#FileVault
Explore tagged Tumblr posts
Text
Historical Apple Bugs - FileVault Information Leak
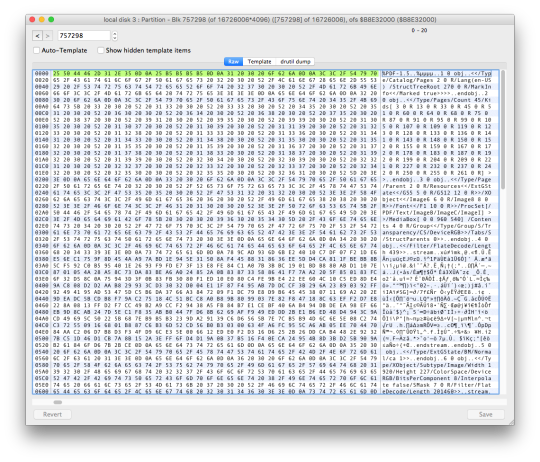
Some of you may recall the transition on MacOS 10.13 High Sierra to APFS. What some of you may not have been aware of was there was an information leak caused by this transition.
Okay Cases
If you were starting fresh on a clean new drive–no issues. If you were already encrypted with FileVault prior to moving to APFS again you are okay–no information leak.
Problem Case
If you upgraded an existing machine to APFS and then enabled FileVault–we have a problem. The issue stems from Apple choosing to move from an encryption scheme that encrypts sectors on disk to one that encrypts files. What ends up happening is any files you had previously deleted on your Mac were at least temporarily accessible even after encryption was enabled. This was a novel situation on the Mac since historically FileVault encrypted disk sectors not files. The transition here proved a bit rocky. The image above is an example of the problem.
This also posed a challenge for securely disposing of machines–because you could not use cryptographic data destruction–since you still had the possibility of plaintext data on disk.
0 notes
Text
Selfservice Recovery: Trellix BitLocker and fileVault Recovery
Trellix Management for Native Encryption (MNE) is a management product that allows ePO administrators to manage Apple FileVault and Microsoft BitLocker. These programs are the native encryption offerings on macOS and Windows operating systems. MNE can also help users in system recovery, and provides rich audit and reporting capabilities. In this article, we shall discuss “Trellix BitLocker and…

View On WordPress
#Bitlocker#bitlocker key#BitLocker Key Recovery#BitLocker Recovery Key Request#BitLocker Recovery Keys#FileVault#Macbook#MacBook M1#MacOS#macOS Big Sur#macOS Monterey#macOS Ventura#Microsoft Windows#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
Month 7, day 3
So my computer might be perma-ded, don't know yet, but here's more designing on that shirt design! Transparent this time so I can see the transparent effects better but they might not transparent correctly on the TeePublic upload. Idk, we'll see! But first I'm gonna finish cleaning this up and playing with effects until I like it so much I don't want to change anything :)
#the great artscapade of 2024#art#my art#Forspoken#Forspoken fan art#Frey Holland#hopefully it actually uploads as transparent bc as I'm typing this it has a white background which is actually hiding the magic effects#but I have it properly transparent in ProCreate so I can still work with it#anyway re: my computer#I think FileVault done goofed somehow because even in safe mode I can't sign in#and when my roommate tried to do a recovery and reinstall the OS it says we can't select the drive#because it's decrypting#which is probably my fault bc I told FileVault to decrypt but it was so I could fix my Mac resetting things whenever I rebooted#iN MY DEFENSE that's what the troubleshooting guide I was following told me to do!!!#I'm starting to think I should just give up on fixing things myself and stick to asking my roommate for help#but I don't usually run into/cause catastrophic errors like this so idk what happened#other than the power outage I speculated yesterday#but I don't actually know why my mac shut off since my stereo and PS5 were still on#which doesn't necessarily rule out a power issue bc this house is held together by unicorn spit and a prayer so the electical is hhhhhshodd#but USUALLY a power flicker bad enough to turn off my Mac also turns off my PS5 and stereo so idk man#idk#anyway here's hoping my Mac fixes itself and lives ¯\_(ツ)_/¯#she named herself Hera she's not supposed to just give up the ghost like this lol#edit: yay it's properly transparent! *\ô/*
5 notes
·
View notes
Text
hmm, parents’ iMac from almost 10 years ago is dying. Fusion drive; HDD seems fine but SSD seems, well, fucked. Kernel panics causing a boot loop—no Macintosh HD visible—etc.
But not completely fucked. Adventure!
Brought it into the Apple Store today: guy turned the computer on in target disk mode (where it behaves like an external hard drive), connected it to a laptop, and there everything is! all the data!
get home, do exactly the same thing—doesn’t work.
The Fusion Drive shows up in disk utility, but of the (adjacent) partitions under “Macintosh HD”, which are (another) “Macintosh HD” and “Macintosh HD - Data”, only the latter will mount. Can’t seem to read anything from it, though. (“Permission denied”—weird.)
Meanwhile, if you mount and open the parent Macintosh HD, you see four empty folders: Library, System, Applications, Users, iirc.
Trying to restore any of these to an external hard drive via disk utility fails because the “seal is broken”. `diskutil apfs list` shows that every disk is unsealed except for the unmountable leaf Macintosh HD, which has a broken seal. (No data/user is encrypted with FileVault or anything on this disk, fwiw. diskutil unlockVolume doesn’t do anything as a result.)
Ok. So, I try `ddrescue`; this is where “Fatal read error: permission denied” comes from. Then I try it on the physical disks. Works fine on the HDD for quite a while, copying away with no errors. Encounters loads of read errors on the SSD. Pretty regularly, too, which I found odd: one every 6-8 seconds without fail. But it’s apparently able to rescue some data in the meantime, so I figure this isn’t just some timeout.
But what use to me is a bunch of corrupted data? It bugs me that it was working in the Apple Store. Let’s just get there again! What was different?
