender equality, but it can also overlook racial differences. Some cyberfeminist ideas assume a white, middle class perspective, leaving out the voices of women of color. Fernandez and Wildling note that much of cyberfeminist writing is targeted toward an “educated, white, upper-middle-class, English-speaking” audience, which can unintentionally exclude others (Daniels, 2009, p. 104). This highlights the need for a more inclusive approach that considers race, class, and access to technology. Additionally, digital activism led by women of color often operates outside mainstream cyberfeminist discourse, reflecting a broader need for intersectionality. While some platforms provide opportunities for marginalized voices, others replicate offline hierarchies, limiting real progress. By expanding cyberfeminism to actively address these exclusion, the movement can become more effective in advocating for digital equity.
Can people truly escape gender and racial identity online, or do digital spaces still reflect real-world inequalities?
Some early cyberfeminists believed that the internet allowed people to leave behind gender and racial identities. However, research shows that digital spaces often reflect real world inequalities. Daniels explains that instead of changing identities online, people “actively seek out online spaces that affirm and solidify social identities along with axes of race, gender, and sexuality” (Daniels, 2009, p. 110). Additionally, many online platforms use algorithms that reinforce existing biases, making marginalized identities more visible and subject to scrutiny. While some individuals may feel a sense of anonymity, structural inequalities persist in the ways people interact, build networks, and gain access to digital resources.
How do cyberfeminist practices differ in the Global North and Global South, and what challenges do women in developing nations face when engaging with digital technologies?
Cyberfeminist practices vary significantly between the Global North and Global South due to differences in economic resources, access to technology, and sociopolitical contexts. In industrialized nations, cyberfeminism often focuses on online activism, digital art, and gender representation in media. In contrast, women in developing nations frequently use digital technology as a tool for survival, resistance, and economic empowerment. Daniels highlights that “while it is true that many affluent women in the global North have ‘depressingly familiar’ practices when it comes to the Internet, this sort of sweeping generalization suggest a lack of awareness about the innovative ways women are using digital technologies to re-engineer their lives” (Daniels, 2009, p. 103). However, barriers such as limited internet access, censorship, and economic inequality continue to restrict their engagement. Addressing these disparities requires cyberfeminist movements to integrate global perspectives and advocate for digital inclusivity on a broader scale.
How do race and technology intersect to perpetuate systemic biases in digital spaces, and what can be done to address these issues?
Nicole Brown discusses how racial biases are embedded in technology, from facial recognition software to algorithmic decision making. These technologies often reinforce systemic inequalities rather than eliminate them. Brown highlights that “facial recognition software has been proven to misidentify Black and Brown individuals at significantly higher rates than white individuals, leading to real world consequences such as wrongful arrests and surveillance” (Brown, 2023). Addressing these issues requires greater accountability in tech development, including diverse representation in AI design, policy changes to regulate biased technologies, and increased advocacy for ethical digital practices. By critically examining the intersection of race and technology, we can work toward creating digital spaces that are equitable for all users.
How does automation in public services contribute to inequality, and what are its impacts on marginalized communities?
Virginia Eubanks argues that automation in public services disproportionately harms low-income and marginalized communities by making access to essential resources more difficult. Automated decision-making systems in welfare programs, housing assistance, and healthcare often reinforce pre-existing biases, leading to further exclusion. Eubanks notes that “they are shaped by our nation’s fear of economic insecurity and hatred of the poor; they in turn shape the politics and experience of poverty” (Eubanks, 2018, p.7). These technologies strip people of their autonomy and create barriers rather than solutions. To address this issue, we must push for transparency in algorithmic decision-making and ensure that automated systems are designed with fairness and social justice in mind.
