#Hashing
Text
here's your computer post ya freakin nerd
tl;dr hash algorithm art


left: sha512 empty string, using the nibbles (4 bytes) choosing a color from a 16-bit color palette
right: sha384 empty string, using the openssh "randomart" algorithm choosing a color from a 16-bit color palette
technical stuff below the cut
problem
one of the common issues in computer science and systems administration is comparing hashes. but the problem arises when you, the human being, have to compare two hashes. hashes come in the form of a very long hexadecimal string. It might look something like this:
da39a3ee5e6b4b0d3255bfef95601890afd80709 (sha1)
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 (sha256)
cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e (sha512)
these strings of text can be very long, and expecting a human being to check the exact match of 128 characters in a row (in the worst case) is unreasonable. it is unlikely to happen, but you can also get very very very close hashes. I remember seeing a twitter post (can't find it for the life of me) that showed two hashes that were different, but a cursory glance at them made them look extremely similar, eg:
e3b0c44298fc1c149afbf4c8996fb92427ae9800998b934ca495991b7852b855
versus
e3b0c44298fc1c14d41d8cd89961b204e9800998ecf8427ea495991b7852b855
it's pretty hard to tell at a glance that these are different. they have the same start and end prefixes, and there are some parts in the middle that are the same. but they're different! that's important! that means you've hashed different data, but it looks the same!
proposed solution
generate some art.
openssh does this. when you generate an SSH key, they give you a "randomart" (which is one of the algorithms I used above) of the key. From the comments:
If you see the picture is different, the key is different. If the picture looks the same, you still know nothing.
(source)
which I would say imparts some wisdom already. all you can use this for is determining if a hash is different. you cannot use it to determine if they're the same. what I've done is added a new dimension for what determines something being "different": a color palette. if you take the two extremely similar hashes from the example and generate a piece of hash art using the nibble method, they look like these:
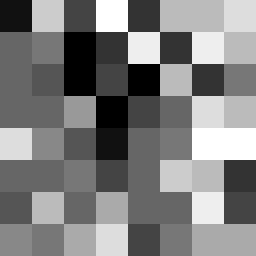

first on the left, second on the right. they look pretty similar, but then you add the element of a color palette and you get visibly different images.
this is not a perfect solution by any means. I completely made up the two example hashes, and actually ran into an issue where my program chose the same color palette for both of them - I had to tweak them. but I think it adds some more value to it.
methodology
this is just an explanation of how this all works. I'm going to avoid posting source code for now because it has my real name attached and I don't like that. maybe I'll strip my name and post it later.
image generation algorithms
there are two image generation algorithms that I have chosen: direct representation using each nibble of the hash, and the openssh "randomart" algorithm (linked at the bottom).
nibble algorithm
the "nibble" method takes each nibble (hex digit) of the hash, laying them out on a grid, and choosing the color that it should use on the selected palette. since all palettes are 16 colors, each value 0x0..0xf is represented. for example, taking the sha1 hash da39a3ee5e6b4b0d3255bfef95601890afd80709, the first row of the image would start with palette indexes 0xd, 0xa, 0x3, 0x9, etc. if we are using the red palette, the first row would start with blocks of these colors: #dd0000, #aa0000, #330000, #990000, etc. it's a direct representation of the hash, and completely lossless. the main downside is explained above - if you have two extremely similar hashes, it will yield two extremely similar images.
randomart algorithm
this has been derived using the openssh randomart algorithm. when you generate an SSH key, you will get some kind of "randomart" that looks like this:

the algorithm is as follows:
start a pointer (called a "worm") in the center cell of a 0-valued matrix (in our case, the matrix is 9 rows by 17 columns).
look at the bottom two bits of the first byte of the hash.
if the bottom bit is 1, then move the worm right - otherwise, move it left. if it cannot move in this direction without exiting the matrix, then don't move left or right.
if the top bit is 1, the move the worm down - otherwise, move it up. if it cannot move in this direction without exiting the matrix, then don't move up or down.
wherever the worm lands, increment the value of that cell.
continue this through the value of the hash, two bits at a time.
this is your output matrix. assign colors (or ascii characters) as you see fit.
I think this is a neat way of doing it, provides a simple piece of art, and two different hashes will, usually, look different.
the main weaknesses that stand out to me: this is a lossy algorithm that could create ambiguities - there are sequences of bytes that could hypothetically produce the same image twice (I am too lazy to come up with these, so that is an exercise left to the reader). additionally, I have noticed that this algorithm tends to drive the worm into a corner, and creates lots of diagonal streaks on its journey. unless the worm hits a wall, it can only ever move diagonally, for better or worse. it looks okay, but I think we can do better.
overall, I think this is a good basis for a new image drawing algorithm, and I might play around with that in the future.
sizing the output image
the images are just a matrix, each cell treated as a pixel, and then I size it up to 32x32 pixel blocks. the number of rows and columns are determined by the art algorithm used, and maybe the hash type (depending on which algorithm is chosen).
for the randomart algorithm, I just use 9 rows by 17 columns - this is what they use in openssh, but I want to play with this because you get pretty boring/dark randomart for hashes with fewer bytes. md5 hashes usually just look like black rectangles with a few lighter blocks, not very useful.
for the nibble algorithm, I tried to make the art as square as possible. for example, sha1 hashes are 160 bits long, or 20 bytes, or 40 nibbles (each nibble = 1 block in the art). 40 nibbles can be sized as a 40x1, 20x2, 10x4, or 8x5 matrix. I opted for the 8x5 matrix, but I want to make this customizable in the future. here are the image sizes I choose for all the hashes I support:
md5 - 128 bits, 16 bytes, 32 nibbles - 8x4
sha1 - 160 bits, 20 bytes, 40 nibbles - 8x5
sha224 - 224 bits, 28 bytes, 56 nibbles - 8x7
sha256 - 256 bits, 32 bytes, 64 nibbles, 8x8
sha384 - 384 bits, 48 bytes, 96 nibbles, 12x8
sha512 - 512 bits, 64 bytes, 128 nibbles, 16x8
choosing the color palette
each palette is 16 colors. there are 8 base color palettes: red, green, blue, black, cyan, yellow, magenta, and white. red palette is #000000, #110000, #220000, ... #ee0000, #ff0000. blue is #000000, #001100, etc. Black and white are the only ones that I think may introduce some ambiguity - black goes from #000000, #111111, etc to #ffffff. white goes in the reverse order, #ffffff, #eeeeee, etc to #000000.
the color palette is chosen by taking the sum of all the bytes in the hash, mod 8. for example, the sha1 hash da39a3ee5e6b4b0d3255bfef95601890afd80709 is broken into the parts 0xda, 0x39, 0xa3, ... 0x07, 0x09. These are added together to get 0x92e, or 2350 in decimal. 2350 % 8 = 6, so we choose the 6th color palette (zero indexed) of RGBBCYMW, magenta.
more ideas
rotating or reflecting the image based on the input hash might yield useful results
adding more color palettes may ensure fewer "similar" images
doing something using a noise algorithm (perlin noise, simplex noise) to generate image matrices using the hash as the seed.
further reading and sources
Hash Visualization: a New Technique to Improve Real World Security (Perrig, Song, 1999)
openSSH randomart algorithm (fetched 2024-05-23, commit hash fc5dc092830de23767c6ef67baa18310a64ee533)
thanks for reading!
22 notes
·
View notes
Text

fox, furze, flowers, flour
brush-tails rush trails
18 notes
·
View notes
Text
The Scrunchie Problem
Last year in August I had a brilliant idea. I will use some scrap red sequined fabric from my stash and create a couple scrunchies for the annual Red Dress Run. It will be easy! I already have everything I need: fabric, elastic, thread, sewing machine. I can knock these out in an hour or two.
So I pull out the quilting cutting mat and fabric pizza wheel and make 2” strips. And thinking about how I’d like my seams to be both clean and easy, I sew the short ends of the fabric to make a loop first. Then the long edge leaving about 1” hole for turning the fabric.
But when I go to turn the fabric after making those seams, I get stuck. At first, I think I’m just physically stuck. The pencil I’m using to turn the fabric tube inside out is starting to get gunked up from the sequin glue. And I can’t seem to get the full turn out.
My hole must be too small and my fabric tube too narrow. That’s okay. I will sew the next strip the same way but leave a larger hole. But this time when the turn out won’t seem to complete, I realize what I’ve done wrong. My wrong-side-out shape was a doughnut. But my right-side-out shape was… tube snake.