The only things I can think of are:
it was turned off (but plugged in) overnight beforehand. I don’t know anything about SSD failures, but maaaaybe something electrical is afoot.
maybe there was something about the exact sequence of things he tried first in the Apple Store. What was it? Recovery mode, safe mode, PRAM reset, halfway through internet recovery, then shut it down and go for target disk mode…?
maybe the fact that he had it plugged into ethernet mattered for some wacky reason. maybe some of the relevant components are near each other. what if the wifi card is heating up and disrupting the SSD, or something? well, that probably wouldn’t be immediate, and so wouldn’t explain the kernel panic. but, who knows.
Maybe something just jostled back into place while carrying the computer into the store and jostled back out while carrying it out.
Favorite option so far is something electrical having a really long relaxation time of some sort. So we’ll see, I guess…!
2 notes
·
View notes
Link
[ad_1] When we think about digital and device security, we mostly think about the fixed locations where people spend most of their time—home, school, and work. But what about when you’re traveling? Some security concerns remain the same when you’re on the road, but new ones crop up. We’ll assume that you already keep your devices up to date, use FileVault on Macs, have at least a six-digit iOS passcode, have strong password habits, and use multi-factor authentication wherever possible. Other options are more specific to travel. As with our more general article about increasing security last month, we’ve divided our list of suggestions into two parts: things that everyone should do and measures that only people who worry about being specifically targeted should employ. Sensible Travel Security Precautions for Everyone These suggestions are appropriate for everyone who travels, and they’re aimed primarily at avoiding relatively common problems: loss, theft, data loss, and generalized snooping: Focus on physical security: As a tourist, you may be targeted by thieves, so it’s important to keep your iPhone in a secure pocket whenever you’re not using it. Carry an iPad or laptop in a bag that can’t be snatched, or leave them locked or at least concealed in your hotel room. Enable Find My for all your devices: You should have already done this, but if not, enable Find My to improve your chances of finding a device you lose or accidentally leave behind. It might help if the device is stolen, but local police cooperation for recovering stolen items can vary widely. Don’t attempt to recover a stolen device yourself. Put AirTags in your luggage and laptop bags: AirTags can help you track down lost luggage—you can now share their locations with airlines—and prevent you from accidentally leaving bags behind. An AirTag may also help with locating a stolen item, but always work with local law enforcement. Enable biometric authentication and Stolen Device Protection: Using Face ID or Touch ID wherever possible and having Stolen Device Protection enabled on your iPhone in Settings > Face/Touch ID & Passcode is even more important when traveling. Use a VPN or iCloud Private Relay: Because you may be using Wi-Fi networks whose security you know nothing about, it’s best to use a VPN like Mullvad VPN, NordVPN, or ProtonVPN to encrypt all your traffic. At a minimum, use iCloud Private Relay, which requires an iCloud+ subscription and won’t encrypt traffic from most non-Apple apps. Use iCloud Photos or another backup option: To ensure you don’t lose precious vacation photos, use iCloud Photos so all your photos are uploaded to the cloud whenever you have access. This will almost certainly require an iCloud+ subscription for sufficient storage space. If Wi-Fi and cellular are too slow or unavailable, consider an external SSD to which you can manually export photos and videos for backup. To speed up the process, you could create a shortcut that automatically copies all photos taken that day. Use iCloud Backup: It’s best to use iCloud Backup to back up your entire iPhone every night. That way, if your iPhone is lost or destroyed, you may be able to buy a replacement and restore from backup in relatively little time. You will probably need an iCloud+ subscription to have enough backup space. Practice dealing with a lost or stolen device: If the worst happens and you lose one of your devices while traveling, you need to know what to do. Immediately go to Find My on another device or iCloud.com and mark the device as lost. If there’s a chance of getting it back, stop there. However, if you believe the device was stolen, your data is at risk, and tracking it is no longer useful, use Erase This Device in Find My to wipe it. Activation Lock will remain enabled to prevent anyone from reusing the device. Increasing Travel Security for People Who May Be Targeted Not all travel is fondue and gamelans. If you’re a journalist, activist, government employee, or corporate executive with access to sensitive data, you could be a target while traveling. This is particularly true if you are headed to countries like China, Russia, or others with authoritarian governments and powerful intelligence agencies. Along with the suggestions above, we recommend: Be aware of local laws and government practices: It’s important to read up on regional laws regarding data access and potential government capabilities at your destination. Knowing what to expect can help you reduce your risks and take appropriate precautions. Use caution with cellular access: Even if your carrier allows roaming, consider using a dedicated eSIM for international travel, separate from your personal one. That way, you can use local cellular networks without revealing your home number. Be aware that your traffic may be monitored. Enable Lockdown Mode: If you’re concerned about your iPhone or iPad being targeted by local law enforcement or government intelligence agencies, turn on Lockdown Mode in Settings > Privacy & Security > Lockdown Mode. To increase security, it blocks most attachment types in Messages, complex Web technologies, incoming FaceTime calls from unknown callers, non-secure Wi-Fi network connections, and incoming invitations to Apple services. Plus, it excludes location information from shared photos, requires approval to connect accessories, and more. Reduce and protect your use of cloud services: While using a VPN is essential, you should still avoid using cloud services much if government entities might have access to stored files. If you need to upload files, encrypt them first using the free and open-source Cryptomator. Know how to disable Face ID and Touch ID: If you find yourself in a situation where you believe you may be compelled to unlock your iPhone or iPad with your face or fingerprint, press and hold the side or top button and either volume button to display the power off slider. This temporarily disables biometric authentication, requiring your passcode for the next unlock. Use dedicated travel devices and accounts: If you’re traveling to a potentially hostile part of the world, we strongly recommend carrying only devices—preferably iPhones or iPads, which are more secure than Macs—configured to contain none of your personal data or regular accounts. Keep them with you at all times, assume they could be confiscated, and be aware you might be compelled to share passcodes or other account information. Create a separate Apple Account for such devices. Best of luck in your travels! With just a little preparation, you can reduce the chances that something bad will happen during a vacation. If you’re traveling on business to somewhere more concerning, putting in additional effort could prevent truly problematic things from happening. (Featured image by iStock.com/metamorworks) !function(f,b,e,v,n,t,s) if(f.fbq)return;n=f.fbq=function()n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments); if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version='2.0'; n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0]; s.parentNode.insertBefore(t,s)(window, document,'script', ' fbq('init', '301716966988128'); fbq('track', 'PageView'); [ad_2] Source link
0 notes
Text
How to Keep Your Rented MacBook Secure During Use
Maintaining the security of your rented MacBook is crucial. Here are some tips:
Set Strong Passwords: Protect your data with robust passwords.
