#BitLocker Recovery Key Request
Explore tagged Tumblr posts
Text
How to fix BitLocker always prompting for Recovery Key
In this article, we will discuss how to fix BitLocker always prompting for Recovery Key. Please see “How to fix you are not allowed to view this folder on SSRS: MBAM reports cannot be accessed because it could not load folder contents“, and How to Change the Lock Screen Wallpaper in Windows 11. BitLocker is an encryption function of the Windows Operating System. Encrypted drives can only be…

View On WordPress
#Bitlocker#BitLocker Backup#bitlocker key#BitLocker Key Recovery#BitLocker Keys in AD#BitLocker Network Unlock#BitLocker Recovery Key Request#BitLocker Recovery Keys#BitLocker Recovery Mode prompted#BitLocker Recovery Password Viewer#Bitlocker Recovery Prompt#Windows#Windows 10#Windows 11
0 notes
Text
Supporting and Troubleshooting Windows 11 Course in Australia: A Complete Guide
Windows 11 has become the operating system of choice for businesses and individuals, offering advanced security, enhanced performance, and a modern interface. However, managing and troubleshooting Windows 11 in a professional environment requires specialized skills. The Supporting and Troubleshooting Windows 11 Course in Australia is designed to equip IT professionals with the knowledge and hands-on experience needed to support and resolve issues in Windows 11 systems efficiently.
Why Enroll in a Supporting and Troubleshooting Windows 11 Course?
With the transition from older Windows versions to Windows 11, IT support teams must adapt to new technologies, security features, and system configurations. Here’s why taking this course is beneficial:
1. Stay Updated with Windows 11 Technology
Learn about the latest Windows 11 features and enhancements.
Understand changes in system architecture and security protocols.
Gain insights into compatibility issues and best practices for troubleshooting.
2. Enhance Your IT Support Skills
Develop expertise in diagnosing and resolving Windows 11 issues.
Master tools like Windows Recovery, Event Viewer, and Command Prompt.
Improve efficiency in handling system crashes, performance issues, and network problems.
3. Increase Job Opportunities and Career Growth
IT professionals with Windows 11 troubleshooting skills are in high demand.
Employers prefer certified experts for desktop support, system administration, and IT helpdesk roles.
The course prepares you for industry-recognized certifications that boost your resume.
Key Topics Covered in the Course
The Supporting and Troubleshooting Windows 11 Course is comprehensive and designed for IT professionals, covering the following crucial areas:
1. Windows 11 Installation and Configuration
Setting up and customizing Windows 11.
Managing user accounts and permissions.
Understanding Windows Update and Feature Management.
2. Troubleshooting Boot and Startup Issues
Identifying and resolving boot failures and startup delays.
Using Advanced Startup Options and Safe Mode.
Repairing the Windows bootloader and system files.
3. Performance Optimization and System Monitoring
Using Task Manager, Resource Monitor, and Performance Monitor.
Troubleshooting slow performance and high CPU/RAM usage.
Managing background applications and startup processes.
4. Network Connectivity and Troubleshooting
Configuring and troubleshooting Wi-Fi, VPN, and Ethernet connections.
Understanding TCP/IP, DNS, and Firewall settings.
Resolving common connectivity issues and IP conflicts.
5. Security and Access Management
Implementing BitLocker encryption and Windows Defender policies.
Managing user authentication and account recovery.
Preventing and troubleshooting malware and ransomware attacks.
6. Hardware and Peripheral Troubleshooting
Diagnosing driver and compatibility issues.
Troubleshooting printer, scanner, and peripheral device failures.
Using Device Manager and Windows Troubleshooters.
7. Data Recovery and Backup Solutions
Configuring OneDrive and local backup solutions.
Recovering lost data using Windows File History and Recovery Tools.
Preventing data loss through effective backup strategies.
Who Should Take This Course?
The Supporting and Troubleshooting Windows 11 Course is ideal for:
IT Support Specialists – Handling user support and troubleshooting requests.
System Administrators – Managing enterprise Windows 11 environments.
Helpdesk Technicians – Assisting with hardware, software, and network issues.
Technical Consultants – Offering Windows 11 support for business clients.
Benefits of Certification in Windows 11 Troubleshooting
Earning a certification after completing this course offers several advantages:
Better Job Prospects: Companies prefer certified IT professionals.
Higher Salary Potential: Skilled troubleshooting experts earn more.
Enhanced Problem-Solving Skills: Learn real-world troubleshooting techniques.
Industry Recognition: Gain credibility as a Windows 11 support specialist.
