#Implementing Strong Authentication Protocols
Explore tagged Tumblr posts
Text
Safeguarding Data Privacy and Security in Virtual Work Environments in Ernakulam
Introduction
In today’s increasingly digital world, virtual work environments have become the norm for many organizations. While these platforms offer flexibility and efficiency, they also bring significant challenges in maintaining data privacy and security. This blog post explores essential strategies to protect sensitive information in virtual work settings and ensure compliance with data protection regulations.
1. Understanding the Risks in Virtual Work Environments: Virtual work environments, while convenient, are vulnerable to various cyber threats, including data breaches, phishing attacks, and unauthorized access. Employees may work from different locations, often using personal devices and unsecured networks, which increases the risk of data leaks. Understanding these risks is the first step toward building a secure virtual workspace.
2. Implementing Strong Authentication Protocols: One of the most effective ways to enhance security in virtual work environments is by implementing robust authentication protocols. Multi-factor authentication (MFA) should be mandatory for accessing company resources. MFA adds an extra layer of security by requiring users to provide two or more verification factors, reducing the likelihood of unauthorized access.
3. Securing Communication Channels: Virtual work often relies on communication tools such as video conferencing, instant messaging, and email. To protect sensitive information, it’s crucial to use encrypted communication channels. End-to-end encryption ensures that only the intended recipients can access the data, safeguarding it from eavesdropping or interception by malicious actors.
4. Regularly Updating Software and Systems: Outdated software and systems are common targets for cyberattacks. Ensure that all software, including operating systems, applications, and security tools, is regularly updated. Patching vulnerabilities as soon as updates are available is critical to prevent exploitation by cybercriminals.
5. Educating Employees on Cybersecurity Best Practices: Human error is a leading cause of data breaches. Educating employees on cybersecurity best practices is essential in creating a secure virtual work environment. Regular training sessions should cover topics such as recognizing phishing attempts, creating strong passwords, and securely handling sensitive information.
6. Implementing Data Encryption: Encrypting data both at rest and in transit is a fundamental security measure. Data encryption converts information into a secure format that can only be read by someone with the decryption key. This ensures that even if data is intercepted, it remains unreadable to unauthorized users.
7. Monitoring and Auditing Access to Data: Regular monitoring and auditing of data access are crucial in detecting suspicious activity. Organizations should implement logging mechanisms to track who accesses data and when. Any unusual patterns or unauthorized access attempts should be promptly investigated to mitigate potential threats.
8. Establishing Clear Data Handling Policies: Clear data handling policies should be established and communicated to all employees. These policies should outline the procedures for storing, sharing, and disposing of sensitive data. Employees should be aware of the consequences of non-compliance, emphasizing the importance of adhering to the guidelines.
9. Ensuring Compliance with Data Protection Regulations: Organizations must comply with data protection regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Understanding and implementing the requirements of these regulations is essential in avoiding legal penalties and maintaining customer trust.
10. Leveraging Secure Cloud Services: Many organizations rely on cloud services to store and manage data in virtual work environments. It’s important to choose cloud providers that prioritize security and offer features such as data encryption, regular backups, and compliance with industry standards. Additionally, access to cloud services should be tightly controlled and monitored.
Conclusion
As virtual work environments continue to evolve, so do the challenges of maintaining data privacy and security. By implementing the strategies outlined in this post, organizations can create a secure virtual workspace that protects sensitive information and minimizes the risk of data breaches. Prioritizing data security not only safeguards the organization’s assets but also builds trust with clients and stakeholders in an increasingly digital world.
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Understanding Encryption: How Signal & Telegram Ensure Secure Communication

Signal vs. Telegram: A Comparative Analysis

Signal vs Telegram
Security Features Comparison
Signal:
Encryption: Uses the Signal Protocol for strong E2EE across all communications.
Metadata Protection: User privacy is protected because minimum metadata is collected.
Open Source: Code publicly available for scrutiny, anyone can download and inspect the source code to verify the claims.
Telegram:
Encryption: Telegram uses MTProto for encryption, it also uses E2EE but it is limited to Secret Chats only.
Cloud Storage: Stores regular chat data in the cloud, which can be a potential security risk.
Customization: Offers more features and customization options but at the potential cost of security.
Usability and Performance Comparison
Signal:
User Interface: Simple and intuitive, focused on secure communication.
Performance: Privacy is prioritized over performance, the main focus is on minimizing the data collection.
Cross-Platform Support: It is also available on multiple platforms. Like Android, iOS, and desktop.
Telegram:
User Interface: Numerous customization options for its audience, thus making it feature rich for its intended audience.
Performance: Generally fast and responsive, but security features may be less robust.
Cross-Platform Support: It is also available on multiple platforms, with seamless synchronization across devices because all the data is stored on Telegram cloud.
Privacy Policies and Data Handling
Signal:
Privacy Policy: Signal’s privacy policy is straightforward, it focuses on minimal data collection and strong user privacy. Because it's an independent non-profit company.
Data Handling: Signal does not store any message data on its servers and most of the data remains on the user's own device thus user privacy is prioritized over anything.
Telegram:
Privacy Policy: Telegram stores messages on its servers, which raises concerns about privacy, because theoretically the data can be accessed by the service provider.
Data Handling: While Telegram offers secure end to end encrypted options like Secret Chats, its regular chats are still stored on its servers, potentially making them accessible to Telegram or third parties.
Designing a Solution for Secure Communication
Key Components of a Secure Communication System
Designing a secure communication system involves several key components:
Strong Encryption: The system should employ adequate encryption standards (e.g. AES, RSA ) when data is being transmitted or when stored.
End-to-End Encryption: E2EE guarantees that attackers cannot read any of the communication, meaning that the intended recipients are the only ones who have access to it.
Authentication: It is necessary to identify the users using secure means such as Two Factor Authentication (2FA) to restrict unauthorized access.
Key Management: The system should incorporate safe procedures for creating, storing and sharing encryption keys.
Data Integrity: Some standard mechanisms must be followed in order to ensure that the data is not altered during its transmission; For instance : digital signatures or hashing.
User Education: To ensure the best performance and security of the system, users should be informed about security and the appropriate use of the system such practices.
Best Practices for Implementing Encryption
To implement encryption effectively, consider the following best practices:
Use Proven Algorithms: Do not implement proprietary solutions that are untested, because these algorithms are the ones which haven't gone through a number of testing phases by the cryptographic community. On the other hand, use well-established algorithms that are already known and tested for use – such as AES and RSA.
Keep Software Updated: Software and encryption guidelines must be frequently updated because these technologies get out of date quickly and are usually found with newly discovered vulnerabilities.
Implement Perfect Forward Secrecy (PFS): PFS ensures that if one of the encryption keys is compromised then the past communications must remain secure, After every session a new key must be generated.
Data must be Encrypted at All Stages: Ensure that the user data is encrypted every-time, during transit as well as at rest – To protect user data from interception and unauthorized access.
Use Strong Passwords and 2FA: Encourage users to use strong & unique passwords that can not be guessed so easily. Also, motivate users to enable the two-factor authentication option to protect their accounts and have an extra layer of security.
User Experience and Security Trade-offs
While security is important, but it's also important to take care of the user experience when designing a secure communication system. If your security measures are overly complex then users might face difficulties in adopting the system or they might make mistakes in desperation which might compromise security.
To balance security and usability, developers should:

Balancing Security And Usability
Facilitate Key Management: Introduce automated key generation and exchange mechanisms in order to lessen user's overhead
Help Users: Ensure that simple and effective directions are provided in relation to using security aspects.
Provide Control: Let the users say to what degree they want to secure themselves e.g., if they want to make use of E2EE or not.
Track and Change: Always stay alert and hands-on in the system monitoring for security breaches as well as for users, and where there is an issue, do something about it and change
Challenges and Limitations of Encryption Potential Weaknesses in Encryption
Encryption is without a doubt one of the most effective ways of safeguarding that communications are secured. However, it too has its drawbacks and weaknesses that it is prone to:
Key Management: Managing and ensuring the safety of the encryption keys is one of the most painful heads in encryption that one has to bear. When keys get lost or fall into unsafe hands, the encrypted information is also at risk.
Vulnerabilities in Algorithms: As far as encryption is concerned the advanced encryption methods are safe and developed well, but it is not given that vulnerabilities will not pop up over the years. Such vulnerabilities are meant for exploitation by attackers especially where the algorithm in question is not updated as frequently as it should be.
Human Error: The strongest encryption can be undermined by human error. People sometimes use weak usernames and passwords, where they are not supposed to, and or even share their credentials with other persons without considering the consequences.
Backdoors: In some cases, businesses are pressured by Governments or law officials into adding back doors to the encryption software. These backdoors can be exploited by malicious actors if discovered.
Conclusion
Although technology has made it possible to keep in touch with others with minimal effort regardless of their geographical location, the importance of encryption services still persists as it allows us to protect ourselves and our information from external invaders. The development of apps like Signal and Telegram has essentially transformed the aspect of messaging and provided their clients with the best security features covering the use of multiple types of encryption and other means to enhance user privacy. Still, to design a secure communication system, it's not only designing the hardware or software with anti-eavesdropping features, but it factors in the design of systems that relate to the management of keys, communication of the target users, and the trade-off between security and usability.
However, technology will evolve, followed by the issues and the solutions in secure communications. However by keeping up with pace and looking for better ways to protect privacy we can provide people the privacy that they are searching for.
Find Out More
3 notes
·
View notes
Text
The Roadmap to Full Stack Developer Proficiency: A Comprehensive Guide
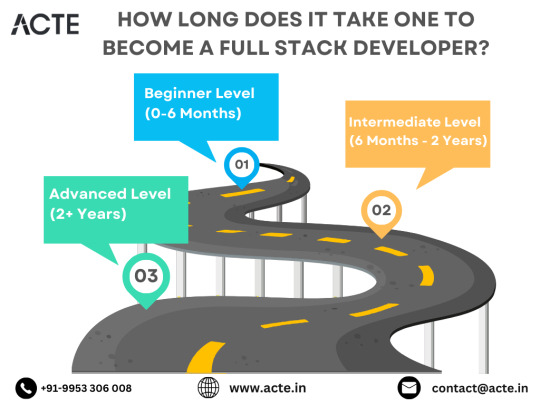
Embarking on the journey to becoming a full stack developer is an exhilarating endeavor filled with growth and challenges. Whether you're taking your first steps or seeking to elevate your skills, understanding the path ahead is crucial. In this detailed roadmap, we'll outline the stages of mastering full stack development, exploring essential milestones, competencies, and strategies to guide you through this enriching career journey.

Beginning the Journey: Novice Phase (0-6 Months)
As a novice, you're entering the realm of programming with a fresh perspective and eagerness to learn. This initial phase sets the groundwork for your progression as a full stack developer.
Grasping Programming Fundamentals:
Your journey commences with grasping the foundational elements of programming languages like HTML, CSS, and JavaScript. These are the cornerstone of web development and are essential for crafting dynamic and interactive web applications.
Familiarizing with Basic Data Structures and Algorithms:
To develop proficiency in programming, understanding fundamental data structures such as arrays, objects, and linked lists, along with algorithms like sorting and searching, is imperative. These concepts form the backbone of problem-solving in software development.
Exploring Essential Web Development Concepts:
During this phase, you'll delve into crucial web development concepts like client-server architecture, HTTP protocol, and the Document Object Model (DOM). Acquiring insights into the underlying mechanisms of web applications lays a strong foundation for tackling more intricate projects.
Advancing Forward: Intermediate Stage (6 Months - 2 Years)
As you progress beyond the basics, you'll transition into the intermediate stage, where you'll deepen your understanding and skills across various facets of full stack development.
Venturing into Backend Development:
In the intermediate stage, you'll venture into backend development, honing your proficiency in server-side languages like Node.js, Python, or Java. Here, you'll learn to construct robust server-side applications, manage data storage and retrieval, and implement authentication and authorization mechanisms.
Mastering Database Management:
A pivotal aspect of backend development is comprehending databases. You'll delve into relational databases like MySQL and PostgreSQL, as well as NoSQL databases like MongoDB. Proficiency in database management systems and design principles enables the creation of scalable and efficient applications.
Exploring Frontend Frameworks and Libraries:
In addition to backend development, you'll deepen your expertise in frontend technologies. You'll explore prominent frameworks and libraries such as React, Angular, or Vue.js, streamlining the creation of interactive and responsive user interfaces.
Learning Version Control with Git:
Version control is indispensable for collaborative software development. During this phase, you'll familiarize yourself with Git, a distributed version control system, to manage your codebase, track changes, and collaborate effectively with fellow developers.
Achieving Mastery: Advanced Phase (2+ Years)
As you ascend in your journey, you'll enter the advanced phase of full stack development, where you'll refine your skills, tackle intricate challenges, and delve into specialized domains of interest.
Designing Scalable Systems:
In the advanced stage, focus shifts to designing scalable systems capable of managing substantial volumes of traffic and data. You'll explore design patterns, scalability methodologies, and cloud computing platforms like AWS, Azure, or Google Cloud.
Embracing DevOps Practices:
DevOps practices play a pivotal role in contemporary software development. You'll delve into continuous integration and continuous deployment (CI/CD) pipelines, infrastructure as code (IaC), and containerization technologies such as Docker and Kubernetes.
Specializing in Niche Areas:
With experience, you may opt to specialize in specific domains of full stack development, whether it's frontend or backend development, mobile app development, or DevOps. Specialization enables you to deepen your expertise and pursue career avenues aligned with your passions and strengths.
Conclusion:
Becoming a proficient full stack developer is a transformative journey that demands dedication, resilience, and perpetual learning. By following the roadmap outlined in this guide and maintaining a curious and adaptable mindset, you'll navigate the complexities and opportunities inherent in the realm of full stack development. Remember, mastery isn't merely about acquiring technical skills but also about fostering collaboration, embracing innovation, and contributing meaningfully to the ever-evolving landscape of technology.
#full stack developer#education#information#full stack web development#front end development#frameworks#web development#backend#full stack developer course#technology
9 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
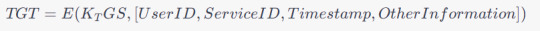
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text
Best 10 Business Strategies for year 2024
In 2024 and beyond, businesses will have to change with the times and adjust their approach based on new and existing market realities. The following are the best 10 business approach that will help companies to prosper in coming year
1. Embrace Sustainability
The days when sustainability was discretionary are long gone. Businesses need to incorporate environmental, social and governance (ESG) values into their business practices. In the same vein, brands can improve brand identity and appeal to environmental advocates by using renewable forms of energy or minimizing their carbon footprints.
Example: a fashion brand can rethink the materials to use organic cotton and recycled for their clothing lines. They can also run a take-back scheme, allowing customers to return old clothes for recycling (not only reducing waste but creating and supporting the circular economy).
2. Leverage AI

AI is revolutionizing business operations. Using AI-fuelled solutions means that you can automate processes, bring in positive customer experiences, and get insights. AI chatbots: AI can be utilized in the form of a conversational entity to support and perform backend operations, as well.
With a bit more specificity, say for example that an AI-powered recommendation engine recommends products to customers based on their browsing history and purchase patterns (as the use case of retail). This helps to increase the sales and improve the shopping experience.
3. Prioritize Cybersecurity
Cybersecurity is of utmost important as more and more business transitions towards digital platforms. Businesses need to part with a more substantial amount of money on advanced protective measures so that they can keep sensitive data private and continue earning consumer trust. Regular security audits and training of employees can reduce these risks.
Example: A financial services firm may implement multi-factor authentication (MFA) for all online transactions, regularly control access to Internet-facing administrative interfaces and service ports as well as the encryption protocols to secure client data from cyberattacks.
4. Optimizing Remote and Hybrid Working Models

Remote / hybrid is the new normal Remote teams force companies to implement effective motivation and management strategies. Collaboration tools and a balanced virtual culture can improve productivity and employee satisfaction.
- Illustration: a Tech company using Asana / Trello etc. for pm to keep remote teams from falling out of balance. They can also organise weekly team-building activities to keep a strong team spirit.
5. Focus on Customer Experience
Retention and growth of the sales follow-through can be tied to high quality customer experiences. Harness data analytics to deepen customer insights and personalize product offers making your marketing campaigns personal: a customer support that is responsive enough can drive a great level of returning customers.
Example – For any e-commerce business, you can take user experience feedback tools to know about how your customers are getting along and make necessary changes. Custom email campaigns and loyalty programs can also be positively associated with customer satisfaction and retention.
6. Digitalization Investment

It is only the beginning of digital transformation which we all know, is key to global competitiveness. For streamlining, companies have to adopt the use advanced technologies such as Blockchain Technology and Internet of Things (IoT) in conjunction with cloud computing.
IoT example : real-time tracking and analytics to optimize supply chain management
7. Enhance Employee Skills
Develop Your Employees: Investing in employee development is key to succeeding as a business. The training is provided for the folks of various industries and so employees can increase their skills that are needed to work in a certain company. Employee performance can be enhanced by providing training programs in future technology skills and soft skills and job satisfaction.
Example: A marketing agency can host webinars or create courses to teach people the latest digital marketing trends and tools This can help to keep employees in the know which results in boosting their skills, making your campaigns successful.
8. Diversify Supply Chains

The ongoing pandemic has exposed the weaknesses of global supply chains. …diversify its supply base and promote the manufacturing of drugs in Nigeria to eliminate total dependence on a single source. In return, this approach increases resilience and reduces exposure to the risks of supply chain interruption.
- E.g., a consumer electronics company can source components from many suppliers in various regions. In so doing, this alleviates avoidable supply chain interruptions during times of political tensions or when disasters hit.
9. Make Decisions Based on Data
A business database is an asset for businesses. By implementing data, they allow you to make decisions based on the data that your analytics tools are providing. For example, sales analysis lets you track trends and better tailor your goods to the market.
Example: A retail chain can use data analytics to find out when a customer buys, and it change their purchasing policies. This can also reduce overstock and stockouts while overall, increasing efficiency.
10. Foster Innovation

Business Growth Innovation is Key A culture of creativity and experimentation should be established in companies. Funding R&D and teaming with startups can open many doors to both solve problems creatively but also tap into new markets.
Example: A software development firm could create an innovation lab where team members are freed to work on speculative projects. Moreover, work with start-ups on new technologies and solutions.
By adopting these strategies, businesses can navigate the turbulence for 2024 and roll up market — progressive.AI with an evolving dynamic market, being ahead of trends and updated is most likely will help you thrive in the business landscape.
#ai#business#business strategy#business growth#startup#fintech#technology#tech#innovation#ai in business
2 notes
·
View notes
Text
Ensuring Robust Security for Your Blogspot Blog

In today's digital landscape, online security is of paramount importance, and bloggers must take proactive steps to safeguard their Blogspot blogs from potential threats. While Blogspot, the popular blogging platform, provides several built-in security features, it's essential for bloggers to implement additional measures to protect their blogs and maintain the trust of their readers. If you want to know about Getting Started with Blogspot, Visit My Article. This article explores various strategies and best practices for enhancing the security of your Blogspot blog.
Keep Your Software Updated
Regularly updating your Blogspot software is vital for ensuring the security of your blog. Google, the owner of Blogspot, continually releases security patches and updates to address any vulnerabilities. Enable automatic updates or manually check for updates to ensure that your blog is running on the latest version of Blogspot.
Secure Your Login Credentials
A strong and unique password is the first line of defense against unauthorized access to your Blogspot account. Avoid using easily guessable passwords and consider utilizing a password manager to generate and securely store complex passwords. Additionally, enable two-factor authentication (2FA) for an extra layer of security, requiring both your password and a verification code for login.
Enable HTTPS
Securing your blog with HTTPS (Hypertext Transfer Protocol Secure) is crucial for protecting sensitive information transmitted between your blog and its visitors. Blogspot offers free HTTPS encryption for custom domains, ensuring that data exchanged between users and your blog remains confidential. To enable HTTPS, go to the "Settings" section of your Blogspot dashboard and select "HTTPS" from the "HTTPS Availability" dropdown menu.
Regularly Backup Your Blog
Performing regular backups of your Blogspot blog is essential to protect your data in the event of a security breach or accidental data loss. Blogspot provides an option to export your entire blog, including posts, comments, and settings, as an XML file. Set a schedule for periodic backups and store them securely, either locally or using a cloud storage service.
Monitor and Manage User Permissions
If you collaborate with others on your Blogspot blog, carefully manage user permissions to restrict access to sensitive areas. Assign roles with appropriate access levels to contributors, ensuring they only have the necessary permissions for their tasks. Regularly review user accounts and remove any inactive or unnecessary users to minimize potential security risks.
Be Mindful of Third-Party Widgets and Plugins
While third-party widgets and plugins can enhance the functionality and appearance of your Blogspot blog, they can also pose security risks if not carefully vetted. Only install widgets and plugins from reputable sources, and regularly update them to ensure you have the latest security patches. Remove any unused or outdated plugins to reduce potential vulnerabilities.
Protect Against Comment Spam and Malicious Links
Blogspot has built-in features to combat comment spam, but it's essential to keep these settings properly configured. Enable comment moderation, captchas, and anti-spam filters to prevent spam comments from appearing on your blog. Additionally, exercise caution when approving comments containing links, as they may direct users to malicious websites. Avoid publishing comments that appear suspicious or contain unverified links.
2 notes
·
View notes
Text
Types of VPN
VPN Security: Encryption, Hashing, and VPN Types | Sfour eSolutions
In today’s digital age, cybersecurity is a top priority for businesses and individuals alike. At Sfour eSolutions, we understand the importance of keeping your online activities private and secure. One of the most powerful tools in your cybersecurity arsenal is a Virtual Private Network (VPN). In this article, we’ll dive into what VPNs are, how they use encryption and hashing to protect your data, and the different types of VPNs available.
What is a VPN?
A Virtual Private Network (VPN) is a secure technology that creates a private tunnel between your device and the internet. This tunnel encrypts your data, ensuring that it remains confidential and protected from hackers, ISPs, and other cyber threats.
VPN security is crucial for:
Protecting sensitive data on public Wi-Fi
Accessing geo-restricted content
Bypassing internet censorship
Enabling secure remote access for employees
How VPNs Use Encryption Technology
At the core of VPN security is encryption technology. Encryption converts your readable data (plaintext) into an unreadable format (ciphertext) that can only be deciphered with the correct key.
Popular encryption algorithms include:
AES (Advanced Encryption Standard): Often used in 128-bit or 256-bit formats, it’s one of the most secure and widely adopted encryption standards.
RSA: Used for secure key exchange and establishing encrypted connections.
This ensures that even if data is intercepted, it remains confidential and inaccessible without the decryption key.
Hashing for Data Integrity and Authentication
While encryption protects data confidentiality, hashing ensures data integrity and authentication. A hash function generates a unique, fixed-length string (hash) from your data. Even the slightest change in the input creates a completely different hash, making it easy to detect tampering.
VPNs use hashing for:
Authentication: Verifying the identity of users and servers.
Data integrity: Ensuring that data is not altered in transit.
Common hashing algorithms include SHA-256 (Secure Hash Algorithm), which is widely trusted for its strong security.
Types of VPNs
Choosing the right VPN is crucial for your organization’s cybersecurity. Here are some of the types of VPNs and their typical use cases:
Remote Access VPN
Enables individual users to securely connect to a private network from any location.
Ideal for remote work and hybrid workforces.
Site-to-Site VPN
Connects entire networks, such as branch offices or data centers.
Perfect for organizations with multiple locations.
Client-to-Site VPN
Provides secure remote access using dedicated client software.
Common for businesses needing reliable secure remote access.
SSL VPN
Uses SSL/TLS protocols (the same as HTTPS websites) for encryption.
Accessible via web browsers, with no need for extra software.
Mobile VPN
Designed for devices that roam between networks (e.g., smartphones).
Ensures uninterrupted secure connectivity.
Why Choose Sfour eSolutions for Your VPN Needs?
At Sfour eSolutions, we specialize in delivering VPN solutions tailored to your business needs. Our expertise in encryption technology, hashing techniques, and secure remote access ensures your data is protected every step of the way.
Contact us today to learn how we can help you implement a secure and reliable VPN solution for your organization.
Final Thoughts
A VPN is an essential tool for protecting your online privacy and business data. By combining encryption, hashing, and the right VPN types, you can ensure robust security for your network.
Need help choosing the right VPN? Sfour eSolutions is here to guide you every step of the way.
0 notes
Text
What Defines a Truly Secure Website?

In today's digital landscape, a website is often the front door to a business, a personal brand, or vital information. With cyber threats constantly evolving, the question isn't just "Is my website online?" but "Is my website truly secure?" Many users look for the padlock icon and "HTTPS" in the address bar and breathe a sigh of relief. While essential, that green lock is merely the beginning of true website security.
HTTPS signifies that the connection between your browser and the website's server is encrypted, protecting data in transit. But a truly secure website goes far beyond encrypting data between two points. It's built on a multi-layered defense strategy, addressing vulnerabilities at every level of the application and infrastructure.
So, what are the characteristics of a website you can genuinely trust?
1. Always Uses HTTPS with Strong TLS Protocols
This is the foundational layer, but its proper implementation is crucial.
What it is: HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between the user's browser and the website's server using TLS (Transport Layer Security, the modern successor to SSL) certificates.
Why it's essential: It prevents eavesdropping, tampering, and message forgery, ensuring that the data you send (like login credentials or credit card numbers) and receive remains private and integral. Modern browsers flag sites without HTTPS as "Not Secure." Crucially, truly secure websites use strong, up-to-date TLS versions (like TLS 1.2 or 1.3), not older, vulnerable ones.
2. Robust Input Validation and Output Encoding
These are fundamental defenses against some of the most common web attacks.
Input Validation: Every piece of data a user submits (forms, search queries, URLs) must be strictly validated before the server processes it. This prevents attackers from injecting malicious code (e.g., SQL Injection, Command Injection) that could manipulate the database or execute commands on the server.
Output Encoding: Any data retrieved from a database or user input that is displayed back on the website must be properly encoded. This prevents Cross-Site Scripting (XSS) attacks, where malicious scripts could be executed in a user's browser, stealing cookies or defacing the site.
3. Strong Authentication & Authorization Mechanisms
Security starts with knowing who is accessing your site and what they are allowed to do.
Authentication:
Strong Password Policies: Enforce minimum length, complexity (mix of characters), and disallow common or previously breached passwords.
Multi-Factor Authentication (MFA): Offer and ideally mandate MFA for all user accounts, especially administrative ones. This adds a critical layer of security beyond just a password.
Secure Session Management: Use secure, short-lived session tokens, implement proper session timeouts, and regenerate session IDs upon privilege escalation to prevent session hijacking.
Authorization: Implement the principle of least privilege. Users should only have access to the data and functionalities strictly necessary for their role. Role-Based Access Control (RBAC) is key here, ensuring a customer can't access admin features, for instance.
4. Regular Security Updates & Patch Management
Software is complex, and vulnerabilities are constantly discovered.
Continuous Patching: The website's underlying operating system, web server software (e.g., Apache, Nginx), Content Management System (CMS) like WordPress or Drupal, plugins, themes, and all third-party libraries must be kept up-to-date with the latest security patches.
Why it's essential: Unpatched vulnerabilities are a common entry point for attackers. A truly secure website has a rigorous system for identifying and applying updates swiftly.
5. Comprehensive Error Handling & Logging
What happens when things go wrong, or suspicious activity occurs?
Generic Error Messages: Error messages should be generic and not reveal sensitive system information (e.g., database connection strings, file paths, or specific error codes) that attackers could use to map your system.
Robust Logging: All security-relevant events – failed login attempts, successful logins, administrative actions, suspicious requests, and critical system events – should be logged. These logs should be stored securely, centrally, and monitored in real-time by a Security Information and Event Management (SIEM) system for anomalies and potential attacks.
6. Secure Development Practices (SDL)
Security isn't an afterthought; it's built in from the ground up.
Security by Design: A truly secure website is born from a development process where security considerations are embedded at every stage – from initial design and architecture to coding, testing, and deployment. This is known as a Secure Development Lifecycle (SDL).
Code Reviews & Testing: Regular security code reviews, static application security testing (SAST), and dynamic application security testing (DAST) are performed to identify and fix vulnerabilities before the code ever goes live.
7. Web Application Firewall (WAF)
A WAF acts as a protective shield for your website.
What it does: It monitors and filters HTTP traffic between the web application and the internet. It can detect and block common web-based attacks (like SQL injection, XSS, DDoS, brute-force attempts) before they reach the application.
Why it helps: It provides an additional layer of defense, especially useful for mitigating new threats before a patch is available or for protecting against known vulnerabilities.
8. Data Encryption at Rest
While HTTPS encrypts data in transit, data stored on servers needs protection too.
Sensitive Data Encryption: Databases, file systems, and backups containing sensitive user information (passwords, PII, financial data) should be encrypted.
Why it's important: Even if an attacker manages to breach your server and access the underlying storage, the data remains unreadable without the encryption key, significantly mitigating the impact of a breach.
9. Regular Security Audits & Penetration Testing
Proactive testing is key to finding weaknesses before malicious actors do.
Vulnerability Scanning: Automated tools scan your website for known vulnerabilities.
Penetration Testing (Pen-Testing): Ethical hackers simulate real-world attacks to exploit vulnerabilities, test your defenses, and assess your overall security posture. These should be conducted regularly and after significant changes to the website.
10. Clear Privacy Policy & Data Handling Transparency
While not a strictly technical security feature, transparency builds user trust and demonstrates responsible data stewardship.
What it includes: A clear, easily accessible privacy policy explaining what data is collected, why it's collected, how it's used, how it's protected, and who it's shared with.
Why it matters: It shows commitment to data security and respects user privacy, a fundamental aspect of a truly trustworthy online presence.
A truly secure website is not a static state achieved by checking a few boxes. It's a continuous commitment to vigilance, proactive measures, and a deep understanding that security is an ongoing process involving people, technology, and robust policies. In a world where digital trust is paramount, building and maintaining a genuinely secure website is an investment that pays dividends in reputation, customer loyalty, and business continuity.
0 notes
Text
Agencia de Influencers
The Strategic Role of a Professional Agencia de Influencers
In the digital age, where content consumption happens at lightning speed and social platforms dictate trends, influencer marketing has emerged as one of the most effective ways for brands to connect with audiences. At the heart of this dynamic ecosystem lies the agencia de influencers—a professional influencer agency that plays a crucial strategic role in bridging brands with digital creators.
In this article, we explore the importance of influencer marketing, how a professional agencia de influencers can amplify brand success, and why businesses should consider this approach as a long-term investment in brand awareness and consumer trust.
The Rise of Influencer Marketing
Over the past decade, influencer marketing has grown into a multi-billion-dollar industry. Unlike traditional advertising, influencer marketing relies on the authentic voice of creators to engage followers. These influencers, ranging from micro-influencers to global celebrities, shape opinions, inspire buying decisions, and create communities around shared values.
What makes influencer marketing effective is trust. Consumers are more likely to believe a product recommendation from a person they follow and admire than from a traditional advertisement. This human element has made influencer marketing an essential part of digital strategy.
What is an Agencia de Influencers?
An agencia de influencers is a specialized agency that manages the relationship between brands and influencers. These agencies handle everything from identifying the right talent and negotiating contracts to overseeing campaign execution and reporting results.
Their main services typically include:
Influencer identification and vetting
Campaign strategy and management
Contract negotiation and compliance
Content guidelines and quality control
Data tracking and analytics
By partnering with a professional agencia de influencers, brands gain access to a network of vetted creators and a team of experts that ensures campaigns are not only creative but also compliant and results-driven.
Why Brands Need a Professional Agencia de Influencers
Strategic Planning and Expertise
A reputable agencia de influencers brings strategic insight into audience behavior, platform algorithms, and content trends. This knowledge is invaluable in designing campaigns that generate maximum engagement and ROI.
Access to a Curated Network of Influencers
Professional agencies maintain strong relationships with influencers across various niches. They understand each influencer’s audience demographics, engagement metrics, and style—ensuring brand partnerships are both authentic and impactful.
Campaign Efficiency and Scalability
Agencies streamline the influencer marketing process. From campaign briefs to legal contracts and payment management, an agencia de influencers takes care of the operational workload, allowing brands to scale their campaigns with ease.
Performance Tracking and Reporting
Without accurate data, it’s difficult to measure success. Agencies use advanced tools to track metrics such as impressions, reach, clicks, and conversions—providing brands with clear insights and actionable recommendations.
Risk Mitigation and Brand Safety
Navigating the digital space can be risky, especially when working with public figures. Agencies conduct thorough background checks and implement brand safety protocols to minimize reputational risks.
Case Study: How an Agencia de Influencers Transformed a Campaign
Consider a beauty brand launching a new line of skincare products. Instead of traditional ads, the company hires an agencia de influencers to create a digital campaign. The agency selects a diverse group of micro and macro influencers aligned with the brand’s values.
The influencers share skincare routines using the new products, post before-and-after photos, and engage with followers through Q&A sessions. The agency monitors the campaign performance in real time, optimizing where needed. The result: a 200% increase in online traffic, a spike in sales, and thousands of organic mentions across social media.
This level of impact would be hard to achieve without the strategic direction and coordination offered by a skilled agencia de influencers.
The Future of Influencer Marketing
Influencer marketing continues to evolve with emerging platforms like TikTok, Threads, and even virtual influencers powered by AI. As the landscape becomes more sophisticated, the role of a professional agencia de influencers becomes even more critical.
Future trends include:
AI-driven influencer selection
Performance-based partnerships
Deeper integration of e-commerce and social platforms
Rise of niche and nano-influencers for hyper-targeted campaigns
Brands that stay ahead will be those that embrace these changes and partner with agencies that understand the complexities of the digital space.
Conclusion
Influencer marketing is no longer just a trend—it is a core element of modern digital strategy. To unlock its full potential, businesses need the guidance and execution capabilities of a professional agencia de influencers.
By aligning with the right creators, crafting authentic content, and measuring results with precision, a good influencer agency helps brands not only reach their target audience but also build lasting relationships based on trust and engagement.
For companies aiming to succeed in the digital world, investing in an experienced agencia de influencers is not just smart—it’s essential.
0 notes
Text
Unmatched Excellence in OTT APP Development: ideyaLabs Powers the Future of Streaming Services

Why Businesses Choose ideyaLabs for Next-Generation OTT APP Development
Businesses today demand high-performing, scalable, and customizable OTT platforms. ideyaLabs stands at the forefront, delivering end-to-end OTT APP development crafted to meet diverse industry requirements. Enterprises, startups, and content creators trust ideyaLabs to launch streaming solutions that provide seamless user experiences, robust content delivery, and secure monetization. Clients rely on ideyaLabs for future-proof technology that supports rapid growth and market adaptability.
OTT APP Development: Shaping Digital Entertainment
OTT APP development redefines how users consume audio and video content. The global shift from traditional broadcasting to streaming platforms fuels massive growth in OTT applications. ideyaLabs engineers robust OTT platforms, allowing businesses to offer on-demand content, live streaming, and interactive services across multiple devices. With the right OTT application, organizations offer viewers flexibility, convenience, and accessibility, maximizing engagement and customer satisfaction.
Key Features in ideyaLabs OTT APP Development Solutions
User experience forms the core of every ideyaLabs OTT platform. Applications feature intuitive interfaces, swift navigation, and personalized content recommendations. Adaptive streaming technology guarantees crystal-clear playback on varied network conditions and device types. ideyaLabs integrates advanced search functionalities, multi-language support, and user profile management. Push notifications and in-app messaging drive higher retention rates and real-time engagement.
Multi-Platform Solutions for Maximum Audience Reach
OTT platforms built by ideyaLabs stream content flawlessly across Android, iOS, Smart TVs, web applications, and connected devices. Single-code deployment accelerates time to market. Businesses maintain brand consistency and performance on every device, reaching wider audiences without compromising content quality or security.
Secured Content Delivery With State-of-the-Art Technology
Content protection remains non-negotiable for streaming enterprises. ideyaLabs implements strong digital rights management (DRM), content encryption, and watermarking protocols to mitigate piracy and ensure secure delivery. Robust authentication, access controls, and transaction security protect both content creators and viewers, ensuring regulatory compliance.
Robust Back-End Infrastructure Supporting Scalability
As viewership and content libraries expand, ideyaLabs ensures that the platform remains fast and reliable. Cloud-native back-end infrastructure enables elastic scaling, high availability, and reduced latency. Advanced analytics provide actionable insights on viewership patterns, revenue streams, and user behavior. IdeyaLabs integrates seamless APIs for payment gateways, third-party services, and advertising networks, maximizing platform monetization.
Customization Tailored to Diverse Business Models
Every OTT service calls for unique business logic and branding. ideyaLabs crafts fully customizable applications, aligning interfaces, workflows, and monetization strategies to individual client goals. Platforms offer multiple subscription modules, including SVOD, AVOD, TVOD, and freemium options. In-app purchases, ad placements, and dynamic pricing models offer businesses continuous revenue growth.
Seamless Migration and Upgradation Services
Legacy platforms often hinder innovation. ideyaLabs streamlines migration to advanced OTT environments with minimal downtime. Teams handle data migration, third-party integrations, and app upgrades with precision. ideyaLabs ensures content, user profiles, and analytics move seamlessly to the modernized platform. Businesses experience enhanced performance, scalability, and security upon migration.
Ongoing Support and Growth-Focused Partnership
Customers receive ongoing support, platform maintenance, and upgrades to keep pace with technological evolution. ideyaLabs commits to rapid bug fixes, feature enhancements, and continuous testing. Long-term partnerships foster product evolution, helping clients lead in the competitive OTT industry landscape.
Driving Innovation in OTT APP Development With AI & Cloud
ideyaLabs leverages AI for intelligent content recommendations, audience insights, and sentiment analysis. Cloud-enabled infrastructure supports global content delivery through CDNs and geo-targeted distribution. Machine learning algorithms enable predictive analytics for content planning, advertising, and customer engagement optimization.
Elevate Viewer Experiences With Personalized OTT Solutions
Interactive features like quizzes, polls, real-time chats, and co-viewing experiences turn viewers into active participants. ideyaLabs adds parental controls, age gating, and regional content curation for enhanced personalization. Platforms support multi-screen synchronization, download options, and offline playback to deliver maximum convenience.
Brand Elevation Through Unique OTT APP Development Strategies
ideyaLabs exceeds expectations with creative UI/UX design, integrated branding elements, and immersive visual experiences. Custom launch screens, content carousels, and dynamic menus strengthen brand visibility. The development team collaborates closely with clients, ensuring the OTT platform aligns with brand aspirations and messaging.
Success Stories With ideyaLabs OTT APP Development
Leading media houses, broadcasters, and content startups have achieved exponential audience growth and retention with ideyaLabs platforms. Case studies showcase increased user engagement, reduction in churn rate, and successful monetization. Clients scale globally, launch region-specific content, and tap into new markets seamlessly.
Navigating the Compliance and Regulatory Landscape
OTT platforms must comply with data protection regulations, content censorship laws, and broadcasting guidelines. ideyaLabs incorporates geo-blocking, content filtering, GDPR compliance, and VOD certifications in every project. Transparent privacy policies and customizable user consent mechanisms maintain platform credibility.
Monetize Your Content With Future-Ready OTT Solutions
Advertisers and content owners capitalize on built-in ad servers, sponsorship modules, and direct billing systems. ideyaLabs platforms support CPM, CPC, and dynamic ad insertion models. Campaign performance analytics enable targeted advertising strategies for optimal ROI.
Choosing ideyaLabs for Your OTT APP Development Journey
Reliability, technical expertise, and proven innovation make ideyaLabs the partner of choice for OTT APP development in 2025. Dedicated teams guide businesses from conceptualization to launch and beyond. ideyaLabs blends agility, creativity, and a customer-centric approach, empowering organizations to shape the future of digital entertainment.
Contact ideyaLabs To Build Your Custom OTT Platform
Ready to launch your own streaming service? ideyaLabs customizes cutting-edge OTT APP development to match your vision, audience, and growth targets. Tap into the expertise, scalability, and creativity required for OTT success. Reach out for a free consultation and discover the ideyaLabs difference.
0 notes
Text
Is a Remote Proctoring Test Safe and Private? Here's the Truth
As online education continues to grow, the remote proctoring test has become an essential tool for institutions to maintain academic integrity during virtual exams. This digital solution enables students to take tests from home while ensuring fairness and security through video monitoring, browser lockdowns, and AI detection. However, it also raises valid concerns about privacy, data handling, and system reliability. Understanding how a remote proctoring test works—and whether it can be trusted—helps students and educators navigate this evolving space confidently. In this article, we break down the security features, myths, and truths behind remote proctoring tests in depth.
Understanding Privacy Concerns in Remote Proctoring
Many students express anxiety about the privacy implications of a remote proctoring test. The idea of being watched through a webcam, having screen activity recorded, and sharing identification details can feel intrusive. Institutions must be transparent about the data they collect, why it’s collected, and how long it’s stored. Most remote proctoring systems only access what’s necessary and comply with privacy laws like GDPR and FERPA. Still, it's essential that users are informed and can consent knowingly. Building trust starts with understanding these concerns and addressing them directly, especially as remote proctoring becomes increasingly common across global platforms.
How a Remote Proctoring Test Protect Your Data?
When taking a remote proctoring test, your personal data and exam footage are handled with layers of digital protection. Secure cloud storage, limited access permissions, and advanced user authentication systems are common safeguards. Reputable proctoring platforms implement strong cybersecurity protocols to protect identity documents, recorded video, and exam logs from breaches. Often, data is encrypted both in transit and at rest to further guard it from hackers or unauthorized access. Moreover, most systems adhere to international privacy standards, ensuring your academic and personal records remain confidential. Ultimately, data protection is a foundational component of a secure remote proctoring test.
Is Your Webcam Secure During Online Exams?
A central feature of any remote proctoring test is the use of a webcam to monitor test-takers. While this raises concerns about potential misuse or unauthorized access, reputable systems ensure camera activation only occurs during the exam session and with user consent. Additionally, many platforms offer transparency by showing live recording indicators and allowing users to test the camera settings beforehand. Proctoring software does not have permanent control over your webcam—it’s programmed to deactivate immediately after the session ends. Robust firewalls and one-time access tokens are also used to minimize risk, ensuring the security of your webcam during online assessments.
What Happens Behind the Scenes of a Remote Proctoring Test?
A remote proctoring test involves more than just a live proctor watching through a webcam. Behind the scenes, artificial intelligence and machine learning algorithms actively monitor behavior for red flags like unusual eye movement, background noise, or sudden tab switches. These systems compile detailed activity logs, flag suspicious behavior, and alert human proctors for manual review. During this process, secure servers collect and store encrypted data for auditing. In many cases, tests are reviewed post-exam to validate flagged issues. This sophisticated combination of automation and human oversight ensures that remote proctoring tests remain fair, secure, and free from technical biases.
Can Remote Proctoring Tests Be Trusted for Fairness?
A well-implemented remote proctoring test can uphold fairness by deterring cheating and ensuring every test-taker has an equal opportunity to perform. AI-based systems monitor all candidates impartially, flagging only rule-breaking behaviors, not appearances or backgrounds. However, fairness also depends on how proctoring software handles accessibility needs, varying internet speeds, and diverse environments. Leading providers allow accommodations like additional time, breaks, or alternative formats for students with special needs. Institutions must also ensure that every flagged case is reviewed by a human to prevent false accusations. When managed responsibly, remote proctoring tests offer a credible and equitable solution for online exams.
Data Encryption in a Remote Proctoring Test Explained
Data encryption is a critical component of security in any remote proctoring test. From the moment you submit your ID or begin recording video, your data is encrypted—converted into a secure, unreadable format that can only be accessed with special keys. Encryption ensures that if data is intercepted, it remains unusable to hackers. There are typically two types used: encryption in transit (as data moves from your device to the server) and encryption at rest (when stored in databases). Together, these methods protect sensitive information from breaches and give both institutions and students peace of mind during virtual exams.
Remote Proctoring Test Myths vs. Reality
There are several myths surrounding the remote proctoring test that create unnecessary fear among students. One common myth is that proctoring software spies on users 24/7, which is false—access is limited to the exam session only. Another misconception is that the AI unfairly targets people, but modern systems are trained for impartiality and always include human review to ensure accuracy. It’s also believed that proctoring tools store videos forever; however, data retention policies usually limit storage to 30–90 days. Understanding the realities behind these myths can help students feel more confident and informed when preparing for a remote proctoring test.
Conclusion
The rise of the remote proctoring test marks a pivotal shift in modern education and assessment. While privacy, fairness, and data protection are valid concerns, technological advancements have made proctoring systems more secure, ethical, and effective than ever before. Institutions and providers must continue to communicate transparently, educate users, and adopt best practices to maintain trust. For students, knowing how the process works—from webcam access to encryption—can ease anxiety and build confidence. As remote learning continues to expand, the remote proctoring test will remain an essential, evolving tool that ensures integrity without compromising security or personal rights.
0 notes
Text
5 Key Security Features Every Fintech Platform Should Have in 2025
In a world where digital transactions are becoming the norm, the security of fintech platforms has never been more critical. With increasing user adoption, evolving cyber threats, and tighter regulations, financial technology providers must make security a top priority. As we move into 2025, here are five essential security features that every fintech platform must implement to ensure user trust and regulatory compliance.
