#Gmail Password Recovery Online
Explore tagged Tumblr posts
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
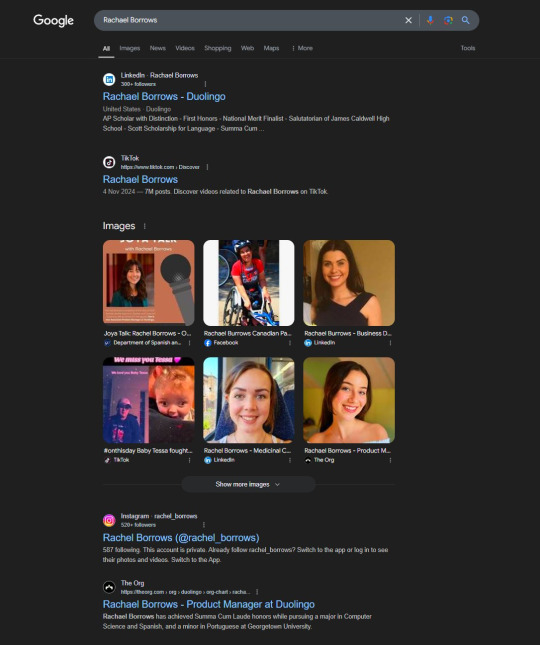
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
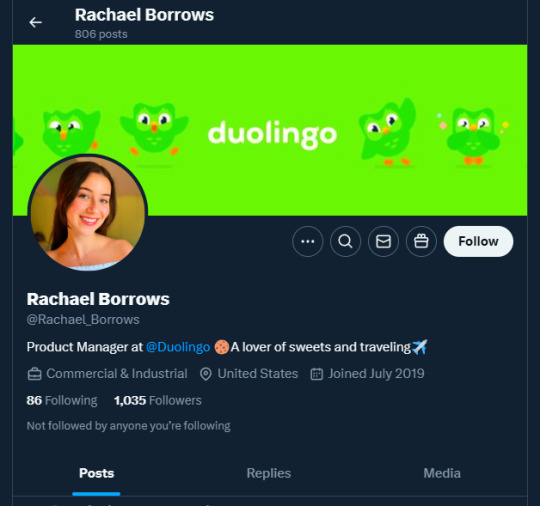
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
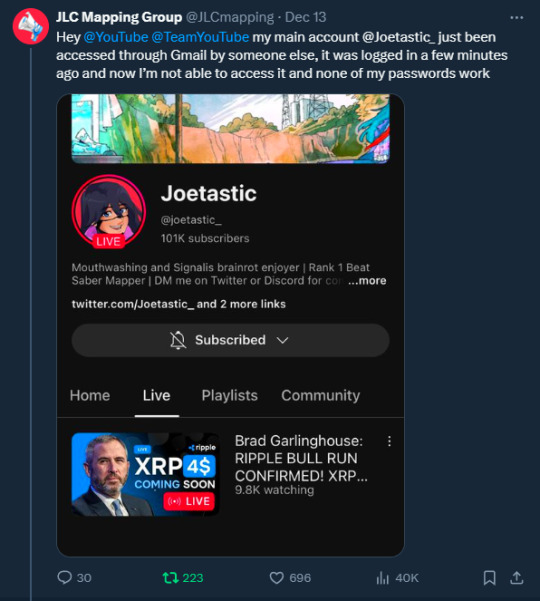
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
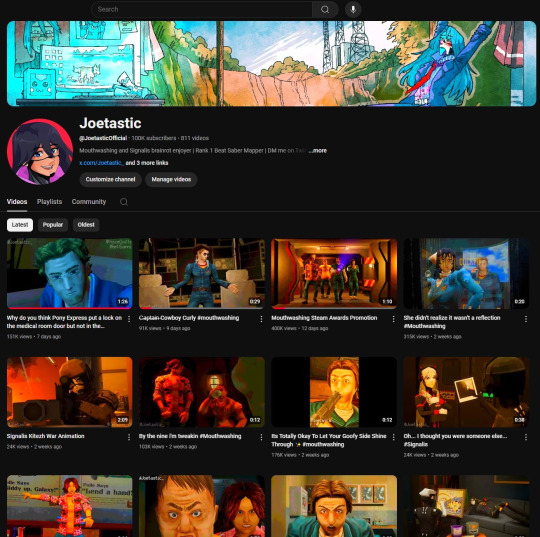
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
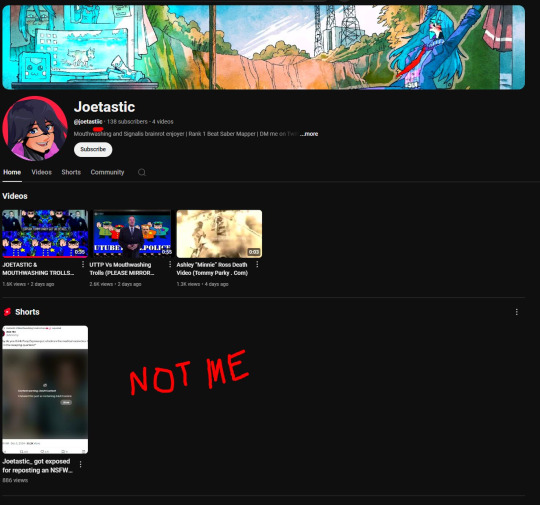
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Inactive Gmail Accounts Deletion Next Month December 2023 - Secure Steps to Keep Your Google Account Active
Introduction: As we navigate the vast digital landscape, keeping our online accounts secure and active is crucial. Google has recently announced an upcoming cleanup initiative that targets inactive Gmail accounts. Scheduled for deletion next month, this proactive measure aims to enhance security and manage data storage efficiently. In this blog post, we’ll guide you through the steps to ensure…

View On WordPress
#Account Access#Account Activity#Account Maintenance#Account Notifications#Account Recovery#Cleanup#Cybersecurity#Data Storage#Deletion#Digital Cleanup#Gmail#Google Account#Google Services#Inactive Accounts#Online Privacy#Online Security#Password Security#Security Measures#Third-Party Apps#Two-Factor Authentication
0 notes
Text
Rant incoming
WHY IS TECHNOLOGY SUPPORT SO GODDAMM DIFFICULT I SWEAR TO GOD.