Choosing the Right Training Provider in Australia
When selecting a training provider for the Supporting and Troubleshooting Windows 11 Course in Australia, consider these factors:
Accreditation: Ensure the provider is recognized by Microsoft.
Hands-on Labs: Look for courses offering real-world troubleshooting scenarios.
Flexible Learning Options: Online, classroom, or hybrid training formats.
Certification Preparation: Providers offering exam support and practice tests.
Student Reviews: Check ratings and testimonials for course quality.
Final Thoughts
The Supporting and Troubleshooting Windows 11 Course in Australia is an essential step for IT professionals looking to expand their expertise in Windows 11 support. With a structured curriculum covering installation, performance tuning, security, and network troubleshooting, this course provides the necessary skills to manage and resolve issues efficiently.
0 notes
Text
Here are all the changes and how you can download the Windows 10 Update 1909 (November 2019)
Microsoft has finally released the Windows 10 update 1909 (also known as November 2019 Update). In addition, the team has revealed all the changes and improvements that this update brings to the table.
You can download the November 2019 ISO files for updating your Windows 10 from the following links:
Windows 10 November 2019 Update (64-bit)
Windows 10 November 2019 Update (32-bit)
If this doesn’t work, you can open your Windows Update settings (Settings > Update & Security > Windows Update) and select Check for updates. Once the update appears, you can select Download and install now.
According to Microsoft, Windows 10 version 1909 makes general battery life and power efficiency improvements for PCs with certain processors. It also adds additional debugging capabilities for newer Intel processors (for hardware manufacturers).
Moreover, this update brings some CPU optimization improvements. In case you weren’t aware of, a CPU may have multiple “favored” cores (logical processors of the highest available scheduling class). To provide better performance and reliability, Microsoft has implemented a rotation policy that distributes work more fairly among these favored cores.
Below you can find all the changes that the Windows 10 November 2019 Update features:
This update will be published to WSUS so that customers can deploy and manage Insider Preview builds alongside their standard ConfigMan/WSUS approach
We are offering pre-release support for 19H2 offered to Windows Insider Program for Business (WIP4Biz) customers who face blocking issues that prevent them from feature evaluation or device use.
Windows containers require matched host and container version. This restricts customers and limits Windows containers from supporting mixed-version container pod scenarios This update includes 5 fixes to address this and allow the host to run down-level containers on up-level for process (Argon) isolation.
A fix to allow OEMs to reduce the inking latency based on the hardware capabilities of their devices rather than being stuck with latency selected on typical hardware configuration by the OS.
Key-rolling or Key-rotation feature enables secure rolling of Recovery passwords on MDM managed AAD devices upon on demand request from Microsoft Intune/MDM tools or upon every time recovery password is used to unlock the BitLocker protected drive. This feature will help prevent accidental recovery password disclosure as part of manual BitLocker drive unlock by users.
A change to enable third-party digital assistants to voice activate above the Lock screen.
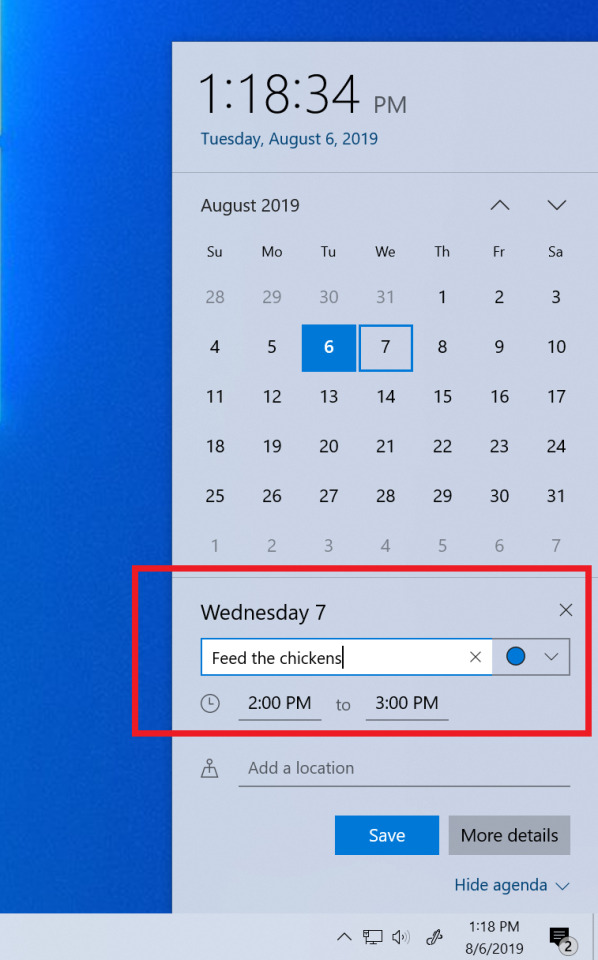
You can now quickly create an event straight from the Calendar flyout on the Taskbar. Just select the date and time at the lower right corner of the Taskbar to open the Calendar flyout and pick your desired date and start typing in the text box–you’ll now see inline options to set a time and location.