Do you remember these toys? IT’s a tube filled with water or gel and when you squeeze it, the inner part shoots to the outside and the entire thing pops out of your hand.
So how did my doughnut become a tube snake?
Both shapes are a form of a torus, or a circular toroid. The torus has two raidii, where r is the radius of a wedge of the doughnut and R is the radius of the entire doughnut ring. If we think of our donut ring as a latitude ring, once we turn it inside out, the latitude has become a meridian. So, our two radii have swapped places. Little r is now the overall radius and big R is now the wedge cross-section radius. Our shape has a large difference in scale between the two radii, so the new shape isn’t a doughnut. We get our tube snake. The tube snake is still a toroid, just a doughnut that has been stretched out to be tall.
Now that we understand the geometry, how do we sew a scrunchie correctly? I felt the internet had a lack of good instructions for this task, despite seeming so simple and like it would be a common craft idea. So I’m here to help!
Scrunchie Sewing Pattern Instructions
1. Cut out a strip of fabric. 2” was a bit narrow, 4” makes a good average sized scrunchie, and 6” will make a big bold scrunchie. The length should be about 24”, but exact measurements are not important.
2. Fold your fabric in half “hot dog” style and pin the long edges together. Sew the long edges together leaving a gap between 1” and 2” in the center.
Fabric Key

Step 2
3. Now we have to bring the short edges together by pulling one end inside of the fabric tube. We are making the tube snake on purpose! The shape will be turned such that the right side of the fabric is the inside surface of the tube snake and only the wrong side is exposed. Align the raw short edges of the tube. Pin and sew the complete ring. Please note that this seam is the entire circumference of little r and only through two layers of fabric.

Step 3
4. Now when we turn our shape with the right-side-out, we will have one big long doughnut.
5. Measure out a strip of elastic. I usually use ¼” width elastic and about 8” of length, but I have very thick hair and regularly destroy hair ties. Adjust based on your fit.
6. Feed the elastic strip through the tube taking care not to lose the tail end. I like to use two safety pins: one securing the tail to the opening and the second to help me feed through the tube. Sew the ends of the elastic to each other in a flat seam.
7. Last step is to close the opening. If you’re feeling fancy you can breakout the hand needle and close with an invisible (ladder) stitch. But if you’re a machine girl, tuck the raw edges in and sew a short straight seam over the opening.
And you’ve done it! You made a scrunchie!

Bonus Round!
What if I wanted to use an off-the-shelf hair elastic instead of a strip? I had black chiffon scraps from a jumpsuit that was too long for my petite height. My white ¼” elastic would be visible (and unattractive) in a scrunchie made from that fabric. How would I get an already looped black elastic in there? I under-thought my very 1st scrunchie attempt. Time to OVER-think it!
In order to get your already loop-shaped hair elastic in your scrunchie, the elastic needs to be integrated in step 1. That means when you fold your strip in half hot dog style, the hairtie is already in the hotdog bun. Fold the fabric around the loop. Part of the hair elastic will be exposed at the ends of the fabric strip. It will look like an inside-out scrunchie already. Take care when sewing your long edge seam to stretch the section of fabric under the machine. Don’t let the scrunchie folds get sewn in.
When you turn your fabric to sew the short edge seam, about half of your hair elastic will be exposed with the other half inside the tube snake. This time you need to be sure not to catch the elastic when you sew the seam.
And here comes the magic. When you turn the fabric right-sides out, the hair elastic is carried to the inner tube. Close your last opening as before.


Can you even tell that I went the extra mile to use a black elastic?
Applications to other sewing projects
My most recent sewing project is a bridesmaid’s dress for me to wear at my sister’s wedding. My requirements were fairly open: black chiffon, maxi length. So I decided to make my own and selected a pattern from Simplicity, S8870 in “View A.”