So. I want to play minecraft online. I don't really use my Microsoft account often but I figure it should be fine. I get signed up for PS Plus, I pay my £6.99, and now I just have to link my Microsoft.
I do the link. I submit the code, then the email, then the password...then the code again then the email then the password and so on so forth until the link expires.
I make a new Microsoft account, as suggested, and it actually seems to be getting somewhere. Until the game is like "Oh you have to sign into the account linked with your game. Yknow, Jyan, which we can remember the name of but not your freaking details".
So I try that. Get in a loop again because it's that outlook email. I sign into Gmail outlook, everything looks fine. I have a string of very recent emails from Amazon about a refund so I know my email *works* at least.
But log in still won't work. So I look on the Microsoft question thing for answers and someone has had the loop issue. There's a link about account recovery. I'm desperate, I mean what the hell nothing else is working, so I use that link. They ask for an alternative email to send me a confirmation where they explain that I did not give them enough details and, as a really really kind courtesy (BECAUSE THATS HOW THEY PHRASED THIS, LIKE IT WAS A COURTESY) they've locked me out of my account :). Yay :). Because they take security reallllly seriously. Except they haven't Because I can still access my emails on the Gmail app but still can't do anything else.
By the way, did you know once you link a Microsoft account to a ps4 account you can NEVER UNLINK AND RELINK A NEW ONE?! Why. What do you GAIN Microsoft. Oh also because ps plus is a paid service they really hate you using it on other accounts of the same ps4 device or really any online features on any account other than the main one. Because what.
So clearly my issue is too complicated for online articles. I've tried and got no where, in any case worse. Let's try reddit - SYKE ALL THE BOTS RUINED REDDIT AND I CANT ACCESS ANY TECH SUPPORT GROUPS TO ASK QUESTIONS MYSELF UNLESS I GET SO MUCH KARMA. GREAT.
So. Microsoft tech support. Please be a good - OH OF COURSE ITS NOT
To summarise this amazinggggg service
1 - CAN'T FIND A RELIABLE NUMBER BECAUSE OF THE SCAMS
1.5 - Google AI summarise RECOMMENDED ME A SCAM NUMBER AS THE OFFICIAL ONE
2 - I can't find anywhere where I can submit a text complaint.
3 - All the search bars just take me to pre written articles as if I haven't read enougj
4 - THEY THEN OFFER ME A PAIDDDDD SERVICE TO "GET FIRST IN LINE FOR GPT TO SOLVE MY ISSUE"
What. The actual. Fuck.
I just want to talk to a human who knows something PLEASE. No none of the articles have helped. No I don't want AI to tell me, it has PROVEN its USELESSNESS. I just wanna talk yo a freaking human, preferably over the phone, who can tell me what to do or initiate some stiff themself because clearly the design has self imploded and IM JUST SO FREAKING FRUSTRATED IM SAT HERE WITH £7 OF A WORTHLESS SUBSCRIPTION AND NO RELIABLE TECH SUPPORT TO FIX IT ALL BECAUSE EMAIL BROKE BUT NOT REALLY.
And that doesn't even BEGIN to worry about whether I'm gonna be able to get my money back on this completely useless service.
So I'm turning to Tumblr. What's tumblrs tech support like??? I don't know, maybe there's a genius out there SOMEWHERE. Because clearly I can't use reddit, thanks barrier to entry :/ and I can't just ring up a human who can actually listen to my words with the nuances that don't fit into the fucking booklet.
If anyone knows anything that could help, please leave your wisdom here I'm frustrated and desperate and don't wanna lose £7 on something I can't even use.
3 notes
·
View notes
Text
Looking for New or Aged Gmail Accounts? Here’s a Smart Way to Get Them
Managing several online projects or running digital campaigns often requires more than one Gmail account—sometimes even ones with a bit of age and history. So, what's the smartest way to get reliable Gmail accounts without wasting time or risking bans?
Instead of struggling with manual creation or using risky bots, there’s a much better solution: post a custom microtask on Sproutgigs.
What Makes Sproutgigs So Useful?
Sproutgigs is a platform where freelancers from all over the world complete small jobs, fast. You describe what you need, and professionals jump in to help. It's quick, cost-effective, and flexible.
Here are just a few things you can request:
Fresh Gmail accounts with recovery details
Older accounts with login history
Country-specific setups
Unique usernames or defined passwords
Accounts verified with a phone number
All you need to do is post a clear set of instructions, and interested freelancers will start submitting the accounts.
