#Essential Developer Software
Note
👀👀 rlly interesting read on ovan, would love to hear some abt ur hcs on him n corbenik
(Now on DW!)
So it's been a hot minute since I watched Terminal Disc so my memory of the details of the canon are very vague, but I definitely think it's likely that the Epitaphs attached themselves to players in reverse numerical order, making Ovan the first and unintentionally the template for how becoming an Epitaph-PC would play out.
Corbenik is sort of funny as a Phase because the way it's laid out in the Epitaph, Corbenik serves no function until the Wave wipes out its intended target, and it's left behind to observe the void. As long as the system state isn't disturbed and no new AI begins to emerge, Corbenik stays passive theoretically forever -- but once it is disturbed, it rouses the rest of the Wave to come clean up what was left unfinished.
(I recognise this isn't how we see it play out in R1, I'm basing this on the idea that Morganna designed the Wave to be essentially self-propagating against Aura. The stalemate is the point, the rolling waves razing any fertile ground for her to develop on in favour of perpetual despair and the call of the void.)
With Corbenik as the rearguard of the apocalypse, it could have easily been the most active (least inactive?) of the Phases during the period of calm after Aura takes over Morganna's duties -- with no AI competing with Aura available to suppress, it was essentially on standby, latching onto Ovan the moment he showed up and then doing nothing until it registered the AIDA that also attached itself to Ovan.
Which is the thing that really fucks Ovan over, I think. The body timeshare he has with Tri-Edge is stressful enough, but Corbenik is also perpetually making him identify himself as the greatest threat to system integrity. So he's essentially getting a triple dose of the Epitaph "the solution is Fucking Kill Yourself" heightened self-destructive urge -- from the nature of the Cursed Wave, from the Vagrant AI-fication of the Phases and being (in part) his own natural-born enemy.
On top of this, Corbenik is perpetually calling to the other Phases like "over here! I've identified the enemy! Here is an AI we need to stop from reaching self-actualisation!" So candidates are drawn to him, unconsciously recognise him as having seniority, and then immediately identify him as the threat to be eliminated. People keep forming a kind of proxy disordered attachment to him, feeling compelled to follow his orders but also feeling threatened by his presence and become driven by the urge to destroy him.
Haseo is particularly vulnerable to this because Skeith and Corbenik are so intertwined in their roles, the first Phase is the one the last calls the strongest, and his personal sense of betrayal only amplifies the destructive resonance. And the influence goes both ways, the more Skeith perceives Corbenik's host as the main threat, the more Corbenik calls on Skeith as the vanguard to eliminate that threat. Haseo's (perceived) perception of him directly influences Ovan's perception of himself -- with everyone else Ovan is very particular about asserting his own reality, but with Haseo, the way Haseo sees him takes priority over how Ovan sees himself.
#van's answers#anonymous#dothack#.hack//g.u.#Ovan#Avatar Corbenik#GU spoilers#<- for my friends who are still playing the games#I have a lot of feelings about how the Cursed Wave is basically the software version of weaponised depression#And about how the games are overall very clear about how happiness and emotional connection aren't frivolous but rather essential to life#Corbenik as the 8th Phase is the pure distilled idea of 'there is a way out and it's by dying in your egg without ever hatching'#and it's supported by the other Phases in creating a vision of the world that has nothing worth living in it#as much as you're afraid of death -- look. See. What else is there?#They're out-of-proportion feelings of doom aimed to keep a consciousness that vastly exceeds human comprehension from having any hope#AND CC CORP JUST FUCKING SLAPPED THEM INSIDE SOME PCS AND GAVE THEM TO PLAYERS LIKE 'here you go! Here's your Personal Cataclysm Gun!'#The real enemy in dothack is closed source software development and corporate vanity
5 notes
·
View notes
Text
Do neurotypicals not do the thing where they're like "this is where the inspiring montage to speed me to the next major plot point and avoid the drudgery of day-to-day life would go" about real life?
#neurotypicals really can just. experience the world w/o having to put everything through a lens huh?#it makes sense that us NDs have to filter life through a lens of (usually) media bc that's always more straightforward than real life#there's a narrator to explain what's happening#you are almost always put in the head of at least one character so you can relate to/understand them#there are tropes and structure that can be learned and recognized#all of which is much easier than trying to figure out the subtleties of real life socializing#(to the point that my apparently traumatized child self developed a dissociative coping mechanism based around that)#(I'm no longer doing therapy so all my Therapy Thoughts™ go in tumblr tags - which is more helpful than the therapy was anyway)#point is it must be fucking wild to not have to essentially put every social interaction through a translation software in your head
2 notes
·
View notes
Text

