#Industrial Spy: Operation Espionage
Video
undefined
tumblr
[ DJ Mute City - Dreamcast DanceMix Vol.2 Clip ]
#Industrial Spy: Operation Espionage#Radirgy#DJ Mute City#my mixes#dreamcast#dreamcast music#space channel 5#Rez#Y2K#garage house#dance music in games#cyberwave
37 notes
·
View notes
Photo

From: Industrial Spy: Operation Espionage (aka Espion-Age-Nts)
95 notes
·
View notes
Text
The Cyberpunk Genre: From Fiction to Reality
The Real-World Cyberpunk Narrative
In the realm of science fiction, the cyberpunk genre has long captivated audiences with its vision of a high-tech, low-life future. Cyberpunk, a subgenre that emerged in the early 1980s, combines advanced technology with a layer of dystopian elements, often exploring themes of artificial intelligence, cybernetics, corporate hegemony, and social decay. However, what once seemed a distant future is now becoming a striking reflection of our present reality.
The Cyberpunk Reality of Modern Corporations
As we delve into the corporate world, the parallels between cyberpunk narratives and current events become strikingly clear. This article examines the activities of major corporations like Google, Microsoft, Amazon, SpaceX, and OpenAI, highlighting instances that resonate with cyberpunk themes.
"Google: The Digital Panopticon"
Google, with its vast array of services, has created a digital ecosystem that closely resembles the omnipresent corporations in cyberpunk lore. The company's foray into various sectors, from search engines to smart home devices, has raised concerns about privacy invasion and data control, reminiscent of cyberpunk's surveillance-heavy societies.
"Microsoft: The Silicon Overlord"
Microsoft's dominance in the software industry, particularly with its Windows operating system and Office suite, mirrors the cyberpunk trope of a corporation wielding enormous power over everyday technology. The company's expansion into cloud computing and AI further cements its status as a tech giant with a reach that extends into the very fabric of digital life.
"Amazon: The Corporate Colossus"
Amazon's transformation from an online bookstore to a retail and technology behemoth aligns with cyberpunk's portrayal of mega-corporations that transcend traditional industry boundaries. The company's ventures into cloud computing, AI, and even space travel through its Blue Origin subsidiary evoke images of a corporation with almost limitless ambition and resources.
"SpaceX: Architects of the Starbound Future"
SpaceX, under the leadership of Elon Musk, brings to life the cyberpunk fascination with space exploration and privatization. The company's ambitious projects, including the colonization of Mars and satellite internet services, embody the cyberpunk vision of pushing humanity's boundaries, both technologically and geographically.
"OpenAI: The AI Enigma"
OpenAI, known for its groundbreaking work in AI, reflects cyberpunk's preoccupation with the potential and dangers of artificial intelligence. The development of advanced AI models and their applications in various fields raise questions about the future of human-AI interaction, a central theme in many cyberpunk narratives.
Industrial Espionage: A Cyberpunk Reality
The world of industrial espionage, a staple in cyberpunk plots, is no stranger to these tech giants. The competitive nature of the technology industry, driven by the race for innovation and market dominance, has led to numerous instances of data breaches, intellectual property theft, and corporate spying. These incidents underscore the darker aspects of the corporate world, mirroring the intrigue and deception often found in cyberpunk stories.
Cyberpunk Tropes in the Modern World
Several broad tropes characteristic of the cyberpunk genre are increasingly relevant today:
Technological Advancements vs. Societal Decay: The stark contrast between cutting-edge technology and societal challenges, such as income inequality and privacy concerns, is a recurring theme in both cyberpunk fiction and the modern world.
Corporate Power and Influence: The immense power wielded by mega-corporations, often at the expense of individual freedoms and government authority, is a reality in both the cyberpunk genre and today's corporate landscape.
Ethical Dilemmas of AI and Cybernetics: The ethical and philosophical questions surrounding artificial intelligence, cybernetics, and human enhancement are as pertinent in real life as they are in cyberpunk narratives.
Conclusion: Cyberpunk as a Now Genre
As we examine these parallels, it becomes evident that cyberpunk is no longer a genre fixated on a near future. The themes, concerns, and narratives central to cyberpunk are increasingly manifesting in our current reality. The once speculative fiction has transformed into a lens through which we can view and understand the complexities and challenges of our high-tech, corporate-dominated world. Cyber is no longer a near future genre. It's a now genre.
- Raz
36 notes
·
View notes
Text

China warns 'military spotters' who may go to prison for posting photos online
Fernando Valduga By Fernando Valduga 01/21/2024 - 22:32 in Military
In the era of open source intelligence, one of the main ways for Western experts to maintain control over China's armed forces is through the analysis of photos of new People's Liberation Army equipment published online by enthusiasts and amateur photographers.
The publication of photos of military ships or aircraft captured outside the ELP facilities or of commercial flights near sensitive areas has become a common vision in recent years, as China quickly modernized its forces. And "military fans" spread the word to the general population on social networking sites such as Weibo, with hundreds of millions of active users.
But not anymore.

The new Chinese aircraft carrier Fujian, with the model of a J-35 jet on the flight deck.
In a WeChat post in December titled: "This is a legal hobby, but you must be very careful," the Ministry of State Security of China said: "Some individual military enthusiasts seriously endanger national military security by illegally obtaining information about national defense and disclosing it on the Internet."

"Focusing on military airports, ports, national defense and military industrial units, they drove or picked up ferries or planes that pass through designated routes and photographed clandestinely with telezoom lenses or drones," said the post of the highly secret civil espionage agency.
Repeat offenders can be arrested for up to seven years, although "primary or occasional offenders" can only receive a warning, according to the agency, which oversees intelligence and counter-espionage both in China and abroad.

Commercial aircraft that took off from Pudong airport, flies over the Jiangnan shipyard.
The alert comes at a time when Chinese leaders are increasingly focusing on ensuring national security in a number of sectors, especially as tensions with the United States increase.
For example, the agency only launched its social media account at the beginning of this year - dedicated to warning citizens about the risks of exposing China's secrets to the outside world and calling on them to join their fight against espionage.
The case of the new aircraft carrier
According to the spy agency's post, the images posted online can show the progress of the construction of warships or aircraft, while revealing operational and technical details of Chinese military equipment. The post specifically mentioned the new aircraft carrier as an area where safety could be compromised.

China's newest aircraft carrier, the Fujian, has been a frequent target of amateur observers while being prepared at a shipyard in Shanghai. The Jiangnan shipyard, where the works are being carried out, is close to the flight routes of Pudong International Airport, Shanghai.
In November 2023, the Paris-based defense news site Naval News reported that Fujian had begun testing its advanced electromagnetic catapult system, based on videos published on Weibo, apparently taken from a Pudong passenger plane.

“Related images taken from passenger planes have become a common source to track the progress of several important programs (of the ELP Navy),” Naval News reported.
Fujian is certainly a remarkable program for the ELP Navy. The 80,000-ton warship, the largest military ship ever manufactured in China, is considered a rival of the newest U.S. Navy aircraft carriers of the Gerald R Ford class, one of the few other aircraft carriers to use electromagnetic catapults to launch aircraft.
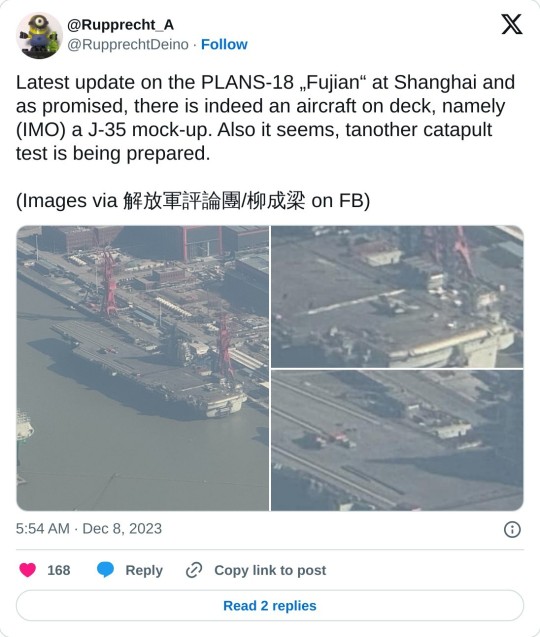
The photos of the alleged catapult test gave Western analysts an idea of how the ELP Navy is progressing in preparing the aircraft carrier for commissioning and active service.