Word Count: 603
Daniels , J. (2009). Rethinking cyberfeminism(s): Race, gender, and embodiment | request PDF. Project Muse . https://www.researchgate.net/publication/236786509_Rethinking_Cyberfeminisms_Race_Gender_and_Embodiment
Eubanks, V. (2018). (PDF) Virginia Eubanks (2018) automating inequality: How high-tech tools profile, police, and punish the poor. New York: Picador, St Martin’s press. https://www.researchgate.net/publication/337578410_Virginia_Eubanks_2018_Automating_Inequality_How_High-Tech_Tools_Profile_Police_and_Punish_the_Poor_New_York_Picador_St_Martin’s_Press
[Nicole Brown]. (2020, September 18). Race and Technology [Video]. Youtube. https://www.youtube.com/watch?v=d8uiAjigKy8
10 notes
·
View notes
Text
BigProfitPulse.io Reviews Explore the Best Trading Conditions
The online trading world is dynamic and ever-evolving making it crucial to choose a reliable and efficient platform that provides traders with the best opportunities. BigProfitPulse.io reviews showcase why this platform stands out as a leader in the financial industry offering a combination of innovative tools competitive trading conditions and high-speed execution. With a diverse range of financial instruments and a user-friendly interface traders can seamlessly engage in trading without unnecessary hurdles. The ability to access real-time market prices and leverage personalized support ensures that every trader from beginners to professionals can optimize their strategies and achieve financial success.
BigProfitPulse.io Reviews Why Traders Choose Us
Traders are always in search of a platform that not only meets their expectations but also exceeds them. BigProfitPulse.io reviews highlight how this platform consistently delivers top-tier trading services ensuring that every trader has access to the best possible conditions. A major reason why traders trust BigProfitPulse.io is the platform’s commitment to transparency and efficiency. With instant order execution and competitive spreads traders can capitalize on opportunities without worrying about delays or hidden fees. Additionally the platform’s training programs provide users with invaluable insights helping them refine their skills and develop well-informed trading strategies. Whether you are just getting started or already an experienced trader BigProfitPulse.io has the tools and resources to support your journey.
BigProfitPulse.io A Cutting-Edge Trading Platform
One of the most discussed features in BigProfitPulse.io reviews is its cutting-edge trading platform which is designed to cater to traders of all levels. The web-based terminal allows users to analyze financial markets track real-time price movements and execute trades effortlessly from their browsers. There is no need for additional software installations or complicated setup procedures making it easier than ever to engage in global trading. Whether you are trading stocks foreign currencies or precious metals BigProfitPulse.io provides an advanced yet accessible trading environment. The platform is equipped with the latest tools for technical analysis ensuring that traders can make data-driven decisions with confidence.
BigProfitPulse.io Reviews Comprehensive Client Support
A key highlight in BigProfitPulse.io reviews is the comprehensive customer support that ensures traders receive assistance whenever they need it. The platform prides itself on offering professional support services with a team of knowledgeable experts available to answer questions resolve technical issues and provide valuable insights. Whether traders require help navigating the trading terminal understanding market trends or optimizing their trading strategies BigProfitPulse.io’s support team is always ready to assist. This level of commitment to customer service sets the platform apart making it a preferred choice for traders looking for reliability and security.
BigProfitPulse.io Real-Time Liquidity and Instant Execution
Market conditions can change in an instant and traders need a platform that provides real-time liquidity and swift order execution. BigProfitPulse.io reviews emphasize how the platform ensures that trades are processed without delays allowing traders to take advantage of market fluctuations as they happen. The integration of interbank liquidity ensures that users get the best available prices maximizing their profitability. By eliminating execution lags and providing seamless order processing BigProfitPulse.io enhances the overall trading experience giving users a competitive edge in the financial markets.
BigProfitPulse.io Reviews Personalized Training for Traders
Education and continuous learning play a significant role in a trader’s success and BigProfitPulse.io reviews highlight how the platform offers personalized training programs to support users at every stage of their trading journey. Traders are matched with experienced tutors who provide insights into market movements risk management and profitable trading strategies. This hands-on approach helps traders develop confidence and refine their skills ensuring they can navigate financial markets with greater precision. The platform’s commitment to education makes it an ideal choice for both newcomers and seasoned professionals looking to expand their knowledge.
