#Government Id Verification API
Explore tagged Tumblr posts
Text
Protect Your Business from Fraud with the Best Identity Verification API
Businesses today face constant threats of fraud and identity theft in the rapidly evolving digital landscape. It is crucial to protect your company and customers from fraudulent activities to maintain trust and credibility. Here, the importance of an authentic and reliable identity verification service comes into play.
A Best Identity Verification API is a powerful tool that helps businesses verify the identities of individuals or entities using various methods such as biometric authentication, document verification, and database checks. With the rise of financial fraud and data breaches, the demand for such services has significantly increased.

Firstly, an identity verification API helps businesses prevent fraud and financial losses. With the use of advanced technology and algorithms, it can quickly and accurately verify an individual's identity, ensuring that they are who they claim to be. This is particularly crucial for businesses that conduct transactions online, as it protects them from fraudulent activities such as account takeovers and fake identities.
Moreover, utilizing an identity verification API can help businesses comply with regulatory requirements. Many industries, such as finance and healthcare, have strict regulations in place to prevent money laundering and identity theft. By using a trusted and reliable identity verification service, businesses can ensure that they are meeting these requirements and maintaining the integrity of their operations.
One of the key advantages of an Identity Verification Service API is its speed and efficiency. With the use of automation and advanced technology, it can verify identities in a matter of seconds, saving businesses time and resources. This is especially beneficial for companies that handle a high volume of transactions or customer onboarding processes regularly. It not only improves the overall customer experience but also reduces the risk of human error.
In addition to identity verification, some APIs also offer Background Verification API. This can be useful for businesses looking to verify the backgrounds of potential employees or business partners. By using an API, businesses can access a comprehensive database and obtain accurate information about an individual's criminal history, education, employment, and more. This ensures that companies are making informed decisions and protecting their business from potential risks.
With its comprehensive features and industry-leading technology, it is the perfect solution for protecting your business and customers. And the best part? You can try it for free with our Background Check API! Don't wait any longer, safeguard your business today with our trusted and reliable identity verification services. For more info give us a call at +1 833-283-7439 or visit us at:- www.authenticate.com!
#check your criminal record#driving record check#criminal history check#identity verification#identity verification service api#background check api#background check api integration#api for background checks#government id verification api
0 notes
Text
What Is a KYC Verification API and Why Your Business Needs One in 2025
KYC Verification APIs allow businesses to digitally validate identities using government-approved IDs like Aadhaar, PAN, and Voter ID. In 2025, regulatory compliance, fraud prevention, and fast onboarding make such APIs a necessity. SprintVerify provides a secure and scalable solution for businesses that want to automate KYC workflows without compromising speed or accuracy.
0 notes
Text
How AI is Transforming Online Identity Verification
As more services shift to digital platforms, the need for secure, accurate identity verification has never been greater. Financial institutions, government agencies, and private businesses are under increasing pressure to protect user data and prevent fraud. Advanced tools like face recognition online and ID document liveness detection are becoming essential in achieving this.
The Rise of Biometric Verification
Traditional passwords and PINs are no longer enough. They can be stolen, forgotten, or guessed. Biometric technology, especially facial recognition, has emerged as a powerful alternative. Using just a webcam or smartphone camera, face recognition online can quickly verify if someone is who they claim to be. It analyzes facial features in real time, making it nearly impossible to fake with static photos or videos.
This process not only streamlines user experiences but also reduces friction during sign-ups, logins, or sensitive transactions. For companies, it adds a vital layer of defense against identity fraud, while for users, it offers a fast and intuitive way to prove their identity.
What is ID Document Liveness Detection?
Pairing facial recognition with ID document liveness detection creates a powerful combo. Liveness detection ensures that the ID being presented is real, unaltered, and being shown by a live person—not a printed copy or digital screenshot. It works by analyzing micro-details like light reflections on the document, movement patterns, and subtle changes in angles during the scan.
This technology plays a crucial role in automated KYC (Know Your Customer) processes, particularly in industries like banking, insurance, and crypto where regulatory compliance is strict. By confirming the authenticity of both the face and the document, companies can dramatically reduce the risk of fraud without slowing down onboarding.
Benefits Across Industries
E-commerce, healthcare, travel, and even education platforms are beginning to adopt these technologies. Users can now open accounts, access sensitive information, or complete secure transactions in seconds. For global businesses, this opens up new opportunities to scale efficiently while maintaining strict security protocols.
Another key advantage is accessibility. With face recognition online, users no longer need to visit physical offices or mail paperwork. Everything can be done remotely, which is especially important in today’s mobile-first, post-pandemic world.
Challenges and Considerations
Despite its benefits, biometric verification isn’t without concerns. Privacy, data storage, and algorithmic bias are critical issues that technology providers must address. Systems need to be tested across diverse populations to ensure fairness and accuracy. Transparency around how data is collected, used, and stored is also essential for building user trust.
Companies implementing these tools must work with vendors who prioritize security and compliance, and who offer flexible, API-friendly solutions that can integrate smoothly into existing systems.
Conclusion: Smarter Security Starts Here
Face recognition and ID verification tools are quickly becoming the gold standard for secure digital interactions. When combined, face recognition online and ID document liveness detection create a seamless, safe, and scalable identity check process that works across industries.
For businesses looking to upgrade their verification process with cutting-edge AI technology, miniai.live offers robust, privacy-conscious solutions designed for real-world use. Whether you're protecting user accounts or streamlining sign-ups, their tools help you do it faster—and smarter.
