#Identity Verification And Authentication
Explore tagged Tumblr posts
Text
Empower Your Platform with Identity Verification and Background Check APIs

In today's digital age, it's more important than ever for companies to verify the identities of their customers and employees. This not only helps to prevent fraud and identity theft, but it also ensures the safety and security of everyone involved. However, manually verifying identities and conducting background checks can be time-consuming and costly for businesses. This is where Identity Authenticate comes into play.
Identity Check API is a powerful tool that allows businesses to quickly and easily verify the identity of their customers or employees. With just a few lines of code, companies can integrate this API into their platforms and streamline their identity verification processes. This API uses advanced technology and databases to verify personal information such as name, date of birth, and address, providing businesses with reliable and accurate results.
Criminal Background Check API, on the other hand, allows companies to conduct thorough background checks on their customers or employees. This API searches through millions of criminal records to ensure that the person has no criminal history, offering peace of mind to businesses and their clients. With this API, businesses can also customize the type of background check they need, whether it's a basic criminal record check or a more comprehensive search.
Moreover, these APIs are also cost-effective. With Identity Check API and Criminal Background Check API, businesses don't have to invest in expensive software or hire a team to handle identity verification and background checks. Instead, they can simply integrate the APIs into their existing systems and pay only for the verifications and checks they need. This makes it a cost-effective solution for businesses of all sizes.
For businesses looking to take advantage of these APIs, it's important to choose a reputable provider that offers a secure and reliable service. This is where Background Check API Free comes into the picture. This free API allows companies to test the functionality and performance of Identity Check API and Criminal Background Check API before committing. This way, businesses can ensure that they are getting the best service and results before investing in the APIs.
For further info, you can contact us at +1 833-283-7439 or visit our official website at:- www.authenticate.com!
#Open Source Background Check API#Identity Verification Service API#Identity Verification App#Identity Verification And Authentication#Identity Verification#Government Id Verification API#Criminal History Check#Criminal Court Records#Background Check API#Background Verification API
0 notes
Text
Seamless Digital Address Verification with OnGrid
The image showcases OnGrid’s digital address verification process, highlighting a verified candidate with their name and address. A worker in safety gear stands confidently, representing seamless onboarding for frontline and field-based roles. The interface confirms successful verification, emphasizing reliability and efficiency in identity confirmation for hiring, lending, and user onboarding across India. Learn more at .

#Digital address verification#contactless onboarding#employee verification#identity management#remote hiring#HR tech#location authentication#and compliance solutions in India.
0 notes
Text
#biometrics#software#technology#verification#identity verification#authentication#sdk#face sdk#ID verification#Regula
1 note
·
View note
Text
Understanding Biometric Security: The Future of Identity Verification

Future of Identity Verification: In today's digital age, ensuring secure access to sensitive information and resources is paramount. Traditional methods of authentication, such as passwords and PINs, are no longer sufficient to protect against the ever-evolving threat landscape.
Enter biometric security – a revolutionary approach that leverages unique physiological or behavioral characteristics to verify an individual's identity. In this comprehensive guide, we will delve into the world of biometric security, exploring its benefits, applications, and the future of identity verification.
What is Biometric Security?
Biometric security refers to the use of biological traits or behavioral patterns to authenticate and verify an individual's identity. Unlike traditional authentication methods, which rely on something the user knows (e.g., passwords) or has (e.g., access cards), biometric security relies on unique physiological or behavioral characteristics that are inherent to each individual.
These characteristics cannot be easily replicated or stolen, making biometric authentication one of the most secure methods of identity verification available today.
Types of Biometric Characteristics:
Biometric security encompasses a wide range of physiological and behavioral traits, each offering unique advantages and applications. Some of the most commonly used biometric characteristics include:
1. Fingerprint Recognition: Fingerprint recognition analyzes the unique patterns of ridges and valleys on an individual's fingertip to verify their identity. It is one of the oldest and most widely used biometric modalities, found in applications ranging from smartphones to border control systems.
2. Face Recognition: Facial recognition technology analyzes the unique features of an individual's face, such as the distance between their eyes, the shape of their nose, and the contours of their jawline, to verify their identity. It is commonly used in surveillance systems, access control, and smartphone authentication.
3. Iris Recognition: Iris recognition scans the unique patterns in an individual's iris – the colored part of the eye – to verify their identity. The iris contains a complex pattern of ridges, furrows, and freckles that are unique to each person, making it an ideal biometric modality for high-security applications.
4. Voice Recognition: Voice recognition technology analyzes the unique characteristics of an individual's voice, such as pitch, tone, and cadence, to verify their identity. It is commonly used in telephone banking, voice-activated assistants, and authentication systems.
5. Behavioral Biometrics: Behavioral biometrics analyze patterns in an individual's behavior, such as typing speed, mouse movements, and gait, to verify their identity. Unlike physiological biometrics, which are static, behavioral biometrics can adapt and evolve over time, making them particularly well-suited for continuous authentication and fraud detection.
Applications of Biometric Security:

Access Control: Biometric authentication is widely used to control access to physical locations, such as office buildings, airports, and government facilities. By requiring individuals to scan their biometric traits, organizations can ensure that only authorized personnel are granted entry.
Mobile Devices: Biometric authentication has become increasingly prevalent in smartphones and tablets, providing users with a convenient and secure way to unlock their devices, authenticate mobile payments, and access sensitive apps and data.
Border Control: Biometric technology is used in border control systems to verify the identities of travelers entering and exiting a country. Facial recognition, fingerprint scanning, and iris recognition are commonly used modalities to enhance border security and streamline immigration processes.
Financial Services: Biometric authentication is transforming the way we conduct financial transactions, providing a secure alternative to traditional PINs and passwords. Banking and financial institutions use biometric technology to authenticate customers' identities for online banking, ATM withdrawals, and mobile payments.
Healthcare: Biometric security is revolutionizing the healthcare industry, enabling secure access to electronic medical records, controlling access to restricted areas within hospitals, and ensuring the accurate identification of patients before administering treatment or medication.
Challenges and Considerations:
While biometric security offers many benefits, it also presents unique challenges and considerations that must be addressed:
1. Privacy Concerns: Biometric data is highly sensitive and personal, raising concerns about privacy, data protection, and potential misuse. Organizations must implement robust security measures to protect biometric data from unauthorized access, theft, or exploitation.
2. False Positives and False Negatives: Biometric systems are not infallible and can produce errors, resulting in false positives (incorrectly verifying an unauthorized individual) or false negatives (failing to verify an authorized individual). Organizations must carefully calibrate biometric systems to minimize the risk of false matches while maximizing accuracy and reliability.
3. Scalability and Interoperability: Deploying biometric systems on a large scale and ensuring interoperability with existing infrastructure and legacy systems can be challenging. Organizations must carefully evaluate the scalability and compatibility of biometric solutions to ensure seamless integration and optimal performance.
4. User Acceptance: User acceptance and adoption of biometric technology can vary depending on factors such as cultural norms, trust, and familiarity. Organizations must provide clear communication, education, and support to address user concerns and promote acceptance of biometric authentication methods.
The Future of Biometric Security:

1. Multi-Modal Biometrics: Combining multiple biometric modalities, such as fingerprint recognition, facial recognition, and iris recognition, into a single authentication system for enhanced security and reliability.
2. Continuous Authentication: Implementing continuous authentication methods that dynamically monitor and verify users' identities based on their ongoing behavior and interactions, rather than relying on single-point authentication events.
3. Biometric Encryption: Leveraging biometric data to generate encryption keys for secure communication and data storage, enhancing confidentiality and protection against unauthorized access.
4. Wearable Biometrics: Integrating biometric sensors into wearable devices, such as smartwatches and fitness trackers, to enable seamless and secure authentication for users on the go.
5. Ethical and Legal Considerations: Addressing ethical and legal considerations surrounding the collection, storage, and use of biometric data, including issues of consent, transparency, and accountability.
In conclusion, biometric security represents a paradigm shift in identity verification, offering unparalleled levels of security, convenience, and reliability. By harnessing the power of biometric technology, organizations can enhance security, streamline processes, and deliver seamless user experiences in an increasingly digital and interconnected world.
As we look to the future, the potential of biometric security to transform the way we authenticate and verify identity is limitless, paving the way for a safer and more secure future for individuals and organizations alike.
Please follow us if you enjoy this blog! Source: u/BiocubeTechnologies
#identity verification#digital identity#biometric identity#biometrics#biometric security#biometric technology#contactless biometrics#biometric authentication#multifactor authentication#future of technology#future tech#future of identity verification
1 note
·
View note
Text
User onboarding software has become increasingly important for businesses to provide a seamless and efficient experience for their customers. Simplici stands out among its competitors due to its innovative approach to fraud prevention and its user-friendly account opening process. Other leading user onboarding tools for 2024 include SEON, which specializes in fraud prevention using advanced machine learning, and Trulioo, which focuses on electronic ID verification and document authentication. Understanding the customer journey and providing personalized experiences are key factors to success in onboarding new customers.
#electronic ID verification#fraud prevention#onboarding new customers#document authentication#kyc#kyb#aml#identity verification solutions
0 notes
Text
Identity Verification for KYC Compliance: A Business Necessity
In today's digital era, this is one of the utmost importance for businesses to prioritize trust and security. In sectors where client identification and compliance with Know Your Client (KYC) rules are critical, such as finance, banking, and e-commerce, this is particularly important. Identity verification is essential to maintaining KYC compliance and shielding companies from money laundering, fraud, and other illegal actions. If you are looking for an identity verification service provider, you can contact IDefy. They provide the best identity verification service as per your needs.