BigProfitPulse.io Reviews Secure and Fast Withdrawals
Security and convenience are top priorities for traders and BigProfitPulse.io reviews confirm that the platform provides a safe and efficient withdrawal process. Users can request fund withdrawals at any time knowing that transactions will be processed swiftly without unnecessary delays. The platform employs advanced security measures to protect user funds and personal data giving traders peace of mind while they focus on their trading activities. Whether traders are actively trading or cashing out their profits they can trust BigProfitPulse.io to handle their transactions smoothly and securely.
BigProfitPulse.io Getting Started is Easy
A major advantage noted in BigProfitPulse.io reviews is the simplicity of getting started on the platform. Registration is quick and straightforward allowing traders to create an account and begin trading within minutes. The low minimum deposit requirement makes it accessible to traders of all backgrounds whether they are testing the waters or fully committing to the trading lifestyle. The platform also provides personalized guidance during the onboarding process ensuring that new traders have all the necessary tools and knowledge to begin their journey with confidence.
BigProfitPulse.io The Advantages of Trading Here
Traders continue to choose BigProfitPulse.io for the numerous advantages it offers. BigProfitPulse.io reviews frequently mention the following key benefits
Competitive spreads and low trading commissions ensuring maximum profitability
Swift and hassle-free processing of withdrawal requests allowing traders to access their funds at any time
Timely updates on significant market events helping traders stay informed and make strategic decisions
Access to global financial markets enabling users to diversify their portfolios and explore multiple investment opportunities
Professional customer support dedicated to resolving issues and providing expert assistance
BigProfitPulse.io Reviews Your Path to Financial Success
Finding the right trading platform is essential for achieving success in the financial markets. BigProfitPulse.io reviews highlight how this platform combines advanced technology expert guidance and superior trading conditions to create an unparalleled trading experience. Whether you are an aspiring trader or a seasoned professional looking for a reliable partner BigProfitPulse.io provides all the tools and resources necessary for success. By choosing BigProfitPulse.io traders gain access to a secure transparent and innovative trading environment that empowers them to reach their financial goals.
6 notes
·
View notes
Text
What are these Levels -Code and Pixels IETM
Code and Pixels Interactive Technologies Private Limited (CNP) is an IT service provider based in Hyderabad (India). We provide end-to-end eLearning solutions and IETM development (INDIAN STANDARD IETM JSG 0852:2001, LEVELS 3,4,5 and European Aviation Standard IETM Level4 ), specialized in innovative use of technology.

#ietm level 4 software requirements#technical documentation#ietm developement#ietm document#ietm documentation#interactive electronic technical manual#Ietm Service Providers#Ietm Software Designers of India#Software Development Company#Elearning Solutions Company#E Learning Content Development Company#Online Education#Digital Education#Digital Content#Software Development Solutions#Elearning#Ietm Developers#Econtent Development#Elearning Solutions Providers#Econtent Developers#Econtent#Mobile Learning#What is Html5#Software Solutions#Software Development & E-learning Solutions
1 note
·
View note
Text
Python for Beginners: Launch Your Tech Career with Coding Skills
Are you ready to launch your tech career but don’t know where to start? Learning Python is one of the best ways to break into the world of technology—even if you have zero coding experience.
In this guide, we’ll explore how Python for beginners can be your gateway to a rewarding career in software development, data science, automation, and more.
Why Python Is the Perfect Language for Beginners
Python has become the go-to programming language for beginners and professionals alike—and for good reason:
Simple syntax: Python reads like plain English, making it easy to learn.
High demand: Industries spanning the spectrum are actively seeking Python developers to fuel their technological advancements.
Versatile applications: Python's versatility shines as it powers everything from crafting websites to driving artificial intelligence and dissecting data.
Whether you want to become a software developer, data analyst, or AI engineer, Python lays the foundation.
What Can You Do With Python?
Python is not just a beginner language—it’s a career-building tool. Here are just a few career paths where Python is essential:
Web Development: Frameworks like Django and Flask make it easy to build powerful web applications. You can even enroll in a Python Course in Kochi to gain hands-on experience with real-world web projects.
Data Science & Analytics: For professionals tackling data analysis and visualization, the Python ecosystem, featuring powerhouses like Pandas, NumPy, and Matplotlib, sets the benchmark.