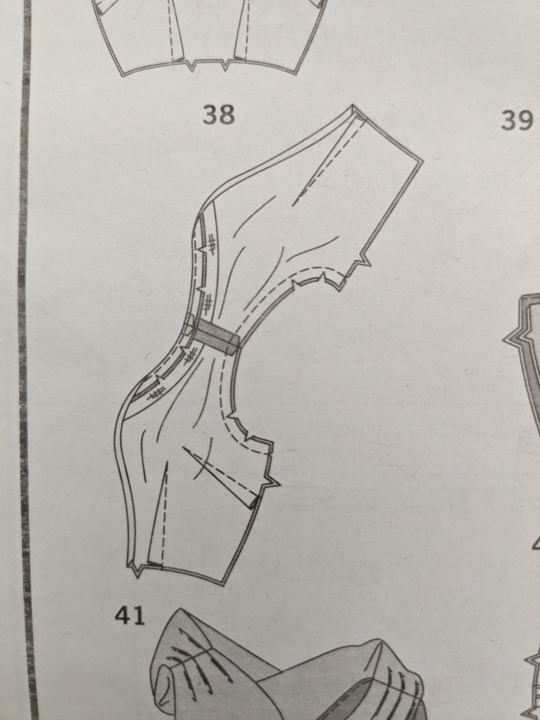
You’ll notice that the dress has a one-strap design with a loose drape that is attached at the left shoulder and then hangs over the right arm. The steps of the pattern have you sew that drape into the shoulder seam before any other steps that associate the overlay and lining or front and back of the bodice. Next, I had to understitch the neckline. Then came my secret application of The Scrunchie Problem.
“38. Tightly roll up drape for View A or Sleeve for View D. FOR VIEWS A, B, D- Stitch lining to bodice at entire armhole edge being careful not to catch drape for View A or sleeves for View D.”
I couldn’t see the drape anywhere in the diagram for that step so I rolled my drape cinnamon roll style and pulled it out of the way of my new seam. But I made the mistake of pulling it to the outside of my new seam. I did it again! I created a new tube snake that I can never pull my drape all the way out of!
The correct interpretation of that step was to roll the drape dosa style and hide within the shoulder section. That’s why I couldn’t see it in the diagram.
Wrap up
I hope I've inspired you to make a scrunchie. It’s a great use for scrap fabric. Especially from maxi dresses that us unfortunate, short ladies had to cut several inches off of the bottom.
What should I share next? Finished bridesmaid dress? Finished wedding present quilt? Or something I haven't even decided to make yet?
#diy#sewing#machine sewing#sewing problems#sewing patterns#scrunchie#hair accessories#hair ties#hair bows#crafts#dressmaking#geometry#torus#nerd alert#sewing nerd#toroid#craft nerd#problem solving#hashing#hash house harriers#red dress run#SOH4
5 notes
·
View notes
Text

rereading homestuck, i found the hash modus particularly interesting (probably because i've been trying to learn react, and, thus, have been looking for things it might be good for), and thought it would be fun to have an interactive version. right now there's only a few hashing algorithms, but i already have fun just putting in words when they come up
#homestuck#react#reactjs#hashing#sylladex#part of a healthy sylladex at least#website#toy#(that's all it is to be honest but it's fun to play with :])#tumblr seems to appreciate my little homestuck things more so#also i hate the notation used in the comic it's just#it's just wrong#i get what it's going for#but
6 notes
·
View notes
Text
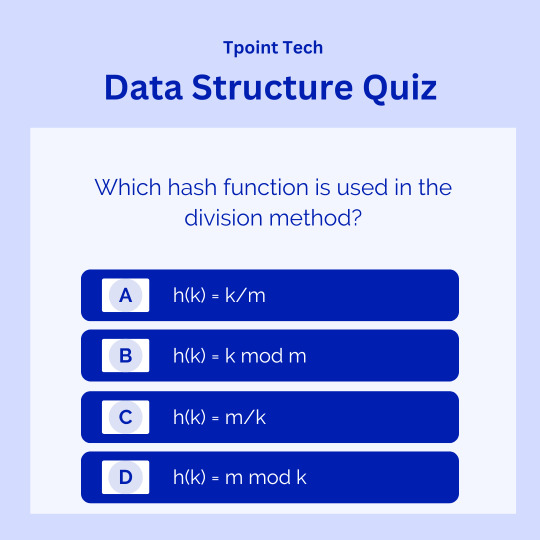
Test Your Knowledge: Quiz Challenge!!! 📝🧠
Which hash function is used in the division method?🤔
For more interesting quizzes, check the link below! 📚
https://bit.ly/3XpXA1y
For the explanation of the right answer, you can check Q.No. 20 of the above link. 📖
0 notes
Text
youtube
1 note
·
View note
Text
Which of the following is a technique used to protect data integrity?
Which of the following is a technique used to protect data integrity? A. Encryption B. Hashing C. Steganography D. Both A and B
The correct answer is:
D. Both A and B
Both encryption and hashing are techniques used to protect data integrity.
Encryption is primarily used to protect data confidentiality by encoding information so that only authorized parties can access it. However, some encryption methods also offer integrity protection by including checksums or cryptographic hashes to detect if the data has been altered.
Hashing is a technique that involves creating a fixed-size hash value from a set of data. It is used to verify the integrity of the data by comparing the hash value of the data before and after transmission or storage to check for any alterations.
Therefore, both encryption and hashing can be used to protect data integrity. Steganography, while useful for hiding information within other files or media, does not inherently protect data integrity.
0 notes
Text
7 tips for preventing pernicious password-based breaches - CyberTalk
New Post has been published on https://thedigitalinsider.com/7-tips-for-preventing-pernicious-password-based-breaches-cybertalk/
7 tips for preventing pernicious password-based breaches - CyberTalk