0 notes
Text
Streamline Identity Checks with Individual Verification API by Nifi Payments
In an era where digital interactions are the norm, verifying the identity of individuals is more critical than ever — especially for businesses dealing with customers, employees, or partners online. Nifi Payments offers a robust Individual Verification API that enables real-time, secure, and government-compliant identity verification, simplifying your KYC (Know Your Customer) and onboarding processes.
What is the Individual Verification API?
The Individual Verification API by Nifi Payments allows businesses to instantly verify the identity of any individual using authentic government data sources such as Aadhaar, PAN, Voter ID, Driving License, and more. This API ensures the person you are engaging with is genuine, helping you build a safe and compliant business ecosystem.
Key Features:
Multiple Document Support Verify identities using PAN, Aadhaar, Voter ID, Driving License, Passport, and other supported documents.
Real-Time Validation Instantly fetch and validate individual details from official government databases.
Secure & Compliant Fully encrypted and compliant with data privacy and KYC norms, ensuring your verification process is safe and lawful.
Easy Integration Lightweight API that integrates smoothly with mobile apps, web platforms, CRMs, or internal systems.
Photo & Name Match Match the individual’s name and photo across databases to prevent impersonation or document misuse.
Bulk Verification Option Verify multiple identities at once — ideal for large-scale onboarding or audits.
Benefits for Your Business:
✅ Faster Onboarding: Complete verifications in seconds instead of days
✅ Fraud Prevention: Detect fake or tampered IDs before onboarding
✅ Regulatory Compliance: Stay aligned with KYC/AML guidelines
✅ Improved Trust & Security: Ensure that your users, customers, or employees are real and verified
✅ Operational Efficiency: Minimise manual document checks and reduce errors
Common Use Cases:
Fintechs & NBFCs verifying borrower or user identities
E-commerce Platforms authenticating delivery partners or vendors
Gig Economy Apps onboarding workers, drivers, or freelancers
Educational Platforms verifying students and staff
Corporate HR Teams conducting employee background verification
Final Thoughts
Whether you're running a tech startup, financial service, e-commerce platform, or HR tool — identity verification is non-negotiable. With Nifi Payments' Individual Verification API, you get speed, security, and scalability, all in one solution. It’s the simplest way to build trust while staying compliant.
Verify smarter, onboard faster – with Nifi Payments’ Individual Verification API.
0 notes
Text
PAN Verification API: Fast & Reliable
SprintVerify's PAN Verification API cross-verifies PAN numbers with government databases to return name and status. Perfect for NBFCs, insurance firms, and payment apps that require government ID proof. It reduces fraud and speeds up KYC.
0 notes
Text
DigiLocker Integration for Seamless User Verification
DigiLocker integration is one of the most secure and efficient ways to access government-issued documents with user consent. SprintVerify’s DigiLocker API allows you to fetch Aadhaar, PAN, Driving License, and more directly from official repositories. This not only eliminates document fraud but also removes the need for users to upload files. The API flow is simple: authenticate, get consent, and receive documents in real time. Ideal for sectors like lending, insurance, and HR, DigiLocker access ensures authenticity and speeds up verification. SprintVerify helps you deliver a truly digital, paperless onboarding journey that users love.
0 notes
Text
How Alcohol Delivery Apps Work in India (And How You Can Build One)
With rising demand for convenience and digital-first lifestyles, alcohol delivery apps have found their niche in India. While the sector is still governed by state-wise regulations, more consumers are turning to their phones for a smooth, legal way to get their favorite drinks delivered to their doorstep.
So, how do these apps actually work in India? Let’s break it down.
Read: Top 9 Alcohol Delivery Apps in 2025
1. State-Wise Legal Compliance First
Unlike other categories like food or groceries, alcohol delivery in India is regulated at the state level. That means:
Some states allow online ordering and home delivery (like Maharashtra, Odisha, West Bengal, and Delhi).
Others have not yet permitted this service or have stricter controls.
How apps comply:
They must get a license for each state they operate in.
The app should include age verification features and restrict delivery zones as per state laws.
2. Tie-Ups with Licensed Retailers
Alcohol delivery apps do not stock inventory themselves. Instead, they:
Partner with licensed liquor stores or distributors.
Display the available stock from those partners in real time.
This B2B2C model keeps the operation lean while ensuring legal compliance.
3. User Flow: From Login to Checkout
A typical alcohol delivery app in India includes:
Age Verification: Users must upload ID proof or input their birth date before browsing.
Location Access: Only pin codes where delivery is legal are activated.
Catalog View: Users browse through categories like beer, wine, whiskey, etc.
Secure Payment: Most apps accept UPI, credit/debit cards, and sometimes cash on delivery (where allowed).
Real-Time Tracking: Just like food delivery, users can track their order live.
4. Delivery Logistics
Some apps have their own delivery staff, while others rely on third-party logistics services.
Key challenges they solve:
Ensuring delivery only to legal-aged users
Timely and secure handling of alcohol
Maintaining cold chain for beverages like beer or wine
5. Backend and Tech Stack
Apps are typically built using:
Flutter for cross-platform compatibility
Firebase or Node.js for real-time updates
Geolocation APIs for service pin codes
Custom UI Kits like GetWidget to speed up development and maintain design consistency
Want to Build Your Own Alcohol Delivery App?
With pre-built Flutter widgets, UI components, and full app templates, GetWidget lets you create your own delivery app 10x faster — with zero compromise on design or scalability.