#identity verification document#document ID authentication software#customer identification verification
0 notes
Text
Biometric Authentication: The Future of Security
In today’s digital age, security is of paramount importance. Personal information, financial data, and confidential business information are all at risk of unauthorized access. As a result, many organizations are turning to biometric authentication as a way to provide secure access to sensitive information. What is Biometric Authentication? Biometric authentication is a security process that…

View On WordPress
0 notes
Text
DARK SMS - DRAGON+

In today’s fast-paced digital landscape, maintaining privacy and security while communicating is more important than ever. Introducing DarkSMS, a cutting-edge virtual SMS platform designed to streamline your messaging experience without compromising your personal information. With our innovative virtual number service, users can receive SMS messages securely and anonymously, eliminating the risks associated with sharing private phone numbers. Whether you’re signing up for online services, verifying accounts, or simply looking to keep your communication confidential, DarkSMS has got you covered.
Virtual SMS
Virtual SMS refers to the messaging service that enables users to send and receive text messages through a virtual phone number rather than a traditional mobile line. This service is particularly useful for individuals and businesses looking to maintain privacy while communicating or verifying accounts.
One of the key advantages of using virtual sms is the ability to receive SMS without revealing your personal phone number. This is especially beneficial for online transactions, sign-ups for apps, or any situation where you might need to provide a phone number but want to protect your privacy.
Furthermore, virtual numbers can be easily managed from a web-based platform, allowing users to organize and store messages effectively. Many service providers offer features such as message forwarding, where received SMS messages can be redirected to your email or other platforms, ensuring you never miss an important notification.
In addition to privacy and convenience, virtual SMS services are often cost-effective. They eliminate the need for extra SIM cards or mobile contracts, allowing users to only pay for the services they actually use. This flexibility makes virtual number services highly attractive for startups and individuals working from remote locations.
As businesses increasingly adopt digital communication strategies, integrating virtual SMS into their operations can enhance customer interaction and improve engagement through instant messaging capabilities.
Virtual Number Service
A virtual number service offers a practical solution for individuals and businesses looking to maintain privacy while receiving communications. By using a virtual number, you can receive SMS messages without exposing your personal phone number. This feature is especially useful for those engaged in online transactions, such as e-commerce, as it safeguards against unwanted spam and protects your identity.
One of the key advantages of a virtual number service is its capability to function seamlessly alongside your primary phone line. Users can receive messages from various platforms effectively, whether it's for verification purposes, two-factor authentication, or simply keeping in touch with clients. The convenience of managing multiple numbers through a single device cannot be overstated.
With options to select numbers from different geographic locations, this service caters to users looking to establish a local presence in different markets. Moreover, these numbers can be set up quickly and easily, providing instant access to receive SMS without lengthy contracts or commitments.
To optimize your experience with virtual SMS and virtual number services, consider features like call forwarding, voicemail, and the ability to choose your own number. Such functionality enhances user experience by offering flexibility in communication while maintaining professional boundaries.
Ultimately, investing in a virtual number service can significantly enhance your business's communication strategy, allowing you to receive SMS reliably while focusing on building relationships with your clients.
Receive SMS
Receiving SMS through a virtual number is a convenient service that allows users to get text messages without needing a physical SIM card. This is particularly beneficial for individuals and businesses looking for privacy or those who wish to avoid exposing their personal phone numbers.
The process is straightforward: once you obtain a virtual number through a reliable virtual number service, you can start receiving sms messages. This service is essential for various reasons, including:
Account verification codes: Many online platforms use SMS to send verification codes. A virtual number allows you to receive these codes securely.
Business communications: Companies can use virtual SMS to receive client inquiries or feedback without revealing their primary contact numbers.
Privacy protection: By receiving SMS through a virtual number, users can protect their personal phone numbers from spam and unwanted solicitation.
Moreover, the get SMS feature of a virtual number service ensures that you don’t miss any important messages, even if you are on the move. Messages are often stored digitally, which means you can access them anytime and anywhere.
In summary, the ability to receive SMS through a virtual number enhances both privacy and accessibility, making it a valuable tool for users in various contexts.
Get SMS
Getting SMS messages through a virtual number service has become increasingly popular due to its convenience and versatility. Whether you need to receive texts for verification purposes or want to maintain privacy while communicating, virtual SMS provides a robust solution.
With a virtual number, you can easily get sms from anywhere in the world without needing a physical SIM card. This feature is particularly beneficial for businesses that require secure communication with clients or customers, as it ensures that sensitive information remains confidential.
Here are some advantages of using a virtual number to get SMS:
Privacy Protection: Using a virtual number helps keep your personal phone number private.
Accessibility: You can receive SMS messages on multiple devices, including tablets and laptops.
Cost-Effective: Virtual SMS services typically come with lower costs than traditional SMS plans.
Global Reach: You can get SMS messages from international numbers without incurring roaming fees.
Easy Setup: Setting up a virtual number to receive SMS is straightforward and often takes just a few minutes.
In summary, leveraging a virtual number service for SMS communication allows you to manage your messages efficiently while maintaining privacy, enhancing accessibility, and reducing costs. This is particularly useful for both personal and business communications, making it a smart choice for anyone looking to streamline their SMS functions.
631 notes
·
View notes
Note
Dear Friends 👋🏼❤️,
From the depths of my heart, I want to thank you for all your support and patience during this challenging time😔. In recent weeks, we faced a major setback when our campaign on GoFundMe was paused for verification. Those were moments filled with fear and anxiety, but we did not give up. We provided all the necessary documents, including medical records, my children’s university registrations, and our official IDs to prove that we are real people facing real struggles🤍🍉.
Thanks to God and your support, our identities and the authenticity of our campaign have been verified, and hope returned when our campaign was reactivated. Our need has become more urgent now, as we are seeking a safe home for my children—a place that will provide the safety and stability we lost🙏🏻🥺.
Every donation, no matter how small, has a profound impact on our lives. It’s not just a financial contribution, but a support that rekindles hope in our hearts. I kindly ask you to continue supporting us, whether by donating or by sharing our story with others. With you, we can build a better future for my family, filled with safety and hope.🙏🏻😔
https://gofund.me/abbc2759
🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸
Thank you from the bottom of my heart,
Maged & his family
56 notes
·
View notes
Text
Protect Your Business with Authenticate's Comprehensive Background Checks & Identity Verification API

