#How to hack any mobile numbers
Explore tagged Tumblr posts
Text
It's a bit of a funny and sad mix, how much of a Lohrak around Dume's neck the Vahki are. Certainly Dume is meant to be flawed as a Turaga, a somewhat suspicious character and cranky old man who think Matoran these days need to learn to respect their elders, but ultimately he's a good guy who'd give his life for the cause while spitting in the face of whatever killed him (see him telling Vezok, Avak and Reidak to go do something anatomically improbable when they try to extort him with a Kanohi Dragon). And given how important Metru Nui is, and how dangerous the outside world was, yeah Metru Nui does need some sort of standing army/police force to ensure that shit like the Barraki rebellion or the Matoran Civil War doesn't threaten to kill Mata Nui and doom the MU to drift endlessly through space, but holy shit the Vahki are so insanely bad at it, it's hard to think he'd sign off on it.
As an army they're pretty okay, they're very mobile with two modes of walking and one flight mode, their equipment is also extremely good offensively (mind control, seeing through your targets eyes, you hurt yourself in your confusion, etc), as well as a Kanoka disc launcher for more direct combat, and they're smart enough to think tactically, all without risking any Matoran/Toa/Turaga in combat (and that's without getting into the elite versions). But for Police work... well, they're okay for a Police State where you don't have to give a shit about what your citizenry thinks, their borderline psychotic nature means they're very effective at terrorizing a population into compliance even before bringing in the Brain Hacking they can do, and they are supposed to be the Police for Makuta!Dume's Police State...
They just also happened to be the Police for Regular!Dume's (Police(?)) State, which is a really bad look for someone who's supposed to be Not Actually A Villain. Based on what we see of them, the Kralhi that preceded the Vahki were probably much better at police duties (given that after being driven out of the city by Matoran who tried to "shut them down" they were totally willing to aid and protect Mavrah without issue they clearly don't share the Vahki's abusive nature) without having to take a number of Matoran away from work to do the police work instead (and thus potentially imperil Mata Nui and the MU as a whole by having them not do the necessary work in his brain). If the issue with them was that they left Matoran too weak to do their job after being policed, then maybe all the Kralhi needed was an equipment overhaul rather than being completely scrapped?
I don't know, Dume is meant to be Flawed but Good, but historically he's just made such a baffling decision with the Metru Nui's police forces, spurred on largely I think by Out-Of-Universe needs than because it made sense in-universe, he kind of ended up accidentally being the BIONICLE equivalent of Sentinel Prime, but because it mostly happened off screen it's easy enough for the story to sweep that under the rug. A lore hungry fandom on the other hand is not so easy to shake and I'm left trying to come up with a reason why he'd agree to the Vahki beyond the incredibly unsatisfying "he doesn't really care about the Matoran" or "he didn't think it through" and variants thereof answers.
69 notes
·
View notes
Note
Okay so I was actually wondering about this but what would happened if ata or Noelle’s darling was a target to get assassinated because of being close to ata or atas assistant? What if darling actually got hurt? Hell if ata darling was pregnant and this actually happened to her while out? How would she deal with it?
Atalanta would actually put the city into a state of emergency if her Darling was threatened, and if she was kidnapped? The whole Montclair family would be mobilized. Jamie and Asteria are coming to the Penthouse and all three of them will be working with both the police and Atalanta's special forces to find Darling. Even Jamie will help, he loves his Daughter-In-Law too. Eventually, they will recover you, and if you are hurt, Ata will dismantle the entire authority that hurt you brick by brick, aided by her parents. And pregnant? Messing with her wife and heir? You may want to off yourself in your cell because if Ata gets ahold of you, you may spend the next few years being brutally tortured. You will be taken to the Montclairs country estate to recover with the entire family hovering over you for a number of months.
If Noelle checks the cameras to find you gone, she is immediately going to the person with the highest chance of helping: Ata. Ata will gladly help, lending Noelle use of her special forces to find you. Noelle, using some less than legal methods, will hack into the city's security cameras and track you down using the trackers she has sewn into your clothes and shoes. From that, she will have the security forces swiftly and secretly extract you. She can't have any of this going public, you know. Ata will frame the group for some sort of horrible crime and there will be a brutal and drawn-out trial where it is made abundantly clear to the entire city that these guys are criminals and will be put away for a long time. You are safely taken either to a private hospital or back to Noelle's apartment to recuperate safely, and you don't have to testify, that would be much too much stress on you. Noelle will ensure their prison sentence is long and terrible, giving them enough torment to rot their brains in their skulls. She would also probably bribe other prisoners to torture them too. Your security team will be doubled and you're not leaving the apartment for at least 9 months now.
#Atalanta my oc#Asteria my oc#Jamie my oc#Noelle my oc#yandere oc#soft yandere#yandere headcanons#yandere darling#yandere imagine#yandere blog#yandere fluff#yandere x darling#yandere#yandere girl#possesive yandere#yandere headcanon#yandere headcannons#yandere lesbian#yandere original character#yandere wlw#yandere x willing reader#yandere x reader#yandere x y/n#yandere x you#yandere thoughts#familial yandere#yandere family
50 notes
·
View notes
Note
Hi :) Perhaps an odd one, but I was wondering if you had any recommendations of games to play out events that have already happened? The end game has been predetermined, but the events that lead to it are more mutable? I'm running a dnd game with a group that has been very open to trying out different systems and I was thinking it could be very fun to put the player characters back in time into the shoes of other characters during the campaign's inciting event. Thanks!
Theme: Recalling Events
Hello friend, so there are definitely games that allow you to do something similar to what you’re looking for. There are games that go back in time, games that flashback to previous events, and games that take place at moments in our real-world history that have already happened. I don’t know if any of those games exactly work for what you’re looking for, but they might be interesting to look at in order to ask yourself how you want to run something in a timeline that you’ve established for a specific setting.




Ten Candles, by Calvary Games.
Ten Candles is a zero-prep tabletop storytelling game designed for one-shot 2-4 hour sessions of tragic horror. It is best played with one GM and 3-5 players, by the light of ten tea light candles which provide atmosphere, act as a countdown timer for the game, and allow you to literally burn your character sheet away as you play.
Ten Candles is described as a "tragic horror" game rather than survival horror for one main reason: in Ten Candles there are no survivors. In the final scene of the game, when only one candle remains, all of the characters will die. In this, Ten Candles is not a game about "winning" or beating the monsters. Instead, it is a game about what happens in the dark, and about those who try to survive within it. It is a game about being pushed to the brink of madness and despair, searching for hope in a hopeless world, and trying to do something meaningful with your final few hours left.
There is only a few facts pre-determined at the beginning of this game, but those facts are important: all of your characters will die. Over the course of the game, you will slowly blow out ten candles as your characters grow closer and closer too their doom.
However, the nature of that doom can be altered. I’ve seen it done for the Locked Tomb, for example, and you can set it in a modern world, a futuristic world, or a fantasy world if you like. If you want to hack this game for your group, I’d recommend playing out a scenario that involves characters that you don’t mind saying goodbye too - perhaps a catastrophe your party heard about, and you can role-play the last moments of some people they failed to save.
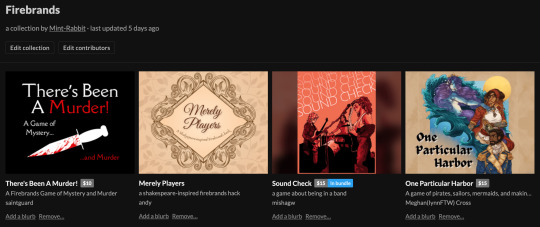
Firebrands Games
Mobile Zero Firebrands is a game about mech pilots getting into fights and falling in love, but more importantly, it’s a game that guides the group through mini-game-like scenes that are common tropes in various stories. The beginning scene and the end scene are usually pre-determined, but all of the other scenes happen in whatever order you prefer.
The original system has been hacked a number of times, so you might find a game or genre that works for you - perhaps you’d like to play pirates in One Particular Harbour, or gods and heroes in Divine || Mundane. You could play members of a religious order looking for a new leader in Hierophants, or look into the complicated lives of mages in Hearts of Magic. If you don’t find anything that works for your specific tastes that already exists, you could also hack the system to make it fit for your specific group.
Eat the Reich, by Rowan, Rook & Decard.
Eat the Reich is a tabletop roleplaying game in which you, a vampire commando, are coffin-dropped into occupied Paris and must cut a bloody swathe through nazi forces en route to your ultimate goal: drinking all of Adolf Hitler’s blood.
This over-the-top, ultra-violent game is designed to be played from beginning to end in one to three sessions of carnage, blood magic, meaningful flashbacks and hundreds upon hundreds of extremely dead fascists. It tells one story, it tells it loud, and it tells it brilliantly. Think Wolfenstein crossed with Danger 5 and you’re not far off the mark.