👉 Start building your alcohol delivery app with GetWidget today
0 notes
Text
The Future of Enterprise Security: Why Zero Trust Architecture Is No Longer Optional

Introduction: The Myth of the Perimeter Is Dead
For decades, enterprise security was built on a simple, but now outdated, idea: trust but verify. IT teams set up strong perimeters—firewalls, VPNs, gateways—believing that once you’re inside, you’re safe. But today, in a world where remote work, cloud services, and mobile devices dominate, that perimeter has all but disappeared.
The modern digital enterprise isn’t confined to a single network. Employees log in from coffee shops, homes, airports. Devices get shared, stolen, or lost. APIs and third-party tools connect deeply with core systems. This creates a massive, fragmented attack surface—and trusting anything by default is a huge risk.
Enter Zero Trust Architecture (ZTA)—a new security mindset based on one core rule: never trust, always verify. Nothing inside or outside the network is trusted without thorough, ongoing verification.
Zero Trust isn’t just a buzzword or a compliance box to tick anymore. It’s a critical business requirement.
The Problem: Trust Has Become a Vulnerability
Why the Old Model Is Breaking
The old security approach assumes that once a user or device is authenticated, they’re safe. But today’s breaches often start from inside the network—a hacked employee account, an unpatched laptop, a misconfigured cloud bucket.
Recent attacks like SolarWinds and Colonial Pipeline showed how attackers don’t just break through the perimeter—they exploit trust after they’re inside, moving laterally, stealing data silently for months.
Data Lives Everywhere — But the Perimeter Doesn’t
Today’s businesses rely on a mix of:
SaaS platforms
Multiple clouds (public and private)
Edge and mobile devices
Third-party services
Sensitive data isn’t locked away in one data center anymore; it’s scattered across tools, apps, and endpoints. Defending just the perimeter is like locking your front door but leaving all the windows open.
Why Zero Trust Is Now a Business Imperative
Zero Trust flips the old model on its head: every access request is scrutinized every time, with no exceptions.
Here’s why Zero Trust can’t be ignored:
1. Adaptive Security, Not Static
Zero Trust is proactive. Instead of fixed rules, it uses continuous analysis of:
Who the user is and their role
Device health and security posture
Location and network context
Past and current behavior
Access decisions change in real time based on risk—helping you stop threats before damage occurs.
2. Shrinks the Attack Surface
By applying least privilege access, users, apps, and devices only get what they absolutely need. If one account is compromised, attackers can’t roam freely inside your network.
Zero Trust creates isolated zones—no soft spots for attackers.
3. Designed for the Cloud Era
It works naturally with:
Cloud platforms (AWS, Azure, GCP)
Microservices and containers
It treats every component as potentially hostile, perfect for hybrid and multi-cloud setups where old boundaries don’t exist.
4. Built for Compliance
Data privacy laws like GDPR, HIPAA, and India’s DPDP require detailed access controls and audits. Zero Trust provides:
Fine-grained logs of users and devices
Role-based controls
Automated compliance reporting
It’s not just security—it’s responsible governance.
The Three Core Pillars of Zero Trust
To succeed, Zero Trust is built on these key principles:
1. Verify Explicitly
Authenticate and authorize every request using multiple signals—user identity, device status, location, behavior patterns, and risk scores. No shortcuts.
2. Assume Breach
Design as if attackers are already inside. Segment workloads, monitor constantly, and be ready to contain damage fast.
3. Enforce Least Privilege
Grant minimal, temporary access based on roles. Regularly review and revoke unused permissions.
Bringing Zero Trust to Life: A Practical Roadmap
Zero Trust isn’t just a theory—it requires concrete tools and strategies:
1. Identity-Centric Security
Identity is the new perimeter. Invest in:
Multi-Factor Authentication (MFA)
Single Sign-On (SSO)
Role-Based Access Controls (RBAC)
Federated Identity Providers
This ensures users are checked at every access point.
2. Micro-Segmentation
Divide your network into secure zones. If one part is breached, others stay protected. Think of it as internal blast walls.
3. Endpoint Validation
Only allow compliant devices—corporate or BYOD—using tools like:
Endpoint Detection & Response (EDR)
Mobile Device Management (MDM)
Posture checks (OS updates, antivirus)
4. Behavioral Analytics
Legitimate credentials can be misused. Use User and Entity Behavior Analytics (UEBA) to catch unusual activities like:
Odd login times
Rapid file downloads
Access from unexpected locations
This helps stop insider threats before damage happens.
How EDSPL Is Driving Zero Trust Transformation
At EDSPL, we know Zero Trust isn’t a product—it’s a continuous journey touching every part of your digital ecosystem.
Here’s how we make Zero Trust work for you:
Tailored Zero Trust Blueprints
We start by understanding your current setup, business goals, and compliance needs to craft a personalized roadmap.
Secure Software Development
Our apps are built with security baked in from day one, including encrypted APIs and strict access controls (application security).
Continuous Testing
Using Vulnerability Assessments, Penetration Testing, and Breach & Attack Simulations, we keep your defenses sharp and resilient.
24x7 SOC Monitoring
Our Security Operations Center watches your environment around the clock, detecting and responding to threats instantly.
Zero Trust Is a Journey — Don’t Wait Until It’s Too Late
Implementing Zero Trust takes effort—rethinking identities, policies, networks, and culture. But the cost of delay is huge:
One stolen credential can lead to ransomware lockdown.
One exposed API can leak thousands of records.
One unverified device can infect your entire network.