Data Warehouse Services
#QuellSoft#Data Warehouse Services#Data Warehousing#Cloud Applications Services#Data Warehousing Essentials#Data Warehouse Application#custom website development#website design and development#website optimization#app development software
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Help my family in northern Gaza survive
Dear Humanity,
My name is Amal, and I am from Gaza. We are 5 family members. Currently, my family and I are living in northern Gaza under conditions of starvation, shelling, and gunfire. Gaza is experiencing a devastating war that has forced many families, including mine, to flee our homes repeatedly. Each time we are displaced, we are unable to take anything with us, losing the little food and clothing we managed to store.


We are enduring an unimaginable crisis right now, facing severe shortages of food and water tainted with harmful viruses and bacteria. This contamination is causing dangerous skin and respiratory diseases, and we are now also grappling with an outbreak of polio.



The scarcity of food is not just a hardship; it is a relentless torment, leaving us weakened and ill. Our lack of income, or rather its complete absence, is tearing our family apart, leaving us helpless and struggling to survive.
This suffering is beyond what any living being should endure. Imagine spending just one night in these conditions how would you feel? From the depths of our hearts, we desperately implore you to support us, to help us escape this famine and the devastation of war.
Our home, my workplace, and all my sources of income as a software developer have been destroyed due to the war. With no stable place to stay and no source of income, we are struggling to survive.

We urgently need your help to:
Purchase essential food and clothing for my family, Secure a temporary shelter, and Leaving Gaza and seeking a safe place to start a new life for me and my family.
Therefore, I implore you to help us provide food, water, and a safe place outside of Gaza for me and my family. Your donations will make a significant difference in our lives. Every contribution, no matter how small, will provide us with the relief we desperately need and the hope to rebuild our future.
Thank you for your kindness and generosity.
Your support will give us a chance to overcome this crisis and look forward to a better tomorrow.
Dear Tumblr Community,
I am delighted to be part of this comunity and seek your support in sharing a post I've crafted. This isn't merely a collection of words but a crucial part of a fundraising effort to assist my family during these challenging times.
I have faith that you will help amplify this message to reach a wide audience.
Thank you sincerely for your support.🙏❤️
#gaza#gaza strip#free palestine#free gaza#gaza donation#donations#donat#gaza genocide#palestinian genocide#gofundme#gaza gfm#palestine news#gaza news#palestine gfm#save gaza#all eyes on palestine#software development#freelance#web developers#support palestine#save palestine
7K notes
·
View notes
Note
(half rant half story)
I'm a physicist. I work for a company that helps develop car parts. Essentially, car companies come to us with ideas on what they want from a part or material, and we make/test the idea or help them make/test it. Usually this means talking to other scientists and engineers and experts and it's all fine. Sometimes this means talking to businesspeople and board execs and I hate them
A bit ago when AI was really taking off in the zeitgeist I went to a meeting to talk about some tweaks Car Company A wanted to make to their hydraulics- specifically the master cylinder, but it doesn't super matter. I thought I'd be talking to their engineers - it ends up being just me, their head supervisor (who was not a scientist/engineer) and one of their executives from a different area (also not a scientist/engineer). I'm the only one in the room who actually knows how a car works, and also the lowest-level employee, and also aware that these people will give feedback to my boss based on how I 'represent the company ' whilst I'm here.
I start to explain my way through how I can make some of the changes they want - trying to do so in a way they'll understand - when Head Supervisor cuts me off and starts talking about AI. I'm like "oh well AI is often integrated into the software for a car but we're talking hardware right now, so that's not something we really ca-"
"Can you add artificial intelligence to the hydraulics?"
"..sorry, what was that?"
"Can you add AI to the hydraulics system?"
can i fucking what mate "Sir, I'm sorry, I'm a little confused - what do you mean by adding AI to the hydraulics?"
"I just thought this stuff could run smoother if you added AI to it. Most things do"
The part of the car that moves when you push the acceleration pedal is metal and liquid my dude what are you talking about "You want me to .add AI...to the pistons? To the master cylinder?"
"Yeah exactly, if you add AI to the bit that makes the pistons work, it should work better, right?"
IT'S METAL PIPES it's metal pipes it's metal pipes "Sir, there isn't any software in that part of the car"
"I know, but it's artificial intelligence, I'm sure there's a way to add it"
im exploding you with my mind you cannot seriously be asking me to add AI to a section of car that has as much fucking code attached to it as a SOCK what do you MEAN. The most complicated part of this thing is a SPRING you can't be serious
He was seriously asking. I've met my fair share of idiots but I was sure he wasn't genuinely seriously asking that I add AI directly to a piston system, but he was. And not even in the like "oh if we implement a way for AI to control that part" kind of way, he just vaguely thought that AI would "make it better" WHAT THE FUCK DO YOU MEANNNNN I HAD TO SPEND 20 MINUTES OF MY HARD EARNED LIFE EXPLAINING THAT NEITHER I NOR ANYONE ELSE CAN ADD AI TO A GOD DAMNED FUCKING PISTON. "CAN YOU ADD AI TO THE HYDRAULICS" NO BUT EVEN WITHOUT IT THAT METAL PIPE IS MORE INTELLIGENT THAN YOU
Posted by admin Rodney.
13K notes
·
View notes
Text
F5 API Security: Safeguarding Your Digital Infrastructure