The navigation pane on the Start menu now expands when you hover over it with your mouse to better inform where clicking goes.
We have added friendly images to show what is meant by “banner” and “Action Center” when adjusting the notifications on apps in order to make these settings more approachable and understandable.
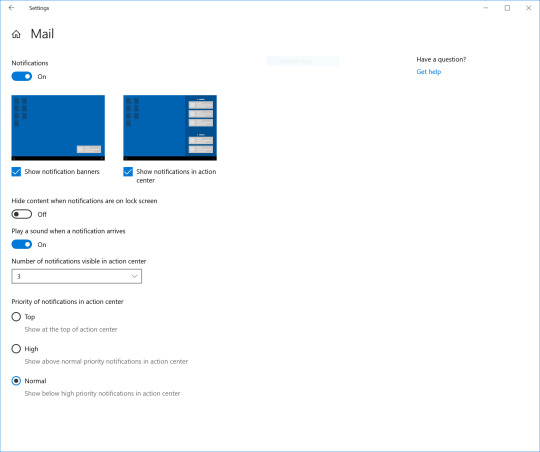
Notifications settings under Settings > System > Notifications will now default to sorting notification senders by most recently shown notification, rather than sender name. This makes it easier to find and configure frequent and recent senders. We have also added a setting to turn off playing sound when notifications appear.
We now show the options to configure and turn off notifications from an app/website right on the notification, both as a banner and in Action Center.
We have added a “Manage notifications” button to the top of Action Center that launches the main “Notifications & actions” Settings page.
We have added additional debugging capabilities for newer Intel processors. This is only relevant for hardware manufacturers.
We have made general battery life and power efficiency improvements for PCs with certain processors.
A CPU may have multiple “favored” cores (logical processors of the highest available scheduling class). To provide better performance and reliability, we have implemented a rotation policy that distributes work more fairly among these favored cores.
We have enabled Windows Defender Credential Guard for ARM64 devices for additional protection against credential theft for enterprises deploying ARM64 devices in their organizations.
We have enabled the ability for enterprises to supplement the Windows 10 in S Mode policy to allow traditional Win32 (desktop) apps from Microsoft Intune.
We’re updating the search box in File Explorer to now be powered by Windows Search. This change will help integrate your OneDrive content online with the traditional indexed results.
We have added the ability for Narrator and other assistive technologies to read and learn where the FN key is located on keyboards and what state it is in (locked versus unlocked).
The post Here are all the changes and how you can download the Windows 10 Update 1909 (November 2019) appeared first on DSOGaming.
Here are all the changes and how you can download the Windows 10 Update 1909 (November 2019) published first on https://touchgen.tumblr.com/
0 notes
Text
Windows 10 Insider Preview Build 18362.10005 (19H2) released

Windows 10 Insider Preview Build 18362.10005 (19H2) released. In addition to the fixes included in KB4507453 for the May 2019 Update, 19H2 Build 18362.10005 includes the following changes and improvements: Windows containers require matched host and container version. This restricts customers and limits Windows containers from supporting mixed-version container pod scenarios This update includes 5 fixes to address this and allow the host to run down-level containers on up-level for process (Argon) isolation.A fix to allow OEMs to reduce the inking latency based on the hardware capabilities of their devices rather than being stuck with latency selected on typical hardware configuration by the OS.Key-rolling or Key-rotation feature enables secure rolling of Recovery passwords on MDM managed AAD devices upon on demand request from in-tune/MDM tools or upon every time recovery password is used to unlock the BitLocker protected drive. This feature will help prevent accidental recovery password disclosure as part of manual BitLocker drive unlock by users.A change to enable third-party digital assistants to voice activate above the Lock screen. Please note that these changes and improvements are currently OFF by default in this build. We may ship features in these updates turned off by default and turn them on via controlled feature rollouts. Read the full article
0 notes
Text
Removal of Azure AD joined devices
I may be asking in the wrong section here, so apologies if so. Please could someone confirm whether any odd behaviour may result, after removing the AD-azure joined devices (laptops) of students who have now left the school. We have BitLocker recovery keys kept securely away from...