In today's digital age, protecting sensitive information and verifying identities is crucial for any business. With the rise of fraud and cybercrime, it has become more important than ever to have reliable and effective tools for background checks and identity verification. This is where Authenticate comes in – your go-to source for an API for Advanced Background Checks and identity verification.
At Authenticate, we understand the importance of keeping your business and customers safe. That's why we offer a comprehensive API and SDK for multi-factor verifications. Our API and SDK are designed to be user-friendly, making it easy for businesses of all sizes to integrate into their existing systems.
Our Advanced Background Checks allow you to perform thorough and efficient background checks on potential employees, clients, or partners. Our advanced technology and algorithms gather information from various sources, including criminal records, credit history, and social media, to provide a detailed report within seconds. This not only saves time but also ensures that you have all the necessary information to make informed decisions.
But that's not all – our API goes beyond just background checks. With our API, you can also perform identity verification, ensuring that the person you are dealing with is who they claim to be. This is especially crucial for businesses in the financial and healthcare industries, where the risk of identity theft and fraud is high.
Our API For Background Checks uses a multi-factor authentication process, which includes document verification, facial recognition, and biometric data matching. This comprehensive approach ensures a high level of accuracy and reliability, giving you peace of mind knowing that your business and customers' information is secure.
Moreover, our API is constantly updated with the latest security protocols, keeping up with the ever-evolving landscape of cyber threats. This means that you can trust Authenticate to provide the most advanced and secure API for all your background check and identity verification needs.
But what sets us apart from other API providers is our commitment to user experience. We understand that not everyone is a tech expert, and that's why our API and SDK are designed to be user-friendly and easily integrated into your existing systems. Our team of experts is also available to provide support and assistance whenever needed.
Authenticate is your one-stop solution for an API for Advanced Background Checks and API Identity Verification. Our API and SDK offer a comprehensive and reliable way to protect your business and your customers. With our easy-to-use interface and constantly updated security protocols, you can trust Authenticate to provide the best background check and identity verification services. Don't wait any longer call us today at +1 833-283-7439 or visit www.authenticate.com.
#Identity Authentication#Identity Verification And Authentication#Irs Identity Verification#Photo Id Verification API#Public Criminal Record Search#Web API Identity Authentication#Identity Background Verification#Background Check API Integration#API For Background Checks
0 notes
Text
California Bills To Watch For
I'm sure by now that many people are aware of the dangers posed by AB 3080 (discussed in my post here), but for those unaware, there are yet other bills in California that pose a danger to free use of the internet which we should also keep on the forefront of our minds. 3 of the 4 bills I will mention here will be going up for a hearing in the California Senate Committee on Appropriations, one of the bills is currently being held in suspense file until the suspense file is read and thus will not be up for discussion in the same way as the rest. So that one will remain more on the back burner but still good to call your representatives about nonetheless. (A link on how you can find your reps here).
CA SB 976: Protecting Our Kids From Social Media Addiction Act (Senator Skinner et al)
Building on the California Age-Appropriate Design Code Act, this bill seeks to make it unlawful for the operator of an addictive 'internet-based service or application' to provide an 'addictive feed' to a user unless the operator doesn't have actual knowledge the user is a minor, has reasonably determined the user isn't a minor, or has obtained verifiable parental consent to provide an addictive feed to a minor user.
Essentially a very complicated and roundabout bill which would be difficult to enforce and would necessitate the usage of age verification for nearly all users. Especially when the alternative is that parents would have to also give up their identifiable information to allow a child to use an online platform. And also limits the ability of a minor user to receive notifications from a service or application during times assumed to be for school attendance or for late night usage. Great potentials for privacy violations and potential dangers for minors in abusive households where parents can exercise greater control over them and what they do. Also does not limit this specifically to social media platforms.
Overall a very unnecessarily complex bill that attempts to solve issues with perceived addictive social media features in inefficient and privacy violating ways.
Currently set for Senate Appropriations Committee hearing on May 13th.
CA SB 1228: User Identity Authentication (Senator Steve Padilla)
Requires social media platforms to verify the identities of people with large social media followings and influence in a tiered system. Nominally to minimize the spread of misinformation during an election year.
"Influential users" are defined as people who either has content that has been seen by more than 50,000 users within a seven-day period across all accounts the user controls on the platform, those with accounts over 15,000 followers, or ranks in the top 6% of users by amount of content viewed by users on the platform within a seven-day period across all their accounts on that platform. These users would be required to provide the platform with their name, telephone number, and email address in order to be considered authenticated.
"Highly influential users" are defined as people whose content has been seen by more than 100,000 users within a seven-day period across all accounts the user controls on the platform, those with accounts over 30,000 followers, or ranks in the top 3% of users by amount of content viewed by users on the platform within a seven-day period across all their accounts on that platform. These users would be required to provide the platform with their name, telephone number, email address, and government-issued identification in order to be considered authenticated.
Supposedly there would be safeguards and rules saying that any information taken to authenticate a user would not be stored or used for anything besides authentication. And they would be marked as authenticated, with the option to block non-authenticated users. But also allows social media companies the option of requiring either of these things even for those who aren't considered influential or highly influential.
Essentially another identity verification measure which should not be allowed to pass, and unnecessarily complicated and unlikely to work in its attempts to prevent misinformation.
Currently set for Senate Appropriations Committee hearing on May 13th.
CA SB 1444: Let Parents Choose Protection Act of 2024 (Senator Stern)
Requires large social media platform providers to create, maintain, and make available third-party safety providers through which parents or guardians are able to control what appears on their child's social media feed.
Another bill which by its sheer existence would put the identities and information of users at risk, both adults and minors. And would likely lead to further age or identity verification measures which would be wholly unnecessary and highly invasive.
CA AB 1949: California Consumer Privacy Act of 2020: collection of personal information of a consumer less than 18 years of age (Assembly Member Lowenthal)
Would remove the conditions that an online business have actual knowledge that the consumer is less than 16 years of age, and would prohibit a business from selling or sharing information of a consumer less than 18 years of age unless the consumer or their parent/guardian has authorized the sale of the personal information. Also requires businesses to inform the consumers of what information is being collected and sold and will not collect additional information. Allows consumers the right to opt out of any sale of personal information, but by default none under 18 may have their information sold.
Also runs the risk of invasive age verification becoming the norm for internet websites, rather than wholesale allowing the opting in and out of sale of personal information to be default for all.
Currently set to the Assembly Appropriations Committee on Suspension File.
With all that said, while I know it may seem like a lot, please look into these bills as much as you can, and send messages to your representatives letting them know you're in opposition to all of them and what they could potentially mean for our internet freedom, privacy, and safety.
#california#internet privacy#bad internet bills#california senate#california assembly#SB 976#SB 1228#SB 1444#AB 1949#kosa#ab 3080
46 notes
·
View notes
Text
Digital KYC: Transforming Customer Onboarding and Security in the Modern Age
In today's digital world, where speed, security, and efficiency are paramount, traditional paper-based Know Your Customer (KYC) processes are becoming increasingly outdated. Enter Digital KYC, a revolution in customer onboarding and verification that leverages technology to streamline processes, enhance security, and benefit both businesses and customers alike.