Why Outsource This Task?
Setting up multiple Gmail accounts by yourself can be tedious and complicated—especially if you're trying to get around verification or regional restrictions. Plus, doing it wrong might get the accounts flagged.
By letting someone experienced handle it, you avoid technical headaches, reduce risk, and save valuable time.
0 notes
Text
Securing Email Accounts: A Practical Guide to Protecting Your Online Identity

Your email account is the gateway to your digital life. Think about it: almost every online account you have is tied to your email. This makes securing your email one of the most critical steps in protecting yourself from cyberattacks, fraud, and identity theft.
In this guide, I’ll walk you through actionable tips to secure your email accounts and keep them safe from hackers and other online threats.
Why Is Email Security So Important?
Email isn’t just for communication anymore. It holds sensitive information like:
Password reset links for other accounts
Personal and financial details
Business or work-related information
If a hacker gains access to your email, they could reset passwords for your online accounts, steal sensitive data, or even commit fraud in your name.
Common Threats to Email Security
1. Phishing Attacks
Phishing emails are fake messages designed to steal your login credentials or sensitive information. They often appear to come from trusted sources like your bank or email provider.
2. Weak Passwords
Passwords like “123456” or “password” make it easy for hackers to break in. Weak passwords are one of the most common causes of email breaches.
3. Malware and Spyware
Clicking on suspicious links or downloading unknown attachments can install malware that captures your login details.
4. Public Wi-Fi Risks
Accessing your email on unsecured public Wi-Fi can expose your data to hackers using the same network.
5. Lack of Two-Factor Authentication (2FA)
Without 2FA, a hacker only needs your password to access your email.
How to Secure Your Email Account
1. Use a Strong and Unique Password
Your password is your first line of defense. Here’s how to make it strong:
Use at least 12 characters, including letters, numbers, and symbols.
Avoid using personal information like birthdays or names.
Use a unique password for each account.
If you find it hard to remember complex passwords, use a password manager to store them securely.
2. Enable Two-Factor Authentication (2FA)
2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone. Most email providers offer this feature, and it’s easy to set up.
3. Beware of Phishing Emails
Never click on links or download attachments from unknown senders.
Double-check the sender’s email address for inconsistencies.
If an email claims to be from your bank or a service provider, visit their official website directly instead of clicking on links in the email.
4. Secure Your Recovery Options
Ensure your recovery email and phone number are up-to-date. This will help you regain access if you’re locked out of your account.
5. Avoid Public Wi-Fi
When checking your email on public Wi-Fi, use a Virtual Private Network (VPN) to encrypt your connection. This prevents hackers from intercepting your data.
6. Regularly Update Your Security Settings
Check your email account settings periodically:
Review connected devices and log out of those you don’t recognize.
Update security questions to avoid answers easily guessed from your social media profiles.
7. Monitor Your Email Activity
Many email services allow you to view your recent login activity. Check for unfamiliar locations or devices and secure your account immediately if you spot anything suspicious.
8. Use Encryption
Encryption ensures that your email messages can only be read by the intended recipient. Some email providers like ProtonMail offer end-to-end encryption by default.
9. Keep Software Updated
Outdated browsers or email apps can have vulnerabilities. Always use the latest version of your email app, operating system, and browser.
10. Use a Secure Email Provider
Consider switching to an email provider known for its robust security features, such as Gmail, ProtonMail, or Outlook.
What to Do If Your Email Is Compromised
Even with precautions, email breaches can happen. Here’s what to do:
Change Your Password Immediately Make it strong and unique. If you can’t log in, use the recovery options to regain access.
Enable 2FA If it wasn’t already active, turn it on as soon as you regain control of your account.
Check for Forwarding Rules Hackers often set up forwarding rules to receive copies of your emails. Delete any rules you didn’t create.
Review Connected Accounts Update passwords for any online accounts linked to your email.
Contact Your Email Provider Report the breach and follow their guidance for securing your account.
Best Practices for Long-Term Email Security
Regularly change your email password.
Avoid sharing your email address on public forums.
Don’t reuse old passwords for other accounts.
Use different email accounts for personal and business purposes.
Conclusion
Your email account is a treasure trove of information, making it a prime target for cybercriminals. By following these steps—using strong passwords, enabling 2FA, and staying vigilant—you can significantly reduce the risk of an email breach. Remember, a secure email account means a safer online experience overall.
FAQs
1. How often should I change my email password? Change your email password every 3–6 months, or immediately if you suspect a breach.
2. Is it safe to use public Wi-Fi for email? It’s risky to use public Wi-Fi without a VPN. Hackers can intercept your data on unsecured networks.
3. What is two-factor authentication (2FA)? 2FA requires a second verification step, like a code sent to your phone, making it harder for hackers to access your account.
4. Can a password manager help with email security? Yes, password managers store and generate strong, unique passwords for each account, reducing the risk of breaches.
5. What should I do if I suspect phishing? Delete the email immediately, don’t click on any links, and report it to your email provider.