The best time to start was yesterday. The second-best time is now.
Conclusion: Trust Nothing, Protect Everything
Cybersecurity must keep pace with business change. Static walls and blind trust don’t work anymore. The future is decentralized, intelligent, and adaptive.
Zero Trust is not a question of if — it’s when. And with EDSPL by your side, your journey will be smart, scalable, and secure.
Ready to Transform Your Security Posture?
EDSPL is here to help you take confident steps towards a safer digital future. Let’s build a world where trust is earned, never assumed.
Visit Reach Us
Book a Zero Trust Assessment
Talk to Our Cybersecurity Architects
Zero Trust starts now—because tomorrow might be too late.
Please visit our website to know more about this blog https://edspl.net/blog/the-future-of-enterprise-security-why-zero-trust-architecture-is-no-longer-optional/
0 notes
Text
Why Video KYC for Banks Is the Future of Secure Digital Onboarding
In today’s competitive banking landscape, speed, convenience, and compliance are key to onboarding new customers. Traditional KYC (Know Your Customer) processes—while secure—often involve physical documentation, branch visits, and long processing times. This results in drop-offs, operational delays, and rising costs. Video KYC for banks is changing the game by offering a compliant, real-time, and paperless way to verify customers.
With increasing adoption across both public and private sector banks, Video KYC is emerging as a cornerstone of modern digital banking.

What Is Video KYC?
Video KYC (Know Your Customer) is a video-based customer identification process (V-CIP) where a customer is verified via a live video call with a KYC officer. The process includes:
Verifying government-issued documents (like Aadhaar, PAN, passport)
Matching the customer’s face to their ID proof
Confirming location via geo-tagging
Conducting liveliness checks to ensure real-time presence
The Reserve Bank of India (RBI) approved the use of Video KYC in 2020, making it a legally valid and widely accepted method for onboarding customers across banks, NBFCs, and fintech platforms.

Why Banks Are Switching to Video KYC
1. Faster Onboarding Video KYC enables banks to verify customers in less than 5 minutes. This drastically reduces onboarding time compared to the traditional process, which can take several days.
2. Enhanced Fraud Prevention AI-driven features like face match, liveliness detection, and document OCR make it harder for fraudsters to manipulate the system. Video interactions also deter impersonation and identity theft.
3. Cost Savings Without the need for field agents or branch infrastructure, banks can cut down onboarding costs by up to 80%. The entire process is digital and automated, which reduces human error and overheads.
4. Remote Access for Customers Whether in a metro city or a rural town, customers can complete their KYC anytime, anywhere. All they need is a smartphone and internet connection—eliminating the need to visit a physical branch.
5. 100% Compliance with RBI Guidelines Video KYC for banks, when implemented correctly, ensures compliance with RBI regulations, including timestamped video recordings, geo-location tagging, consent capture, and secure data storage.
How Gridlines Enables Effortless Video KYC for Banks
At Gridlines, we’ve built a robust, enterprise-ready Video KYC API that helps banks verify customers instantly and securely. Our plug-and-play solution integrates seamlessly into your onboarding flow—be it on a mobile app or a web platform.
Key features include:
AI-based Face Match & Liveliness Detection: Prevents spoofing and deepfake attempts
Secure Document Capture & OCR: Extracts and verifies details from Aadhaar, PAN, etc.
Geo-tagging & Time Stamping: For regulatory compliance
Multilingual Support: To serve diverse customer bases
Audit-Ready Recordings: With encrypted storage and retrieval
Our platform is designed to handle thousands of verifications per day—ensuring scalability, reliability, and compliance.
Real-World Impact
Banks using Gridlines' Video KYC API have reported:
30–40% reduction in onboarding drop-offs
Up to 3x faster KYC completion times
Significant fraud detection improvements
From savings accounts to business loans, the applications of Video KYC are vast. It’s especially powerful for banks expanding their reach to underbanked regions or scaling digital-only products.
Final Thoughts
Video KYC for banks is not just a tech upgrade—it’s a competitive differentiator. It allows banks to meet customer expectations for speed and convenience while staying compliant with regulatory norms. As financial institutions continue to digitize, adopting a secure and scalable Video KYC solution is no longer optional—it’s essential.With Gridlines, you get a future-ready KYC platform built for speed, security, and scale. Simplify onboarding. Reduce risk. Delight your customers.
#Video KYC#Digital Onboarding#Banking Technology#Customer Verification#KYC Compliance#Fintech APIs#Gridlines
0 notes
Text
How can startups implement a cost-effective KYC solution?

For startups navigating the fast-paced world of business, balancing compliance with cost efficiency is a constant challenge. One crucial area where this balance becomes vital is in the implementation of Know Your Customer (KYC) and identity verification processes. As regulations tighten and digital transactions become the norm, startups must find ways to meet KYC requirements without draining their resources.
So, how can startups implement a cost-effective KYC solution while maintaining accuracy, security, and regulatory compliance?
Understanding the Basics: What Is KYC?
KYC, or Know Your Customer, is a mandatory process that businesses use to verify the identity of clients before or during a transaction or partnership. It involves collecting and validating personal information such as a user’s name, government-issued ID, address, and sometimes biometric data.
KYC and identity verification are critical in preventing financial fraud, money laundering, and identity theft. For startups, especially those in finance, e-commerce, or digital services, a functional KYC framework isn’t just a legal requirement—it’s a foundation for trust and long-term success.