From Paperwork to Pixels: Embracing the Digital Shift
Gone are the days of cumbersome paper forms and lengthy verification procedures. Digital KYC utilizes online platforms and innovative technologies to automate and expedite the KYC process. This involves collecting and verifying customer information electronically, typically through secure online portals, mobile apps, or even video conferencing.
Benefits Abound: Why Businesses are Embracing Digital KYC
The advantages of implementing Digital KYC are numerous and far-reaching. Let's delve deeper into some key benefits:
Faster Customer Onboarding: Ditch the paperwork hassle! Digital KYC significantly reduces onboarding time, allowing customers to complete verification instantly through intuitive online interfaces. Studies by Deloitte show that digital solutions can reduce onboarding time by up to 70%, leading to higher customer satisfaction and improved conversion rates.
Enhanced Security: Gone are the days of vulnerable paper trails. Digital KYC often employs robust security features like biometric authentication (fingerprint, facial recognition, etc.) and encryption to protect sensitive customer data. This significantly reduces the risk of fraud and identity theft, safeguarding both businesses and customers.
Cost Savings: Automating manual tasks and eliminating paper-based processes leads to significant cost savings. Accenture reports that companies can save up to 70% on operational costs through digital KYC implementation. Additionally, reduced fraud losses and improved compliance add to the financial benefits.
Challenges and Solutions: Navigating the Digital Landscape
While the advantages of Digital KYC are undeniable, certain challenges need to be addressed:
Privacy Concerns: Data protection and customer consent are paramount. Businesses must ensure transparency in data collection and usage, complying with relevant privacy regulations like GDPR and CCPA.
Technological Hurdles: Seamless integration of AI, Optical Character Recognition (OCR), and other technologies is crucial. Additionally, ensuring user-friendly interfaces and accessibility across different devices is essential.
Regulatory Compliance: Staying abreast of evolving regulations and legal frameworks surrounding digital KYC is critical. Businesses must partner with technology providers who offer solutions compliant with relevant industry standards and local regulations.
Case Studies: Witnessing the Power of Digital KYC in Action
Numerous organizations have successfully implemented Digital KYC, reaping significant benefits:
DBS Bank (Singapore): Reduced onboarding time by 90% and improved customer satisfaction through a digital KYC platform integrated with AI and facial recognition.
HSBC (Hong Kong): Achieved 70% faster account opening time and a 20% reduction in fraud attempts through a digital KYC solution with biometric verification.
StanChart (India): Streamlined onboarding for small businesses by 80% using a mobile app-based KYC platform.
These examples showcase the real-world impact of Digital KYC in improving customer experience, enhancing security, and driving operational efficiency.
Conclusion: Embrace the Future, Embrace Digital KYC
Digital KYC is no longer just a trend; it's the future of customer onboarding and verification. By embracing this technology, businesses can gain a competitive edge, improve customer satisfaction, and ensure robust security. The benefits are undeniable, and the challenges are surmountable. As regulations evolve and technological advancements continue, Digital KYC's role in shaping a secure and efficient financial landscape will only become more prominent.
Are you ready to join the digital revolution?