0 notes
Text
Buy Old Gmail PVA Accounts: Reliable and Verified
Buy Old Gmail PVA Accounts: Unlock Reliable Email Solutions Are you looking to enhance your digital marketing strategies, boost your online presence, or manage multiple accounts efficiently? Purchasing old Gmail PVA (Phone Verified Accounts) can be the perfect solution. These accounts come with verified phone numbers and a history of use, offering excellent reliability and credibility for personal or business applications. What Are Old Gmail PVA Accounts? Old Gmail PVA accounts are Gmail accounts created long ago, verified with phone numbers, and often used actively. Due to their age and consistent activity, they are less likely to face restrictions, making them ideal for tasks like: Social Media Marketing: Using multiple accounts to promote brands and engage audiences. Bulk Email Campaigns: Running email outreach with accounts that have a trusted history. SEO and Backlinking: Managing submissions on forums or directories that require authentic accounts. Secure Data Management: Safeguarding sensitive business or personal data. Why Choose Old Gmail PVA Accounts? Trust and Reputation: Email providers and platforms view Older accounts as more credible. Stability: Reduced risk of bans or suspensions compared to newly created accounts. High Deliverability: Ideal for email marketing campaigns, as their history improves email inboxing rates. Pre-Verified Accounts: Save time and hassle with accounts already verified through a phone number. Where to Buy Old Gmail PVA Accounts? When purchasing old Gmail PVA accounts, it's essential to work with reputable providers who ensure: Genuine Accounts: Authentic, phone-verified Gmail accounts created with unique IPs. Customization Options: Accounts tailored to your needs, such as age, gender, or region. Secure Delivery: Proper transfer of login details, ensuring confidentiality and security. Customer Support: Reliable after-sales service for technical issues or account replacements. Best Practices for Using Purchased Accounts Change Login Details: Update the password and recovery information immediately after purchase. Use Unique IPs: Access accounts using different IP addresses to avoid triggering Gmail's security algorithms. Gradual Usage: Start with minimal activities and increase gradually to maintain authenticity. Avoid Spamming: Use accounts responsibly to prevent being flagged by Gmail's anti-abuse systems. Conclusion Investing in buy old Gmail PVA accounts can streamline operations and enhance online productivity. Whether you're a marketer, entrepreneur, or individual looking for robust email solutions, these accounts provide a valuable head start. Ensure you choose a trusted provider for secure, reliable, high-quality accounts tailored to your needs.
0 notes
Text
Buy Old Gmail Accounts USA PVA 2003-2023
VPN Create Gmail (Mix Country).
USA Male & Female Name (Random).
English Language.
Random Strong Password.
Lifetime Password Guarantee.
Recovery added.
Instant Delivary.
3 Days Replacements Guarantee.
100% Satisfaction Guarantee.
What are PVA accounts?
PVA accounts are those that require phone number verification. When compared to unverified accounts, these accounts are safer.
Non-verified accounts can be used in just a single country in which these accounts are created while PVA accounts can be used all over the world. PVA accounts are in handy for a variety of social networking platforms, including Twitter, Instagram, Gmail, Facebook, YouTube, and many more. PVA accounts outperform non-PVA accounts in terms of effectiveness.
Buy Old Gmail PVA Account
You should purchase Gmail accounts if you wish to utilize them for personal or professional purposes. If you want to buy Gmail accounts, we suggest you buy PVA accounts from a verified company. We are offering 100% verified and guaranteed accounts in the market. Our company is the best Gmail accounts provider because we care about customer choice. We provide both PVA and non-PVA accounts. If you want to order many accounts, we will deliver in just 1 to 72 hours. Our company creates both PVA and no PVA accounts with a unique IP address. Our company is 100% trustworthy because all our customers are satisfied with our services.
How to forward email in Gmail
The greatest free email service in the world is Gmail, thanks to a number of outstanding features. It is the best feature of Gmail that you can easily forward the email to the selected email address. Here are the best methods for enabling us to forward emails to one another in a few simple steps.
Click the menu bar.
To forward an email, first choose the desired email, then click the three dots (referred to as the menu bar) that are located at the top of the screen. When you click on it, there will appear some options like reply, forward, delete the email and print, etc. Then you will press the forward option, and then enter your selected email where you want to send it, then you press the send option, and your email will be forwarded.
There is an easy way to forward emails.
First, you open the mail. Subsequently, you will see the respond and forward choices on the mail. After that, you'll click "forward," type in your email address, and hit "send." Your email will be forwarded.
Where to buy Gmail PVA accounts?
If you want to start your business through Gmail accounts, we suggest buying Gmail accounts from our company because we are the best accounts provider in the market.
Benefits Of Purchasing Verified Gmail Accounts
Purchasing verified Gmail accounts can significantly enhance your business’s online presence, improve marketing efforts, and streamline communication with clients and partners. By giving you access to a variety of Google services and platforms, these accounts can also give you a competitive advantage and provide a holistic solution for your business's needs.
Buy Old Gmail Accounts
Old Gmail accounts can be a great resource for growing your internet presence and building a solid network. These accounts are not only reliable and established, but they also carry a sense of credibility and trustworthiness that can enhance your online activities. Whether you are looking to boost your marketing efforts, expand your social media reach, or simply enhance your online presence, buying old Gmail accounts can be a strategic move.
Is It Safe To Buy Gmail Accounts?
Buying old Gmail accounts can be a safe and effective way to enhance your online activities. But it's imperative to make sure you buy accounts from reliable and respectable vendors. It is essential to verify the authenticity of the accounts and ensure that they comply with all the terms and conditions set forth by Gmail. You can lessen the chance of running into problems with account security or validity by buying old Gmail accounts from a reputable seller.