F5 API Security, In today's digital age, Application Programming Interfaces (APIs) have become the backbone of numerous web and mobile applications. They allow applications to communicate, share data, and enhance functionality. As the use of APIs grows, so do the associated security risks. In this article, we will delve into the world of F5 API security, understanding its significance, common threats, and how F5's solutions can help protect your digital assets.
Understanding the Importance of API Security
APIs play a pivotal role in modern software development, enabling the seamless exchange of data between different systems. However, the very nature of this data exchange also makes APIs susceptible to various security threats. It's imperative to secure your APIs to protect sensitive information and maintain the trust of your users.
Common API Security Threats
Authentication and Authorization
One of the primary concerns in API security is ensuring that only authorized users or applications can access your API endpoints. F5 provides robust solutions for authentication and authorization, preventing unauthorized access.
Data Encryption
Securing data in transit is crucial. F5 offers encryption services that safeguard your API traffic from eavesdropping and data breaches.
Rate Limiting
APIs are vulnerable to abuse through excessive requests. F5's rate limiting capabilities help prevent API overuse and potential disruption.
F5 Solutions for API Security
F5 offers a range of tools to protect your APIs effectively:
Web Application Firewall (WAF)
A WAF is a crucial component of API security, safeguarding against various web-based attacks. F5's WAF ensures that malicious traffic is filtered out, keeping your API endpoints secure.
API Gateway
An API gateway acts as a traffic cop for your APIs, routing requests, and enforcing security policies. F5's API gateway provides robust security features, including authentication and rate limiting.
Bot Protection
APIs can be targeted by malicious bots. F5's bot protection technologies help differentiate between legitimate and malicious bot traffic, ensuring smooth API operations.
Implementing API Security with F5
Setting Up a WAF
Implementing a WAF involves defining security policies, traffic inspection, and custom rule creation. F5 simplifies this process with an intuitive interface, making it easier to secure your APIs.
Configuring an API Gateway
Setting up an API gateway involves defining access controls, rate limiting policies, and API documentation. F5's API gateway streamlines this setup, ensuring your APIs are secure and well-documented.
Leveraging Bot Protection
Protecting against malicious bots requires configuring bot policies and monitoring bot traffic. F5's bot protection tools make it easier to safeguard your APIs from automated threats.
Best Practices for F5 API Security
To ensure a robust API security framework:
Regularly audit and monitor API traffic and security policies.
Maintain proper version control of your APIs to avoid compatibility issues.
Invest in training and awareness programs to educate your team about API security best practices.
Case Studies: Real-world Examples of F5 API Security Success
Explore real-world success stories where organizations have used F5's API security solutions to protect their digital assets. These case studies highlight the effectiveness and reliability of F5's offerings.
Conclusion
In an era of rapid digital transformation, securing your APIs is non-negotiable. F5 API security solutions offer a comprehensive defense against the most common threats, ensuring the uninterrupted operation of your applications and the safety of your data.
FAQs on F5 API Security
What are the primary security threats to APIs?
Common threats include authentication issues, data breaches, and abuse through excessive requests.
How does F5 safeguard APIs against malicious bots?
F5 employs advanced bot protection technologies to differentiate between legitimate and malicious bot traffic, ensuring API security.
Why is API security essential in modern software development?
API security is crucial to protect sensitive data and maintain the trust of users in an interconnected digital world.
What are the key features of F5's Web Application Firewall (WAF)?
F5's WAF offers features such as web-based attack protection, traffic filtering, and security policy enforcement.
How can I get started with F5 API security solutions?
To get started with F5 API security.
#F5 API Security#Why is API security essential in modern software development?#Leveraging Bot Protection
0 notes
Text
#digtal marketing#Essential E-Commerce Services#software#web developing company#business#seo services#seo changbin#web design
0 notes
Text
The conversation around AI is going to get away from us quickly because people lack the language to distinguish types of AI--and it's not their fault. Companies love to slap "AI" on anything they believe can pass for something "intelligent" a computer program is doing. And this muddies the waters when people want to talk about AI when the exact same word covers a wide umbrella and they themselves don't know how to qualify the distinctions within.
I'm a software engineer and not a data scientist, so I'm not exactly at the level of domain expert. But I work with data scientists, and I have at least rudimentary college-level knowledge of machine learning and linear algebra from my CS degree. So I want to give some quick guidance.