EXECUTIVE SUMMARY:
Remember the infamous 2021 SolarWinds supply chain attack? Cyber criminals were able to coordinate the attack because an intern rendered the password ‘solarwinds123’ publicly accessible via a GitHub repository, in 2018. While this led to an extreme business compromise situation, SolarWinds is not the only organization that’s ever struggled with password management…
World Password Day is celebrated on the first Thursday in May and serves as an annual reminder to reevaluate and upgrade organizational password security.
In fact, research shows that eighty-one percent of corporate data breaches occur due to poor password management — an avoidable problem that can cost an organization as much or more than $4.35 million, which is the average cost of a data breach.
Despite the seeming triviality of passwords, as evidenced by the SolarWinds episode, it can prove exceedingly difficult for organizations to recover – financially and reputationally – from password-based breaches. In this article, brush up on best practices for preventing serious incidents that start with a password.
7 tips for preventing password-based breaches
1. Leverage strong password requirements. Although no password is ever entirely hack-proof, longer passwords are challenging for cyber criminals to guess, decipher or otherwise exploit.
Require a minimum number of password characters, a mix of upper and lower case letters, numbers and special characters. In addition, due to the nature of cyber criminal tactics, consider disallowing the use of dictionary words, common phrases and personal information within passwords.
2. Enable multi-factor authentication (MFA). In the event that a password or multiple passwords are compromised, multi-factor authentication (MFA) provides an extra layer of security. MFA should be applied for all user accounts and critical systems.
One factor in the MFA model is typically a standard password – something that the employee knows. While another factor, like a code received via text, is generally something that the employee has. Biometrics can theoretically represent yet another factor, however, experts advise against widely applying biometric authentication mechanisms for security purposes.
3.“Hashing” and “salting” passwords. These protocols are recommended by the National Institute of Standards and Technology (NIST). In case the terms are unfamiliar, NIST defines a hash as “a function that maps a bit string of arbitrary length to a fixed-length bit string”. In other words, the practice of hashing effectively scrambles the password characters in a way that ensures that a database never exposes a list of plain text passwords to cyber criminals. Salting involves adding supplementary data to passwords ahead of hashing, rendering stored passwords particularly challenging to exploit.
4. Educate and empower employees. Ensure that your organization’s employees are aware of common phishing tactics used to gain passwords. Emphasize that hackers commonly pose as trustworthy parties and/or may send users malicious webpages through which to input credentials. When it comes to employee education, review a variety of plausible scenarios through which cyber criminals may attempt to pinch passwords. Empower employees to protect their credentials.
5. Leverage a lockout mechanisms. NIST suggests locking a user out of password protected accounts in the event that an incorrect password has been input multiple consecutive times. NIST says that no more than 100 login attempts should be permitted. Many organizations opt to lock accounts after three to five incorrect login attempts.
6. Apply the principle of least privilege. Provide employees with the privileges that they require in order to effectively complete job requirements. Avoid providing employees with superfluous permissions. This way, in the event of account compromise, the damage will likely be limited.
7. Respond to suspicious activity. Set up alerts that can provide your team with information about suspicious activities, such as a substantive series of failed login attempts from unfamiliar locations. Ensure that your team investigates and responds to these alerts, as this will help prevent potential breaches.
For more password security insights, please see CyberTalk.org’s past coverage. To receive inspiring cyber security insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#account compromise#Accounts#alerts#analyses#Article#authentication#biometric#biometrics#breach#Business#code#compromise#credentials#cyber#cyber criminals#cyber security#cybersecurity#data#data breach#Data Breaches#Database#education#Employee Education#employees#factor#github#hack#hackers#Hash#hashing
0 notes
Text