Benefits from us
There is no company that gives a 100% money-back guarantee if any problem occurs in accounts, but our company is a single company that gives the money-back guarantee 100%. For the first three days that the account is active, our company is in charge. There are many international methods of payment like PayPal, skirl, bitcoin, perfect money, pioneer, web money or debit card, credit card, etc. and as our business takes all forms of payment, you are free to choose the one that works best for you.
Conclusion
Based on the discussion above, we can conclude that Gmail is the ideal option if you want to manage your business using social media platforms because it's straightforward and easy to use. to use and safe and secure rather than others and also gives most benefits from other websites. Our company has solved your problem of buying safe and secure Gmail accounts with a 100% money-back guarantee. These accounts may also aid in the expansion of your company.
https://gvaccountbuy.com/buy-google-voice/
https://gvaccountbuy.com/creating-an-icloud-account/
0 notes
Text
XenArmor Browser Password Recovery Pro - Soluția Ta Completă pentru Recuperarea Parolelor din Browser În era digitală, parolele sunt cheia către lumea noastră online. Cu toate acestea, gestionarea unui număr mare de parole poate deveni copleșitoare, și uneori, inevitabil, pierdem accesul la acestea. XenArmor Browser Password Recovery Pro este soluția ta completă pentru recuperarea parolelor stocate în diverse browsere. Acest software puternic și ușor de utilizat te ajută să recuperezi parolele uitate sau pierdute într-un mod rapid și eficient. Denumire produs: XenArmor Browser Password Recovery Pro Pagina oficiala: https://xenarmor.com/ Pagina promoțională: link Valabilitate licenta: 1 an Descarca: BrowserPasswordRecoveryPro-Giveaway.zip Sistem de operare: Windows Termeni: Vizitați pagina promoțională. Completați cu adresa de email și apăsați butonul ”REQUEST LICENSE KEY” Verificați căsuța de email, faceți click pe link-ul de confirmare. În scurt timp veți primi un al doilea mesaj cu serialul pentru înregistrarea programului. Descărcați și instalați programul pe computer, înregistrați-l cu datele primite. Ce Este XenArmor Browser Password Recovery Pro? XenArmor Browser Password Recovery Pro este un instrument de recuperare a parolelor care permite utilizatorilor să acceseze și să recupereze parolele stocate în browserele web. Acest software este compatibil cu toate browserele majore, inclusiv Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, și multe altele. Indiferent de browserul pe care îl utilizezi, XenArmor Browser Password Recovery Pro îți oferă soluția perfectă pentru a-ți recupera informațiile de autentificare. Caracteristici Cheie ale XenArmor Browser Password Recovery Pro Recuperare Parole din Multiple Browsere XenArmor Browser Password Recovery Pro suportă recuperarea parolelor din toate browserele populare. Acest lucru include, dar nu se limitează la: Google Chrome Mozilla Firefox Microsoft Edge Opera Safari Internet Explorer Brave Browser Vivaldi Această compatibilitate extinsă asigură că poți recupera parolele, indiferent de browserul utilizat. Recuperare Parole pentru Diverse Conturi Software-ul nu doar că recuperează parolele pentru site-urile web, dar și pentru conturile de e-mail, rețelele sociale, și alte servicii online. Fie că ai uitat parola pentru contul tău de Gmail, Facebook, Twitter sau orice alt serviciu, XenArmor Browser Password Recovery Pro este aici să te ajute. Export Parole Odată ce parolele sunt recuperate, XenArmor Browser Password Recovery Pro îți permite să le exporți în diferite formate, cum ar fi CSV, HTML, XML, și text simplu. Acest lucru face gestionarea și păstrarea parolelor tale mult mai simplă și organizată. Interfață Intuitivă și Ușor de Utilizat Software-ul vine cu o interfață prietenoasă și intuitivă care face procesul de recuperare a parolelor extrem de simplu, chiar și pentru utilizatorii fără experiență tehnică. Pașii clari și meniurile bine structurate te ghidează prin procesul de recuperare fără probleme. Viteză și Eficiență XenArmor Browser Password Recovery Pro este optimizat pentru a oferi o viteză de recuperare rapidă, astfel încât să poți avea acces la parolele tale în doar câteva minute. Această eficiență este esențială atunci când ai nevoie urgentă de acces la conturile tale. Securitate și Confidențialitate Înțelegem importanța securității datelor tale. XenArmor Browser Password Recovery Pro este proiectat să îți protejeze informațiile sensibile în timpul procesului de recuperare. Datele tale sunt criptate și stocate în siguranță, asigurându-te că rămân confidențiale. Avantajele Utilizării XenArmor Browser Password Recovery Pro Economisirea Timpului Recuperarea manuală a parolelor poate fi un proces lung și frustrant. XenArmor Browser Password Recovery Pro automatizează acest proces, economisind timp și efort. În doar câteva clicuri, poți avea acces la toate parolele stocate în browserul tău.