What is AI? And what is not AI?
So what's the difference between just a computer program, and an "AI" program? Computers can do a lot of smart things, and companies love the idea of calling anything that seems smart enough "AI", but industry-wise the question of "how smart" a program is has nothing to do with whether it is AI.
A regular, non-AI computer program is procedural, and rigidly defined. I could "program" traffic light behavior that essentially goes { if(light === green) { go(); } else { stop();} }. I've told it in simple and rigid terms what condition to check, and how to behave based on that check. (A better program would have a lot more to check for, like signs and road conditions and pedestrians in the street, and those things will still need to be spelled out.)
An AI traffic light behavior is generated by machine-learning, which simplistically is a huge cranking machine of linear algebra which you feed training data into and it "learns" from. By "learning" I mean it's developing a complex and opaque model of parameters to fit the training data (but not over-fit). In this case the training data probably includes thousands of videos of car behavior at traffic intersections. Through parameter tweaking and model adjustment, data scientists will turn this crank over and over adjusting it to create something which, in very opaque terms, has developed a model that will guess the right behavioral output for any future scenario.
A well-trained model would be fed a green light and know to go, and a red light and know to stop, and 'green but there's a kid in the road' and know to stop. A very very well-trained model can probably do this better than my program above, because it has the capacity to be more adaptive than my rigidly-defined thing if the rigidly-defined program is missing some considerations. But if the AI model makes a wrong choice, it is significantly harder to trace down why exactly it did that.
Because again, the reason it's making this decision may be very opaque. It's like engineering a very specific plinko machine which gets tweaked to be very good at taking a road input and giving the right output. But like if that plinko machine contained millions of pegs and none of them necessarily correlated to anything to do with the road. There's possibly no "if green, go, else stop" to look for. (Maybe there is, for traffic light specifically as that is intentionally very simplistic. But a model trained to recognize written numbers for example likely contains no parameters at all that you could map to ideas a human has like "look for a rigid line in the number". The parameters may be all, to humans, meaningless.)
So, that's basics. Here are some categories of things which get called AI:
"AI" which is just genuinely not AI
There's plenty of software that follows a normal, procedural program defined rigidly, with no linear algebra model training, that companies would love to brand as "AI" because it sounds cool.
Something like motion detection/tracking might be sold as artificially intelligent. But under the covers that can be done as simply as "if some range of pixels changes color by a certain amount, flag as motion"
2. AI which IS genuinely AI, but is not the kind of AI everyone is talking about right now
"AI", by which I mean machine learning using linear algebra, is very good at being fed a lot of training data, and then coming up with an ability to go and categorize real information.
The AI technology that looks at cells and determines whether they're cancer or not, that is using this technology. OCR (Optical Character Recognition) is the technology that can take an image of hand-written text and transcribe it. Again, it's using linear algebra, so yes it's AI.
Many other such examples exist, and have been around for quite a good number of years. They share the genre of technology, which is machine learning models, but these are not the Large Language Model Generative AI that is all over the media. Criticizing these would be like criticizing airplanes when you're actually mad at military drones. It's the same "makes fly in the air" technology but their impact is very different.
3. The AI we ARE talking about. "Chat-gpt" type of Generative AI which uses LLMs ("Large Language Models")
If there was one word I wish people would know in all this, it's LLM (Large Language Model). This describes the KIND of machine learning model that Chat-GPT/midjourney/stablediffusion are fueled by. They're so extremely powerfully trained on human language that they can take an input of conversational language and create a predictive output that is human coherent. (I am less certain what additional technology fuels art-creation, specifically, but considering the AI art generation has risen hand-in-hand with the advent of powerful LLM, I'm at least confident in saying it is still corely LLM).
This technology isn't exactly brand new (predictive text has been using it, but more like the mostly innocent and much less successful older sibling of some celebrity, who no one really thinks about.) But the scale and power of LLM-based AI technology is what is new with Chat-GPT.
This is the generative AI, and even better, the large language model generative AI.
(Data scientists, feel free to add on or correct anything.)
3K notes
·
View notes
Text