Enable FileVault: Encrypt your hard drive to safeguard information.
Regular Updates: Keep the system and applications updated to patch vulnerabilities.
Use Trusted Networks: Avoid public Wi-Fi or use a VPN for secure connections.
By following these practices, you can ensure your data remains secure. For more information on secure rentals, visit Laptops on Rent.
0 notes
Text
Expert Apple Technicians Recover Crashed Mac Drives
A crashed Mac drive can stop everything in its tracks locking you out of your system and making essential files seem permanently lost. Whether it’s your work machine, personal laptop, or a studio Mac with years of creative projects, a drive crash can feel like a digital disaster. The good news? Expert Apple technicians recover crashed Mac drives every day using tools and techniques specifically designed for Apple hardware and macOS.
If your Mac suddenly won’t boot, is stuck on a loading screen, or displays disk errors, now is the time to call in certified professionals who know exactly how to restore your system—and your data.
What Causes a Mac Drive to Crash?
A crashed drive can occur due to a number of issues, often without warning. Some of the most common causes include:
Hardware Issues
Aging or worn-out hard drives (especially HDDs)
SSD corruption due to bad memory cells
Power surges or unexpected shutdowns
Overheating or physical damage (e.g., from drops)
Software Problems
Failed macOS updates or installations
File system corruption (APFS, HFS+)
Malware or third-party software conflicts
Improper shutdown or forced restarts
A crash can make your Mac unbootable, freeze on the Apple logo, or display a flashing folder with a question mark—indicating your system can't locate a valid startup disk.
Why Trust Expert Apple Technicians?
When it comes to recovering data from a crashed drive, not all recovery services are created equal. Apple-certified technicians bring unique advantages:
Trained in Apple-Specific Systems
They have expert knowledge of macOS, Apple’s custom hardware, and unique security features like FileVault and the T2/M1/M2 chips. These systems require precise handling for successful recovery.
Access to Specialized Tools
From proprietary Apple diagnostics to advanced recovery utilities, certified technicians use industry-grade tools to recover data without causing further damage.
Safe Handling of Encrypted Drives
If your Mac uses FileVault or has a security chip, standard data recovery attempts may fail. Apple technicians understand the correct protocols to access encrypted data—securely and legally.
High Success Rate
Thanks to their experience and equipment, Apple experts boast much higher recovery rates than generic repair shops or consumer software solutions.
The Recovery Process, Simplified
Apple technicians follow a structured, step-by-step approach to recover crashed Mac drives:
1. Initial Assessment
Technicians begin by diagnosing the drive using Apple’s diagnostic tools and external recovery systems to determine the nature and extent of the crash.
2. Non-Invasive Cloning
If the drive is still accessible, a bit-by-bit clone is created to preserve the data and prevent further corruption during the recovery process.
3. Deep File Recovery
Using specialized tools for APFS, HFS+, and encrypted volumes, technicians extract data from the cloned image or directly from the original drive.
4. Data Verification
Recovered files are checked for completeness and integrity, ensuring they are usable and error-free before delivery.
5. Data Delivery & Backup Solutions
Your recovered files are returned to you on an external drive, cloud storage, or a replacement Mac. Apple experts can also help set up Time Machine or iCloud for ongoing protection.
What Can Be Recovered?
Depending on the condition of the drive, Apple technicians can often retrieve:
Documents, spreadsheets, and PDFs
Photos, videos, and music libraries
Email files and app data
iMovie, Final Cut, and Logic Pro projects
User profiles, preferences, and settings
Complete drive images or partitions
Even partially corrupted or encrypted files may be recoverable with the right tools and experience.
Warning Signs of a Failing Mac Drive
Don’t wait until your Mac crashes completely. Contact an expert if you notice:
Frequent crashes or freezes
Mac is stuck on the Apple logo
Apps take unusually long to open
Disk Utility reports drive errors
Files mysteriously disappear or won’t open
Clicking or buzzing noises (on older HDDs)
Catching these early can significantly improve the chances of a successful recovery.
Tips to Prevent Future Drive Crashes
After recovery, Apple experts often recommend proactive steps to prevent another data loss event:
Use Time Machine: Apple's built-in backup system can automatically protect your files.
Enable iCloud Syncing: Especially for documents, desktop files, and photos.
Avoid Forced Shutdowns: Always power down your Mac properly.
Keep macOS Updated: Regular updates patch security holes and improve disk management.
Don’t Ignore Disk Utility Warnings: Run First Aid regularly to fix minor errors before they grow.
A crashed Mac drive doesn’t mean all is lost. With the help of certified professionals, Apple technicians can recover data from even the most stubborn drive failures. Their deep knowledge of Apple systems, secure practices, and advanced recovery tools ensure you get the best chance at saving your data—quickly and safely.
If your Mac is showing signs of a crash or has already failed, don’t delay. Reach out to certified Apple experts today and take the first step toward recovery and peace of mind.
#iPhone Battery Replacement#Iphone Repair#Macbook Repair#iPad Screen Repair#macbook battery replacement
0 notes
Text
MacADUK 2025
I have to say after watching about 80% of the presentations this was a mixed bag year for MacADUK. The content was not up to the standards I would have hoped for out of a professional conference. A lot of the presentations I was left scratching my head wondering why they needed to be presented. It had a bit of the feel of a conference that got insufficient submissions to be sufficiently selective.