"Removal of Azure AD joined devices" by James Howard originally published October 19th 2018 in Office 365 topics
I may be asking in the wrong section here, so apologies if so.
Please could someone confirm whether any odd behaviour may result, after removing the AD-azure joined devices (laptops) of students who have now left the school. We have BitLocker recovery keys kept securely away from Azure AD, in case we should receive a request for the key in the future (I realise that old students should ideally change their BitLocker details)
But, are students likely to observe any strange behaviour, following the removal of the devices from Azure AD? I don't really want to create nightmare for them!
Read Full Post
0 notes
Text
Here’s How To Protect Your Privacy In Trump’s America
Gregor Cresnar / The Noun Project / Getty / Chip Somodevilla
You’d think texts to your mom and calls to your takeout place are hardly in the government’s interest, but the feds might be monitoring your communications anyway. Sweeping government surveillance programs have grown in recent years – and some digital privacy advocates believe that civilian snooping will continue to expand under President Trump’s watch.
In the first half of 2016, government requests for Facebook account data were up 27% from the previous year, while requests for Google user data in the same period hit a record high of 44,943. The country that submitted the most requests to both of those sites? The United States.
Both presidents Bush and Obama supported domestic surveillance, and experts are concerned that the Trump administration will only strengthen that authority. According to Jay Stanley, a senior policy analyst at the American Civil Liberties Union, “There are extra reasons to worry under a Trump administration based on things he has supported.”
Trump has specifically called for the monitoring of mosques and activist groups like Black Lives Matter. He has also supported the reauthorization of NSA’s data collection program, which was discontinued in June 2015.
So, if you’re feeling, er, unnerved, here’s how to protect your information not only from Uncle Sam, but from hackers and prying corporations, too.
When you’re looking for tools to protect your privacy, there are many aspects to consider, but here are three important ones, according to the Electronic Frontier Foundation’s Noah Swartz:
1. Is the program open source? This allows other engineers to verify that its code is kept up to date, and that its encryption and privacy settings retain strong encryption and best practices.
2. Where is the data stored? Is it on someone else’s servers? In that case, find out who has the encryption keys.
3. Does it make promises that are too good to be true? Steer clear of vague language.
Hackers find security vulnerabilities all the time, so nothing is 100% bulletproof. That’s why it’s important to update your personal technology frequently, create strong passwords, and change those passwords often. The word encryption is thrown around a lot when you’re looking for secure apps and services. Here’s what it means: When a message sent to you is encrypted, the message looks like gibberish to anyone except you and the sender. It’s a complex algorithm that ensures the message can’t be intercepted by your internet provider or your data carrier. The most common way apps use encryption is in transit, when the message is traveling through Internet cables or bouncing between cell towers. If you’re looking for a platform that’s truly secure, it should offer what’s called end-to-end encryption, which means that it’s encrypted all the way, as it travels between “ends”: when it leaves the sender’s device, when it hits the platform’s servers, and when it arrives at the recipient’s device. But, ultimately, end-to-end encryption doesn’t matter if an unauthorized person can easily get into one of those “ends” AKA your phone, computer, or accounts. Encryption is only as secure as your personal devices, so here are the most ~*basic*~ security measures you can, and should, take:
Add a passcode, dummy!
You wouldn’t leave your bike unlocked on the street, would you? At the very least, add a numeric code to your phone. (Pro-tip: don’t use “1234” or “0000.”) For those who want to be *super* secure, add a passcode with both numbers and letters, or an alphanumeric code.
For now, police can’t compel you to give up your passcode, but they can force you to use your fingerprint. So be wary of Touch ID, Pixel Imprint, and other fingerprint unlock features that are convenient, but may compromise your security.
In iOS, go to Settings > Touch ID & Passcode > Change Passcode > tap Passcode Options > Custom Alphanumeric Code. In Android, go to Settings > under Personal, tap Security > Screen lock > PIN or Password. Additionally, encrypt your phone from the Security page (iPhones are encrypted by default).
Nicole Nguyen / BuzzFeed News
On your computer, add a login password and encrypt your computer’s hard drive.
On the Mac, go to System Preferences > Security & Privacy and set to Require a password for a certain time after sleep. Then move to the FileVault tab to turn on encryption. Don’t forget your FileVault recovery key!
On a PC, go to Start > type encryption > select Change device encryption settings > Manage BitLocker > Turn on BitLocker.
Turn on remote lock-and-erase for your devices.