1. End-to-End Data Encryption
Data encryption is the backbone of secure digital transactions. Fintech platforms must ensure that all data—whether in transit or at rest—is encrypted using industry-grade standards like AES-256 and TLS 1.3. Encryption ensures that sensitive information such as account numbers, transaction details, and personal identification data remains inaccessible to unauthorized parties. This is especially crucial when integrating services like UPI, IMPS, or net banking into apps and platforms
2. Multi-Factor Authentication (MFA)
Passwords alone are no longer sufficient to protect financial accounts. Multi-Factor Authentication (MFA) adds an extra layer of defense by requiring users to verify their identity using two or more methods—such as a password combined with a one-time password (OTP), biometric scan, or security token. In 2025, advanced MFA methods using biometric verification (like fingerprint or facial recognition) are expected to become standard for all fintech platforms.
3. Real-Time Fraud Detection Systems
Cybercriminals are constantly finding new ways to bypass security protocols. Therefore, fintech platforms must deploy intelligent, AI-driven fraud detection systems that can monitor transactions in real time. These systems should be capable of identifying suspicious activities—such as unusual transaction patterns, IP mismatches, or high-frequency requests—and flag or block them instantly. A strong fraud detection engine not only protects the platform but also builds trust among users.
4. Role-Based Access Control (RBAC)
Not every employee or user should have access to all data. Role-Based Access Control (RBAC) ensures that individuals only have access to the information and system functions necessary for their specific role. By limiting access based on predefined roles and responsibilities, fintech companies reduce the risk of internal data breaches and unauthorized actions. This feature is especially critical in platforms serving banks, NBFCs, and large financial institutions.
5. Compliance and Audit Trail Mechanisms
In 2025, compliance with national and international regulations—such as RBI guidelines, PCI DSS, and GDPR—is non-negotiable. Fintech platforms must have built-in mechanisms that ensure adherence to these standards. Additionally, a detailed audit trail system should be in place to log user activities, transactions, and access events. This not only supports legal compliance but also enables faster investigations in the event of a breach or fraud attempt.
Security is not just a technical requirement—it’s a cornerstone of trust in the fintech industry. As digital finance continues to grow, platforms must stay ahead of cyber threats by adopting robust, future-ready security measures. The five features discussed above are not just best practices—they are essential foundations for operating a trustworthy fintech platform in 2025 and beyond.
For More Information Visit Us:
0 notes
Text
How White-Label Payment Solutions Ensure PCI Compliance

As digital commerce becomes the norm, businesses are under increasing pressure to secure financial transactions and protect customer data. Implementing white-label payment solutions has become a strategic choice for many, helping companies streamline operations while ensuring compliance with global standards—particularly PCI DSS.
At Payomatix, we help businesses build branded payment experiences backed by robust security infrastructure. In this document, we’ll explore how white-label solutions ensure PCI compliance while supporting scalable business growth.
What Are White-Label Payment Solutions?
White-label payment solutions allow companies to use a third-party payment infrastructure under their own brand. These platforms come pre-equipped with essential features like:
Payment gateway integrations
Fraud detection mechanisms
Multi-currency support
PCI compliance tools
Instead of developing a payment system from the ground up, businesses save time and reduce costs—focusing instead on growth, product development, and customer experience.
Understanding PCI Compliance and Why It Matters
What is PCI DSS?
PCI DSS (Payment Card Industry Data Security Standards) is a set of guidelines created by major credit card companies to protect cardholder information. It includes 12 key requirements such as:
Maintaining secure firewalls
Encrypting cardholder data
Implementing strong access control measures
Monitoring and testing network systems regularly
Why It’s Crucial
Non-compliance with PCI standards can lead to:
Financial penalties
Legal liabilities
Customer trust issues
Data breaches
White-label platforms provide built-in PCI compliance tools that ease the burden on businesses.
How White-Label Payment Solutions Support PCI Compliance
1. Pre-Certified Payment Infrastructure
White-label providers often offer pre-certified PCI-compliant systems. This allows businesses to bypass the complex and expensive certification process.
2. Tokenization & Encryption
Sensitive payment data is replaced with tokens and encrypted to prevent unauthorized access, ensuring cardholder information is never stored in raw format.
3. Regular Security Audits
Providers perform ongoing penetration testing and vulnerability scans to meet evolving PCI DSS requirements.
4. PCI-Compliant Hosting
The platforms are hosted in secure, PCI-compliant environments, covering storage, transmission, and processing of data.
5. Compliance Reporting Tools
White-label services include dashboards and real-time alerts for monitoring and documenting compliance status.
Benefits of PCI-Compliant White-Label Solutions
Faster Go-to-Market
Launch payment offerings quickly without the delays of building and certifying infrastructure.
Increased Customer Trust
Secure transactions build confidence, leading to higher customer retention and conversion.
Lower Risk Exposure
Reduce the chances of data breaches, fraud, and fines with built-in security protocols.
Cost-Efficient Compliance
Avoid the high costs of independent PCI certification with turnkey white-label solutions.
Scalable Infrastructure
Grow locally or internationally with a secure and compliant system that scales with your business.
How Payomatix Ensures PCI Compliance
Payomatix offers end-to-end white-label solutions built for compliance and security. Key features include:
PCI-DSS certified infrastructure
Real-time fraud detection
Secure APIs with live monitoring
Advanced chargeback management
24/7 technical support
Whether you're an online store, SaaS business, or digital marketplace, Payomatix ensures your payments remain secure and compliant.
Key PCI Features to Look for in White-Label Solutions
When selecting a provider, ensure the platform offers:
Tokenization and encryption
2FA (Two-Factor Authentication)
Role-based access control
Regular vulnerability scanning
Real-time fraud detection
Cloud-based PCI-compliant hosting
Payomatix includes all of the above, offering a secure foundation for your business operations.
The Future of Payment Security
As cyber threats evolve, payment platforms must stay a step ahead. Emerging trends in white-label security include:
AI-powered fraud detection
Biometric authentication
Blockchain verification systems
By choosing a forward-looking provider like Payomatix, your business remains protected against current and future threats.
Final Thoughts
White-label payment solutions offer more than branding—they deliver a secure, scalable, and PCI-compliant pathway to online transactions. With Payomatix’s Security & Compliance Suite, you can:
Launch quickly
Stay secure
Scale globally
Take Action
Want to secure your payments the smart way? 👉 [Talk to our experts at Payomatix] and explore white-label PCI-compliant solutions tailored to your business.
FAQs
1. What is PCI compliance in white-label payment solutions?
It ensures the payment infrastructure meets strict standards for securing cardholder data, protecting against fraud and breaches.
2. How do these platforms secure customer data?
Through encryption, tokenization, and secure, monitored hosting environments.
3. Can using white-label providers help avoid PCI penalties?
Yes. Providers like Payomatix manage PCI requirements, helping you avoid fines and regulatory issues.
4. What services are included in PCI compliance?
Tokenization, encryption, access controls, regular security scans, and reporting tools.
5. Are white-label solutions safe for online payments?
Absolutely. They use the latest security technologies to ensure safe, branded, and seamless transactions.
0 notes