#Extensions used by Hackers
Explore tagged Tumblr posts
Text

madame ginko i got from @setzeri
#storing for potential pfp use#shin megami tensei#soul hackers#i was thinking about her japanese voice#i have not played soul hackers yet i know it extensively#because i have a friend who's very much into SMT
240 notes
·
View notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
UPDATE: As of 25/04/2025, 4chan is back up and running again. This post and its addendum will be kept as is, and will no longer be updated unless it goes back down again. If you were on /ghost/, it was a pleasure shitposting with you.
All right, I know no one gives a shit, but let me give you a recounting of the fall of 4chan from the perspective of someone who was there and has been lurking both 4chan and tumblr for a few years now.
I'll try to provide as much context as I can, but a lot of images were either lost or im too lazy to look for them in the +5000 reply thread in soyjak party.
Anyways, info below:
So, necessary context: a few years back, 4chan had a board called /qa/, which if you know little about the page, you may think every board is like /b/ or /pol/, which means a containment cess pool of grifters, (you) baiters, incels, and other deranged individuals. The thing is, /qa/ was somehow worse. The entire board was plagued and infested with soyjack edits, board culture was a nuclear disaster, anons were incredibly hostile in there, you know the drill, the big bad 4chan, but this time its actually true.
One day, moderation deleted /qa/, anons that posted there got mad, tried to raid other boards, failed, and then moved on to an altchan called soyjack party, which entire purpose you can guess from its name alone.
Apparently, the boards that allow pdf uploads (paper and origami, for example) didn't check if the uploaded file was actually a pdf file, so postscript files could be used to get access. This is as far as my understanding of web backend goes, sorry.
The hacker claims to have been working on this since 2021, and that he had access since about a year ago, but was recopilating data.
Now, what actually happened when the hack ocurred? Well, a banner of miku dancing with a song that played automatically was placed on top of every board, with the text "/QA/ IS BACK", this was possible because apparently no board was ever deleted, they were just hidden from the public.
A thread was then made on soyjack party, claiming authorship over the hack, and shit went south from there. Anons went en masse to talk there, a lot of weird discussion happened, the thread got the bump limit removed and got pinned, more than 5k posts were amassed on the first night alone. Keep in mind this happened at about 8 pm and most of the stuff went on through midnight.
So, the hacker leaked some things, first of all, the html files for the entirety of /j/ and the email address for every moderation member (important note: the pressence of .gov mails was disproven by the hacker themselves, so i guess there were never any feds), what is /j/? the board exclusive for jannies and moderators to discuss actions taken on the website regarding spam, ban evaders, threads spiraling out of control, etc. Among other things, some of the inner workings of 4chan got revealed, such as the web extension for jannies that allows them to do their job easily, how reports are handled, and other stuff. (Anecdotically, some guy got permabanned for calling anons jews or n-words over a 100 times in the same few threads)
Then, the source code got leaked. Important to say, the hacker removed the part of the source code related to the captcha, as to not facilitate bot attacks on the future, and all information related to email verification or 4chan pass users information also got removed, so all in all users are safe.
What was found on the sourcecode? That it was old, mostly. Most boards used code that hasn't been updated since about 2016, and /flash/ used the exact same code from when it was created back on 2011.
From there, desuarchive, a site that archives threads that die from bump limit, opened a dragon ball general on ghost mode, and thus began what later got called /ghost/, a solely text based thread with well over 20k replies as of right now, where a fraction of the 4chan population took refuge and is currently discussing random things with no particular topic. Kinda hard to read, but its comfy.
What does this mean for other sites? Not a lot, really. A lot of anons already crossposted in 4chan and tumblr already, and the ones that din't most likely wont come here. Some of the bigger/most dedicated groups, like /vt/, migrated to other boards. Various altchans are trying/tried to catch some of the flock of users that got lost, but i doubt it will get anywhere, since soyjak party for example was struggling with just the influx of users that came for the hack thread given its poor infrastructure. Kiwifarms saw a surge of new accounts apparently, but a lot of anons kinda loathe the idea of having to register, so theres that.
Smaller communities, such as generals that didn't get a lot of traffic, or boards on the slower end (say, /ic/, /lit/, etc) will probably vanish or disseminate until (or if) 4chan comes back up. I'd say give it a month, don't get your hopes up whether you want it to stay dead or want it to come back.
Given how many anons are staying on places like /ghost/ or other similar archives with the same ghost posting feature, i doubt it will be as bad as people are making it sound. Besides, the communities that are most likely to migrate to places like tumblr are either /co/, /vg/ or /lgbt/ refugees, which aren't THAT bad. Not every board was like the main cesspools (/b/, /r9k/, /pol/).
From now on, either 4chan comes back up in a few weeks (somewhere between 2 weeks to a month is expected), altchans capture the migrating anons, or a brand new imageboard rises from the ashes to become the new go-to site for old 4chan posters.
In conclusion, nothing ever happens, but also don't worry, chances are this won't affect tumblr in the slightest. If it does, you can cash in your "you were wrong" ticket whenever you want, i'll take the L.
As a footnote, keep in mind: NO users were compromised, if you ever posted there and are worried for your safety, physical or digital, you are safe.
Edit: Forgot to add, if you are a 4chan refugee, im BEGGING you to dm me and tell what board you were from and where are you migrating, if at all.
487 notes
·
View notes
Text
My earliest memory of 4chan was sitting up late at night, typing its URL into my browser, and scrolling through a thread of LOLcat memes, which were brand-new at the time.
Back then a photoshop of a cat saying "I can has cheezburger" or an image of an owl saying “ORLY?” was, without question, the funniest thing my 14-year-old brain had ever laid eyes on. So much so, I woke my dad up by laughing too hard and had to tell him that I was scrolling through pictures of cats at 2 in the morning. Later, I would become intimately familiar with the site’s much more nefarious tendencies.
It's strange to look back at 4chan, apparently wiped off the internet entirely last week by hackers from a rival message board, and think about how many different websites it was over its more than two decades online. What began as a hub for internet culture and an anonymous way station for the internet's anarchic true believers devolved over the years into a fan club for mass shooters, the central node of Gamergate, and the beating heart of far-right fascism around the world—a virus that infected every facet of our lives, from the slang we use to the politicians we vote for. But the site itself had been frozen in amber since the George W. Bush administration.
It is likely that there will never be a site like 4chan again—which is, likely, a very good thing. But it had also essentially already succeeded at its core project: chewing up the world and spitting it back out in its own image. Everything—from X to Facebook to YouTube—now sort of feels like 4chan. Which makes you wonder why it even needed to still exist.
"The novelty of a website devoted to shock and gore, and the rebelliousness inherent in it, dies when your opinions become the official policy of the world's five or so richest people and the government of the United States," the Onion CEO and former extremism reporter Ben Collins tells WIRED. “Like any ostensibly nihilist cultural phenomenon, it inherently dies if that phenomenon itself becomes The Man.”
My first experience with the more toxic side of the site came several years after my LOLcat all-nighter, when I was in college. I was a big Tumblr user—all my friends were on there—and for about a year or so, our corner of the platform felt like an extension of the house parties we would throw. That cozy vibe came crashing down for me when I got doxed the summer going into my senior year. Someone made a “hate blog” for me—one of the first times I felt the dark presence of an anonymous stranger’s digital ire, and posted my phone number on 4chan.
They played a prank that was popular on the site at the time, writing in a thread that my phone number was for a GameStop store that had a copy of the ultra-rare video game Battletoads. I received no less than 250 phone calls over the next 48 hours asking if I had a copy of the game.
Many of the 4chan users that called me mid-Battletoad attack left messages. I listened to all of them. A pattern quickly emerged: young men, clearly nervous to even leave a message, trying to harass a stranger for, seemingly, the hell of it. Those voicemails have never left me in the 15 years I've spent covering 4chan as a journalist.
I had a front-row seat to the way those timid men morphed into the violent, seething underbelly of the internet. The throbbing engine of reactionary hatred that resented everything and everyone simply because resentment was the only language its users knew how to speak. I traveled the world in the 2010s, tracing 4chan’s impact on global democracy. I followed it to France, Germany, Japan, and Brazil as 4chan's users became increasingly convinced that they could take over the planet through racist memes, far-right populism, and cyberbullying. And, in a way, they did. But the ubiquity of 4chan culture ended up being an oddly Pyrrhic victory for the site itself.
Collins, like me, closely followed 4chan's rise in the 2010s from internet backwater to unofficial propaganda organ of the Trump administration. As he sees it, once Elon Musk bought Twitter in 2022 there was really no point to 4chan anymore. Why hide behind anonymity if a billionaire lets you post the same kind of extremist content under your real name and even pays you for it?
4chan’s “user base just moved into a bigger ballpark and started immediately impacting American life and policy," Collins says. "Twitter became 4chan, then the 4chanified Twitter became the United States government. Its usefulness as an ammo dump in the culture war was diminished when they were saying things you would now hear every day on Twitter, then six months later out of the mouths of an administration official."
But understanding how 4chan went from the home of cat memes to a true internet bogeyman requires an understanding of how the site actually worked. Its features were often overlooked amid all the conversations about the site's political influence, but I'd argue they were equally, if not more, important.
4chan was founded by Christopher “Moot” Poole when he was 15. A regular user on slightly less anarchic comedy site Something Awful, Poole created a spinoff site for a message board there called “Anime Death Tentacle Rape Whorehouse.” Poole was a fan of the Japanese message board 2chan, or Futaba Channel, and wanted to give Western anime fans their own version, so he poorly translated the site's code and promoted his new site, 4chan, to Something Awful's anime community. Several core features were ported over in the process.
4chan users were anonymous, threads weren't permanent and would time out or "404" after a period of inactivity, and there were dozens of sub-boards you could post to. That unique combination of ephemerality, anonymity, and organized chaos proved to be a potent mix, immediately creating a race-to-the-bottom gutter culture unlike anything else on the web. The dark end point of the techno-utopianism that built the internet. On 4chan you were no one, and nothing you did mattered unless it was so shocking, so repulsive, so hateful that someone else noticed and decided to screenshot it before it disappeared into the digital ether.
"The iconic memes that came out of 4chan are because people took the time to save it, you know? And the fact that nobody predicted, nobody could predict or control what was saved or what wasn't saved, I think, is really, really fascinating," Cates Holderness, Tumblr's former head of editorial, tells WIRED.
Still, 4chan was more complicated than it looked from the outside. The site was organized into dozens of smaller sections, everything from comics to cooking to video games to, of course, pornography. Holderness says she learned to make bread during the pandemic thanks to 4chan's cooking board. (Full disclosure: I introduced Holderness to 4chan way back in 2012.)
"When I switched to sourdough, I got really good pointers," she says.
Holderness calls 4chan the internet's “Wild West” and says its demise this month felt appropriate in a way. The chaos that defined 4chan, both the good and the very, very bad, has largely been paved over by corporate platforms and their algorithms now.
Our feeds deliver us content; we don't have to hunt for it. We don't have to sit in front of a computer refreshing a page to find out whether we're getting a new cat meme or a new manifesto. The humanness of that era of the web, now that 4chan is gone, is likely never coming back. And we'll eventually find out if that's a good thing or a bad thing.
"The snippets that we have of what 4chan was—it's all skewed,” Holderness says. “There is no record. There's no record that can ever encapsulate what 4chan was."
161 notes
·
View notes
Text
Cleantech has an enshittification problem

On July 14, I'm giving the closing keynote for the fifteenth HACKERS ON PLANET EARTH, in QUEENS, NY. Happy Bastille Day! On July 20, I'm appearing in CHICAGO at Exile in Bookville.

EVs won't save the planet. Ultimately, the material bill for billions of individual vehicles and the unavoidable geometry of more cars-more traffic-more roads-greater distances-more cars dictate that the future of our cities and planet requires public transit – lots of it.
But no matter how much public transit we install, there's always going to be some personal vehicles on the road, and not just bikes, ebikes and scooters. Between deliveries, accessibility, and stubbornly low-density regions, there's going to be a lot of cars, vans and trucks on the road for the foreseeable future, and these should be electric.
Beyond that irreducible minimum of personal vehicles, there's the fact that individuals can't install their own public transit system; in places that lack the political will or means to create working transit, EVs are a way for people to significantly reduce their personal emissions.
In policy circles, EV adoption is treated as a logistical and financial issue, so governments have focused on making EVs affordable and increasing the density of charging stations. As an EV owner, I can affirm that affordability and logistics were important concerns when we were shopping for a car.
But there's a third EV problem that is almost entirely off policy radar: enshittification.
An EV is a rolling computer in a fancy case with a squishy person inside of it. While this can sound scary, there are lots of cool implications for this. For example, your EV could download your local power company's tariff schedule and preferentially charge itself when the rates are lowest; they could also coordinate with the utility to reduce charging when loads are peaking. You can start them with your phone. Your repair technician can run extensive remote diagnostics on them and help you solve many problems from the road. New features can be delivered over the air.
That's just for starters, but there's so much more in the future. After all, the signal virtue of a digital computer is its flexibility. The only computer we know how to make is the Turing complete, universal, Von Neumann machine, which can run every valid program. If a feature is computationally tractable – from automated parallel parking to advanced collision prevention – it can run on a car.
The problem is that this digital flexibility presents a moral hazard to EV manufacturers. EVs are designed to make any kind of unauthorized, owner-selected modification into an IP rights violation ("IP" in this case is "any law that lets me control the conduct of my customers or competitors"):
https://locusmag.com/2020/09/cory-doctorow-ip/
EVs are also designed so that the manufacturer can unilaterally exert control over them or alter their operation. EVs – even more than conventional vehicles – are designed to be remotely killswitched in order to help manufacturers and dealers pressure people into paying their car notes on time:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
Manufacturers can reach into your car and change how much of your battery you can access:
https://pluralistic.net/2023/07/28/edison-not-tesla/#demon-haunted-world
They can lock your car and have it send its location to a repo man, then greet him by blinking its lights, honking its horn, and pulling out of its parking space:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
And of course, they can detect when you've asked independent mechanic to service your car and then punish you by degrading its functionality:
https://www.repairerdrivennews.com/2024/06/26/two-of-eight-claims-in-tesla-anti-trust-lawsuit-will-move-forward/
This is "twiddling" – unilaterally and irreversibly altering the functionality of a product or service, secure in the knowledge that IP law will prevent anyone from twiddling back by restoring the gadget to a preferred configuration:
https://pluralistic.net/2023/02/19/twiddler/
The thing is, for an EV, twiddling is the best case scenario. As bad as it is for the company that made your EV to change how it works whenever they feel like picking your pocket, that's infinitely preferable to the manufacturer going bankrupt and bricking your car.
That's what just happened to owners of Fisker EVs, cars that cost $40-70k. Cars are long-term purchases. An EV should last 12-20 years, or even longer if you pay to swap the battery pack. Fisker was founded in 2016 and shipped its first Ocean SUV in 2023. The company is now bankrupt:
https://insideevs.com/news/723669/fisker-inc-bankruptcy-chapter-11-official/
Fisker called its vehicles "software-based cars" and they weren't kidding. Without continuous software updates and server access, those Fisker Ocean SUVs are turning into bricks. What's more, the company designed the car from the ground up to make any kind of independent service and support into a felony, by wrapping the whole thing in overlapping layers of IP. That means that no one can step in with a module that jailbreaks the Fisker and drops in an alternative firmware that will keep the fleet rolling.
This is the third EV risk – not just finance, not just charger infrastructure, but the possibility that any whizzy, cool new EV company will go bust and brick your $70k cleantech investment, irreversibly transforming your car into 5,500 lb worth of e-waste.
This confers a huge advantage onto the big automakers like VW, Kia, Ford, etc. Tesla gets a pass, too, because it achieved critical mass before people started to wise up to the risk of twiddling and bricking. If you're making a serious investment in a product you expect to use for 20 years, are you really gonna buy it from a two-year old startup with six months' capital in the bank?
The incumbency advantage here means that the big automakers won't have any reason to sink a lot of money into R&D, because they won't have to worry about hungry startups with cool new ideas eating their lunches. They can maintain the cozy cartel that has seen cars stagnate for decades, with the majority of "innovation" taking the form of shitty, extractive and ill-starred ideas like touchscreen controls and an accelerator pedal that you have to rent by the month:
https://www.theverge.com/2022/11/23/23474969/mercedes-car-subscription-faster-acceleration-feature-price
Put that way, it's clear that this isn't an EV problem, it's a cleantech problem. Cleantech has all the problems of EVs: it requires a large capital expenditure, it will be "smart," and it is expected to last for decades. That's rooftop solar, heat-pumps, smart thermostat sensor arrays, and home storage batteries.
And just as with EVs, policymakers have focused on infrastructure and affordability without paying any attention to the enshittification risks. Your rooftop solar will likely be controlled via a Solaredge box – a terrible technology that stops working if it can't reach the internet for a protracted period (that's right, your home solar stops working if the grid fails!).
I found this out the hard way during the covid lockdowns, when Solaredge terminated its 3G cellular contract and notified me that I would have to replace the modem in my system or it would stop working. This was at the height of the supply-chain crisis and there was a long waiting list for any replacement modems, with wifi cards (that used your home internet rather than a cellular connection) completely sold out for most of a year.
There are good reasons to connect rooftop solar arrays to the internet – it's not just so that Solaredge can enshittify my service. Solar arrays that coordinate with the grid can make it much easier and safer to manage a grid that was designed for centralized power production and is being retrofitted for distributed generation, one roof at a time.
But when the imperatives of extraction and efficiency go to war, extraction always wins. After all, the Solaredge system is already in place and solar installers are largely ignorant of, and indifferent to, the reasons that a homeowner might want to directly control and monitor their system via local controls that don't roundtrip through the cloud.
Somewhere in the hindbrain of any prospective solar purchaser is the experience with bricked and enshittified "smart" gadgets, and the knowledge that anything they buy from a cool startup with lots of great ideas for improving production, monitoring, and/or costs poses the risk of having your 20 year investment bricked after just a few years – and, thanks to the extractive imperative, no one will be able to step in and restore your ex-solar array to good working order.
I make the majority of my living from books, which means that my pay is very "lumpy" – I get large sums when I publish a book and very little in between. For many years, I've used these payments to make big purchases, rather than financing them over long periods where I can't predict my income. We've used my book payments to put in solar, then an induction stove, then a battery. We used one to buy out the lease on our EV. And just a month ago, we used the money from my upcoming Enshittification book to put in a heat pump (with enough left over to pay for a pair of long-overdue cataract surgeries, scheduled for the fall).
When we started shopping for heat pumps, it was clear that this was a very exciting sector. First of all, heat pumps are kind of magic, so efficient and effective it's almost surreal. But beyond the basic tech – which has been around since the late 1940s – there is a vast ferment of cool digital features coming from exciting and innovative startups.
By nature, I'm the kid of person who likes these digital features. I started out as a computer programmer, and while I haven't written production code since the previous millennium, I've been in and around the tech industry for my whole adult life. But when it came time to buy a heat-pump – an investment that I expected to last for 20 years or more – there was no way I was going to buy one of these cool new digitally enhanced pumps, no matter how much the reviewers loved them. Sure, they'd work well, but it's precisely because I'm so knowledgeable about high tech that I could see that they would fail very, very badly.
You may think EVs are bullshit, and they are – though there will always be room for some personal vehicles, and it's better for people in transit deserts to drive EVs than gas-guzzlers. You may think rooftop solar is a dead-end and be all-in on utility scale solar (I think we need both, especially given the grid-disrupting extreme climate events on our horizon). But there's still a wide range of cleantech – induction tops, heat pumps, smart thermostats – that are capital intensive, have a long duty cycle, and have good reasons to be digitized and networked.
Take home storage batteries: your utility can push its rate card to your battery every time they change their prices, and your battery can use that information to decide when to let your house tap into the grid, and when to switch over to powering your home with the solar you've stored up during the day. This is a very old and proven pattern in tech: the old Fidonet BBS network used a version of this, with each BBS timing its calls to other nodes to coincide with the cheapest long-distance rates, so that messages for distant systems could be passed on:
https://en.wikipedia.org/wiki/FidoNet
Cleantech is a very dynamic sector, even if its triumphs are largely unheralded. There's a quiet revolution underway in generation, storage and transmission of renewable power, and a complimentary revolution in power-consumption in vehicles and homes:
https://pluralistic.net/2024/06/12/s-curve/#anything-that-cant-go-on-forever-eventually-stops
But cleantech is too important to leave to the incumbents, who are addicted to enshittification and planned obsolescence. These giant, financialized firms lack the discipline and culture to make products that have the features – and cost savings – to make them appealing to the very wide range of buyers who must transition as soon as possible, for the sake of the very planet.
It's not enough for our policymakers to focus on financing and infrastructure barriers to cleantech adoption. We also need a policy-level response to enshittification.
Ideally, every cleantech device would be designed so that it was impossible to enshittify – which would also make it impossible to brick:
Based on free software (best), or with source code escrowed with a trustee who must release the code if the company enters administration (distant second-best);
All patents in a royalty-free patent-pool (best); or in a trust that will release them into a royalty-free pool if the company enters administration (distant second-best);
No parts-pairing or other DRM permitted (best); or with parts-pairing utilities available to all parties on a reasonable and non-discriminatory basis (distant second-best);
All diagnostic and error codes in the public domain, with all codes in the clear within the device (best); or with decoding utilities available on demand to all comers on a reasonable and non-discriminatory basis (distant second-best).
There's an obvious business objection to this: it will reduce investment in innovative cleantech because investors will perceive these restrictions as limits on the expected profits of their portfolio companies. It's true: these measures are designed to prevent rent-extraction and other enshittificatory practices by cleantech companies, and to the extent that investors are counting on enshittification rents, this might prevent them from investing.
But that has to be balanced against the way that a general prohibition on enshittificatory practices will inspire consumer confidence in innovative and novel cleantech products, because buyers will know that their investments will be protected over the whole expected lifespan of the product, even if the startup goes bust (nearly every startup goes bust). These measures mean that a company with a cool product will have a much larger customer-base to sell to. Those additional sales more than offset the loss of expected revenue from cheating and screwing your customers by twiddling them to death.
There's also an obvious legal objection to this: creating these policies will require a huge amount of action from Congress and the executive branch, a whole whack of new rules and laws to make them happen, and each will attract court-challenges.
That's also true, though it shouldn't stop us from trying to get legal reforms. As a matter of public policy, it's terrible and fucked up that companies can enshittify the things we buy and leave us with no remedy.
However, we don't have to wait for legal reform to make this work. We can take a shortcut with procurement – the things governments buy with public money. The feds, the states and localities buy a lot of cleantech: for public facilities, for public housing, for public use. Prudent public policy dictates that governments should refuse to buy any tech unless it is designed to be enshittification-resistant.
This is an old and honorable tradition in policymaking. Lincoln insisted that the rifles he bought for the Union Army come with interoperable tooling and ammo, for obvious reasons. No one wants to be the Commander in Chief who shows up on the battlefield and says, "Sorry, boys, war's postponed, our sole supplier decided to stop making ammunition."
By creating a market for enshittification-proof cleantech, governments can ensure that the public always has the option of buying an EV that can't be bricked even if the maker goes bust, a heat-pump whose digital features can be replaced or maintained by a third party of your choosing, a solar controller that coordinates with the grid in ways that serve their owners – not the manufacturers' shareholders.
We're going to have to change a lot to survive the coming years. Sure, there's a lot of scary ways that things can go wrong, but there's plenty about our world that should change, and plenty of ways those changes could be for the better. It's not enough for policymakers to focus on ensuring that we can afford to buy whatever badly thought-through, extractive tech the biggest companies want to foist on us – we also need a focus on making cleantech fit for purpose, truly smart, reliable and resilient.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/26/unplanned-obsolescence/#better-micetraps

Image: 臺灣���寫真上色 (modified) https://commons.wikimedia.org/wiki/File:Raid_on_Kagi_City_1945.jpg
Grendelkhan (modified) https://commons.wikimedia.org/wiki/File:Ground_mounted_solar_panels.gk.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#procurement#cleantech#evs#solar#solarpunk#policy#copyfight#copyright#felony contempt of business model#floss#free software#open source#oss#dmca 1201#interoperability#adversarial interoperability#solarization#electrification#enshittification#innovation#incumbency#climate#climate emergency
433 notes
·
View notes
Text
Astro Observations #1 -
Virgo Venus: Beauty & Desirability



I've noticed in virgo venus people (celebrities mostly), they're usually highly desirable or desirability is a big part of their image/career despite their venus being in a debilitated sign.
for example: vinnie hacker, bella hadid, nct jaemin, kim kardashian, kylie jenner, charlize theron, i could go on but my point is on some level their fame is tied to their looks for better or worse.



virgo's general attention to detail/reliance on routine/tendency to prioritise bodily health, in a planet like venus usually makes the native acutely aware of your appearance and how it may/may not match up conventionally.
and therefore leads to knowing exactly which details to tweak to look better, paired with rigorous upkeep/routine, usually leads to an enhanced appearance that comes through effort, rather than the effortless beauty that comes with a strong/well-placed venus.
this could be anything from an extreme beauty regimen to a strict gym routine or regularly getting procedures done or even just learning how to do makeup perfectly for your features.
in bella hadid for example, growing up as the undesirable sister and then becoming a supermodel, kim's history with plastic surgery procedures and using it to launch her empire, or kylie jenner getting lip filler and that being the start of her brand, or vinnie hacker mentioning he used thirst traps to kickstart his career, even jaemin's dramatic bodily transformation as a result of his extensive gym routine that he's upkept regularly even after doing 3 hour concerts.
this is like my first ever post in this tumblr so anyyyy feedback on posts like this would be really helpful moving forward. I've wanted to start an astrology blog for some time and im still tweaking the details but glad i could finally begin with it and share what i know :D
#astro notes#virgo venus#astro observations#astrology#astroblr#bella hadid#jaemin#nct dream#vinnie hacker
466 notes
·
View notes
Note
another one from suspiciously green anon i did like, extensive research on elliot here are some headcanons about him and his business!! -Contrary to popular belief, he is EXTREMELY well paid, his average wage being hundreds of bucks an hour. Especially because his dad is the manager. -Builder Brother's pizza is, in fact, a family owned pizza place. Like everyone in the family has worked at it at some point -Mia, the youngest of the family and also Elliot's younger sister, is going to work here some day. She's not complaining because it'll make good money -She'd like to be a chef, specifically! -Ironically, the majority of the family is lactose intolerant -The reason the place is so wealthy is because it's like a historical landmark, everyone loves WAAPP! -Humility runs in the family, and the business continues to be a humble pizza chain. They'd always decline collabs from larger brands in their early days, look at them now! -Builderman is considered a family friend toward the Builders (Mr. Builder, Elliot Builder, ykyk) -The Pizza place has a flexible way of getting employees, letting pretty much anyone work there whenever. Is it smart? Not really, but they have more than enough money to insure absolute safety. -Elliot continues to have low self worth, though I believe this would be because of past problems in school that went untreated and were never brought up due to Elliot believing they would burden his peers and family. -I don't mind angry Elliot enjoyers, pop off! But personally I think he'd be more like Spongebob. He pretends to be happy all the time, and will explode whenever he gets TOO angry (he will drop the f bomb on everybody in the cabin, even the killers if they're there). -It's easy to tell when he doesn't mean what he says because he instantly apologizes to those he didn't mean to insult once he gets his emotions in line. -He never apologizes to Twotime. -He does eventually apologize to 007n7, however. I'd say this is because he notices 007n7 is trying to genuinely be better but he's shaken up incredibly bad. Elliot can sort of empathize with 007n7, because he was also ostracized at some point. This was in school, however. oh yeah also some 007n7 headcanons -Everyone eventually forgives him because I'm allowed to be happy. The list of forgiveness goes as follows! I would include survivors not ingame yet but idk about their personalities -Guest-1337 (EXTREMELY understanding and sympathetic, i've watched the last guest and I don't think he's as stern as he is in the game. Maybe a bit shaken up after the grenade (spoilers he survived in the actual movie after being tackled by an ally into a pit), but he tries to be nice to everyone. -Chance (He's just a chill guy who lowkey don't gaf, he can see 007n7 is trying to change for the better) -Builderman (He's pretty understanding despite his status as the big man of Roblox. He knows that people can change, and although hesitant, warmed up to 007n7.) -Noob (They're a bit naive, but that's okay in this situation) -Two-Time (Two-time thinks 007n7 got rebirthed or something, and is hypervigilant about how 007n7 uses his '2nd chance'. -Elliot (After being afraid for a long time, grew to forgive 007n7 after putting himself in his shoes. Hackers are usually just very foolish young people, 007n7 grew up and he had to carry on with the guilt for THAT long? Let alone he got ostracized, that's crazy!!) -Shedletsky (He is stubborn. Like really fucking stubborn he REFUSED to believe 007n7 could change because he thinks all hackers are messed up. But, as everyone grew to forgive him he became neutral with 007n7. He still keeps a watchful eye on 007n7 though, if he fucks up again he is going to flip out!) roblox autism back at it again! -suspiciously green anon, the autismer
Another peak post from the suspiciously green anon. We love to see it.
#forsaken headcanons#forsaken#forsaken roblox#roblox forsaken#suspiciously green anon#elliot forsaken#007n7 forsaken#guest 1337 forsaken#chance forsaken#builderman forsaken#noob forsaken#two time forsaken#shedletsky forsaken
76 notes
·
View notes
Text
007n7 and C00lkid Block Tales AU!

Cross posted on Ao3 under the same name as my Tumblr account!!!
This is going to be a bit long. (Some things will change once Demo 4 comes out)
007n7
Backstory:
He's still a hacker, a really dangerous and powerful one. He mastered code manipulation and even Builderman had trouble with banning him. After a really close call with banhammer, 007n7 decided that he needs someone who will go to front lines for him, so he could still do the hacking without risking being banned. So he got to work and after some time he created C00lkid using android body he created and fragment of his own code (more specifically a part of code that includes memories from his youth where he started taking hacking seriously)
With C00lkid he made a lot hacking attacks, which resulted in him being feared across whole Robloxia. He got banned once, by Builderman and ended up in Banlands, but thanks C00lkid's help he ended up escaping. He decided to lay low for a while and ended up moving to small village [in the area where Demo 4 will take place].
More info:
- He's more emotionally distant than his Forsaken version, and doesn't regret anything he done in the past. He feels proud of his accomplishments.
- He doesn't view C00lkid as actual person, just a bunch of code in android body/ a tool that helps him hack. Despite this he still allows C00lkid to call him dad.
- He has a control panel for C00lkid, where he can also read the mood of his creation or any thought C00lkid sends him, is able to access his point of view and is able to control him (he rarely uses the last option)
- Believes that relationship are nothing more than a distraction and a obstacle.
- Is focused on his work, despite being in hiding from Builderman he hadn't stopped experimenting with the code. But he does it in unsuspicious amount.
- After Builderman went missing (time when game events take place) he became a bit more open with his hacking. Which resulted in getting Shedletsky's attention, who sent Player to investigate [this happens after events of Demo 4]
- 007n7 and Shedletsky came to understanding/ created an alliance. 007n7 can continue his experiments but the bigger ones need to be reported and must have someone trusted by Shed to supervise.
- At first 007n7 was reluctant but with time he realised that this alliance is beneficial for him. And now he legally does illegal things.
- Works as cashier in local market.
- With time people started trusting him more and now he sometimes helps around village, uses his hacking skills in different way than before.
- After spending some more time with Shedletsky and Player he slowly came to conclusion that C00lkid has, in fact, a human traits and he might've been too harsh to him. And he slowly started becoming a bit nicer to C00lkid, although he still has moments where he comes back to old ways.
C00lkid
Backstory:
He's an android created by 007n7 with his sole purpose being a extension of his C00lgui and someone to take blame for his hacking attacks. Because 007n7's code that gave him sentience was from his youth, C00lkid's mental age is around 12 years old. When 007n7 got banned in front of him. C00lkid escaped and since his Ai/code has the ability to analyse and adapt he was able to hack into the Banlands to save his father.
When they started over in the village [Demo 4 area] C00lkid started experiencing being a 'normal' child and tried to make friends, but because of his past everyone stayed away. His dad also weren't a good emotional support, but he just assumed it's normal.
After events of Demo 4, Player is the first one who treats C00lkid like actual child and not deadly hacker or line of code. Which resulted with other village kids and adults to become more open.
More info:
- C00lkid believes everything that his dad says and thinks that there's nothing wrong with the way he treats him.
- He knows he's artificial life and he is okay with this. He uses it to his advantage.
- Because his code is able to self learn, he's incredibly smart. And uses this to prank people. (He's a mischievous little guy). He especially enjoys changing people's clothes into Team C00lkid all red 'uniform'.
- Loves helping out around village, with his unnatural strength and hacking skills people learned to appreciate him. (He's more liked than 007n7)
- His power is mostly locked away now, so he incidentally won't cause a disaster.
- C00lkid begged Player to teach him how to sword fight, after being approved by Shedletsky they started meeting up and train with wooden swords.
- He meet Red and Blue Noobs, when Player was babysitting them and they became friends (especially him and Red). Let's just say that Player had a eventful day.
- C00lkid is on Hatred's hit list. Not even Player knows why.
- Cherishes every bit of attention/care he gets from his dad. And was overjoyed when he started to give him more attention.
- Has trust issues when it comes to anything related to Builderman and Banhammer (because of his dad getting banned and what he heard from Players rant about Hatred disguising as Builderman)
- Enjoys copying/mimicing people.
- Want's to become champion of Swords Fights On The Heights
#forsaken roblox#007n7 forsaken#c00lk1dd forsaken#roblox 007n7#c00lkidd#roblox game#roblox block tales#block tales#blocktales#player block tales#shedletsky block tales#builderman block tales#007n7 fanart#c00lkid fanart#block tales au
94 notes
·
View notes
Text
Some ways to avoid generative AI in web searches
Our web searches are being filled with more and more AI-generated slop. GenAI creates misinformation that can be difficult to tell apart from the correct answer to whatever question you're looking up. GenAI mixes things up that have similar names. In one example that is especially easy to recognize, genAI has thought that a baseball team and the bird that it was named after must both be the same creature, with a bizarre combination of their eating habits and behaviors. This mistake still happens with specialized topics that could be harder for you to recognize unless if you're already very familiar with the topic in question. GenAI also makes up fake sources and facts out of thin air, and you can't tell until you try to find them somewhere else. The tech is more like advanced predictive text than something capable of research or reasoning, even though it can look enough like it that it can fool you if you don't know how to spot its mistakes.
Not only are the results of genAI unreliable, the source texts and images that they’re based on were used without permission. Sometimes they aren't modified enough to avoid plagiarism, but it's worse than that. Source images have turned out to be private medical photos and intimate personal photos that hackers had stolen and leaked to harass the people in the photos. Another reason why this technology is unethical is that each genAI query has such a high energy cost that it's significantly harmful to the environment, contributing to the climate crisis.
Here are some things that you can do when you use Google, DuckDuckGo, or other conventional general web search engines:
To turn off Google's AI Overview, set "web" as default. Here's how to do that on your devices and web browsers.
Add this string to any web search to only show results from before the genAI fad. Before:2021
Install the web browser extension uBlacklist. You give it a list of web addresses to not show you in your web searches anymore. Other people maintain lists for it that you can subscribe to so that you won’t see certain types of results in your web searches. Follow the instructions in Laylavish’s Huge AI Blocklist to subscribe to that list which will rid your web search results of AI-generated pages or images.
Since genAI slop is getting to be such a big problem on them, use alternatives to conventional general web search engines some of the time:
Use a specialized search engine instead of a general one. For example, if you only wanted to find a particular science article, there are specialized search engines that only look for those. The blog post "Skip Google for Research" has a list of specialized search engines for academics.
GenAI is notoriously bad at math because that’s too far outside the scope it was designed for: advanced predictive text. In any case, genAI is overpowered for math that is easy for computers to do. If you want to use a very advanced calculator, or even ask a math question in natural language, use Wolfram Alpha.
For questions about how to do things, look them up in WikiHow, the Youtube channel Dad, How Do I? or The Ultimate Manuals Library.
You can search within Wikipedia, but unfortunately vandals have been putting machine-generated falsehoods into it, as well as genAI images. To avoid this, use the article history to view versions of the article from before 2022.
Ask yourself if there are some topics that you often do a web search for just because you keep forgetting an answer to something. Start saving those answers in a book or file that you can refer to offline. This is called a commonplace book. For an example of one, Beth and Angel made theirs into a zine, Stuff I Often Google.
How about a completely different sort of web search than present-day Google or DuckDuckGo? Marginalia Search only brings up results that are text-heavy and similar to the web of the 1990s and 2000s. Its software is independent and open-source.
Have you been using a web search engine to take you to the websites that you visit on a regular basis? Switch to saving them in your web browser's bookmarks folder. Your web browser, Firefox, can sync your bookmarks to your other devices. If you often need to refer to a large number of static web pages (ones that don't change what is on them every day), then you can save and organize them in your Zotero, a bibliography management program. You can sort them with folders and tags so you can find them again.
#anti generative AI#anti genAI#anti-AI#anti AI#anti-genAI#rated G#Google#degoogling#ungoogling#DuckDuckGo#bibliography#research#math#environment#consent#wiki#commonplace book#journaling#software#web browser#Firefox
50 notes
·
View notes
Text
*hacker voice* I'm in.
Okay my fellow non-American, here's how you do it. One, log on to your computer (I'm yet to find a work around on mobile), do not be logged into Amazon (It doesn't like it), open Edge (appropriate), download the free VPN extension VEEPN, make an account, connect to US, now log into Amazon. Boom, you're there.
Now I'm supposed to be working, but after work it's finally sledging time.

89 notes
·
View notes
Text
Hi everyone, I have a bit of an announcement to make. Nobody is in trouble, and yes I’m safe and okay. I just wanted to let everyone know that there may be a slight break or pause on art or emojis for a bit, as I have lost all of my digital art, wips, brushes, bases, YCHs, everything including Procreate. I hope to slowly come back over time.
It started with my iPad misbehaving and not allowing me to enter my password. I thought maybe I had simply forgotten my password of 6 years, and kept trying variations. I kept at this over the course of a few days, praying one of them would work. I was certain someone had tampered with my iPad, whether it was a hacker or family member I’m not sure. Today, I finally reached the dreaded “iPad unavailable” screen, meaning my absolute only option was to factory reset it and download a previous backup. So, of course I Googled and Youtubed everything I could, downloading software on my computer to try and fix everything. But my only option was to wipe it.
Once the deed had been done, I logged in and went to download a backup. Though I was presented with an issue; I had no backups (unless you count my mom’s current phone, as my iPad was still tied to her account). There was nothing from that point I could do to get everything back.
The only truly important things on there were my art things, since any photos had been saved or backed up elsewhere by now. I lost all of my Procreate data, including 6 years of art progress, references I had been working on for art fight next month, all of the emojis I have made and continue to use as bases, self portraits, drawings of pets that have since passed, fanart and gifts for friends, brushes I have made personally or downloaded myself, and a very detailed and extensive animatic I had been working on for about a year. All those frames, layers, and pixels are now lost.
It feels really bad, but also freeing. I have a fresh canvas to start from, and empty library to build up, and that’s exciting to me. I am finally off of my mother’s account and I have my own freedom for that device (yes I know it sounds silly), so hopefully I will try new things and feel a little more relaxed with my art.
All of this being said, art and emojis will likely be slow for a bit, if not completely halted for a few days or more. I’m not sure how long, I really want to keep creating but it’s probably gonna be difficult to face an empty Procreate (after paying the $13 fee again… yuck). I’m really sorry, but this is actually pretty difficult for me. But good at the same time.
In summary, my iPad went kaput and erased all of my data, including Procreate and my digital art. Nothing is recoverable. So I will be on a little art break until I can build everything back up again somehow.
Take care everyone, and thank you for reading.
#artists on tumblr#art#procreate#digital art#emoji blog#emote blog#whimsii yap#announcement#info#ipad
21 notes
·
View notes
Text
OKAY so im not about to be petty over internet safety advice but sims community's post on the sfs thing feels like they summarized my post hello ajdhjdvkv
like read this...
Always remember that Sims 4 custom content files should only have the .package or .ts4script extensions. Never download or run .exe files, and ideally avoid automatically unpacking ZIP or RAR files directly into your Mods folder. Instead, inspect each file individually to ensure it’s safe. Always verify that you are downloading from official, creator-posted links, and avoid suspicious URLs, especially those using link shorteners. It’s also important to stay on top of security hygiene. As well as regular antivirus scans and the ModGuard mod mentioned above, consider setting up a weekly system restore point in Windows before adding new mods and back up your important files regularly. this includes Sims saves, mods, and any personal documents. If you use services like Google or Firefox, take advantage of features that scan for password breaches, enable two-factor authentication, and routinely check logged-in sessions across your accounts. Lastly, for both creators and players: be mindful and cautious. Don’t rush to download every new mod or piece of CC, take a moment to ask yourself if you actually need it. For creators, regularly monitor your files and hosting platforms to ensure nothing has been tampered with. These precautions might not guarantee 100% protection, but staying vigilant and informed will greatly reduce your risk of encountering malicious content.


HELLO???? svlhlfkbvnm
feels like they put my post through chat gpt to summarize it
okay "notthatsophie" if you cant do a simple google search to get internet safety rules and have to spoof a tumblr post....that speaks volumes about you tbh
man this is why i dont leave tumblr cause the fucking moment i leave i find my shit plagiarized like we are in highschool or something
god this is the funniest thing that happened to me dzvjcnvklm
whatever man if it gets people to be more cautious i guess
40 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
The feud between U.S. President Donald Trump and Elon Musk didn’t come as a total surprise. There were always those who doubted that the two mega-narcissists could co-exist for long in the same White House. On June 11, Musk issued a statement expressing regret for some of his social media posts about Trump, but one is inclined to doubt that his mea culpa will patch things up.
The spat between the two billionaires, however, has diverted the public’s attention from a more urgent matter. Two stories that appeared this week should draw fresh attention to a problem that should have been obvious to everyone from the very beginning of the Tesla CEO’s disastrous adventure at the head of the so-called Department of Government Efficiency (DOGE). Musk is not only the richest man in the world. He is also the biggest risk to the security of the government of the United States—which, in a government riddled with walking security risks, is saying something.
On June 7, the Washington Post reported that DOGE personnel had ignored the concerns of White House cybersecurity staff by installing a Starlink terminal on the roof of an adjacent building in February. Starlink, you might recall, connects to the satellite network owned and operated by Musk’s SpaceX company. The White House Starlink connection enabled those who used it to bypass the security restrictions usually imposed on staffers working in the building. The Post’s sources told the newspaper that “those managing the systems weren’t able to monitor such connections to stop sensitive information from leaving the complex or hackers from breaking in.”
Three days later, the Wall Street Journal released another bombshell, reporting that the Department of Homeland Security and the Justice Department had “tracked foreign nationals coming and going to Elon Musk’s properties” in 2022 and 2023. The monitoring of Musk’s questionable ties started before the Trump administration, the paper noted, and “highlights concerns about the number of foreign nationals in Musk’s orbit.”
Of course, visits by “foreign nationals” are not inherently something to be worried about. But the fact that both agencies saw fit to do this tracking suggests that they had specific concerns—which may not be surprising, given the extreme sensitivity of Musk’s work for the U.S. government.
What foreign nationals might they have in mind? Russians, perhaps. (The Journal story contains a vague reference to people from “Eastern Europe” among Musk’s visitors.) We learned last fall that Musk had been in regular phone contact with Russian President Vladimir Putin staring in late 2022. During their conversations Putin is said to have asked Musk, among other things, to refrain from activating Starlink over Taiwan, which a Russian intelligence source said was done as a favor to Putin’s buddy, Chinese President Xi Jinping. Coincidence or not, the Taiwanese still don’t have Starlink service today.
Did Putin also thank the influential billionaire for his extensive use of X to insult and belittle Ukrainian President Volodymyr Zelensky—and for supporting Russian military operations by not allowing the Ukrainians Starlink access over Crimea, a part of Ukraine? (To be fair, Musk has largely maintained Starlink service for the Ukrainian military, which has proved to be a vital asset in Kyiv’s fight against the Russians.) We don’t know the details of these conversations. But what we do know would almost be the best case; the possibilities are so much worse.
Why Musk would do this remains an open question. But the far more alarming question is why this is only now beginning to catch media and government attention. Musk’s regular private contact with the head of a hostile autocracy should, in its own right, have activated a gigantic flashing red light for any U.S. administration. For Musk is not just an average U.S. citizen; he is a man with a high-level security clearance tied to a range of business interests involving NASA and the intelligence community.
NASA, of course, is now uncomfortably dependent on SpaceX’s rockets—as Musk himself noted during his feud with Trump, when the CEO threatened to decommission the Dragon spacecraft, a mainstay of travel to the International Space Station. Musk took back the threat three hours later. But the space station link is far from the only source of concern. In March 2024, it was revealed that SpaceX has been building a spy satellite network for the U.S. National Reconnaissance Office, a highly secret agency that conducts surveillance from space. Musk is doing the work under a $1.8 billion contract from 2021 with terms that remain classified.
China is another justified source of anxiety. Musk’s electric car company has huge exposure to the Chinese Communist Party. Musk has famously described himself—unusually for a MAGA loyalist and Trump campaigner—as “kind of pro-China.” In 2020, Tesla opened a factory in Shanghai, where the company now produces half of its cars; Tesla also manufactures a large share of its batteries at a facility in China. Permits for both factories were issued with remarkable speed, and the company has benefited hugely from favorable loans from Chinese banks, evidence of a cozy relationship with the government.
Musk certainly has a high enough profile to have held multiple meetings with Xi as well as Premier Li Qiang. To be sure, other U.S. business leaders have done the same. But few of them boast Musk’s top-secret clearance—or, now, anything like his access to sensitive government information through DOGE.
Musk has shown that he knows what’s expected of him in return. He has lavished obsequious praise on China. He has stated that “there’s a certain inevitability” for Beijing to absorb Taiwan, which he has referred to as “an integral part” of China. China is a key building block of Musk’s business empire—and given that a political decision in Beijing could crush his operations in a second, this makes him profoundly susceptible to potential pressure by the Chinese Communist Party. How far would he be willing to go to protect his interests?
This, then, is the man to whom the Trump administration gave comprehensive and unfettered access to the personal data of tens of millions of Americans during DOGE’s rampage in the first months of this year. Musk’s “takeover of federal government infrastructure,” as Wired magazine called it, gave inexperienced young software programmers access to a wide variety of sensitive information, including records from the Office of Personnel Management (OPM). Few Americans understand the significance of the OPM, which holds vast amounts of data about citizens, but the Chinese considered it important enough to target it in one of the biggest cyberattacks in history in 2015. Two DOGE staffers even tried to gain access to the networks that contain classified material about the United States’ nuclear weapons—which raises serious questions about why Musk’s people would need such information for a budget-cutting exercise.
Indeed, DOGE’s work has been characterized by a stunningly cavalier attitude to data security, prompting some experts to speak in Foreign Policy about the “the most consequential security breach” in the U.S. government’s history. The initiative has operated with minimal transparency and oversight. It has violated countless strictures on the confidentiality of federal employee information. The chaos and uncertainty sown by its firing of thousands of federal workers could potentially offer openings to foreign intelligence services, which will be keen to capitalize on the grievances of discarded employees. And granting DOGE staffers access to the government’s internal payments system has risked compromising intelligence operations that rely on the same mechanism. We will probably need years to fully understand the extent of the damage.
Government concern about Musk is not entirely new. In December, the New York Times reported that Musk and SpaceX “have repeatedly failed to comply with federal reporting protocols aimed at protecting state secrets, including by not providing some details of his [Musk’s] meetings with foreign leaders.” The Pentagon’s inspector general opened a review of Musk’s security clearance last year, as did the Air Force and the undersecretary of defense for intelligence and security. Nothing seems to have come of any these investigations, but I somehow don’t find that reassuring. I wonder if it’s just a coincidence that Trump fired Pentagon Inspector General Robert Storch in January, a few weeks after the publication of the Times report.
Recently, even before his fight with Musk, Trump seems to have had second thoughts about the carte blanche he has granted him. It was Trump who apparently canceled Musk’s access to a planned top-secret Pentagon briefing in April. Now, as the feud between the two men simmers, Steve Bannon, Trump’s longtime consigliere, has called on the president to pull Musk’s security clearance.
I never thought I would ever agree with Bannon on anything. But here we are.
27 notes
·
View notes
Text
Taking a brief look at Dinosaurus! (1960)
There's barely any coverage of this film on this site so I guess I'll rectify that.

Dinosaurus! (Yes the exclamation point is part of the title) is one of those middling science fiction films of the 1950's/1960's that's hard to recommend if you aren't a child or already a genre enthusiast looking for more stuff to watch that isn't terrible, but there's enough fun to be had.

The film takes place on an unnamed Carribean island where an American construction company is building a harbor, and the deepsea explosives they use unearth two frozen dinosaurs, a Tyrannosaurus and a Brontosaurus, who are then revived that night by a bolt of lightning alongside a caveman also freed from the ice, henceforth everyone on the island has to rush and make defenses against being stuck here with no communication infrastructure available.

I think of immediate notice is that Dinosaurus! is in color and wide-screen, an absolute luxury for an independent monster movie from the turn of the decade and probably the most noteworthy thing about the film as a whole. It really lets the island setting, shot on location, come into its own as the blues and greens look remarkable, especially when contrasted with the reddish colored Tyrannosaurus.

You may have noticed I glossed over discussing any characters in the plot synopsis and that is unfortunately because they mostly exist for plot functions and might as well be caricatures from future genre parodies. Ward Ramsey as Bart might be the only time a genuine stereotypical "square jawed hero" proper would be seen in a film like this, essentially doing the majority of heroic actions in this film. Kristina Hanson's Betty is the woman, Fred Engleberg's Hacker is the malicious greedy person who makes the situation with homicidal monsters on the loose more complicated than it needs to be, so on and so forth. The highlights might be Alan Roberts as Julio, a kid who knows more about dinosaurs than anyone else present and befriends the Brontosaurus and caveman (a genre archetype much more common in tokusatsu than western monster movies) and Gregg Martell as the eponymous caveman, who derails the film for minutes at a time in comedic hijinks of how a prehistoric human doesn't know what glass or a radio or paintings are. Though the film boasts something like half a dozen fucking comedy relief characters, the caveman actually transcends the future tired gag it would become by actually getting into the action to defend against the Tyrannosaurus. Dinosaurus! is also the only film of its type that features a substantial number of afro-latinx people though shamefully they're almost entirely relegated to background non-speaking roles.

The film is more or less structured around key special effects sequences such as the dinosaurs coming to life, the Tyrannosaurus attacking a bus, the two dinosaurs fighting, the Tyrannosaurus trying to eat people hiding inside a cave, and the Tyrannosaurus fighting an excavator on a cliffside. Both dinosaurs are realized through a combination of stop motion and puppetry and they're both damn good, largely thanks to the nuanced slimey coloration and skin texture on both of them. The Tyrannosaurus gets primary focus given that it actually kills and eats people versus the Brontosaurus mostly just moseying about.

It would be too harsh to call Dinosaurus! "forgotten" especially in the context of it getting a 4K restoration and a Blu-Ray release but it's now mostly known for individual scenes (mentioned above) being likely forerunners to key moments in films such as Jurassic Park (1993) and Aliens (1986). Dinosaurus! might actually be the best dinosaur film to come out in the extensive period between King Kong (1933) and Jurassic Park, though that's much more an indictment of the quality of every other dinosaur film for 60 years than an appraisal of Dinosaurus!' own quality. I can personally vouch for the fact that this is better than either Ray Harryhausen film starring dinosaurs at least.
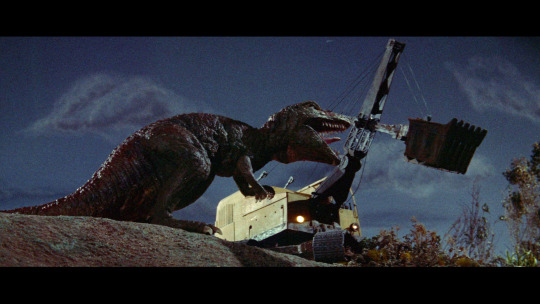
22 notes
·
View notes
Note
What does ggy mean
GGY is the name of a story in one of the fnaf books; Tales from the Pizzaplex #5: The Bobidots Conclusion to be exact.
the story is about a 12 year old boy named Tony Becker who needs to write a nonfiction story for his group project in writing class. He and his friends come up with little nicknames for each other during their project, Tony taking the name Tarbell (after Ida Tarbell, a famous reporter), Ellis taking the name Boots (short for Puss in Boots cause he’s a nerd) and Gregory (yes, that Gregory) taking the name Dr. Rabbit. they head to the Mega Pizzaplex to look for ideas and just hang out. Tony finds the initials GGY on a lot of the arcade games with high scores WAY above anyone else’s. He begins to get curious and decides to dig deeper, trying to figure out if this is just a really good player or a hacker messing with the machines. During his searches of breaking into Pizzaplex security and literally his own school after hours to get more info; he finds out that GGY is a lot more than what he thinks. Apparently GGY has a modified guest pass to the Pizzaplex that acts more like a security badge, allowing them into places normal guests wouldn’t be allowed into. We also get a couple of initials of some of his guests, who turn out to be the missing guidance counselors from Tony’s school that I forgot to mention.
Once Tony finishes his story he hands it to his slacker friends so they can edit and revise and get their credit in this little story. Dr. Rabbit (Gregory) doesn’t seem to have much of a positive opinion on it, returning the next day with the story edited beyond belief. One of the edited lines reads “GGY was the Wizard’s most favored apprentice.” This may sound like I’m going batshit insane but GGY/Dr. Rabbit/Gregory are implied to be the same person and also under Glitchtrap’s control (much like Vanessa with Vanny). Towards the end, Tony’s in the library sorting books for detention because he got caught sneaking into the school and using the library computer to do his research. Greg walks in to try and “make things better” by offering Tony to come with him to the Mega Pizzaplex. It’s implied that Greg is going to lure Tony to the Pizzaplex and kill him off because of his extensive knowledge of GGY’s hacks and implied crimes.
ALSO THIS STORY IS FUCKING CANON LETS GO!!! GREGORY HAS CANONICALLY KILLED PEOPLE!!!!! YAAAAYYYYYY!!!
sorry if this makes no sense I’m very insane about this book and this whole thing I just wrote is too big for me to read over rn because I’m so tired.
#Please tell me if I made any spelling or grammar mistakes#Also GGY fans pls tell me if I forgot anything because it’s 8:30 AM and I’m still half asleep my bad#hope this helps :3#Also sorry for yapping#fnaf#ggy#gregory fnaf#dr rabbit#tony ggy#tony becker#ellis ggy#fnaf ellis#tales from the pizzaplex#oh my god I’m so tired
24 notes
·
View notes