The Challenge for Startups
Startups often face tight budgets, lean teams, and the need to scale quickly. Traditional KYC methods—manual verification, in-person documentation, and lengthy onboarding procedures—are slow, expensive, and error-prone. These legacy systems are not practical for a startup environment where speed and efficiency are crucial.
To stay competitive, startups need smart, scalable, and affordable ways to verify customer identities without sacrificing compliance or customer experience.
Key Strategies for Implementing a Cost-Effective KYC Solution
1. Leverage Digital KYC Tools
One of the most efficient ways for startups to cut costs is by adopting digital KYC and identity verification tools. These tools automate the verification process, reducing the need for manual labor and minimizing human error.
Cloud-based KYC platforms offer flexible pricing models—often pay-as-you-go or usage-based—that allow startups to pay only for what they use. This scalability is perfect for growing businesses that need to onboard users gradually.
2. Choose Modular and API-Driven Solutions
Instead of investing in an expensive, end-to-end compliance suite, startups can opt for modular KYC tools that allow them to build customized solutions. API-driven KYC services let startups integrate identity verification directly into their platforms or apps.
By choosing only the features they need—such as document verification, facial recognition, or watchlist screening—startups avoid paying for unnecessary functionality. This modular approach ensures efficiency without compromising compliance.
3. Automate Where Possible
Automation can drastically reduce the cost and time involved in KYC. For example, using AI-powered optical character recognition (OCR) can automatically extract data from ID documents, while facial recognition can match a user’s selfie with their photo ID in real time.
Automating these steps removes the need for large verification teams and shortens customer onboarding time, resulting in better user satisfaction and lower operational expenses.
4. Adopt Risk-Based KYC Approaches
Not all customers pose the same level of risk. A cost-effective KYC solution for startups involves using a risk-based approach—applying different levels of scrutiny depending on the risk profile of the customer.
Low-risk users may only need basic document verification, while high-risk clients might undergo enhanced due diligence. By tailoring the verification process based on risk, startups can optimize resources and reduce overhead costs.
5. Outsource When Necessary
Building a KYC infrastructure from scratch is resource-intensive. Many startups choose to outsource their KYC and identity verification processes to specialized third-party providers. This outsourcing can significantly lower initial setup costs and provide access to expert tools and regulatory updates without maintaining an in-house compliance team.
However, it’s essential to choose a reputable partner that complies with data protection regulations and offers secure and customizable services.
6. Monitor and Update Regularly
KYC isn’t a one-time task. Ongoing monitoring and periodic re-verification are essential, especially as regulations evolve. Startups should invest in tools that support continuous monitoring of user behavior and real-time alerts for suspicious activity.
Regular updates to the KYC process ensure the startup remains compliant, avoids penalties, and adapts to changing risks without major overhauls or expenses.
A Practical Example
Let’s imagine how a company like Xettle Technologies—a startup in the tech space—could implement a cost-effective KYC solution. Instead of building its own verification system, Xettle Technologies might integrate an API-based KYC provider offering facial recognition and document scanning. By selecting a pay-as-you-go pricing plan and automating the verification process, the company reduces manual workload and speeds up user onboarding.
Additionally, by classifying users based on transaction value or location, Xettle Technologies applies enhanced checks only where necessary, ensuring compliance without bloated costs.
Conclusion
Implementing a cost-effective KYC and identity verification system is not only possible for startups—it’s a strategic move that supports growth and builds trust. By embracing automation, leveraging digital tools, and tailoring verification processes to customer risk levels, startups can remain compliant while saving time and money.
The key lies in starting small, staying flexible, and scaling KYC systems as the business evolves. In today’s digital economy, a smart and lean approach to KYC isn’t just an option—it’s a necessity for startup success.
0 notes
Text
Verified Google Play Developer Accounts
Verified Google Play Developer Accounts: Why They Matter & How to Get One
As the Android app ecosystem continues to grow, the need for trust and security on the Google Play Store is more crucial than ever. Whether you're a startup, freelancer, or established app development firm, having a Verified Google Play Developer Account is no longer optional—it’s a necessity.
🔍 What is a Verified Google Play Developer Account?
A verified Google Play Developer Account is one that has undergone Google’s identity verification process. This verification ensures that the developer is a real individual or legitimate business entity, helping to maintain the integrity and safety of the Play Store for both developers and users.
🚀 Benefits of Having a Verified Account
Increased Trust and Credibility Users are more likely to download apps from verified developers, which can lead to higher install rates.
Improved Security Verification helps prevent fraud, impersonation, and spam apps, making the Play Store a safer place.
Eligibility for Advanced Features Certain features and API access are only available to verified accounts.
Faster App Approvals Verified developers may experience quicker review times as their identities are already confirmed.
Business Transparency Companies can display verified business names, improving professionalism and user confidence.
📝 What’s Required for Verification?
Valid Government ID (for individuals) or Business Registration Documents (for organizations)
Payment Information for the $25 one-time registration fee
Phone Number and Email Verification
Developer Profile Information including a name, email, and website (if applicable)
❗ Important Tips
Use accurate and consistent information across all fields.
Avoid using third-party sellers of accounts—they violate Google’s terms and can result in bans.
Keep your developer information updated to maintain verification status.
Getting your Google Play Developer Account verified is a smart and necessary step if you're serious about app development. It not only protects your brand but also boosts user trust and opens doors to additional Google services. Whether you're launching your first app or scaling your mobile portfolio, verification is a foundational part of your developer journey.
Would you like a version of this formatted for Medium, WordPress, or social media promotion?