For Mac and iOS, set up Find My Mac and Find My iPhone. From iCloud.com/find, you can completely wipe data from your Apple device remotely, as soon as it connects to the Internet. For Android, find my phone is automatically enabled once you’ve connected the device to your Google account. Go to http://ift.tt/149V2zm to locate or erase data on the phone by performing a factory reset. For Windows 10 computers, go to http://ift.tt/1ukQ86e to locate, ring, lock, and erase.
Update your software as soon as a new version is available, no matter how annoying those pop-ups are.
It is always worth your time to do so. If you don’t, it’ll make you more vulnerable to hackers who monitor which security holes were patched in the new update, in order to target those in older versions of the software.
Add two-factor authentication to every account you can.
Not just for email and social media accounts, but for online banking, gaming, and retail, too. It requires that you submit a verification code sent to your phone, in addition to a traditional password, to log in. Do it for Gmail immediately! Then, make sure your recovery email or phone are equally secure. Here’s a comprehensive list of websites that support two-factor authentication.
Nicole Nguyen / BuzzFeed News
After enabling two-factor, add an additional layer of security to your mobile carrier account by requiring a PIN when you call customer service. If someone has your name and the last four digits of your Social Security number, they can change the SIM number associated with your phone, rerouting two-factor verification codes to another device. An extra PIN helps prevent this. Here’s how to add one if you’re a Verizon, T-Mobile, Sprint, or AT&T customer.
OK, this is going to be a long section, because there are a lot of encrypted messaging apps out there. The TL;DR is that if you’re using one of the five apps mentioned here, you’re already communicating pretty securely.
Signal (free for iOS and Android), Wickr (free for iOS and Android), WhatsApp (free for iOS, Android and Windows Phone), Google Allo’s incognito mode (free for iOS and Android), and iMessage between iPhones (free for iOS) are five messaging apps that provide end-to-end encryption. If a government issues a request to any of these platforms, they won’t be able to hand over the content of messages. However, each service handles their users’ metadata (in other words, who you messaged and when) a bit differently. It’s important to keep in mind that none of these apps can guarantee you total, uncrackable security — each one has its pros and cons.
Signal
The pros: Signal is very popular. NSA whistleblower Edward Snowden endorsed the app, and after Trump was elected, downloads increased by 400%.
By default, Signal doesn’t store your messages or metadata. The app provides a “safety number” for each conversation used to verify a person’s authenticity. Users can also elect to make messages disappear during intervals, whether it’s of five seconds or a week. Most important of all, Signal’s code is open to review and anyone can audit the software or contribute improvements.
The cons: When you sign up, Signal requires access to your address book, and as my colleague Hamza Shaban pointed out, that risks ratting out whistleblowers — if someone knows your number, they can tell whether or not you’re on Signal. If you were spilling stories about your company’s wrongdoings to a journalist, you might not want your boss to know that you’re using Signal. Moxie Marlinspike, the founder of Open Whisper Systems, the nonprofit behind Signal, suggests using a throwaway Google Voice or VoIP number as a workaround to sign up for Signal.
Wickr
The pros: Wickr offers all of Signal’s encrypted features. One advantage the app has over Signal is that Wickr does not need your phone number to sign up. Users have the option to create a unique handle, which protects those who don’t want their identities linked to the service.
The cons: Its code isn’t available for independent review, and Wickr’s user base isn’t as large as Signal’s, so it’s likely that you’ll need to convince contacts to sign up before you can start messaging with them.
WhatsApp
The pros: WhatsApp uses Signal’s protocol for encryption. It has the advantage of having over one billion users already on its platform, and it’s a feature-rich app with group messaging, voice calls and video chat built-in.
The cons: While the app, which is owned by Facebook, can’t read individual messages, it can record metadata like date, time stamp, and phone numbers associated with that message, according to a recently revised privacy policy. The app also announced last year that it was going to start sharing user information with Facebook, though it does let you opt out before agreeing to the updated terms of service. If you don’t opt out at that time, you have an additional 30 days to make your choice.
WhatsApp doesn’t include the option for disappearing messages. It also turns off security notifications when a contact’s key has changed (which occurs when they’ve re-installed WhatsApp on a new phone) by default, making you more susceptible to “man-in-the-middle” attacks by hackers.
Furthermore, the app allows you to backup your messages to iCloud or Google, which, while convenient if you lose your phone to switch to a new one, is not protected by WhatsApp’s end-to-end encryption.
Nicole Nguyen / BuzzFeed News
Allo
The pros: Google’s new messaging app includes the company’s artificial intelligence Google Assistant, which can help with tasks like making restaurant reservations or looking up movie times. It offers encrypted messaging with limited features (Google Assistant won’t work with it turned on) and you can set their messages to disappear after a certain period of time.