HEAD CANON: What if walking mushrooms sat on decaying corpses to get their nutrients. A useful tactic when they roam dungeon areas that aren't their typical environments and can't provide them food so this is how they adapt 👀 hufhufhfuf
alternatively:

#Dungeon Meshi#Laios#Marcille#Chilchuck#Senshi#Walking Mushroom#big thanks to me fwens for helping me hash this out#comics take so long and they kept me sane while i try to finish this ahhHH#fanart
14K notes
·
View notes
Text
I love hash tables.
0 notes
Text







no more fan-ta-sizing about it! everything's already changed~
#dimension 20#fantasy high junior year#fhjy#figueroth faeth#riz gukgak#adaine abernant#fabian seacaster#gorgug thistlespring#kristen applebees#fh class quangle#my! class swap thing! I guess this is like the poster for it now#got overinvested and finished it properly instead of winging it lol#in closeup order: cleric!gorgug; bard!riz; rogue!fabian; sorcerer!kristen; barbarian!fig; artificer!adaine#this one does have the harpoon gun I'd give fabian during sophomore year but literally only figured out for this piece lol#I like how it looks tho Im glad I hashed it out#thinking abt power armor adaine a lot tbh... she has the transhumanist audacity. she's villain-adjacent enough#to attempt unspeakable acts of body improvement#(its funny bc to wear a rig like that would Also demand a certain level of physical strength from you)#also yeah this is the thing with riz holding a megaphone that got me considering#its fun! it fits the aesthetics! maybe it'd grant him range for bardics#maybe he gets to keep that Im just not sure how he'd carry it around lol#fig gets to have all of her makeup... I like almost never remember to draw it usually kdsjfhdjk listen. I just forgor#I always forget makeup is real#also dont ask me what's in kristen's thermos it Is usually tea but you truly never know#sometimes its soup. it can be lighter fluid. soap perhaps. hot chocolate#also if u come knocking on my door abt kristen's somatic in this piece: I wont be home#she gets to be gross especially bc shes funny and 17yo and gay. we give it to her#okay I. whoo I should lay down. finally I can move on to other things#cheers! wahoo. yahha perhaps
4K notes
·
View notes
Text
How Does Hash Function Help Secure Blockchain Technology?
Blockchain has taken the world by storm, promising enhanced transparency, security, and decentralization across countless industries. But what exactly makes this groundbreaking technology so secure? The answer lies in a unique cryptographic tool known as a hash function.
In the blockchain universe, hashes serve as vigilant guardians, enabling key security capabilities that uphold the integrity…