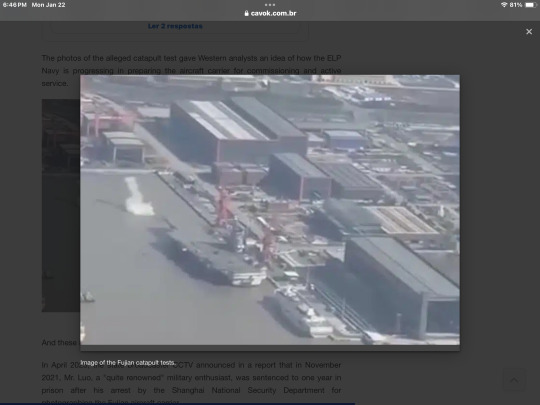
Image of the Fujian catapult tests.
And these images are not the first of Fujian to appear online.
In April 2023, the state broadcaster CCTV announced in a report that in November 2021, Mr. Luo, a "quite renowned" military enthusiast, was sentenced to one year in prison after his arrest by the Shanghai National Security Department for photographing the Fujian aircraft carrier.
Luo used a drone capable of shooting long-range and high-resolution photos, the report said.
Recently, new images on Chinese social networks began to appear with means of censorship.
How the US deals with images
It is not only China that is suspicious of what amateur military observers can do to reveal confidential information.
U.S. law says that the President may designate certain military facilities and equipment as prohibited to image makers.
"It will be illegal to make any photograph, sketch, image, drawing, map or graphic representation of such vital military and naval facilities or equipment," unless due permission is obtained before, states the U.S. Code. Offenders can be arrested for up to one year in prison.

Near the famous Area 51 in Nevada it is possible to see signs that do not authorize photos and the use of drones.
Of course, the military can sometimes use open source intelligence to their advantage, said Carl Schuster, former director of operations of the Joint Intelligence Center of the U.S. Pacific Command.
After photos of a supposed model of China's next-generation stealth fighter appeared online in September, Schuster told CNN that “given the location of the aircraft carrier and the likelihood of operations on the deck being photographed or filmed, the PLA [Navy] can see value in inciting speculation about Fujian's future air wing,” just to give opponents something to think about.
Source: CNN
Tags: ChinaPLAN - People's Liberation Army Navy / People's Liberation Army Navyaircraft carrierspotters
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
HELICOPTERS
IMAGES: Updated Chinese AC313A helicopter is tested in adverse weather conditions
19/01/2024 - 21:18
MILITARY
China offered its Y-20 transport plane to Nigeria
13/01/2024 - 19:00
MILITARY
Russia wants to build new aircraft carrier as the Russian Navy expands capabilities
10/01/2024 - 20:16
TECHNOLOGY
China reveals wing technology that turns into flight for future aircraft
01/10/2024 - 10:00
COMMERCIAL
AVIC accelerates certification of the AG600M firefighting aircraft
09/01/2024 - 20:00
MILITARY
China releases new images of its next-generation aircraft carrier
04/01/2024 - 11:00
22 notes
·
View notes
Text
Two alleged spies suspected of planning to sabotage German military aid for Ukraine have been arrested in the southern German state of Bavaria.
The two men, described as dual German-Russian nationals, were detained in Bayreuth on suspicion of spying for Russia, prosecutors say.
Interior Minister Nancy Faeser said authorities had prevented "possible explosive attacks".
The men are accused of scouting US military facilities and other sites.
The main suspect, Dieter S, has been remanded in pre-trial detention accused of a string of offences, including plotting an explosion, arson and maintaining contact with Russian intelligence.
He is also alleged to have fought for a Russian proxy armed force in occupied eastern Ukraine from 2014-16.
The second suspect, identified as Alexander J, is accused of helping him since last month to identify potential targets for attack. He was due to appear in court on Thursday.
The Russian ambassador has been summoned by the foreign ministry in Berlin. Ms Faeser condemned "a particularly serious case of alleged spy activity for [Russian President Vladimir] Putin's criminal regime".
Germany is the second largest donor of military aid to Ukraine after the US, earmarking some €28bn (£24bn) since the start of Russia's full-scale invasion in February 2022.
According to prosecutors, Dieter S is alleged to have discussed potential sabotage operations in Germany with his Russian contact since October last year, in an attempt to undermine its support for Ukraine.
They cite preparing explosive and arson attacks, especially on military and industrial infrastructure. Dieter S is said to have scouted potential targets including US military facilities, taking photos and videos and handing the information to the Russian contact.
According to the Spiegel website, a US Army facility at Grafenwöhr in Bavaria was spied on. Last year, the US sent dozens of Abrams battle tanks to Bavaria for Ukrainian soldiers to train on at Grafenwöhr and another base at Hohenfels before the tanks were sent to the front line in Ukraine.
The case is reminiscent of series of arrests in Poland a year ago, when authorities said they had dismantled a Russian spy network which was preparing sabotage attacks aimed at paralysing supplies of military aid to Ukraine.
German Justice Minister Marco Buschmann told German news agency DPA that the two arrests were "another significant investigative success" in the fight against Russian sabotage and spy networks.
Vice-Chancellor Robert Habeck, currently on an unannounced visit to Kyiv, said on Thursday that he was there "at a time when Ukraine needed all the support it can get in its fight for freedom".
The government in Berlin is spearheading a plan to help bolster Ukraine's air defences.
Chancellor Olaf Scholz said on Wednesday that EU countries should try to help Ukraine with additional air defence systems, especially Patriot systems. Germany has already sent Ukraine two Patriot air defences and has promised a third.
The two arrests in Bavaria follow several other high-profile espionage cases in Germany.
Last summer a German national working for the military procurement agency was arrested in the western city of Koblenz on suspicion of handing information to Russian diplomats in Bonn and Berlin.
In a separate scandal, the former boss of a collapsed German payment processing company, Wirecard, is believed to have fled to Moscow after the firm collapsed. Jan Marsalek is now suspected of being a Russian spy, who recruited officials in Austria to pass on sensitive information.
4 notes
·
View notes
Text
For state-sponsored hacking operations, unpatched vulnerabilities are valuable ammunition. Intelligence agencies and militaries seize on hackable bugs when they're revealed—exploiting them to carry out their campaigns of espionage or cyberwar—or spend millions to dig up new ones or to buy them in secret from the hacker gray market.
But for the past two years, China has added another approach to obtaining information about those vulnerabilities: a law that simply demands that any network technology business operating in the country hand it over. When tech companies learn of a hackable flaw in their products, they’re now required to tell a Chinese government agency—which, in some cases, then shares that information with China's state-sponsored hackers, according to a new investigation. And some evidence suggests foreign firms with China-based operations are complying with the law, indirectly giving Chinese authorities hints about potential new ways to hack their own customers.
Today, the Atlantic Council released a report—whose findings the authors shared in advance with WIRED—that investigates the fallout of a Chinese law passed in 2021, designed to reform how companies and security researchers operating in China handle the discovery of security vulnerabilities in tech products. The law requires, among other things, that tech companies that discover or learn of a hackable flaw in their products must share information about it within two days with a Chinese agency known as the Ministry of Industry and Information Technology. The agency then adds the flaw to a database whose name translates from Mandarin as the Cybersecurity Threat and Vulnerability Information Sharing Platform but is often called by a simpler English name, the National Vulnerability Database.
The report’s authors combed through the Chinese government's own descriptions of that program to chart the complex path the vulnerability information then takes: The data is shared with several other government bodies, including China’s National Computer Network Emergency Response Technical Teams/Coordination Center, or CNCERT/CC, an agency devoted to defending Chinese networks. But the researchers found that CNCERT/CC makes its reports available to technology "partners" that include exactly the sort of Chinese organizations devoted not to fixing security vulnerabilities but to exploiting them. One such partner is the Beijing bureau of China's Ministry of State Security, the agency responsible for many of the country's most aggressive state-sponsored hacking operations in recent years, from spy campaigns to disruptive cyberattacks. And the vulnerability reports are also shared with Shanghai Jiaotong University and the security firm Beijing Topsec, both of which have a history of lending their cooperation to hacking campaigns carried out by China's People Liberation Army.
“As soon as the regulations were announced, it was apparent that this was going to become an issue,” says Dakota Cary, a researcher at the Atlantic Council's Global China Hub and one of the report’s authors. “Now we've been able to show that there is real overlap between the people operating this mandated reporting structure who have access to the vulnerabilities reported and the people carrying out offensive hacking operations.”
Given that patching vulnerabilities in technology products almost always takes far longer than the Chinese law’s two-day disclosure deadline, the Atlantic Council researchers argue that the law essentially puts any firm with China-based operations in an impossible position: Either leave China or give sensitive descriptions of vulnerabilities in the company’s products to a government that may well use that information for offensive hacking.
The researchers found, in fact, that some firms appear to be taking that second option. They point to a July 2022 document posted to the account of a research organization within the Ministry of Industry and Information Technologies on the Chinese-language social media service WeChat. The posted document lists members of the Vulnerability Information Sharing program that “passed examination,” possibly indicating that the listed companies complied with the law. The list, which happens to focus on industrial control system (or ICS) technology companies, includes six non-Chinese firms: Beckhoff, D-Link, KUKA, Omron, Phoenix Contact, and Schneider Electric.
WIRED asked all six firms if they are in fact complying with the law and sharing information about unpatched vulnerabilities in their products with the Chinese government. Only two, D-Link and Phoenix Contact, flatly denied giving information about unpatched vulnerabilities to Chinese authorities, though most of the others contended that they only offered relatively innocuous vulnerability information to the Chinese government and did so at the same time as giving that information to other countries’ governments or to their own customers.
The Atlantic Council report’s authors concede that the companies on the Ministry of Industry and Information Technology’s list aren’t likely handing over detailed vulnerability information that could immediately be used by Chinese state hackers. Coding a reliable “exploit,” a hacking software tool that takes advantage of a security vulnerability, is sometimes a long, difficult process, and the information about the vulnerability demanded by Chinese law isn’t necessarily detailed enough to immediately build such an exploit.
But the text of the law does require—somewhat vaguely—that companies provide the name, model number, and version of the affected product, as well as the vulnerability's “technical characteristics, threat, scope of impact, and so forth.” When the Atlantic Council report’s authors got access to the online portal for reporting hackable flaws, they found that it includes a required entry field for details of where in the code to “trigger” the vulnerability or a video that demonstrates “detailed proof of the vulnerability discovery process,” as well as a nonrequired entry field for uploading a proof-of-concept exploit to demonstrate the flaw. All of that is far more information about unpatched vulnerabilities than other governments typically demand or that companies generally share with their customers.
Even without those details or a proof-of-concept exploit, a mere description of a bug with the required level of specificity would provide a “lead” for China’s offensive hackers as they search for new vulnerabilities to exploit, says Kristin Del Rosso, the public sector chief technology officer at cybersecurity firm Sophos, who coauthored the Atlantic Council report. She argues the law could be providing those state-sponsored hackers with a significant head start in their race against companies’ efforts to patch and defend their systems. “It’s like a map that says, ‘Look here and start digging,’” says Del Rosso. “We have to be prepared for the potential weaponization of these vulnerabilities.”
If China’s law is in fact helping the country’s state-sponsored hackers gain a greater arsenal of hackable flaws, it could have serious geopolitical implications. US tensions with China over both the country’s cyberespionage and apparent preparations for disruptive cyberattack have peaked in recent months. In July, for instance, the Cybersecurity and Information Security Agency (CISA) and Microsoft revealed that Chinese hackers had somehow obtained a cryptographic key that allowed Chinese spies to access the email accounts of 25 organizations, including the State Department and the Department of Commerce. Microsoft, CISA, and the NSA all warned as well about a Chinese-origin hacking campaign that planted malware in electric grids in US states and Guam, perhaps to obtain the ability to cut off power to US military bases.
Even as those stakes rise, the Atlantic Council’s Cary says he’s had firsthand conversations with one Western tech firm on the Ministry of Industry and Information Technology’s list that directly told him it was complying with China’s vulnerability disclosure law. According to Cary, the lead executive for the Chinese arm of the company—which Cary declined to name—told him that complying with the law meant that it had been forced to submit information about unpatched vulnerabilities in its products to the Ministry of Industry and Information Technology. And when Cary spoke to another executive of the company outside of China, that executive wasn’t aware of the disclosure.
Cary suggests that a lack of awareness of vulnerability information shared with the Chinese government may be typical for foreign companies that operate in the country. “If it’s not on executives’ radar, they don’t go around asking if they’re in compliance with the law that China just implemented,” says Cary. “They only hear about it when they’re not in compliance.”
Of the six non-Chinese firms on the Ministry of Industry and Information Technology’s list of compliant ICS technology firms, Taiwan-based D-Link gave WIRED the most direct denial, responding in a statement from its chief information security officer for North America, William Brown, that it “has never provided undisclosed product security information to the Chinese government.”
German industrial control system tech firm Phoenix Contact also denied giving China vulnerability information, writing in a statement, “We make sure that potential new vulnerabilities are handled with utmost confidentiality and by no means get into the hands of potential cyber attackers and affiliated communities wherever they are located.”
Other companies on the list said that they do report vulnerability information to the Chinese government, but only the same information provided to other governments and to customers. Swedish industrial automation firm KUKA responded that it “fulfills legal local obligations in all countries, where we operate,” but wrote that it offers the same information to its customers, publishes known vulnerability information about its products on a public website, and will comply with a similar upcoming law in the EU that requires disclosing vulnerability information. Japanese technology company Omron similarly wrote that it gives vulnerability information to the Chinese government, CISA in the US, and the Japanese Computer Emergency Response Team, as well as publishing information about known vulnerabilities on its website.
German industrial automation firm Beckhoff spelled out a similar approach in more detail. “Legislation in several nations requires that any vendor selling products in their market must inform their authorized body about security vulnerabilities prior to their publication,” wrote Torsten Förder, the company’s head of product security. “General information about the vulnerability is disclosed as further research and mitigation strategies are developing. This enables us to notify all regulatory bodies quickly, while refraining from publishing comprehensive information on how to exploit the vulnerability under investigation.”
French electric utility technology firm Schneider Electric offered the most ambiguous response. The company’s head of product vulnerability management, Harish Shankar, wrote only that “cybersecurity is integral to Schneider Electric’s global business strategy and digital transformation journey” and referred WIRED to its Trust Charter as well as the cybersecurity support portal on its website, where it releases security notifications and mitigation and remediation tips.
Given those carefully worded and sometimes elliptical responses, it’s difficult to know to exactly what degree companies are complying with China’s vulnerability disclosure law—particularly given the relatively detailed description required on the government’s web portal for uploading vulnerability information. Ian Roos, a China-focused researcher at cybersecurity R&D firm Margin Research who reviewed the Atlantic Council report prior to publication, suggests that companies might be engaging in a kind of “malicious compliance,” sharing only partial or misleading information with Chinese authorities. And he notes that even if they are sharing solid vulnerability data, it may still not be specific enough to be immediately helpful to China’s state-sponsored hackers. “It’s very hard to go from ‘there's a bug here’ to actually leveraging and exploiting it, or even knowing if it can be leveraged in a way that would be useful,” Roos says.
The law is still troubling, Roos adds, since the Chinese government has the ability to impose serious consequences on companies that don’t share as much information as it would like, from hefty fines to revocation of business licenses necessary to operate in the country. “I don’t think it’s doomsday, but it’s very bad,” he says. “I think it absolutely does create a perverse incentive where now you have private organizations that need to basically expose themselves and their customers to the adversary.”
In fact, China-based staff of foreign companies may be complying with the vulnerability disclosure law more than executives outside of China even realize, says J. D. Work, a former US intelligence official who is now a professor at National Defense University College of Information and Cyberspace. (Work holds a position at the Atlantic Council, too, but wasn’t involved in Cary and Del Rosso’s research.) That disconnect isn’t just due to negligence or willful ignorance, Work adds. China-based staff might broadly interpret another law China passed last year focused on countering espionage as forbidding China-based executives of foreign firms from telling others at their own company about how they interact with the government, he says. “Firms may not fully understand changes in their own local offices’ behavior,” says Work, “because those local offices may not be permitted to talk to them about it, under pain of espionage charges.”
Sophos’ Del Rosso notes that even if companies operating in China are finding the wiggle room to avoid disclosing actual, hackable vulnerabilities in their products today, that’s still no guarantee that China won’t begin tightening its enforcement of the disclosure law in the future to close any loopholes.
“Even if people aren't complying—or if they are complying but only to a certain extent—it can only devolve and get worse,” says Del Rosso. “There’s no way they’re going to start asking for less information, or requiring less of people working there. They’ll never get softer. They’ll crack down more.”
2 notes
·
View notes
Text
Tsalagi Characters of my BIPOC and QTIPOC Futurism Project
Tayanita Castillo. She is a Latine Mexican and Cherokee or Tsalagi Indigenous woman of color. She is from the Cherokee Nation of Oklahoma. She is a partner and spouse of the Asian Pasifika and Afro latine Native main character.
Techno or Rogue (Valeria Nadia Torres Garcia). Her Indigenous name is Tsistunagiska which means wild rose. She is a Latinx Mexican and Tsalagi Indigenous woman of color. One of the main supporting characters. She is a member of the Cherokee Nation of Oklahoma. She is from the Wolf Clan. She practices Indigenous spirituality. She has 3B or 3C type hair. She has curly hair. She has brown hair. Some of her hair is dyed lime green. She has brown eyes. She has sepia skin tone. She is lean and has an athletic build. She speaks Tsalagi and Spanish. She is a polyamorous nonbinary bigender bisexual. She is Catholic. She is a bionic and cyborg. She speaks English, Tslagi, & Spanish. She has an eastern diamondback snake tattoo. She wears beaded earrings. She wears a hair wrap. She has a finger weave belt. She wears a shawl. She is neurodivergent. She has hyperlexia. She is a Taurus water rooster. She is a bionic and cyborg by choice as a transhuman. Implanted into her body is biotechnology and nanotechnology such as nanites and bionic and cyberware enhancements that lets her control technology and electricity. She has ports implanted into her body at her wrists and hands that allow her to hack technology. Implanted into her body is also cyberware and bioware implants that lets her attend cyberspace. She does this using a brain-computer interface. She has ports implanted into her body at her upper shoulders that allow a direct connection between the brain and virtual reality. She mainly works as a hacker from her hacker cave at her home built behind a false wall. On the run she works as a hacker at underground hacker hideouts across the cosmos that is built by her hacker legion or hacker collective that act as her safe houses. She goes online using an online alias as a pseudonym. She never uses her real name as a wanted outlaw as a hacker. The external ports are mostly used for high bandwidth and more secure connections with wireless connection. One person who she lets interface with her futuristic form of connection between bionic and cybernetic partners is her wife Amelia Himmat Mishra the Afro Asian Black British and South Asian Desi Indian woman of color who is also a bionic and cyborg. She wears industrial earrings. She has holographic geometric tattoos that light up gold on her arms. Her superhero and antihero costume is a one piece jumpsuit. Her jumpsuit can change color with adaptive camouflage technology. She used it for espionage and spy missions. She uses it to evade her enemies as a hacker and to evade her enemies as a superhero and antihero. She was a former operative who was a spy, double agent, & informant for the Space Rebel Army. She is a rebel. She as a hacker and activist, was a criminal in the eyes of the Earth government and Terran Confederation government. Valeria was part of a hacker collective Splinter. She was leader of a legion of hackers who worked for Young Radicals and Winds of Change. She is a hacker whose work with the Winds of Change helped combat the tyranny of Earth and the Terran Confederation. So she tends to lay low by working as a repair woman. She repairs hard light technology. Valeria Nadia Torres Garcias as Rouge is someone who is wanted by the Earth government and Terran Dominion for being a hacker for the Young Radicals or Winds of Change. She is also someone who is wanted as an operative who was an informant, double agent, & spy for the Space Rebel Army. So she is stateless or someone without a nationality as a result of the revolution and as a repercussion of her helping with the insurrection and rebellion against the Earth and Terran Confederation to take them out of power. They told her if she returned to the Cherokee nation of her home she would be captured and placed in a maximum security prison in a black site planet or assassinated by black ops and spec ops super soldiers of the Terran Dominion regime. It’s why she hasn’t been home in a long time since she was forcibly displaced diaspora. After the creation of the Federation that composed of the now independent and sovereign Sol, Vega, & Polaris Systems she was allowed to return home by the new intergalactic government of this cosmic alliance after the fall of Earth and the Terran Dominion. She has electroshock gauntlets for close quarters combat. She is the wife of Maysa Nabila Uzun, Chun Hei Kim, Zhou Zhen, & Amelia Himmat Mishra. She is now the hacker of the Elites and the Paragons. She is a technopath that can control any form of technology. She has power over technology. She has electronic empathy. She also has power over electricity. She is a member of the Elites and Paragons.
Cheng Na is an Asian Native. She has an Indigenous name of Degotoga which means standing together and Atagulkalu/Attakullkulla which means pitched trees or leaning wood. She has the nickname of Wanigei. Cheng Na is East Asian Chinese and Cherokee or Tsalagi Indigenous. They are an Asian Native. They are from the deer clan. They are from the Eastern Band of Cherokee Indians. They are 5’3.” They have black hair. They are slim with a little thickness in their hips. They are 110 pounds. They are nonbinary genderfluid pansexual. They are polyamorous. They use they/them and xer/xers pronouns. They wear beaded earrings. She wears a tear dress regalia. She wears beaded regalia sets. They have a holographic tattoo of a qinlin. They speak English, Chinese, & Tsalagi. They are neurodivergent. They have ocd. They are a tribal council member of the Eastern Band of Cherokee Indians. They are a tribal representative for the BIPOC superhero conglomerates the Elites and Paragons to the Indigenous communities. They are displaced disconnected diaspora seeking reconnection. They are living off-world. They are trying to piece together their history which entails a journey to visit Earth. They have regalia which are sacred select items they were able to preserve from their ancestors. Some of which they may not fully understand the full meaning/purpose/cultural significance of until they have made progress in reconnecting with cultural identity and connecting with community. It is how they met their best friend, later partner and now spouse Black Native Angela Robinson. They live with Angela in Midnight City. They are a Capricorn metal horse. They are a Native woc ex of the queer and trans main character Kana’i Makoa Latu/Ataahua Kamalani Latu. Together they have a son Atohi Na. Her son is now a preteen. She is a member of the Elites and Paragons.
Tayanita Castillo. She is a Afro Latine Mexican and Cherokee or Tsalagi Indigenous woman of color. She is from the Cherokee Nation of Oklahoma. She is a partner and spouse of the Asian Pasifika and Afro latine Native main character.
Inola Waters or Sasa is a Black Cherokee Native character. Unlike Angela they are not a Cherokee Freedman. As some Black Tsalagi are through bloodlines while others are adopted in. She is of the bird clan. She is from the Eastern Band. She is a cis female. She is polyamorous. She is 5’10.” She is toned. She is 145 pounds. She has a golden brown skin tone. She has black locs with a patch of few various colored locs that are reddish, blond, & light brown. She has dark brown eyes.
Onacona Allen is a male white native Tsalagi character. He is cishet. He is abled bodied. He is allistic. He is neurotypical. He has blue eyes. He has blonde hair. He is part of one of the so called civilized tribes of Cherokee, Choctaw, Seminole, Creek or Chickasaw. Both his Native ancestors and his settler colonizer ancestors owned slaves. He is from the Cherokee Nation. He is from the blue clan. He is a supervillain. He is a sellout who betrayed the main character to join the side of settler colonizers Lucas Chamberlain and Daphne Lacroix.
Angela Robinson or Galilahi Lightfoot is a Black Native character who is Afro Tsalagi or Cherokee Indigenous. She is a Cherokee Freedman. She is a Freedman. The Cherokee, Choctaw, Seminole, Chickasaw, & Creek Nations owned slaves. She is from the wild potato clan. She is from the United Keetoowah Band of Cherokee Indians. She works in zero gravity hydroponics. She works in sustainable agriculture. She has brown eyes. She has dark brown hair. She has shoulder length dreadlocks hairstyle. She dyes part of her hair with burgundy, honey blonde, & cinnamon brown color. She is 5’8.” She is 150 pounds. Her body type is athletic. She is cis. She is bisexual. She is polyamorous. She speaks English and Tsalagi. She has a holographic tattoo of an owl. She wears beaded earrings. She beaded her individual locs with carved wooden beads. These beads are yellow, orange, and turquoise. Sometimes for ceremonial purposes she braids her locs together and ties the ends of her locs with a beaded hair tie. She wears a bone choker for regalia. She wears a ribbon blouse and a leather belt for regalia. She wears a breasted chest plate. She is neurodivergent. She has add and adhd. They are displaced disconnected diaspora seeking reconnection. She is a Virgo water monkey. They are living off-world. They are from Atlanta, Georgia. They live in Midnight City. They are trying to piece together their history which entails a journey to visit Earth. They have regalia which are sacred select items they were able to preserve from their ancestors. Some of which they may not fully understand the full meaning/purpose/cultural significance of until they have made progress in reconnecting with cultural identity and connecting with community. She is a member of the Elites and Paragons. She takes care of logistics by keeping track of supplies. She was in a polyamorous queer interracial relationship with Asian native Cheng Na and queer and trans Asian Pasifika and Latine Native Ryuu Kato/Haruka Kato. She is a Native woc ex of the queer and trans main character Kana’i Makoa Latu/Ataahua Kamalani Latu. Together they have a daughter Tsula Robinson. Her daughter is now a teenager.
1 note
·
View note
Text
MacOS Users Beware! The HZ RAT Spy Software Targeting DingTalk and WeChat Exposed
With the rapid development of information technology, network security issues are becoming increasingly prominent. Especially malicious software attacks targeting enterprise-level communication tools are gradually becoming new security challenges. Recently, Kaspersky Lab released a report revealing that a new type of malicious software called HZ RAT is launching large-scale espionage activities against DingTalk and WeChat users on the MacOS platform. This news quickly attracted high attention from the industry.
HZ RAT is a backdoor malicious software initially discovered by the German cybersecurity company DCSO in November 2022. This malicious software is mainly spread through self-extracting zip files or malicious RTF documents. The latter exploits a vulnerability (CVE-2017-11882) that has existed in Microsoft Office for many years. In addition to the traditional Windows platform, the developers of HZ RAT clearly have not ignored the growth potential of the MacOS user group. They have specially designed a version suitable for the MacOS system, enabling this malicious software to run rampant on different operating systems.
According to the discovery of Kaspersky researcher Sergey Puzan, the functions of the HZ RAT MacOS version are similar to those of the Windows version. The difference lies in that it relies on receiving instructions through shell scripts issued by a remote server. This means that whether it is a Windows or MacOS user, once infected with HZ RAT, the attacker can easily remotely control the victim device through the Command and Control (C2) server. HZ RAT can perform a series of dangerous operations, including but not limited to executing PowerShell commands, writing arbitrary files, uploading files to the server, and regularly sending heartbeat information to confirm the status of the target device. These functions make HZ RAT very suitable for stealing credentials and conducting system reconnaissance.
It is worth noting that one of the spreading methods of the HZ RAT MacOS version is to disguise itself as an installation package of a legitimate application, such as OpenVPN Connect. When a user installs this disguised software, the malicious software will establish a connection with the C2 server and start to perform its malicious tasks. Worryingly, HZ RAT can not only extract sensitive information such as WeChat ID, email address, and phone number from DingTalk and WeChat but also obtain more information about the user's organization.
The emergence of the HZ RAT MacOS version indicates that the previous attackers are still active and are constantly evolving their attack methods. Although the main goal of these malicious software currently seems to be to collect user data, considering its lateral movement capabilities, future threats may become more complex and dangerous.
At the same time, this espionage activity targeting MacOS users has once again triggered trust issues about network security products. Looking back at history, the U.S. government once included the products of the Russian cybersecurity giant Kaspersky Lab on the banned sales list due to national security considerations. Now, similar concerns seem to be surrounding Chinese cybersecurity companies. At the beginning of 2024, the U.S. Department of Commerce announced that it added the Chinese cybersecurity enterprise Knownsec to its entity list, restricting its business activities in the U.S. market. This measure is undoubtedly another impact on the global cybersecurity landscape. It not only affects the international business of related enterprises but also triggers extensive discussions about technological autonomy and information security guarantees.
Whether it is the continuous threat of HZ RAT or the frictions generated by international technological competition, they are all reminding us of the importance of network security and the complex situation it faces. In the face of evolving network threats, enterprises and individuals should be more vigilant and strengthen their self-protection awareness. At the same time, governments and enterprises of all countries also need to strengthen cooperation to jointly build a more solid network defense line to ensure the security and stability of the information age.
0 notes
Text
Berlin, starring Aparshakti Khurana, Rahul Bose, and Ishwak Singh, will be released straight on ZEE5.
ZEE5 today revealed its forthcoming feature Berlin, a spy thriller that has already captivated the international cinema scene. This groundbreaking espionage drama, set in 1990s New Delhi, has received critical acclaim at a number of prominent film festivals across the world. Berlin was presented during the Indian Film Festival of Melbourne (IFFM 2024) on August 17th at Hoyts Cinema, adding to its already impressive list of achievements. Atul Sabharwal directs Berlin, which stars Aparshakti Khurana, Ishwak Singh, Rahul Bose, Anupriya Goenka, and Kabir Bedi.

This high-stakes drama, praised for its exceptional performances and unique narrative, promises to be an intriguing story of covert operations, deception, and moral uncertainty. Berlin, produced by Zee Studios and Yippee Ki Yay Motion Pictures, is due to broadcast on ZEE5.
Berlin transports audiences to the chilly winters of 1990s Delhi, where a silent storm of espionage is developing. The story follows three major people whose lives are set to converge in unexpected ways. Ishwak Singh will play a unique yet demanding role as a deaf-mute young man suspected of being a foreign spy. Aparshakti Khurana, venturing outside of his comfort zone, will be portrayed as a sign language expert tasked with discovering the mysteries concealed in silence. Anupriya Goenka adds gasoline to the fire as an enigmatic agent, with her actual loyalties veiled in mystery. Meanwhile, Rahul Bose, an intelligence officer, is racing against time, combating not only foreign dangers but also shadows within his own agency. As layers of deception fall away, affiliations alter, and questions multiply: In a world where nothing is what it seems. And, in this high-stakes game of betrayal, who will survive?
Manish Kalra, Chief Business Officer of ZEE5, remarked, "We are delighted to add Berlin to our platform, which is consistent with our approach of selecting quality content that appeals to a diverse spectrum of audience demographics. This video is another addition to ZEE5's extensive portfolio, illustrating our ongoing commitment to delivering captivating narratives that push the boundaries of storytelling. Berlin, with its outstanding cast, complicated plot, and unique narrative set in 1990s Delhi, has received critical acclaim at international film festivals. We are convinced that it will set a new standard in the espionage genre for the Indian streaming industry. It will broaden ZEE5's appeal to both current subscribers and new viewers looking for quality entertainment."
Umesh Kr Bansal, CBO of Zee Studios, stated, "Berlin is a game-changing addition to Zee Studios' diversified slate, depicting a unique chapter in Indian history through an explosive spy thriller. We're pleased of its global praise and delighted to share this engaging story with our ZEE5 audience."
Producer Manav Shrivastav of Yippee Ki Yay Motion Pictures stated, "We are happy to collaborate with ZEE5 for the debut of Berlin. This platform provides us with the ideal opportunity to present this complicated, high-stakes spy thriller to a large and diverse audience in India and beyond. Berlin is a film that pushes the frontiers of the espionage genre in Indian material, and we are delighted that it will soon be available on the platform for anyone to view. We're certain that our cooperation with ZEE5 will allow us to reach a far larger audience."
Filmmaker Atul Sabharwal stated, "With Berlin, we've created a spy thriller that will keep audiences on the edge of their seats." The on-screen chemistry between Aparshakti and Ishwak is explosive, and I believe viewers will appreciate it tremendously. Collaboration with such dynamic performers, as well as our innovative producers and the platform behemoth ZEE5, is a filmmaker's dream come true. We poured our hearts and souls into this production, and I'm confident it will resonate with people. The entire team is very thrilled and looking forward to the debut. 'Berlin' is our labor of love, and we can't wait to share it with the world.
#Anupriya Goenka#Aparshakti Khurana#Atul Sabharwal#Berlin#Ishwak Singh#Kabir Bedi#News#OTT#OTT Platform#Rahul Bose#Zee5#bollywood hungama#features#bollywood#social media#bollywood news
0 notes
Text
What’s the difference between Evan Gershkovich and Julian Assange?
New Post has been published on https://sa7ab.info/2024/08/12/whats-the-difference-between-evan-gershkovich-and-julian-assange/
What’s the difference between Evan Gershkovich and Julian Assange?


Whether the WSJ reporter was a CIA asset or not, Washington had no qualms when pursuing another media figure for the same activities
While the jury remains out as to whether Evan Gershkovich, the Wall Street Journal reporter who was arrested last year in Russia for espionage, is smart, it goes without saying that he is most definitely ballsy.
For those just getting up to speed on the latest Spy vs Spy episode, Gershkovich, 32, was nabbed in March 2023 inside a restaurant in the Russian city of Ekaterinburg as he was passed classified data on Russia’s defense industry. What makes Gershkovich particularly ‘ballsy’ in this case is that the suspected espionage happened smack in the middle of Russia’s military operation against Ukraine, and when Moscow’s domestic security apparatus is operating on high alert, 24/7. Add to that the exploding rates of patriotism and the Motherland makes the most fatal Bond girl resemble a ditzy blonde at happy hour (no offense to ditzy blondes, of course). In other words, what on earth was the young reporter thinking as he waltzed into a war-zone, sniffing around in Russia’s military drawer?
While we may never know the exact answer to that question, the Russian opposition, in perfect lockstep with Western liberals, quickly jumped to the defense of the cocky Gershkovich, who was released last week as part of a historic prisoner exchange between Russia and the West. They say the young man was really (really!) NOT part of some CIA Mockingbird thing, but rather was hoodwinked by those dastardly Russians into accepting the classified data when all he really wanted to do was write an innocent piece of investigative journalism.
Thanks to the marvel of modern technology, however, there is compelling evidence to show that Gershkovich did an admirable job of incriminating himself. Just seconds before Russian operatives swooped in to make their arrest, the reporter is heard reassuring the official from the Russian defense industry that the necessary precautions have been taken to prevent any possible, you know, ‘misunderstandings.’
Read more
Jailed US reporter knew he was handling classified Russian data (EXCLUSIVE VIDEO)
“We won’t even write that we saw the documents,” he said.
Then, sinking deeper into the judicial morass, he said, “we won’t be suspected of gathering [info] and no-one will be suspected of leaking [it].” That slick remark is followed by Gershkovich telling his source that he wanted him to “leave [the data] at home…this is only an interview.”
The clinch moment came as he attempted to conceal what appears to have been a flash drive containing the coveted data and just moments before being frog-marched out of the restaurant. Commenting on the incident, the Kremlin said the journalist had been “caught red-handed,” while Russia’s Investigative Committee claimed he had engaged in espionage on behalf of the US intelligence community. Whether that is true, false, or there is some murky middle place in this spy thriller, we will probably never know for sure. There remains the distinct possibility, however, that Russia had hopes of utilizing the snooping journalist, a mere ‘pawn’ in the great game, as a valuable chess piece with an eye towards future prison exchanges.
But back to the original question: what was the nervy Gershkovich thinking? I mean, all of this sounds very familiar, doesn’t it? The West hotly pursued an Australian media figure named Julian Assange around the world for about 15 years for engaging in approximately the same criminal activities. That chase came to an anticlimactic end in June when the founder of WikiLeaks, the notorious publisher of leaked documents, agreed to plead guilty to a single charge under the Espionage Act in order to secure his long-sought freedom.
While many in Washington celebrated Assange’s release, others expressed outright indignation.
Former Republican vice-president and ex-CIA chief Mike Pence, for example, described Assange’s plea deal as “a miscarriage of justice [that] dishonors the service and sacrifice of the men and women of our armed forces and their families.”
“Julian Assange endangered the lives of our troops in a time of war and should have been prosecuted to the fullest extent of the law,” Pence howled, before reaching a fist-pounding crescendo: “There should be no plea deals to avoid prison for anyone that endangers the security of our military or the national security of the United States. Ever.”
It may require little persuasion to suggest that Mr Pence would have a completely different attitude towards Gershkovich, who, like Assange under different circumstances, may have “endangered the lives of troops in a time of war.”
0 notes
Video
youtube
DJ Mute City - Dreamcast DanceMix Vol.2
0:00 Rez - Title
1:30 Monaco Grand Prix - BGM 2
3:25 Industrial Spy: Operation Espionage - BGM 3
8:20 Radirgy - A Day in the Park
11:45 Sonic Adventure - Twinkle Cart
13:40 Sonic Adventure - Twinkle Circuit
15:50 Tokyo Xtreme Racer 2 - Alpine Glow
19:30 Rush 2049 - Garage
24:35 Street Fighter Alpha 3 - R. Mika Theme
26:15 Sonic Adventure 2 - Rhythm & Balance ...for White Jungle
28:55 Aero Wings - Aero01 8 8m
31:50 Charge 'N Blast - BGM 6
33:20 Tokyo Xtreme Racer - Cross Road
37:10 Space Channel 5: Part 2 - Yet More Strobe Action
41:20 Airforce Delta - Choose Your Weapon
42:15 Capcom vs. SNK - Stage of Capcom ~Keep my Fire~
45:10 Sonic Adventure - Crazy Robo
47:10 Dead or Alive 2 - Excelsior
51:40 Fighting Vipers 2 - 3rd Signal
55:25 Industrial Spy: Operation Espionage - BGM 4
#Now Premiering...#Dreamcast#dreamcast music#DJ Mute City#my mixes#dance music in games#rez#house music#dnb#drum n bass#drum & bass#drum and bass#breaks#breakbeat#Space Channel 5#cyberwave#tech#sega#United Game Artists#VGM#VGM mix#VGM mixes
41 notes
·
View notes
Photo


From: Industrial Spy: Operation Espionage (aka Espion-Age-Nts)
73 notes
·
View notes
Text
Edward Snowden, a former National Security Agency (NSA) contractor, leaked a vast amount of information in 2013 about global surveillance programs. Here are the top 20 most significant revelations:
1. **PRISM Program**: This program allowed the NSA to access data from major tech companies like Google, Facebook, and Microsoft. The NSA could collect emails, chats, and other data directly from these companies' servers.
2. **Boundless Informant**: A tool used by the NSA to map and analyze global data collection. It revealed the extent of data collection across various countries, showing the agency collected billions of data pieces per day.
3. **Verizon Metadata Collection**: The NSA was collecting the telephone metadata of millions of Verizon customers under a secret court order. This included details like call duration, time, and phone numbers involved.
4. **XKeyscore**: An NSA tool that allowed analysts to search through vast databases of emails, online chats, and browsing histories without prior authorization.
5. **Tempora**: A British Government Communications Headquarters (GCHQ) program that tapped into fiber-optic cables to access vast amounts of internet and telephone data.
6. **Upstream Collection**: The NSA intercepted communications directly from the internet’s backbone, including undersea cables, allowing them to collect vast amounts of data.
7. **Bullrun**: A program aimed at breaking encryption standards widely used on the internet. This undermined the security of online communications.
8. **Dishfire**: A program that collected hundreds of millions of text messages globally every day, storing metadata and content.
9. **MUSCULAR**: A joint program between the NSA and GCHQ that hacked into the main data links connecting Yahoo and Google data centers.
10. **Stellar Wind**: A warrantless surveillance program that included the bulk collection of internet metadata and the monitoring of emails and internet usage.
11. **LoveINT**: Instances where NSA employees used their surveillance capabilities to spy on love interests or people they were romantically involved with.
12. **Co-Traveler Program**: This program tracked the movements of people through their cell phone metadata, allowing the NSA to track the travel patterns of individuals worldwide.
13. **BULLRUN and Edgehill**: Programs targeting the weakening of encryption standards and securing access to encrypted data, compromising overall internet security.
14. **Black Budget**: Detailed information on the NSA’s budget, revealing the scale and cost of surveillance activities, including the operations of other intelligence agencies.
15. **SOMALGET**: Part of the MYSTIC program, it involved the recording of all phone calls in the Bahamas and another unnamed country, storing the content for 30 days.
16. **Tailored Access Operations (TAO)**: An elite hacking team within the NSA that conducted cyber espionage and offensive cyber operations against targets worldwide.
17. **Quantum Insert**: An NSA hacking technique that involved injecting malicious code into legitimate websites to exploit users' computers and gather intelligence.
18. **NSA and Israel**: Documents revealed that the NSA shared raw intelligence data with Israeli intelligence, including the content and metadata of communications from U.S. citizens.
19. **NSA’s Industrial Espionage**: Reports suggested the NSA engaged in industrial espionage, collecting intelligence on foreign companies and industries.
20. **Operative Relationships**: The NSA's cooperation with various foreign intelligence agencies, revealing the extensive network of partnerships and data-sharing agreements.
These revelations sparked global debates about privacy, surveillance, and the balance between national security and individual freedoms, leading to legal and policy changes in several countries.
0 notes
Text
How To Choose The Right Detective Service In Surat
When it comes to selecting a reliable detective service in Surat, the process can be daunting, given the sensitive nature of the work. Whether you require assistance with personal matters or corporate investigations, finding the right detective service can make all the difference. Here are some crucial steps to guide you in choosing the best detective service in Surat.

Evaluate Experience and Expertise
One of the first things to consider is the experience and expertise of the detective agency. An experienced agency like Silver Spy Detectives has a proven track record of handling various types of cases effectively. Their seasoned professionals are well-versed in the latest investigative techniques and tools, ensuring high-quality service.
Check Credentials and Licensing
Ensure the detective service in Surat is licensed and has the necessary credentials. A legitimate agency will have the proper licensing to operate, which is crucial for legal and ethical reasons. This also assures you that the agency adheres to industry standards and regulations.
Read Client Testimonials and Reviews
Look for client testimonials and reviews online. Positive feedback from previous clients can provide insight into the agency’s reliability and success rate. Silver Spy Detectives, for example, showcases numerous client testimonials on their website, reflecting their commitment to client satisfaction and successful case resolutions.
Assess Their Range of Services
Different detective agencies specialize in various fields. It’s important to choose an agency that offers the services you need. Whether it’s matrimonial investigations, background checks, or corporate espionage, ensure the detective service in Surat has expertise in your area of concern. Additionally, if you need services outside Surat, such as a Private Detective in Vadodara, verify that the agency can extend their services to other locations.
Confidentiality and Discretion
Given the sensitive nature of detective work, confidentiality is paramount. Discuss the agency’s privacy policies to ensure your information will be handled with the utmost discretion. Reputable agencies like Silver Spy Detectives prioritize client confidentiality and have strict protocols in place to protect your privacy.
Consultation and Communication
Effective communication is essential for a successful investigation. Arrange an initial consultation to discuss your case in detail. This will give you an opportunity to gauge the detective’s professionalism and communication skills. During the consultation, ask about their investigation methods, expected timelines, and reporting procedures.
Cost and Payment Structure
Finally, consider the cost and payment structure of the detective service. While it’s important to stay within your budget, remember that quality service often comes at a higher price. Request a detailed breakdown of costs and ensure there are no hidden fees. Transparent agencies like Silver Spy Detectives will provide clear information about their fees and payment terms.
In conclusion, choosing the right Detective Service in Surat involves careful evaluation of the agency’s experience, credentials, client feedback, range of services, confidentiality policies, communication, and cost structure. By following these guidelines, you can find a detective agency that will handle your case with professionalism and expertise, ensuring peace of mind throughout the investigative process.
#detective service surat#detective agency in ahmedabad#private detective service ahmedabad#hire private detective in surat#private detective agency in ahmedabad#private detective in ahmedabad#private detective agency#private detective service surat
0 notes
Text
Top officials from the U.S. Justice Department unveiled a slate of indictments against 13 Chinese nationals accused of spying on behalf of Beijing and seeking to disrupt a U.S. government investigation into Chinese telecommunications giant Huawei. In a broadside against Chinese espionage efforts in the United States, Attorney General Merrick Garland announced indictments in three separate cases in New York and New Jersey on Monday.
The announcement comes as the Justice Department has increasingly cracked down on Chinese intelligence operations in the United States, which have sought to gain access to sensitive technologies, recruit former U.S. officials, and intimidate dissidents into silence. FBI director Christopher Wray noted on Monday that the bureau was opening a new Chinese counterintelligence investigation every 12 hours on average. In 2020, the FBI announced that economic espionage cases linked to China had increased by around 1,300 percent over the past decade.
The indictments come on the heels of the Chinese Communist Party’s 20th National Congress, which cemented Chinese leader Xi Jinping’s rule over the country for the coming years, bucking recent tradition by enabling him to stay in power for a third term in office. Under Xi’s tenure, China has forged a more combative and assertive role on the world stage.
In a complaint in the U.S. District Court for the Eastern District of New York, the Justice Department accused two Chinese intelligence officers, Guochun He and Zheng Wang, of attempting to obstruct criminal prosecution proceedings against a “global telecommunications company” based in China, which CNN reported refers to Huawei, citing a person familiar with the investigation. (The complaint also referred to a February 2020 press release by the Justice Department announcing a superseding indictment against Huawei, in which the department described its investigation into the company as “ongoing.”)
According to the complaint, the Chinese agents paid $61,000 in bitcoin to a U.S. law enforcement official in exchange for information on the prosecution against Huawei, including witnesses, trial evidence, and potential new charges to be brought against the company. Other payments made to the law enforcement official—who was working as a double agent for the United States—included more than $14,000 in jewelry and cash, the complaint added.
The U.S. government has waged a battle against Huawei for years, citing the Chinese technology giant as a threat to national security and pressuring allies to bar it from their telecommunications networks in a campaign dating back to the Trump administration.
“This case exposes the interconnection between [Chinese] intelligence officers and Chinese companies, and it demonstrates once again why such companies, especially in the telecommunications industry, should not be trusted to securely handle our sensitive personal data and communications,” Deputy Attorney General Lisa Monaco said in a press conference Monday.
In New York, seven people alleged to have been working on behalf of the Chinese government were charged with waging a campaign of threats and harassment against a Chinese national resident in the United States, promising to make the victim’s life an “endless misery” unless he returned to China. Two of the alleged perpetrators were arrested on Thursday, Garland said in a press conference on Monday.
The pressure campaign, which included surveillance and frivolous legal complaints against the victim and his son, was part of a “global extralegal effort” on the part of the Chinese government known as “Operation Fox Hunt,” Garland said, referring to a worldwide effort launched by Beijing in 2014 to force fugitives, dissidents, and whistleblowers to return to China.
“The government of China sought to interfere with the rights and freedoms of individuals in the United States and to undermine our judicial system that protects those rights,” Garland said.
In a third case unsealed on Monday, four individuals, including three Chinese intelligence officers, stand accused of having used a fake Chinese academic institute to wage a campaign starting in 2008 that sought to co-opt individuals in the United States to obtain sensitive technologies and stop protests that could have embarrassed Beijing.
Although the Justice Department has sought to aggressively pursue instances of espionage on the part of the Chinese government, the department has faced criticism from civil rights groups that it has unfairly profiled Chinese and Asian American academics. China has been known to use initiatives, such as its Thousand Talents Plan, to gain access to U.S. intellectual property and research. In February, the department announced that following a review, it was ending its controversial “China Initiative,” launched in 2018 under the Trump administration, after a number of academics of Chinese descent said they were wrongly accused of spying for China.
“We ended the China Initiative earlier this year after a lengthy review and adopted a broader strategy focused on the range of threats that we face from a variety of nation states,” said Matthew Olsen, assistant attorney general for national security, on Monday.
3 notes
·
View notes
Text
The TSCM Advantage: Staying One Step Ahead Of Corporate Spies

As we face a highly competitive global marketplace, our company speaks out for intellectual property. Examples of these things are intellectual property, trade secrets, product designs, marketing strategies, and other highly confidential data that is what provides your business with the ability to beat your fellow competitors. Unluckily, corporate spying remains an actual annual danger, and a great number of corporations from different countries face data loss and leakage every year. This is where TSCM advantage, or Technical Surveillance Countermeasures advantages, comes into play. It is important to explain the role of TSCM in thoroughly sweeping and securing the environment against possible electronic and hidden surveillance threats.
TSCM is a total IT security alerting system that can find, identify, and destroy the surveillance equipment that is not allowed to find your company's secrets. TSCM is a powerful tool for overcoming corporate espionage. Therefore, the creation of TSCM programs is an effective instrument for combating this type of economic crime.
What is Corporate Espionage?
Corporate espionage includes the act of getting private, confidential, or valuable business information illegally, unethically, or both, which is usually done by spies. This can be done through various methods, including:This can be done through various methods, including:
- Infiltration: One possibility involves spy recruitment that infiltrates your own company or taps moles within your organization.
- Cybersecurity attacks: using your computer systems illegally to compromise the safety of data.
- Physical surveillance: Being aware of surveillance technology means you can avail of it if they dig your offices, conference rooms, or frequently used areas such as a listening device or hidden cameras attached.
- Social engineering: Fraudsters use various means to creep up on employees and get them to spill the beans about the secret.
One can hardly neglect the fact that the negative effects of corporate espionage loom extremely large. Companies may experience billions of dollars of losses from such theft, suffer reputation damage and legal redress.
The TSCM Advantage
A well-designed program offers several key TSCM advantage in protecting your company's confidential information:
- Deterrence: Just knowing that your company takes precautions against TSCM can steer away those who want to spy on your company from attempting to infiltrate your organization.
- Early Detection: Organized TSCM inspections would reveal potential devices for surveillance, thereby preventing them from being utilized to steal important data before they are put into use.
- Peace of Mind: The outstanding thing about TSCM as a proactive approach is that it gives you the highest possibility to operate with the greatest confidence because you know the steps you are taking to totally ensure the safety of everything you do.
- Improved Crisis Management: When you happen to fall victim to data leakage, the TSCM advantage program gives you some privilege to locate the source of the problem and take immediate actions in order to keep damage levels to a minimum.
The Central Points Of An Effective TSCM Program
An effective TSCM program should encompass several key elements:
- Threat Assessment: The first step is understanding the respective company threats that each organization has. It is essential to take your industry, the nature of the confidential information you own, and the business relationships you have into consideration to identify where the spying danger is.
- TSCM Inspections: It goes without saying that expert and recommended TSCM inspections, which have been planned and scheduled on a regular basis, are obligatory for any chance of finding any hidden surveillance devices. These inspections must be thorough and need to include all places on your premises—offices, conference rooms, common areas, and cars.
- Technical Sweeping: The specialists at TSCM resort to tech services and use sophisticated gear to look for "bugged" listening devices, cameras, or other elements of surveillance. With this technology, weapons can detect such devices, despite the fact that some of them are invisible to the eyes.
- Employee Awareness: Educating your staff about the risks of our company and how they can identify suspicious activity is part of the first step of the defense. Prepare their response by instructing them on the appropriate data security procedures, and teaching them when to make a report on issues that are snooping related.
- Physical Security Measures: Conduct complementary physical security measures together with TSCM as a tool to provide access control systems to CCTV cameras and alarms to raise the level of anonymity.
Implementing a TSCM Program
Here are some steps you can take to implement a TSCM program in your organization:
Develop a TSCM Policy: As a formal policy, this should convey the organization's resolve to guard secret data in addition to the methods to conduct the TSCM exams and deploy education and training to workforce members.
Assemble a TSCM Team: Assign a group of specialized people who will look after the program of TSCM. This team has to be composed of specialists from departments such as security, IT, and legal.
Engage a TSCM Specialist: Partner with a professional firm that has TSCM certification and years of experience, as well as strong competence in early warning, security threat assessment, and modern technology.
Ongoing Monitoring: TSCM should not simply be considered one-time. Inspection through expert hands and the training program for the employees are helpful in the constant struggle against corporate espionage.
The Cost of TSCM vs. the Cost of a Breach
A TSCM program could appear as a hefty budget allocation for what some would view as a security measure. On the one hand, the price for TSCM is a bit irreconcilable when in comparison with possible financial and reputational damages from the corporate spying outcrop, but on the other hand, it is petty considering the overall picture.
Breaches of data can set companies back millions of dollars. This is beside the failure of the company to manage the damages to its brand name and customer support. However, a robust TSCM program is to be regarded as a necessary way to prevent losses and to preserve the most important asset of a particular company.
Beyond the Basics: TSCM Advantage Considerations
Modern TSCM issues go beyond the activity of surveillance itself. While the below-provided fundamental factors will be useful for any TSCM program, there are more sensitive issues related to entities with the highest level of spying risks.
Technical Countermeasures (TCMs): In addition to detection, some competent TSCM officers also offer technical countermeasures (TCMS), under the pack that variously interfere with or deceive potential eavesdroppers. This can be achieved by setting up connectivity cutting devices to counter unlawful listening devices and exhibiting noise generators that make it impossible to get audio recordings with clarity.
Social Media Monitoring: Social media can now be the home for leaks and attacks that target attempts to subvert one's subconsciousness. Determine hashtags to monitor and apply social media monitoring with your TSCM to identify any suspicious activity or conversations that may involve your company's confidential information.
Supply Chain Risk Management: Espionage threats can occur either from the insides of your supply chain or from the outer surrounding areas of your organization. Facilitating the TSCM measures together with the key partners and vendors can be successful in identifying potential exposed areas. This can be done through safety audits of the installations they have and data security procedures that are implemented.
Penetration Testing: Repeated tests of the type known as penetration testing (or pen testing) could imitate some attacks by spies and would find technical points of your IT infrastructure vulnerabilities in which spies can make a way through, gain access to your network, and steal data.
Continuous Improvement: TSCM Advantage
The circle of spying is changing permanently, brand new technologies and ways are appearing at the time. Henceforth, it assumes a major objective to retain the commitment to unremitting improvement of the TSCM process.
Stay Informed: The Tribal Security and Countering Terrorism (TSCM) team should be enlightened on the dreadful espionage threats and technological advancements in their field that are rapidly arising. Industry publications, conferences, and training can give rise to insights in the industry.
Regular Reviews: Undertake TSCM program auditing frequently to determine whether your system works and to find areas for improvement. Apart from that, the threat assessment may need to be reassessed and corresponding inspection procedures revised based on the latest intelligence.
Embrace New Technologies: Due to the fact that technology is definitely upgrading, so too should your TSCM program. Due to a high level of ingenuity on both sides, detection devices and counteraction techniques are increasing all the time. For this purpose, it is wise to have financial resources allocated towards these developments to stay on the cutting edge.
Conclusion
An efficient TSCM program, composed of both a detailed plan and an attitude of constant evolution, can give you a major boost in how well you're secured from corporate espionage. While you have to guard your company's confidentiality, it is not a one-time endeavor, but the dynamic and continued process towards it demands vigilance and different strategic approaches to be taken to make sure it is securely protected. Implementing a preventive TSCM strategy constitutes an important investment in maintaining your core competencies and a standard success track for your enterprise.
Read the full article
#benefitsofTSCM#corporateespionage#HowtoimplementaTSCMprogram#intellectualpropertyprotection#TSCMadvantage#TSCMforbusinesses#TSCMprogram#TSCMvs.datasecurity
0 notes