LaRue Burbank, mathematician and computer, is just one of the many women who were instrumental to NASA missions.
4 Little Known Women Who Made Huge Contributions to NASA
Women have always played a significant role at NASA and its predecessor NACA, although for much of the agency’s history, they received neither the praise nor recognition that their contributions deserved. To celebrate Women’s History Month – and properly highlight some of the little-known women-led accomplishments of NASA’s early history – our archivists gathered the stories of four women whose work was critical to NASA’s success and paved the way for future generations.
LaRue Burbank: One of the Women Who Helped Land a Man on the Moon
LaRue Burbank was a trailblazing mathematician at NASA. Hired in 1954 at Langley Memorial Aeronautical Laboratory (now NASA’s Langley Research Center), she, like many other young women at NACA, the predecessor to NASA, had a bachelor's degree in mathematics. But unlike most, she also had a physics degree. For the next four years, she worked as a "human computer," conducting complex data analyses for engineers using calculators, slide rules, and other instruments. After NASA's founding, she continued this vital work for Project Mercury.
In 1962, she transferred to the newly established Manned Spacecraft Center (now NASA’s Johnson Space Center) in Houston, becoming one of the few female professionals and managers there. Her expertise in electronics engineering led her to develop critical display systems used by flight controllers in Mission Control to monitor spacecraft during missions. Her work on the Apollo missions was vital to achieving President Kennedy's goal of landing a man on the Moon.
Eilene Galloway: How NASA became… NASA