However, to my mind the trend is a broader one in the Mac Admin conference scene. I have seen this with PSU MacAdmins and JNUC etc. The presentations get less and less technical, and the topics get more and more repetitive.
To give some examples from MacADUK:
Workbrew - this is an interesting product with some interesting applications, but the presentation felt like something a Sales Engineer would give. Not what I would have hoped for.
AI Adventures - I am not sure what the point of this presentation was, but it was a mess. I don't know what the adventure was, and I really am not sure what part of it was interesting or something I should care about.
Apple Silicon Virtualization - I feel like this has been done to death. Apple Silicon and virtualization is an oft discussed topic, and I was sad to see really nothing new added to the discussion.
Tokens - this was a bewildering meander through various tokens with some loose FileVault history. I am not sure what point was supposed to be taken away.
MacStadium AI - This is one of those presentations that would have been so much cooler as a technical presentation–rather than an overview.
Packaging - I feel like this is a topic that shows up at almost every Mac conference in some form. I just keep wondering when we will get a year without this same rehash?
Data Corruption - This was one of the strangest vendor presentations that tired to mix data corruption with product placement with I am not sure what. I honestly couldn't watch it all.
Vendor presentations as always: Jamf, Omnissa, OWC and AWS–may have been more. I tend to ignore these unless they are talking about something I am interested in.
Just a sample of the kind of mixed bag I am talking about. Perhaps this is just that I am interested in technical talks. Probably why I enjoy Super Compute so much more.
0 notes
Text
Great question — and let me tell you, the truth is way more interesting (and a bit scarier) than most people think. Just because you delete something doesn’t mean it’s gone. Let’s break it down:
⸻
What REALLY Happens When You Delete Data
1. File Deletion Isn’t True Destruction
When you hit delete, your device:
• Removes the reference to the file in the file system index (kind of like tearing out a page in the table of contents)
• BUT the actual file still exists on the disk/SSD until it’s overwritten by new data
This is like taking your name off a mailbox but leaving the mail inside. Anyone who knows how to check the box can still read it.
⸻
2. What About the Trash/Recycle Bin?
• On most systems, deleted files go to a temporary folder (Trash or Recycle Bin)
• Not actually deleted until you empty the bin
Still recoverable at this point with basic tools.
⸻
3. Even After Emptying the Trash…
• On traditional HDDs (spinning hard drives), data can often be recovered using forensic tools unless it’s been securely overwritten.
• On SSDs, things get weirder due to a process called TRIM, which helps with wear-leveling and may mark the data for deletion more efficiently — but even then, recovery might still be possible in some cases.
⸻
4. Who Can Still See Your Deleted Data?
• Hackers using data recovery software
• Forensic analysts during investigations
• Even some apps or system services might still store metadata, previews, or cache versions elsewhere
⸻
5. Want It REALLY Gone? Here’s How:
a. Overwrite It
Use tools like:
• CCleaner (with secure erase)
• BleachBit
• Mac’s Disk Utility (secure erase options for drives)
b. Encrypt First, Then Delete
If data was encrypted, deletion is more final because the key deletion = permanent loss.
c. Use “Secure Delete” Tools
Programs like:
• sdelete (Windows)
• shred or wipe (Linux)
• FileVault (macOS encryption)
d. Physically Destroy the Drive
If you’re going full CIA/NSA mode — smash, drill, or melt that sucker.
⸻
TL;DR:
“Delete” doesn’t mean “destroy.”
The data lives on — in limbo — until it’s overwritten or securely wiped.
⸻
Want me to show you how to securely wipe files from your Mac or external drive? Or how hackers can recover deleted files in forensics? Let’s go deeper if you want!
0 notes
Text
How to Prevent Common MacBook Repairs and Keep Your Laptop Running Smoothly

MacBooks are known for their sleek design, powerful performance, and durability. However, even the best laptops can experience issues over time. With proper care, you can avoid many common Macbook repairs and keep your device running smoothly for years. Here’s how:
Regularly Clean Your MacBook
Dust and debris can accumulate inside your MacBook, leading to overheating and potential hardware damage. Use a soft, lint-free cloth to wipe down the exterior, including the keyboard, screen, and trackpad. Consider using a can of compressed air to clean out the vents and keyboard. This simple step will help keep your MacBook cool and extend its lifespan.
Protect the Battery
Battery issues are one of the most common Macbook air repairs. To prolong your battery life, avoid charging it to 100% or letting it drain to 0% frequently. Instead, aim for a range between 20% and 80% for optimal battery health. Additionally, avoid leaving your MacBook plugged in for extended periods. If you’re not using it for a while, try to charge it to about 50% before storing it.
Use a Reliable Antivirus and Keep Software Updated
Cyber threats can lead to data loss or system malfunctions. Install a trusted antivirus program and keep it updated regularly to protect against malware and viruses. Additionally, always keep your macOS up to date, as software updates often include critical bug fixes and security patches that help your MacBook run efficiently.
Avoid Overheating
Excessive heat can damage internal components and lead to performance issues. To prevent overheating, ensure your MacBook is used in a well-ventilated area. Avoid using it on soft surfaces like beds or couches that can block the air vents. You can also invest in a cooling pad to provide additional airflow when using your MacBook for heavy tasks like gaming or video editing.
Handle with Care
Your MacBook is a precision piece of technology, so it’s important to handle it with care. Avoid dropping it, placing heavy objects on top of it, or putting pressure on the screen. Always use a protective case or sleeve when carrying it around to minimize the risk of physical damage.
Free Up Space on Your Hard Drive
Running out of storage can slow down your MacBook and cause it to behave erratically. Regularly check your storage and delete unnecessary files, apps, or documents. Consider using iCloud or an external hard drive to store large files and keep your internal storage optimized for faster performance.
Keep Your MacBook Secure
Security issues like accidental data loss can lead to major headaches. Always back up your MacBook using Time Machine or a cloud service to prevent data loss in case of theft or failure. Use strong passwords and enable FileVault to encrypt your data and protect it from unauthorized access.