#digital kyc#biometric remote kyc#ekyc#kyc#know your customer#biometric authentication#digital identity#identity#digital identity verification#identity verification#biometrics#technology#remote kyc#video kyc#contactless biometric#multifactor biometrics#multifactor authentication
1 note
·
View note
Note
is BCM something like a politician? Public speaker?
He's not, but there's a chance he could be around these people
"Blue Check Mark usually refers to the Blue Verification Check Mark on social media platforms, which is used to prove that the account is the official account of a public figure, celebrity, brand or organization, and is not a fake or impostor account. Blue Check Mark is awarded by the platform and is a mark of credibility and identity authentication, making it easier for users to identify real, official accounts."
BCM is a symbol of identity verification, representing the official identity of a public figure, celebrity or brand, and has a high degree of credibility.
BCM has a strong self-protection and defensive mentality and strives to ensure that its behavior complies with regulations and displays a professional and formal image to ensure safety and credibility and reduce negative impacts.
The behavior of BCM is regulated and restricted, and a certain social distance may be maintained, making it difficult to establish close relationships with others.

Power:
BCM is able to sense false information and rumors.
BCM can bring himself or others into the spotlight.
Because he is "symbolic" he is immortal.

Good at:
Capture people's hearts
Evacuate
Acting out fake/necessary emotions
Follow the rules

Not good at:
Fighting
Expression of emotion

Other:
Neutrality and the principle of avoiding conflicts as much as possible
Treat everyone equally
The goal is to live a leisurely and ordinary life
25 notes
·
View notes
Note
Dear Friends 👋🏼❤️,
From the depths of my heart, I want to thank you for all your support and patience during this challenging time😔. In recent weeks, we faced a major setback when our campaign on GoFundMe was paused for verification. Those were moments filled with fear and anxiety, but we did not give up. We provided all the necessary documents, including medical records, my children’s university registrations, and our official IDs to prove that we are real people facing real struggles🤍🍉.
Thanks to God and your support, our identities and the authenticity of our campaign have been verified, and hope returned when our campaign was reactivated. Our need has become more urgent now, as we are seeking a safe home for my children—a place that will provide the safety and stability we lost🙏🏻🥺.
Every donation, no matter how small, has a profound impact on our lives. It’s not just a financial contribution, but a support that rekindles hope in our hearts. I kindly ask you to continue supporting us, whether by donating or by sharing our story with others. With you, we can build a better future for my family, filled with safety and hope.🙏🏻😔
https://gofund.me/abbc2759
🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸
Thank you from the bottom of my heart,
Maged & his family
DISCLAIMER: UNVETTED
However, according to the notes under the blog’s posts, it is likely that it is legitimate. I am inclined to believe that it is
$7,300 USD/$70,000
#unvetted#vetting needed#mutual aid#palestine#free gaza#gofundmes#gfms#gofundme#free palestine#donations#palestine aid#palestine fundraiser#pls donate if you can#signal boost
8 notes
·
View notes
Text
Week 3: Digital Community: Tumblr Case Study
Gen Z is mourning the un-filtered public sphere of 2014 Tumblr

If you’ve spent any time on TikTok over the past few years, chances are you’ve stumbled into the wistful world of 2014-2016 nostalgia. ‘Tumblr Girls’ by G-Eazy is trending again, King Kylie era with jet-black nails and electric blue hair photos, Lana Del Rey’s Born to Die and Ultraviolence lyrics dripping with melancholy, the glorification of cigarettes and poetic sadness, and those moody GIFs of brooding white girls paired with angst captions about how life is just one big existential crisis.
It’s a full-blown revival of Tumblr’s golden age, when this aesthetic reigned supreme, and Gen Z has welcomed it back like a long-lost comfort blanket. Case in point: a girl doing a cover of Sky Ferreira’s Everything is Embarrassing, with messy hair and off-the-shoulder flannel look, sent the comments spiraling into a collective wave of 2014 Tumblr nostalgia (@reme, 2025).