Eilene Galloway wasn't a NASA employee, but she played a huge role in its very creation. In 1957, after the Soviet Union launched Sputnik, Senator Richard Russell Jr. called on Galloway, an expert on the Atomic Energy Act, to write a report on the U.S. response to the space race. Initially, legislators aimed to essentially re-write the Atomic Energy Act to handle the U.S. space goals. However, Galloway argued that the existing military framework wouldn't suffice – a new agency was needed to oversee both military and civilian aspects of space exploration. This included not just defense, but also meteorology, communications, and international cooperation.
Her work on the National Aeronautics and Space Act ensured NASA had the power to accomplish all these goals, without limitations from the Department of Defense or restrictions on international agreements. Galloway is even to thank for the name "National Aeronautics and Space Administration", as initially NASA was to be called “National Aeronautics and Space Agency” which was deemed to not carry enough weight and status for the wide-ranging role that NASA was to fill.
Barbara Scott: The “Star Trek Nerd” Who Led Our Understanding of the Stars

A self-described "Star Trek nerd," Barbara Scott's passion for space wasn't steered toward engineering by her guidance counselor. But that didn't stop her! Fueled by her love of math and computer science, she landed at Goddard Spaceflight Center in 1977. One of the first women working on flight software, Barbara's coding skills became instrumental on missions like the International Ultraviolet Explorer (IUE) and the Thermal Canister Experiment on the Space Shuttle's STS-3. For the final decade of her impressive career, Scott managed the flight software for the iconic Hubble Space Telescope, a testament to her dedication to space exploration.
Dr. Claire Parkinson: An Early Pioneer in Climate Science Whose Work is Still Saving Lives

Dr. Claire Parkinson's love of math blossomed into a passion for climate science. Inspired by the Moon landing, and the fight for civil rights, she pursued a graduate degree in climatology. In 1978, her talents landed her at Goddard, where she continued her research on sea ice modeling. But Parkinson's impact goes beyond theory. She began analyzing satellite data, leading to a groundbreaking discovery: a decline in Arctic sea ice coverage between 1973 and 1987. This critical finding caught the attention of Senator Al Gore, highlighting the urgency of climate change.
Parkinson's leadership extended beyond research. As Project Scientist for the Aqua satellite, she championed making its data freely available. This real-time information has benefitted countless projects, from wildfire management to weather forecasting, even aiding in monitoring the COVID-19 pandemic. Parkinson's dedication to understanding sea ice patterns and the impact of climate change continues to be a valuable resource for our planet.
Make sure to follow us on Tumblr for your regular dose of space!
#NASA#space#tech#technology#womens history month#women in STEM#math#climate science#computer science
2K notes
·
View notes
Text
How GitHub is useful for computer science students
How GitHub is useful for computer science students
As a computer science student, you might be familiar with GitHub. It’s a web-based hosting service for version control using git, a distributed revision control system. While it’s commonly used by software developers, GitHub is also an excellent resource for computer science students.
How GitHub is useful for computer science students
How GitHub…

View On WordPress
#Access to learning resources#Bug tracking#clean#Collaboration#Computer Science Students#concise#CSS#efficient code#essential#excellent resource#feedback#github#Harshada Ghate#How GitHub is useful#HTML#JavaScript#Learning new technologies#Learning to code#Portfolio building#software developers#software development project
1 note
·
View note
Text
Node.Js Development: Important Facts And Features | Dew Studio

#JavaScript is widely used for developing standard or even advanced custom software. Node.js is everything developers need and look for with#which encourages developers to produce advanced and diversified software applications.#Applications of PayPal#Netflix#Uber#eBay and many others are a few longstanding examples of Node.js’ exemplary possibilities. If you want your organization to enjoy one such r#then choose DEW Studio#the top low-code app development platform for your next software development projects.#Server-centric or Server Side programming powers of Node.js elevate every app development process when combined with JavaScript frameworks.#Let us uncover the important facts and features about node.js.#Discover 12 Interesting Node.Js Facts And Features#To choose Node.js#learning about its facts will be useful and essential.#A server engine at its core#Node.js#works only after you properly set it up and alter it to fulfil your needs.#It is part of the community of JavaScript. So this allows developers to alter or manipulate it with User Interfaces#JS tools and also connectors.#Node.js is completely open source. Additionally#it is a building framework that perfectly allows developers for cross-platform or hybrid mobile app development.#Your familiarity with JavaScript will help you to understand and use Node.js very easily. That is why node js is famous. You can hire a top#JavaScript is the easiest to work with. But it is Node.js that unleashes its true potential making it wonderful for every kind of web and m#Google’s V8 engine powers Node.js to run in the backend#while JavaScript runs in the front end with Google Chrome. Even Google itself mentions Node.js as its honorary#along with additional engine power structures.#Chrome 57+ has a Node.js debugging feature to eliminate errors from front-end and backend processes.#The JavaScript Object Notation – JSON is one stable#realistic and common data exchanging format. It is highly easy to create APIs with JSON.#Node.js group is always accommodating to exchanging its core bundles. Sharing becomes simple and effective. This answers why node js is bet#Node Package Manager [NPM] is used and its in-depth support has propelled growth Possibilities for the Node community.
0 notes
Text
today i was given a new task at work, and it is so complicated it frightens me. like i’m not sure what is asked of me is even possible. but i am also not knowledgeable enough to know for certain that i cannot do it.
i might solve it simply because i didn’t know it couldn’t be done.
#programming is hell sometimes#times like these my salary makes sense#i’m not essential to society in any way#but the problems are so complex sometimes#that companies have no choice but to throw cash at people naive enough to attempt solutions#software development#programmer problems#software engineer
0 notes
Note
Hi Neil!!
I’m a HS student and software developer, and I’m designing an app to help promote reading in kids. It’s similar to Duolingo, with rewards, a streak, and other incentives to encourage kids to read. The app is basically a fun reading tracker!
Anyways, my team and I were wondering if you could give us permission to use your quotes encouraging reading to add into our app?
This won’t go in any app store, we will make no profit; it’s essentially a big school project and is technically only experimental (for the moment). I’m just asking permission for your quotes because absolutely anything copyrightable needs to be done with permission of the author or company so we can cite that.
Thank you for your time, and I hope you consider it!
Sure.
797 notes
·
View notes
Note
Cactus fascinates me, does it run on code similar to an existing instruction set or is it completely original on that front?
What can you do with it? What's it's storage?
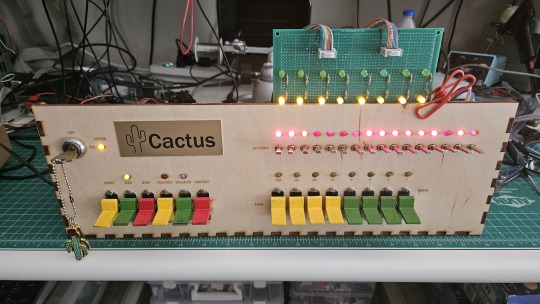
Both the Cactus (the original wooden prototype from years ago) and the new PCB Cactus(es) are essentially derived from a minimal 6502 computer design by Grant Searle for their core logic. Here's what that would look like on a breadboard:

There isn't much to it, it's 32K of RAM, 16K of ROM containing Ohio Scientific's version of Microsoft BASIC, a 6850 ACIA for serial interaction, some logic gates, and of course a 6502 microprocessor (NMOS or CMOS, doesn't matter which). You hook it into a terminal and away you go.
Grant's design in turn can be best described as a distilled, modernized version of the OSI Challenger series of computers. Here's an OSI-400 and a Challenger 4P respectively:
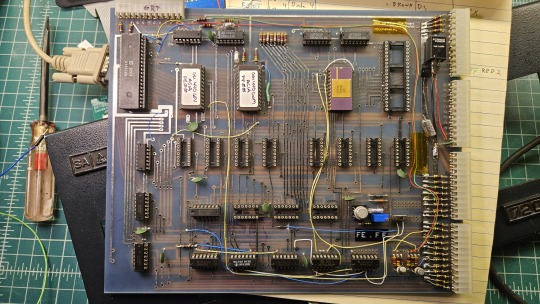

The left one is a replica of the 400 circa 1976, also called the Superboard. It was affordable, endlessly reconfigurable and hackable, but ultimately very limited in capabilities. No BASIC, minimal monitor ROM you talk to over serial, but you could connect it to a bus to augment its features and turn it into a more powerful computer.
Whereas the OSI C4P on the right from about 1979 has more RAM, a video card, keyboard, BASIC built in, serial interface, cassette tape storage, and that's just the standard configuration. There was more room to expand and augment it to your needs inside the chassis (alot changed in 3 years for home computer users).
Grant's minimal 6502 design running OSI BASIC is a good starter project for hobbyists. I learned about the 6502's memory map decoding from his design. I modified and implemented his design on a separate cards that could connect to a larger backplane.

Here are the serial, ROM, RAM, and CPU cards respectively:

Each one is 100% custom, containing many modifications and fixes as I developed the design. However, that's only half of the computer.
I really wanted a 6502 machine with a front panel. People told me "nobody did that", or couldn't think of examples from the 1970s but that seemed really strange to me. Especially since I had evidence to the contrary in the form of the OSI-300:
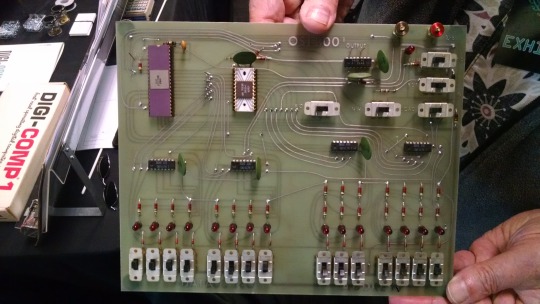
This one I saw at VCF West back in 2018 illustrates just how limited of a design it is. 128 bytes of RAM, no ROM, no serial -- just you, the CPU, and toggle switches and LEDs to learn the CPU. I was inspired the first time I saw one in 2015 at VCF East, which is probably when this whole project got set in motion.
Later that year I bought a kit for a miniature replica OSI-300 made by Christopher Bachman, and learned really quickly how limited the design philosophy for this particular front panel was. It was a major pain in the ass to use (to be clear, that's by OSI's choice, not any fault of Christopher in his implementation)

So... I designed my own. Took awhile, but that's the core of what the Cactus is: my attempt at experiencing the 1970s homebrew scene by building the computer I would have wanted at the time. Over half of the logic in the Cactus is just to run the front panel's state machine, so you can examine and modify the contents of memory without bothering the 6502. I added in all of the things I liked from more advanced front panels I had encountered, and designed it to my liking.
Here's the original front panel, accompanying logic, and backplane connected to the modern single board computer (SBC) version of the machine:

And here's the new Cactus SBC working with the new front panel PCB, which combines the logic, physical switch mountings, and cabling harnesses into a single printed circuit board.
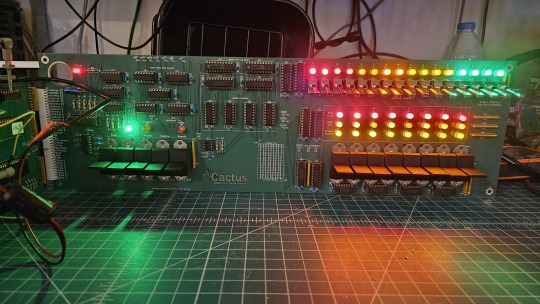
So, what can you do with it? Pretty much the same things I do already with other contemporary 1970s computers: play around in BASIC, fire up the occasional game, and tinker with it.
I've got no permanent storage designed for the Cactus as yet, it's been one of those "eventually" things. The good news is that a variety of software can be ported to the hardware without too much trouble for an experienced hobbyist. A friend of mine wrote a game called ZNEK in 6502 assembly which runs from a terminal:

Right now, you have to either toggle in machine programs from the front panel from scratch, burn a custom ROM, or connect it to a serial terminal to gain access to its more advanced features:

Here's it booted into OSI BASIC, but I have also added in a modern descendant of Steve Wozniak's WOZMON software for when I need to do lower level debugging.
I've also got a video card now, based on the OSI-440. I have yet to implement a keyboard, or modify BASIC to use the video board instead of the serial connection. Even if I did, screen resolution is pretty limited at 24x24 characters on screen at once. Still, I'm working on that...


Anyway, I hope that answers your question. Check the tags below to see the whole process stretching back to 2017 if you're curious to learn more of the project's history. I'm also happy to answer any more questions you might have about the project.
267 notes
·
View notes
Text

Hermit-a-Day May, day 17: EthosLab. Today's style/medium is the mobile game Crossy Road. I'm gonna be honest, this was my backup style and mostly a joke, but my first choice was not working out and I didn't have time to fiddle with it. Crossy Road is essentially just a modern Frogger, so it fits what Etho's been up to this season (at least, I think--I've never actually played the game). Details and references under the read more!
Materials/software: Blockbench for most of it; I exported the image to Krita to add a background and clean up the details.
References: I primarily based Etho's features on two of the developer insert characters from the Australian update, Ben Weatherall and Andy Sum. I borrowed the play button from a screenshot of the game and hand-wrote the font pixel by pixel, referencing several different screenshots.


This was my first time using Blockbench and I went in completely blind, but it was actually pretty intuitive! I was pleasantly surprised. I'm realizing now that I made Etho's legs a bit too short but it's fiiiine. I think that's... about all I have to say, actually. This piece was mostly a "do it for the meme" kind of thing, but I am proud of how much it looks like the source material.
#hermitaday#hermit a day may#hermitcraft#hermitcraft fanart#ethoslab#ethoslab fanart#...technically#my art
269 notes
·
View notes