Manage Your Apps
Too many apps running simultaneously can slow down your fix MacBook’s performance. Close unused apps and check your Activity Monitor regularly to monitor resource-heavy apps. Be selective about the apps you download and keep your system streamlined for better performance.
Avoid Spilling Liquids
Spilling liquids on your fix MacBook is one of the quickest ways to cause damage. Keep drinks away from your laptop, and if an accidental spill does occur, turn off your MacBook immediately, dry it off, and take it to a professional for inspection.
Use a Quality Charger
Using a low-quality or non-certified charger can damage your MacBook’s battery and charging port. Always use an Apple-approved charger and cables to ensure safe and efficient charging.
Conclusion:
By following these simple yet effective tips, you can minimize the need for Macbook pro repairs and keep your laptop running smoothly. Regular maintenance, careful handling, and smart usage will help extend the life of your MacBook, saving you time, money, and frustration in the long run. Should you encounter any issues, don’t hesitate to reach out to a professional technician for repairs. Keeping your MacBook in top condition ensures that it remains a powerful tool for work, creativity, and entertainment.
#MacBook Repair#MacBook Repair near me#MacBook Repair shop near me#MacBook Repair Shop#MacBook Air Repair#Same Day MacBook Repair#Expert MacBook Repair#macbook repair shop#macbook repair price#macbook repair cost
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer About Crucial As a brand of Micron, one of the largest flash storage manufacturers in the world, Crucial is backed by the same expert quality and engineering innovation that has produced some of the world's most advanced memory and storage technologies for over 40 years. Built on a heritage of award-winning SSDs, thousands of hours of pre-release validation, and dozens of qualification tests, the Crucial X8 Portable SSD will keep your photos, videos, & documents safe & within reach, no matter where you go. Crucial X8 Crucial X8 Protect your memories with the Crucial X8 Portable SSD — back up important photos, videos, and documents with up to 2TB capacity. Expand storage on your PS4, Xbox One, iPad Pro, Android device, or simply free up space on your computer quickly with speeds up to 1050MB/s¹,². The Crucial X8 runs up to 1.8x faster than other portable SSDs and up to 7.5x faster than portable HDDs¹. Store with confidence on the Crucial X8. Incredible performance with read speeds up to 1050MB/s¹ Incredible performance with read speeds up to 1050MB/s¹ Beautiful and durable design, featuring an anodized aluminum unibody core. Drop proof up to 7.5 feet. Extreme-temperature, shock, and vibration proof Beautiful and durable design, featuring an anodized aluminum unibody core. Drop proof up to 7.5 feet. Extreme-temperature, shock, and vibration proof Fast, easy storage for your PC and Mac Quickly and easily add storage to your PC and Mac with the Crucial X8 Portable SSD. Just plug it in — no reformatting required. Back up important photos, videos, and documents with up to 2TB capacity. Encrypt your drive and protect your data using Windows Bitlocker to Go or Apple’s FileVault. Crucial X8 also works with popular endpoint protection services from brands like Symantec and McAfee. Expand Android storage for all your movies and shows⁴ Download your Netflix or Amazon videos to the Crucial X8, allowing you to save LTE data and enjoy high-fidelity video while in transit or offline. Store up to 2TB of photos and videos on your Android smartphone or tablet. Works with popular photo-editing software like Adobe Photoshop Express on Android. Expand Android storage
for all your movies and shows⁴ Download your Netflix or Amazon videos to the Crucial X8, allowing you to save LTE data and enjoy the high-fidelity video while in transit or offline. Store up to 2TB of photos and videos on your Android smartphone or tablet. Works with popular photo-editing software like Adobe Photoshop Express on Android. More capacity for your creativity on iPad Pro [2018 USB-C model]⁵ Unleash your creative energy in the field with the Crucial X8 portable SSD and Apple’s iPad Pro. Add up to 2TB of capacity to your tablet instantly. Curate, edit, and export multi-stream videos without your computer or an internet connection. Seamlessly works with popular video-editing software like LumaFusion. PC & Mac PS4 & Xbox One Android iPad Pro Phenomenal Speed Wherever you are, access your games, photos, and videos quickly — even offline. With reading speeds up to 1050MB/s, you can load files up to 1.8x faster than most portable SSDs, 7.5x faster than portable hard drives, and 100x faster than USB flash drives.¹ Works with a Broad Range of Devices. Increase storage capacity for nearly any computer, tablet, phone, or console. Works with Windows, Mac, iPad Pro, Chromebook, Android, Linux, PS4, and Xbox. Connect with a USB-C 3.2 Gen2 interface or use our included adapters for USB-C or USB-A connections.² Built for the Toughest Conditions. Indoors or outdoors, at home or off the grid, the X8 is manufactured to be durable, rugged, and compact. Tested against extreme temperatures, shock, vibration, and even a 7.5-foot drop⁶, you can trust that your drive will withstand the elements. Sleek Style, Innovative design Form meets function with the crucial X8, Built with a unibody core of anodized aluminum, the case not only looks and feels great but dissipates heat efficiently to maximize performance. Complete Data Protection Store your photos, videos, and files with confidence.
You can use Windows Backup, macOS Time Machine, Windows Bitlocker to Go, and Apple FileVault, along with third-party endpoint-protection software suites like Symantec and McAfee. A Reputation for Reliability When you need ultimate peace of mind, trust the expert quality and engineering innovation of Crucial, a brand of Micron, one of the leading flash storage manufacturers in the world. Enjoy comprehensive support materials, such as operating instructions for various platforms and articles on maximizing your drive’s performance. Incredible performance with read speeds up to 1050 MB/s Works with Windows, Mac, iPad Pro, Chromebook, Android, Linux, PS4, and Xbox One with USB-C 3.1 Gen2 and USB-A connectors Durable design featuring an anodized aluminum core, drop proof up to 7.5 feet, extreme-temperature, shock and vibration proof Backed by Micron, one of the largest manufacturers of flash storage in the world [ad_2]
0 notes
Text
Security Features in the Latest MacBook Models
Top Security Features in the Latest MacBook Models
Touch ID and Face ID
Biometric authentication for secure access to your MacBook.