Machine Learning & AI: Spearheading advancements in artificial intelligence development, Python boasts powerful tools such as TensorFlow and scikit-learn.
Automation & Scripting: Simple yet effective Python scripts offer a pathway to amplified efficiency by automating routine workflows.
Cybersecurity & Networking: The application of Python is expanding into crucial domains such as ethical hacking, penetration testing, and the automation of network processes.
How to Get Started with Python
Starting your Python journey doesn't require a computer science degree. Success hinges on a focused commitment combined with a thoughtfully structured educational approach.
Step 1: Install Python
Download and install Python from python.org. It's free and available for all platforms.
Step 2: Choose an IDE
Use beginner-friendly tools like Thonny, PyCharm, or VS Code to write your code.
Step 3: Learn the Basics
Focus on:
Variables and data types
Conditional statements
Loops
Functions
Lists and dictionaries
If you prefer guided learning, a reputable Python Institute in Kochi can offer structured programs and mentorship to help you grasp core concepts efficiently.
Step 4: Build Projects
Learning by doing is key. Start small:
Build a calculator
Automate file organization
Create a to-do list app
As your skills grow, you can tackle more complex projects like data dashboards or web apps.
How Python Skills Can Boost Your Career
Adding Python to your resume instantly opens up new opportunities. Here's how it helps:
Higher employability: Python is one of the top 3 most in-demand programming languages.
Better salaries: Python developers earn competitive salaries across the globe.
Remote job opportunities: Many Python-related jobs are available remotely, offering flexibility.
Even if you're not aiming to be a full-time developer, Python skills can enhance careers in marketing, finance, research, and product management.
If you're serious about starting a career in tech, learning Python is the smartest first step you can take. It’s beginner-friendly, powerful, and widely used across industries.
Whether you're a student, job switcher, or just curious about programming, Python for beginners can unlock countless career opportunities. Invest time in learning today—and start building the future you want in tech.
Globally recognized as a premier educational hub, DataMites Institute delivers in-depth training programs across the pivotal fields of data science, artificial intelligence, and machine learning. They provide expert-led courses designed for both beginners and professionals aiming to boost their careers.
Python Modules Explained - Different Types and Functions - Python Tutorial
youtube
#python course#python training#python#learnpython#pythoncourseinindia#pythoncourseinkochi#pythoninstitute#python for data science#Youtube
3 notes
·
View notes
Text
What are the effects of Saturn in the 5th house of a Virgo woman?
In Vedic astrology, the placement of Saturn in the 5th house of a Virgo woman's birth chart can influence various aspects of her life, including her creativity, education, children, and romantic relationships. Here are some potential effects:
Intellectual pursuits: Saturn in the 5th house may indicate a serious and disciplined approach towards education and intellectual pursuits. The individual may have a methodical way of learning and may excel in subjects that require deep concentration and focus.
Creativity: Saturn's presence in the 5th house can sometimes indicate challenges or restrictions in expressing creativity. The individual may have a more structured or disciplined approach to creative endeavors, preferring practical and tangible outcomes over spontaneous expression.
Romantic relationships: Saturn's placement in the 5th house can bring a sense of responsibility and maturity to romantic relationships. The individual may approach love affairs with caution and may prefer long-term commitments over casual flings. There may be a tendency to attract partners who are serious, disciplined, or older.
Children: Saturn in the 5th house may bring delays or challenges in matters related to childbirth or raising children. The individual may take a disciplined and cautious approach to parenting, emphasizing structure and responsibility in their interactions with their children.
Speculative activities: The 5th house also governs speculative activities like gambling and investments. Saturn's presence here may indicate a conservative approach towards such activities, with a preference for long-term and low-risk investments rather than speculative ventures.
Mental health: Saturn's influence in the 5th house may sometimes lead to a tendency towards pessimism or a serious outlook on life. The individual may need to consciously work on developing a more positive and optimistic mindset to counteract any tendencies towards negativity.