0 notes
Text
Empower Your Platform with Identity Verification and Background Check APIs

In today's digital age, it's more important than ever for companies to verify the identities of their customers and employees. This not only helps to prevent fraud and identity theft, but it also ensures the safety and security of everyone involved. However, manually verifying identities and conducting background checks can be time-consuming and costly for businesses. This is where Identity Authenticate comes into play.
Identity Check API is a powerful tool that allows businesses to quickly and easily verify the identity of their customers or employees. With just a few lines of code, companies can integrate this API into their platforms and streamline their identity verification processes. This API uses advanced technology and databases to verify personal information such as name, date of birth, and address, providing businesses with reliable and accurate results.
Criminal Background Check API, on the other hand, allows companies to conduct thorough background checks on their customers or employees. This API searches through millions of criminal records to ensure that the person has no criminal history, offering peace of mind to businesses and their clients. With this API, businesses can also customize the type of background check they need, whether it's a basic criminal record check or a more comprehensive search.
Moreover, these APIs are also cost-effective. With Identity Check API and Criminal Background Check API, businesses don't have to invest in expensive software or hire a team to handle identity verification and background checks. Instead, they can simply integrate the APIs into their existing systems and pay only for the verifications and checks they need. This makes it a cost-effective solution for businesses of all sizes.
For businesses looking to take advantage of these APIs, it's important to choose a reputable provider that offers a secure and reliable service. This is where Background Check API Free comes into the picture. This free API allows companies to test the functionality and performance of Identity Check API and Criminal Background Check API before committing. This way, businesses can ensure that they are getting the best service and results before investing in the APIs.
For further info, you can contact us at +1 833-283-7439 or visit our official website at:- www.authenticate.com!
#Open Source Background Check API#Identity Verification Service API#Identity Verification App#Identity Verification And Authentication#Identity Verification#Government Id Verification API#Criminal History Check#Criminal Court Records#Background Check API#Background Verification API
0 notes
Text
What Is a KYC Verification API and Why Your Business Needs One in 2025
KYC Verification APIs allow businesses to digitally validate identities using government-approved IDs like Aadhaar, PAN, and Voter ID. In 2025, regulatory compliance, fraud prevention, and fast onboarding make such APIs a necessity. SprintVerify provides a secure and scalable solution for businesses that want to automate KYC workflows without compromising speed or accuracy.
0 notes
Text
From SMS to RCS: A Smarter Way to Engage and Convert Customers!

In the age of digital transformation, the way businesses communicate with customers is evolving fast. Rich Communication Services (RCS) is redefining mobile messaging by offering app-like interactivity within the default messaging app—no downloads required. Compared to traditional SMS, RCS offers richer engagement, and industries are rapidly adopting it for enhanced customer experiences. In this blog, we’ll compare RCS and SMS marketing, look at real-world use cases, break down pricing and setup costs, and help you decide which solution suits your business best.
RCS vs. SMS Marketing: What’s the Real Difference? SMS (Short Message Service) has been the backbone of mobile communication for decades. It’s text-only, limited to 160 characters, and cannot include media or advanced interactions. It’s great for alerts and reminders but lacks engagement.
RCS, on the other hand, is a modern messaging protocol that supports:
Rich media (images, videos, carousels)
Verified sender branding (business name, logo, color themes)
Suggested replies and action buttons
Interactive chat flows and transactional capabilities
This makes RCS ideal for marketing campaigns, customer support, product showcases, and transactional messages.
How Industries Are Using RCS Messaging Retail & E-commerce: Product carousels, flash sale alerts, cart abandonment recovery.
Banking & Finance: Interactive account summaries, bill payments, fraud alerts with quick action.
Travel & Hospitality: Booking confirmations, boarding passes, hotel check-in, and service feedback.
Healthcare: Appointment scheduling, medication reminders, wellness tips with videos.
These use cases prove that RCS isn't just messaging—it's a full-fledged customer engagement platform.
Pricing & Initial Setup: RCS vs. SMS (with DLT) Here’s a breakdown of the costs associated with both services in the Indian market:
SMS Marketing (Transactional/Promotional): DLT Registration (mandatory as per TRAI):
Entity registration: ₹5,900 (approx. for all major operators)
Header (Sender ID) registration: ₹250–₹500 per ID
Template approval: ₹0–₹200 per template depending on provider
SMS Sending Cost:
Promotional: ₹0.14 – ₹0.18 per SMS
Transactional: ₹0.18 – ₹0.25 per SMS
Additional Costs:
Platform usage fee (varies by provider)
Bulk purchase discounts may apply
RCS Messaging: Brand Verification & Setup:
One-time brand onboarding & verification: ₹3,000 – ₹7,000 (depends on provider)
Campaign setup/management (optional, per campaign): ₹1,000 – ₹2,000
Messaging Cost:
Per session or message-based billing: ₹0.25 – ₹1.00 per message/session
No DLT registration required (as RCS is not governed under TRAI DLT currently)
Additional Costs:
Creative design (if outsourced)
Rich media hosting (may be included by provider)
While RCS has a higher per-message cost, its enhanced engagement, higher CTRs, and app-like experience often lead to a better return on investment.
How to Get Started with RCS Messaging Partner with an RCS Messaging Provider: Choose a Google-verified partner like Dove Soft for access to RCS APIs and tools.
Brand Verification: Submit your business profile for Google’s verification.
Build Campaigns: Create interactive messages with rich media, buttons, and flows using the dashboard.