The cons: End-to-end encryption is disabled by default and you need to turn on incognito mode yourself.
Nicole Nguyen / BuzzFeed News
iMessage
The pros: Apple does provide end-to-end encryption for iMessage content (read more about its encryption technique on page 41 of this guide), and the company itself can’t decrypt the data – but only when both users sending messages have iPhones.
The cons: When you enter a phone number into iMessage, that number is sent to to Apple servers to determine whether or not that contact’s bubble should be green or blue (or, rather, whether to send the text through iMessage or SMS). Apple retains that data for up to 30 days and can be forced to hand it over to law enforcement with a subpoena or court order.
Many of the same apps that offer secure messaging also offer encrypted phone calls, including Signal and WhatsApp.
If you don’t use Signal or Whatsapp, any app that uses Ostel, an open source, end-to-end encrypted phone call tool, allows you to talk freely and securely. The easiest and cheapest way (it’s free!) to place a call through Ostel is through the Jitsi app for Mac, Windows, and Linux. An iOS app called Acrobits Softphone will cost you a one-time $7 fee to download the app, but this version only allows you to receive encrypted calls. Placing encrypted calls costs an additional $25.
While Gmail emails are encrypted in transit, Google’s popular email service is not secure enough for sensitive information. Google reads the contents of your email to determine which email appears in the Priority Inbox and, ultimately, to show you more personalized ads. If you’re getting a lot of emails about winter boots, you’ll see more winter boot banner ads.
For simple encryption, you can use Chrome extension CryptUp for Gmail, which is easy to set up for n00bs but has an advanced settings options for nerds. It allows users to add a “challenge question” that only your recipient can answer to decrypt the message. If the recipient has CryptUp installed, you can send small, encrypted attachments as well.
To take your email security a step further, you’ll need to familiarize yourself with “PGP” or “Pretty Good Privacy” encryption. First, install the Mailvelope extension for Chrome or Firefox, which works for Gmail, Outlook.com, Yahoo! Mail, and GMX. Click on the extension icon and then click Options. Follow the instructions to Generate Key. Now, you have a public and private key.
Nicole Nguyen / BuzzFeed News
from DIYS http://ift.tt/2jwK3Re
0 notes
Text
Here’s How To Protect Your Privacy In Trump’s America
Gregor Cresnar / The Noun Project / Getty / Chip Somodevilla
You’d think texts to your mom and calls to your takeout place are hardly in the government’s interest, but the feds might be monitoring your communications anyway. Sweeping government surveillance programs have grown in recent years – and some digital privacy advocates believe that civilian snooping will continue to expand under President Trump’s watch.
In the first half of 2016, government requests for Facebook account data were up 27% from the previous year, while requests for Google user data in the same period hit a record high of 44,943. The country that submitted the most requests to both of those sites? The United States.
Both presidents Bush and Obama supported domestic surveillance, and experts are concerned that the Trump administration will only strengthen that authority. According to Jay Stanley, a senior policy analyst at the American Civil Liberties Union, “There are extra reasons to worry under a Trump administration based on things he has supported.”
Trump has specifically called for the monitoring of mosques and activist groups like Black Lives Matter. He has also supported the reauthorization of NSA’s data collection program, which was discontinued in June 2015.
So, if you’re feeling, er, unnerved, here’s how to protect your information not only from Uncle Sam, but from hackers and prying corporations, too.
When you’re looking for tools to protect your privacy, there are many aspects to consider, but here are three important ones, according to the Electronic Frontier Foundation’s Noah Swartz:
1. Is the program open source? This allows other engineers to verify that its code is kept up to date, and that its encryption and privacy settings retain strong encryption and best practices.
2. Where is the data stored? Is it on someone else’s servers? In that case, find out who has the encryption keys.
3. Does it make promises that are too good to be true? Steer clear of vague language.
Hackers find security vulnerabilities all the time, so nothing is 100% bulletproof. That’s why it’s important to update your personal technology frequently, create strong passwords, and change those passwords often. The word encryption is thrown around a lot when you’re looking for secure apps and services. Here’s what it means: When a message sent to you is encrypted, the message looks like gibberish to anyone except you and the sender. It’s a complex algorithm that ensures the message can’t be intercepted by your internet provider or your data carrier. The most common way apps use encryption is in transit, when the message is traveling through Internet cables or bouncing between cell towers. If you’re looking for a platform that’s truly secure, it should offer what’s called end-to-end encryption, which means that it’s encrypted all the way, as it travels between “ends”: when it leaves the sender’s device, when it hits the platform’s servers, and when it arrives at the recipient’s device. But, ultimately, end-to-end encryption doesn’t matter if an unauthorized person can easily get into one of those “ends” AKA your phone, computer, or accounts. Encryption is only as secure as your personal devices, so here are the most ~*basic*~ security measures you can, and should, take:
Add a passcode, dummy!