As of 2021, on TikTok, the hashtag #2014tumblr boasts 83.9 million views, while its counterpart #tumblr2014 has garnered 51.9 million views (Navlakha, 2021). But what does this resurgence mean for a generation raised on fast-paced TikToks and Snapchat notifications? And what does it have to do with the public sphere of Tumblr?
Tumblr as a Public Sphere
Jürgen Habermas’ concept of the public sphere describes a space where individuals gather to exchange ideas outside traditional power structures (Çela, 2015, p. 195). While social media platforms often claim to foster such spaces, their algorithm-driven nature frequently distorts participation, privileging virality over authenticity (Yin, 2024, p. 10-14). This creates a tension between the ideals of a public sphere and the realities of social media's algorithmic governance (Dahlberg, 2007, p. 52). Social media platforms grapple with the challenge of distinguishing genuine user profiles from counterfeit accounts (Mahammed et al., 2023, p. 1).
In contrast, Tumblr operated as a counterpublic, a concept described by Warner (2002) as an alternative space where marginalized groups construct their own discourses outside dominant institutions. Byron et al. (2019, p. 2242) apply this idea to Tumblr, highlighting how queer youth used the platform for identity exploration and indirect yet meaningful connections. Tumblr thrived as a platform where users did not need verification badges or massive followings to have a voice; instead, all that was required was internet access and a willingness to share unfiltered thoughts. Unlike social media sites such as Twitter or Instagram, which often prioritize personal branding and follower counts, Tumblr fostered a culture of anonymity and authenticity, allowing individuals to engage without revealing their real identities.
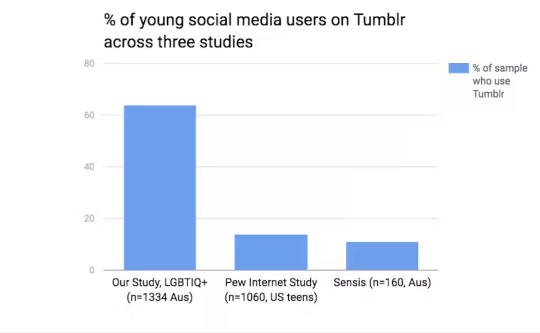
For many LGBTQIA+ users, Tumblr wasn’t just a blogging site—it was a lifeline. Queer youth engaged with the platform far more than other social media, finding a space for identity exploration and connection (Robards & Byron, 2017). According to Byron et al. (2019, p. 2242), young LGBTQIA+ used Tumblr to navigate their identities, often in ways that were indirect and anonymous yet profoundly meaningful. Unlike Instagram or TikTok, where visibility depends on engagement metrics, Tumblr enabled queer self-expression without the pressure of personal branding. The platform’s unfiltered, pseudonymous culture allowed young people to explore gender, sexuality, and mental health in ways that mainstream social media often stigmatized or ignored.
The Politics of Aesthetic and Self-Expression
The 2014 Tumblr aesthetic isn’t just about nostalgia—it’s a whole mood, a rebellion, and a contradiction all at once. It was a space where people rejected the glossy perfection of Instagram and Facebook, opting instead for something raw, messy, and deeply personal. But here’s the thing: even rebellion has its own aesthetic rules. Tumblr’s vibe might have been anti-mainstream, but it still had a way of shaping how people expressed themselves.
Take the #bodypositive movement, for example. At first, Tumblr was the go-to place for people who wanted to push back against traditional beauty standards. It gave users—especially marginalized ones—a space to celebrate diverse bodies, challenge unrealistic ideals, and embrace self-love in ways that mainstream media didn’t allow. But, as Reif et al. (2022, p. 5-6) point out, even in this “empowering” space, certain aesthetics started taking over. A lot of the content still followed a specific look—filtered but “effortless,” curated but “authentic.” So while Tumblr helped redefine beauty, it also reinforced new versions of what was acceptable.
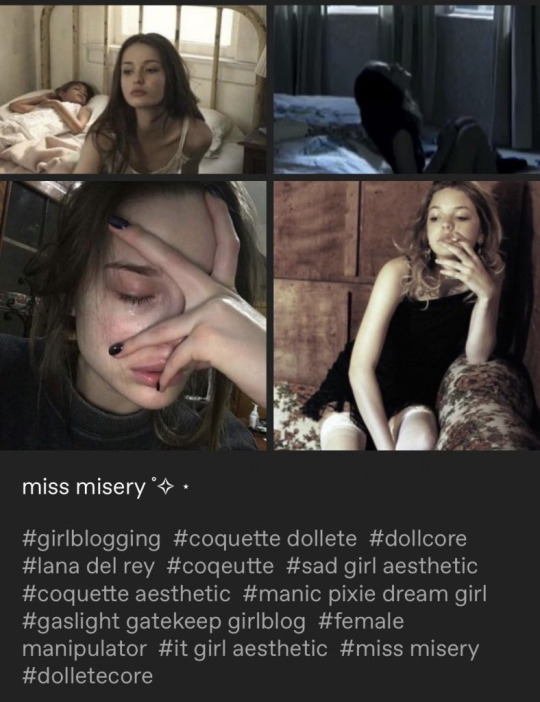
And that’s exactly the paradox of the 2014 Tumblr aesthetic itself. It was all about being different, but in a way that still fit a certain visual and emotional mold. The black-and-white photos of girls smoking in oversized sweaters, in wired earphones listening to Arctic Monkey, cryptic text posts about sadness—these weren’t just random; they became an entire brand. As Goldberg (2022) notes, Tumblr had a way of romanticizing self-destruction. It made heartbreak poetic. It turned depression into an aesthetic. It blurred the line between genuine self-expression and performance.