Education and learning: Saturn's presence can indicate a strong sense of discipline and responsibility towards education and learning. The individual may be willing to put in the hard work and effort required to achieve their academic goals, even if it means overcoming obstacles or facing delays.
Overall, the influence of Saturn in the 5th house for a Virgo woman may vary depending on the overall configuration of her birth chart, including aspects and conjunctions with other planets. For more accurate interpretation you can use Kundli Chakra Professional 2022 software.
#astrology#astro#horoscope today#matchmaking#astroworld#astro placements#marriage#numerology#astrology observations#vivah#astro notes#astro community#astro chart#astro observations#astro memes#astro boy#astro tumblr#astro posts#astroblr#astronaut#astrophysics
27 notes
·
View notes
Text
Hire Dedicated Developers in India Smarter with AI
Hire dedicated developers in India smarter and faster with AI-powered solutions. As businesses worldwide turn to software development outsourcing, India remains a top destination for IT talent acquisition. However, finding the right developers can be challenging due to skill evaluation, remote team management, and hiring efficiency concerns. Fortunately, AI recruitment tools are revolutionizing the hiring process, making it seamless and effective.

In this blog, I will explore how AI-powered developer hiring is transforming the recruitment landscape and how businesses can leverage these tools to build top-notch offshore development teams.
Why Hire Dedicated Developers in India?
1) Cost-Effective Without Compromising Quality:
Hiring dedicated developers in India can reduce costs by up to 60% compared to hiring in the U.S., Europe, or Australia. This makes it a cost-effective solution for businesses seeking high-quality IT staffing solutions in India.
2) Access to a Vast Talent Pool:
India has a massive talent pool with millions of software engineers proficient in AI, blockchain, cloud computing, and other emerging technologies. This ensures companies can find dedicated software developers in India for any project requirement.
3) Time-Zone Advantage for 24/7 Productivity:
Indian developers work across different time zones, allowing continuous development cycles. This enhances productivity and ensures faster project completion.
4) Expertise in Emerging Technologies:
Indian developers are highly skilled in cutting-edge fields like AI, IoT, and cloud computing, making them invaluable for innovative projects.
Challenges in Hiring Dedicated Developers in India
1) Finding the Right Talent Efficiently:
Sorting through thousands of applications manually is time-consuming. AI-powered recruitment tools streamline the process by filtering candidates based on skill match and experience.
2) Evaluating Technical and Soft Skills:
Traditional hiring struggles to assess real-world coding abilities and soft skills like teamwork and communication. AI-driven hiring processes include coding assessments and behavioral analysis for better decision-making.
3) Overcoming Language and Cultural Barriers:
AI in HR and recruitment helps evaluate language proficiency and cultural adaptability, ensuring smooth collaboration within offshore development teams.
4) Managing Remote Teams Effectively:
AI-driven remote work management tools help businesses track performance, manage tasks, and ensure accountability.
How AI is Transforming Developer Hiring
1. AI-Powered Candidate Screening:
AI recruitment tools use resume parsing, skill-matching algorithms, and machine learning to shortlist the best candidates quickly.
2. AI-Driven Coding Assessments:
Developer assessment tools conduct real-time coding challenges to evaluate technical expertise, code efficiency, and problem-solving skills.
3. AI Chatbots for Initial Interviews:
AI chatbots handle initial screenings, assessing technical knowledge, communication skills, and cultural fit before human intervention.
4. Predictive Analytics for Hiring Success:
AI analyzes past hiring data and candidate work history to predict long-term success, improving recruitment accuracy.
5. AI in Background Verification:
AI-powered background checks ensure candidate authenticity, education verification, and fraud detection, reducing hiring risks.
Steps to Hire Dedicated Developers in India Smarter with AI
1. Define Job Roles and Key Skill Requirements:
Outline essential technical skills, experience levels, and project expectations to streamline recruitment.
2. Use AI-Based Hiring Platforms:
Leverage best AI hiring platforms like LinkedIn Talent Insightsand HireVue to source top developers.
3. Implement AI-Driven Skill Assessments:
AI-powered recruitment processes use coding tests and behavioral evaluations to assess real-world problem-solving abilities.