You wouldn’t leave your bike unlocked on the street, would you? At the very least, add a numeric code to your phone. (Pro-tip: don’t use “1234” or “0000.”) For those who want to be *super* secure, add a passcode with both numbers and letters, or an alphanumeric code.
For now, police can’t compel you to give up your passcode, but they can force you to use your fingerprint. So be wary of Touch ID, Pixel Imprint, and other fingerprint unlock features that are convenient, but may compromise your security.
In iOS, go to Settings > Touch ID & Passcode > Change Passcode > tap Passcode Options > Custom Alphanumeric Code. In Android, go to Settings > under Personal, tap Security > Screen lock > PIN or Password. Additionally, encrypt your phone from the Security page (iPhones are encrypted by default).
Nicole Nguyen / BuzzFeed News
On your computer, add a login password and encrypt your computer’s hard drive.
On the Mac, go to System Preferences > Security & Privacy and set to Require a password for a certain time after sleep. Then move to the FileVault tab to turn on encryption. Don’t forget your FileVault recovery key!
On a PC, go to Start > type encryption > select Change device encryption settings > Manage BitLocker > Turn on BitLocker.
Turn on remote lock-and-erase for your devices.
For Mac and iOS, set up Find My Mac and Find My iPhone. From iCloud.com/find, you can completely wipe data from your Apple device remotely, as soon as it connects to the Internet. For Android, find my phone is automatically enabled once you’ve connected the device to your Google account. Go to http://ift.tt/149V2zm to locate or erase data on the phone by performing a factory reset. For Windows 10 computers, go to http://ift.tt/1ukQ86e to locate, ring, lock, and erase.
Update your software as soon as a new version is available, no matter how annoying those pop-ups are.
It is always worth your time to do so. If you don’t, it’ll make you more vulnerable to hackers who monitor which security holes were patched in the new update, in order to target those in older versions of the software.
Add two-factor authentication to every account you can.
Not just for email and social media accounts, but for online banking, gaming, and retail, too. It requires that you submit a verification code sent to your phone, in addition to a traditional password, to log in. Do it for Gmail immediately! Then, make sure your recovery email or phone are equally secure. Here’s a comprehensive list of websites that support two-factor authentication.
Nicole Nguyen / BuzzFeed News
After enabling two-factor, add an additional layer of security to your mobile carrier account by requiring a PIN when you call customer service. If someone has your name and the last four digits of your Social Security number, they can change the SIM number associated with your phone, rerouting two-factor verification codes to another device. An extra PIN helps prevent this. Here’s how to add one if you’re a Verizon, T-Mobile, Sprint, or AT&T customer.
OK, this is going to be a long section, because there are a lot of encrypted messaging apps out there. The TL;DR is that if you’re using one of the five apps mentioned here, you’re already communicating pretty securely.
Signal (free for iOS and Android), Wickr (free for iOS and Android), WhatsApp (free for iOS, Android and Windows Phone), Google Allo’s incognito mode (free for iOS and Android), and iMessage between iPhones (free for iOS) are five messaging apps that provide end-to-end encryption. If a government issues a request to any of these platforms, they won’t be able to hand over the content of messages. However, each service handles their users’ metadata (in other words, who you messaged and when) a bit differently. It’s important to keep in mind that none of these apps can guarantee you total, uncrackable security — each one has its pros and cons.
Signal
The pros: Signal is very popular. NSA whistleblower Edward Snowden endorsed the app, and after Trump was elected, downloads increased by 400%.
By default, Signal doesn’t store your messages or metadata. The app provides a “safety number” for each conversation used to verify a person’s authenticity. Users can also elect to make messages disappear during intervals, whether it’s of five seconds or a week. Most important of all, Signal’s code is open to review and anyone can audit the software or contribute improvements.
The cons: When you sign up, Signal requires access to your address book, and as my colleague Hamza Shaban pointed out, that risks ratting out whistleblowers — if someone knows your number, they can tell whether or not you’re on Signal. If you were spilling stories about your company’s wrongdoings to a journalist, you might not want your boss to know that you’re using Signal. Moxie Marlinspike, the founder of Open Whisper Systems, the nonprofit behind Signal, suggests using a throwaway Google Voice or VoIP number as a workaround to sign up for Signal.