View On WordPress
0 notes
Link
MD5 Generator
0 notes
Text
so fucked up that walter white is out there right now stealing christmas. just hauling that shit away. and lying to jesse that he’s just taking his tree back to his workshop to fix it up because there’s a light on one side that won’t light quite right and getting him a glass of water and sending him back to bed?? that’s fucked.
32K notes
·
View notes
Video
youtube
So VirusTotal. Last week they published a report titled "Deception at Scale," where they laid out the terrain of the malware samples that are uploaded to them more or less constantly to be analyzed. They sit in the perfect place to see what's going on. They've got great scope.
I've explained in the past that signing my own executables, I've discovered the hard way, because people were saying, hey, Windows is saying this is not safe, you've got a virus, it's like, no, I don't. Actually, it didn't say that. It just said this is, you know, you don't have any reputation here. So the point is that signing my executables was not sufficient proof of the integrity of my apps to bypass various of what are now hair-triggered malware cautions.
But VirusTotal reported among other things, get this, that fully 87% of the more than one million malicious samples which were signed at the time they were uploaded to VirusTotal since the start of last year, January 2021, contained a valid signature. 87% had a valid signature, those that were signed. So what that tells us is that signing code no longer means much. It's necessary, but not sufficient. The bad guys are arranging to obtain code-signing credentials, just like any other legitimate code publisher would. Just like I do.
So moving forward, the only thing that can be used, that is, can be relied upon, is the reputation of the hash of a given executable that is earned over time. Any new hash will need to start over from scratch earning the reputation that that specific exact code that it's the hash of is trustworthy.
And there was another little interesting tidbit. If you care to protect yourself somewhat by inspecting the Certificate Authority who issued the Authenticode certificate that was used to sign a program which you're considering running, it's worth noting that more than half, actually more than 58% of the most-often-abused code-signing certificates were all issued by just one company, a Certificate Authority known as Sectigo.
And if the name Sectigo isn't ringing any bells, it's probably because they renamed themselves after their repeated conduct spoiled and soiled their previous name, which was Comodo. We've talked about Comodo quite a bit in the past, all the different mistakes they made like allowing people to create their own certificates through problems in their web interface and giving certificate minting authentication to people who didn't warrant it and so forth.
Anyway, I imagine that they're the favorite of malware authors mostly because their certs are less expensive than the competition. And really it's not their fault that VirusTotal sees most malware signed by their certs, since anyone can purchase a code-signing certificate from any certificate authority, so going to go with the cheapest.
I don't, but I don't want to be signed by Comodo, now named Sectigo. And the whole thing is roughly analogous to what Let's Encrypt did to TLS connections; right? Once upon a time having a web server certificate meant something. Not anymore. Today, everyone needs to have one, and they mean nothing because they're just being minted by automation based on the domain of the server that they're sitting behind. So okay.
Anyway, VirusTotal also revealed that the top three most-often-spoofed programs were Skype, Adobe Reader, and VLC Player. Malware is masquerading as those three utilities - one of those three, Skype, Adobe Reader, and VLC as the top three - as basically, obviously, as a means to abuse the well-earned trust that they've earned, that those apps have earned with users everywhere.
And while those are the top three, the top 10 are rounded out by 7-Zip, TeamViewer, CCleaner, Edge, Steam, Zoom, and WhatsApp. So, yeah, the top of the popular apps that people are needing now to grab wherever they are.
So VirusTotal said in their report last week: "One of the simplest social engineering tricks we've seen involves making malware look like a legitimate program. The icon of these programs is a critical feature used to convince victims that these programs are legitimate." Just the icon. Of course, no one is surprised that threat actors employ a variety of approaches to compromise endpoints by tricking unwitting users into downloading and running seemingly trusted executables.
The other way this is achieved is by taking advantage of genuine domains, at least the top-level or second-level domains, to get around IP-based firewall defenses. Some of the most abused domains which VirusTotal has seen are discordapp.com, squarespace.com, amazonaws.com, mediafire.com, and qq.com. In total, more than 2.5 million suspicious files were downloaded from 101 domains belonging to Alexa's top 1,000 websites. In other words, 10% of the top 100 website domains have been used as sources for malware. And the misuse of Discord has been well-documented, with that platform's content delivery network becoming a fertile ground for hosting malware alongside Telegram, while also offering a perfect communications hub for attackers.
So ultimately, checking anything that's downloaded which might be suspicious against VirusTotal, I think, is the best thing anyone can do. As I mentioned a while ago, back when I was needing to bring old DOS machines onto my network in order to debug SpinRite on them, I was sometimes needing to go to well-off-the-beaten-path driver repositories to locate old drivers for old network adapters. Driver repositories are classic sources of malware.
So in every case, I ran anything that I downloaded past VirusTotal to make sure that it didn't raise any alarms. And normally you get like one or two, some weird obscure, you know, VirusTotal I think scans across or against as many as 75 different virus, you know, antivirus engines. And you'll typically get a couple reds, misfires, false positives from some scanners you've probably never heard of. And so that's not a problem. It's when you see like 20 or 30 of them lighting up red that it's like, okay, do not click this thing so that it's able to run. And stepping back from all this a little bit, it's so annoying that so much energy is being spent holding back the forces of darkness. Look at how much we put in now to doing that. But on balance it's worth it because what can be done with computers today is truly amazing.
0 notes
Text
Day 3 - SC-900 - Encryption, Hashing, & Broad Compliance Concepts
Hashing is a one way function designed to scramble plain text into an unique digest in an indecipherable way.
Hashing has the following requirements:
-Must accept any length of characters into its input
-Must produce a fixed length of characters for its output
-Must be relatively easy to compute
-Must not be reversible
-Must avoid collisions(having two different inputs that produce the same output)
Encryption is the act of scrambling plain text in a way that can be reversed via a medium(key, passphrase, silly dance, etc)
Symmetric encryption is when plaintext is encrypted & decrypted by the same key. Symmetric encryption is often fast to operate & used for working with bulk encryption/decryption.
Asymmetric encryption is when plantext is encrypted with a single key & then decrypted by a different key.
-Public/Private key encryption
#certification#sc 900#100 days of cyber security#cybersecurity#iam#what is a break?#infosecurity#encryption#hashing#compliance#symmetric#asymmetric
0 notes