Touch ID uses fingerprints, and Face ID scans facial features for added security.
Secure Enclave Technology
A dedicated coprocessor securely stores sensitive information, such as biometric data.
Protects data even if the main processor is compromised.
FileVault Encryption
Full-disk encryption that safeguards your data if your MacBook is lost or stolen.
Prevents unauthorized access without the encryption key.
Gatekeeper
Ensures only trusted apps from the App Store or those signed by Apple are allowed to run.
Protects against potentially harmful software.
Two-Factor Authentication (2FA)
Adds an extra layer of security to your Apple ID.
Requires secondary authentication (e.g., trusted device or SMS code) even if your password is compromised.
T2 Security Chip
Custom Apple chip that enhances security with secure boot, real-time encryption, and secure data storage.
Powers privacy features like processing Siri voice requests locally.
Safari Security Enhancements
Intelligent Tracking Prevention blocks advertisers from tracking your online activity.
Provides protection against harmful websites and phishing attempts.
Mac App Store Security
A curated environment for downloading and installing apps.
Apps undergo rigorous security checks to ensure safety.
Automatic Software Updates
Seamless updates that ensure your MacBook is always protected with the latest security patches.
No need for manual intervention.
Privacy Controls
Granular control over app permissions for accessing sensitive data like location, contacts, and camera.
Empowers users to manage and restrict unnecessary data access.
Conclusion The latest MacBook models feature a comprehensive suite of security measures, from biometric authentication to encryption and privacy controls, making them an excellent choice for those prioritizing security and privacy.
Want to Buy MacBook in Bulk at Affordable Prices From Vstl?
If you're looking to buy MacBooks in bulk at affordable prices, VSTL offers competitive deals for businesses and organizations. VSTL provides a reliable platform for purchasing multiple MacBook units with attractive discounts and bulk pricing options. Whether for educational institutions, enterprises, or other large-scale purchases, VSTL ensures you get high-quality Apple products at cost-effective rates.
0 notes
Text
Cách Bảo Vệ Dữ Liệu Khi Bảo Trì Máy Tính - Bí Quyết An Toàn Từ PECO
Bảo trì máy tính là một việc làm cần thiết để đảm bảo hiệu suất và tuổi thọ thiết bị. Tuy nhiên, nhiều người lo lắng rằng việc bảo trì có thể gây mất mát hoặc rò rỉ dữ liệu quan trọng. Chính vì vậy, việc bảo vệ dữ liệu trong quá trình bảo trì máy tính là một bước không thể bỏ qua.
Bạn hãy yên tâm, PECO sẽ chia sẻ những cách hiệu quả để bảo vệ dữ liệu của bạn khi thực hiện bảo trì máy tính.

1. Sao lưu dữ liệu trước khi bảo trì
Tại sao cần sao lưu? Sao lưu là cách tốt nhất để đảm bảo bạn không bị mất dữ liệu quan trọng nếu xảy ra sự cố trong quá trình bảo trì.
Cách sao lưu hiệu quả:
Sử dụng ổ cứng rời hoặc USB để lưu trữ dữ liệu quan trọng.
Dùng các dịch vụ lưu trữ đám mây như Google Drive, Dropbox hoặc OneDrive để lưu trữ.
Sử dụng phần mềm sao lưu tự động như Acronis True Image hoặc EaseUS Todo Backup.

2. Bảo vệ dữ liệu bằng mật khẩu
Mã hóa file quan trọng: Trước khi bảo trì, hãy mã hóa các file nhạy cảm bằng các công cụ như BitLocker (Windows) hoặc FileVault (macOS).
Sử dụng mật khẩu mạnh: Đặt mật khẩu phức tạp cho máy tính và các thư mục chứa dữ liệu nhạy cảm.
3. Chọn đơn vị bảo trì uy tín
Tại sao điều này quan trọng? Đơn vị bảo trì máy tính là bên trực tiếp truy cập vào thiết bị của bạn. Việc chọn một đơn vị uy tín như PECO Technology sẽ giúp bạn đảm bảo rằng dữ liệu không bị rò rỉ hay xâm phạm.
Cách nhận biết đơn vị uy tín:
Có hợp đồng rõ ràng cam kết bảo mật dữ liệu.
Có đội ngũ chuyên gia giàu kinh nghiệm và quy trình bảo trì chuyên nghiệp.
Được đánh giá tốt từ khách hàng trước đó.
4. Kiểm tra và tắt các phần mềm quan trọng
Ngăn chặn rò rỉ dữ liệu từ phần mềm:
Đăng xuất khỏi các tài khoản quan trọng như email, ngân hàng trực tuyến hoặc phần mềm quản lý doanh nghiệp.
Tắt các ứng dụng hoặc phần mềm đang chạy để tránh xung đột khi bảo trì.
5. Sử dụng phần mềm bảo mật
Quét virus trước khi bảo trì: Dùng các phần mềm bảo mật như Kaspersky, Bitdefender để quét toàn bộ hệ thống, đảm bảo không có virus hoặc malware tiềm ẩn.
Cài đặt tường lửa: Kích hoạt tường lửa để ngăn chặn truy cập trái phép vào dữ liệu trong quá trình bảo trì.

6. Lập danh sách dữ liệu cần kiểm tra sau bảo trì
Sau khi bảo trì xong, bạn nên:
Kiểm tra xem dữ liệu quan trọng có bị mất hoặc thay đổi không.
Đối chiếu với bản sao lưu trước đó để đảm bảo không có bất kỳ vấn đề gì xảy ra.
Tại sao nên chọn PECO để bảo trì máy tính?
Cam kết bảo mật dữ liệu tuyệt đối: PECO có quy trình bảo trì chuẩn mực với cam kết không xâm phạm hoặc làm mất dữ liệu của khách hàng.