Test & Deploy: Run test messages, refine the content, and launch to your audience.
Measure & Optimize: Track delivery rates, interactions, and user journeys in real time.
Final Thoughts RCS messaging is the future of mobile messaging, offering rich engagement and branded communication that SMS simply can’t match. However, SMS remains relevant for critical alerts and wide-reaching broadcasts, especially where smartphone penetration or RCS availability may be limited.
For businesses that want to engage, convert, and retain customers more effectively, RCS messaging is a game-changer worth the investment. Now is the time to modernize your communication strategy .
0 notes
Text

Revolutionizing KYC Verification with Advanced API Services
In today’s digital age, Know Your Customer (KYC) compliance is critical for businesses across industries. With the rise in digital transactions and financial services, the need to verify customer identities in real-time has never been greater. EKYCHub steps into this space, offering robust KYC verification API services to ensure secure, seamless, and automated identity verification for businesses.
What is KYC?
KYC (Know Your Customer) refers to the process of verifying the identity of clients to prevent fraud, money laundering, and ensure regulatory compliance. It’s an essential process for financial institutions, fintech startups, e-commerce platforms, and other businesses handling sensitive customer data. KYC involves several verification steps like document verification, biometric authentication, and face matching to confirm that the customer is who they claim to be.
The Need for KYC Verification
In the modern digital economy, KYC processes are necessary to ensure:
Fraud Prevention: Verifying customer identities helps reduce the risk of identity theft, account takeover, and other fraudulent activities.
Regulatory Compliance: Many industries, particularly finance, are heavily regulated, and KYC is a mandatory requirement to meet legal obligations.
Risk Management: Understanding your customers allows businesses to assess and mitigate potential risks.
Trust Building: Offering a secure platform where users’ identities are verified instills trust and credibility in your business.
EKYCHub KYC Verification API: A Game-Changer
EKYCHub offers a comprehensive KYC Verification API that allows businesses to integrate identity verification into their platforms easily. The API service provides an end-to-end solution for both individual and business KYC compliance, ensuring that users can authenticate their identities in seconds without compromising security.
Here’s a breakdown of the features and benefits of EKYCHub’s KYC Verification API:
1. Document Verification
EKYCHub’s API allows businesses to verify government-issued documents such as passports, driver’s licenses, and national IDs. The system checks for authenticity and ensures that the documents meet the required standards.
Supported Documents: Passports, National IDs, Driver’s Licenses, Bank Statements, Utility Bills, and more.
Real-Time Verification: The system scans and verifies the document within seconds to provide immediate feedback.
2. Face Recognition
EKYCHub offers advanced facial recognition technology that matches a person’s live photo or selfie to the image on their government-issued ID. This reduces the risk of identity fraud and ensures that the individual in question is the one on the document.
Biometric Authentication: Facial recognition technology provides an added layer of security.
Selfie-to-ID Verification: Ensures that the customer is present and not using a stolen image.
3. Liveness Detection
The API also includes liveness detection, which ensures that the person is physically present during the verification process. This prevents fraudsters from using photos or videos to bypass authentication.
Anti-Spoofing Technology: Detects and prevents fraudulent activities such as using images or pre-recorded videos.
Real-Time Liveness Detection: Verifies user presence in real time during facial recognition.
4. AML and PEP Screening
EKYCHub’s KYC API includes AML (Anti-Money Laundering) and PEP (Politically Exposed Person) screening, ensuring that businesses are compliant with regulatory frameworks like the Financial Action Task Force (FATF).
Global Database Checks: Cross-referencing customers against global databases to identify potential risks.
AML Compliance: Helps businesses avoid financial crimes and penalties.
5. Scalability and Flexibility
EKYCHub’s KYC API can scale to meet the needs of businesses of all sizes. Whether you’re a startup looking for a small solution or a large enterprise with thousands of customers, EKYCHub’s infrastructure can handle the load.
Cloud-Based: No need for extensive hardware or software installations.
Customizable: The API can be tailored to fit specific business requirements.
6. Seamless Integration
Integrating EKYCHub’s KYC API into your existing platform is simple. The API supports multiple programming languages, including Python, Java, and PHP, making it developer-friendly.
Easy-to-Use Documentation: Comprehensive guides to assist with integration.
Multi-Platform Support: Works with web applications, mobile apps, and other platforms.
7. Cost-Effective
EKYCHub offers competitive pricing for its KYC API services, making it accessible for businesses of all sizes, from startups to large enterprises.
Pay-per-Use Model: You only pay for what you use, ensuring you can scale your KYC operations as needed without upfront costs.
Affordable Pricing Tiers: Flexible pricing based on transaction volume and business needs.
Benefits of Using EKYCHub’s KYC Verification API
Enhanced Security: Robust verification technologies help ensure that only genuine customers are onboarded.
Improved Customer Experience: Quick, seamless, and hassle-free verification processes result in a better user experience.
Regulatory Compliance: EKYCHub’s KYC solution ensures that your business remains compliant with global KYC and AML regulations.
Fraud Prevention: Reduces the risk of fraudulent activities through advanced document and biometric verification technologies.
Speed and Efficiency: Automated processes ensure that KYC checks are completed swiftly, reducing wait times for customers.
Who Can Benefit from EKYCHub’s KYC API?
EKYCHub’s KYC verification API is designed to cater to a wide range of industries and use cases:
Financial Institutions: Banks, fintech companies, and online lenders can use EKYCHub to comply with KYC regulations and prevent fraud.