4. Conduct AI-Powered Video Interviews:
AI-driven interview tools analyze body language, sentiment, and communication skills for improved hiring accuracy.
5. Optimize Team Collaboration with AI Tools:
Remote work management tools like Trello, Asana, and Jira enhance productivity and ensure smooth collaboration.
Top AI-Powered Hiring Tools for Businesses
LinkedIn Talent Insights — AI-driven talent analytics
HackerRank — AI-powered coding assessments
HireVue — AI-driven video interview analysis
Pymetrics — AI-based behavioral and cognitive assessments
X0PA AI — AI-driven talent acquisition platform
Best Practices for Managing AI-Hired Developers in India
1. Establish Clear Communication Channels:
Use collaboration tools like Slack, Microsoft Teams, and Zoom for seamless communication.
2. Leverage AI-Driven Productivity Tracking:
Monitor performance using AI-powered tracking tools like Time Doctor and Hubstaff to optimize workflows.
3. Encourage Continuous Learning and Upskilling:
Provide access to AI-driven learning platforms like Coursera and Udemy to keep developers updated on industry trends.
4. Foster Cultural Alignment and Team Bonding:
Organize virtual team-building activities to enhance collaboration and engagement.
Future of AI in Developer Hiring
1) AI-Driven Automation for Faster Hiring:
AI will continue automating tedious recruitment tasks, improving efficiency and candidate experience.
2) AI and Blockchain for Transparent Recruitment:
Integrating AI with blockchain will enhance candidate verification and data security for trustworthy hiring processes.
3) AI’s Role in Enhancing Remote Work Efficiency:
AI-powered analytics and automation will further improve productivity within offshore development teams.
Conclusion:
AI revolutionizes the hiring of dedicated developers in India by automating candidate screening, coding assessments, and interview analysis. Businesses can leverage AI-powered tools to efficiently find, evaluate, and manage top-tier offshore developers, ensuring cost-effective and high-quality software development outsourcing.
Ready to hire dedicated developers in India using AI? iQlance offers cutting-edge AI-powered hiring solutions to help you find the best talent quickly and efficiently. Get in touch today!
#AI#iqlance#hire#india#hirededicatreddevelopersinIndiawithAI#hirededicateddevelopersinindia#aipoweredhiringinindia#bestaihiringtoolsfordevelopers#offshoresoftwaredevelopmentindia#remotedeveloperhiringwithai#costeffectivedeveloperhiringindia#aidrivenrecruitmentforitcompanies#dedicatedsoftwaredevelopersindia#smarthiringwithaiinindia#aipowereddeveloperscreening
5 notes
·
View notes
Text
PC Engine - Where in the World is Carmen Sandiego?
Title: Where in the World is Carmen Sandiego? / カルメンサンディエゴを追え! 世界編
Developer: Broderbund Software
Publisher: Pack-in-Video (Victor Company of Japan)
Release date: 30 March 1990
Catalogue No.: PVCD0001
Genre: Detective Puzzle / Mystery Education Adventure
Format: CD-ROM2


At last! Another Japan-exclusive PC Engine CD game that also allows you to play the game in English. Good news! The graphics and CD music are pretty good. Really good. So is the narrative of this game. Overall, I thoroughly enjoyed each and every minute I spent playing 'Where in the World is Carmen Sandiego?'; it was a blast. Either way, you play this game, whether it be through using the Internet or an almanac, you're in for a good time. I can see how some gamers may be upset over having to buy an almanac to play it, but it was required for the original version, and it's really no surprise that it is required here (this is a learning game after all, and you can write your passcodes in the cover which is something modern emulators already alleviate). This game has excellent replay value, a progressively increasing difficulty level, the ability to be played in five different languages, and is easily enjoyed by gamers of all ages... not to mention YOU WILL LEARN! Don't think that these are all kiddie-level questions here, sure there are some easy ones, but more often than not you will find yourself stumped. So, pull up a chair, an almanac, or a buddy, and try your hand at answering one of the most legendary questions in gaming history.



youtube
7 notes
·
View notes