Đội ngũ chuyên gia giàu kinh nghiệm: Được đào tạo để xử lý tất cả các tình huống phát sinh, đảm bảo an toàn cho cả phần cứng và phần mềm.
Dịch vụ toàn diện: Từ sao lưu, bảo mật đến kiểm tra toàn diện sau bảo trì, PECO mang đến sự an tâm tối đa cho khách hàng.

Liên hệ ngay với PECO Technology
Nếu bạn lo lắng về an toàn dữ liệu khi bảo trì máy tính, hãy để PECO hỗ trợ bạn. Chúng tôi cung cấp dịch vụ bảo trì máy tính chuyên nghiệp, an toàn và bảo mật.
📞 Hotline: 09 6368 0939 📧 Email: [email protected] 🌐 Website: www.peco.vn
>>> Xem thêm: Quy trình bảo trì máy tính chuyên nghiệp tại PECO - Đảm bảo hiệu suất tối ưu
Bài gốc: https://peco.vn/cach-bao-ve-du-lieu-khi-bao-tri-may-tinh-bi-quyet-an-toan-tu-peco/
0 notes
Text

Crucial® X9 Pro
Unleash the Power of Crucial X9 Pro! 💻✨ With lightning-fast read and write speeds up to 1,050MB/s, this portable SSD is a game-changer for Mac, iPad, iPhone 15 Pro/Pro Max, iMovie, Photos, and more. 🚀💦 IP55 water and dust resistant, drop-proof up to 7.5 feet, and secure with password protection and Apple FileVault encryption. Anodized aluminum meets a rubberized soft-touch base in a compact 65x50mm design, 🎨✨
#TechEssentials#DataSecurity#LightningSpeeds#PortableSSD#GulfTech#MacUsers#DigitalCreativity#SeoFriendly#TechGadgets#OnTheGoStorage#X9ProExperience#CrucialInnovation#DataProtection#Ad#TechLovers#CompactDesign#GameChanger
0 notes
Text
Today’s connected lifestyle and the harsh reality that the government monitors pretty much everything that you download, share, or view, has made it evident that privacy has gone out the window. The bigger surprise is how unaffected people seem to appear when it comes to the safety of their personal data, mostly out of arrogance that it could never happen to them. While the most computer or smartphone users think that only non-encrypted communication is susceptible to data hacks, it is also believed that many encrypted technologies are vulnerable. Web experts say that hackers can now crack the code for anything from email to skype accounts, or worse, net banking accounts. Most computer users take data security very casually. However, it has been always emphasized by good security books and information security experts. What this basically means is that none of our activities on the internet are secure on the internet, no matter what it is. It’s practically almost impossible to prevent at least some of your personal data from getting accessed, but there’s plenty you can do to make sure that your communications are less vulnerable. So, here are some tips to help you secure your personal data: 1. Email Yes, email is the most obvious place to start because internet users send an average of 20 emails per day. The best way to make sure that your emails and email account are secure is to reconfigure your entire email setup. And seeing that free is usually a synonym for worthless, you’re going to have to shell out for a specialized email service. Fastmail, for example, is a paid email client that is based outside the United States, offering highly secure email services. Paid email services are not a really big deal, but will soon gain dominance as individuals & businesses realize that free email clients simply aren’t doing enough to protect users’ data. The worst part is that even the information that goes along with a secured email, metadata, can reveal more personal data than the actual contents of the email. This metadata cannot be encrypted since it is what the internet routing system uses to get mail to its destination. 2. Encryption Earlier, encryption meant safety and was considered to be the pinnacle of online security. But all that has changed over the past few years, with applications like GPG for Mail. GPG is an open plug-in for the Apple Mail program, allowing users to encrypt & decrypt, or even electronically sign and verify any email with OpenPGP standards. This renders secured data vulnerable to even basic computer users that are looking to acquire personal data. There have also been various improvements in data encryption to help maintain security over personal data. The Apple OS X operating system, for example, features a unique program called “FileVault” that encrypts a computer’s hard drive. Microsoft has developed a similar program for its Windows platform. This software scrambles your data in ways that make it almost impossible to hackers to decipher, but it doesn’t prevent government authorities from getting encryption key, as it is allowable under the Regulation of Investigatory Powers Act. 3. Web Browsing You might be shocked at the amount of personal data that gets sent from a computer while just innocently browsing the internet. But considering the amount of surfing the average user does in a day, it is almost shameful to see that very few users take browser security seriously. Web browsing data logs are so easily accessible, that they’re as good as public records in a government library. Mainstream browsers like Google Chrome, Internet Explorer & Opera should be avoided, but that doesn’t mean you’re going to have to download a paid browser. As far as the security goes, the Tor Browser is one of the most secure web browsers that you can download for free. Users can adjust their browser settings so that they give off the least amount of personal data. 4. Cloud Services This one is a
no-brainer; millions of people’s personal data stored on an online cloud is obviously no safe house. And if the 2013 Snowden incident has taught us anything is that users should avoid using all cloud services, including iCloud, Dropbox, and even Evernote. As a rule of thumb, you’re better off avoiding any cloud service that originates from the UK, France, and especially the United States, as they’re the ones who are big on transparency. In the unavoidable situation where you have to store your data on a cloud, make sure it is fully encrypted. 5. File Storage and Archiving Another increasingly popular trend is people setting up and operating their own personal cloud services, using applications like Transporter, PogoPlug, and so on. The services provide users with Dropbox-type facilities, built on connected drives that are owned & controlled by the user. Those that routinely transport sensitive data on a USB drive should encrypt their data with TrueCrypt. 6. Social Networking The problem with social networking is that connects you with people who might be looking to access your personal data. If you can’t bring yourself to delete your Facebook or Twitter account, just remember that even simple information like your DOB can be misused in the wrong hands. Because even with the so-called privacy settings, you can’t control everything that is shared on your social networking feed. 7. Location Data Location data is probably the biggest leak when it comes to personal data. Avoid using location data services like the plague, including services like Google Maps, FourSquare, and any other location-based apps. Also, remember to configure the privacy settings of such apps as soon as you download them, ensuring that you’re not sharing more information than you intend to. 8. Wireless Services Even non-internet wireless services such as Infrared & Bluetooth can be doorways to your personal data. So, it’s best to keep these off, when not in use. Another gaping hole in your personal data security blanket is Wi-Fi, especially the public kind. As an added measure, try only browsing secure HTTPS connections, instead of the typically unencrypted HTTP connections. 9. Personal Security Personal security refers to the various PIN, pass and security codes that we use to access our devices and personal data. All these offer a degree of protection against unauthorized access, but even they can be decrypted. The best option is to use a passphrase instead of a password, as it’ll be too long for a hacker to decipher. Optionally, you can use password management apps, including 1Password and LastPass as they require multi-layered authentications to access. 10. Search Engines Another vulnerability is search engines; they might give you access to a world of information, but they also give the world access to yours! All mainstream search engines monitor & log things like search history, cookies, etc. These engines they create personalized results based on the information collected. The solution is to switch to a search engine that doesn’t track your searches. I am sure these 10 tips will help you secure your personal data. Please let us know if you have any other tips or suggestion and we will try to include that in next article. Article Updates Minor issue fixes and broken link fixes: March 2017 Mauricio Prinzlau works for Cloudwards.net the authority on cloud service reviews and applications for your personal and business life.