Wickr
The pros: Wickr offers all of Signal’s encrypted features. One advantage the app has over Signal is that Wickr does not need your phone number to sign up. Users have the option to create a unique handle, which protects those who don’t want their identities linked to the service.
The cons: Its code isn’t available for independent review, and Wickr’s user base isn’t as large as Signal’s, so it’s likely that you’ll need to convince contacts to sign up before you can start messaging with them.
WhatsApp
The pros: WhatsApp uses Signal’s protocol for encryption. It has the advantage of having over one billion users already on its platform, and it’s a feature-rich app with group messaging, voice calls and video chat built-in.
The cons: While the app, which is owned by Facebook, can’t read individual messages, it can record metadata like date, time stamp, and phone numbers associated with that message, according to a recently revised privacy policy. The app also announced last year that it was going to start sharing user information with Facebook, though it does let you opt out before agreeing to the updated terms of service. If you don’t opt out at that time, you have an additional 30 days to make your choice.
WhatsApp doesn’t include the option for disappearing messages. It also turns off security notifications when a contact’s key has changed (which occurs when they’ve re-installed WhatsApp on a new phone) by default, making you more susceptible to “man-in-the-middle” attacks by hackers.
Furthermore, the app allows you to backup your messages to iCloud or Google, which, while convenient if you lose your phone to switch to a new one, is not protected by WhatsApp’s end-to-end encryption.
Nicole Nguyen / BuzzFeed News
Allo
The pros: Google’s new messaging app includes the company’s artificial intelligence Google Assistant, which can help with tasks like making restaurant reservations or looking up movie times. It offers encrypted messaging with limited features (Google Assistant won’t work with it turned on) and you can set their messages to disappear after a certain period of time.
The cons: End-to-end encryption is disabled by default and you need to turn on incognito mode yourself.
Nicole Nguyen / BuzzFeed News
iMessage
The pros: Apple does provide end-to-end encryption for iMessage content (read more about its encryption technique on page 41 of this guide), and the company itself can’t decrypt the data – but only when both users sending messages have iPhones.
The cons: When you enter a phone number into iMessage, that number is sent to to Apple servers to determine whether or not that contact’s bubble should be green or blue (or, rather, whether to send the text through iMessage or SMS). Apple retains that data for up to 30 days and can be forced to hand it over to law enforcement with a subpoena or court order.
Many of the same apps that offer secure messaging also offer encrypted phone calls, including Signal and WhatsApp.
If you don’t use Signal or Whatsapp, any app that uses Ostel, an open source, end-to-end encrypted phone call tool, allows you to talk freely and securely. The easiest and cheapest way (it’s free!) to place a call through Ostel is through the Jitsi app for Mac, Windows, and Linux. An iOS app called Acrobits Softphone will cost you a one-time $7 fee to download the app, but this version only allows you to receive encrypted calls. Placing encrypted calls costs an additional $25.
While Gmail emails are encrypted in transit, Google’s popular email service is not secure enough for sensitive information. Google reads the contents of your email to determine which email appears in the Priority Inbox and, ultimately, to show you more personalized ads. If you’re getting a lot of emails about winter boots, you’ll see more winter boot banner ads.
For simple encryption, you can use Chrome extension CryptUp for Gmail, which is easy to set up for n00bs but has an advanced settings options for nerds. It allows users to add a “challenge question” that only your recipient can answer to decrypt the message. If the recipient has CryptUp installed, you can send small, encrypted attachments as well.
To take your email security a step further, you’ll need to familiarize yourself with “PGP” or “Pretty Good Privacy” encryption. First, install the Mailvelope extension for Chrome or Firefox, which works for Gmail, Outlook.com, Yahoo! Mail, and GMX. Click on the extension icon and then click Options. Follow the instructions to Generate Key. Now, you have a public and private key.
Nicole Nguyen / BuzzFeed News
from DIYS http://ift.tt/2jwK3Re
0 notes
Text
Selfservice Recovery: Trellix BitLocker and fileVault Recovery
Trellix Management for Native Encryption (MNE) is a management product that allows ePO administrators to manage Apple FileVault and Microsoft BitLocker. These programs are the native encryption offerings on macOS and Windows operating systems. MNE can also help users in system recovery, and provides rich audit and reporting capabilities. In this article, we shall discuss “Trellix BitLocker and…

View On WordPress
#Bitlocker#bitlocker key#BitLocker Key Recovery#BitLocker Recovery Key Request#BitLocker Recovery Keys#FileVault#Macbook#MacBook M1#MacOS#macOS Big Sur#macOS Monterey#macOS Ventura#Microsoft Windows#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes