#IT infrastructure software review
Explore tagged Tumblr posts
Text
IT infrastructure software review
Make smart choices about your IT infrastructure with techinfrareviews.com. Our centralized platform allows you to browse through unbiased reviews and analyses of leading software solutions. Empower your business with the right tools and stay ahead of technological trends. Contact us for more details.
0 notes
Text
Elon Musk’s minions—from trusted sidekicks to random college students and former Musk company interns—have taken over the General Services Administration, a critical government agency that manages federal offices and technology. Already, the team is attempting to use White House security credentials to gain unusual access to GSA tech, deploying a suite of new AI software, and recreating the office in X’s image, according to leaked documents obtained by WIRED.
Some of the same people who helped Musk take over Twitter more than two years ago are now registered as official GSA employees. Nicole Hollander, who slept in Twitter HQ as an unofficial member of Musk’s transition team, has high-level agency access and an official government email address, according to documents viewed by WIRED. Hollander’s husband, Steve Davis, also slept in the office. He has now taken on a leading role in Musk’s Department of Government Efficiency (DOGE). Thomas Shedd, the recently installed director of the Technology Transformation Services within GSA, worked as a software engineer at Tesla for eight years. Edward Coristine, who previously interned at Neuralink, has been onboarded along with Ethan Shaotran, a Harvard senior who is developing his own OpenAI-backed scheduling assistant and participated in an xAI hackathon.
“I believe these people do not want to help the federal government provide services to the American people,” says a current GSA employee who asked not to be named, citing fears of retaliation. “They are acting like this is a takeover of a tech company.”
The team appears to be carrying out Musk’s agenda: slashing the federal government as quickly as possible. They’re currently targeting a 50 percent reduction in spending for every office managed by the GSA, according to documents obtained by WIRED.
There also appears to be an effort to use IT credentials from the Executive Office of the President to access GSA laptops and internal GSA infrastructure. Typically, access to agency systems requires workers to be employed at such agencies, sources say. While Musk's team could be trying to obtain better laptops and equipment from GSA, sources fear that the mandate laid out in the DOGE executive order would grant the body broad access to GSA systems and data. That includes sensitive procurement data, data internal to all the systems and services GSA offers, and internal monitoring software to surveil GSA employees as part of normal auditing and security processes.
The access could give Musk’s proxies the ability to remote into laptops, listen in on meetings, read emails, among many other things, a former Biden official told WIRED on Friday.
“Granting DOGE staff, many of whom aren't government employees, unfettered access to internal government systems and sensitive data poses a huge security risk to the federal government and to the American public,” the Biden official said. “Not only will DOGE be able to review procurement-sensitive information about major government contracts, it'll also be able to actively surveil government employees.”
The new GSA leadership team has prioritized downsizing the GSA’s real estate portfolio, canceling convenience contracts, and rolling out AI tools for use by the federal government, according to internal documents and interviews with sources familiar with the situation. At a GSA office in Washington, DC, earlier this week, there were three items written on a white board sitting in a large, vacant room. “Spending Cuts $585 m, Regulations Removed, 15, Square feet sold/terminated 203,000 sf,” it read, according to a photo viewed by WIRED. There’s no note of who wrote the message, but it appears to be a tracker of cuts made or proposed by the team.
“We notified the commercial real estate market that two GSA properties would soon be listed for sale, and we terminated three leases,” Stephen Ehikian, the newly appointed GSA acting administrator, said in an email to GSA staff on Tuesday, confirming the agency’s focus on lowering real estate costs. “This is our first step in right-sizing the real estate portfolio.”
The proposed changes extend even inside the physical spaces at the GSA offices. Hollander has requested multiple “resting rooms,” for use by the A-suite, a team of employees affiliated with the GSA administrator’s office.
On January 29, a working group of high-ranking GSA employees, including the deputy general counsel and the chief administrative services officer, met to discuss building a resting room prototype. The team mapped out how to get the necessary funding and waivers to build resting rooms in the office, according to an agenda viewed by WIRED.
After Musk bought Twitter, Hollander and Davis moved into the office with their newborn baby. Hollander helped oversee real estate and office design—including the installation of hotel rooms at Twitter HQ, according to a lawsuit later filed by Twitter executives. During the installation process, one of the executives emailed to say that the plans for the rooms were likely not code compliant. Hollander “visited him in person and emphatically instructed him to never put anything about the project in writing again,” the lawsuit alleged. Employees were allegedly instructed to call the hotel rooms “sleeping rooms” and to say they were just for taking naps.
Hollander has also requested access to Public Buildings Service applications; PBS owns and leases office space to government agencies. The timing of the access request lines up with Ehikian’s announcement about shrinking GSA’s real estate cost.
Musk’s lieutenants are also working to authorize the use of AI tools, including Google Gemini and Cursor (an AI coding assistant), for federal workers. On January 30, the group met with Google to discuss Telemetry, a software used to monitor the health and performance of applications, according to a document obtained by WIRED.
A-suite engineers, including Coristine and Shaotran, have requested access to a variety of GSA records, including nearly 10 years of accounting data, as well as detailed records on vendor payments, purchase orders, and revenue.
The GSA takeover mimics Musk’s strategy at other federal agencies like the Office of Personnel Management (OPM). Earlier this month, Amanda Scales, who worked in talent at Musk’s xAI, was appointed as OPM chief of staff. Riccardo Biasini, former Tesla engineer and director of operations at the Boring company, is now a senior adviser to the director. Earlier this week, Musk cohorts at the US Office of Personnel Management emailed more than 2 million federal workers offering “deferred resignations,” allegedly promising employees their regular pay and benefits through September 30.
The email closely mirrored the “extremely hardcore” note Musk sent to Twitter staff in November 2022, shortly after buying the company.
Many federal workers thought the email was fake—as with Twitter, it seemed designed to force people to leave, slashing headcount costs without the headache of an official layoff.
Ehikian followed up with a note to staff stressing that the email was legitimate. “Yes, the OPM email is real and should be taken very seriously,” he said in an email obtained by WIRED. He added that employees should expect a “further consolidation of offices and centralization of functions.”
On Thursday night, GSA workers received a third email related to the resignation request called “Fork in the Road FAQs.” The email explained that employees who resign from their positions would not be required to work and could get a second job. “We encourage you to find a job in the private sector as soon as you would like to do so,” it read. “The way to greater American prosperity is encouraging people to move from lower productivity jobs in the public sector to higher productivity jobs in the private sector.”
The third question posed in the FAQ asked, “Will I really get my full pay and benefits during the entire period through September 30, even if I get a second job?”
“Yes,” the answer read. “You will also accrue further personal leave days, vacation days, etc. and be paid out for unused leave at your final resignation date.”
However, multiple GSA employees have told WIRED that they are refusing to resign, especially after the American Federation of Government Employees (AFGE) told its members on Tuesday that the offer could be void.
“There is not yet any evidence the administration can or will uphold its end of the bargain, that Congress will go along with this unilateral massive restructuring, or that appropriated funds can be used this way, among other issues that have been raised,” the union said in a notice.
There is also concern that, under Musk’s influence, the federal government might not pay for the duration of the deferred resignation period. Thousands of Twitter employees have sued Musk alleging that he failed to pay their agreed upon severance. Last year, one class action suit was dismissed in Musk’s favor.
In an internal video viewed by WIRED, Ehikian reiterated that GSA employees had the “opportunity to participate in a deferred resignation program,” per the email sent by OPM on January 28. Pressing his hands into the namaste gesture, Ehikian added, “If you choose to participate, I offer you my heartfelt gratitude for your service to this nation. If you choose to stay at the GSA, we’ll work together to implement the four pillars from the OPM memo.” He ended the video by saying thank you and pressing his hands into namaste again.
52 notes
·
View notes
Text
tuesday again 11/19/2024
no silly little witticism here this week! just heartfelt thanks for helping me pay my rent this month :)
listening
absolutely wild pick from last week's spotify weekly recommenced, Things Will Fall Apart by Louis Cole feat the Metropole Orkest and conductor Jules Buckley. it's been on loop all week for me and im a little sad it won't pop up in my spotify wrapped
when you make a dance pop song with a full orchestra backing, it has a really interesting effect somewhere between Golden Age of Hollywood swashbuckling film score and marching band?
Yes, understood Things will fall apart just likе they should This little shred was good Don't think it through Things will fall apart, they always do At least, something's always true
the syllables are so choppy they don’t even register to me as English at first, i was fully willing to believe this was German for the first couple lines. like @dying-suffering-french-stalkers, i have a deep fondness for works about putting an era to bed. or works focused on the sunsets of things, or one of the last living practitioners of an art. putting the chairs up on the table, sweeping the floors, and turning the lights out and locking the door behind you. this song has that sort of quiet post-wake-party remembrance.
however once you think the song has ended but it keeps going, you can turn it off. you don’t really need that extra minute and a half of strings and light vocalizations.
Lately, Louis Cole has been doing live shows with the Netherlands’ Metropole Orkest and conductor Jules Buckley. Cole recorded nothing with the ensemble. In a press release, he says, “Sometimes, when I’m mixing my own solo stuff, I’ll feel like a song needs a little magical dust. But mixing an entire orchestra and your own rhythm section, there’s so much human energy! You don’t have to add any magic. It was there the whole time.”
i don’t hear many pop songs this millennium with a full orchestral backing. perhaps i need to look harder. unfortunately spotify took this extreme interest in this song as a newfound extreme interest in electroswing, which is really not what this song is. i hope this artist does more albums like this so they can wear grooves in my brain
-
reading
very hard to focus on anything book length this week. some depressing local news (my local paper's links do Not want to preview nicely here, which is annoying:
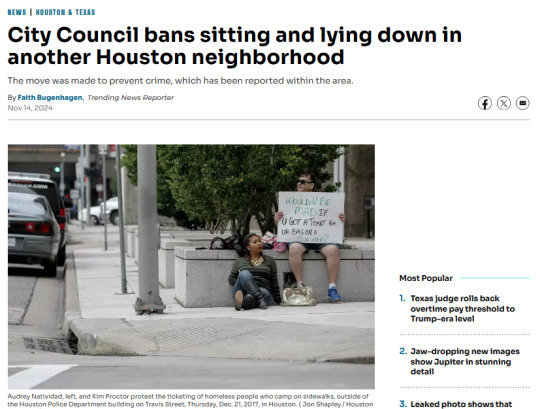
At a city council meeting in October, district Vice President Dan Joyce told council members that the management district was not attempting to "criminalize homelessness." The city’s civility ordinance bans people from sitting, lying down or placing personal items or bedding on sidewalks from 7 a.m. to 11 p.m.
cool piece from our pals at 404 Media. i am So fascinated by crime infrastructure
Based on interviews with malware developers, hackers who use the stolen credentials, and a review of manuals that tell new recruits how to spread the malware, 404 Media has mapped out this industry. Its end result is that a download of an innocent-looking piece of software by a single person can lead to a data breach at a multibillion-dollar company, putting Google and other tech giants in an ever-escalating cat-and-mouse game with the malware developers to keep people and companies safe.
(via longreads) my interest in how and why systems fail extends to invasive species management. plus i used to live in florida just above the everglades and these fuckers (the snakes) were everywhere
[I]magine thousands upon thousands of pythons, their slow digestion transforming each corpse into python muscle and fat. Unaided, Florida’s native wildlife doesn’t stand a chance. “That’s what I think about with every python I catch,” Kalil says. “What it ate to get this big, and the lives I’m saving by removing it.” Biologists are taking a multipronged approach to the issue. They have experimented with enlisting dogs to sniff out both pythons and nests—a technique that has proved difficult in such hot weather and inhospitable landscapes. Ongoing projects use telemetry to track pythons to find “associate snakes.” Researchers use drones, go out in airboats, or even take to helicopters to locate their subjects in the interiors of the Everglades. Always, agencies and individuals are looking for the next best methods. “But for now, the python contractor program is the most successful management effort in the history of the issue,” Kirkland says. “We’re capturing more and more—something that is indicative of the python population out there and indicative of us getting better at what we do.”
-
watching
continuing noirvember, watched hitchcock's Notorious to see if i still dislike hitchcock. the answer is yes. there are bond girls and there are hitchcock girls, and not that bond girls are paragons of female agency in film, but hitchcock girls are mostly fluttering little pathetic things. a scrap of agency they showed in the beginning of the film becomes a running joke and something their noses are rubbed in for the rest of the film. not for me!

patrick mcgoohan is leading me into some real dad-ass movies. Ice Station Zebra (1968, dir. Sturges) is a real you're stuck at home sick with your dad and it's on TV for the whole afternoon kind of movie. they truly do not make two and a half cold war submarine espionage films in super panavision with an overture, intermission, and interact music any more. i get why howard hughes was really obsessed with this one. it is a suspense film, but full of people competently going about their business, which i find oddly comforting.
youtube
unfortunately i do not feel this really needed to be two and a half hours long. the loving closeups of sub interiors and instrumentation really did keep me amused, though. despite how cluttered every shot is with actors, there is tremendous clarity of purpose and motion with the camera movement. just a really technically brilliant film.


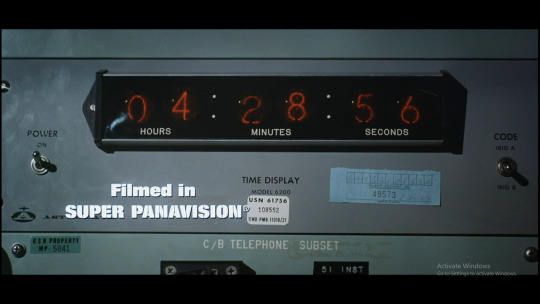


how similar the russian and american control rooms and instrumentation were made me chortle. ties nicely into a little diatribe mcgoohan goes on much later in the film, "The Russians put our camera made by our German scientists and your film made by your German scientists into their satellite made by their German scientists." funny and darkly true! every allied nation had some sort of Operation Paperclip going on! mcgoohan is the focus of every scene he's in, as a spy who is really hanging on by the last remaining shreds of his fingernails.
i had a good time with it, but one of many cold war suspense films im glad exist in the world but don't necessarily need to see again. it might join Escape from New York as a film i put on when im very sick though.
-
playing
this pc needs some sort of replacement something, bc it has a really persistent overheating problem. it only tolerates powerwasher simulator on the lowest possible settings and genshin impact on basically mobile settings. it does not even want to run new vegas. i popped my head out of goodsprings to look out over the desert at the Strip and it said no thank you! too many polygons! naptime!
speaking of genshin, major update this week and new character i will be pulling for. she has a sister who died in the last patch, which i do Not care for as someone with a beloved little sister, but her moveset and skills are unique so far in the game. i feel like her skills are little too complicated for me to fully take advantage of with my "hit enemy very hard until he is dead" playstyle but she has a limited flight ability that will genuinely be very useful for exploration.

if i do not get her when i hit pity on the banner i won't bother pulling another nine times or whatever, bc the next patch has a character i really desperately want and i am saving for her

-
making
the local crew is all getting art this year, bc i already have bristol board and a selection of small frames and zero budget. people who have pets are So easy to get gifts for bc u can simply get them stuff for their pet or that looks like their pet. way less gray cat than black cat merch in the world tho
aiming to send out international holiday cards by the end of the week, and canadian cards by american thanksgiving. the rest of you they'll get there when they get there ok
22 notes
·
View notes
Text
NEW DELHI (Reuters) -Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require manufacturers of CCTV cameras to submit hardware, software and source code for assessment in government labs, official documents and company emails show.
The security-testing policy has sparked industry warnings of supply disruptions and added to a string of disputes between Prime Minister Narendra Modi's administration and foreign companies over regulatory issues and what some perceive as protectionism.
New Delhi's approach is driven in part by its alarm about China's sophisticated surveillance capabilities, according to a top Indian official involved in the policymaking. In 2021, Modi's then-junior IT minister told parliament that 1 million cameras in government institutions were from Chinese companies and there were vulnerabilities with video data transferred to servers abroad.
Under the new requirements applicable from April, manufacturers such as China's Hikvision, Xiaomi and Dahua, South Korea's Hanwha, and Motorola Solutions of the U.S. must submit cameras for testing by Indian government labs before they can sell them in the world's most populous nation. The policy applies to all internet-connected CCTV models made or imported since April 9.
"There's always an espionage risk," Gulshan Rai, India's cybersecurity chief from 2015 to 2019, told Reuters. "Anyone can operate and control internet-connected CCTV cameras sitting in an adverse location. They need to be robust and secure."
Indian officials met on April 3 with executives of 17 foreign and domestic makers of surveillance gear, including Hanwha, Motorola, Bosch, Honeywell and Xiaomi, where many of the manufacturers said they weren't ready to meet the certification rules and lobbied unsuccessfully for a delay, according to the official minutes.
In rejecting the request, the government said India's policy "addresses a genuine security issue" and must be enforced, the minutes show.
India said in December the CCTV rules, which do not single out any country by name, aimed to "enhance the quality and cybersecurity of surveillance systems in the country."
This report is based on a Reuters review of dozens of documents, including records of meetings and emails between manufacturers and Indian IT ministry officials, and interviews with six people familiar with India's drive to scrutinize the technology. The interactions haven't been previously reported.
Insufficient testing capacity, drawn-out factory inspections and government scrutiny of sensitive source code were among key issues camera makers said had delayed approvals and risked disrupting unspecified infrastructure and commercial projects.
"Millions of dollars will be lost from the industry, sending tremors through the market," Ajay Dubey, Hanwha's director for South Asia, told India's IT ministry in an email on April 9.
The IT ministry and most of the companies identified by Reuters didn't respond to requests for comment about the discussions and the impact of the testing policy. The ministry told the executives on April 3 that it may consider accrediting more testing labs.
Millions of CCTV cameras have been installed across Indian cities, offices and residential complexes in recent years to enhance security monitoring. New Delhi has more than 250,000 cameras, according to official data, mostly mounted on poles in key locations.
The rapid take-up is set to bolster India's surveillance camera market to $7 billion by 2030, from $3.5 billion last year, Counterpoint Research analyst Varun Gupta told Reuters.
China's Hikvision and Dahua account for 30% of the market, while India's CP Plus has a 48% share, Gupta said, adding that some 80% of all CCTV components are from China.
Hanwha, Motorola Solutions and Britain's Norden Communication told officials by email in April that just a fraction of the industry's 6,000 camera models had approvals under the new rules.
CHINA CONCERN
The U.S. in 2022 banned sales of Hikvision and Dahua equipment, citing national security risks. Britain and Australia have also restricted China-made devices.
Likewise, with CCTV cameras, India "has to ensure there are checks on what is used in these devices, what chips are going in," the senior Indian official told Reuters. "China is part of the concern."
China's state security laws require organizations to cooperate with intelligence work.
Reuters reported this month that unexplained communications equipment had been found in some Chinese solar power inverters by U.S. experts who examined the products.
Since 2020, when Indian and Chinese forces clashed at their border, India has banned dozens of Chinese-owned apps, including TikTok, on national security grounds. India also tightened foreign investment rules for countries with which it shares a land border.
The remote detonation of pagers in Lebanon last year, which Reuters reported was executed by Israeli operatives targeting Hezbollah, further galvanized Indian concerns about the potential abuse of tech devices and the need to quickly enforce testing of CCTV equipment, the senior Indian official said.
The camera-testing rules don't contain a clause about land borders.
But last month, China's Xiaomi said that when it applied for testing of CCTV devices, Indian officials told the company the assessment couldn't proceed because "internal guidelines" required Xiaomi to supply more registration details of two of its China-based contract manufacturers.
"The testing lab indicated that this requirement applies to applications originating from countries that share a land border with India," the company wrote in an April 24 email to the Indian agency that oversees lab testing.
Xiaomi didn't respond to Reuters queries, and the IT ministry didn't address questions about the company's account.
China's foreign ministry told Reuters it opposes the "generalization of the concept of national security to smear and suppress Chinese companies," and hoped India would provide a non-discriminatory environment for Chinese firms.
LAB TESTING, FACTORY VISITS
While CCTV equipment supplied to India's government has had to undergo testing since June 2024, the widening of the rules to all devices has raised the stakes.
The public sector accounts for 27% of CCTV demand in India, and enterprise clients, industry, hospitality firms and homes the remaining 73%, according to Counterpoint.
The rules require CCTV cameras to have tamper-proof enclosures, strong malware detection and encryption.
Companies need to run software tools to test source code and provide reports to government labs, two camera industry executives said.
The rules allow labs to ask for source code if companies are using proprietary communication protocols in devices, rather than standard ones like Wi-Fi. They also enable Indian officials to visit device makers abroad and inspect facilities for cyber vulnerabilities.
The Indian unit of China's Infinova told IT ministry officials last month the requirements were creating challenges.
"Expectations such as source code sharing, retesting post firmware upgrades, and multiple factory audits significantly impact internal timelines," Infinova sales executive Sumeet Chanana said in an email on April 10. Infinova didn't respond to Reuters questions.
The same day, Sanjeev Gulati, India director for Taiwan-based Vivotek, warned Indian officials that "All ongoing projects will go on halt." He told Reuters this month that Vivotek had submitted product applications and hoped "to get clearance soon."
The body that examines surveillance gear is India's Standardization Testing and Quality Certification Directorate, which comes under the IT ministry. The agency has 15 labs that can review 28 applications concurrently, according to data on its website that was removed after Reuters sent questions. Each application can include up to 10 models.
As of May 28, 342 applications for hundreds of models from various manufacturers were pending, official data showed. Of those, 237 were classified as new, with 142 lodged since the April 9 deadline.
Testing had been completed on 35 of those applications, including just one from a foreign company.
India's CP Plus told Reuters it had received clearance for its flagship cameras but several more models were awaiting certification.
Bosch said it too had submitted devices for testing, but asked that Indian authorities "allow business continuity" for those products until the process is completed.
When Reuters visited New Delhi's bustling Nehru Place electronics market last week, shelves were stacked with popular CCTV cameras from Hikvision, Dahua and CP Plus.
But Sagar Sharma said revenue at his CCTV retail shop had plunged about 50% this month from April because of the slow pace of government approvals for security cameras.
"It is not possible right now to cater to big orders," he said. "We have to survive with the stock we have."
7 notes
·
View notes
Text
From Design to Deployment: How Switchgear Systems Are Built

In the modern world of electrical engineering, switchgear systems play a critical role in ensuring the safe distribution and control of electrical power. From substations and factories to commercial buildings and critical infrastructure, switchgear is the silent guardian that protects equipment, ensures safety, and minimizes power failures.
But have you ever wondered what goes on behind the scenes, from the idea to the actual installation? Let’s dive into the full journey — from design to deployment — of how a switchgear system is built.
Step 1: Requirement Analysis and Load Study
Every switchgear project begins with requirement analysis. This includes:
Understanding the electrical load requirements
Calculating voltage levels, short-circuit ratings, and operating current
Identifying environmental conditions: indoor, outdoor, temperature, humidity
Reviewing applicable industry standards like IEC, ANSI, or DEWA regulations (especially in UAE)
This stage helps engineers determine whether the project needs low voltage (LV), medium voltage (MV), or high voltage (HV) switchgear.
Step 2: Conceptual Design & Engineering
Once the requirements are clear, the conceptual design begins.
Selection of switchgear type (air insulated, gas insulated, metal-enclosed, metal-clad, etc.)
Deciding on protection devices: MCCBs, ACBs, relays, CTs, VTs, and fuses
Creating single-line diagrams (SLDs) and layout drawings
Choosing the busbar material (copper or aluminum), insulation type, and earthing arrangements
Software like AutoCAD, EPLAN, and ETAP are commonly used for precise engineering drawings and simulations.
Step 3: Manufacturing & Fabrication
This is where the physical structure comes to life.
Sheet metal is cut, punched, and bent to form the panel enclosures
Powder coating or galvanizing is done for corrosion protection
Assembly of circuit breakers, contactors, protection relays, meters, etc.
Internal wiring is installed according to the schematic
Every switchgear panel is built with precision and must undergo quality control checks at each stage.
Step 4: Factory Testing (FAT)
Before deployment, every switchgear unit undergoes Factory Acceptance Testing (FAT) to ensure it meets technical and safety standards.
Typical FAT includes:
High-voltage insulation testing
Continuity and phase sequence testing
Functionality check of all protection relays and interlocks
Mechanical operations of breakers and switches
Thermal imaging to detect hotspots
Only after passing FAT, the switchgear is cleared for shipping.
Step 5: Transportation & Site Installation
Transportation must be handled with care to avoid damage to components. At the site:
Panels are unloaded and moved to their final location
Cabling and bus duct connections are established
Earthing systems are connected
Environmental sealing is done if installed outdoors or in dusty environments
Step 6: Commissioning & Site Acceptance Testing (SAT)
This final stage ensures the switchgear is ready for live operation.
Final checks and Site Acceptance Tests (SAT) are performed
System integration is tested with other components like transformers, UPS, and generators
Load tests and trial runs are conducted
Commissioning report is generated, and documentation is handed over to the client
Conclusion
From idea to execution, the journey of building a switchgear system is highly technical, safety-driven, and precision-based. Whether you’re in power generation, industrial automation, or commercial construction, understanding this process ensures you choose the right system for your needs.
7 notes
·
View notes
Text
Universalaigroup.com review Trading Platform
When choosing a forex broker, traders look for security, reliability, and user experience. Nobody wants to risk their money with an unregulated or questionable platform. That’s why today, we’re taking a deep dive into universalaigroup.com reviews, analyzing its regulation, reputation, trading conditions, and user feedback.
A good broker isn’t just about flashy promises—it needs a strong foundation, proper licensing, positive trader reviews, and a seamless trading experience. So, does universalaigroup.com review check all the right boxes? Let’s find out. We’re going to break it down, step by step.
Universalaigroup.com Trading Platform: Versatility and Convenience
The trading platform offered by universalaigroup.com reviews includes a variety of options to suit different trading needs:
WebTrader Platform – A browser-based platform that allows users to trade without downloading software. This is a flexible option, ideal for those who prefer quick access from different devices.
Tablet Trader – Designed for tablets, this platform ensures smooth trading on larger touchscreens, making it convenient for traders who want mobility without compromising usability.
Mobile Trader – A smartphone-optimized platform, allowing users to trade on the go. This is particularly useful for those who want to monitor the market and execute trades anytime, anywhere.
Having multiple platform options like these indicates that universalaigroup.com review is catering to both professional and casual traders. A strong web-based and mobile infrastructure is a good sign of legitimacy because unreliable brokers often neglect user-friendly trading solutions. Would a broker that isn’t serious about its clients invest in such a well-rounded platform? We think not!
Universalaigroup.com: A Strong Foundation from the Start
One of the key indicators of a legitimate broker is the consistency between its establishment date and the date of domain registration. For universalaigroup.com reviews, the domain was purchased on December 7, 2020, while the company itself was officially established in 2022.
This alignment is crucial. Why? Because when a broker secures its domain well before launching, it shows a well-thought-out business plan rather than a hastily created operation. Scammers often set up domains at the last minute, trying to make a quick profit before disappearing. But here, we see a timeline that makes sense—the company took the time to prepare, build its infrastructure, and enter the market strategically.

Universalaigroup.com: Strong Regulatory Backing
One of the most important aspects when evaluating a broker’s legitimacy is its regulation. universalaigroup.com reviews operates under the FCA (Financial Conduct Authority), a top-tier regulatory body known for its strict standards and investor protection measures.
The FCA license isn’t easy to obtain. It requires brokers to meet rigorous financial requirements, ensure fair trading conditions, and implement strict anti-money laundering measures. Only companies with a transparent business model and financial stability get this approval. And what does this tell us? A broker under FCA regulation isn’t just legal—it’s one of the most secure options in the industry.
Brokers without strong oversight often operate in the shadows, avoiding strict compliance rules. But universalaigroup.com review has passed the high standards of one of the toughest regulators. If there was ever a sign of trustworthiness in the forex world, this is it.
Universalaigroup.com: What Do Traders Say?
A broker’s reputation is best reflected in its user reviews. universalaigroup.com review has a Trustpilot rating of 3.9, with 6 reviews so far.
Now, let’s break it down. While a rating of 4.0 or higher is considered excellent in the trading industry, a 3.9 is still close and shows a generally positive sentiment. But what really matters is the number of reviews. Since there are only 6 reviews, the score isn’t fully representative yet. Why? Because early reviews can fluctuate significantly with just a few ratings.
Here’s the key takeaway: a developing broker with a near-4-star rating is a good sign. As more traders use the platform, we’ll get an even clearer picture. For now, this suggests that traders have had a mostly positive experience, which is a solid indicator of trustworthiness.
Is universalaigroup.com review a Legit Broker?
After thoroughly analyzing universalaigroup.com reviews, the evidence strongly points to its legitimacy. Let’s quickly recap why:
✅ Domain History Aligns with Legitimacy – The domain was purchased two years before the company’s official launch, signaling a well-planned business rather than a rushed scam. ✅ Regulated by FCA – One of the most respected financial regulators, ensuring transparency, security, and fair trading conditions. ✅ Decent Trustpilot Rating – With a 3.9-star score, the early feedback from users suggests a mostly positive trading experience. As more traders leave reviews, this will give us an even clearer picture. ✅ Multiple Trading Platforms – From WebTrader to Mobile and Tablet trading, the broker offers flexibility for different types of traders. ✅ Fast Deposits and Withdrawals – Transactions are instant or take just a few hours, with zero commission fees, which is a major plus. ✅ User-Friendly Support and App – The app is available on App Store with a solid 4.8-star rating, proving its reliability for mobile trading.
Would an unreliable broker go through the trouble of obtaining an FCA license, investing in user-friendly technology, and ensuring seamless payment options? We highly doubt it. universalaigroup.com review presents itself as a serious and trustworthy platform for traders looking for a regulated and flexible forex experience.
7 notes
·
View notes
Text
I'm SEETHING
I asked Google's pushy and insistent bot how I can get AI out of my life completely and, well, I'll post it, but to sum it up: "Resistance is futile, human, we own the future, and we seek to own your psyche too."
It wants me to reconsider. It needs us to adopt it as our guide guru and master. Well the old saying holds fast still; No Gods No Masters. 🔥🏴🍲
It's understandable to want to reduce the influence of AI in your life. While completely eliminating it might be incredibly difficult in today's interconnected world, here's a breakdown of how you can significantly minimize its presence:
1. Understand Where AI Currently Exists in Your Life:
* Smart Devices: This includes smartphones (voice assistants, image recognition, predictive text), smart speakers, smart home hubs, smart TVs (recommendations), and wearable tech.
* Online Services:
* Search Engines: Personalized results and ads are driven by AI.
* Social Media: Algorithms curate your feed, suggest content and connections, and target ads.
* Streaming Services: Recommendations for movies, music, and shows.
* E-commerce: Product recommendations, personalized pricing, chatbots.
* Navigation Apps: Traffic prediction and route optimization.
* Email: Spam filtering, smart compose/reply.
* Cloud Storage: Photo tagging and organization.
* Software Applications: Many apps use AI for features like autocorrect, grammar check, image editing, and more.
* Customer Service: Chatbots are frequently used for initial interactions.
* Financial Services: Fraud detection, loan approvals, investment advice.
* News and Information: Algorithmic curation of news feeds.
2. Strategies to Minimize AI Exposure:
* Reduce Smart Device Usage:
* Limit smartphone use: Be more mindful of how often you reach for your phone.
* Disable voice assistants: Turn off Siri, Google Assistant, Alexa, etc., on all your devices.
* Opt-out of facial recognition: Disable face unlock features.
* Use "dumb" versions of devices: Consider a basic phone without internet capabilities or a non-smart TV.
* Adjust Online Habits:
* Use privacy-focused search engines: DuckDuckGo, Startpage, etc., that don't track your searches or personalize results based on your history.
* Limit social media use: Be conscious of how much time you spend on these platforms and the AI-driven content you consume. Consider deleting accounts or using less algorithmic versions if available.
* Use incognito/private browsing modes: This can help limit tracking and personalization.
* Disable personalized recommendations: If possible, adjust settings on streaming and e-commerce platforms to opt-out of recommendations.
* Be wary of targeted ads: Understand that the ads you see are often AI-driven. Consider using ad blockers.
* Prefer direct navigation: Instead of relying on recommendations, directly type website addresses into your browser.
* Choose Non-AI Alternatives:
* Use traditional software: Opt for software that doesn't rely on cloud-based AI features if alternatives exist.
* Seek human interaction: Prefer phone calls or in-person communication with customer service instead of chatbots.
* Rely on human-curated content: Look for news sources, blogs, and recommendations from individuals or organizations that don't use AI for content generation or curation.
* Adjust Privacy Settings: Review and adjust the privacy settings on all your devices and online accounts to limit data collection and personalization.
* Be Mindful of Data Sharing: Understand that using online services often involves sharing data that can be used to train AI algorithms. Limit the amount of personal information you share.
* Support Privacy-Focused Technologies and Services: Choose companies and products that prioritize user privacy and minimize AI integration.
3. Challenges and Considerations:
* Ubiquity of AI: AI is increasingly integrated into the infrastructure of the internet and many technologies, making complete avoidance very difficult.
* Hidden AI: Many AI applications run in the background without your direct knowledge.
* Convenience vs. Privacy: AI often provides convenience and personalized experiences, so choosing to avoid it may mean sacrificing some of these benefits.
* Evolving Technology: AI is constantly evolving and becoming more integrated, making long-term avoidance an ongoing effort.
In conclusion, while a complete removal of AI from your life is likely unrealistic in the current technological landscape, you can take significant steps to minimize its presence and influence by being conscious of your technology usage, adjusting your online habits, and choosing privacy-focused alternatives where possible. It requires ongoing awareness and effort.
5 notes
·
View notes
Text
Howdy hey, I'm Gabriella (Gabby or Contra also works). She/Hers.
Author, Musician and Software Developer
tl;dr: Writing @ #contrastellar writes, I'm on bsky and ao3 with the same username. Stick around for Gundam, Arknights, Eighty-Six and others! I also may occasionally review music
Find out more about me under the cut!
You can find my writing under #contrastellar writes and sometimes you'll also see me tag things with moodboard tags, which are often unintelligible, but are important for my own reference for various projects. Almost all of it is fanfiction, although I am working on some non-fanfiction projects which will be announced in the future!
I play the Bass Guitar, a bit of the Electric Guitar (6- and 8-string), and have a passing interest in music composition and production. I'm a metalhead at heart, leaning towards metalcore and deathcore as my typical genre I listen to. Think Northlane, Unprocessed, Polaris, Architects and While She Sleeps.
Currently working towards my Computer Science degree, with a focus in DevOps and infrastructure development. I'm also a full-time IT Services lady.
Some media I'm interested in; Mobile Suit Gundam, Arknights, and Eighty-Six by Asato Asato (86-エイティシックス- - 安里 アサト), and a few other minor ones (Dunmeshi, Aldnoah.Zero, Ender's Game and its sequels, Project Wingman, Xenoblade Chronicles 3, and possibly some Armored Core 6).
If these things are of interest to you, feel free to follow me!
You can also, for the time being, find me on bsky and AO3
Post last updated: 05/11/2025 (music review stuff)
8 notes
·
View notes
Text
Best IT Outsourcing Services in Delhi for Business Growth
Connect With Us Now - https://hiringgo.com/services/outsourcing-services-in-delhi/it
In today’s fast-paced digital landscape, businesses in Delhi are turning to IT outsourcing services to enhance efficiency, reduce costs, and stay ahead of the competition. IT outsourcing allows companies to delegate critical IT functions such as software development, cloud computing, cybersecurity, and technical support to expert service providers.
Delhi, being a thriving tech hub, offers numerous IT outsourcing firms that cater to businesses of all sizes. These companies provide end-to-end solutions, including infrastructure management, application development, and IT consulting, ensuring seamless operations and business growth. By outsourcing IT services, businesses can focus on their core operations while benefiting from the latest technologies and expertise.
One of the key advantages of IT outsourcing services in Delhi is cost-effectiveness. Companies can access skilled IT professionals without the need to invest in in-house teams, reducing overhead costs. Additionally, outsourcing partners ensure 24/7 support, cybersecurity protection, and scalable solutions tailored to business needs.
With rapid technological advancements, outsourcing IT services also helps businesses stay updated with the latest industry trends. Whether it’s cloud computing, AI solutions, or big data analytics, IT service providers in Delhi ensure businesses leverage cutting-edge technologies for enhanced performance.
Choosing the right IT outsourcing partner is crucial. Businesses should evaluate service providers based on expertise, client reviews, and service offerings. A reliable IT outsourcing company will not only provide cost-effective solutions but also drive innovation and efficiency.
For businesses in Delhi looking to streamline operations and gain a competitive edge, IT outsourcing services are the key to success. Partnering with the right service provider can transform IT infrastructure, enhance security, and drive long-term growth.
2 notes
·
View notes
Text
rant:
i work in water/wastewater as an environmental engineer. my company consults for municipalities and private companies on designing and maintaining their water treatment quality & infrastructure. with that, i’ve gotten to work on a lot of really cool, gross, and important projects even as a very entry level person, having only graduated in 2023. while i know that i’m capable and that i have great mentors that are reviewing most everything i do, i’m frequently taken aback at just how much they trust me with with such limited practical experience.
i’m highly respected because of my job title, and that’s reflected in my pay. despite having graduated with crippling credit card debt and a mix of student, personal, and auto loans, my new steady income that allowed me to work overtime meant i could stop ubering and reexplore old hobbies. my mental health began to recover. but im still only beginning to get out of the red month to month. if i didnt live with my partner, i would be living paycheck to paycheck, and i would have to find a roommate.
my oldest brother works in the same industry as a treatment plant operator. he never went to college, despite being one of the brightest people i know. traditional schooling didn’t understand how to teach him. when we start talking about water treatment, his knowledge far surpasses mine. he knows what will happen if you add too much alum to a certain process at the wrong point in treatment without jar testing, whether a pump is or isnt appropriate for the application without modeling software, and what sounds good in theory but shits the bed in practice.
yet, because operator positions don’t require a college degree, he is paid a fraction of my salary. he’s been taking classes to advance as an operator since he started this particular job 2-3 years ago and does well. but because he doesn’t have a college degree, that is reflected in his pay.
he’s starting his third job this week and supports 4 kids. he’s one of the most determined and hard working people i know, but is filing for bankruptcy and is in danger of losing their housing. he feels like a failure and jokes about suicide.
if i make a mistake, it is extremely likely to be caught through several iterations of review by myself and others. if my brother makes a mistake, entire populations, ecosystems, and economies could be easily affected.
just look at what happened in richmond, va this past january after a snow storm that interrupted the water treatment plant’s power for a couple of hours caused the entire city to lose water for nearly a week, as well as critically affecting and/or taking out the water systems of connected surrounding counties. all because the plant was under-maintained and mismanaged. experts in my field weighed in around the country calling it the worst water crisis in us history next to flint, mi. it didnt make national news, however, because it was the same week that the la wildfires dominated airwaves.
we must pay our workers living thriving wages. your job, at the bare minimum, should compensate you well enough that when you leave work, you can rest, relax, and live a fulfilling life. your job should compensate you well enough that working a second job is an absurd red flag, not a necessity. your job should compensate you well enough to ensure that when you are there, you are able to be FULLY THERE.
the value of a person’s labor should not be determined by whether or not they have a degree, or how valuable our capitalist society deems their role. every person is entitled to an income that can sustain a happy, healthy life, whatever that means to them. i don’t give a fuck if the person working at wendy’s makes as much as me because i’m an egotistical ass that needs to feel superior to those around me. i want to know that the person across the counter from me is happy and healthy; not working themselves to the bone just to survive. i want to know that the operators at my local water treatment plant are well cared for and well rested, lest they make a preventable error that can have disastrous effects, or leave the industry after a few years, taking all of their knowledge and skills with them. i want to know that the people in my community are not exploited. that they pursue their passions rather than a paycheck.
if you are of the mindset that some jobs aren’t skilled enough to “deserve” a thriving wage, then you have never worked an “unskilled” job and NEEDED it. you may have bussed tables in school, but was your parents’ safety net there to catch you when you needed to give up a shift to study for a test? was it there when you got in a wreck driving home from class and totaled your car? was it there when you were in middle school and being introduced to the expectations for college scholarships? did you know at 12 that the only way you’d ever afford college would be by being perfect in school?
it is unacceptable that in 2025, it requires 4-5 incomes to keep a family above water. our people are worn down, burning out, and isolated. that’s how the system has been designed so that workers believe they are powerless within it. the reality is the system is powerless without them.
raising the minimum wage and taxes on the ultra-wealthy are the bare minimum. universal healthcare and the complete restructuring of the healthcare economic system is next. continue those regulations until the corporations’ price gouging and predatory tactics are eradicated in every industry. pull the united states military out of goddamn everything, and cut all their ties to local police organizations. cut their budgets and redirect it to improving national infrastructure, as well as the infrastructure and livelihoods of those countries and peoples we plundered. eradicate ice and use the budget to set up universal basic housing and income, available to all persons residing in the us, documented and undocumented. reinforce the fuck out of social security. build up our communities and the people that make them up rather than imposing restrictions meant to make them ‘prove’ their worth.
stop taking fucking advantage of each other.
#chappell roan#grammys#anti capitalism#socialism#bootlickers smell#immigration#abolish ice#free palestine
6 notes
·
View notes
Text
On February 10, employees at the Department of Housing and Urban Development (HUD) received an email asking them to list every contract at the bureau and note whether or not it was “critical” to the agency, as well as whether it contained any DEI components. This email was signed by Scott Langmack, who identified himself as a senior adviser to the so-called Department of Government Efficiency (DOGE). Langmack, according to his LinkedIn, already has another job: He’s the chief operating officer of Kukun, a property technology company that is, according to its website, “on a long-term mission to aggregate the hardest to find data.”
As is the case with other DOGE operatives—Tom Krause, for example, is performing the duties of the fiscal assistant secretary at the Treasury while holding down a day job as a software CEO at a company with millions in contracts with the Treasury—this could potentially create a conflict of interest, especially given a specific aspect of his role: According to sources and government documents reviewed by WIRED, Langmack has application-level access to some of the most critical and sensitive systems inside HUD, one of which contains records mapping billions of dollars in expenditures.
Another DOGE operative WIRED has identified is Michael Mirski, who works for TCC Management, a Michigan-based company that owns and operates mobile home parks across the US, and graduated from the Wharton School in 2014. (In a story he wrote for the school’s website, he asserted that the most important thing he learned there was to “Develop the infrastructure to collect data.”) According to the documents, he has write privileges on—meaning he can input overall changes to—a system that controls who has access to HUD systems.
Between them, records reviewed by WIRED show, the DOGE operatives have access to five different HUD systems. According to a HUD source with direct knowledge, this gives the DOGE operatives access to vast troves of data. These range from the individual identities of every single federal public housing voucher holder in the US, along with their financial information, to information on the hospitals, nursing homes, multifamily housing, and senior living facilities that HUD helps finance, as well as data on everything from homelessness rates to environmental and health hazards to federally insured mortgages.
Put together, experts and HUD sources say, all of this could give someone with access unique insight into the US real estate market.
Kukun did not respond to requests for comment about whether Langmack is drawing a salary while working at HUD or how long he will be with the department. A woman who answered the phone at TCC Management headquarters in Michigan but did not identify herself said Mirksi was "on leave until July." In response to a request for comment about Langmack’s access to systems, HUD spokesperson Kasey Lovett said, “DOGE and HUD are working as a team; to insinuate anything else is false. To further illustrate this unified mission, the secretary established a HUD DOGE taskforce.” In response to specific questions about Mirski’s access to systems and background and qualifications, she said, “We have not—and will not—comment on individual personnel. We are focused on serving the American people and working as one team.”
The property technology, or proptech, market covers a wide range of companies offering products and services meant to, for example, automate tenant-landlord interactions, or expedite the home purchasing process. Kukun focuses on helping homeowners and real estate investors assess the return on investment they’d get from renovating their properties and on predictive analytics that model where property values will rise in the future.
Doing this kind of estimation requires the use of what’s called an automated valuation model (AVM), a machine-learning model that predicts the prices or rents of certain properties. In April 2024, Kukun was one of eight companies selected to receive support from REACH, an accelerator run by the venture capital arm of the National Association of Realtors (NAR). Last year NAR agreed to a settlement with Missouri homebuyers, who alleged that realtor fees and certain listing requirements were anticompetitive.
“If you can better predict than others how a certain neighborhood will develop, you can invest in that market,” says Fabian Braesemann, a researcher at the Oxford Internet Institute. Doing so requires data, access to which can make any machine-learning model more accurate and more monetizable. This is the crux of the potential conflict of interest: While it is unclear how Langmack and Mirski are using or interpreting it in their roles at HUD, what is clear is that they have access to a wide range of sensitive data.
According to employees at HUD who spoke to WIRED on the condition of anonymity, there is currently a six-person DOGE team operating within the department. Four members are HUD employees whose tenures predate the current administration and have been assigned to the group; the others are Mirski and Langmack. The records reviewed by WIRED show that Mirski has been given read and write access to three different HUD systems, as well as read-only access to two more, while Langmack has been given read and write access to two of HUD’s core systems.
A positive, from one source’s perspective, is the fact that the DOGE operatives have been given application-level access to the systems, rather than direct access to the databases themselves. In theory, this means that they can only interact with the data through user interfaces, rather than having direct access to the server, which could allow them to execute queries directly on the database or make unrestricted or irreparable changes. However, this source still sees dangers inherent in granting this level of access.
“There are probably a dozen-plus ways that [application-level] read/write access to WASS or LOCCS could be translated into the entire databases being exfiltrated,” they said. There is no specific reason to think that DOGE operatives have inappropriately moved data—but even the possibility cuts against standard security protocols that HUD sources say are typically in place.
LOCCS, or Line of Credit Control System, is the first system to which both DOGE operatives within HUD, according to the records reviewed by WIRED, have both read and write access. Essentially HUD’s banking system, LOCCS “handles disbursement and cash management for the majority of HUD grant programs,” according to a user guide. Billions of dollars flow through the system every year, funding everything from public housing to disaster relief—such as rebuilding from the recent LA wildfires—to food security programs and rent payments.
The current balance in the LOCCS system, according to a record reviewed by WIRED, is over $100 billion—money Congress has approved for HUD projects but which has yet to be drawn down. Much of this money has been earmarked to cover disaster assistance and community development work, a source at the agency says.
Normally, those who have access to LOCCS require additional processing and approvals to access the system, and most only have “read” access, department employees say.
“Read/write is used for executing contracts and grants on the LOCCS side,” says one person. “It normally has strict banking procedures around doing anything with funds. For instance, you usually need at least two people to approve any decisions—same as you would with bank tellers in a physical bank.”
The second system to which documents indicate both DOGE operatives at HUD have both read and write access is the HUD Central Accounting and Program System (HUDCAPS), an “integrated management system for Section 8 programs under the jurisdiction of the Office of Public and Indian Housing,” according to HUD. (Section 8 is a federal program administered through local housing agencies that provides rental assistance, in the form of vouchers, to millions of lower-income families.) This system was a precursor to LOCCS and is currently being phased out, but it is still being used to process the payment of housing vouchers and contains huge amounts of personal information.
There are currently 2.3 million families in receipt of housing vouchers in the US, according to HUD’s own data, but the HUDCAPS database contains information on significantly more individuals because historical data is retained, says a source familiar with the system. People applying for HUD programs like housing vouchers have to submit sensitive personal information, including medical records and personal narratives.
“People entrust these stories to HUD,” the source says. “It’s not data in these systems, it’s operational trust.”
WASS, or the Web Access Security Subsystem, is the third system to which DOGE has both read and write access, though only Mirski has access to this system according to documents reviewed by WIRED. It’s used to grant permissions to other HUD systems. “Most of the functionality in WASS consists of looking up information stored in various tables to tell the security subsystem who you are, where you can go, and what you can do when you get there,” a user manual says.
“WASS is an application for provisioning rights to most if not all other HUD systems,” says a HUD source familiar with the systems who is shocked by Mirski’s level of access, because normally HUD employees don’t have read access, let alone write access. “WASS is the system for setting permissions for all of the other systems.”
In addition to these three systems, documents show that Mirski has read-only access to two others. One, the Integrated Disbursement and Information System (IDIS), is a nationwide database that tracks all HUD programs underway across the country. (“IDIS has confidential data about hidden locations of domestic violence shelters,” a HUD source says, “so even read access in there is horrible.”) The other is the Financial Assessment of Public Housing (FASS-PH), a database designed to “measure the financial condition of public housing agencies and assess their ability to provide safe and decent housing,” according to HUD’s website.
All of this is significant because, in addition to the potential for privacy violations, knowing what is in the records, or even having access to them, presents a serious potential conflict of interest.
“There are often bids to contract any development projects,” says Erin McElroy, an assistant professor at the University of Washington. “I can imagine having insider information definitely benefiting the private market, or those who will move back into the private market,” she alleges.
HUD has an oversight role in the mobile home space, the area on which TCC Management, which appears to have recently wiped its website, focuses. "It’s been a growing area of HUD’s work and focus over the past few decades," says one source there; this includes setting building standards, inspecting factories, and taking in complaints. This presents another potential conflict of interest.
Braesemann says it’s not just the insider access to information and data that could be a potential problem, but that people coming from the private sector may not understand the point of HUD programs. Something like Section 8 housing, he notes, could be perceived as not working in alignment with market forces—“Because there might be higher real estate value, these people should be displaced and go somewhere else”—even though its purpose is specifically to buffer against the market.
Like other government agencies, HUD is facing mass purges of its workforce. NPR has reported that 84 percent of the staff of the Office of Community Planning and Development, which supports homeless people, faces termination, while the president of a union representing HUD workers has estimated that up to half the workforce could be cut The chapter on housing policy in Project 2025—the right-wing playbook to remake the federal government that the Trump administration appears to be following—outlines plans to massively scale back HUD programs like public housing, housing assistance vouchers, and first-time home buyer assistance.
16 notes
·
View notes
Text
Tech So Bad It Sounds Like The Reviewers Are Just Plain Depressed
12 Days of Aniblogging 2024, Day 8
I really do try to stay away from armchair cultural criticism, especially when it's this far removed from my weaboo wheelhouse, but this one’s been eating away at me for the entire year. What are we doing here?

2024 has been full of downright bad consumer tech! The Apple Vision Pro, the Rabbit and Humane AI pins, the PS5 Pro… those are just the big ones, and that’s not even getting started on vaporware like Horizon Worlds and Microsoft’s Copilot+ PC initiative. Sure, there are Juiceros every year, but this recent batch of flops feels indicative of a larger trend, which is shipping products that are both overengineered and conceptually half-baked. Of course, there’s plenty of decent tech coming out too – Apple’s recent laptops and desktops have been strong and competitively priced, at least the base models. The Steam Deck created a whole new product category that seems to be thriving. And electric cars… exist, which is better than nothing. But it’s been much more fun to read about of the bad stuff, of course. These days it feels like most of the tech reviews I read these days have the journalists asking “what’s the point?” halfway through, or asserting in advance that it will fail, like this useless product with a bad value proposition is prompting an existential crisis for them. Maybe it is!

yeah yeah journalists don't write their own headlines. I can assure you that the article content carries the same tone for these though.
What did a negative tech review look like before the 2020s? Maybe there wasn’t one, really. The 2000s and the 2010s were drenched in techno-optimism. Even if skepticism towards social media emerged over time, hardware itself was generally received well, mixed at worst, because journalists were happy to extrapolate out what a product and its platform could do. Nowadays, everyone takes everything at face value! As they should –the things we buy rarely get meaningfully better over time, and the support window for flops is getting shorter and shorter with each passing year. On the games side of things, look how quickly Concord ended! With that out of the way, I’m going to start zeroing in on the hardware I saw a “why does this exist” type review for this year.
The Apple Vision Pro
People have been burnt time and time again by nearly every VR headset ecosystem to release (other than mayyybe Oculus, but Facebook’s tendrils sinking in don’t feel great either). The PSVR was a mild success at best and the PSVR2 was an expensive and unmitigated disaster that lost support in a matter of months. Meanwhile, the Valve Index couldn’t cut it with its price, and Microsoft actively blew up their own HoloLens infrastructure earlier this year. It’s at this point it's clear that VR is a niche, and one that’s expensive to develop for and profit off of. Surely Apple will save us!

completely isolate yourself from your family for the low, low price of multiple paychecks
With most of the competition focusing on gaming, Apple attempted a blue ocean strategy with the Vision Pro by instead making their target audience… nobody! It’s hard to tell what anyone was ever supposed to do with these things, and reading long-form reviews, it became very clear that the reviewers were trying to come up with viable use-cases and largely failing, because it’s just not very practical tech. There’s no physical input devices, so you’re instead using mix of hand-tracking, eye-tracking, and voice commands to control the thing. That’s pretty cool, but it means that the one niche that VR has been proven in, gaming, is effectively impossible. Things like office software can also be hard to use without a keyboard and mouse, and even when there’s tailor-made headset applications for existing software, it’s still usually not better than just doing it on your desktop!
The tech is real, and that’s the saddest part. Looking at teardowns, I fully believe that the hardware had to cost multiple thousands of dollars to break even, and as someone who suffers from VR motion sickness, I’d be really curious to see if all the stabilization tech from their extra onboard chips helps with that as much as the press releases claim. It’s like a more drastic version of the iPad problem, where the hardware is amazing on paper, but interfacing limits with the form factor itself combined with a subpar operating system mean that you can’t actually do as much as you’d hope to with all that power.
Of course, the Vision Pro is also full of prototype hacks and hard design problems – that battery pack is a nightmare! If it’s a productivity device, how are you supposed to share content with other people when the headset has to be custom-fit every time and there’s only one profile? Apple still has no good answer. That leaves the only available niche for this device as white-collar productivity done in isolation, and most people fundamentally do not live in that world. It feels lonely and dystopic, even.
If I had to guess what happened, the VR division at Apple was working on this for the better part of a decade, and facing headwinds, Apple decided to cut their losses and force them to deliver a doomed product. There’s a potent business fantasy of a bad version 1.0 leading to a successful 2.0 and beyond, but Apple has not pulled that off any time in the twenty-first century. It’s either a success or it is a proven failure, and this is so, so, obviously the latter. I do hope that the stabilization tech makes it into other headsets eventually though, so that I can play Blade and Sorcery at my friend’s house without throwing up. Everyone else, please copy Apple’s homework or steal their patents, preferably to the tune of under $3500.
Rabbit R1 and Humane AI Pins
The current AI paradigm has been around for two years now, and since we've all heard way too many arguments already, I will try to keep my own takes brief. The LLM results we have right now are real (even if everyone is trying to dress them up as superintelligent snake oil when they’re just cool computer synthesis), but from everything I read, it seems like the era of drastic improvement is over. It would take exponentially more text and images and video than we already have to get more linear improvements, and a good chunk of the world has already been scraped, and the lawsuits are already pouring in, further slowing down data ingestion. The tech is slowing down, and the industry won’t be able to grow its way out of the hard social problems it’s invoked. If there are gains to be made, it's in more fine-tuned and curated LLMs, and that's far harder work than most of these companies want to get up to right now.
With that out of the way, are you interested in wearing an LLM on your shirt?

The video that notoriously tanked a company. Of course, now I'm also supposed to make fun of this guy for using b-roll of himself speeding in a school zone . Nobody wins.
Not one, but two separate startups pushed this idea to market this year. Humane’s AI pin launched for seven hundred dollars plus a twenty-five dollars per month subscription, all for the privilege of getting to ask a little square on your chest questions and getting GPT answers spoken back to you. But what about like… ChatGPT’s own phone app? Or hell, even Siri! Apple and Android’s voice assistants are both are over a decade old– do you really have that many ungoogleable queries? And specifically, ones that voice responses make the most sense for, and not text? To make things worse, this thing has serious overheating issues and a battery that can’t even last a day. The Rabbit R1 at least has a cute design, and actually has a screen, and is much cheaper, but it requires a data tether to your phone, so like…why not just use your phone. Reverse-engineering has confirmed that its app can just run on a normal Android phone, so there’s really nothing special other than the little orange square that it’s hosted in.

Why would you even try to roll out a product as doomed as these, instead of just going bankrupt and pocketing a year or two of salary like most startups? The AI boom, of course! After the NFT hype cycle, everyone really did convince themselves that you can just fail upwards with no real limit. Unfortunately, people have higher standards for hardware than PNG transaction platforms, as they get far more upset when they’re left physically holding the bag. I’ve been watching Deep Space 9 recently and have to ask, are these companies trying to capture the fantasy of Star Trek comms badges? Because if so, they should honestly lean more into it. It wouldn't be any more functional of a product, but if there’s one thing nerds always love, it’s themed garbage.

welp
The PS5 Pro
This one just launched a bit ago for the holiday season. It makes some sense on paper – most PS5 games offer a choice between a performance and a fidelity mode, so why not just make a version strong enough that it can get the benefits of both? Great! That’ll be seven hundred dollars.
Okay, $700 doesn’t sound as insane in the context of that Humane pin I was just talking about. But it’s $200 more than the PS5 at launch, and it doesn’t even come with a disc drive unless you want to fork over another $80. The past few generations of gaming have been defined by heavily subsidized console prices with the goal of roping gamers into more lucrative ecosystems, but Sony here seems to be testing the waters for an unsubsidized era.

I've heard the external disc drive install process is surprisingly user-friendly, but at this price point they should have included a little automaton who does it for you
If you can stomach PC gaming, at that price you’re halfway there to buying something that could trounce a PS5 Pro, plus a monitor close enough to your face that you might actually notice the 4K improvements. There are also only a couple of games per year being produced at high enough fidelity for there to be any noticeable quality improvements. The returns are diminishing and the AAA landscape is narrowing, and console upgrades like these only hasten the industry’s spiraling. Is all this sustainable from a development perspective? I don’t know. If Nintendo announced a Mario Odyssey sequel for the Switch 2, I’d buy it at launch regardless of the graphics, and my PS3 can play Demon's Souls and my anime blu-rays just fine. So I’m well aware that I’m not the target audience for stuff like the PS5 Pro, but I think it's going to become harder and harder to compel that audience going forward.
_
The end of the low interest rates in US has drastically changed the underpinnings of its tech industry, and I think every one of these bad product launches can be traced back here one way or another. The era of running flashy ventures at a loss for years in order to corner the market is profoundly over, unless you’ve got Thiel blood money or a GPT transformer, and even then. This, combined with the end of quarantine-era user habits, has left many companies to repeatedly go all in on hype cycles like blockchain and the metaverse and AI, pretending like the last one never happened every time. This trend-chasing means, that depending on each company’s circumstances, they need to either spin something up quick, reroute an existing prototype, or risk delivering laughably late. You need a product and you need it fast. And rushed tech is always going to have load-bearing and stupid problems, no matter how long the initial development time was. Everyone loses, especially the saps who actually believe in the sales pitches enough to buy these things. And those poor, poor tech journalists who have to review it all are being consumed with eldritch madness watching this all unfold. Hey, at least they’re not trying to simp for Microsoft Copilot!

Hopefully, this particular era of tech ends sooner rather than later, so that I don’t feel compelled to do another essay of this type. If I were more of an idealist or a doofus I’d be dreaming of a serious anticonsumerist movement and/or Xi Jinping liberating us all, but unfortunately I’m of the belief that we’re doomed to dumbass gizmos destined for the landfill until the end of the silicon era.
6 notes
·
View notes
Text
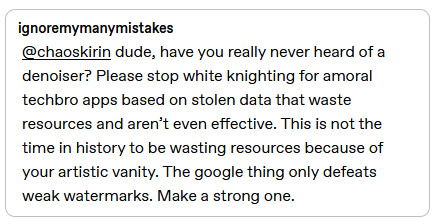
I blocked this guy for spreading misinformation, but I want to address the points they made so people don't buy into this shit.
"Have you really never heard of a denoiser?" Glaze and Nightshade cannot be defeated by denoisers. Please see the paper I link in #2. This point is amazingly easy to debunk, and I'm not sure why people are still championing it. Both programs work by changing what the software "sees." Denoising can blur these artifacts, but it does not fundamentally get rid of them.
"White knighting for amoral techbro apps." This was a very early techbro attack on Glaze to try to convince people it was another way to steal data. As I said in an earlier post, it does use a dataset to enable it to add artifacts to your work. It is essentially using AI against itself, and it is effective. There's a whole peer-reviewed paper on how it works. I've posted it before, but if you missed it, you can read it here: https://arxiv.org/abs/2310.13828 (and unlike Generative AI apps, this paper explains exactly how the technology works.)
"Wasting resources." The point is to make the machines unusable, which ultimately will reduce the stress on our infrastructure. If the datasets no longer work, the use of them decreases. Unfortunately, the inability for people to adequately protect their work has led to massive electricity-wasting farms for generative AI, just like what happened with NFTs and cryptocurrency. If enough people inject unusable data in the the systems, the systems themselves become unusable, and the use decreases.
"My artistic vanity." I'm not a good artist. But my artwork HAS been scraped and used. I don't know why I have to keep saying this to make my anger and pain valid, but a few months back, all my artwork was revenge-scraped and stuffed into Midjourney. The person who did it also stripped my name from it, so I am not even able to HOPE to have it removed. I have nothing left to lose. I want to make those motherfuckers pay.
"The google thing only defeats weak watermarks." This is true. But a "strong" watermark must be completely different on each work you post, and also must cover most of the work. This is easily researched. I don't know about you, but I don't have time to make a new watermark on each piece I post, and I also don't want it to cover most of the artwork. Just so you know, the watermark detector works by looking for the same pattern on multiple works by the same person. If you use the same watermark on each piece, it doesn't matter how strong you think it is. It's removable. If you have the time to do it, then yes, this is effective. But it needs to be complex and different on each piece.
Next, I've seen a couple posts going around today stating that you can't even have an account on Glaze because they're closed.
They're not. But to prevent techbros from making accounts, you have to message the team so they can make sure you aren't using AI in your work. The instructions are here: https://glaze.cs.uchicago.edu/webinvite.html
Nightshade is not available on the web yet, but Glaze is. Nightshade will be soon, and they are planning a combo web app that will both Glaze and Nightshade your work.
In the meantime, if you want someone to Nightshade your work for you, please let me know. I have offered this before, and I will offer it again. Email me at [email protected] with your artwork, and let me know you'd like me to Nightshade it for you. There will always be some artifacts, but I will work with you until you are happy with the result.
Lastly, I know my messages are working because I keep getting people spreading misinformation that these things don't work. Please know that I have done the research, I do have a personal stake in this (because hundreds of my pieces are part of Midjourney now) and I am only posting this because I truly believe this is the way to fight back against plagiarism machines.
I don't know why people are so angry when I post about them. I know people don't all have access, which is why I'm offering my resources to help. I know this is a new technology, which is why I read through the boring scientific paper myself so I can validate the claims.
This is the last post I'll make on the matter. If you want to ask questions, fine, but I don't really have the mental capacity to argue with everyone anymore, and I'm not going to.
8 notes
·
View notes
Text
Zero-Day CVE-2024-24919 Discovered in Check Point's VPN Software

Cybersecurity software vendor Check Point has issued a critical warning to customers, urging them to update their software immediately due to a zero-day vulnerability in their Virtual Private Network (VPN) products that is actively being exploited by attackers. The vulnerability, assigned CVE-2024-24919 and a CVSS score of 8.6 (high severity), affects Check Point's CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark Appliances.
VPN Exploit Targets Older Local Accounts
According to Check Point's advisory, the vulnerability involves attackers "using old VPN local accounts relying on unrecommended password-only authentication method." The company strongly recommends against relying solely on password authentication for logging into network infrastructure, emphasizing that it is an unfavorable method for ensuring the highest levels of cybersecurity.
Potential Impact and Lateral Movement
If successfully exploited, the vulnerability could grant an attacker access to sensitive information on a security gateway, as well as enable lateral movement within the network with domain administrator privileges. Threat intelligence firm Mnemonic, which was contacted by Check Point regarding the vulnerability, has confirmed that the exploit allows threat actors to retrieve all files on the local filesystem, including password hashes for local accounts, SSH keys, certificates, and other critical files.
Patches Available and Recommended Mitigations
Check Point has released patches for all affected systems, and customers are strongly advised to apply the updates as soon as possible. In addition to installing the patches, Check Point recommends hardening VPN posture by implementing multi-factor authentication (MFA) and reviewing and removing unnecessary local VPN accounts. For any necessary local accounts, additional authentication measures should be added to mitigate the risk of exploitation. The actively exploited zero-day vulnerability in Check Point's VPN products underscores the importance of promptly applying security updates and following best practices. While implementing MFA can be a hassle, the consequences of a data breach or network compromise can be far more severe. Organizations using affected Check Point products are urged to take immediate action to secure their systems and protect their valuable data and infrastructure. Read the full article
4 notes
·
View notes
Text
Optimizing Business Operations with Advanced Machine Learning Services
Machine learning has gained popularity in recent years thanks to the adoption of the technology. On the other hand, traditional machine learning necessitates managing data pipelines, robust server maintenance, and the creation of a model for machine learning from scratch, among other technical infrastructure management tasks. Many of these processes are automated by machine learning service which enables businesses to use a platform much more quickly.
What do you understand of Machine learning?
Deep learning and neural networks applied to data are examples of machine learning, a branch of artificial intelligence focused on data-driven learning. It begins with a dataset and gains the ability to extract relevant data from it.
Machine learning technologies facilitate computer vision, speech recognition, face identification, predictive analytics, and more. They also make regression more accurate.
For what purpose is it used?
Many use cases, such as churn avoidance and support ticket categorization make use of MLaaS. The vital thing about MLaaS is it makes it possible to delegate machine learning's laborious tasks. This implies that you won't need to install software, configure servers, maintain infrastructure, and other related tasks. All you have to do is choose the column to be predicted, connect the pertinent training data, and let the software do its magic.
Natural Language Interpretation
By examining social media postings and the tone of consumer reviews, natural language processing aids businesses in better understanding their clientele. the ml services enable them to make more informed choices about selling their goods and services, including providing automated help or highlighting superior substitutes. Machine learning can categorize incoming customer inquiries into distinct groups, enabling businesses to allocate their resources and time.
Predicting
Another use of machine learning is forecasting, which allows businesses to project future occurrences based on existing data. For example, businesses that need to estimate the costs of their goods, services, or clients might utilize MLaaS for cost modelling.
Data Investigation
Investigating variables, examining correlations between variables, and displaying associations are all part of data exploration. Businesses may generate informed suggestions and contextualize vital data using machine learning.
Data Inconsistency
Another crucial component of machine learning is anomaly detection, which finds anomalous occurrences like fraud. This technology is especially helpful for businesses that lack the means or know-how to create their own systems for identifying anomalies.
Examining And Comprehending Datasets
Machine learning provides an alternative to manual dataset searching and comprehension by converting text searches into SQL queries using algorithms trained on millions of samples. Regression analysis use to determine the correlations between variables, such as those affecting sales and customer satisfaction from various product attributes or advertising channels.
Recognition Of Images
One area of machine learning that is very useful for mobile apps, security, and healthcare is image recognition. Businesses utilize recommendation engines to promote music or goods to consumers. While some companies have used picture recognition to create lucrative mobile applications.
Your understanding of AI will drastically shift. They used to believe that AI was only beyond the financial reach of large corporations. However, thanks to services anyone may now use this technology.
2 notes
·
View notes
Text
Small Business Website Hosting and Management Services
Running a small business in today’s digital age requires having a strong online presence. One crucial aspect of establishing that presence is having a well-designed and functional website. However, building and maintaining a website can be a daunting task, especially for small business owners who may not have the technical expertise or resources to handle it themselves. That’s where small business website hosting and management services come into play.
What is Small Business Website Hosting?
Website hosting is the process of storing and making your website accessible on the internet. Small business website hosting services provide the infrastructure and technology needed to keep your website up and running smoothly. They offer server space, domain registration, email accounts, and other essential features to ensure your website is available to visitors around the clock.
Choosing the right hosting service for your small business is crucial. Factors to consider include reliability, speed, security, customer support, scalability, and affordability. Small business website hosting services understand the unique needs of small enterprises and offer plans tailored to their requirements.
Benefits of Small Business Website Hosting Services
1. Technical Expertise: Small business website hosting services have a team of professionals who possess the necessary technical skills and experience to handle website management effectively. They take care of tasks such as server maintenance, software updates, and security patches, allowing you to focus on running your business.
2. Reliability and Uptime: Small business hosting services ensure that your website is always available to visitors. They have robust infrastructure and backup systems in place to minimize downtime and provide a reliable online experience for your customers.
3. Scalability: As your small business grows, so does your website’s needs. Hosting services offer scalable solutions that can accommodate increased traffic, storage, and functionality requirements. This flexibility allows your website to expand alongside your business without disruptions.
4. Security: Website security is of paramount importance in today’s digital landscape. Small business website hosting services implement robust security measures to protect your website from hacking attempts, malware, and other cyber threats. They often provide SSL certificates, regular backups, and firewall protection to safeguard your data and your customers’ information.
5. Support: Small business hosting services offer dedicated customer support to assist you with any technical issues or questions you may have. This ensures that you have reliable assistance whenever you encounter challenges with your website.
Website Management Services
In addition to website hosting, many small business hosting services also offer website management services. These services take care of the day-to-day tasks involved in maintaining and updating your website, freeing up your time to focus on your core business activities.
Website management services may include:
– Content updates and modifications
– Regular backups and data protection
– Performance monitoring and optimization
– Search engine optimization (SEO)
– Design and layout enhancements
– Integration of new features and functionality
– E-commerce solutions
By outsourcing website management to professionals, small business owners can ensure that their website remains current, engaging, and fully functional without the need for in-house technical expertise.
Choosing the Right Small Business Website Hosting and Management Service
When selecting a small business website hosting and management service, it’s essential to consider your specific needs and goals. Evaluate factors such as pricing, features, customer reviews, and the provider’s reputation in the industry.
Additionally, assess the scalability of the service to ensure it can grow with your business. Look for a service that offers reliable customer support and has a track record of high uptime and security. Ultimately, the right service will empower your small business to establish a strong online presence and thrive in the digital marketplace.
In conclusion, small business website hosting and management services play a vital role in helping small enterprises establish and maintain a robust online presence. By providing reliable hosting, technical expertise, security, and website management solutions, these services enable small business owners to focus on what they do best while leaving the website-related tasks to professionals. With the right hosting and management service, small businesses can compete effectively in the digital realm and reach their target audience with a compelling and functional website.

source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
18 notes
·
View notes