Eat the Reich both happens at a very specific point in time - WWII - and also has a mechanic that allows characters to flash-back to various points in their shared backstories in order to play through a high-action sequence while still getting to know the characters. Your vampires have been working together for a long time, and while Eat the Reich is meant to be rather fast, these flashbacks allow you to speed up that relationship-building by letting you fill the details in backwards.
Eat the Reich started out as a hack of Havoc Brigade, if I remember correctly, so the system is definitely hack-able: perhaps you can think of a big event that happened in your party’s past or even in another part of the world, and then design characters that represent folks who were behind the big event. I think this kind of game would work best for heists or high-stakes assassination - anything that expects your players to put their lives on the line for a big, sweet payoff.
Retrocausality, by Weird Age Games.
Retrocausality is a tabletop RPG about time travel adventures, in the vein of Bill & Ted's Excellent Adventure or Back to the Future.
It uses a rules-light, card-based system that lets you decide how time travel works. Whether you have a specific movie you want to emulate, you have Opinions on the Novikov self-consistency principle, or you prefer not to ask too many questions, Retrocausality can make it happen. Even better, the rules are so light you can use Retrocausality to run a time travel adventure in a different game. That's twice as much game.
Many of the examples shown in Retrocausality indicate that the time travellers you play will be messing with a timeline, and since the rules can be ported into a different game, that tells me that you could use this for any genre you like. This of course, means that you’re not just telling a story about your characters’ pasts - your characters are actually going back in time to a specific part of history.
I suppose you could use this to either bring your characters back to a time period before they were born, or maybe instead you’re interested in taking new heroes back to a point in time when your characters were doing something significant off-camera.
Houses of the Sun By Night, by Emily Zhu.
These are 13 houses of the underworld that the sun passes through at night.
These are 13 minigames you can play in specific situations, during your other games or on their own.
This is how the dead come back to life.
This series of games is explicitly designed to be hackable, with a setting that can be ripped apart if you like. The original setting is a nod to the underworld of Egyptian mythology, but the moments themselves can be zoomed in on a small moment or used to navigate a special event that may have big effects on the larger story. I think you can use some of the games in here to re-visit moments of your characters’ pasts, or reference events that may have happened to NPCs that the characters were not necessarily witness to.
If you want to learn more about this set of games, you can watch Aaron Voight’s review of the game on Youtube!
Other Games To Check Out
Feng Shui 2, by Atlas Games.
Time Travel Recommendation Post
111 notes
·
View notes
Text
So i found this beauty in the electronics bin :(

An ACER e300 series travel companion from 2006.
GPS and multimedia player in the shape of a mobile device. it seems to be rare enough that i cant find anything about it, other than the manual.
this thing runs on Windows CE. Basicly just mobile windows that is stripped down to the bare essentials.
I don't have any use for a pocket gps as it doesn't even have a map, but the audio playback is very good for it's size. With the inclusion of an SD card slot and a AUX port. (now that something you cant find on a modern device)
So i thought i'd use it as a ipod of sorts.
The first problem i came across was that this doesn't support anything outside of MP3s and WAV files. as i wanted to pull some videogame audio onto it, witch were Ogg files.
So as the tech lover with a tendency of slipping my fingers into most devices i own (and don't own...). I just had to see if i can update it to support a wider variety of formats. And maybe along the way remove the old interface for a more purpose built one... maybe.
The issues
The software for accessing this thing are obsolete as hell and are no longer supported.
Shes built like a tank and i cant get her open :(
related to number 1. any guide on how to access the software has a "pocket pc" witch this is not...
The goal is to hack this and make it mine :3. maybe make my own splash screen and menu, but essentially make it read more formats.
i'll continue this post ones i get something going.
#objectum#techum#computers#microsoft windows#and for those robot girls reading#i hope you get hacked and made to run someone elses code ;3
19 notes
·
View notes
Text
(So as much as I want to actually write out the events of Project Thunder as ficlets like I did with the Wonder Arc, at this point it's pretty clear that if we want this done this year I'm gonna have to just summarize events. Also, I'll be doing it in sections, each in a different post, so that the tag limit doesn't screw me over.
Project Thunder: Intro
The fleet arrives at the edge of the CCC's system, the physical Firewalls and an army of Twilight and various Brobot models before them. The fleet itself is massive, made up of both the airship-based Codeships and a whole bunch of different ships from different media (mostly Nintendo Properties, of course), as well as Fairy World's military led by Jorgen von Strangle (since Fairies are inherently Codeproof), the Admins (including both our main crew and all the SMG Server Admins we haven't been properly introduced to yet), The Firewall Twins and Supervisors, their other Code-level allies, and any character-levels who can fight at that kind of power (with most needing code stabilizer harnesses and others, namely Ecolo, not) and aren't on one of the infiltration teams.
The Jubilation is also revealed to be a massive space station designed to look like a cupcake with a blue base and pink frosting, and also like a Powerup Mushroom thanks to the frosting section's shape and a pair of "eyes" on the front of the base. While it's the largest ship by a lot, easily Death Star sized, it isn't actually built for direct combat. Instead, it's actually a massive mobile hospital, with nearly all the external weapon systems geared towards defense... and also using cake, confetti, and other party-related foods and supplies as ammunition, because along with Phineas and Ferb, Pinkie Pie also had a hand in its creation and decided to include her own brand of Advanced Partylery in the mix. She's also the ship's captain, because why not. Still, while it's Pinkie's ship, it's Kelsie's House. Pinkie and her crew are in charge if keeping the Jubilation safe and functional, while Kelsie is the one in charge of the massive number of doctors, field medics and the like who staff the place, and it's their job to keep the rest of the fleet safe and functioning to the best of their ability.
On the other side we have the mentioned army of mooks, as mentioned, but also every Code-Level Program the CCC has access to shows up when the alert is sounded... except for Comedy and Tragedy, who were tasked by Mr. L with guarding the Purchase Keys in case of a potential rescue attempt, because he is by far the best villain in the AU at understanding when celebrating a victory would be premature.
Anyway, Peach hails Jayin (via Zoom Call because of course) for a shot at actually negotiating for their friends' release (and potentially having the three dangerous criminals she's harboring be transferred to Alliance Custody, but that one's open for discussion, hence why it's a negotiation and not an ultimatum). Jayin, of course, sees absolutely no value in giving the demands of some video game character, especially Princess Peach of all things, and no reason to hand over her intellectual property. She even points out that she can just take legal action against Glitch Productions and the Grid for hacking into her company like this... except Peach corrects her, pointing out that to do that she'd have to explain how it was even possible, and either the world won't believe her and she'll be seen as a nutcase, or they will believe her, the Digital Multiverse will be revealed, and in the process she'll end up airing all her dirty laundry for everyone to see. She can either lose her games (because even if the fleet falls there will still be others who will rise up. It's not a matter of if the CCC loses, it's a matter of when) or lose her reputation (the one thing that matters most to her). There is no version of this where she wins.
Obviously Jayin doesn't take this well, hanging up on Peach and ordering her forces to attack, and the battle is on.
#project thunder au#meme alliance#the grid#brobot#jorgen von strangle#pinkie pie#kelsie#princess peach#jayin
4 notes
·
View notes
Text
How Fast Can You Increase Organic Traffic? (The SEO Secrets No One Talks About)

Meet Alex, a small business owner who creates and sells handmade leather goods. It was a beautiful website but no sales. He used to eagerly check his website analytics every single day, hoping to see an uptick in organic traffic, only to find little movement in the numbers. Alex was frustrated and desperate, thinking about splurging on expensive ads, but his ad budget was all spent.
After a night of searching for affordable SEO, he came across a digital marketing agency — Brand Brighten. But, dubious yet curious about their budget-friendly SEO method, Alex opted to roll the dice. What happened next, however, changed his business forever.
The Harsh Reality: SEO Takes Time, But Strategy Can Speed It Up
“SEO is a long-term game,” say SEO experts. This is true, but you can speed up organic traffic growth — if you know how. Most businesses suffer because they stick to old plays or fall for myths that slow them down.
Alex thought, in the beginning, it takes years of hard work to get high on Google. Instead, Brand Brighten has proven to him that you could make the changes to your life that would have, previously, taken over a decade in a couple of months, just by executing a plan well. So what did he do differently?
The Hidden SEO Secrets That No One Talks About
1. Manual Website Audit: The Foundation of Success
Before we implemented any major changes, we manually audited Alex’s website. This revealed some major issues like page loading time, broken links, and missing meta descriptions. Most businesses will overlook this process, but a proper audit can highlight areas of weakness that should be addressed immediately.
2. Keyword Research Beyond Search Volume
Alex was going after generic, high-volume keywords such as “handmade leather wallets.” Brand Brighten found him find long-tail keywords like “best handmade leather wallets under $50,” which had far less competition, but higher conversion.
3. Technical SEO: The Silent Traffic Booster
Backend, being a very vast technical aspect of a website directly influences organic rankings at great depth. Optimizing Alex’s site speed, fixing crawl errors and mobile-friendliness took just a few weeks, and his site���s organic visibility skyrocketed 40% in that short span.
4. Google My Business (GMB) Optimization
Since Alex had a physical address, it allowed him to show up in local searches via Google My Business. Smaller details like updating images, responding to reviews, and adding keywords in his GMB profile also did wonders.
5. Strategic Off-Page SEO: It’s Not Just About Backlinks
Rather than spam hundreds of poor-quality backlinks, Brand Brighten invested in high-authority guest posts, local business citations, and niche directory listings. In terms of link-building, quality will always trump quantity.
6. Content That Solves Problems, Not Just Sells
Rather than only push his products, Alex began to blog with answers to customer questions, like:
“How to Care for a Leather Wallet”
5 Top Mistakes to Avoid in Buying Handmade Leather Goods
This strategy established his brand as a leader, sparking improved organic visitors and consumer trust.
7. Social Media SEO: The Underrated Traffic Magnet
Many businesses handle social media and SEO as two separate things, however they work in close proximity. Then came the magic — Alex used SEO-optimized captions, hashtags, and engagement hacks to attract traffic from Instagram and Pinterest to his website.

The Results: A 250% Increase in Organic Traffic in 3 Months
These SEO strategies helped Alex increase his website traffic by 250% within three months. His Google rankings improved and his sales skyrocketed without spending thousands to ads.
His story shows that with the right approach to SEO, organic traffic growth can happen quicker than you’d think, even on a budget.
How You Can Apply These Strategies Today
If low organic traffic is an issue for you, this is what you can do:
✅ Perform a manual website audit to discover and resolve severe problems.
✅ Search for highly specific long-tail keywords instead of trying to rank on super broad keywords.
✅ Set up technical SEO best practices, including speed, mobile friendliness and indexing.
✅ Register your Google My Business profile and optimize it for local searches
✅ No instead of quantity backlinks, take care of quality backlinks.
✅ Produce content that will help users with their problems
✅ Use social media SEO to increase organic reach.
Take the Next Step: Get a Free SEO Audit Today
Want to see how fast you can increase your website’s organic traffic? Brand Brighten offers a free, no-obligation SEO audit to identify opportunities specific to your business.
📩 Contact us at [email protected] or visit Brand Brighten for expert SEO solutions.
🚀 Don’t wait months or years — start growing your traffic today!
See How Emma Grew Her Business with Brand Brighten
🤔 𝐖𝐡𝐲 𝐈 𝐓𝐫𝐮𝐬𝐭 𝐁𝐫𝐚𝐧𝐝 𝐁𝐫𝐢𝐠𝐡𝐭𝐞𝐧 𝐟𝐨𝐫 𝐒𝐄𝐎 — 𝐍𝐨 𝐌𝐨𝐫𝐞 𝐆𝐮𝐞𝐬𝐬𝐰𝐨𝐫𝐤! ✅
Emmma Sartwell founded Somatic Spiritual Counseling along with serving as its CEO when she partnered with Brand Brighten to advance her website operations. 🌟
Frequently Asked Questions (FAQs)
1. How long does it take to see results from SEO?
SEO is a long-term effort; however, with the correct strategies you can notice significant improvement in 3 to 6 months. The time required is influenced by such as competition, keyword difficulty, and website health.
2. What is the fastest way to increase organic traffic?
Technical SEO improvements, optimizing Google My Business, long-tail keywords, and high-quality content are among the fastest ways to boost your ranking. Starting with a manual website audit is a good place to start.
3. Does social media impact SEO rankings?
Social media has nothing to do with your rankings, but it helps to send traffic, boost engagement, and promote your brand — everything that eventually affects your SEO performance.
4. Are backlinks still important in 2025?
Yes! And authoritative and relevant backlinks are still one of the main-ranking factors. Instead, concentrate your efforts on link earning via guest blogging, PR and other industry partnerships.
5. Can I do SEO on a low budget?
Absolutely! You could determine which things not for the kind of thing by starting free tools such as Google Search Console tools, Google Analytics, and listen to them, improve existing content, and local SEO. Their e-commerce platform also provides affordable SEO packages to allow businesses to develop.
Conclusion: SEO Is Evolving, But Opportunities Are Endless
SEO is not a set-and-forget exercise, it’s a continual practice. But with smart strategies, staying ahead of trends, and working with experts like Brand Brighten, businesses can achieve accelerated organic traffic growth as well as sustainable, long-term success.
Ready to dominate search rankings? Take action today and watch your business thrive!
#SEOExperts#BrandGrowth#SEOResults#GoogleRankings#WebsiteTraffic#MarketingStrategy#BusinessSuccess#EntrepreneurLife#SEOBoost
2 notes
·
View notes
Text
S.P.E.C.I.A.L. STATS - REVAMPED
I did a Fallout 4 version of these a while back, so now it's time for the Fallout: New Vegas version.
STRENGTH - Strength governs how much weight players can carry as well as how effective melee attacks will be. I put it at a 1 in the other version not because I think Norm is especially fragile due to being short, but because I had a lot less points to work with and they were needed elsewhere. I can see him at about a 3, probably no higher than that.
PERCEPTION - Perception covers the skills of Explosives, Lockpick, and Energy Weapons (i.e. laser/plasma pistols/rifles) and determines the range that red compass markings show up on the HUD to indicate enemy threats. I don't think we've seen any conclusive evidence that Norm possesses these particular skills yet, but his Perception is quite high by default.
ENDURANCE - Endurance is a measure of overall physical fitness, providing bonuses to the total number of Health Points, Environmental Resistance, and the Survival and Unarmed skills.
CHARISMA - High Charisma will increase the base disposition of other characters, and governs the Barter and Speech skills. I know this is something of an unpopular opinion since the fanon consensus is that Norm has absolute minimal charisma, but I think he has more than most people will give him credit for. It’s just that instead of using his charisma to de-escalate or persuade people non-violently the way his sister makes an effort to, Norm uses his to say things that can upset people. He pushes their boundaries and tests how they react and exploits weaknesses in their logic or authority. He'd be more likely to take the option to lie or intimidate someone with his intelligence.
INTELLIGENCE - Intelligence is tied to the Science, Repair, and Medicine skills. Being the son of Rose and Hank MacLean, it's no surprise that Norm definitely makes frequent use of the Science skill, easily hacking the Overseer's terminal in Vault 32 and then Betty's in 33. Following after his Tagged Skills, Repair and Medicine come in around the 4th and 5th highest.
AGILITY - Agility affects the Guns and Sneak skills, as well as the number of Action Points (AP) available in V.A.T.S. I am hesitant to accept everything about Norm's build in the mobile game as canon, but I do kind of like that he carries a tranq gun by default. He would probably be forced to ditch it much sooner than Lucy did and upgrade to something more capable, but I like the idea that like his sister, his first instinct when the matter is put in his hands could be to incapacitate, not kill unless absolutely necessary and unavoidable. When it comes to Sneak, we see plenty of evidence that this is one of his stronger skills.
LUCK - High luck increases all skills slightly and improves the chance of scoring a critical hit with all weapons. I don't have much to contribute for this one other than giving Norm a small boost on the skills he's already good at.
STRENGTH: 3
PERCEPTION: 8
ENDURANCE: 4
CHARISMA: 4
INTELLIGENCE: 9
AGILITY: 6 (+1)
LUCK: 6
SKILLS
Barter - 13
Energy Weapons - 21
Explosives - 21
Guns - 19
Lockpick - 36
Medicine - 23
Melee - 11
Repair - 23
Science - 38
Sneak - 34
Speech - 13
Survival - 13
Unarmed - 13
Tagged Skills: Lockpick, Science, Sneak (Basically the way I play every RPG. Don't like to be locked out of shit.)
PERKS
Swift Learner - You gain an additional 10% whenever experience points are earned.
Friend of the Night - Your eyes adapt quickly to low-light conditions.
TRAITS
Small Frame - Due to your small size, you have +1 AGI, but your limbs are more easily crippled. (25% extra limb damage)
2 notes
·
View notes
Text
Piers Morgan will find many ways to deny phone hacking – but how long before his number is up?
Archie Bland
Following a judge’s ruling in favour of Prince Harry, the former Daily Mirror editor’s confected outrage is starting to look a little desperate
Mon 18 Dec 2023 14.15 GMT
So how much, exactly, did Piers Morgan know about phone hacking when he was editor of the Daily Mirror? It depends when you ask him. And since he edited the newspaper for nine years when hacking was at its zenith, and since other people similarly accused have spent time in prison, this seems important for reasons that do not depend on your feelings about Prince Harry.
On Friday, for example, Morgan had a simple line for reporters gathered outside his house. Perhaps his thinking had been clarified by the unfortunate news that a judge ruling on claims from Harry and others had found that there had been extensive hacking going on at the Daily Mirror, and that there was no doubt Morgan knew about it. Similar evidence has been presented to the Leveson inquiry and in previous litigation, but never as extensively or with such a powerful endorsement from a judge as this. But it’s all nonsense, Morgan sputtered, who would do such a thing? “I’ve never hacked a phone, or told anybody else to hack a phone,” he said. Simple.
As he also said, this is a line he’s maintained for a long time. You would be amazed at how carefully he has maintained it. He used exactly the same words to the BBC in September. He used exactly the same words to the BBC in May. He used exactly the same words on Twitter (now X) in 2015. He used exactly the same words to the Guardian in 2014. He used exactly the same words on CNN in 2011. Ask Piers Morgan what his favourite biscuit is at any point in the last 15 years and the response is likely to have been that he never hacked a phone, and he never told anyone else to, either.
If you view the narrow precision of Morgan’s repetition as interesting, you will probably go looking for other things he’s said about phone hacking. And you will find a laundry list of public statements from a bygone era that don’t exactly contradict his later recitations, but do cast them in a different light. In 2003, he told Charlotte Church that she should change the security number on her phone to stop reporters from accessing her voicemails. In 2006, he wrote that he had been “played a tape of a message Paul [McCartney] had left for Heather [Mills] on her mobile phone”. In 2007, he told Press Gazette that hacking was “an investigative practice that everyone knows was going on”.
What are we to make of this change of emphasis? If we take him at his word, we will have to conclude that Morgan knew absolutely loads about phone hacking, but had absolutely nothing to do with commissioning it. You might wonder if there was any need to tell the voicemail interception specialists used by the Mirror to hack a phone, and reflect that when you get the plumber round because your sink is blocked, you don’t need to encourage them to bring a plunger.

Alastair Campbell at Hay festival, Hay on Wye, UK, May 2018
‘Alastair Campbell gave ‘compelling evidence’ pointing to illegal techniques being used by the Mirror’s agents to obtain details of his mortgage.’ Photograph: Steven May/Alamy
The thing is, Mr Justice Fancourt didn’t take him at his word, and went to great lengths to explain why.
In rejecting the judge’s 386-page ruling, Morgan dwelled on the evidence of Omid Scobie, who was once an intern at the Mirror. Scobie said that he had heard Morgan being told that a story about Kylie Minogue was sourced from a voicemail. Morgan said Scobie was a “deluded fantasist”. As for Alastair Campbell, who, according to the judge, gave “compelling evidence” pointing to illegal techniques being used by the Mirror’s agents to obtain details of his mortgage: he is “another proven liar who spun this country into an illegal war”.
Now, you might not trust Scobie or Campbell. But what Morgan left out is that Scobie’s story fits precisely with invoices, numbers on a Mirror reporter’s phone, and a matching article about Minogue bylined to someone the judge described as “a known phone hacker”. Campbell’s claims, meanwhile, are lent considerable weight by the fact that the Mirror had just used the same private investigators to do exactly the same thing to Peter Mandelson. The corroboration for Morgan’s claim of innocence, on the other hand, is simply that he keeps making it.
Set Scobie and Campbell aside, if you think they have sold the judge a pup. Perhaps because it was cold outside, Morgan didn’t find time in his doorstep speech to critique the rest of the evidence cited in the judgment.
Melanie Cantor, an agent and publicist, said that Morgan “always seemed to be the first person to know about events that had recently happened” involving her clients, and that invoices and phone records demonstrated that she had been repeatedly hacked by the Mirror’s reporters. The judge concluded that “sensitive information … was passed to Mr Morgan, who must have known how it had been obtained”.
Benjamin Wegg-Prosser, the head of strategic communications at Downing Street under Tony Blair, said that Morgan had explained to him how hacking had been used to get a story about Ulrika Jonsson’s affair with Sven-Göran Eriksson. And David Seymour, the Mirror’s political editor, said that he had watched Morgan playing that McCartney voicemail to a group of reporters. Morgan, he added, was “unreliable and boastful [and] apt to tell untruths when it suited him”. The judge said he accepted Seymour’s evidence “without hesitation”.
Those are just the human sources. The judge also drew on mountains of invoices, emails and phone records. Still, Morgan had another card to play, another that he turns to quite a lot: an enthusiastic swing at the motivations of Prince Harry, who he said was on a mission with his wife, Meghan, to “destroy the British monarchy”.
If that is the purpose of Harry’s exhaustive legal crusade against the Mirror, the Daily Mail, and the Sun, it seems an odd way of going about it. But hacking has never just been about Harry. Even on Friday, there were three other claimants. The wider litigation involved more than 100 others.
Hacking was certainly not just about Morgan, either. But his confected outrage as the evidence against him mounts does give a sense of how we can expect the story to continue from here.
The financial consequences are instructive, too. Harry won £141,000 in damages; another claimant won £32,000; another two didn’t get a penny, because their claims were made too late. Morgan will not have to pay any of it. Meanwhile, he is under contract at Rupert Murdoch’s TalkTV and the Sun, on a deal reportedly worth about £50m. Both outlets would have had ample evidence to suggest his involvement in hacking before this case even began, and neither has shown any signs of abandoning their man, who never hacked a phone, and never told anyone else to.
Archie Bland is the editor of the Guardian’s First Edition newsletter, and writes on media, culture and technology
Following a judge’s ruling in favour of Prince Harry, the former Daily Mirror editor’s confected outrage is starting to look a little desperate
-
starting to?
8 notes
·
View notes
Note
What are you favorite Eggman mechs? Like the Death Egg Robo, for example :3
This will be a rapid fire one, because with the sheer number that come to mind, and the urge to resist listing every single one of them, even the laughable ones like Egg Dealer (I'm a diehard Eggfan, what do you expect?), I'd be here all day if I went into extensive detail for each of them, and it would also be pointless because most of them amount to "it cool :3". This will include mechs piloted by other characters that were nonetheless very likely to have been made by the good doctor.
Egg Pistons - For the first final boss in the series, the idea is very creative despite its simplicity. I like the concept of the room itself being the danger, an idea that's shared by the final bosses of Sonic 1 and 2 on the MS/GG.
Catcher Eggman - I like how neon it is, and it's a surprisingly tricky boss for so early on in Sonic 2. Not super tricky granted, but moreso than any other up until Metropolis.
Brass Eggman - He's good with the instruments. My favourite part is when Eggman starts playing tennis with Sonic and then transforms into a giant boar monster.
Death Egg Robot - It's a classic for a reason. I'm so happy its iteration in the second movie was as faithful as it was. And of course, I love all of the spiritual successors that we've seen over the course of the series. The Super Egg Robo in Advance 1, the Super Egg Robo Z in Advance 2, the Eggrobo in Lost World, Black Eggman/Metal Robotnik in the OVA...
Screw Mobile - Bouncing off the water gushers to hit him is fun.
Drill Mobile - Why do people say Marble Garden is forgettable when it has a highlight moment for Tails?
Big Arm - This is one of the Egg Mobile attachments that everyone loves, and rightly so. It's so simple, yet so badass.
Hang Mobile - Gee S3&K, how come SEGA gave you TWO bosses that resemble a penis?
Egg Golem (S3&K) - I like it when Eggman incorporates his tech into natural structures or ancient monuments and weaponizes them. It's a nice spin on his usual schtick, and it's for similar reasons that I like the SA2 Egg Golem, as well as the Rusty Ruin boss from 3D Blast.
Hot Mobile - It looks cool, and the lead-up to it is one of S3&K's many iconic moments. Shame the boss itself amounts to waiting for it to unalive itself.
Great Eggman Robo and the Final Weapon - They both contribute to why S3&K has one of the best finales in the series.
Speed Slider Boss - The boss itself is perhaps not very good (the bosses in Chaotix are not what I'd call a tour de force), but a carousel-themed boss is delightful and on-point for Eggman's character, so whatever.
E-Mech - tfw it's only pathetically easy because if it had access to the moves you can use when you hack Fighters to play as him, you would stand no chance against him. He was too OP for his own good. A testament to his genius.
Egg Viper - The design is top class. The fight is top class. The meme is top class. But my favourite part of the whole thing is the sui-dive at the end, and how the music goes completely silent from the moment you land the last hit, all the way until it finally crashes into the pit in a glorious inferno. Would a half-hearted villain have gotten such a cool not-death scene? I think not.
Egg Walker (SA1) - "You fool. Away... before I make suggestive art of the new character in less than 24 hours after they were revealed."
Egg Walker (SA2) - Yeah, it's weird how he doesn't use any other mechs in the whole game when you put the gameplay justification aside, but as a portable version of the aforementioned walker, it's just as effective as its bigger brother, and packed equally to the brim.
Egg Spider - One of the trickier water zone bosses in the series... unless you're playing as certain characters I guess.
Egg Hammertank II - As Advance 2 was my first Sonic game, this was my first Eggman boss, so there's a nostalgic soft spot present for it.
Egg Bomber - It's Eggman in a tank. That's it, that's the reason.
Egg Totem - This has always been one of my favourite bosses in Advance 2 due to the balancing act you have to pull for it, and it caps off the already excellent Music Plant.
Egg Saucer - I love it when the fandom suffers for its sins. Even if that includes me.
Egg Shrimp - "Don't worry lads, there's a very important reason why I'm building this." *captures little kid's mother just to spite them*
Egg Emperor - Another instant badass. Metal Sonic may have been the one piloting it, but he wouldn't have used it for his ruse cruise if it wasn't Eggmanny, and it probably was the real Eggman who piloted it in Generations 3DS, so there.
Egg Mobile (Battle) - I don't know if this counts since it's just the Egg Mobile on its lonesome with red armor. But it's a boss, so I guess that's all that's required. He only has two attacks, yet he's still one of the harder opponents in the whole game regardless, and it's followed shortly after by him driving Emerl insane and forcing Sonic to Old Yeller him. Well done, Ivo, that's the kind of wholesome content I'm sure the fandom has in mind when they talk about you.
The Advance 3 bosses in general - Just for how hilariously checked out G-Merl looks when he's crammed into random places on said mechs. Special mention for the Egg Cube in Toy Kingdom for being a unique ring out boss.
Egg Breaker - This is basically just Egg Emperor Jr. (even has the same face lol), but it's still cool with its morning star arm and its YOU KNOW WHAT THEY SAY, THE MORE THE MERRIER, YOU KNOW WHAT THEY SAY, THE MORE THE MERRIER, YOU KNOW WHAT THEY SAY- I know this only happens in the Mad Matrix version, don't ruin the joke
Egg King - Running on the mech itself, even if only briefly, is the hypest shit.
Egg Salamander - The one with the funny song about coffee.
Ghost Titan - Whisker was the pilot, but he himself is an Eggman robot, so... I just enjoy how chunky and tank-like it is for something that can float.
Egg Wizard - This is one of the most underrated final Eggman mechs, and one of the most underrated final bosses in the series period. Its design sets itself apart from others in the doctor's catalogue, as do the magic-based attacks gifted by its theft of the Jeweled Scepter. Only downside is that Nega's there.
Egg Dragoon - You knew this one was coming. Iconic design, iconic battle, better than Dark Gaia and its ridiculous number of back-to-back QTEs without question. Then it returned in Generations with some Egg-Wyvern wings and a nice Egg Viper tail. Good stuff.
Nega-Wisp Armor - Eggman finally got to be the true final boss of a 3D game. Only took over a decade. Bowser never had to wait that long. The fight itself, while easy, is still memorable with how he uses the Wisps' abilities against you. Even the announcer is on his side.
Time Eater - He finally got one of them under his control, and gave it a sick clockwork aesthetic. I will always sing the praises for this achievement, especially when later material has regressed back to square one for no good reason. I like to imagine that its jittery movements is the creature itself trying and failing to fight back against Eggman's control. Gives the whole thing an extra layer of cruelty, and remains consistent with the doctor's modus operandi of shoving sentient beings in steel coffins when they never asked for it.
Weather Mobile - The gimmick is both fun and funny. As is the infamous buzzing at the end.
Gachapandora - Gotta catch 'em all.
Phantom Egg - Despite looking like a ronper suit, the fight itself and how it incorporates the non-King Heavies makes it a winner. And the music, obviously.
Klepto Mobile - How is a hastily cobbled together piece of shit able to keep up with Phantom King to a standstill? Because that's the magic of Eggman when he's used properly.
Mega Death Egg Robot - Storing a second mech inside the first one is the most Eggman thing ever, and a final example of how cunning he was throughout all of Forces.
Bridge Island Boss - It's already a good spin on the Death Egg Robot archetype, but then it summons the Big Arm claws. It's still the first boss when all is said and done, but it's one of the best first bosses, and considering how the later bosses in Superstars have gained a reputation for being challenging, starting off with something like this is some good foreshadowing.
Sky Temple Boss - The Wacky Workbench boss, but actually a threat for reasons beyond forgetting which platforms you shouldn't bother with.
Egg Diablo - What do you get when you cross a villain that takes pride in his evil, and a fandom that insists on making him a good father and demanding he retire from villainy altogether? I'll tell you what you get: you get what you fuckin' deserve. The shogun influence is interesting, kind of like the classic equivalent of the Egg Emperor's knight motif. And I like the rewind gimmick, which I'm still convinced is a reference to the unused Final Fever from Taxman CD. (Seeing how the Black Dragon was likely inspired by the unused dragon boss concept in S3&K, it doesn't seem too farfetched.)
Fang's Mech - Yes, Fang has an engineering side, but it's got Metal Sonic eyes, he was already working for Eggman in this game, and there's no way he could have given players a concussion without some assistance from the man who gave us the Egg Diablo.
6 notes
·
View notes
Text
Thess vs Renovations
No, not the ones my stepfather's doing.
...Well. Not only the ones my stepfather's doing.
We're hacking away at the typing queue and while we're getting the numbers down somewhat, we've got a long row to hoe on this one. It doesn't help that some of the doctors are ... just ... I mean... I think it's that they're expected to get through a whole metric fucktonne of reports and they rush and kind of screw up the dictation. I mean, on top of the regular crop of Undesirables, I got:
The guy best known for the massively long atrocities outdid himself today - managed to cut out a whole section of dictation in such a way that it could technically be a valid sentence unless you're actually looking at what your typing and going, "Wait ... no, that's not right", seems to have left out some of his usual detail on one of the bits of block key, and referenced a piece of specimen that doesn't actually exist (he sited slice 20; the specimen was cut into 13 slices). So I had to type that, work out where the errors were, bold them, print-to-PDF the messed-up report and send it to him so he could review it properly. Because going into the report directly to view and even change it never crosses this man's radar as a possibility.
A relatively new one ... I don't know how she did it, but she managed to record a piece of the block key before the rest of the dictation. This led me to thinking she'd just neglected to dictate it, but no, turns out it just ... was like that.
Then there's the one who's usually fairly good but occasionally has a habit of dictating multiple cases on one dictation file. This is a no-no, by the way. Especially when the cases are on two entirely separate systems, one of which I CANNOT ACCESS. I tried typing the one that I could, adding a comment giving the exact time stamp of where the one for the other system started, and then dumping it into their queue ... but they dumped it back into our queue and since I can't access their system, I don't know whether they typed it and sent it back or just didn't read the comment and thought someone else fucked up. I left an email with Scruffman about that one; he can deal with that shit tomorrow.
And then, among all this ... well. A few weeks ago, I got a little note stuffed into my mailbox. This note was from the guy who lives one floor above me, saying, "Hey, I'm doing some renovations on my flat; it shouldn't be too noisy except for just this one day when we're ripping tile out of the bathroom. Sorry for the inconvenience". The renovations started on 30th October, and probably won't be done any time immediately soon. Which is unfortunate, because today was about two hours of power drill, directly above my head. This made the wall vibrate and also made an ungodly amount of noise. So much for 'just this one day'. I'm pretty sure I'm developing a migraine.
But was that the end of it? Nope. I'm bashing away at the typing when my mobile rings. It's my stepdad, asking if he can pop in to look at the fuse box for a minute. Of course, he hasn't thought to bring his copy of the keys to this flat, so I'm going to have to let him in. Which means a knock on the door, which I will probably have trouble hearing between my helps-me-focus music, the dictation I'm listening to, and the power drilling. So he says he'll be there in ten minutes so I get a few bits of dictation done and then turn off the stereo with maybe a minute or two to spare. No knock. Time passes. I'm afraid to start the typing back up in case I miss the door. Apparently, "ten minutes or so" for my stepfather means twenty minutes. Also, "can I look at the fuse box for a minute?" is "can I bring an electrician in here to poke around at things for about fifteen minutes?" During which I was obviously loath to just leave them to it because a) I want to hear what's going to get done, b) I'm worried that he'll have to poke something and shut off the power, and I don't want to be mid-dictation when that happens, and c) I have to shut and lock the door behind them when they leave. I still don't know what that was in aid of but apparently there's going to be some electrical work in here, and I don't know when.
(He thanked me for the cookies and complimented them highly, though. So that was nice.)
My head hurts. My everything hurts. And I still have to go and take out the trash. But at least I can tell myself "one more day and I get a week off". Most of which I will probably spend in bed, or on the sofa, not doing a fucking thing. I need to recover and I have had zero chance to do that lately. Just ... today was apparently designed to be as inconvenient to me as possible. Yaaaaaaaay.
2 notes
·
View notes
Text
How to Recover If Your Facebook Account Is Hacked? Easy Steps
In today's digital age, social media platforms like Facebook have become an integral part of our lives. We use them to connect with friends and family, share our thoughts and experiences, and even conduct business. However, the convenience of social media also comes with security risks, and one of the most common problems users face is having their Facebook account hacked. If you find yourself in this unfortunate situation, it's essential to act quickly to recover your account and secure your personal information.
In this comprehensive guide, we'll walk you through the steps to recover your hacked Facebook account, protect your data, and prevent future breaches.
1. Recognize the Signs of a Hacked Facebook Account
The first step in recovering your hacked Facebook account is to recognize the signs of a compromise. Common indications include:
Unauthorized login notifications: Facebook sends notifications when someone logs into your account from an unfamiliar device or location.
Unusual activity: Strange posts, messages, or friend requests that you didn't initiate.
Changed password or email address: If you can't log in because your password or email address has been changed without your consent, it's a strong indicator of hacking.
Locked out of your account: If you're unable to access your account due to suspicious activity, your account may have been compromised.
2. Immediate Actions to Take
Upon suspecting or confirming a hack, take the following immediate actions:
Change your password: If you can still access your account, change your password immediately. Make it strong by using a combination of upper and lower-case letters, numbers, and symbols.
Log out of other devices: Go to Facebook's Security Settings and log out of all devices to prevent the hacker from continuing to access your account.
Enable two-factor authentication (2FA): Set up 2FA to add an extra layer of security. This usually involves receiving a code on your mobile device that you'll need to enter when logging in.
Check your email account: Ensure that your email account associated with Facebook is secure. Change its password and enable 2FA if you haven't already.
3. Report the Hacked Account to Facebook
To report your hacked account to Facebook, follow these steps:
Go to the Facebook Help Center.
Navigate to the "Security and Login" section.
Click on "I think my account was hacked or someone is using it without my permission."
Follow the on-screen instructions to secure your account and recover it.
4. Recovering Your Hacked Account
Facebook provides a dedicated recovery process for hacked accounts. Follow these steps to recover your account:
Visit the Facebook Account Recovery page.
Enter your email address, phone number, or Facebook username associated with your account.
Follow the instructions to verify your identity. You may be asked to provide a photo ID or answer security questions.
Facebook will guide you through the account recovery process, allowing you to reset your password and secure your account.
5. Check for Unauthorized Activity
Once you regain access to your account, review your activity log for any unauthorized actions, such as posts, messages, or friend requests. Remove any malicious content and unfriend or block suspicious accounts.
6. Strengthen Your Account Security
To prevent future hacks and secure your Facebook account:
Regularly update your password: Change your password at least every six months, and use a unique combination of characters for each platform.
Enable two-factor authentication (2FA): Ensure that 2FA is enabled to provide an extra layer of protection.
Review app permissions: Periodically check which apps have access to your Facebook account and remove any unnecessary ones.
Be cautious with emails and messages: Avoid clicking on suspicious links or providing personal information in response to unsolicited messages.
Educate yourself: Stay informed about common hacking techniques and scams to protect yourself better.
6. Monitor Your Account
Continuously monitor your Facebook account for any unusual activity. Facebook offers features like login alerts, which notify you of any login attempts from unrecognized devices or locations. Stay vigilant and report any suspicious activity promptly.
7. Protect Your Personal Information
Remember that hackers target personal information. Limit the amount of personal data you share on your profile, such as your phone number, address, and birthdate. Adjust your privacy settings to control who can see your posts and personal information.
Conclusion
Recovering a hacked Facebook account can be a stressful experience, but by taking swift and informed action, you can regain control of your profile and protect your data. Follow the steps outlined in this comprehensive guide, and remember to prioritize account security by regularly updating your password, enabling two-factor authentication, and staying vigilant against potential threats. With these precautions in place, you can enjoy the benefits of social media while keeping your personal information safe from hackers.
For More Information - https://www.linkedin.com/pulse/how-recover-your-facebook-account-hacked-neha-kumari
More Articles -
2 notes
·
View notes
Note
AHH Lena ive got a problem!! so i think my blog got hacked into???? but theres nothing diffrent/changed so im not sure but it i was looking at stuff and it says i was "active" at some place ive never been to? but the thing is that weekend i had traveled and somewhat close (like to the neighboring state but it was on the other side away from me) and im not sure if it could just be a glitch? but im still quite worried. i mean i just changed my password but it says it was active recently and i dont know what to do and i dont want to delete my blog (its super small anyways so it wouldnt matter tho)
Don’t panic friend! I’ve got some ideas for you based on some research I’ve done.
(Also apologies for any typos, i’m typing this out on mobile in a waiting room lol)
So, i hadn’t heard of this “active sessions” section of Tumblr before, but quickly found it on the web version under account settings. According to Tumblr’s FAQs, this shows any log ins/access sessions to your Tumblr account by browser, and includes location info, to help you keep your account secure.
Looking at mine, I recognized various devices I’ve used over the past several months, with the locations as my home town. Two logs stood out to me though. 1 - my current session (marked as “current” in green) says my location is in a different part of the state. Odd, but could be due to having a new phone? 2 - apparently a session back in April came from a completely different state. Very odd right?
If i’d come across this back in April, i probably would’ve freaked out like you anon. But the fact it happened 3 months ago (and i haven’t noticed any unusual activity on my account), i couldn’t help but wonder how accurate these locations are…
Hence a research rabbit hole about IP addresses. You’ll notice underneath the city/state display is a string of numbers. This is the IP address of the browser’s network connection. There are several free websites where you can search that IP address and get a much more accurate location… Apparently, IP addresses may not always be accurate due to the geolocation databases they run through. So at the time of that connection, my location was displaying as one place when I was really somewhere else. But when I search that IP address now, it shows my current and accurate location.
I’ve also experienced odd location issues in other areas… like when I access Netflix from a new device and it sends a confirmation email, it usually has the city wrong.
So… this is what I did to look into the odd location activity on my account and i’m comfortable saying it was a IP address geolocation error. It’s possible that’s what you’re seeing on your account too.
If not… next step i would recommend is to double check the email address you have on the account. If someone actually hacked your account, that would be one of the first things they’d change in order to keep access. Really look at the address because sometimes they’ll try to throw you off by making a similar email but with like an added dot, or an extra letter that you wouldn’t catch at first glance. You can change it back to your own address in addition to changing your password.
Those are my two main ideas. I’m not an expert in these things but that’s where i would start, especially if you’re not seeing any suspicious activity on your account. Anyone else with ideas or experience here, feel free to chime in!
2 notes
·
View notes
Note
gundam themed/similar games?
THEME: Gundam
Hello friend! This actually made me go back into my previous game recs and realize that I hadn’t properly tagged my Mechs Part 1 and Part 2 recs - so now you should be able to find them! Out of the games listed there, I’d definitely recommend Disaster/Wing by A Couple of Drakes, Mobile Zero Firebrands,by Lumpley Games, and Apocalypse Frame by Binary Star Games.
Now, let’s see what else we can rustle up.





Last Sentinels, by Jason Price.
The people of AUGUR-V had been cast into the stars, pursued by the vengeful forces of the New Alliance. But one Sentinel pilot still offered them hope. This is their story.
Last Sentinels is a GM-less storytelling tabletop roleplaying game for 3 or 4 players. It focuses on one main protagonist, a gifted young civilian who escapes the besieged planet of AUGUR-V on a titanic starship with their remaining people. They must defend these survivors against overwhelming odds as a vast fleet pursues the ship through their former empire.
But your protagonist is doomed.
Their story will end in death or betrayal when they succumb to the intense pressures of hope, despair, scheming foes and high-stakes mech combat.
Last Sentinels is more focused on the structure of the narrative than it is on the fights between mechs. Because the game is GM-less, the story becomes a negotiation, with the responsibilities of the players depending on where they sit at the table. Another thing unique about this game is the fact that no one player is responsible for any one character. This is because this is a story with one protagonist - similar to Amuro Rey from the original series. The game isn’t meant to tell a happy story - this is a game with a tragic ending. If you want a game that treats the subject matter of war with the same gravity as Mobile Suit Gundam, this is the game for you.
IGNOBLECORPS: Pilots of Command, by Declan Lowthian.
Hello Pilot You are about to embark on your first mission for the glory of Command. We have faith that your training will not fail you, and that you in turn will not fail us. You have your mission. Ready for launch.
IGNOBLECORPS is a game about desperate mech pilots working within a titanic organization spanning the galaxy. Fight for and against Command's control and try to get out alive.
This is a hack of a game called NOBLECORE, a game about metal space fantasy with legendary heroes. This system uses exploding dice pools, which means that when you roll the highest number on any given dice, you get to re-roll for a chance at more success! This is also a collaborative game, so it expects all of the players at the table to generate the galaxy around you, rather than providing you with chapters and chapters of lore. This game reminds me of Gundam because it expects combat to be brutal and desperate - even if the moves are flashy, the war behind them is gritty and dark.
Armored Battle Frame, by Mundos Infinitos.
The WORLD is in a WAR fought with MECHAS. You are a PILOT, shaped to fight, witness to atrocities, bearer of wounds, a tool for victory. This is the story of your dreams and ambitions.
As a pamphlet game, expect Armored Battle Frame to be quick to pick up and quick to play. The designer, Benjamin A. Reyna, is very good at fitting a lot of information into a small space. This game can be played with or without a GM, and it can also be played solo! Mobile Suit Gundam is also listed as an inspiration in the game description. The designer also has another Mech game called Real Robot TechaMech: Professional Level, which uses a game system found among a number of Reyna’s games.
Battle Century G: Remastered, by GimmickLabs.
Express your creativity without mechanical restrictions. The game is effects-based, so how you do something does not matter as much as what you do. And what you do is pilot a kickass Mecha, command a badass Battleship, or ride a terrifying Kaiju.
Employ tactics and teamwork to defeat your enemies. Enemies in Battle Century G are powerful, you'll have to adapt on the fly to their weapons and schemes, watch each other's backs with your allies to ensure no one gets shot down, and employ synchronized combination attacks to defeat superbosses.
Explore a solarpunk future. The setting included in this book presents an environmentalist, inclusive and transhumanist society opposing an industrialist empire with the looming threat of kaiju mechabeasts on the horizon. It is inspired by the likes of Turn A Gundam, Nausicaa of the Valley of the Wind, Dune and Sid Meier's Alpha Centauri.
Battle Century G boasts fast-paced combat and big powers that make you feel more than competent. It also includes advice on playing for both GMs and players, in what looks to be an effort to make the game as easy to step into as possible, and the themes and setting information allow for a number of societies that look very different from our own - great for speculative fiction.This is a game that is the result of various playtests and previous editions, so it’s less likely to feel like a quick hack and more likely to feel like a full game.
Maharlika, by makapatag.
MAHARLIKA RPG is a technomystic Science Fantasy mecha RPG inspired by Filipino Mythology, centered around Mekanized Weapons or Meka, and their pilots: the eponymous Maharlika.
You will play as these titular spirit-warriors, mavericks, aces, and knights that all swear loyalty to a Datu, one of the CEOs of the Megacorporations, so that you can protect the technospiritual galaxy of Arkipelago.
As a Maharlika, you venture out into space where you will take on dangerous missions, fight for your ideals, hack the spiritual internet that is the Lambat, repel Xenobeings, trade love and resources, and participate in fiestas to survive, thrive, and protect what is yours in the dangerous Starsea.
Maharlika is inspired by a number of mech media, including Mobile Suit Thunderbolt and Iron Blooded Orphans from the Gundam series. The game has two modes of play: Maharlika (narrative) and Meka (mech combat). You’ll use mainly d10s and d20s for these rolls, and add modifiers for skills and stats that your character is strong in. The setting itself is described as technomystical, and the lore is heavily inspired by Filipino mythology, so if you want to really lean into the supernatural abilities such as the psychic abilities suggested in Mobile Suit Gundam’s Newtypes, this might be worth checking out. Maharlika is possibly also the most technically complex game on this list.
Games I’ve Recommended in the Past
Spectres of Brocken, by ehronlime.
Lancer, by Massif Press.
137 notes
·
View notes
Text
What to Do if Your Crypto Is Stolen: A Recovery Guide

Cryptocurrency has revolutionized the way we think about money. It has allowed people to store and transfer wealth securely without relying on traditional banks. However, as with all innovations, the rise of digital currencies has also brought new challenges. One of the most daunting concerns for crypto holders is the possibility of having their assets stolen. Whether through a hack, phishing scam, or compromised private keys, the loss of cryptocurrency can be distressing. However, it’s not all doom and gloom. There are steps you can take to recover your stolen crypto, and with the right approach, you may be able to track down the assets and regain control.
In this recovery guide, we’ll walk you through a series of steps to help you get your stolen crypto back. We’ll also discuss how to protect yourself in the future and reduce the likelihood of crypto theft happening again.
1. Verify the Theft
The first step is to confirm that your crypto has actually been stolen. Before jumping to conclusions, make sure you haven’t simply misplaced your private key or forgotten your wallet’s password. Here are some things to check:
Check Your Wallet Balance: Log into your crypto wallet and verify that your balance has decreased or that there have been unauthorized transactions. Most wallets show transaction history and activity logs, so if you see any unfamiliar activity, this could indicate a theft.
Look for Suspicious Activity: If you’ve been receiving strange emails, messages, or pop-up alerts, these may be signs that someone is attempting to access your wallet. Double-check for any interactions that may have led to the compromise.
Check the Blockchain: Blockchain technology is transparent, and all transactions are publicly recorded. You can check your wallet’s public address on a blockchain explorer to see if your funds have been moved.
Once you've verified that your cryptocurrency has indeed been stolen, it’s time to act fast and take appropriate action.
2. Change Your Security Details
After confirming that your crypto is stolen, the next critical step is to change your security credentials. This can minimize further damage and help you protect your other assets.
Change Your Passwords: If your wallet is linked to an account with a password (like an exchange or digital wallet service), immediately change your password. Ensure you create a strong password with a mix of letters, numbers, and symbols.
Enable Two-Factor Authentication (2FA): If you haven’t already, enable 2FA for your wallet and any related services. This additional layer of security can prevent unauthorized access to your accounts, even if your password is compromised.
Revoke Access to Devices: If your wallet is accessed through a mobile app or a desktop computer, consider revoking access to those devices temporarily while you assess the situation.
3. Contact the Relevant Authorities
At this point, if you are serious about recovering your stolen crypto, you need to reach out to authorities. How to recover lost or stolen crypto can be challenging, but starting with the right channels can help improve your chances of success. Here are some options:
File a Report with Local Authorities: Depending on where you live, cryptocurrency theft is a crime, and you can file a police report. However, it's essential to note that not all law enforcement agencies have the expertise to track digital assets. Nevertheless, filing a report establishes an official record of the theft, which may prove helpful later.
Report the Theft to Your Wallet Provider or Exchange: If your crypto was stored with a third-party wallet provider or exchange, report the incident to them immediately. Many exchanges have teams that monitor suspicious activities and may be able to help you track the movement of your stolen assets. While they can’t always reverse the theft, they might be able to freeze transactions or flag the thief’s account.
Notify the Blockchain Network: While blockchain networks are decentralized, some of them have groups or organizations dedicated to resolving issues like stolen funds. Look for any emergency resources available within the specific network or blockchain you’re using.
4. Track the Movement of Your Stolen Crypto
One of the most powerful aspects of blockchain technology is its transparency. The decentralized nature of blockchains means every transaction is recorded and publicly visible. If you know your wallet’s public address, you can monitor any transactions made using your stolen crypto.
Use Blockchain Explorers: Websites known as blockchain explorers allow users to trace transactions. By entering your stolen wallet’s address, you can see every transaction made with the stolen funds. This information may help you track down the person who stole your crypto or at least understand how the stolen funds are being used.
Monitor for Transfers: Keep an eye out for transfers made to exchanges or new wallets. Often, criminals will try to sell the stolen crypto quickly, which could lead to their identification if the transaction is traced back to a regulated exchange. Some exchanges may have fraud detection teams that can help stop these transactions from going through.
5. Check with a Crypto Recovery Expert
Crypto theft recovery can be a complex process. While some individuals have successfully recovered stolen funds on their own, it’s not always easy. This is where expert help might be necessary. You can consider reaching out to crypto recovery specialists who have the tools and expertise to track stolen crypto and possibly assist in retrieving it.
These specialists have access to sophisticated tools and resources that can enhance your chances of recovery. While it’s important to be cautious about hiring third parties (as some scammers also prey on victims), there are legitimate services available that specialize in cryptocurrency fraud and recovery.
6. Understand the Limitations
While there are certainly actions you can take to try and recover your stolen crypto, it’s important to understand that success is not guaranteed. The decentralized nature of cryptocurrencies means there’s no central authority or institution that can reverse transactions once they’ve been confirmed. Additionally, the anonymity of blockchain technology makes it challenging to identify and track criminals.
Even if your stolen funds are traced to an address, it can be difficult to identify the thief or stop the transaction. In many cases, stolen crypto ends up in wallets that are beyond the reach of the authorities or experts. Therefore, it's essential to manage your expectations and understand that recovery efforts may not always yield results.