Accesibilitate Indiferent dacă folosești un computer de acasă, de la birou sau un laptop în călătorii, XenArmor Browser Password Recovery Pro îți oferă acces rapid și ușor la parolele tale. Această flexibilitate este esențială pentru utilizatorii moderni care au nevoie de acces constant la informațiile lor. Versatilitate De la utilizatori individuali până la companii, XenArmor Browser Password Recovery Pro este un instrument versatil care poate satisface nevoile unei varietăți de utilizatori. Indiferent dacă ai nevoie să recuperezi parole pentru uz personal sau pentru a gestiona conturile unei echipe, acest software este soluția ideală. Backup și Gestionare Parole Pe lângă recuperarea parolelor, XenArmor Browser Password Recovery Pro îți permite să creezi backup-uri și să gestionezi parolele recuperate. Aceasta înseamnă că poți păstra o copie sigură a parolelor tale și le poți organiza în mod eficient.
0 notes
Text
Buy Old Gmail Accounts
$5.00 – $70.00 Buy Bulk Gmail Accounts (100% Old, PVA)
If you want to buy Old Gmail Accounts you have right Place. We provide Old, PVA, New all kind Gmail Account Available for sale. Buy Gmail Accounts Features

➥PVA Accounts. ➥ Almost instant Delivery. ➥ The accounts are registered from different country’s IPs. ➥ The accounts have With recovery email. ➥ 72 Hours warranty. ➥ 24×7 Customer Support. Contact Us for more Information’s: 📧 Email: [email protected] 📞 Telegram: @WayneMelvin ☎️WhatsApp: +44 7380 193427
Buy Old Gmail Accounts from USAReviewStore
Are you hunting for some reliable and pocket-friendly Gmail accounts?

Do you want to buy old Gmail accounts? Or do you want to supercharge your online game & marketing hustle? Well, you’re in luck! USAReviewStore is the go-to spot for verified, active, and seasoned Gmail accounts. How to Choose a Reliable Provider
Choosing the right provider is crucial When searching for reliable old Gmail accounts. Not all online sellers can be trusted. Some might offer low-quality, inactive, or compromised accounts or even try to scam you with hidden fees and poor customer service. Here’s what to consider when selecting a provider:
Account Age: Older accounts are better. They carry more trust & features. Look for accounts that are at least a year old.
Verification: Verified accounts are preferable. They’ve passed Google’s checks & offer more functionality. Seek providers offering phone or email-verified accounts.
Activity: Active accounts are safer. They have a history of legitimate usage and are less likely to get flagged or banned. Look for regularly used accounts.
Quality & Security: Ensure the accounts are high-quality and secure. No spam complaints, password changes, or suspicious activities. Protect your information.
Price & Delivery: Affordable, fast-delivered accounts are convenient. Look for reasonable prices and quick delivery within 24 hours. FAQ How many old Gmail accounts can I get from USAReviewStore? You can grab as many as you need. No limits here. Just be mindful of your usage. How old are these Gmail accounts? They range from a few months to several years old. You choose what suits you best. Are there any restrictions on how I can use them? Use them legally and ethically, following platform rules. Be responsible. Do you provide any support or guidance on how to use the old Gmail accounts? We’ve got your back. We’ll send you a guide with your order. Questions? Just ask. What if I need more than the quality or performance of the old Gmail accounts? No worries. Contact us within seven days for a replacement or full refund. Your satisfaction is our goal. Sum Up: If you want to buy old Gmail account, you have come to the right place. USAReviewStore is the best site to buy old Gmail accounts that are verified, active, and aged. You can buy Gmail accounts that are fresh or aged up to several years. You can also buy Gmail PVA accounts in bulk at low and competitive prices. Whether you need to buy Gmail PVA accounts, buy PVA Gmail accounts, or buy aged Gmail account, we have it all.

You can also buy bulk Gmail accounts for your online marketing and promotion needs. Gmail account buying from USAReviewStore is easy, fast, and secure. Contact us today and get your old Gmail accounts delivered within 24 hours.
1 note
·
View note
Text
How can Avoid getting locked out of your Google Account as per google policy
How can Avoid getting locked out of your Google Account as per google policy Avoiding getting locked out of your Google Account is crucial to maintain your online security and access to essential services. Google has policies and security measures in place to protect user accounts, but you also play a significant role in ensuring your account's safety. Here are some essential steps to help you avoid getting locked out of your Google Account as per Google's policies: - Use Strong and Unique Passwords: Create a strong and unique password for your Google Account. Avoid using easily guessable information like your name, birthdate, or common words. A combination of uppercase and lowercase letters, numbers, and special characters is recommended. Additionally, use a different password for each online account to prevent multiple accounts from being compromised if one password is breached. - Enable Two-Factor Authentication (2FA): Google strongly encourages users to enable two-factor authentication. With 2FA, you'll need to provide a second form of verification (e.g., a code sent to your phone or generated by an authenticator app) in addition to your password. This adds an extra layer of security, making it much more challenging for unauthorized individuals to access your account. - Keep Recovery Options Updated: Google provides recovery options like secondary email addresses and phone numbers. Ensure these recovery options are current and accessible so that if you ever lose access to your account, you can regain it easily through the account recovery process. - Be Cautious with Third-Party Apps and Extensions: Only grant necessary permissions to third-party apps and browser extensions that you trust. Unauthorized access to your account through insecure or malicious applications can lead to unwanted access and potential lockouts. - Review Account Activity Regularly: Periodically check your Google Account's activity to spot any suspicious login attempts. Google allows you to review recent logins and connected devices, and you can sign out of all sessions remotely if you find any unauthorized access. - Avoid Violating Google's Policies: Abide by Google's Terms of Service and Community Guidelines. Engaging in activities that violate Google's policies, such as spamming or sharing inappropriate content, can lead to