Cryptocurrency Exchanges: KYC verification is crucial in crypto trading platforms to prevent illegal activities like money laundering.
E-commerce Platforms: Online retailers can verify their customers to ensure secure transactions and protect against fraud.
Online Marketplaces: Platforms with user-generated content or listings can use KYC to verify the identity of sellers and buyers.
Healthcare Providers: Verifying the identity of patients to ensure secure health record management.
Conclusion
EKYCHub’s KYC Verification API is an essential tool for businesses looking to streamline and secure their customer onboarding process. With its advanced features like document verification, face recognition, and AML screening, EKYCHub helps businesses comply with KYC regulations, reduce fraud, and enhance the user experience. Whether you’re a startup or an established enterprise, integrating EKYCHub’s KYC API can give you the confidence and security to operate in today’s digital world.
#tech#ekychub#techinnovation#identityvalidation#fintech#technews#technology#kycverificationapi#API#aadhaarverificationapi#apiverification#secureidentityauthentication#digitalverification#Aadhaarintegration#KYCVerificationAPI#identityverification#APIforKYC
1 note
·
View note
Text
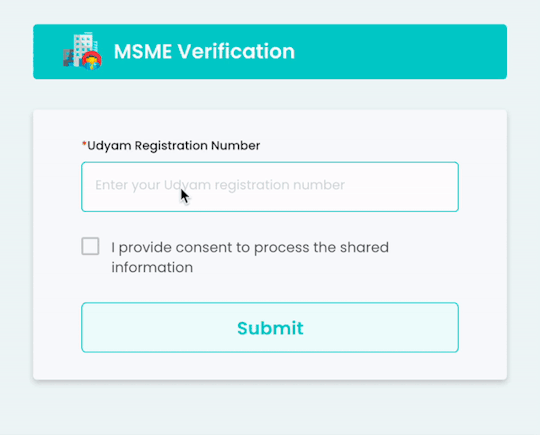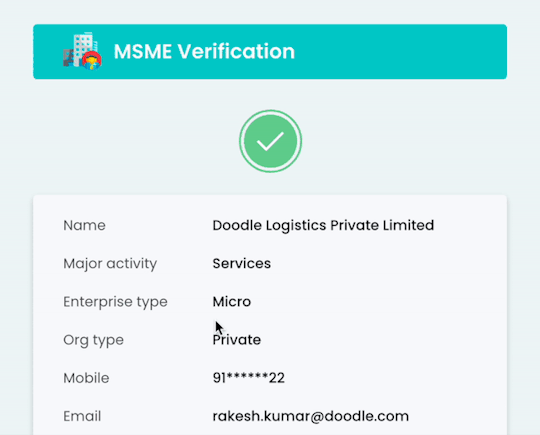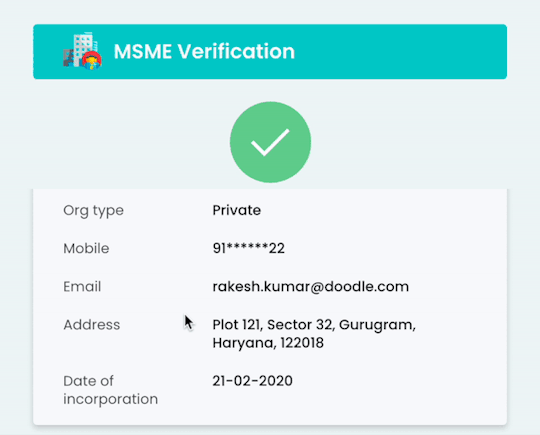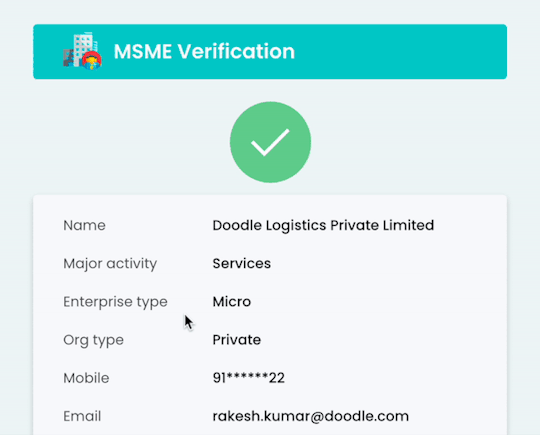
Streamline MSME Verification with Gridlines' Robust API Solution
Udyam registration and Udyog Aadhaar reference are unique IDs assigned to small and medium-sized enterprises by the Ministry of MSMEs. These identifiers serve as official government recognition, verifying the legitimacy and operational status of MSMEs. Gridlines’ MSME Verification API provides instant validation of these registrations, reducing fraudulent risks and ensuring compliance with regulatory standards.
Why Gridlines
Instant MSME Validation
Enables immediate confirmation of Udyam registrations, crucial for verifying small and medium enterprise identities as recognized by the Ministry of MSMEs.
Efficient Partner Integration
Accelerates the integration of business partners or merchants, streamlining the onboarding process for better operational flow.
Regulatory Compliance Check
Assures that businesses are operating in accordance with government standards, maintaining legal and regulatory compliance.
Reliable Security Measures
Strengthens the verification process with robust security, ensuring the legitimacy of MSME merchants.
#MSMEVerification#UdyamRegistration#UdyogAadhaar#GridlinesAPI#BusinessCompliance#SecureVerification#InstantValidation#FraudPrevention#DigitalVerification#MSMESolutions#APIIntegration
0 notes