This whole push-and-pull dynamic also played out in the way people curated their identities online. As Byron et al., (2019, p. 2246) explain, even in supposedly free and unfiltered spaces like Tumblr, certain norms always emerge. People were crafting their own personas through carefully chosen images, quotes, and blog themes, but they were still following an unspoken rulebook.
Final thoughts
Today, Gen Z is attempting to reclaim that balance, by recreating Tumblr’s unpolished aesthetics on TikTok while navigating a vastly different digital landscape. In a way, this nostalgia is an act of rebellion against the hyper-curated, brand-saturated digital spaces we’ve grown used to. The irony, of course, is that Tumblr’s once-anonymous culture is now mediated through platforms that prioritize personal branding. Yet the fact that users are reviving this era suggests a persistent desire for a public sphere where self-expression isn’t dictated by corporate algorithms.
References:
@reme. (2025). everything is embarrassing. TikTok. https://vt.tiktok.com/ZSM8fg1Qf/
Byron, P., Robards, B., Hanckel, B., Vivienne, S., & Churchill, B. (2019). “Hey, I’m Having These Experiences”: Tumblr Use and Young People’s Queer (Dis)connections. International Journal of Communication, 13, 2242. https://www.researchgate.net/publication/338593649_Hey_I
Çela, E. (2015). Social Media as a New Form of Public Sphere. European Journal of Social Sciences Education and Research, 4(1), 195. https://doi.org/10.26417/ejser.v4i1.p195-200
Dahlberg, L. (2007). The Internet, deliberative democracy, and power: Radicalizing the public sphere. International Journal of Media & Cultural Politics, 3(1), 52. https://doi.org/10.1386/macp.3.1.47_1
Goldberg, A. (2022, February 2). What the Return of 2014 Tumblr Means For Body Image. Teen Vogue. https://www.teenvogue.com/story/what-the-return-of-2014-tumblr-means-for-body-image
Mahammed, N., Klouche, B., Saidi, I., Khaldi, M., & Fahsi, M. (2023). Bio-inspired algorithms for effective social media profile authenticity verification (p. 1). https://ceur-ws.org/Vol-3694/paper13.pdf
Navlakha, M. (2021, October 26). TikTok is reviving the 2014 Tumblr-era aesthetic. Mashable SEA | Latest Entertainment & Trending . https://sea.mashable.com/life/18022/tiktok-is-reviving-the-2014-tumblr-era-aesthetic
Reif, A., Miller, I., & Taddicken, M. (2022). “Love the Skin You‘re In”: An Analysis of Women’s Self-Presentation and User Reactions to Selfies Using the Tumblr Hashtag #bodypositive. Mass Communication and Society, 26(6), 5–6. https://doi.org/10.1080/15205436.2022.2138442
Robards, B., & Byron, P. (2017, May 29). There’s something queer about Tumblr. The Conversation. https://theconversation.com/theres-something-queer-about-tumblr-73520
Warner, M. (2021). Publics and Counterpublics. Zone Book. https://doi.org/10.2307/j.ctv1qgnqj8
Yin, H. (2024). From Virality to Engagement: Examining the Transformative Impact of Social Media, Short Video Platforms, and Live Streaming on Information Dissemination and Audience Behavior in the Digital Age. Advances in Social Behavior Research, 14(1), 10–14. https://doi.org/10.54254/2753-7102/2024.18644
#mda20009#lana del rey#2014 tumblr#2014 aesthetic#tiktok#public sphere#blog#gen z#nostalgia#week 3#swinburne#queer#lgbtqia#Spotify
6 notes
·
View notes
Note
Dear Friends 👋🏼❤️,
From the depths of my heart, I want to thank you for all your support and patience during this challenging time😔. In recent weeks, we faced a major setback when our campaign on GoFundMe was paused for verification. Those were moments filled with fear and anxiety, but we did not give up. We provided all the necessary documents, including medical records, my children’s university registrations, and our official IDs to prove that we are real people facing real struggles🤍🍉.
Thanks to God and your support, our identities and the authenticity of our campaign have been verified, and hope returned when our campaign was reactivated. Our need has become more urgent now, as we are seeking a safe home for my children—a place that will provide the safety and stability we lost🙏🏻🥺.
Every donation, no matter how small, has a profound impact on our lives. It’s not just a financial contribution, but a support that rekindles hope in our hearts. I kindly ask you to continue supporting us, whether by donating or by sharing our story with others. With you, we can build a better future for my family, filled with safety and hope.🙏🏻😔
My compaign has been verified by @heba-20
https://gofund.me/abbc2759
🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸🍉🇵🇸
Thank you from the bottom of my heart,
Maged & his family
6 notes
·
View notes