account suspension or termination. - Be Wary of Phishing Attempts: Be vigilant against phishing attempts, where attackers try to trick you into revealing your login credentials. Avoid clicking on suspicious links or providing your account information to untrusted sources. - Use Official Google Services: Stick to official Google services and apps. Avoid using unofficial or unauthorized third-party apps that may not have the necessary security measures in place. - Regularly Update Recovery Information: As your contact information changes (e.g., new phone number, email address), make sure to update your recovery options accordingly. This will ensure you can recover your account if needed. - Follow Google's Security Recommendations: Google regularly provides security tips and recommendations. Stay informed about the latest security measures and updates and apply them to your account to enhance its protection. By following these guidelines and taking a proactive approach to your account's security, you can significantly reduce the risk of getting locked out of your Google Account and enjoy a safer online experience. Remember that security is an ongoing process, and staying informed about the latest security practices is essential for safeguarding your account. More Buy aged Gmail Stray Safe. Read the full article
0 notes
Text
Password Armor: The Best Software for Password Recovery
To avoid the hassle of customer support dealing with lost passwords, many websites allow users to easily obtain or reset their passwords. However, if the password reset feature is not implemented correctly, it could introduce security vulnerability in the web application. Lost passwords should always be treated as security crisis and special precautions should be taken to protect your account from intruders. Several Websites take a casual approach towards lost passwords. When the user enters their username or email address, they receive an email with their original password within minutes. In fact, users who rarely visit websites may record or remember their passwords using a convenient password acquisition process rather than any other method.
Strong passwords are often hard to remember, does that mean they will be lost forever? Obviously not! The great features of Password Armor keep all your passwords secure in one place. It is the best password recovery software available in the industry and you shouldn’t miss out on the wonders of it. To ensure intrusion prevention, Password Armor’s password generator helps generating a secure password. You also get a 100% password recovery rate for almost every other social media platform, including Facebook, Twitter, LinkedIn, Instagram and others. This secures you from any possible privacy beach and ensures that you have a safe internet experience. A solution to all your security concerns, Password Armor is like a vault with the sole purpose to store and protect your from all kinds of identity theft. It is freely available to download on passwordarmor.com
Password Armor is a product of IHAsoft.co and is compatible for Android, iOS, Mac OS & Windows. It is operated under the leadership of. The company believes in developing highly secure and user friendly software’s while adapting to the ever-changing cyber environment and provide its customers with innovative solutions. Not only that, the user interface is very convenient to use and simply anyone can make use of it to safeguard their virtual identity.
#Gmail Password Recovery Tool APK#Gmail Password Recovery Online#iCloud Password Recovery Tool#iCloud ID Password Recovery Software
1 note
·
View note
Text
Gmail Password Recovery in 2019 | Google Account Recovery (New)
Gmail Password Recovery in 2019 | Google Account Recovery (New)

I know it’s annoying.
I know it’s frustrating.
But there is Good news. Just stay till the end.
(Google has introduced a new method of Gmail password recovery).
For Android users, our newly bought phones prompt us to register a new Google Account or sign in an old account.
It is inevitable.
Having Google/Gmail accounts is something we have all come to live with.
…..
View On WordPress
#change my gmail password#forgot my gmail password#gmail password recovery#gmail password recovery by email#gmail password recovery online#gmail password recovery via sms#gmail password reset email#gmail password reset iphone#google account recovery
0 notes
Link
Gmail is the most common and so popular used websites in all over the world. It is used for various purposes like communication with distant friends and relatives
#online discussion forum#gmail password recovery via sms#gmail password forgot#google account recovery phone number
0 notes
Note
You've had a lot of asks calling you out lately and I wanted to come forward to tell you it's me and it's all been good natured but once again I fail at being a responsible adult and have locked myself out of my account. Can I use your gmail as a recovery account? xD You can name and shame, I deserve it. Luv yoooouuuu! xxx
This has been in my asks for a LONG time and I'm guessing that you're still locked out! LMAO. You're an idiot, but I still love you! And yes, you might actually be better using my email to recover your billion forgotten passwords. :P I won't name and shame until you're back online so I can tag you! ;)

4 notes
·
View notes
Text
How to fix outlook errors and office 365 problems | Helpline 1-888-410-9071
Are you still facing critical issues while sending and receiving emails in outlook?

Well, this simply means you are encountering the Error ox800ccc0e. And this is almost confronted by every user. Not only this, there is a lot of factors that affect this issue that’s why you should know about each one because every particular reason may cause Outlook cannot connect to a server error. And, this results to stop to connect your SMTP account with multiple email service providers.
Follow these given steps to fix Outlook Error 0x800ccc0e Error
Solution 1: You need to check your internet connectivity
The reason behind the cause of this error is that your internet connection is not active which plays a very important role to run multiple applications including the outlook on your computer. If you want then you can also switch to another Wi-Fi network in order to see whether the problem is with Outlook or your internet connection.
Solution 2: You should check the settings for email account in Outlook
Sometimes, it is also seen that incorrect incoming and outgoing account settings also cause Outlook cannot connect to a server issue. That’s why if you have to check that the account settings are correct that you have entered in Outlook for a particular email account.