0 notes
Text
Apple Experts Recover Data from Damaged Drives
In an increasingly digital world, the data stored on our devices is more important than ever. For Apple users, MacBooks, iMacs, and Mac Minis often contain years of memories, projects, or essential work documents. So when a hard drive becomes damaged, the threat of permanent data loss can be overwhelming. Fortunately, Apple experts recover data from damaged drives every day safely, efficiently, and with a high success rate.
Whether the issue stems from a sudden hardware failure or corrupted software, certified Apple professionals are equipped with the tools and knowledge needed to bring your data back to life.
Understanding Damaged Drives in Macs
Drive damage can occur for many reasons, some of which are beyond the user’s control. In general, damage falls into two categories:
1. Physical Damage
This includes:
Dropped devices
Power surges
Water exposure
Mechanical wear (especially in older HDDs)
Overheating
2. Logical (Software) Damage
This type of issue is more common in modern Macs with SSDs:
Corrupted filesystems (like APFS)
Failed macOS updates or installations
Deleted or overwritten partitions
Malware infections (rare on Mac, but possible)
FileVault encryption errors
Both physical and logical issues can lead to inaccessible data. In more severe cases, the Mac might not even boot or recognize the internal drive at all.
Why Apple Experts Are Your Best Bet
You might come across software tools or online guides claiming to recover data from damaged drives. While these may work for minor logical issues, using them incorrectly could make things worse. Apple experts offer several clear advantages:
Apple-Certified Knowledge
These technicians have deep experience working specifically with macOS, APFS, HFS+, T2/M1/M2 security chips, and Apple hardware. Their training ensures proper handling of everything from encryption protocols to firmware-based storage.
Specialized Tools & Recovery Equipment
Apple professionals use proprietary diagnostics and imaging tools designed for Macs. This allows them to assess the damage without further compromising the drive or your data.
Secure, Confidential Data Handling
Apple-authorized centers and technicians follow strict privacy protocols. Your files are handled with discretion, and only essential personnel will access them if needed for recovery.
High Success Rates
With the right tools and expertise, Apple-certified experts can recover data even from drives considered unrecoverable by generic services.
The Apple Data Recovery Process
Here’s a step-by-step look at how Apple experts handle data recovery:
Step 1: Evaluation & Diagnosis
Technicians inspect your Mac using Apple-specific tools. They’ll assess whether the problem is physical (e.g., failed hardware) or logical (e.g., file corruption). If physical, the drive may be removed and treated using cleanroom techniques.
Step 2: Cloning the Drive
If possible, a bit-by-bit clone of the drive is created. This prevents further data loss during the recovery process, allowing technicians to work from a safe copy rather than the original damaged drive.
Step 3: Data Extraction
Experts then scan the clone using advanced data recovery software tailored to Apple’s file systems. They extract files, reconstruct damaged directories, and recover deleted or lost partitions.
Step 4: File Verification
Recovered files are tested to ensure they work as expected. Apple experts will provide you with a full report and recovered data on an external drive or cloud delivery system.
Step 5: Restoration & Prevention
If you’d like, the recovered data can be restored to a new drive or reinstalled on a repaired Mac. Experts may also help set up Time Machine or iCloud for future backups.
When to Call for Help
Here are signs that your Mac’s drive may be damaged—and that you should contact an Apple expert right away:
Mac won’t boot or freezes during startup
Disk Utility cannot repair your disk
Files are missing, corrupted, or won’t open
You hear clicking sounds (on HDDs)
macOS installation repeatedly fails
Drive doesn’t show up in Finder or Disk Utility
If you’re experiencing any of these, power off the device and avoid using third-party software. Continuing to use a damaged drive can permanently overwrite recoverable data.
Protecting Your Data Moving Forward
Apple experts not only help recover your data—they help you avoid losing it again. Here are a few pro tips they might recommend:
Enable Time Machine: Automatic backups to an external drive.
Use iCloud Drive: Sync essential documents to the cloud.
Monitor Drive Health: Use tools like Disk Utility to check drive status.
Power Down Safely: Always shut down your Mac properly to avoid file system damage.
Avoid Suspicious Software: Especially apps from untrusted sources.
Data loss may feel catastrophic, but with the right help, it doesn’t have to be permanent. Apple experts recover data from damaged drives using a combination of certified skills, advanced tools, and a deep understanding of the Mac ecosystem. From minor file corruption to complete drive failure, your data is in good hands with Apple-certified professionals.
If you're experiencing hard drive issues, don’t take risks with generic fixes. Reach out to Apple experts and get your valuable files back safely, securely, and professionally.
#iPhone Battery Replacement#Iphone Repair#Macbook Repair#iPad Screen Repair#macbook battery replacement
0 notes