7. Take Preventive Measures for the Future
Prevention is always better than recovery. Here are a few important steps to help safeguard your crypto assets moving forward:
Store Your Crypto in a Secure Wallet: If you store your crypto on an exchange, consider transferring it to a more secure wallet. Hardware wallets or cold storage options are the safest for long-term storage, as they’re not connected to the internet and are less susceptible to hacking.
Regularly Backup Your Private Keys: One of the most crucial aspects of crypto security is backing up your private keys. If your private key is lost, you could lose access to your funds permanently.
Be Wary of Phishing Scams: Always double-check URLs and email addresses before entering sensitive information like private keys or passwords. Phishing scams are common in the crypto world, and a single wrong click can result in stolen funds.
Stay Updated on Security Best Practices: The world of crypto is always evolving, so it’s important to stay informed about the latest security practices. Regularly check for updates to your wallet or exchange software, and always use the latest security features.
Conclusion
Losing your crypto to theft can be a devastating experience, but it’s essential to stay calm and take immediate action. By verifying the theft, changing your security details, reaching out to the right authorities, and utilizing blockchain tools, you can maximize your chances of recovering your stolen funds. Furthermore, taking proactive steps to secure your crypto moving forward will help prevent future thefts.
For more information on how to secure your crypto assets and understand the recovery process better, visit https://www.tawnyswift.com/.
0 notes
Text
How to Get Unbanned on Fortnite in 2025
Using hacks, cheats, or any third-party software that gives you an advantage in Fortnite is in violation of Epic Games' terms of service. It could result in the possibility of a temporary or permanent ban from the game. To avoid bans To avoid a ban, make sure you follow the game's terms of services and report abusive behavior or the harassment. If you'd like to stay clear of the risk of getting an IP ban, try VPN. VPN. 1. Appeal the ban There are several ways to appeal your Fortnite ban. You must first navigate to the Support section on the Epic Games site. There you can fill out an appeals form, which includes your email address and a short account of the incident which resulted in your ban.
youtube
The next thing to do is waiting for Epic Games to review your appeal. It could take some time for them to respond, and it's important that you're patient throughout the process. If your ban is for a long time then you'll be unable to lift it unless you contact Epic directly. You could be banned the HWID you use is blocked, and this is applicable to VPNs as well. HWID bans only impact the IP address of your device, not your serial number or device identifier. Because of this, using an VPN can be dangerous if you're trying to stay clear of being banned permanently. 2. Change your IP address You can attempt to have your ban overturned by contacting Epic Games, the game's creator. They might be able to provide you with more details on why you were banned and ways to avoid being caught later on. This won't help if the ban was for serious violations like cheating or hacking. The fastest method of avoiding Fortnite IP bans is by using a VPN. Installed on your mobile or PC, these apps will change your IP address and allow you to enjoy the game. They are also more reliable than hotspots, which can cost you money and limit your data. NordVPN has the fastest speeds and the lowest ping of any gaming VPN. It's important to keep your gaming running smoothly especially when you're trying to dodge a ban. 3. Use an VPN You may receive an Fortnite banning that is unfair or illegitimate. A VPN can assist you in attempting to avoid the IP-based bans by connecting to another server, which masks your original IP address. NordVPN is the best VPN to use for Fortnite. It offers gaming-optimized server options that will assist you in reducing the ping of your game while enjoying smooth gameplay. You can connect up to 10 devices simultaneously and the service comes with a guarantee. Another alternative is PIA It offers servers in more than 91 countries and can assist you in lowering your ping by finding a route that is close to the servers of the game. It's simple to use, and works with desktops (PC and Mac), smartphones (iOS and Android) and consoles (with the option of setting up your router manually). The no-logs policy permits users to remain completely anonymous on the Internet. You can try it for no cost. 4. Contact Epic Games Banning yourself from Fortnite can be a frustrating and stressful experience. The loss of V-Bucks and skins can be an unsettling experience for any player. It is important to know the reason behind your ban, and how to obtain your Fortnite account back. A ban placed on your account puts limitations on the use of your Epic Games account, and won't allow you to play the game until you submit an appeal to a ban. Based on the severity of your offence, the ban may be temporary or permanent. Hardware ID bans, in contrast is a ban on your computer's device ID, and blocks your ability to access the game. It is possible to bypass an HWID block by using a spoofer, VPN or any other tool. But, you'll be required to appeal the ban. Video by YouTube
1 note
·
View note
Text
How to Protect Your Dubai-Based Business from Cyber Threats
In today’s digital world, protecting your Dubai-based business from cyber threats is more important than ever. Cyberattacks can cause severe damage, including financial losses, loss of customer trust, and even legal troubles. As businesses in Dubai grow and embrace technology, they must understand the risks and take steps to stay safe online. This guide will help you learn how to protect your business and keep it secure.

What Are Cyber Threats?
Cyber threats are dangers that come from the internet or computer systems. These include hacking, phishing, malware, ransomware, and other attacks that can harm your data or systems. For businesses in Dubai, these threats can target sensitive information like customer details, financial records, and trade secrets.
Why Is Cybersecurity Important for a Dubai-Based Business?
Dubai is a global business hub with many companies relying on digital tools. A cyberattack can stop business operations, damage your reputation, and lead to a loss of money. Moreover, Dubai has strict laws about protecting data, so failing to secure your business can result in penalties.
Investing in cybersecurity not only protects your assets but also builds trust with your customers and partners.
Key Ways to Protect Your Dubai Business
1. Use Strong Passwords and Change Them Regularly
Passwords are the first line of defense. Encourage employees to use complex passwords with letters, numbers, and symbols. Avoid simple passwords like "123456" or "password." Change passwords regularly, especially after employees leave the company.
2. Install and Update Antivirus Software
Good antivirus software protects your systems from viruses, malware, and spyware. Make sure to keep the software updated because hackers find new ways to attack all the time.
3. Secure Your Wi-Fi Network
A safe Wi-Fi network stops hackers from gaining access to your data. Use strong encryption methods like WPA3 and hide your network name (SSID). Also, change the default router password.
4. Backup Important Data Regularly
Backups ensure that even if your data is lost or encrypted by ransomware, you can recover it. Store backups offline or in a secure cloud service and test them regularly.
5. Train Employees on Cybersecurity Awareness
Your team is your strongest defense. Conduct regular training sessions on identifying phishing emails, avoiding suspicious links, and reporting any unusual activity.
6. Use Firewalls and Encryption
Firewalls block unauthorized access to your network. Encryption scrambles your data, making it unreadable to anyone without the key. Use both to protect sensitive business information.
7. Control Access to Sensitive Information
Not everyone in your company needs access to all data. Use role-based access controls so employees only see what they need for their job.
8. Monitor Your Systems for Suspicious Activity
Keep an eye on network activity to catch threats early. Use security tools that alert you to unusual behavior, such as multiple failed login attempts.
9. Have a Cybersecurity Response Plan
In case of an attack, knowing what to do can save your business. Create a plan that includes who to contact, how to contain the attack, and steps to recover.
10. Work with Trusted IT Professionals
If cybersecurity feels overwhelming, hire experts to help set up strong defenses and keep your systems secure.
Pro Tips
Regularly Update Software: Outdated software has security holes that hackers can exploit. Always install updates and patches on your operating systems and applications.
Use Multi-Factor Authentication (MFA): MFA adds an extra step to login, such as a code sent to your phone, making it harder for attackers to get in.
Secure Mobile Devices: Many employees use mobile phones for work. Protect these devices with passwords and encryption.
Limit Use of Public Wi-Fi: Avoid accessing company systems over public Wi-Fi. Use a Virtual Private Network (VPN) if needed.
Review Third-Party Security: If you use external services or vendors, ensure they follow strong security practices.
FAQs
1. What are the biggest cyber threats to a Dubai-based business?
The biggest threats include phishing attacks, ransomware, data breaches, and malware infections.
2. How often should I train my employees on cybersecurity?
Ideally, training should happen at least twice a year, with regular reminders and updates.
3. Can a small business in Dubai afford cybersecurity?
Yes, there are many affordable tools and services tailored for small businesses to protect against cyber risks.
4. What should I do if my business is hacked?
Immediately isolate affected systems, notify your IT team or experts, and follow your cybersecurity response plan.
5. Does Dubai have laws about cybersecurity?
Yes, Dubai has strict data protection laws. Businesses must follow these rules to avoid penalties and protect customer data.
Conclusion
Protecting your Dubai-based business from cyber threats is essential in today’s connected world. As hackers become more advanced, businesses must remain vigilant and invest in robust security measures. From implementing strong passwords to training employees and having a response plan, each step counts.
Taking these precautions will not only secure your business but also build confidence among your clients and partners. Start today by assessing your current security and making improvements. Remember, cybersecurity is an ongoing process, not a one-time task.
0 notes