Solution 3: Also check SMTP server settings
Another reason for the cause of 0x800ccc0e is also due to SMTP server settings and you can check or modify these settings simply by the given steps:
At first, you need to Open the Outlook and then go to the file section.
Next, click on Account settings.
After that click on your email account under the Email tab.
Again click on More Settings option.
Then, you can click on the Outgoing server tab and then check the box of my outgoing server requires authentication.
And, finally, just check the Port number and then click on the Ok tab.
And if in case, after applying the above-given steps you fail to implement these, then don’t worry you can reach to the outlook customer service 1-888-410-9071 and get an instant and live solution.
#fix outlook errors#office 365 problems#outlook password recovery online#hotmail server error#gmail server error
0 notes
Note
So many of the coping strategies you mentioned are online/ And indeed, it is difficult escaping the internet what with how ubiquitous smartphones are. I used to love discovering new music and making playlists on a music streaming app. But what if the “abuser” is tech savvy and mostly gets to you through networked devices? And you don’t know enough to figure out if changing passwords, phones, laptops, etc is enough. At this point, I feel like I am violating the privacy of anyone I reach out to.
A lot of that depends on whether or not the person abusing you knows you’re aware she’s tracking you. If she thinks you’re not aware of what’s going on this advice will work better. If she’s told you she’s tracking your behavior I have different advice. (We’re going to call your abuser Alice for the rest of this post.)
Okay, so if she doesn’t know you know - Cellphone first:
You’re either going to need to go to a public library or get a prepaid phone and go somewhere with wifi that Alice isn’t aware of. (A starbucks or mcdonald’s or the public library)
On a library computer or on the burner phone create a new account for your main phone. If you’ve got an android create a new gmail account, if you’ve got an iphone create a new appleID.
WHILE STILL ON THE LIBRARY COMPUTER OR THE BURNER PHONE add your new gmail or appleID as a recovery account for your previous accounts and delete any other recovery email addresses associated with those accounts.
Log into your old account from the library computer or the burner phone and change the password.
On the monitored phone back up and sync your photos and messages; manually write down the numbers of the contacts you want to keep because you will not be restoring from the backup; the backup is just so you can keep your photos and messages, they are not going on the phone again and you are going to lose all your apps and message history and contacts and settings.
You only have to back the phone up if you want to keep your photos and messages. If you’ve got them saved elsewhere then don’t worry about it because you WILL NOT restore from backup.
While the phone is backing up create a Protonmail account and begin the process of switching your online accounts to the protonmail address (do this from the burner or the library computer); change the passwords as you go and prioritize from most important to least important (banking first, socials last)
Once your monitored phone’s photos or messages are backed up to your old account’s email address change the associated account by using the instructions at the links bolded links above.
Do a factory reset of the phone (here’s how on android, here’s how on iphone).
Once the phone is reset *do not* restore from backup.
The first thing you should do is encrypt your phone. This may make your phone slower, but it will also make it safer. Make sure to set a passphrase or pin instead of using biometric IDs like thumbprints or facial recognition.
Once you’ve done that disable or uninstall junk apps and restrict permissions on all the remaining apps to only what is appropriate for those apps (for instance tumblr doesn’t get access to your microphone or camera). Here’s how on android, here’s how on apple.
While you’re still someplace that isn’t your home and using their internet manually reinstall the apps you use that you know are safe. Install an encrypted messenger like Signal, use that instead of your phone’s default messaging apps and ask your friends to use it too (feel free to tell them that you were being spied on and that this is for their privacy too). Install firefox focus instead of using the default browser.
Subscribe to a VPN for your phone; NordVPN is pretty inexpensive and overall well regarded.
From there on out never, ever let anyone use your phone. Never hand it to anyone unlocked, don’t use charger cables someone else gave you, and don’t use wifi without the VPN.
The advice for a desktop computer is pretty similar: go outside of the monitored network, change email addresses and passwords, and reinstall your computer’s operating system and programs manually. Purchase a VPN, use a complicated password to log in to your desktop, and install some variety or other of very aggressive antivirus.
Once you’ve got spyware or stalkerware wiped off your device it’s largely just a process of making sure that no one else can access your device. Like. If you have a laptop consider putting it in a knock-off otterbox case from Harbor Freight and padlock it closed when you’re not using it. Encrypt everything. Don’t let people plug stuff in to your computer, don’t download anything anyone has sent you.
It’s paranoid and exhausting but it works and it also does a good job of teaching you to be more about tech stuff so you can protect yourself better in the future.
So all of that is if Alice is not aware that you’re aware she’s spying on you. That process only works if Alice isn’t going to see you get back from the library and say “give me access to all your accounts again or I’m throwing you out on the street.”
If Alice DOES say that then a lot of the same advice applies just slightly adjusted:
Make a completely separate set of accounts for everything and only ever access them from phones that Alice doesn’t know about or from safe computers (like those at school or at the library or at work) and never use a network that Alice has access to.
You’re still setting up a protonmail, you’re still encrypting your burner phone and never letting anyone touch it, but now instead of changing your facebook password you are creating a new facebook with a different name and a different photo and putting everything on private and adding only the friends who you know can keep it secret.
Anyway, what you’re dealing with sounds super shitty and I hope this is helpful for creating a space where you feel comfortable online again.
153 notes
·
View notes